Intrusion detection method and system based on Nginx proxy server
A proxy server and intrusion detection technology, applied in the computer field, can solve the problems that the security needs to be improved, the intrusion detection system cannot notify the server client in time, etc., so as to reduce the load, ensure security, and reduce the false alarm rate and leakage. The effect of rate of return
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
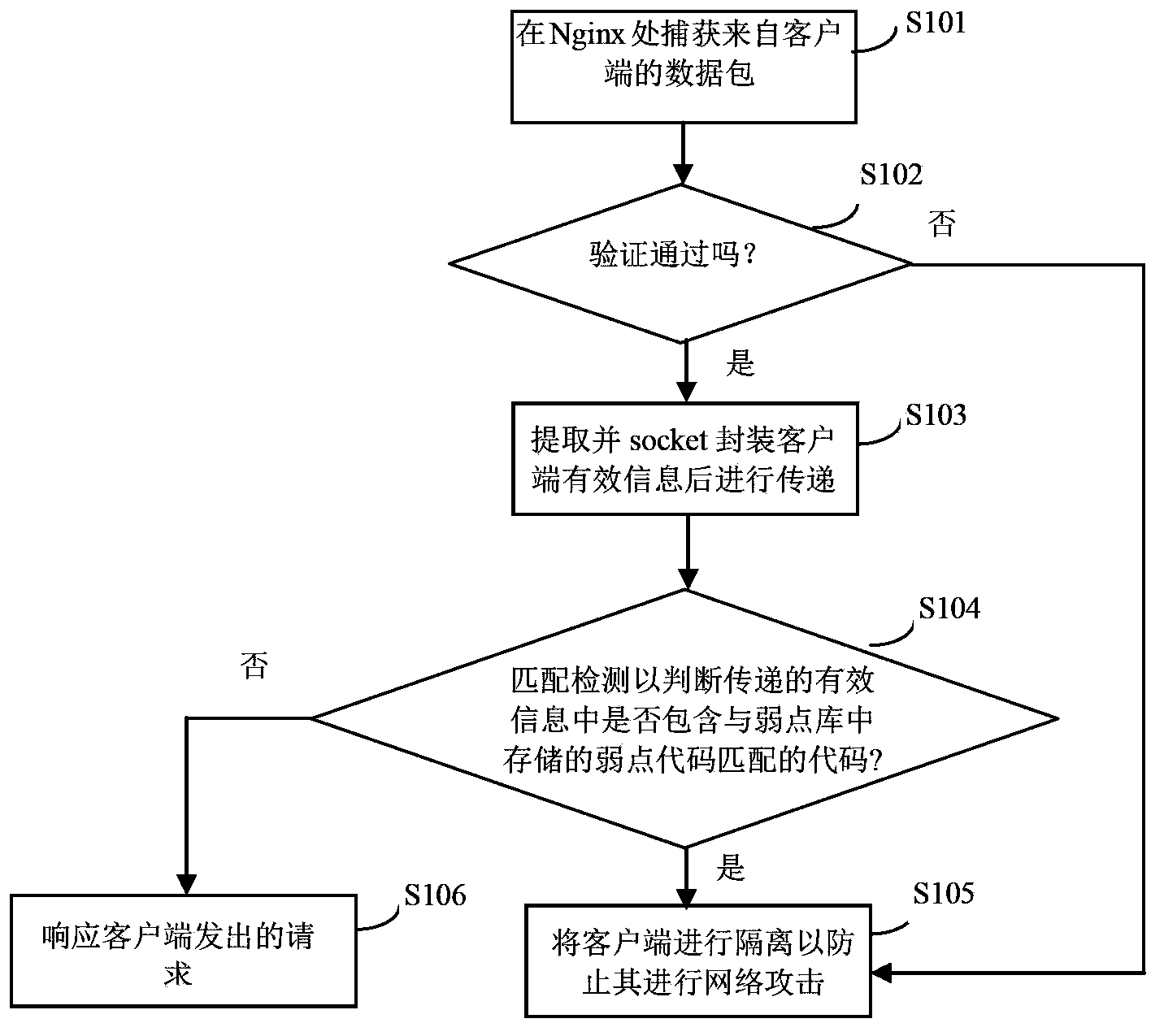
[0042] like Figure 1a Shown, wherein shows the flowchart of the intrusion detection method based on Nginx proxy server according to an embodiment of the present invention.
[0043] First, in the capture step, when the client sends a data packet containing the request message to the network, the Nginx proxy server captures the data packets from each client by it, as shown in step S101.
[0044] The client request first reaches the proxy server Nginx. In order to improve the response speed of the proxy server, the captured data is implemented as an embedded module on Nginx, which can be directly obtained through the built-in variables in Nginx.
