DNS (Domain Name System) tunnel Trojan detection method based on communication behavior analysis
A technology of DNS tunneling and behavior analysis, which is applied in the direction of instruments, character and pattern recognition, digital transmission systems, etc., and can solve the problems that the DNS tunnel detection method cannot be fully applied to detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
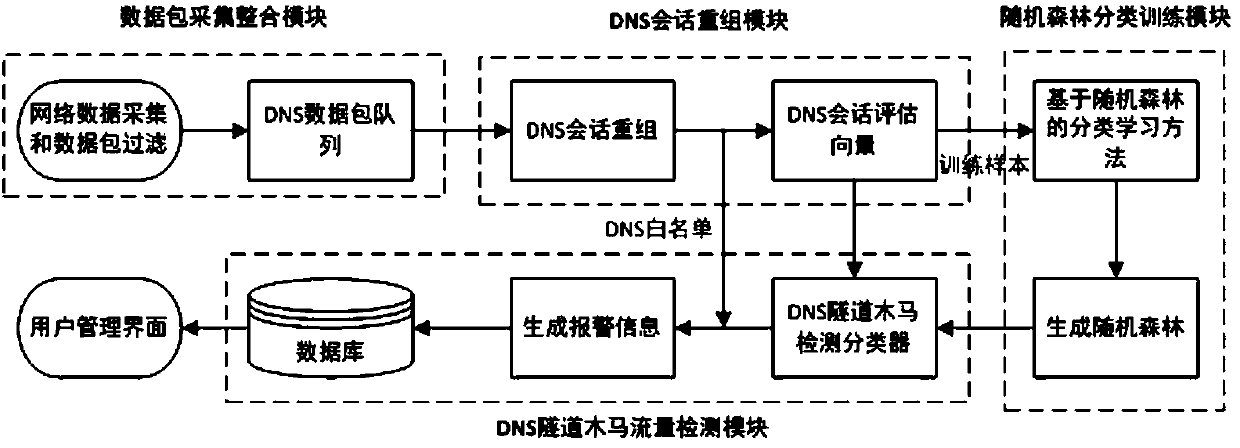
[0053] The framework design of DNS tunnel Trojan horse detection system see figure 1 . The DNS tunnel Trojan horse detection system has four parts: data packet collection integration collection module, DNS session reorganization module, random forest classification training module and DNS tunnel Trojan horse traffic detection module, plus user management interface interface.
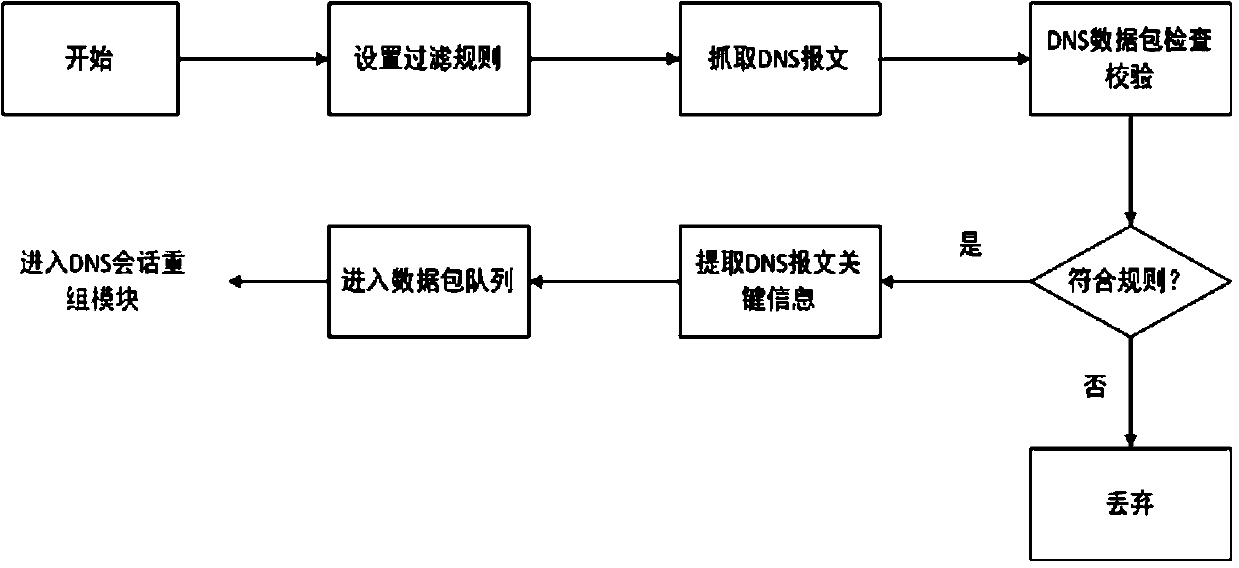
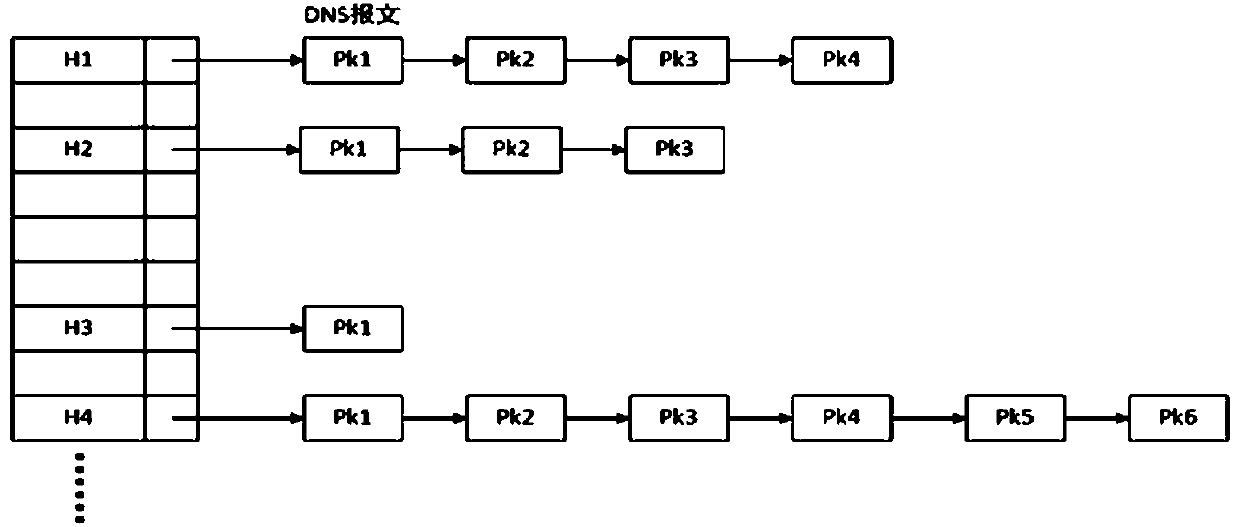
[0054] The data packet collection integration module mainly uses the underlying filtering mechanism of Winpcap capture technology to capture DNS traffic. The DNS session reorganization module clusters the captured DNS traffic according to quintuples to form a DNS session, and extracts the DNS session data flow into a DNS session evaluation vector representation, which is used as a random forest classification training module and DNS tunnel Trojan traffic detection input to the module. This detection model also considers the IP direct-connected DNS tunneling Trojan horse. If an untrusted external network ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com