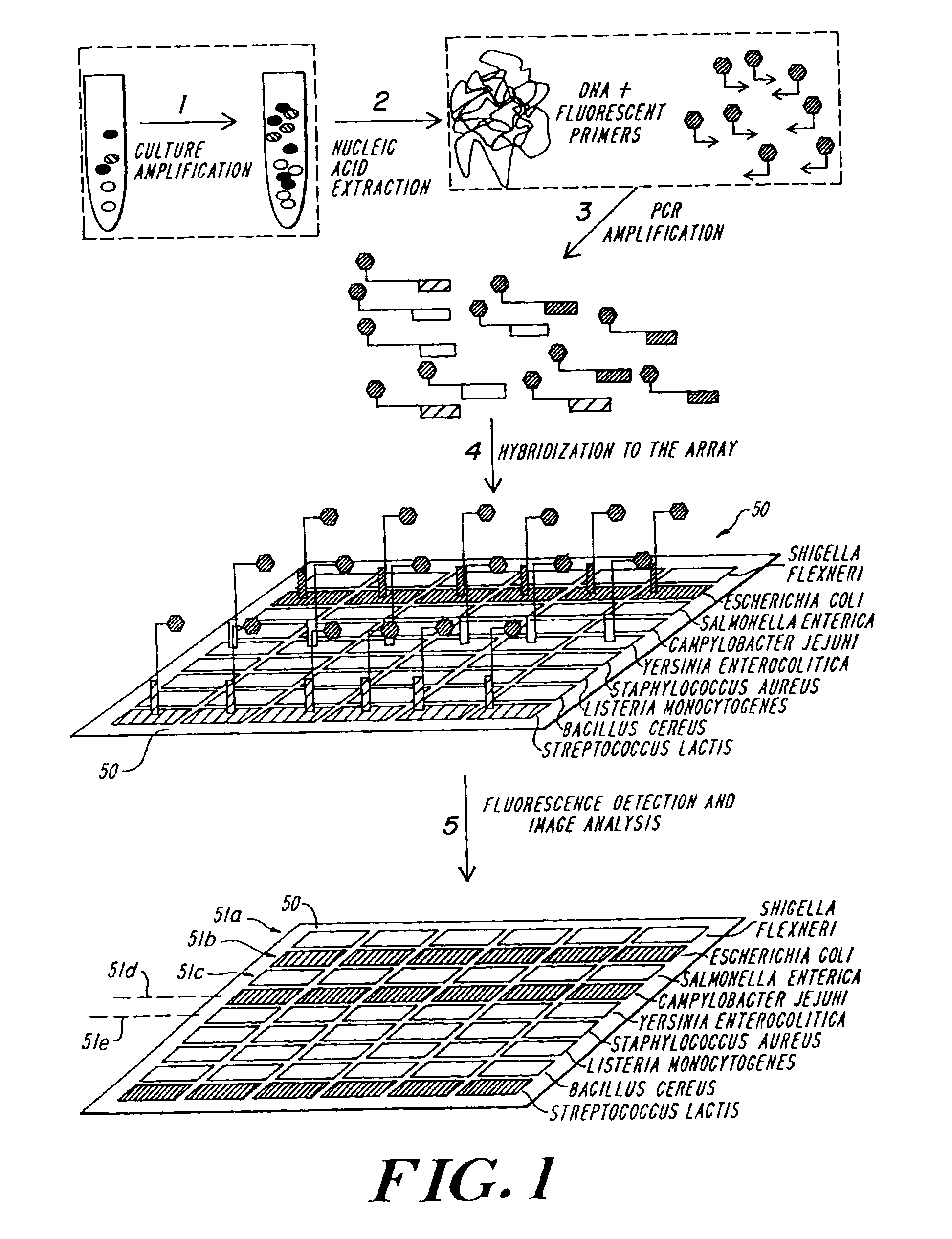
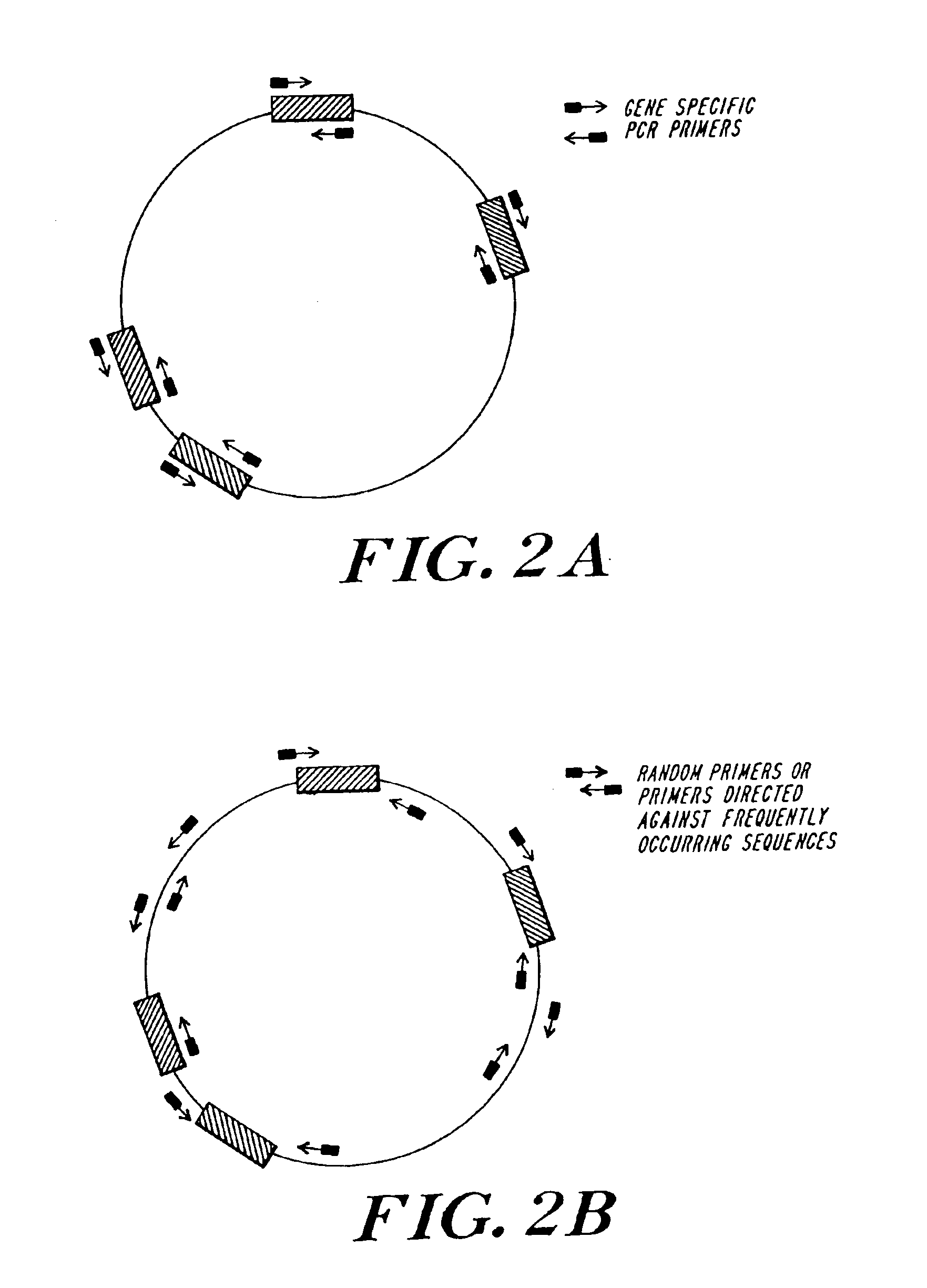
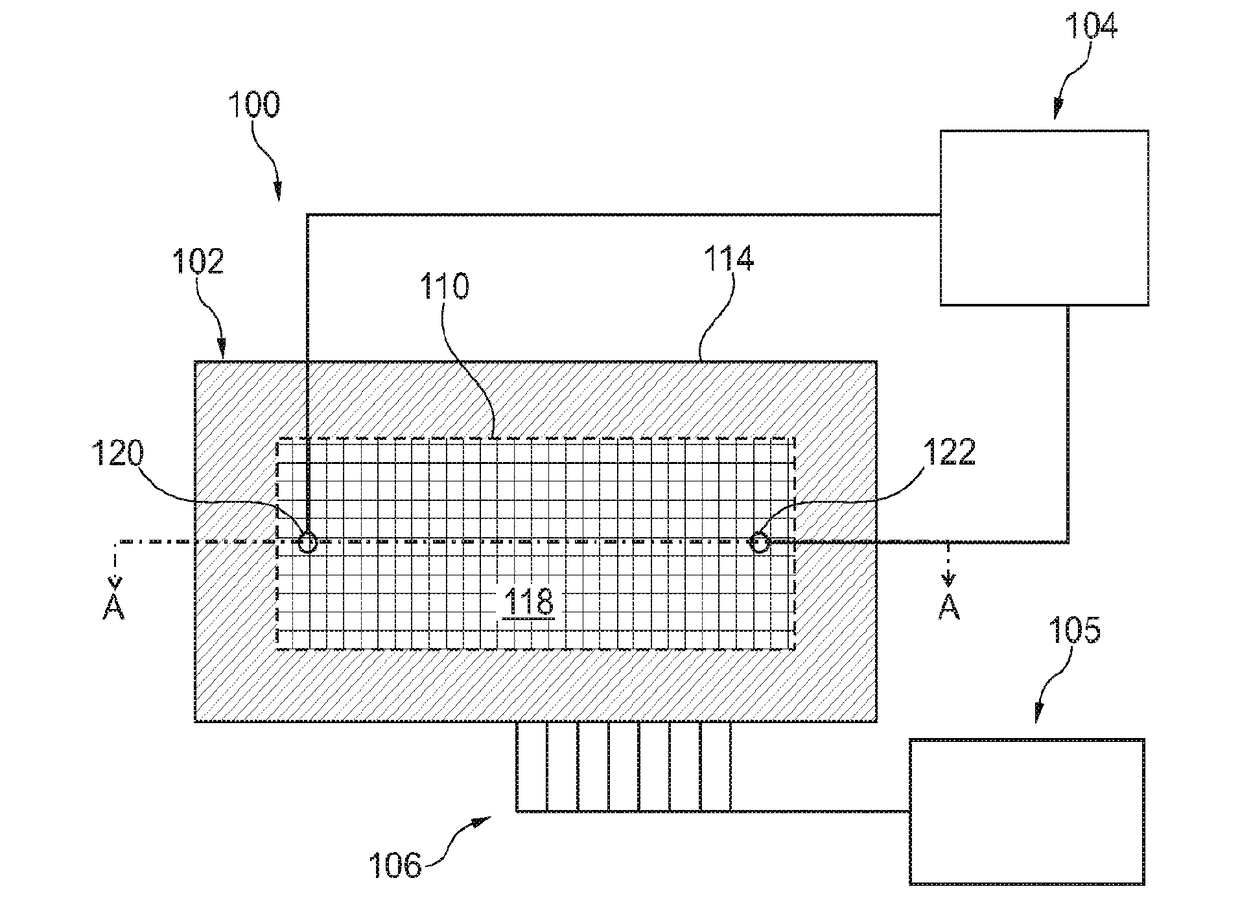
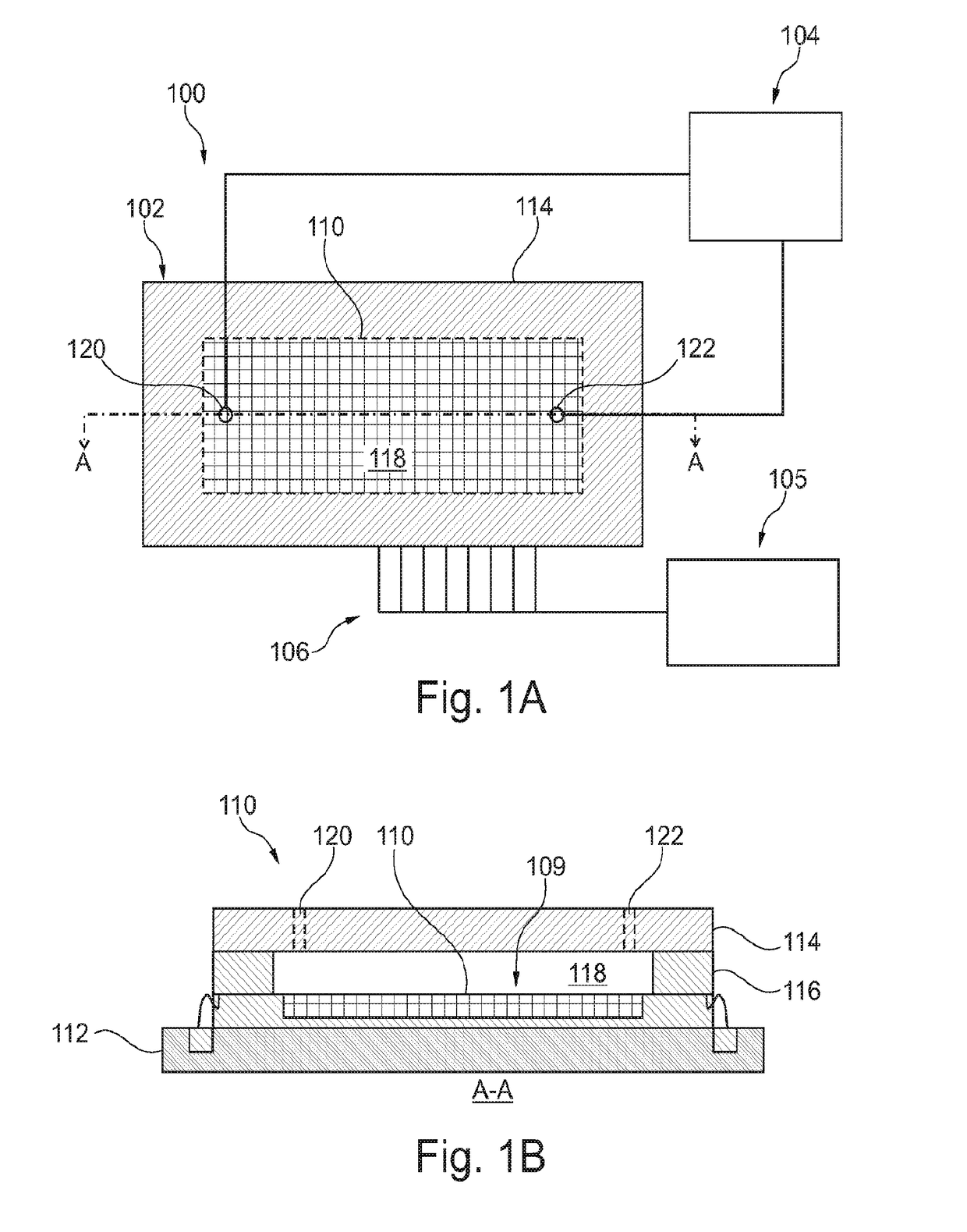
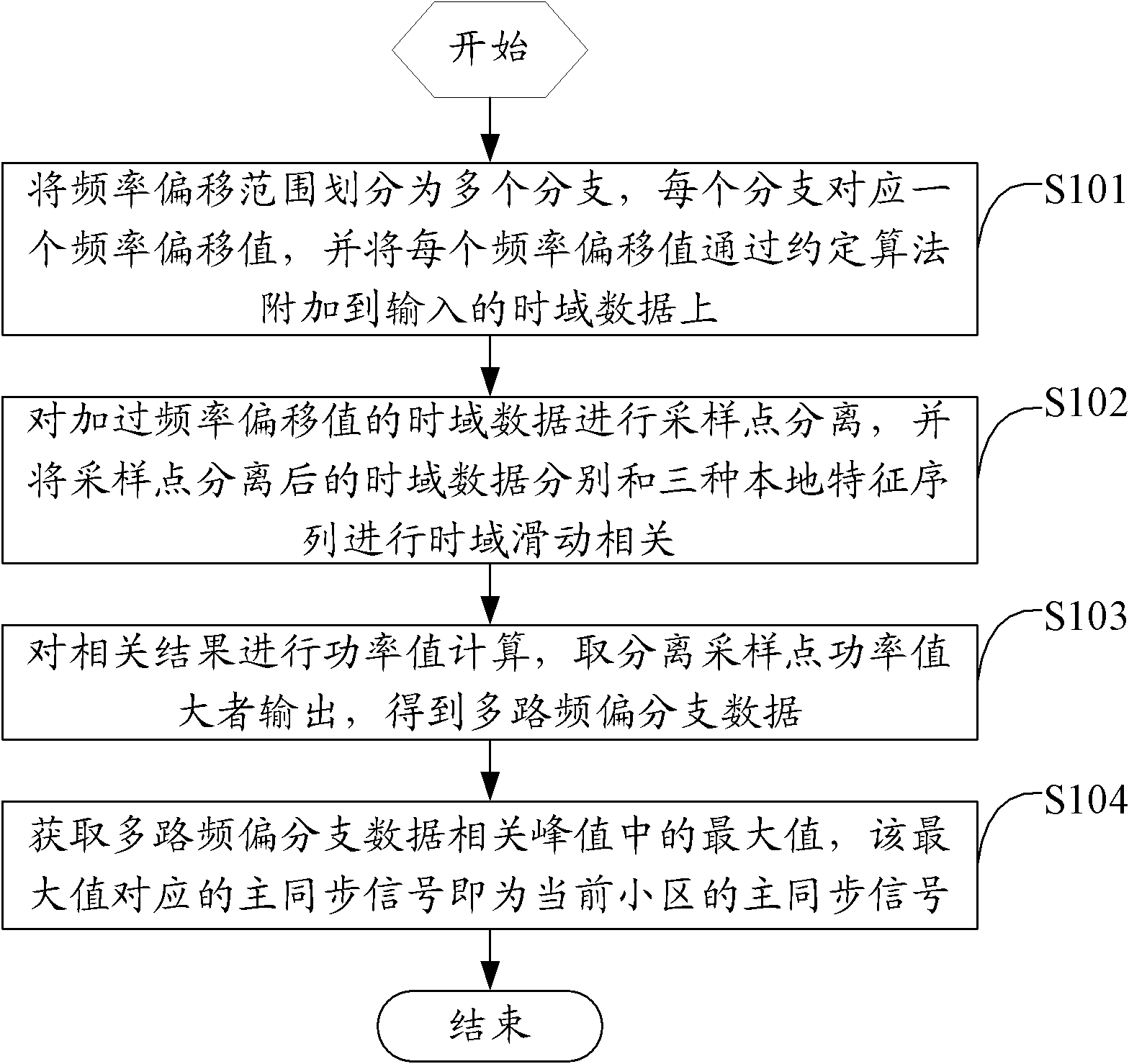
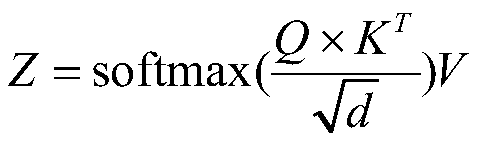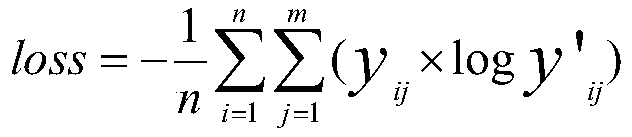Patents
Literature
313 results about "Characteristic sequence" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
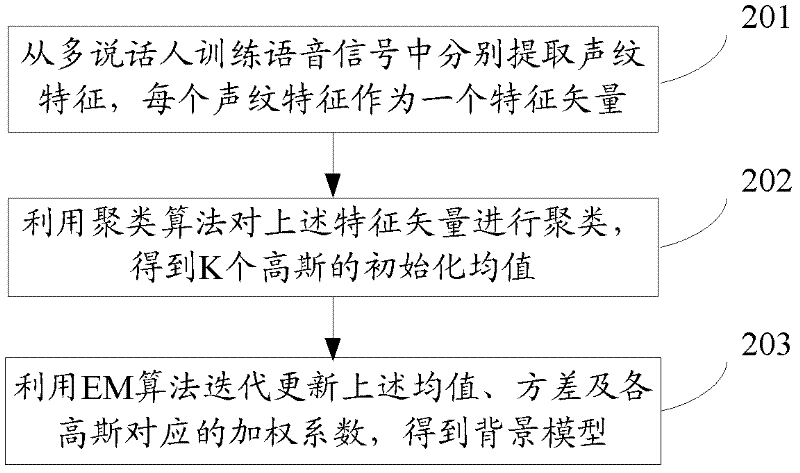
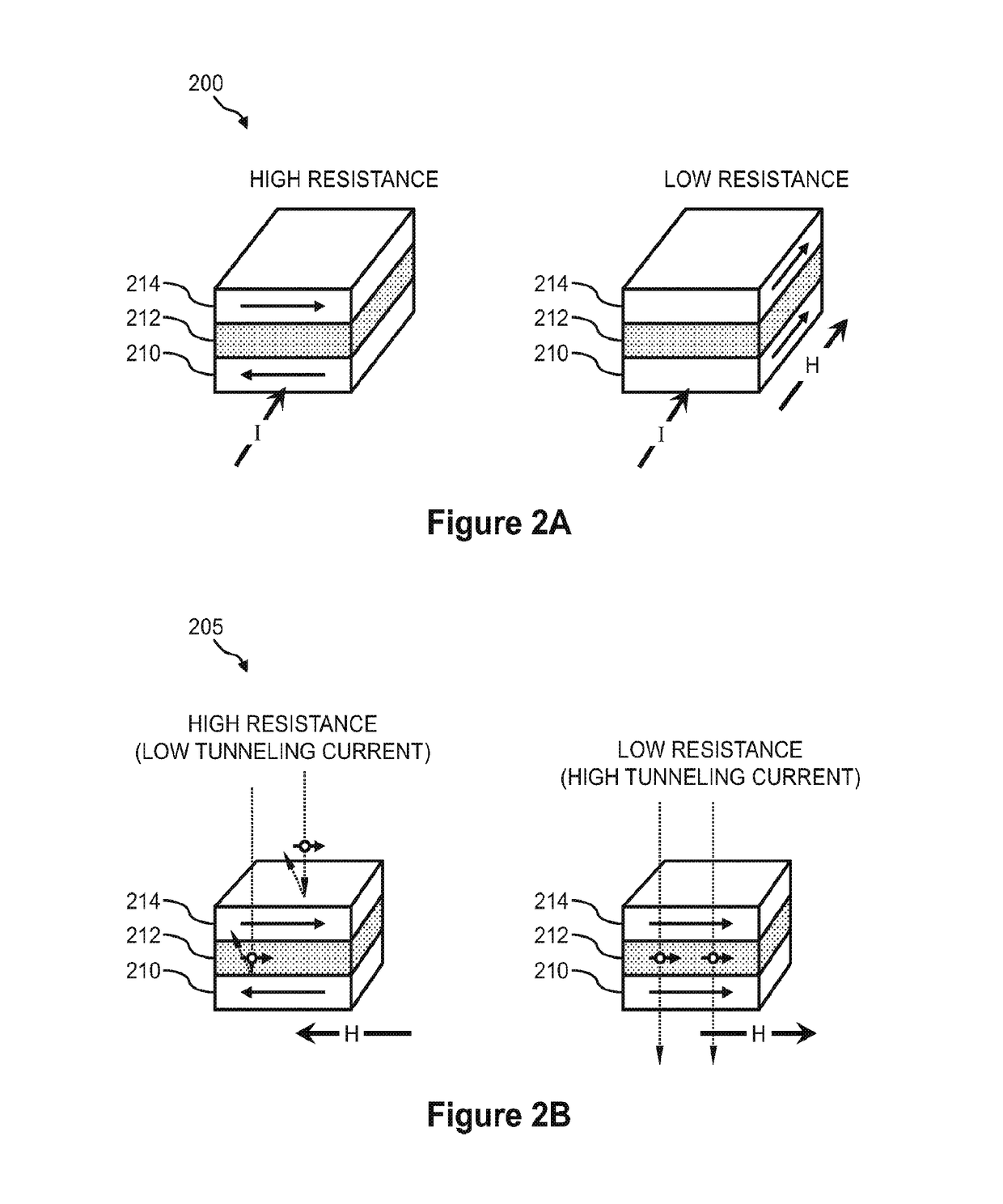
Probably the most fundamental characteristic of a sequence of numbers is its distribution. The PRNGs in the ThinAir library (with a few exceptions) produce uniformly distributed number sequences. Other distributions include normal, Poisson, geometric, binomial, and student-t.
Personalized recommendation method based on deep learning
InactiveCN110196946AReduce serial operationsImprove training efficiencyDigital data information retrievalAdvertisementsPersonalizationRecommendation model
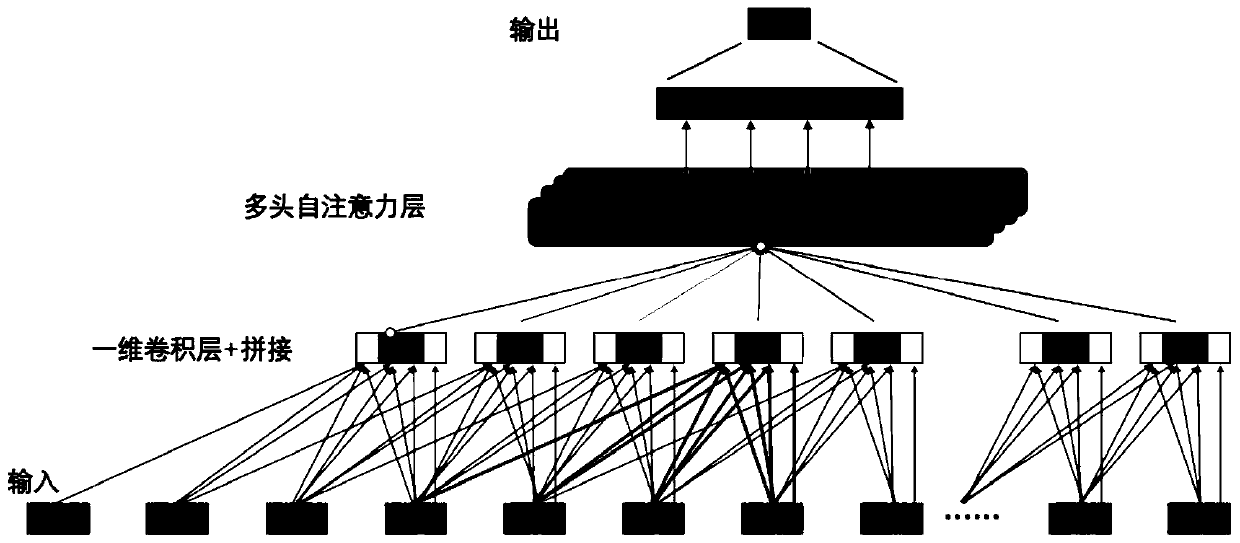
The invention discloses a personalized recommendation method based on deep learning. The method comprises the steps of according to the viewing time sequence behavior sequence of the user, predictingthe next movie that the user will watch, including three stages of preprocessing the historical behavior characteristic data of the user watching the movie, modeling a personalized recommendation model, and performing model training and testing by using the user time sequence behavior characteristic sequence; at the historical behavior characteristic data preprocessing stage when the user watchesthe movie, using the implicit feedback of interaction between the user and the movie to sort the interaction data of each user and the movie according to the timestamp, and obtaining a corresponding movie watching time sequence; and then encoding and representing the movie data,wherein the personalized recommendation model modeling comprises the embedded layer design, the one-dimensional convolutional network layer design, a self-attention mechanism, a classification output layer and the loss function design. According to the method, the one-dimensional convolutional neural network technologyand the self-attention mechanism are combined, so that the training efficiency is higher, and the number of parameters is relatively small.
