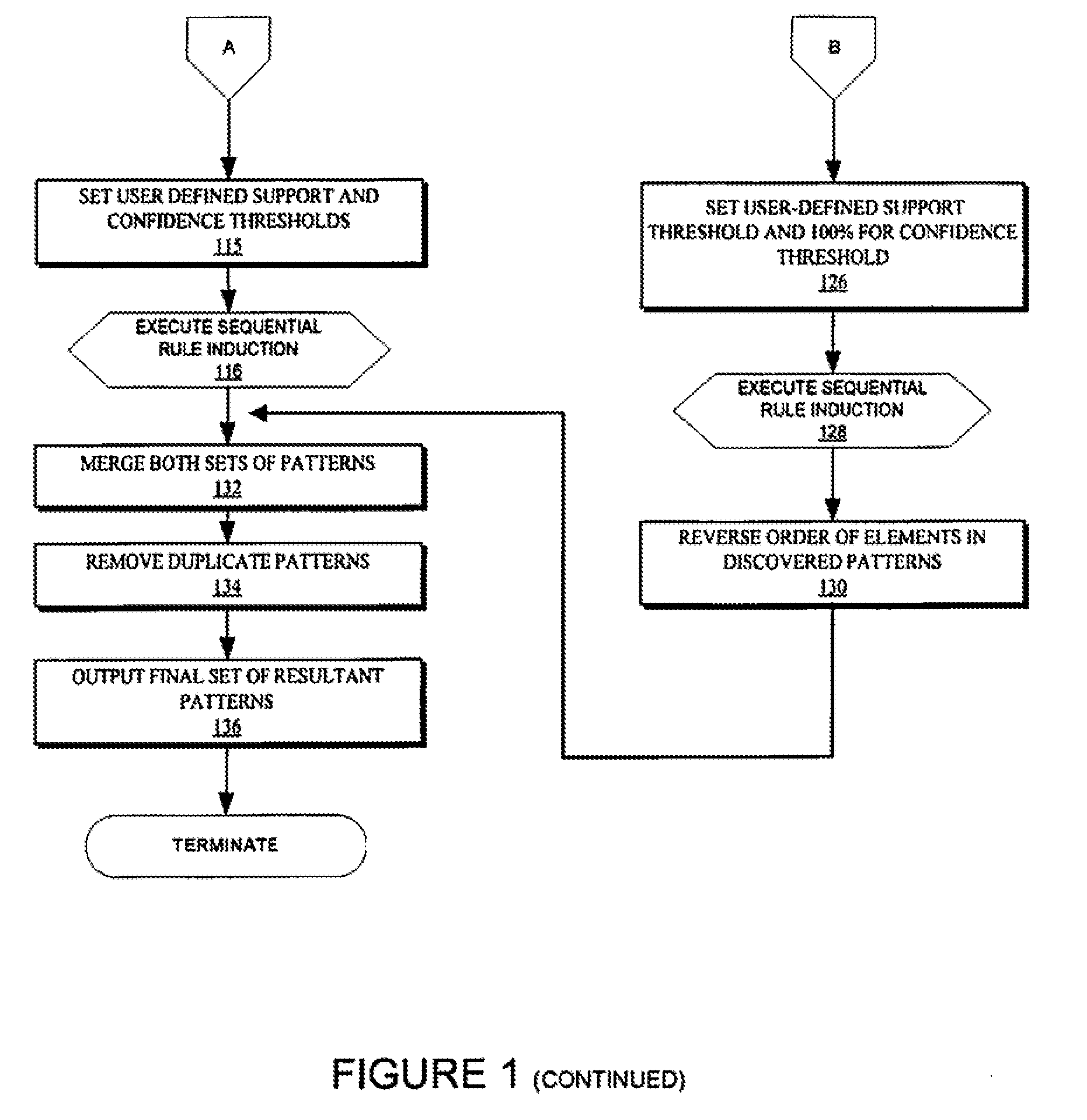
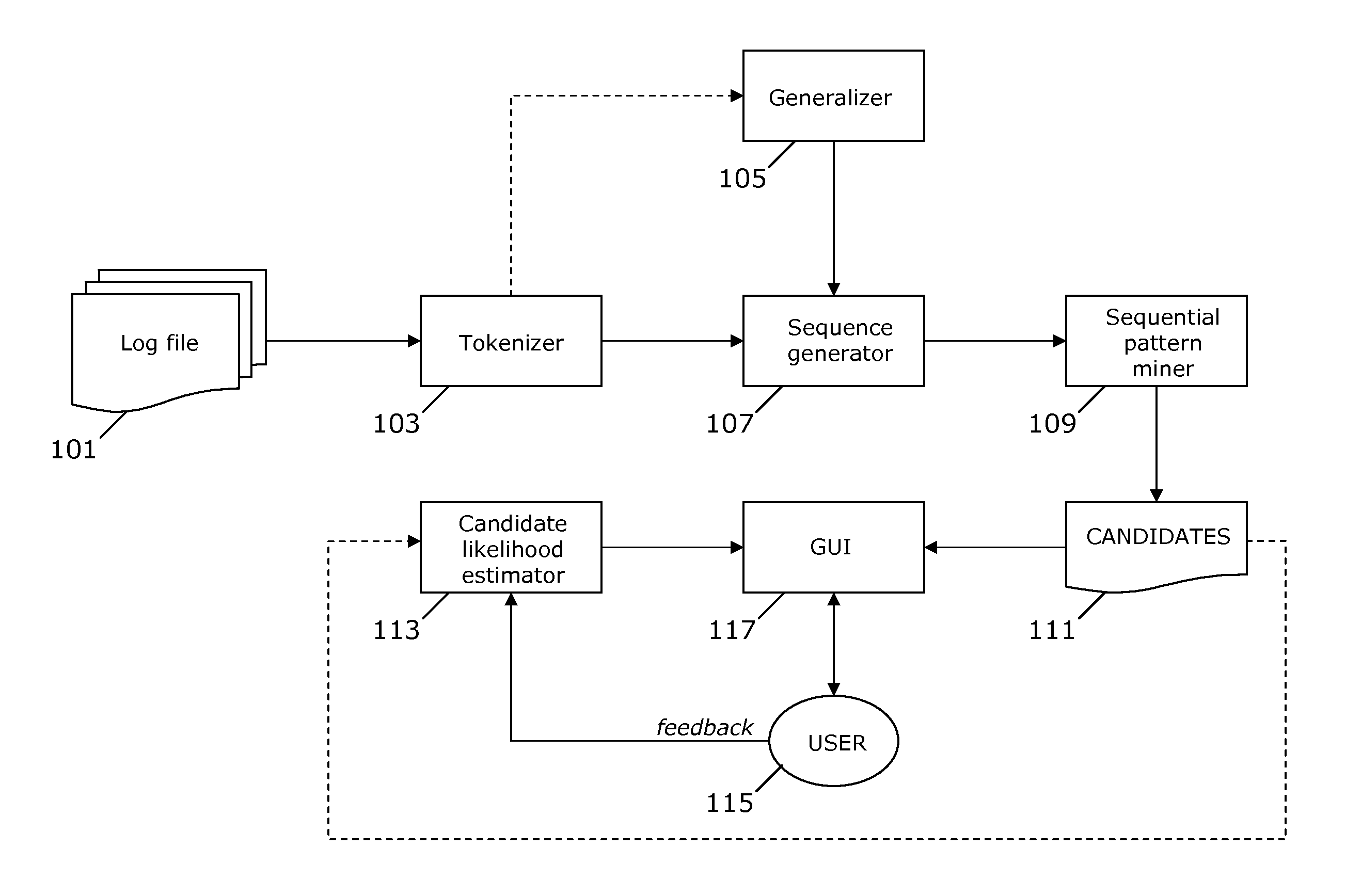
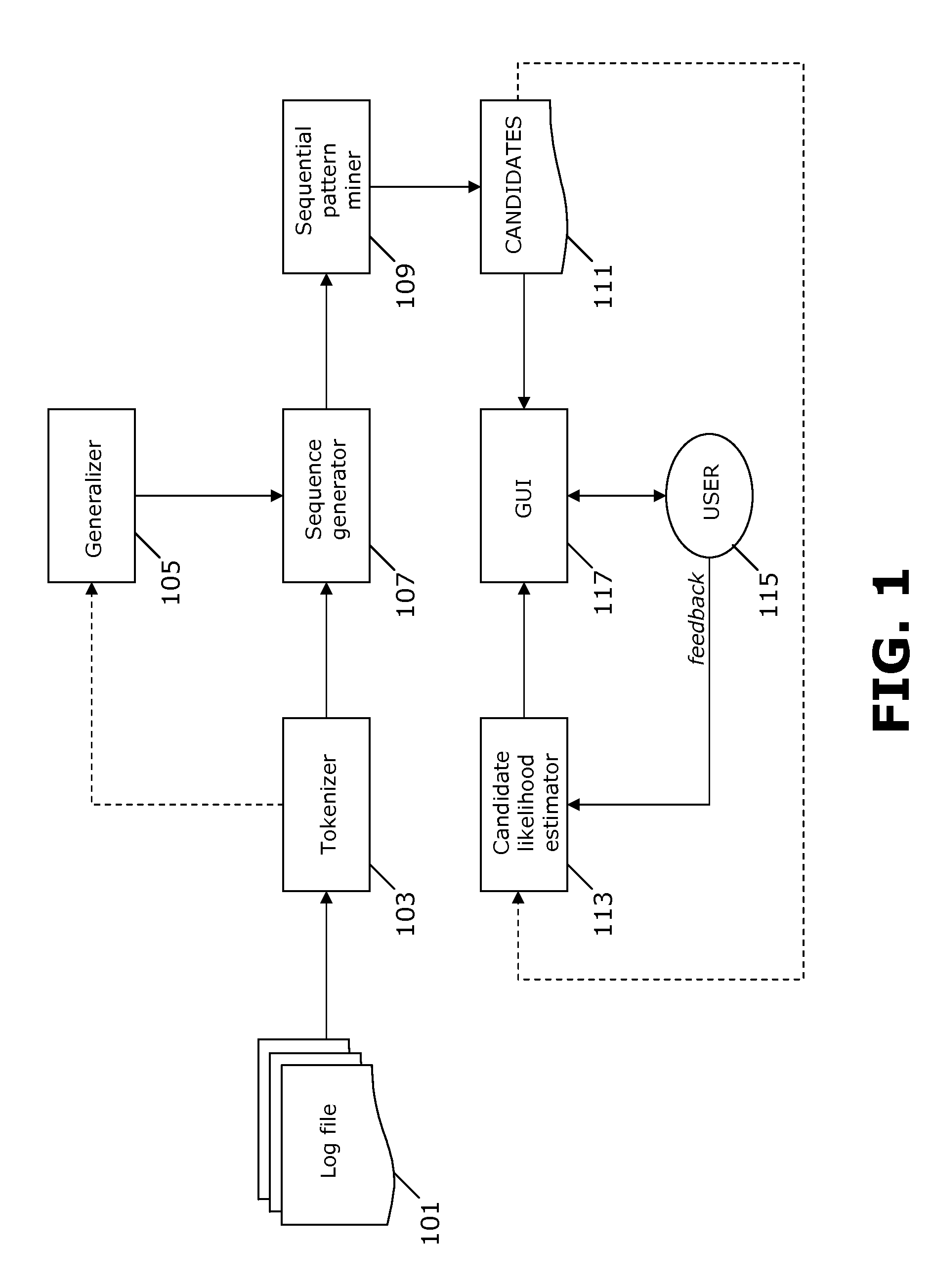
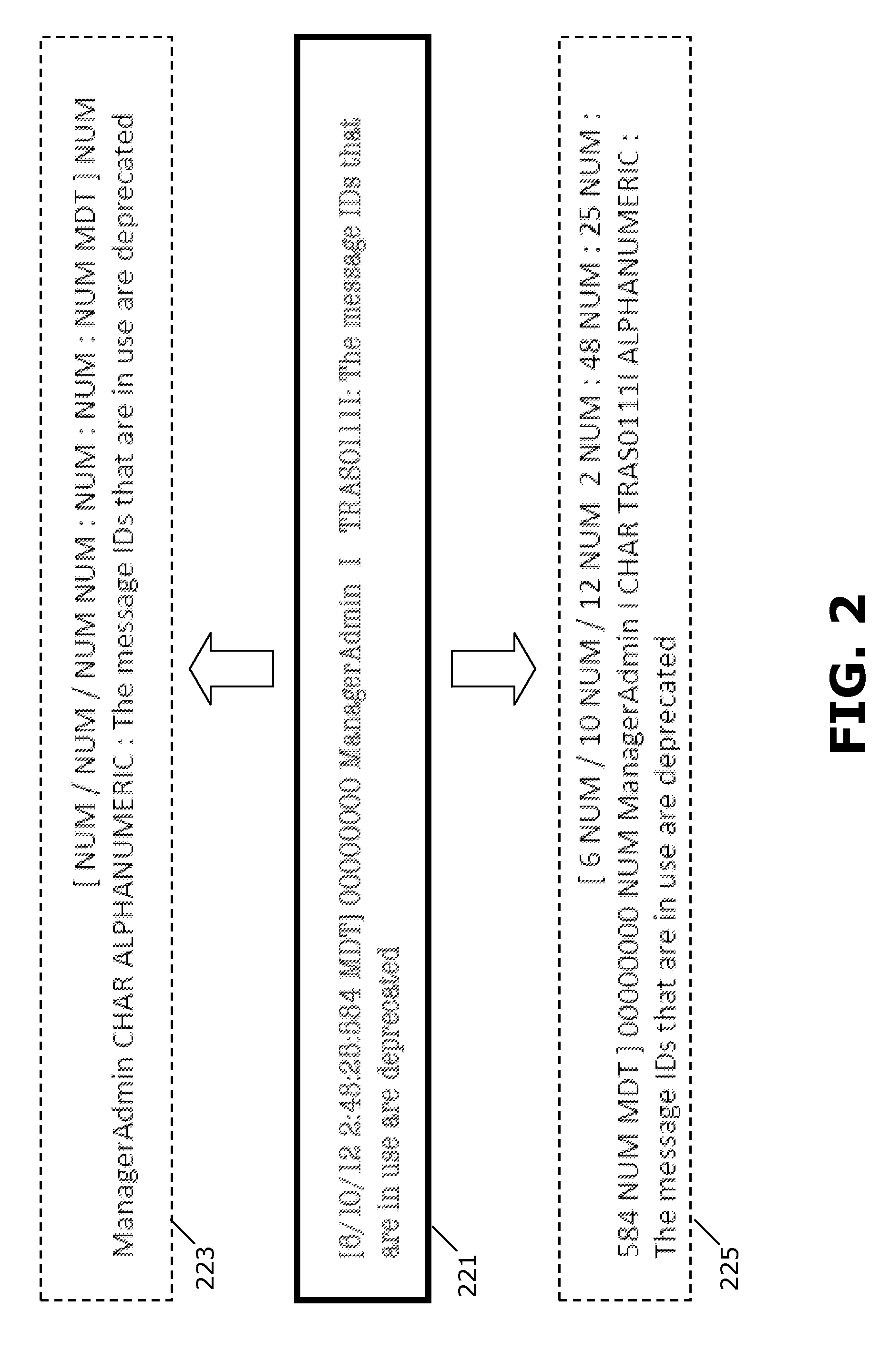
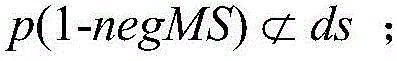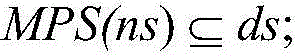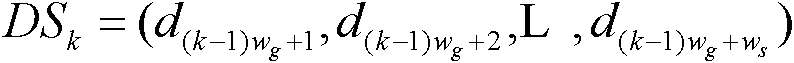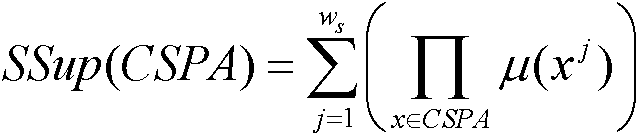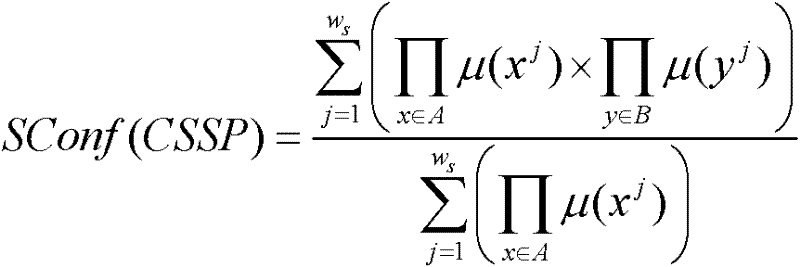Patents
Literature
58 results about "Sequential Pattern Mining" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Sequential pattern mining is a topic of data mining concerned with finding statistically relevant patterns between data examples where the values are delivered in a sequence. It is usually presumed that the values are discrete, and thus time series mining is closely related, but usually considered a different activity. Sequential pattern mining is a special case of structured data mining.
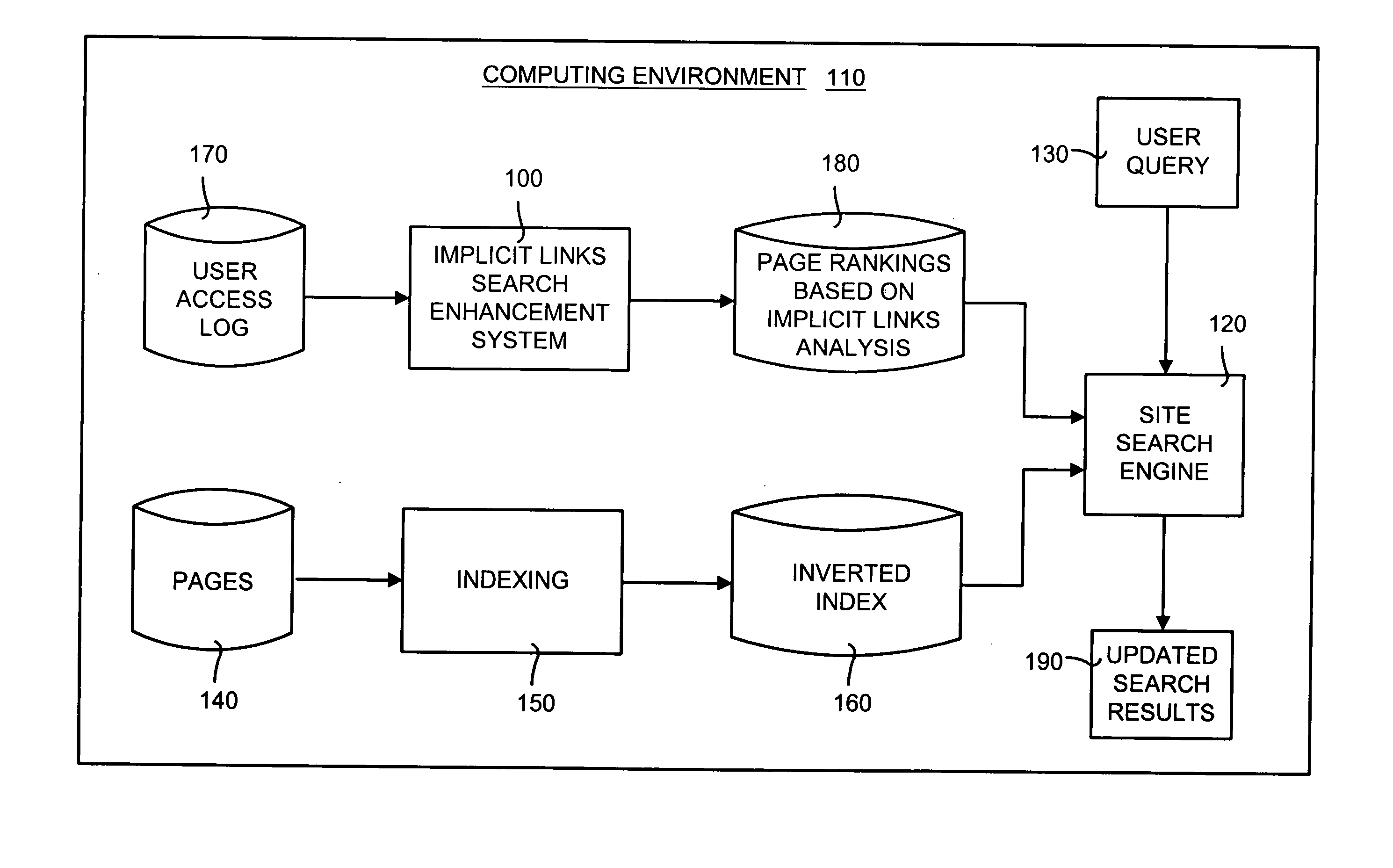
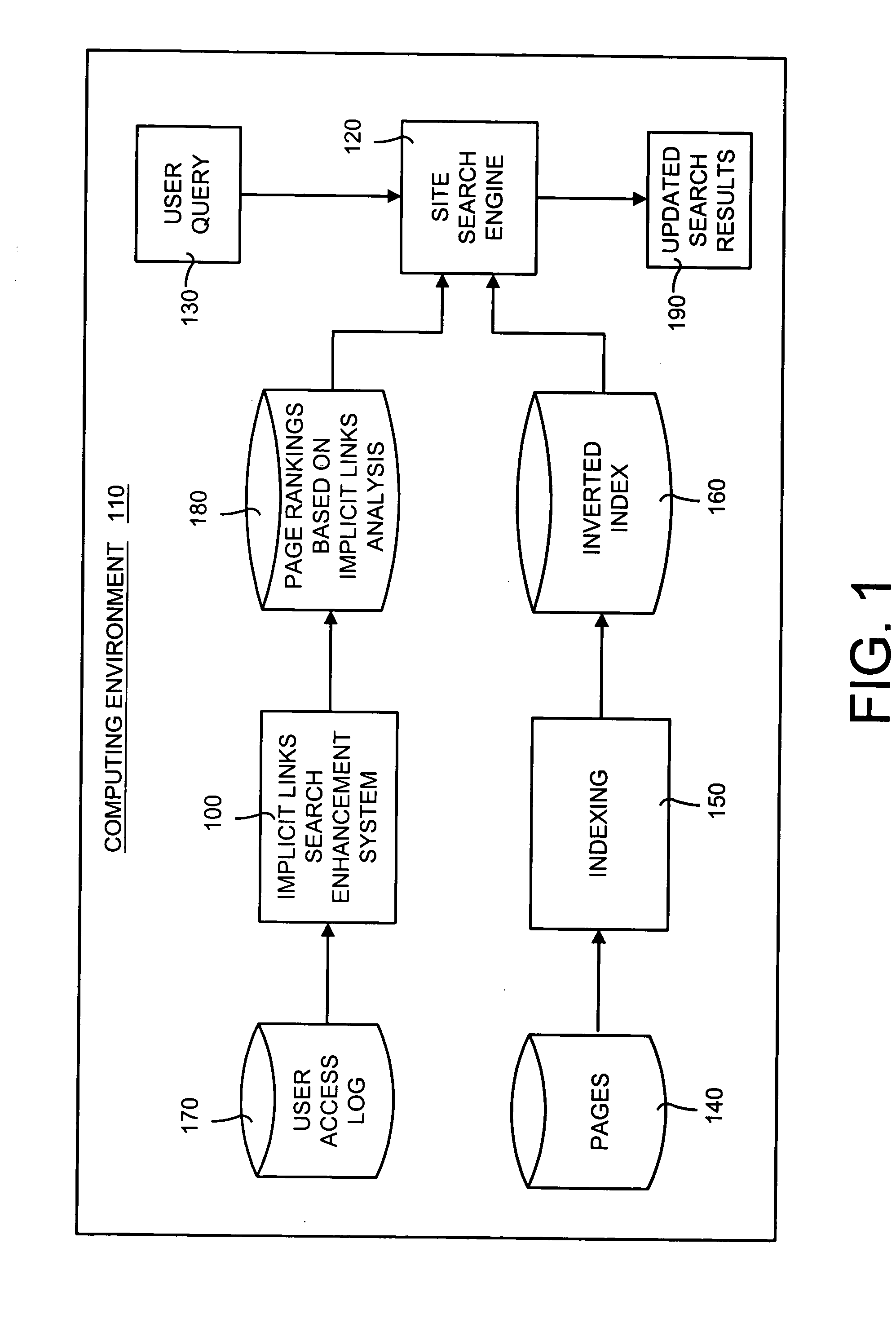
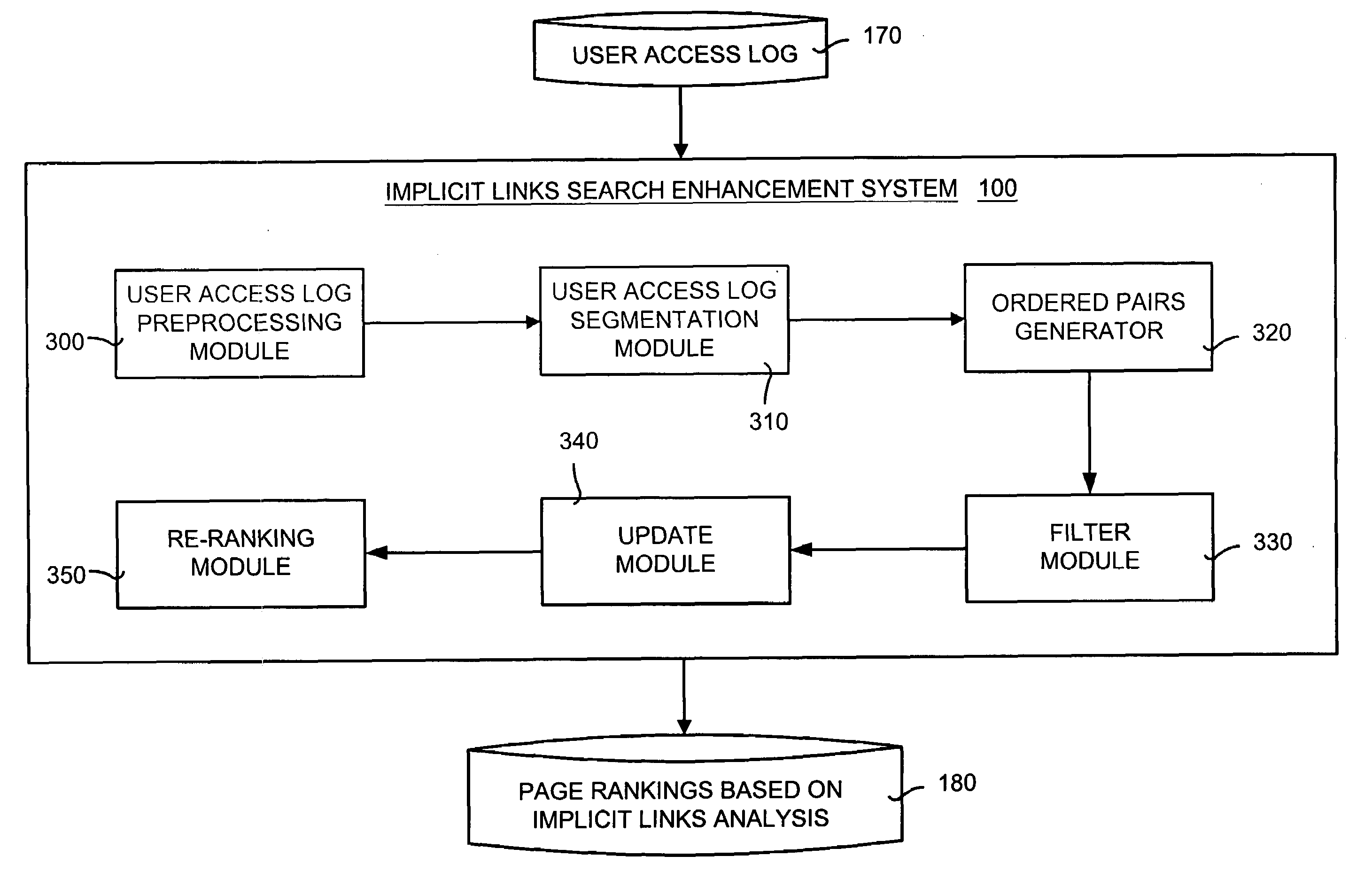
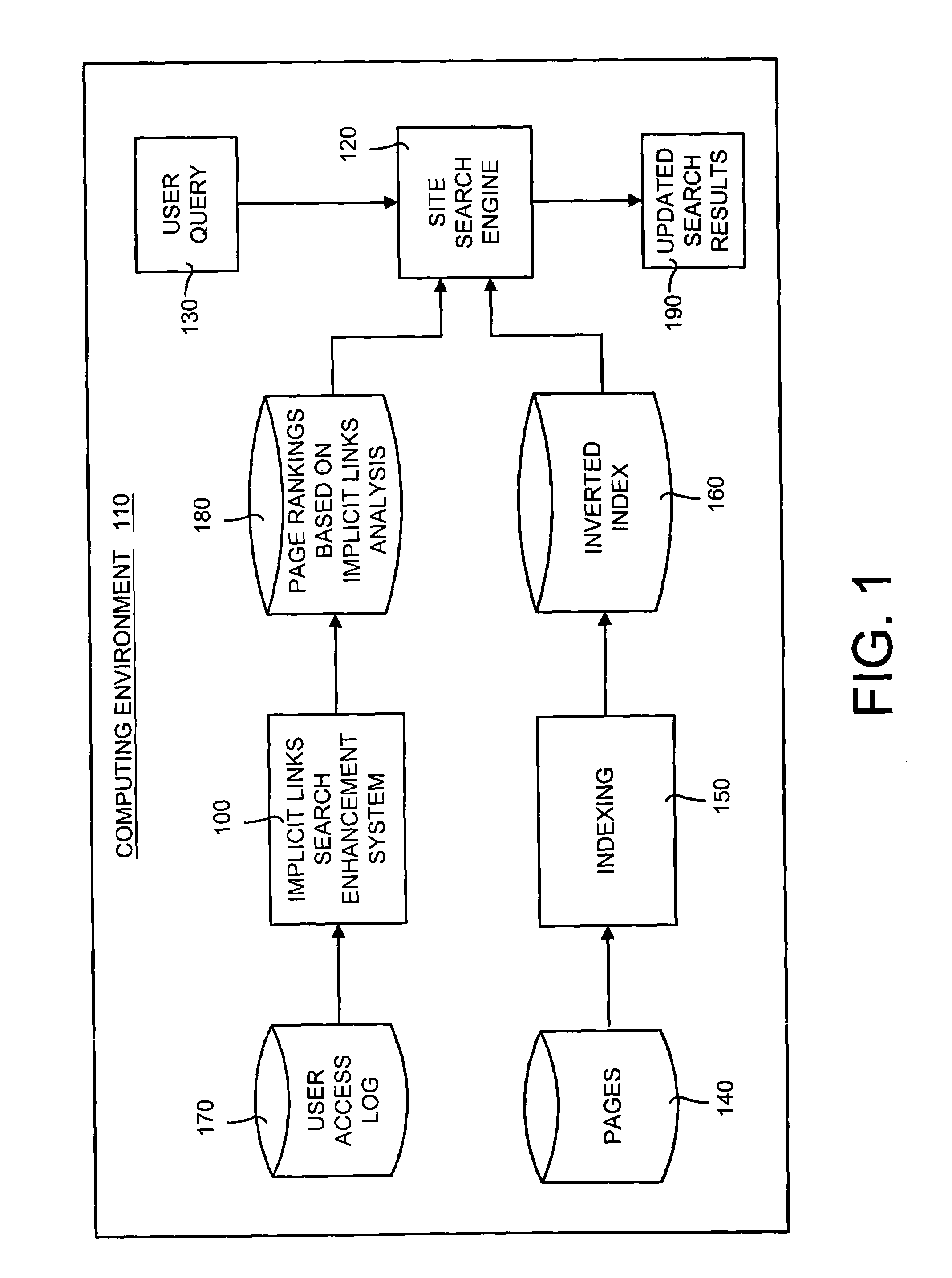
Implicit links search enhancement system and method for search engines using implicit links generated by mining user access patterns
InactiveUS20050071465A1Handy search resultsSearch results are accurateData processing applicationsDigital data information retrievalWeb sitePattern generation
An implicit links enhancement system and method for search engines that generates implicit links obtained from mining user access logs to facilitate enhanced local searching of web sites and intranets. The implicit links search enhancement system and method includes extracting implicit links by mining users' access patterns and then using a modified link analysis algorithm to re-rank search results obtained from traditional search engines. More specifically, the implicit links search enhancement method includes extracting implicit links from a user access log, generating an implicit links graph from the extracted implicit links, and computing page rankings using the implicit links graph. The implicit links are extracted from the log using a two-item sequential pattern mining technique. Search results obtained from a search engine are re-ranked based on an implicit links analysis performed using an updated implicit links graph, a modified re-ranking formula, and at least one re-ranking technique.
