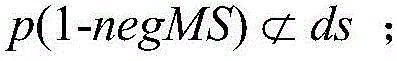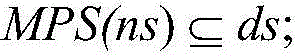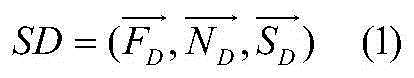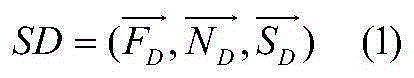Patents
Literature
68 results about "Serial pattern" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
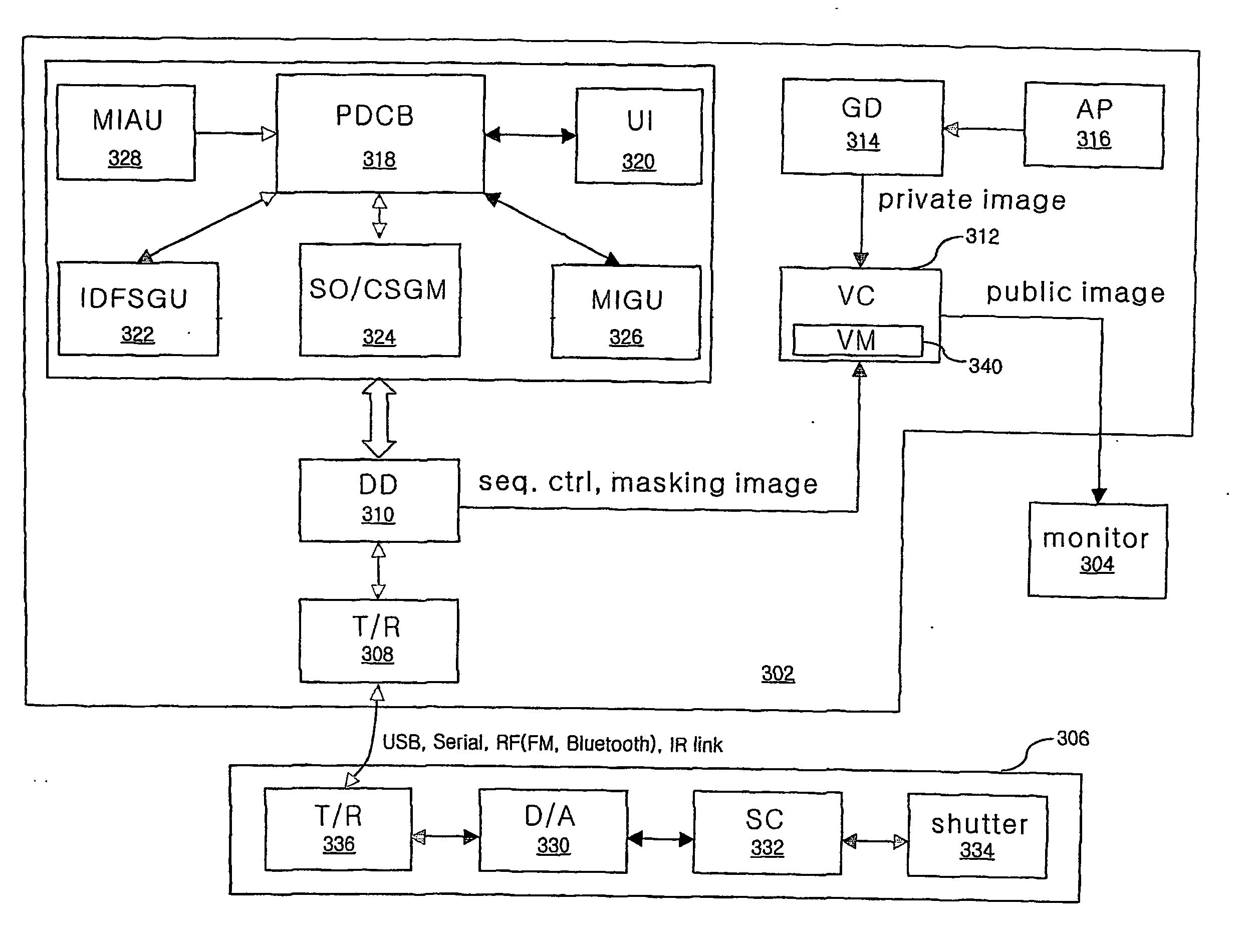
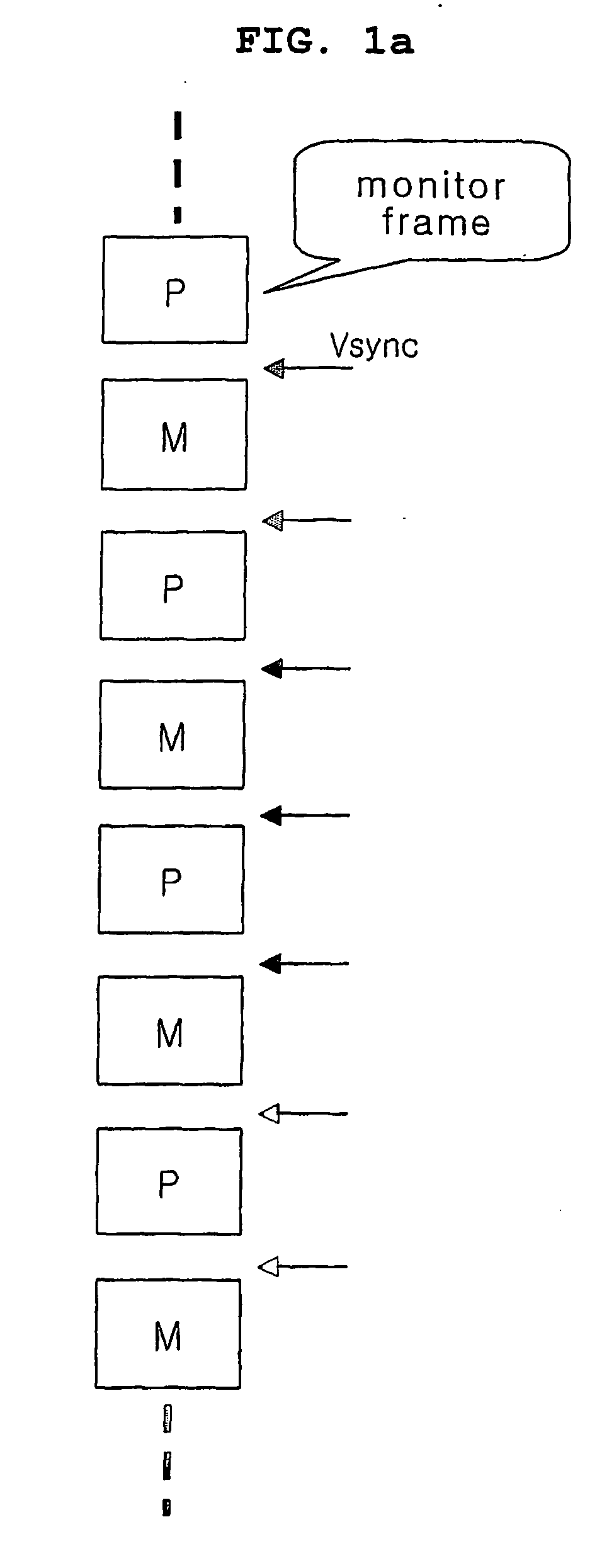
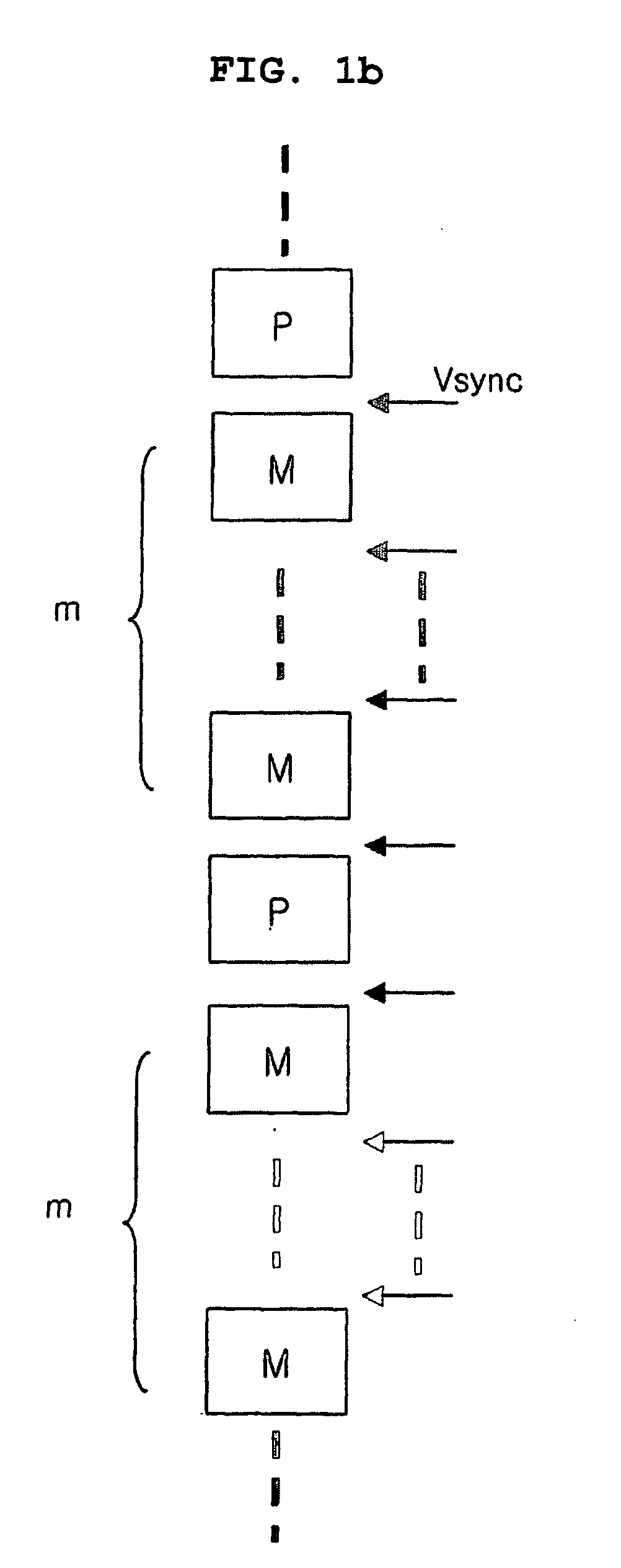
Device and method for outputting a private image using a public display
InactiveUS20060221067A1Efficiently concealedImprove performanceDigital data processing detailsAnalogue secracy/subscription systemsSerial patternDisplay device
Disclosed are a device and a method for displaying a private image on a public display device. Image sequence pattern is generated for the private image and the corresponding masking image. The masking image is made from the dynamic inverse image of the private image, based on the refresh rate of the display device and the image sequence pattern. The masking image can screen the private image more effectively. The private image and the masking image is displayed on the display device according to the image sequence pattern.