Owner:SOUTH CHINA UNIV OF TECH
Behavior recognition technical method based on deep learning
PendingCN110188637AGood feature expression abilityEasy to useCharacter and pattern recognitionNeural architecturesVideo monitoringNetwork model
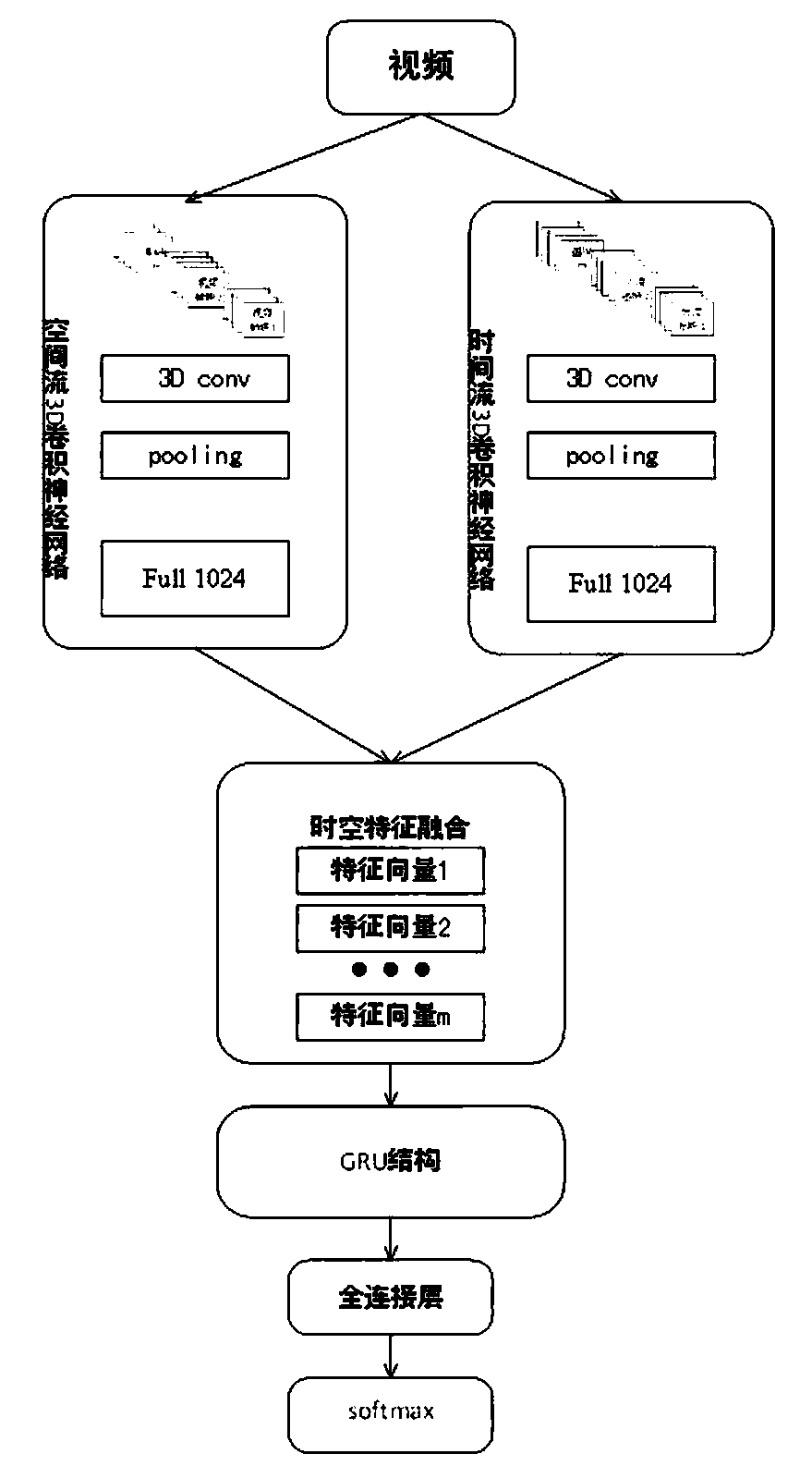
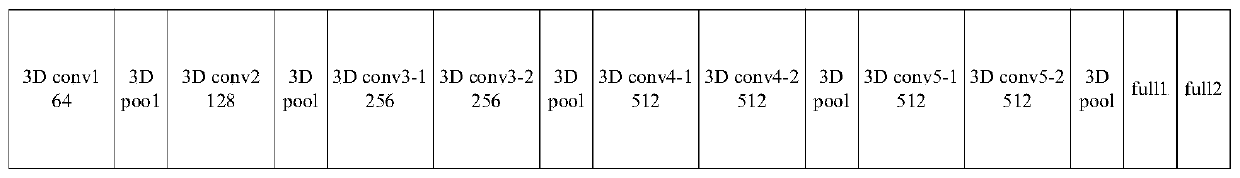
The invention discloses a behavior recognition technical method based on deep learning, which solves a problem that the intelligentization of a video monitoring system in the prior art needs to be improved. The method comprises the following steps of constructing a deeper space-time double-flow CNN-GRU neural network model by adopting a mode of combining a double-flow convolutional neural networkand a GRU network; extracting the time domain and space domain features of the video; extracting the long-time serialization characteristics of the spatial-temporal characteristic sequence according to the capability of the GRU network for memorizing information, and carrying out the behavior recognition of a video through employing a softmax classifier; proposing a new related entropy-based lossfunction; and with the help of a method for processing the mass information by referring to a human brain visual nerve attention mechanism, introducing an attention mechanism before a space-time double-flow CNN-GRU neural network model performs space-time feature fusion. The accuracy of the model provided by the technology is 61.5%, and compared with an algorithm based on a double-flow convolutional neural network, the recognition rate is improved to a certain extent.
Owner:XIDIAN UNIV
Voiceprint password authentication method and system
ActiveCN102238189AImprove accuracyUser identity/authority verificationSpeech analysisPasswordAuthentication system
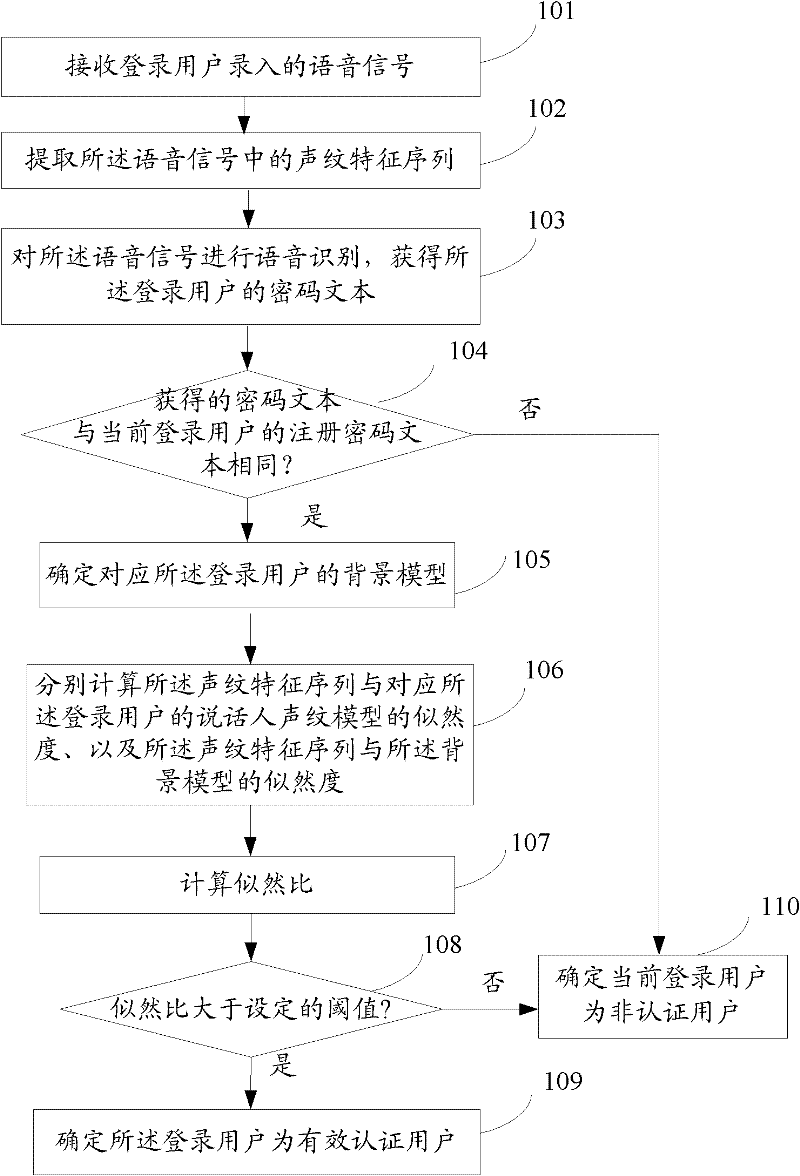
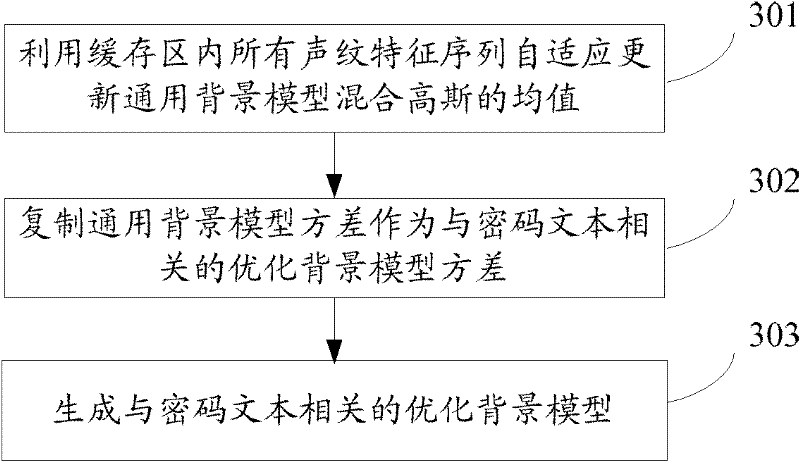
The invention discloses a voiceprint password authentication method and a voiceprint password authentication system. The method comprises the following steps of: receiving a voice signal recorded by a login user; extracting a voiceprint characteristic sequence from the voice signal; performing voice recognition on the voice signal to obtain the password contents of the login user; if the obtained password contents are different from a registration password text, determining the login user is an unauthenticated user; otherwise computing likelihood between the voiceprint characteristic sequence and each of a speaker voiceprint mode corresponding to the login user and a background model selected for the login user, wherein the background model comprises a text-unrelated universal background model and a text-related optimized background model; computing a likelihood ratio according to the obtained likelihood; and if the likelihood is greater than a preset threshold value, determining the login user is an effectively authenticated user, otherwise determining the login user is the unauthenticated user. By the method and the system, the voiceprint password authentication accuracy can be improved.
Owner:IFLYTEK CO LTD
Speaker recognition method and system
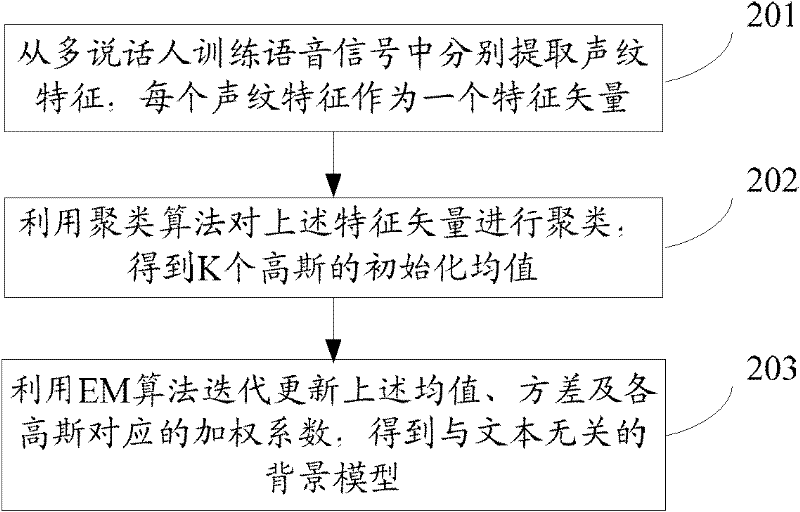
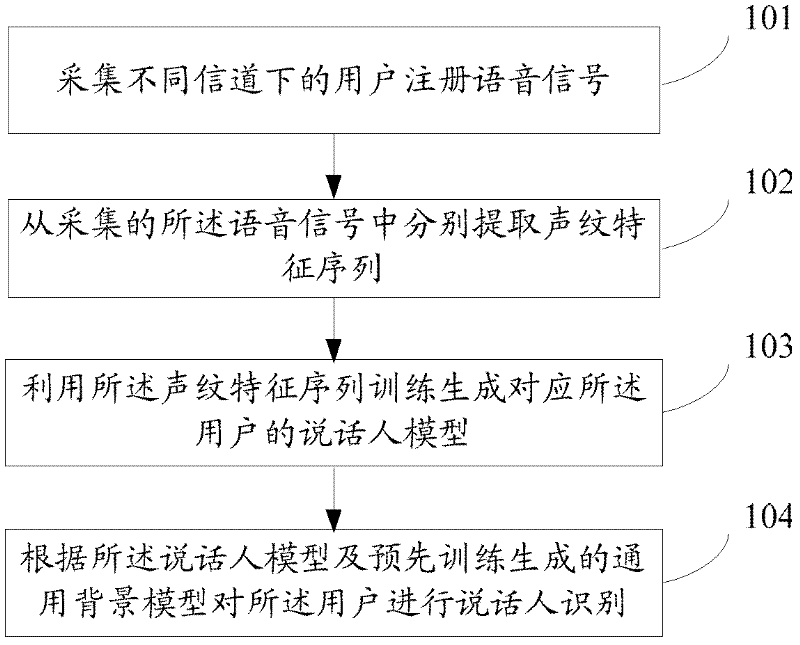
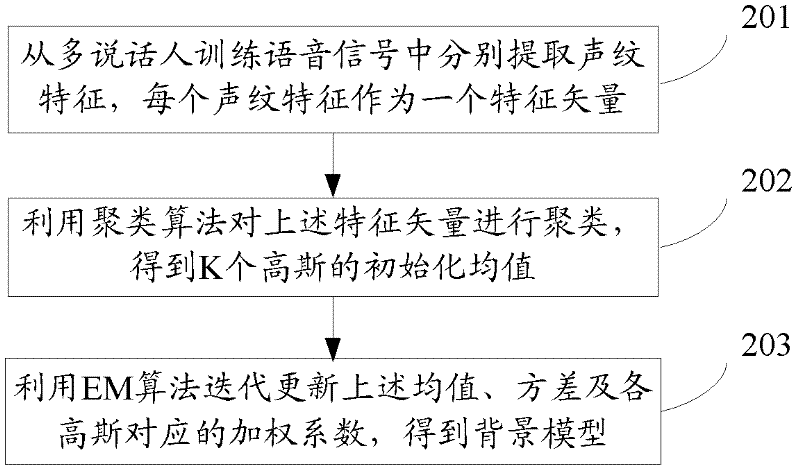
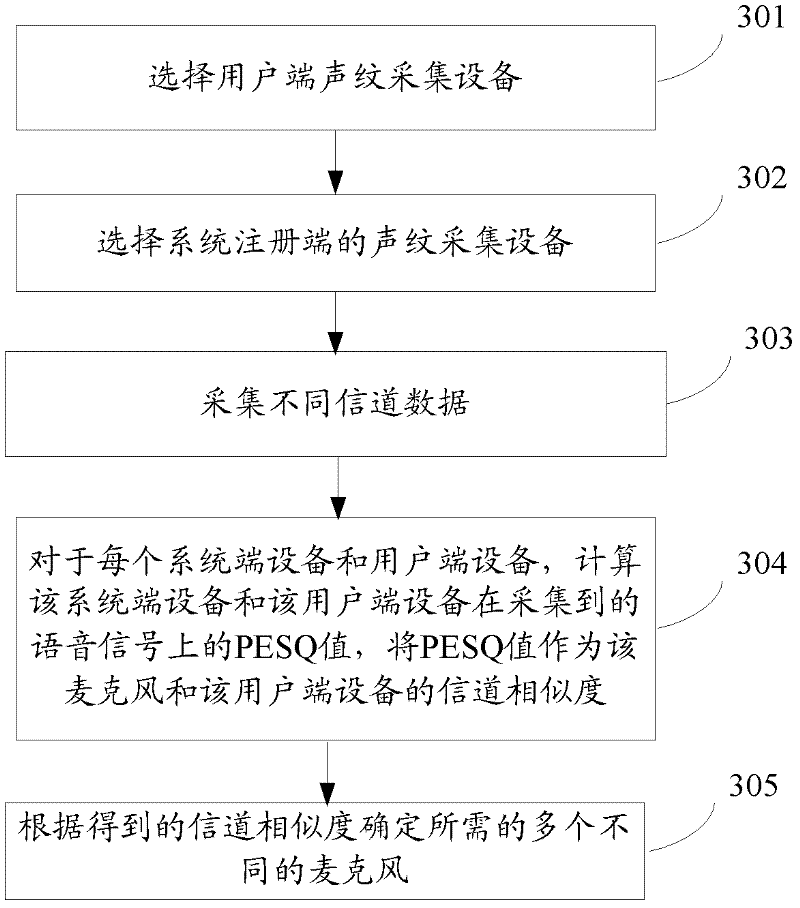
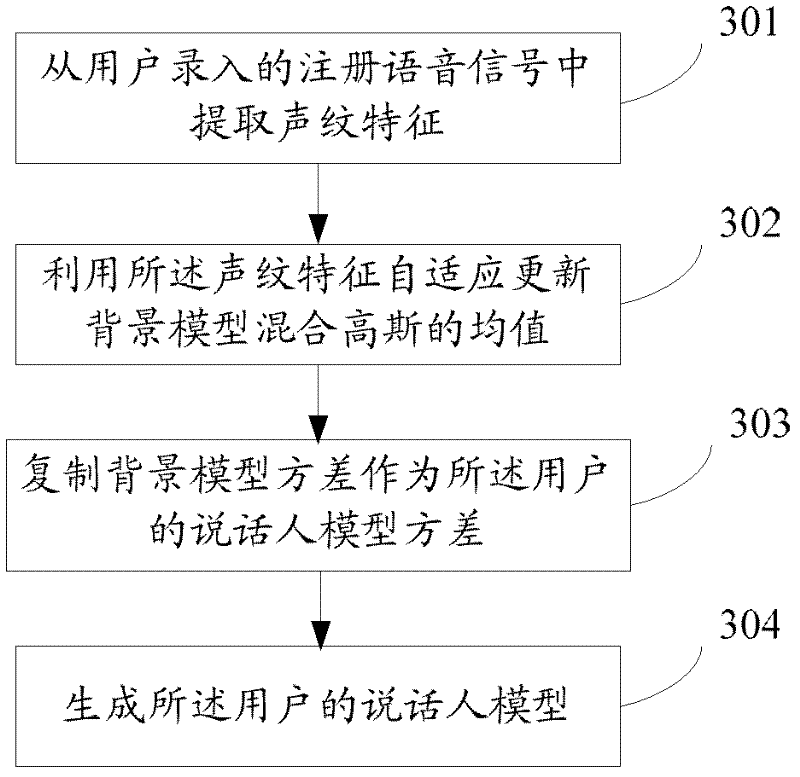
The invention relates to the technical field of identity identification, and discloses a method and a system for identifying a speaker. The method comprises the following steps of: collecting user registration voice signals under different channels; respectively extracting voiceprint characteristic sequences from the collected voice signals; generating a speaker model relative to a user by training the voiceprint characteristic sequences; and performing speaker identification of the user according to the speaker model and a universal background model which is trained and generated in advance.The method and the system for identifying the speaker disclosed by the invention can be applicable to different channel environments. The system performance is improved.
Owner:IFLYTEK CO LTD
Method and apparatus for complexity reduction in detection of delay and doppler shifted signature sequences
InactiveUS20080170602A1Easy to detectComputationally efficientAmplitude-modulated carrier systemsAmplitude demodulationWireless transmissionRound complexity
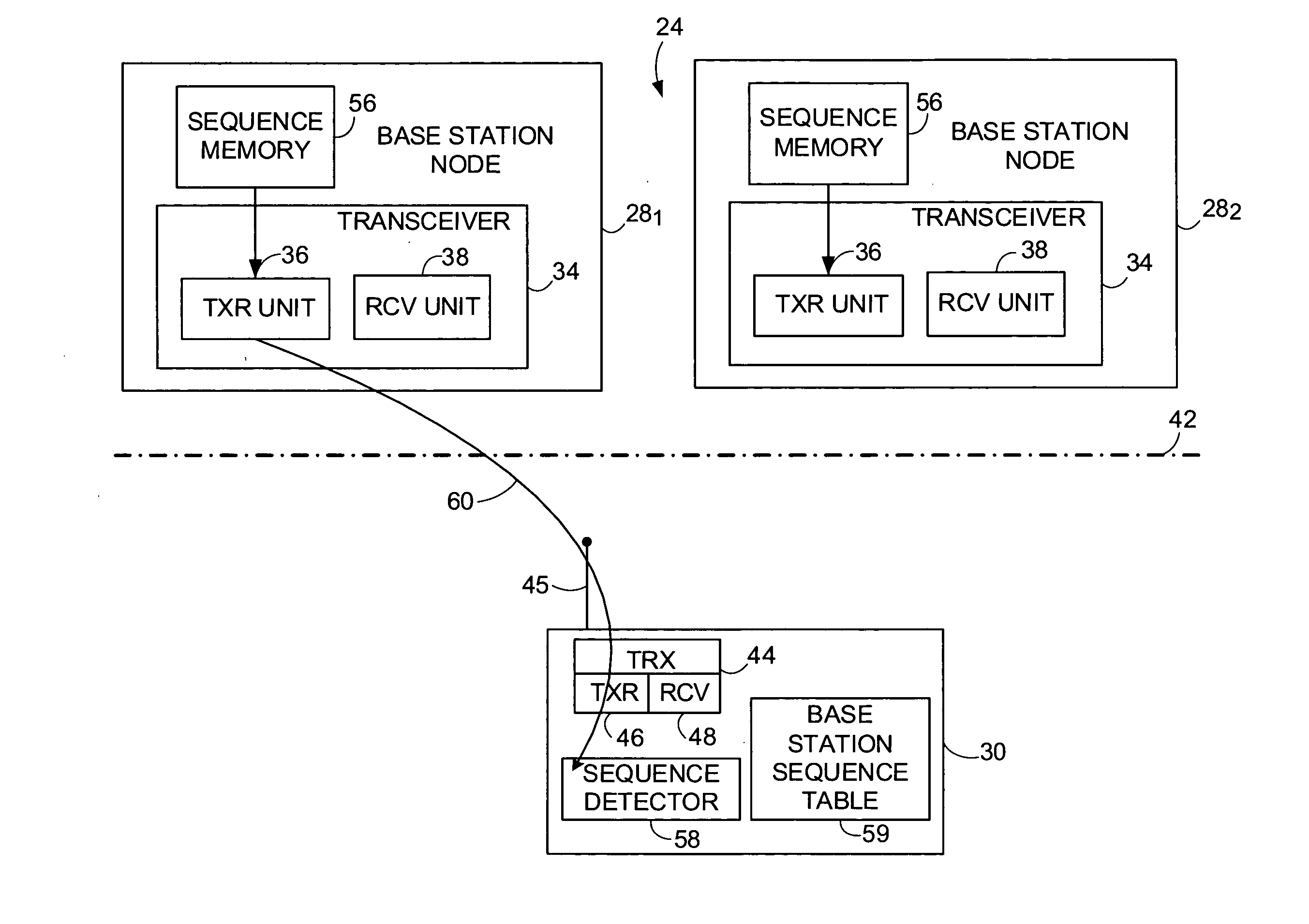
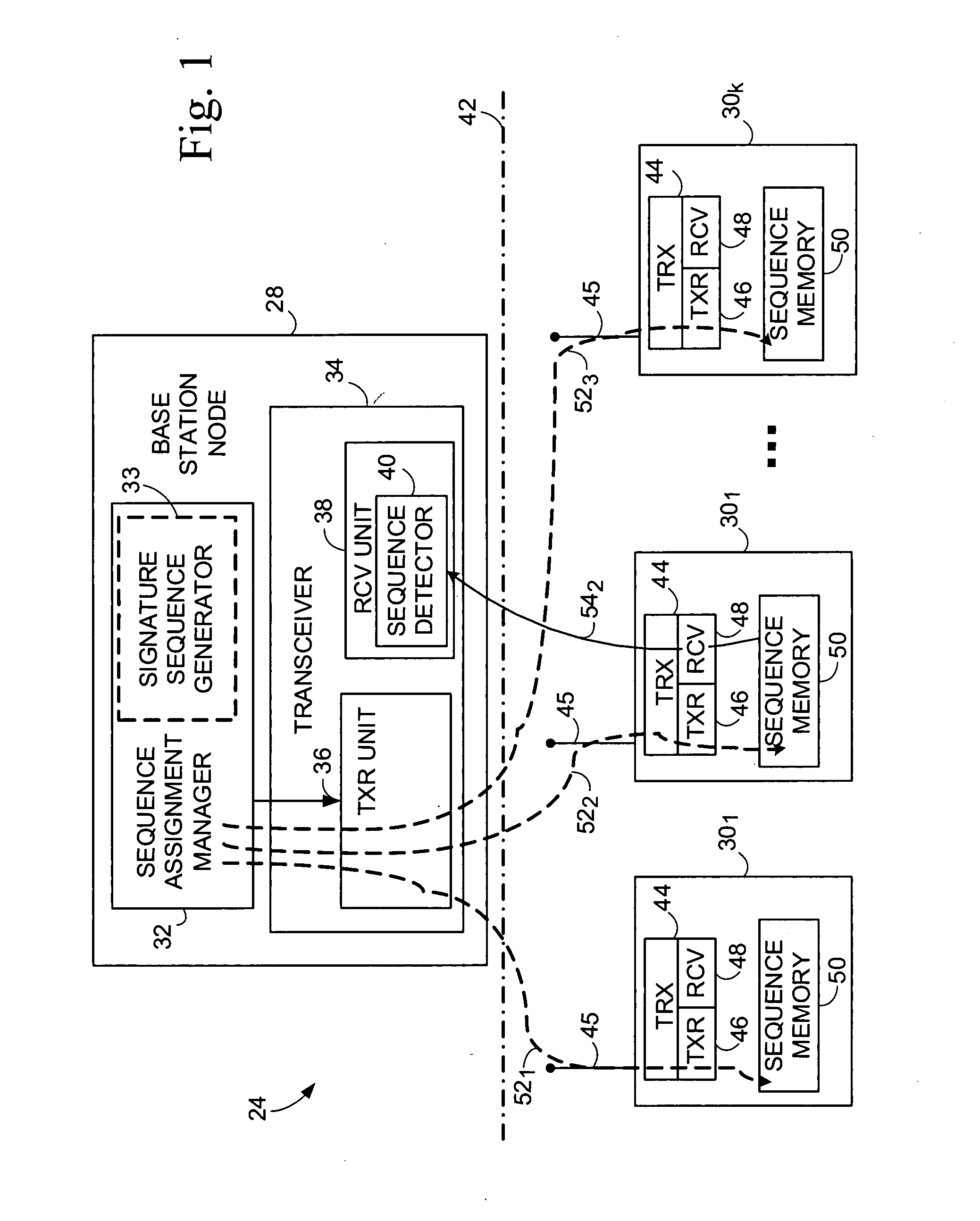
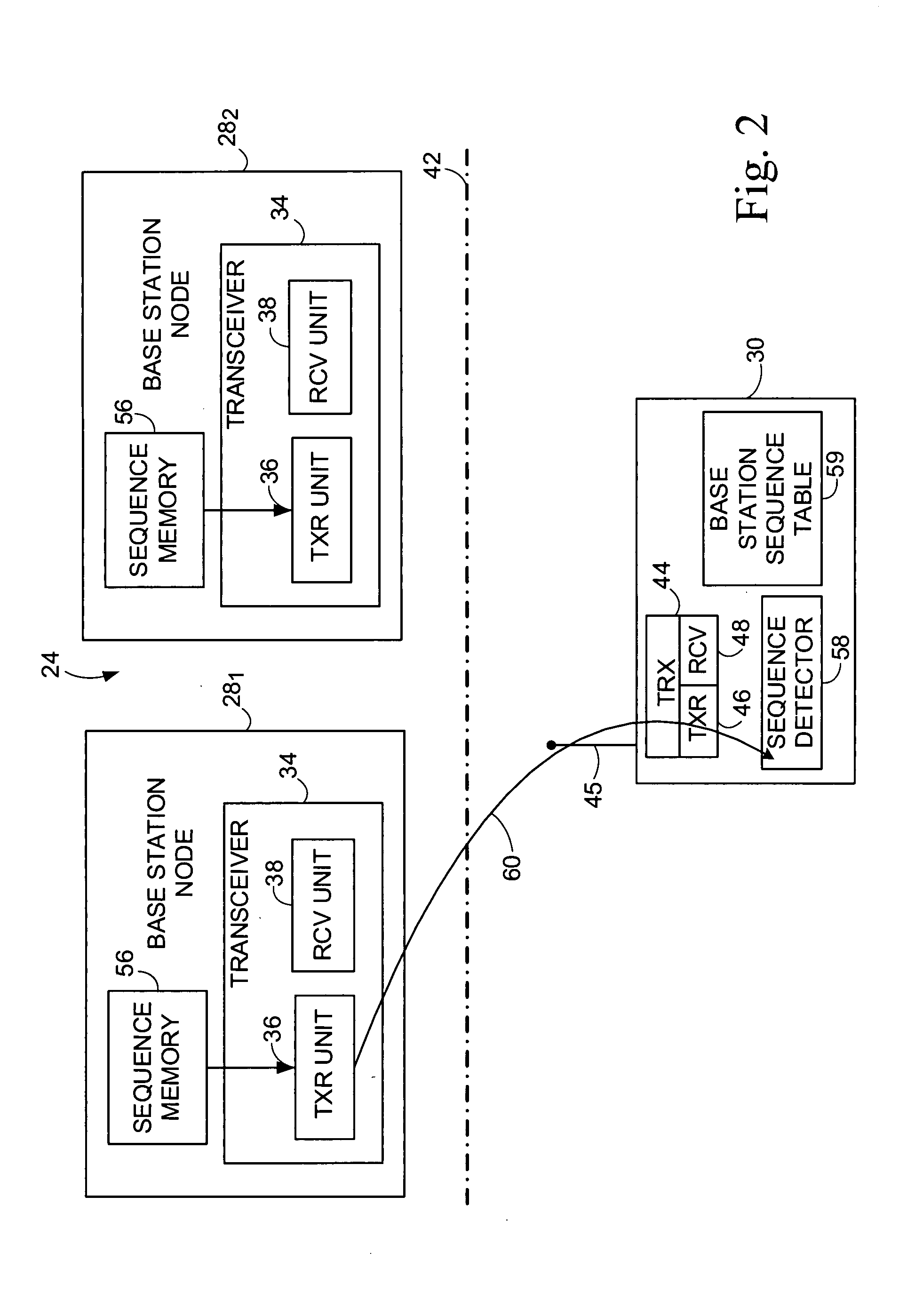
A signature sequence is employed in a wireless transmission over a channel and is detected by a receiving station. The signature sequence is selected from a subset of sequences chosen from a set of sequences formed by delay-Doppler shifts of a base sequence. Use of the subset of sequences simplifies detection of the signature sequence by, e.g., facilitating use of a simpler detector structure. A subset of N2 sequences of the specially-constructed delay-Doppler shifted sequence set is selected to facilitate more efficient computation of the detection metric. A simplified detector employs algebraic techniques (such as Discrete Fourier 'Transform (DFT)) that exploit prudent sequence assignment strategy. As an advantageous variation, for a particular class of base sequences that can be represented by segments of equal-length sinusoids, even greater complexity reduction can be achieved by segmenting the delay-Doppler correlation accordingly and reusing past outcome in subsequent overlapping segments.