Owner:MICROSOFT TECH LICENSING LLC
Knowledge discovery from data sets
InactiveUS20030130991A1Digital data processing detailsRelational databasesData setMultidimensional data
A system is disclosed that allows a multi-dimensional data set to be mined as a single dimension data set so that useful information can be derived from that data set in an efficient manner. In one embodiment, the present invention allows for association rules and / or sequential patterns to be generated from M-dimensional data using a 1-dimensional mining process. In one implementation, one or more conditional items are appended to a data item in order to transform the multi-dimensional data to one-dimensional data.
Owner:REIJERSE FIDEL +1
Implicit links search enhancement system and method for search engines using implicit links generated by mining user access patterns
InactiveUS7584181B2Handy search resultsSearch results are accurateData processing applicationsDigital data information retrievalWeb search engineWeb site
An implicit links enhancement system and method for search engines that generates implicit links obtained from mining user access logs to facilitate enhanced local searching of web sites and intranets. The implicit links search enhancement system and method includes extracting implicit links by mining users' access patterns and then using a modified link analysis algorithm to re-rank search results obtained from traditional search engines. More specifically, the implicit links search enhancement method includes extracting implicit links from a user access log, generating an implicit links graph from the extracted implicit links, and computing page rankings using the implicit links graph. The implicit links are extracted from the log using a two-item sequential pattern mining technique. Search results obtained from a search engine are re-ranked based on an implicit links analysis performed using an updated implicit links graph, a modified re-ranking formula, and at least one re-ranking technique.
Owner:MICROSOFT TECH LICENSING LLC
Safe log analyzing method and system
InactiveCN101399658AEfficient discoveryRealize detectionSecuring communicationInformation processingSerial pattern
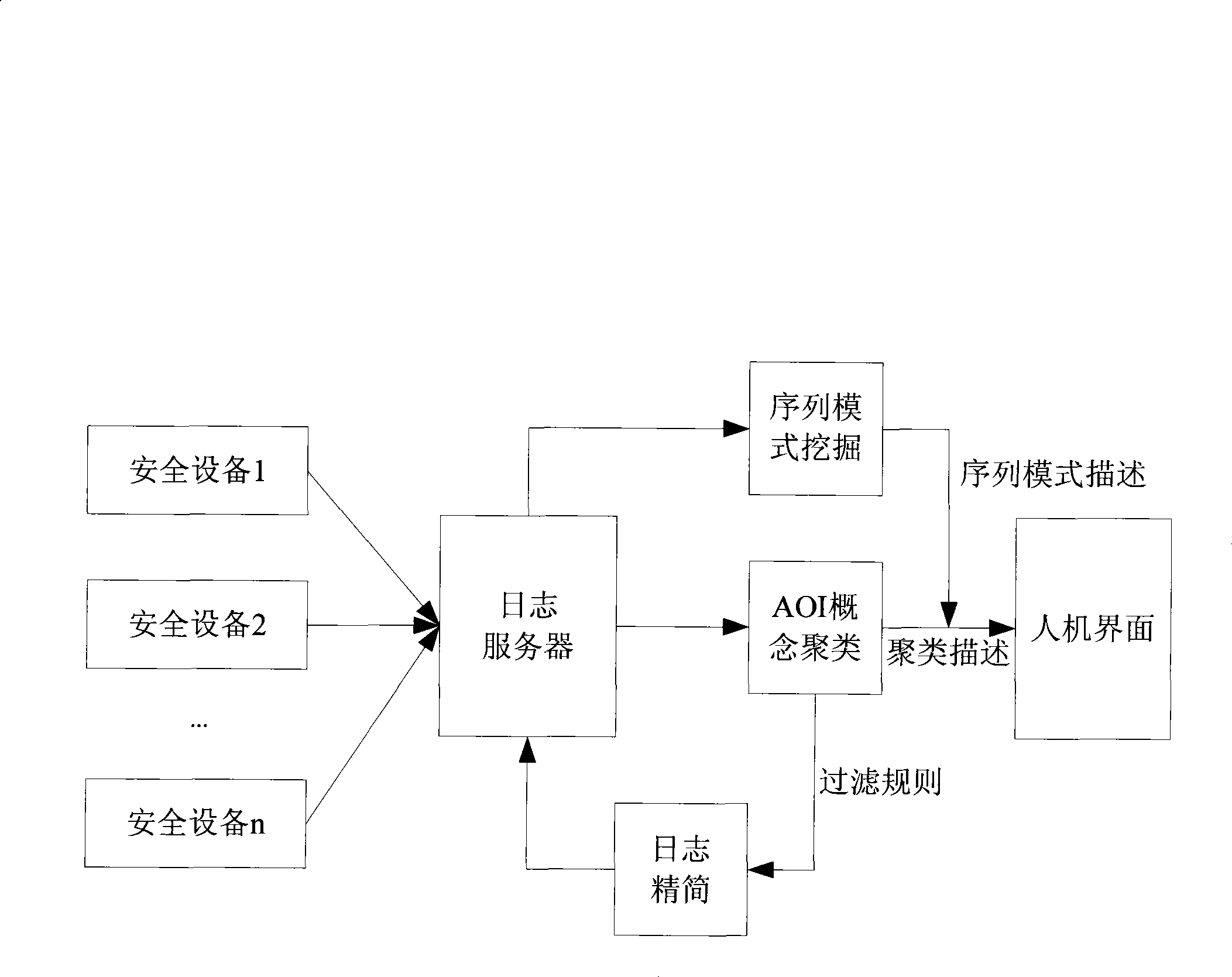
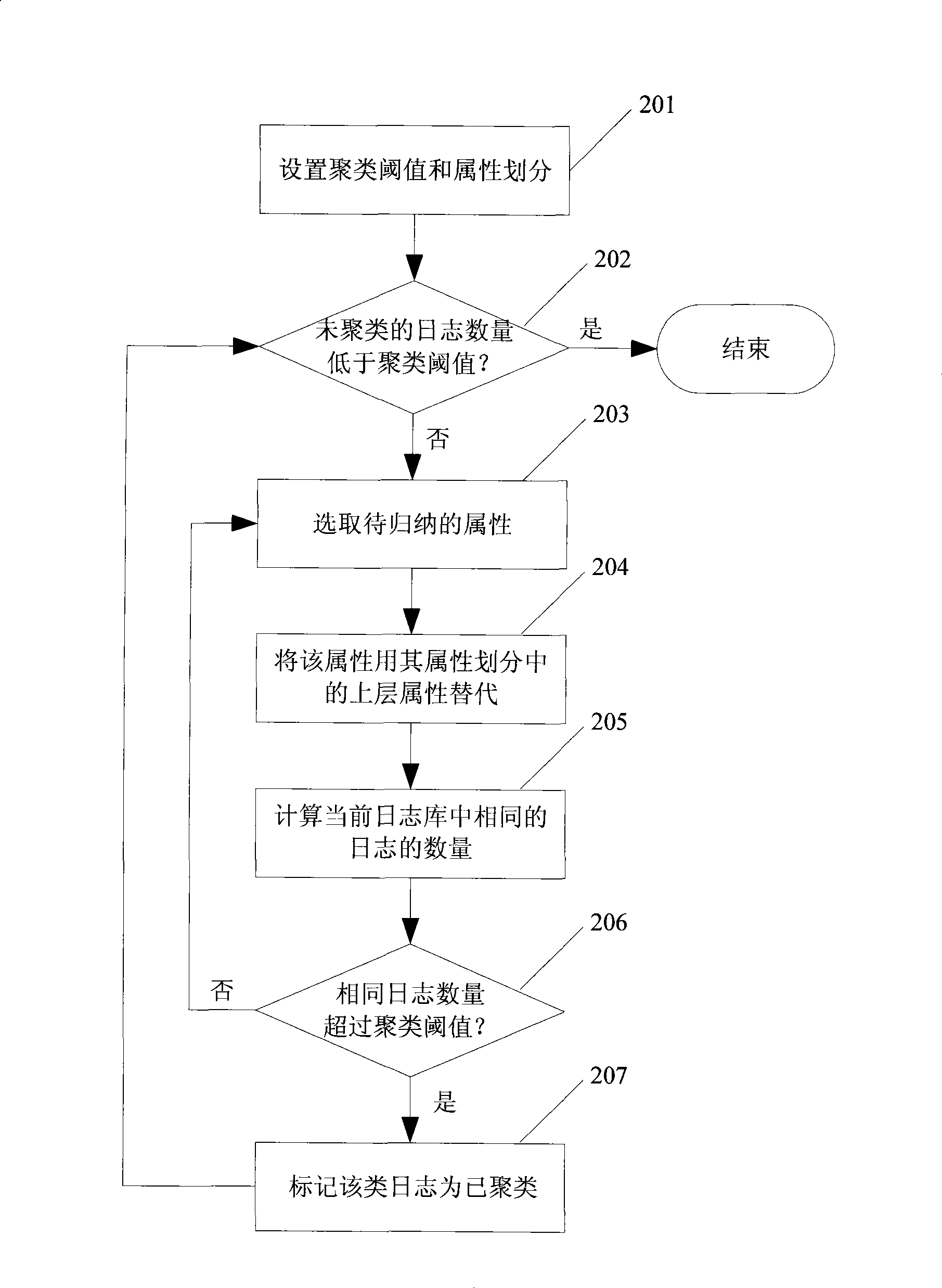
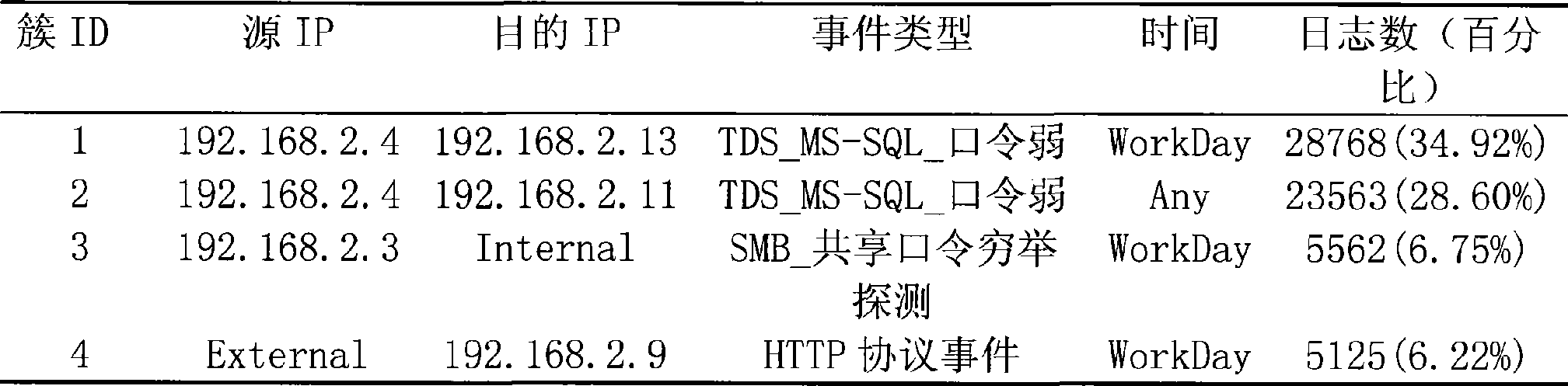
The invention discloses a method for analyzing a security log and a system thereof, which realizes filtration of invalid logs and misreported logs in mass logs, and discovers large-scale network security events and common attack sequences. The method comprises the following steps: the mass logs are subject to cluster analysis by the attribute-oriented inductive algorithm so as to generate class description of each class of log after clustering; an administrator sets filtration regulations according to the clustered class description, unrelated and misreported logs are removed from the current log base so as to simplify the mass logs; Internet Worms, distributed denial of service attacks and other large-scale network security events characteristics are extracted; the simplified log is subject to sequential pattern mining to find attack behavior sequence description commonly used by attackers to be finally submitted to the administrator. The system comprises a clustering analysis module, a filtration module and a sequential pattern mining module. The method and the system can be applied to information processing of the mass logs of security products.
Owner:BEIJING VENUS INFORMATION TECH
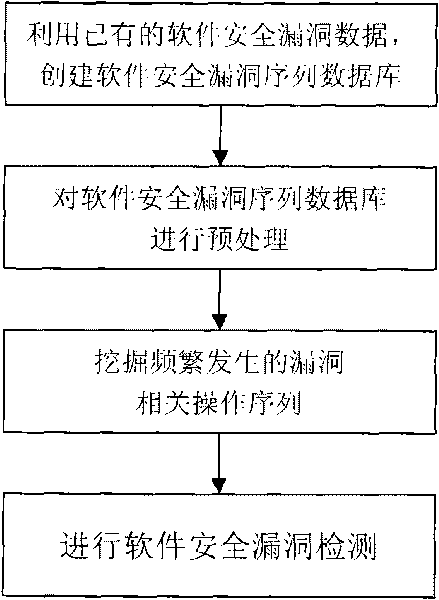
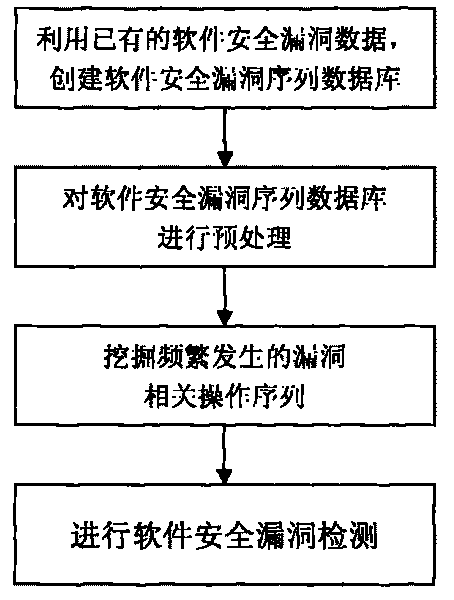
Software security flaw detection method based on sequential pattern mining
InactiveCN101710378AImprove detection efficiencyReduce the false negative rate of vulnerability detectionPlatform integrity maintainanceSpecial data processing applicationsSequence databaseSoftware system
