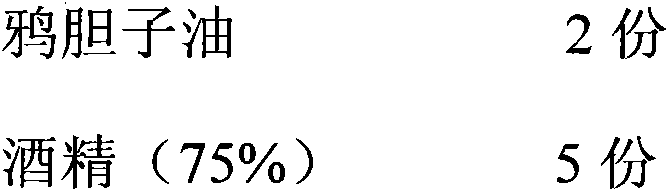Patents
Literature
41 results about "Birthmark" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A birthmark is a congenital, benign irregularity on the skin which is present at birth or appears shortly after birth, usually in the first month. They can occur anywhere on the skin. Birthmarks are caused by overgrowth of blood vessels, melanocytes, smooth muscle, fat, fibroblasts, or keratinocytes.
Ultrasound-based treatment methods for therapeutic treatment of skin and subcutaneous tissues
The disclosure provides a method and apparatus for noninvasive and minimally-invasive treatment of skin and subcutaneous tissues with ultrasound with or without nano- or microparticles. The treatment includes, but is not limited to, hair removal, skin rejuvenation (wrinkle removal), scar removal, treatment of spider veins and varicose veins, removal of birthmarks, acne treatment, wound treatment, abnormal pigmentation and stretch mark removal, abnormal tissues in skin and subcutaneous layers, and tattoo removal. Skin and subcutaneous tissues which can be treated with the methods described include, but are not limited to, the dermis, epidermis, subcutaneous fat, connective tissue, muscle tissue, blood vessels, scar tissues, tendons, and cartilage tissues, and abnormal tissues in skin and subcutaneous layers. The disclosure is especially applicable to hair removal and skin rejuvenation.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
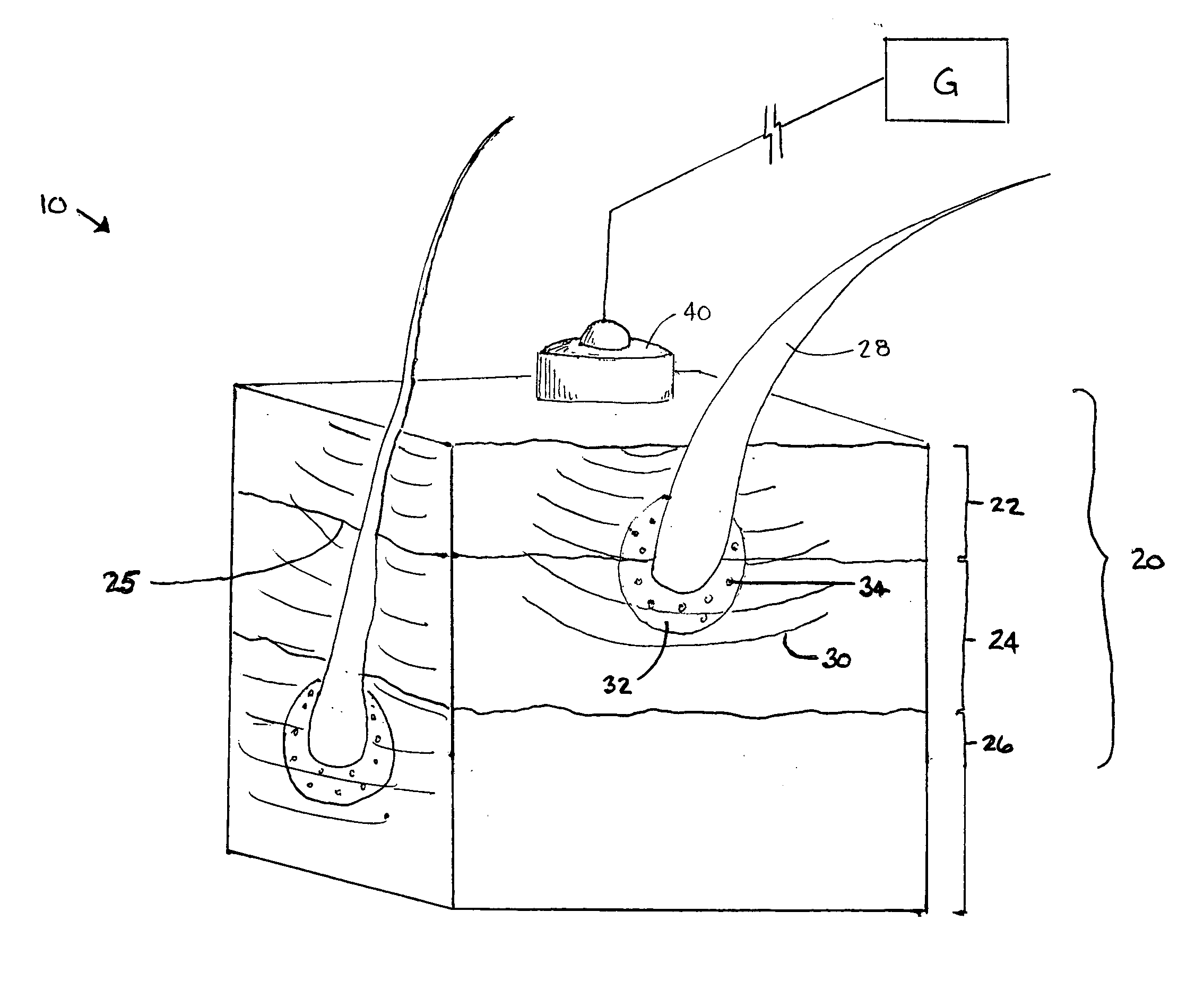
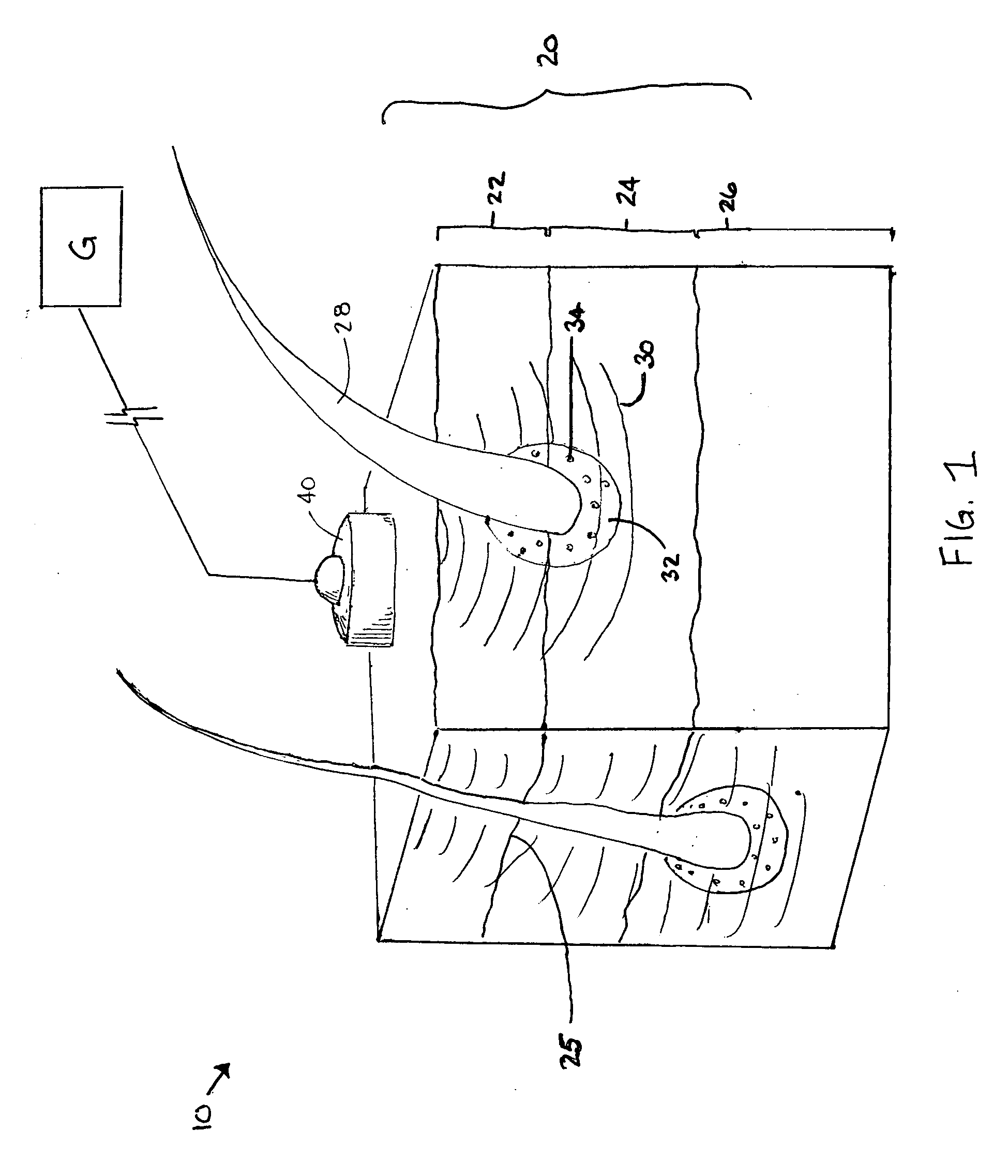
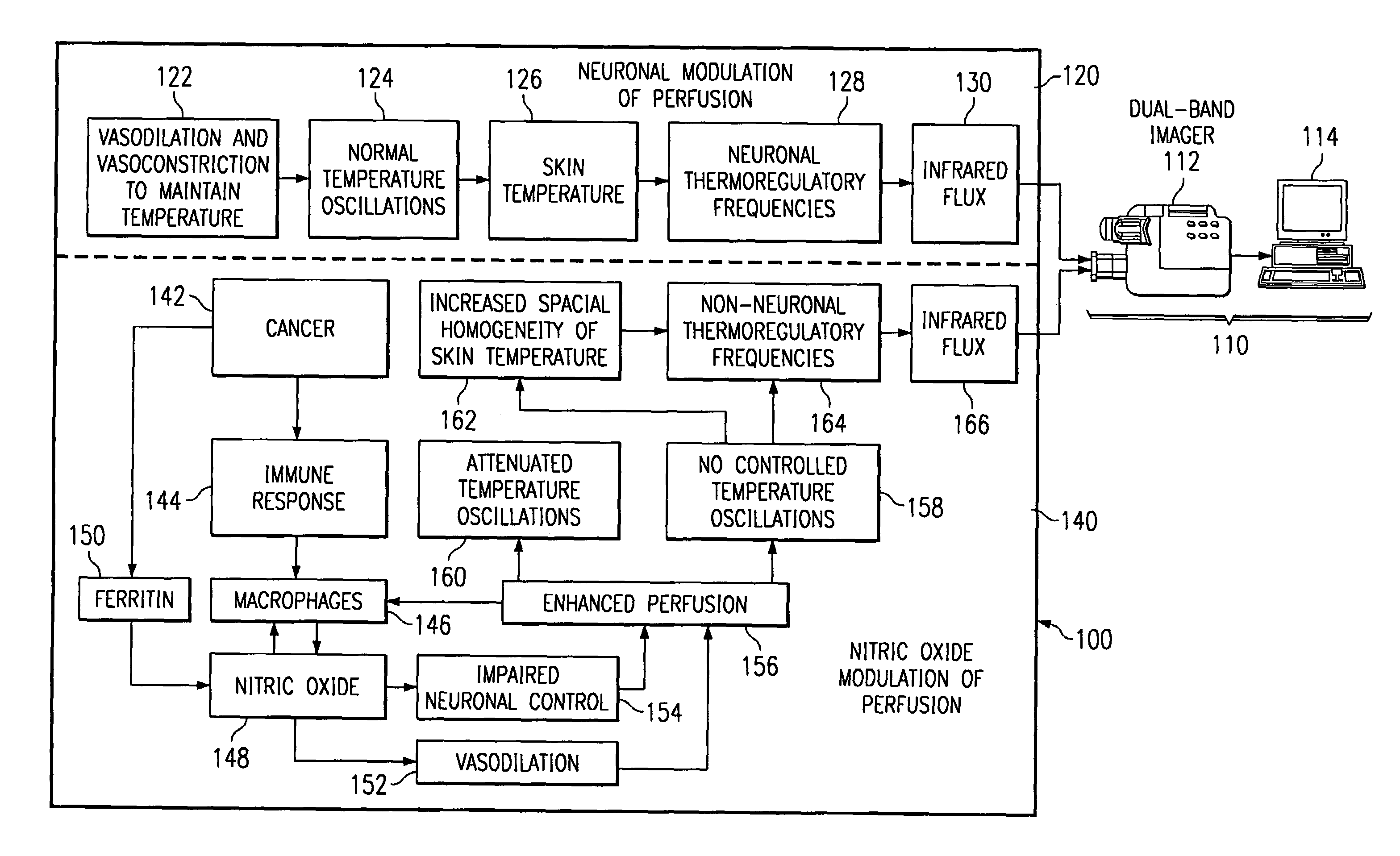
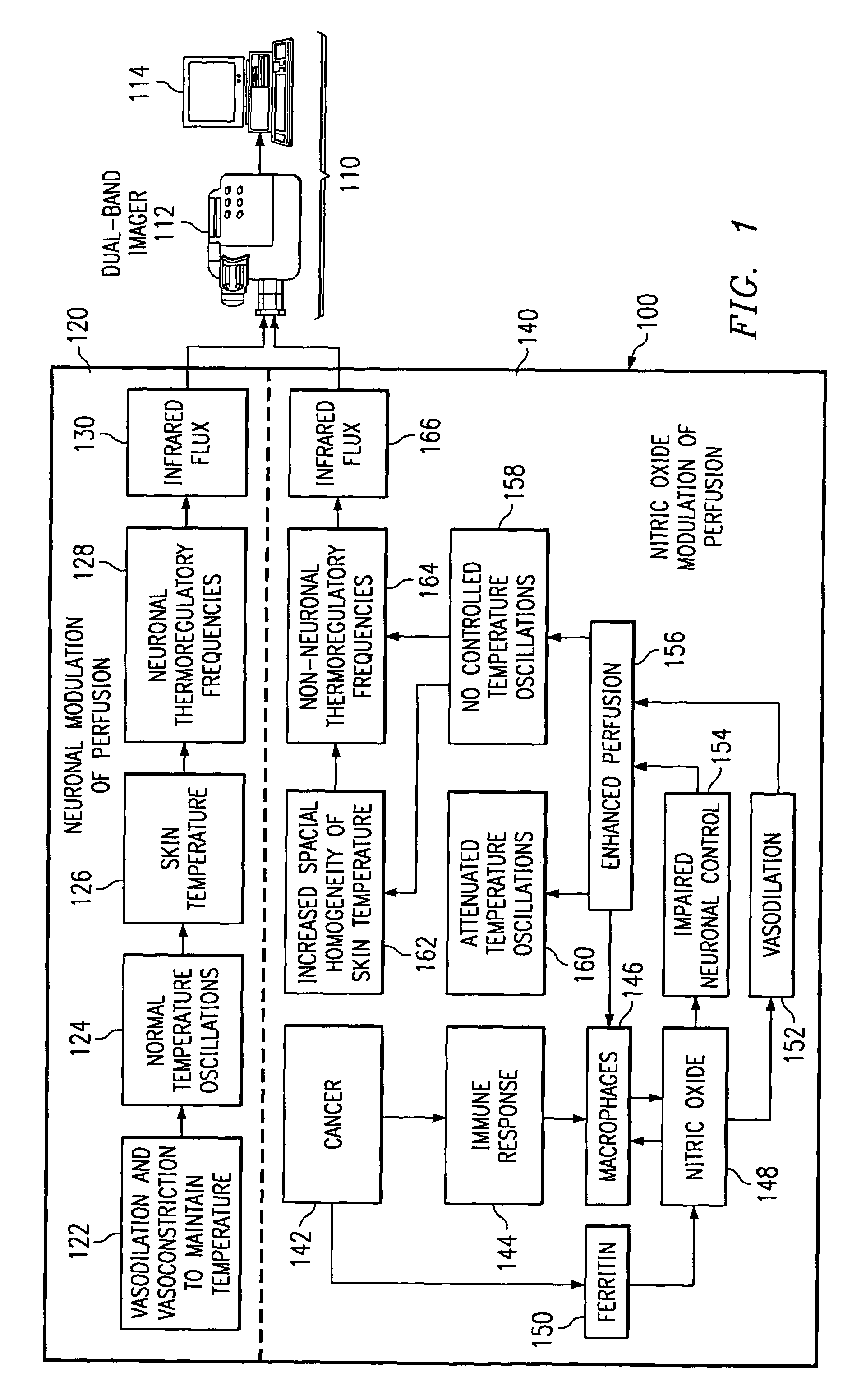
Method of and apparatus for detecting diseased tissue by sensing two bands of infrared radiation
A method of and apparatus for detecting diseased tissue based upon infrared imaging in two different bands of infrared wavelengths is described. The use of two series of infrared images taken in two different bands of infrared wavelengths increases sensitivity to the subtle temperature changes caused by diseased skin and tissue, especially in the case of cancerous tissue. By sensing skin temperature, the homogeneity thereof, the time variations thereof and the correlation between the two series of infrared images, the present invention decreases the rate of false positives and false negatives. The increased discrimination due to two series of infrared images allows for reliable detection of diseased or cancerous tissue even in the presence of skin tone variations such as birthmarks, tattoos and freckles. The present invention finds special application in the field of breast cancer detection where subtle skin temperature variations may readily be sensed using two series of infrared images.
