A method of code obfuscation using Markov chain
A Markov chain and code obfuscation technology, applied in the field of computer security, can solve the problems of code obfuscation, the first crack of the competition team, and the difficulty of software cracking, etc., to achieve the effect of slowing down the speed and realizing the protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
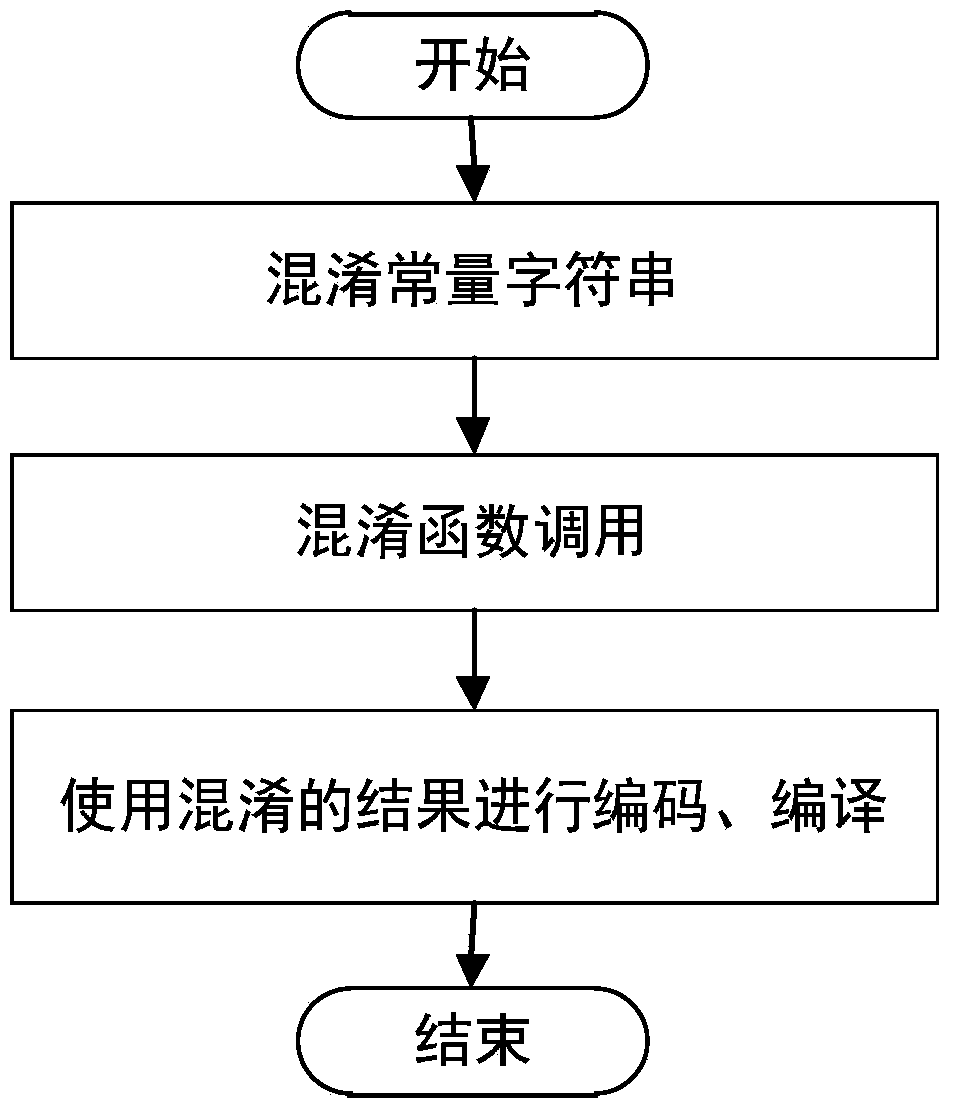
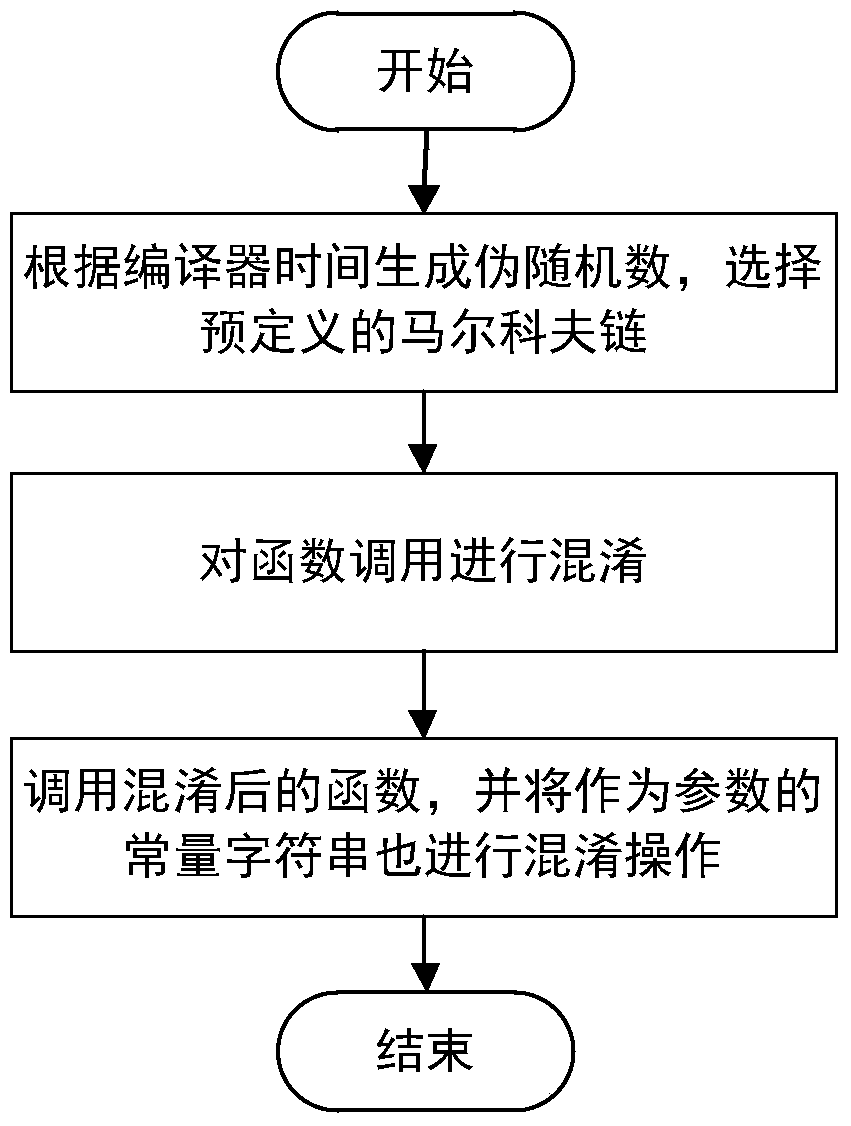