Owner:TELEFON AB LM ERICSSON (PUBL)
Method and kits for multiplex hybridization assays
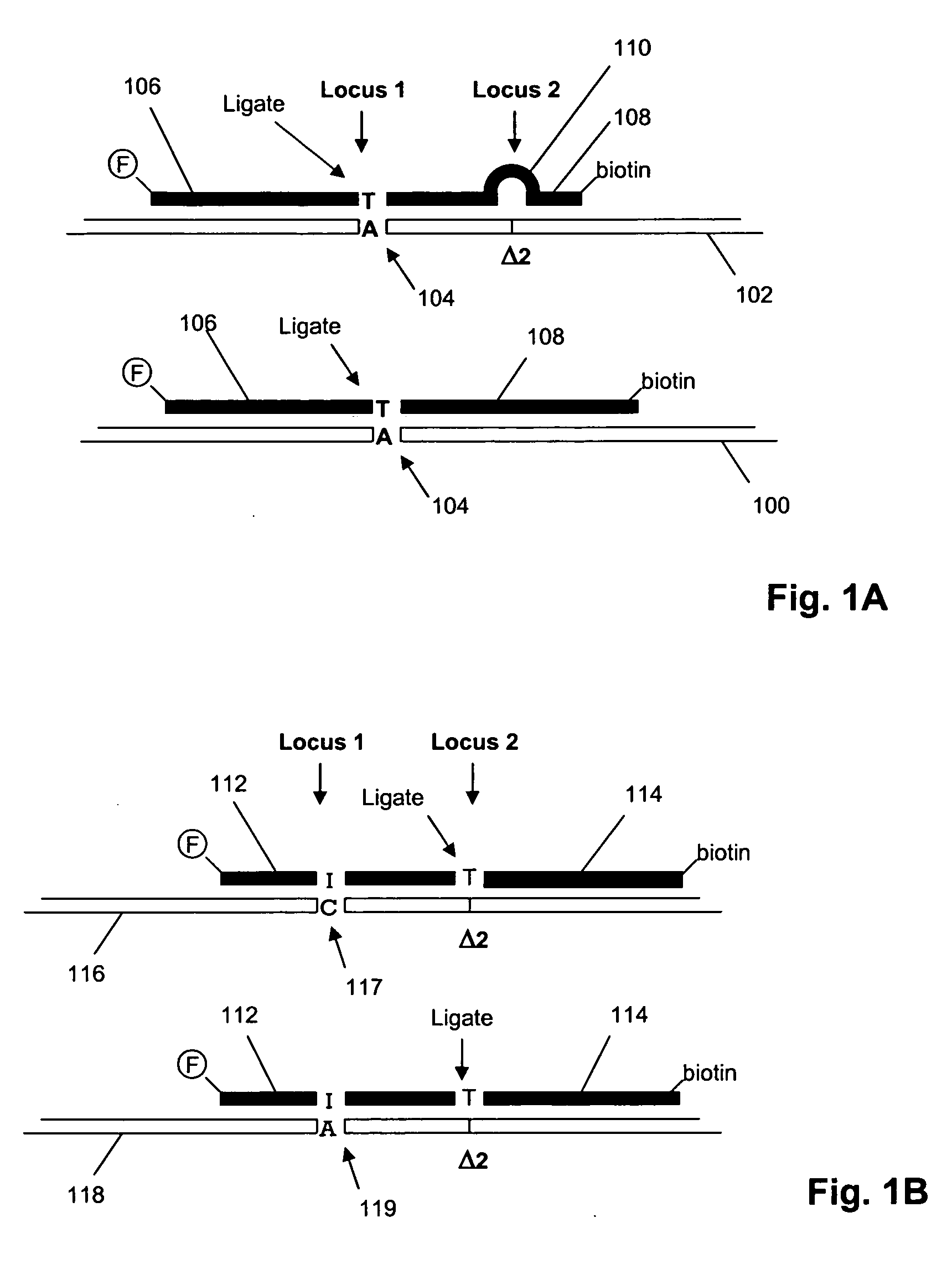
ActiveUS20060281098A1Improve matchSugar derivativesMicrobiological testing/measurementGenomic DNAPolynucleotide
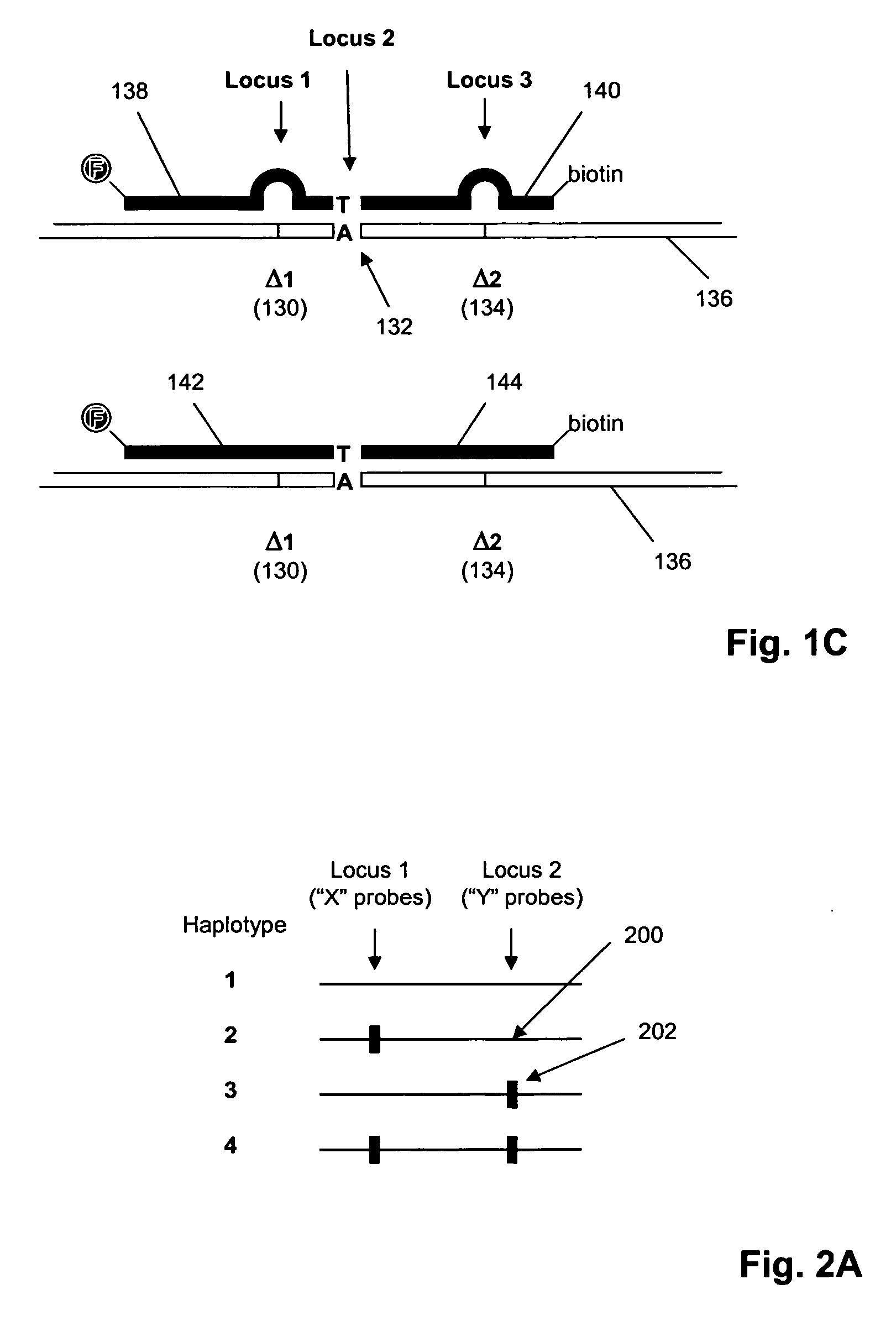
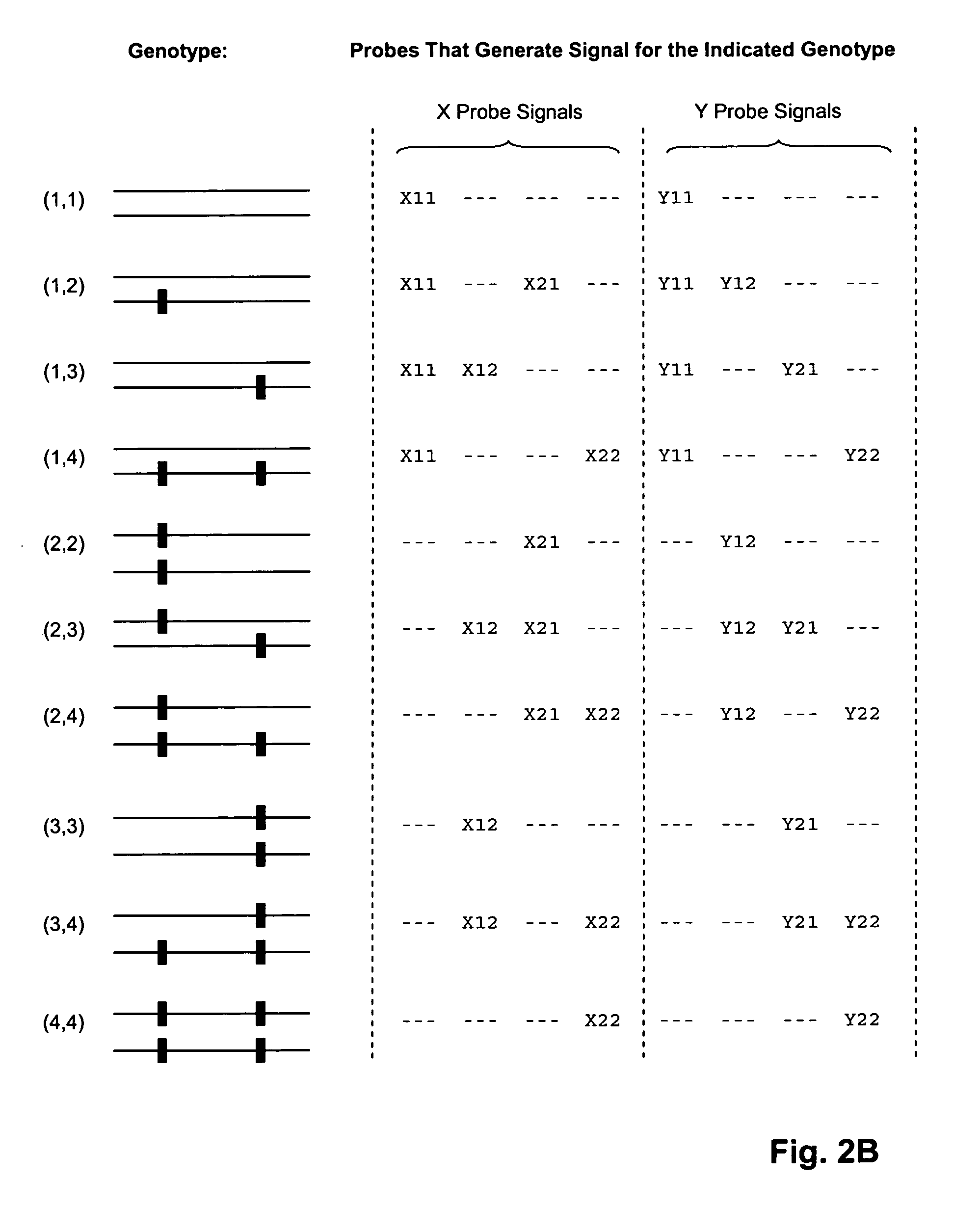
The invention provides a method for genotyping interfering polymorphic loci in a target polynucleotide, such as a strand of genomic DNA, in a multiplex hybridization-based assay. The invention also provides nucleic acid standards for validating the performance of such hybridization-based assays. In one aspect, the method of the invention is carried out by providing for each interfering polymorphic locus one or more probes so that at least one probe is capable of forming a perfectly match duplex at the locus regardless of the characteristic sequence of an adjacent polymorphism.
Owner:AFFYMETRIX INC
Character identifying method and character identifying system
ActiveCN106960206AReduce complexityReduce workloadCharacter and pattern recognitionAttention modelFeature extraction
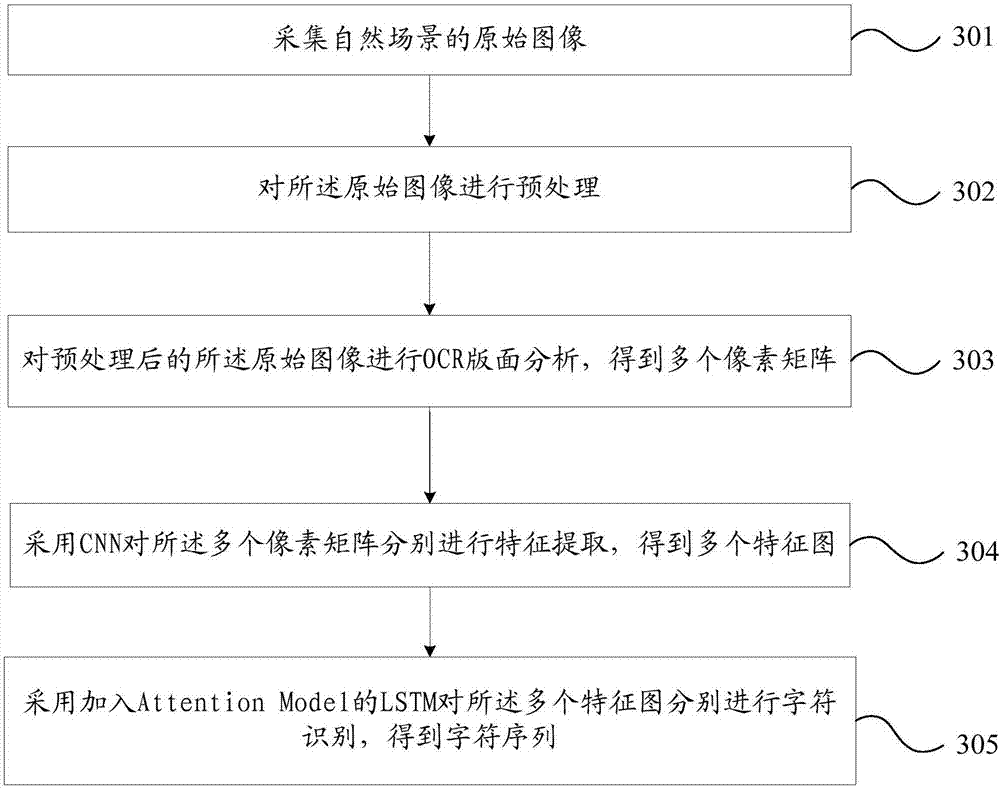
An embodiment of the invention provides a character identifying method and system. The method includes collecting an original image of a nature scene; performing pre-treatment on the original image; performing OCR layout analysis on the original image subjected to the pre-treatment and obtaining a plurality of pixel matrixes; performing characteristic extraction on the pixel matrixes by adopting a CNN (Convolutional Neural Network) and obtaining a plurality of characteristic patterns; performing character identification on the characteristic patterns by adopting an LSTM (Long Short Term Memory) provided with an Attention Model and obtaining a character sequence, wherein a forget gate of the LSTM provided with the Attention Model is replaced with the Attention Model. According to the invention, by utilizing the LSTM algorithm provided with the Attention Model, the characteristic sequence extracted by using the CNN algorithm is identified as the corresponding character sequence, so that required text information is obtained and operation parameters are reduced. At the same time, through control of different influence on current characters by different context content, information in long term memory can be transmitted to the current characters perfectly, so that character identification accuracy is improved.
Owner:BEIJING SINOVOICE TECH CO LTD
Abnormal behavior identification method based on contour
InactiveCN101464952AReduce intensityCharacter and pattern recognitionCharacteristic sequenceAnomalous behavior
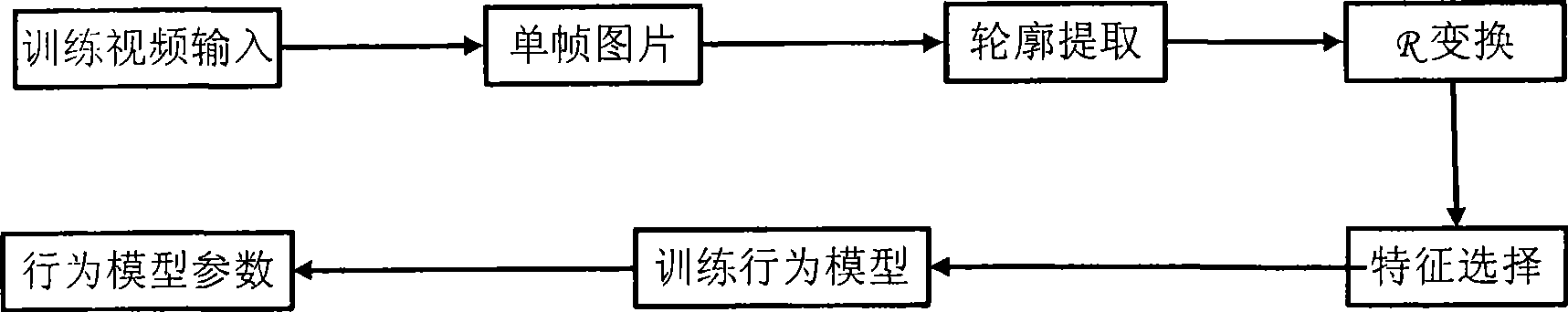
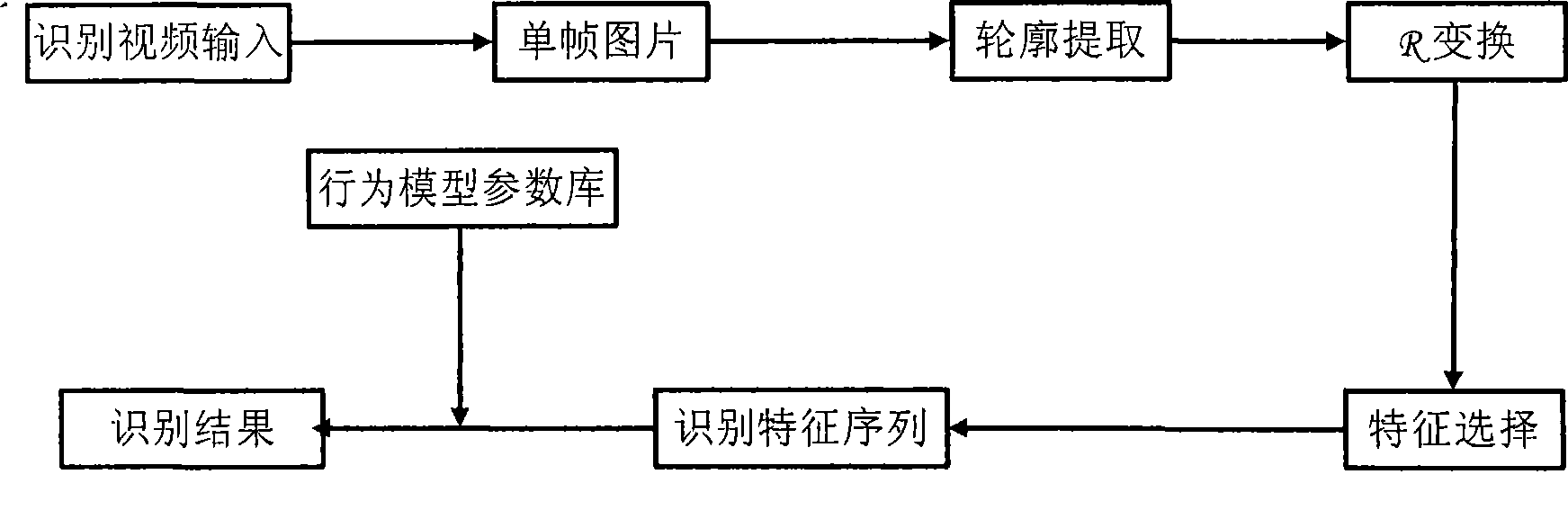
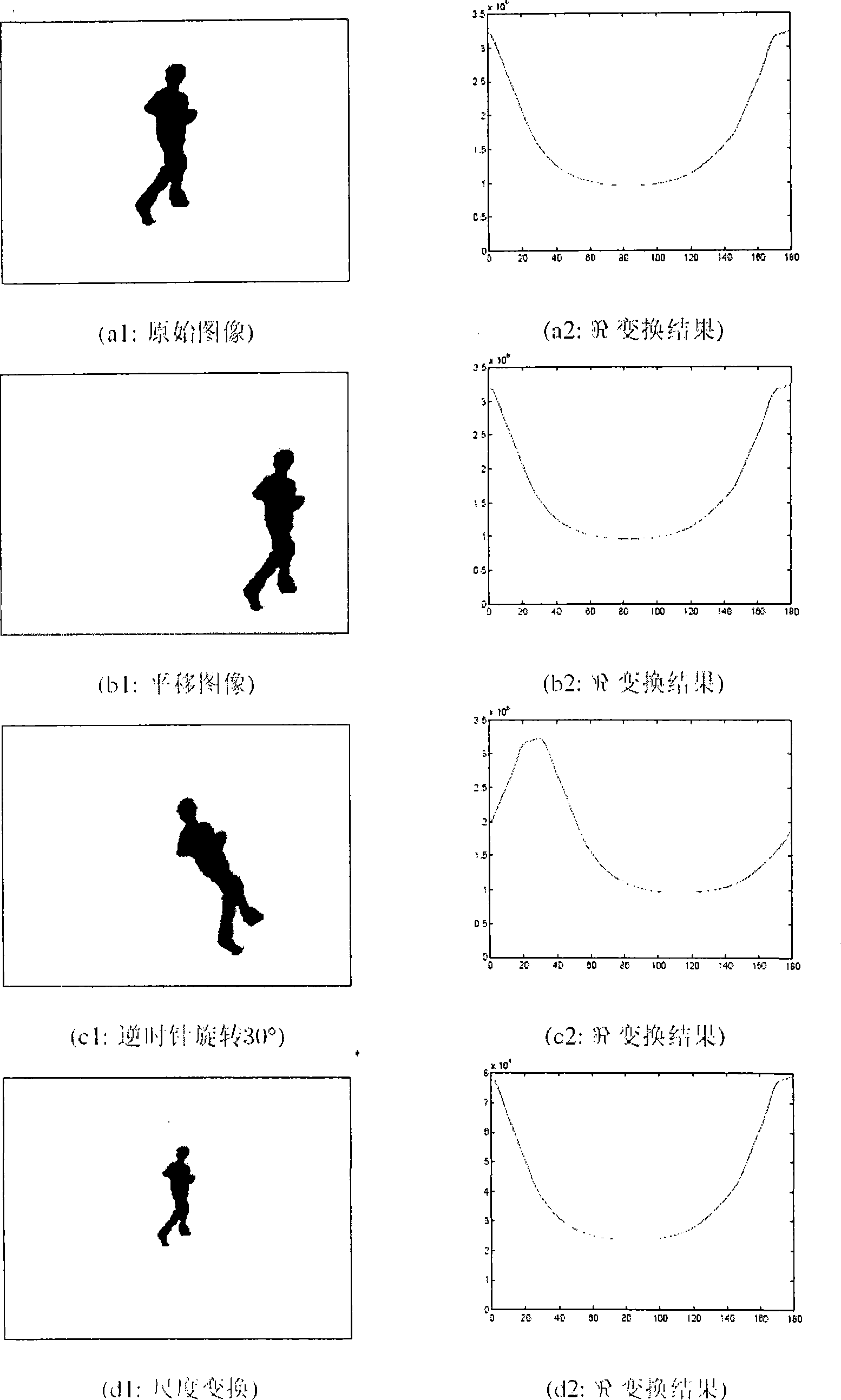
The invention discloses a method for recognizing aberrant behaviors based on contours. The method is characterized in that the detection and the tracking of moving targets are primarily performed for the image sequences collected by a camera so as to extract target contours; then spatial information of the moving targets in each frame is indicated by utilizing R transformation; then the spatial information is rearranged and combined as characteristic vectors of behavior analysis and the characteristic dimension reduction is performed by adopting principal component analysis; finally the transformation relation of the contour sequences with spatial information in the time is indicated by utilizing a hidden Markov model, and all the behaviors can be indicated with respective parameters of the hidden Markov model. In the recognition process, the characteristic sequences of new behaviors are compared with the storage parameters, and the behaviors best matched are selected upon the maximum likelihood principle. Therefore, the method for recognizing aberrant behaviors has an important significance of automatic analysis for intelligent visual monitoring, so that time, places and characters of occurrence events in the scene can be known without assistance of the people; moreover, the method for recognizing aberrant behaviors also can be used for video retrieval so as to assist the people to seek for the interesting events in the video frequency.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Detecting method and system for malicious codes
InactiveCN102360408APlatform integrity maintainanceSpecial data processing applicationsRelational databaseSvm classifier