Owner:LOCKHEED MARTIN CORP
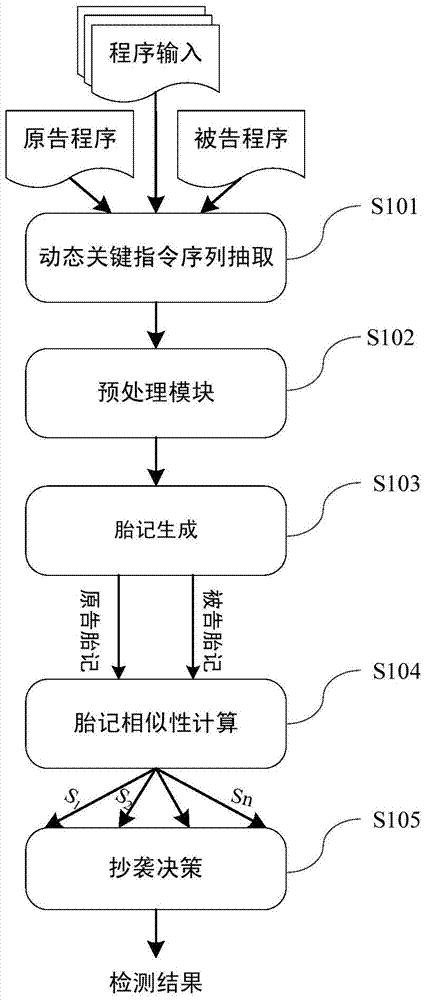
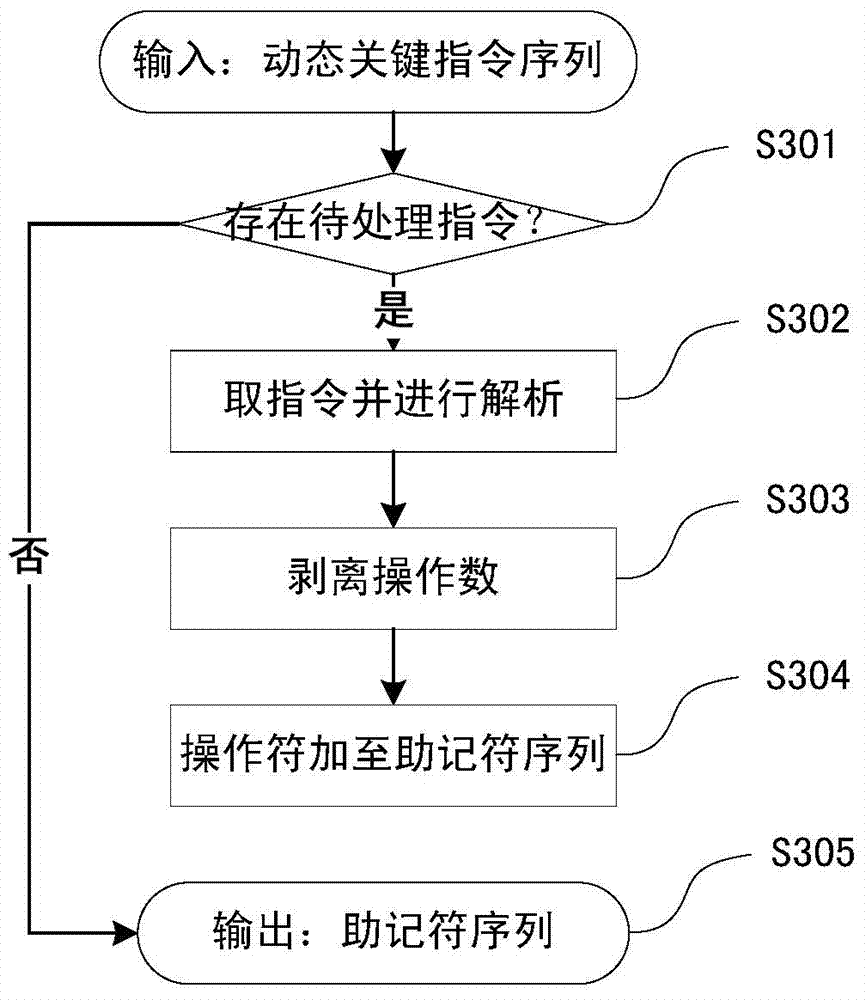
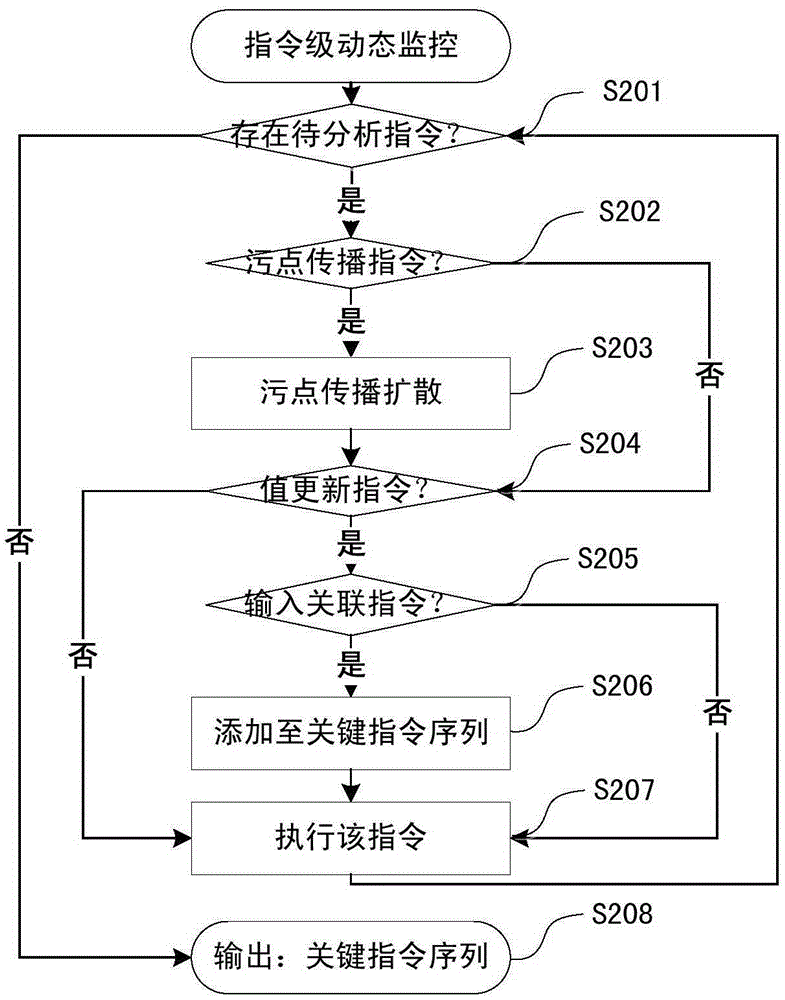
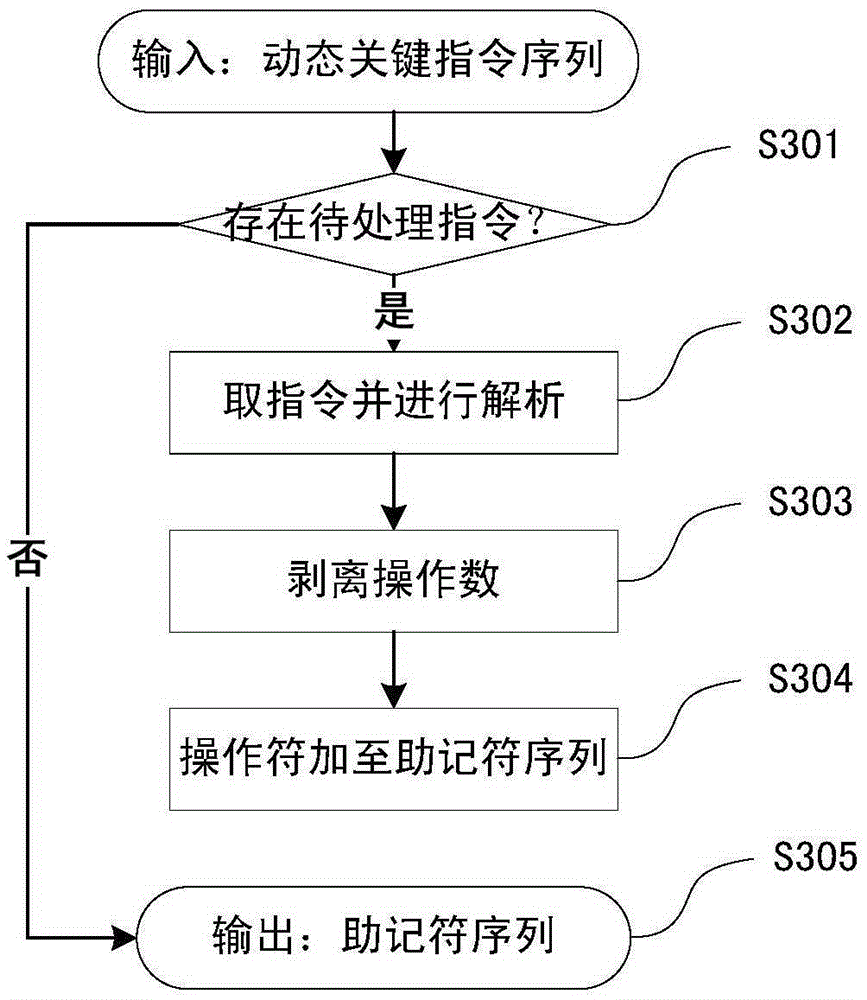
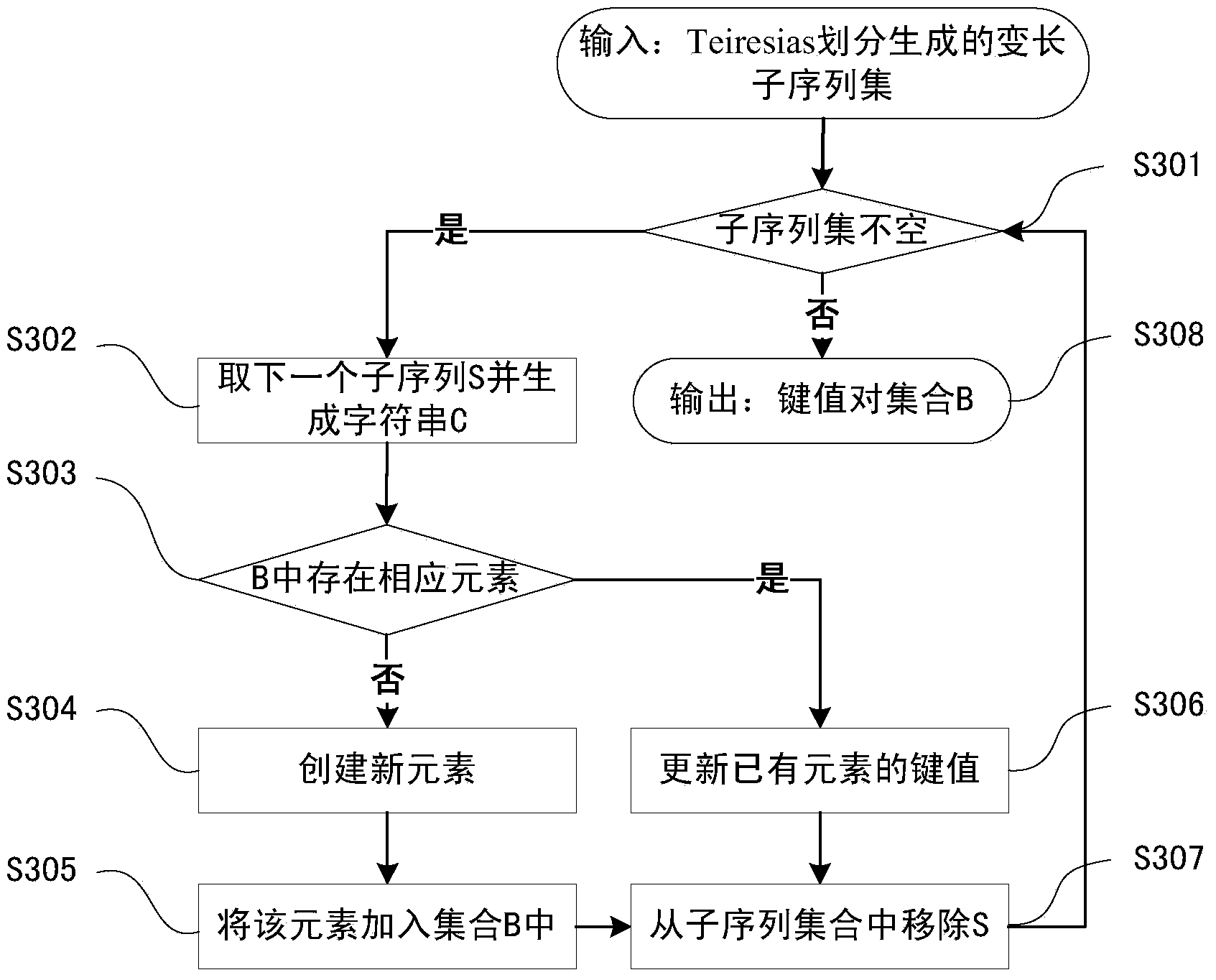
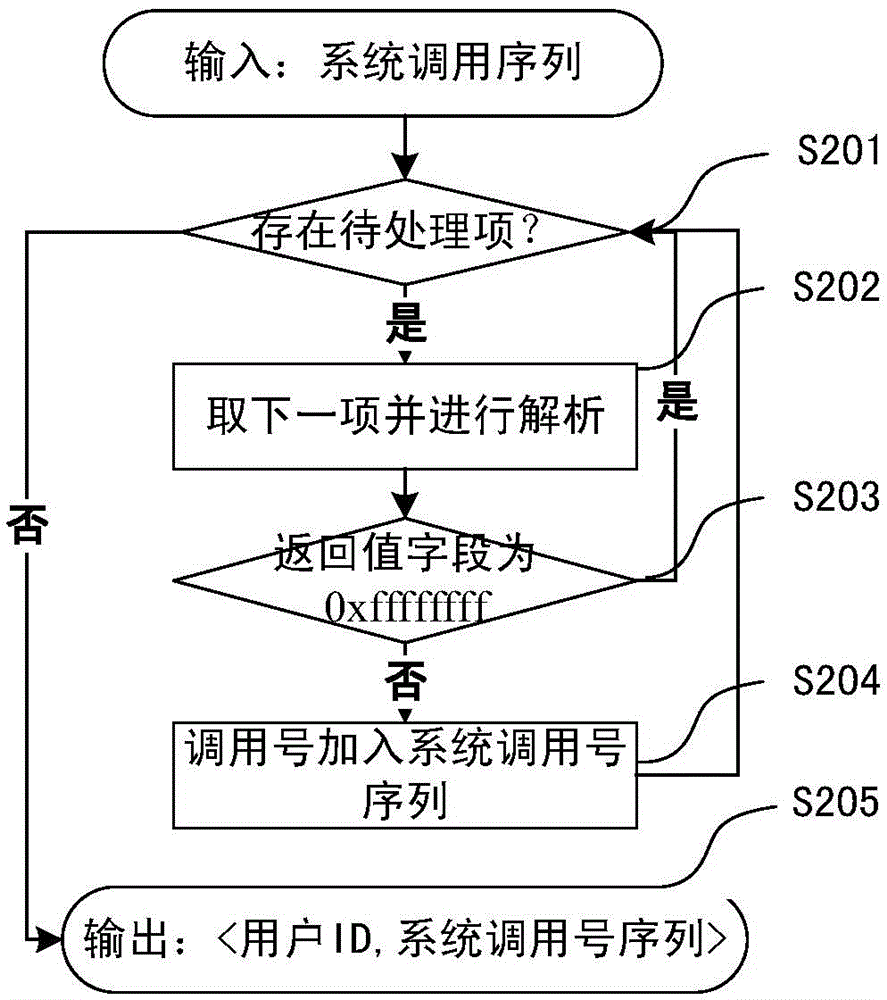
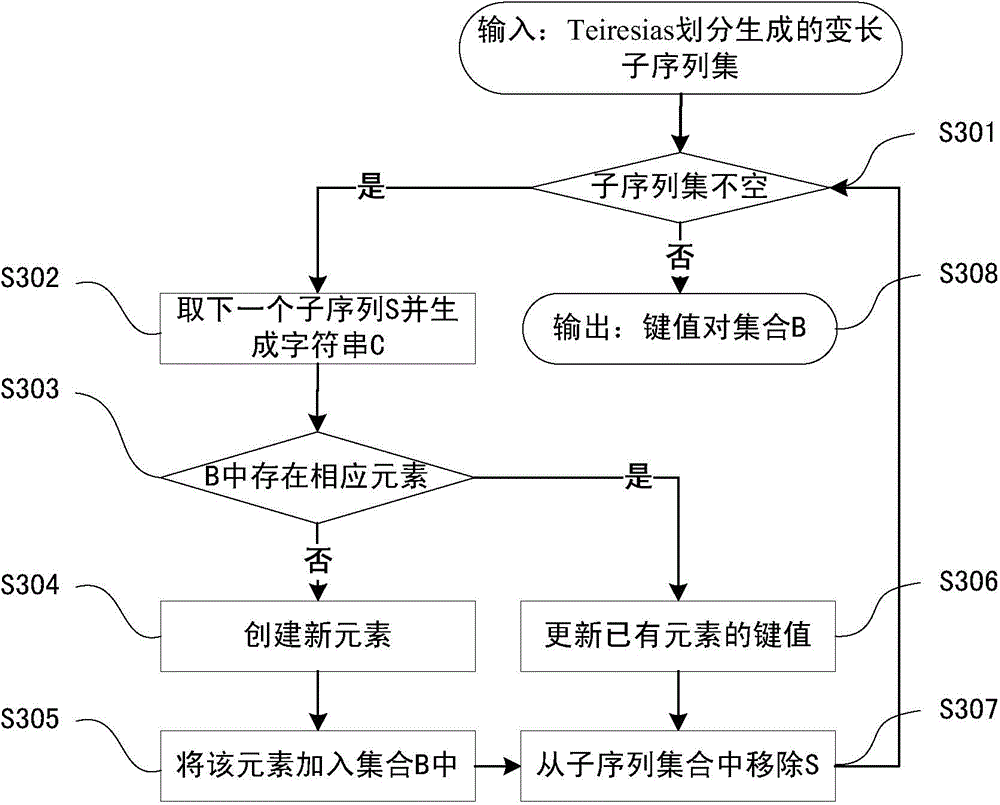
Dynamic key command sequence birthmark-based software plagiarism detecting method
ActiveCN103577323ANo limitationsStrong resistanceSoftware testing/debuggingObfuscationDynamic instrumentation
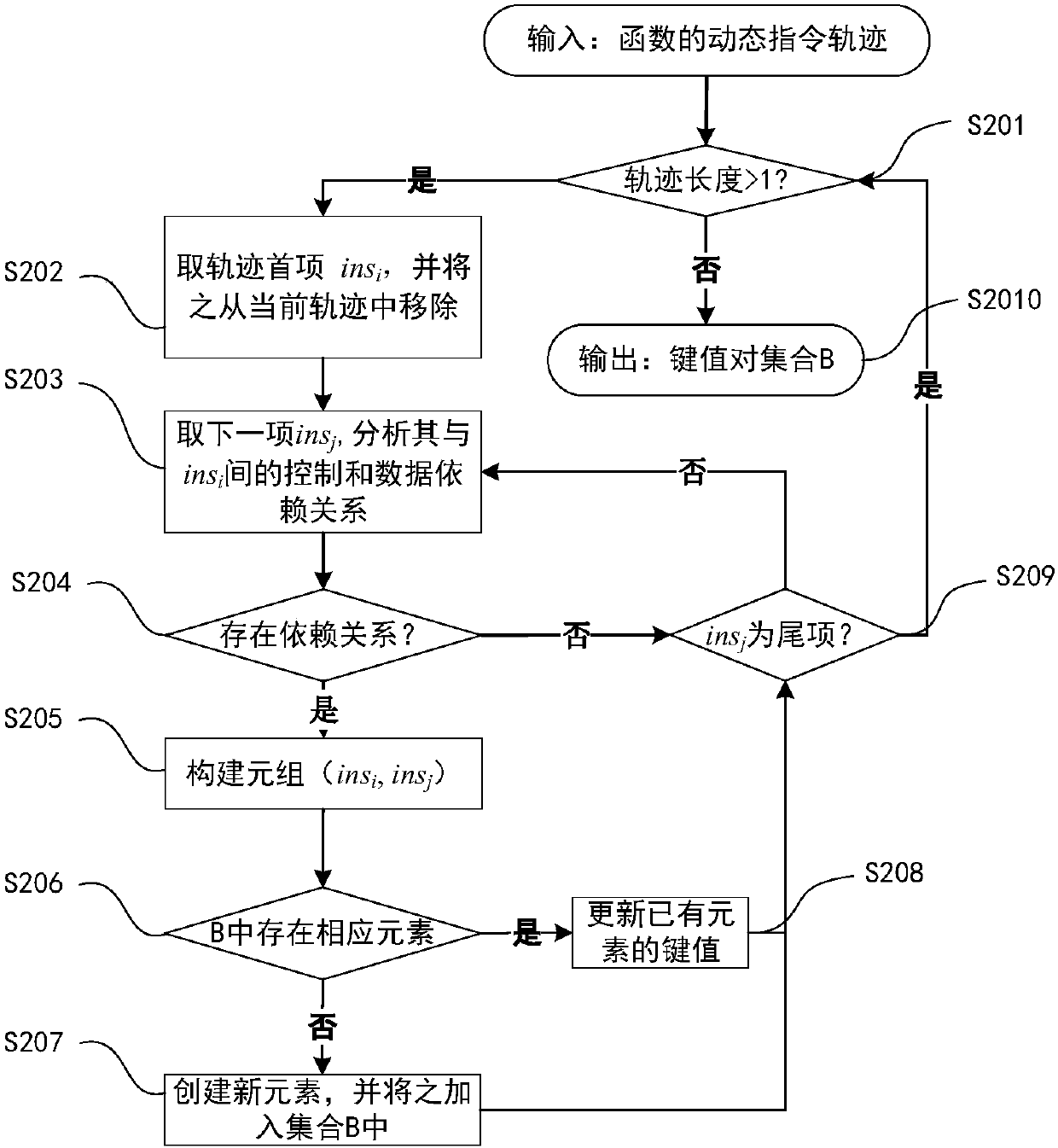
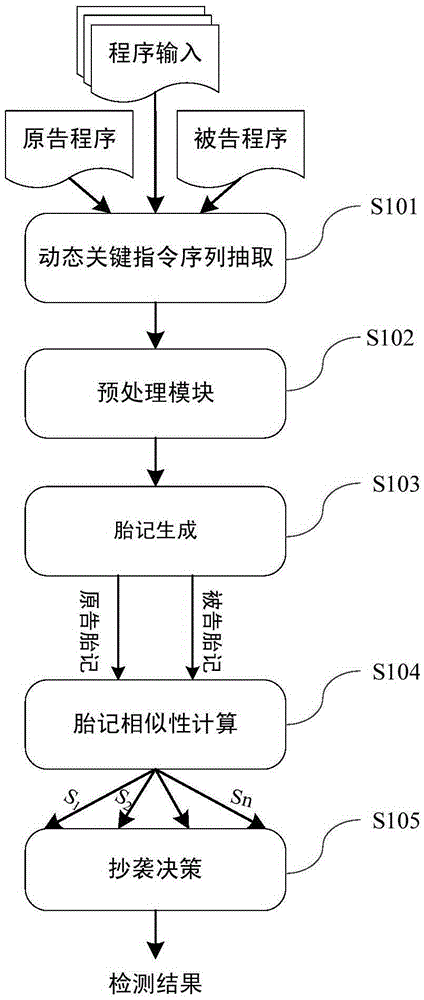
The invention provides a dynamic key command sequence birthmark-based software plagiarism detecting method, which comprises the steps of (1) monitoring a program to be analyzed based on a dynamic instrumentation and identifying and recording a key command by combining with dynamic stain analysis in real time; (2), preprocessing the recorded key command sequence, stripping an operation number and extracting a mnemonic sequence; (3) on the basis, respectively generating a dynamic key command sequence birthmark for two software to be detected; (4) calculating the similarity of the birthmarks; (5) making the design of plagiarism or not by the average value of the similarity of the birthmarks and a given threshold value. The dynamic key command sequence birthmark-based software plagiarism detecting method directly aims at the binary codes without the need of existence of source codes and has more practical significance; the detection means does not depend on a specific platform or programming language, has wider application range and has better resistance to the code obfuscation technology with reversed semantics, so the detection capability of deep plagiarism is improved.
Owner:XI AN JIAOTONG UNIV
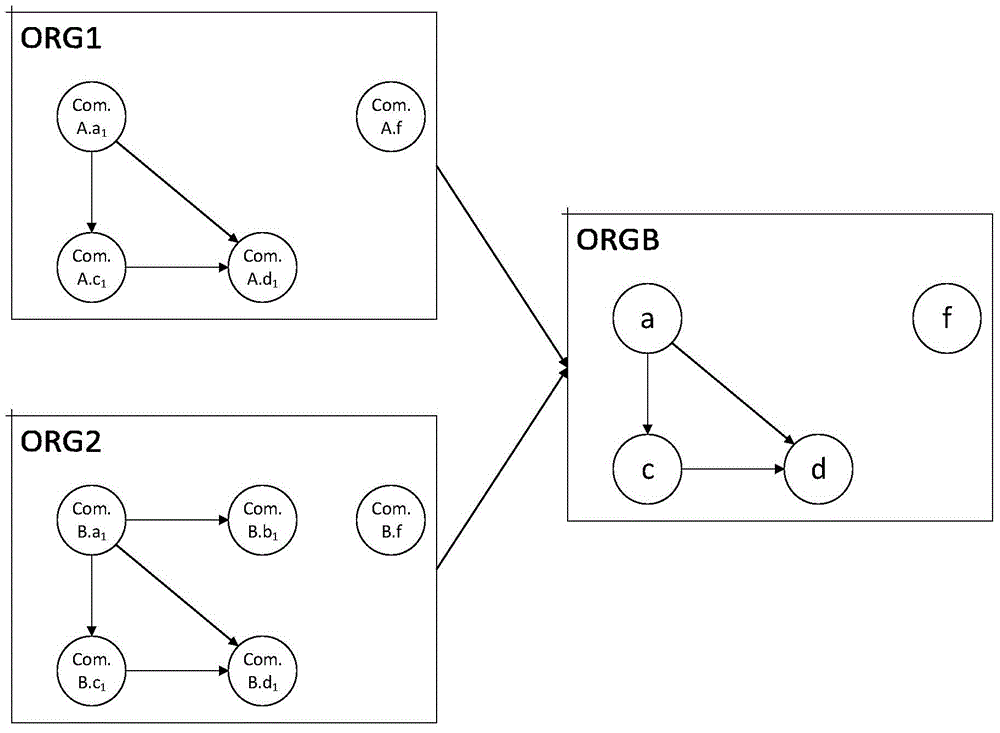
Object reference graph-based Android cellphone malicious software detection method
ActiveCN104866764AAvoid obfuscated attacksReduce overheadPlatform integrity maintainanceControl flowObject based
The invention discloses an object reference graph-based Android cellphone malicious software detection method and relates to an Android cellphone malicious software detection method. The invention provides the object reference graph-based Android cellphone malicious software detection method which solves the problems that an inner core level monitoring method relates to inner core modification, and the system detection cost is high; a sandbox technology only providing a finite system service is easily attacked; a control flow method is easily attacked by code confusion, an API calling dynamic birthmark establishing-based method needs more API calling and has larger limitation, and the detection efficient of an ORGB extraction method and a VF2 algorithm is low. The method is realized by the steps of: 1 extracting an object reference graph (ORG); 2, obtaining ORGB of a malicious program; 3 screening a possible type of an unknown program; 4, determining that the unknown program is in a certain type of matched malicious program. The invention is applied to the field of detection of Android cellphone malicious software.
