Detecting method and system for malicious codes
A malicious code and detection method technology, applied in the field of malicious code network behavior characteristic analysis and detection system, can solve the problems of increasing computer systems being infected and attacked, malicious code is complicated, and cannot be identified
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
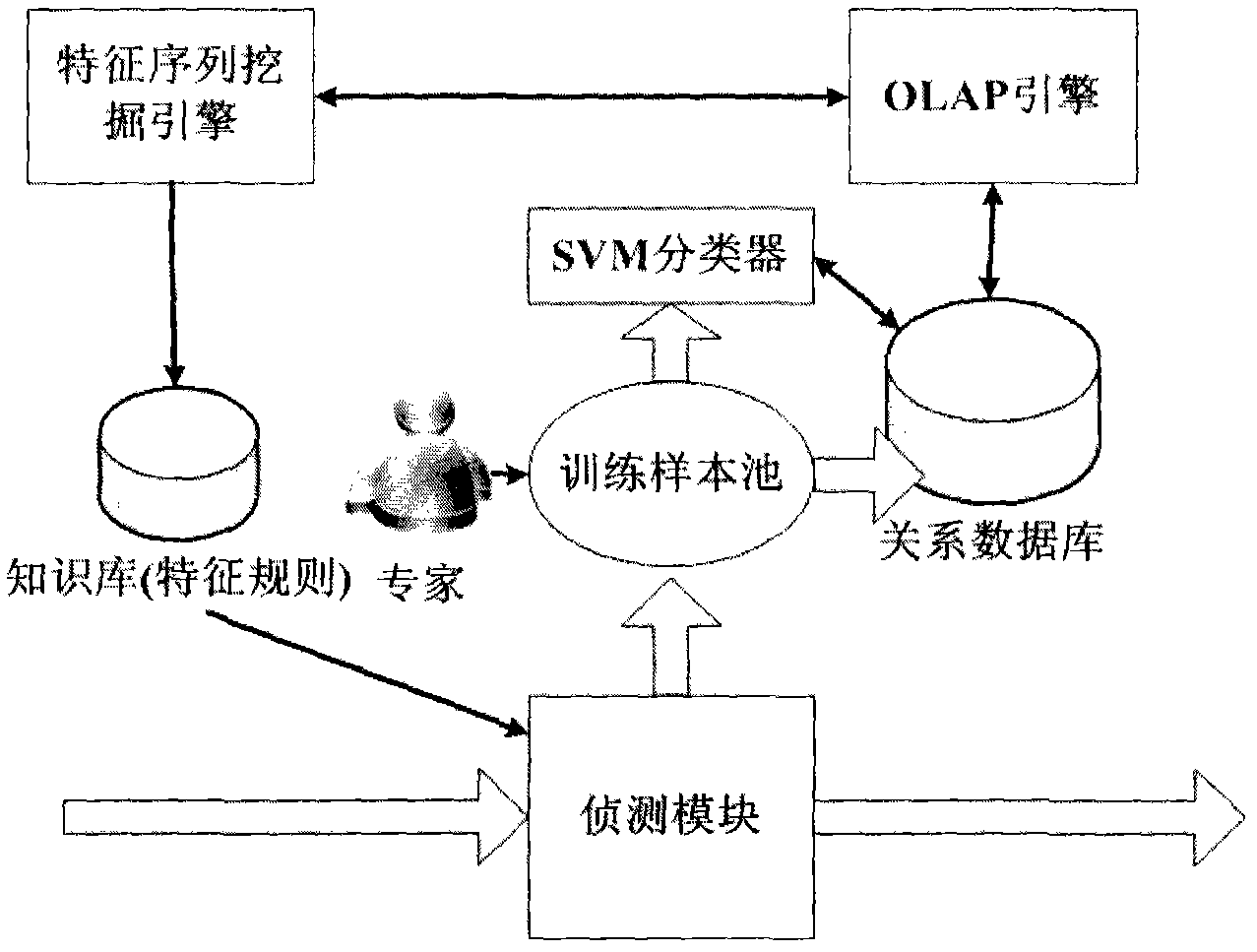
[0019] The features and technical effects of the technical solution of the present invention will be described in detail below with reference to the accompanying drawings and in conjunction with schematic embodiments. , A mining-based malicious code detection method; this method utilizes an OLAP engine, and by building a Cube, it can improve the processing speed of massive behavioral feature data, and provide a friendly data query and access interface; at the same time, this method can track the host of malicious code in real time. Behavior changes ensure that the knowledge base is updated automatically in a timely manner to obtain information on malicious code variants.