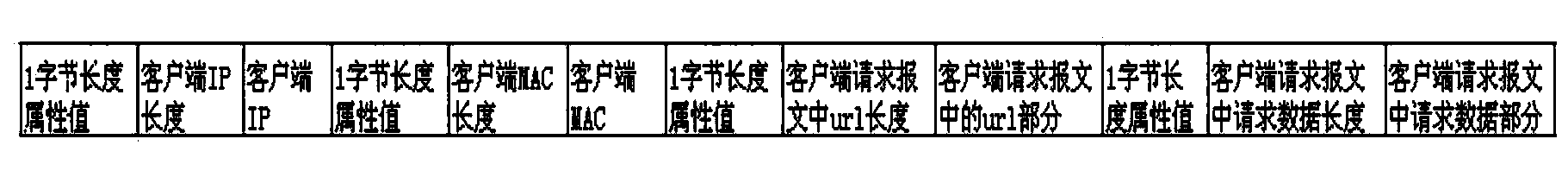
[0045]Nginx can capture all content in the HTTP (Hyper-text Transfer Protocol) request message. Among them, the effective information of the client data packet captured from the network includes: client IP, client MAC, client session (Session) information, and the web page address (Uniform Resource Locator, URL) in the client HTTP requ...
no. 2 example
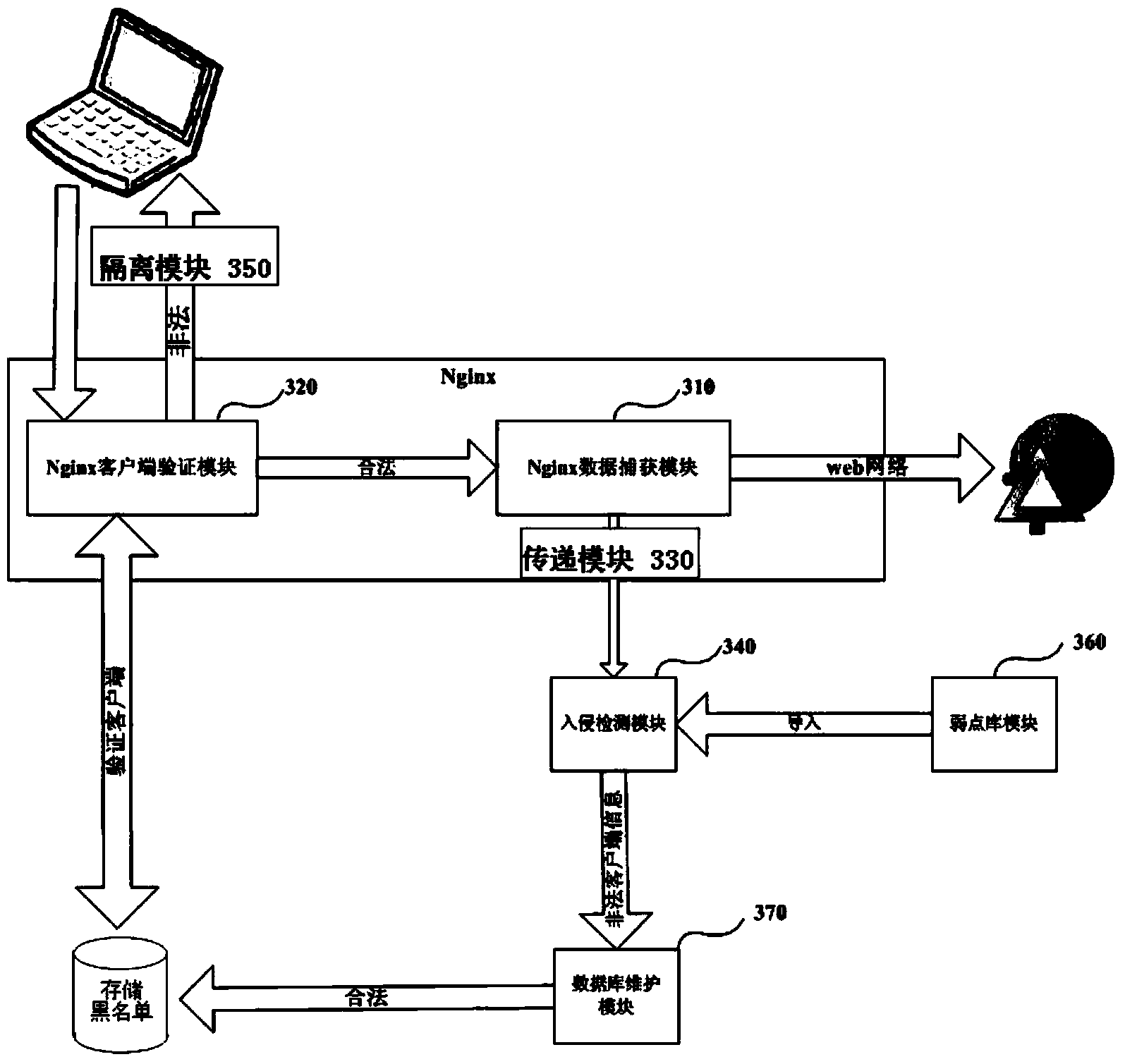
[0063] like image 3 Shown, wherein shows the intrusion detection system based on Nginx proxy server of the present invention. it includes:
[0064] Nginx data capture module 310, it is located in the Nginx proxy server, is used for capturing the packet from each client from the proxy server side;
[0065] Nginx client verification module 320, it communicates with Nginx data capture module 310, carries out legitimacy verification to captured data packet, verifies whether data packet carries the legal certificate that authentication server distributes, if yes, communicates with transfer module 330, If not, communicating with the isolation module;
[0066] Delivery module 330, which is used to extract valid information in the verified client data packet and deliver it after encapsulation in socket form;
[0067] Matching detection module 340, which is used to receive the transmitted effective information, and perform matching detection on the effective information according t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com