Owner:HARBIN INST OF TECH
Android application completeness verification method based on register architecture
InactiveCN104598808AAvoid mistakesRealize verificationDigital data protectionPlatform integrity maintainanceProcessor registerParallel computing
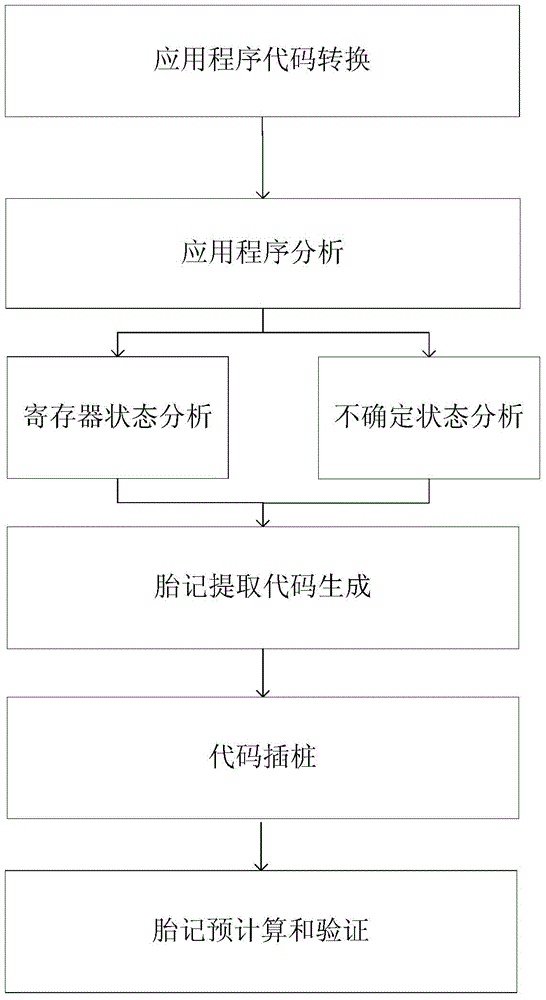
The invention relates to an Android application completeness verification method based on a register architecture. The method comprises the following steps: converting an Android application program code to be a Dalvik virtual instruction code; carrying out the birthmark analysis for a code segment to be protected to obtain an instruction code state capable of being used for extracting a birthmark and register state information, and generating a corresponding birthmark extraction code; implanting the birthmark extraction code into a Smali format virtual instruction code by virtue of a code inserting process, re-editing the Smali format virtual instruction code to generate a novel application; pre-calculating birthmark information by dynamically executing the application, and carrying out the completeness verification for the application by utilizing the birthmark information in the use process of the application. By extracting the birthmark information in the application execution process, whether the operation process of the application code segment is abnormal or not can be initiatively verified, so that the verification of the core code segment and the execution process can be realized.
Owner:INST OF INFORMATION ENG CAS
Medicine capable of eliminating freckles and acnes, scars and moles, and various stains and wrinkles
InactiveCN102697985AImprove microcirculationTo promote metabolismDermatological disorderPlant ingredientsSalvia miltiorrhizaWrinkle skin
The invention relates to a medicine capable of eliminating freckles and acnes, scars and birthmarks, and various stains and wrinkles, i.e., freckle-removing and mole-eliminating ling. The medicine comprises angelica sinensis, salvia miltiorrhiza, pawpaw, herba leonuri, saffron crocus, radix angelicae and liquorice. The medicine capable of eliminating freckles and acnes, scars and birthmarks, and various stains and wrinkles disclosed by the invention is prepared from pure traditional Chinese medicines, and has the advantages of being good in treatment effect, little in side effect, short in treatment course and the like; and the medicine has effects of promoting blood circulation and removing stasis, conditioning internal secretion, improving body microcirculation, promoting skin metabolism, avoiding the excessive accumulation of pigments in skin tissues, whitening skin, and eliminating various stains, wrinkles, moles and scars, and has functions of prolonging life and preventing ageing. The medicine has characteristics of a quick effectiveness and a high cure rate for treatment on acne vulgarises, freckles, acnes, scars, moles, and various stains and wrinkles.
Owner:陈玉堂
Software similarity detection method based on dynamic control flow graph sequence birthmark
ActiveCN108830049AAvoid lack of source codeAvoid the difficult problem of reverse disassemblyProgram/content distribution protectionGraph sequencePlagiarism detection
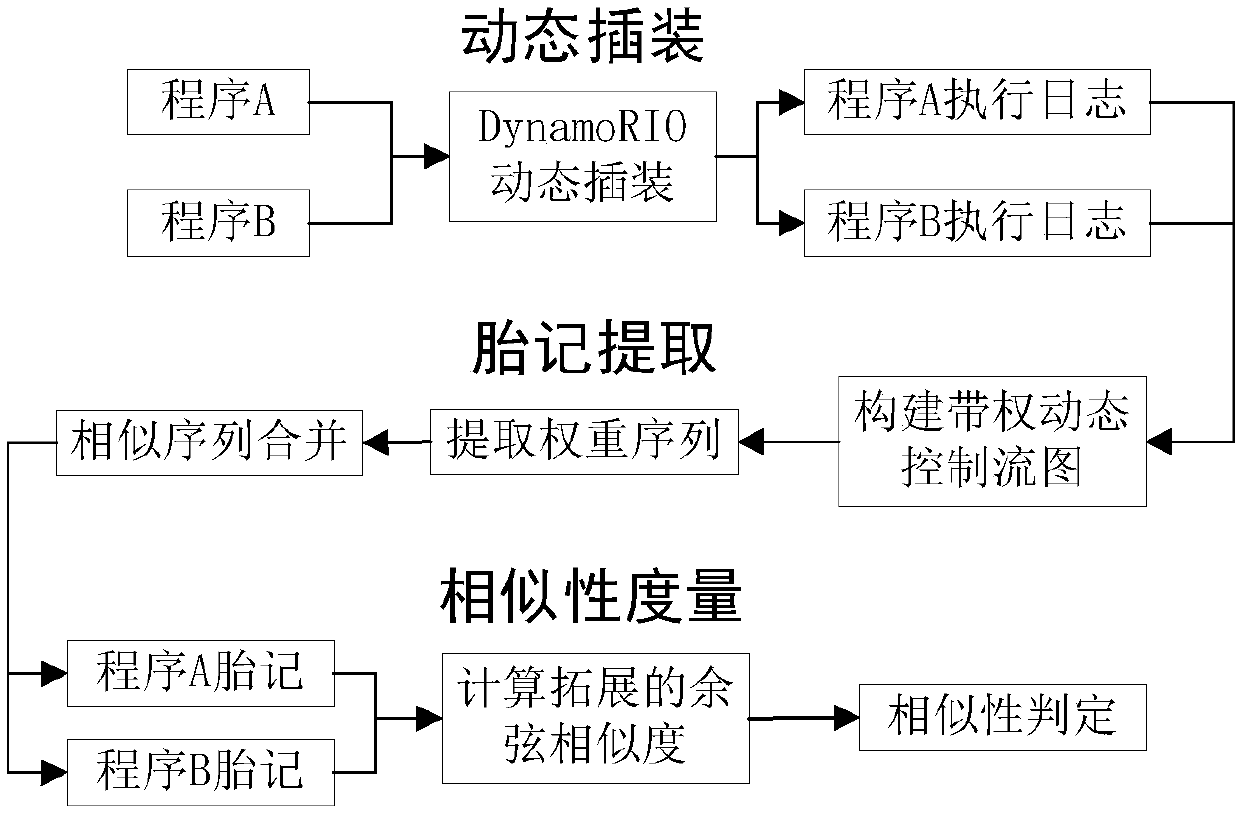
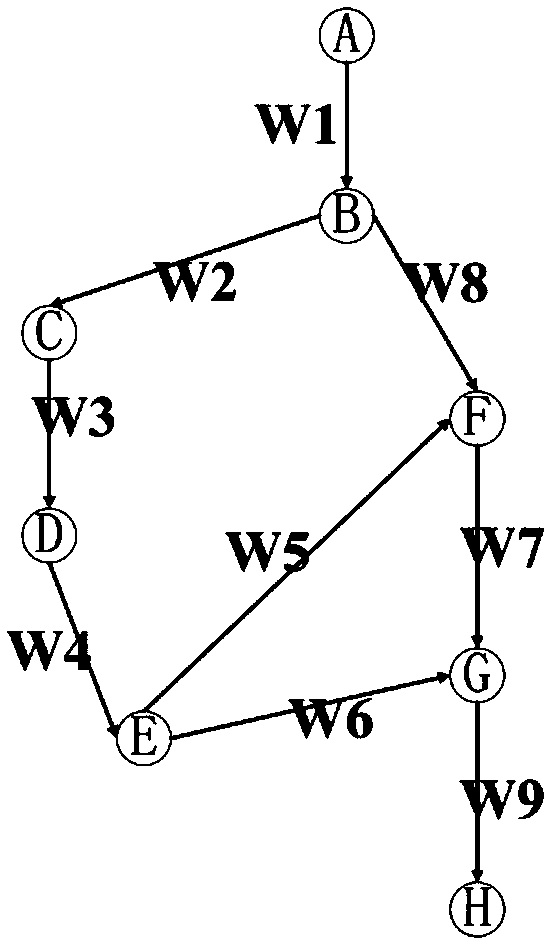
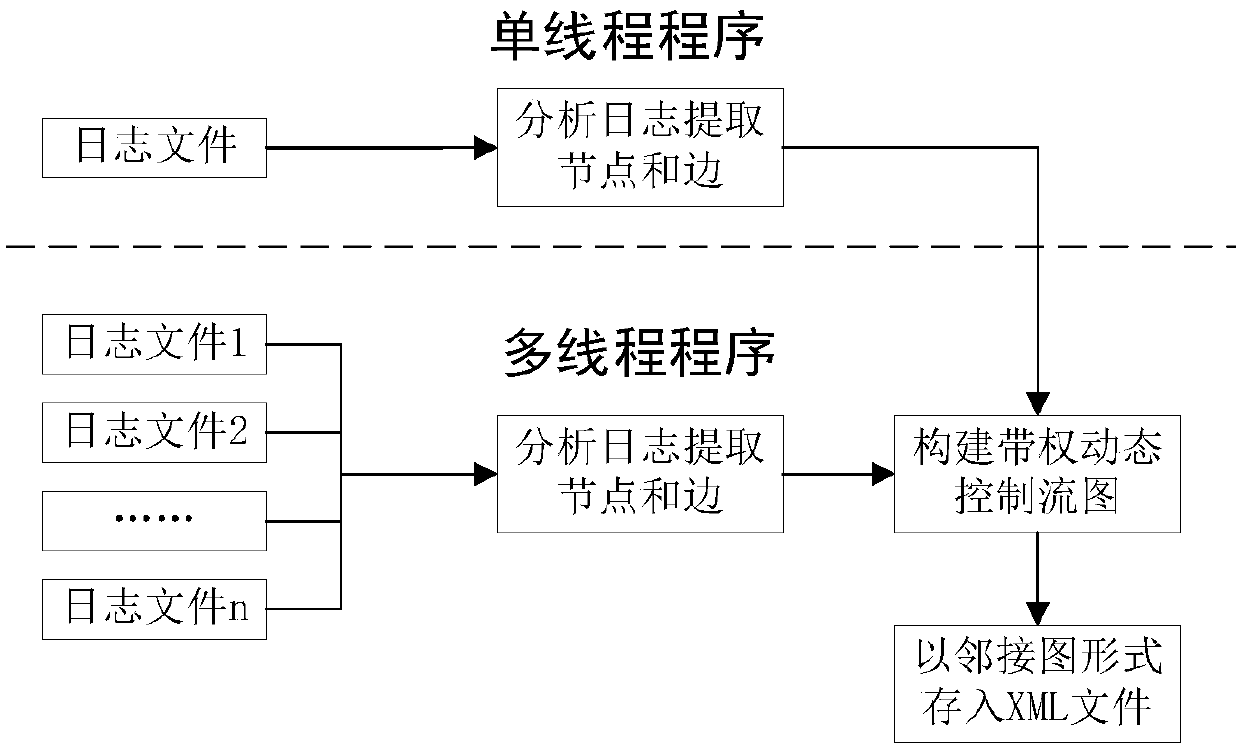
The invention discloses a software similarity detection method based on dynamic control flow graph sequence birthmark. The method comprises the following steps: firstly assembling a starting address of a basic block in the plug-in program record program execution process and a branch hopping address at the ending of the basic block under a dynamic plug-in platform DynamoRIO; and then analyzing a log file, constructing a program dynamic control flow graph, and endowing the weight; establishing a weight sequence birthmark set WSB, and serving the length ratio of the WSB as parameter to compute the similarity of each pair of programs. By adopting the dynamic plug-in analysis and extracting the feature of the software in operation, the problems that the source code is absent and the reverse disassembling is difficult in the software plagiarism detection can be avoided; only the basic block starting address and the branch hopping condition are recorded in the dynamic plug-in analysis, and the expenditure is less in comparison with the birthmark based on the dynamic data flow tracking and like technology; the influence by unrelated interference information in the dynamic operation can beresisted, and the program similarity can be detected even if the software encrypts by using an encryption shell.
Owner:SICHUAN UNIV +2
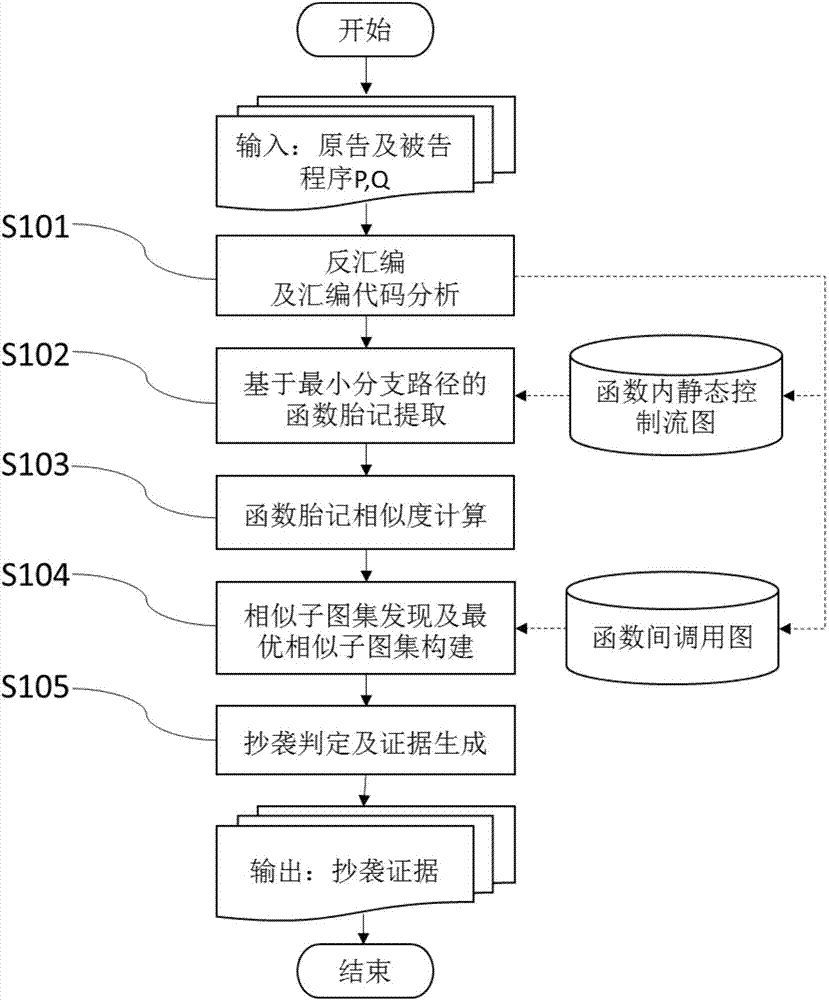
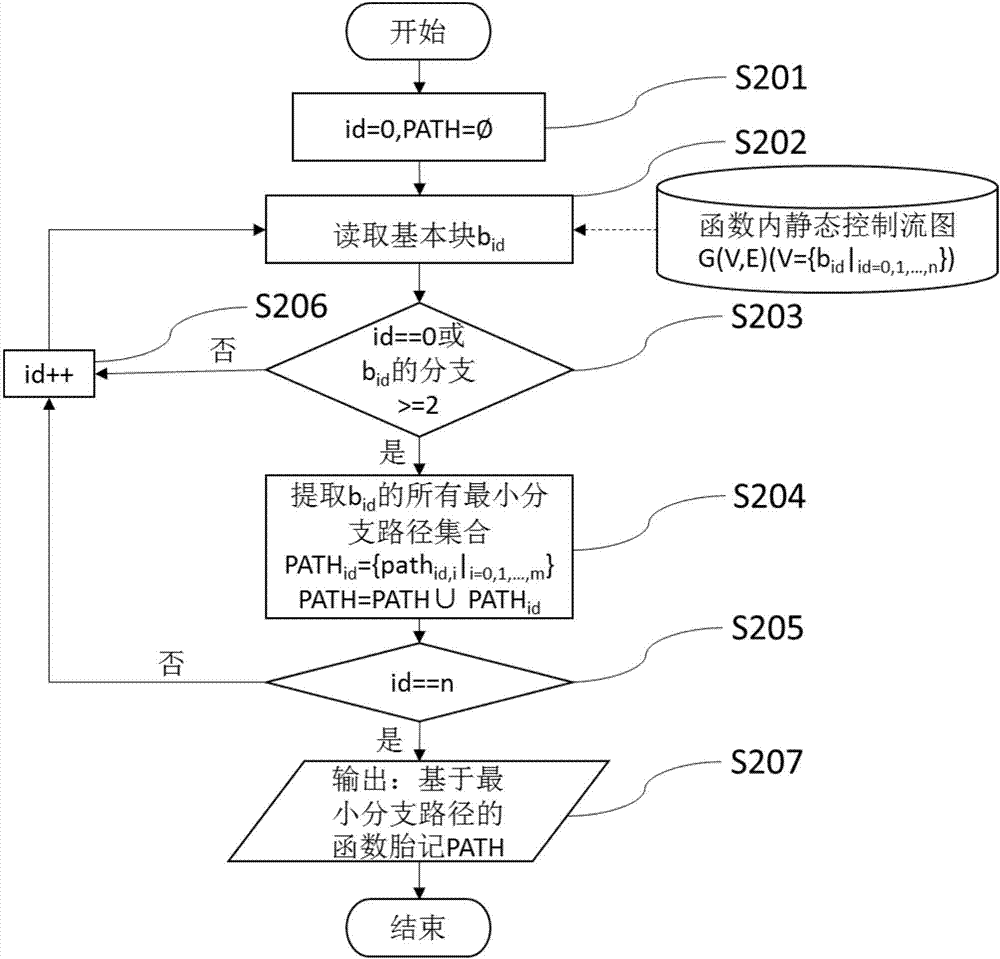
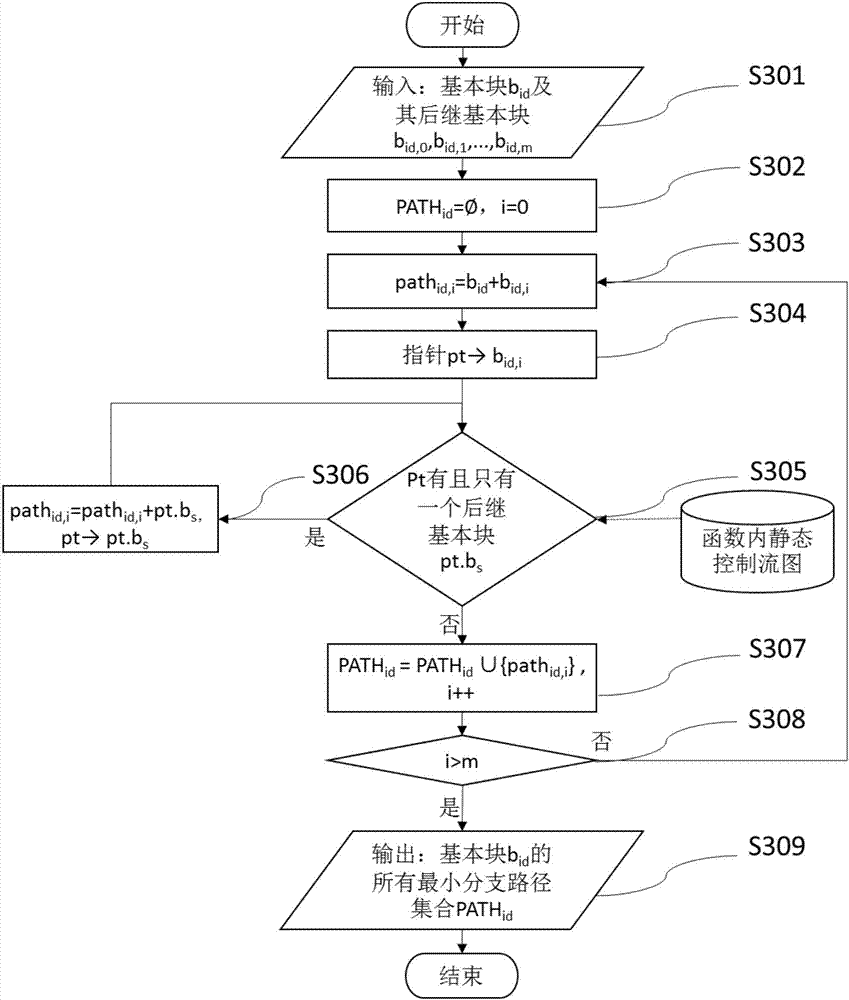
Software local plagiarism evidence generation method for minimum branch path based function birthmarks
ActiveCN107967152AImprove applicabilityEasy to detectSoftware engineeringSpecific program execution arrangementsReverse analysisTheoretical computer science
The invention discloses a software local plagiarism evidence generation method for minimum branch path based function birthmarks. The method comprises the steps that static information of a program isextracted by conducting reverse analysis on the program; on the basis of a control flow graph, a basic block, an instruction sequence and the like of a function, the minimum branch path based function birthmarks are extracted so as to represent behavior characteristics of the function; the similarity degree among the function birthmarks is calculated, and the similarity among functions is obtained; on the basis of the similarity among the functions, and in combination of a function calling graph, a best similar subgraph set is built and serve as judgment basis of local plagiarism among the programs and powerful plagiarism evidence, and initial evidence is provided for real software infringement cases.
Owner:XI AN JIAOTONG UNIV
Multifunctional wart and nevus removing cream
The invention provides a multifunctional wart and nevus removing cream, which is an external application cream especially for removing warts and naevus on a human body and aims to beautify appearance by removing wart, nevus, freckle, verruca plana, verruca vulgaris, plane warts, ecphyma, birthmark, senile plaque, corn and other skin defects on the human body on the premise that scar is not left and patients do not feel pain. The cream is prepared by blending oleum fructus bruceae, alcohol, glutinous rice flour, sodium carbonate, calcium hydroxide, medical talc powder, pearl powder and fresh jig juice, wherein the powdered solids and liquids are respectively mixed, and are uniformly stirred in a container until paste is obtained. When the cream is used, the paste is applied to warts, and the warts can be removed in 3-7 days.
