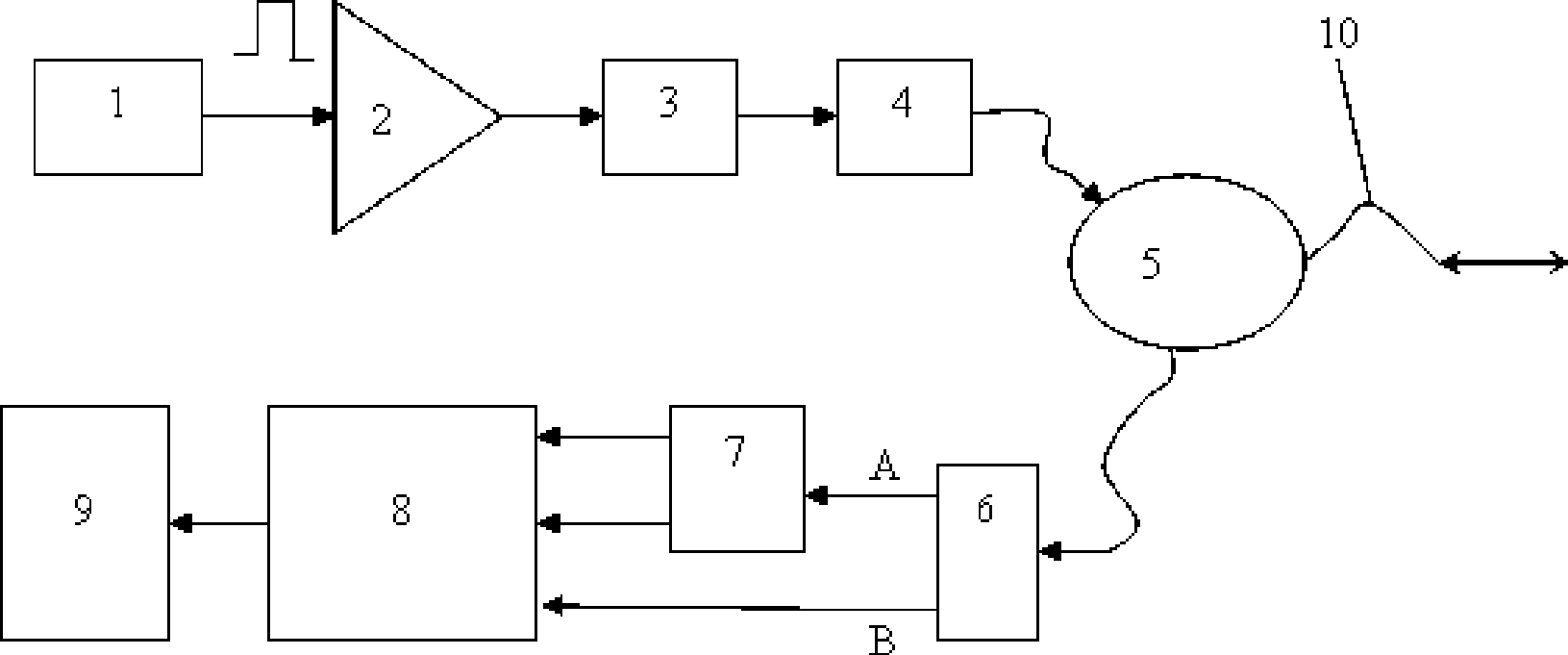
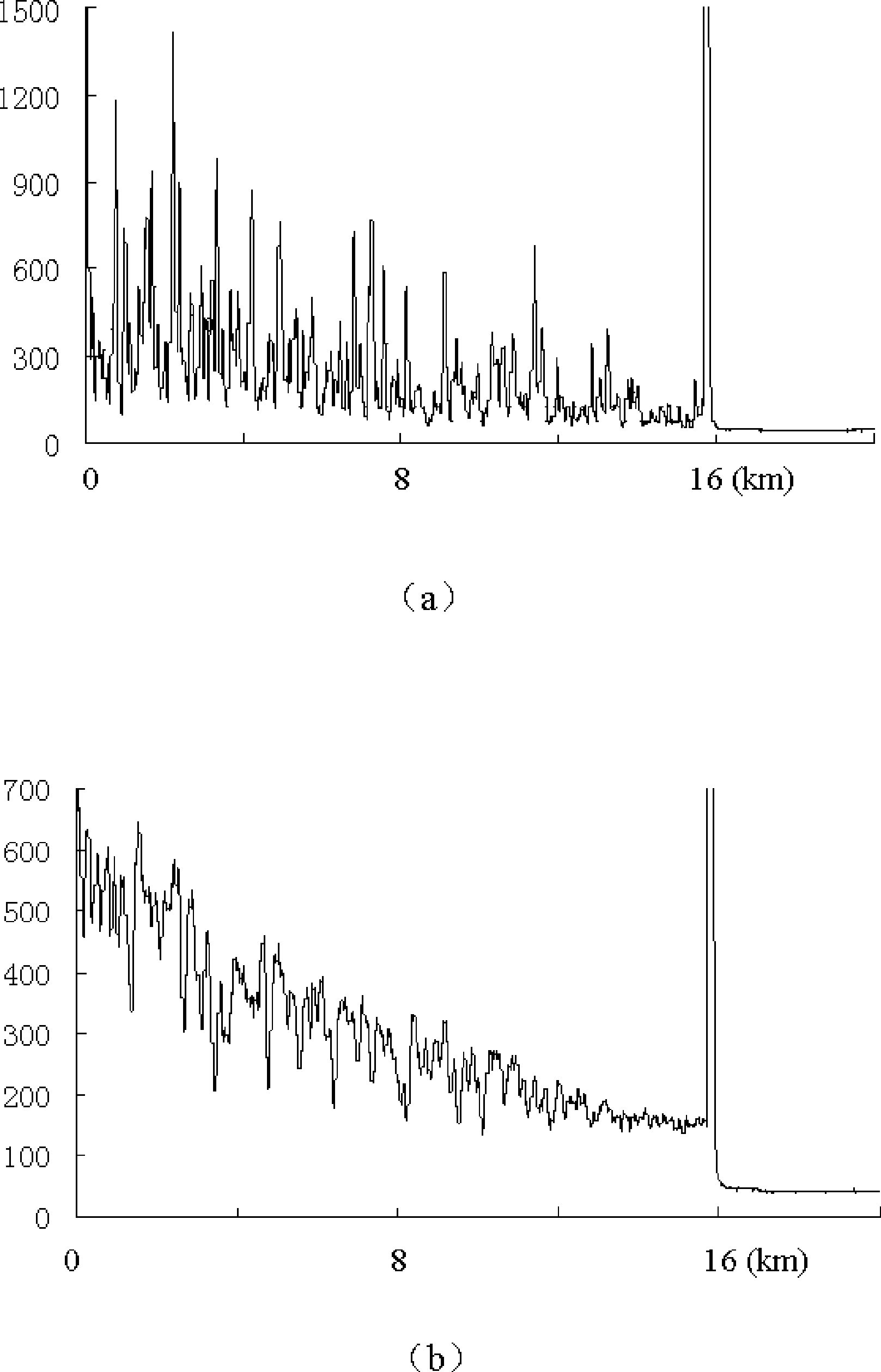
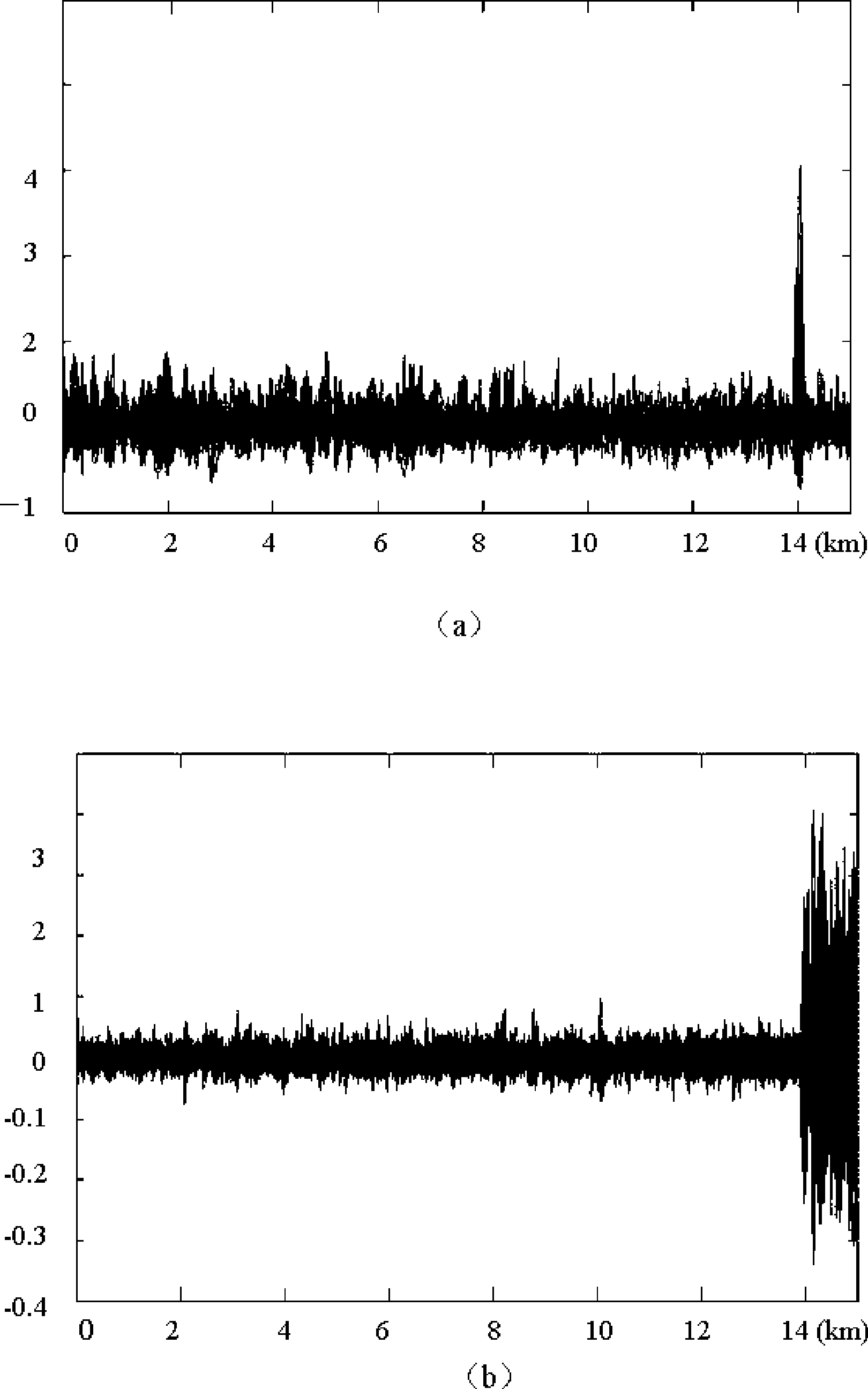
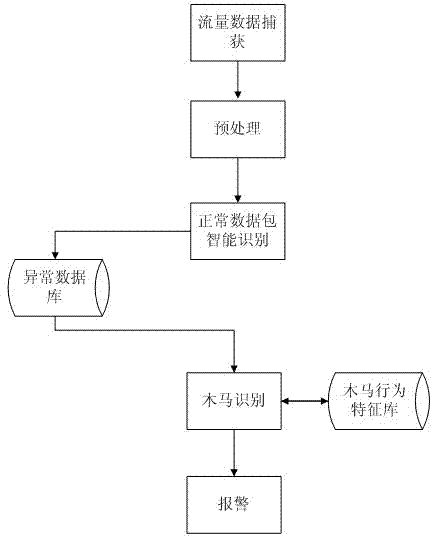
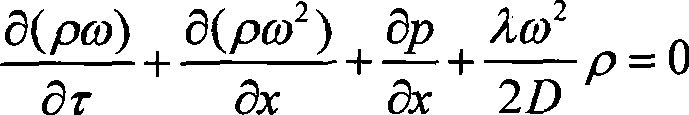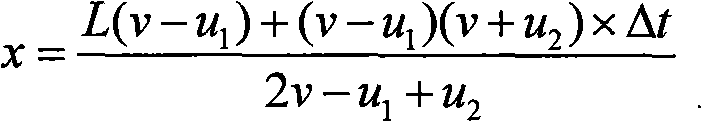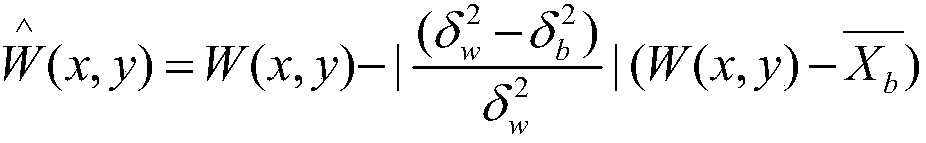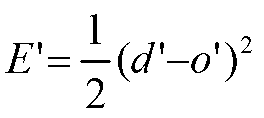Patents
Literature
424 results about "Reporting rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Uncertainty as to relative under-reporting plagues the comparisons of spontaneous reporting rates as a tool for decision-making in pharmacovigilance. However, it is generally accepted that under-reporting should be reasonably similar for similar drugs sharing the same indication, country and period ...
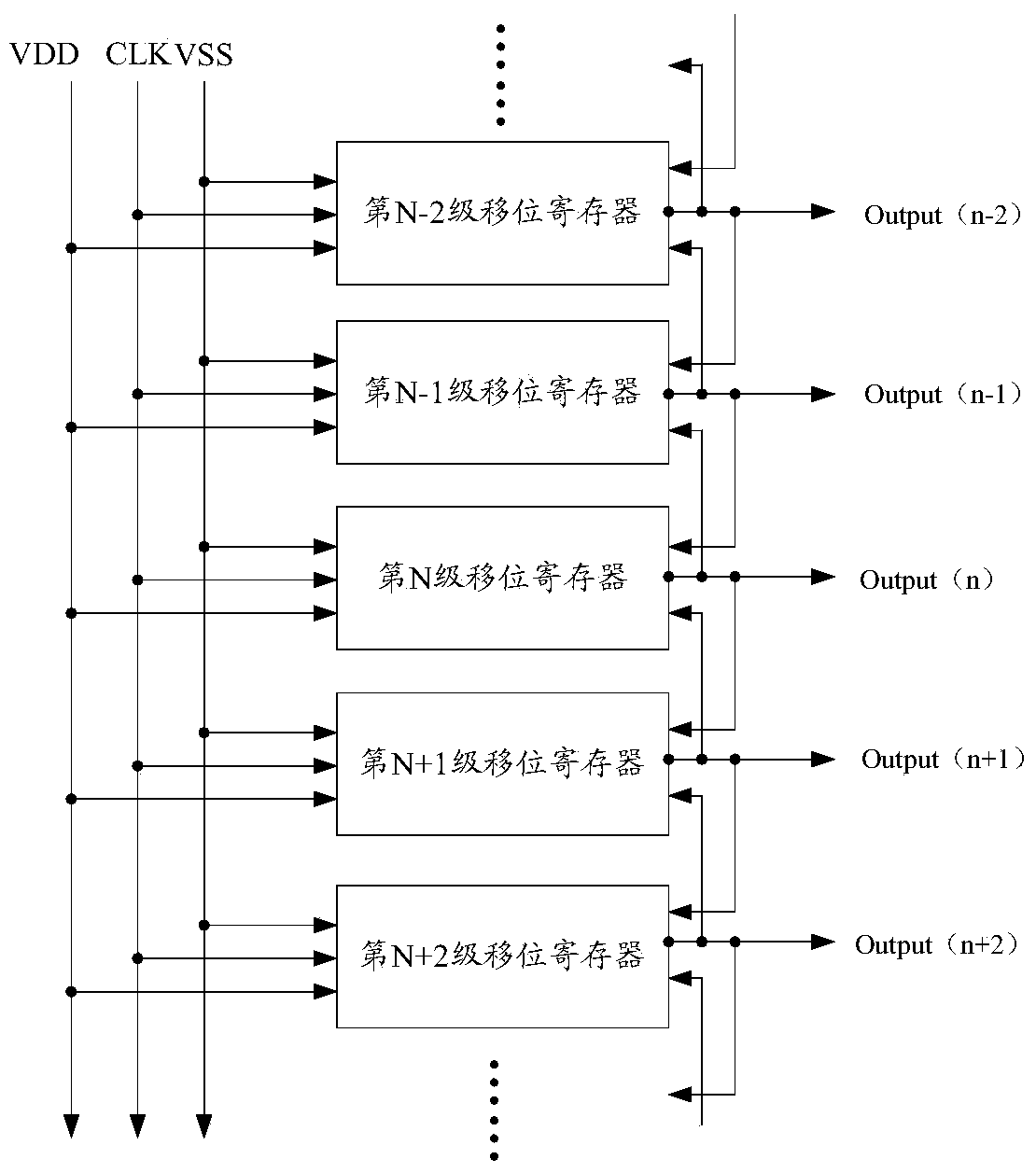
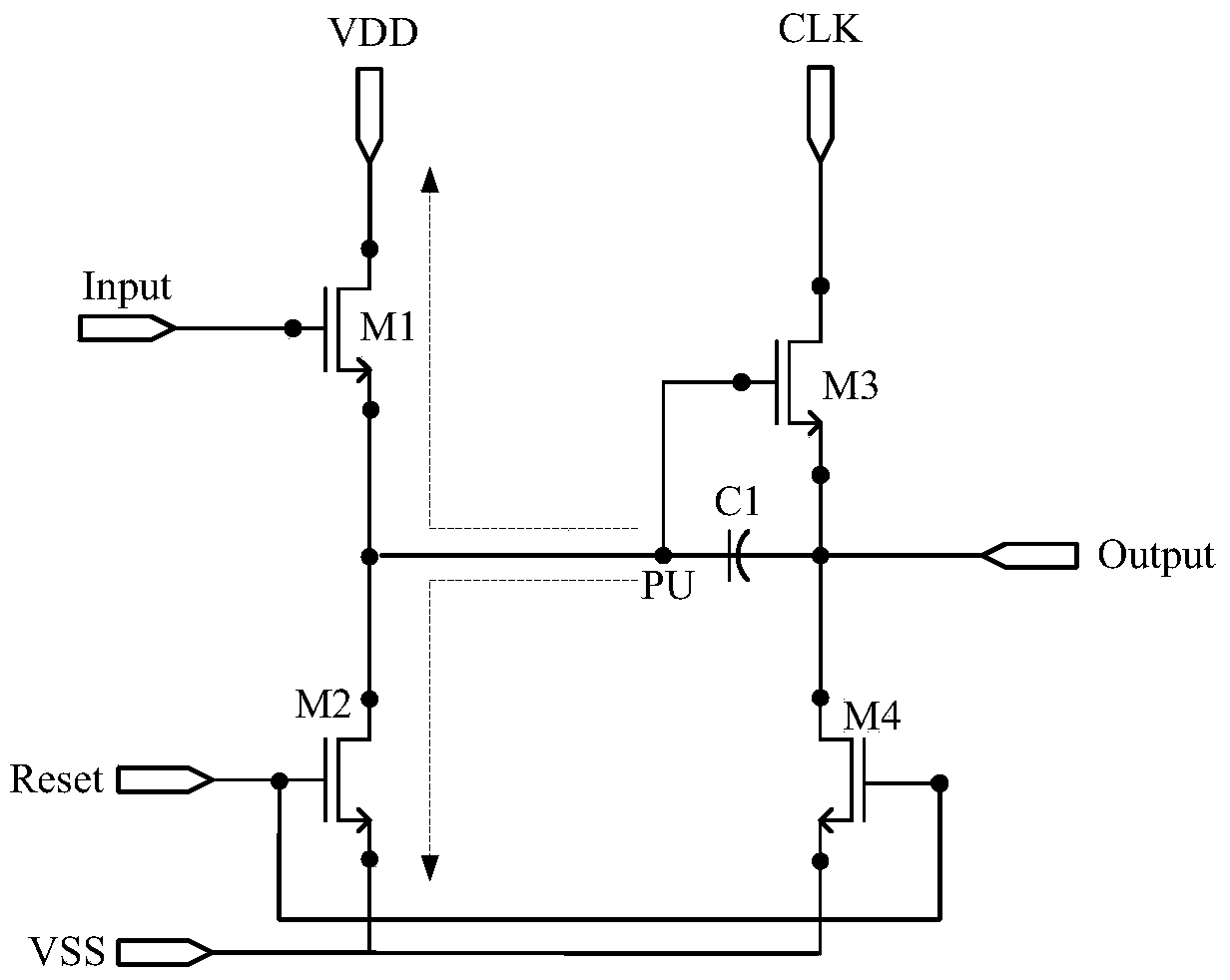
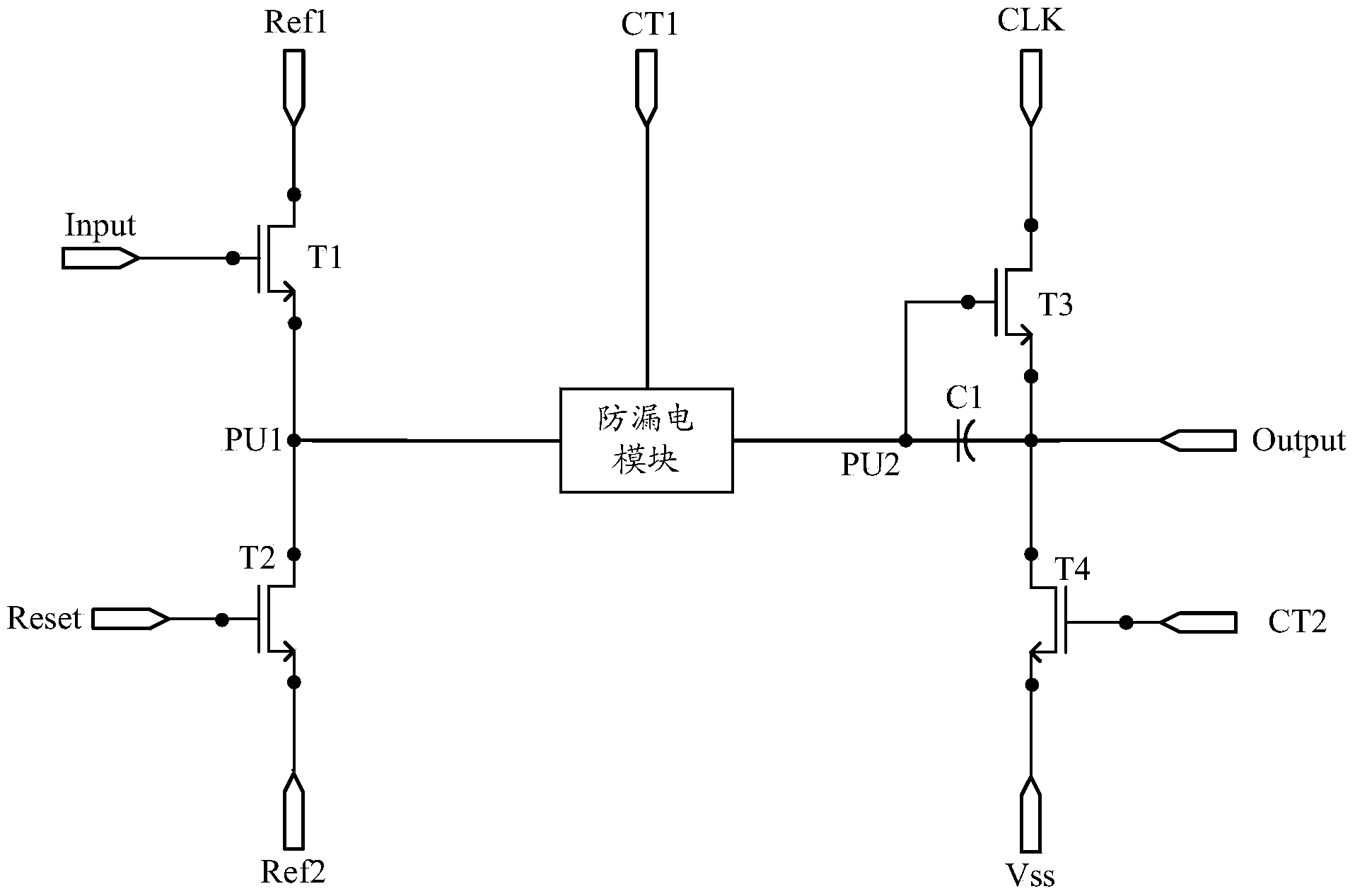
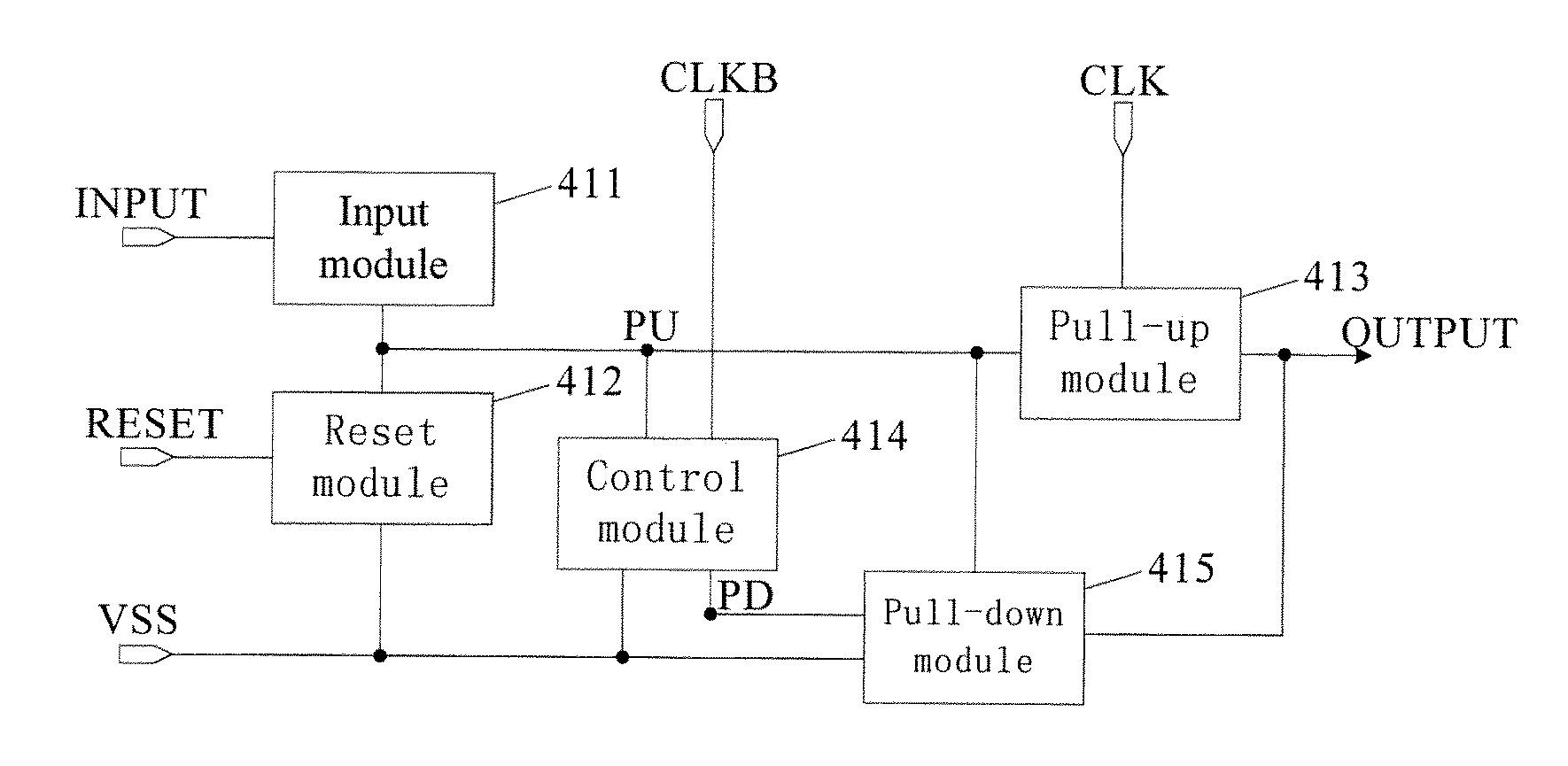
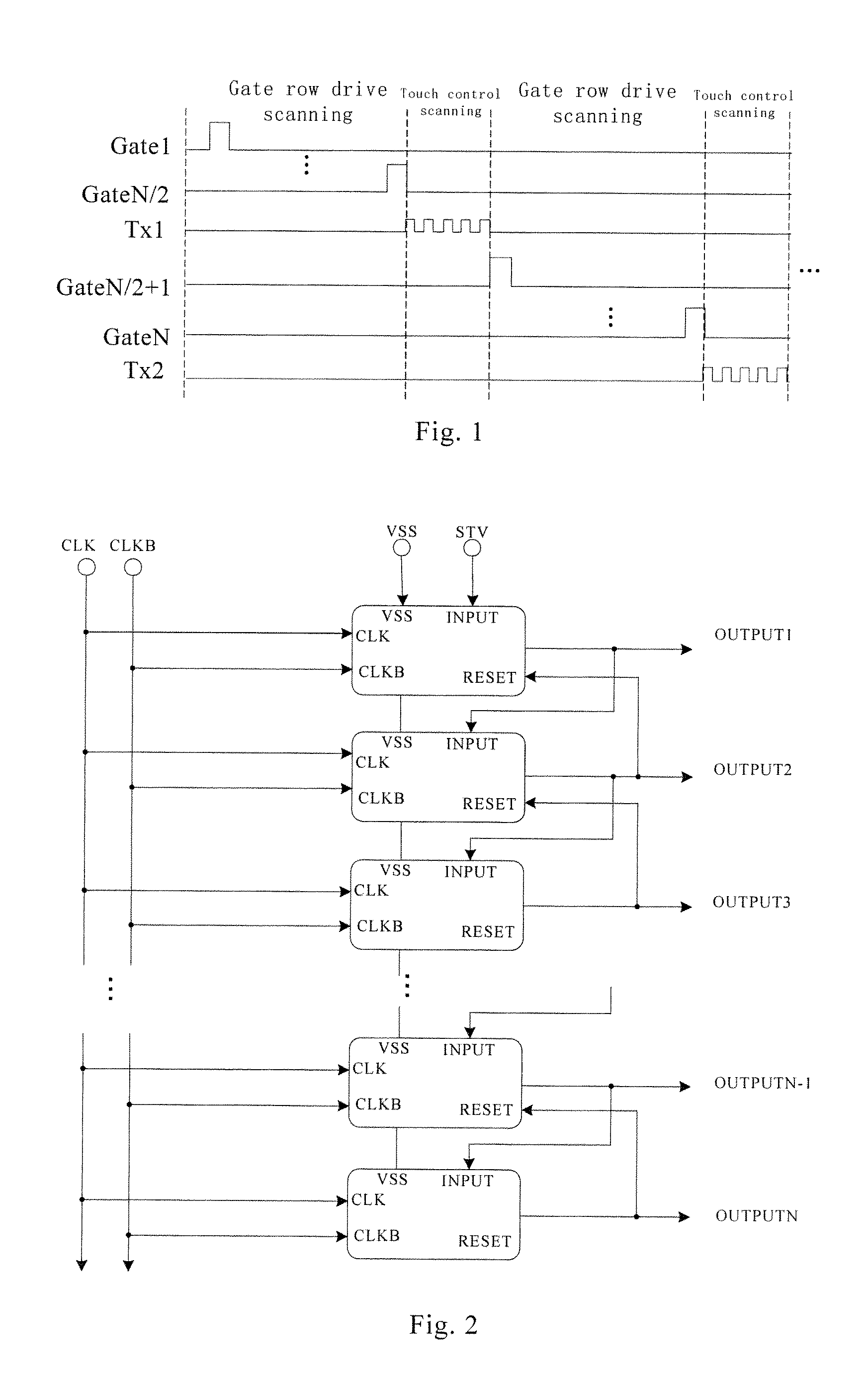
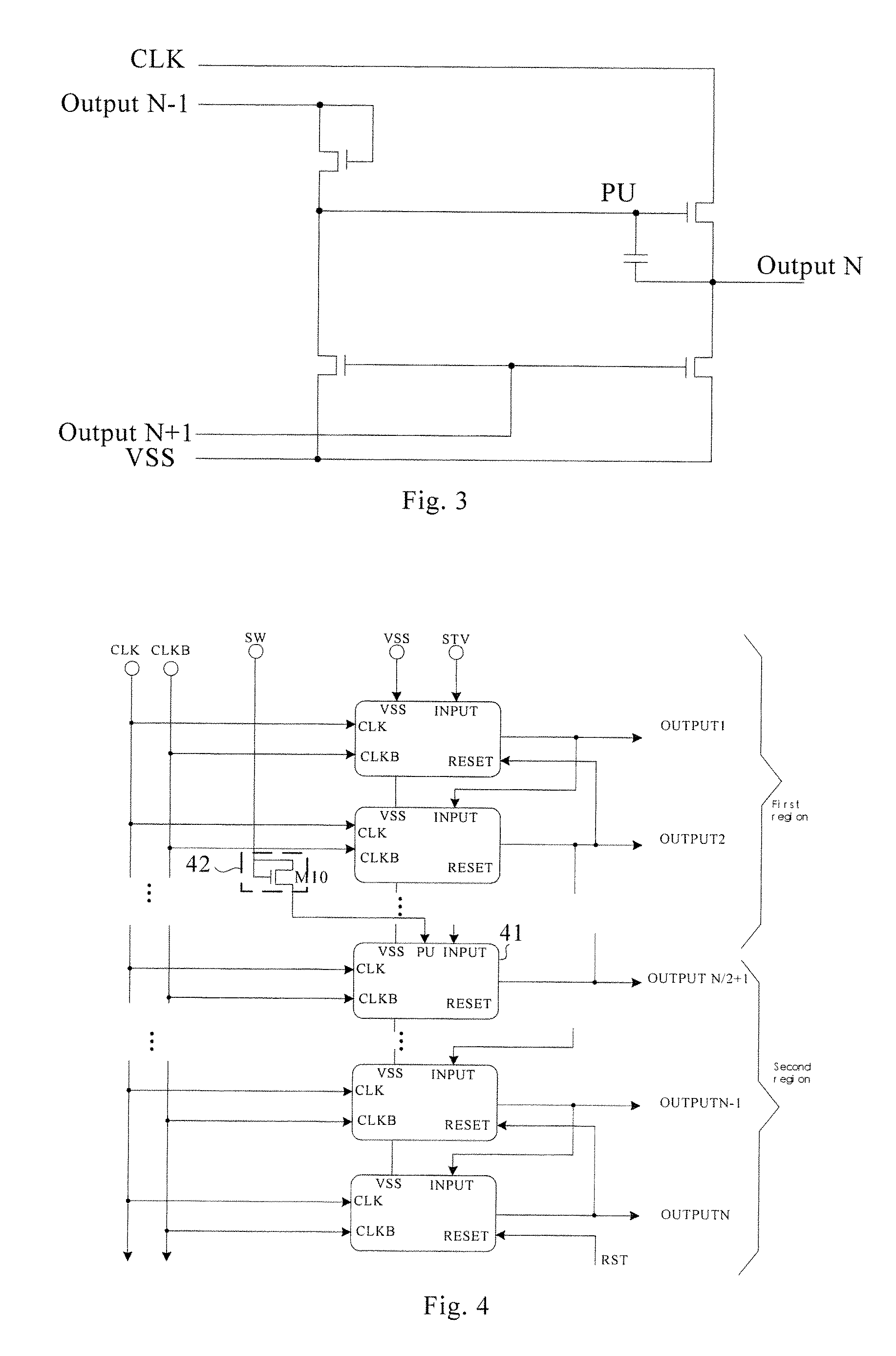
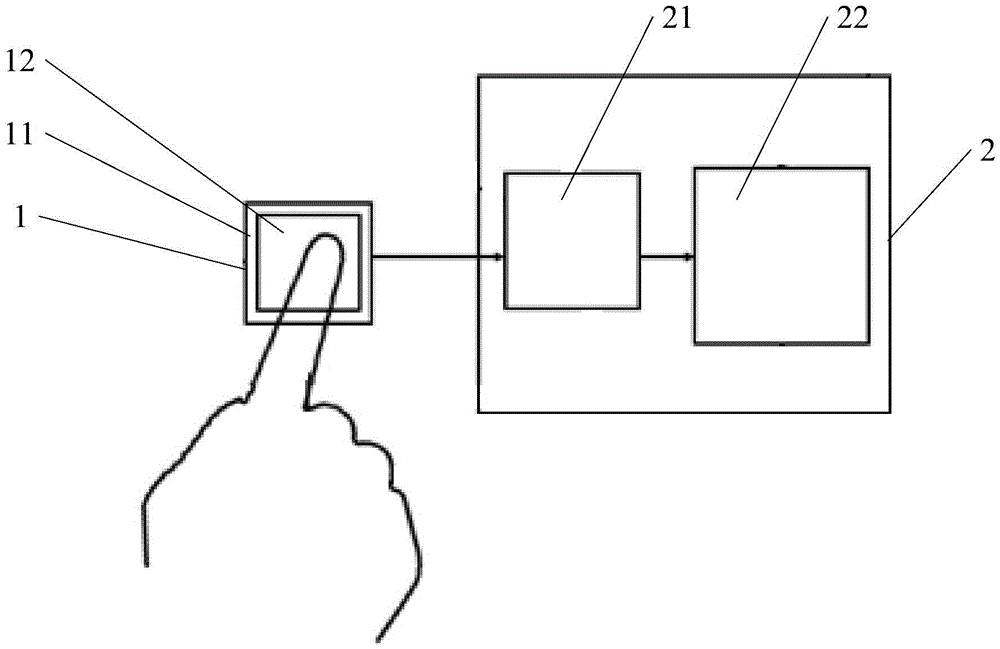
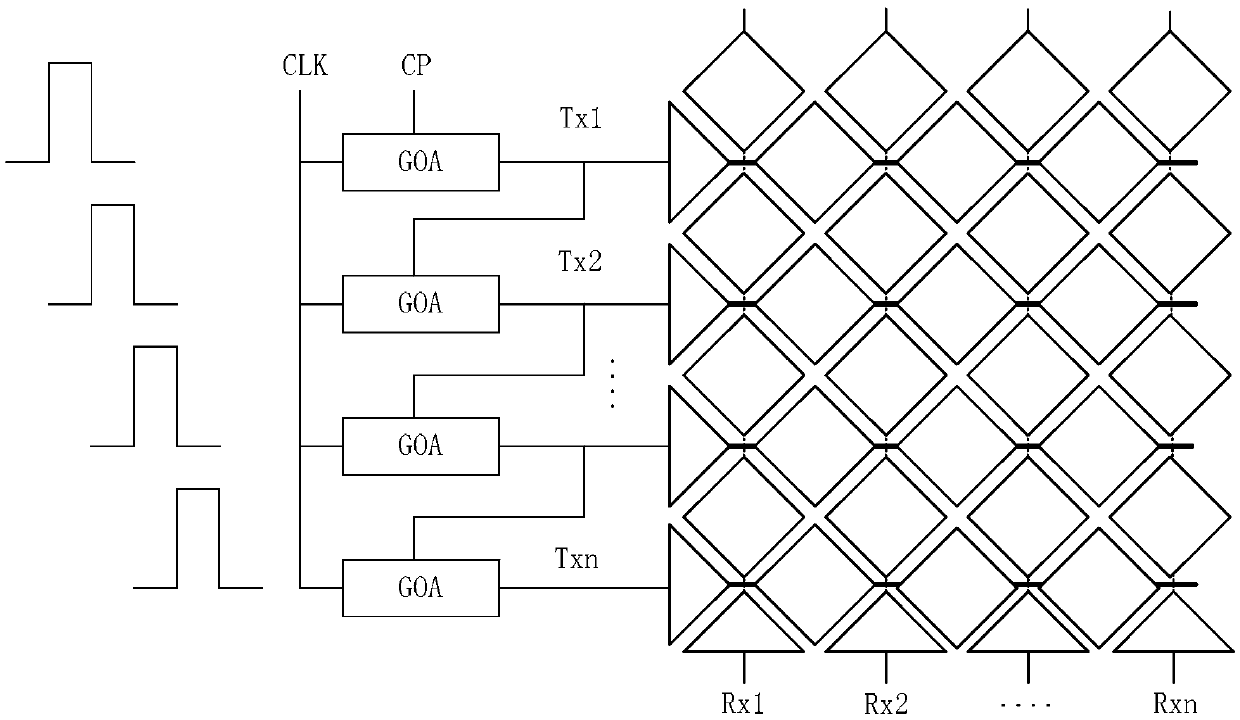
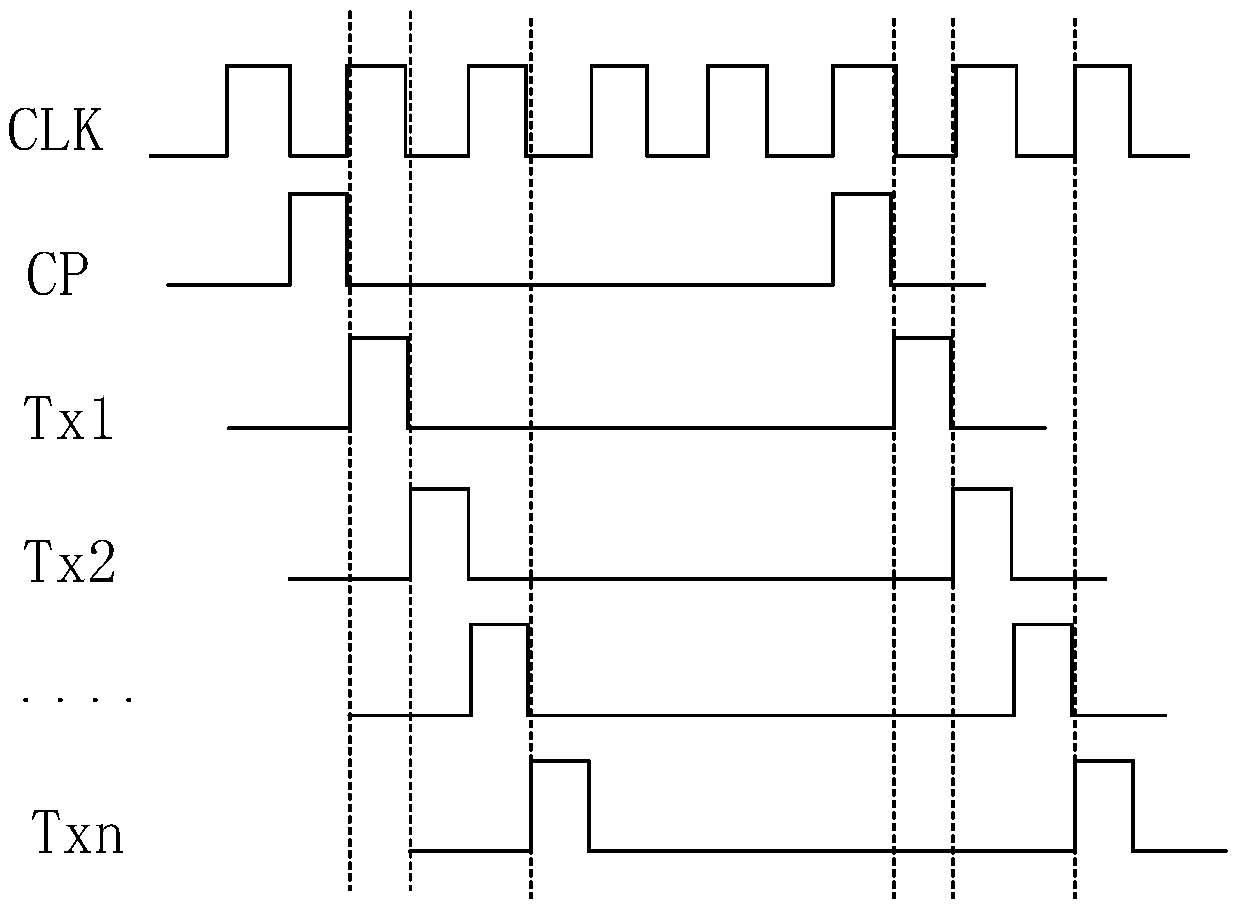
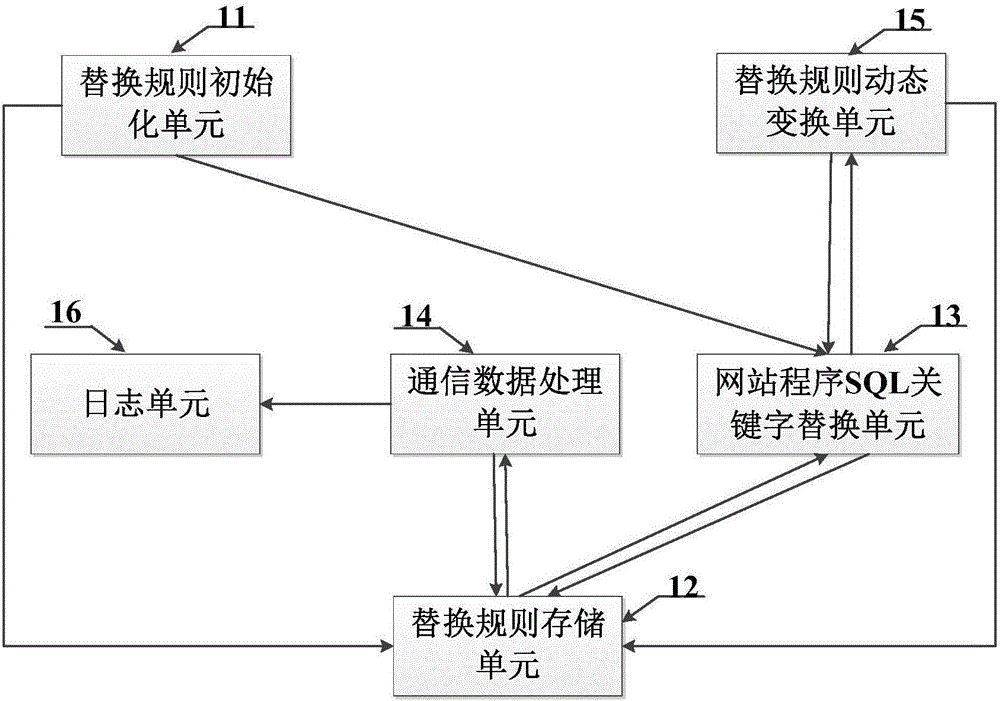
Shifting register, grid integration drive circuit and display screen
ActiveCN104021769AShorten the timeReduce leakage speedStatic indicating devicesDigital storageCapacitanceShift register
The invention discloses a shifting register, a grid integration drive circuit and a display screen. The joint of a source of a first thin film transistor and a drain of a second thin film transistor is set as a first upward-pull node, the joint of a capacitor and a grid of a third thin film transistor is set as a second upward-pull node, and a electric leakage prevention module is added between the first upward-pull node and the second upward-pull node; the first upward-pull node and the second upward-pull node are connected in display time duration of a frame through the electric leakage prevention module under the control of a display control signal end so that a grid startup signal can be normally outputted by the shifting register; the first upward-pull node and the second upward-pull node are disconnected in the touch control