Owner:SAYEN
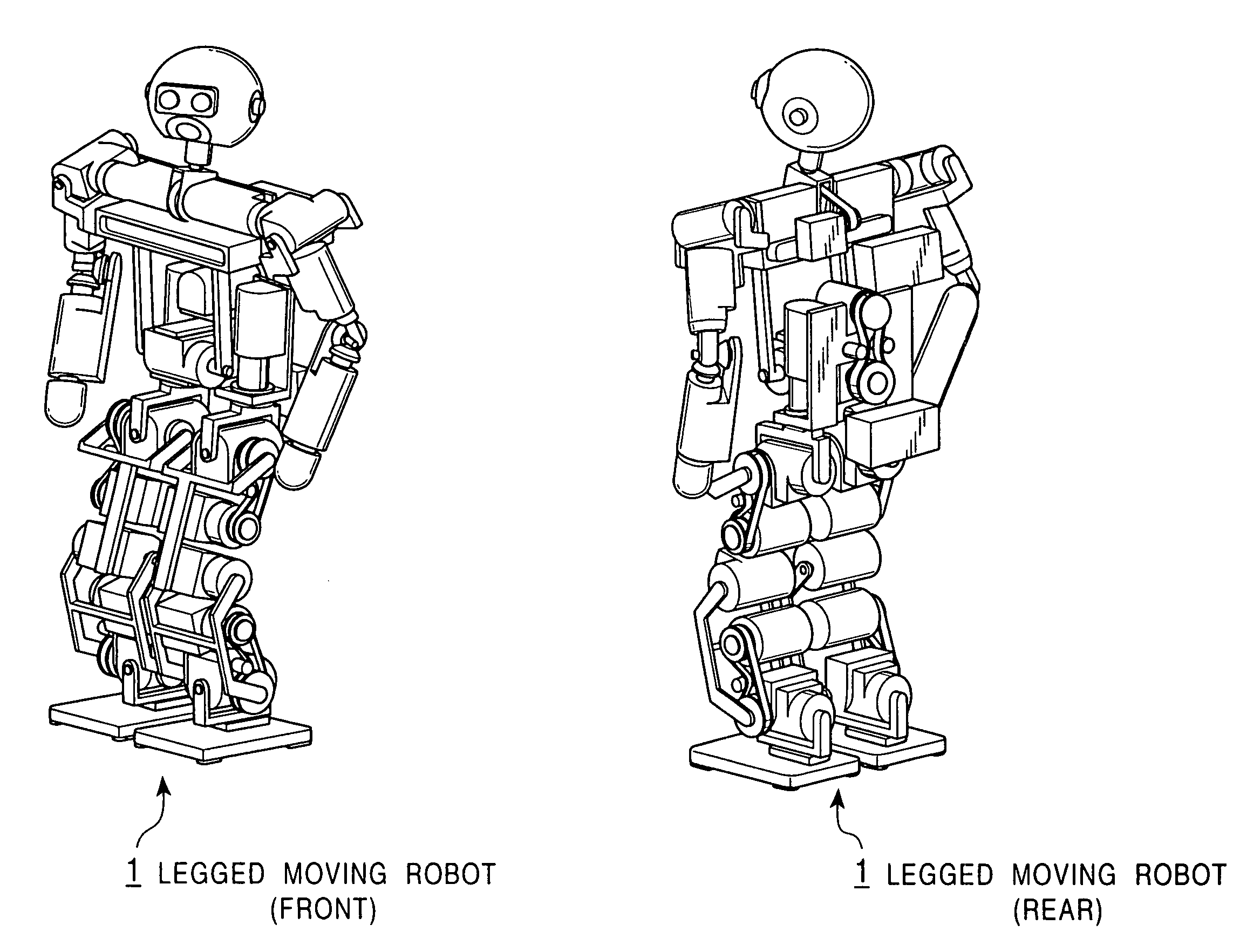
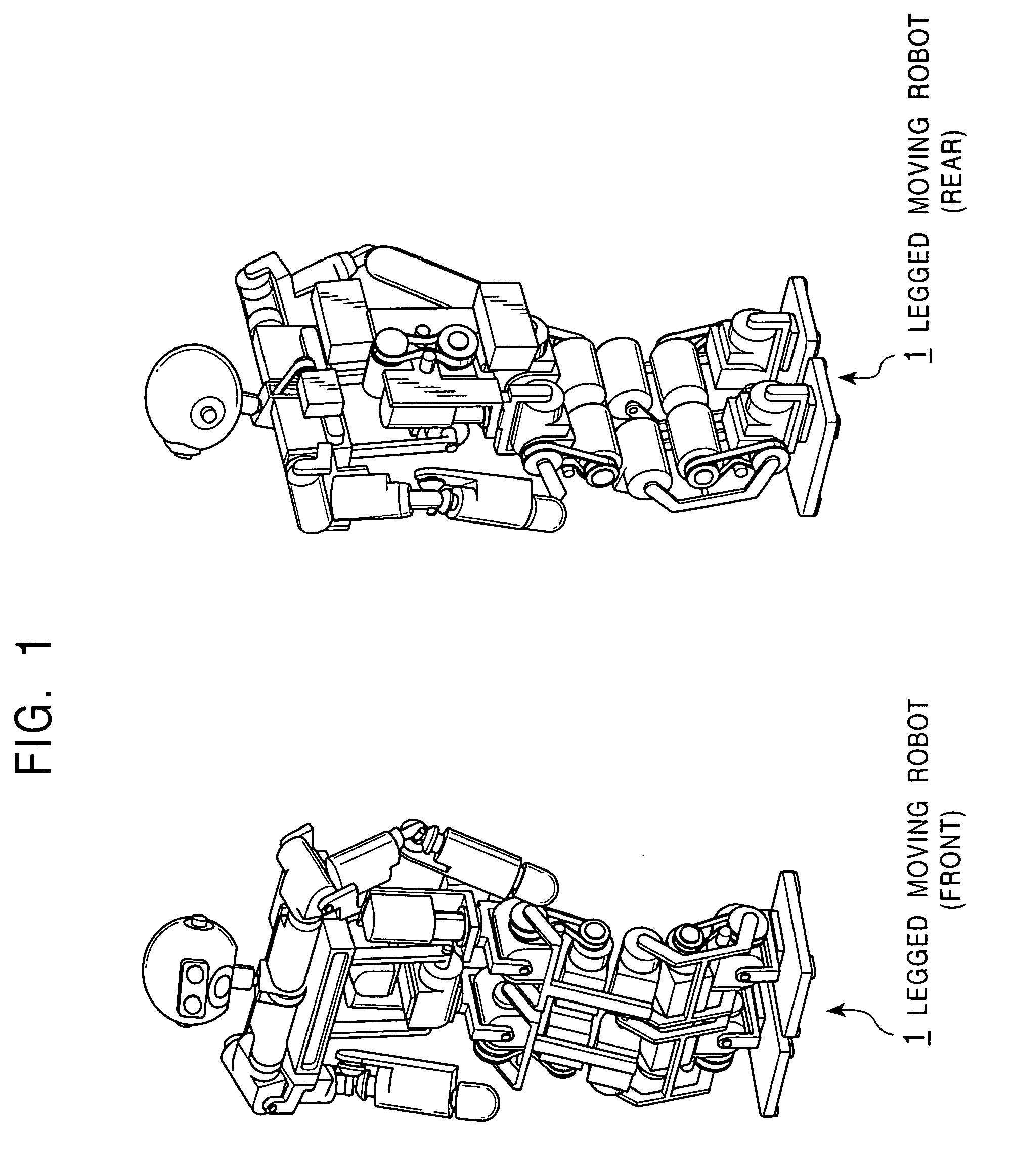
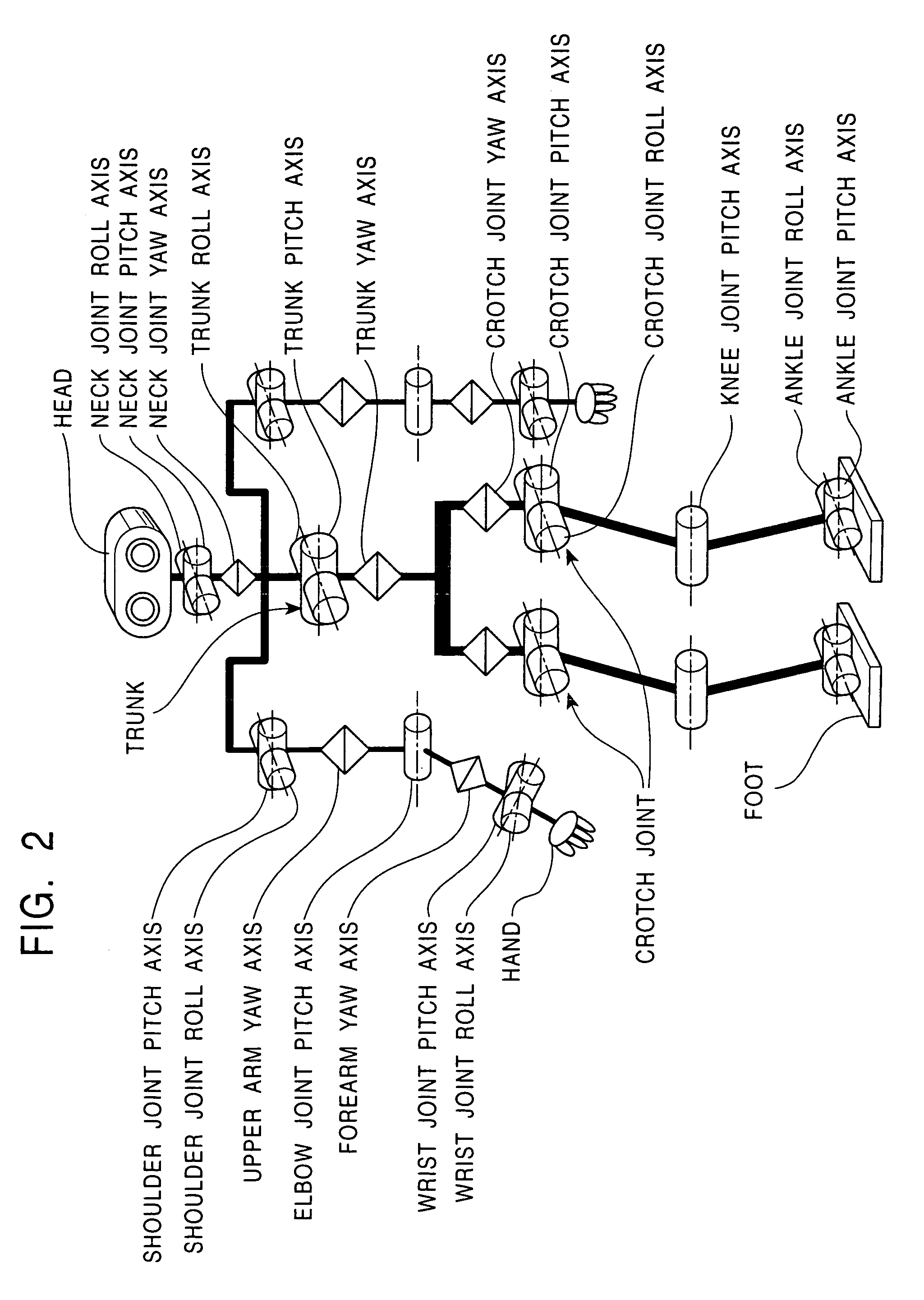
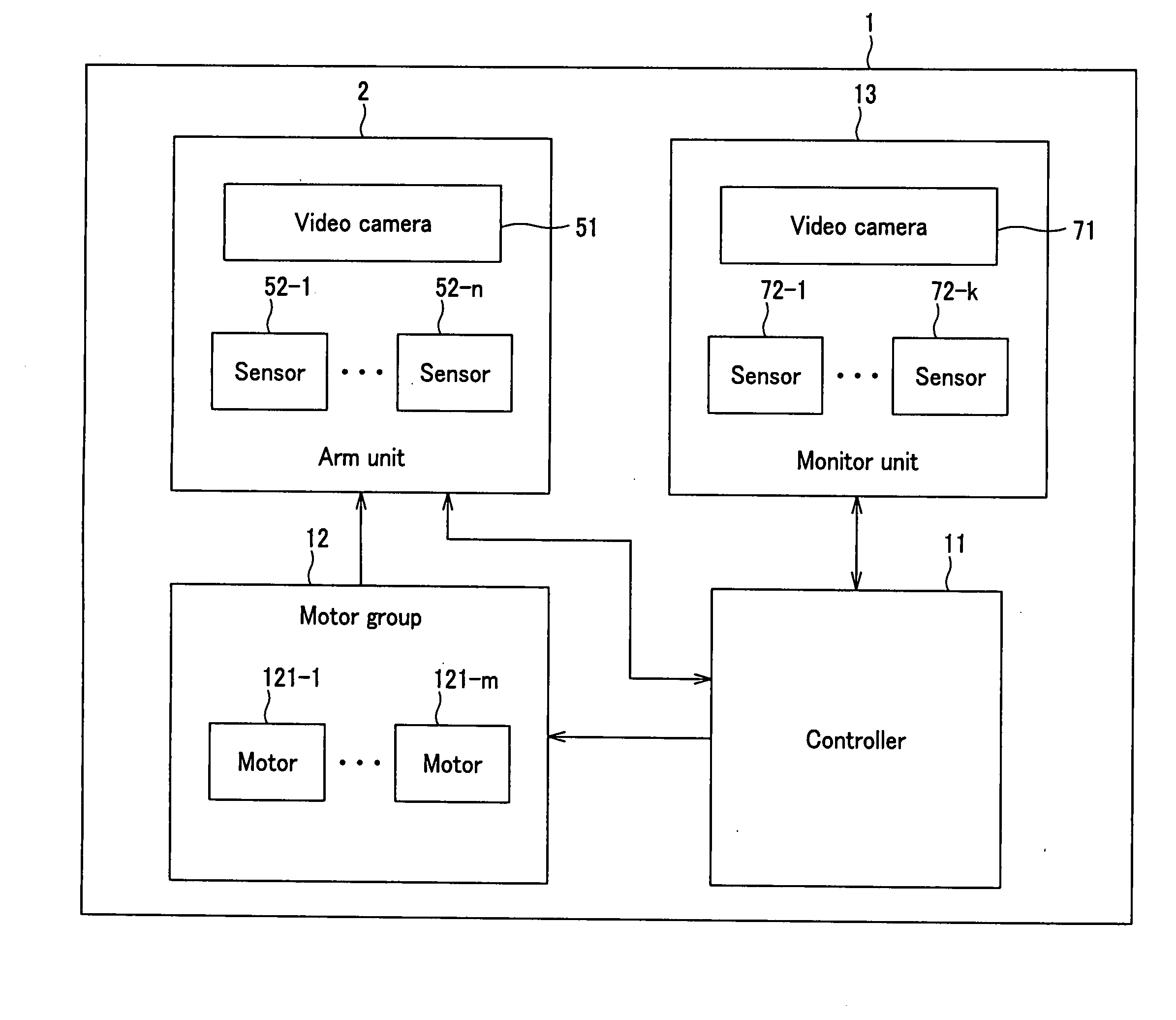
Legged mobile robot and its motion teaching method, and storage medium
Learning-type motion control is performed using a hierarchical recurrent neural network. A motion pattern provided through human teaching work is automatically time-serially segmented with the hierarchical recurrent neural network, and the motion control of a machine body is carried out with a combination of the segmented data, whereby various motion patterns can be produced. With the time-serial segmentation, local time-serial patterns and an overall pattern as a combination of the local time-serial patterns are produced. For those motion patterns, indices for static stability and dynamic stability of the machine body, e.g., ZMP stability criteria, are satisfied and hence control stability is ensured.