[0033] This specific embodiment provides a method for implementing code obfuscation by using a Markov chain, which specifically includes the following steps:
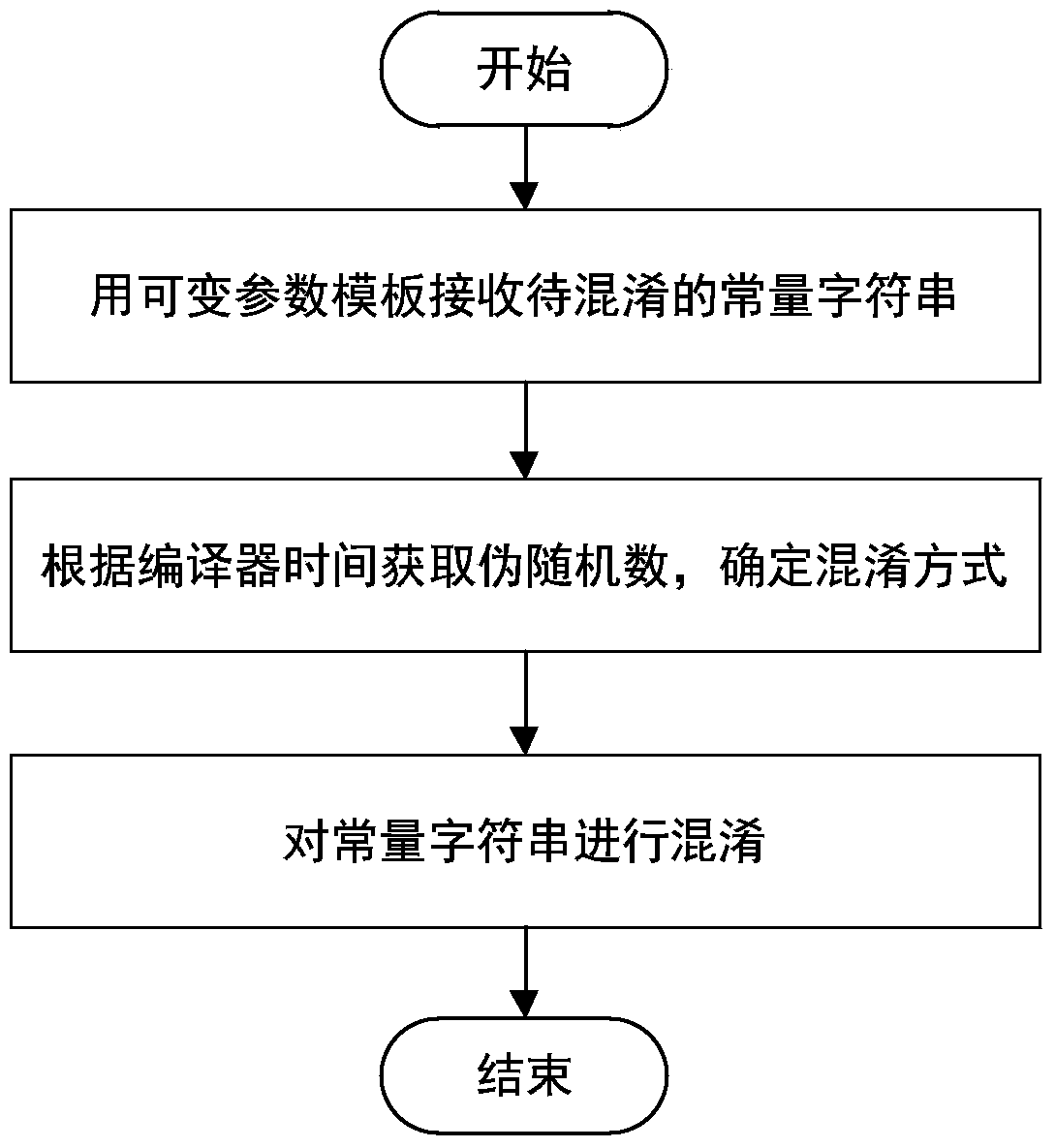
[0034] Step 1. Obfuscate the constant string; for the constant string A to be obfuscated in the program source code, perform the following steps:
[0035] Step 1-1: Randomly select one of the preset encryption methods as the encryption method for the constant string A; among them, the preset encryption method needs to satisfy symmetric encryption, that is, when the program is running, the obfuscated The character string is restored to the original character string, such as the XOR encryption method; this step should occur during the program compilation process, that is, it will not affect the operating efficiency of the program;
[0036] Step 1-2: Use a time-based pseudo-random number algorithm to generate a random number K, and the value K is used as the key used in the encryption method selected in step 1-1 to partici...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com