time duration of the frame, that is, a resistor with large resistance is connected to a discharge path of the capacitor in series, and therefore time of the capacitor for discharge can be greatly shortened, the electric leakage speed of the capacitor is effectively decreased, and the problem that normal display may not be achieved when the capacitor is applied to a touch screen with high report rate is solved.
Owner:BOE TECH GRP CO LTD +1
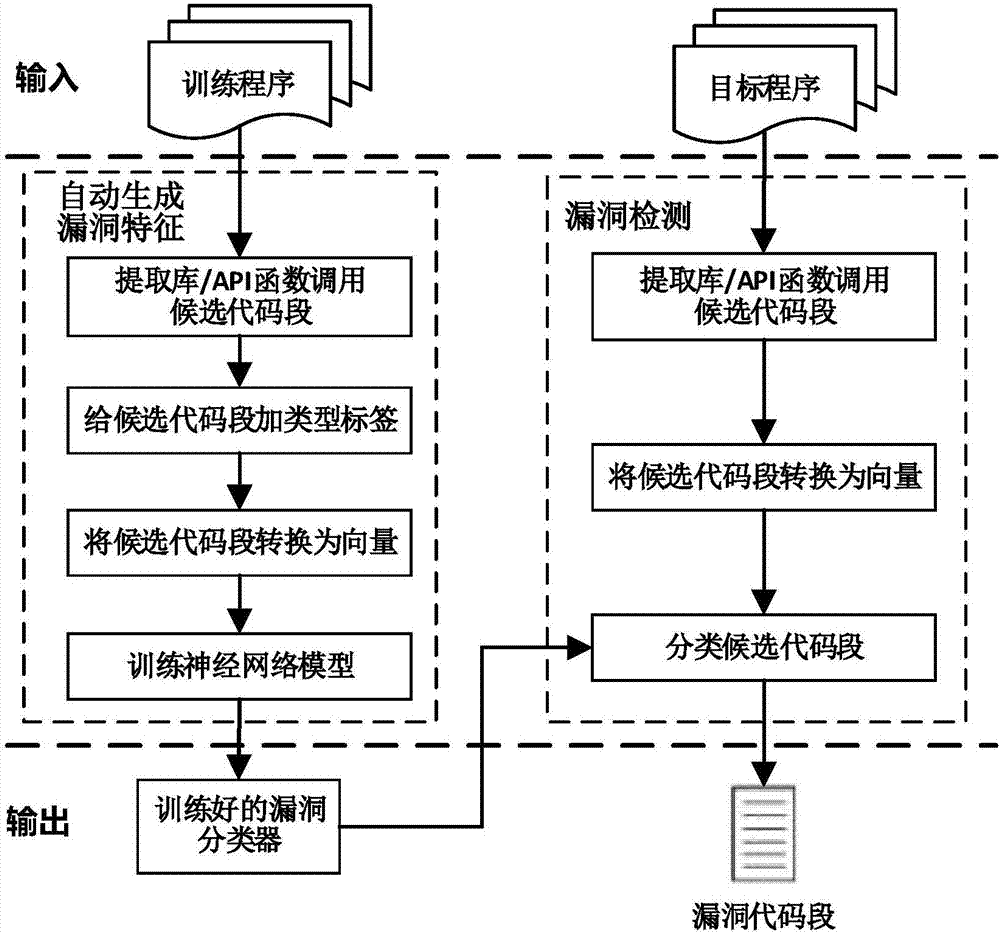
Deep learning-based vulnerability detection method and system
ActiveCN107885999AUnlimited Vulnerability TypeImprove accuracyPlatform integrity maintainanceLearning basedTraining program
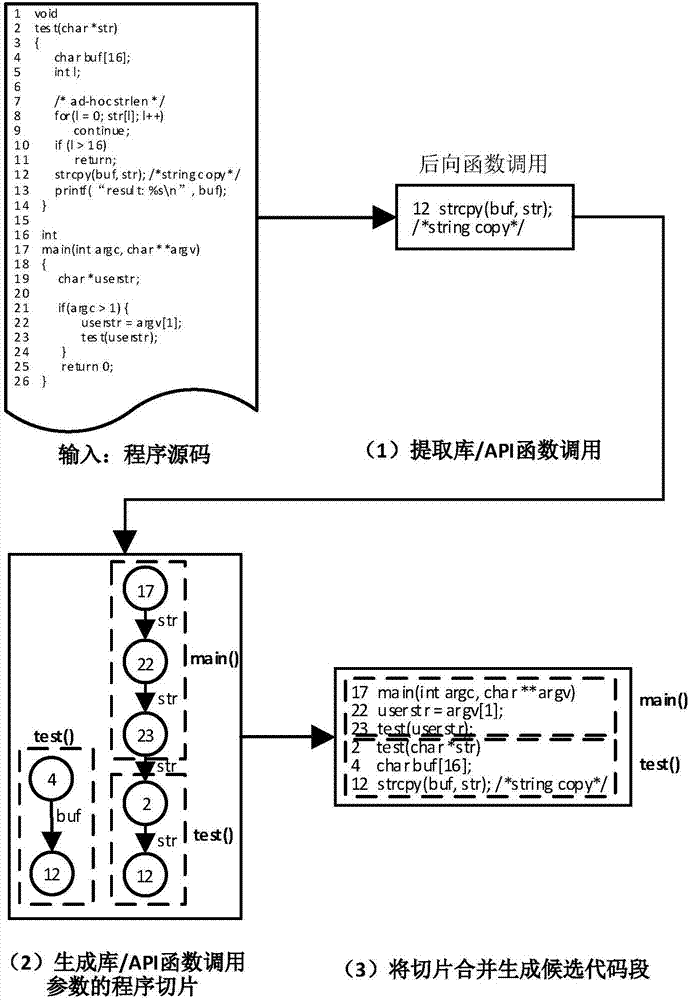
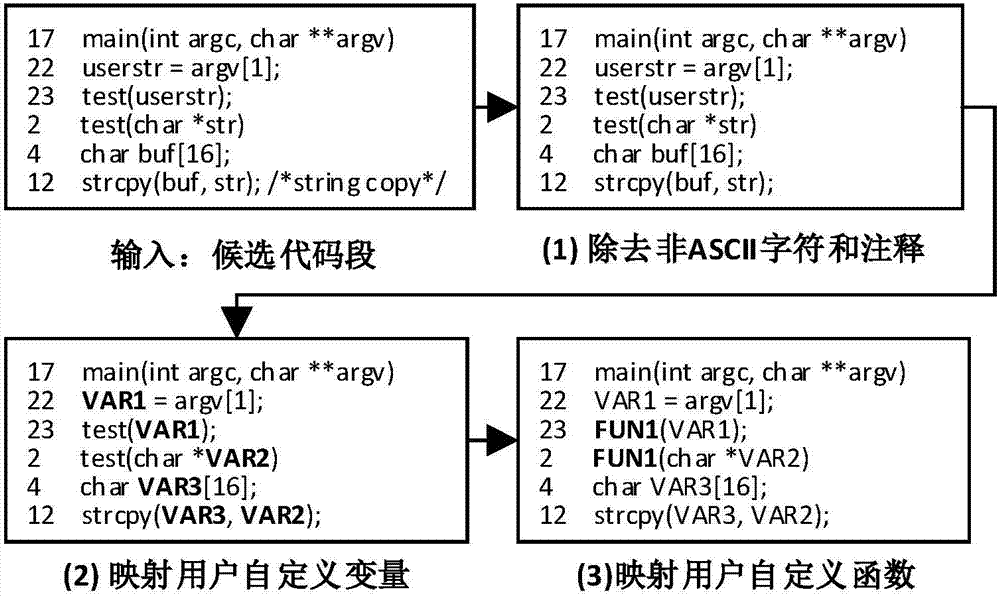
The invention discloses a deep learning-based vulnerability detection method and system. The method comprises an offline vulnerability classifier training part and an online vulnerability detection part. The offline vulnerability classifier training part comprises the following steps of: calling candidate code sections for a training program extraction library / API function; adding type label for the candidate code sections; converting the candidate code sections into vectors; inputting the vectors into a neural network model to carry out training; and finally outputting a vulnerability classifier. The online vulnerability detection part comprises the following steps of: calling candidate code sections for a target program extraction library / API function; converting the candidate code sections into vectors; classifying the candidate code sections by adoption of the trained vulnerability classifier; and finally outputting the code sections which contain online vulnerabilities in the classification result. According to the method and system, vulnerability features aiming at library / API function calling can be automatically generated, and the operation does not depend on expert knowledges and is not restricted to vulnerability types, so that the false report rate and missing report rate of vulnerability detection in target programs can be remarkably reduced and vulnerability positions can be given.