The invention provides a software security flaw detection method based on sequential pattern mining. Firstly, a great quantity of relevant operation sequence data of a detected software security flaw is used for building a relevant operation sequence database of the security flaw; then, a closed sequential pattern mining arithmetic in the data mining is used to mine frequently appearing relevant operation sequence of the flaw; the mined frequently appearing relevant operation sequence of the flaw is used for detecting the security flaw of the current software system so as to lower flaw detection missing report rate as well as improve security flaw detection efficiency. Along with the accumulation of flaw data, the advantage of high security flaw detection efficiency of the invention is more outstanding.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +2
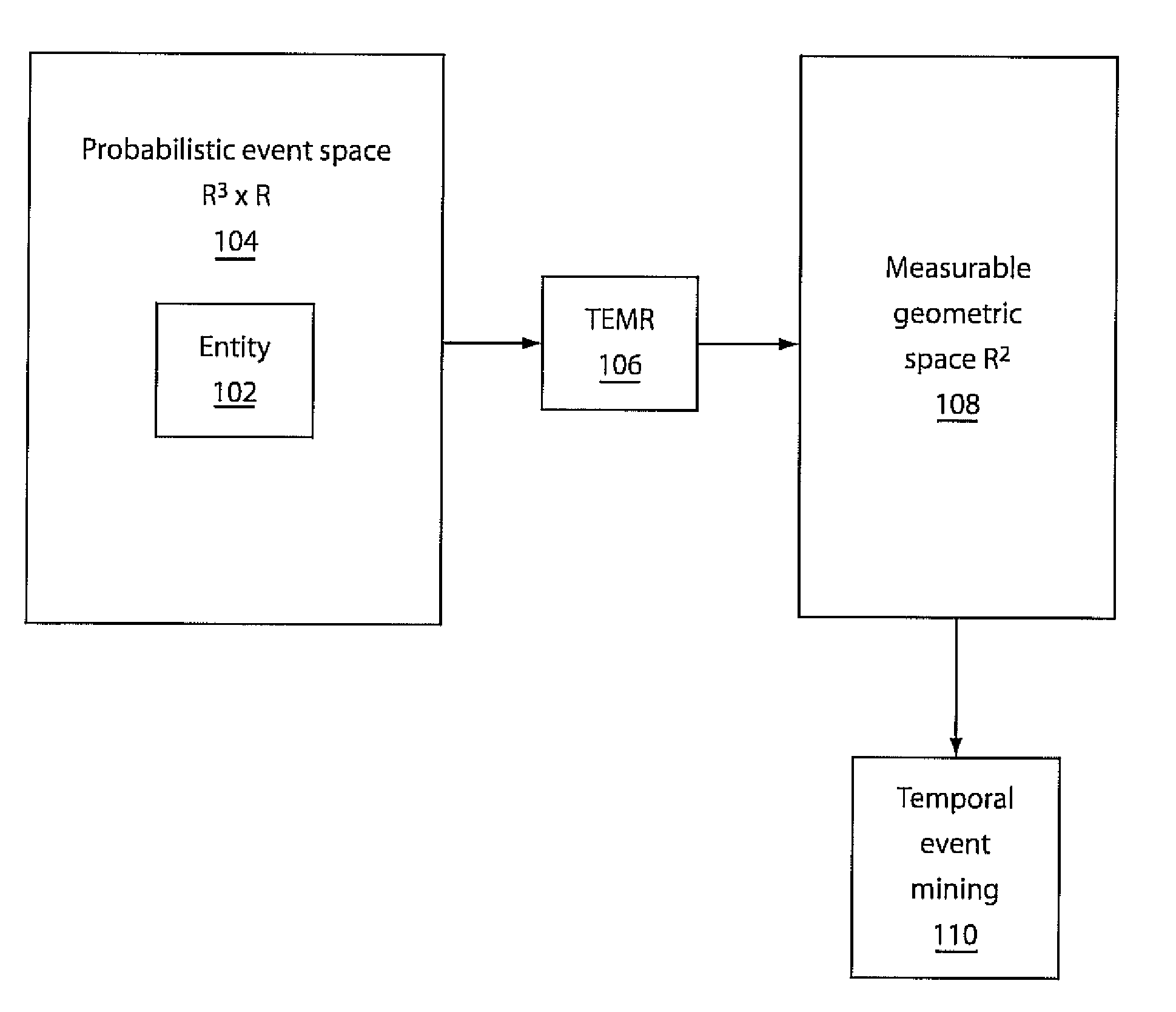
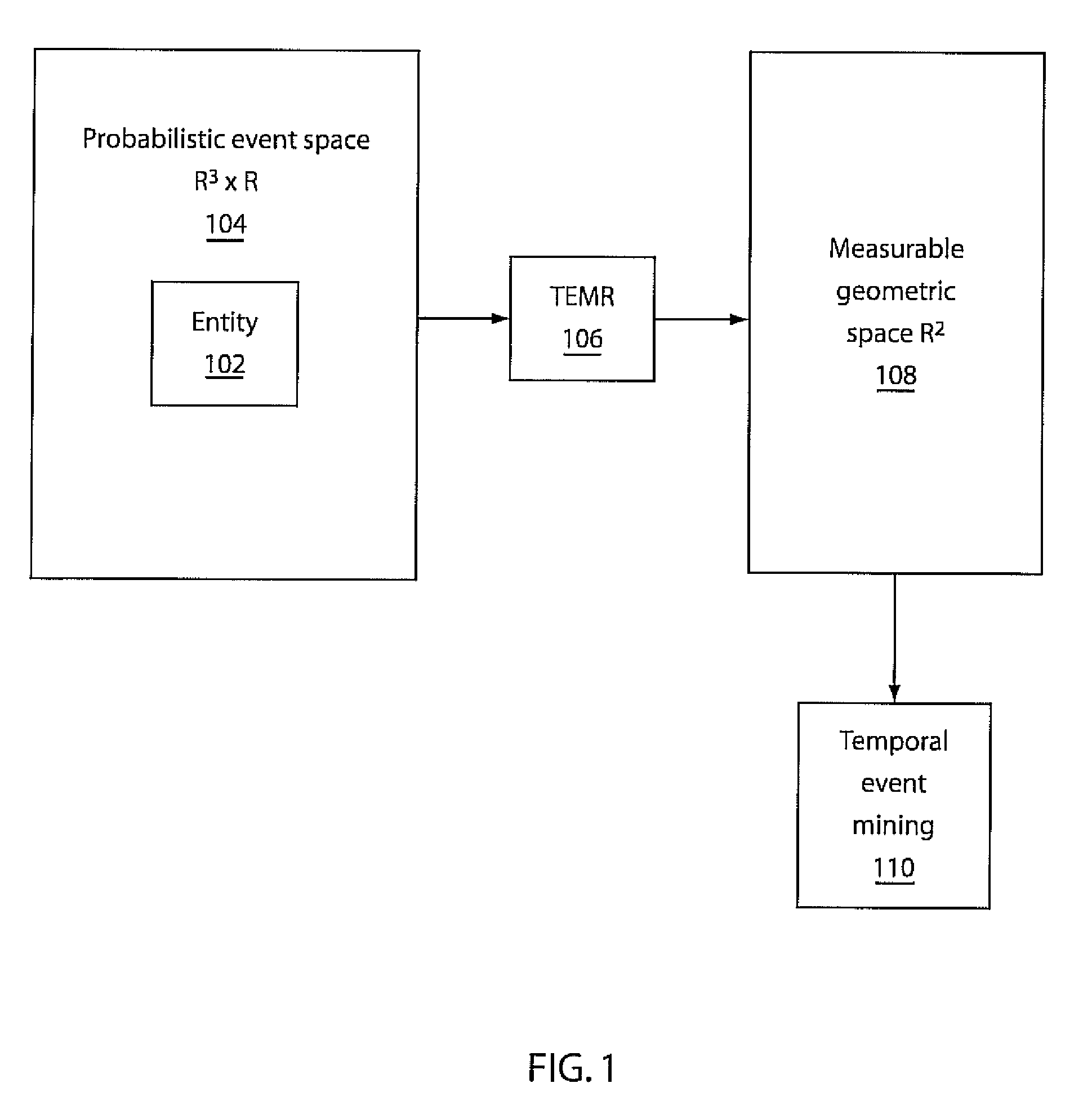
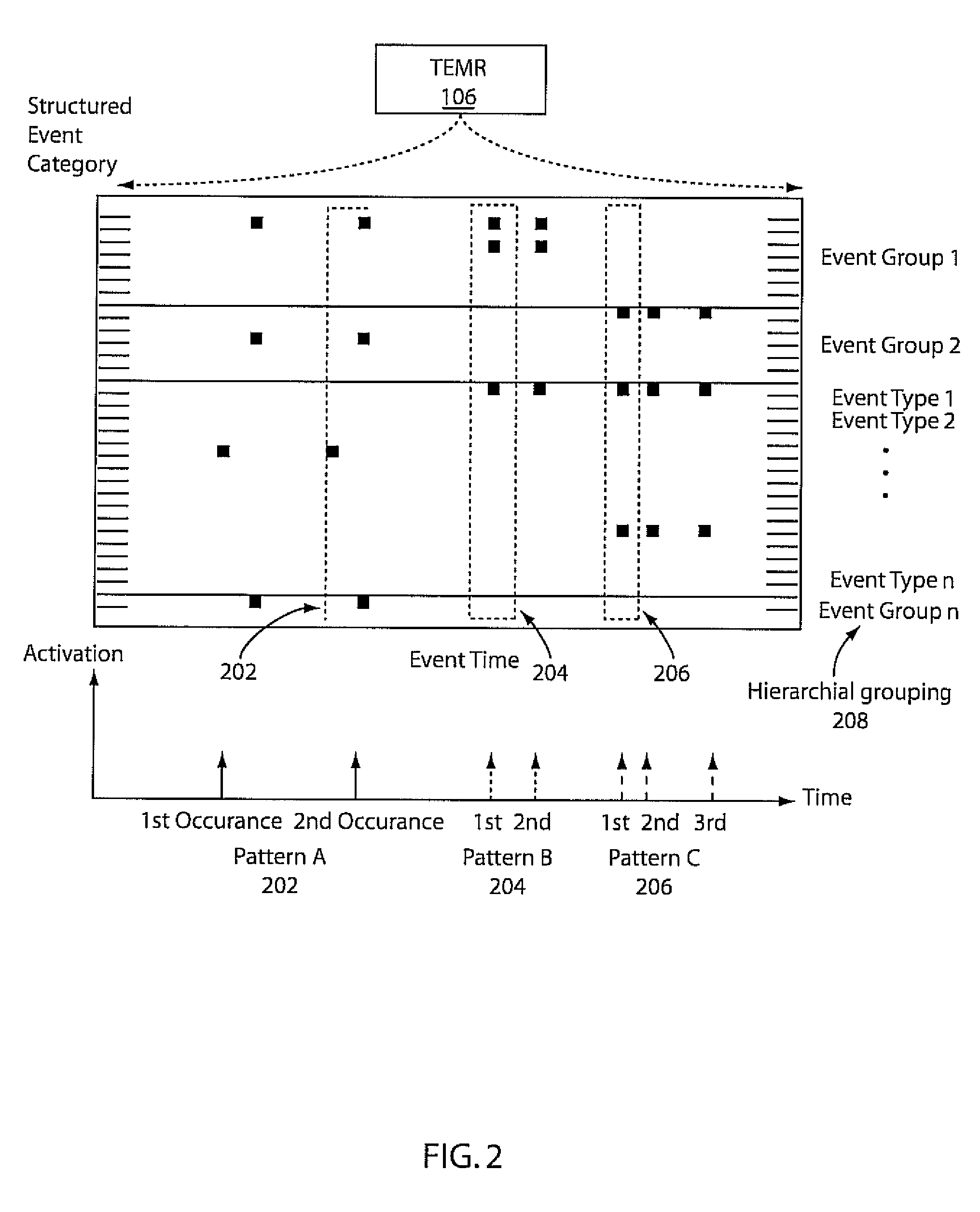
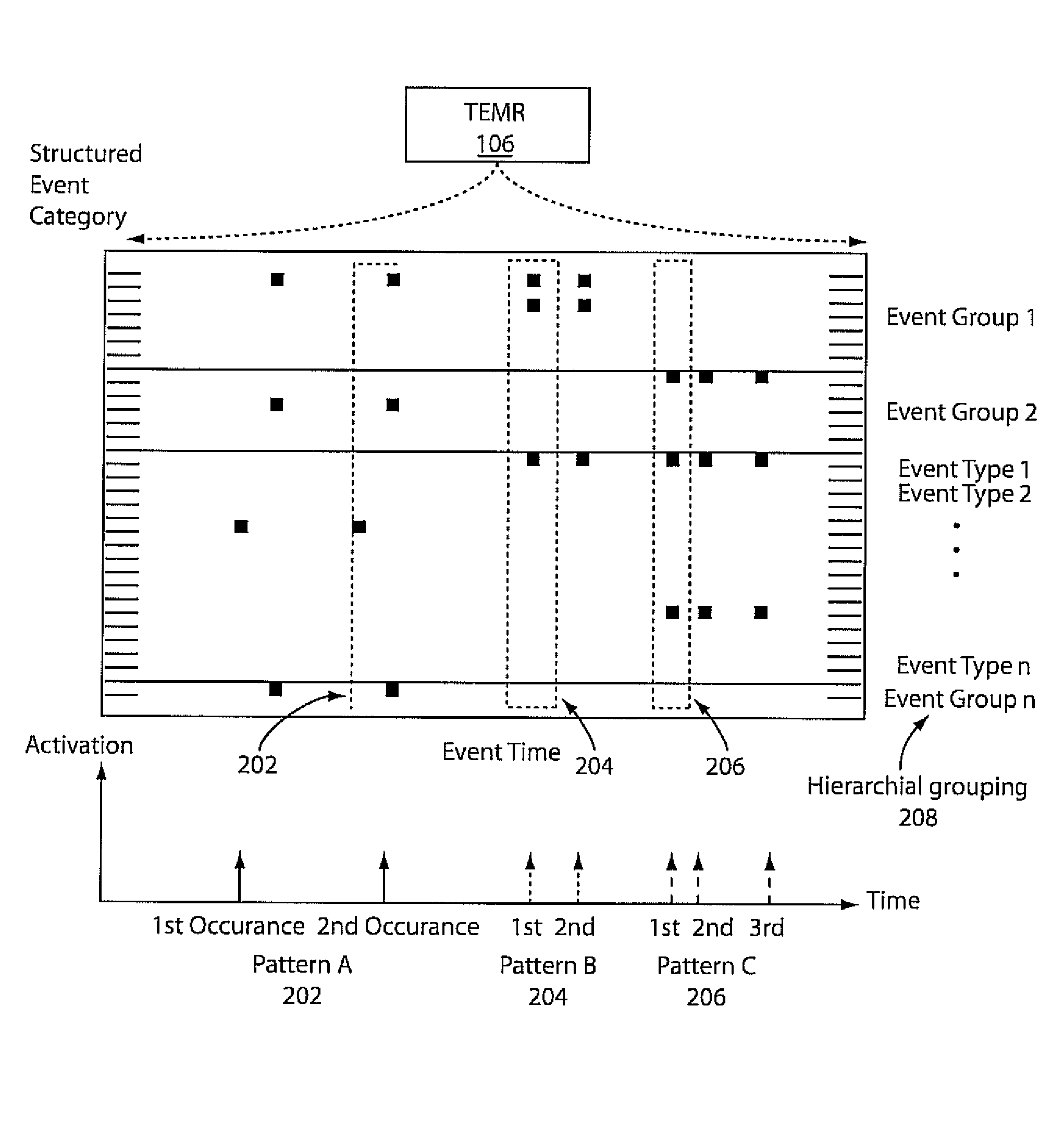
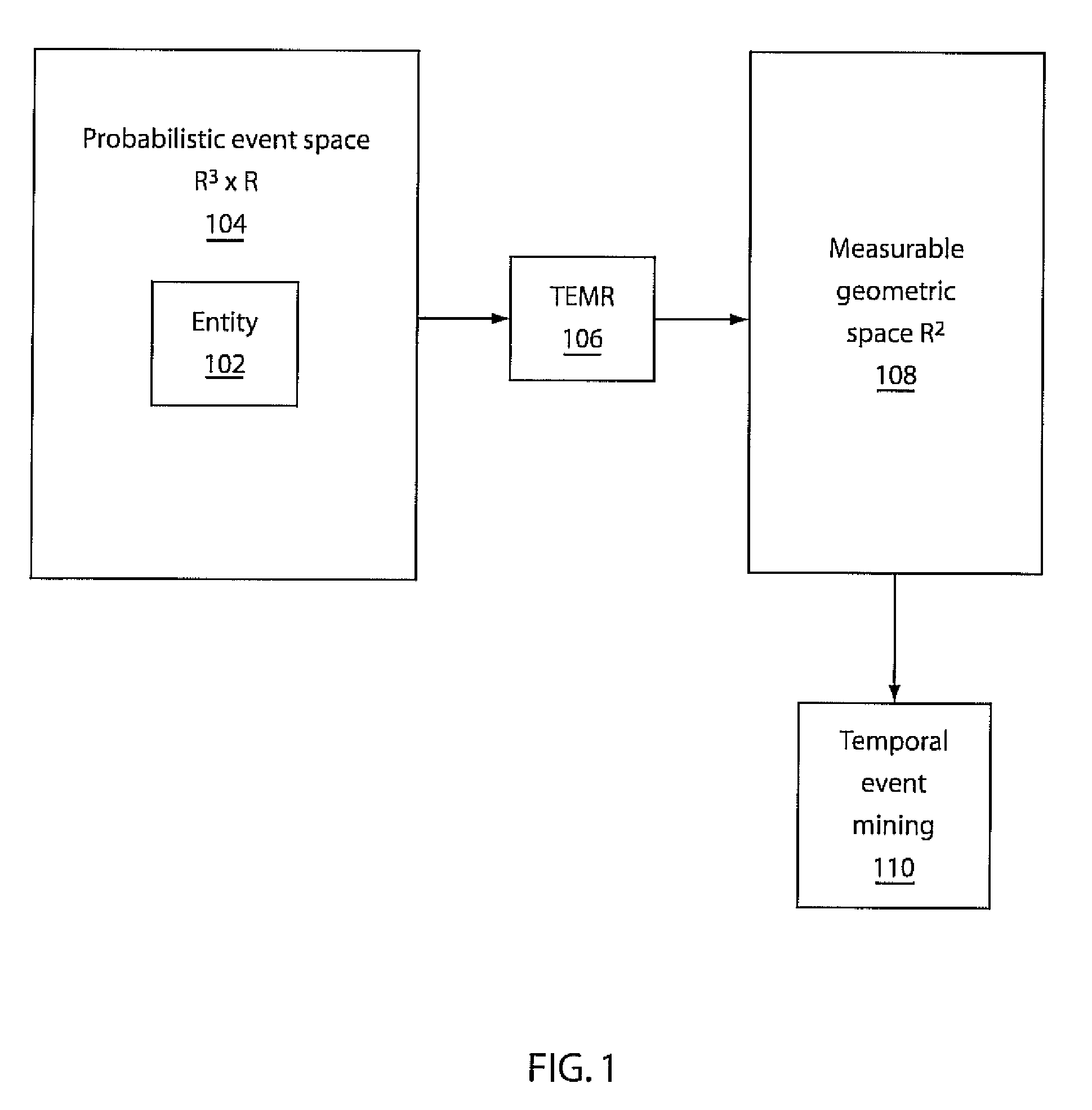
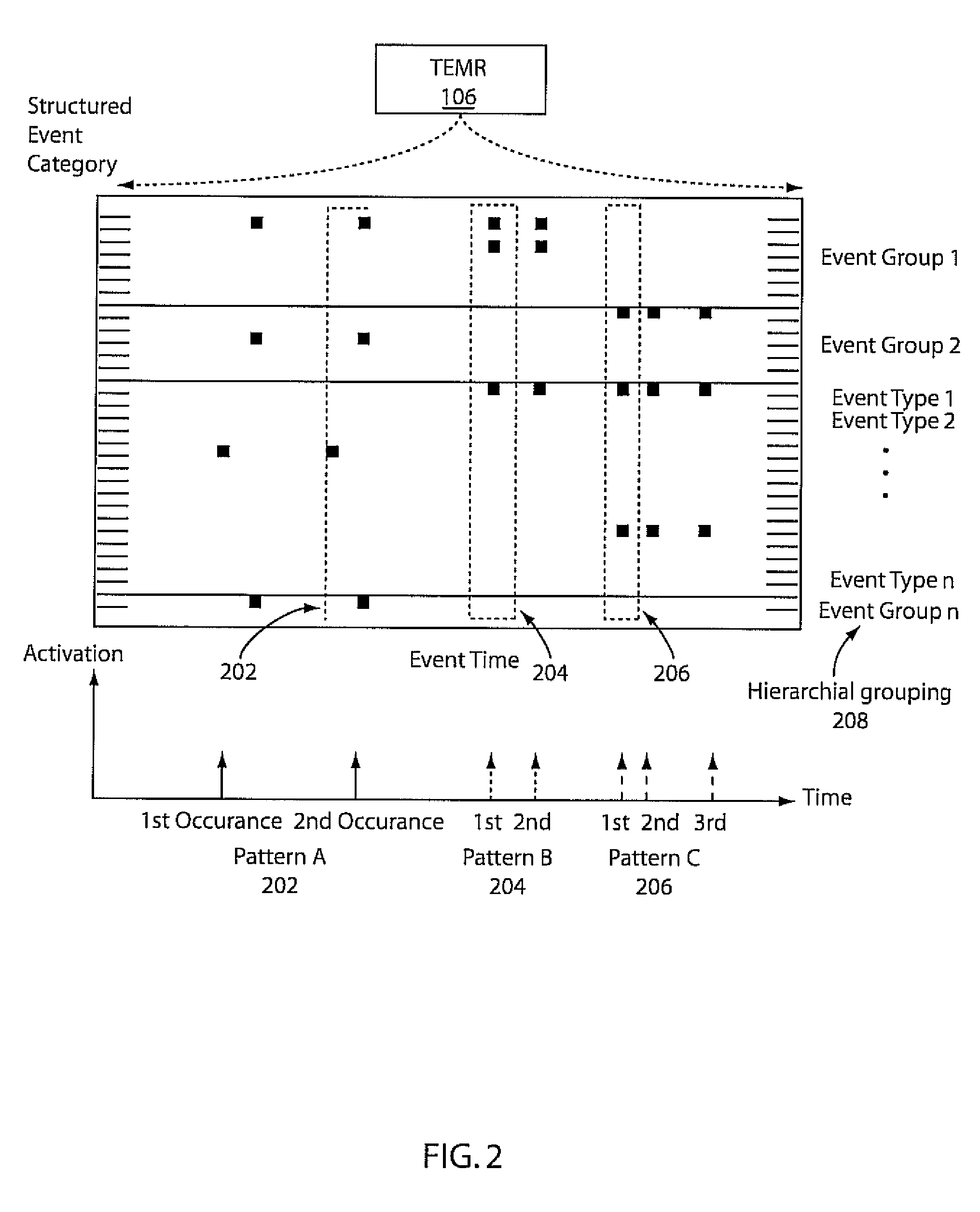
Mining temporal patterns in longitudinal event data using discrete event matrices and sparse coding
Methods and systems for event pattern mining are shown that include representing longitudinal event data in a measurable geometric space as a temporal event matrix representation (TEMR) using spatial temporal shapes, wherein event data is organized into hierarchical categories of event type and performing temporal event pattern mining with a processor by locating visual event patterns among the spatial temporal shapes of said TEMR using a constraint sparse coding framework.
Owner:IBM CORP
Automatic log record segmentation
Owner:IBM CORP
Maximal frequent sequential pattern mining method based on distributed log
ActiveCN108874952AImprove scalabilitySolve mining problemsSpecial data processing applicationsData setSerial pattern
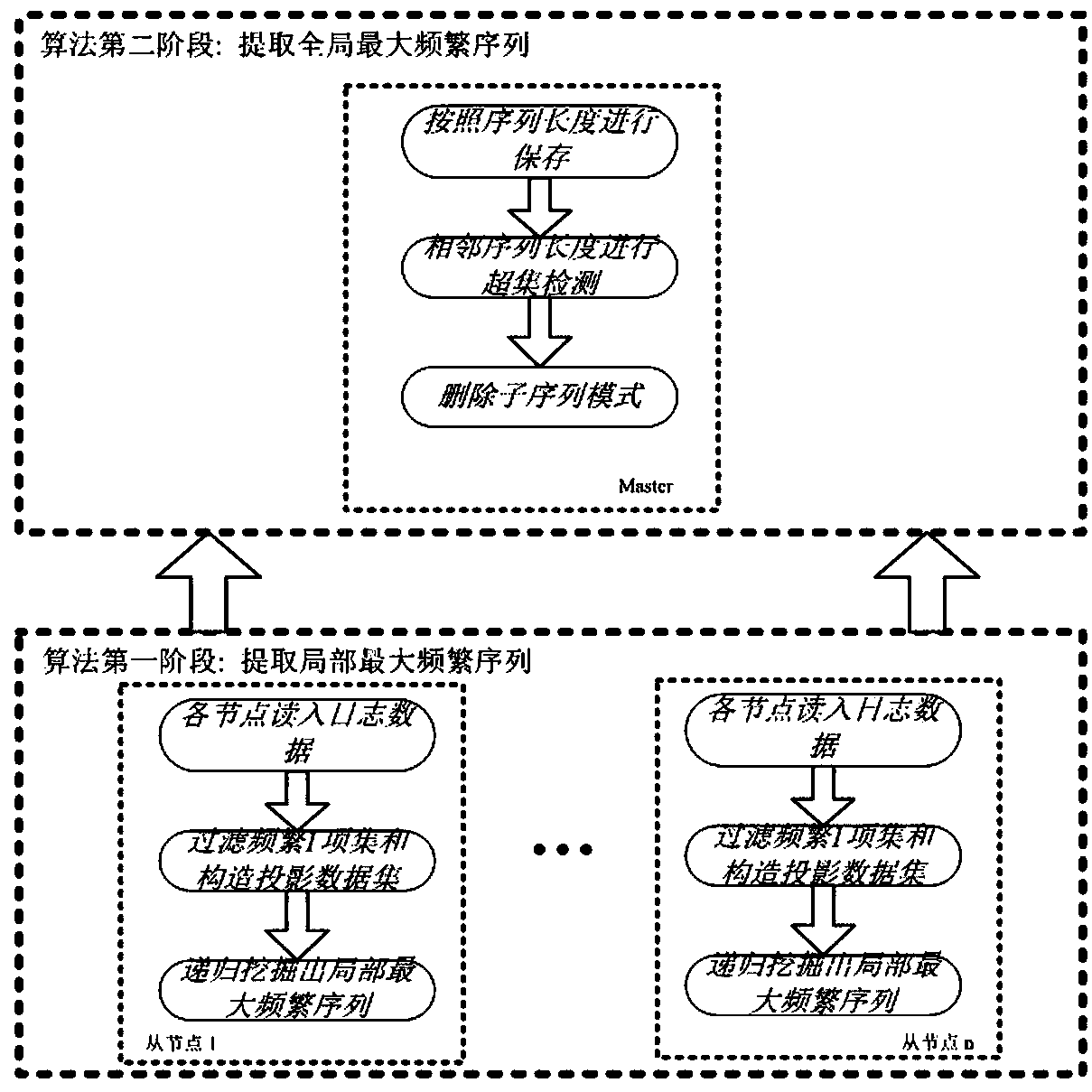
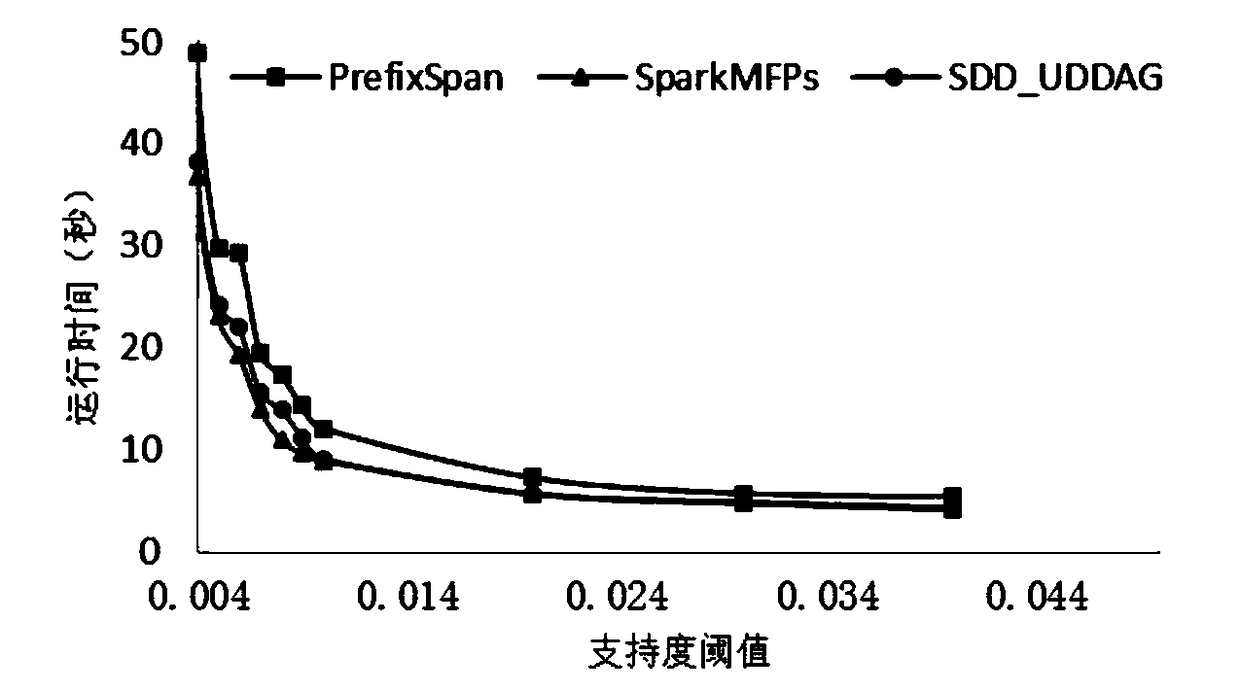
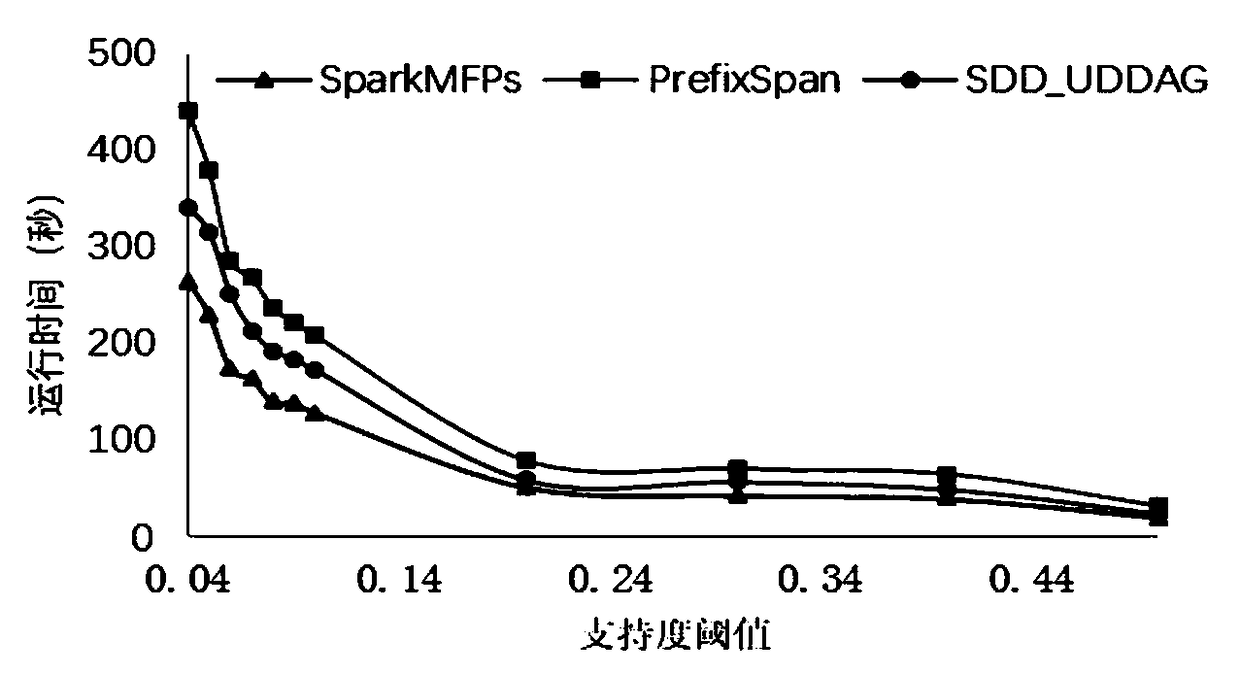
The invention relates to a maximal frequent sequential pattern mining method based on a distributed log.The method comprises the following steps that: on the basis of a Spark distributed computation framework, extracting a local maximal frequent sequence; utilizing prefix projection to divide search space, and carrying out recursive extraction on the local maximal frequent sequence, wherein a first frequent sequence deletes infrequent items in a log sequence dataset, a database scanning scale is lowered, and meanwhile, a corresponding relationship between the frequent sequential pattern and the maximum frequent sequential pattern is used for reducing a candidate sequence number; extracting a global maximum frequent sequence; storing the local maximal frequent sequence according to different lengths, and carrying out superset detection on the sequential pattern of adjacent lengths to judge whether a superset relationship is in the presence or not; and if the superset relationship is inthe presence, deleting a redundant sequence, and extracting a global maximum frequent sequence. The maximal frequent sequential pattern mining method based on the distributed log has higher efficiency, and supports the mining of larger-scale event sequence data.
Owner:FUJIAN NORMAL UNIV
Mining temporal patterns in longitudinal event data using discrete event matrices and sparse coding
Methods and systems for event pattern mining are shown that include representing longitudinal event data in a measurable geometric space as a temporal event matrix representation (TEMR) using spatial temporal shapes, wherein event data is organized into hierarchical categories of event type and performing temporal event pattern mining with a processor by locating visual event patterns among the spatial temporal shapes of said TEMR using a constraint sparse coding framework.