Owner:郭广会
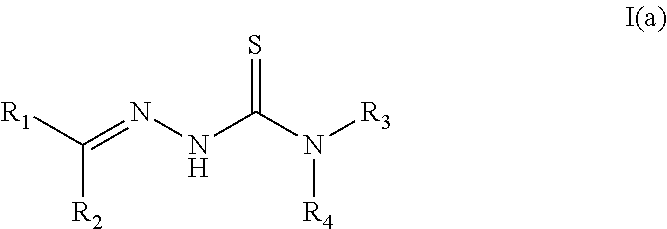
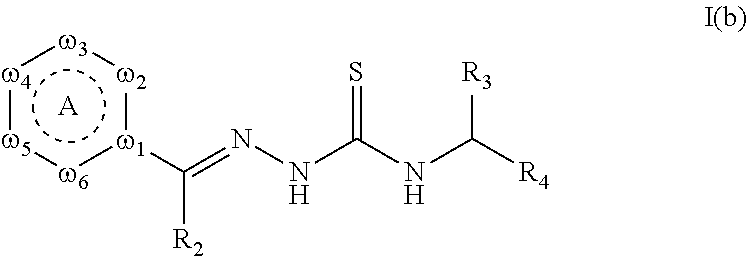
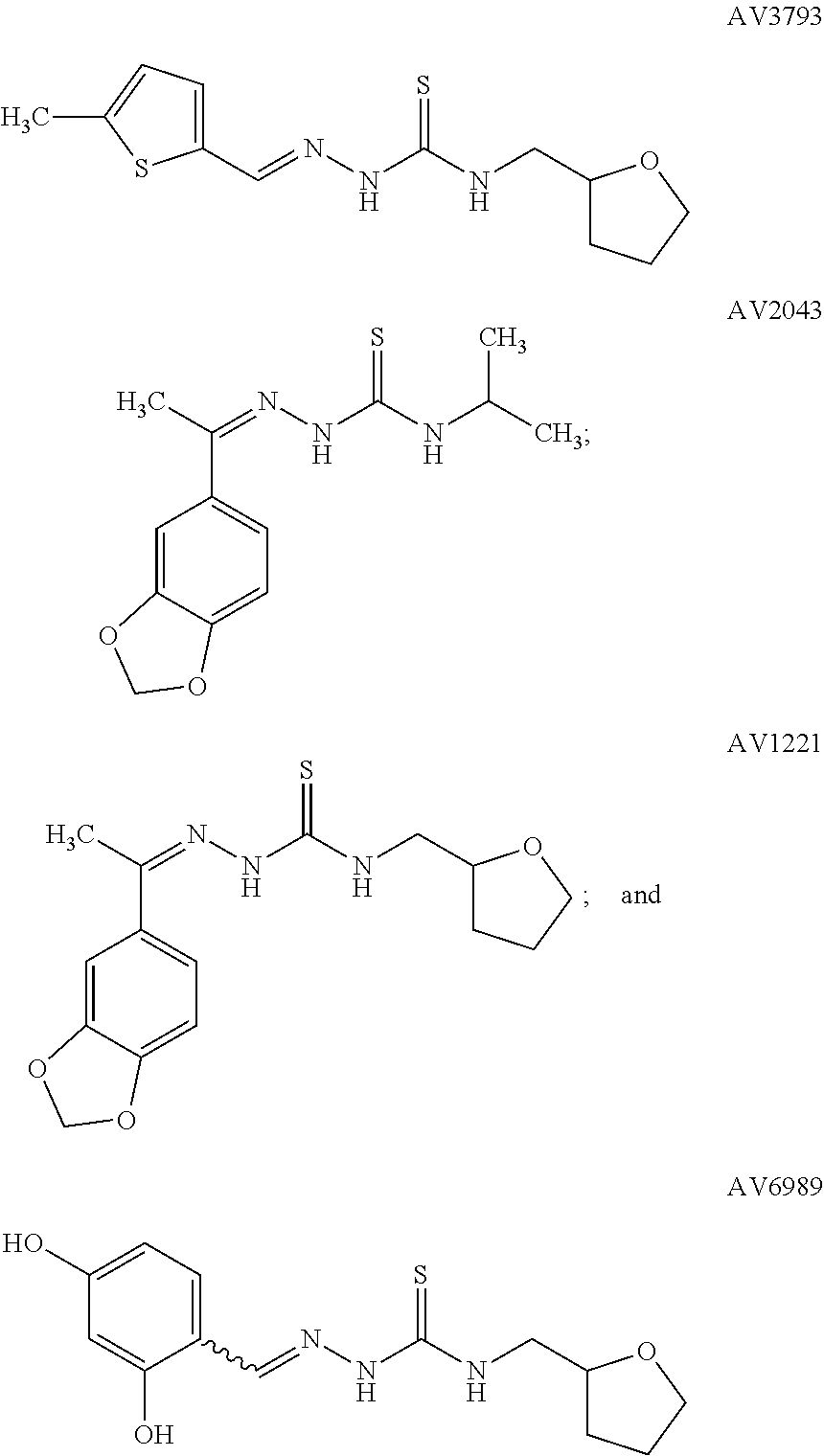
Tyrosinase inhibitors
InactiveUS20150174034A1Signs improvedReduce pigmentationBiocideCosmetic preparationsNail stainPostinflammatory hyperpigmentation
The compositions and methods of described herein comprise novel ingredients effective to reduce unwanted pigmentation, such as skin discoloration, freckles, age spots, liver spots, sun damage, tans, pigmented acne marks, scars, pigmented birthmarks, hyperpigmentation, post-inflammatory hyperpigmentation, post-injury hyperpigmentation, melasma, cholasma, after-burn scar, nail stain, yellowing of skin, dark circles under eyes, and the like. The composition may include additional ingredients accordingly for a colored cosmetic, moisturizer, cleanser, toner, and the like.
Owner:AVON PROD INC
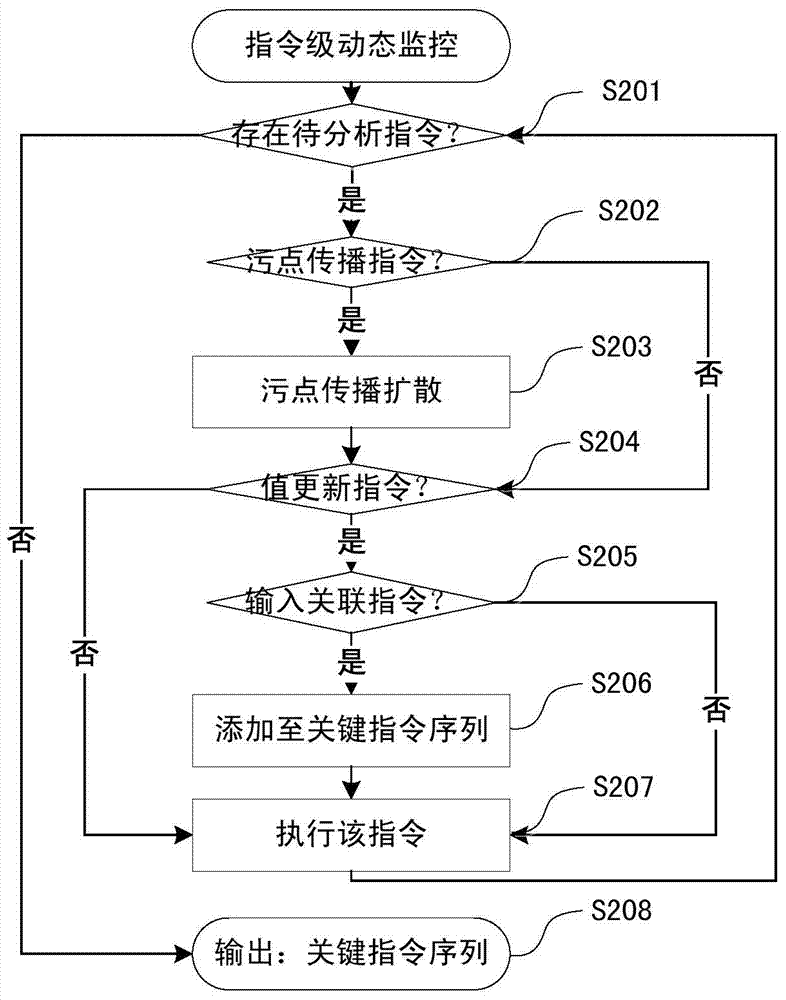
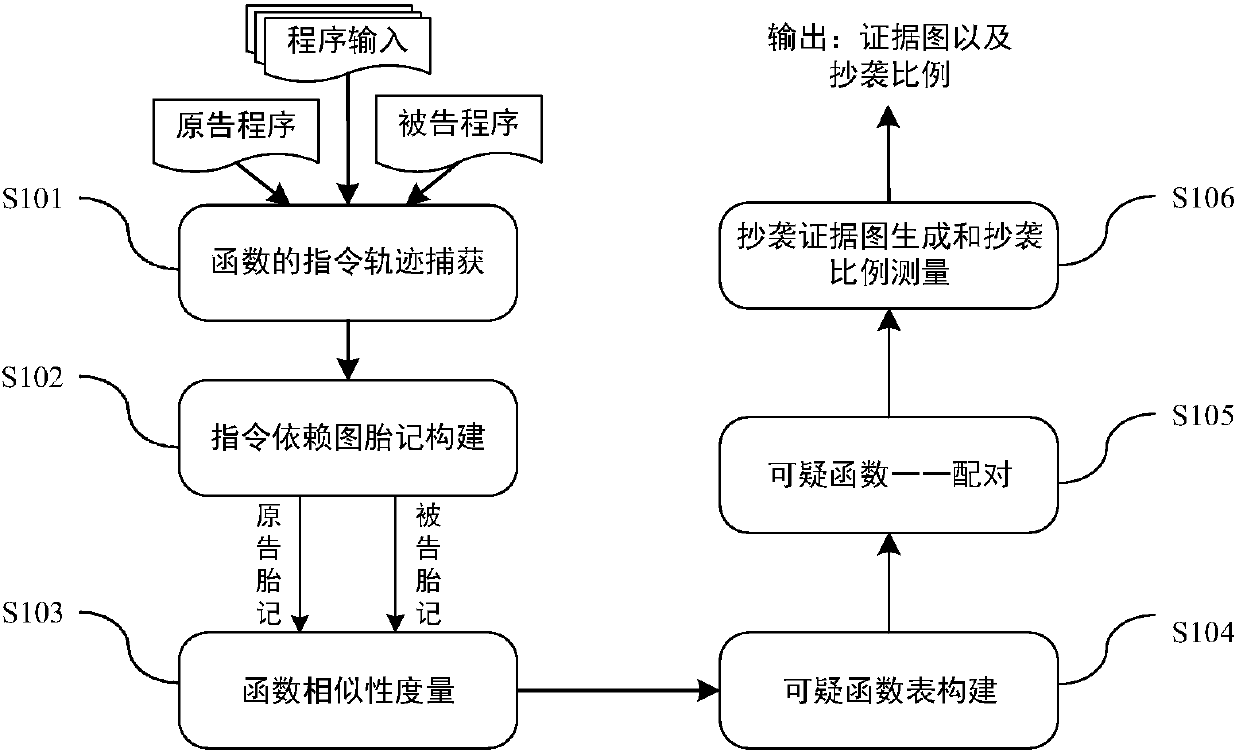
Software local plagiarism detection method based on dynamic instruction dependency graph birthmark
ActiveCN108399321ANot easy to confuse and destroyImproved ability to combat deep obfuscationProgram/content distribution protectionDynamic instrumentationPlagiarism detection
The present invention provides a software local plagiarism detection method based on the dynamic instruction dependency graph birthmark. The method comprises: 1) using dynamic instrumentation to perform instruction level monitoring on a to-be-analyzed program, and capturing an instruction trajectory of each function; 2) for a dynamic instruction trajectory recording each function, carrying out data dependency and control dependency analysis, and constructing a dynamic instruction dependency graph birthmark; 3) calculating the similarity between instruction dependency graph birthmarks, and implementing the measure of similarity between functions; 4) based on the given threshold, constructing a list of suspicious functions for each function in the plaintiff program; 5) extracting the staticfunction call graph of the program, and performing precise pairing of the suspicious functions under the guidance of the calling dependency; and 6) based on the calling dependency, assembling matchedfunction pairs to generate a plagiarism evidence map, and measuring the proportion of suspected plagiarism part. According to the method provided by the present invention, local plagiarism detection is implemented by constructing a function-level birthmark; and the concept of a plagiarism evidence map is proposed for the first time, and the effectiveness of the evidence can be greatly enhanced.
Owner:XIAN UNIV OF POSTS & TELECOMM
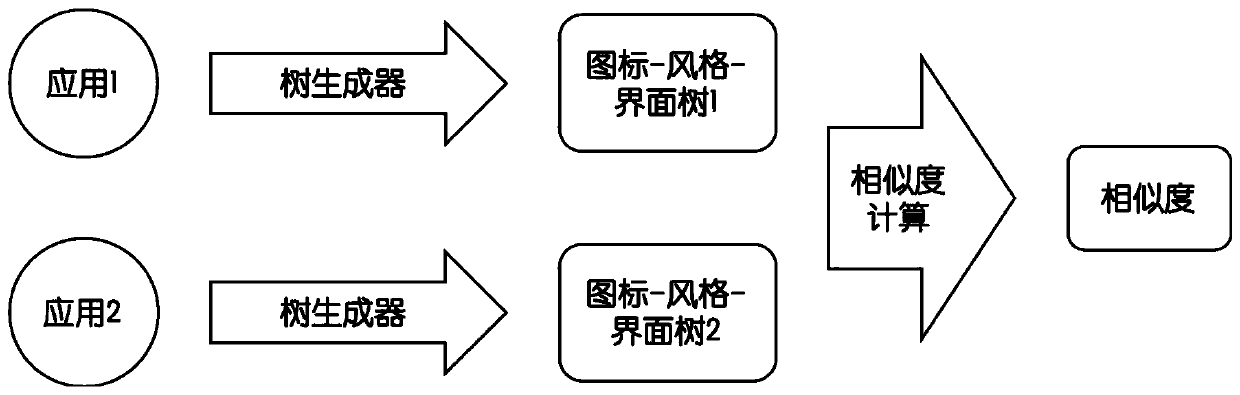
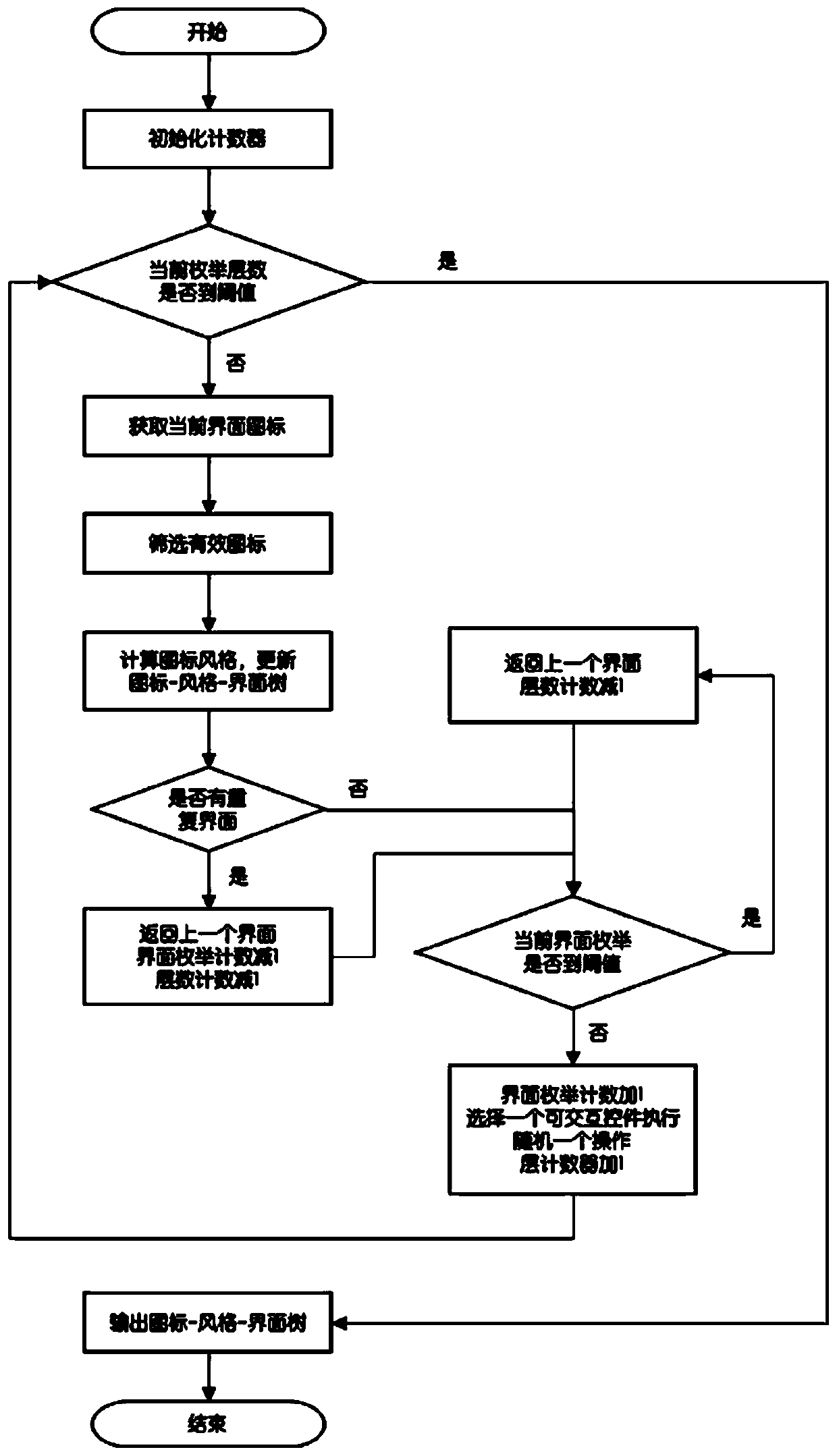
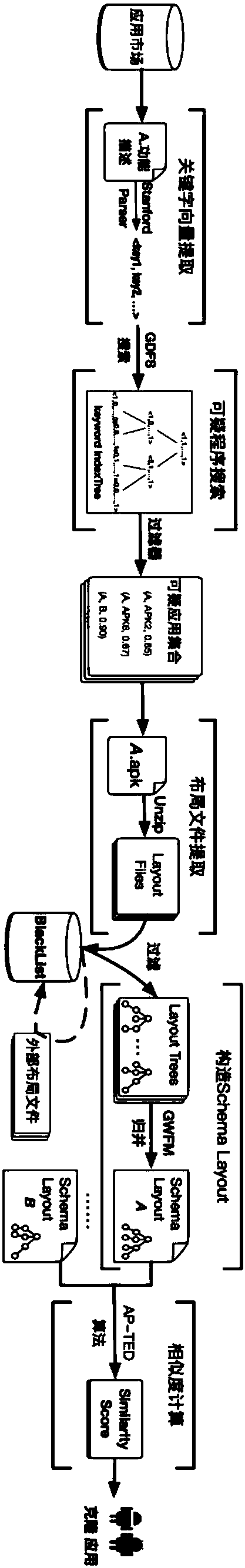
An android software repackaging detection method based on interface icon characteristics
ActiveCN109815699AHigh precisionLower limit requirementPlatform integrity maintainanceEnergy efficient computingConfusionApplication software
The invention discloses an Android software repackaging detection method based on interface icon characteristics, which comprises the following steps: S1, dynamically executing an Android application,screening each interface, and dumping all icons of the interface; S2, classifying the dumped icons according to styles to obtain an icon-style-interface tree, and taking the icon-style-interface treeas an application software birthmark; S3, calculating similarity of the icon-style-interface tree of to-be-compared Android application pairs, when the similarity of a pair of the icon-style-interface tree is greater than a threshold value, the two corresponding applications are judged to be repackaged. According to the Android software similarity comparison method, the visual feature, namely theicon, is combined with the strategy of dynamically executing the Android application, so that the resistance to two anti-detection modes, namely code confusion and encryption, is improved, and the repackaging detection accuracy of the Android application is improved.
Owner:NANJING UNIV
Tyrosinase inhibitors
ActiveUS20150111897A1Signs improvedReduce pigmentationBiocideOrganic active ingredientsNail stainHyperpigmentation
The compositions and methods of described herein comprise novel ingredients effective to reduce unwanted pigmentation, such as skin discoloration, freckles, age spots, liver spots, sun damage, tans, pigmented acne marks, scars, pigmented birthmarks, hyperpigmentation, post-inflammatory hyperpigmentation, post-injury hyperpigmentation, melasma, cholasma, after-burn scar, nail stain, yellowing of skin, dark circles under eyes, and the like. The composition may include additional ingredients accordingly for a colored cosmetic, moisturizer, cleanser, toner, and the like.