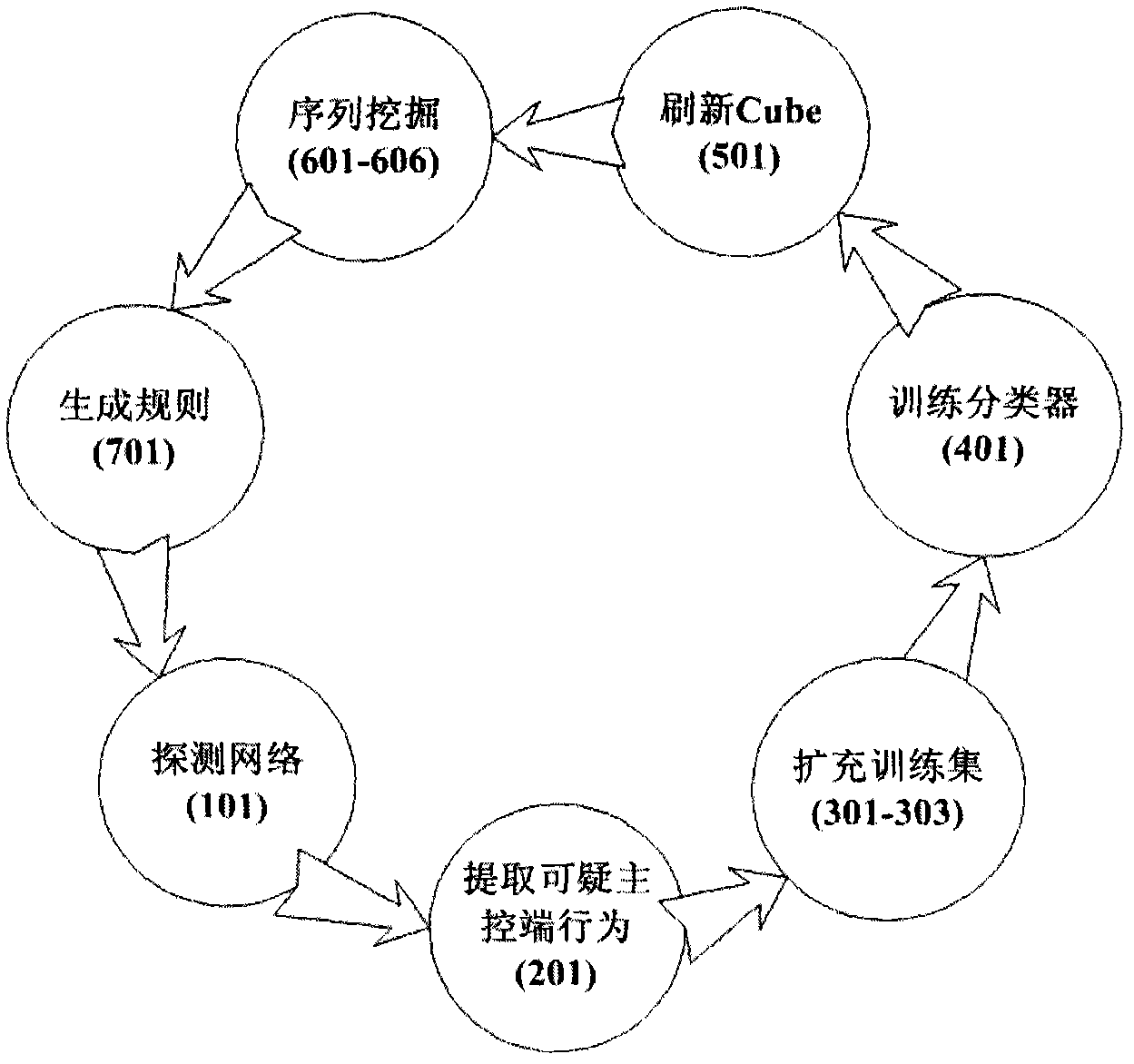
[0020] The detection and analysis process of the entire malicious code interaction behavior characteristics is as follows: figure 1 , first detect the network step 101; then extract the suspicious main control terminal behavior 201; next expand the training set 301-303; train the classifier 401; refresh the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com