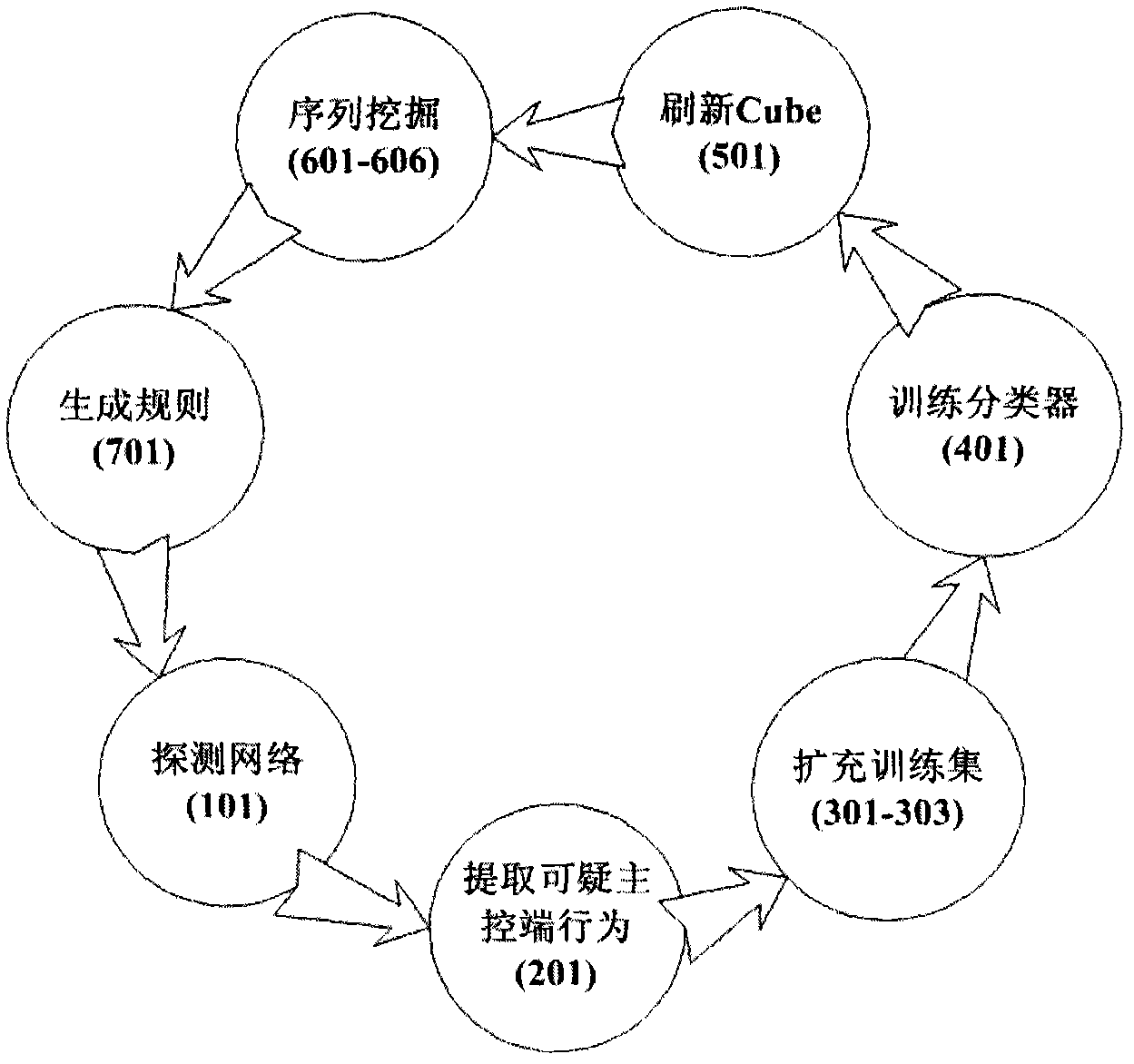
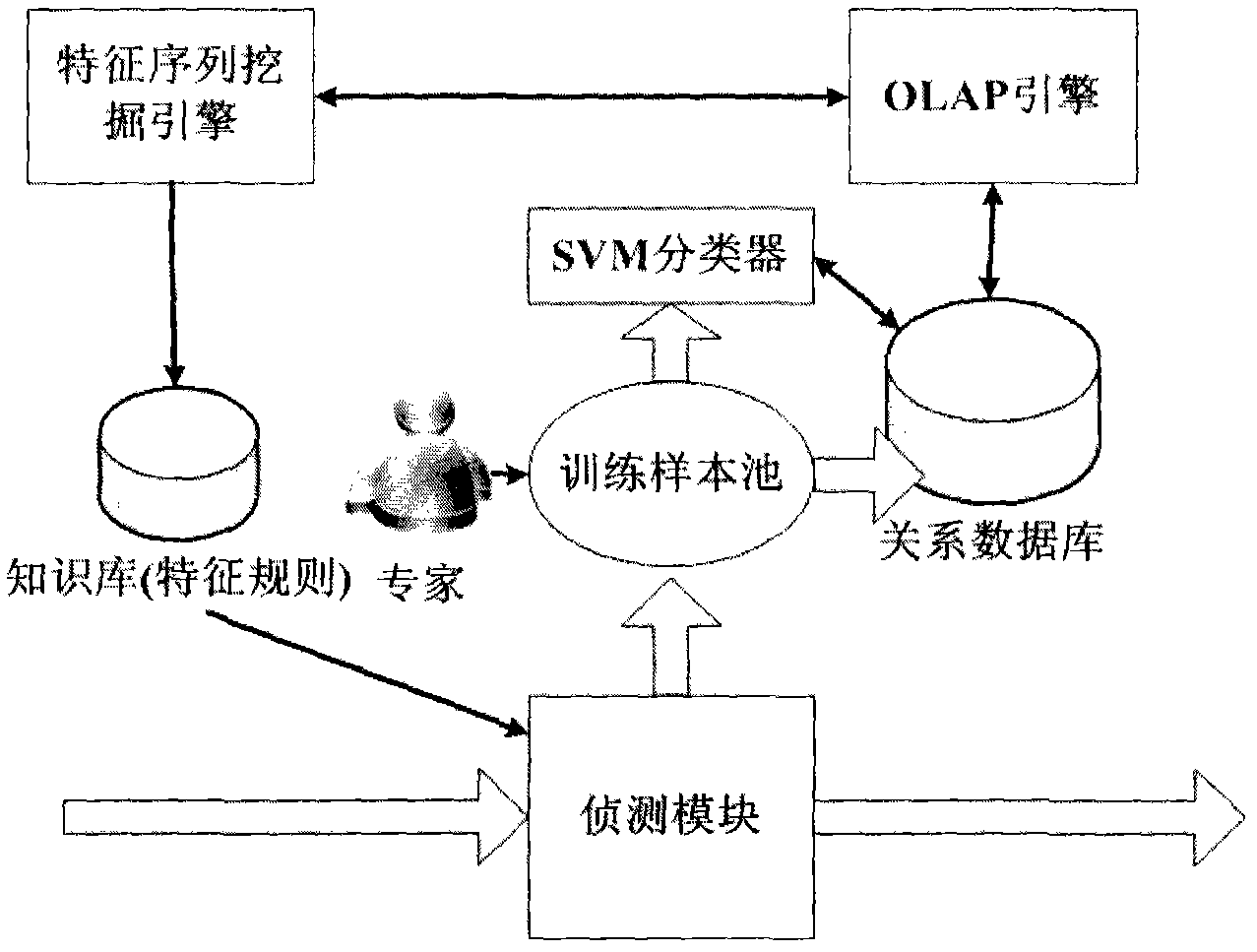
The invention provides a detecting method and a system for malicious codes, which are assisted by an OLAP engine, characterized by interaction behaviors of a main control end and a controlled end of malicious codes and are based on excavation, wherein the detecting method comprises a step 101 of detecting a network; a step 201 of extracting suspicious main control end behaviors; steps 301-303 of expanding a training set; a step 401 of training a classifier; a step of 501 of brushing Cube; steps 601-606 of excavating sequences; and a step 701 of generating a rule. The detecting system comprises a detecting module, a training sample pool, an SVM classifier, a relation database, an OLAP engine, a characteristic sequence excavation engine and a knowledge base.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
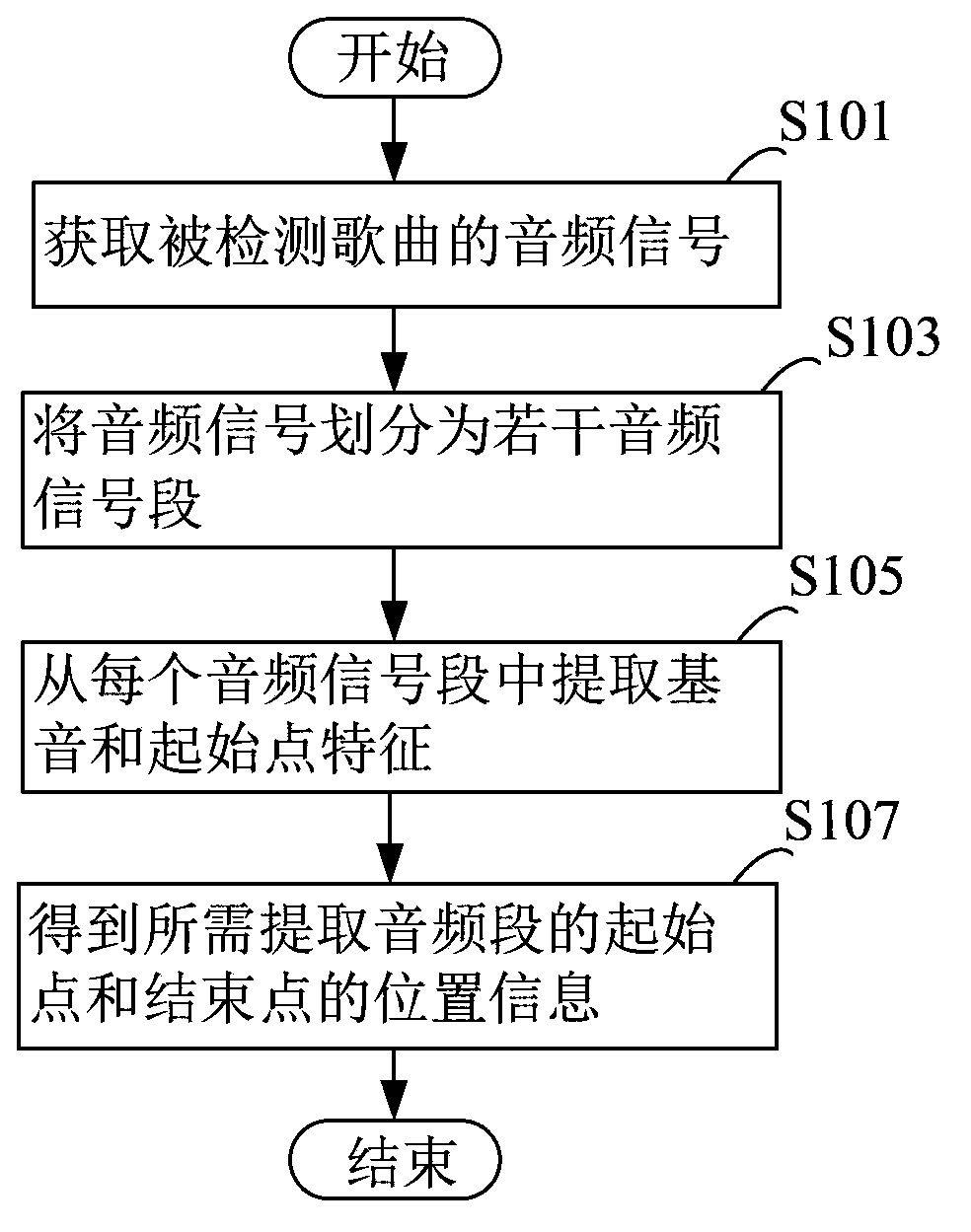
Audio band extraction method and extraction device
The invention relates to an audio band extraction method and extraction device. The extraction method comprises that: an audio signal of the detected song is obtained; framing processing is performedon the audio signal according to a preset time interval so that the audio signal is divided into multiple audio signal bands; characteristics of fundamental tone and start points are extracted from each audio signal band so that characteristic sequences of the fundamental tone and the start points are formed respectively; and each audio signal band is detected according to the characteristic sequences so that position information of the start points and end points of the audio bands needed to be extracted are obtained. The position information of the needed audio bands can be accurately and rapidly extracted so that an application requirement for real-time detection can be met.
Owner:GUANGZHOU KUGOU COMP TECH CO LTD
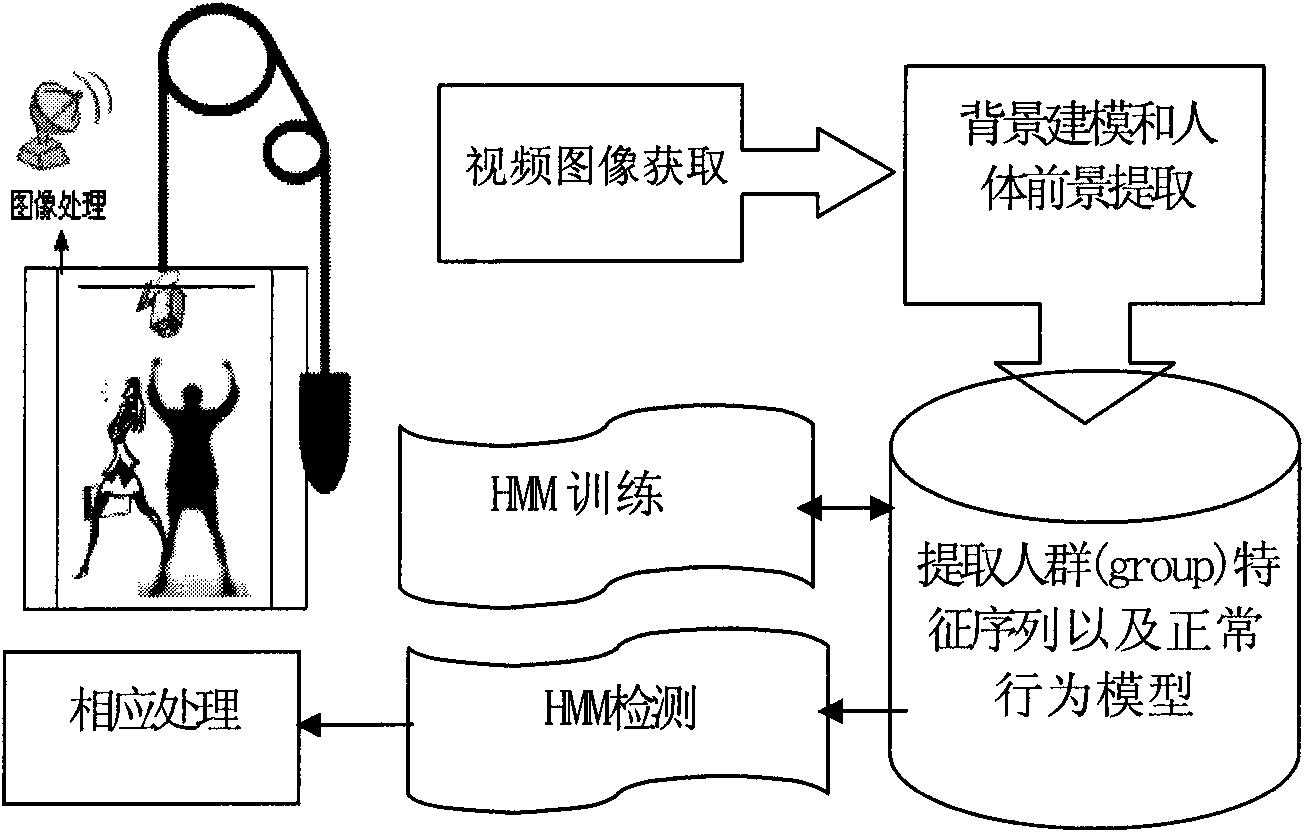
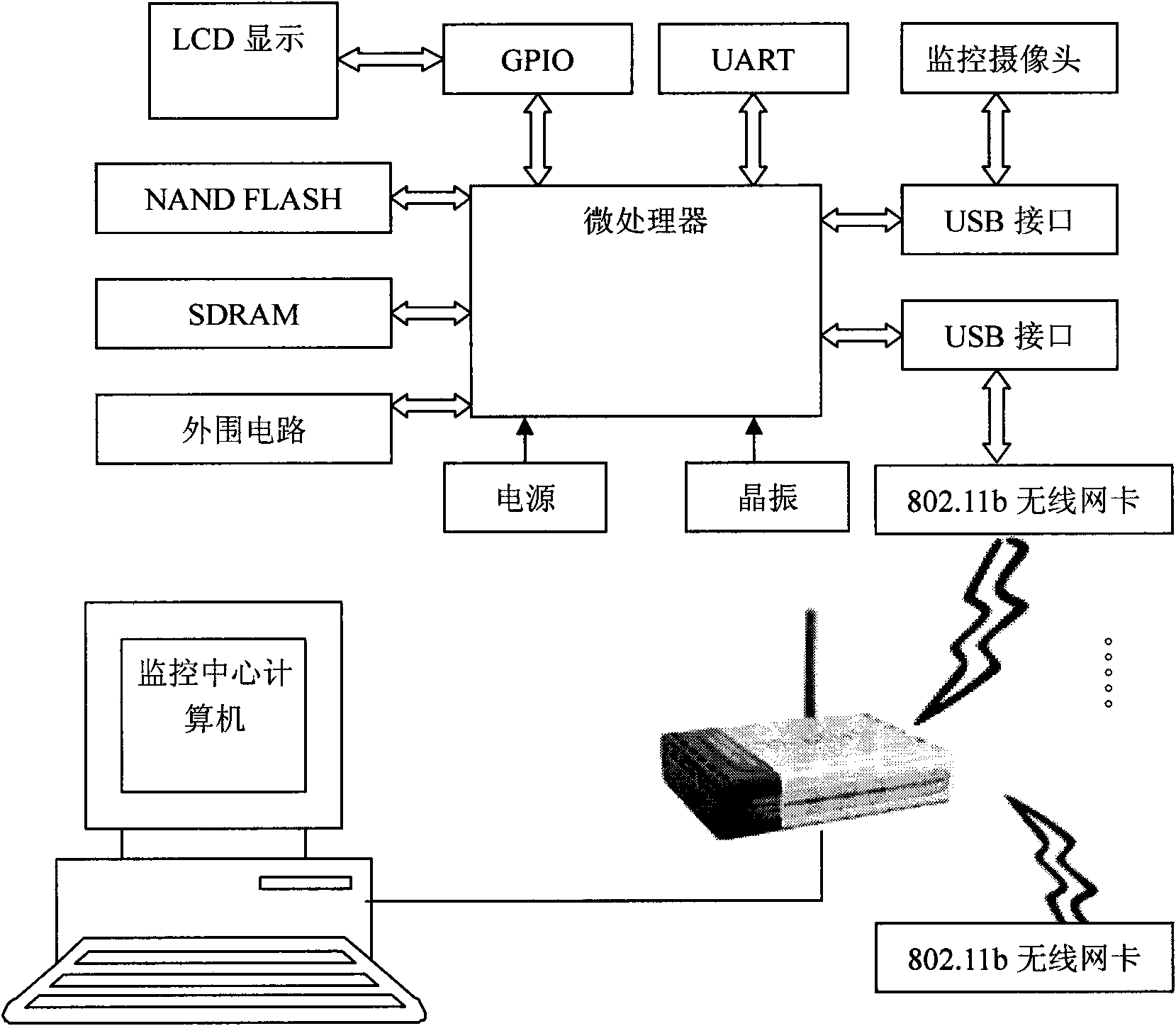
Intelligent detecting device for violent behavior in elevator car based on computer vision
InactiveCN101557506ACharacter and pattern recognitionClosed circuit television systemsHuman bodyDisplay device
The invention discloses an intelligent detecting device for violent behavior in an elevator car based on computer vision, which comprises a video sensor arranged at the top part of the elevator car, an embedded system used for transmitting video data, and a monitoring center computer used for monitoring the interior of the elevator car. The video sensor is connected with the embedded system; the embedded system is wirelessly connected with the monitoring center computer; the monitoring center computer comprises a video image reading module in the car used for displaying the video data in the elevator car in real time; the video image reading module in the car is connected with a display device; the video sensor is communicated with the wireless data of the monitoring center computer; the monitoring center computer comprises a microprocessor used for the safety precaution in the elevator car; the microprocessor also comprises a background modeling and human body foreground object extracting module, a crowd behavior characteristic sequence extracting module, a modeling module of a hidden Markov model as well as an identifying module and an alarm module of violent behaviors. The intelligent detecting device for violent behavior in an elevator car based on computer vision has the advantages of intellectualization, real-time online and strong reliability.
Owner:ZHEJIANG UNIV OF TECH +1
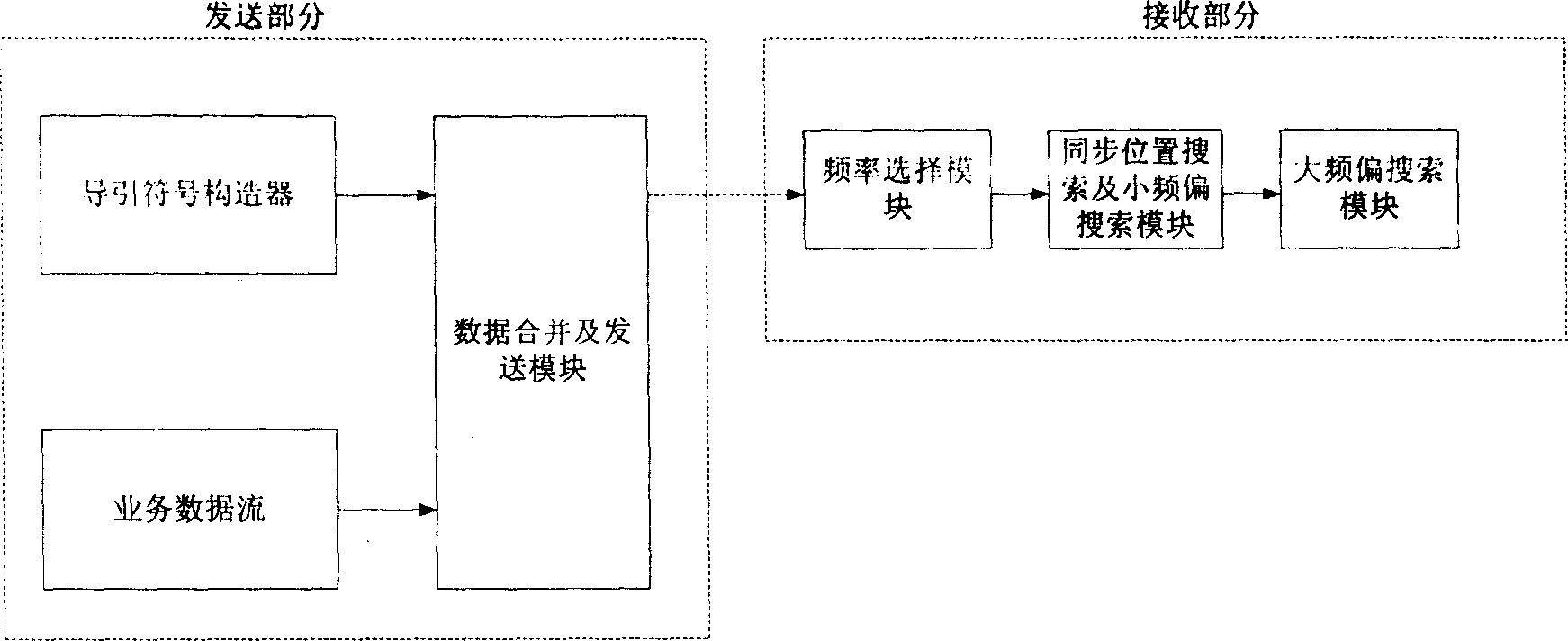
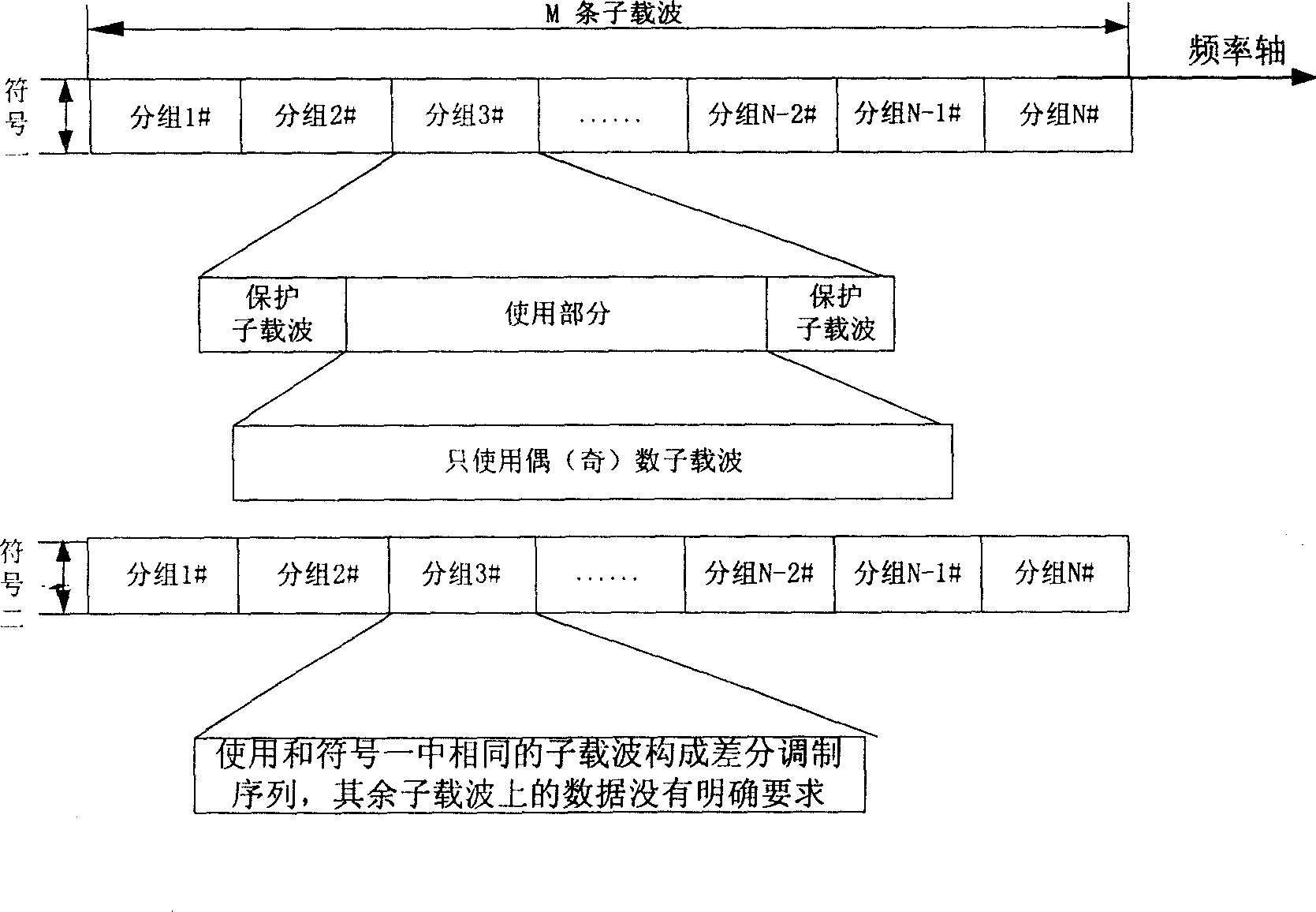
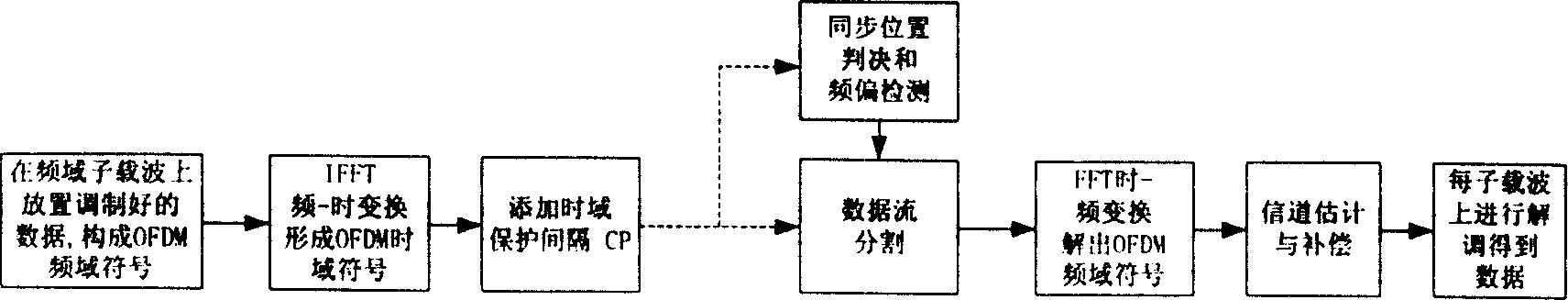
A method for synchronization in OFDM system
InactiveCN1691659ANormal sync processAvoid interferenceMulti-frequency code systemsCarrier signalBroadcasting
A method for synchronization in orthogonal frequency division multiplexing system comprises steps: sending end transmits induce signal structure contained OFDM signal; receiving end locates the OFDM signal by checking the induce signal. The invention divides the sub carrier wave of OFDM signal, assigns different subsection to different small segment and avoids mutual disturbance, can make user's terminal take normal synchronization process, and discerns different characteristic sequence code of small segment, even can transmit broadcast inside.
