Modeling technology-based software security test method
A security testing and security technology, applied in the field of software security testing based on defect modeling technology, to achieve the effects of ensuring test effectiveness, shortening software security testing cycle, and high social and economic benefits
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
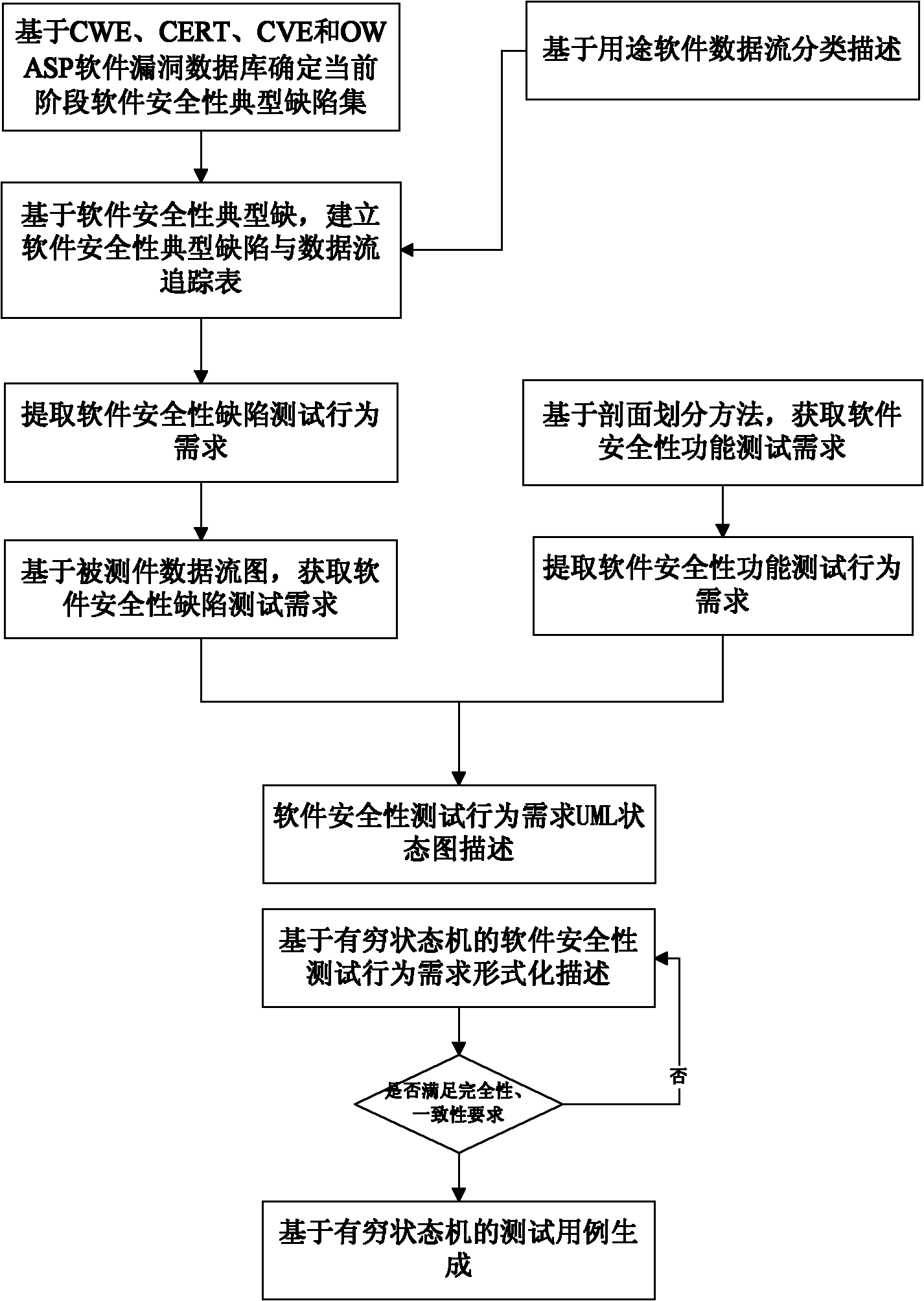
[0084] The present invention will be further described below in conjunction with the accompanying drawings. A software security testing method based on modeling technology, the security test case acquisition method comprises the steps of:
[0085] (a) Based on the CWE, CERT, CVE and OWASP software vulnerability databases, determine the typical defect sets of software security at the current stage;