Owner:SONY CORP
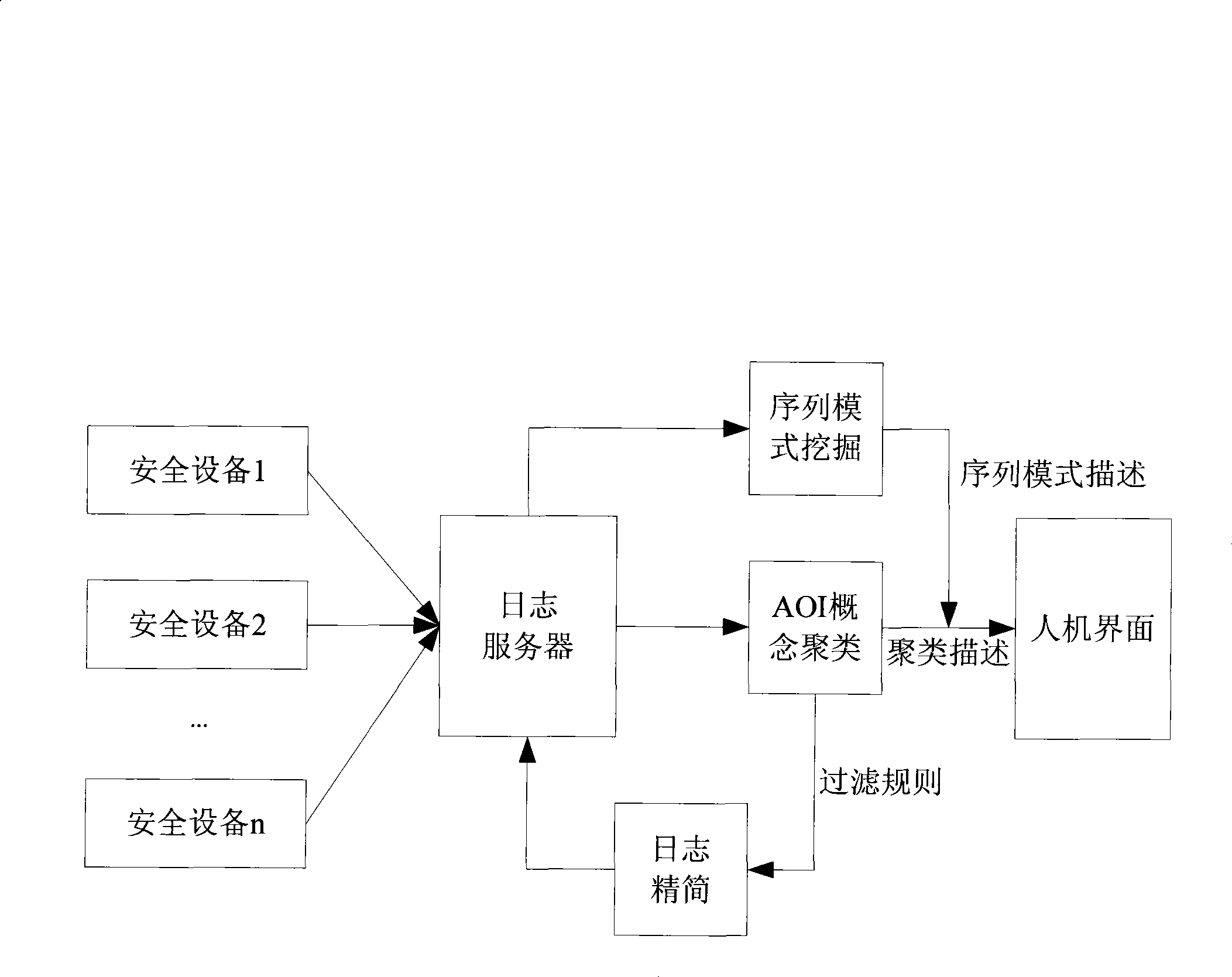
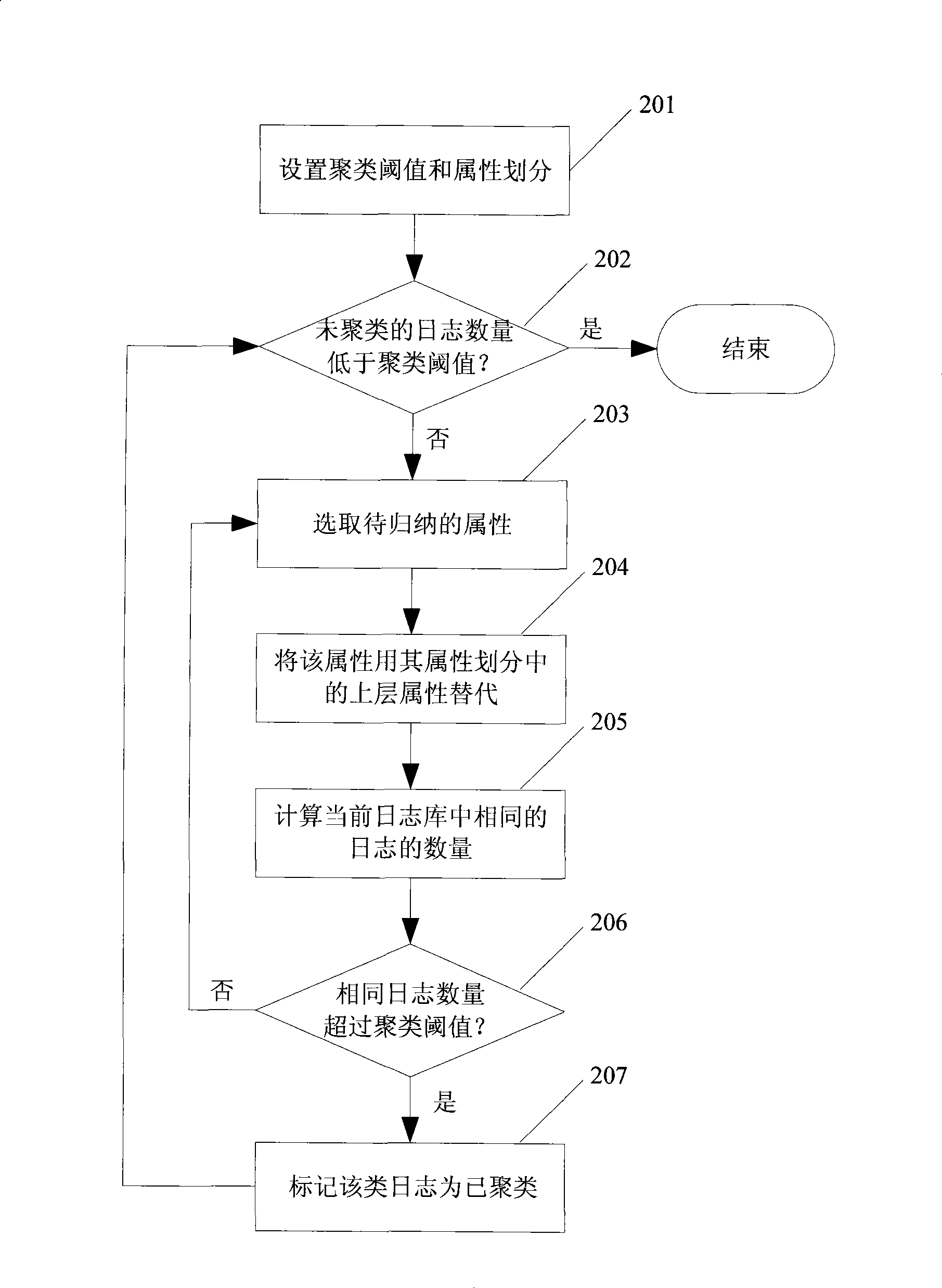
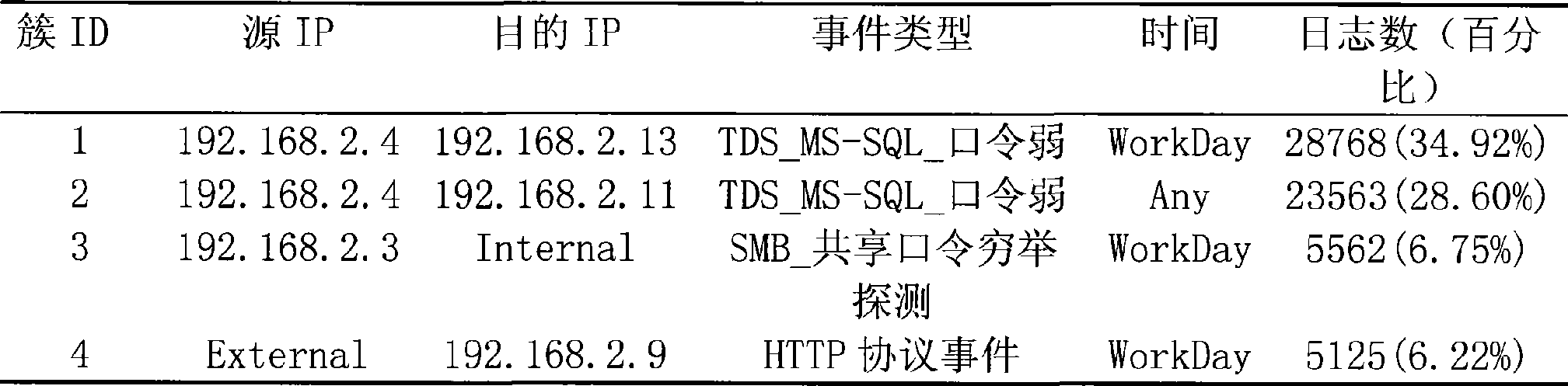
Safe log analyzing method and system
InactiveCN101399658AEfficient discoveryRealize detectionSecuring communicationInformation processingSerial pattern
The invention discloses a method for analyzing a security log and a system thereof, which realizes filtration of invalid logs and misreported logs in mass logs, and discovers large-scale network security events and common attack sequences. The method comprises the following steps: the mass logs are subject to cluster analysis by the attribute-oriented inductive algorithm so as to generate class description of each class of log after clustering; an administrator sets filtration regulations according to the clustered class description, unrelated and misreported logs are removed from the current log base so as to simplify the mass logs; Internet Worms, distributed denial of service attacks and other large-scale network security events characteristics are extracted; the simplified log is subject to sequential pattern mining to find attack behavior sequence description commonly used by attackers to be finally submitted to the administrator. The system comprises a clustering analysis module, a filtration module and a sequential pattern mining module. The method and the system can be applied to information processing of the mass logs of security products.