Owner:INT BUSINESS MASCH CORP
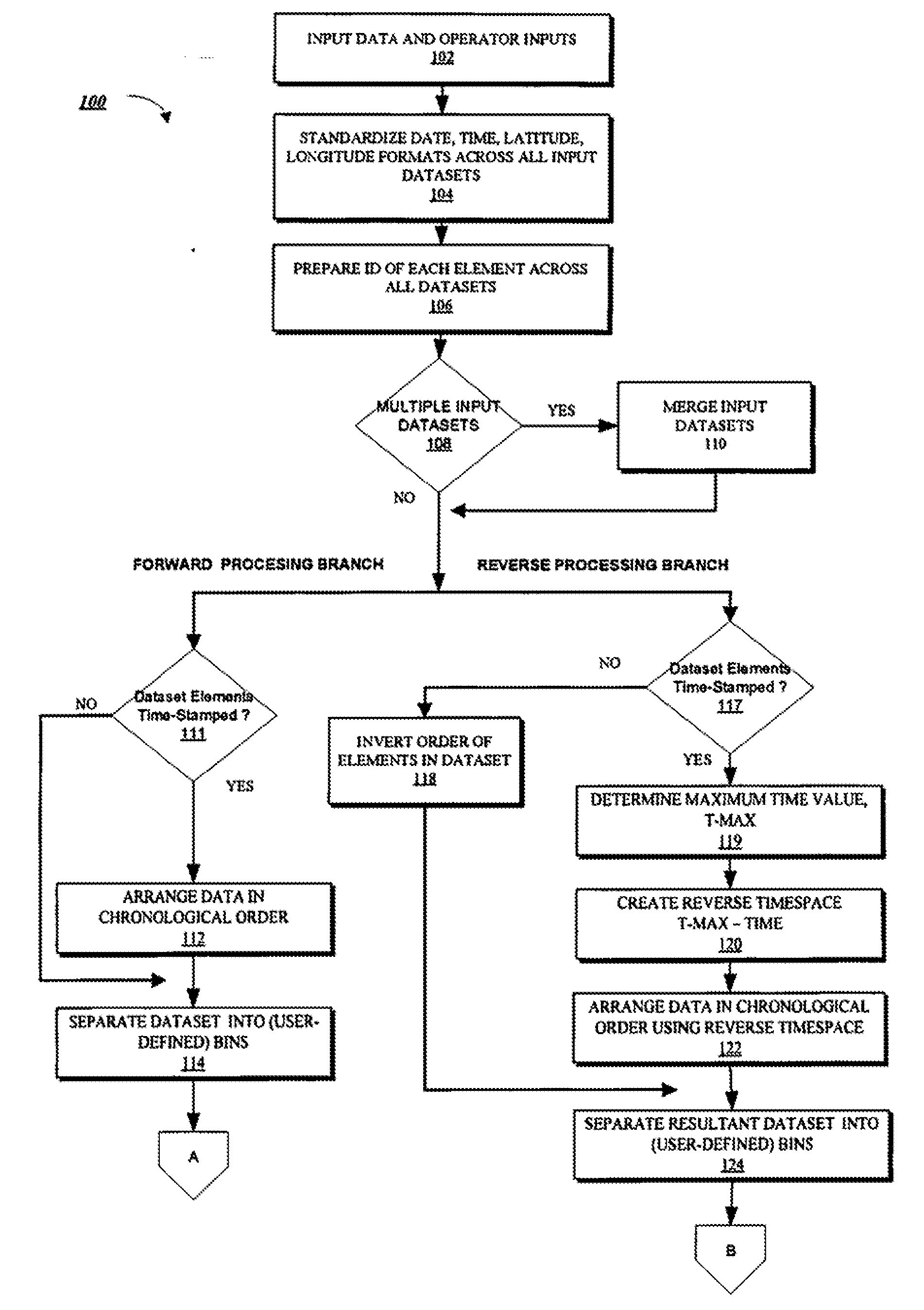
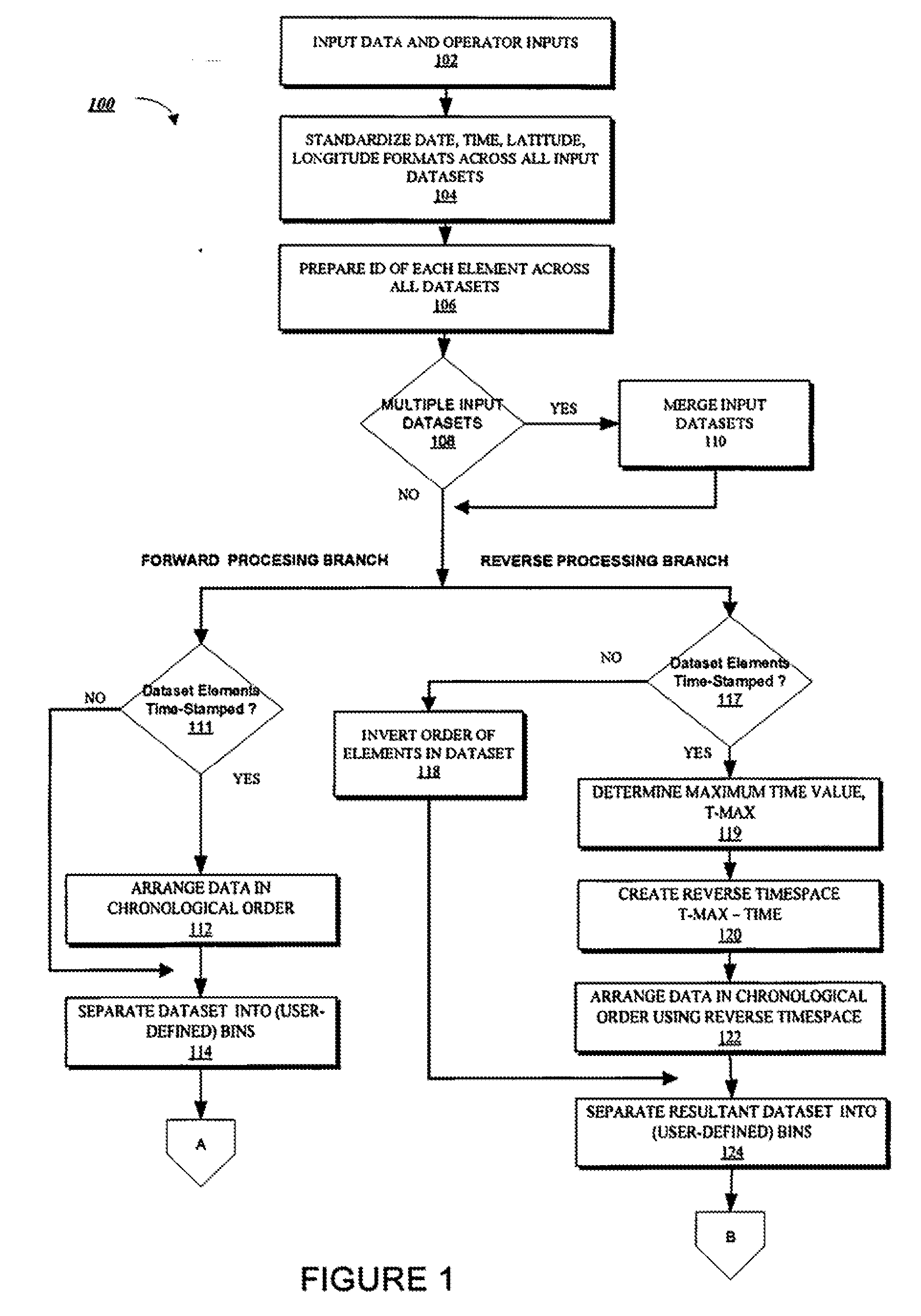
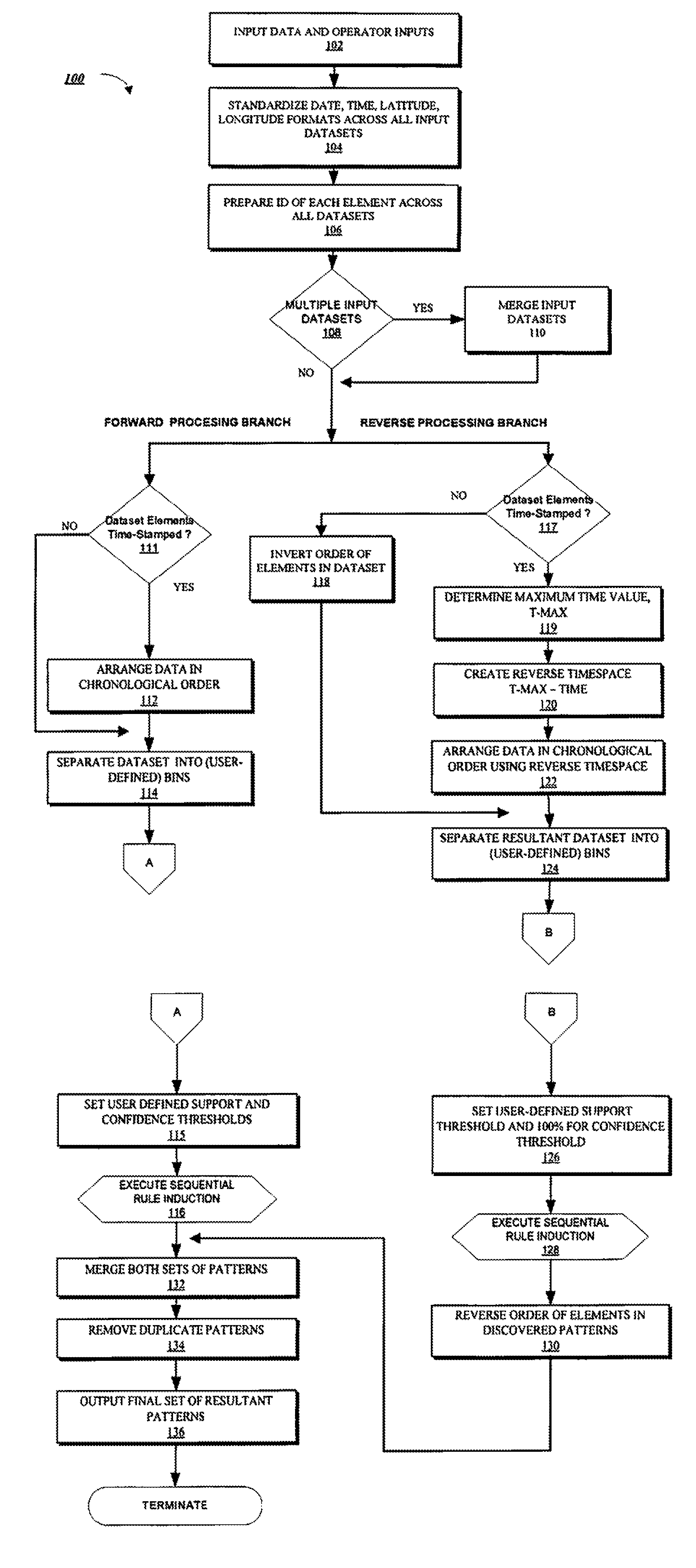
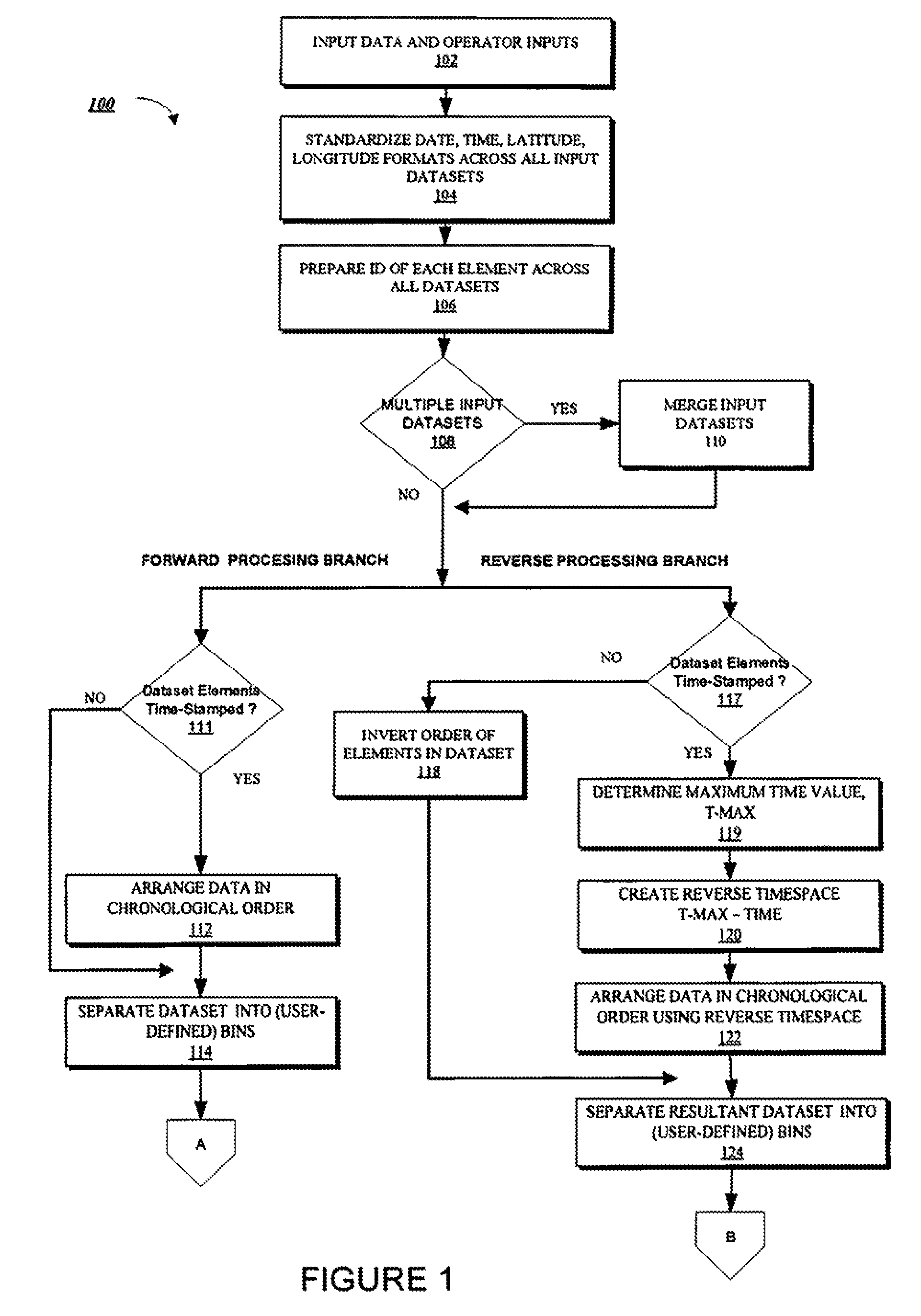
Pattern Discovery Through Reversing Time Flow
InactiveUS20090228443A1Facilitate automated discoveryDigital data information retrievalData processing applicationsReverse timeIntelligent database
The present invention provides systems and methods for automatically mining massive intelligence databases to discover sequential patterns therein using a novel combination of forward and reverse temporal processing techniques as an enhancement to well known pattern discovery algorithms.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
Automatic log record segmentation
ActiveUS20150293920A1Digital data information retrievalMemory loss protectionSequential Pattern Mining
Owner:IBM CORP
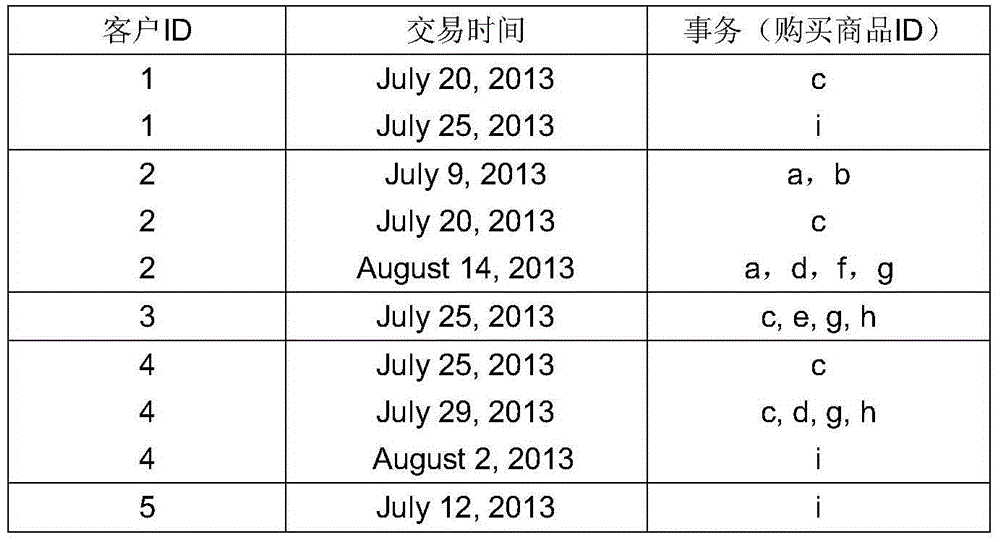
Method for quickly applying negative sequence mining patterns to customer purchasing behavior analysis
PendingCN104574153AIncrease trading opportunitiesIncrease loyaltySpecial data processing applicationsMarketingBehavioral analyticsSerial pattern
The invention provides a method for quickly applying negative sequence mining patterns to customer purchasing behavior analysis. A fast algorithm named as f-NSP is proposed to efficiently mine the negative sequential patterns. According to the main idea of the algorithm, firstly, a positive sequential pattern is obtained through a positive sequential pattern mining algorithm, and as for all frequent positive sequences, an efficient bitmap storage structure is used for storing data sequences including the frequent positive sequences; secondly, negative candidates are generated through a method which is the same as e-NSP and is used for generating negative candidate sequences; finally, data bitmaps are subjected to and operation, or operation and xor operation by means of a formula, the support degree of the negative candidates is quickly calculated, the negative sequential pattern meeting the minimum support degree is mined, and a database does not need to be scanned again. Purchasing behaviors of customers are analyzed through screened sequential patterns so that a seller can predict subsequent commodity buying and selling conditions according to current commodity buying and selling conditions; as a result, the seller can arrange placement of commodities better, and the sale quantity of the commodities can be increased.
Owner:QILU UNIV OF TECH
Program -class operating system debug method based on serial mode excavation
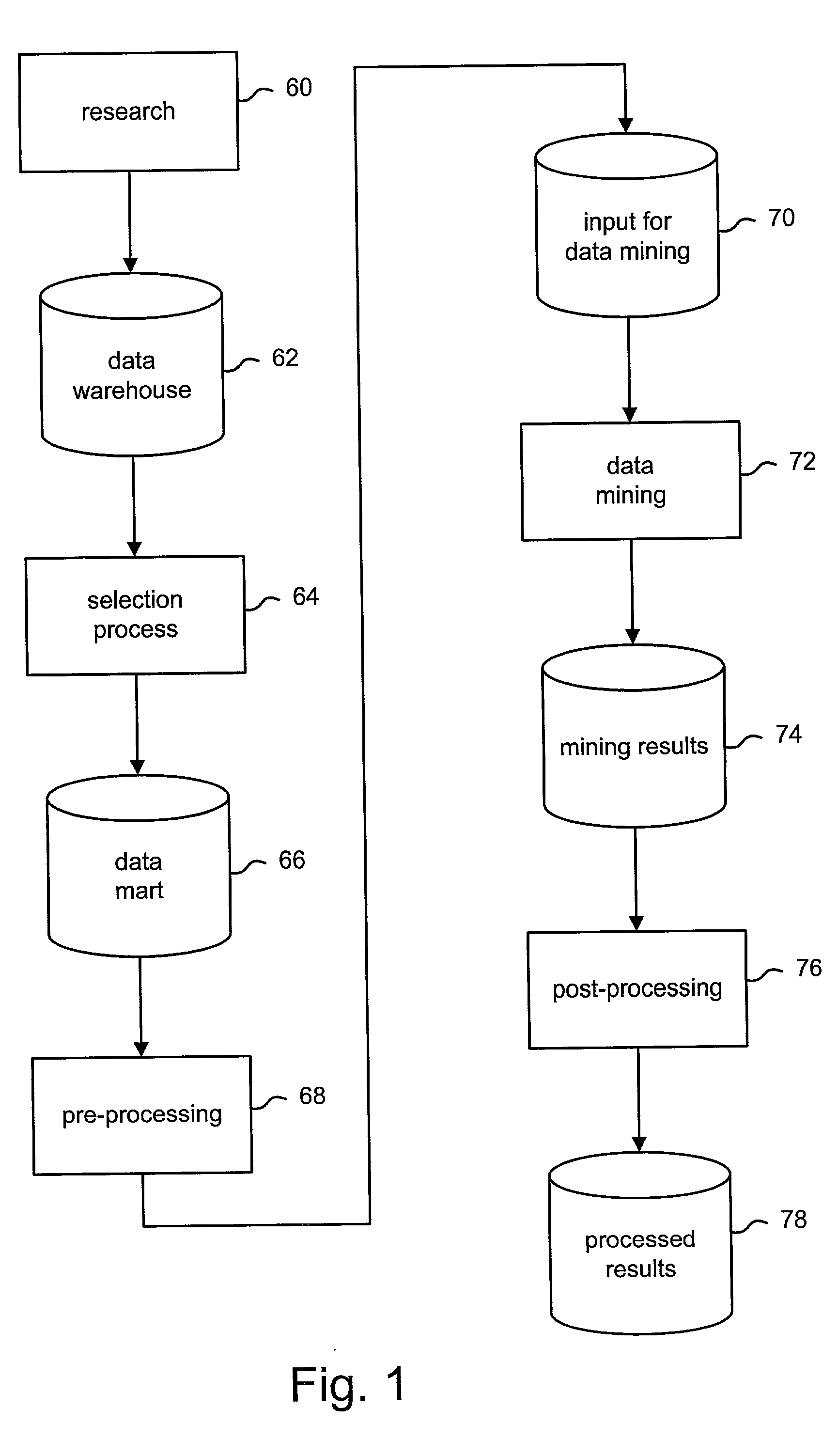
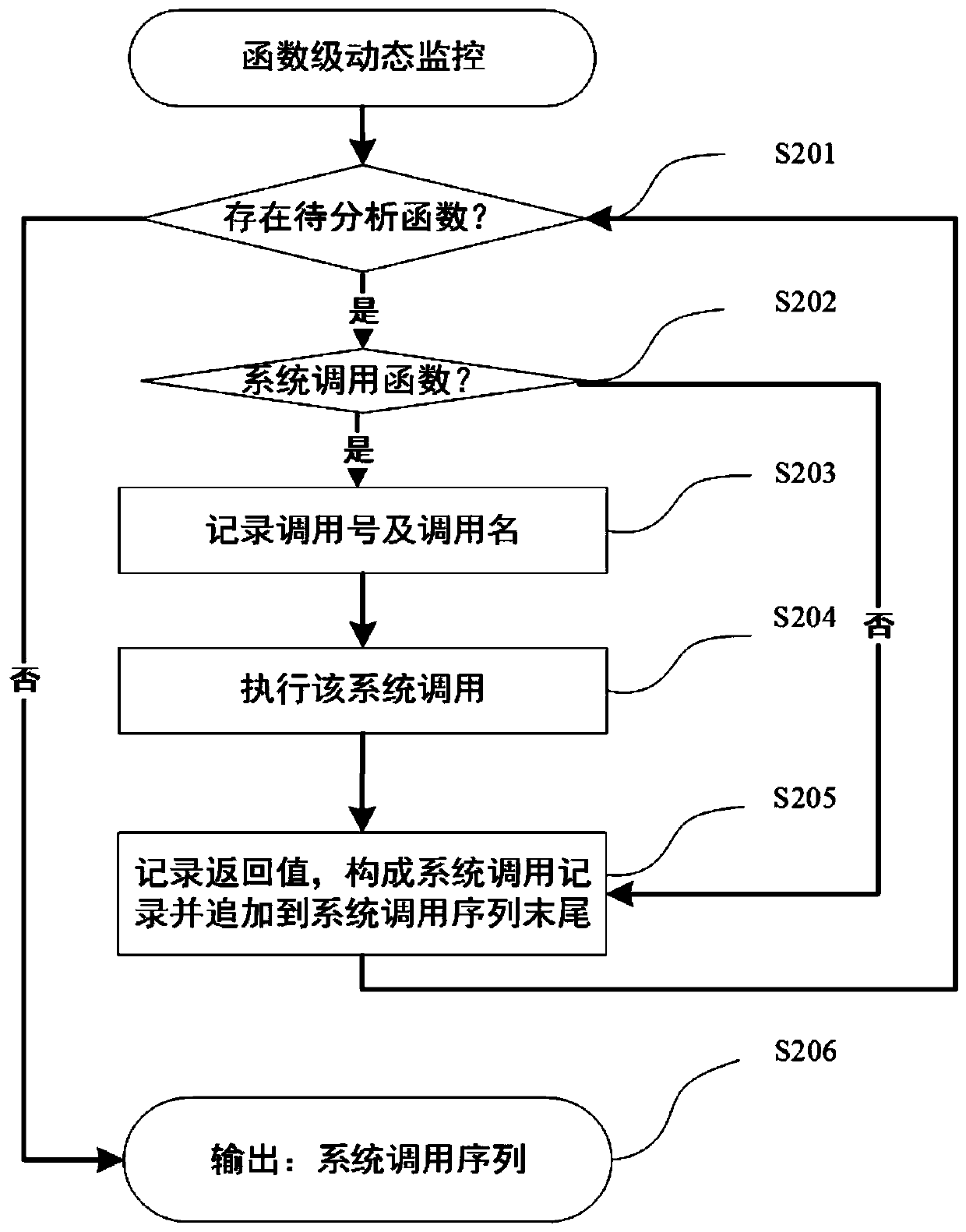
InactiveCN101308473APrecise positioningRapid positioningSoftware testing/debuggingOperational systemSerial pattern
The invention discloses a program-level operating system debugging method based on sequential pattern mining, comprising the following steps: to find all the frequent system calling sequential patterns through sequential pattern mining; to compute all the parameters in a hidden Markov model to identify abnormal system calling sequences. The method makes use of the sequential pattern mining method to carry through pattern mining to the system calling sequence set in the desktop operating system to find all the frequent sequence set, and also makes use of the frequent sequence set to train the hidden Markov model so as to eventually identify the abnormal system calling sequences through the Markov model to accurately and quickly target the bug location of the entire desktop operating system to help the user to improve the operating system.
Owner:ZHEJIANG UNIV
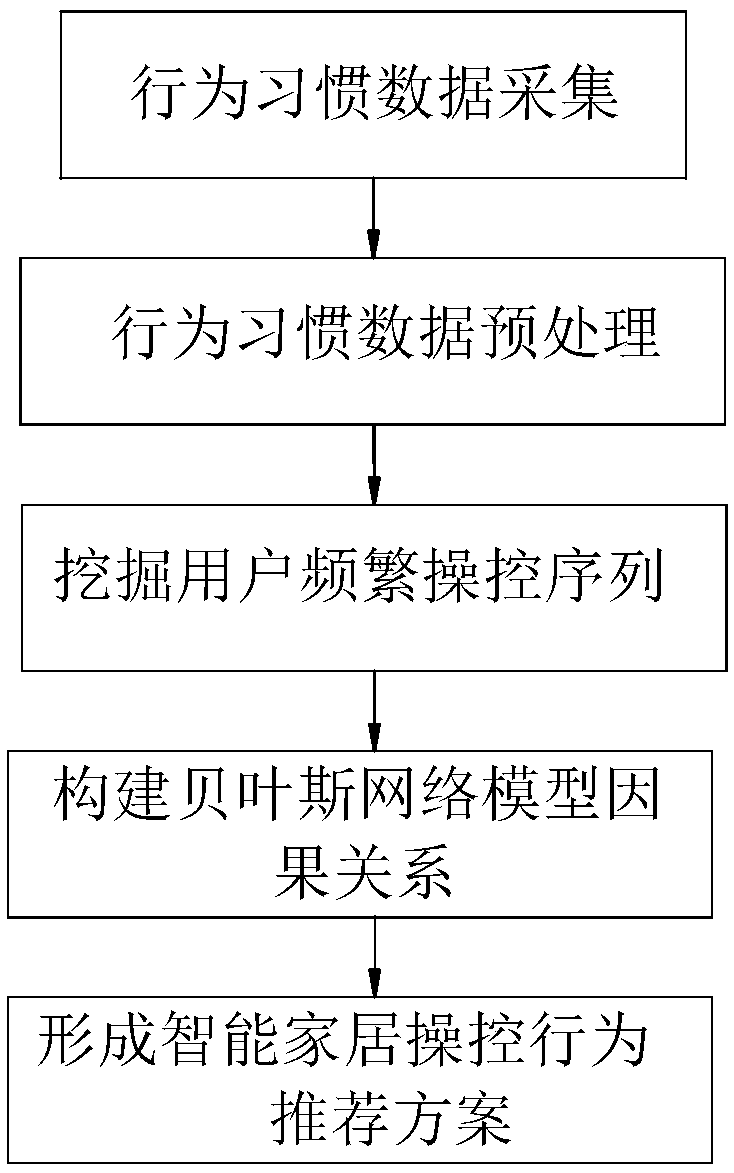
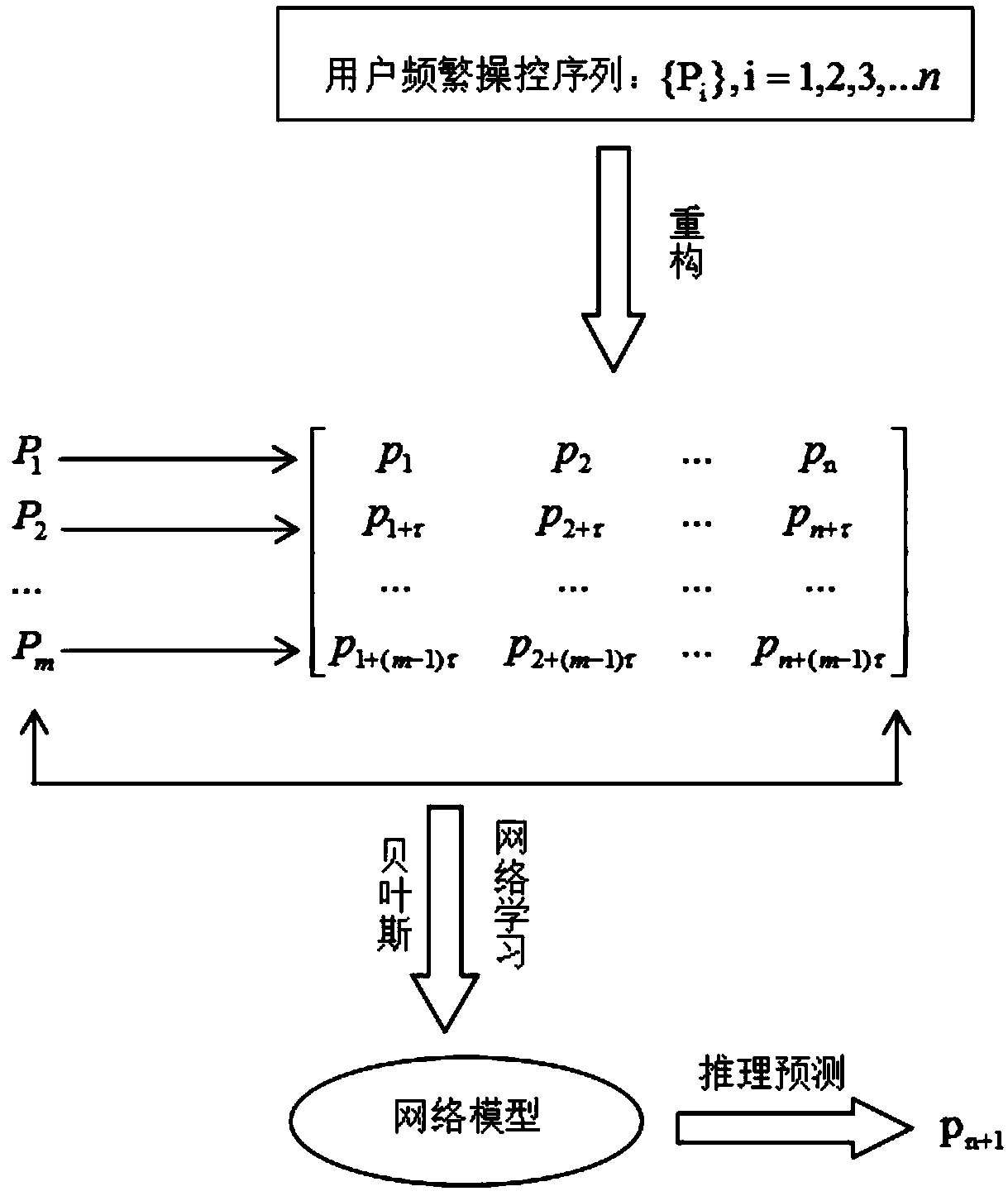
Smart home user manipulation behavior recommendation method based on temporal causality analysis
ActiveCN109542944AReduce noiseEnhancing strong temporal correlationDigital data information retrievalCharacter and pattern recognitionComputation complexityData set
The invention relates to a smart home user manipulation behavior recommendation methodbased on temporal causality analysis. A large number of user behavior habit data are segmented, and then the sequence of frequent user operations is extracted from the data by a sequential pattern mining algorithm. Based on the sequence of frequent user operations, the causal relationship between the mining sequences of Bayesian network is constructed, so as to construct the process of intelligent home manipulation behavior recommendation scheme. The invention combines the advantages of a pattern mining algorithm and a Bayesian model, reduces the entire data set to a selected set of frequently manipulated sequences through pattern mining, greatly reduces the computational complexity and the noise in the causal relationship computation, which is conducive to more efficient formation of a more user-friendly smart home manipulation behavior recommendation scheme, and at the same time enhances the strongtime correlation between each device of the smart home manipulation behavior recommendation scheme, and fills in the shortcomings of the traditional algorithm.