Owner:BEIJING SAMSUNG TELECOM R&D CENT +1
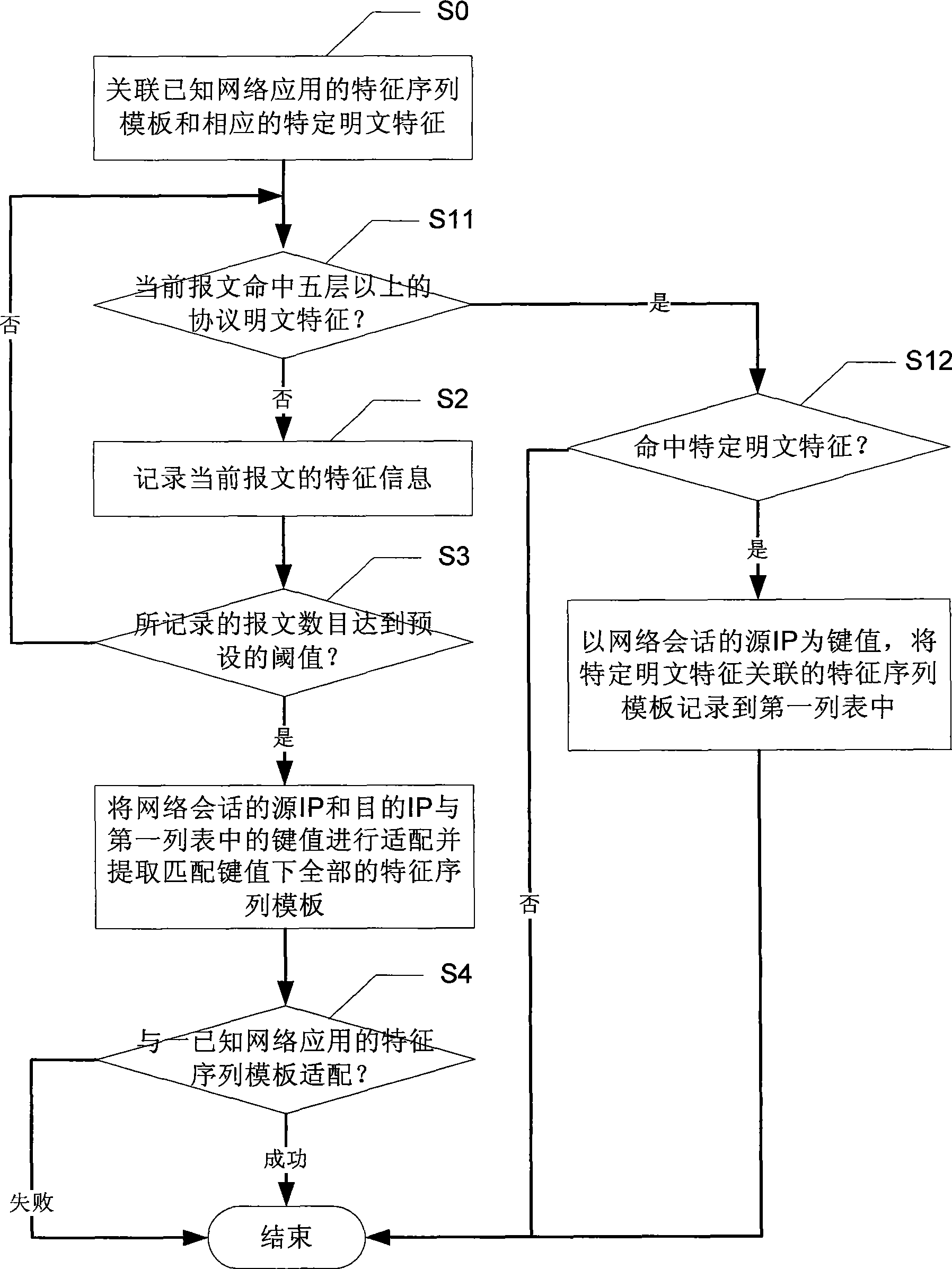
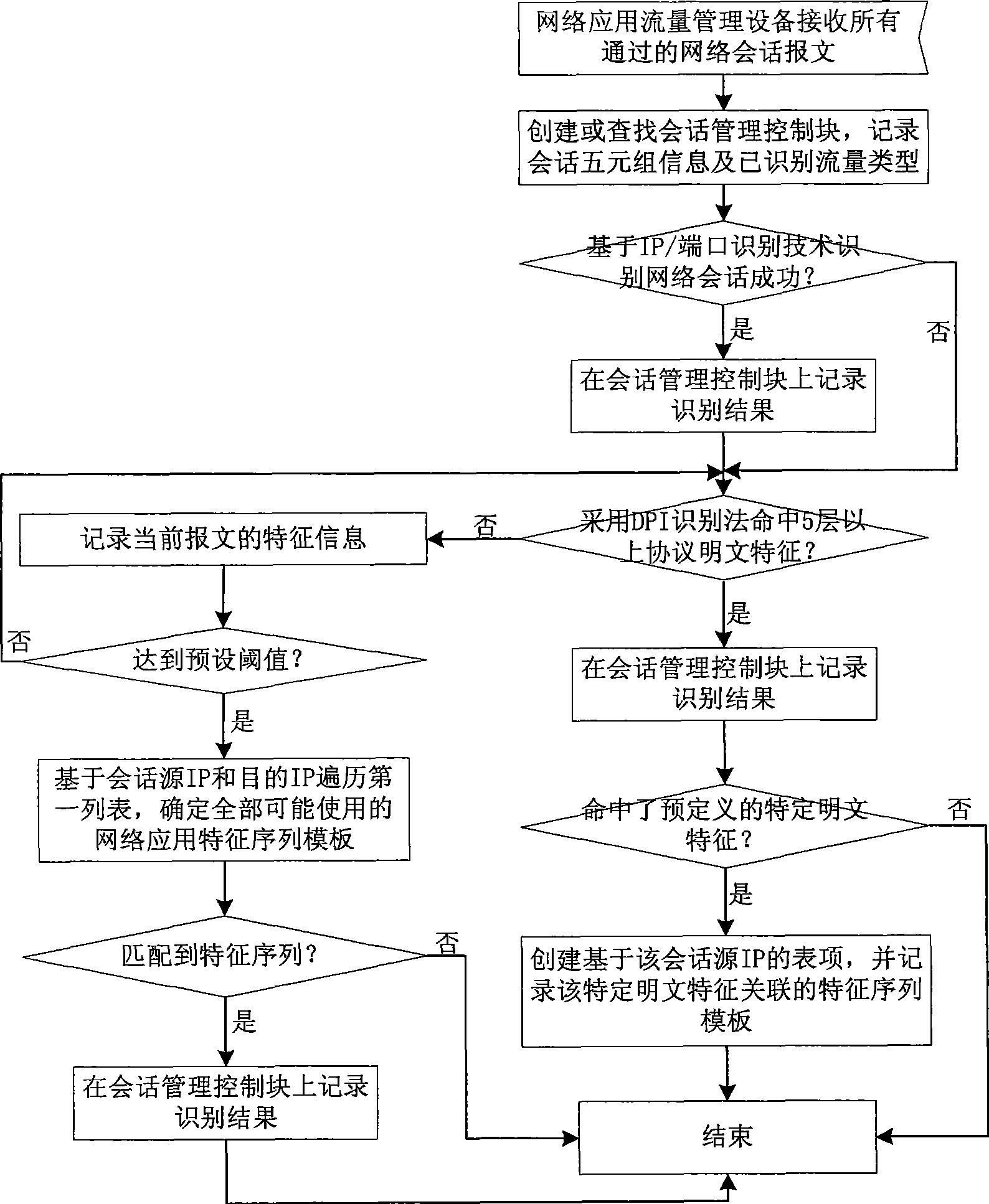
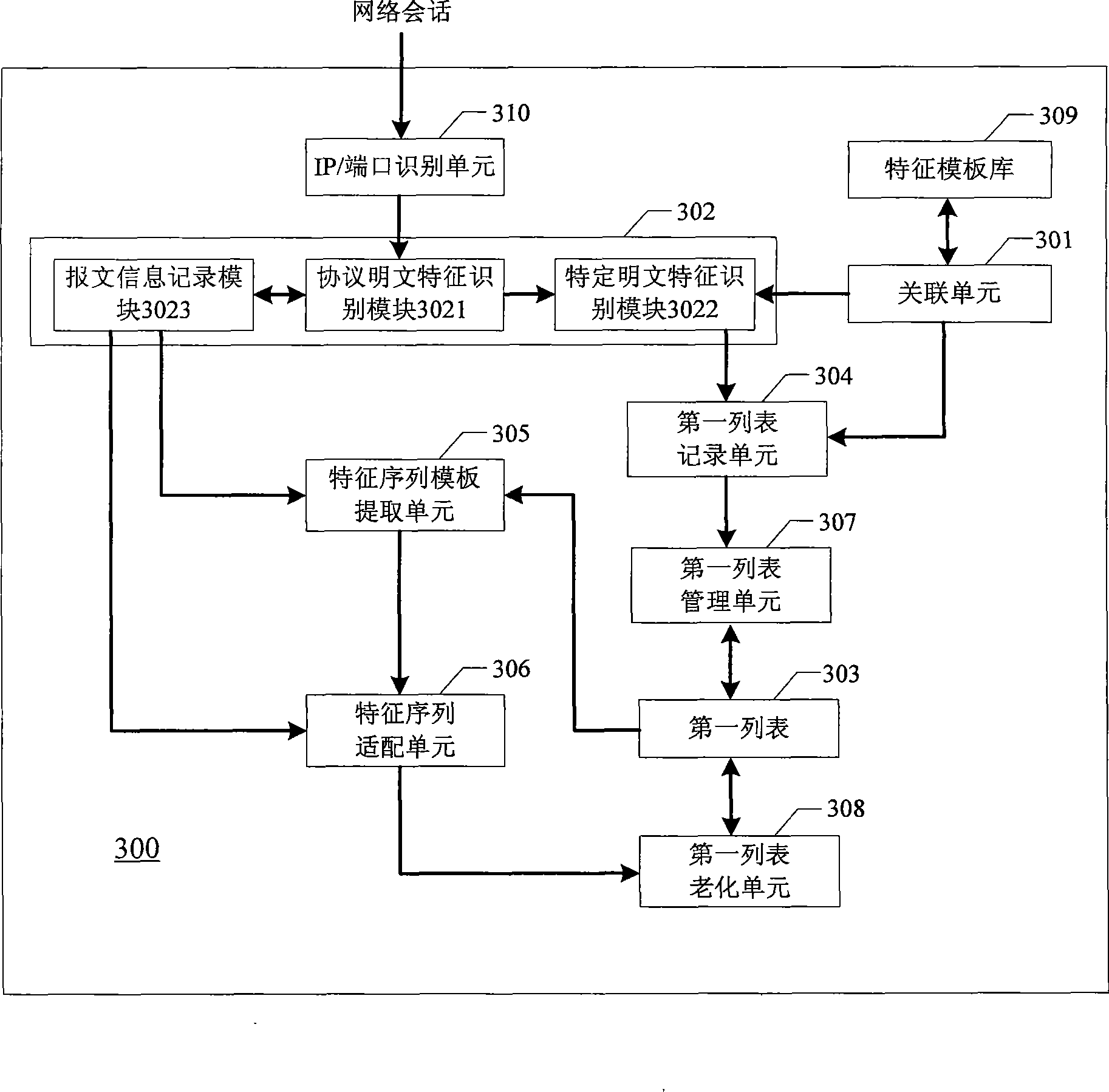
Network application flow recognition method and apparatus and network application flow management apparatus
InactiveCN101505276ALimit application trafficImprove recognition efficiencyData switching networksReporting rateFlow management
The invention discloses a network application traffic identification method, a network application traffic identification device and network application traffic management equipment. The method comprises the following steps of: associating a characteristic sequence template of known network application and corresponding specific plaintext characteristics; taking a source IP of network session as a key value to record the characteristic sequence template which is identified by DPI and is associated with the specific plaintext characteristics into a first list; and for network session which fails to be identified by the prior art, recording characteristic information of a current message, and adapting the characteristic information to the entire characteristic sequence templates under a corresponding key value when a preset threshold is reached to obtain a network application traffic identification result. The network application traffic identification method and the network application traffic identification device can identify network application traffic which fails to be identified by a DPI identification method, improve identification efficiency at the same time, reduce identification cost, and reduce the false report rate of the identification.
Owner:NEW H3C TECH CO LTD
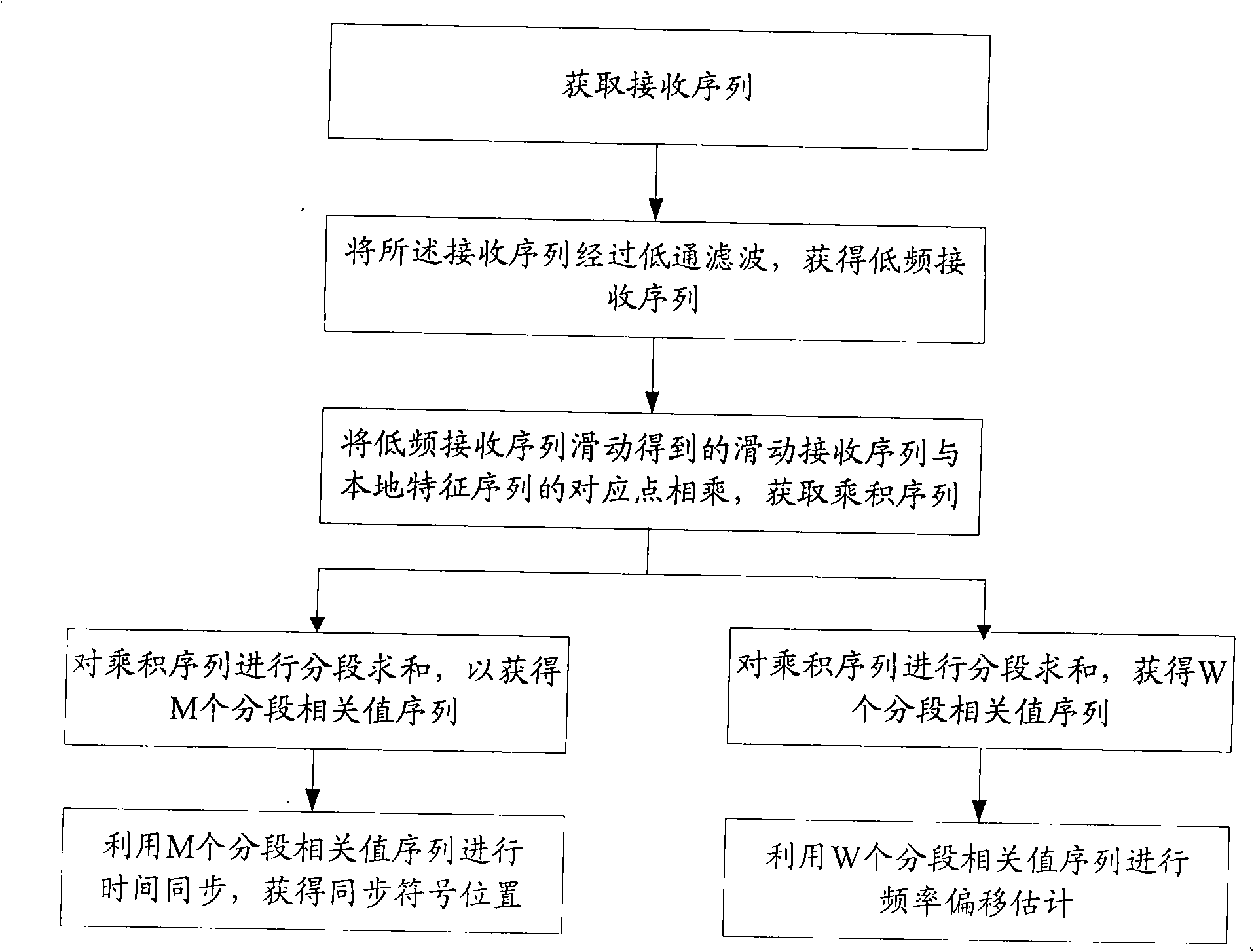
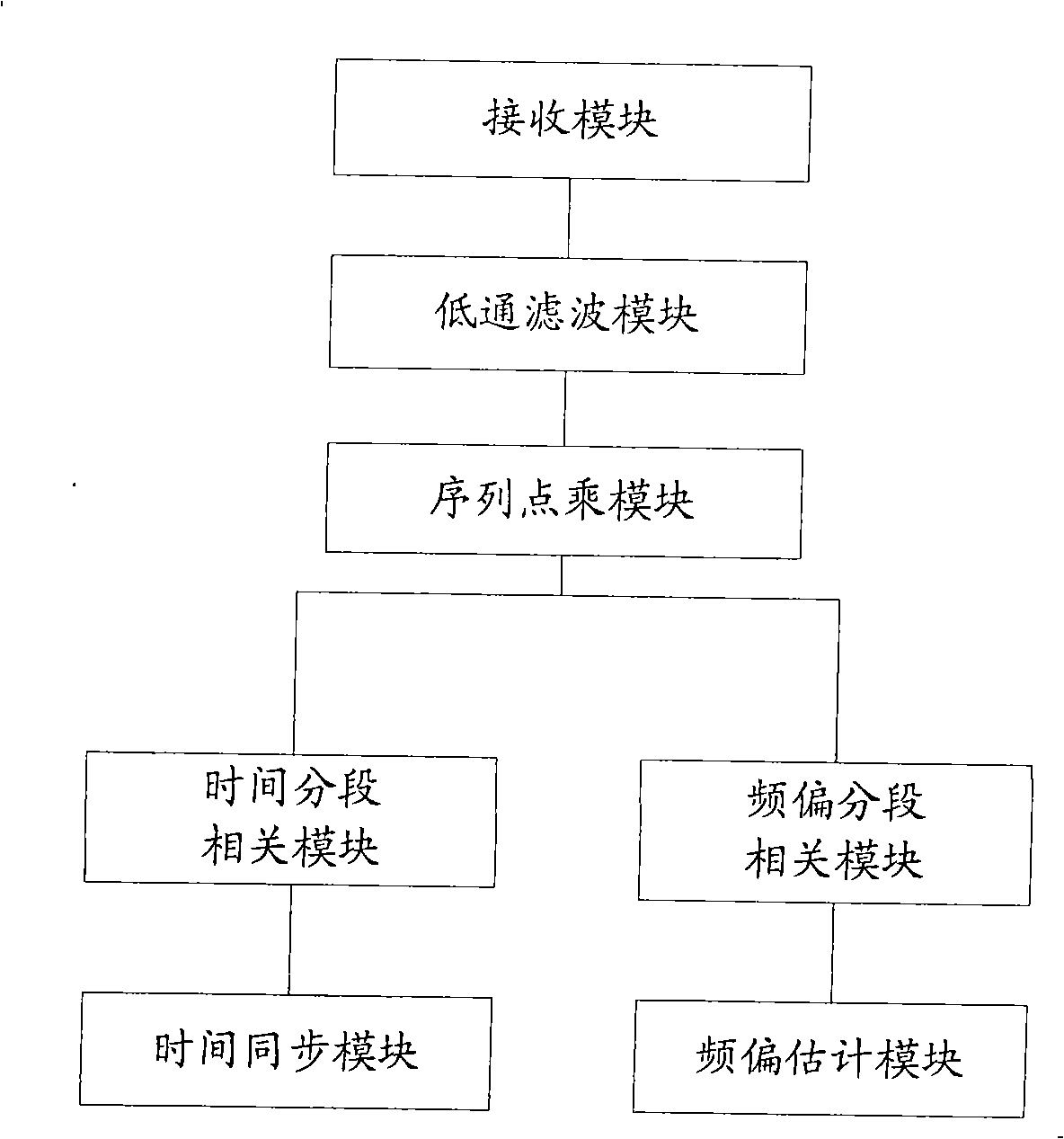
Synchronizing process, frequency deviation estimation method, synchronizing apparatus, frequency deviation estimation apparatus
InactiveCN101325450AReduce the disadvantages of being more sensitive to frequency offsetImprove accuracyRadio transmission for post communicationSynchronising arrangementEstimation methodsPeak value
The invention provides a synchronizing method, a frequency deviation estimating method, a synchronizing device and a frequency deviation estimating device, wherein, the synchronizing method comprises: performing the low pas filter on the received sequence and obtaining the low frequency receiving sequence; respectively multiplying the slide receiving sequence which is obtained after the low frequency receiving sequence slide with the same length of the local characteristic sequence with the local characteristic sequence and obtaining the product sequence; segmenting the product sequence according to a first segmenting rule, and summing the sequence after segmenting, obtaining the correlation sequence of the first segment; detecting the position of the synchronizing signal according to the obtained maximum crest of the first segment correlation sequence. According to the invention, the received sequence is divided into a plurality of segments, which is processed with the related operation, to solve the defect of being more sensitive on the frequency deviation between the transreceivers when performing the related computation on the one-segment sequence through the traditional technique, advance the accuracy of time synchronism and frequency deviation estimation.
Owner:ST ERICSSON SEMICON BEIJING
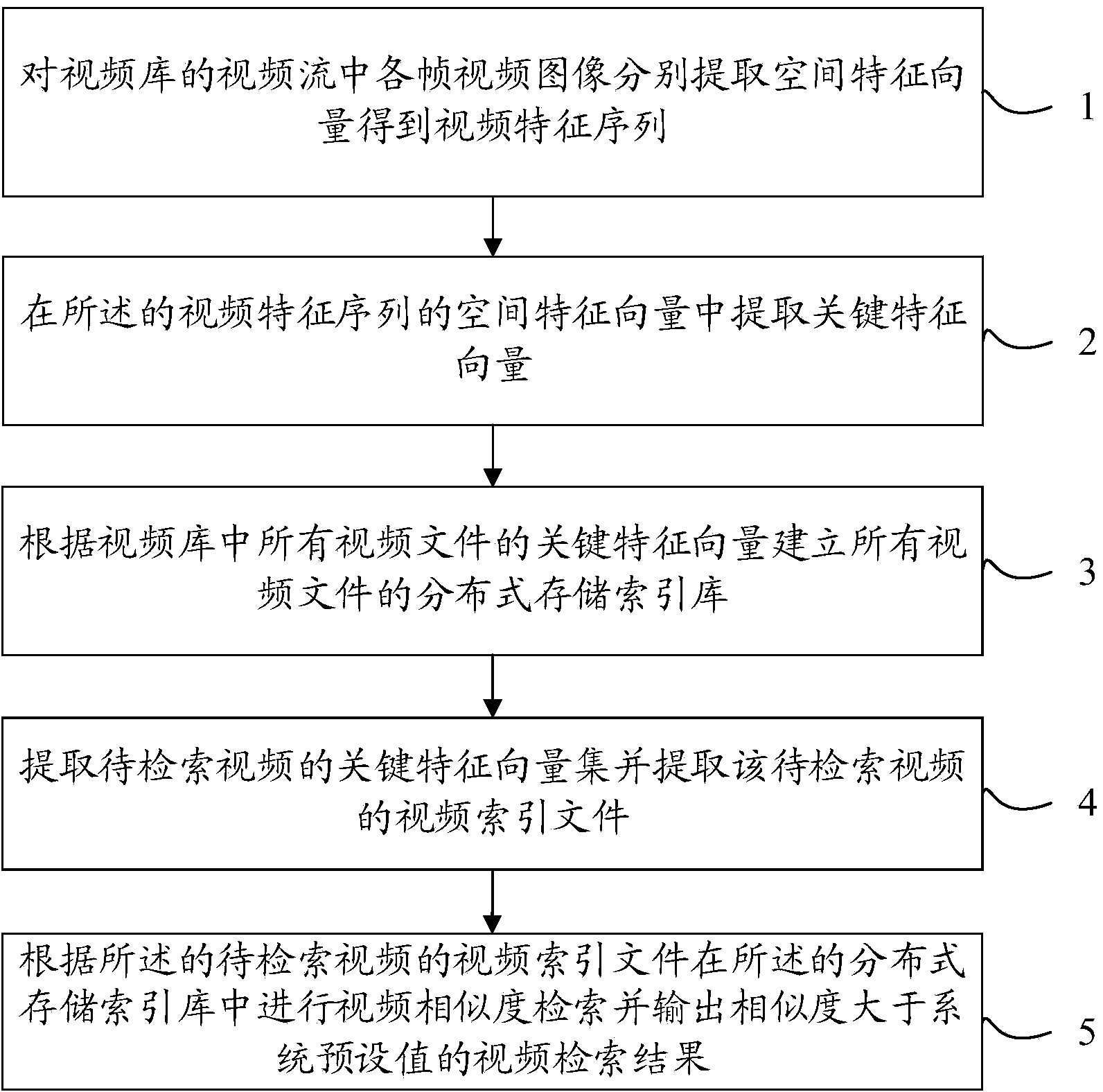
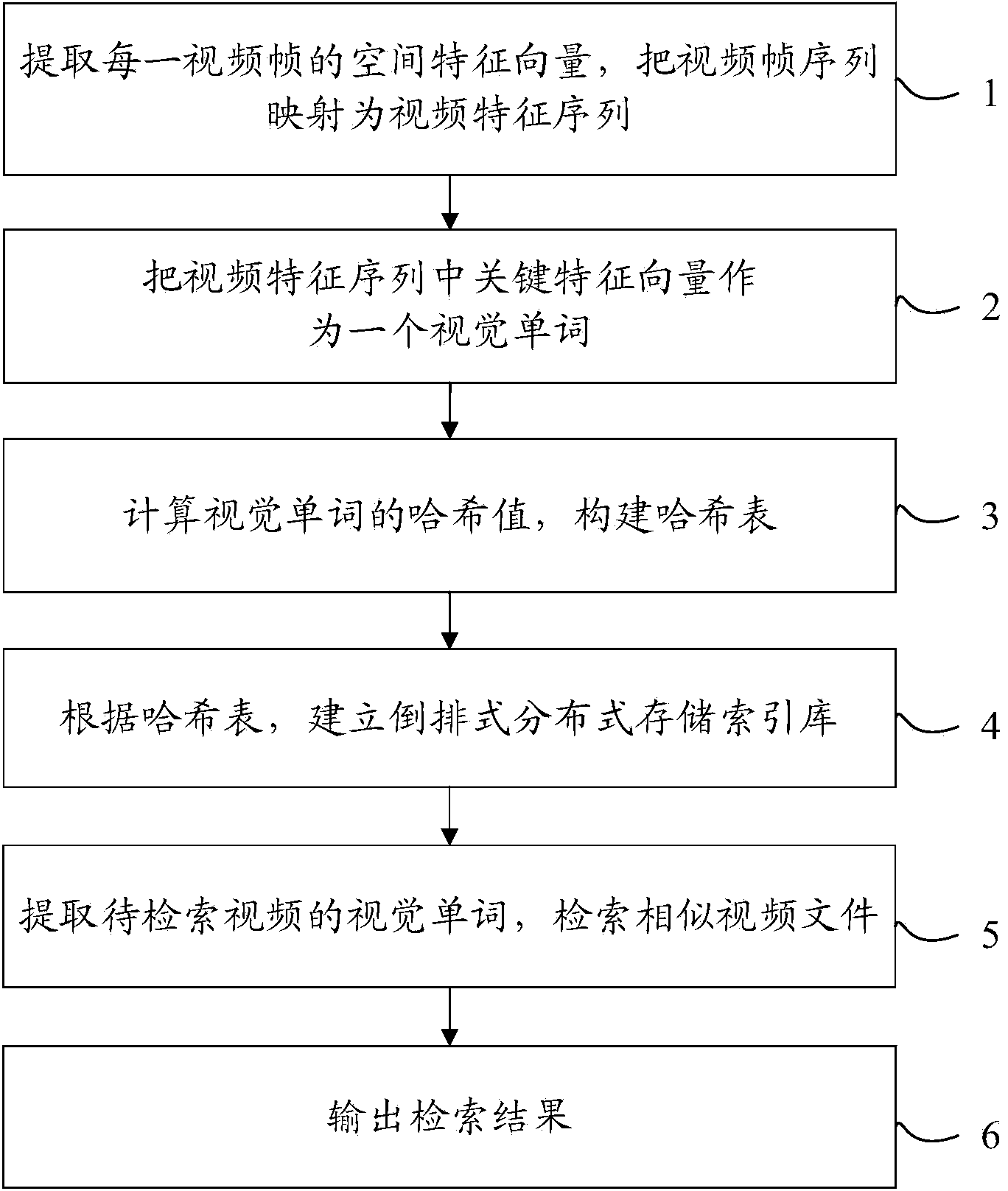
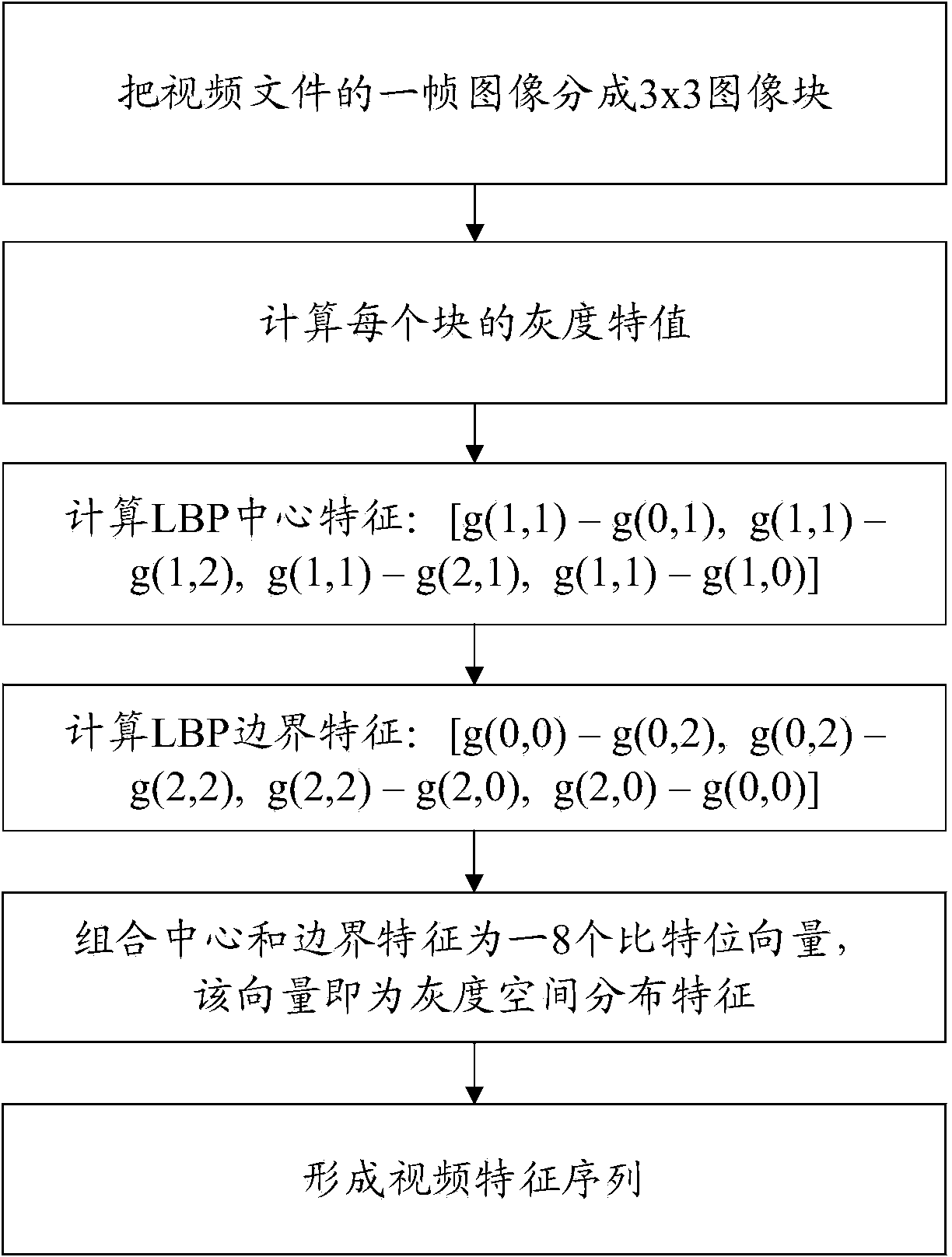
Method for realizing quick retrieval of mass videos
ActiveCN104050247AOvercoming Extraction Parameter Selection ProblemsImprove retrieval speedVideo data indexingCharacter and pattern recognitionVideo retrievalFeature vector
The invention relates to a method for realizing the quick retrieval of mass videos. The method comprises the following steps: respectively extracting spatial feature vectors from all frame video images in a video stream of a video library to obtain video feature sequences; extracting key feature vectors from the spatial feature vectors; establishing a distributed storage index database according to the key feature vectors of all video files in the video library; extracting key feature vector sets of videos to be retrieved and extracting video index files of the videos to be retrieved; performing the video similarity retrieving in the distributed storage index database according to the video index files of the videos to be retrieved and outputting video retrieval results of the video files with the similarity larger than the preset value of the system. Through the adoption of the method with the structure, representative visual words are adopted to replace key frames, video information is completely represented, a large amount of redundant of video information does not exist, the video information is very compact, the retrieval speed is increased, and the method has mass data concurrent processing capacity, and is wider in application range.
