Method for achieving code obfuscation through finite automaton
A technology of code obfuscation and code, applied in the field of computer programs, to achieve the effect of increasing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0015] Example 1: Such as figure 1 , figure 2 , image 3 , Figure 4 As shown, a method of using finite automata to achieve code obfuscation is not limited to the past obfuscation methods and then a little innovation, changing the soup without changing the medicine, but based on the new language features provided by C++11\14, using a A brand-new way and cooperating with finite automata for code obfuscation, not only improves efficiency but also is easy to implement.
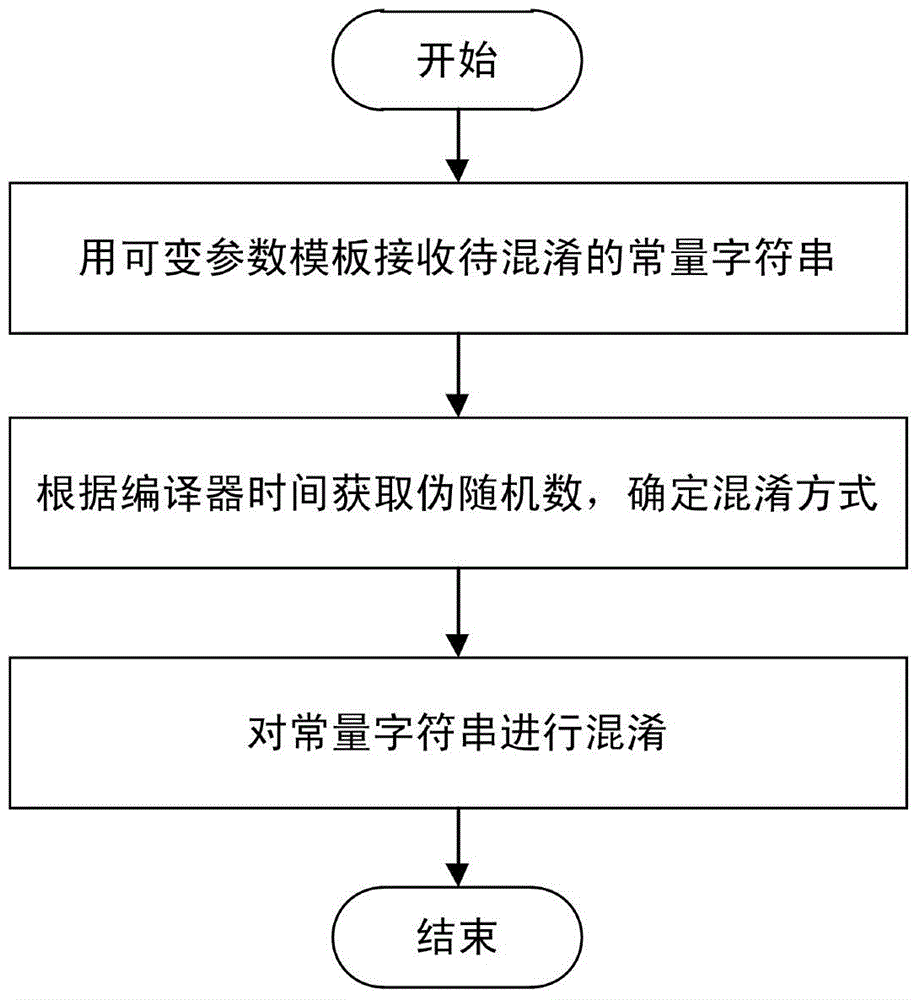
[0016] By using the new features provided by the C++11\14 language standard, the template meta-programming feature of the compiler is used to realize a variety of obfuscators, including hidden string obfuscators, non-explicit call function obfuscators, and automatic The machine model performs various debugging and identification functions, and then realizes the protection of software or special code fragments.
[0017] A method for implementing code obfuscation using finite automata, including the following technica...