Owner:BEIJING VENUS INFORMATION TECH
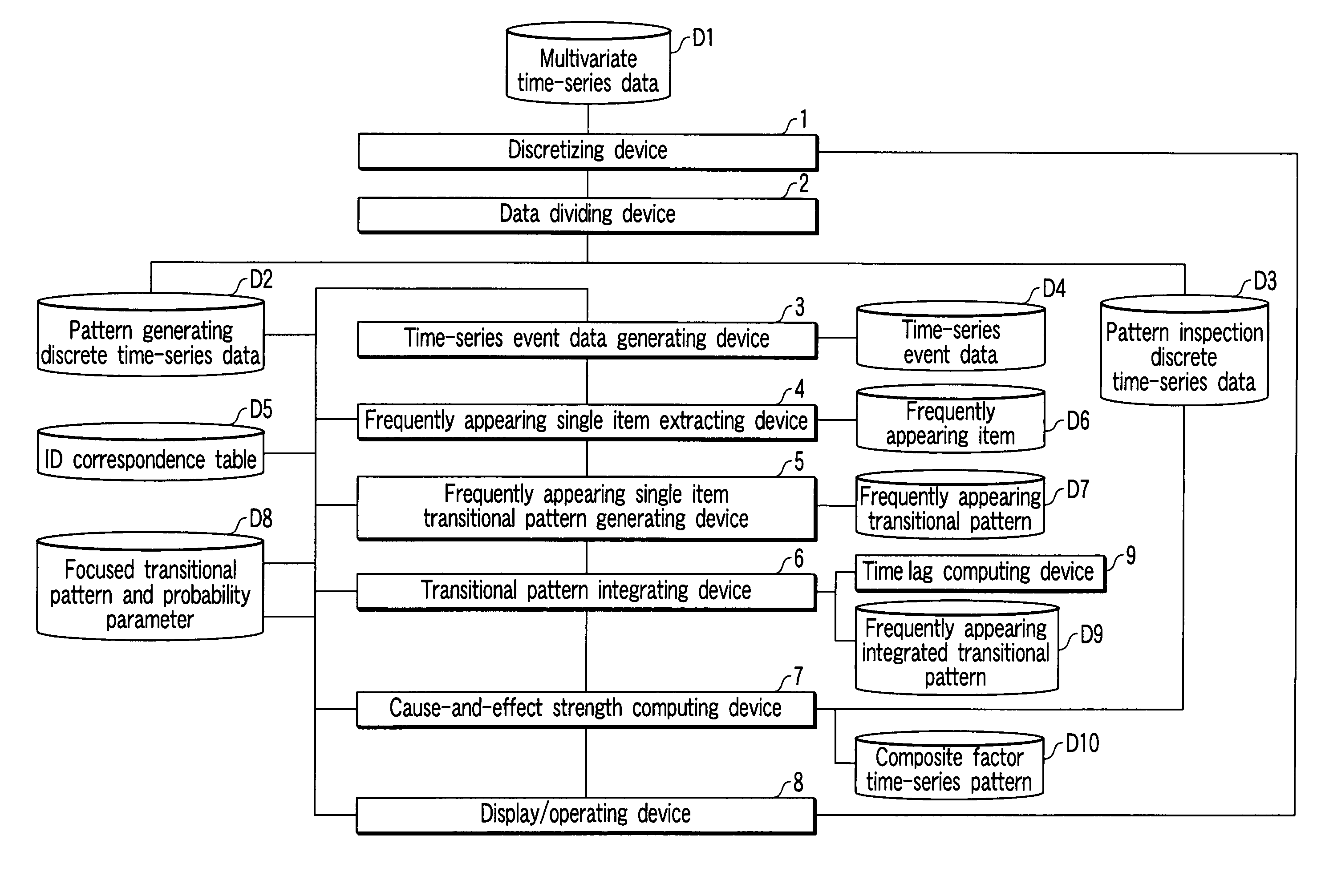
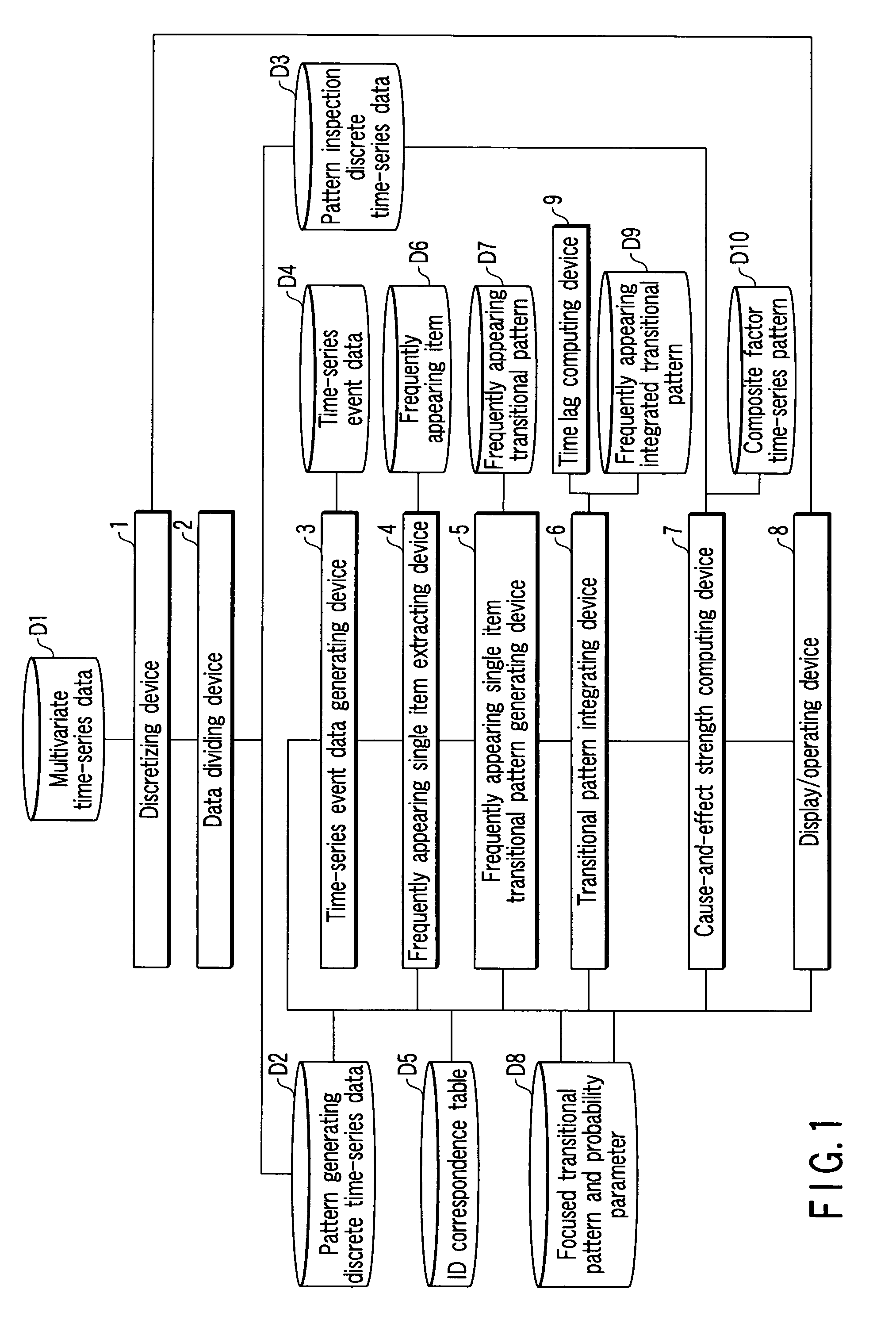
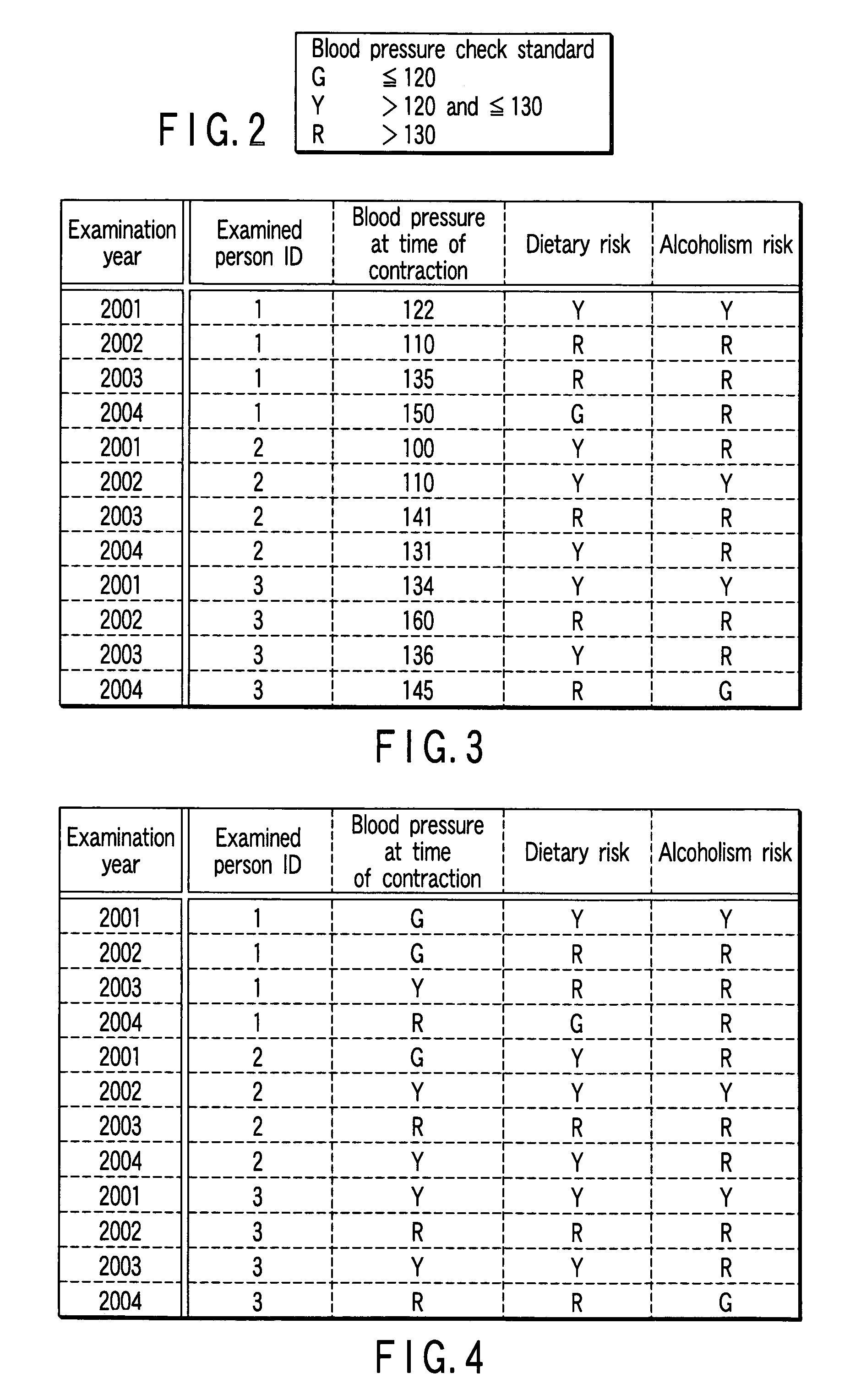
Time-series data analyzing apparatus
A time-series data analyzing apparatus which extracts a composite factor time-series pattern from time-series data. The apparatus includes a dividing device which divides the time-series data into pattern generation time-series data and pattern inspection time-series data which do not include pattern generation time-series data. A first generating device generates a transitional pattern including a support time data indicating a transition of support time and having a transition occurrence probability higher than a minimum occurrence probability in the pattern generation time-series data. A second generating device generates frequently appearing integrated transitional patterns. A second computing device computes cause-and-effect strength of each of the frequently appearing integrated transitional patterns using the pattern inspection time-series data. A display device displays the composite factor time-series pattern having the cause-and-effect strength higher than the minimum cause-and-effect strength given preliminarily.