Owner:NEW AVON LLC
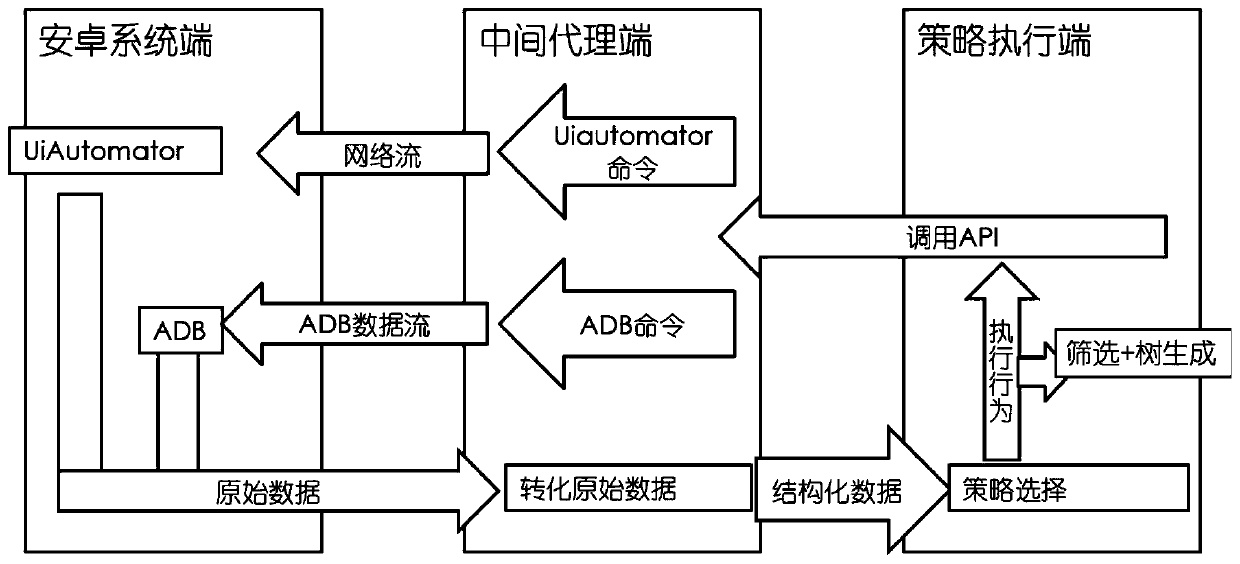
Anti-reinforcement fast detection method of Android platform cloning application program
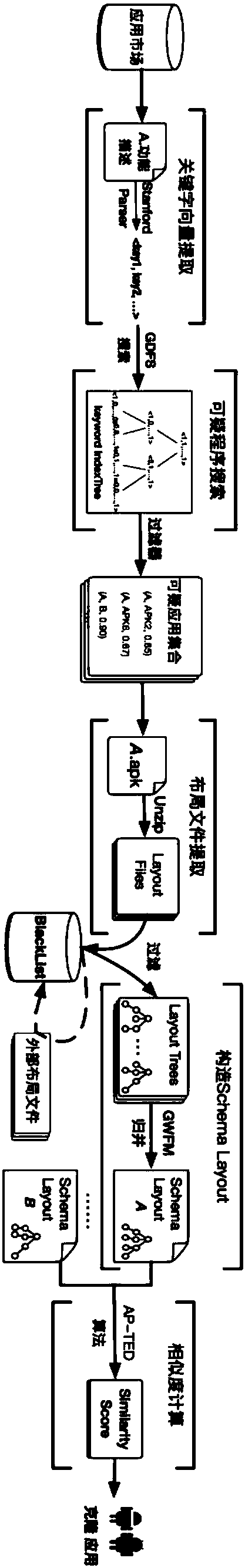
ActiveCN107622201AAvoid the impact of hardening technologyAvoid influencePlatform integrity maintainanceTheoretical computer scienceApplication software
The invention discloses an anti-reinforcement fast detection method of an Android platform cloning application program. The method comprises a preprocessing stage and an accurate detection stage. At the preprocessing stage, keywords are extracted from function description of the application program by using the natural language processing technology so as to construct vectors, and suspicious cloning application program pairs with similar functions are quickly searched by using an improved searching method based on a balanced binary tree. At a formal detection stage, the invention provides an application program birthmark that is based on interface layout features and are completely independent from source codes, so that the influence of the reinforcement technology can be effectively defended, and finally the similarity between the suspicious cloning application program pairs can be accurately calculated by using a similarity calculation method based on a tree editing distance. By adoption of the anti-reinforcement fast detection method, the interference of the reinforcement technology can be effectively defended, meanwhile the fast detection of the cloning applications can be achieved, and thus the practicability is very high.
Owner:HUNAN UNIV
Software plagiarism detection method based on dynamic key instruction sequence birthmark
ActiveCN103577323BNo limitationsStrong resistanceSoftware testing/debuggingObfuscationDynamic instrumentation
The invention provides a dynamic key command sequence birthmark-based software plagiarism detecting method, which comprises the steps of (1) monitoring a program to be analyzed based on a dynamic instrumentation and identifying and recording a key command by combining with dynamic stain analysis in real time; (2), preprocessing the recorded key command sequence, stripping an operation number and extracting a mnemonic sequence; (3) on the basis, respectively generating a dynamic key command sequence birthmark for two software to be detected; (4) calculating the similarity of the birthmarks; (5) making the design of plagiarism or not by the average value of the similarity of the birthmarks and a given threshold value. The dynamic key command sequence birthmark-based software plagiarism detecting method directly aims at the binary codes without the need of existence of source codes and has more practical significance; the detection means does not depend on a specific platform or programming language, has wider application range and has better resistance to the code obfuscation technology with reversed semantics, so the detection capability of deep plagiarism is improved.
Owner:XI AN JIAOTONG UNIV
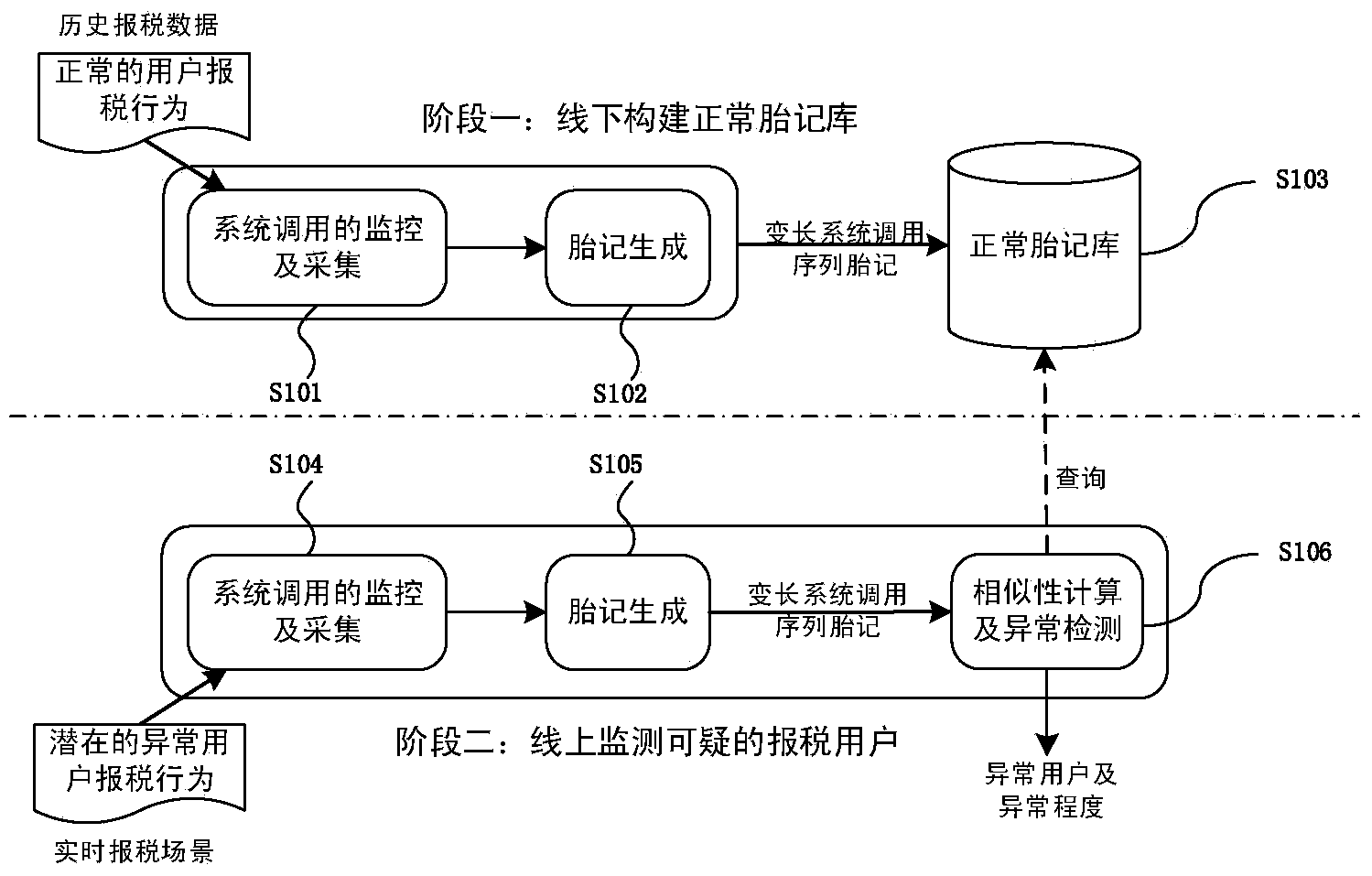
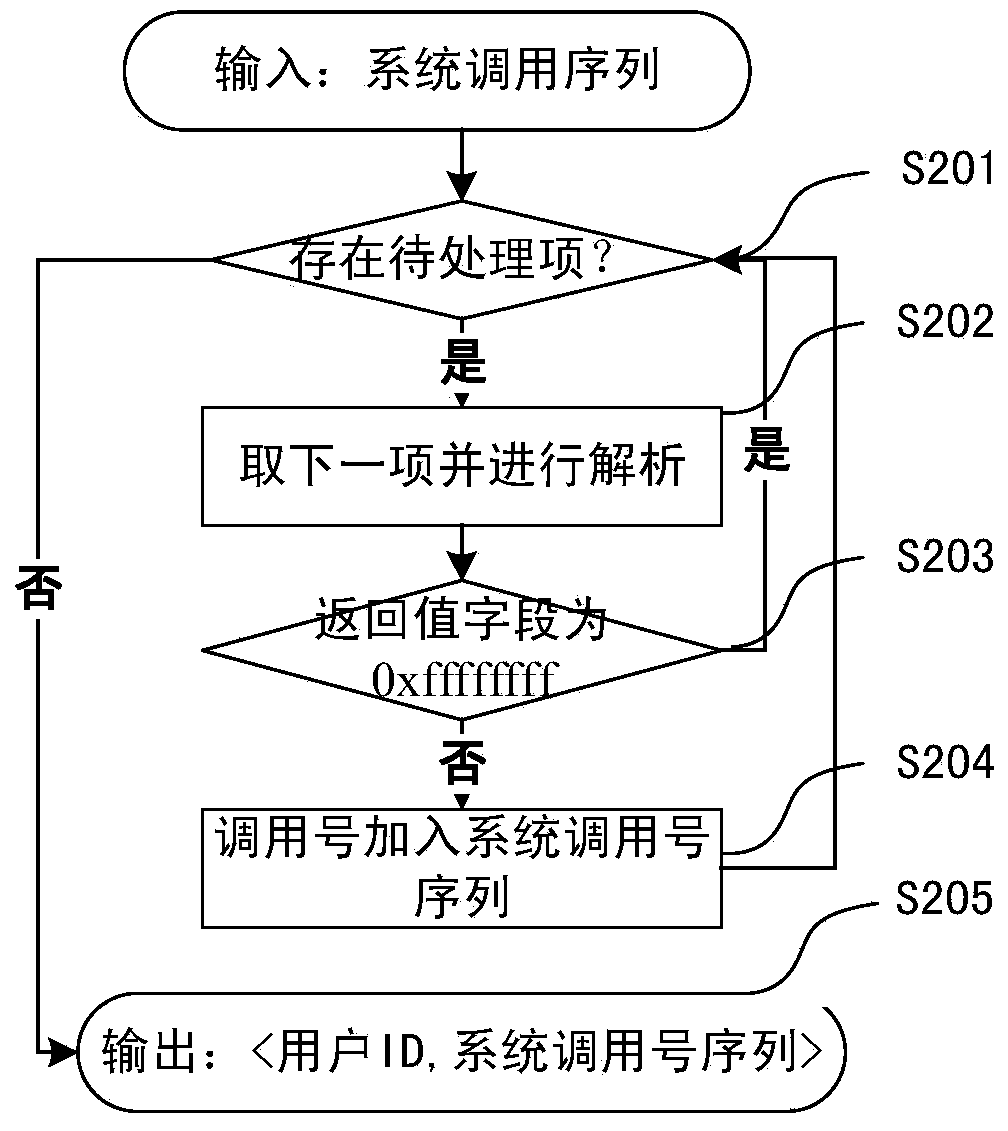
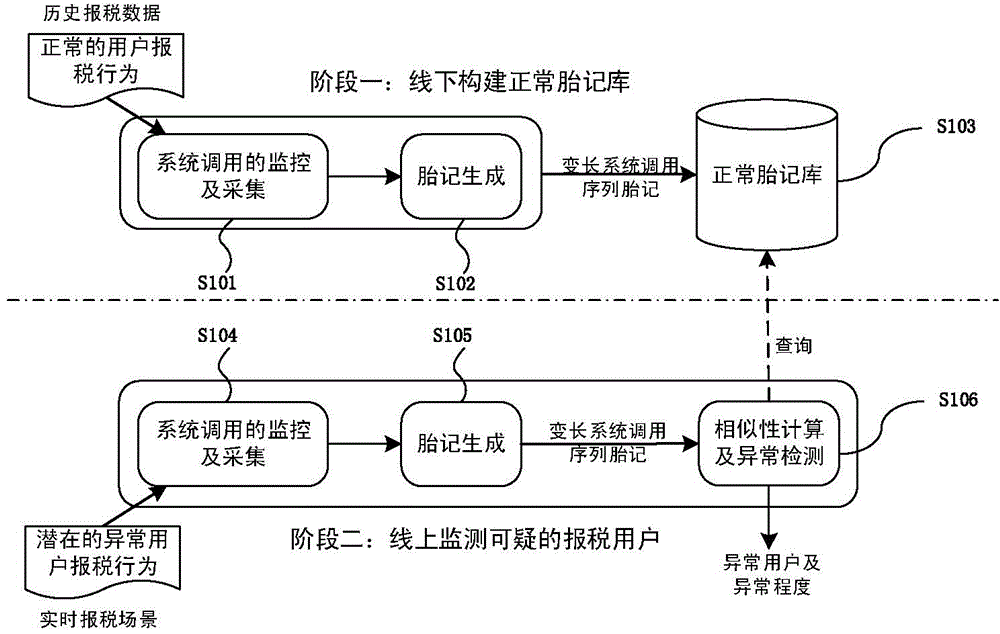
Online taxpayer identity recognition method based on variable-length system calling sequence birthmarks
ActiveCN104077404AThe method is novel and uniqueAvoid large-scale service performance degradationComputer security arrangementsSpecial data processing applicationsSoftware systemInternet privacy
The invention provides an online taxpayer identity recognition method based on variable-length system calling sequence birthmarks. The online taxpayer identity recognition method is divided into two stages, namely the stage of establishing an offline normal birthmark library based on normal historical tax behaviors of a user, and the stage of recognizing the user identity in real time for the real-time tax scene of the user; the method is used for realizing real-time online recognition on the behaviors and the identities of the taxpayers by extracting the system calling sequence characteristics that the software system shows in the operation processes of different taxpayers, and therefore, the recognition of the identifies of the taxpayers can be realized in case that the identity authentication information of the taxpayers is stolen.
Owner:SERVYOU SOFTWARE GRP
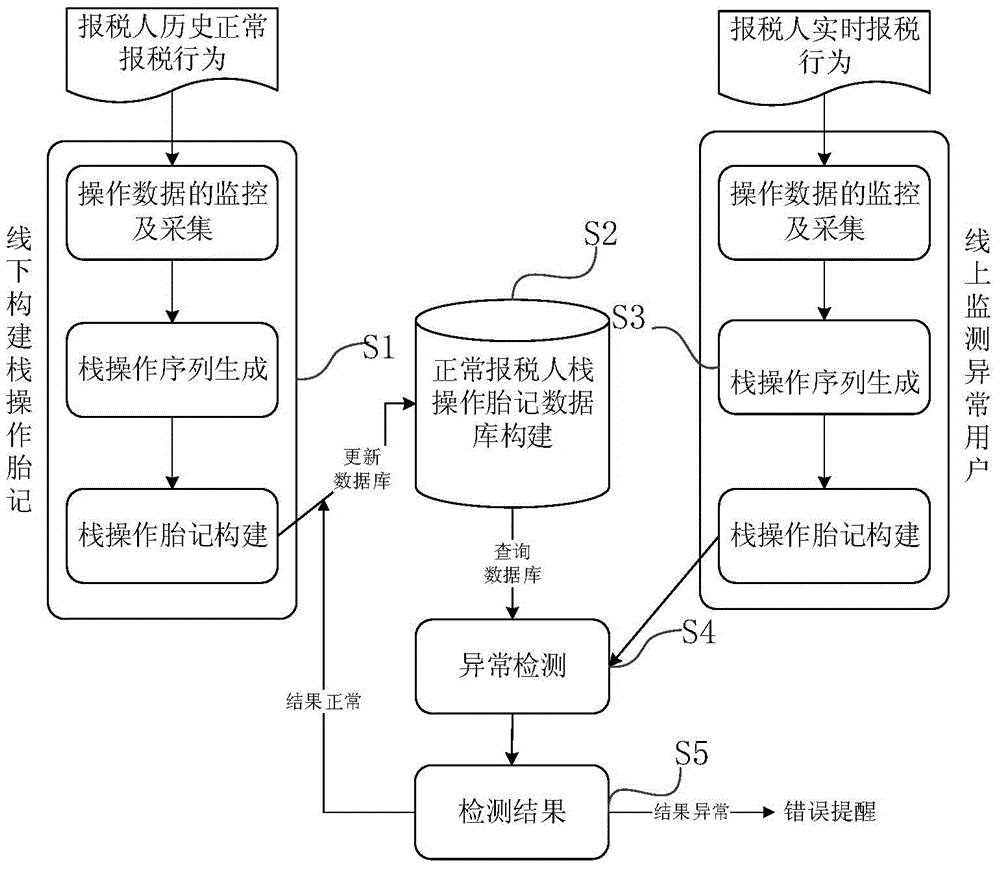
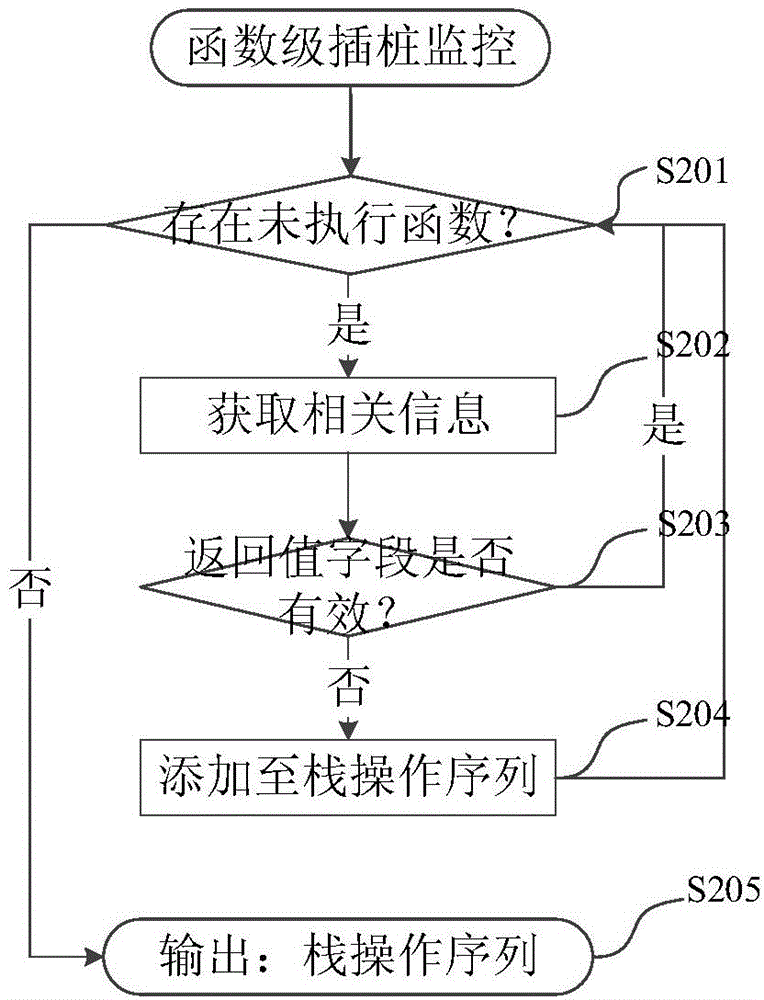
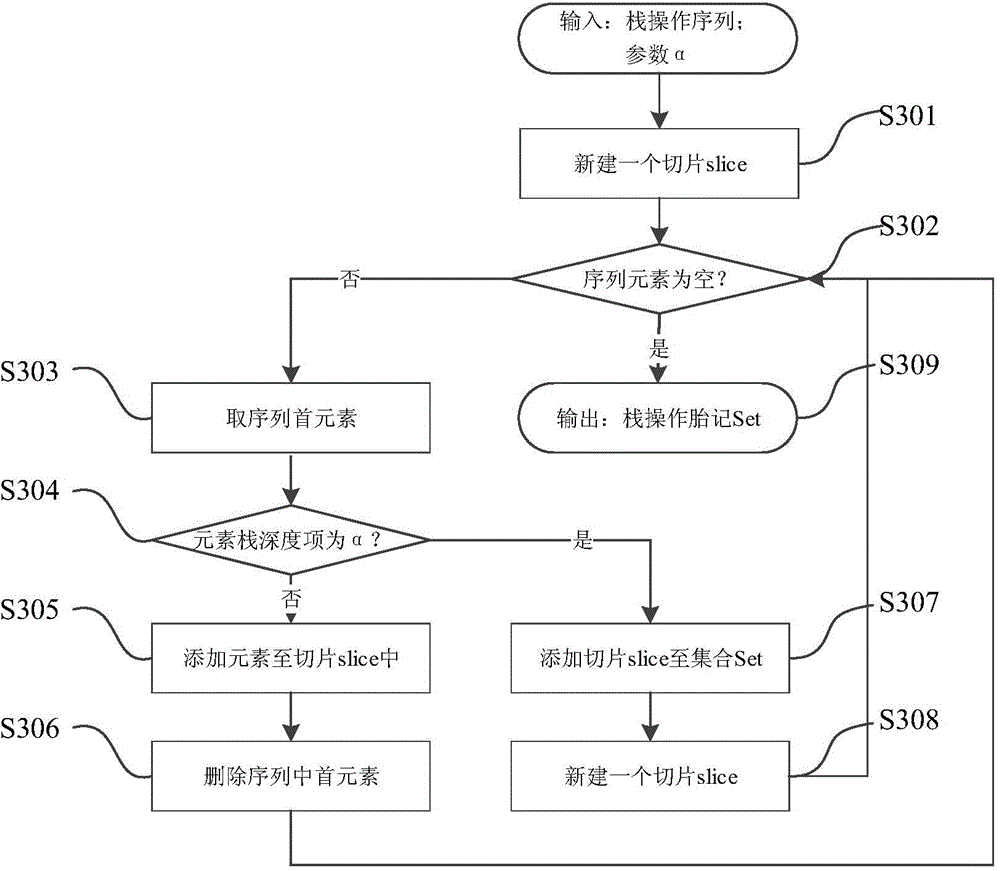
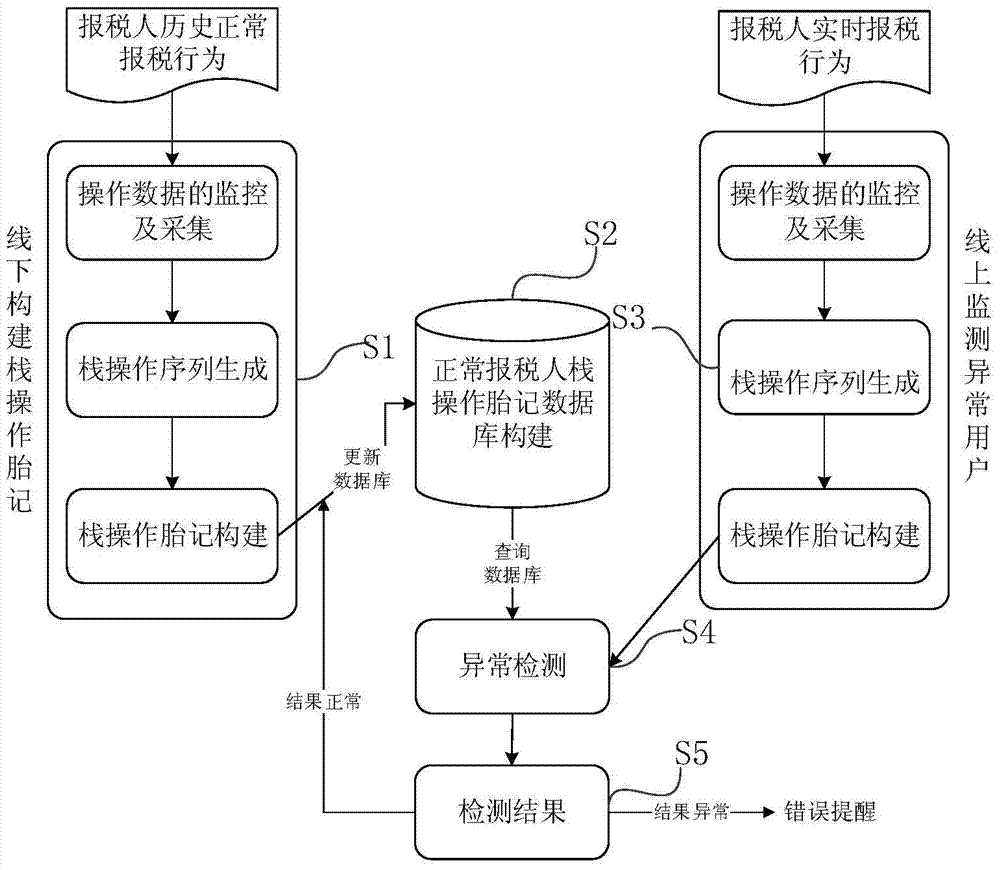
Tax declarer identity dynamic authentication method based on operand stack birthmarks
ActiveCN104091283AThe method is novel and uniqueReduce loadFinanceDigital data authenticationInternet privacyOperand
The invention provides a tax declarer identity dynamic authentication method based on operand stack birthmarks. The method mainly comprises the steps of off-line normal birthmark library construction based on tax declarer historical normal tax declaration behaviors, and user identity monitoring and identity abnormality identification in a user real-time tax declaration scene. According to the tax declarer identity dynamic authentication method based on the operand stack birthmarks, through different characteristics of behaviors of different users when tax declaration is completed through software, behavior characteristics of the software are abstracted, corresponding birthmark-operand stack birthmarks can be constructed, legality of the tax declaration behaviors of the users is determined according to similarity of the birthmarks, and on-line authentication of the identity of the users is carried out according to similarity of the birthmarks.