Owner:SHANGHAI MEIQI PUYUE COMM TECH
Modeling method and modeling device for language identification
InactiveCN101894548AImprove accuracyReduce operational complexitySpeech recognitionAlgorithmLanguage type
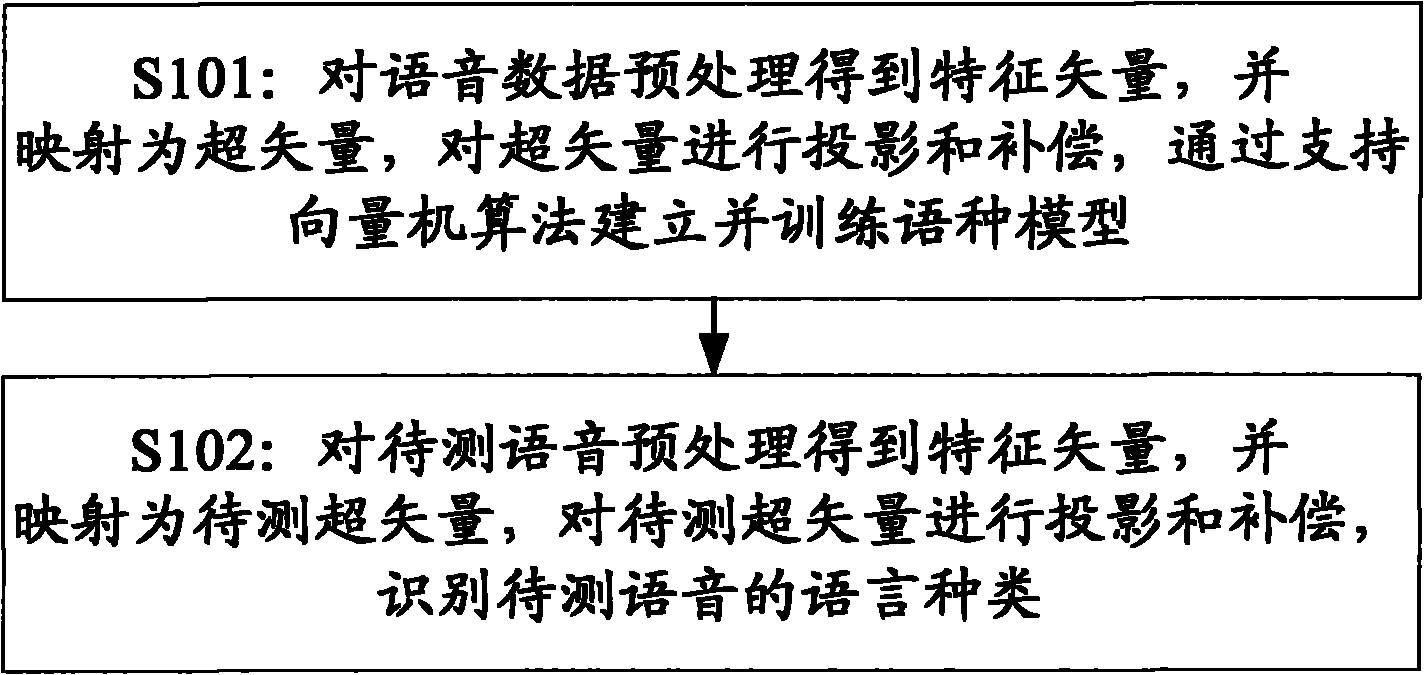
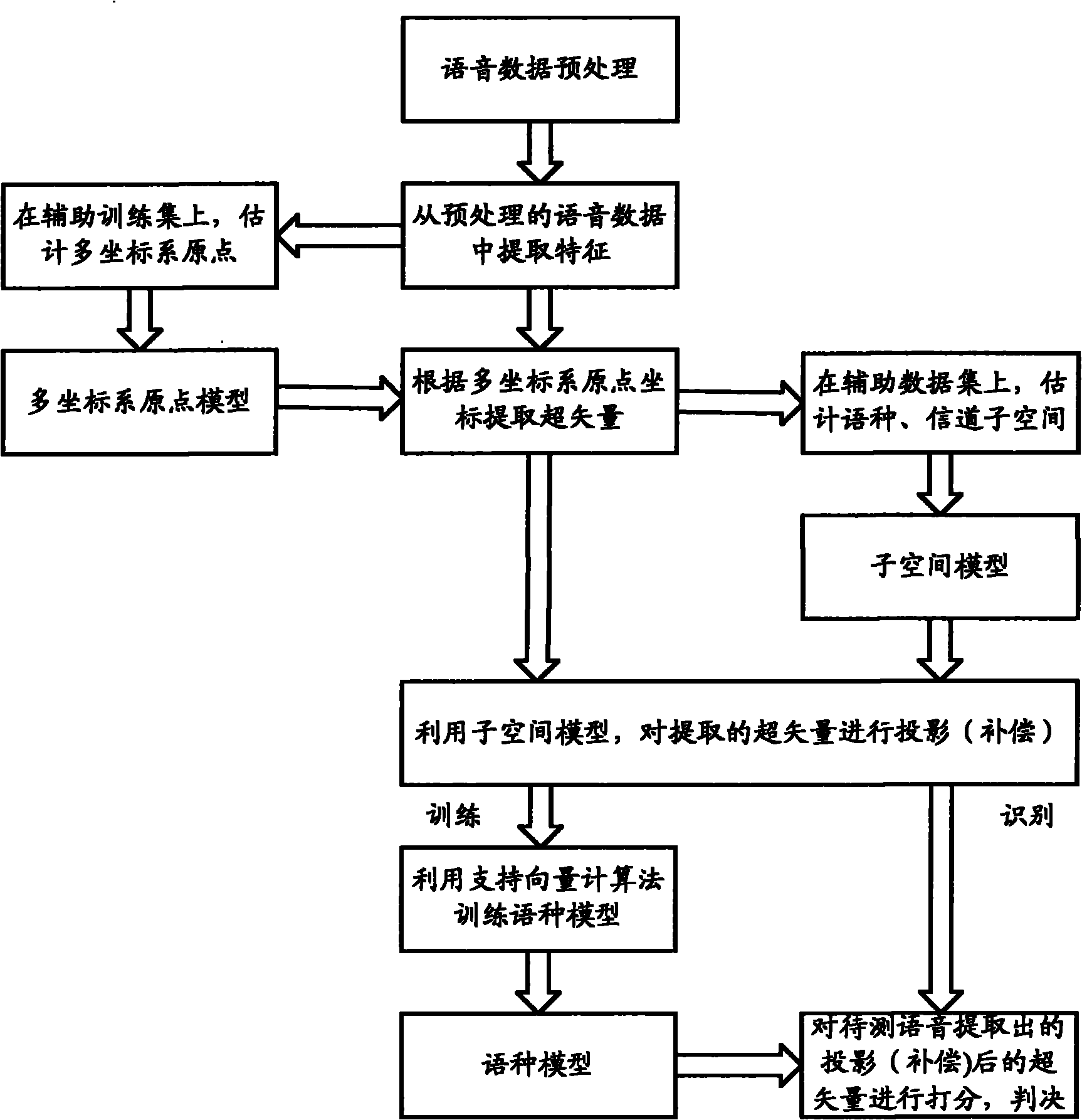
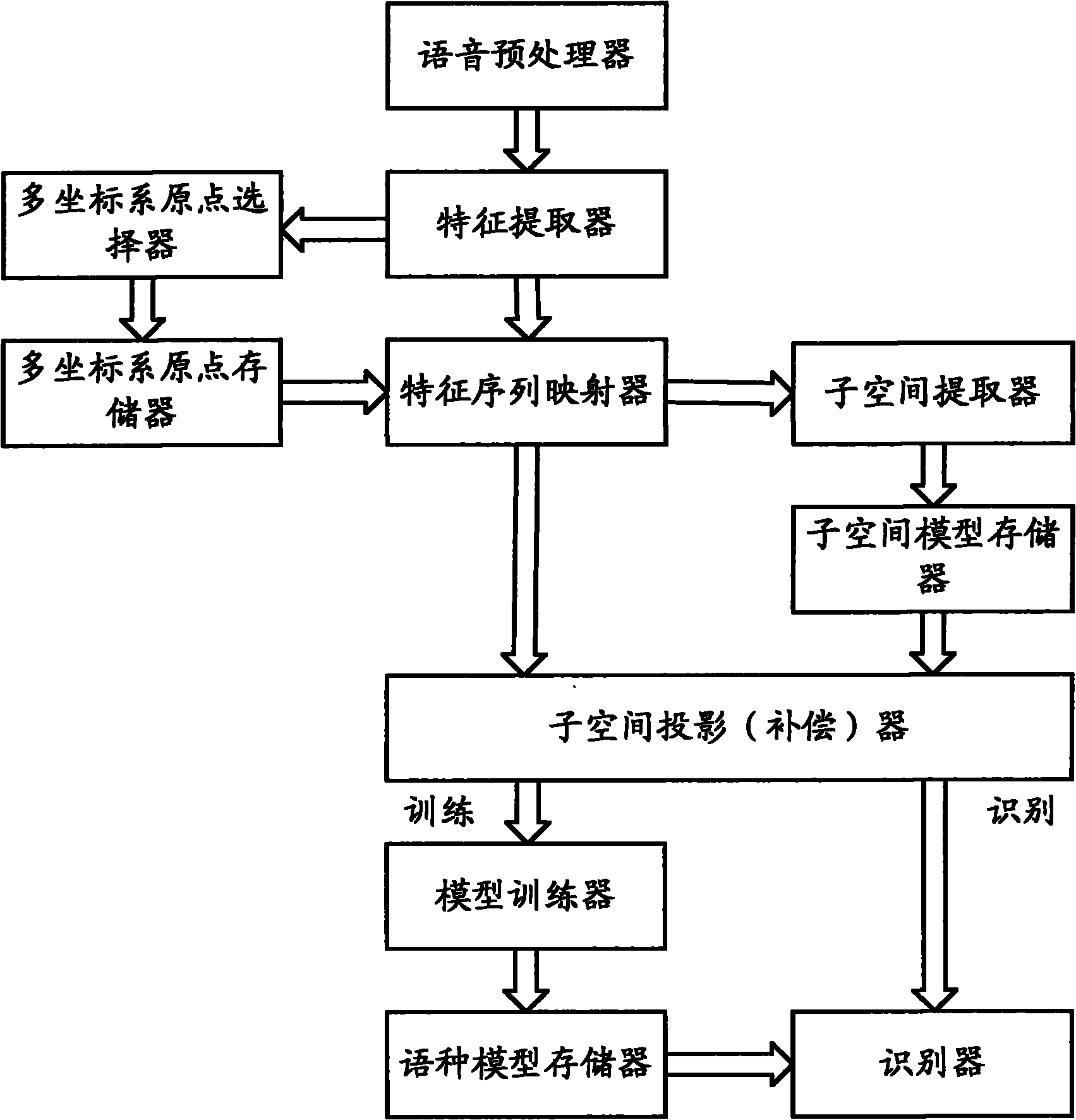
The embodiment of the invention provides a modeling method for language identification, which comprises the following steps of: inputting voice data, preprocessing the voice data to obtain a characteristic sequence, mapping a characteristic vector to form a super vector, performing projection compensation on the super vector, and establishing a training language model through an algorithm of a support vector machine; and adopting the steps to obtain a super vector to be measured of the voice to be measured, performing the projection compensation on the super vector to be measured, grading the super vector to be measured by utilizing the language model, and identifying language types of the voice to be measured. The embodiment of the invention also provides a modeling device for the language identification, which comprises a voice preprocessing module, a characteristic extraction module, a multi-coordinate system origin selection module, a characteristic vector mapping module, a subspace extraction module, a subspace projection compensation module, a training module and an identification module. According to the method and the device which are provided by the embodiment of the invention, information which is invalid to the identification in high-dimension statistics is removed, the correction rate of the language identification is improved, and the computational complexity on an integrated circuit is reduced.
Owner:TSINGHUA UNIV
Identity authentication method and system
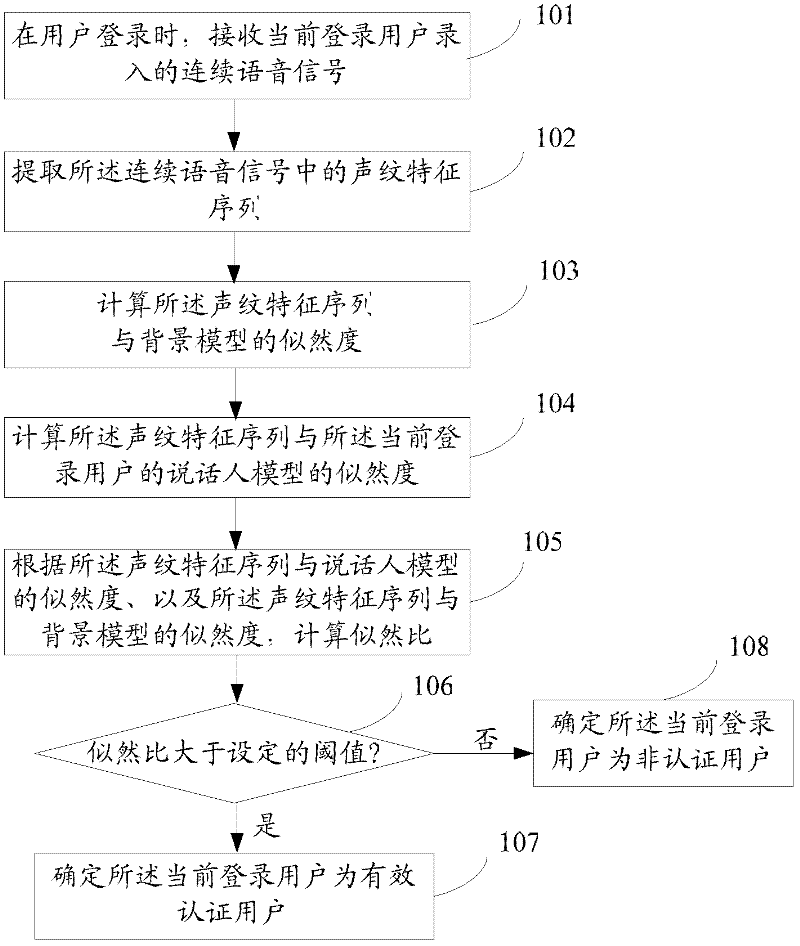
ActiveCN102238190AImprove accuracyUser identity/authority verificationSpeech analysisPasswordLikelihood-ratio test
The invention discloses an identity authentication method and an identity authentication system. The method comprises the following steps of: in the login of a user, receiving a continuous voice signal recorded by the current login user; extracting a voiceprint characteristic sequence from the continuous voice signal; computing likelihood between the voiceprint characteristic sequence and a background model; computing the likelihood between the voiceprint characteristic sequence and a speaker model of the current login user, wherein the speaker model is a polyhybrid Gaussian model constructed according to the repetition times and frame number of the registration voice signals recorded in the login of the current login user; computing a likelihood ratio according to the likelihood between the voiceprint characteristic sequence and the speaker model and the likelihood between the voiceprint characteristic sequence and the background model; and if the likelihood ratio is greater than a preset threshold value, determining the current login user is an effectively authenticated user, otherwise determining the current login user is an unauthenticated user. By the method and the system, the voiceprint-password-based identity authentication accuracy can be improved.
Owner:IFLYTEK CO LTD
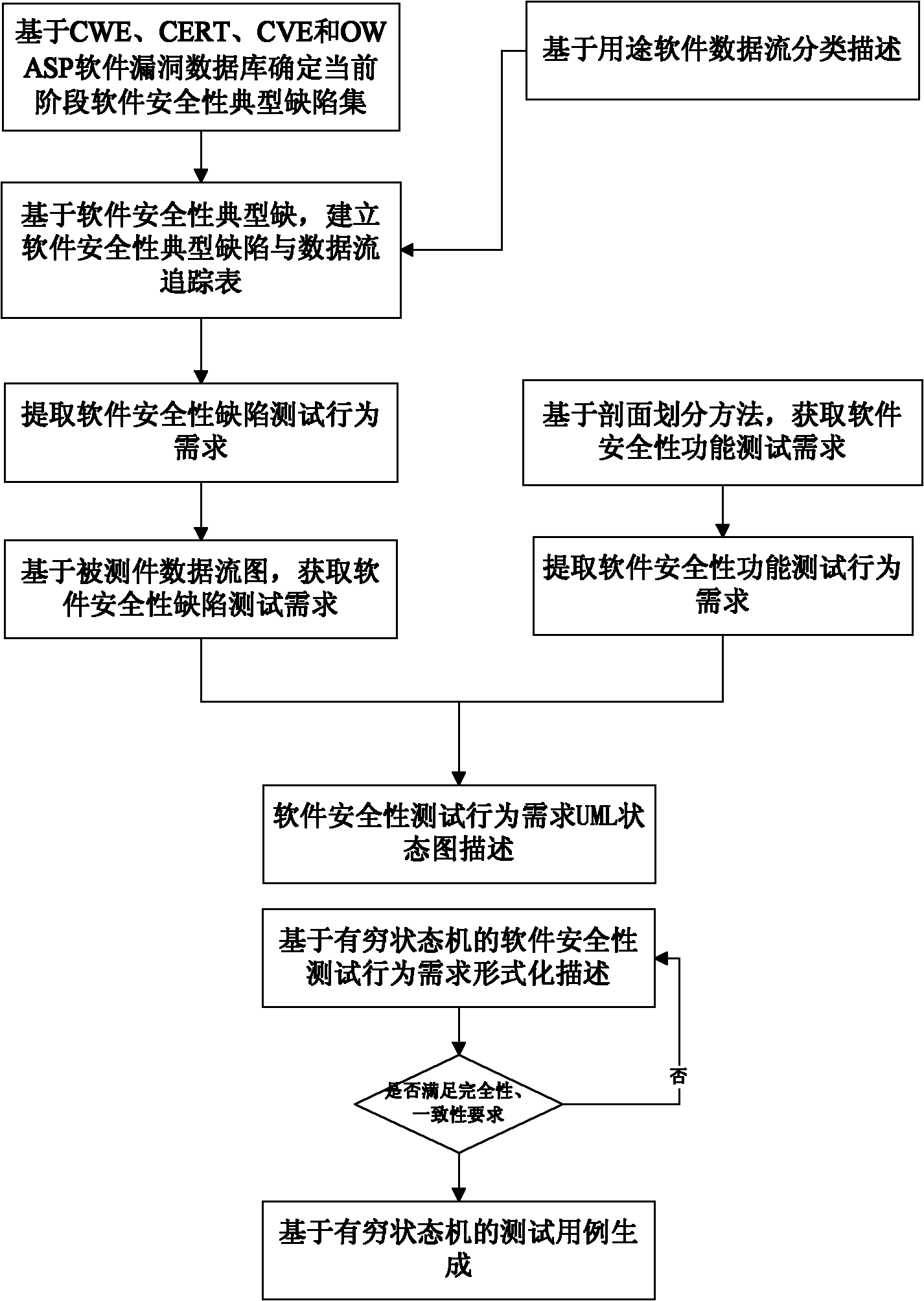
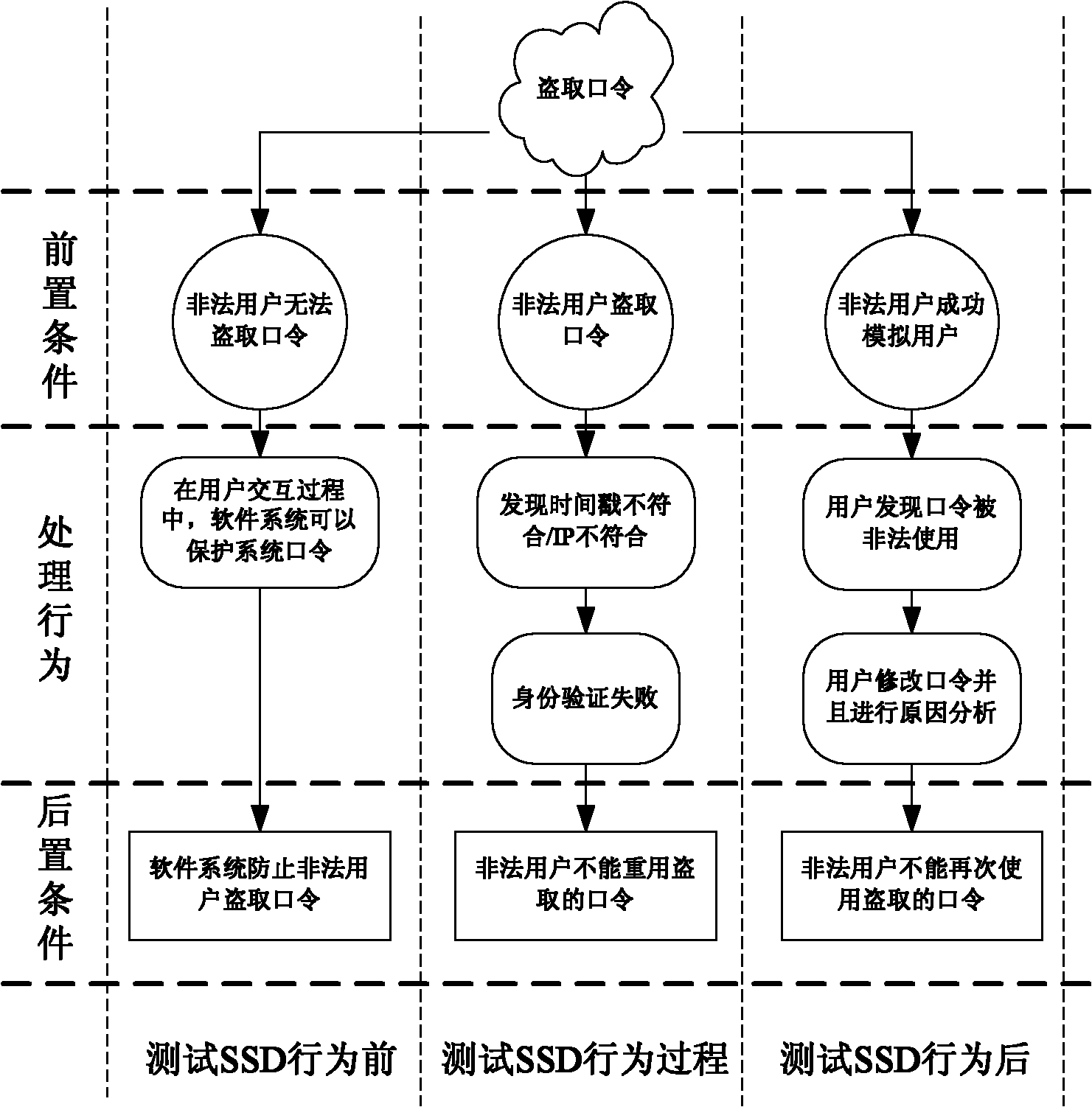
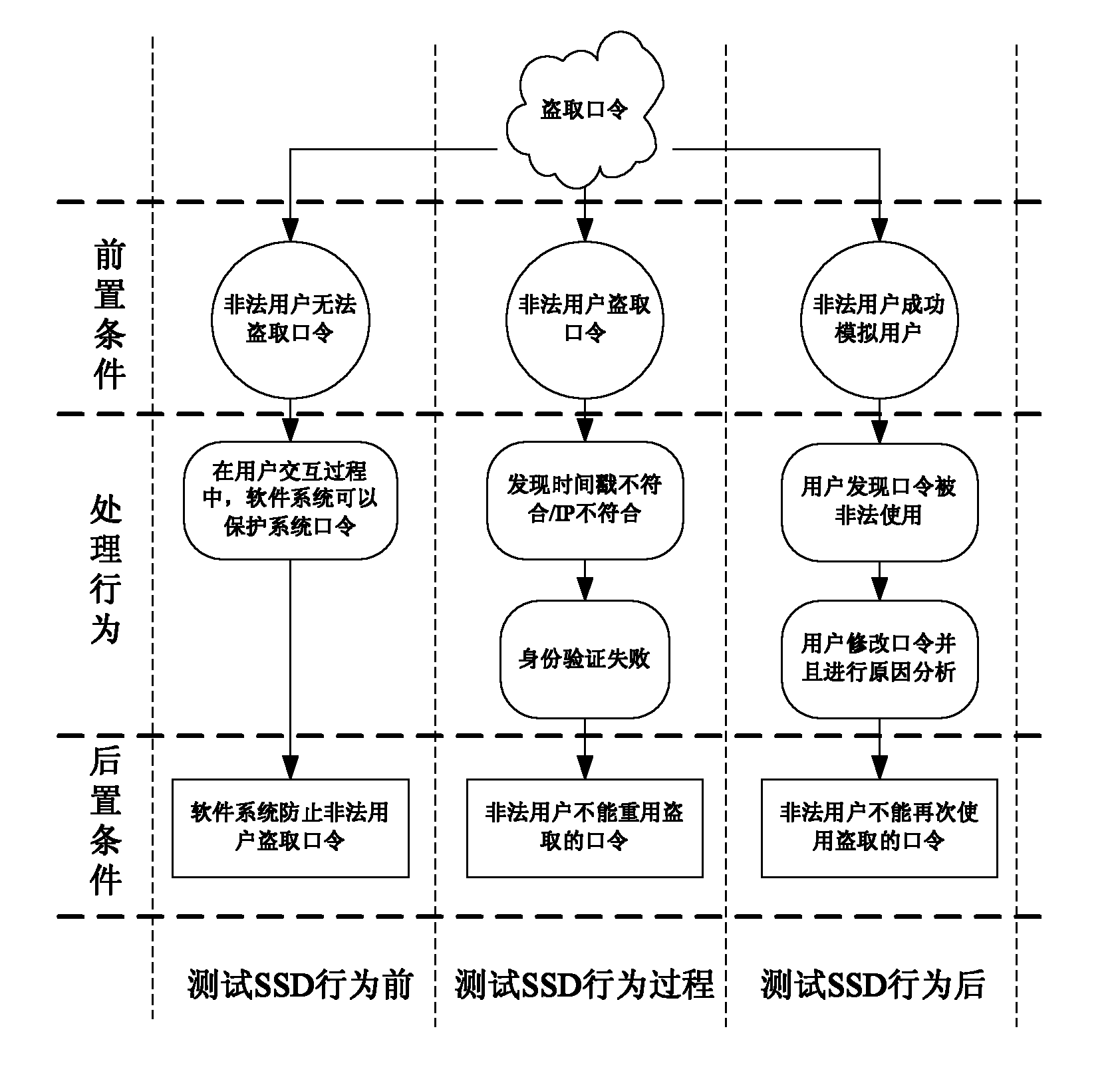
Modeling technology-based software security test method
ActiveCN101950271AGuaranteed test validityImprove targetingSoftware testing/debuggingRequirements modelSupporting system
The invention discloses a modeling technology-based software security test method, which comprises the following steps of: transforming a software security defect test behavior demand and a software security function test behavior demand into formalized software security test behavior demand models, and generating security test cases of a finite state machine characteristic sequence based on the acquired models; and meanwhile, extracting security defects for the acquired security test cases, and complementing a security defect library. The method provided by the invention solves the problem of security test demand extraction in the current standard and an engineering system, and ensures the coverage and validity of the software security test demands. Meanwhile, the method provides a test process system from security test demand extraction, formalized demand description to automatic generation of the test cases, forms a set of full software security test method system and support system, shortens the software security test period at the same time of improving the pertinence, and is favorable for improving the software security quality.