[0086] (b) Classification and description of software data flow;
[0087] (c) Establish a pre-correspondence table between the typical defects of software security obtained through step (a) and the classification description of software data stream obtained through step (b);
[0088] (d) Based on the data flow diagram of the tested part, according to the pre-correspondence table between typical software security defects and data flow obtained in step (c), initially obtain the testing requirements for software security defects;
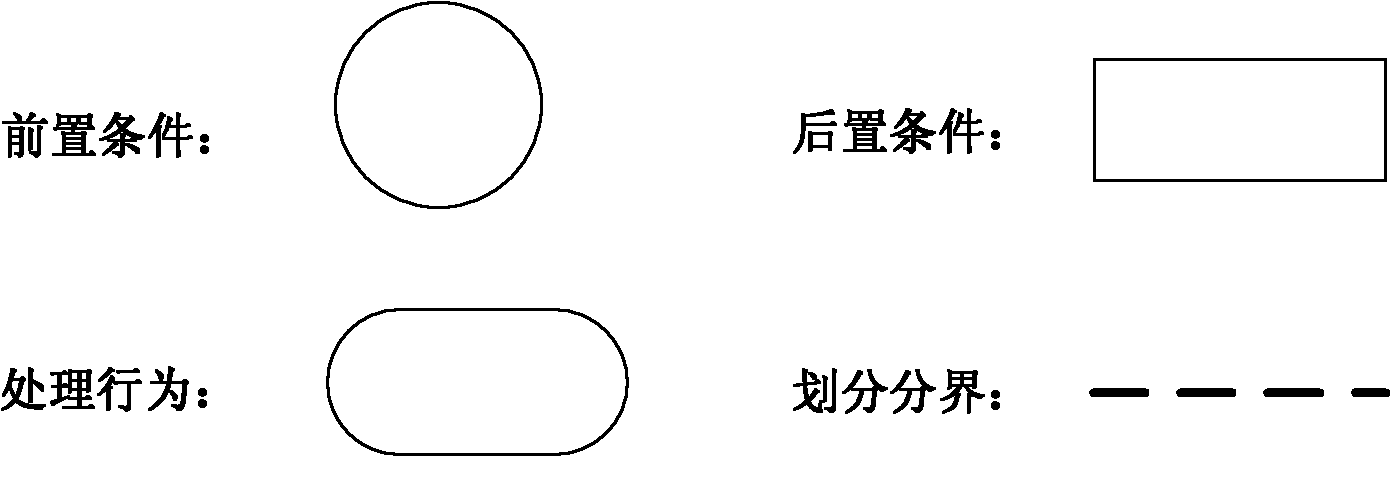
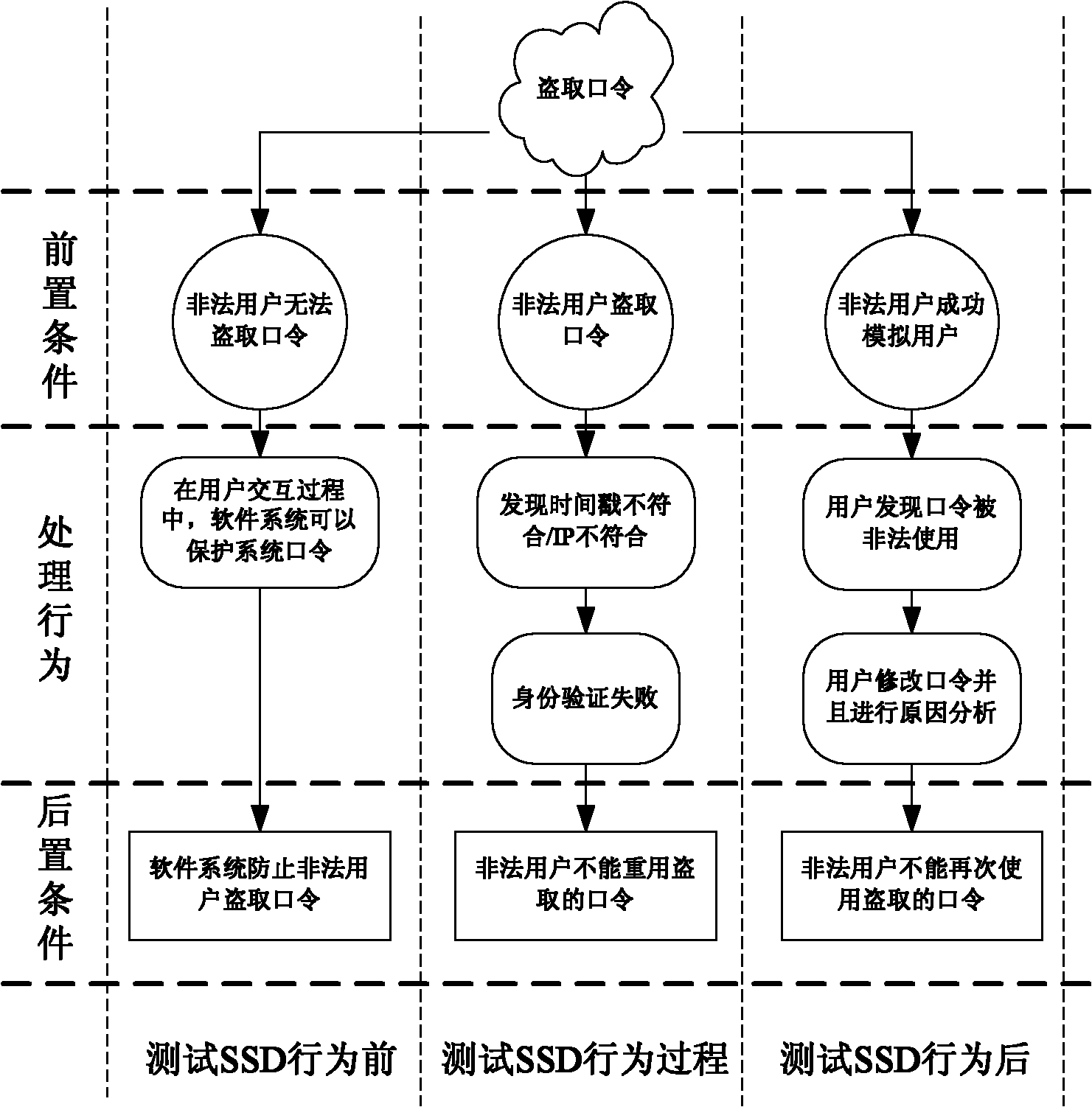
[0089] (e) Realize the behavioral description of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com