Owner:HUAZHONG UNIV OF SCI & TECH
Airport target tracking system
ActiveUS20100231721A1Easy to operateHighly robust redundant designImage enhancementImage analysisError reportingVision based
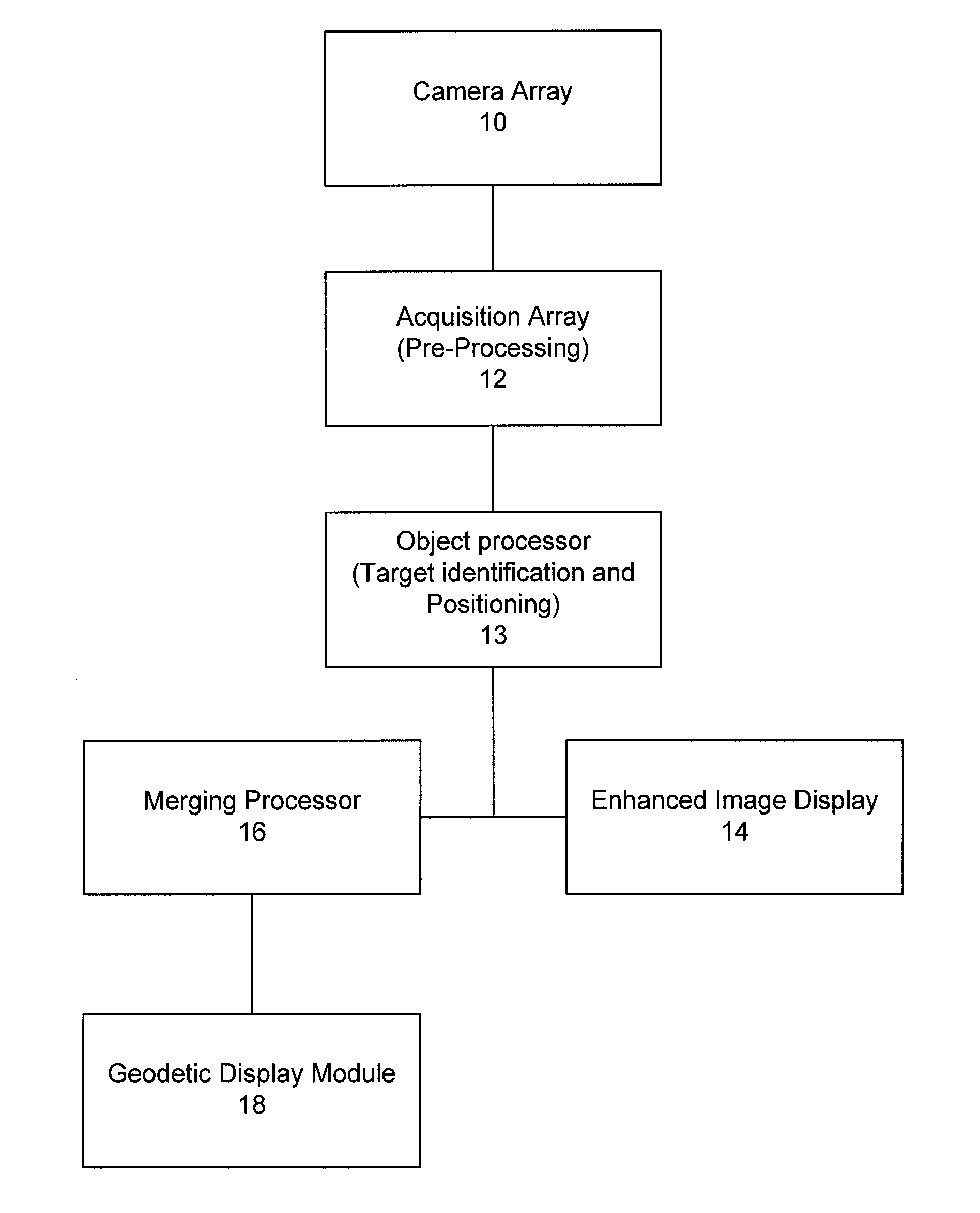
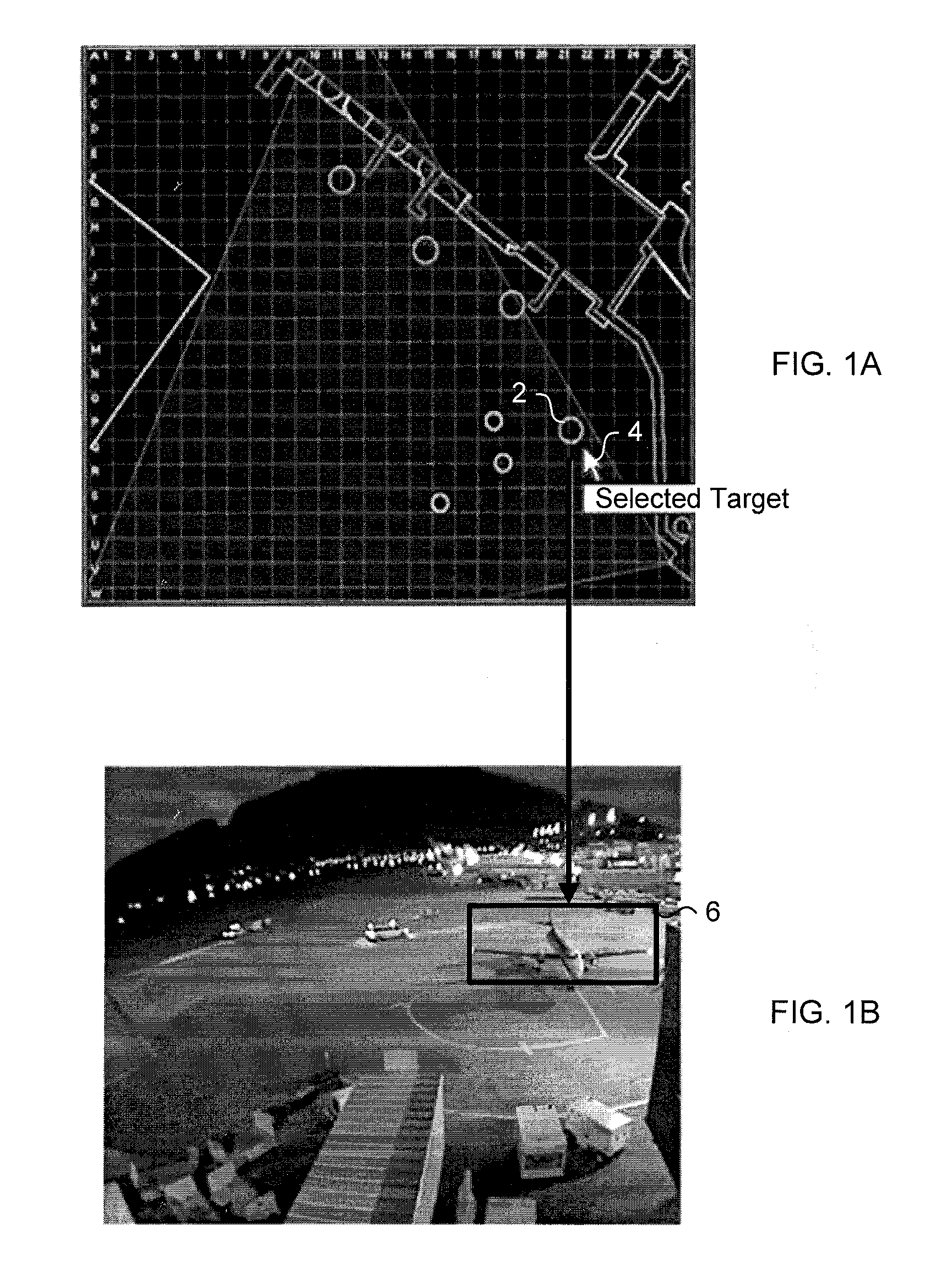
A system for tracking objects using an Intelligent Video processing system in the context of airport surface monitoring. The system addresses airport surface monitoring operational issues such as all weather conditions, high robustness, and low false report rate. The output can be used to complement existing airport surface monitoring systems. By combining the use of multi-sensors and an adverse weather optimized system, the system is capable of producing an improved stream of information for the target object over traditional computer vision based airport surface monitoring systems.
Owner:SEARIDGE TECH
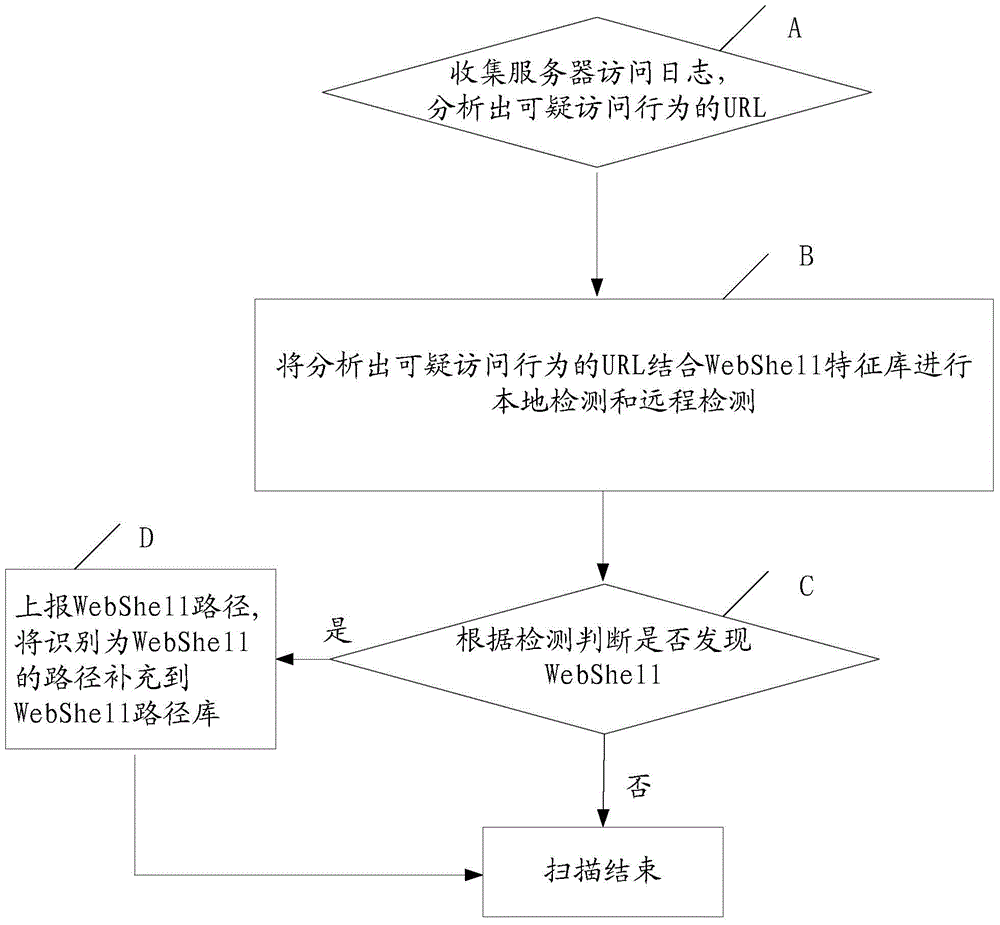
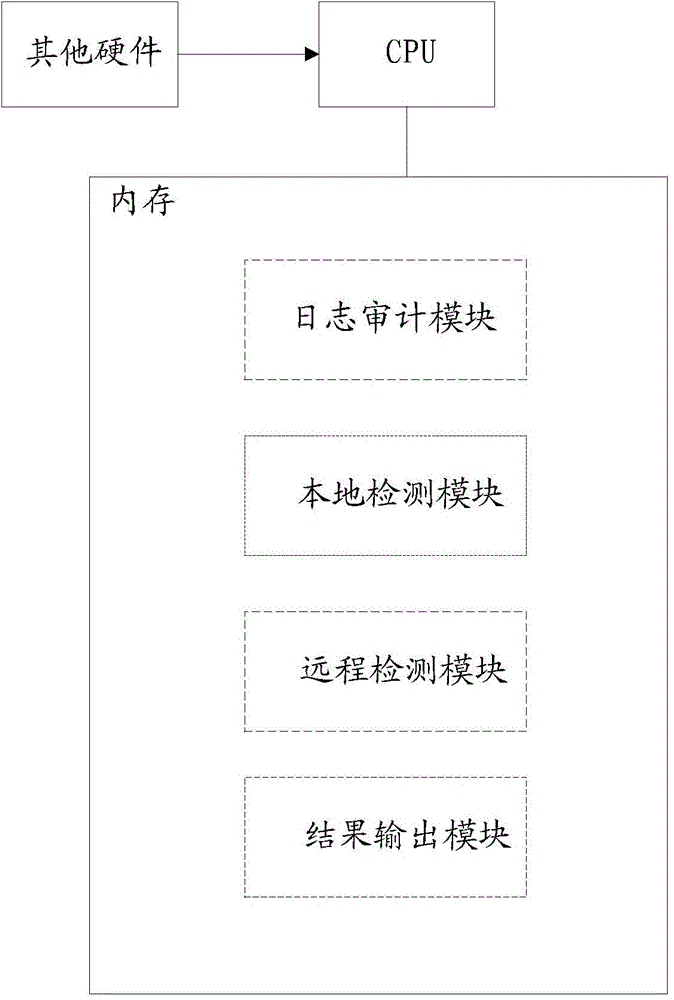
WebShell detection method and system
ActiveCN104468477AImprove accuracyImprove the detection rateTransmissionWeb applicationUniform resource locator
The invention provides a WebShell detection method and system. The system comprises a log auditing module, a local detection module, a remote detection module and a result output module. The system executes the following processing flow: A, collecting a server access log, and analyzing a URL (Uniform Resource Locator) with suspicious access behaviors; B, performing local detection and remote detection on the analyzed URL with suspicious access behaviors in combination with a WebShell feature library; C, and performing judgment according to the detection, reporting a WebShell path if WebShell is found, and meanwhile adding the path identified as WebShell into a WebShell path library. Through adoption of the method and the system, the detection rate and detection efficiency of WebShell detection in network Web application are increased, and the missing report rate and false report rate are lowered.
Owner:杭州迪普信息技术有限公司
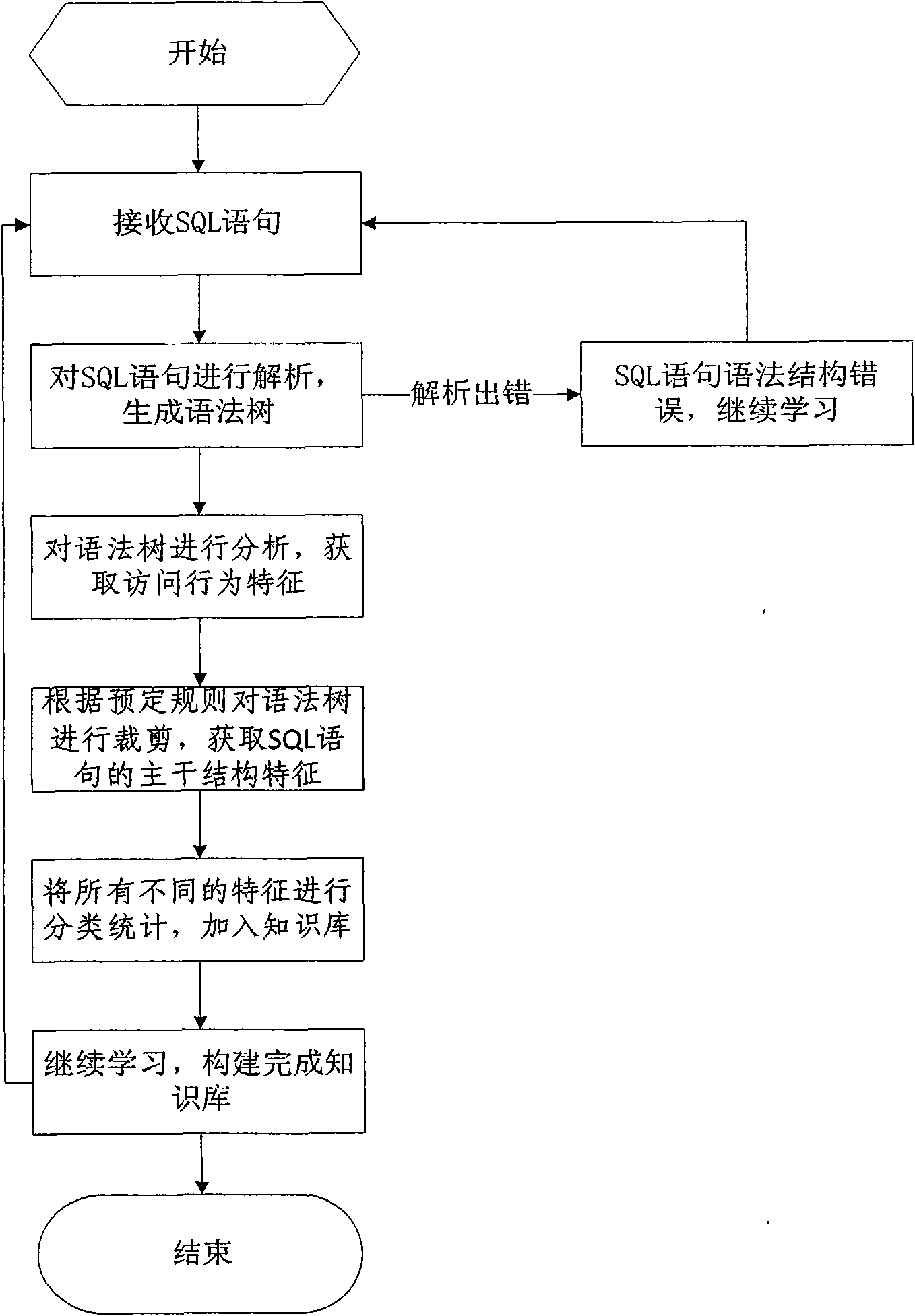
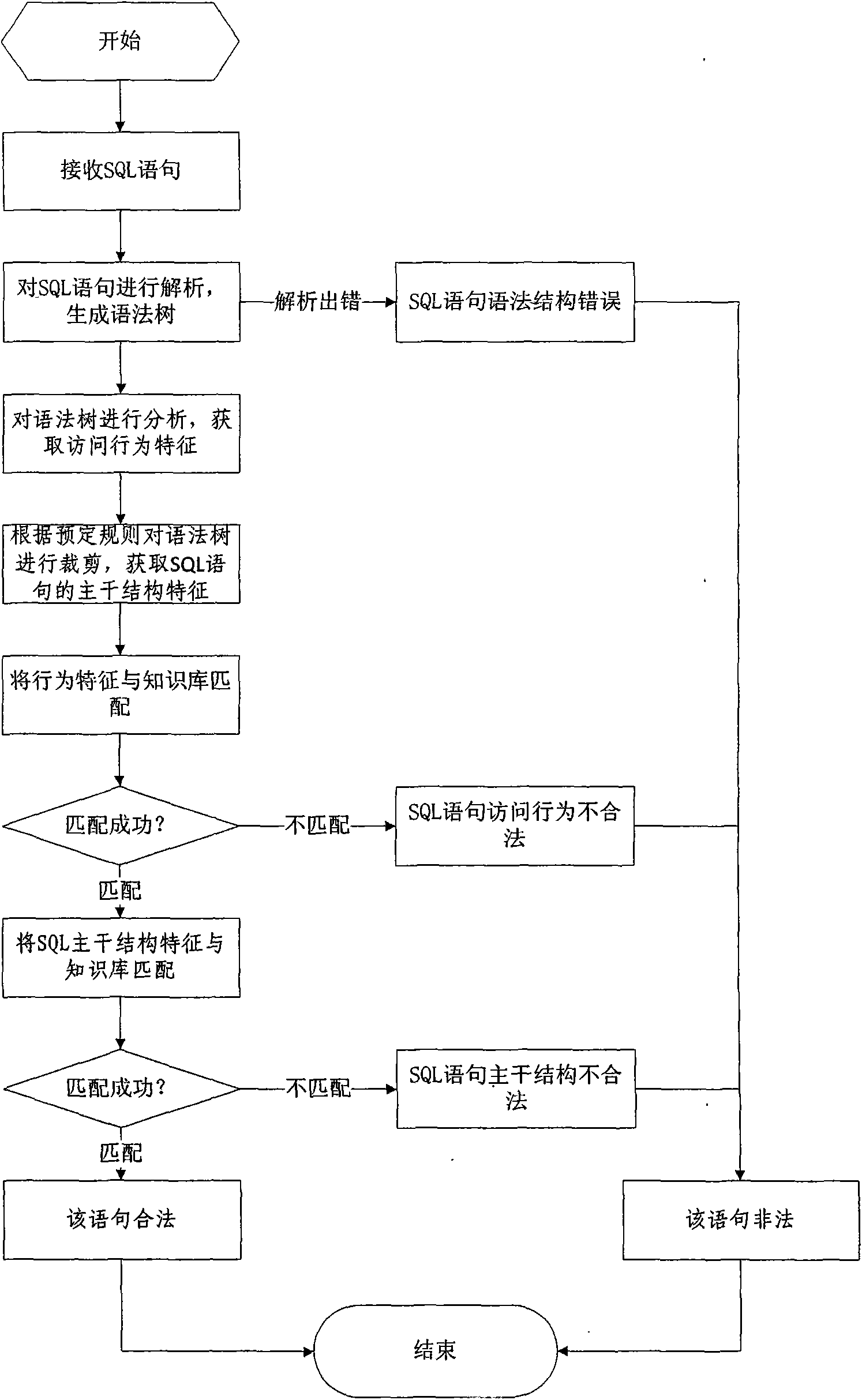
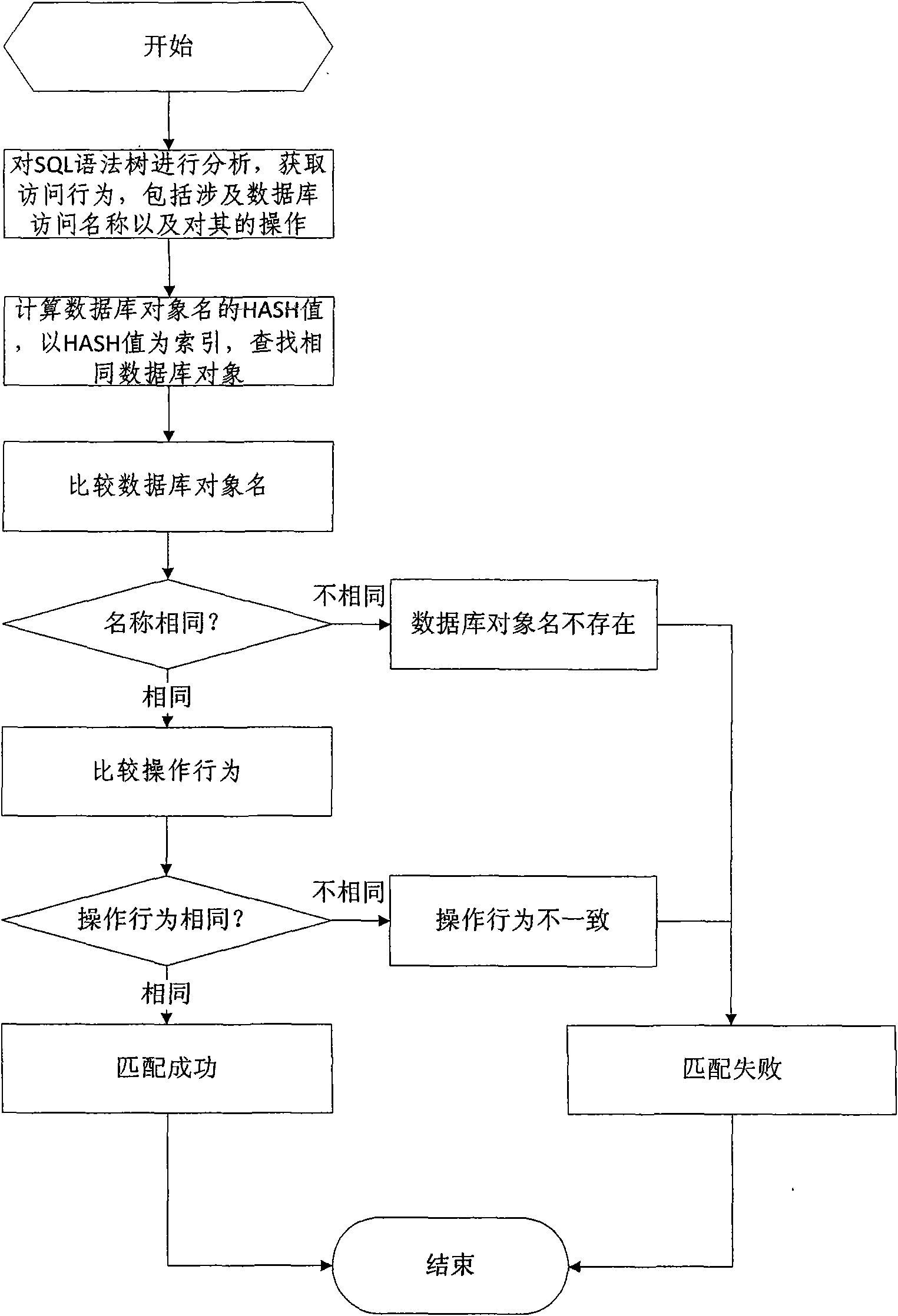
Database SQL infusion protecting method based on self-learning
InactiveCN101609493AOvercome false negativesOvercome the False Positive FlawComputing modelsDigital data protectionLearning basedSQL injection
The invention discloses a database SQL infusion protecting method based on self-learning, comprising a learning phase and a filtering phase. The learning phase works in safe environment. At the moment, all SQL sentences are legitimate SQL sentences generated by an application system. A knowledge model (knowledge base) of the legitimate SQL sentences can be constituted by analyzing the sentences as well as analyzing and summarizing the characteristics of the sentences on the basis of sentence analysis results. The filtering phase works in real environment. At the moment, all SQL sentences are assumed to be possibly illegitimate SQL sentences. The sentences undergo pattern matching with the knowledge base established in the safe environment. If the matching is successful, the sentences are legitimate SQL sentences, otherwise, the sentences are illegitimate SQL sentences. The database SQL infusion protecting method has the advantage that an SQL infusion protecting system based on learning the legitimate SQL sentences can greatly reduce the false report rate and missing report rate which are caused by traditional SQL infusion protection, and the defending capability of the whole system can be improved.
Owner:STATE GRID ELECTRIC POWER RES INST +1
Method for performing gas pipeline leakage position by using instant change on-line diagnosis coupling excitation frequency response
InactiveCN101413628ARealize online real-time detectionReduce false alarm ratePipeline systemsEngineeringPressure response
The invention provides a method which uses transient online diagnosis coupling frequency response to position the leakage of natural gas pipeline, and relates to a natural gas pipeline failure detection and positioning method which can solve the problems that the existing method for detecting and positioning the leakage of the natural gas pipeline can not detect in real time, has long detection period, low positioning precision and high error report rate; real-time pressure value and real-time flux value are respectively collected at the upstream and downstream of the pipeline; the real-time downstream pressure value and the real-time flux value when the pipeline runs stably are reduced by the practical real-time pressure value and the practical real-time flux value at the downstream; if both of the two differences exceed the valve value, the leakage is considered to occur, otherwise the values are collected again; an excitation pressure wave is generated at the downstream end of the pipeline and the wave speed of the response wave of the excitation pressure wave is gained; according to the wave speed of the excitation pressure response wave and the time difference when the excitation pressure response wave is transmitted to the upstream and the downstream, the position of the leakage point is gained. The measurement and collection of the values are completed by normal equipments and the method can be used both in the built pipeline or pipelines under construction.
Owner:HARBIN INST OF TECH
Method for measuring and locating leakage of gas pipelines
ActiveCN101625071ARealize the monitoring functionRealize the positioning functionPipeline systemsData acquisitionEngineering
The invention discloses a method for measuring and locating leakage of a gas pipeline network based on a geographic information system (GIS) and supervisory control and data acquisition technology (SCADA). The specific method comprises the following steps of establishing a gas pipeline network GIS system; reading and storing a pipe network graph, pipeline network attribute data and the like; collecting parameters of pressure, temperature and flow for each section of gas pipeline in real time by the SCADA system; comparing the collected parameters and the stored data and calculating; calculating the measuring values of the head end and the tail end of the pipeline and calculating the difference among parameter values; representing the abnormal pipeline information; searching extreme points and determining the pressure catastrophe points; calculating the position of the leakage point according to the parameters of gas consumption, temperature and pressure by using a leakage locating formula. By adopting SCADA, GIS and simulation calculations, the invention can realize self monitoring and locating of the gas pipelines with the advantages of quick measuring speed, high measuring precision, low missing report rate and false report rate and the like.