Owner:PLA UNIV OF SCI & TECH
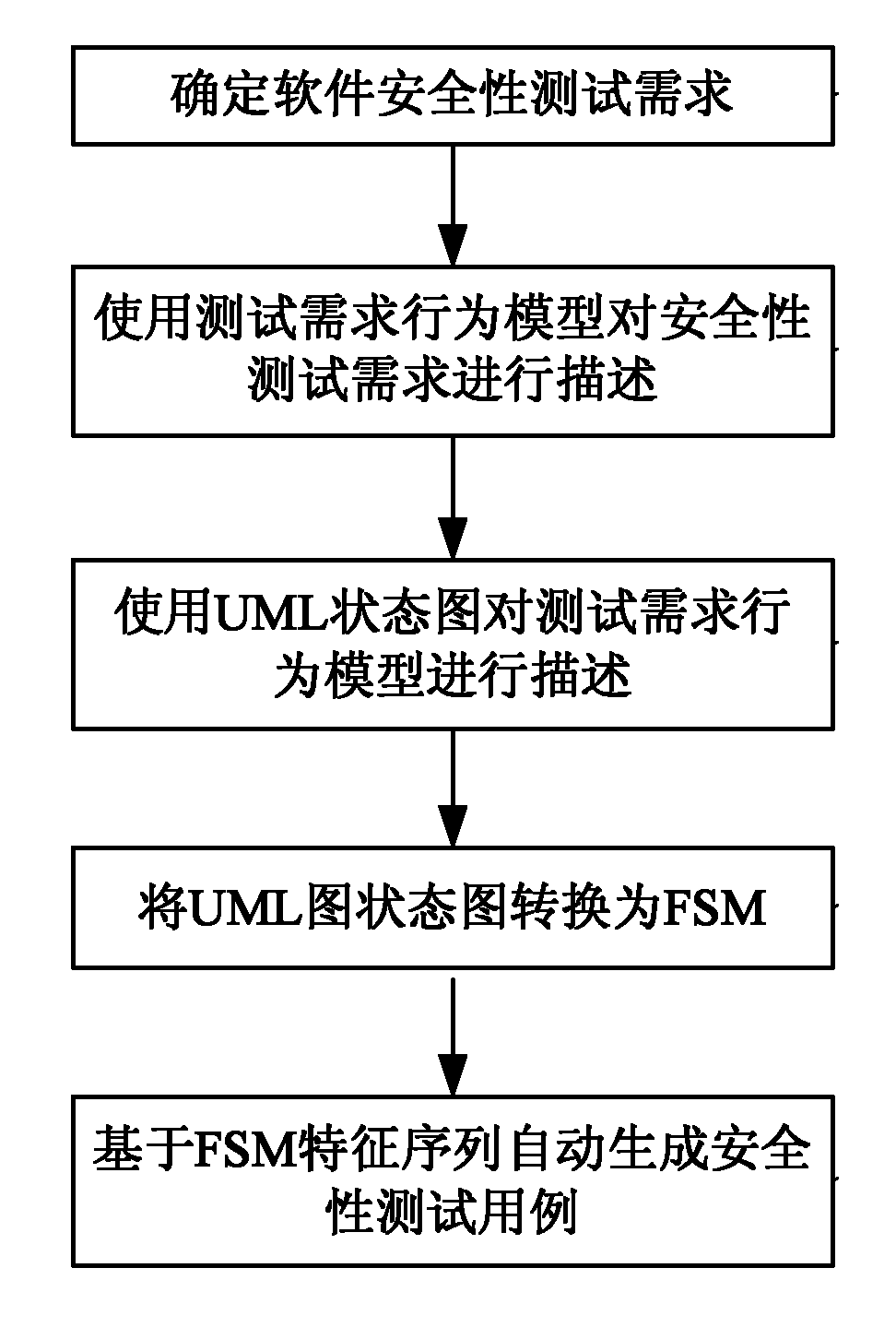
Behavioral model-based software security test case generation method
ActiveCN101968769AOvercome one-sidednessReduce workloadSoftware testing/debuggingCost effectivenessUnified Modeling Language
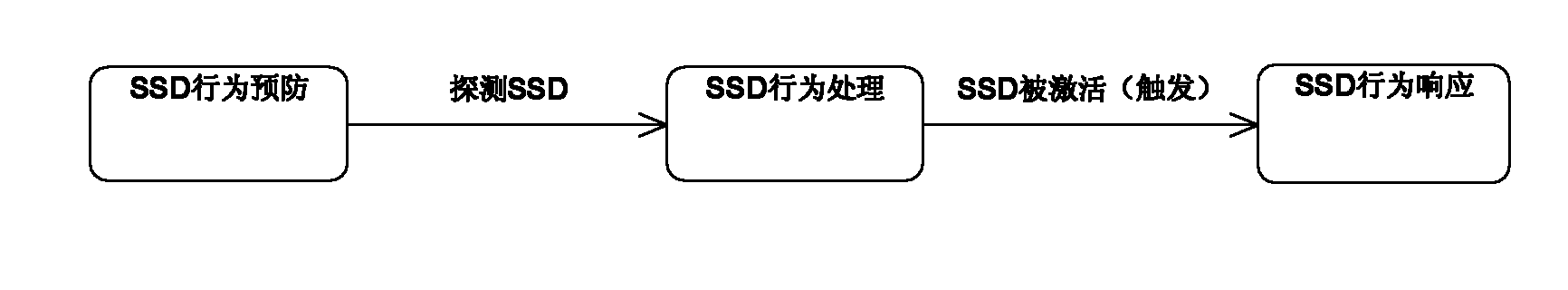
The invention discloses a behavioral model-based software security test case generation method, which comprises the following steps of: (1) determining software security test needs; (2) describing the security test needs by using a test need behavioral model; (3) describing the test need behavioral model by using a unified modeling language (UML) state chart; (4) transforming the UML state chart into a finite state machine (FSM); and (5) automatically generating a security test case based on a characteristic sequence of the FSM. In the behavioral model-based software security test case generation method provided by the invention, security test is performed primarily from a software security defect (SSD) behavior prevention mechanism, an SSD behavior detection mechanism and an SSD behavior response mechanism, so that the one-sidedness and need imperfection of conventional software security tests are overcome and the test effectiveness is ensured. Simultaneously, the test case automatic generation method provided by the invention reduces the workload of testers, improves the efficiency and level of automation of the test and ensures test effects.
Owner:PLA UNIV OF SCI & TECH
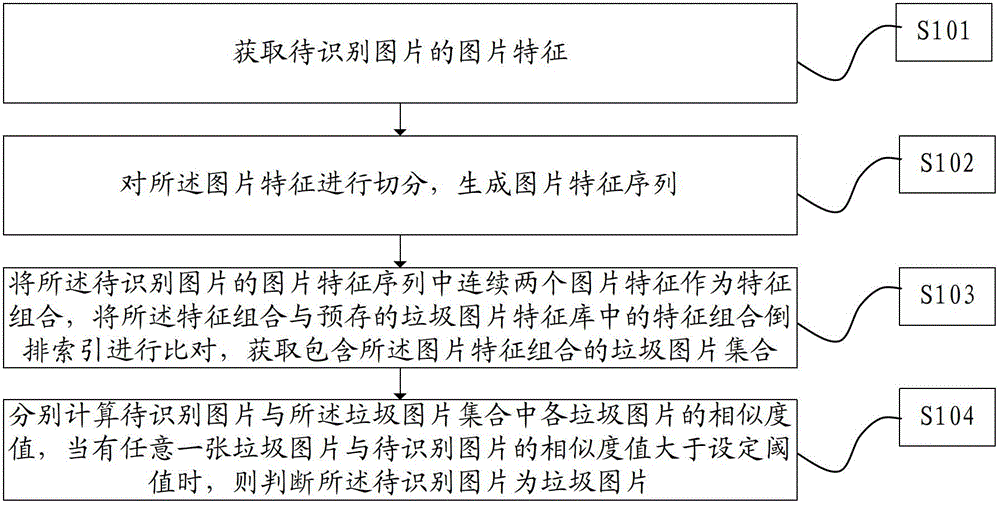
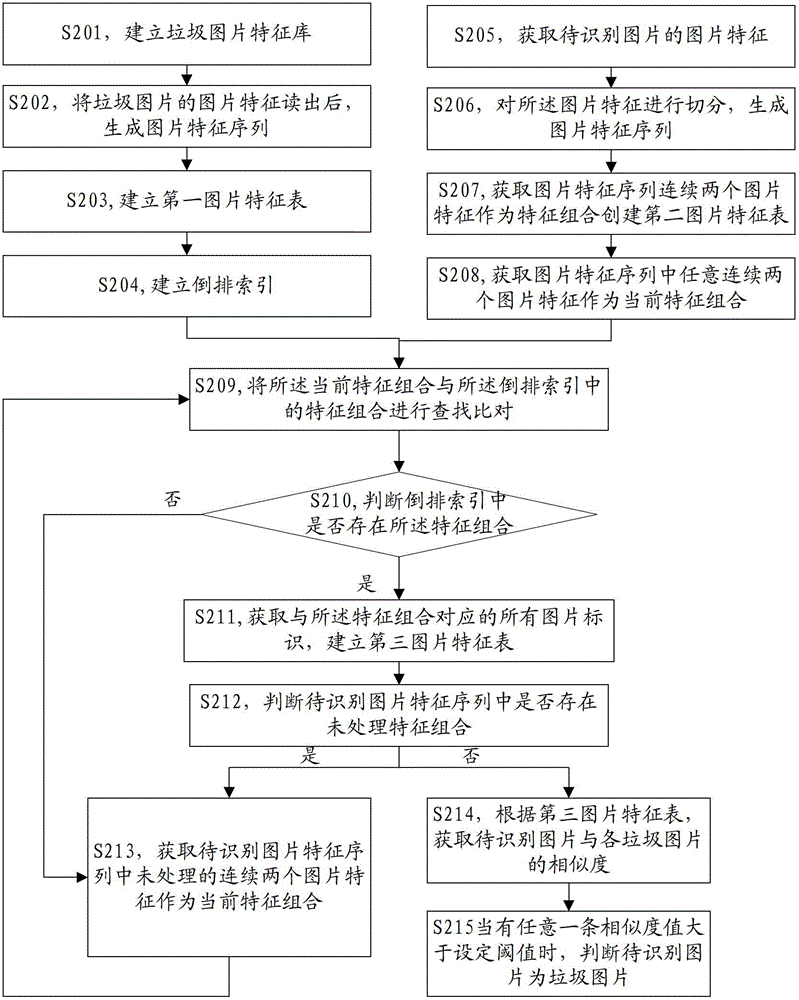
Method and device for identifying garbage pictures
ActiveCN102722709AImprove recognition efficiencyAdaptableImage analysisCharacter and pattern recognitionPattern recognitionImaging processing
The invention relates to the technical field of image processing, in particular to a method and a device for identifying garbage pictures. The method comprises the following steps of: acquiring picture characteristics of a picture to be identified; splitting the picture characteristics to generate a picture characteristic sequence; and quickly comparing the characteristic combination, namely two continuous picture characteristics in the picture characteristic sequence, with a characteristic combination in a pre-stored garbage picture characteristic library through reverse index to obtain a garbage picture set comprising the picture characteristic combination; and calculating the similarity value of the picture to be identified and each garbage picture in the garbage picture set, and when the similarity value of any one garbage picture and the picture to be identified is greater than a set threshold value, determining that the picture to be identified is a garbage picture. By the method, on the one hand, the identification efficiency of garbage pictures can be improved, and on the other hand, the identification effect is improved because the method has strong adaptability to changes of the garbage pictures.
Owner:杭州网易智企科技有限公司
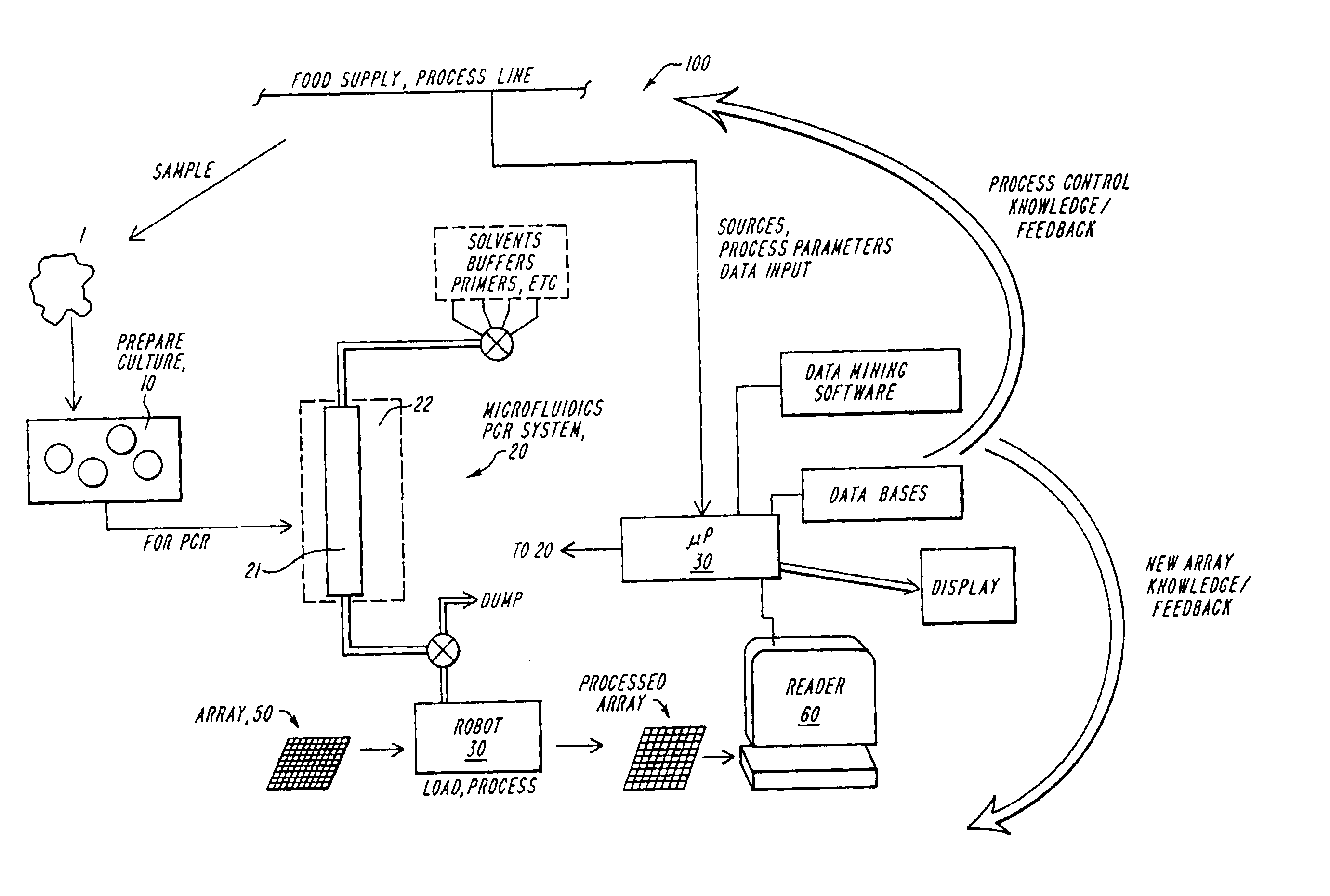
Multispecies food testing and characterization organoleptic properties
InactiveUS6878517B1High sensitivityThe testing process is simpleBioreactor/fermenter combinationsBiological substance pretreatmentsAdditive ingredientOrganism
A testing system useful for food products employs a multispecies testing array to test for presence or amount of a plurality of organisms in a sample by detecting plural characteristic sequences for each of plural organisms to form a multispecies distribution output or microbial profile, and this is processed or used in conjunction with data mining or other processing to provide trend, warning or other data. The processor correlates and stores information relating to taste, smell, texture, processing conditions, quality or source of a component or ingredient, potential pathogenicity or other factor, with correlations on a multidimensional space yielding new preconditions or warning indications, and providing a mechanism for specialization of the species distribution data for specific products, as well as for incorporation or development of process changes and company trade secrets.
Owner:CONAGRA FOODS
Systems and methods using magnetically-responsive sensors for determining a genetic characteristic
ActiveUS20180237850A1Microbiological testing/measurementMaterial analysis by electric/magnetic meansElectrical resistance and conductanceBiology
Sequencing-by-synthesis (SBS) method is provided that includes providing a detection apparatus that includes an array of magnetically-responsive sensors. Each of the magnetically-responsive sensors is located proximate to a respective designated space to detect a magnetic property therefrom. The detection apparatus also includes a plurality of nucleic acid template strands located within corresponding designated spaces. The method also includes conducting a plurality of SBS events to grow a complementary strand by incorporating nucleotides along each template strand. At least some of the nucleotides are attached to corresponding magnetic particles having respective magnetic properties. Each of the plurality of SBS events includes detecting changes in electrical resistance at the magnetically-responsive sensors caused by the respective magnetic properties of the magnetic particles. The method also includes determining genetic characteristics of the complementary strands based on the detected changes in electrical resistance.
Owner:ILLUMINA INC
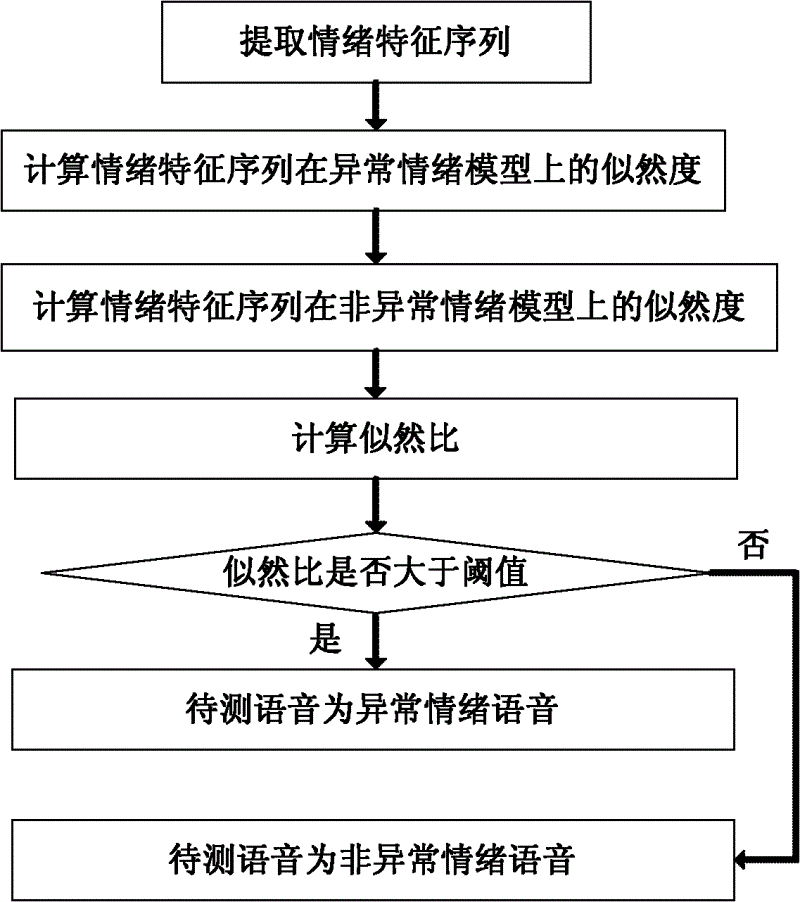
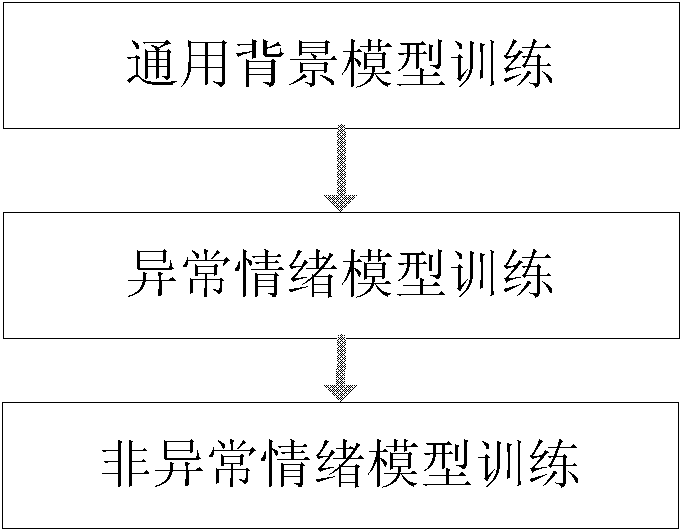
Abnormal emotion automatic detection and extraction method and system on basis of short-time analysis
ActiveCN102623009ARealize automatic and efficient judgmentImprove the ability to distinguishSpeech recognitionPattern recognitionAbnormal voice
The invention discloses an abnormal emotion automatic detection and extraction method and an abnormal emotion automatic detection and extraction system on the basis of the short-time analysis. The method comprises the following steps of: extracting an emotion characteristic sequence from a voice signal to be detected; calculating the likelihood of the emotion characteristic sequence and an abnormal emotion model in a preset emotion model and calculating the likelihood of the emotion characteristic sequence and a non-abnormal emotion model in the preset emotion model; according to the likelihood of the emotion characteristic sequence and the abnormal emotion model and the likelihood of the emotion characteristic sequence and the non-abnormal emotion model, calculating the likelihood ratio; and judging whether the likelihood ratio is greater than a set threshold value, determining the voice signal to be detected is abnormal emotion voice if yes, or determining the voice signal to be detected is a non-abnormal voice signal. Due to the utilization of the abnormal emotion automatic detection and extraction method and the abnormal emotion automatic detection and extraction system, the automatic high-efficiency judgment on the abnormal emotion in the voice signal can be implemented and the automatic processing efficiency of mass customer service data is improved.
Owner:武汉讯飞兴智科技有限公司
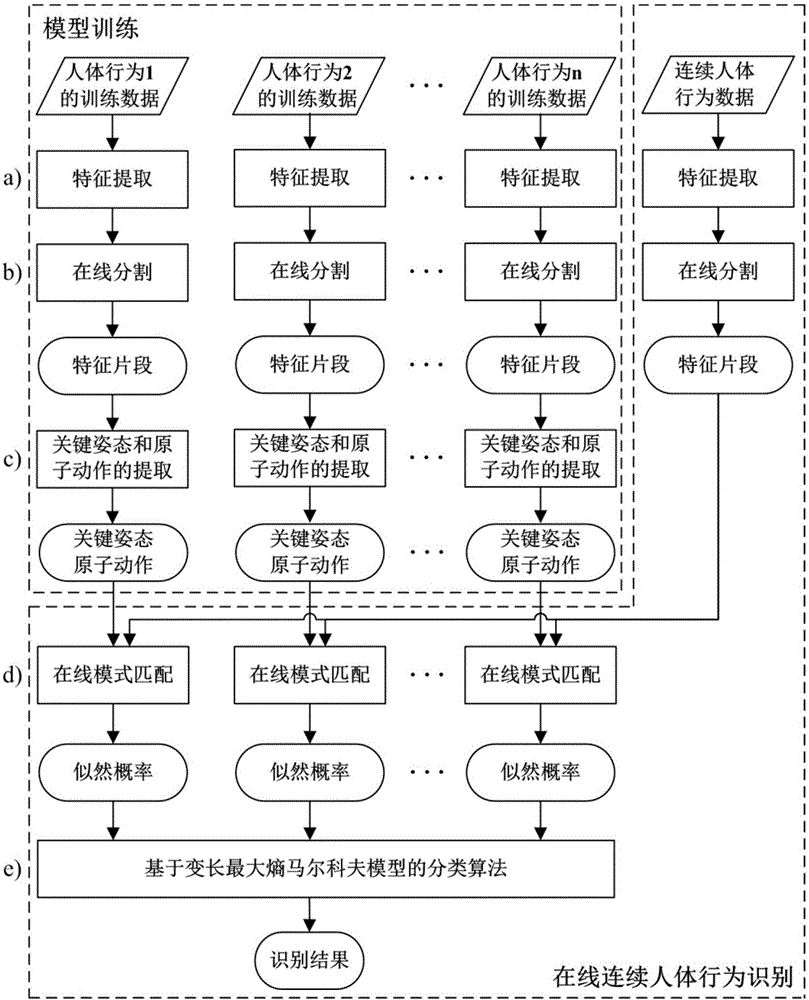
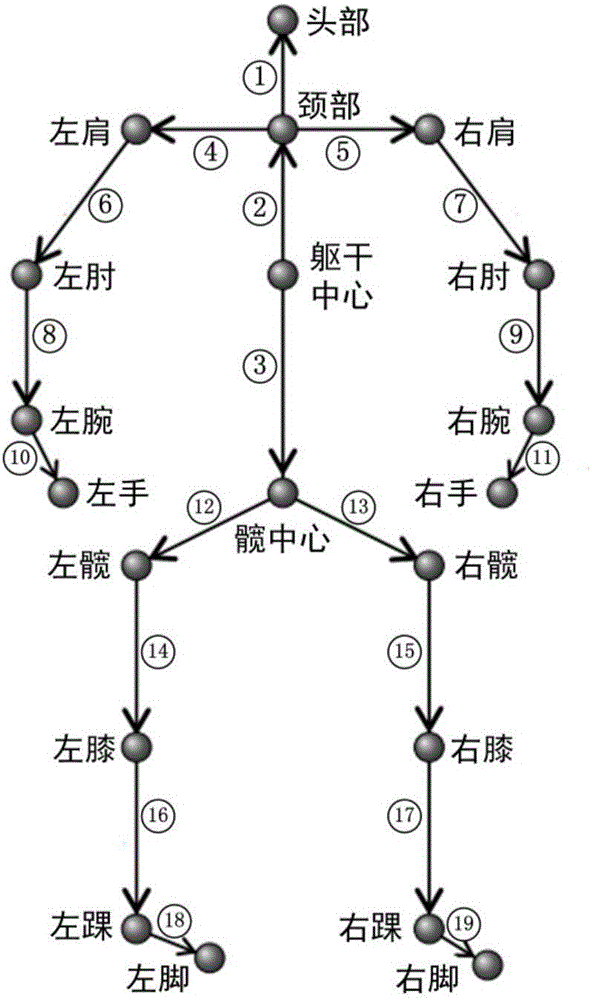
Online continuous human behavior identification method based on Kinect
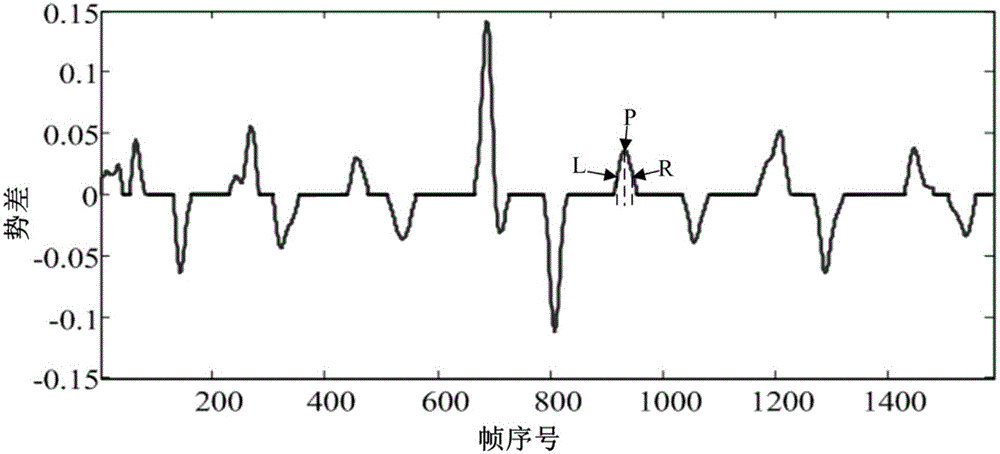
InactiveCN106650562AQuick identificationGuaranteed identifiabilityCharacter and pattern recognitionHuman behaviorPattern matching
The invention discloses an online continuous human behavior identification method based on Kinect, comprising the following steps: (a) extracting human skeleton information from an RGB-D image collected by Kinect, and calculating the normalized relative orientation feature of each joint; (b) carrying out online dynamic segmentation on a feature sequence through an online segmentation method based on feature sequence potential difference to get a gesture feature fragment and an action feature segment; (c) respectively extracting key gestures and atomic actions from the gesture feature fragment and the action feature segment obtained through segmentation; (d) carrying out online mode matching between the feature segments obtained through segmentation and key gestures or atomic actions obtained through offline training, and calculating the likelihood probability that the feature segments are identified as the key gestures or atomic actions of a kind of behavior; and (e) using a variable-length maximum entropy Markov model to identify human behaviors based on the likelihood probability calculated. Compared with the known algorithms, there is no need to detect the start and end time points of each human behavior in advance, and identification can be executed online and in real time.