Owner:SERVYOU SOFTWARE GRP
Pro-drugs of nsaias with very high skin and membranes penetration rates and their new medicinal uses
ActiveUS20100172960A1Low pharmacologic effectToxic burdenOrganic active ingredientsBiocideDiseaseSolubility
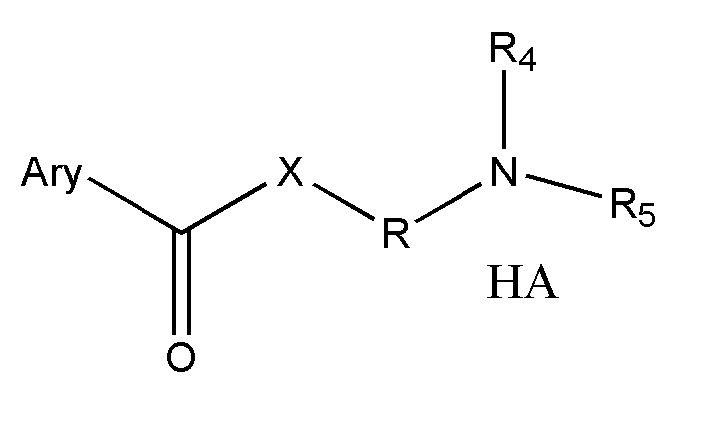
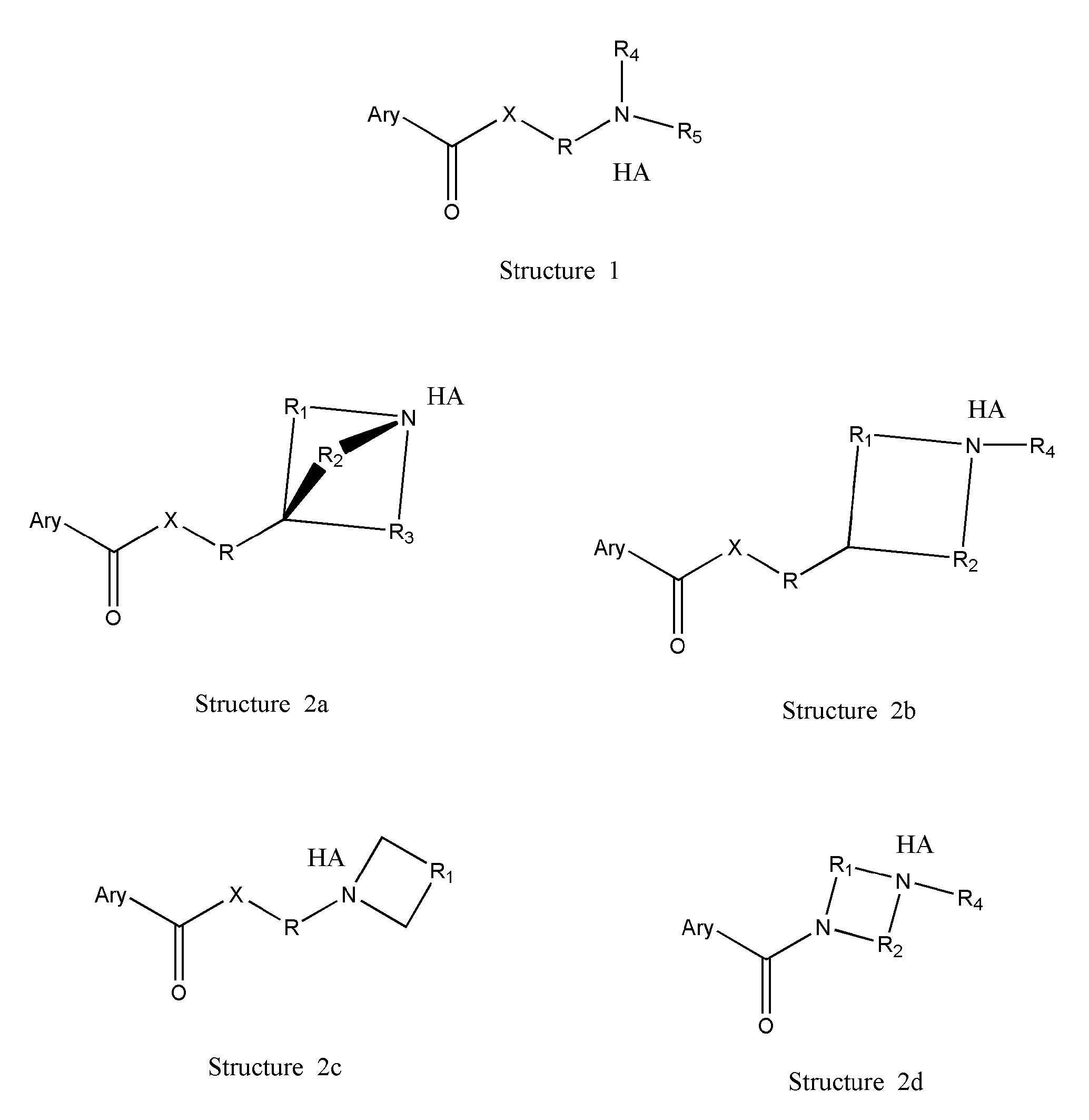
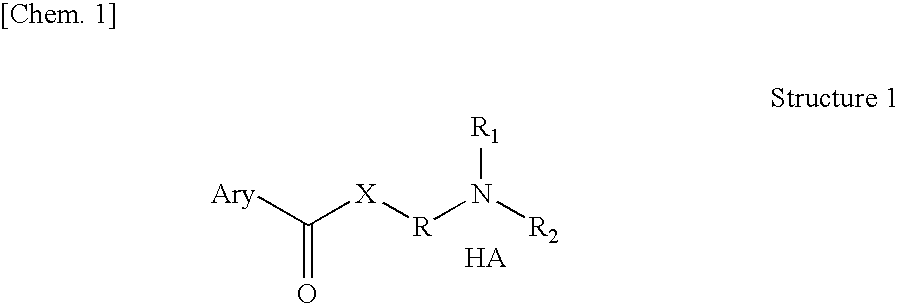
The novel positively charged pro-drugs of NSAIAs in the general formulas (1, 2a, 2b, 2c, or 2d) “Structure 1, 2a, 2b, 2c, or 2d” were designed and synthesized. The compounds of the general formulas (1, 2a, 2b, 2c, or 2d) “Structure 1, 2a, 2b, 2c, or 2d” indicated above can be prepared from metal salts, organic base salts, or immobilized base salts of NSAIAs with suitable halide compounds. The positively charged amino groups in the pro-drugs in this invention largely increase the solubility of the drugs in water and will bond to the negative charge on the phosphate head group of membrane. Thus, the local concentration of the outside of the membrane or skin will be very high and will facilitate the passage of these pro-drugs from a region of high concentration to a region of low concentration. This bonding will disturb the membrane a little bit and may make some room for the lipophilic portion of the pro-drug. When the molecules of membrane move, the membrane may “crack” a little bit due to the bonding of the pro-drug. This will let the pro-drug insert into the membrane. At pH 7.4, only about 99% of the amino group is protonated. When the amino group is not protonated, the bonding between the amino group of the pro-drug and the phosphate head group of the membrane will disassociate, and the pro-drug will enter the membrane completely. When the amino group of the pro-drug flips to the other side of the membrane and thus becomes protonated, then the pro-drug is pulled into the cytosol, a semi-liquid concentrated aqueous solution or suspension. These pro-drugs can be used for treating and preventing diabetes (type I or / and type II), abnormal blood glucose and lipid levels, stroke, heart attack, and other heart and vascular diseases Alzheimer's diseases, Parkinson's diseases and other neurodegenerative diseases, psoriasis, discoid lupus erythematosus, systemic lupus erythematosus (SLE), autoimmune hepatitis, multiple sclerosis (MS), and other autoimmune diseases, amyotrophic lateral sclerosis (ALS), oculopharyngeal muscular dystrophy (OPMD), and other muscle disorders, inflamed hemorrhoids, cryptitis, other inflammatory conditions of the anorectum, and pruritus ani, prostatitis, prostatocystitis, varicose veins, autoimmune liver inflammation, autoimmune kidney inflammation, vein inflammation and other inflammations, skin cancers, breast cancer, colon-rectum cancer, oral cancer, and other cancers, scars, abnormal vascular skin lesions, birthmarks, moles (nevi), skin tags, aging spots (liver spots), and other skin disorders. These pro-drugs can be administered transdermally without the help of skin penetration enhancers.
Owner:TECHFIELDS BIOCHEM CO LTD
Ointment paste for eliminating birthmark and preparation method of ointment paste
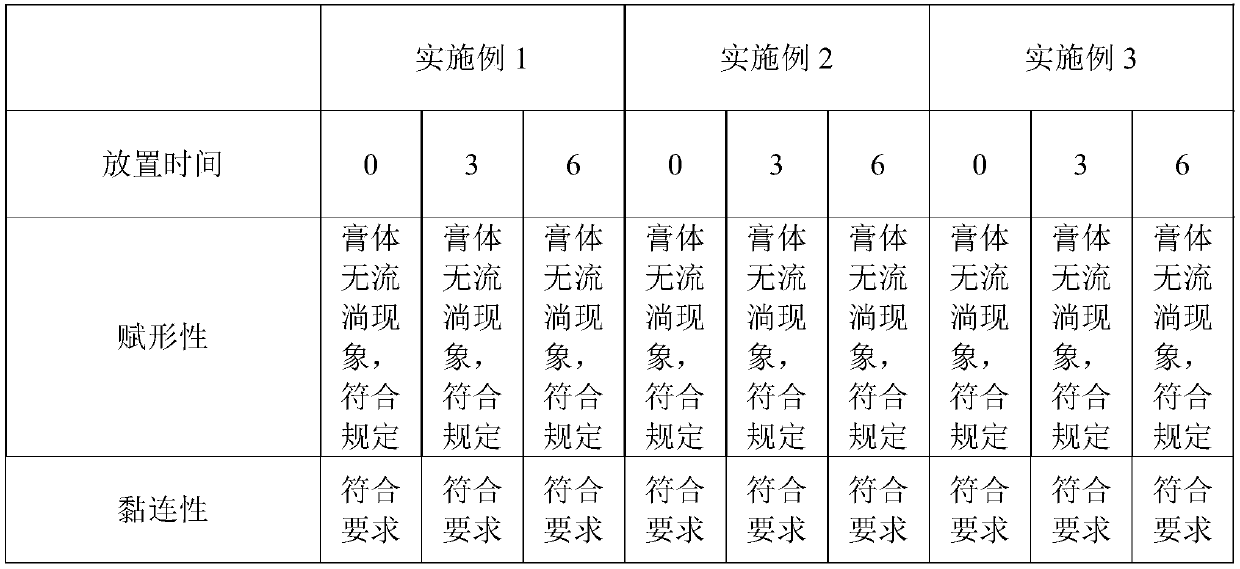
InactiveCN110384764APromote maturityProtect healthDermatological disorderSheet deliveryCross-linkReflux extraction
The invention discloses an ointment paste for eliminating a birthmark and a preparation method of the ointment paste. The ointment paste is prepared from the following raw materials of a Chinese herbextract, an adhesive, a humectant, a cross-linking agent, a filling agent and an appropriate permeation enhancer. The preparation method of the ointment paste for eliminating the birthmark comprises the following steps that S1, various raw materials are well prepared; S2, part of medicinal materials are soaked for 1-2 h by using 75% of ethyl alcohol; S3, then reflux extraction is conducted for 1-2h, and extraction is conducted for 2-3 times; S4, then filter liquid is taken, water is used for reflux extraction of filter residue and other medicinal materials, filter liquid is taken, and filterresidue is abandoned; S5, then the two times of the filter liquid are concentrated; S6, the extractive, the filling agent and the cross-linking agent are mixed to obtain a component 1; S7, the adhesive is mixed with water to serve as a component 2, and the wetting agent and the humectant and the permeation enhancer serve as a component 3; and S8, the three components are mixed and stirred, and then coat on non-woven fabrics, and drying is conducted to obtain the ointment paste.
Owner:江苏博润医疗集团有限公司
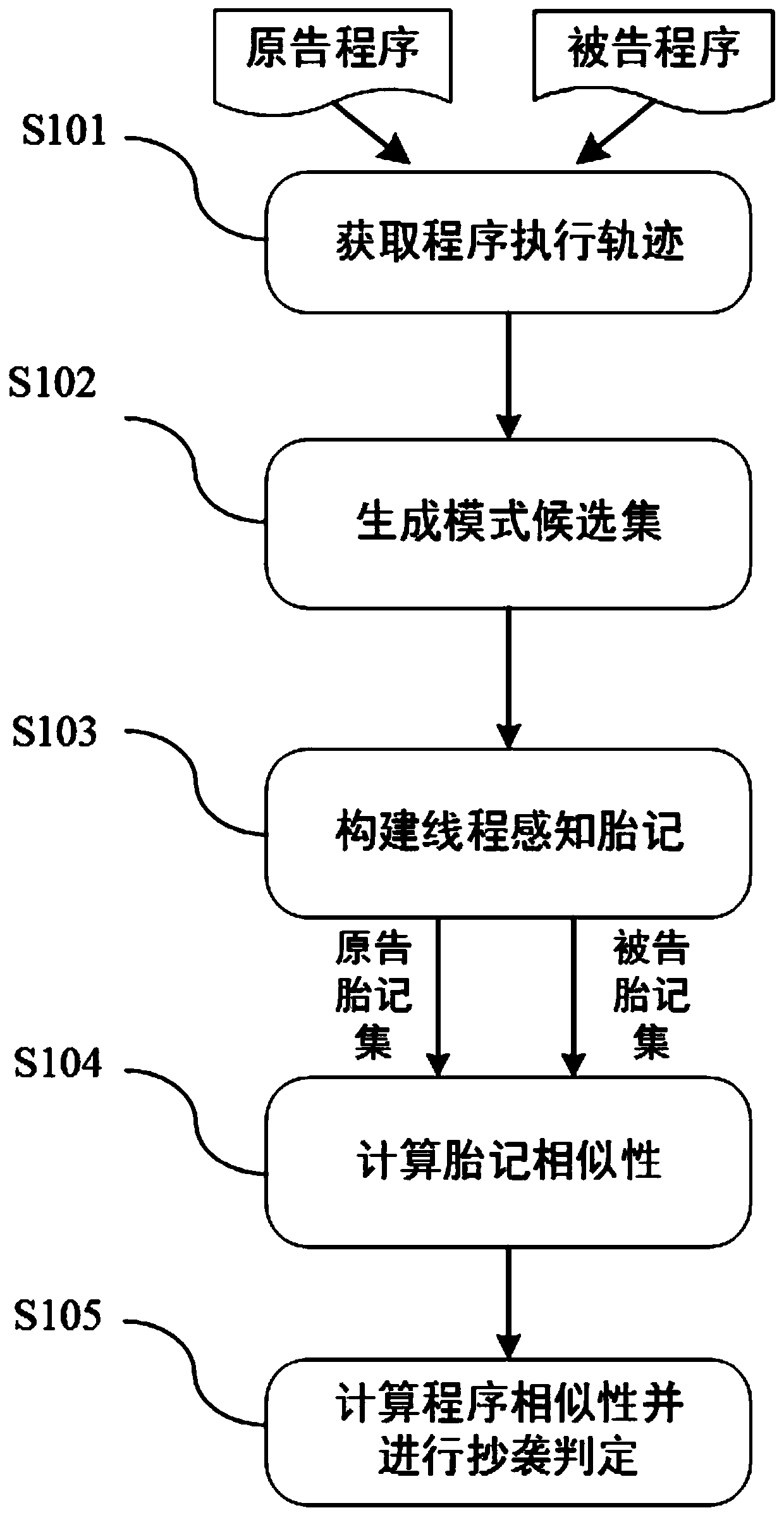
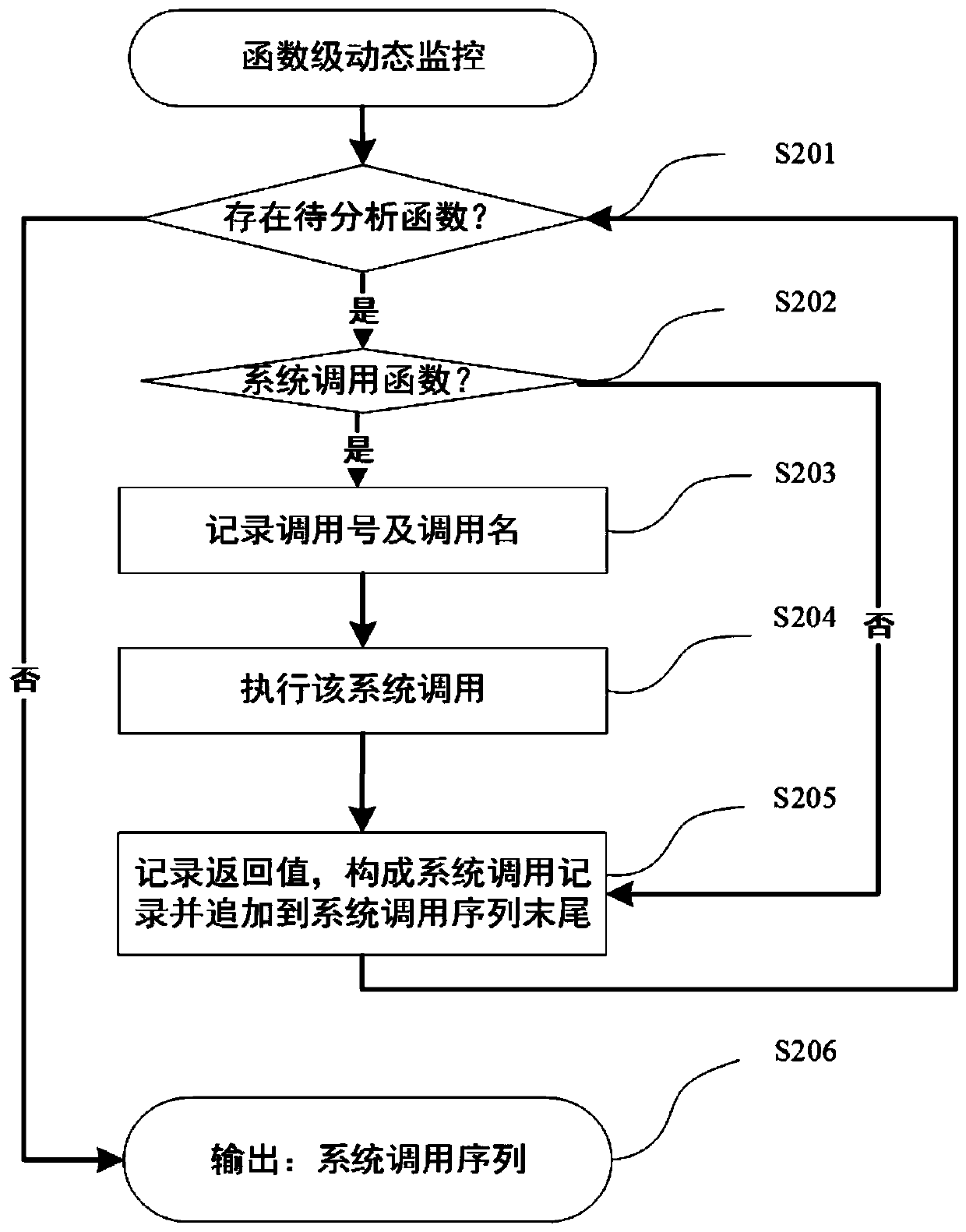
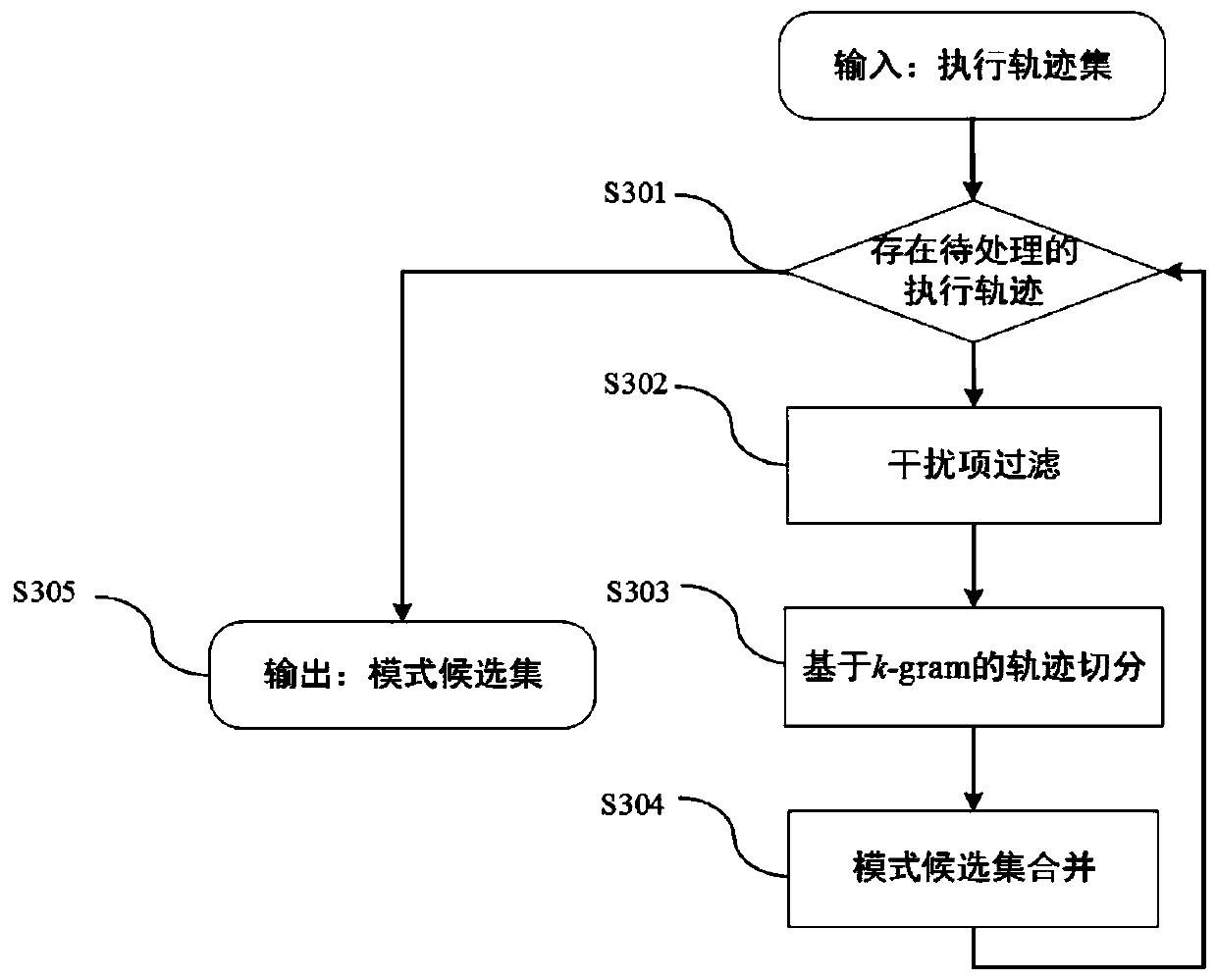
Multi-thread program plagiarism detection method based on frequent pattern mining
ActiveCN110532739AObfuscation worksEffective handling of obfuscation meansProgram/content distribution protectionPlagiarism detectionTheoretical computer science
The invention discloses a multi-thread program plagiarism detection method based on frequent pattern mining. The method comprises the following steps: 1) dynamically monitoring to obtain a plurality of execution tracks of a program under the condition of multiple times of execution of the same input; 2) preprocessing the program execution trajectory set to generate a mode candidate set; 3) utilizing a frequent pattern mining algorithm to process the pattern candidate set, generating a frequent pattern set, performing Hash processing, and then constructing a thread perception birthmark; 4) calculating the similarity between the original announcement program birthmarks and the announced program birthmarks under specific input; and 5) making plagiarism judgment and outputting a detection result based on the mean value of the birthmark similarity under the plurality of inputs and a given threshold value. According to the method, the executable program is directly used as an analysis object, and program source codes are not needed; according to the method, frequent pattern mining is utilized to extract a behavior pattern from a plurality of execution tracks corresponding to multiple times of program operation under the same input to generate a thread perception birthmark, so that the interference of thread interleaving uncertainty is greatly reduced.