Owner:GUANGDONG UNIV OF TECH
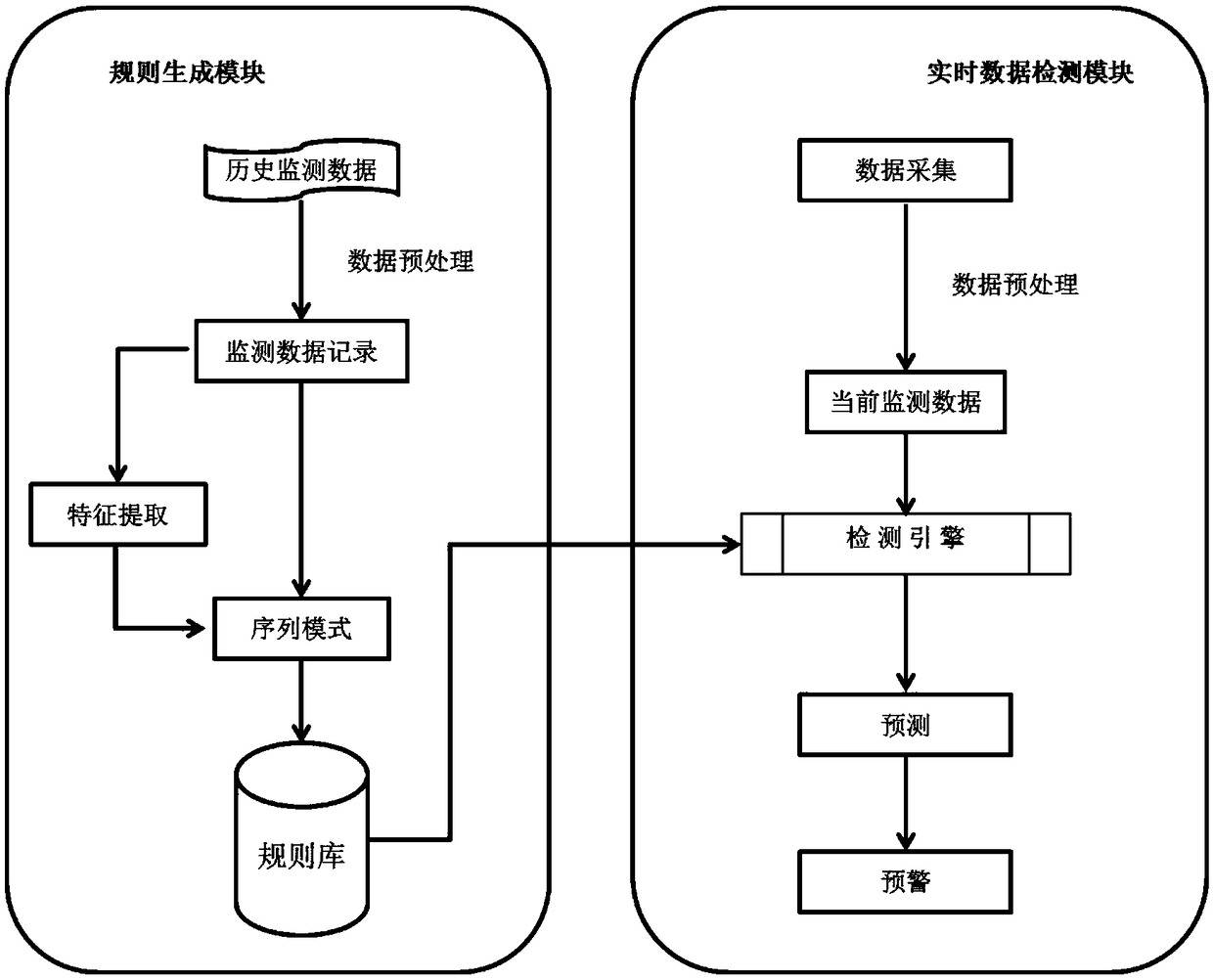
Energy-saving optimization method of ball mill pulverization system in thermal power plant based on sequential pattern mining
The invention discloses an energy conservation optimizing method of a heat-engine plant ball mill pulverizing system based on sequential pattern mining, and the method comprises the following steps: carrying out a sequential pattern mining process on the on-site record data, so as to automatically obtain a mill load 1, the outlet temperature ot of the mill, the inlet negative pressure inp of the mill, the opening uh of a hot wind door, and sequential modes among circulation wind door opening ur, the mill output force pc, the mill load set value lsv, mill outlet temperature set value otsv and the mill inlet negative set value inpsv; and determining the best set values of the mill load, the mill outlet temperature and the mill inlet negative pressure at the current working condition on the basis of the current operation data and the obtained sequential mode by adopting a search method item by item, thus the energy conservation optimizing method is simple and feasible and has good commonality, and the pulverizing system can operate in a best manner on the premise of safety and stability, thus not only providing an effective guarantee for the excellent-quality burning of a boiler system, but also providing beneficial effects on a heat-engine plant.
Owner:XI AN JIAOTONG UNIV
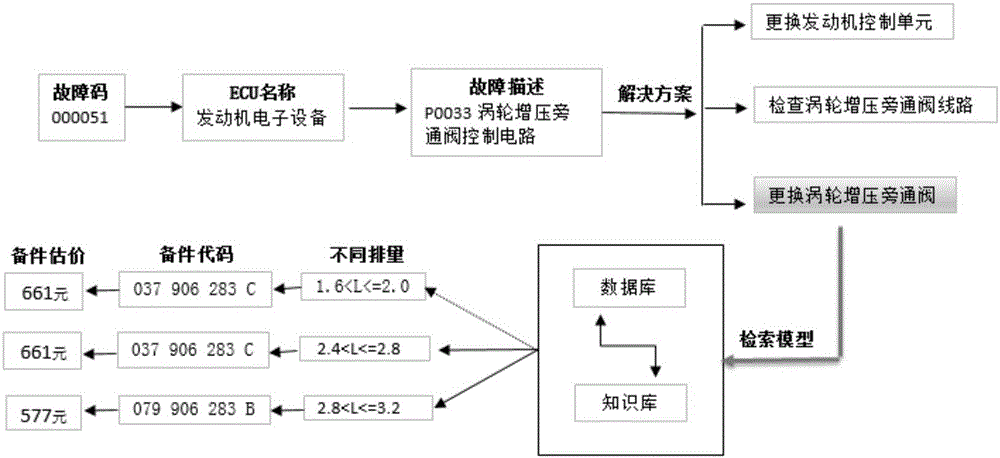
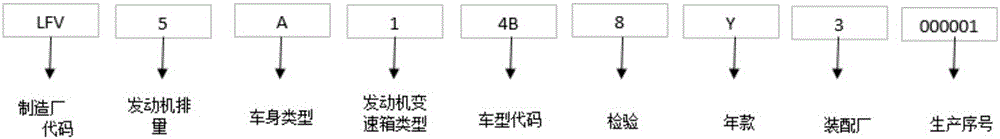
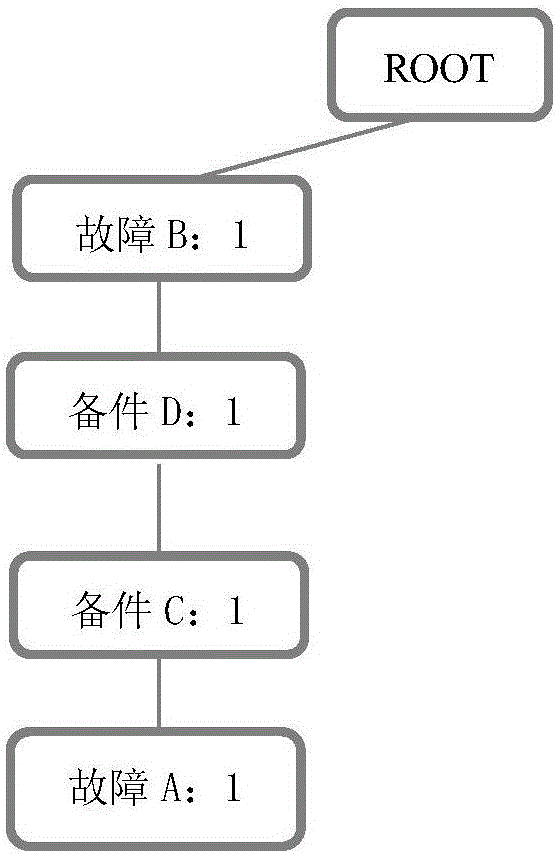
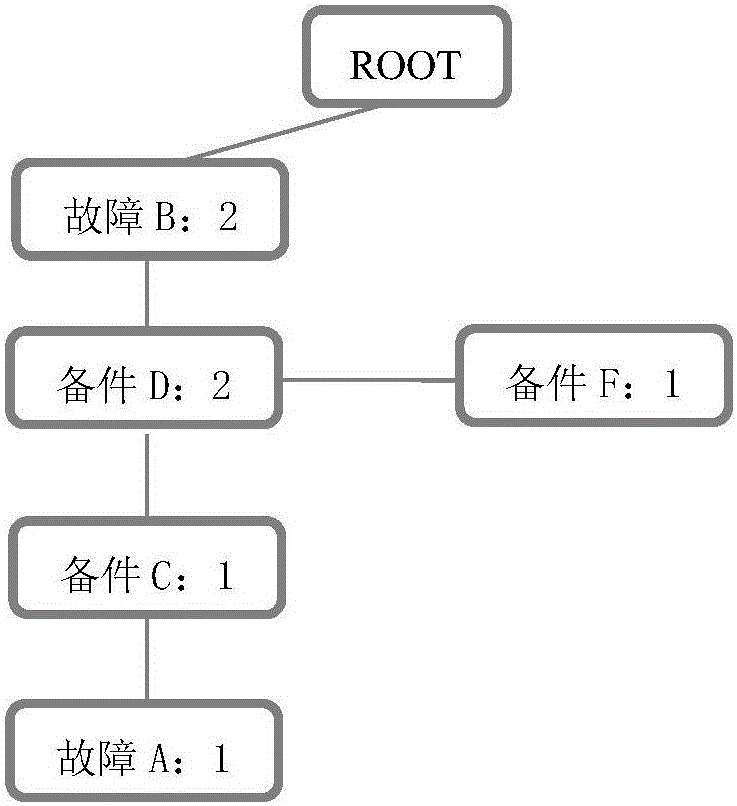
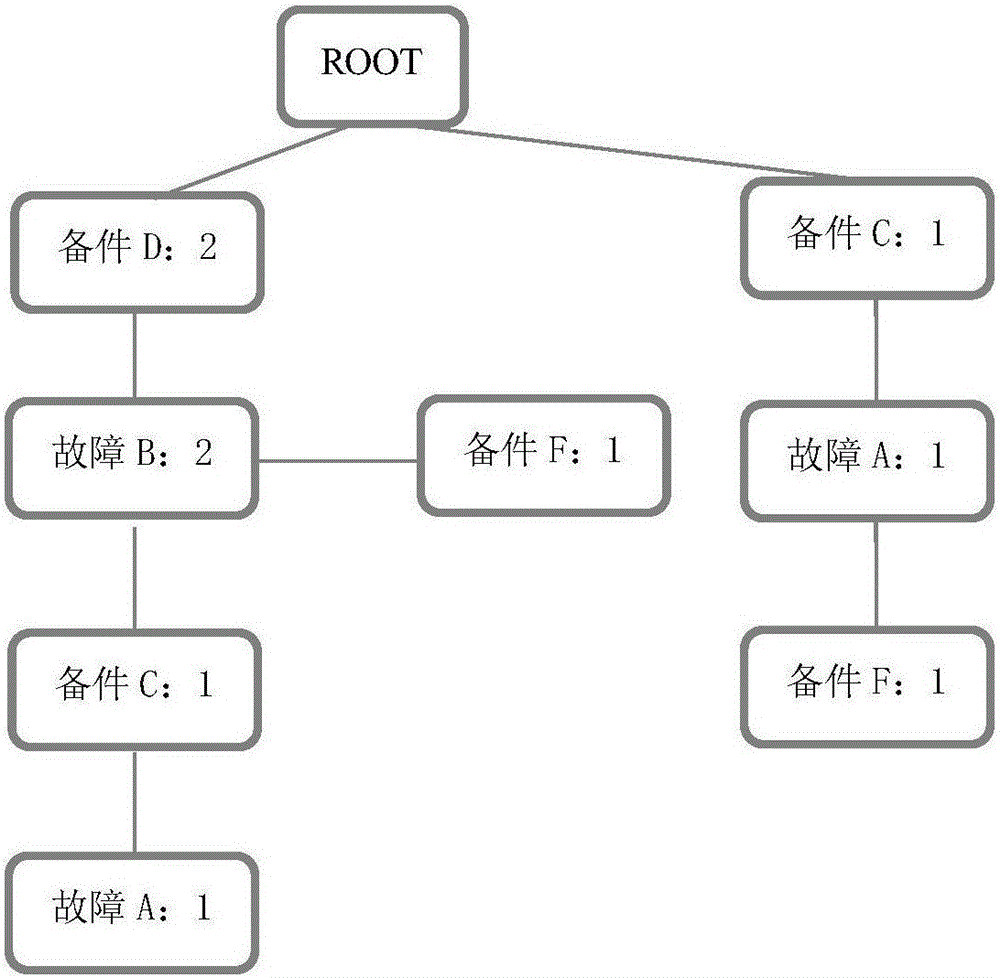
Fault code diagnosis vehicle item and spare part retrieval method based on FP-Tree sequential pattern mining
The invention provides a fault code diagnosis vehicle item and spare part retrieval method based on FP-Tree sequential pattern mining, and belongs to the field of information retrieval. The technical key points are that vehicle VIN codes are analyzed so that variables are obtained, wherein the variables include engine displacement, the vehicle body type and the engine gearbox type which are obtained through analysis of the VIN codes; decision tree analysis is performed on spare part codes corresponding to the variables and variable data classification is completed to form spare part information, and indexes are established so that a diagnosis knowledge base is formed; step four, a frequent item set of the corresponding relation of the fault codes and the replacement spare parts is created through an FP-Tree algorithm according to an affair database; topological searching is performed by utilizing the topological relation between the position of the spare parts and the ECU position of the faults, and the frequent item set is selected; the corresponding relation between the spare parts and maintenance items is constructed so that a diagnosis database of the corresponding items of the fault codes is formed; and the diagnosis database is correlated with the diagnosis knowledge base, and a primary key is established. The effects are that the solutions for the common faults and the corresponding spare parts and the items can be quickly found after acquisition of the fault codes.
Owner:DALIAN ROILAND SCI & TECH CO LTD
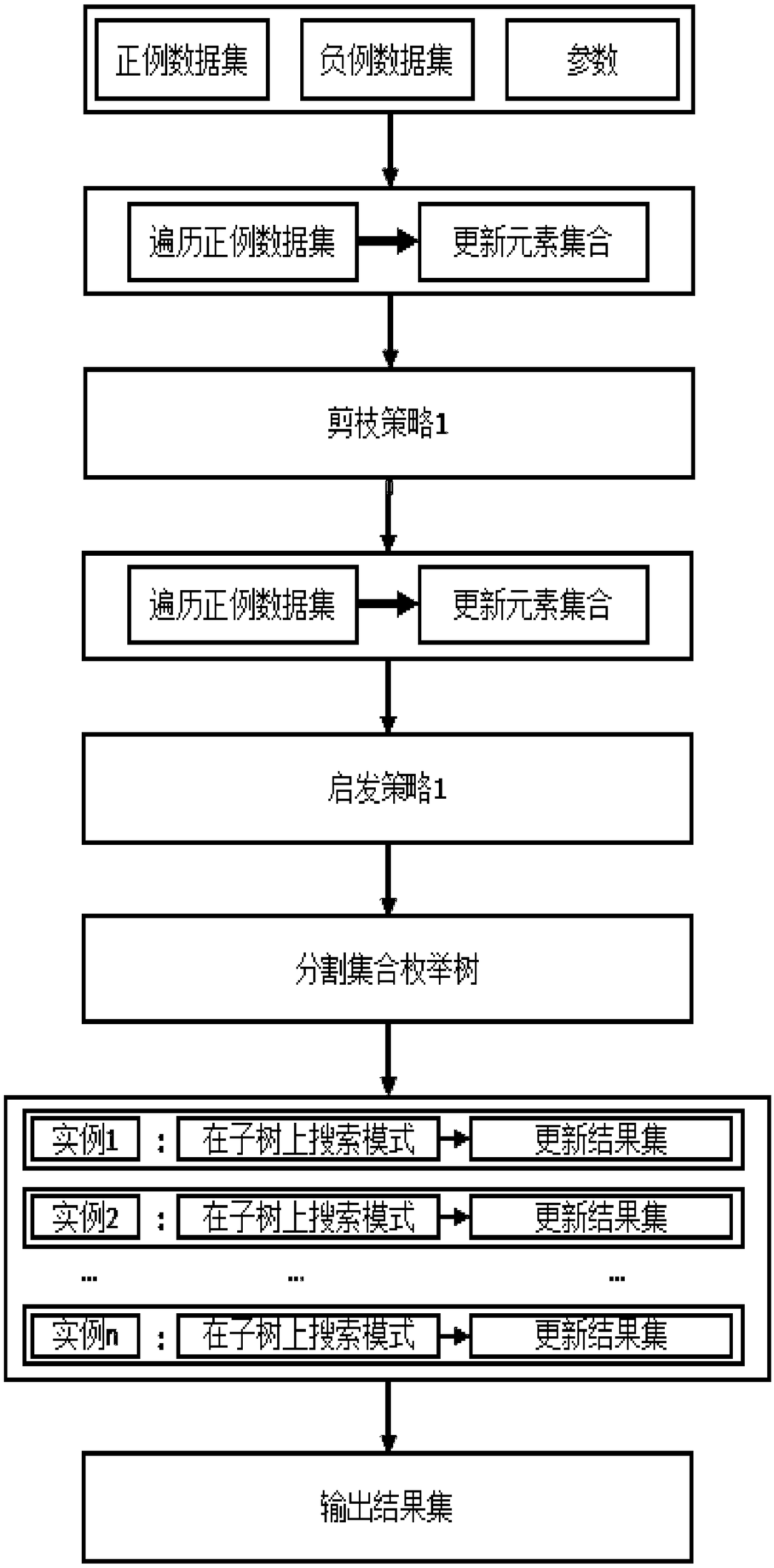
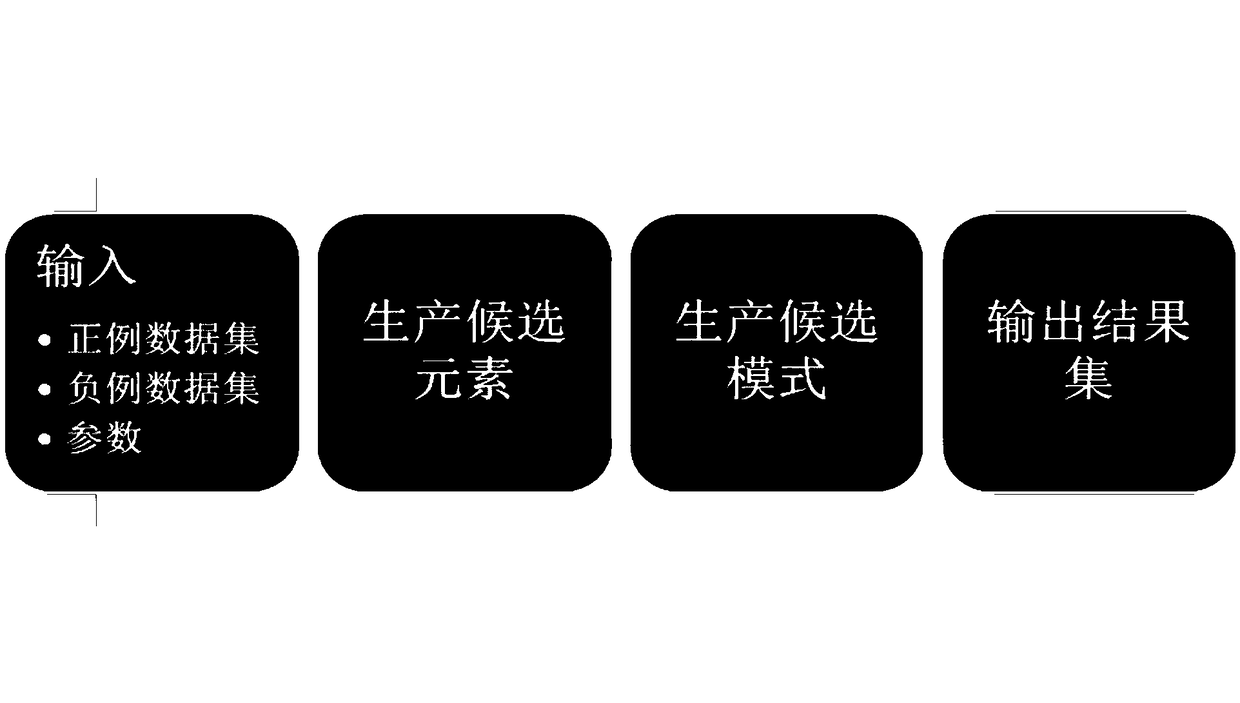
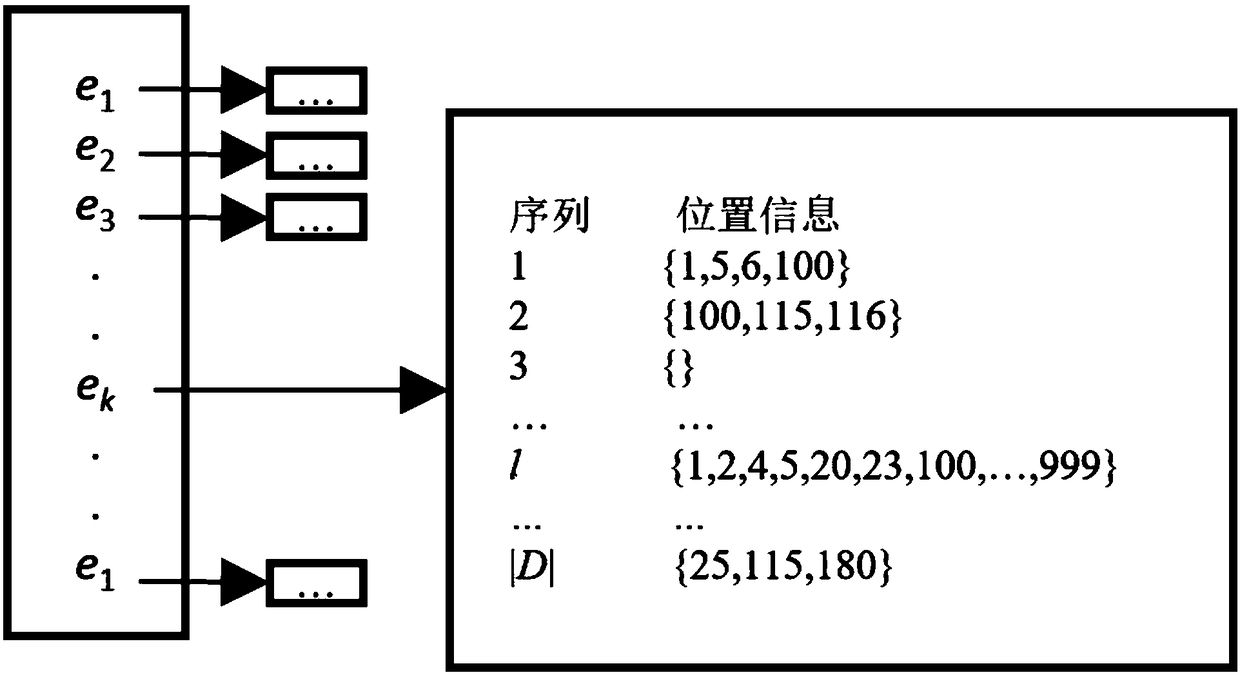
A Top-K contrast sequential pattern mining algorithm based on concurrence and having interval constraints
InactiveCN109033341APrevent missImprove interpretabilitySpecial data processing applicationsSequential Pattern MiningData set
The invention discloses a Top-K contrast sequential pattern mining algorithm based on concurrence and having interval constraints, which includes: inputting data sets and parameters according to the prescribed format; scanning a data set, a set of production candidate elements and position information of all elements therein; a data set enumeration tree traverses all candidate patterns to find thek patterns with the most significant contrast. The k modes with the most prominent contrast are output to the specified position. Based on the mining of contrast sequence patterns with interval constraints, the invention introduces the concept of top-k. The contrast sequential pattern mining algorithm with interval constraints aims to find the k contrast sequential patterns whose support degree varies most significantly between two data sets. This method can avoid the loss of useful patterns due to inappropriate thresholds. Only the number of desired modes can be set by the user, and the usedifficulty is greatly reduced compared with the previous methods; At the same time, it enhances the interpretability of the mining results.