Owner:TIANJIN UNIV
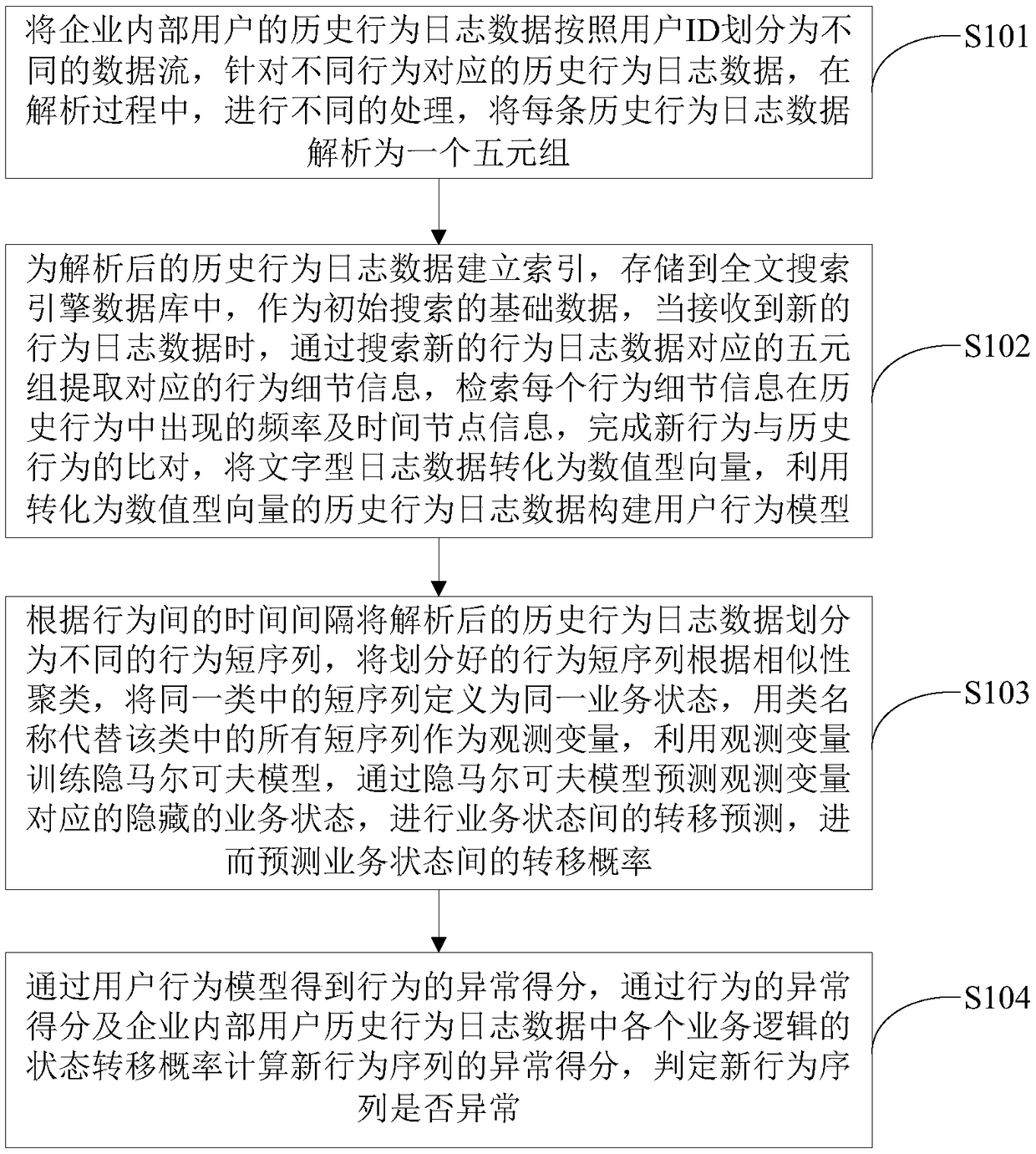
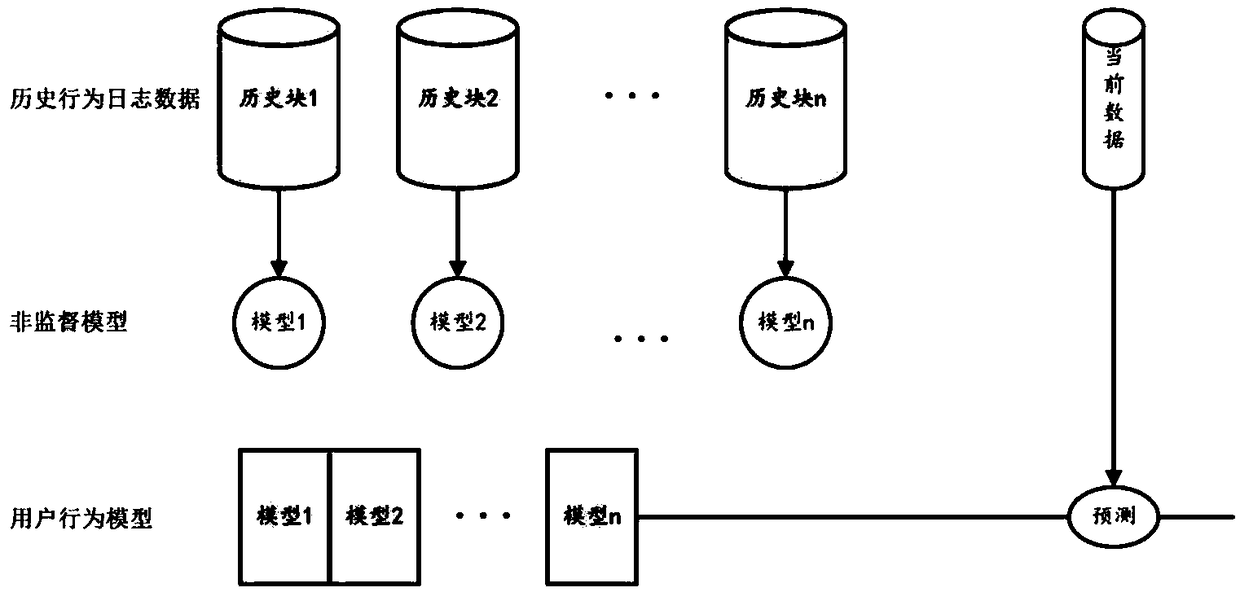
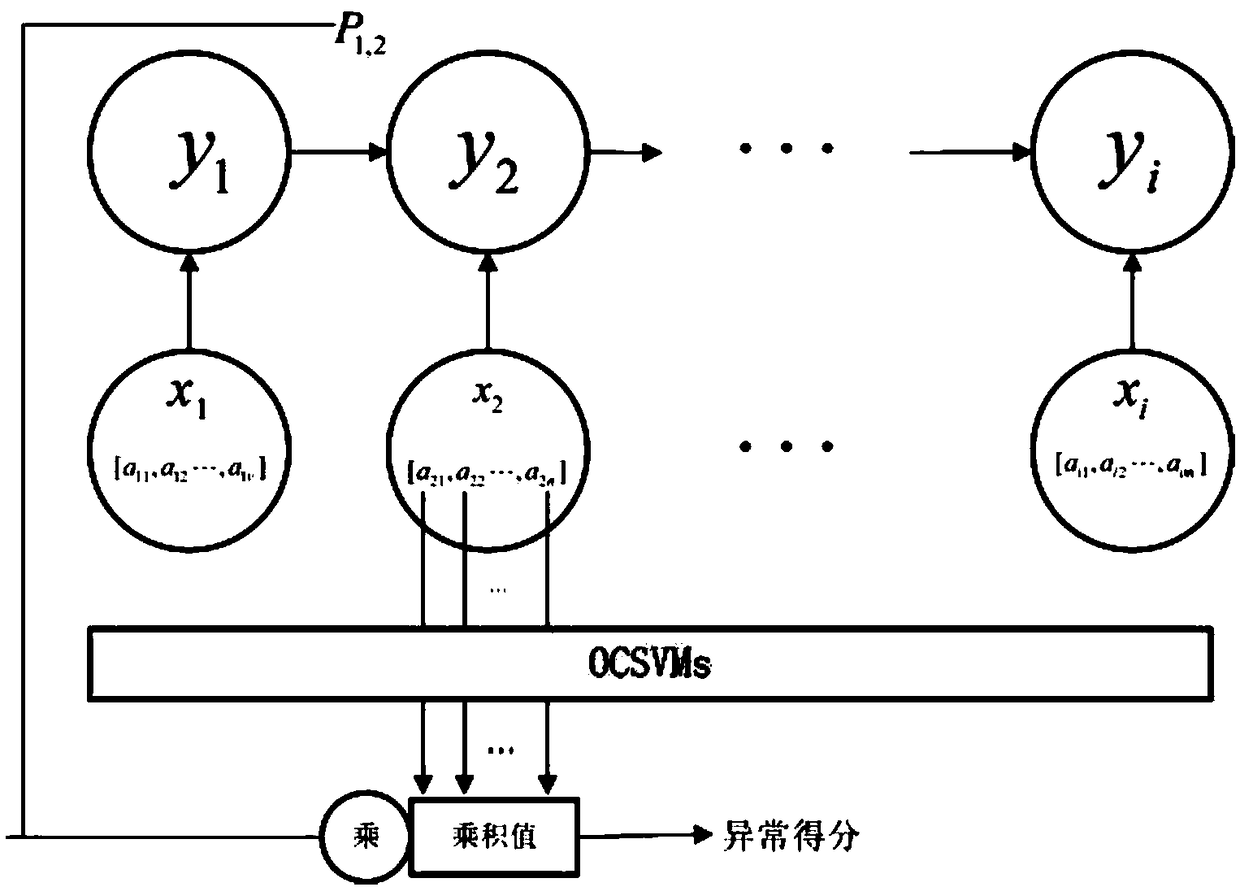
Enterprise internal user abnormal behavior detection method and device
ActiveCN108881194ATake advantage ofSolve the problem of missing detailsCharacter and pattern recognitionTransmissionInternet privacyAnomalous behavior
The invention relates to the technical field of network security, in particular to an enterprise internal user abnormal behavior detection method and device, discloses an enterprise internal user abnormal behavior detection method, and further discloses an enterprise internal user abnormal behavior detection device. The enterprise internal user abnormal behavior detection device comprises a behavior log acquiring and preprocessing module, a behavior detail modeling module, a service state transfer prediction module and a malicious behavior score discrimination module. According to the enterprise internal user abnormal behavior detection method and device, an unsupervised machine learning method is used, a user behavior model is built by fully utilizing unmarked unhistorical behavior log data in an enterprise, the accurate rate of abnormal behavior detection is increased, the false reporting rate and the missing reporting rate are decreased, and an effective means is provided for detecting enterprise internal threats.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +2
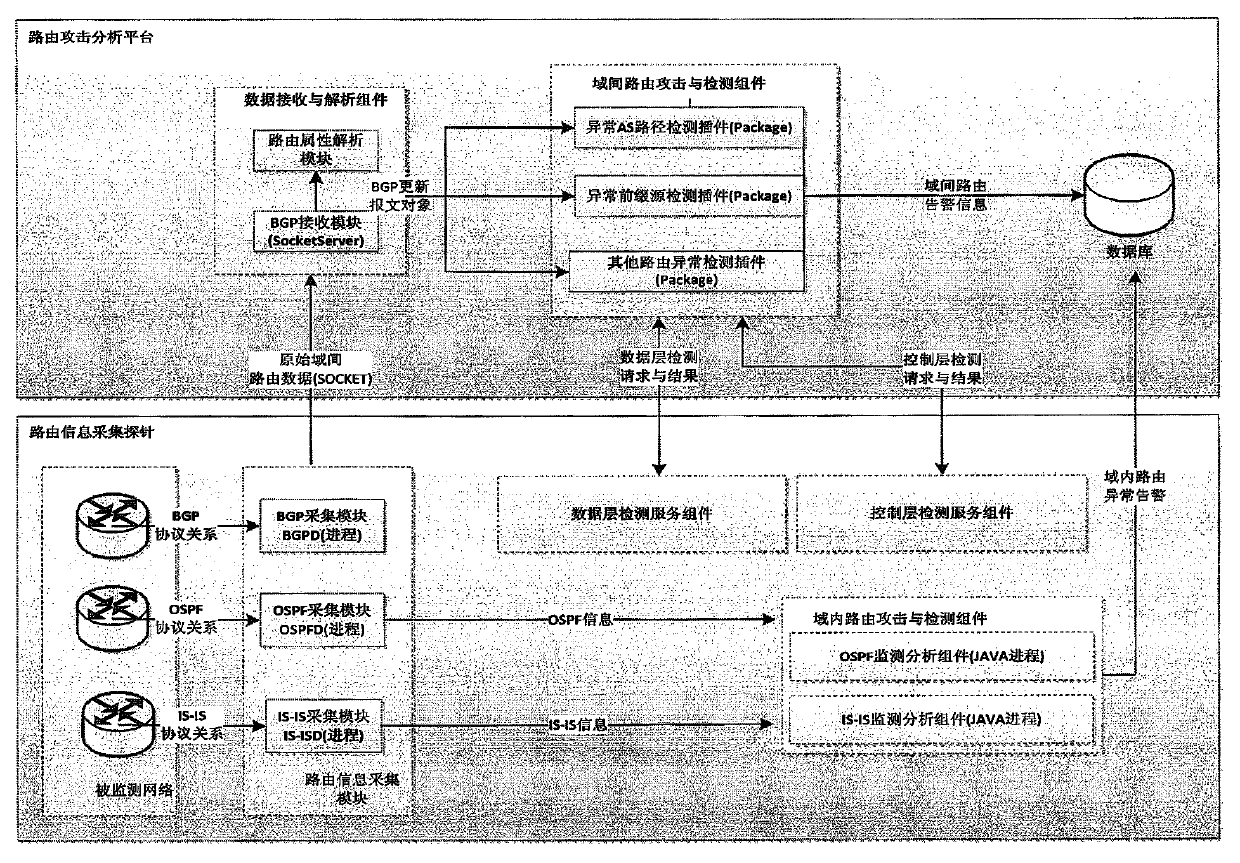
System and method for detecting routing security
ActiveCN103442008AReduce false negative rateReduce false alarm rateData switching networksIp addressComputer science
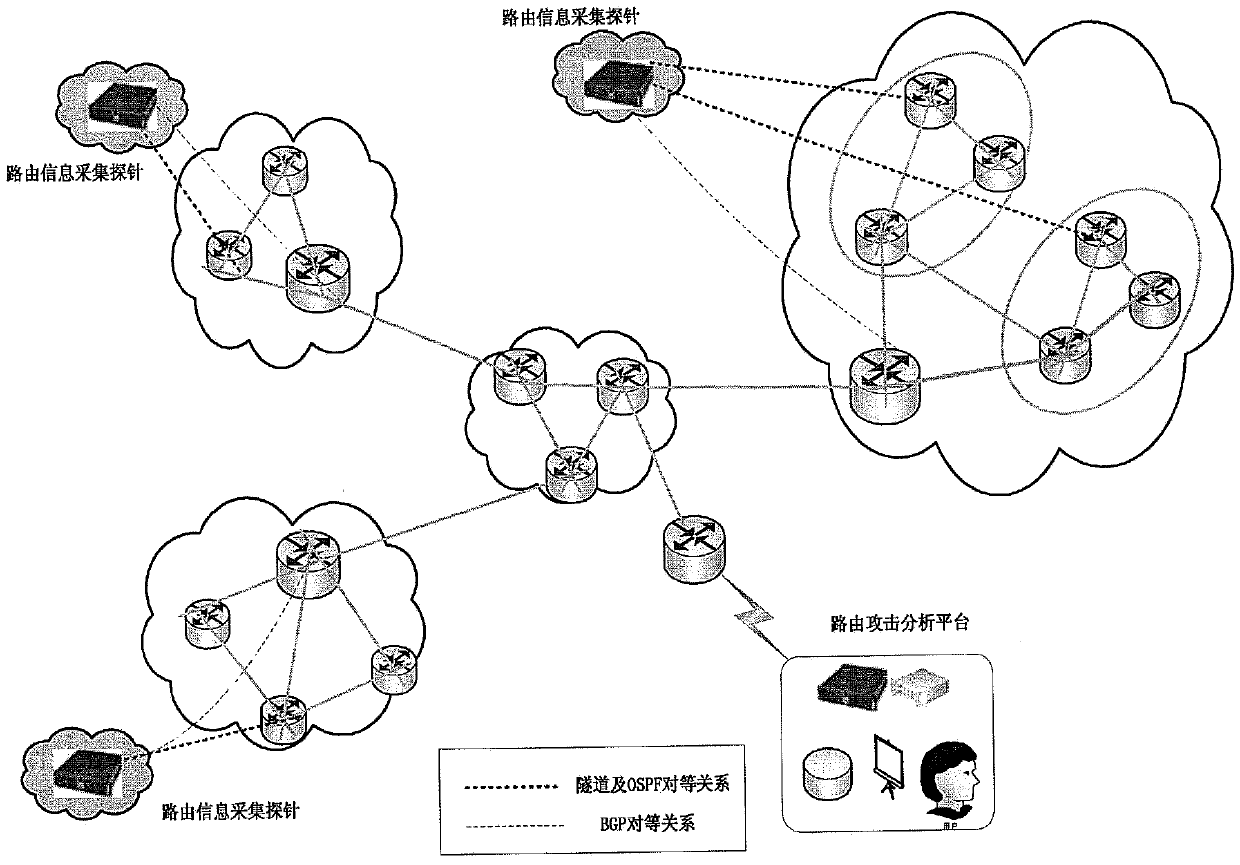
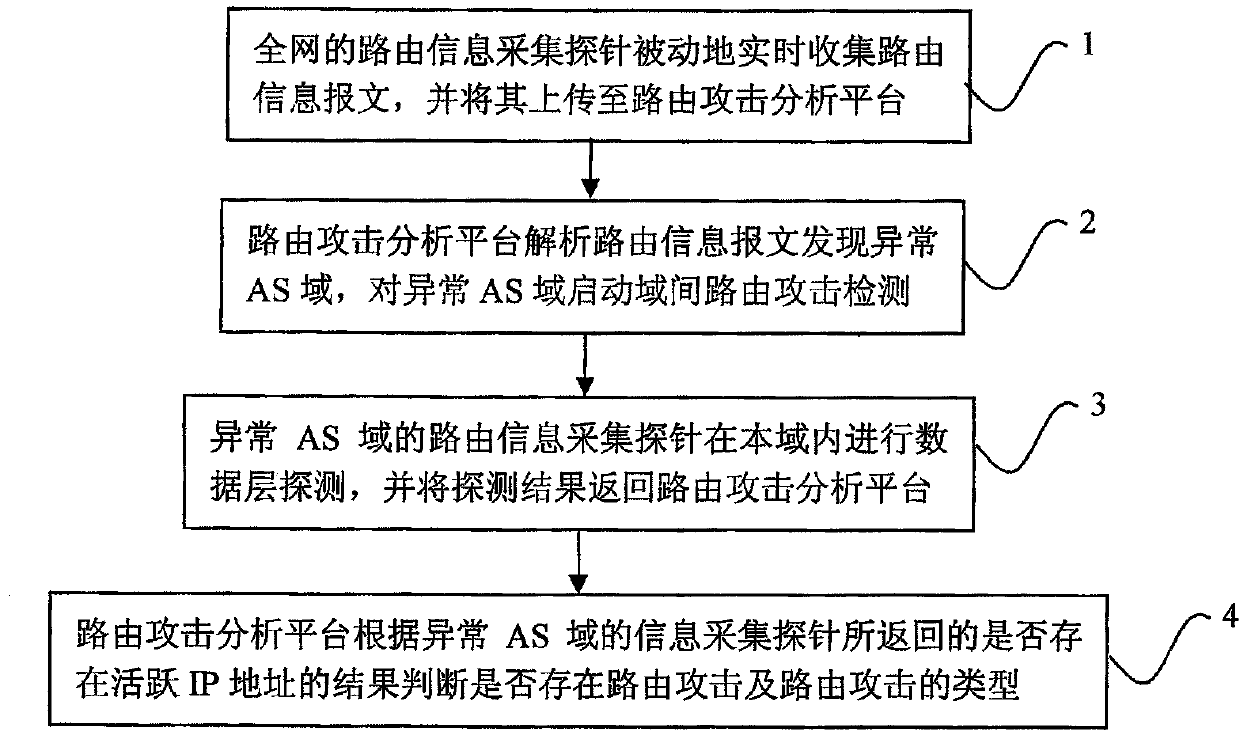
The invention provides a system for detecting routing security. The system for detecting the routing security comprises routing information collecting probes and a routing attack analyzing platform, wherein the routing information collecting probes are used for passively collecting routing information messages in real time and uploading the routing information messages to the routing attack analyzing platform, the routing information collecting probes are also used for receiving instructions of the routing attack analyzing platform to detect whether active IP addresses exist in the domain where the routing information collecting probes are located and feeding back a detection result, the routing attack analyzing platform is used for analyzing the routing information messages reported by the routing information collecting probes to discover abnormal AS domains and sending detection instructions to the routing information collecting probes in the abnormal AS domains, and the routing attack analyzing platform is also used for judging whether routing attack exits according to results fed back by the routing information collecting probes of the abnormal AS domains. The system and method for detecting routing security have the advantages that the missing report rate and false report rate of the routing attack detection can be reduced, real-time monitoring of a large-scale network system is achieved on the premise that cost is quite low, and the routing attack can be found out as early as possible.
Owner:上海星地通讯工程研究所
Artificial intelligence-based unmanned aerial vehicle power transmission line inspection system and method
ActiveCN108037770AImprove inspection efficiencyIncrease the level of automationTarget-seeking controlImaging analysisUncrewed vehicle
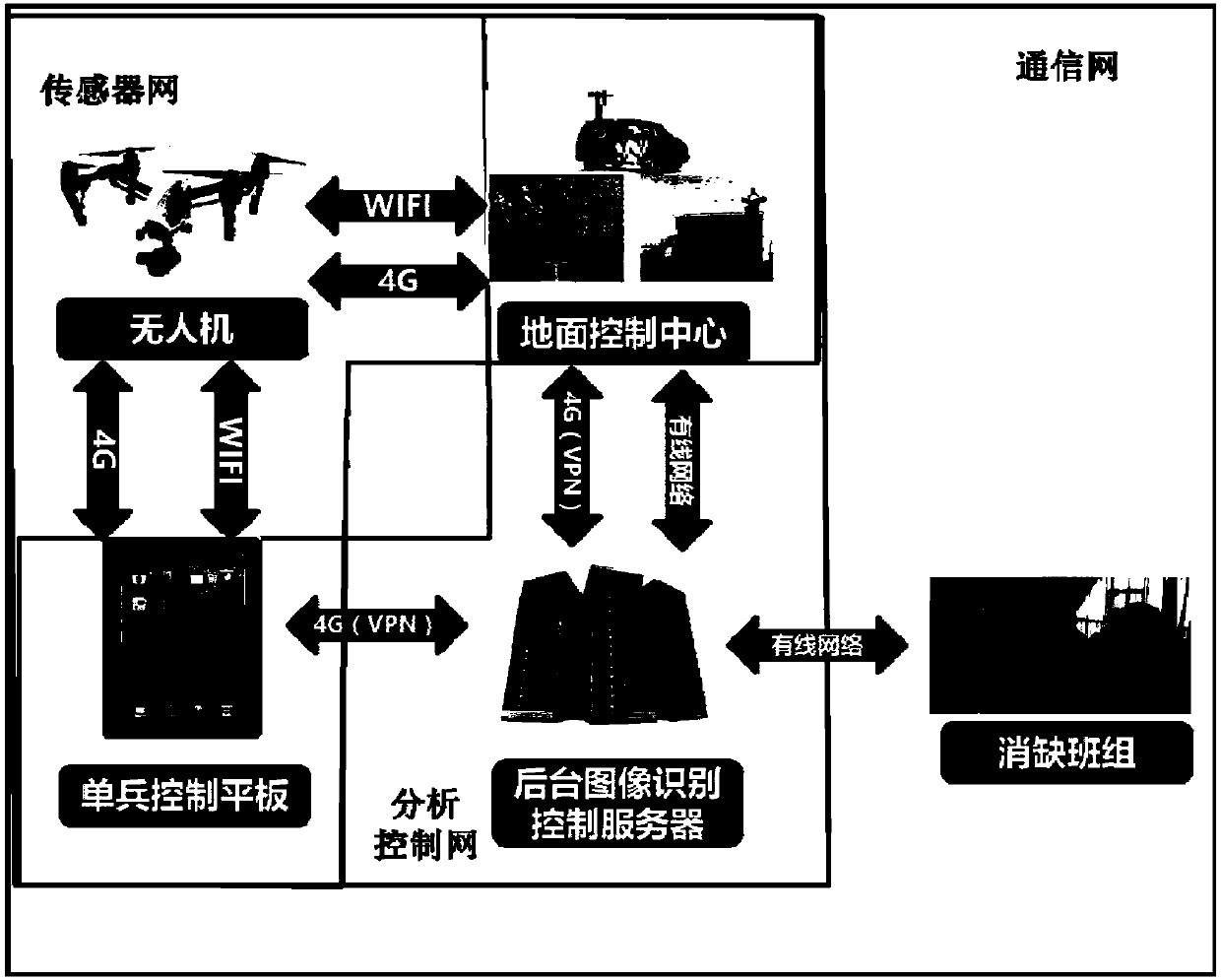
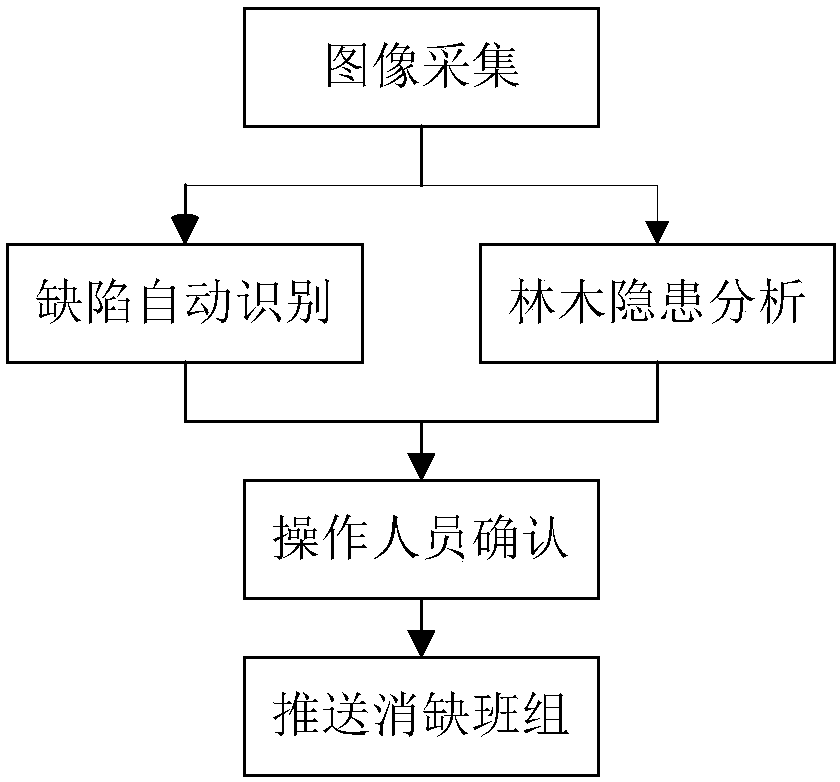
The invention discloses an artificial intelligence-based unmanned aerial vehicle power transmission line inspection system and a method. The system comprises an unmanned aerial vehicle, a background server and an unmanned aerial vehicle control platform. The unmanned aerial vehicle acquires a target image according to a preset control instruction and transmits the target image to the background server. The background server receives the target image, performs image analysis, and sends the analysis result to the unmanned aerial vehicle control platform. The image analysis comprises the steps ofdefect automatic identification and forest hidden danger analysis. The unmanned aerial vehicle control platform is used for receiving a control instruction of an operator about the unmanned aerial vehicle, and pushing the analysis result to a shortcoming-eliminating team / group according to a confirmation instruction of the analysis result. According to the invention, the automation level of the line inspection and shortcoming-eliminating operation is improved. The false alarm rate and the missing report rate of manual identification and treatment are reduced. The accuracy and the effectiveness of the analysis are improved.
Owner:JINING POWER SUPPLY CO OF STATE GRID SHANDONG ELECTRIC POWER CO +1
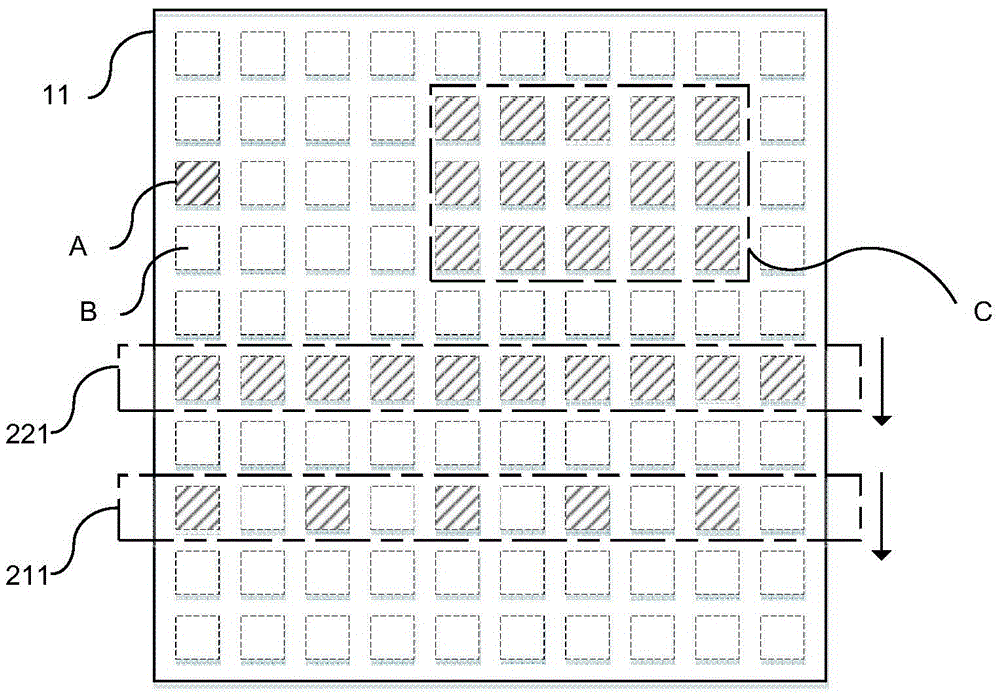
Gate driving circuit and a driving method thereof, as well as a display device
ActiveUS20170010731A1Avoid underchargingImprove reporting rateStatic indicating devicesDigital storageShift registerProcessor register
The present invention provides a gate driving circuit and a driving method thereof, a display device, which relates to the field of display technology. The gate driving circuit may comprise a plurality of mutually cascaded shift register units and a pre-charging unit, the gate row drive scanning and touch control scanning of the plurality of mutually cascaded shift register units are performed alternately. By additionally arranging a pre-charging unit connected with the corresponding first stage of shift register unit when the gate row drive scanning is performed again after the touch control scanning is accomplished, the first stage of shift register unit can be pre-charged during the touch control scanning. In this way, the electric leakage phenomenon of the pull-up control node (PU point) of the corresponding first stage of shift register unit when the gate row drive scanning is performed again after the touch control scanning is accomplished due to a relatively long touch control scanning time interval between outputs of two rows of shift register units is avoided, thereby avoiding the defect of insufficient charging rate of row of pixels while ensuring touch control scanning of high report rate.