Owner:XIAN UNIV OF POSTS & TELECOMM
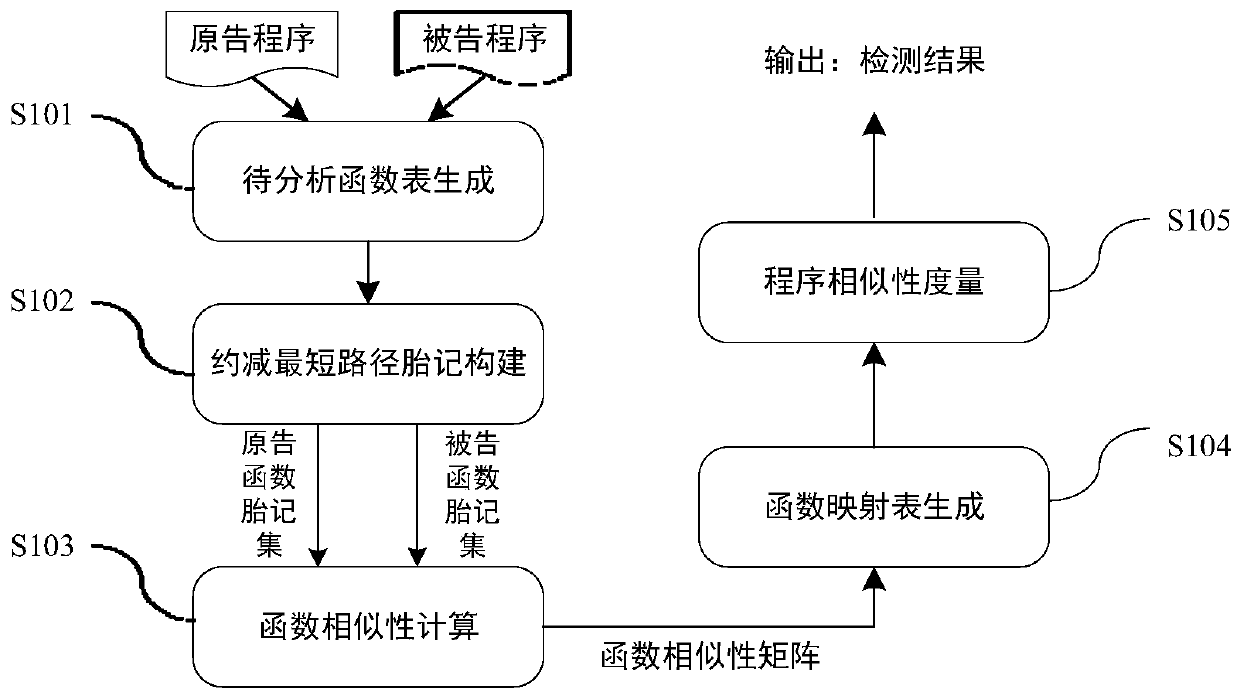
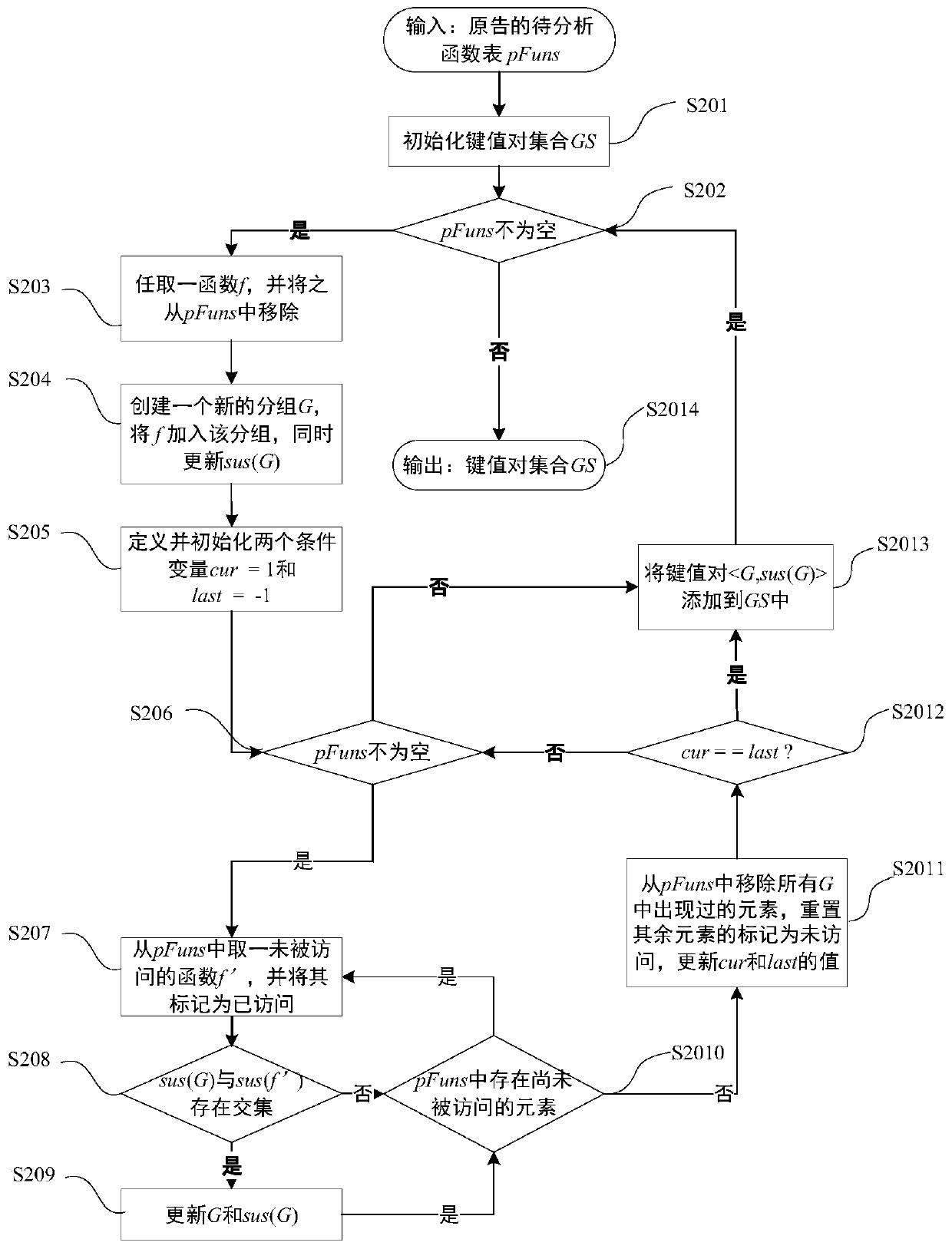
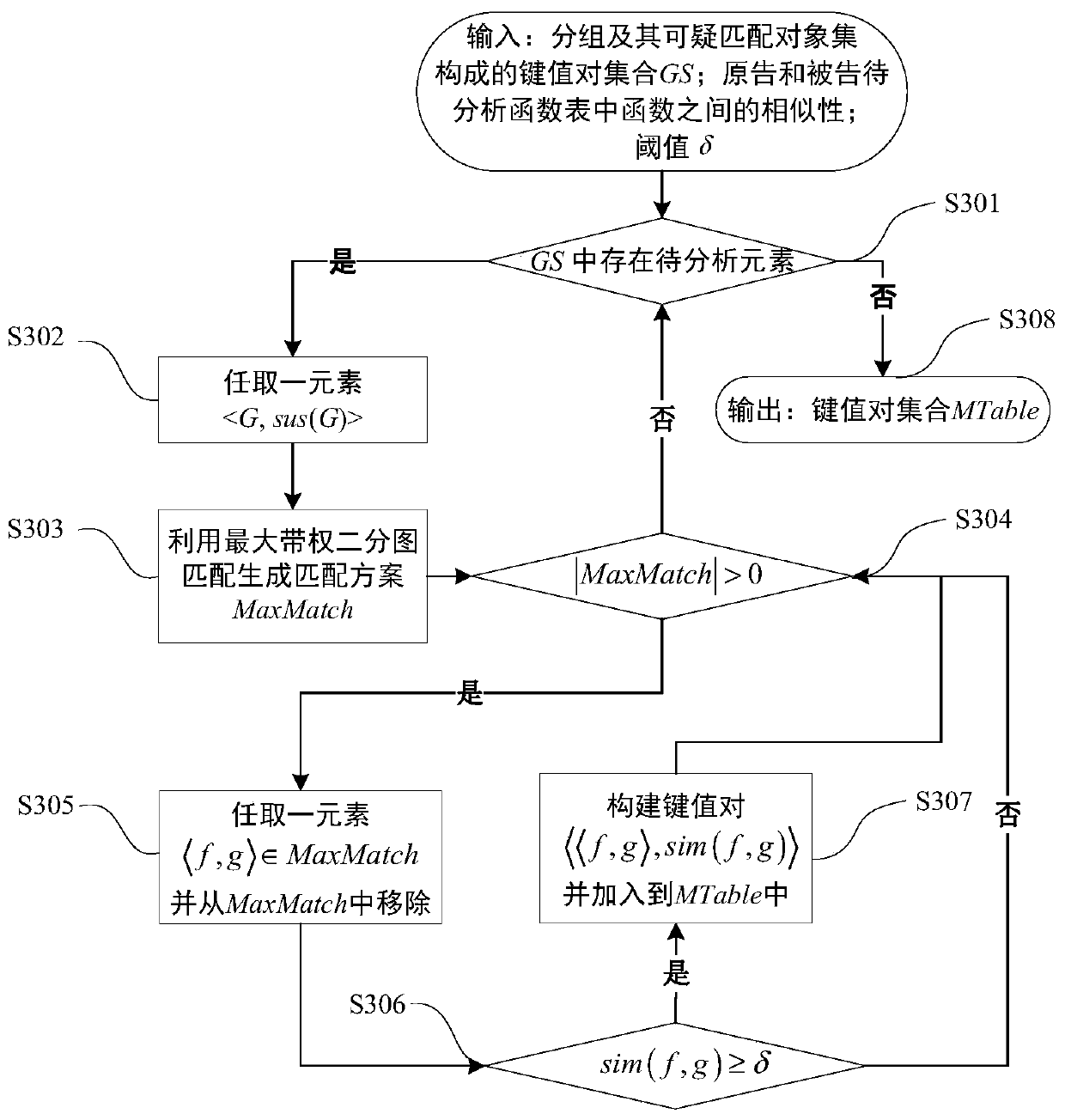
Software plagiarism detection method based on reduced shortest path birthmarks
ActiveCN110083534AEffective support for partial plagiarismIncrease coverageSoftware testing/debuggingFuzzy hashingNODAL
The invention discloses a software plagiarism detection method based on reduced shortest path birthmarks, which comprises the following steps: 1) statically disassembling a to-be-analyzed program to generate a to-be-analyzed function table; 2) for each function, searching a shortest path set from an entrance node of the control flow graph to other nodes, performing path reduction and abstraction,and constructing a reduced shortest path birthmark; 3) calculating the similarity between the reduced path birthmarks by using fuzzy hashing to serve as a measure of the similarity between functions;4) grouping the functions, and generating a function mapping table through maximum weighted bipartite graph matching; 5) calculating the similarity between the original program and the announced program, carrying out plagiarism judgment, and outputting a detection result. Through path searching and abstraction, the code confusion resisting capacity of the method is improved, and through fuzzy hashing and grouping matching, it is guaranteed that the method is applied to scalability of a large-scale real binary program.
Owner:XIAN UNIV OF POSTS & TELECOMM
External ointment
InactiveCN108310273ARelieve painSimple treatmentAerosol deliveryOintment deliveryAdemetionineExternal Ointment
The invention discloses external ointment. The external ointment is prepared from the traditional-Chinese-medicine raw materials in parts by weight: 3-8 parts of ammonium chloride, 3-8 parts of bungecherry seed, 2-5 parts of peach kernel, 2-5 parts of almond kernel, 2-5 parts of coix seed and 2-5 parts of castor bean. In preparation, the traditional-Chinese-medicine raw materials are crushed to be 80-100 meshes, and then are mixed uniformly, and the mixture is blended to be pasty by using baijiu, and is stored under the normal-temperature sealing c ondition. The external ointment disclosed bythe invention is prepared by adopting the pure-natural traditional-Chinese-medicine raw materials, and can be applied to a diseased part of a patient; the treatment method is simple, realizes safe clinical application and an obvious treating effect, and can relieve the pain of the patient; the external ointment can be used for treating warts, birthmarks, hemangioma, lipomyoma, syringoma, freckles, nevi and corns.
Owner:胡映奇
A rapid detection method for anti-hardening android platform clone applications
ActiveCN107622201BAvoid the impact of hardening technologyDetection speedPlatform integrity maintainanceApplication softwareBinary tree
The invention discloses a fast detection method for an anti-hardening Android platform clone application program, which includes a preprocessing stage and an accurate detection stage. In the preprocessing stage, by using natural language processing technology to extract keywords from the functional description of the application to construct a vector, the improved search method based on a balanced binary tree is used to quickly find pairs of suspicious clone applications with similar functions. In the formal detection stage, the present invention proposes an application birthmark based on interface layout features and completely independent of source code, which can effectively resist the influence of reinforcement technology, and finally uses the similarity calculation method based on tree-based edit distance, which can accurately calculate Find out the similarity between pairs of suspicious clone programs. The invention can effectively resist the interference of the reinforcement technology, and at the same time realize the fast detection of the cloning application, and has strong practicability.
Owner:HUNAN UNIV
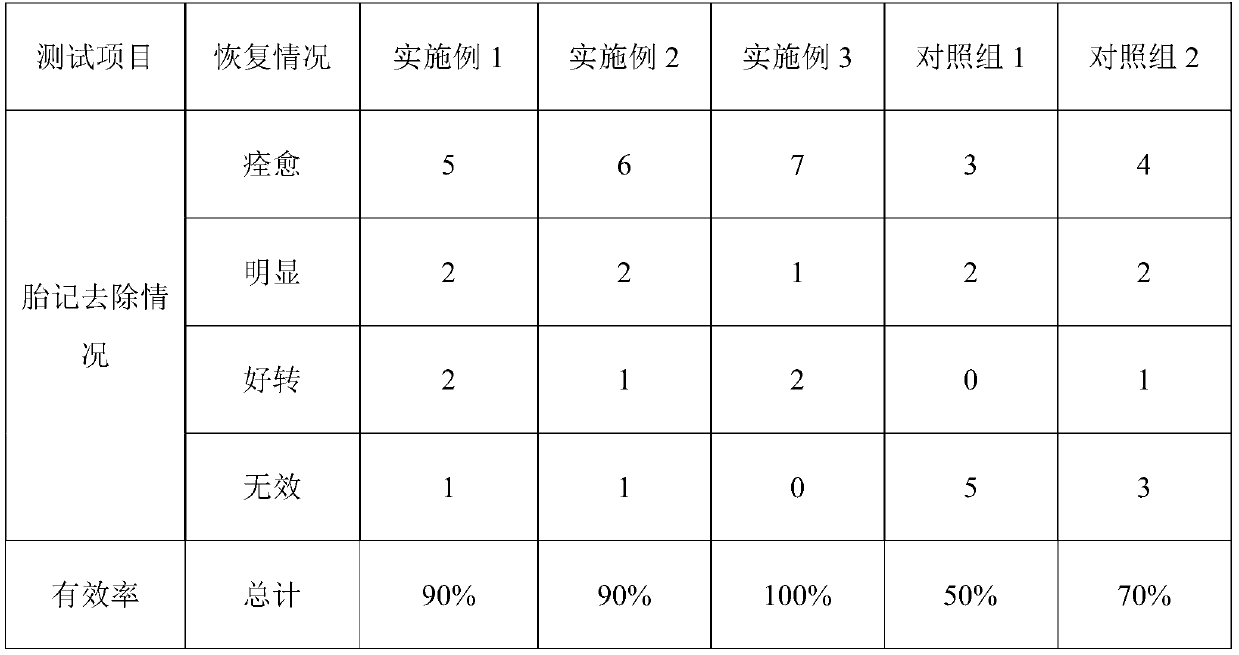
Medicine for treating birthmarks
InactiveCN109125603ANo side effectsNo drug dependenceAnthropod material medical ingredientsDispersion deliverySide effectMedicine
A medicine for treating birthmarks is characterized by being prepared from 50 g of radix angelicae, 50 g of radix ampelopsis, 50 g of rhizoma atractylodis macrocephalae, 50 g of rhizoma bletillae, 50g of white muscardine silkworms, 50 g of white lotus nuts and 50 g of white poria cocos. A preparation method includes the steps that all the medicinal materials are ground into fine powder, an appropriate amount of clean water is poured in, and after uniform mixing, the medicine is taken after meals tree times a day. The medicine solves the problem that an existing medicine for treating birthmarks is large in side effect, addictive, long in treatment time and high in relapse rate after medicine withdrawal and cannot achieve a radical cure; the medicine is suitable for treating birthmarks.
Owner:杨超
Tax declarer identity dynamic authentication method based on operand stack birthmarks
ActiveCN104091283BThe method is novel and uniqueReduce loadDigital data authenticationProgram/content distribution protectionInternet privacyOperand
The invention provides a tax declarer identity dynamic authentication method based on operand stack birthmarks. The method mainly comprises the steps of off-line normal birthmark library construction based on tax declarer historical normal tax declaration behaviors, and user identity monitoring and identity abnormality identification in a user real-time tax declaration scene. According to the tax declarer identity dynamic authentication method based on the operand stack birthmarks, through different characteristics of behaviors of different users when tax declaration is completed through software, behavior characteristics of the software are abstracted, corresponding birthmark-operand stack birthmarks can be constructed, legality of the tax declaration behaviors of the users is determined according to similarity of the birthmarks, and on-line authentication of the identity of the users is carried out according to similarity of the birthmarks.
