DDoS(Distributed Denial of Service)attack defensive system for application layer based on multiple feature recognition
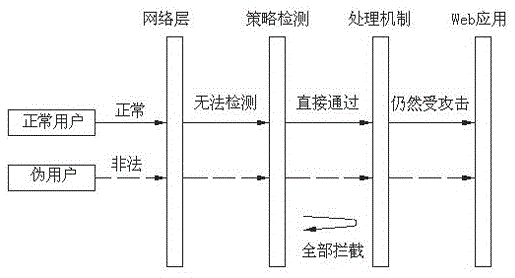
An attack defense system and multiple features technology, applied in the field of comprehensive DDoS defense algorithms, can solve the problems of inability to prevent application layer attacks, limited computing resources, single firewall detection mechanism, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] The technical scheme of the patent of the present invention will be described in further detail below in conjunction with specific embodiments.
[0015] see figure 1 and Figure 4 , an application layer DDoS attack defense system based on multiple feature recognition, the technical solution of this patent will be further described in detail below in conjunction with specific implementation methods.
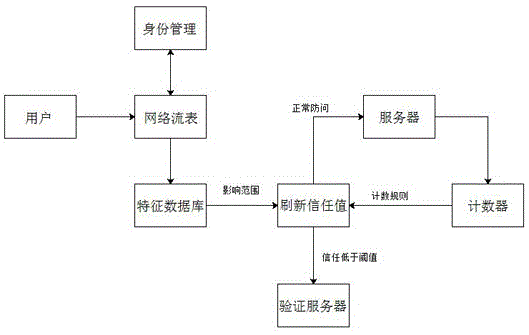
[0016] When a user initiates a request, the system stores the user data packet information into the net-node network flow table, analyzes and processes the user data packet, and records its last access time, source address, destination address, destination port, and sending data. and the size of the received data packet to determine whether the source is authentic and reliable; insert a verification data when returning data to the user, and check whether the source is authentic and reliable again. After confirming that the source is authentic, add the user to the white li...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com