Owner:STATE GRID CHONGQING ELECTRIC POWER CO ELECTRIC POWER RES INST +2
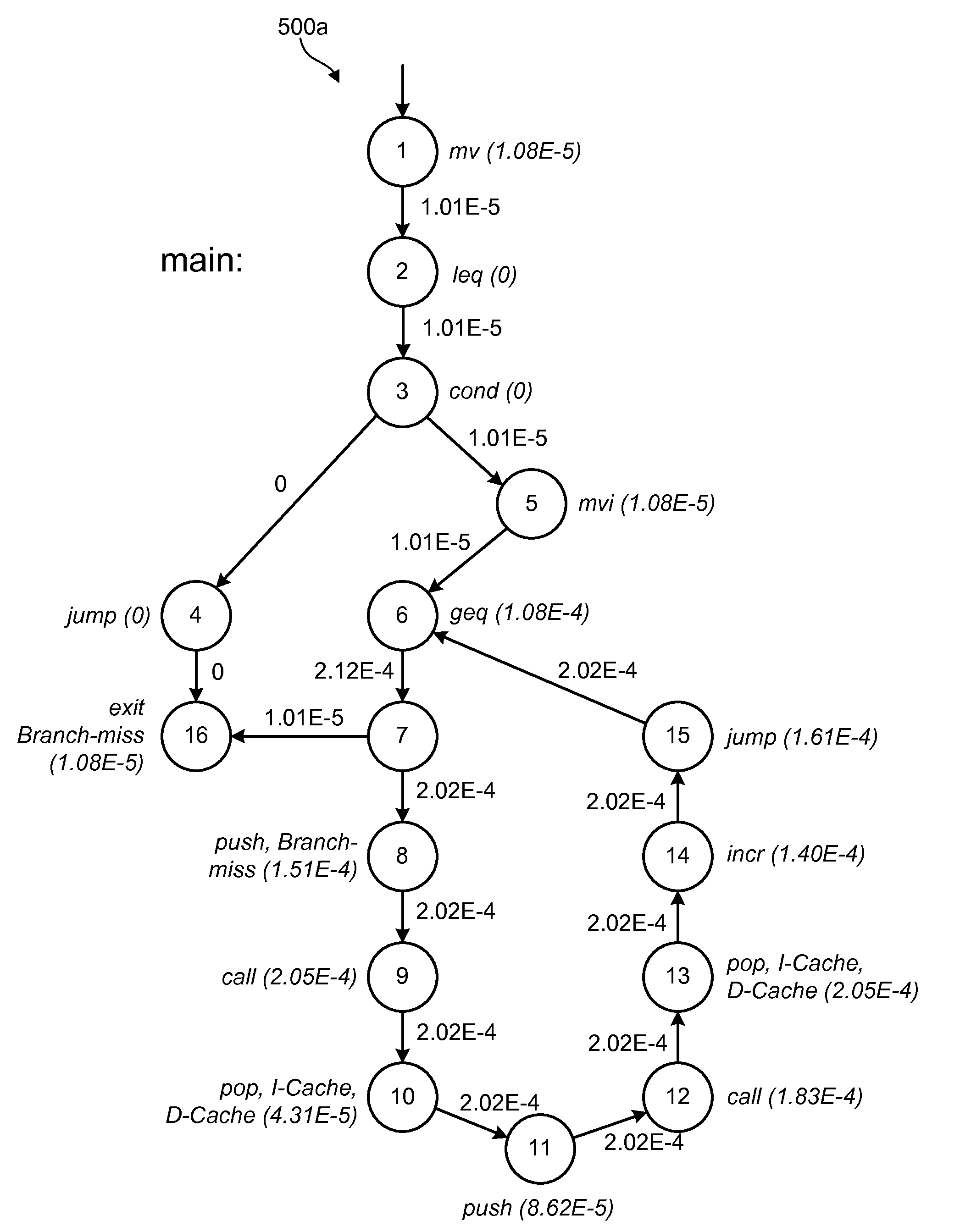
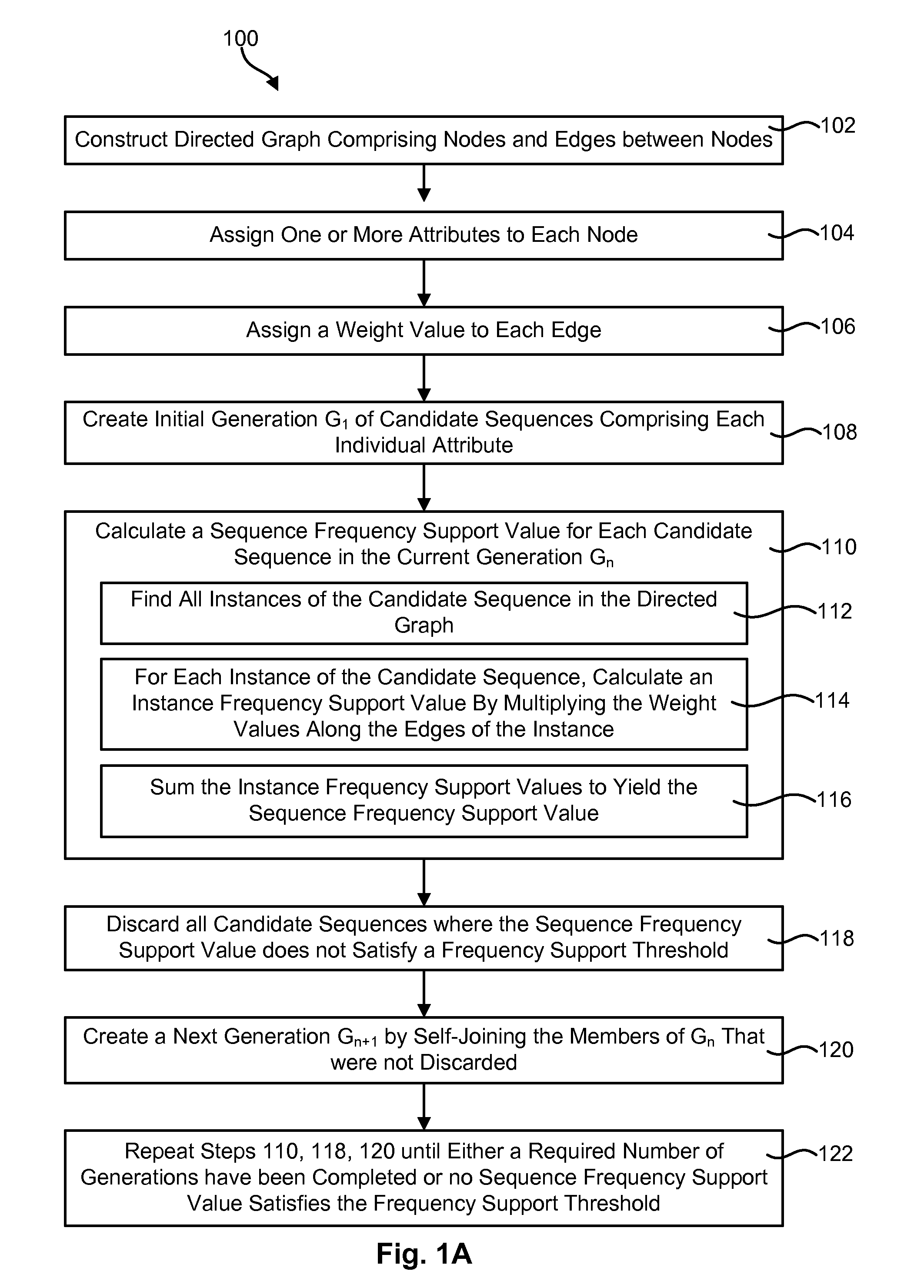
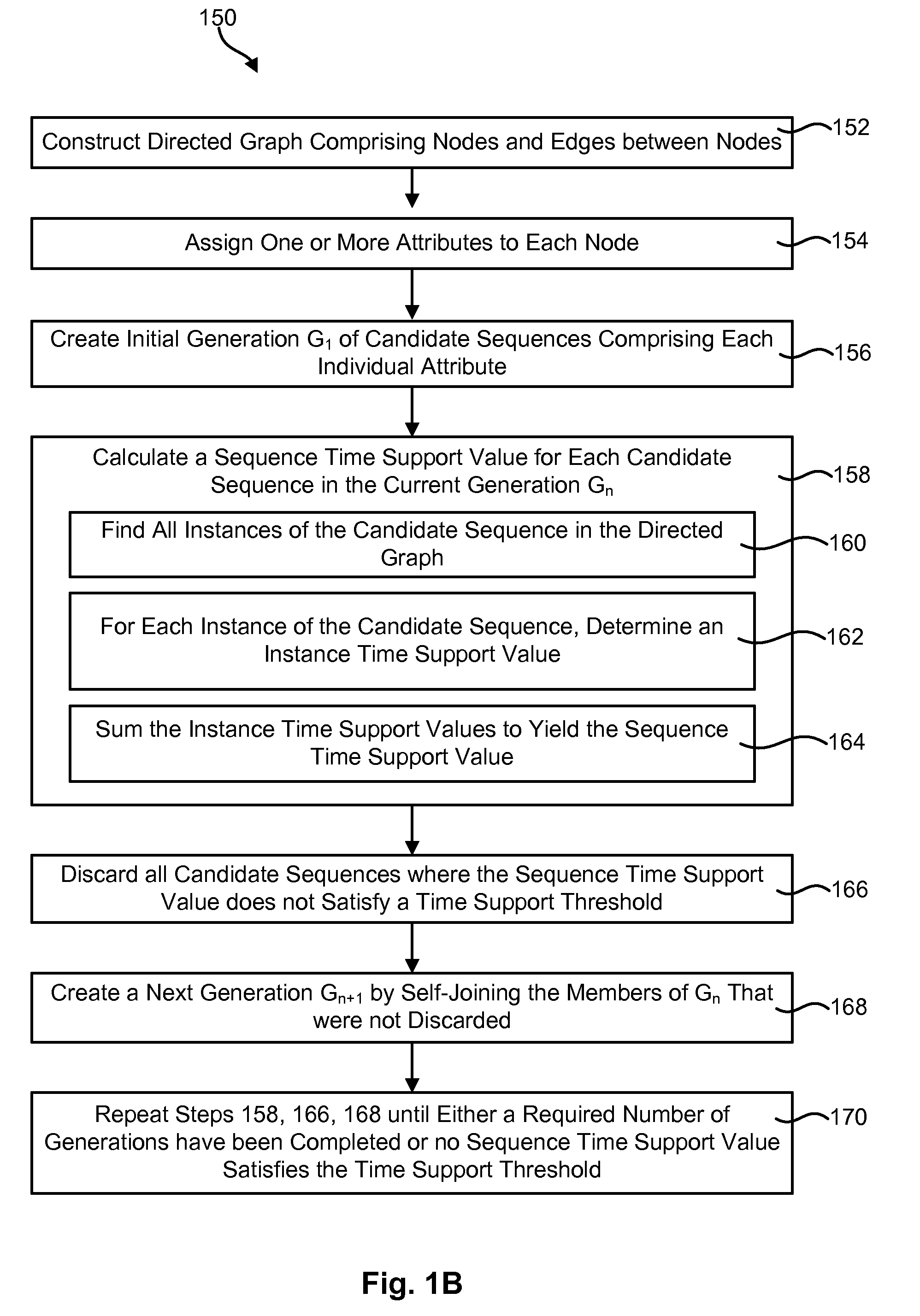
Mining sequential patterns in weighted directed graphs
InactiveUS20120197854A1Digital data processing detailsError detection/correctionDirected graphSerial pattern
A method for finding sequential patterns of attributes in a directed graph includes constructing a directed graph comprising multiple nodes and edges between the nodes. Each of the nodes may be assigned one or more attributes. Similarly, each of the edges may be assigned a weight value which may indicate the probably the edge will be traversed during traversal of the directed graph. The method may further include finding sequences of attributes in the directed graph that have some minimum amount of frequency and / or time support. In performing this step, the frequency support of each individual instance of a sequence of attributes may be calculated by multiplying the weight values along the edge or edges of the instance. A corresponding apparatus and computer program product are also disclosed and claimed herein.
Owner:INT BUSINESS MASCH CORP
FP-Tree sequential pattern mining-based fault diagnosis and valuation platform
The invention discloses an FP-Tree sequential pattern mining-based fault diagnosis and valuation platform. The platform comprises a corresponding relationship module, a topologic search module and a solution module, wherein the corresponding relationship module creates a frequent item set of a corresponding relationship between a fault code and a replacement spare part through an FP-Tree algorithm according to a transactional database; the topologic search module performs a topologic search by utilizing a topologic relationship between the position of the spare part and an ECU position where a fault is located, and selects the frequent item set; and the solution module obtains a complete solution of the spare part corresponding to the fault code and a repair item according to a corresponding relationship established by the spare part and the repair item. According to the diagnosis and valuation platform, the corresponding relationship is searched for through the frequent item set algorithm FP-Tree and the sequential pattern mining algorithm; the two algorithms are fused for use; the platform is suitable for the possibility of parallel solving of multiple faults in addition to a single fault; the spare part needed to be repaired and the item are judged by remotely estimating the fault code of the vehicle; the complete solution is provided; and a reference is provided for vehicle repair.
Owner:DALIAN ROILAND SCI & TECH CO LTD
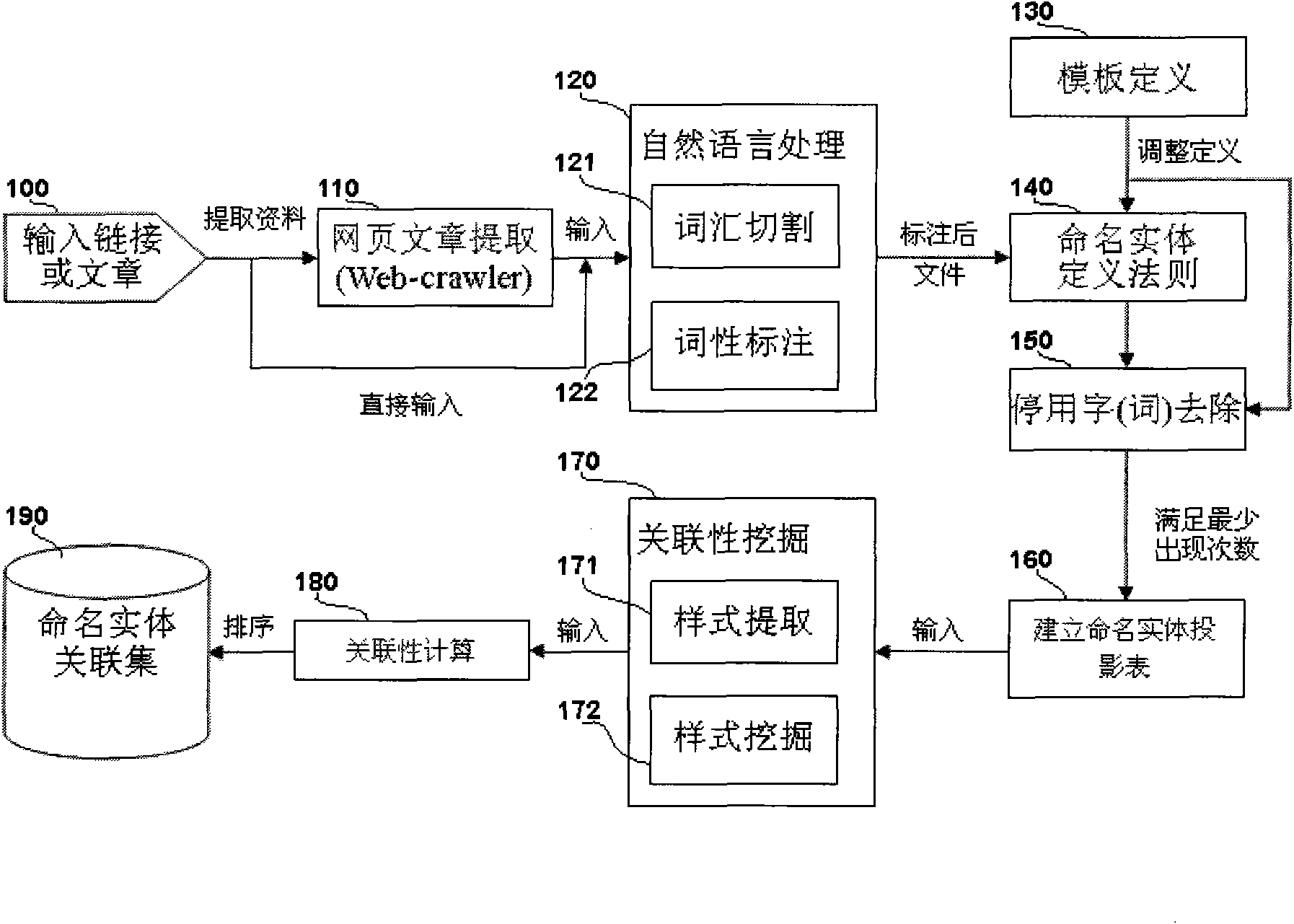
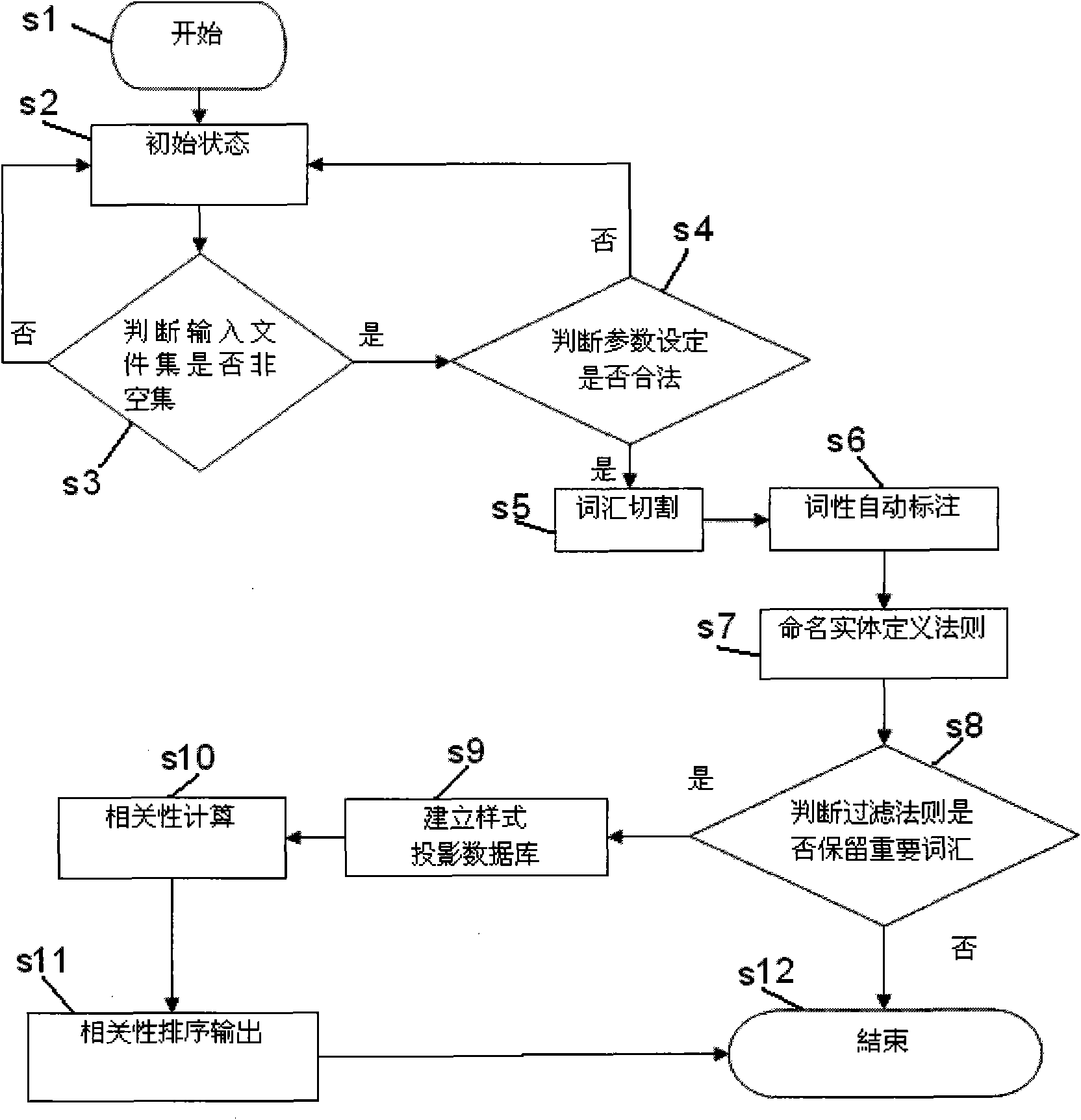
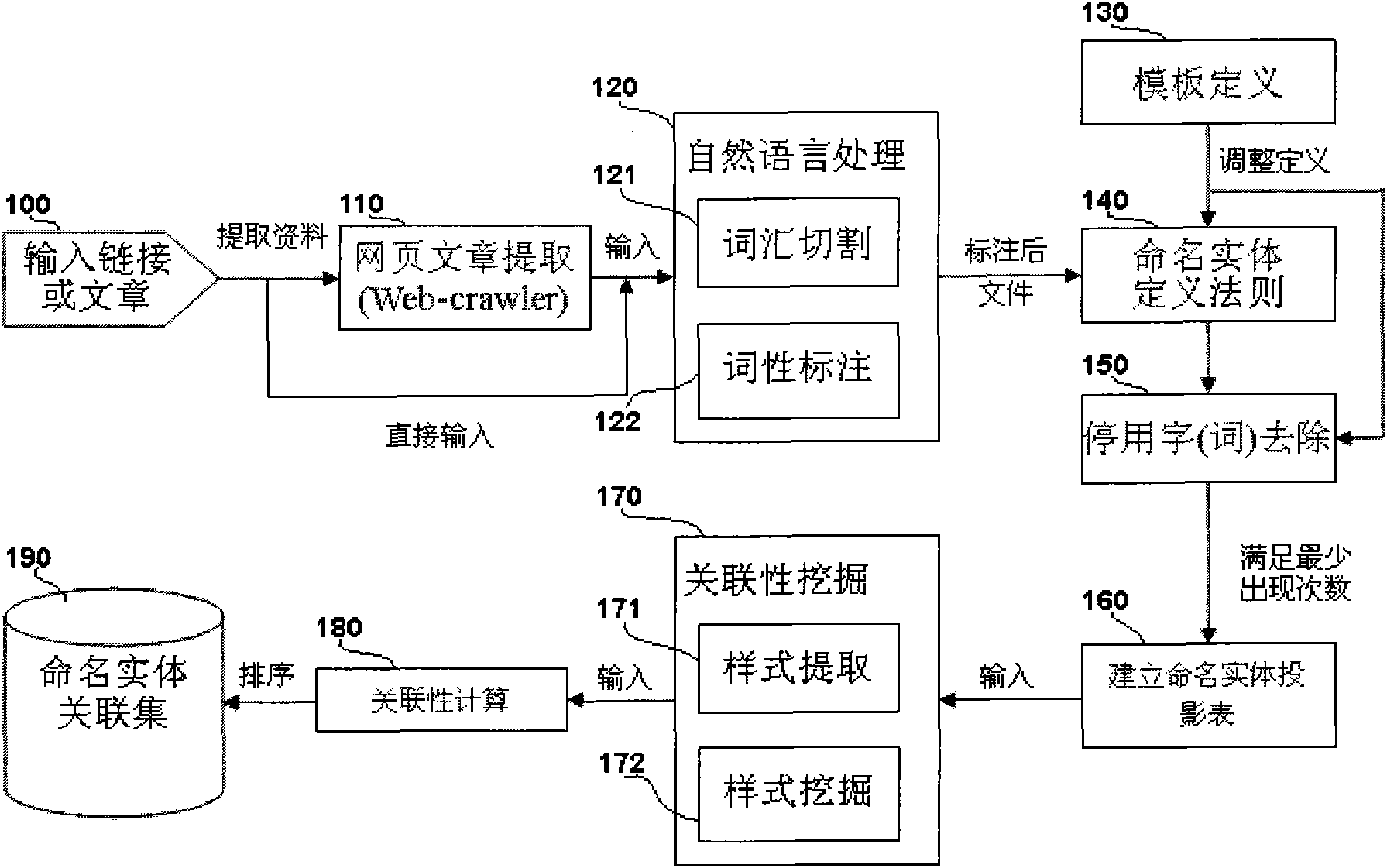
Mining method and system for correlation of vocabulary entities based on template
The invention provides a mining method and a system for correlation of vocabulary entities based on a template. The invention is characterized by defining according to part-of-speech styles predefined by a user, disused words and named entities, and mining and presenting the correlation styles meeting statistical independence or correlation by a sequential pattern mining method according to the correlation of various styles. Process detail regulation of the invention is parameterized, and can be defined and added to other file information such as time, date, source and the like according to the favor of a user; and the user can obtain highly relevant named entities or vocabulary relation styles in a designated fileset within a limit time.
Owner:吴毓杰 +1
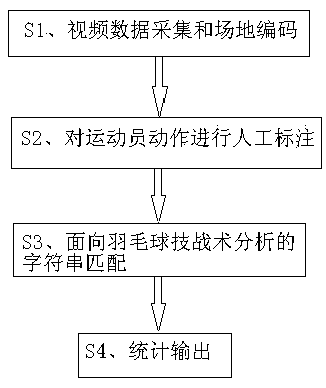
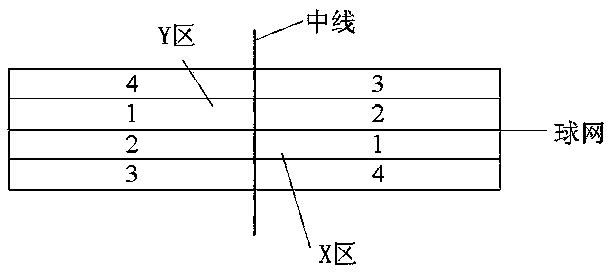
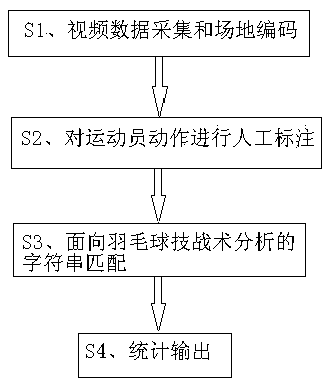
Badminton player technical and tactical analysis method based on sequence pattern mining
ActiveCN109977752ASimplified sports informationImprove technical and tactical levelCharacter and pattern recognitionOther databases queryingData acquisitionStatistical Output
The invention discloses a badminton player technical and tactical analysis method based on sequence pattern mining. The method comprises: S1, video data collection and site coding, S2, manual markingof athlete actions, S3, character string matching for badminton technical and tactical analysis, and S4, statistical output. According to the invention, an efficient badminton skill and tactical coding mode is adopted to mark an input badminton match motion video; and carrying out matching analysis on the manually marked character string data adopted by each score of the athlete to be analyzed inthe acquired competition video and the code of each key technique and tactics by utilizing a character string matching method. Then the badminton technical and tactics frequently used by the athlete is determined according to the occurrence frequency of the code of the preset key skill and tactics in the action of the score point of the athlete to be analyzed. The method is helpful for badminton players to know the technical advantages of the badminton players, so that the technical and tactical level of the badminton players is improved, and the technical and tactical analysis before and after the competition and the technical and tactical summary after the competition of coach teams are of great significance.