Owner:TOSHIBA DIGITAL SOLUTIONS CORP
Encoding method and system for reducing inter-symbol interference effects in transmission over a serial link
ActiveUS7359437B2Reduce bit error rateIncreased source data transmission rateError detection/prevention using signal quality detectorPicture reproducers using cathode ray tubesComputer hardwareCommunications system
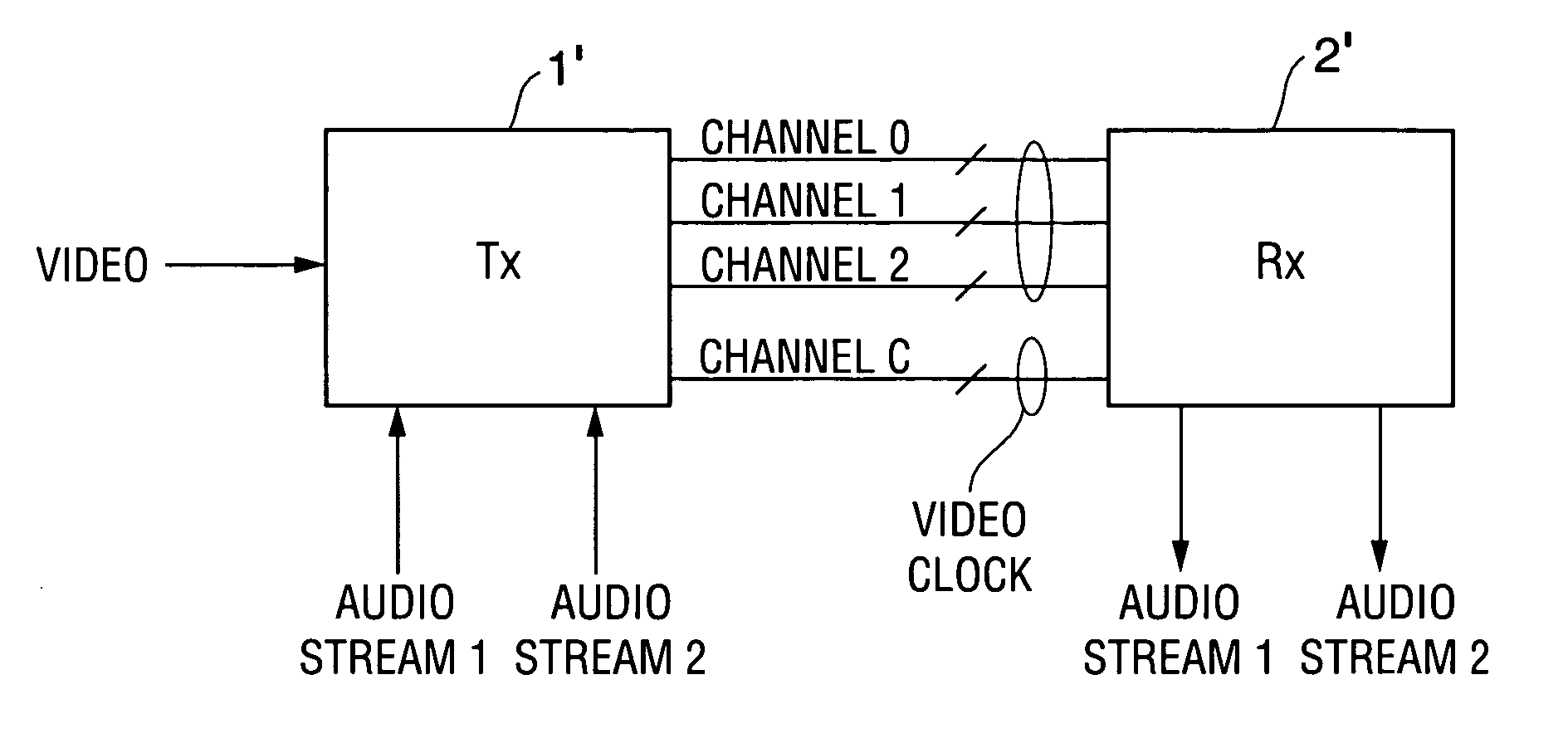
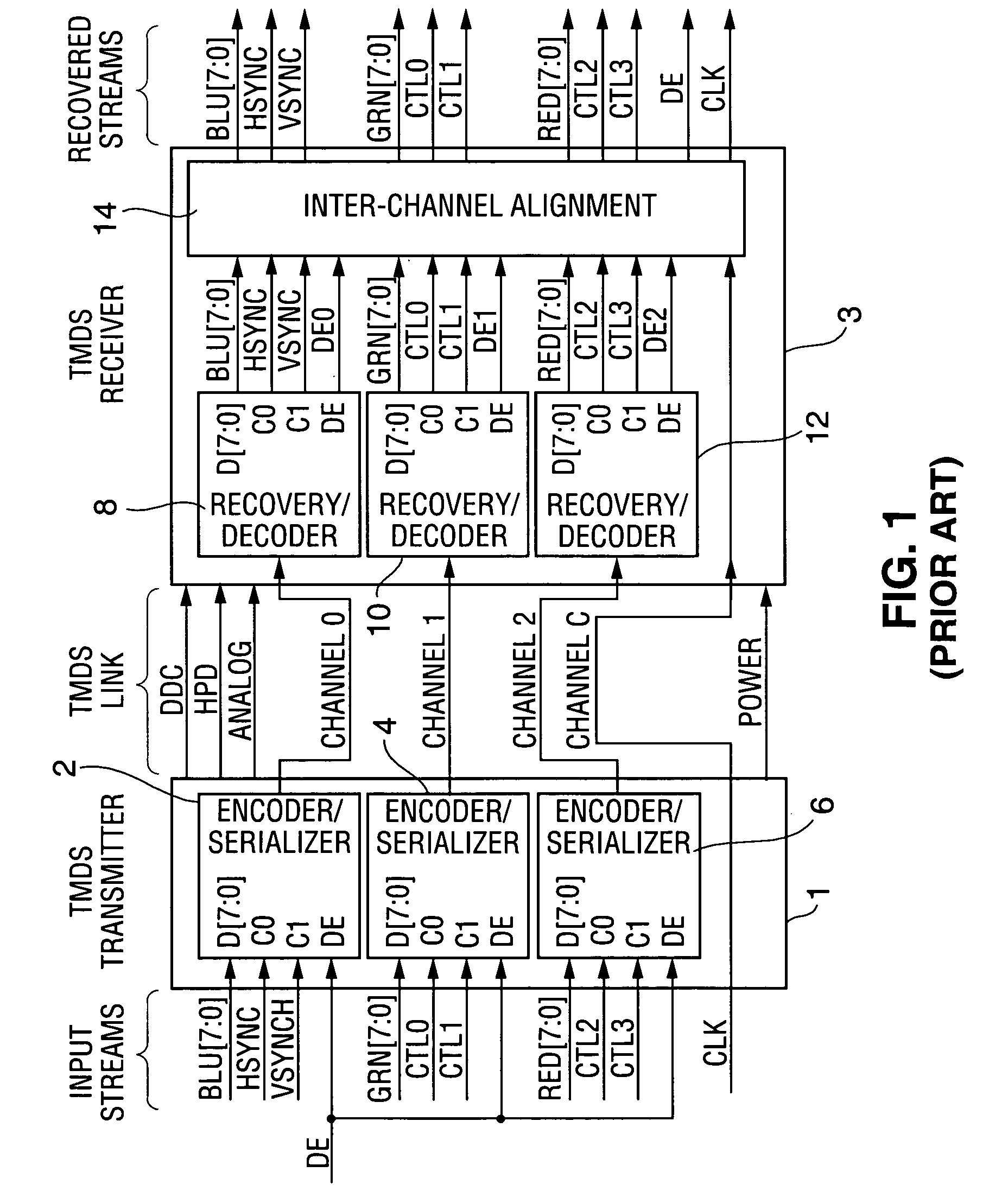
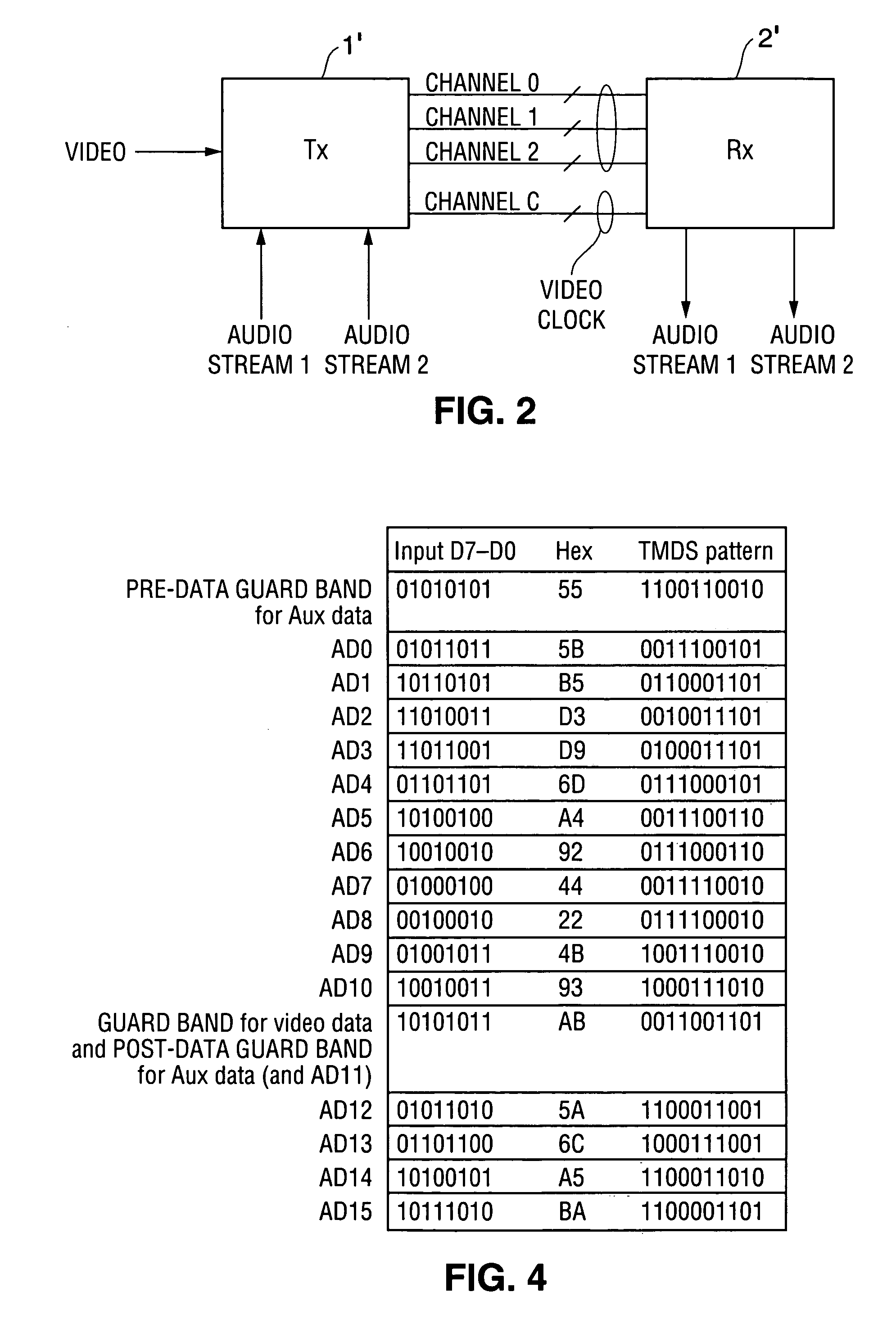
A communication system including a transmitter, a receiver, and a serial link, in which encoded data (e.g., encoded video data and encoded auxiliary data) are transmitted from the transmitter to the receiver. The serial link can but need not be a TMDS or TMDS-like link. In typical embodiments, alternating bursts of encoded video data and encoded auxiliary data are transmitted over each of one or more channels of the link. Other aspects of the invention are transmitters for use in encoding data for transmission over a serial link, and methods for sending encoded data over a serial link. In accordance with the invention, the data to be transmitted are encoded using a subset (sometimes referred to as a selected set of code words) of a full set of code words. The selected set of code words is selected such that each stream of encoded data (comprising only such code words) transmitted over a serial link has a bit pattern that is less susceptible to inter-symbol interference (“ISI”) during transmission than is the bit pattern determined by a conventionally encoded version of the same data (comprising not only the selected set of code words but also other members of the full set). In general, the best choice for the selected set of code words selected from a full set of binary code words depends on the particular coding implemented by the full set. Typically, the selected set of code words includes words whose serial patterns (during transmission) have fewer contiguous zeros and ones (and thus are less susceptible to ISI during transmission) than do those code words in the full set that are not selected. In preferred embodiments in which the bits of the selected set of code words are transmitted over a serial link as sequences of rising and falling voltage transitions, the bit pattern of each transmitted stream of the selected set of code words implements DC balancing to limit the voltage drift over time.