Owner:BOE TECH GRP CO LTD
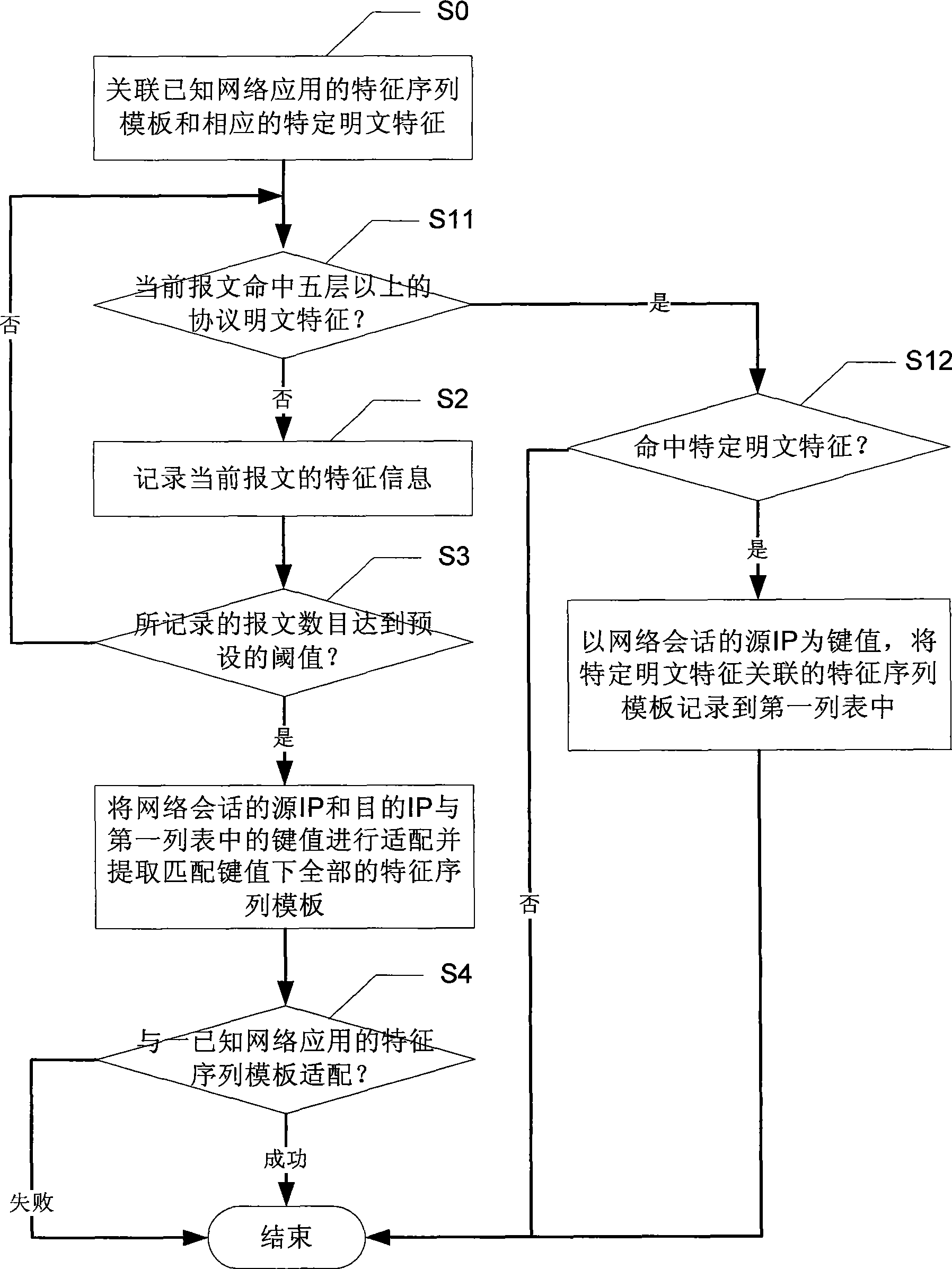
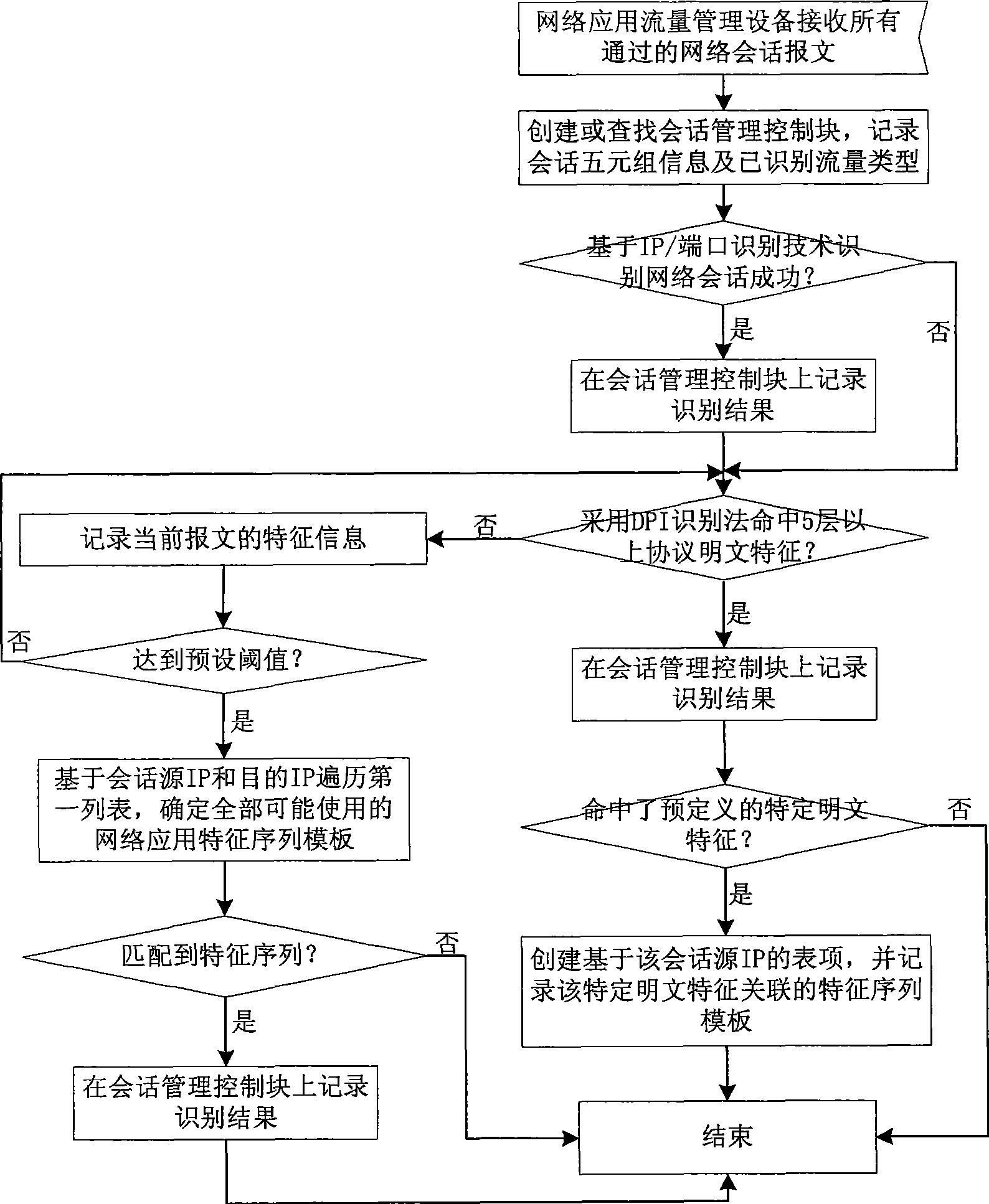
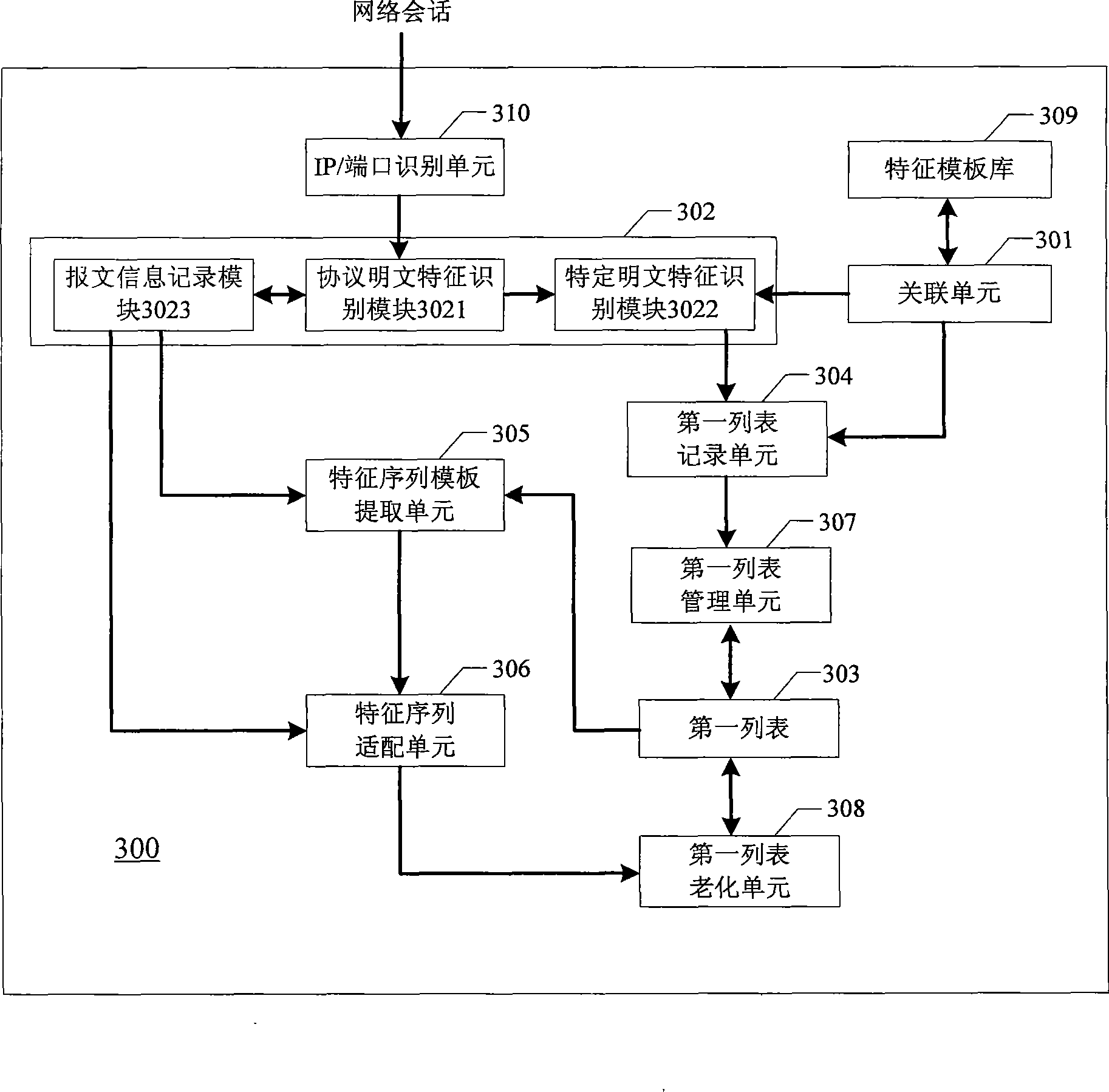
Network application flow recognition method and apparatus and network application flow management apparatus
InactiveCN101505276ALimit application trafficImprove recognition efficiencyData switching networksReporting rateFlow management
The invention discloses a network application traffic identification method, a network application traffic identification device and network application traffic management equipment. The method comprises the following steps of: associating a characteristic sequence template of known network application and corresponding specific plaintext characteristics; taking a source IP of network session as a key value to record the characteristic sequence template which is identified by DPI and is associated with the specific plaintext characteristics into a first list; and for network session which fails to be identified by the prior art, recording characteristic information of a current message, and adapting the characteristic information to the entire characteristic sequence templates under a corresponding key value when a preset threshold is reached to obtain a network application traffic identification result. The network application traffic identification method and the network application traffic identification device can identify network application traffic which fails to be identified by a DPI identification method, improve identification efficiency at the same time, reduce identification cost, and reduce the false report rate of the identification.
Owner:NEW H3C TECH CO LTD
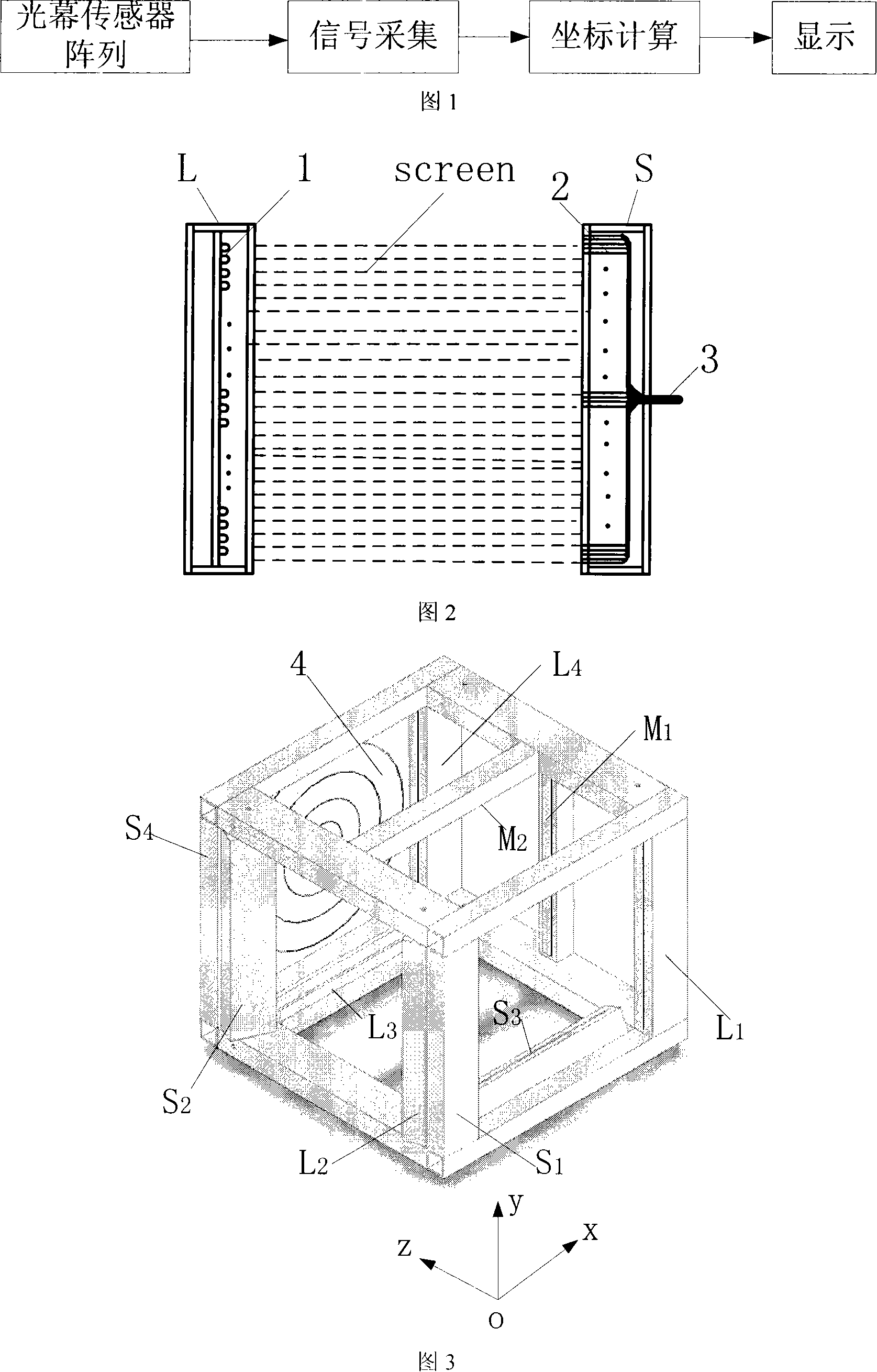
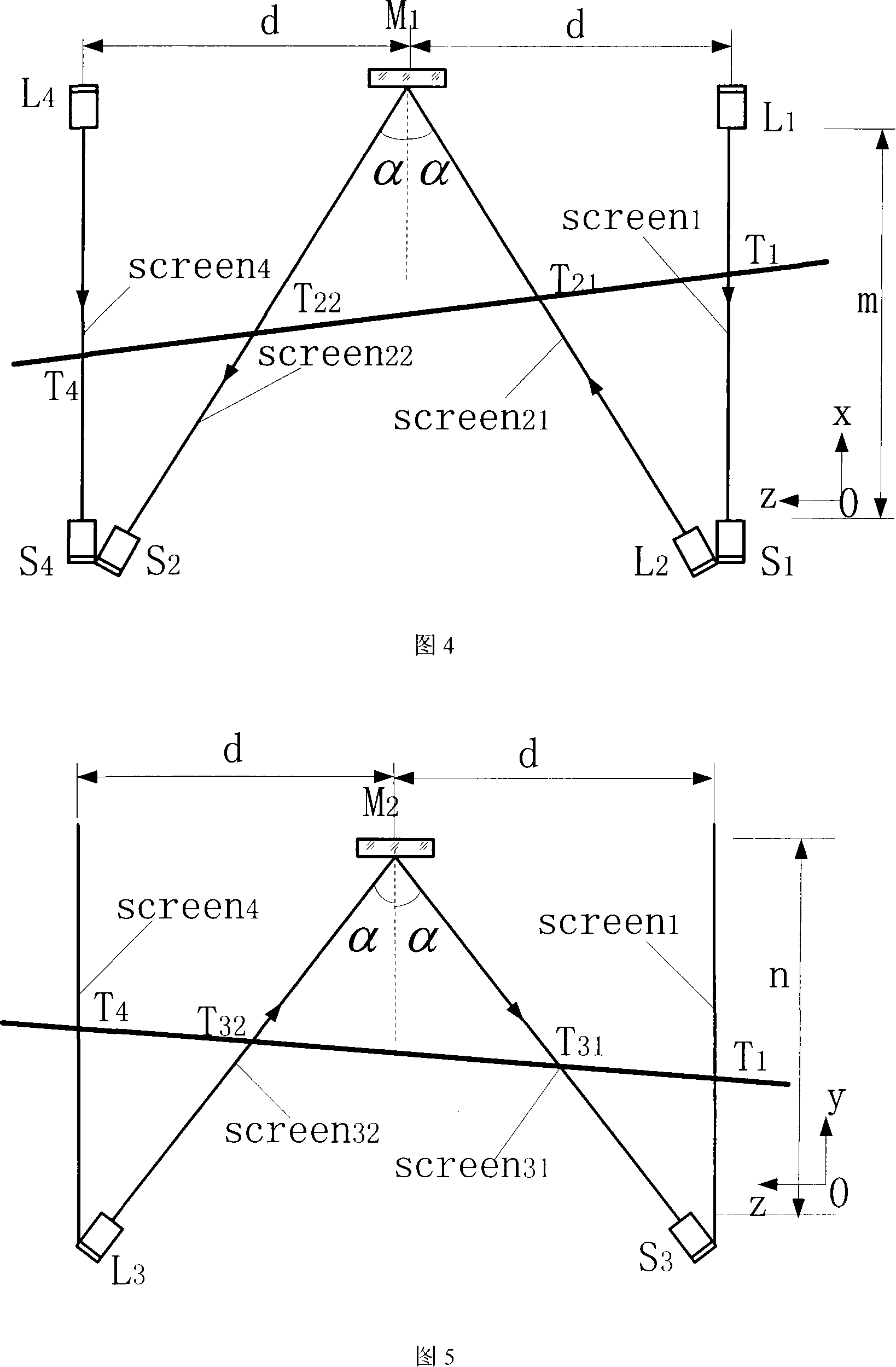
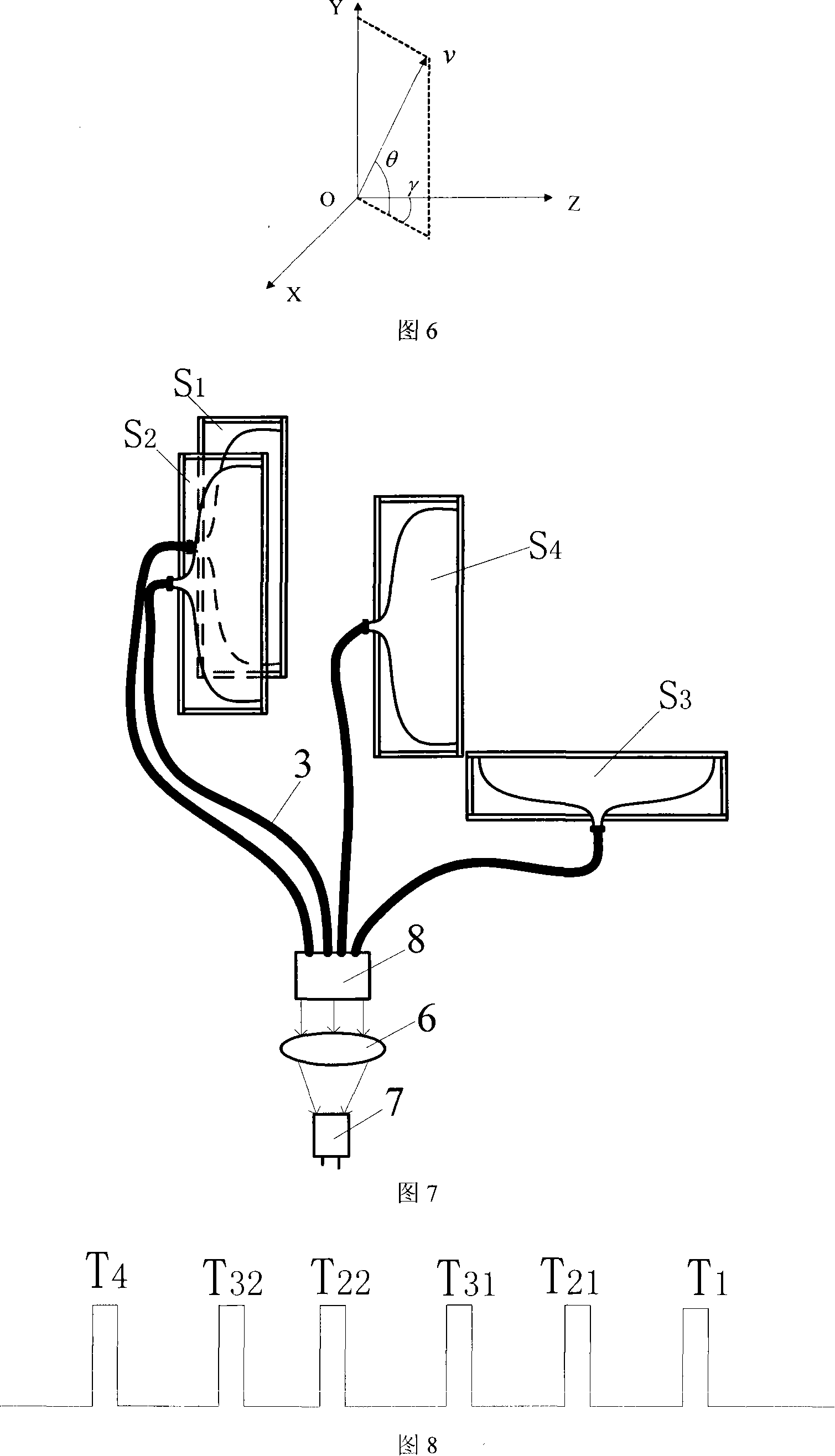
Light curtain array automatic scoring round target device and method
InactiveCN101149245AAchieving Stereoscopic Data AcquisitionRealize multivariate data collectionTarget detectorsSensor arrayExact location
This invention discloses an automatic target-reporting method and system for indoor and outdoor bullet shooting. It includes veiling sensor array, signal collection, coordinates computation and display parts. The basic cell array of the veiling sensor is composed of a linear light source L and corresponding receiving device. The linear light source L is composed of light-emitting diodes that are arranged in line. The receiving device S is formed by the end face of optical fiber. The veiling sensor is three-dimensional frame structure. Two parallel veiling are used together in the X and Y computed coordinate directions. Each of them has two V shaped veiling which form alpha angle with the two parallel veiling. Thus, they form the special veiling sensor array. Only four sets of veiling basic cell arrays can fulfill the three-dimensional no touch measurement of the bullet. It can give the exact location and speed of the bullet on the target. The rate of false reporting rate is low. It will not be interfered by adjacent target.
Owner:XIAN TECHNOLOGICAL UNIV
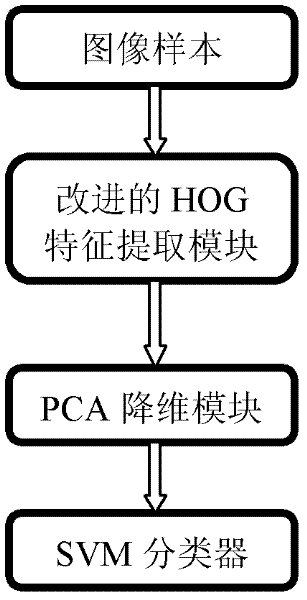
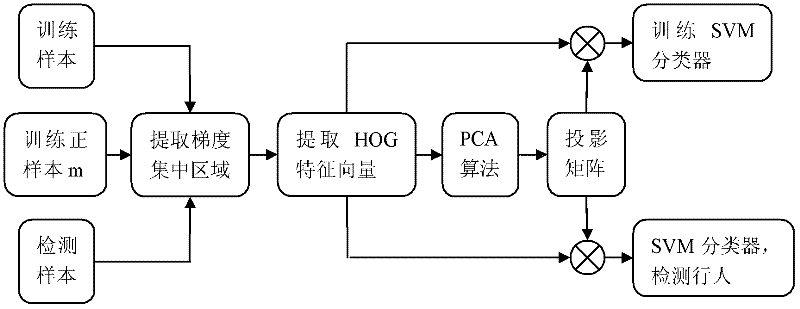
Pedestrian detecting method based on improved HOG feature and PCA (Principal Component Analysis)
ActiveCN102609716AImprove detection rateReduce training speedCharacter and pattern recognitionFeature vectorPrincipal component analysis
The invention relates to a pedestrian detecting method based on improved HOG feature and PCA (Principal Component Analysis). The method comprises the following steps: extracting a sample feature by using a feature extracting algorithm for HOG feature cascaded PCA in a concentrated area of gradient information of a pedestrian in a sample image; training a SVM classifier by utilizing the feature extracted from the sample; and utilizing a feature extracting method to extract a feature vector for a detected sample and utilizing the trained and obtained SVM classifier to detect the pedestrian. The invention provides a pedestrian detecting method based on improved HOG feature and PCA, with the capabilities of efficiently reducing the training speed and reducing the false detecting rate and missing report rate.
Owner:ENJOYOR COMPANY LIMITED +1
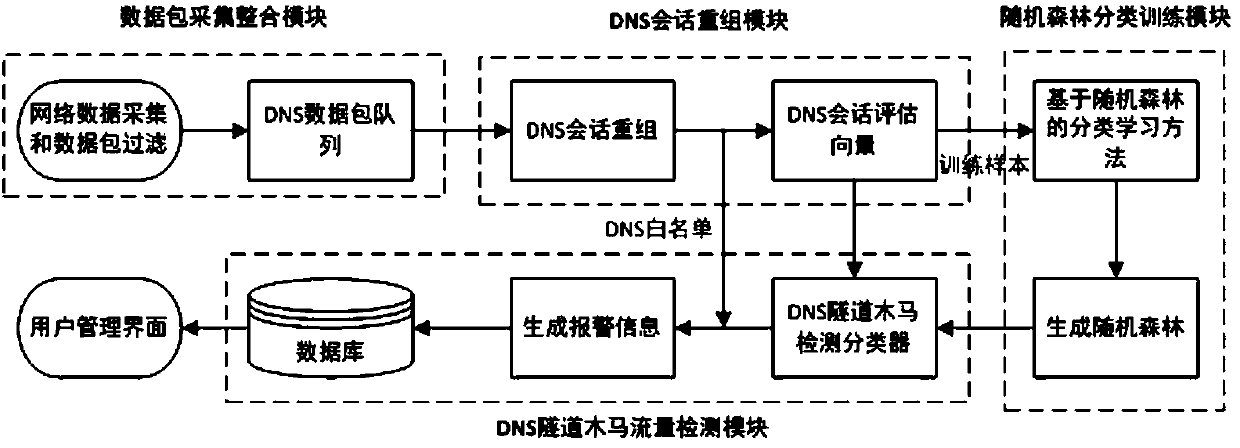
DNS (Domain Name System) tunnel Trojan detection method based on communication behavior analysis
ActiveCN107733851ACharacter and pattern recognitionData switching networksExperimental testingNetwork packet
The invention discloses a DNS (Domain Name System) tunnel Trojan detection method based on communication behavior analysis. The DNS tunnel Trojan detection method mainly comprises four parts, namely,a data packet acquisition and integration module, a DNS session reorganization module, a random forest classification training and learning module and a DNS tunnel Trojan traffic detection module. Thecommunication mode of DNS tunnel Trojan is analyzed from the perspective of DNS session; seven attributes which are different from normal DNS session characteristics are extracted; a classification trainer is constructed with an improved random forest algorithm; and finally, a DNS tunnel Trojan detection model is built. As proved by experimental testing, a DNS tunnel Trojan detection technology based on communication behavior analysis disclosed by the invention can effectively detect high-concealment DNS tunnel Trojans, and has the advantages of low false alarm rate, low missing report rate and a very good detection effect on unknown DNS tunnel Trojans.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Optical fiber disturbance detection method and apparatus
ActiveCN101488805AImprove accuracyHigh sensitivityReflectometers dealing with polarizationSubsonic/sonic/ultrasonic wave measurementRayleigh scatteringTime domain
The invention relates to an optical fiber sensor. The invention discloses an optical fiber destabilization detecting method combining based on a phase sensitivity light time domain reflection and a polarization sensitivity light time domain reflection method and distributed optical fiber sensing system thereof to improve the detecting accuracy and reliability of the optical fiber destabilization. The method comprises: a. injecting an optical signal with determined polarization state into the optical fiber; b. receiving the back rayleigh scattering light in the optical fiber; c. diving the rayleigh scattering light into two bundles to perform the Phi-OTDR data acquisition and the POTDR data acquisition; d. determining the destabilization and position thereof based on the distortion points of the Phi-OTDR data and the POTDR data. The invention also discloses an optical fiber destabilization detecting device. The technical scheme of the invention is used for monitoring and protecting the optical cable lines, thereby greatly improving the precision and the sensitivity of the monitoring system and reducing the erroneous judgment rate and the missing report rate.
