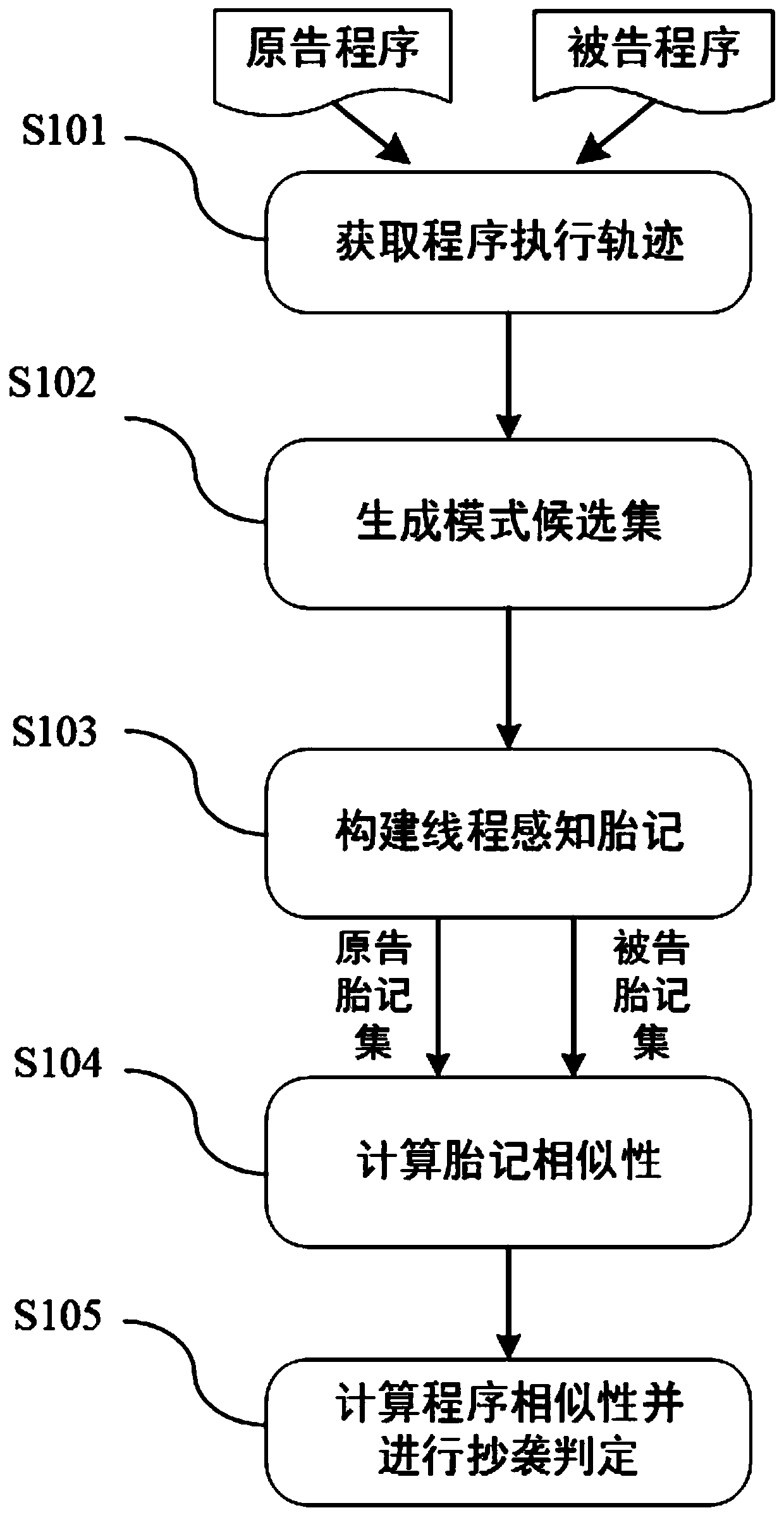
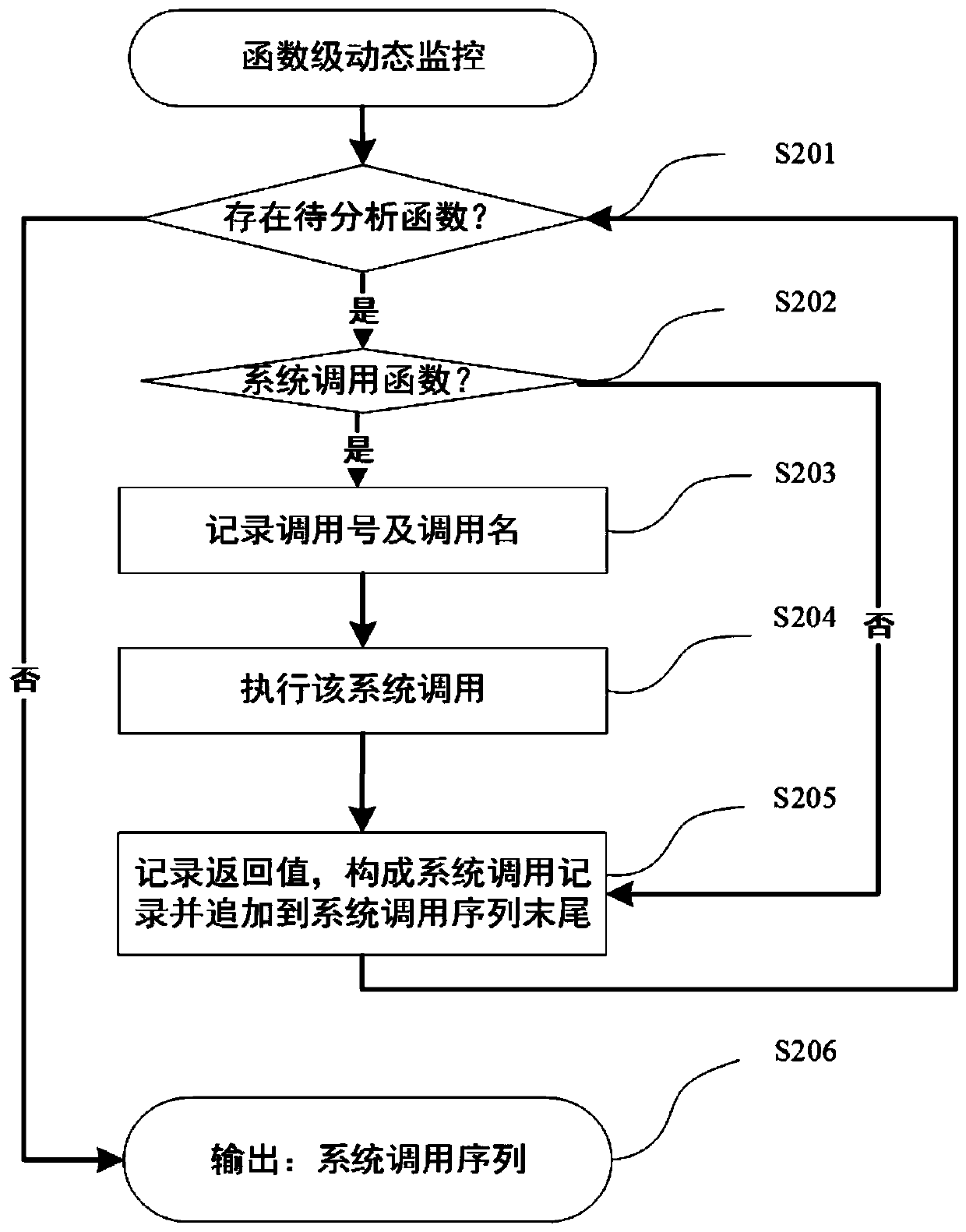
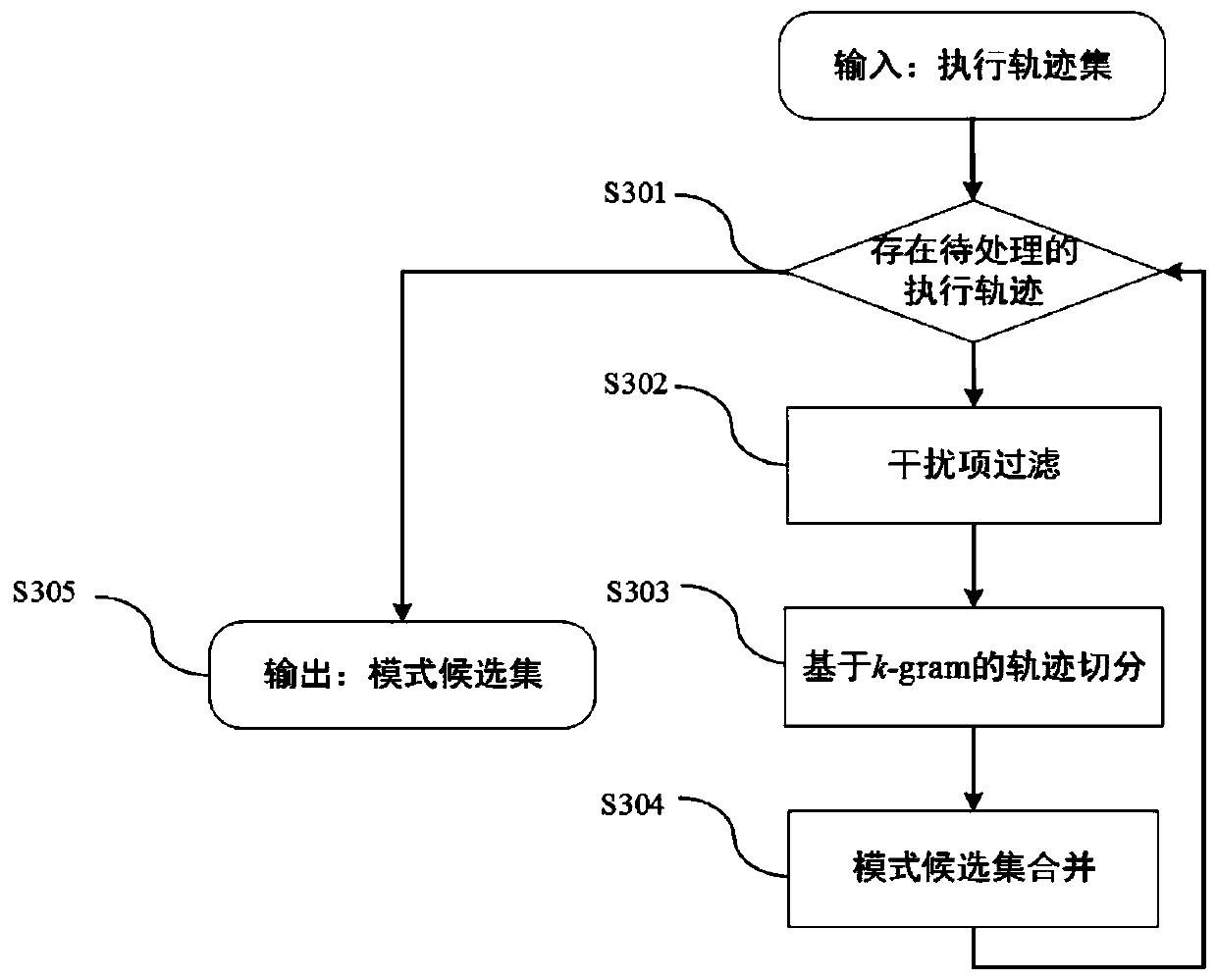
Multi-thread program plagiarism detection method based on frequent pattern mining
A technology of frequent patterns and detection methods, applied in the direction of program/content distribution protection, etc., to achieve the effect of reducing interference
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0069] Example 1: Assume that program p is at some input I 1 The following has been executed twice, and the execution trajectories after filtering by interference items are and Among them, respectively use I 1 1 and I 1 2 Indicates that the program is inputting I 1 The first execution and the second execution under.
[0070] Assuming that the value of τ is 3 (only for the convenience of expression, the actual value is preferably between 8-10), then, for the trajectory of the first execution After processing in step S303, the pattern candidate set (allowing elements to be repeated) of the execution track is obtained as follows:
[0071]
[0072] Similarly, the trajectory corresponding to the second execution The pattern candidate set for is:
[0073]
[0074] Then, program p at some input I 1 The set of schema candidates (allowing element repetitions) under is:
[0075]
[0076] Step S103: use the frequent pattern mining algorithm to process the candidat...
Embodiment 2
[0083] Embodiment 2: Assume that according to step S401, for the program p in embodiment 1 in a certain input I 1 After processing the pattern candidate set below, the obtained frequent pattern set is:
[0084]
[0085] Further according to the flow described in steps S401-S405, obtain the program p in a certain input I 1 The thread-aware birthmark under:
[0086]
[0087] Step S104: given the plaintiff program p and the defendant program q under the input I thread sense birthmark and The formula (1) is used to realize the calculation of birthmark similarity:
[0088]
Embodiment 3
[0089] Example 3: For another program q, assume that at input I 1 The frequent pattern extracted according to steps S101-S103 is The resulting thread-aware birthmark is:
[0090] Then, program q and program p in Example 2 are input I 1 The similarity of the software birthmark under is:
[0091]
[0092] Step S105: The dynamic birthmark is related to the input, which is an abstraction of the semantics and behavior of the program under a specific input, and the judgment result made only by a single input is not reliable. In this regard, multiple different inputs are provided and steps S101-S104 are repeated to sequentially obtain the similarity of the birthmarks of the plaintiff and defendant programs under corresponding inputs, and take the mean value of the similarity as the similarity of the plaintiff and defendant programs. Specifically, formula (2) is used to calculate program similarity:
[0093]
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com