Owner:KONINKLJIJKE PHILIPS NV
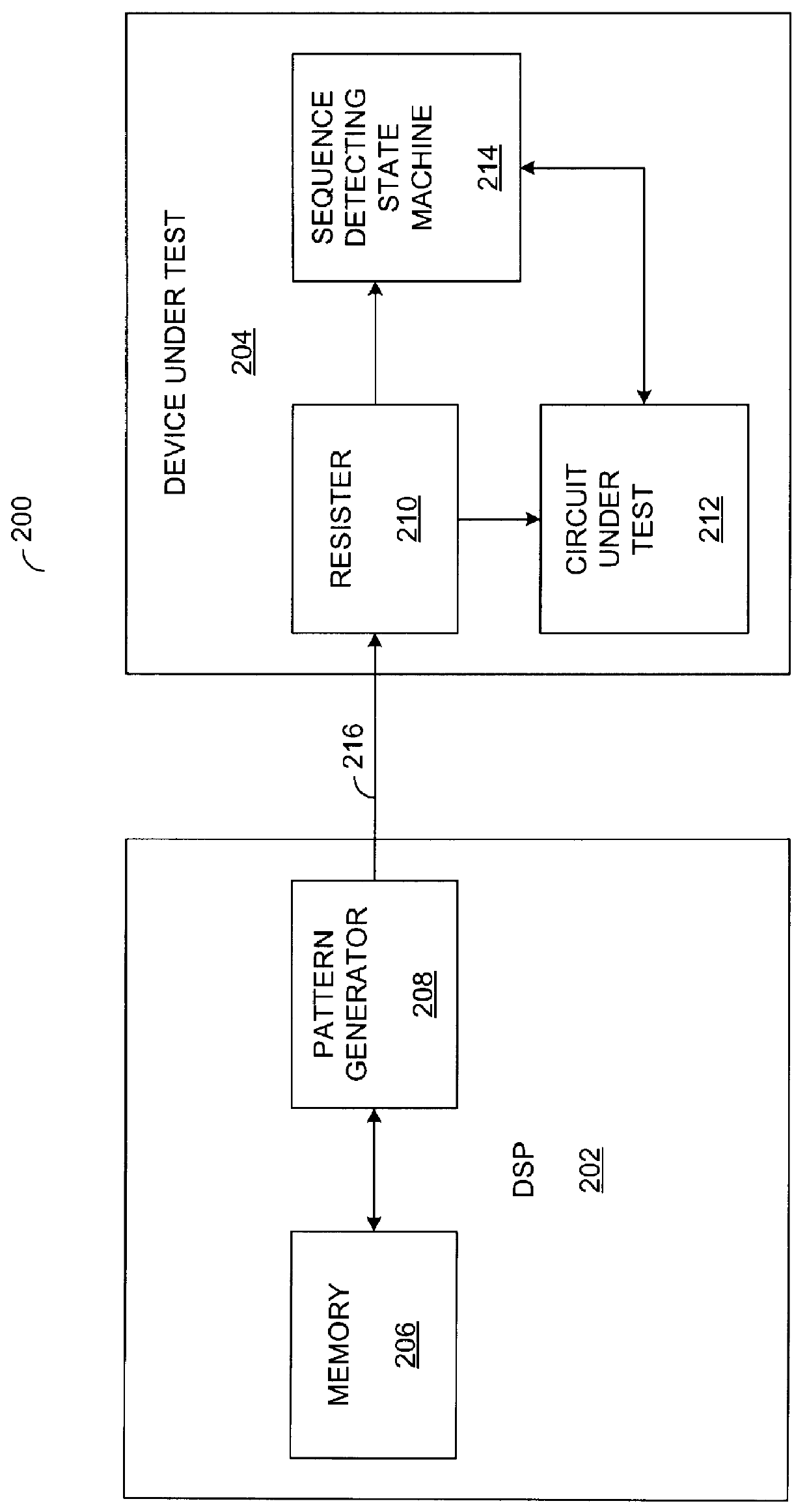
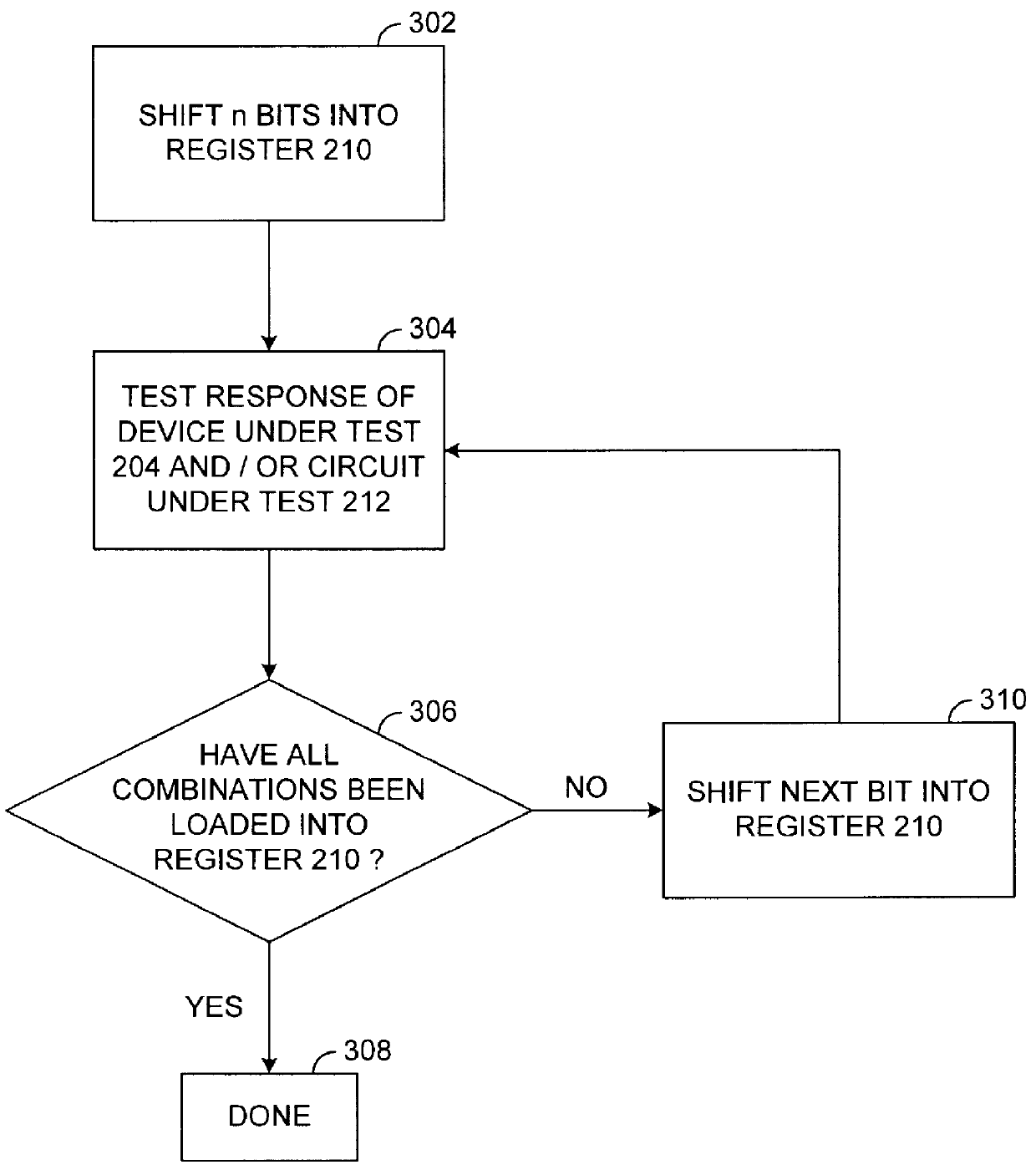
Method and apparatus for generating test pattern for sequence detection
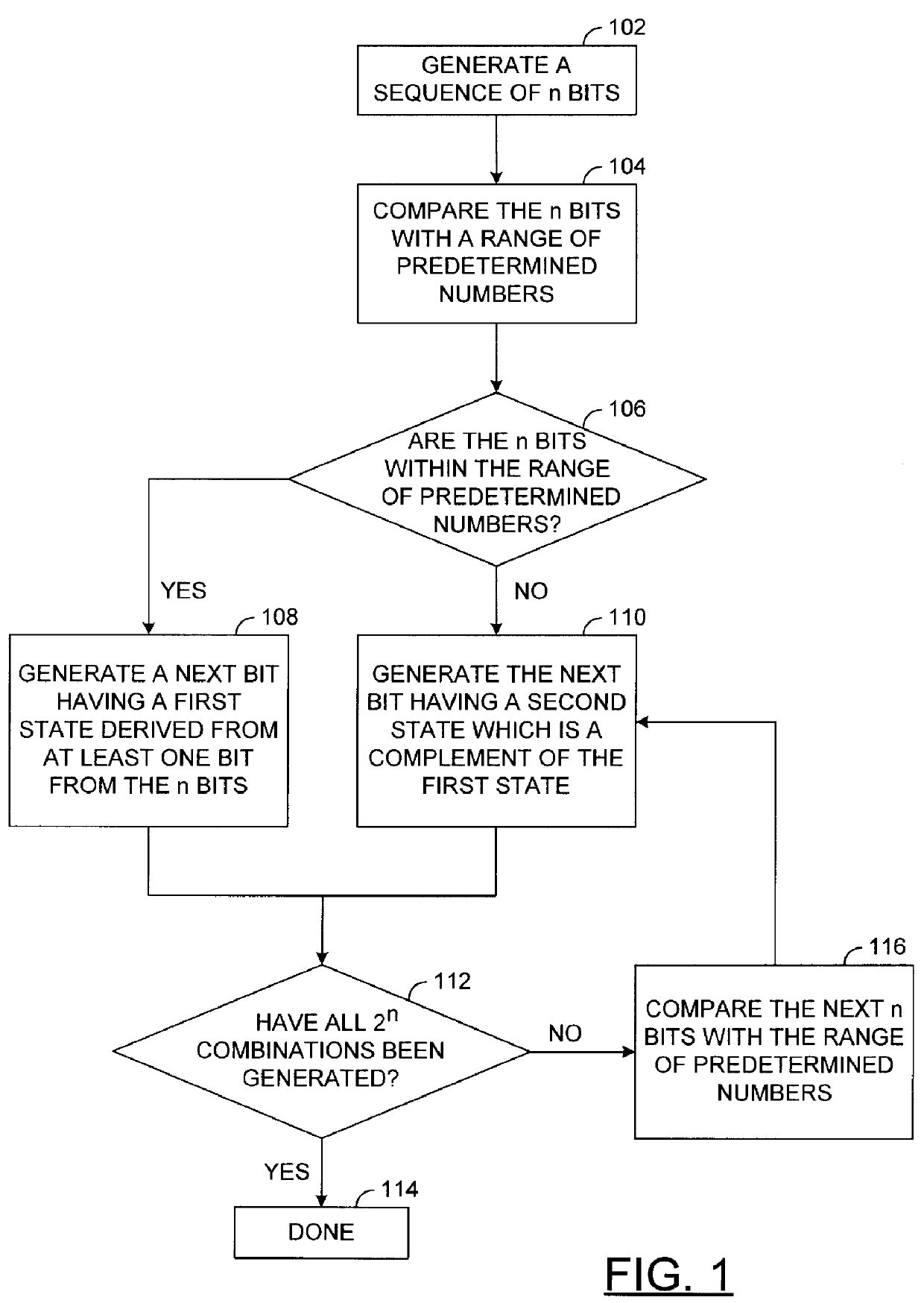
InactiveUS6061817AShorten the timeRandom number generatorsElectronic circuit testingComputer hardwareSerial pattern
A method and apparatus for generating a serial test pattern for sequence detection. The serial test pattern has a first plurality of bits and is generated by a pattern generator. A second plurality of bits is generated having a first value. The second plurality of bits includes less bits than the first plurality of bits. The first value of the second plurality of bits is then compared with one or more numbers to generate a comparison result. A next bit is then generated in the serial pattern based upon the comparison result and one or more bits of the second plurality of bits.