Owner:DALIAN UNIV OF TECH
Pattern discovery through reversing time flow
InactiveUS7945572B2Facilitate automated discoveryData processing applicationsDigital data information retrievalReverse timeSequential Pattern Mining
The present invention provides systems and methods for automatically mining massive intelligence databases to discover sequential patterns therein using a novel combination of forward and reverse temporal processing techniques as an enhancement to well known pattern discovery algorithms.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
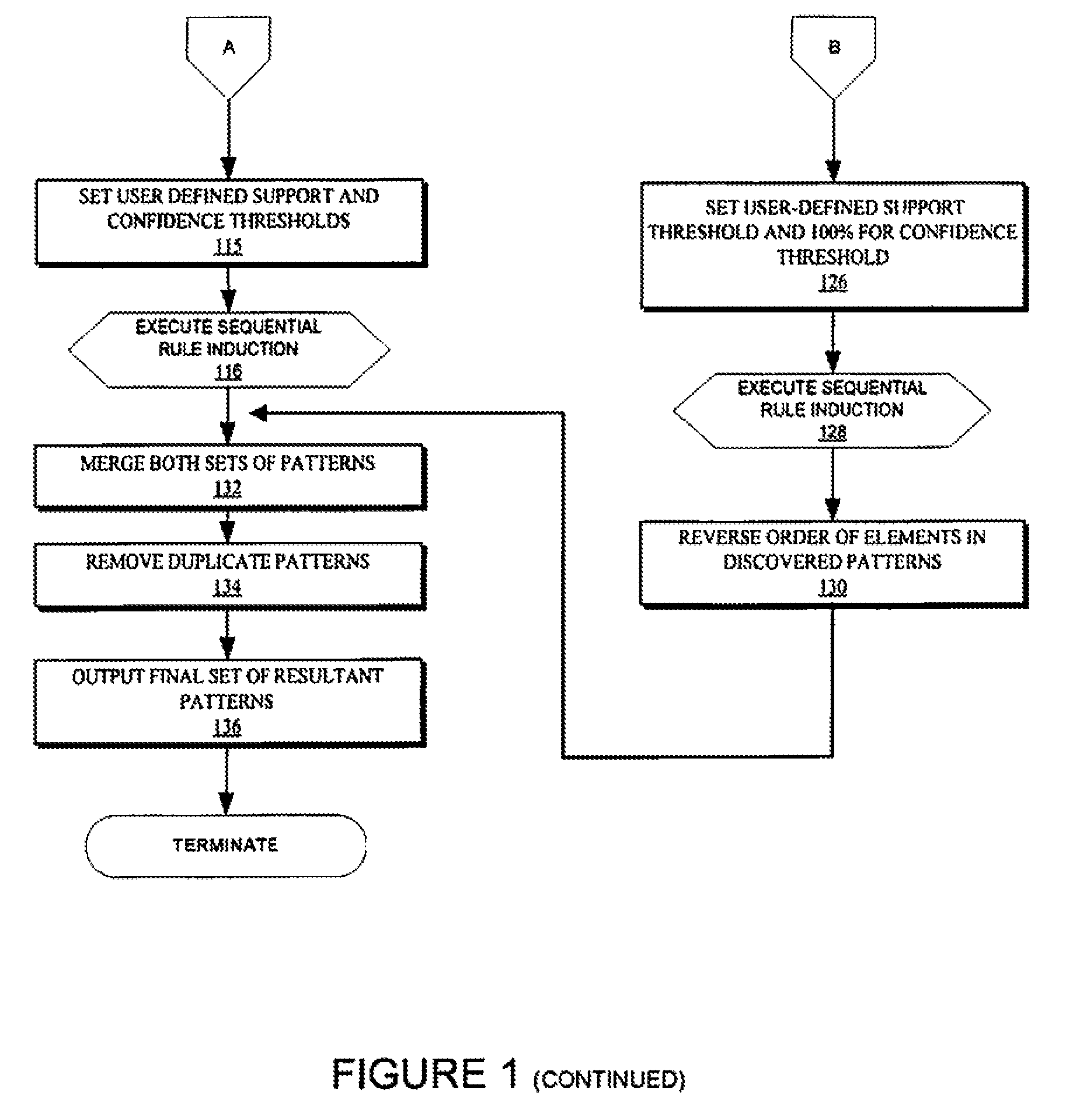
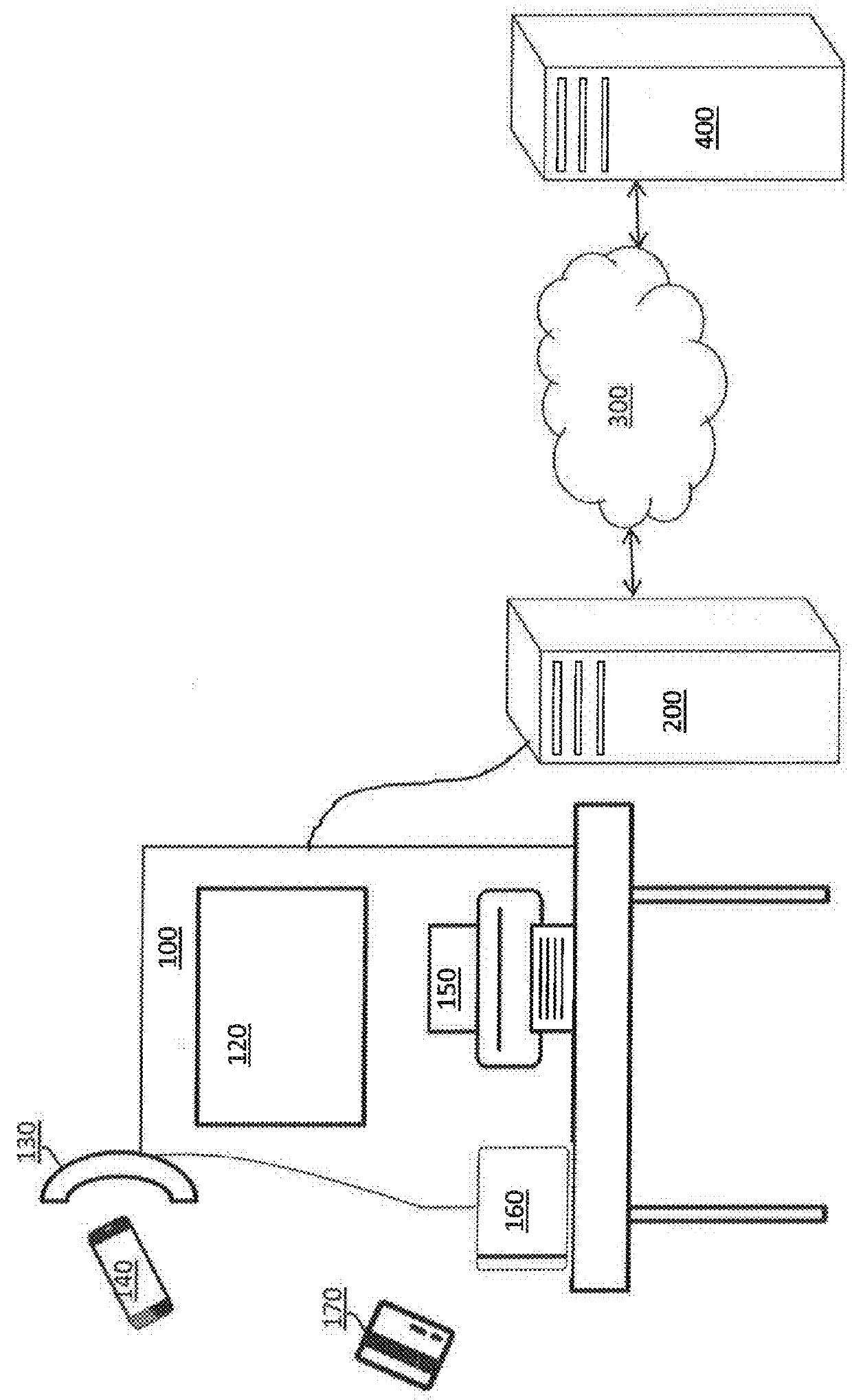
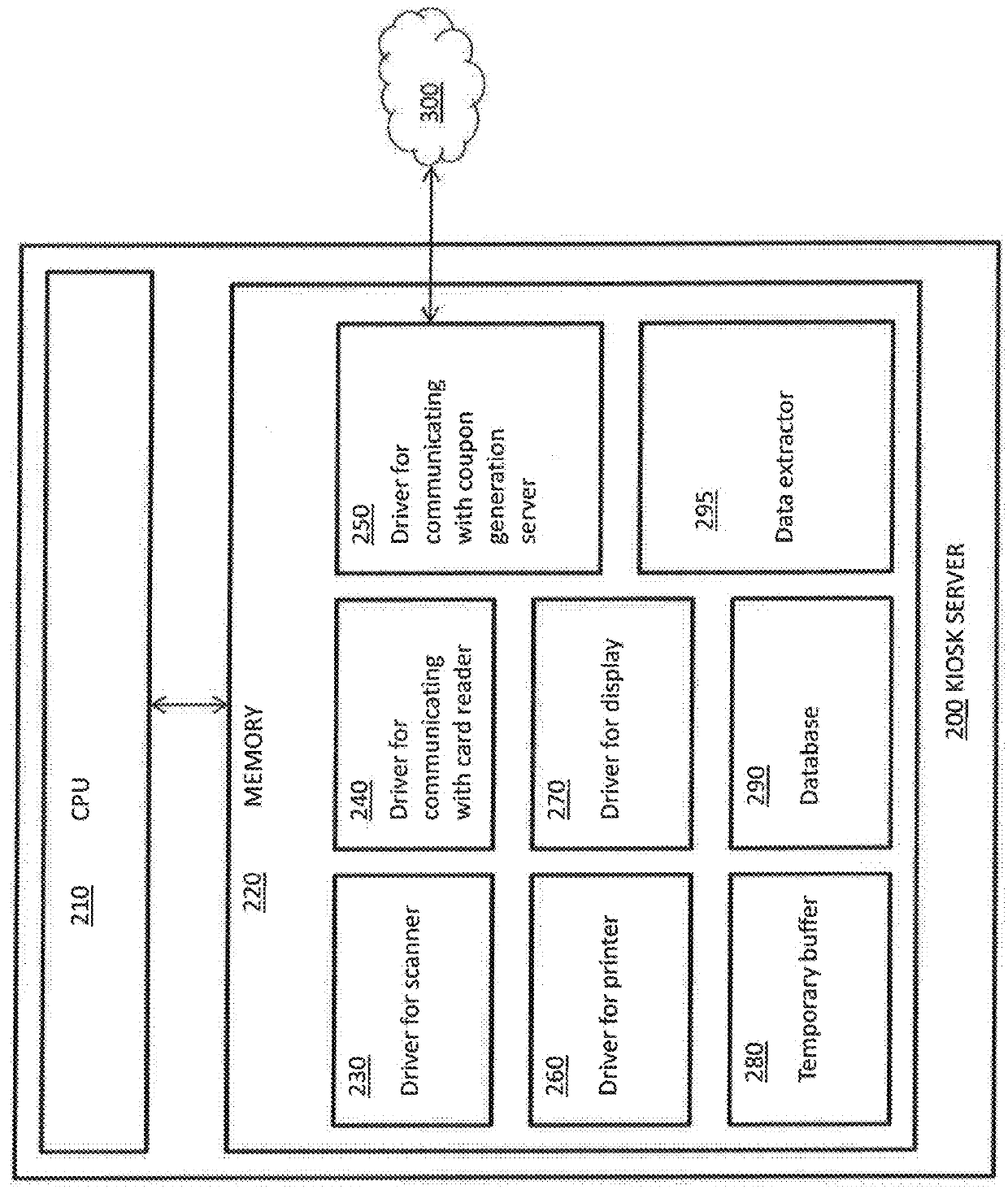
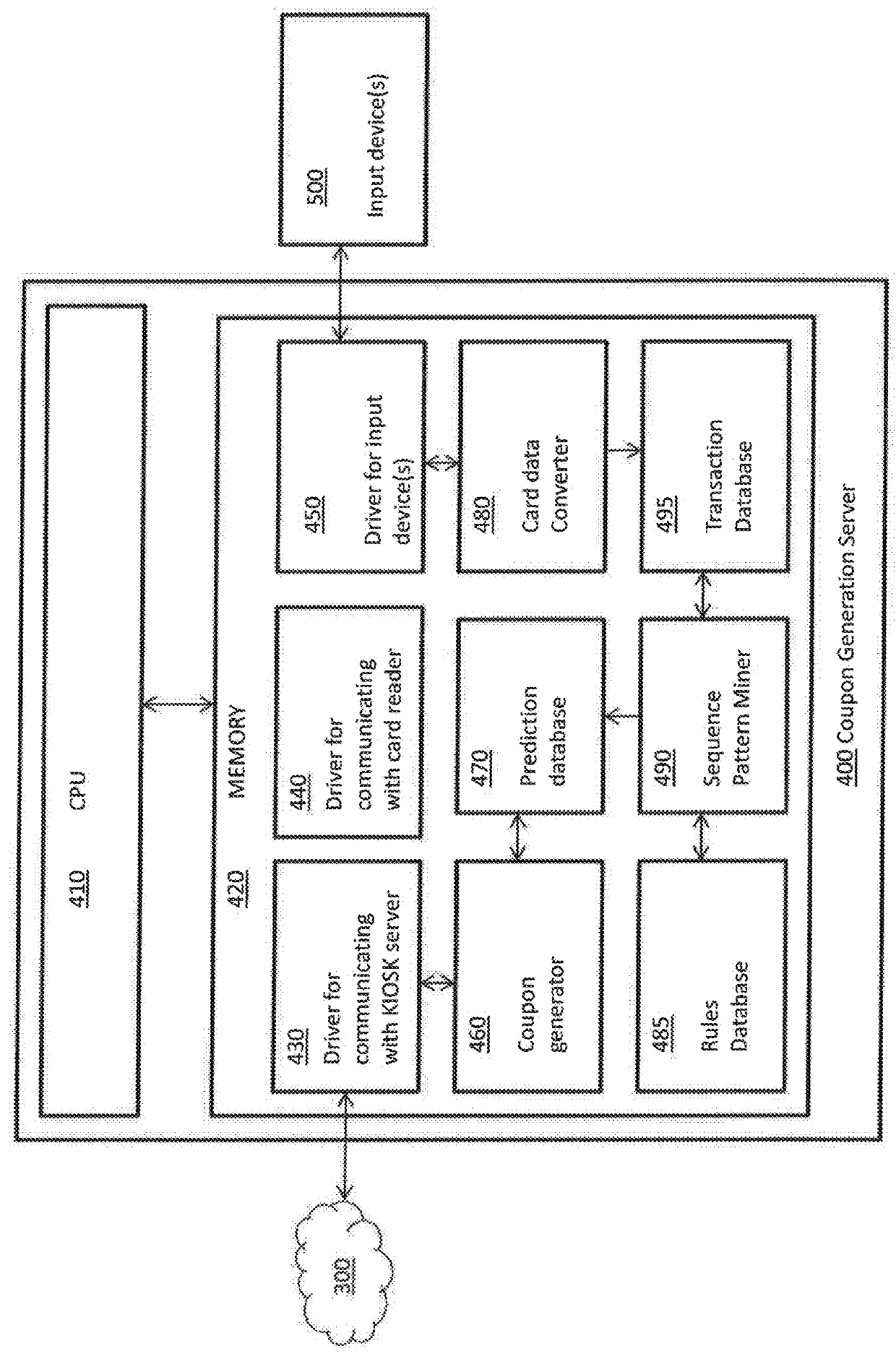
System for predicting future purchase using sequence pattern mining of credit/debit data
A system for managing generation of an electronic coupon (eCoupon) includes a terminal configured to process a credit / debit card to determine a card number of the credit / debit card; and computer server configured to generate a plurality of transactions from a pool of credit / debit card data, perform sequence pattern mining on the transactions to determine a sequence likely to result in an amount of spending in a pre-defined spending category within a subsequent period of time that exceeds a pre-defined spend threshold, receive the card number across a computer network from the terminal, and generate the eCoupon when existing purchases by the card number include the sequence.
Owner:AFFINITY SOLUTIONS INC
An energy consumption evolution optimization method during GCC compiling based on frequent pattern mining and storage device
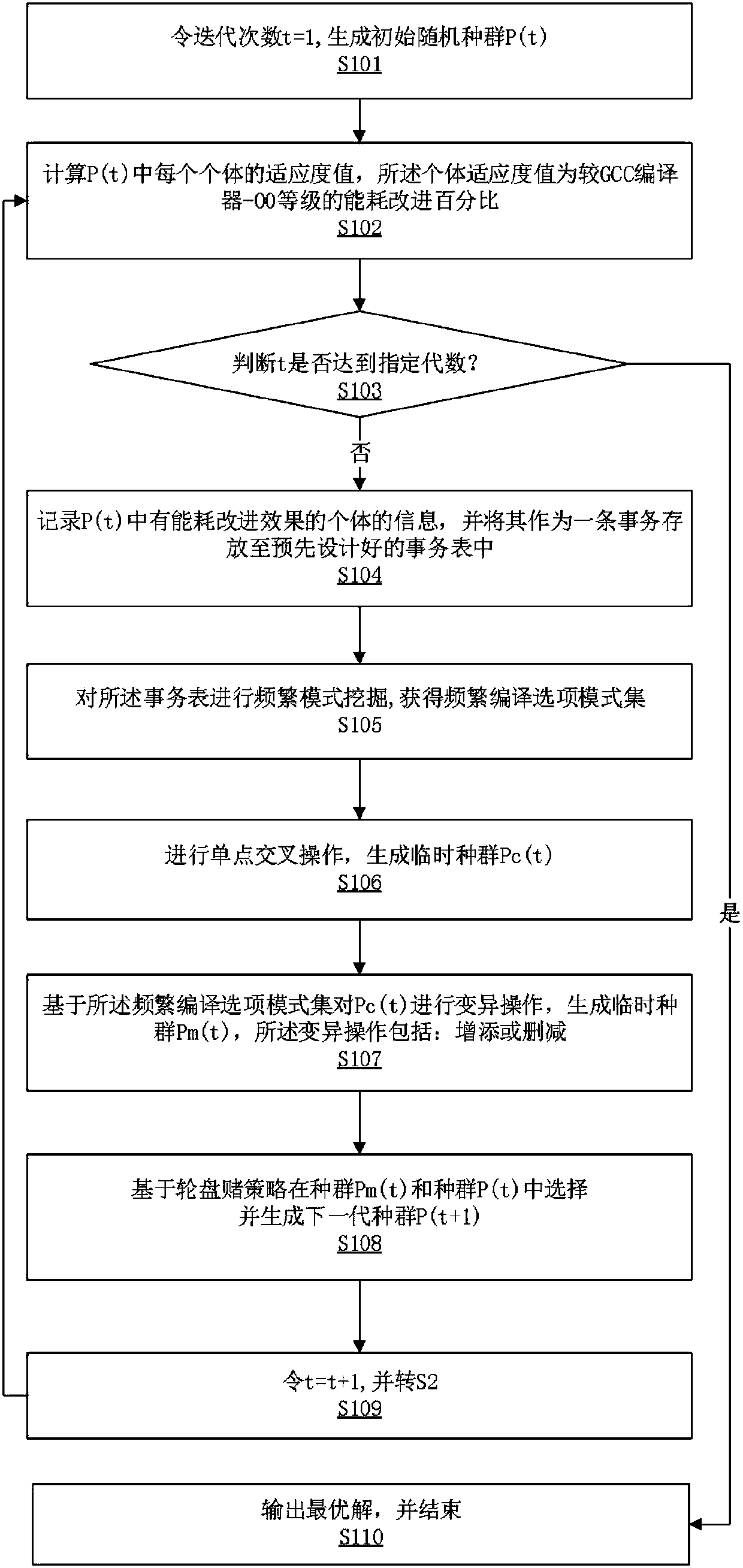
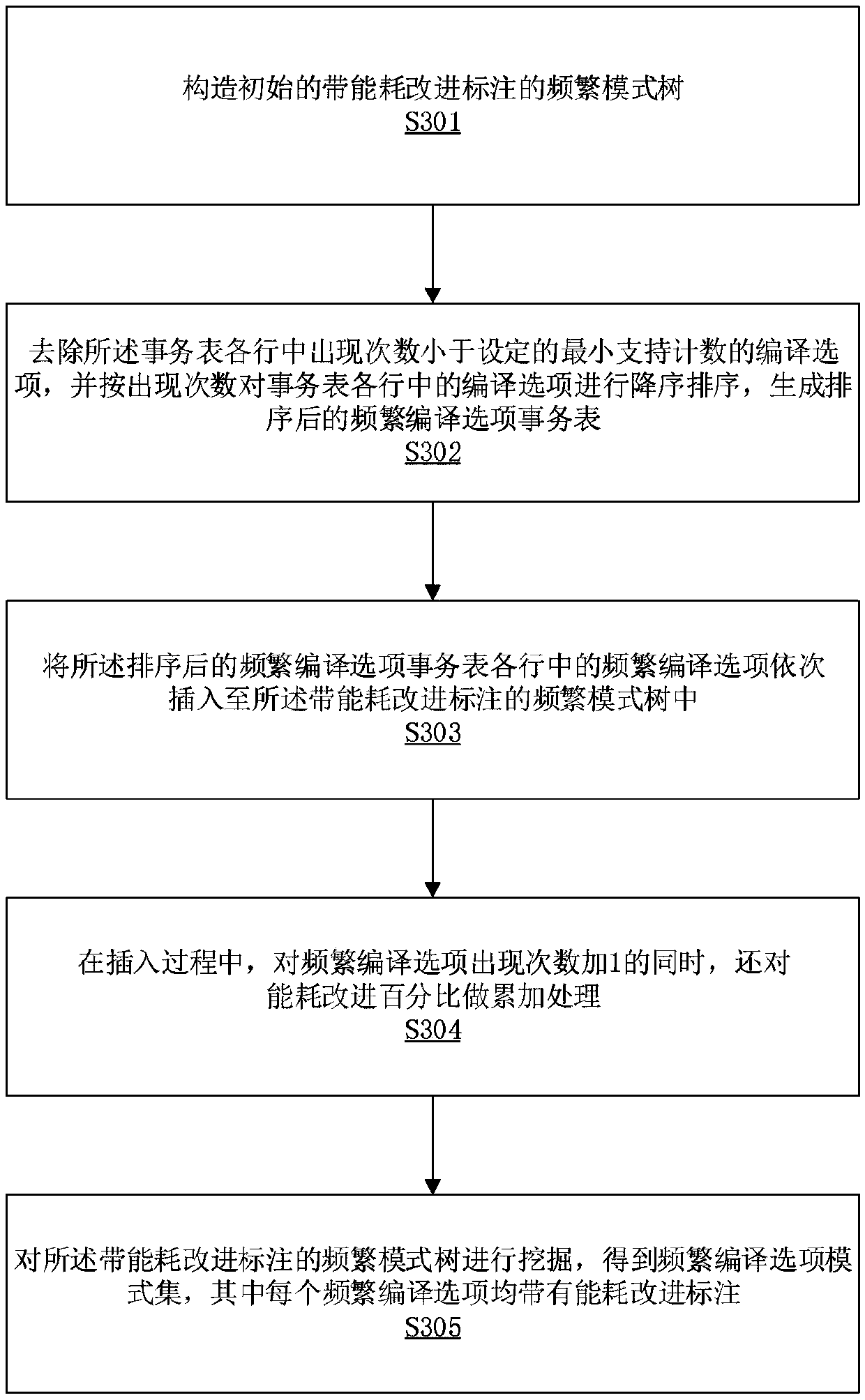
InactiveCN109669698AImprove solution qualityFast convergenceCode compilationInformation processingTemporary population
The invention relates to the technical field of information processing, in particular to an energy consumption optimization method based on frequent pattern mining. The energy consumption optimizationmethod based on frequent pattern mining comprises the following steps of S1 generating an initial random population P (t); S2 calculating the fitness value of each individual in P (t); S3 if t reaches a specified algebra, turning to S4; S4 recording information of individuals with an energy consumption improvement effect in the P (t), and storing the information as a transaction in a pre-designedtransaction table; S5 generating a temporary population Pc (t), and performing frequent pattern mining on the transaction table to obtain a frequent compilation option pattern set; S6 performing mutation operation on the Pc (t) based on the frequent compilation option mode set to generate a temporary population Pm (t); and S7 selecting and generating a next generation of population P (t+1) from the population Pm (t) and the population P (t) based on a roulette strategy. In this way, the mutual influence possibly existing between different compiling options is fully considered, and the solution quality can be improved, and the convergence speed can be increased.
Owner:FUZHOU SANXINLONG CASTING +1
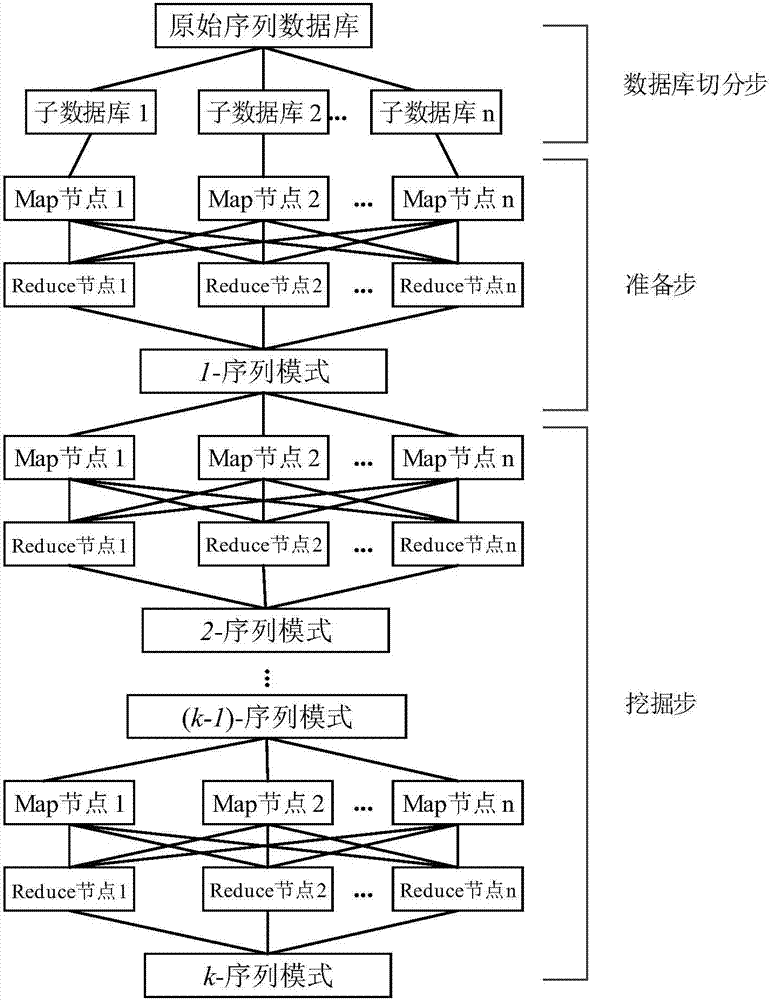
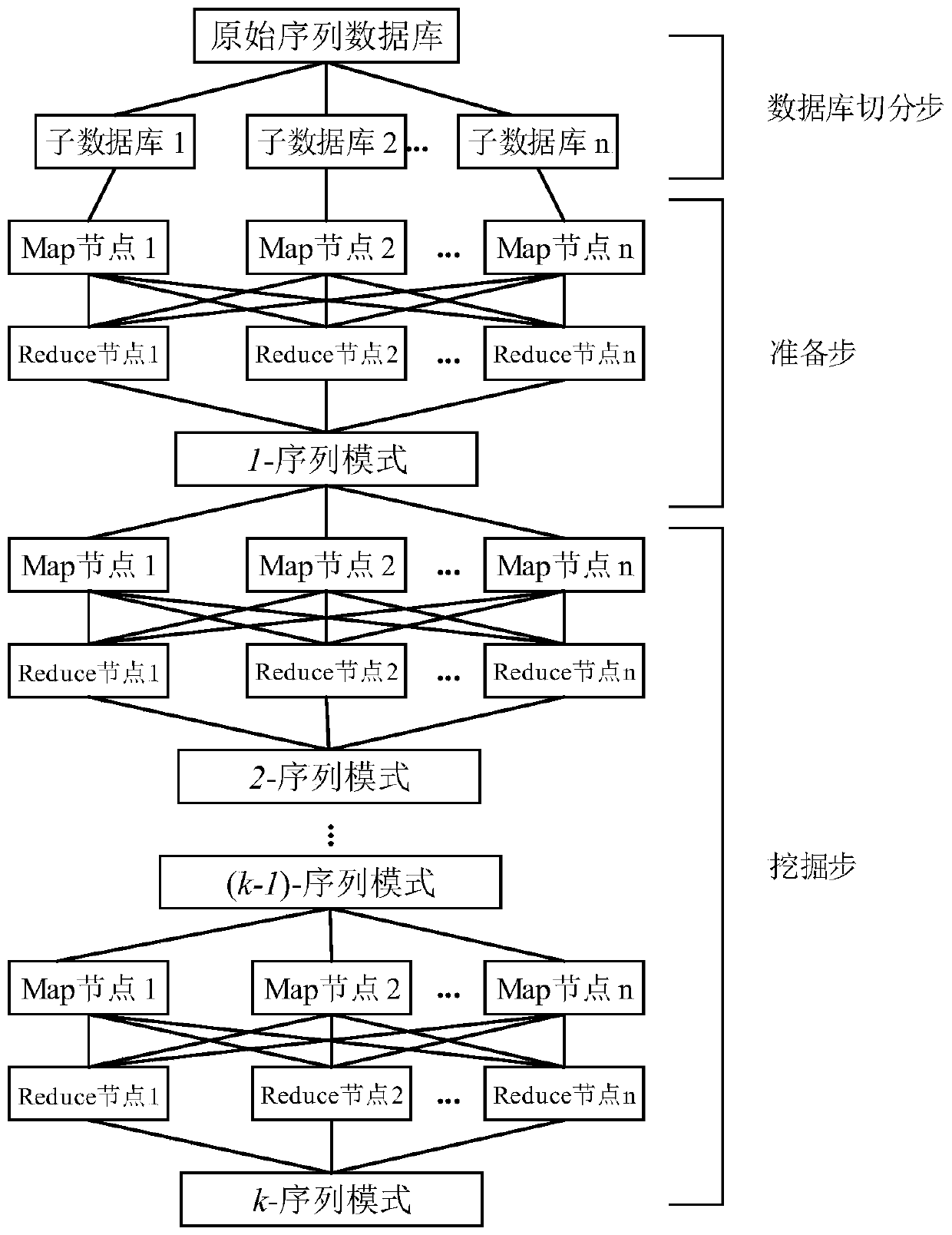
Spark platform-based parallel sequential pattern mining method
InactiveCN107145548AImprove digging efficiencySolve the problem of load imbalanceSpecial data processing applicationsTheoretical computer scienceGSP Algorithm
The invention discloses a Spark platform-based parallel sequential pattern mining method. Aiming at the problem of conventional serial sequential pattern mining algorithms that the computing power is inefficient when massive data is processed, and the problems of conventional Hadoop-based parallel sequential pattern mining algorithms that the IO (Input / Output) overhead is high and the load is unbalanced, the method has the characteristics that a reasonable sequential database decomposing strategy is designed, and the problem of unbalanced load is solved to the maximum limit; and on the basis of the characteristics of a MapReduce programming frame, primal GSP (Generalized Sequential Pattern) algorithms are paralleled, and the massive data sequential pattern mining efficiency is increased by utilizing the large-scale parallel computing power of a Spark cloud computing platform.
