Dynamic key command sequence birthmark-based software plagiarism detecting method
A technology of key instructions and detection methods, applied in the field of plagiarism detection based on dynamic software birthmarks, can solve problems such as small scope of application, obfuscation technology, and difficult to cope with codes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The implementation of the software plagiarism detection method based on the dynamic key instruction sequence birthmark of the present invention will be described in detail below in conjunction with the accompanying drawings.
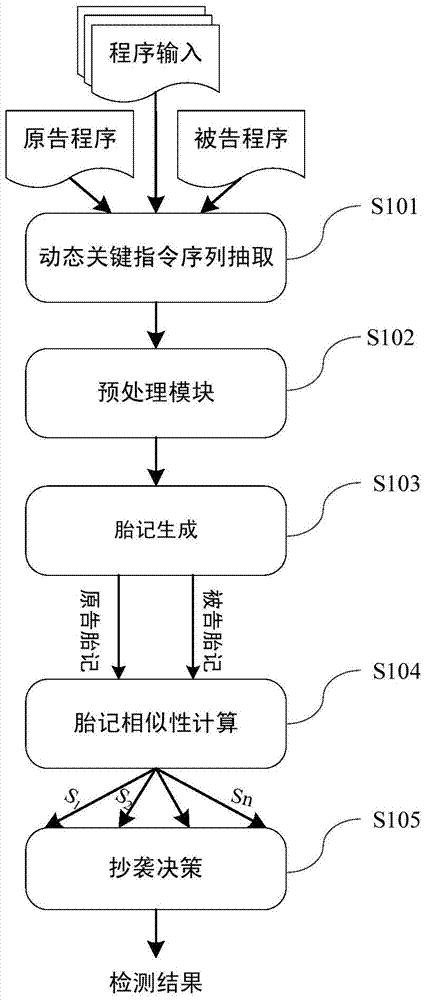
[0058] figure 1 It is the processing flow of the software plagiarism detection method based on the birthmark of dynamic