Owner:CYPRESS SEMICON CORP
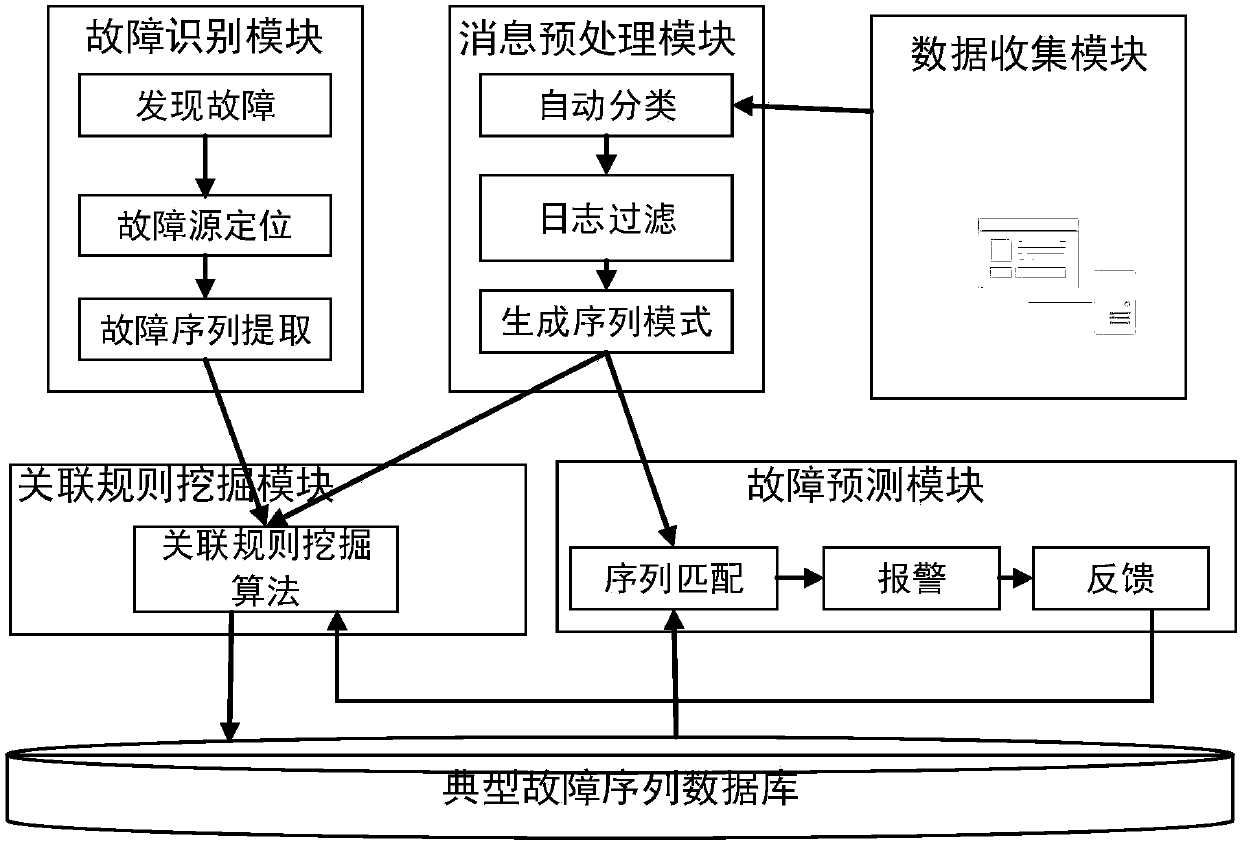
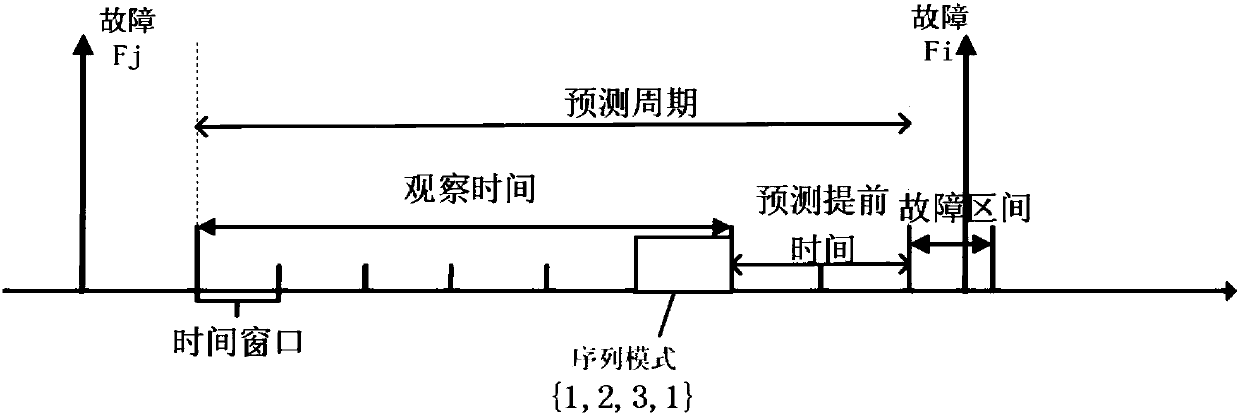
Large-scale mixed heterogeneous storage system-oriented node fault prediction system and method
ActiveCN108415789AImprove accuracyImprove recallFault responseCharacter and pattern recognitionExtensibilityPrediction algorithms
The invention provides a large-scale mixed heterogeneous storage system-oriented node fault prediction system and method. A time sequence-based association rule mining algorithm is adopted to construct a node fault prediction system architecture, and a main process of node fault prediction includes: collecting state data and log information of each storage node; carrying out data preprocessing, and generating sequence modes on the basis of a sliding window; using the sequence modes and fault sequences, which are extracted in a fault identification process, together as input of an association rule algorithm, and outputting output results as typical fault sequences; carrying out matching on the typical fault sequences and sequence modes generated in real time; and if a matching result meetsan established rule, issuing early warning to notify a system administrator, and giving feedback to a prediction result by the administrator according to a subjective interest degree. According to thesystem and method, real-time online fault prediction is carried out for nodes of a large-scale mixed heterogeneous storage system, and accuracy and recall which are better than those of existing fault prediction algorithms and better scalability can be obtained.