Owner:OPTICAL SCI & TECH (CHENGDU) LTD
Intelligent Trojan horse detecting device based on behavior features in network flows and method thereof
ActiveCN103179105AImprove detection efficiencyLow false positiveTransmissionNerve networkUser Datagram Protocol
The invention relates to an intelligent Trojan horse detecting device based on Trojan horse behavior features reflected in network flows and a method thereof. The device and the method thereof play an active role in detecting Trojan horses and are high in detecting efficiency and low in mistaken report rate and miss report rate. The method includes the steps of firstly, collecting TCP (transmission control protocol), UDP (user datagram protocol) data packets; secondly, pretreating collected data packets; thirdly, filtering data packets according to a neural network to identify abnormal data packets; fourthly, identifying data packets with Trojan horse behaviors from the abnormal data packets; and fifthly alarming when data packets with Trojan horse behaviors are found.
Owner:INFORMATION & TELECOMM COMPANY SICHUAN ELECTRIC POWER +1
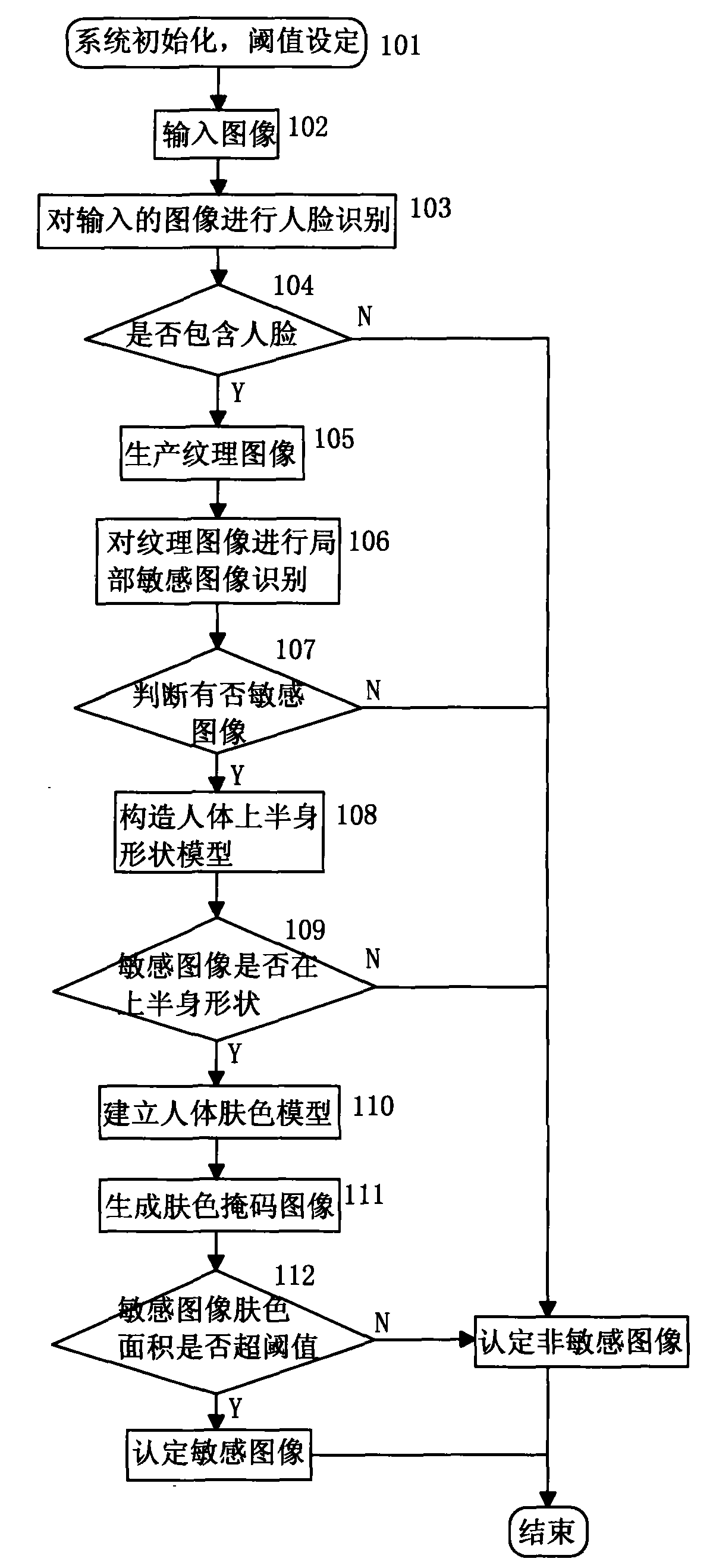
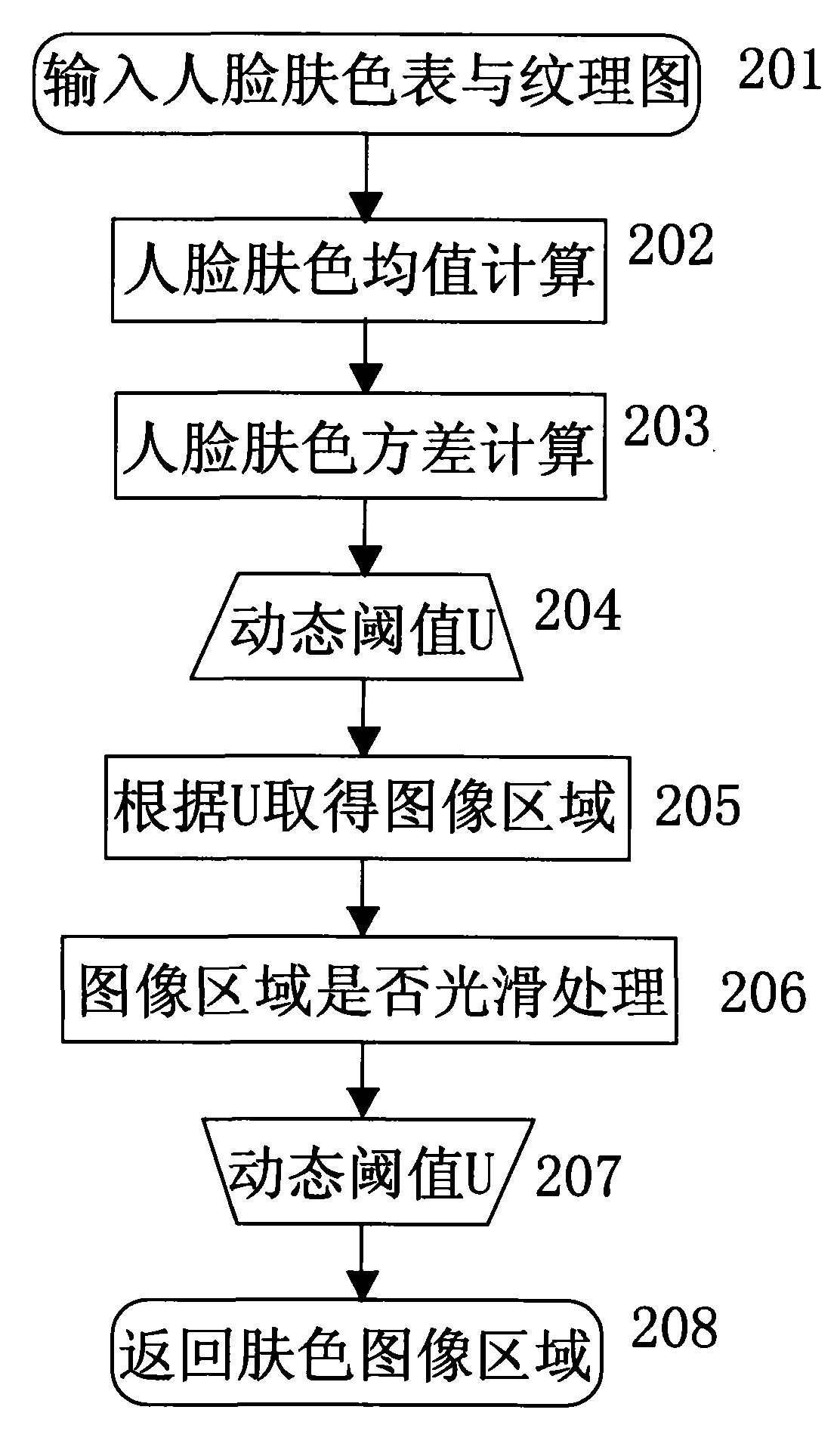
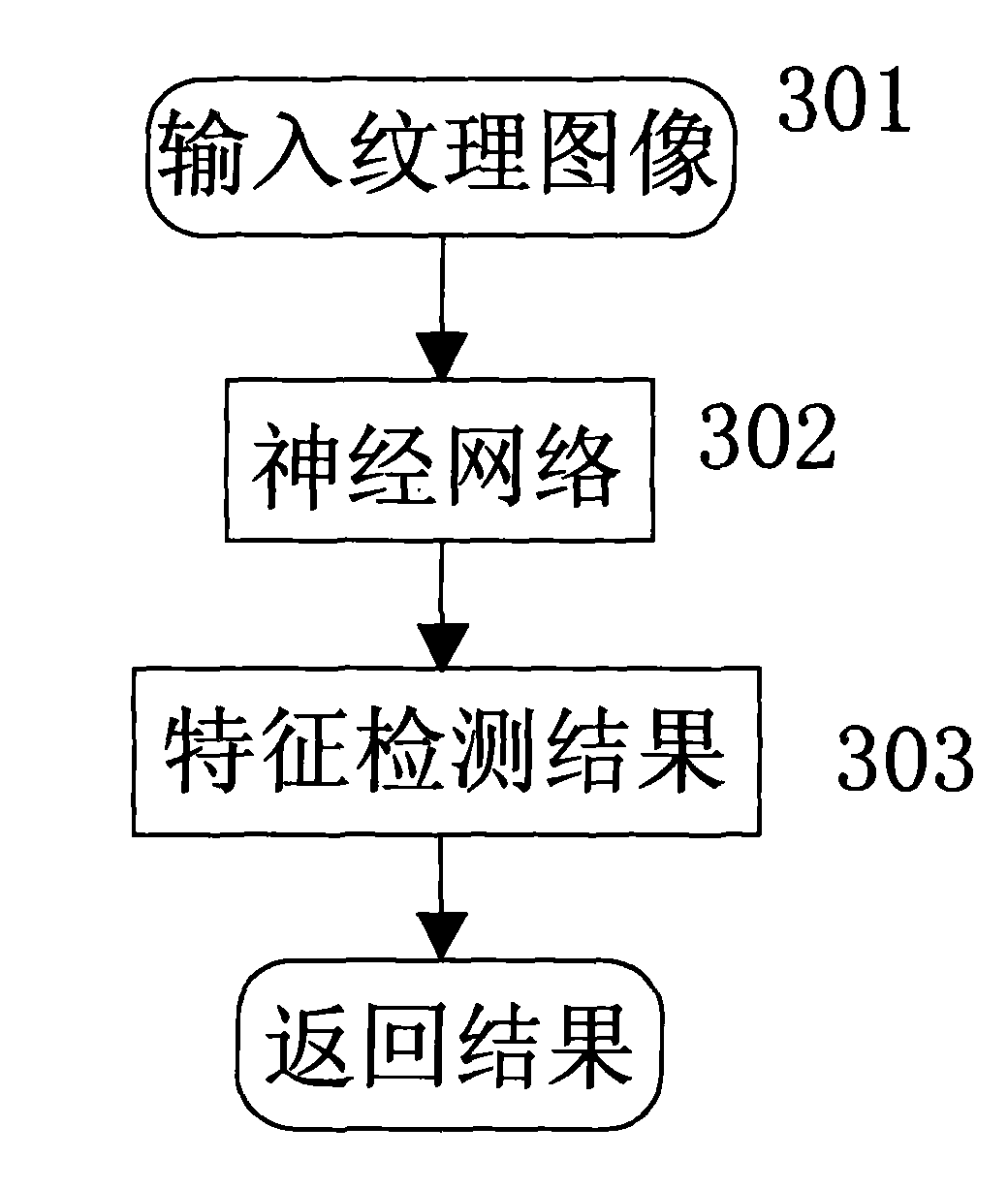
Content-based human body upper part sensitive image identification method and device
ActiveCN101996314AReduce false alarm rateCharacter and pattern recognitionPattern recognitionHuman skin
The invention discloses a content-based human body upper part sensitive image identification method and a content-based human body upper part sensitive image identification device. The method comprises the following steps of: performing human face identification on static images and removing images which do not contain human face information; identifying a texture image by using neural network identification and finding out related sensitive information positions; generating a human body skin color model of the image by using the color distribution information in a detected human face area and the default skin color information; extracting the human body skin area from the image according to the established human body skin color model; and if the sensitive information image and the human face information image are consistent with a human body upper part shape model, and the skin ratio of the sensitive information image exceeds a threshold, determining the image as the sensitive image. In the invention, human face identification, human body upper part identification and sensitive image identification are used in combination to differentiate sexy photo images from pornographic sensitive images, so that the error report rate of the sexy photo images is effectively reduced.
Owner:XIAMEN MEIYA PICO INFORMATION
Method of monitoring faults in sections for intermittent control system
InactiveCN103279123AThe phase division complies withThe phase division is more in line with the batch process actually in line withElectric testing/monitoringFuzzy clustering analysisPrincipal component analysis
The invention discloses a method of monitoring faults in sections for an intermittent control system and relates to a fault monitoring method. Firstly, a plurality of batches of collected intermittent process data are standardized in a way of expanding variables, and a data matrix on each sampling time is subjected to principal component analysis; secondly, a fuzzy C-means clustering is a fuzzy clustering analysis method which is suitable for soft partition and is generated through combining a fuzzy set theory and a k-means clustering; and thirdly, after segmentation is finished, an improved MPCA (Multiway Principal Component Analysis) model with a time varying principal element covariance on the basis of expanding variables is established on each subphase, then when on-line monitoring is carried out, which phase a new batch of data belongs to is judged, whether the data exceeds the fault monitoring control limit or not is calculated and judged, if so, a fault occurs, and the fault monitoring in sections ends. According to the invention, process multi-phase partition is more accurate, misinformation and missing report rates in monitoring are reduced, and the practical application and operability are strong.
Owner:SHENYANG INSTITUTE OF CHEMICAL TECHNOLOGY
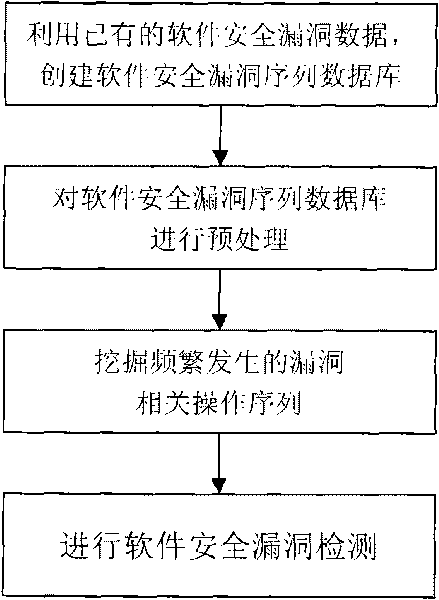
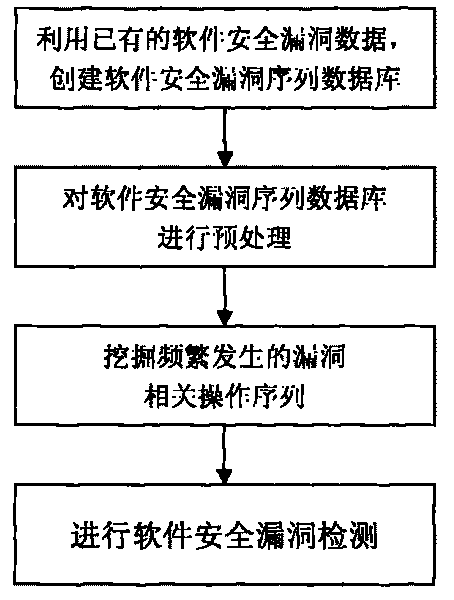
Software security flaw detection method based on sequential pattern mining
InactiveCN101710378AImprove detection efficiencyReduce the false negative rate of vulnerability detectionPlatform integrity maintainanceSpecial data processing applicationsSequence databaseSoftware system
The invention provides a software security flaw detection method based on sequential pattern mining. Firstly, a great quantity of relevant operation sequence data of a detected software security flaw is used for building a relevant operation sequence database of the security flaw; then, a closed sequential pattern mining arithmetic in the data mining is used to mine frequently appearing relevant operation sequence of the flaw; the mined frequently appearing relevant operation sequence of the flaw is used for detecting the security flaw of the current software system so as to lower flaw detection missing report rate as well as improve security flaw detection efficiency. Along with the accumulation of flaw data, the advantage of high security flaw detection efficiency of the invention is more outstanding.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +2
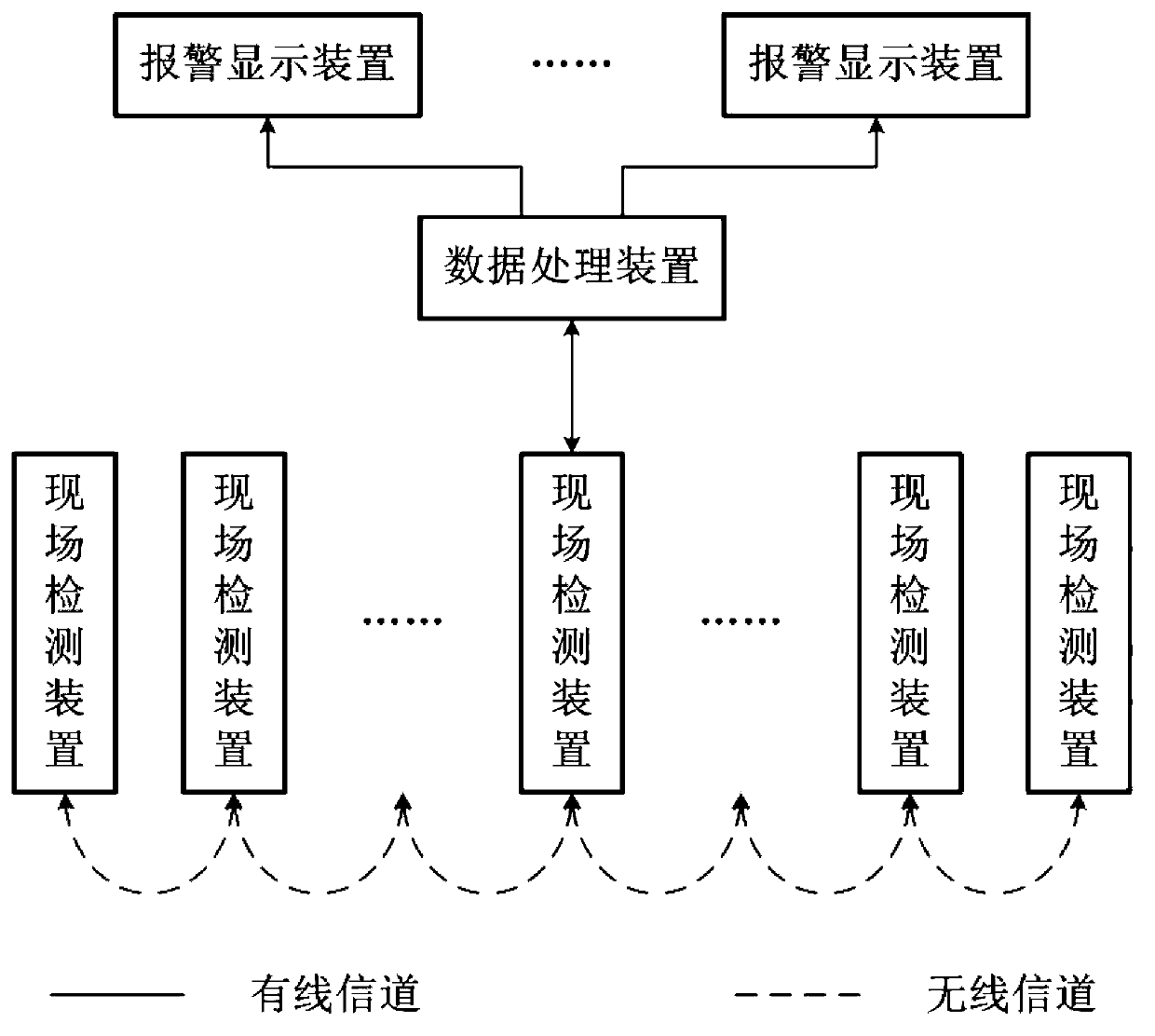
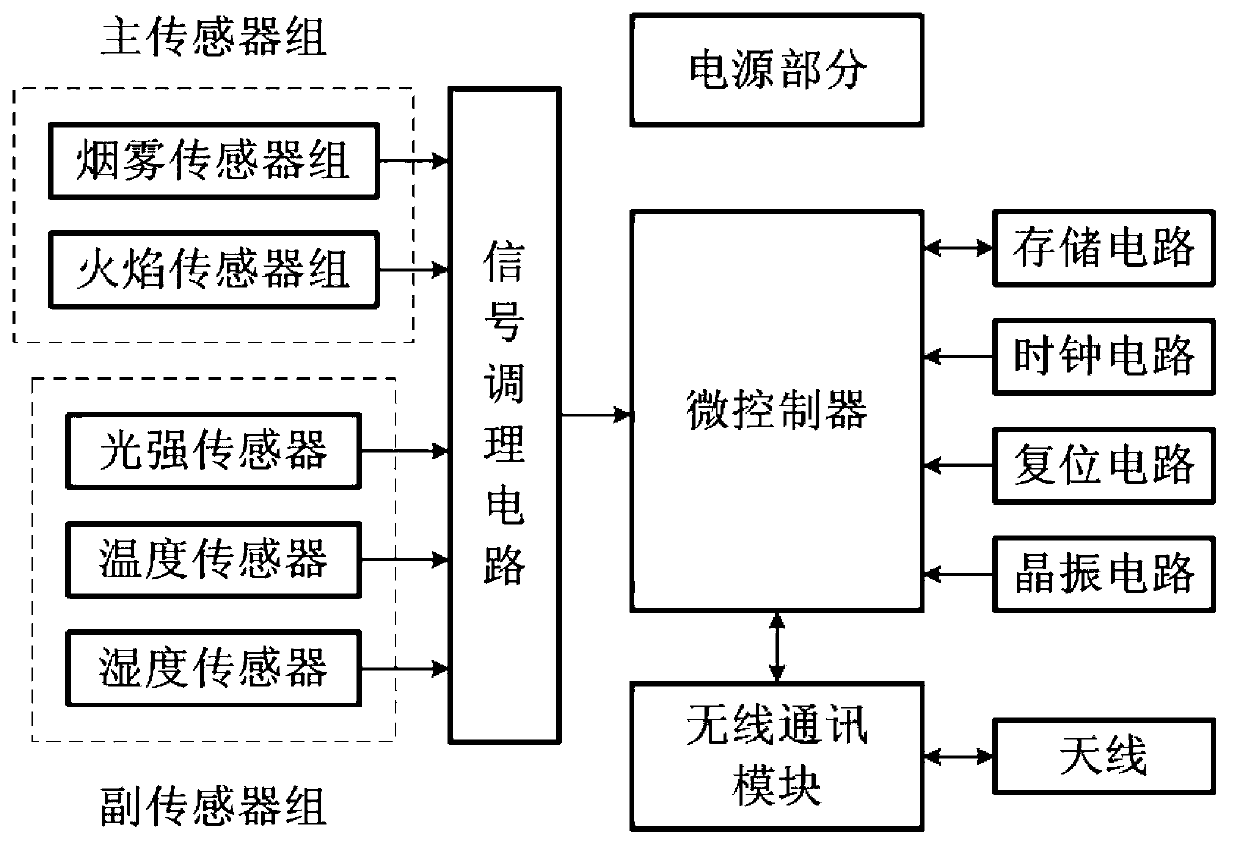
Tunnel fire early-warning controlling method based on multi-sensor data fusion technology and system using the same
ActiveCN103136893ADynamic Fire Threshold Adjustment MethodFlexible Fire Threshold Adjustment MethodBiological neural network modelsFire alarmsEarly warning systemFire - disasters
A tunnel fire early-warning controlling method based on multi-sensor data fusion technology and a system using the tunnel fire early-warning controlling method based on the multi-sensor data fusion technology comprise steps as below: recording of history data of a main sensor group, reading of data of an auxiliary sensor group at a regular time, calculation of a neural network, passing back of a calculation result, execution controlling on site and the like, and the system specially using the tunnel fire early-warning controlling method based on the multi-sensor data fusion technology comprises a site detection device, a data processing device and an alarming displaying device. The tunnel fire early-warning controlling method based on the multi-sensor data fusion technology comprises a dynamic and flexible fire disaster threshold value adjusting method, namely, a method calculating with a neural network to analyze current data of the history data of the main sensor group and the auxiliary sensor group to obtain a fire disaster threshold value of current environment factors, and the original fire disaster threshold value is replaced by the new fire disaster threshold value. The tunnel fire early-warning controlling method based on the multi-sensor data fusion technology can effectively reduce judgment differences of a fire disaster caused by changing of environment of the tunnel, and reduce misstatement rate and missing reporting rate of the funnel fire disaster early-warning system.
Owner:四川九通智路科技有限公司
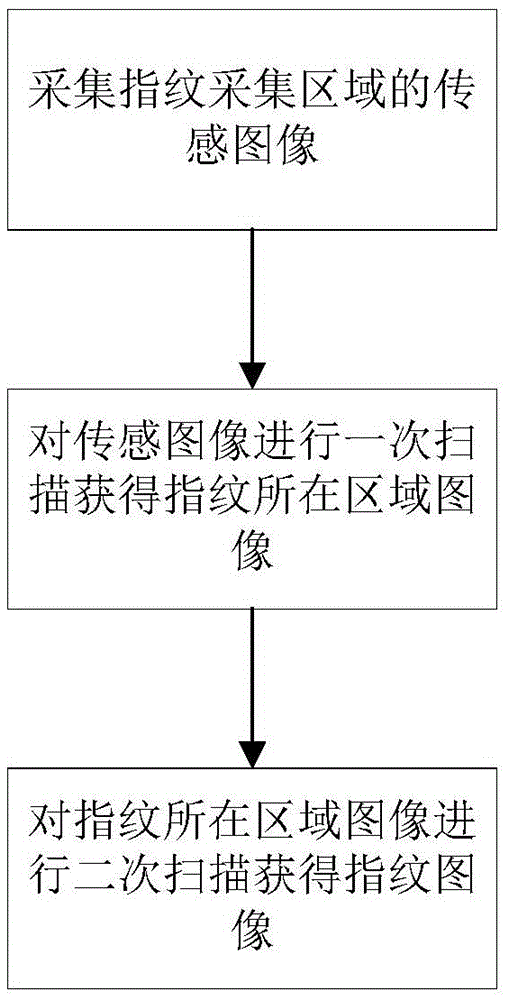
Fingerprint scanning method and device and gesture recognition method and device
InactiveCN105528592ARapid positioningReduce power consumptionPrint image acquisitionDigital ink recognitionPattern recognitionReporting rate
The invention is to provide a fingerprint scanning method and device and a gesture recognition method and device, and is mainly to solve the problems of low fingerprint scanning speed, low point reporting rate of gesture recognition and high error recognition rate in the prior art. The fingerprint scanning method comprises carrying out primary scanning on a sensor area to position a fingerprint area; and carrying out secondary scanning on the fingerprint area to obtain a fingerprint image. The fingerprint scanning method comprises two scanning; one scanning is coarse scanning carried out in the whole sensing image range, and fingerprint area images can be obtained quickly; and then, the fingerprint area is subjected to secondary scanning to obtain the fingerprint images without carrying out fine scanning on the whole sensing images, thereby ensuring precise fingerprint images and meanwhile, improving scanning speed effectively, and reducing average power consumption of sensors.
