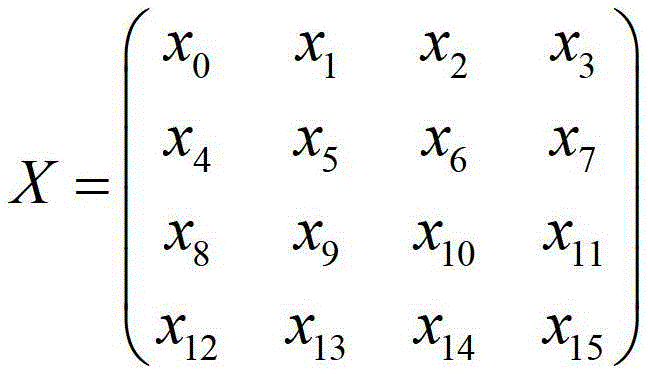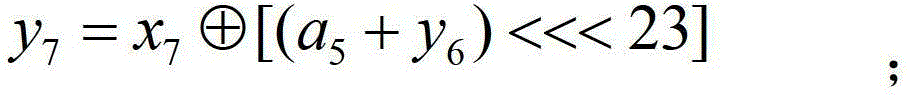Encryption Method of Inner Round Permutation Stream Cipher with Variable Key
An encryption method and a technology of permutation streams, which are applied in the field of information security, can solve the problems of poor internal scrambling effect, difficult internal operation of stream cipher encryption algorithm, and vulnerability to attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
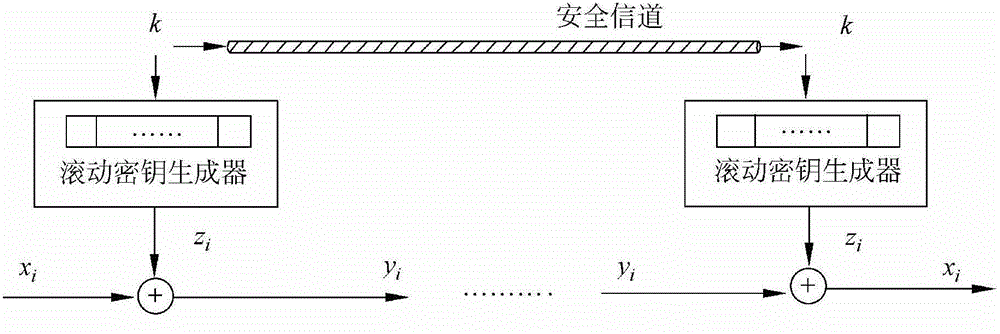
[0100] A method for encrypting an inner round permutation stream cipher with a variable key, comprising the following steps:
[0101] (1) Internal state initialization phase:
[0102] (1.1) Randomly select 3 to 8 32-bit seed keys K=(k 0 , k 1 ,...,k 7 ) and three 32-bit initial vectors v=(v 0 , v 1 , v 2 ), determine three 32-bit constant values c=(c 0 , c 1 , c 2 ); Start two 32-bit count vectors t=(t 0 , t 1 ).
[0103] The seed key K=(k 0 , k 1 ,...,k 7 ) is 3×32 bits, then the seed key K=(k 0 , k 1 ,...,k 7 ) Randomly select the first 3 words, namely k 0 ,k 1 ,k 2 , and the remaining 5 characters are k 3 ,k 4 ,k 5 ,k 6 ,k 7 It is fixed as all zeros or all ones;
[0104] The seed key K=(k 0 , k 1 ,...,k 7 ) is 4×32 bits, then the seed key K=(k 0 , k 1 ,...,k 7 ) Randomly select the first 4 words, namely k 0 ,k 1 ,k 2 ,k 3 , the remaining 4 characters are k 4 ,k 5 ,k 6 ,k 7 It is fixed as all zeros or all ones;
[0105] Seed key K=(k...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com