Genetic algorithm based software code obfuscation operation selection method
A genetic algorithm and software code technology, which is applied in the field of software code obfuscation operation selection based on genetic algorithm, can solve the problems of strong randomness, lack of optimal selection of balance between software code performance and obfuscation degree, etc., and achieve low impact on software performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
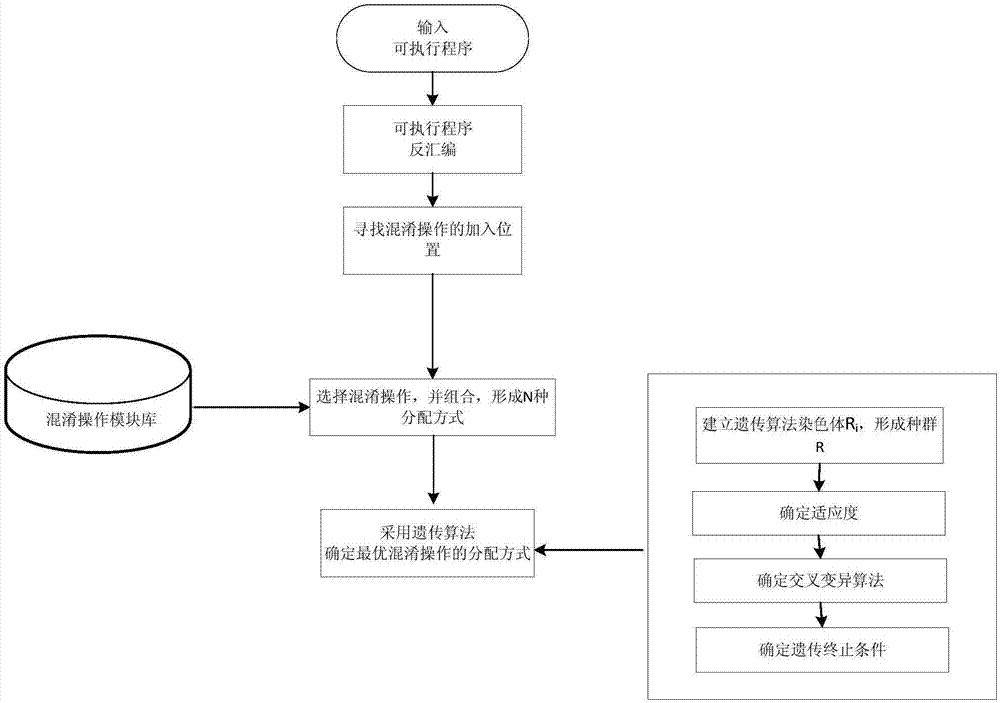
[0027] Such as figure 1 As shown, the present invention proposes a software code obfuscation operation selection method based on genetic algorithm, and the specific steps include:
[0028] (1) Establish a library of obfuscated operation modules, which is composed of obfuscation operations. Obfuscation operations include control flow obfuscation operations, data obfuscation operations, and comprehensive control flow obfuscation and data obfuscation operations. For example, control flow obfuscation operations include adding redundant jumps to the program and reorganizing the control flow in the program, and data obfuscation operations include reorganizing variables and mixing and transforming numeric variables.
[0029] (2) Find the entry of the executable program to be confused and disassemble the executable program to be confused.
[0030] (3) To traverse the code obtained by disassembly, looking for the JUMP, CALL, XOR code among them, as the place where the obfuscation operation i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com