Owner:SERVYOU SOFTWARE GRP
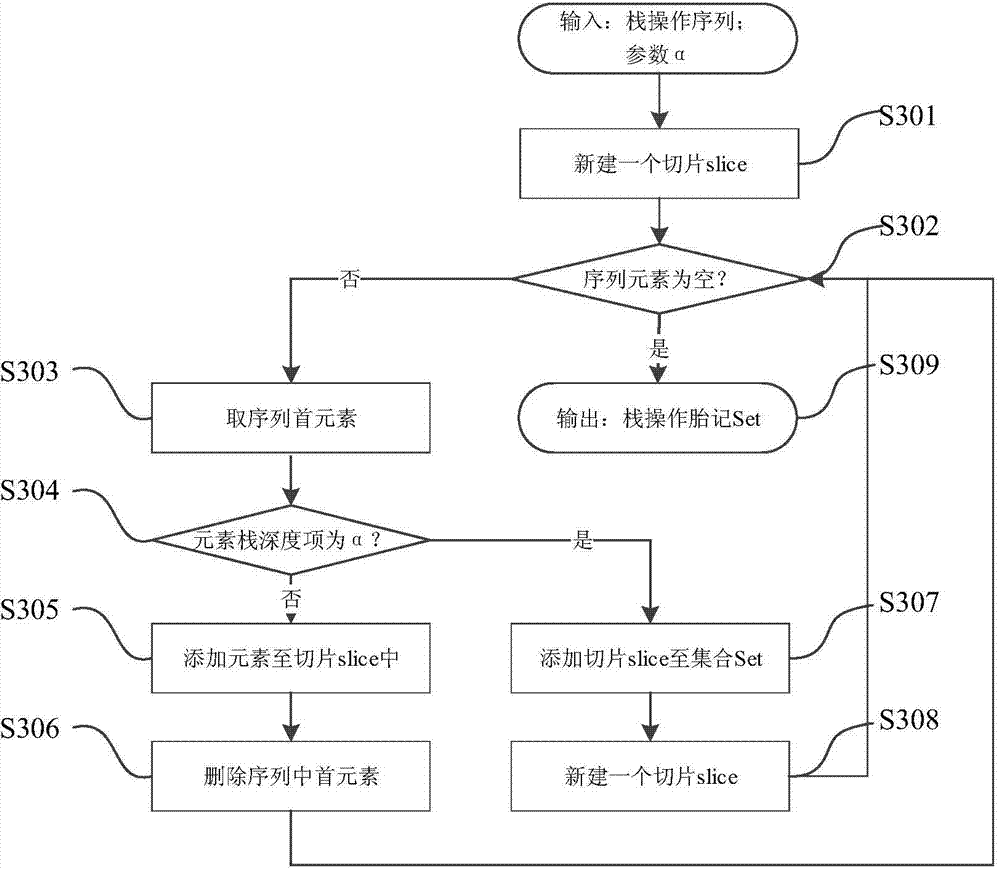
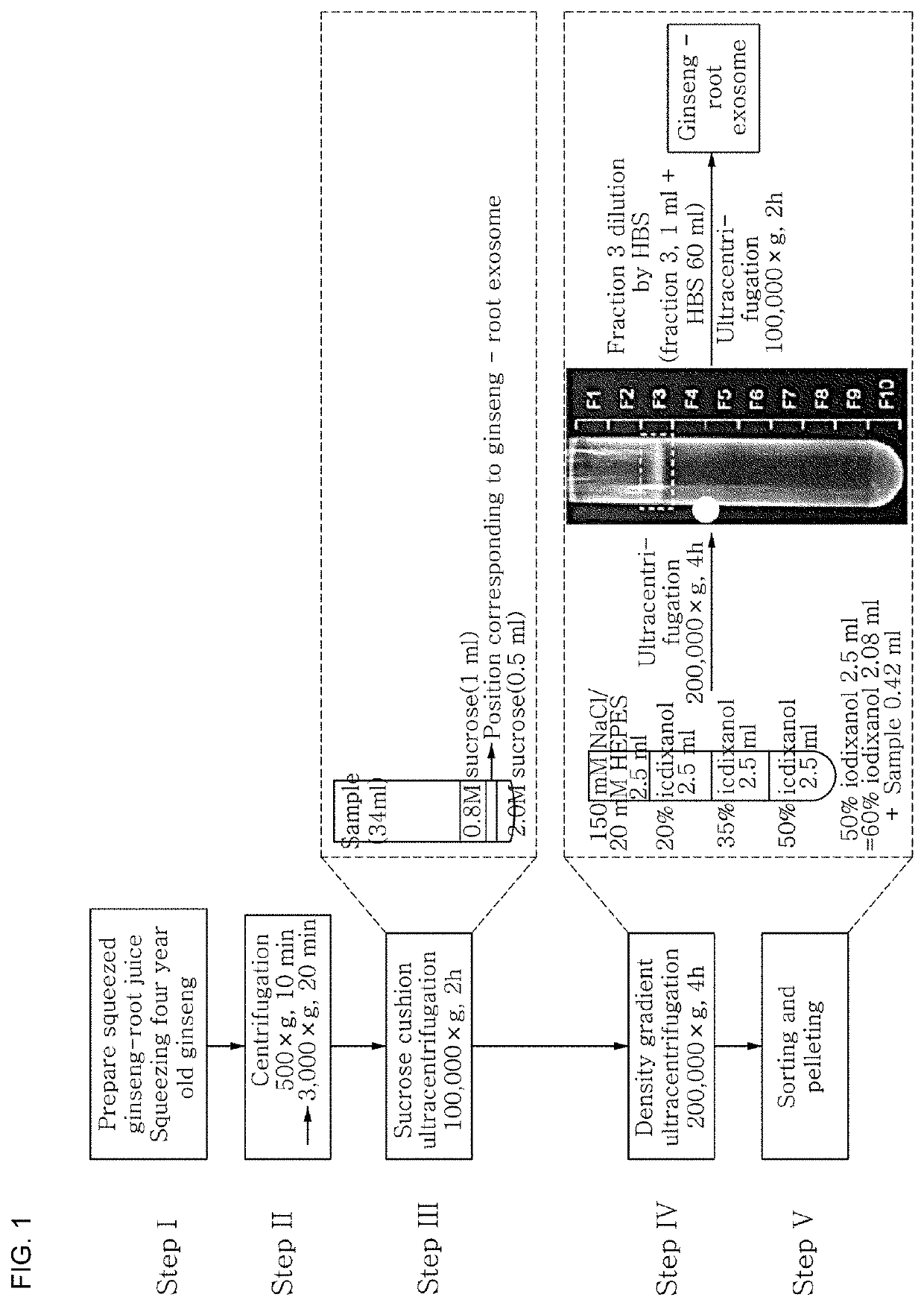
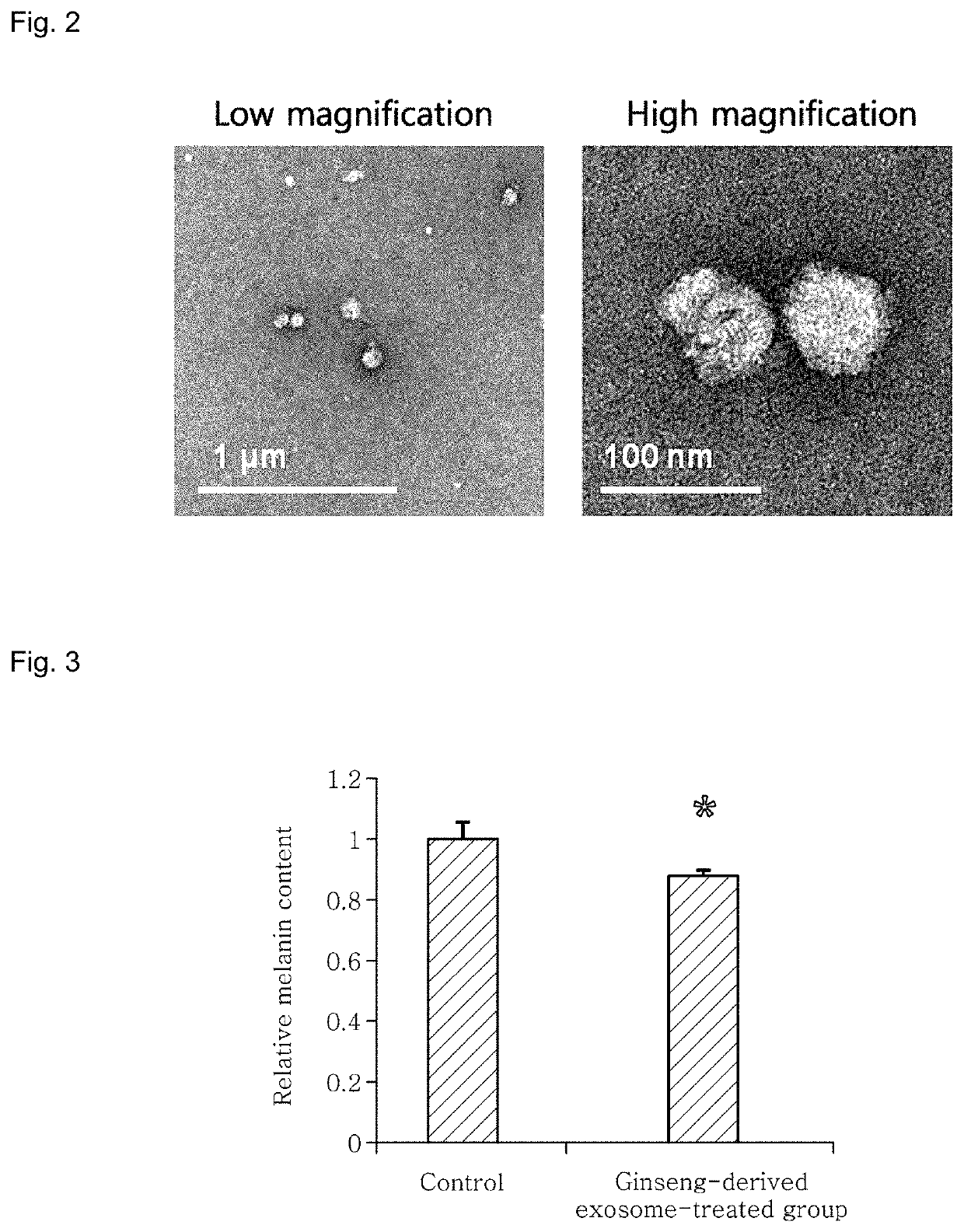
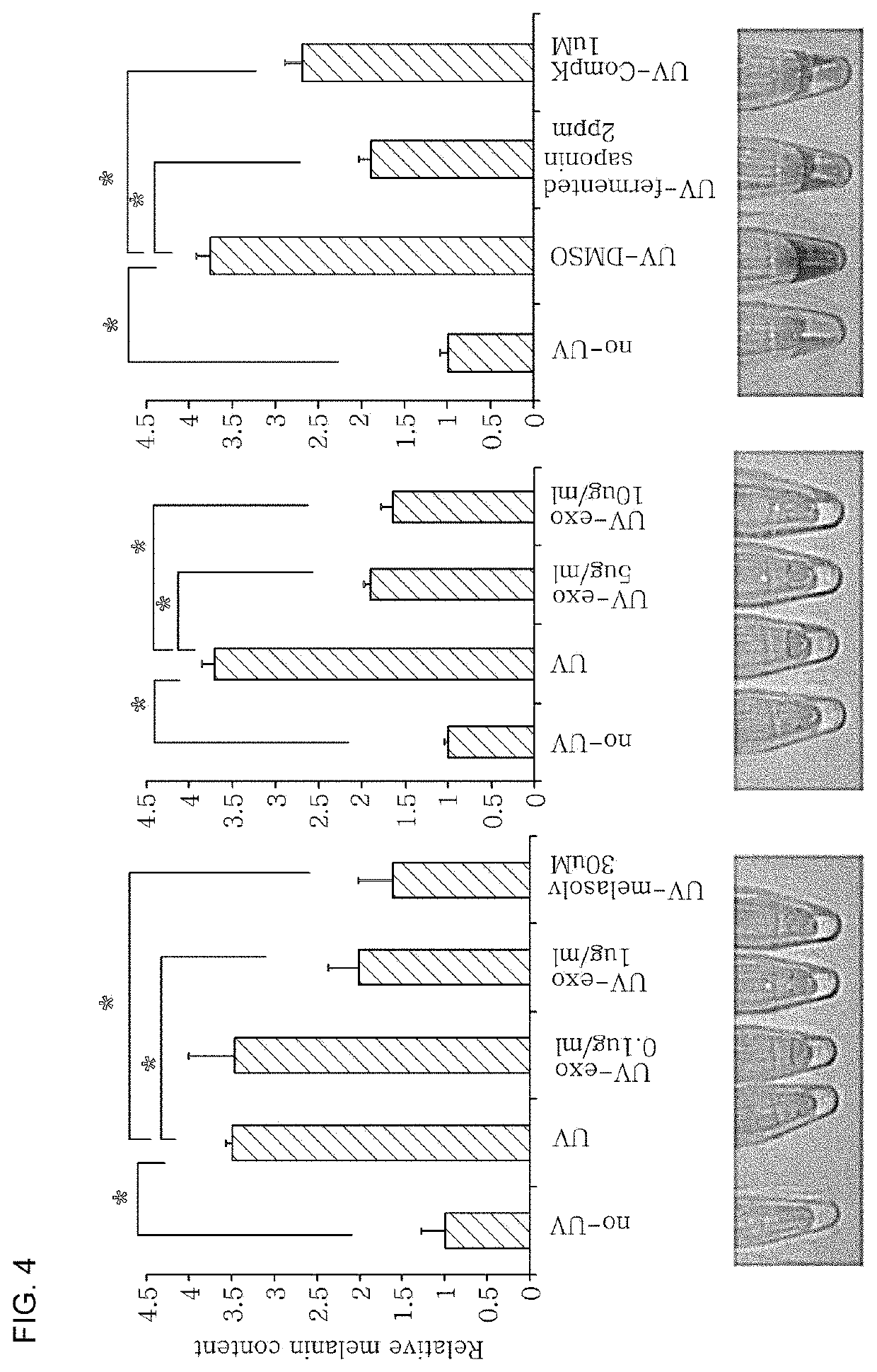
Lightening composition comprising ginseng-derived exosome-like vesicles
Owner:AMOREPACIFIC CORP
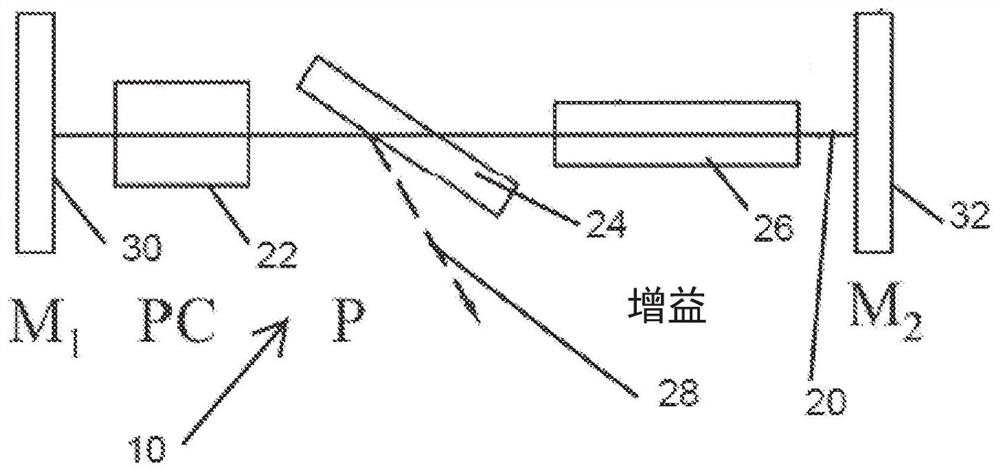
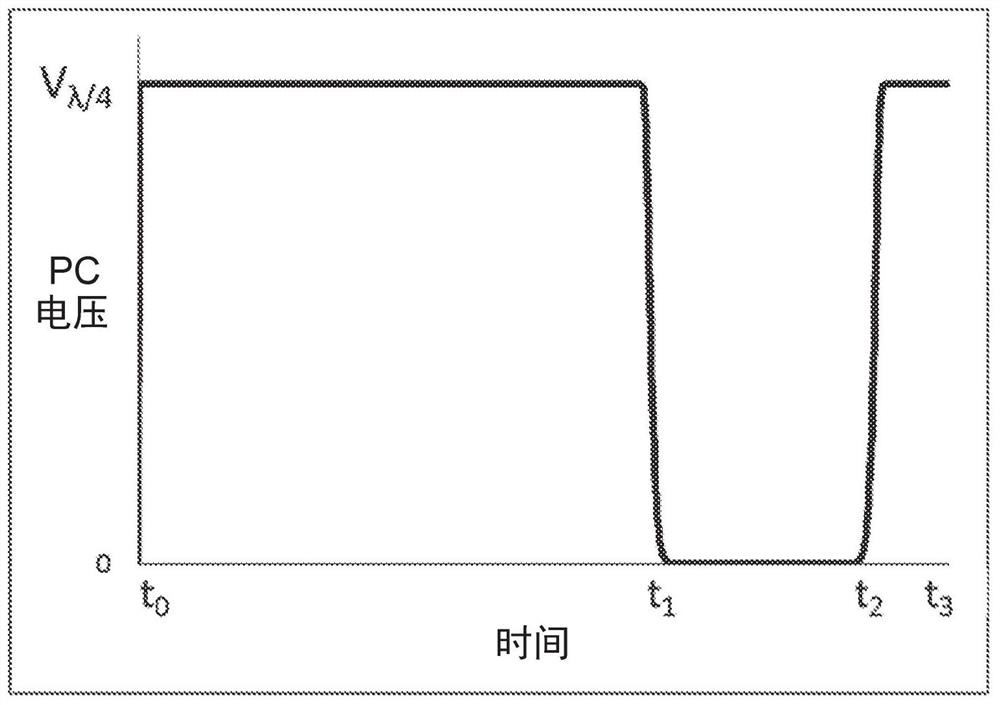
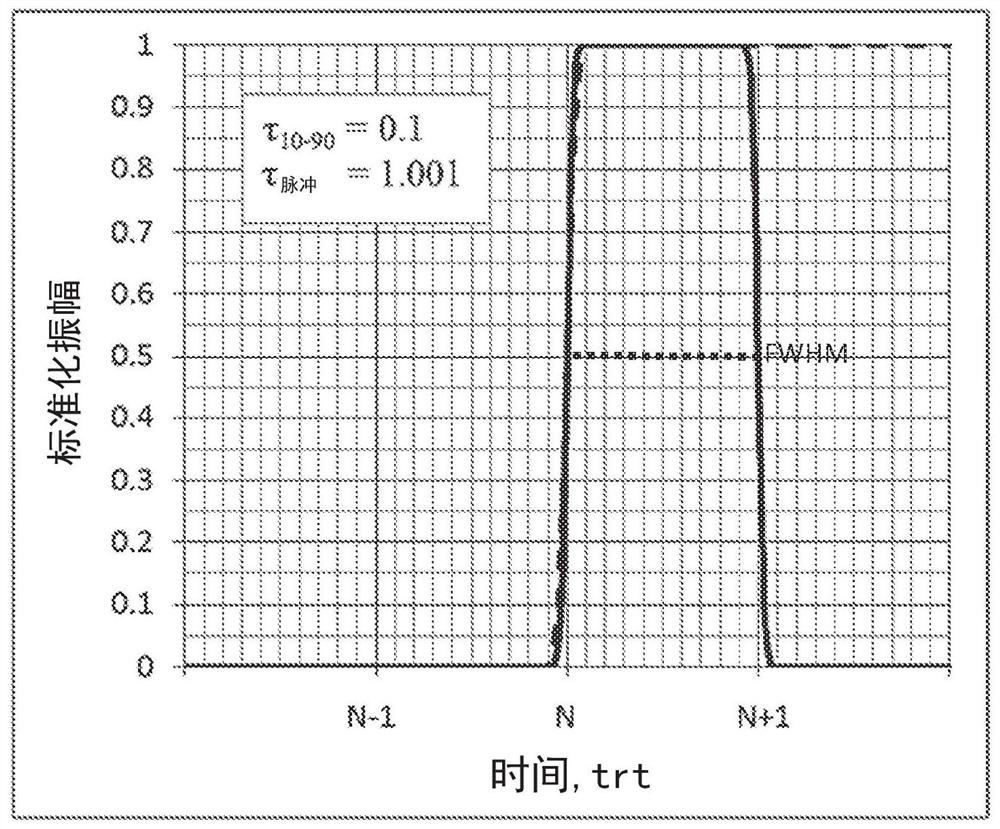
Q-switched cavity dumped sub-nanosecond laser
Apparatuses and methods are disclosed for applying laser energy having desired pulse characteristics, including a sufficiently short duration and / or a sufficiently high energy for the photomechanicaltreatment of skin pigmentations and pigmented lesions, both naturally-occurring (e.g., birthmarks), as well as artificial (e.g., tattoos). The laser energy may be generated with an apparatus having aresonator with a sub-nanosecond round trip time.
Owner:赛诺秀有限公司
Online taxpayer identity identification method based on variable-length system call sequence birthmark
ActiveCN104077404BThe method is novel and uniqueAvoid large-scale service performance degradationComputer security arrangementsSpecial data processing applicationsSoftware systemIdentity recognition
The invention provides an online taxpayer identity recognition method based on variable-length system calling sequence birthmarks. The online taxpayer identity recognition method is divided into two stages, namely the stage of establishing an offline normal birthmark library based on normal historical tax behaviors of a user, and the stage of recognizing the user identity in real time for the real-time tax scene of the user; the method is used for realizing real-time online recognition on the behaviors and the identities of the taxpayers by extracting the system calling sequence characteristics that the software system shows in the operation processes of different taxpayers, and therefore, the recognition of the identifies of the taxpayers can be realized in case that the identity authentication information of the taxpayers is stolen.
Owner:SERVYOU SOFTWARE GRP
External preparation for removing nevus, verruca vulgaris, birth marks, warts and spots as well as preparation method and application of external preparation
PendingCN111544496AEffectively removeNo side effectsHydroxy compound active ingredientsAerosol deliveryFood scienceSandalwood
The invention is applicable to the technical field of traditional Chinese medicine, and provides an external preparation for removing nevus, verruca vulgaris, birthmarks, warts and spots as well as apreparation method and application thereof. The preparation comprises andrographis paniculata, fructus viticis, active calcium oxide, monkshood, borneol, pseudo-ginseng powder, white sandalwood, moleplant seeds, belvedere fruits, an ethanol solution and deionized water. The preparation provided by the invention can be applied to the surfaces of skin flaws such as nevus and freckles in a one-to-onecorrespondence manner, so that the drug enters through the skin surface layer, reaches the dermis layer, dissolves melanin accumulation, extracts melanin to the epidermis layer, balances the melaninlevel, activates the skin cell function to return to normal, and finally achieves the purpose of no nevus, freckle or other skin flaws in the whole life. The preparation not only can be used for effectively removing skin flaws such as nevus, verruca vulgaris, birthmarks, warts and spots, but also has the advantages of no toxic or side effect, convenience in removing means, low cost and the like.
Owner:任发军
Tyrosinase inhibitors
InactiveUS20150164758A1Signs improvedReduce pigmentationCosmetic preparationsOrganic active ingredientsNail stainHyperpigmentation
The compositions and methods of described herein comprise novel ingredients effective to reduce unwanted pigmentation, such as skin discoloration, freckles, age spots, liver spots, sun damage, tans, pigmented acne marks, scars, pigmented birthmarks, hyperpigmentation, post-inflammatory hyperpigmentation, post-injury hyperpigmentation, melasma, cholasma, after-burn scar, nail stain, yellowing of skin, dark circles under eyes, and the like. The composition may include additional ingredients accordingly for a colored cosmetic, moisturizer, cleanser, toner, and the like.
Owner:AVON PROD INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com