Owner:CHIPONE TECH BEIJINGCO LTD
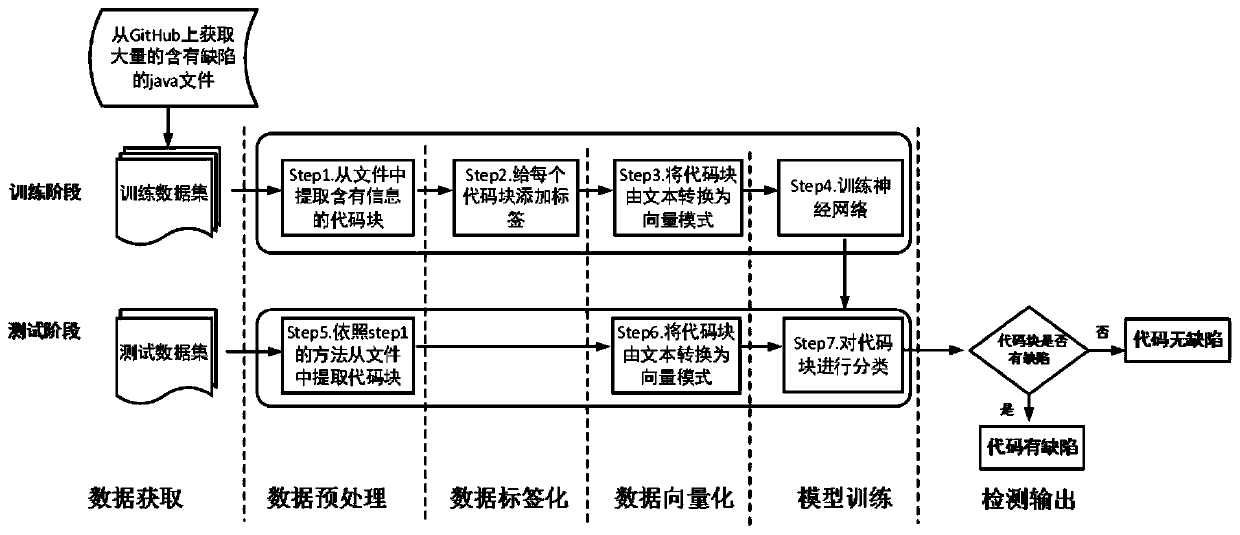
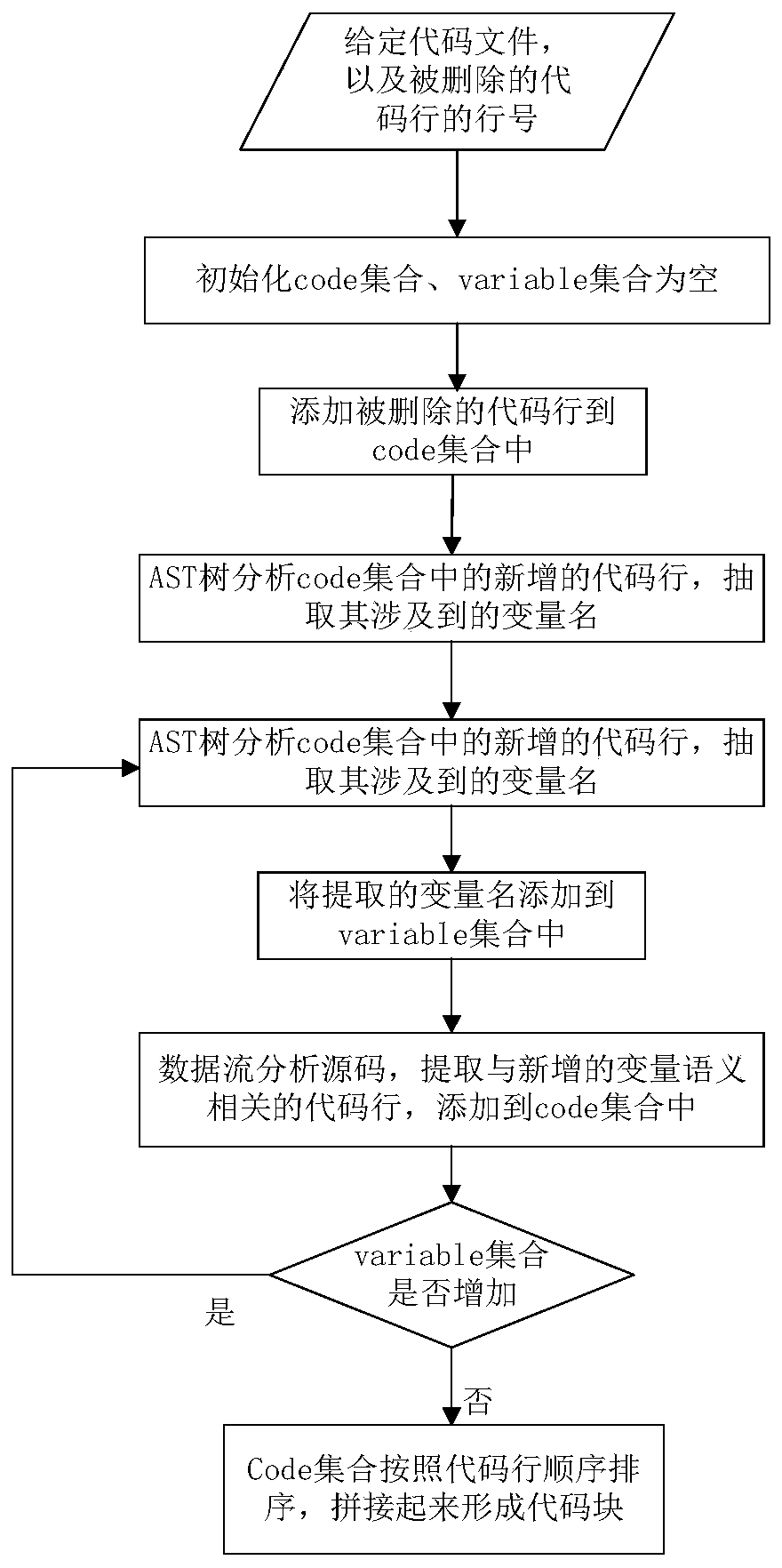
A software defect automatic detection method based on an open source code library
ActiveCN109697162AReduce false negative ratePrecise positioningSoftware testing/debuggingNeural architecturesData streamFeature extraction
The invention discloses a software defect automatic detection method based on an open source code library. The software defect automatic detection method comprises a bidirectional LSTM framework related to a source code feature extraction technology, a word vector representation method in natural language processing and a deep learning technology. The detection method is based on a code change record in a large-scale open source code warehouse Github. Through acquiring a large number of defect codes in the code changing process and using a static code analysis technology, data stream characteristics of defect code fragments are extracted, a code defect detection model is designed by the aid of a bidirectional LSTM framework in deep learning, technical support is provided for code defect static detection, defect detection on target files is achieved, and accurate vulnerability positions are reported on the premise of low missing report rate.
Owner:NORTHWEST UNIV(CN)
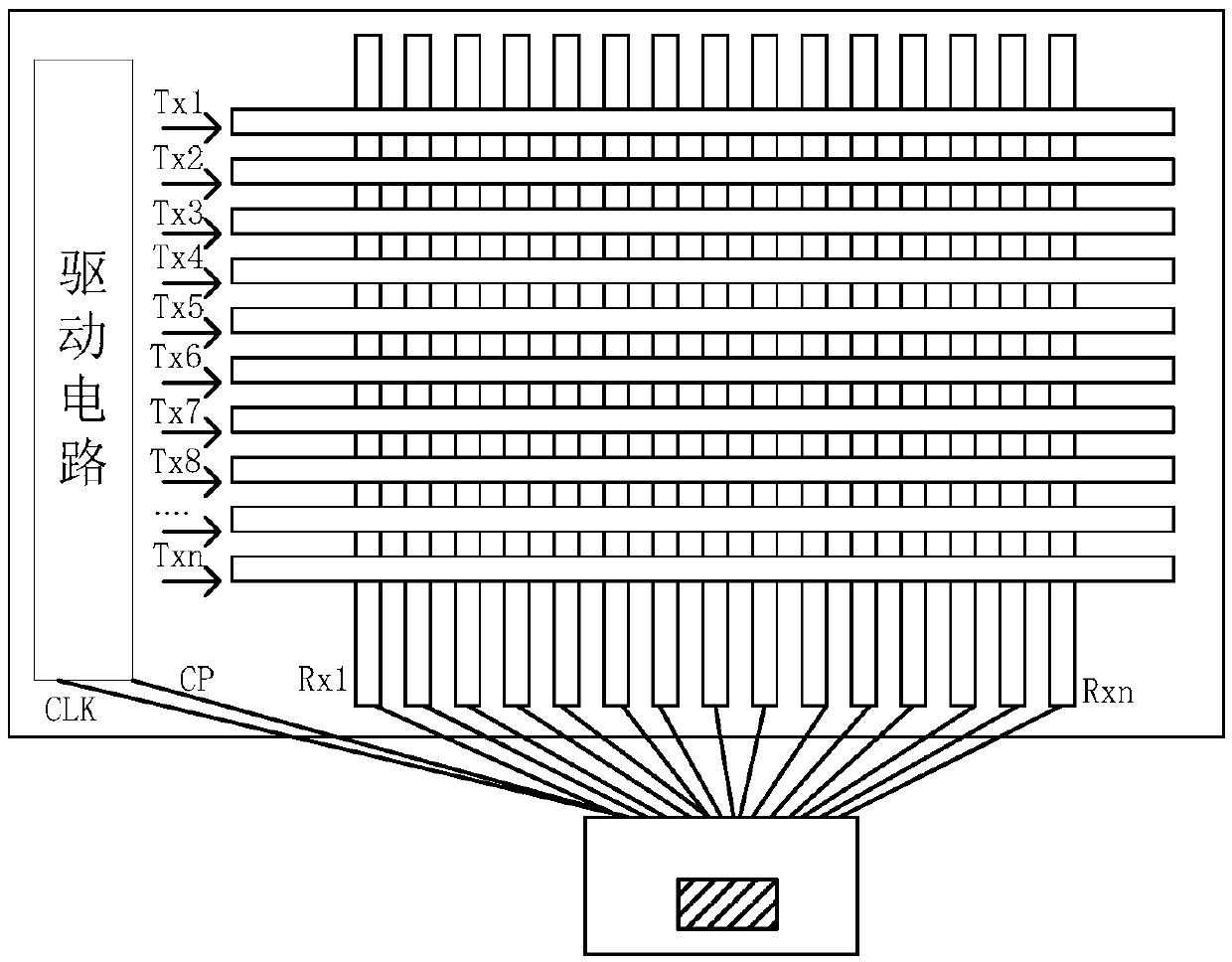
Touch display panel, driving method thereof and detecting method of induction signals
ActiveCN105528118AImprove reporting rateReduce scan timeInput/output processes for data processingEngineeringReporting rate
The invention discloses a touch display panel, a driving method thereof and a detecting method of induction signals, relates to the field of display and solves the problems that the report rate is influenced due to long scanning period and thin film transistors in a visible range are prone to electrical conductivity reduction. A plurality of touch driving electrodes and touch induction electrodes are arranged in a touch area of the touch display panel, and a driving unit is arranged on the edge; the driving unit comprises a first gate driving circuit to an Nth gate driving circuit which are coupled sequentially in a cascading manner, the enable end of the first gate driving circuit is connected with a field synchronizing signal line arranged on the edge of the touch display panel, and the output end of the (N-1)th gate driving circuit is connected to the enable end of the Nth gate driving circuit adjacently connected with the (N-1)th gate driving circuit; the input ends of the first gate driving circuit to the Nth gate driving circuit are connected with a driving signal line respectively, and the output ends of the first gate driving circuit to the Nth gate driving circuit are coupled with the corresponding touch driving electrodes respectively.
Owner:BOE TECH GRP CO LTD +1
Smoke and fire detection device based on videos
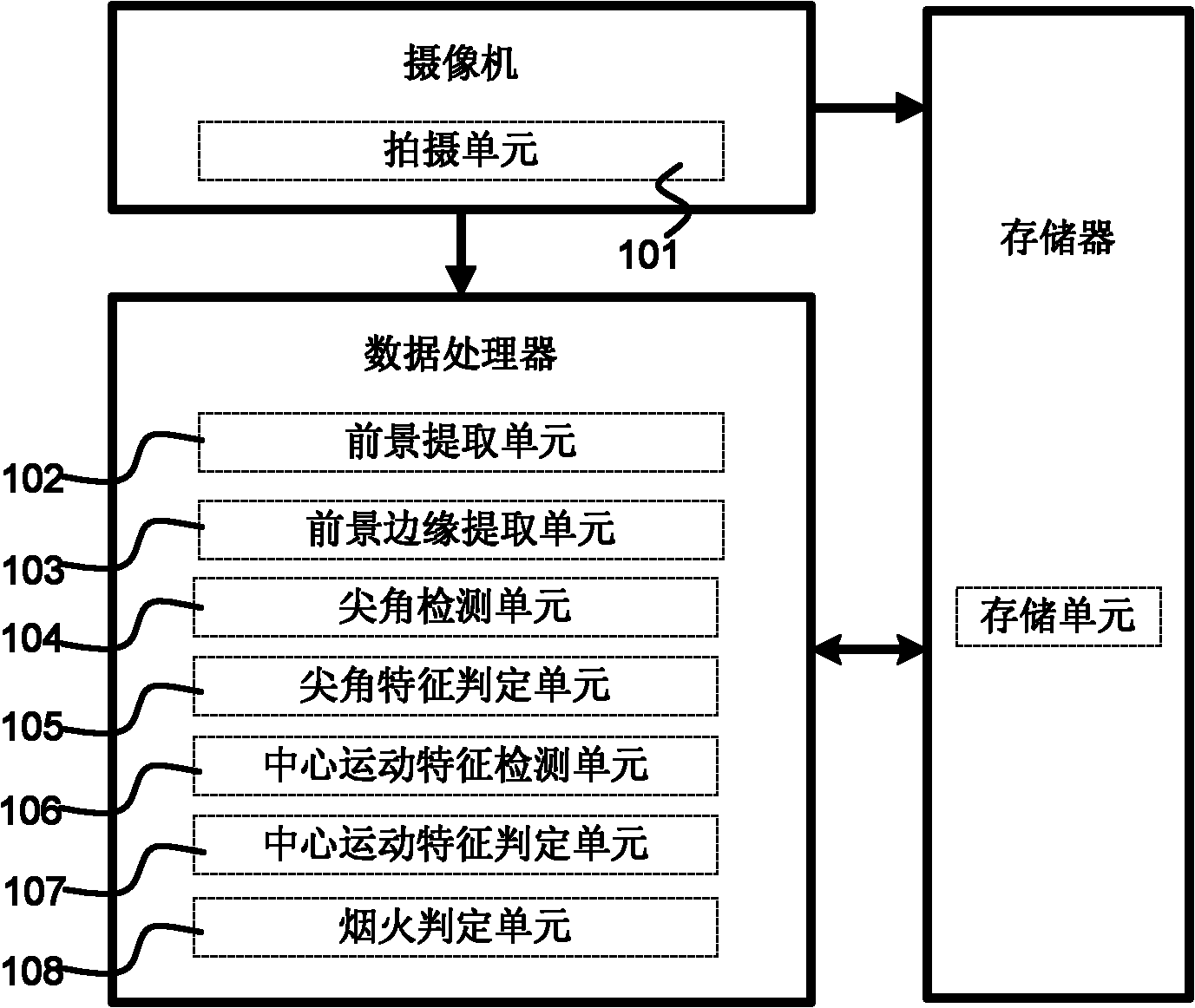
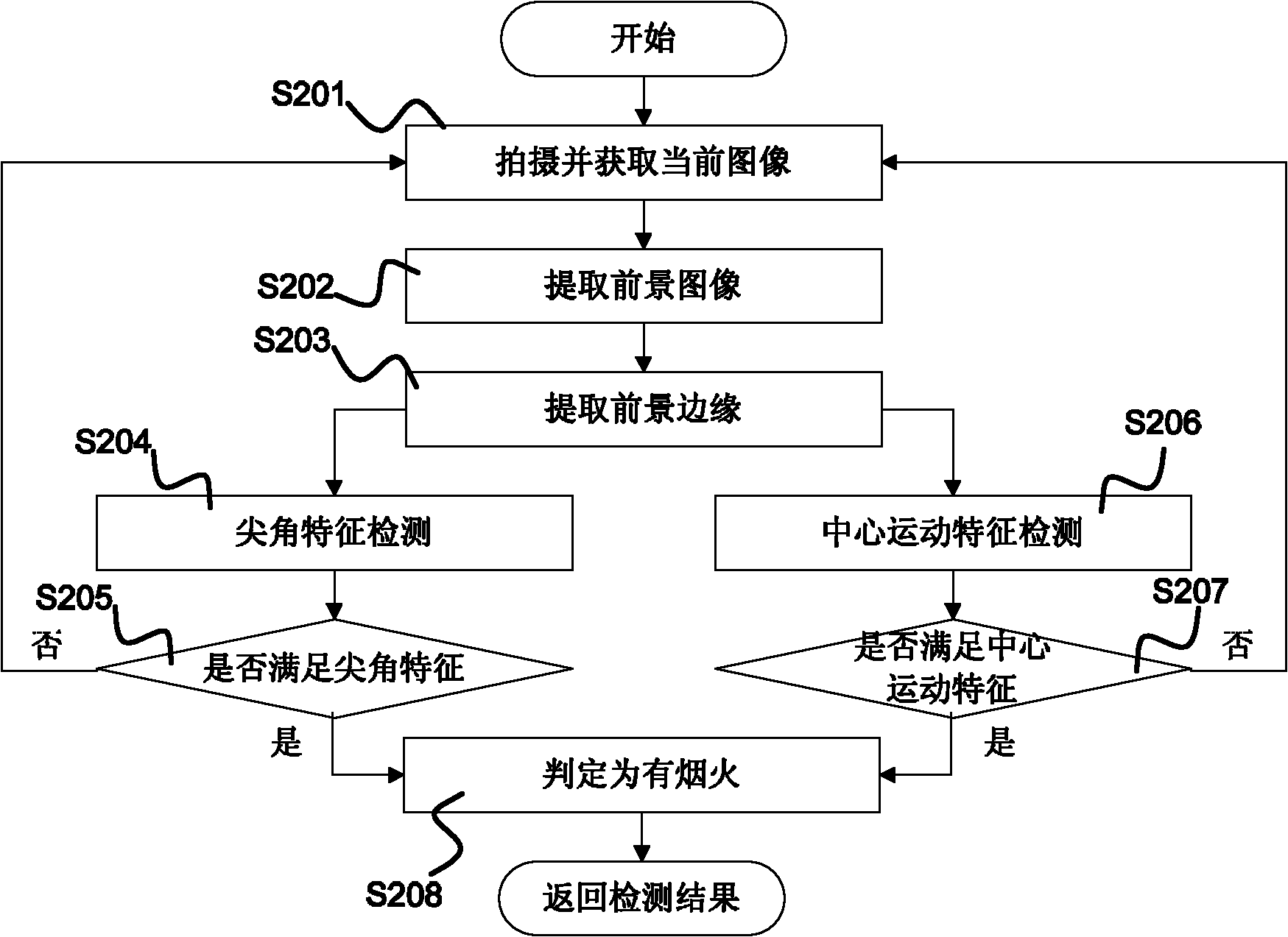
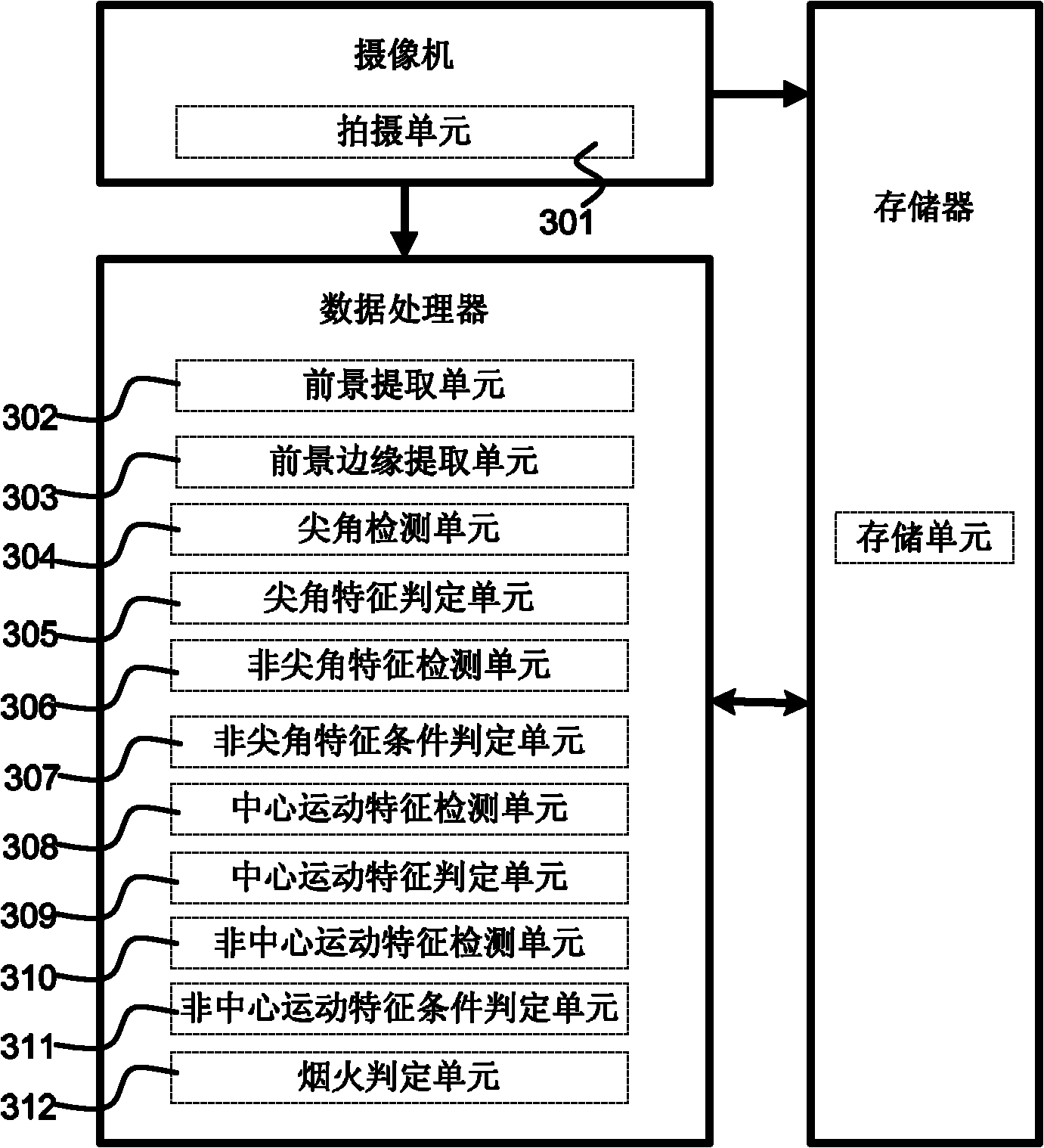
InactiveCN101944267AImprove recognition accuracyReduce false alarm ratePhotogrammetry/videogrammetryClosed circuit television systemsSharp angleReporting rate
The invention discloses a smoke and fire detection device based on videos, which is characterized by acquiring the edge shape of the foreground area by a shooting unit, a foreground extracting unit and a foreground edge extracting unit; judging whether the foreground area has flame sharp angle feature by a sharp angle detecting unit and a sharp angle feature judging unit; judging whether the foreground area has the smoke center movement feature by a center movement feature detecting unit and a center movement feature judging unit; and finally judging whether the smoke and fire exist by a smoke and fire judging unit according to the results obtained by the sharp angle feature judging unit and the center movement feature judging unit. The device and the method have the advantages of high recognition accuracy, low misdeclaration rate and missing report rate, capability of effectively removing external factor interference such as illumination, shadow, etc.
Owner:FURUNO SOFTECH DALIAN
Combined type intrusion detecting method on basis of data fusion of improved core vector machine
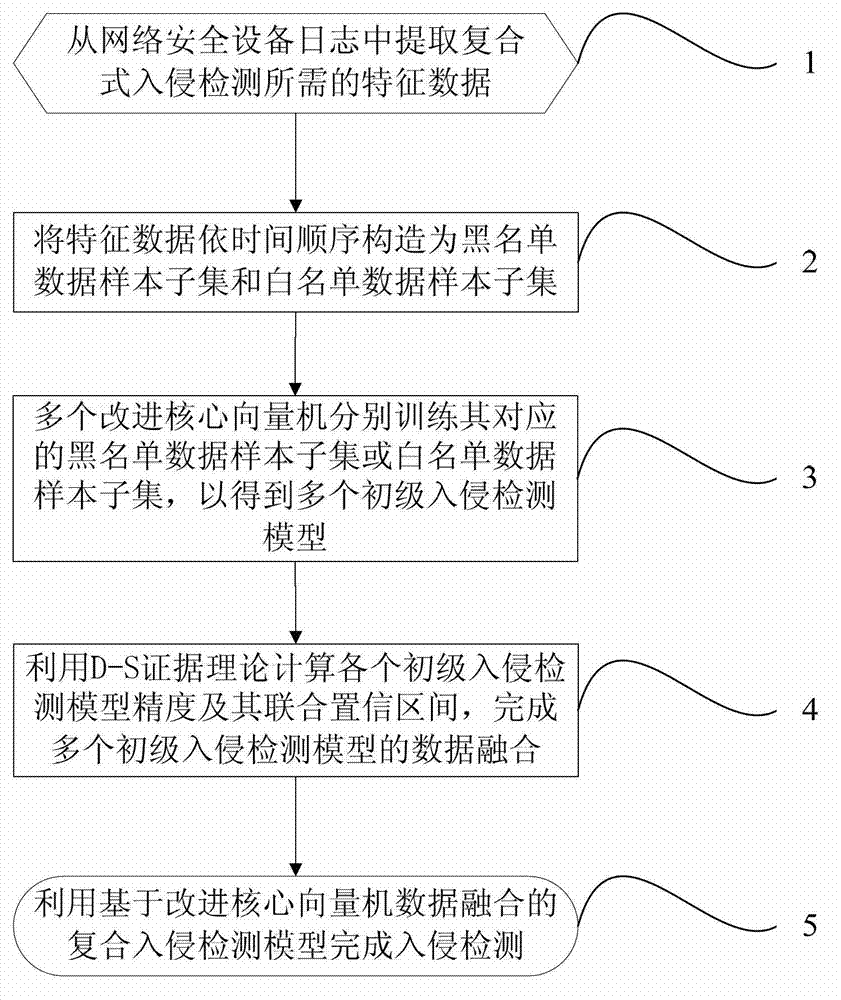
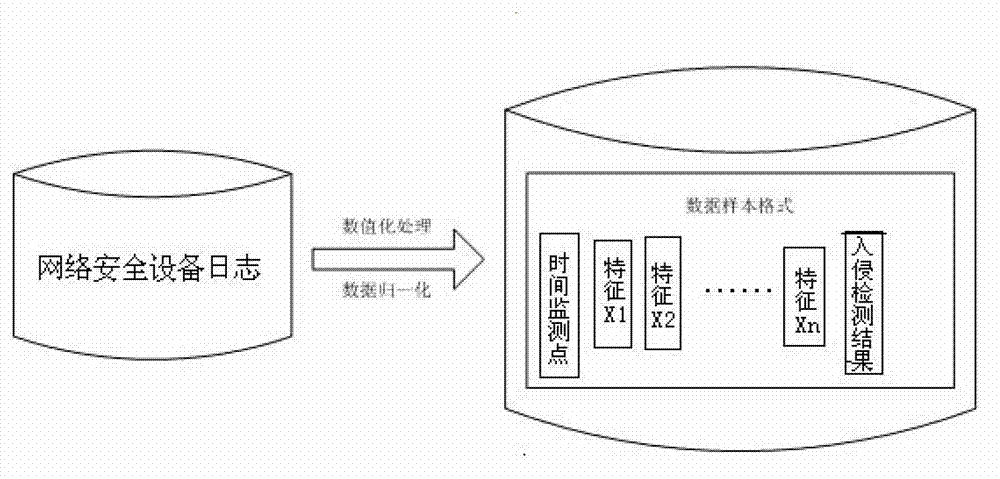
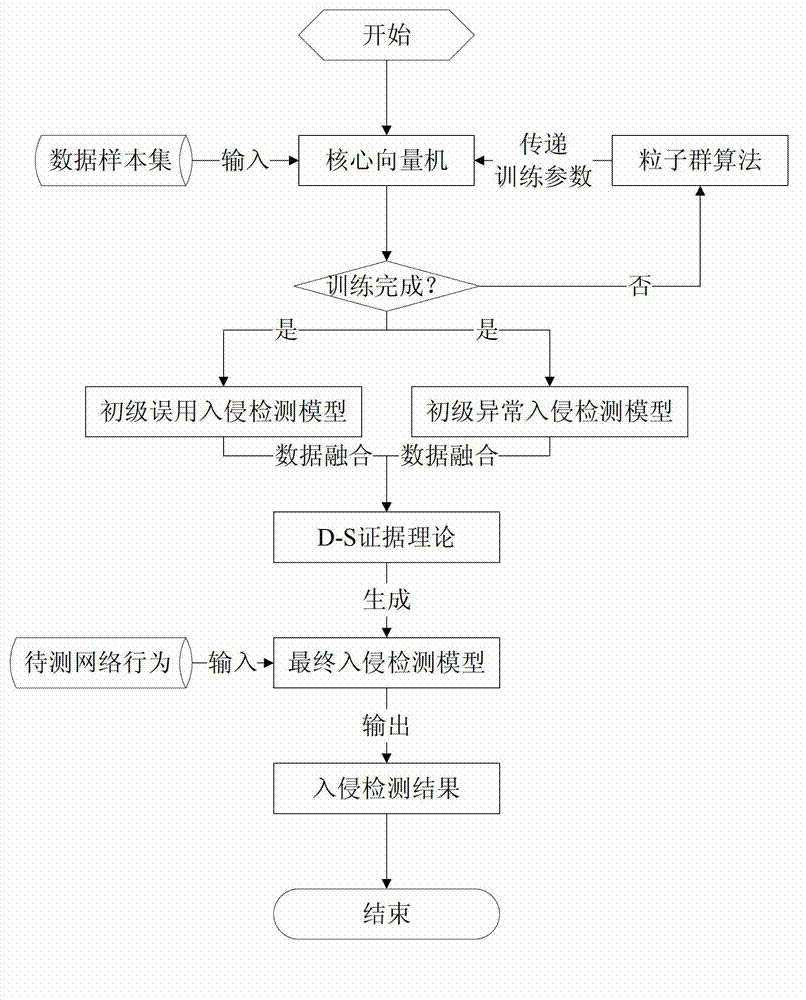
ActiveCN103077347AImprove real-time performanceImprove recognition accuracyPlatform integrity maintainanceCore vector machineConfidence interval
The invention discloses a combined type intrusion detecting method on the basis of data fusion of an improved core vector machine, which belongs to the technical field of network safety. The method comprises the following steps: extracting characteristic data of all time monitoring points required by misuse intrusion detection and abnormal intrusion detection from a network safety equipment log of a target network; respectively constructing the characteristic data into black and white list data sample subsets; training the black and white list data sample subsets, thereby respectively obtaining a primary misuse intrusion detection model and a primary abnormal intrusion detection model; realizing the data fusion of the primary misuse intrusion detection model and the primary abnormal intrusion detection model through a D-S evidence theory, thereby obtaining a combined intrusion detection model and a combined confidence interval of the combined intrusion detection model; and obtaining a final detecting result. The method provided by the invention has excellent properties at the aspects of increasing the instantaneity of an intrusion detecting system, reducing the missing report rate and false report rate of the intrusion detecting system and increasing the generalization of the intrusion detecting system.