Embodiment 2
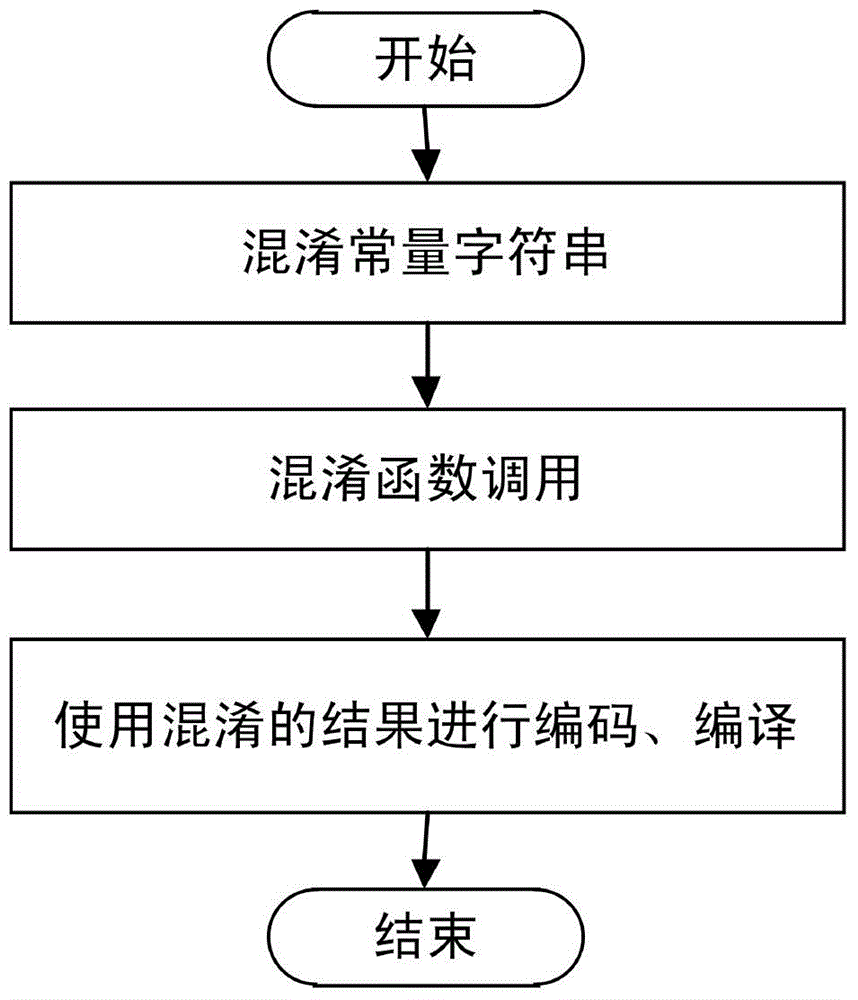
[0036] Example 2: Such as figure 1 , figure 2 , image 3 , Figure 4 As shown, a method for implementing code obfuscation using finite automata includes the following steps:
[0037] Step 1. Obfuscate the constant string; for the constant string A in the program source code to be obfuscated, perform the following steps:
[0038] Step 1-1: Randomly select one of the preset encryption methods as the encryption method for the constant string A; among them, the preset encryption method needs to meet the symmetric encryption; this step should occur in the program compilation process, That does not affect the operating efficiency of the program;
[0039] Step 1-2: Use a time-based pseudo-random number algorithm to generate a random number K. The value K is used as the key used in the encryption method selected in step 1-1 to participate in the encryption of the constant string A; this step should happen In the process of program compilation, that does not affect the operating efficiency...
Embodiment 3
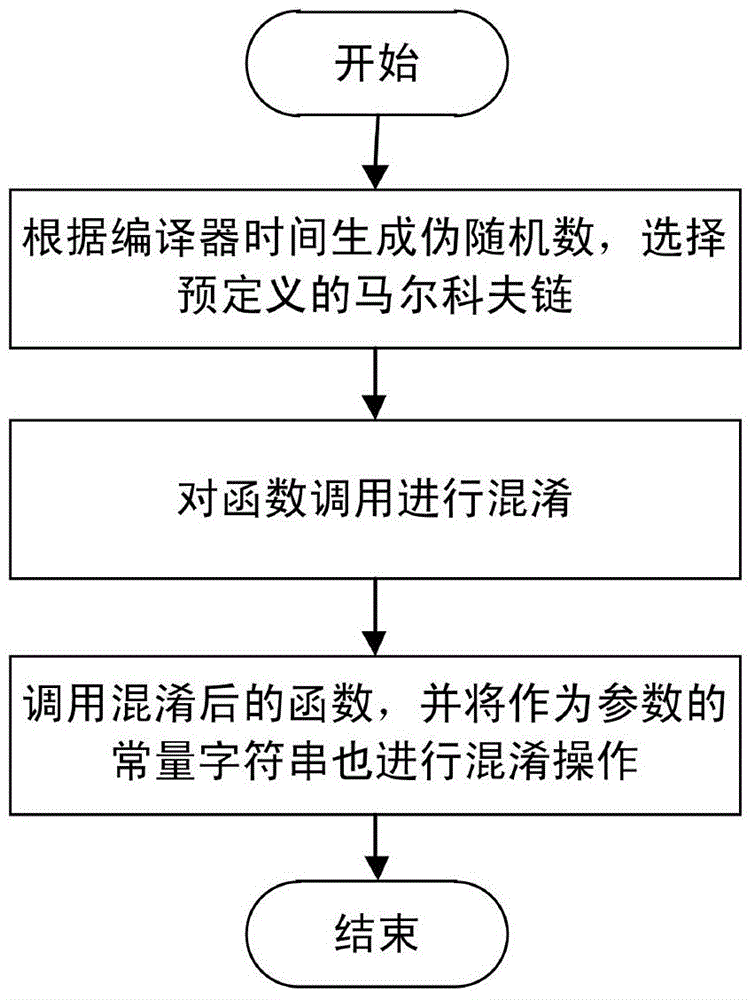
[0054] Example 3: Such as Figure 4 As shown, a method for implementing code obfuscation using finite automata, a Markov chain constructed when obfuscating function calls includes the following steps:
[0055] Step 1-1: Set several automata states. According to the complexity required in this example, set 5 states (State1, State2, State3, State4, State5), and use State1 as the starting state of the automaton and State5 as the end state of the automaton;
[0056] Step 1-2: Set the state you can jump to for each state. In this example, State1 can jump to State2, State3; State2 can jump to State3, State4; State3 can jump to State1 or its own state; State4 can jump to State3, State5; State5 will end the operation of the automaton;
[0057] Steps 1-3: Set the jump probability for all jumpable states of each state, and the sum of the jump probabilities of all jumpable states of each state must be 1.
[0058] In this example, State1 has a probability of 0.3 to jump to State2, and a probabi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com