Owner:XIDIAN UNIV
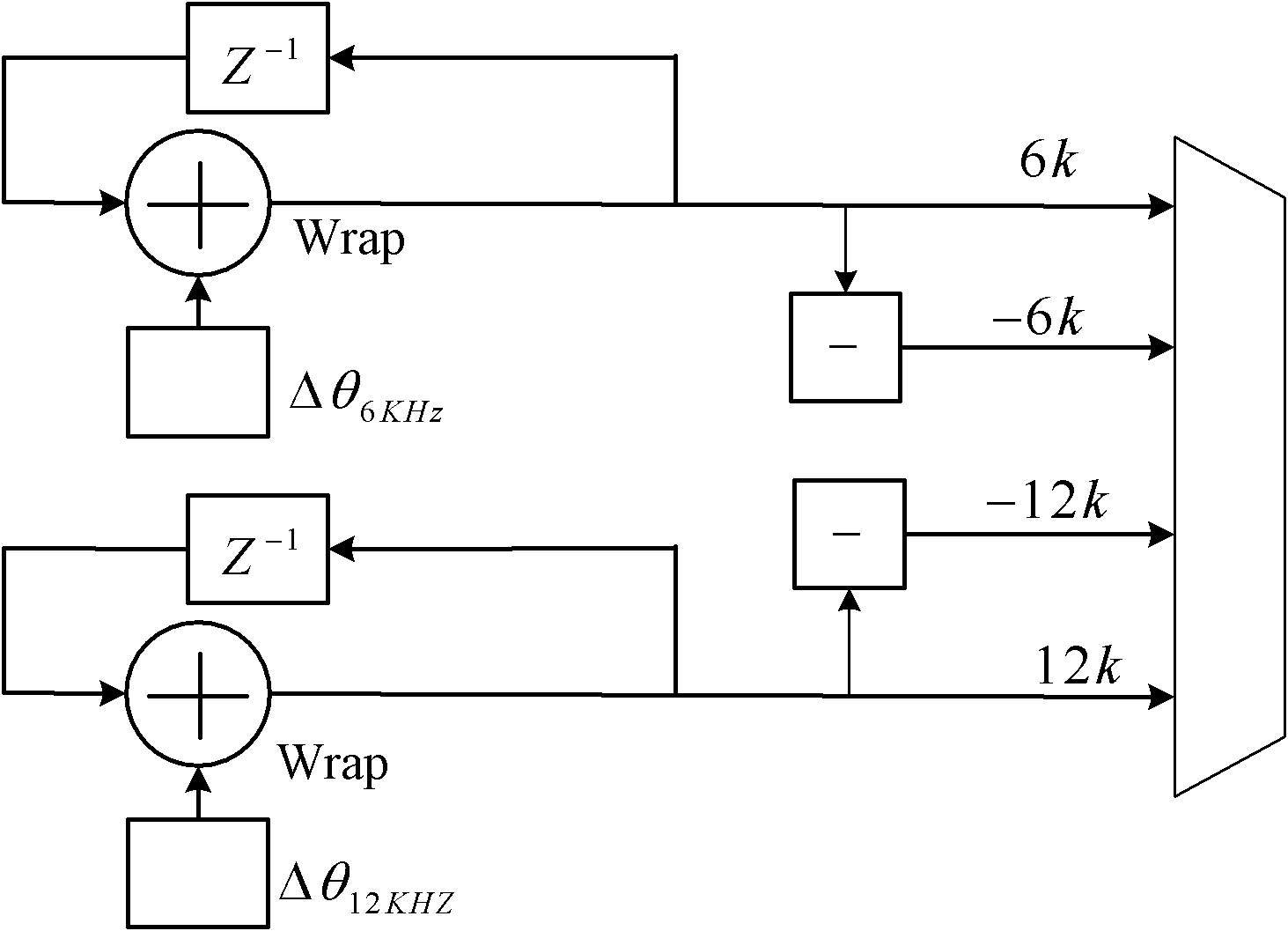
Method, device and terminal for detecting long term evolution (LTE) master synchronizing signal
ActiveCN102122997AIncrease success rateExpand the detection range of frequency offsetTransmission monitoringRadio transmission for post communicationTime domainCurrent cell
The invention relates to a method, device and terminal for detecting a long term evolution (LTE) master synchronizing signal. In the method, frequency shift range is divided into a plurality of branches, each branch corresponds to a frequency shift value, and each frequency shift value is attached to input time domain data by a coordinated rotation digital computer algorithm; the time domain data with frequency shift value is subjected to sampling point separation, and time domain data subjected to the sampling point separation is respectively subjected to time domain slippage correlation with three local characteristic sequences; power value calculation is carried out on the correlation results, and the separated sampling points with big power value are output so as to obtain multichannel frequency shift branch data; and the maximum value in peak values related to multichannel frequency shift branch data is acquired, the master synchronizing signal corresponding to the maximum value is the master synchronizing signal of the current cell, and the frequency shift value corresponding to the maximum value is an initial frequency shift estimation value. According to the invention, the detection success rate of a master synchronizing signal position is greatly improved, the range of detecting the frequency shift is enlarged, the system resources are reduced, and the implementation is convenient.
Owner:SANECHIPS TECH CO LTD
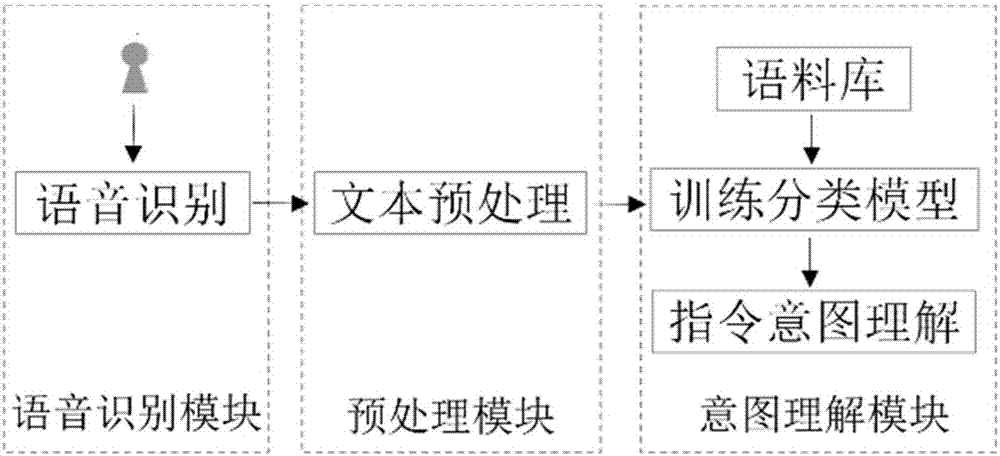
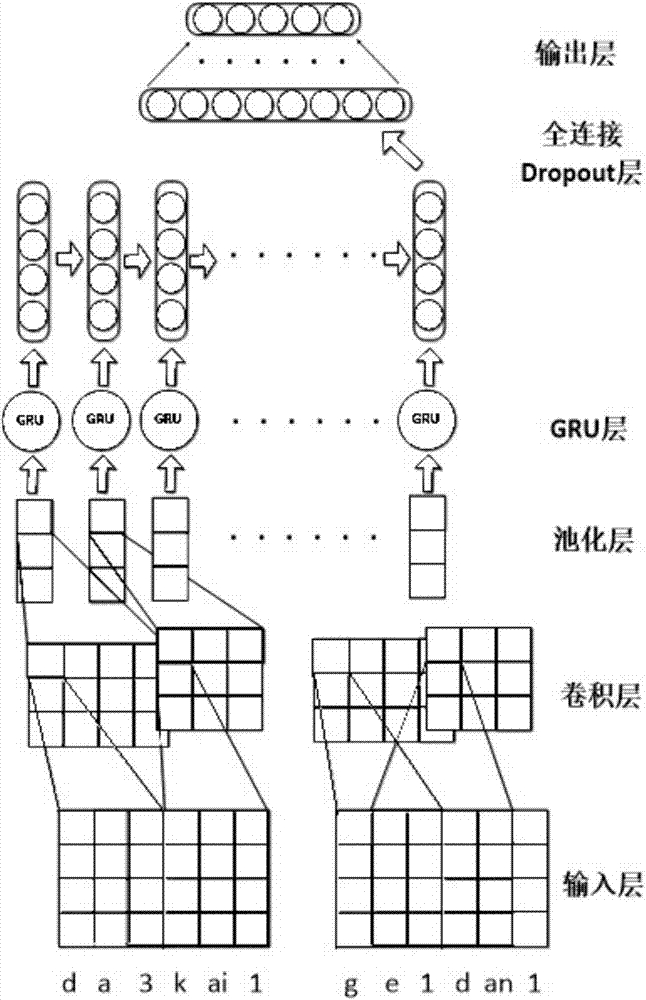
Semantic comprehension system and method oriented to Chinese text
InactiveCN107577662AResolve unmeasured wordsSolve the relationship between wordsNeural architecturesSpecial data processing applicationsPart of speechCurse of dimensionality
The invention provides a semantic comprehension system and method oriented to a Chinese text. Based on deep learning, a deep learning text classification model is provided; the model is divided into an input layer, a convolutional layer, a pooling layer, a GRU (Gated Recurrent Unit) layer, a fully connected layer and an output layer; a pinyin characteristic sequence of text segmentation is used asinput; characteristics are obtained through multi-layer characteristic extraction; and an intention category is predicted to obtain a text classification result. According to the semantic comprehension system and method oriented to the Chinese text, the part of speech of a statement does not need to be judged, a complex preprocessing process such as a syntax analysis tree and the like does not need to be generated, the text only needs to be segmented and the segmented text is converted into pinyin, and the problems that the relation between words and words cannot be measured, a lot of external prior knowledge is needed and the curse of dimensionality is easily generated when large-scale corpuses are processed in a conventional characteristic extraction method are solved.
Owner:SHANGHAI JIAO TONG UNIV +1
Flame detection method based on kinetic characteristic and color spatiotemporal information
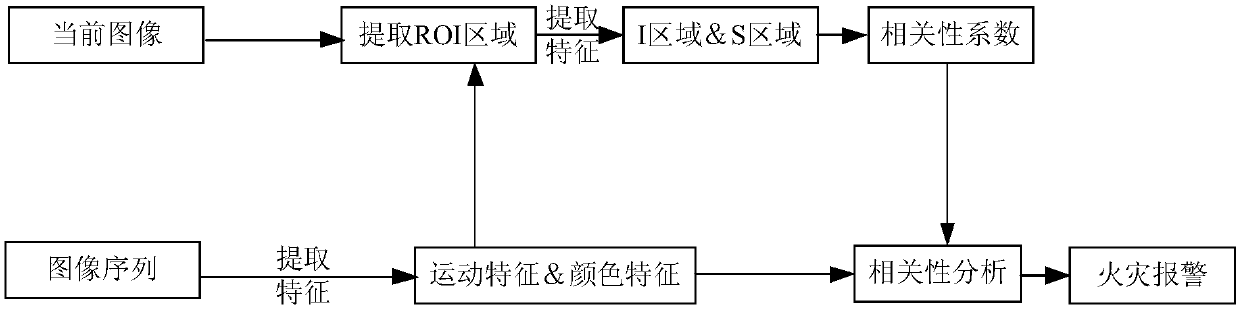
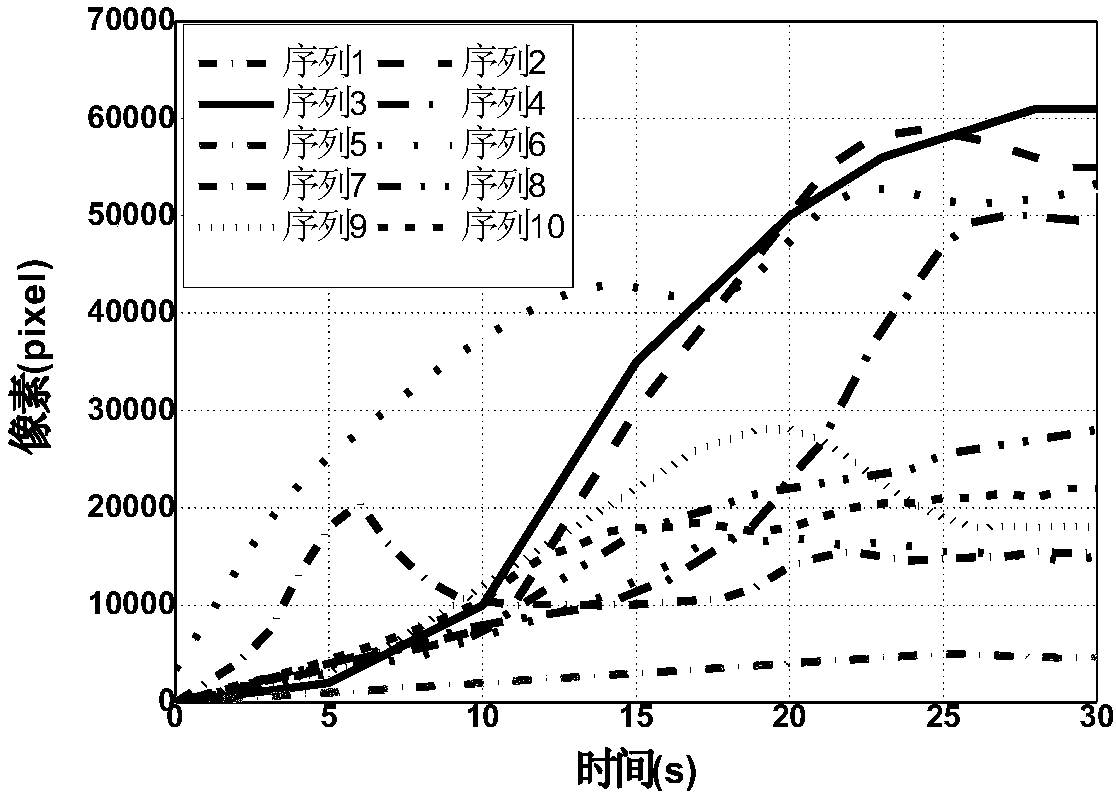
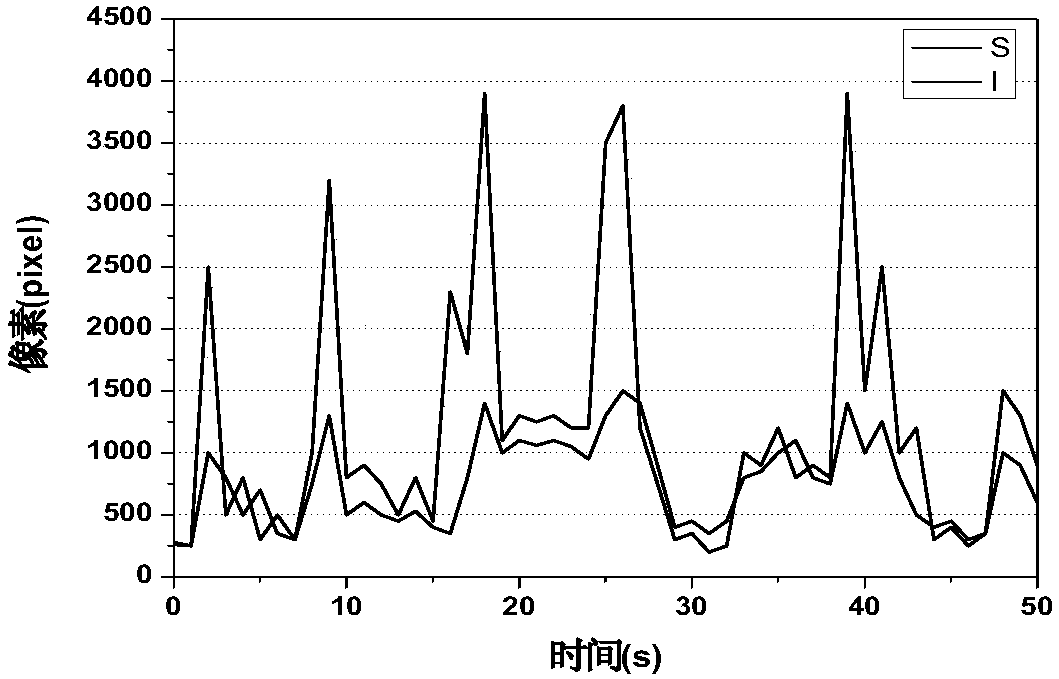
ActiveCN107025652AEliminate distractionsEfficient separationImage analysisPattern recognitionCorrelation analysis
The invention discloses a flame detection method based on a kinetic characteristic and color spatiotemporal information. The method is characterized by converting a region of interest into a brightness component and a saturation component by using the color spatiotemporal information characteristic of a real flame area; obtaining a foreground region by means of a threshold value; successively obtaining a foreground region I and a foreground region S according to an image sequence time sequence; storing the foreground region I and the foreground region S to form a characteristic sequence; inputting a observation characteristic value sequence into a correlation analysis formula for calculation to obtain a confirmation result indicating whether real flame exists in the region of interest; and when a correlation analysis result is greater than a confirmation threshold, determining that the real flame exists in the region of interest and giving an alarm. The flame detection method has good rapidity, has a high detection rate and a low false detection rate within short processing time, has good robustness to illumination, and can be widely used in fire monitoring occasions.
Owner:TAIYUAN UNIV OF TECH
Secondary protein structureprediction method based on deep neural network
InactiveCN105930686AImprove forecasting efficiencyImprove forecast accuracySpecial data processing applicationsNeural learning methodsNerve networkAlgorithm
The invention discloses a secondary protein structureprediction method based on a deep learning andneural network method, and relates to the technical field of neural networks and secondary protein structureprediction. The method comprises the steps of inputting a protein characteristic sequence, and predicting a space secondary structure of an amino acid residue at each site of the sequence through a designed deep recurrent neural network model. The method provided by the invention realizes automatic predication of the secondary structure based on input characteristics, has better generalization ability, and can train a specific model and realize secondary structure predication with high accuracy according to the different input characteristics.
Owner:SICHUAN UNIV
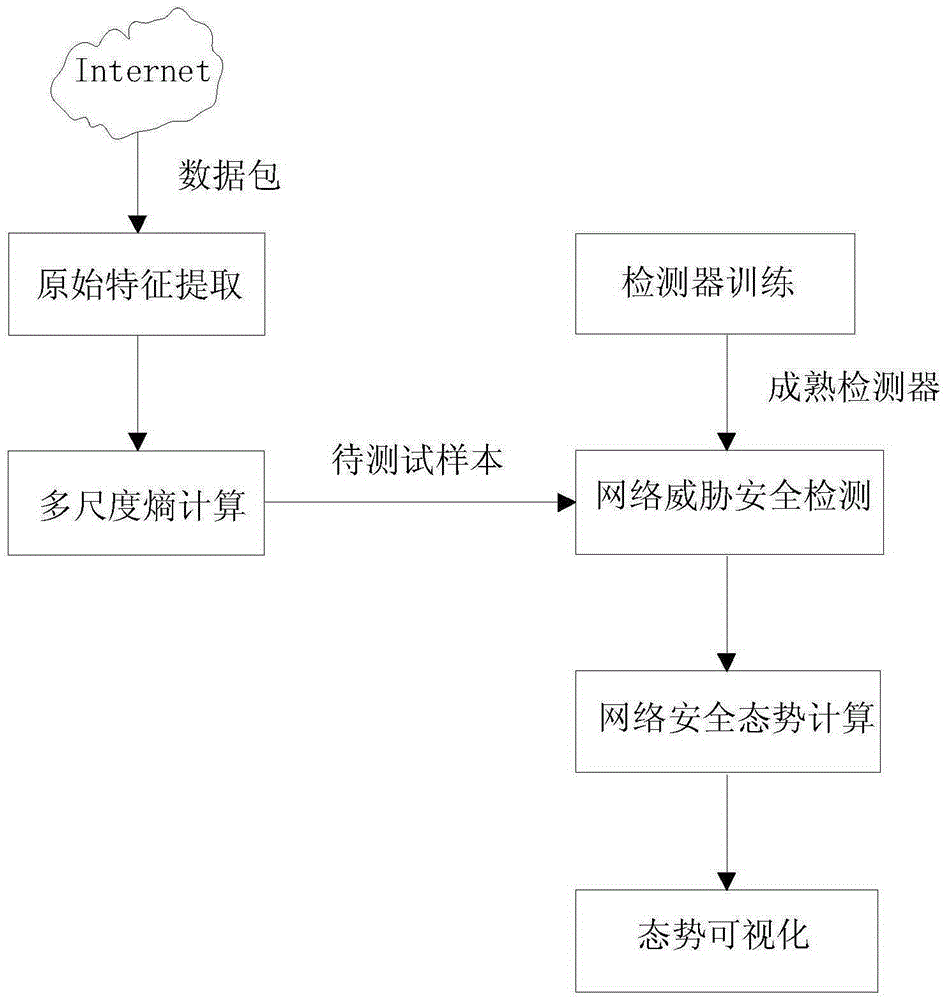
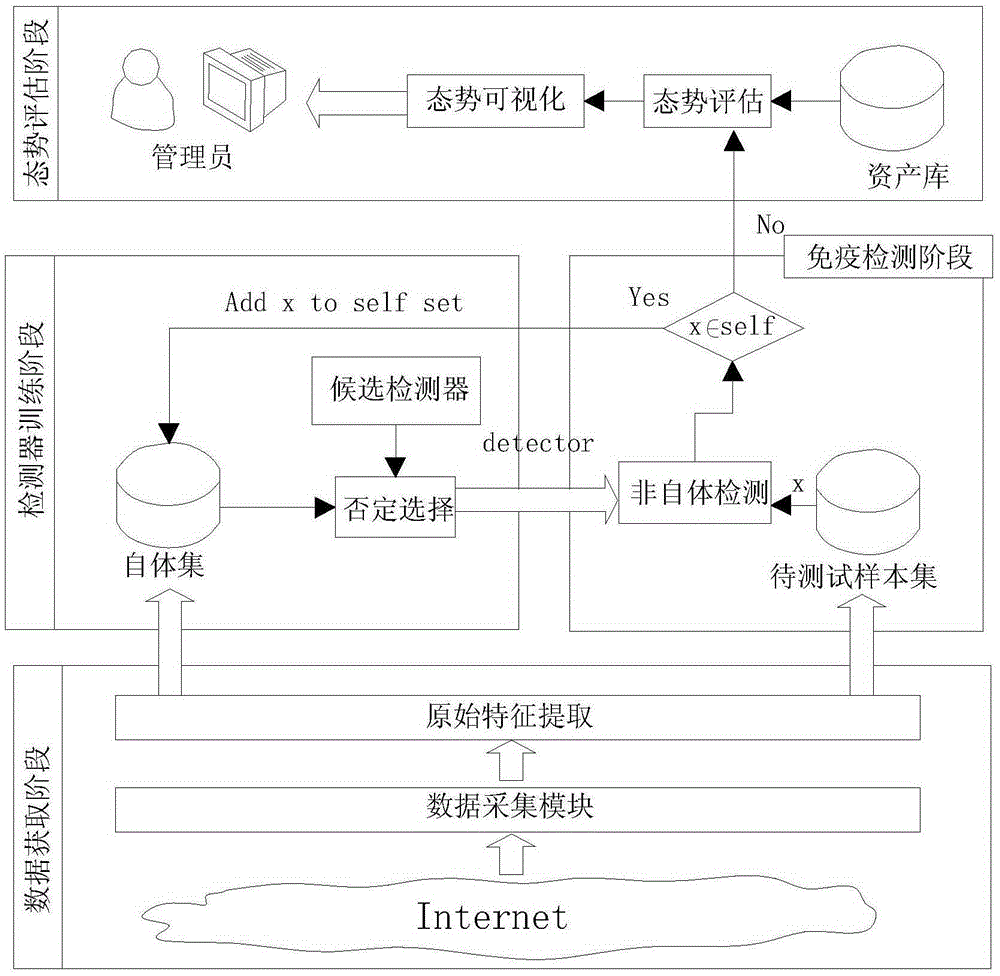
Cyberspace security situation real-time detection method
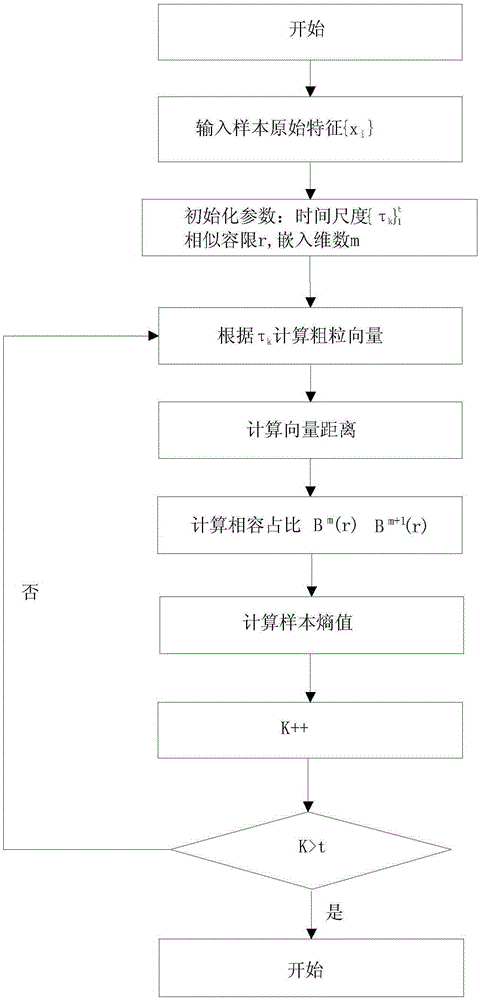
ActiveCN105357063AComprehensive time scaleHigh level of integrationData switching networksOriginal dataMulti scale entropy
The invention discloses a cyberspace security situation real-time detection method. The method comprises the following steps: original characteristic extraction that original network data packet characteristics are obtained from a network, multi-scale entropy calculations that sample entropy of an original data packet characteristic sequence is calculated at different time scales, detector training that a mature immunization detector is trained and generated by utilizing a sample entropy characteristic vector and a negative-selection algorithm at the different time scales, network threat security detection that a network sample is detected by utilizing the trained mature immunization detector at the different time scales, cyberspace security situation calculations that cyberspace security situations at the different time scales and different network layers, and situation visualization that the cyberspace security situations are expressed by different colors of curve charts at different time and the different network layers. The time scales considered in the method is relatively comprehensive, the fusion level is high, a situation assessment result is relatively accurate, a complex characteristics of a network behavior can be described, and the whole process of a network threat behavior can be carved in a fine-grained manner.
Owner:金润方舟科技股份有限公司
Method for generating human vocal print biometric key
ActiveCN103873254AFree from memory burdenUser identity/authority verificationComputer hardwareKey size
The invention provides a method for generating a human vocal print biometric key. According to the method, a vocal print characteristic sequence is projected into a high-dimensional space, the characteristic sequence is stabilized within an acceptable fluctuation range in the high-dimensional space, and the stabilized sequence is encoded, and the biometric key is extracted from a code. In the whole method, the vocal print template of a user does not need to be recorded on a to-be-authenticated user side or an authentication server side, the user generates a (user name and key) pair locally by acquiring own voice, and network identity authentication is performed through various authentication methods derived from the (user name and key) pair. The vocal print key can be applied to network identity authentication as well as encryption of various user private data in a safe and convenient manner. The user does not need to remember redundant passwords, and meanwhile a key sequence with a sufficient length can be obtained. The key length of an extracted novel human vocal print biometric key can be greater than 256bit.
Owner:HANGZHOU DIANZI UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com