Owner:CHINA ELECTRIC POWER RES INST +2
SQL (structured query language) injection attack defensive system and defensive method based on grammar transformation
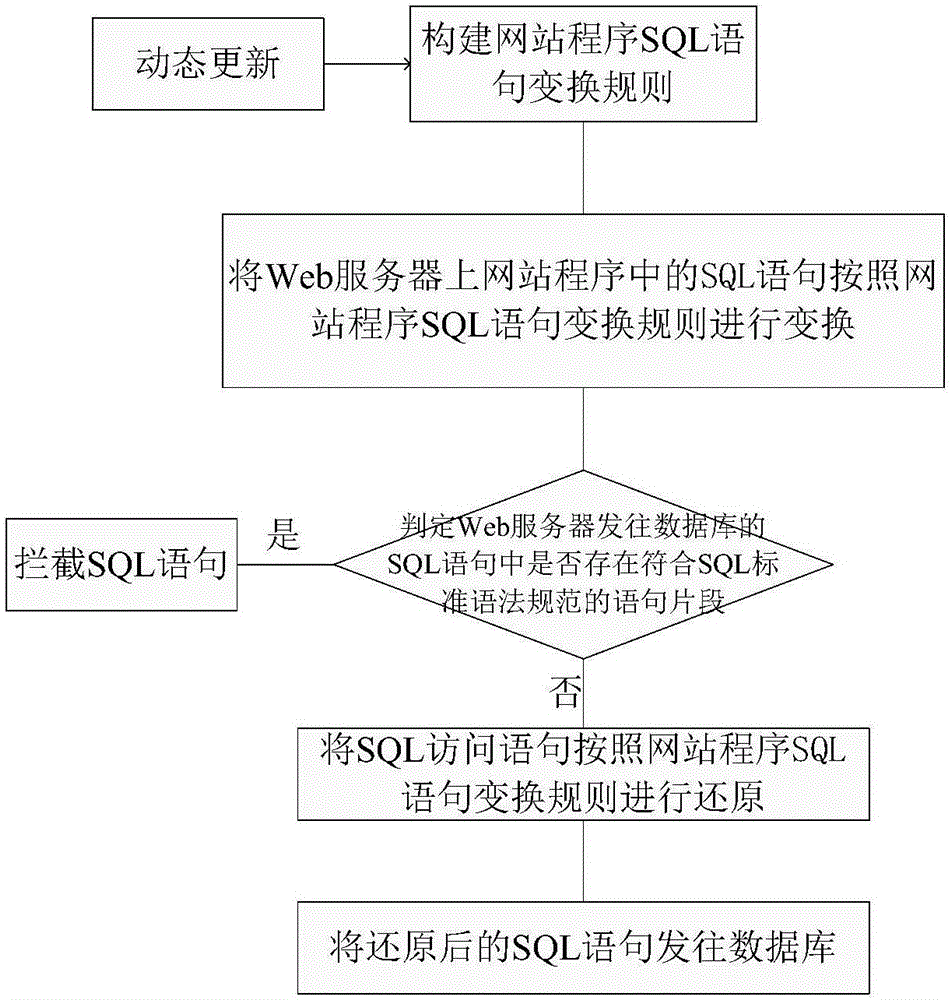
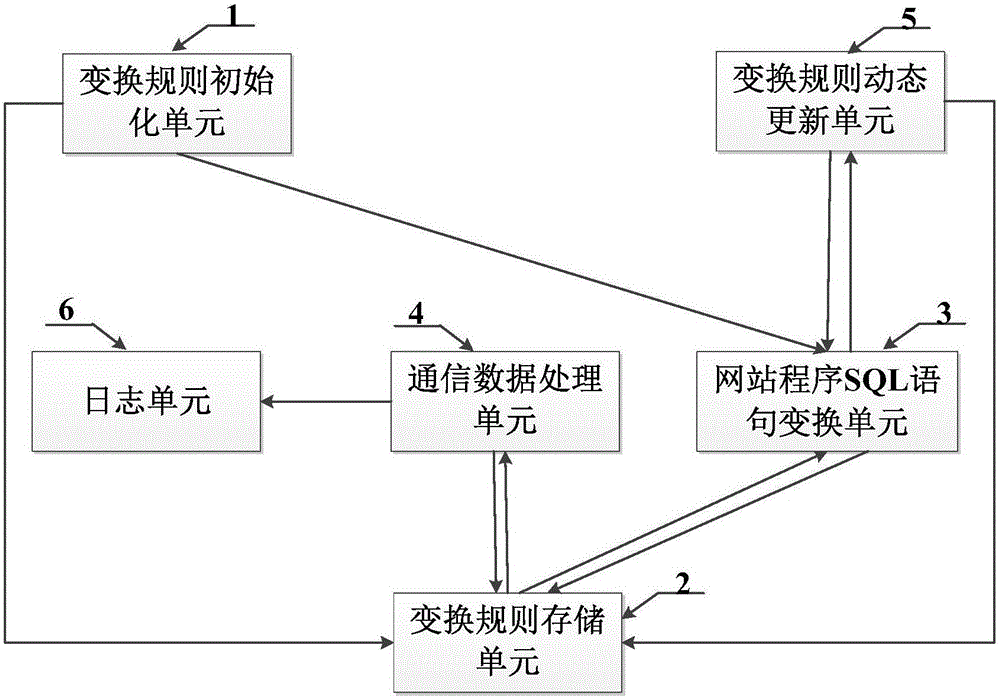
ActiveCN106355094AReduce development and maintenance costsReduce false alarm ratePlatform integrity maintainanceWeb serviceSQL injection
The invention provides an SQL (structured query language) injection attack defensive system and method based on grammar transformation. The SQL statement transformation rule of website program is built; SQL statements in the website program on a Web server are subjected to initialization transformation operation; whether attack statements are injected into SQL access statements sent to a database by the Web server or not is judged; the SQL statement transformation rule of the website program is dynamically transformed, so that the effective defense on the SQL injection attack is realized. The SQL injection attack defensive system and method based on grammar transformation do not depend on rules; the vicious SQL injection attack is precisely recognized on the basis of statement transformation and grammatical analysis; the false alarm rate and the missing report rate are extremely low; the system and the method are applicable to various types of Web servers and database systems; the SQL injection attack behavior can be effectively defensed; the safety protection on the Web server and a background database is obviously improved.
Owner:北京卫达信息技术有限公司
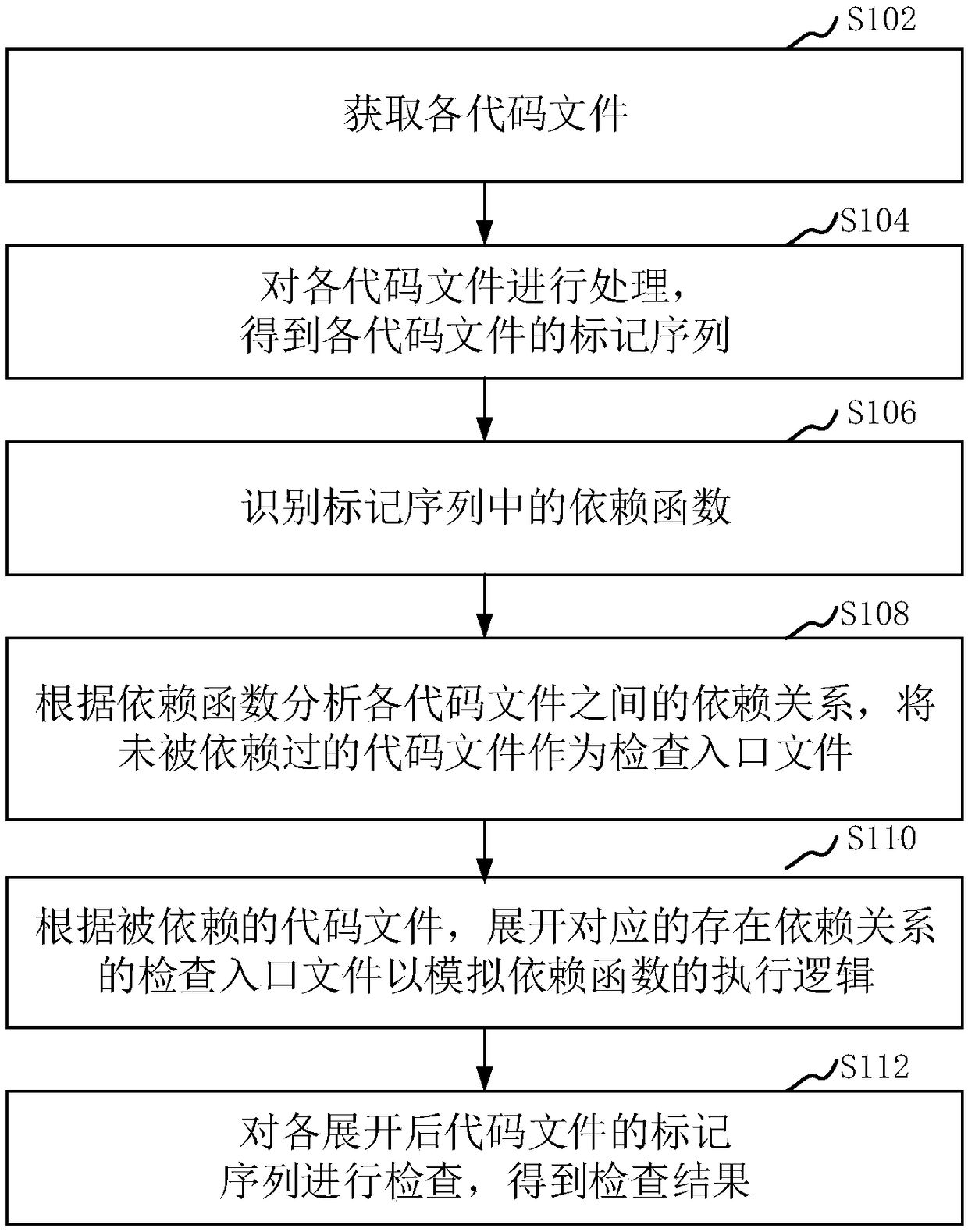
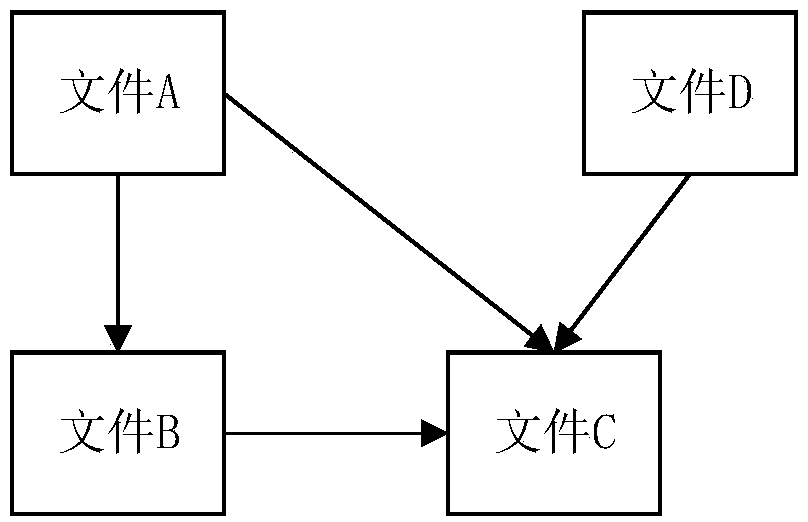
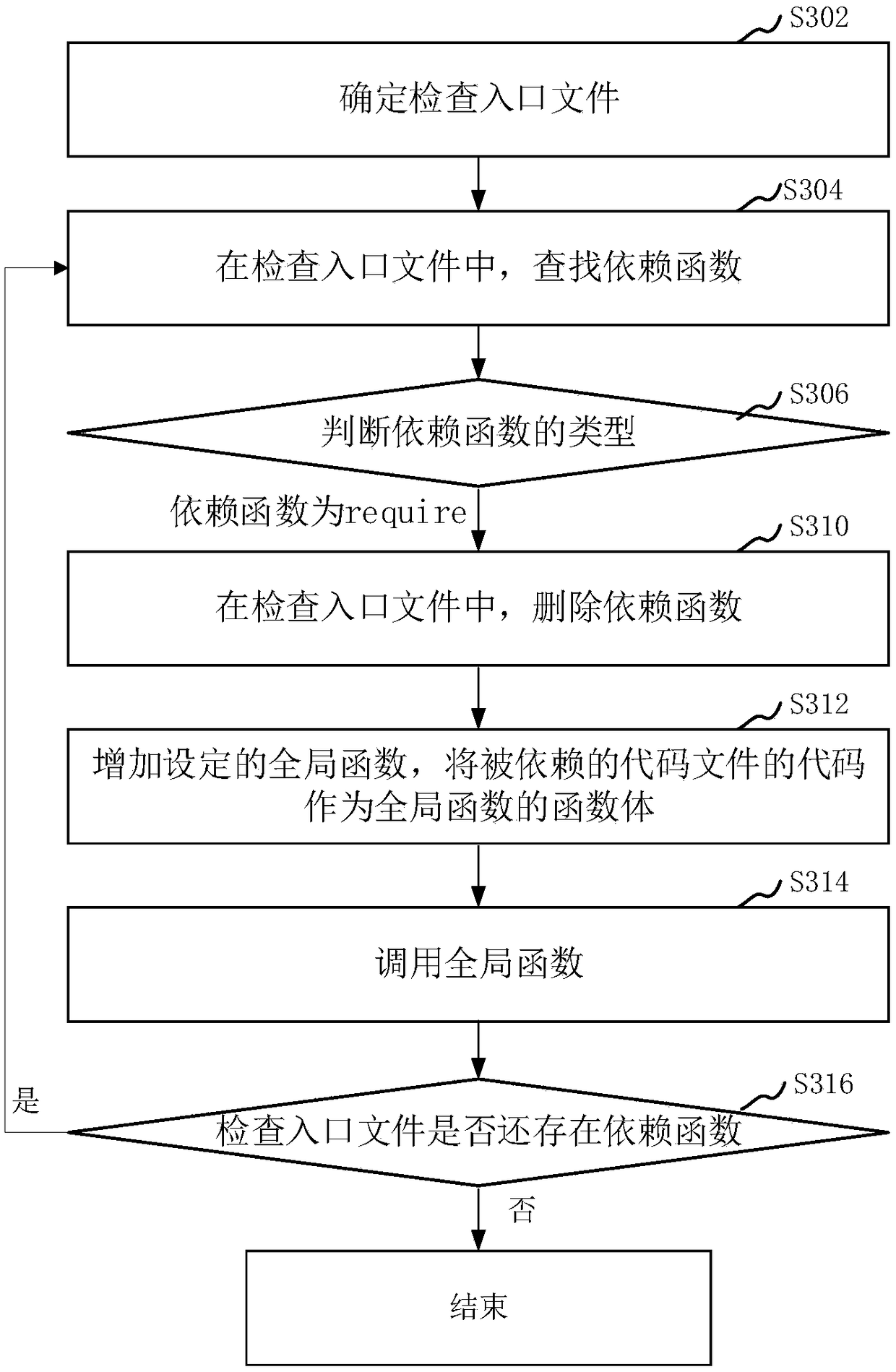
Static code check method and apparatus, storage medium and computer device
ActiveCN108614707AImprove accuracyReduce false alarm rateSoftware testing/debuggingCode compilationReporting rateInspection method
The invention relates to a static code check method and apparatus, a storage medium and a computer device. The method comprises the steps of obtaining code files; processing the code files to obtain amarker sequence of the code files; identifying a dependency function in the marker sequence; according to the dependency function, analyzing a dependency relationship between the code files, and taking the code files which other code files do not depend on as check entry files; according to the code files which other code files depend on, expanding the corresponding check entry files with the dependency relationship to simulate executive logic of the dependency function; and checking the marker sequence of the expanded code files to obtain a check result. The method considers characteristicsof global variable distribution in different files, and realizes cross-file static code check processing of codes, thereby reducing the false report rate of global variable check.
Owner:SHENZHEN TENCENT NETWORK INFORMATION TECH CO LTD
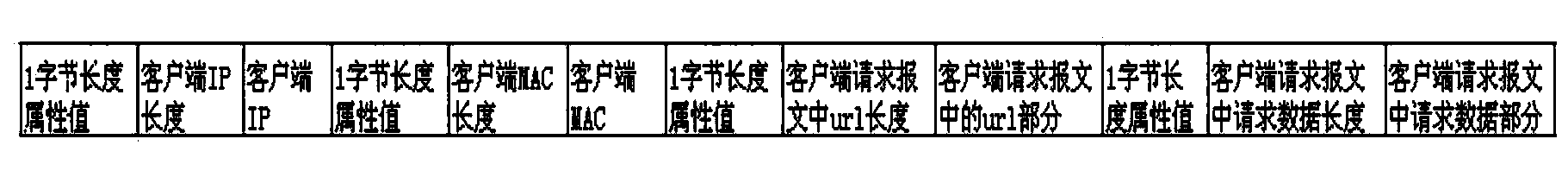
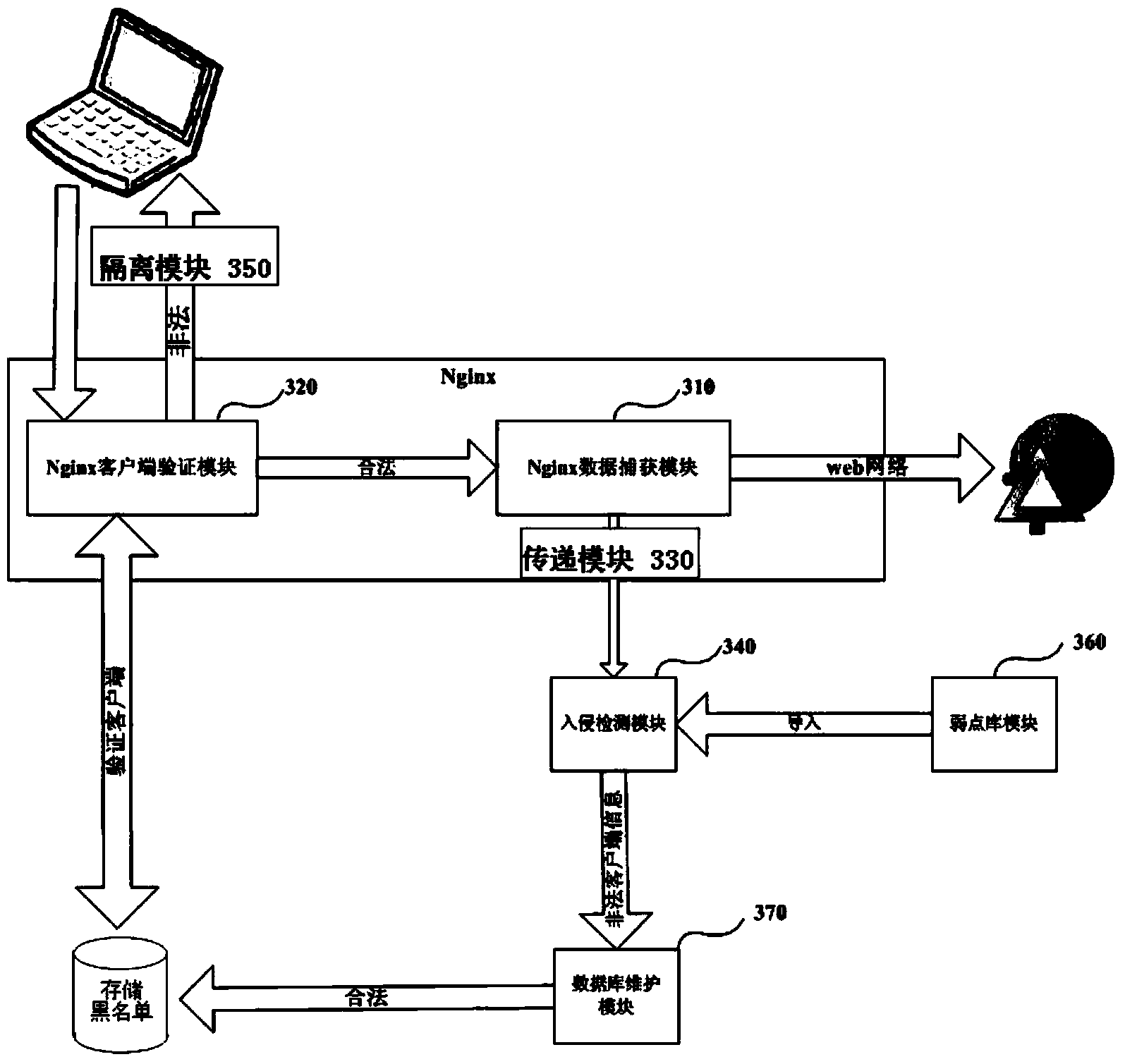
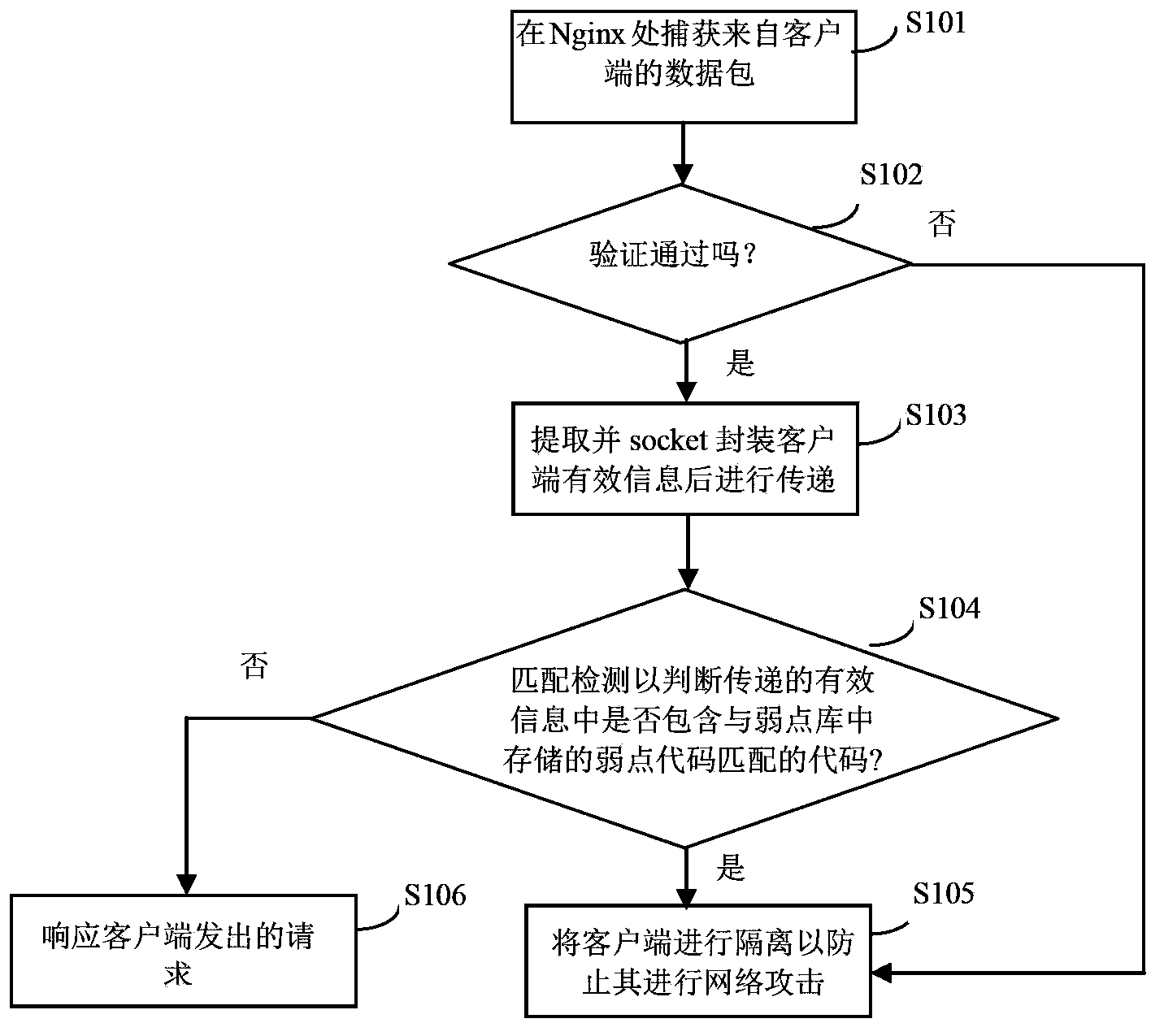
Intrusion detection method and system based on Nginx proxy server
The invention provides an intrusion detection method based on a Nginx proxy server. The intrusion detection method comprises the capture step, the verification step, the transmitting step, the matching detection step and the isolation step. According to the capture step, data packages from all client ends are captured on the Nginx proxy server. According to the verification step, validity verification is conducted on the captured data packages, and whether the data packages carry legal certificates distributed by a certificate server is verified. According to the transmitting step, the effective information in the passed data packages of the client ends is extracted, packaged and then transmitted. According to the matching detection step, the transmitted effective information is received, matching detection is conducted on the effective information according to weakness codes stored in a weakness library, and whether the effective information contains codes matched with the weakness codes stored in the weakness library is judged. According to the isolation step, the client ends are isolated to prevent the client ends from conducting hostile attack on a network. The intrusion detection method and system can lower the false report rate and the miss report rate due to the fact that the response speed of a detecting system is far smaller than the transmission speed of the network, and the safety of a server end is guaranteed maximally.
Owner:CHINA STANDARD SOFTWARE
Method and system for detecting phishing website based on SEO (search engine optimization)
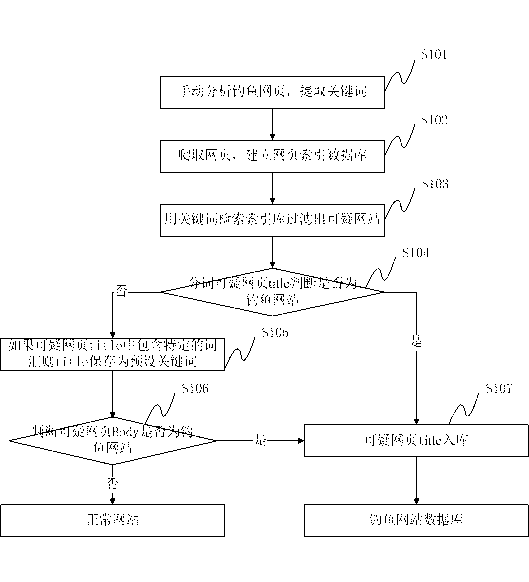
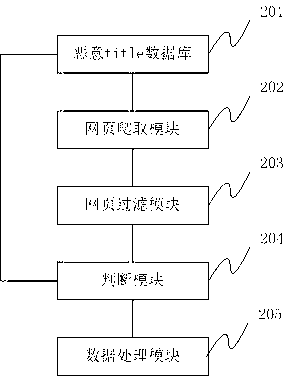
InactiveCN103324615AHigh trafficNarrow your searchTransmissionSpecial data processing applicationsPhishingUniform resource locator
The invention provides a method for detecting a phishing website based on SEO. The method comprises the steps as follows: the known phishing website is analyzed, and a title of the known phishing website is taken as a keyword and added into a malicious title database; a webpage obtained by saving a webpage crawler, and a webpage index database is built after an obtained webpage abstract and a corresponding URL (uniform resource locator) are filtered and reabsorbed; the webpage abstract in the webpage index database is retrieved by using the keyword in the malicious title database and / or a preset keyword, and a successfully matched webpage is saved as a suspicious webpage; and the suspicious webpage is judged with a judgment strategy, the title of the suspicious webpage which is judged to be the phishing website is added into the malicious title database. The invention further discloses a system for detecting the phishing website based on the SEO. According to the method and the system for detecting the phishing website based on the SEO, the retrieval range is reduced by abstracting the keyword, active crawling and judgment are performed on the website and the database is updated continuously, the false alarm rate is decreased, the obtained phishing website is judged automatically, and the missing report rate is reduced.
Owner:HARBIN ANTIY TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com