key instruction sequence, where the first program (plaintiff program) refers to the original program developed by the program owner, and the second program (defendant program) refers to the software that is considered to have copied the original program. Suspicious program.
[0059] A kind of software plagiarism detection method based on dynamic key instruction sequence birthmark of the present invention comprises the following steps:
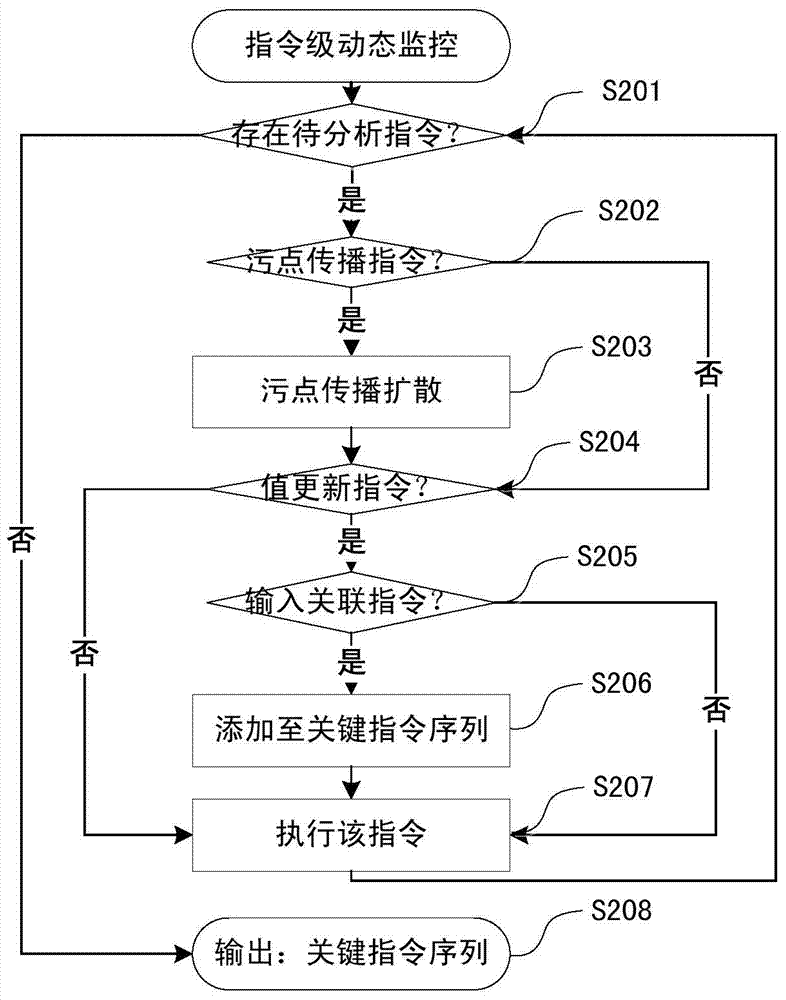
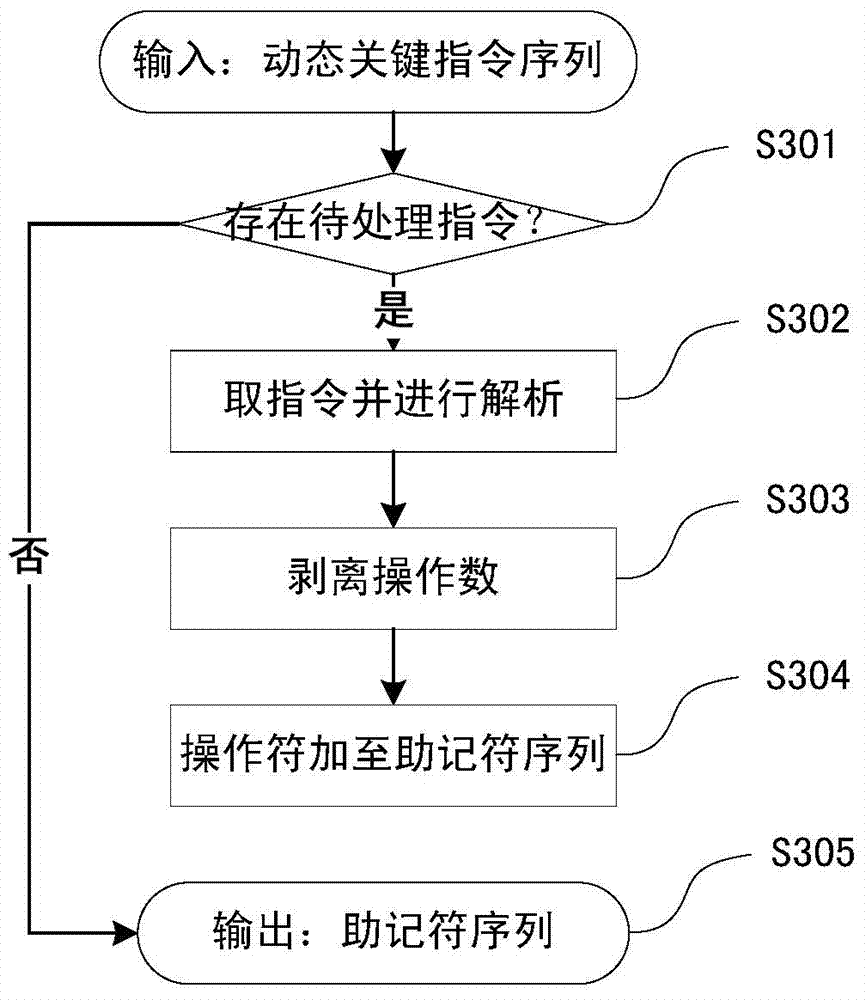
[0060] Step S101: Use dynamic instrumentation tools such as Pin, Valgrind, etc., to implant analysis code before each instruction of the program to be analyzed is executed, so as to monitor the i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com