Owner:WUHAN UNIV
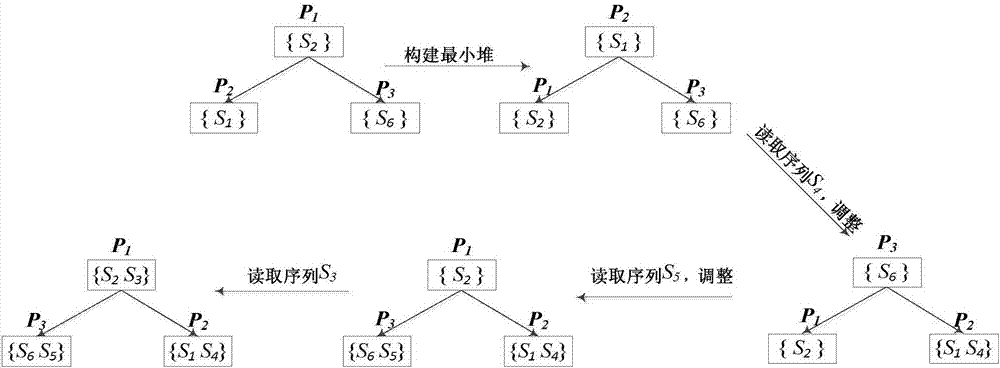
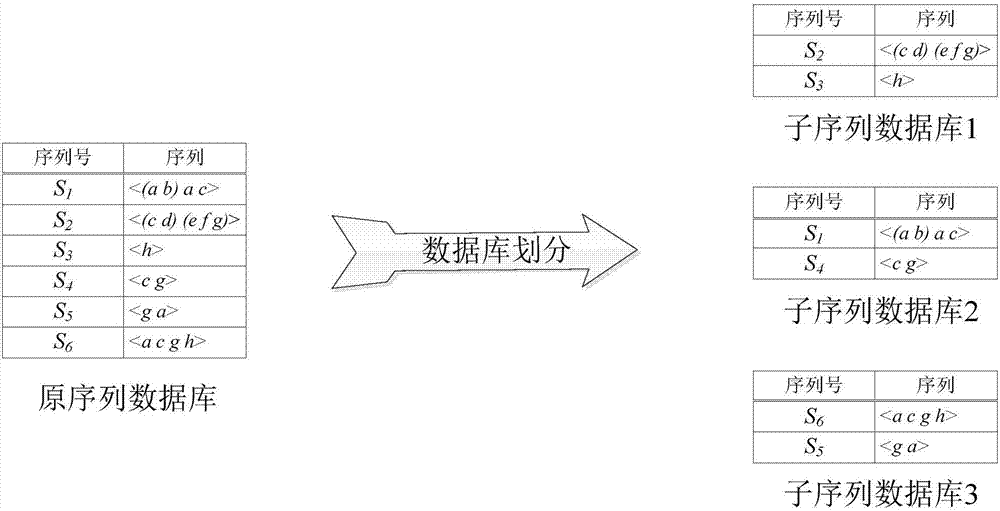
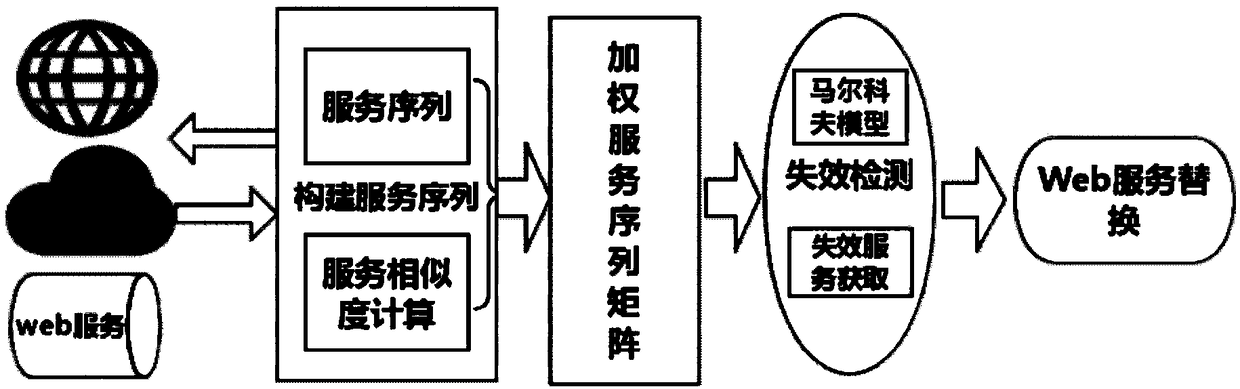
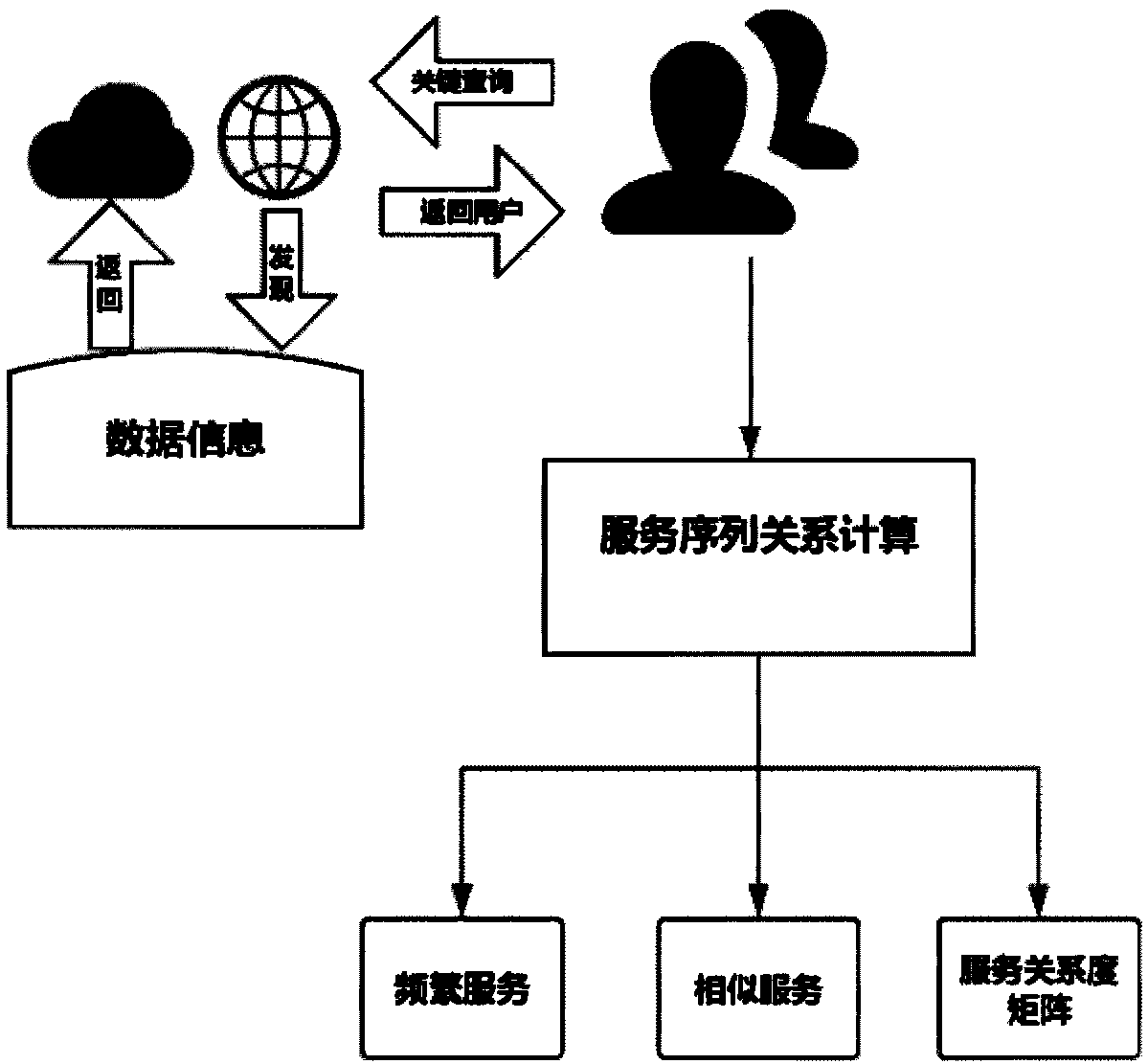
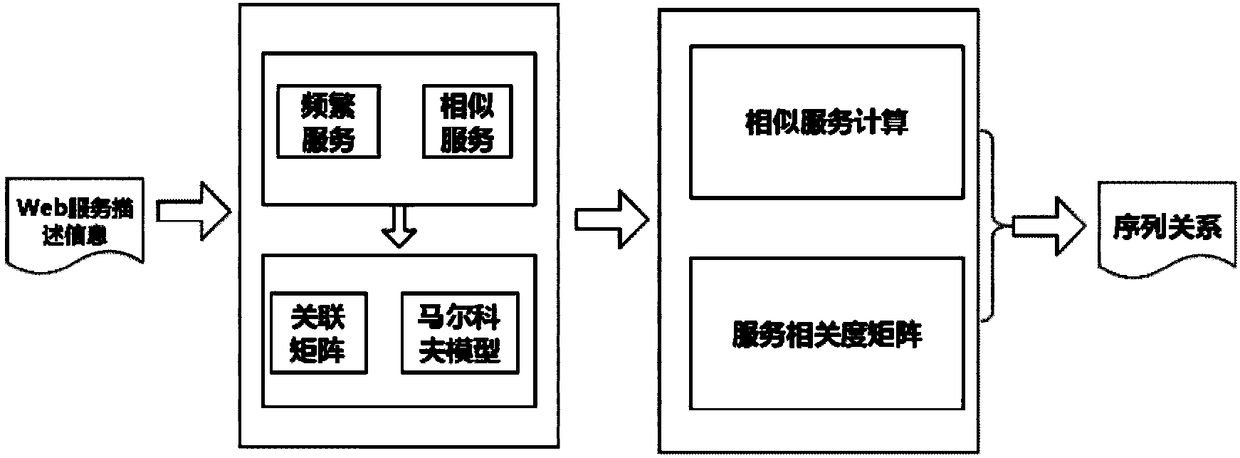
Web service replacing method based on weighted sequence relation
ActiveCN108470181AAccurate and efficient replacementImprove service efficiencyCharacter and pattern recognitionResourcesConfidence intervalWeb service
The invention discloses a Web service replacing method based on a weighted sequence relation. The method comprises the following steps of acquiring a service set from the interaction information of aWeb service and calculating and acquiring a service sequence; according to the calculated service set, a service similarity in the service sequences of subsets and a calculated service sequence probability, acquiring a frequent service sequence; constructing a correlation matrix formed by the frequent service sequence and a preset similar service sequence, carrying out weighted processing on the frequent service sequence in the matrix so as to obtain a weighted service sequence, and normalizing the weighted service sequence; and using a sequential pattern mining model to mine the normalized weighted service sequence, calculating the confidence of the preset similar service sequence in the weighted service sequence to the frequent service sequence, acquiring a confidence interval and takingas the selection range of a replaceable service, and selecting the replaceable service and executing replacing. In the invention, service similarity matrix model construction is added into a servicereplacing process so that a replacing service query target is increased and service replacing efficiency is improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
A Parallel Sequential Pattern Mining Method Based on Spark Platform
InactiveCN107145548BImprove digging efficiencySolve the problem of load imbalanceDatabase updatingSpecial data processing applicationsTheoretical computer scienceGSP Algorithm
The invention discloses a Spark platform-based parallel sequential pattern mining method. Aiming at the problem of conventional serial sequential pattern mining algorithms that the computing power is inefficient when massive data is processed, and the problems of conventional Hadoop-based parallel sequential pattern mining algorithms that the IO (Input / Output) overhead is high and the load is unbalanced, the method has the characteristics that a reasonable sequential database decomposing strategy is designed, and the problem of unbalanced load is solved to the maximum limit; and on the basis of the characteristics of a MapReduce programming frame, primal GSP (Generalized Sequential Pattern) algorithms are paralleled, and the massive data sequential pattern mining efficiency is increased by utilizing the large-scale parallel computing power of a Spark cloud computing platform.
Owner:WUHAN UNIV
Repeated data deletion framework-based reverse index representation method and system
ActiveCN106202154AEffectively deleteIncrease the compression ratioSpecial data processing applicationsReverse indexDocument preparation
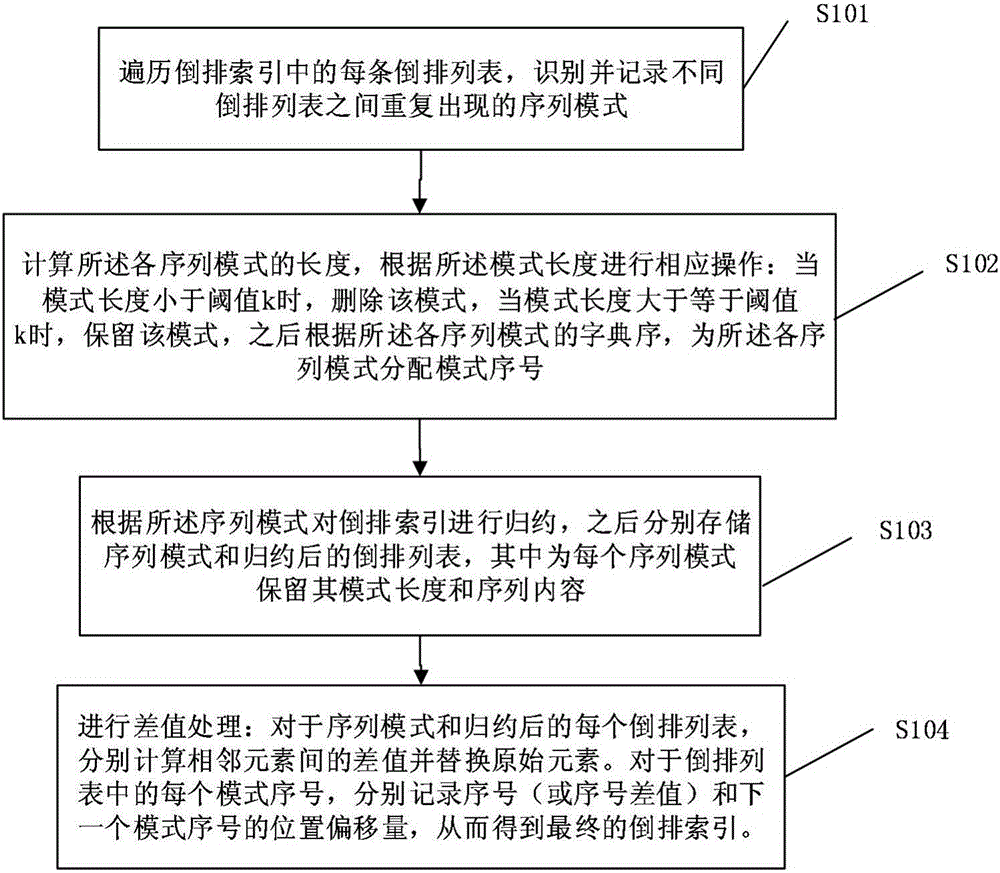
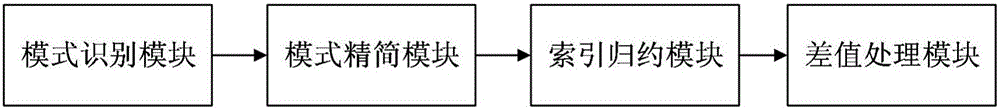
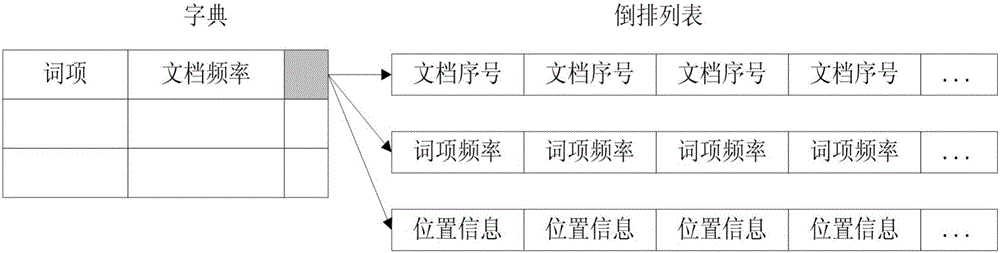
The invention discloses a repeated data deletion framework-based reverse index representation method and system, and the method and system are suitable for search engines and social network data processing. The method comprises the following steps of: 1, traversing reverse lists in reverse indexes, and recognizing and recording sequential patterns which repeatedly emerge between different reverse lists; 2, calculating the length of each sequential pattern, carrying out corresponding operations according to the lengths, and distributing a mode serial number for each sequential pattern according to a lexicographical order of the sequential patterns; 3, reducing the reverse indexes according to the sequential patterns, and respectively storing the sequential patterns and the reduced reverse lists; and 4, difference value processing: carrying out difference value calculation on adjacent document serial numbers in the sequential patterns, and recording pattern serial numbers and position offsets of adjacent pattern serial numbers, wherein the pattern serial numbers are expressed as two-tuples. The method and system disclosed by the invention can effectively delete the repeated data in the reverse indexes, thereby decreasing the amount of the document serial numbers, improving the compression rate of the reverse indexes, shortening the query response time of the search engines and improving the user experience.
Owner:NANKAI UNIV
A system and method for predicting tobacco insect status
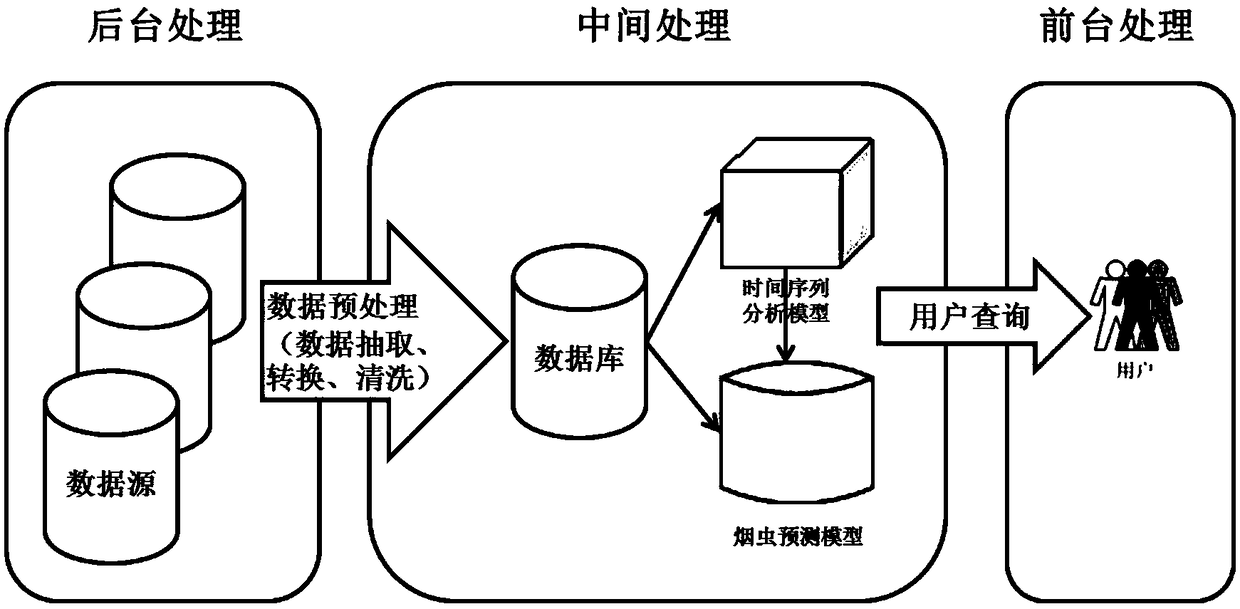
InactiveCN109213800AAchieving Trend ForecastingData processing applicationsDigital data information retrievalBusiness forecastingBiology
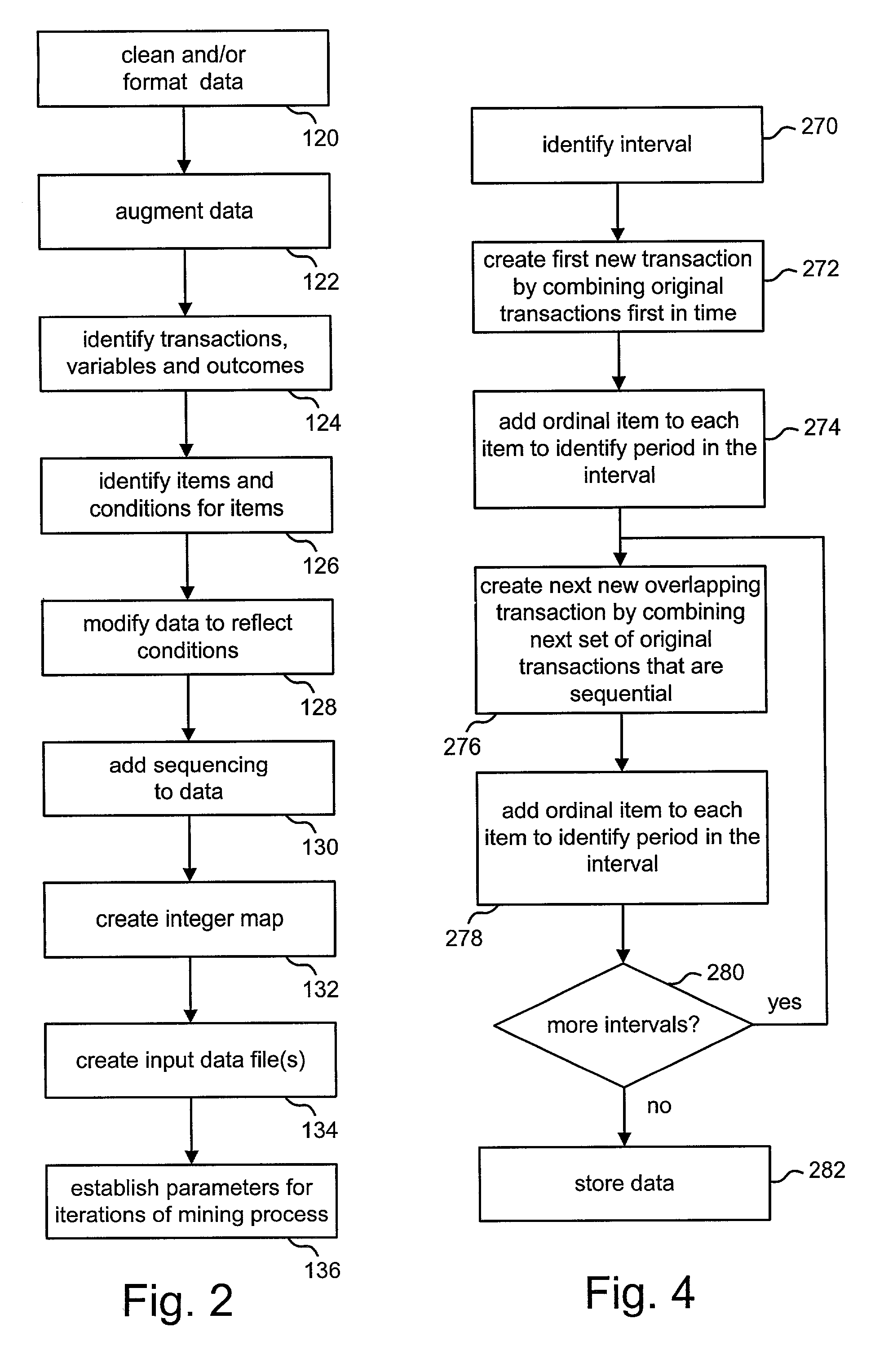
The invention discloses a tobacco insect situation forecasting method and a tobacco insect situation forecasting system. The tobacco insect situation forecasting method and the tobacco insect situation forecasting system preprocess the tobacco insect situation data by acquiring data. Constructing time series analysis model to form tobacco pest prediction model; mining the sequential pattern of insect situation and obtaining the prediction result. The invention can discover frequent patterns and predict the quantity of insect conditions through the sequential pattern mining technology.
Owner:CHINA TOBACCO SHANDONG IND
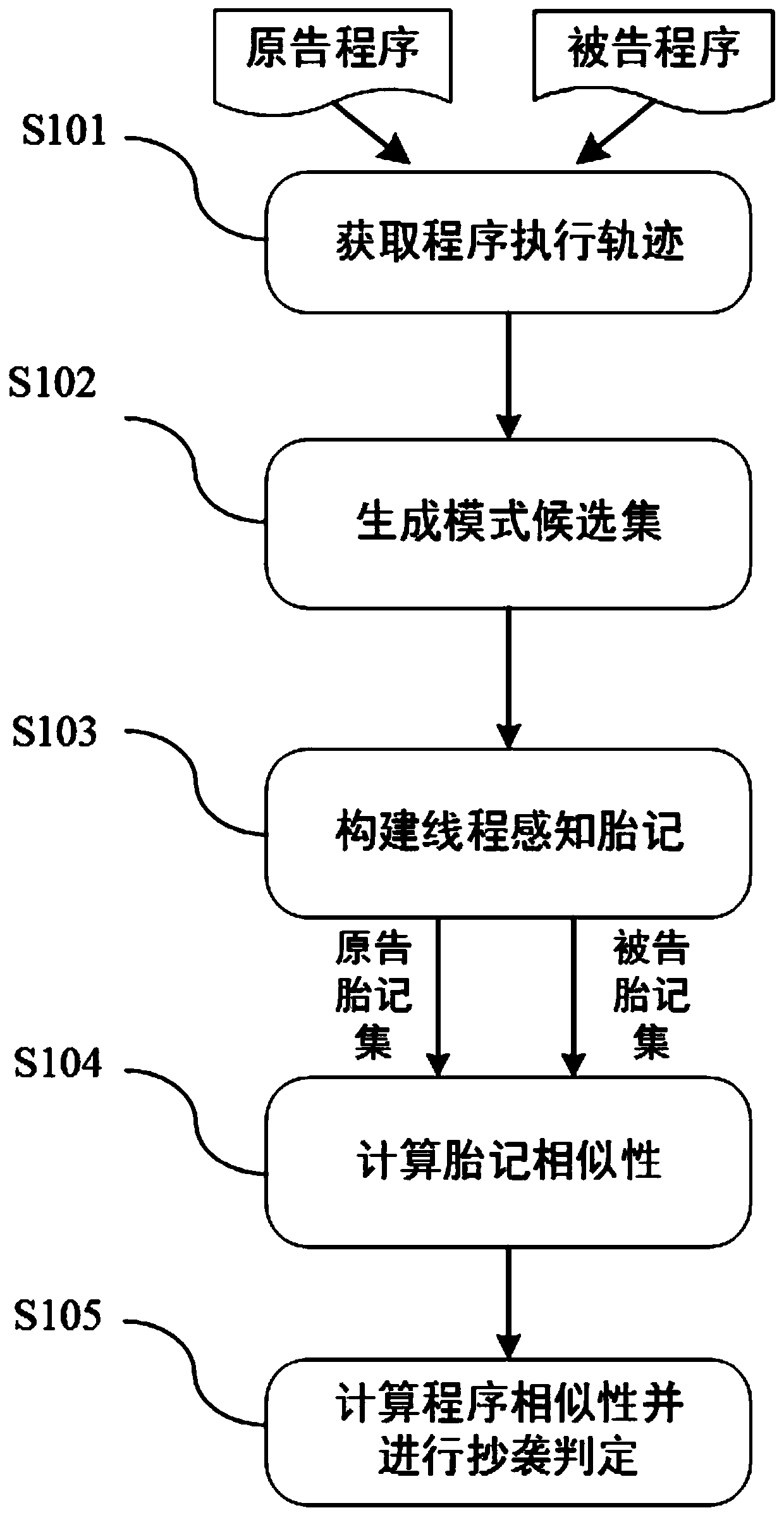
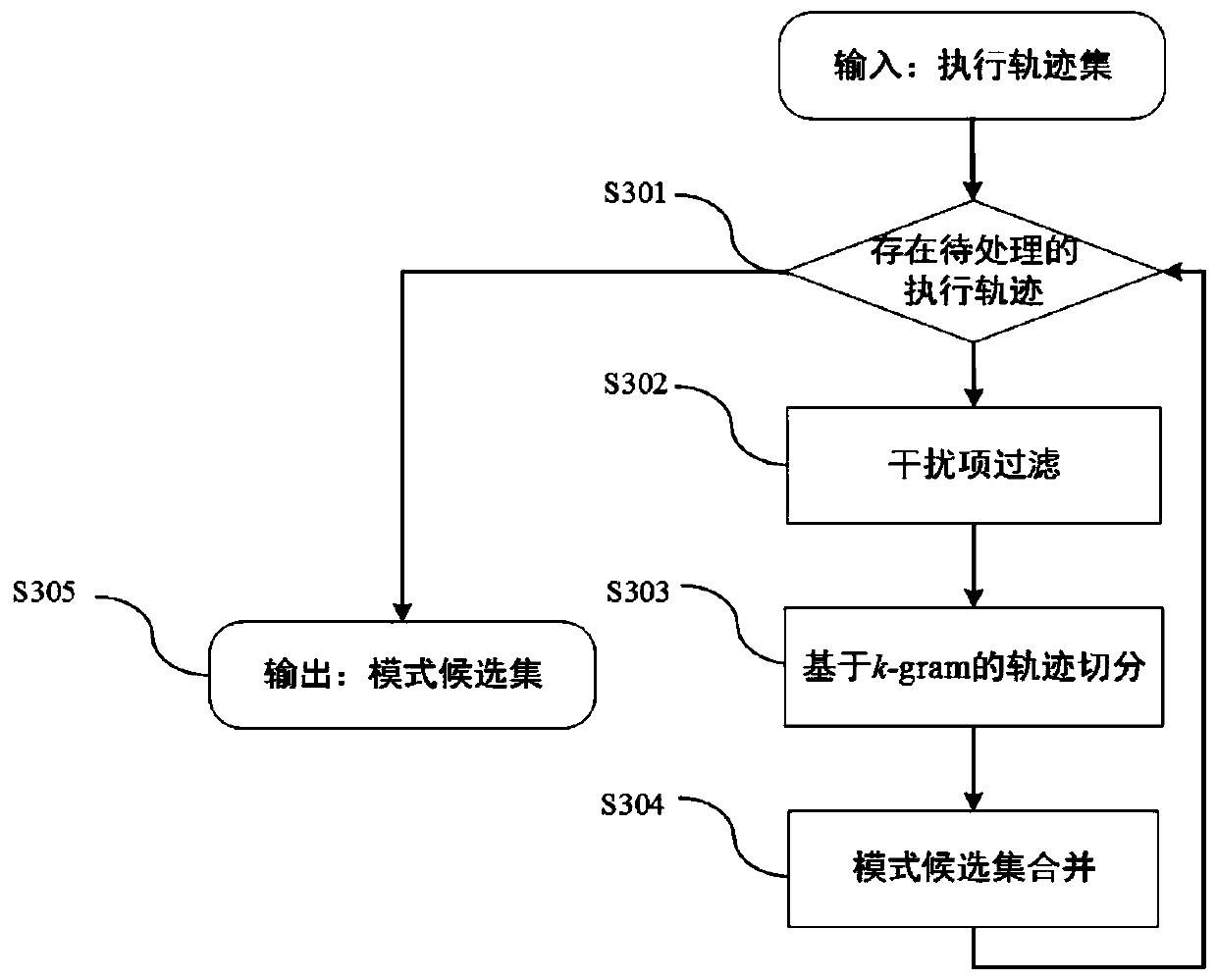
Multi-thread program plagiarism detection method based on frequent pattern mining
ActiveCN110532739AObfuscation worksEffective handling of obfuscation meansProgram/content distribution protectionPlagiarism detectionTheoretical computer science
The invention discloses a multi-thread program plagiarism detection method based on frequent pattern mining. The method comprises the following steps: 1) dynamically monitoring to obtain a plurality of execution tracks of a program under the condition of multiple times of execution of the same input; 2) preprocessing the program execution trajectory set to generate a mode candidate set; 3) utilizing a frequent pattern mining algorithm to process the pattern candidate set, generating a frequent pattern set, performing Hash processing, and then constructing a thread perception birthmark; 4) calculating the similarity between the original announcement program birthmarks and the announced program birthmarks under specific input; and 5) making plagiarism judgment and outputting a detection result based on the mean value of the birthmark similarity under the plurality of inputs and a given threshold value. According to the method, the executable program is directly used as an analysis object, and program source codes are not needed; according to the method, frequent pattern mining is utilized to extract a behavior pattern from a plurality of execution tracks corresponding to multiple times of program operation under the same input to generate a thread perception birthmark, so that the interference of thread interleaving uncertainty is greatly reduced.
Owner:XIAN UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com