Owner:XI AN JIAOTONG UNIV
Front-background related auditing method and system for Web server
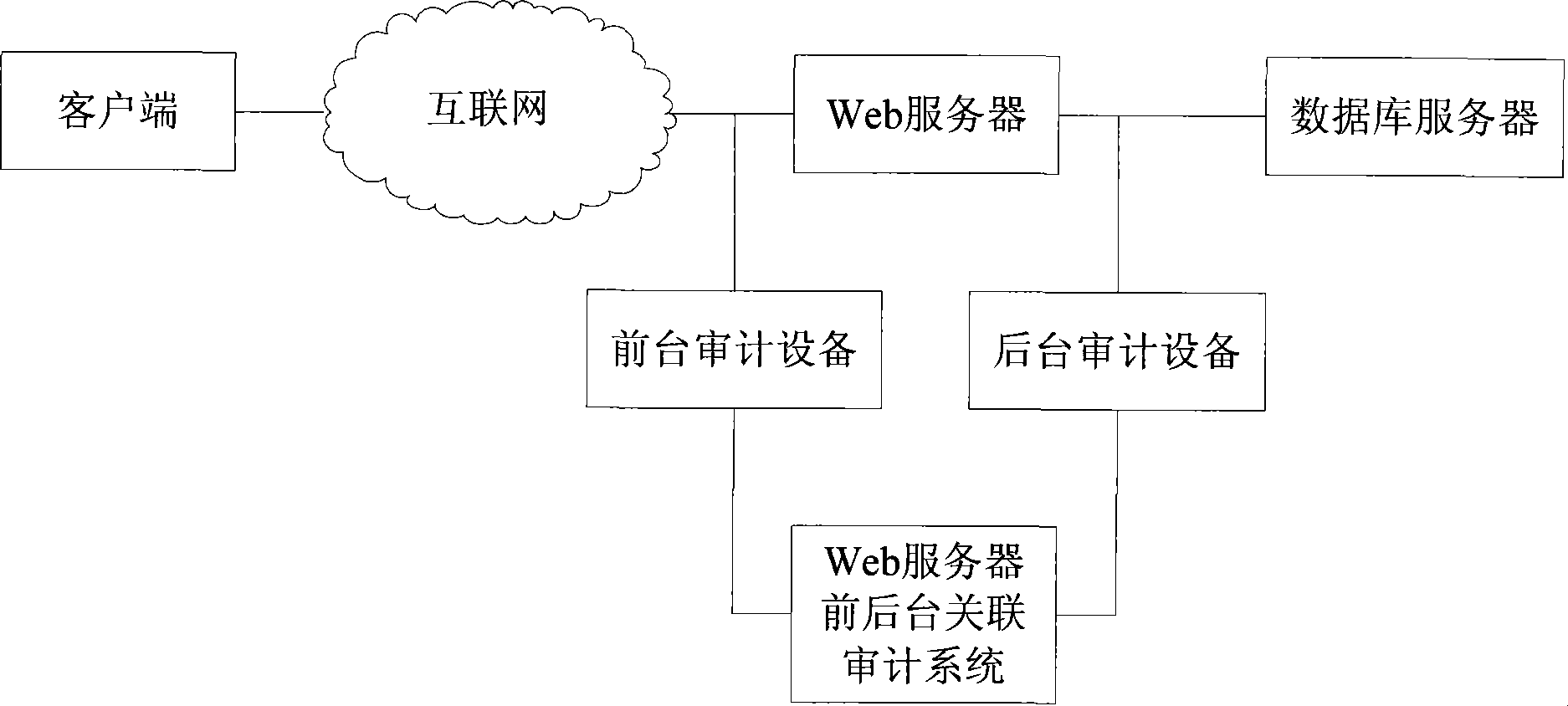
InactiveCN101388899AAccurate judgmentImprove accuracyData switching networksSpecial data processing applicationsWeb serviceSerial pattern
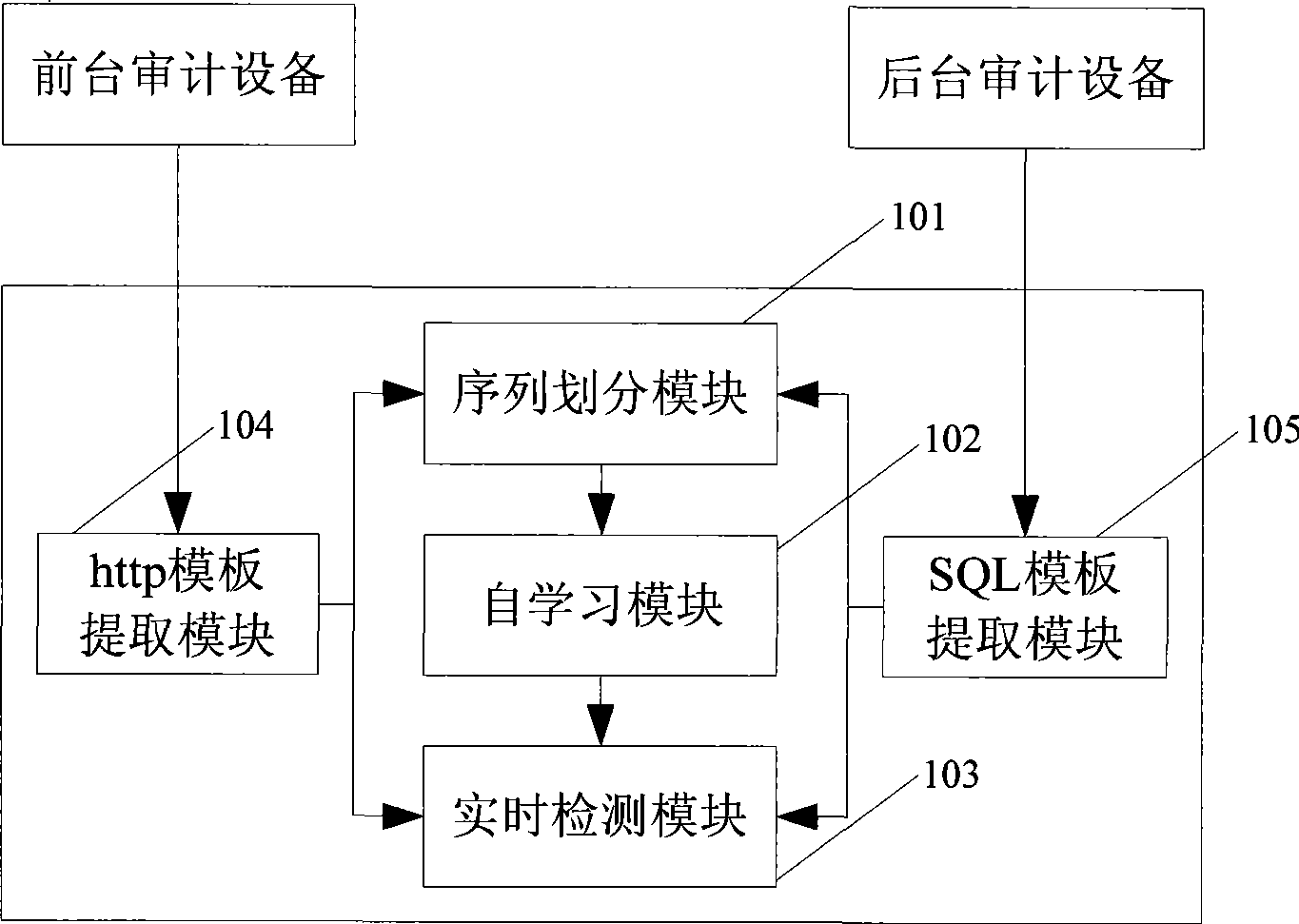
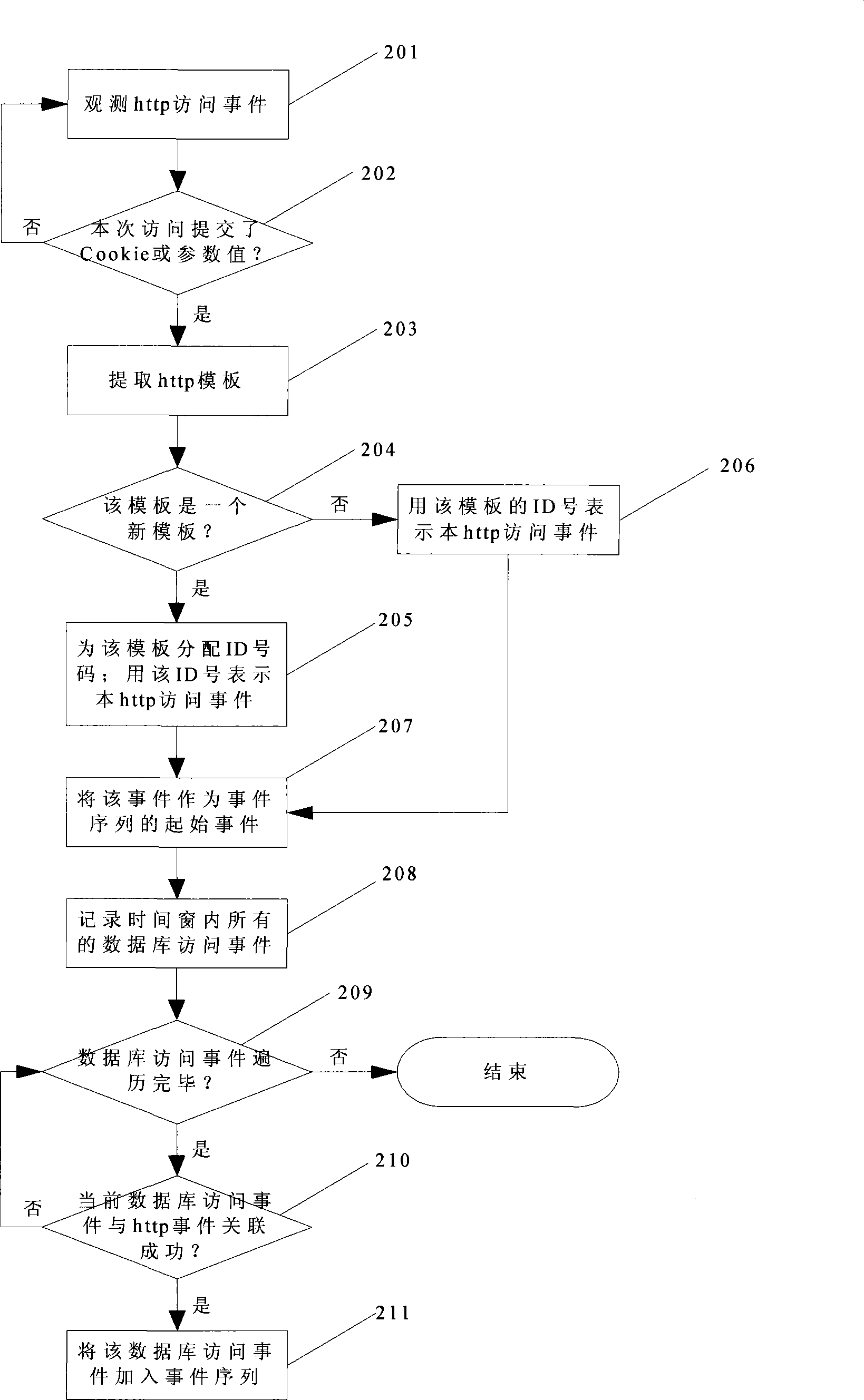
The invention discloses a Web server foreground background association audition method and system thereof which realize the association of the background with the concrete http access happening on the foreground. The method comprises: acquiring the foreground and background access happening respectively though a safety audition equipment; implementing sequence division to the foreground and background access happenings; mining the sequential pattern of the divided happening sequences to find the time sequence relation between them; confirming the http access which triggers the background access according to the acquired relations. The system comprises: a sequence dividing module, a self-learning module and a real time monitoring module. The invention is adapted to the service audition for Web server.
Owner:BEIJING VENUS INFORMATION TECH
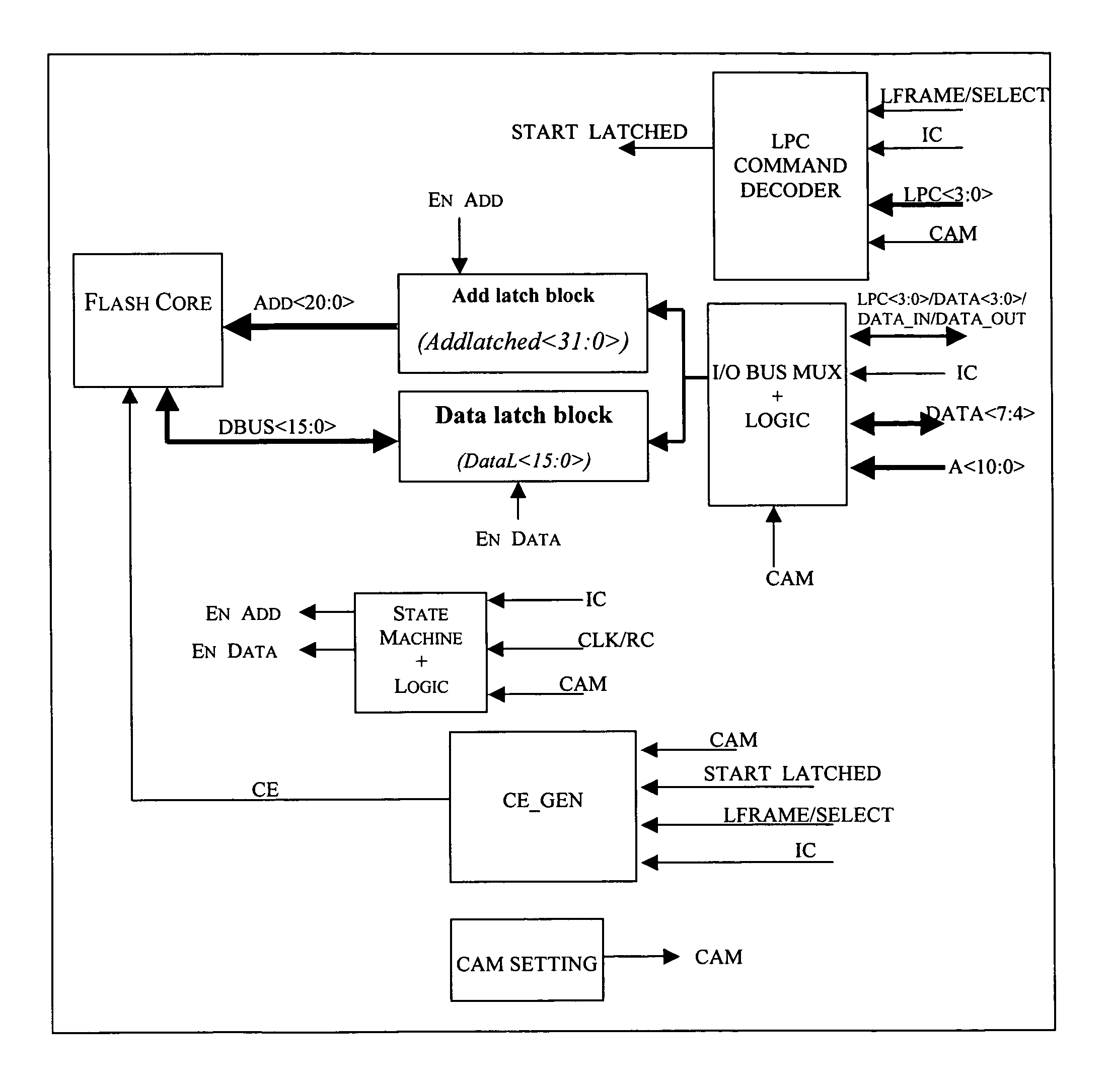
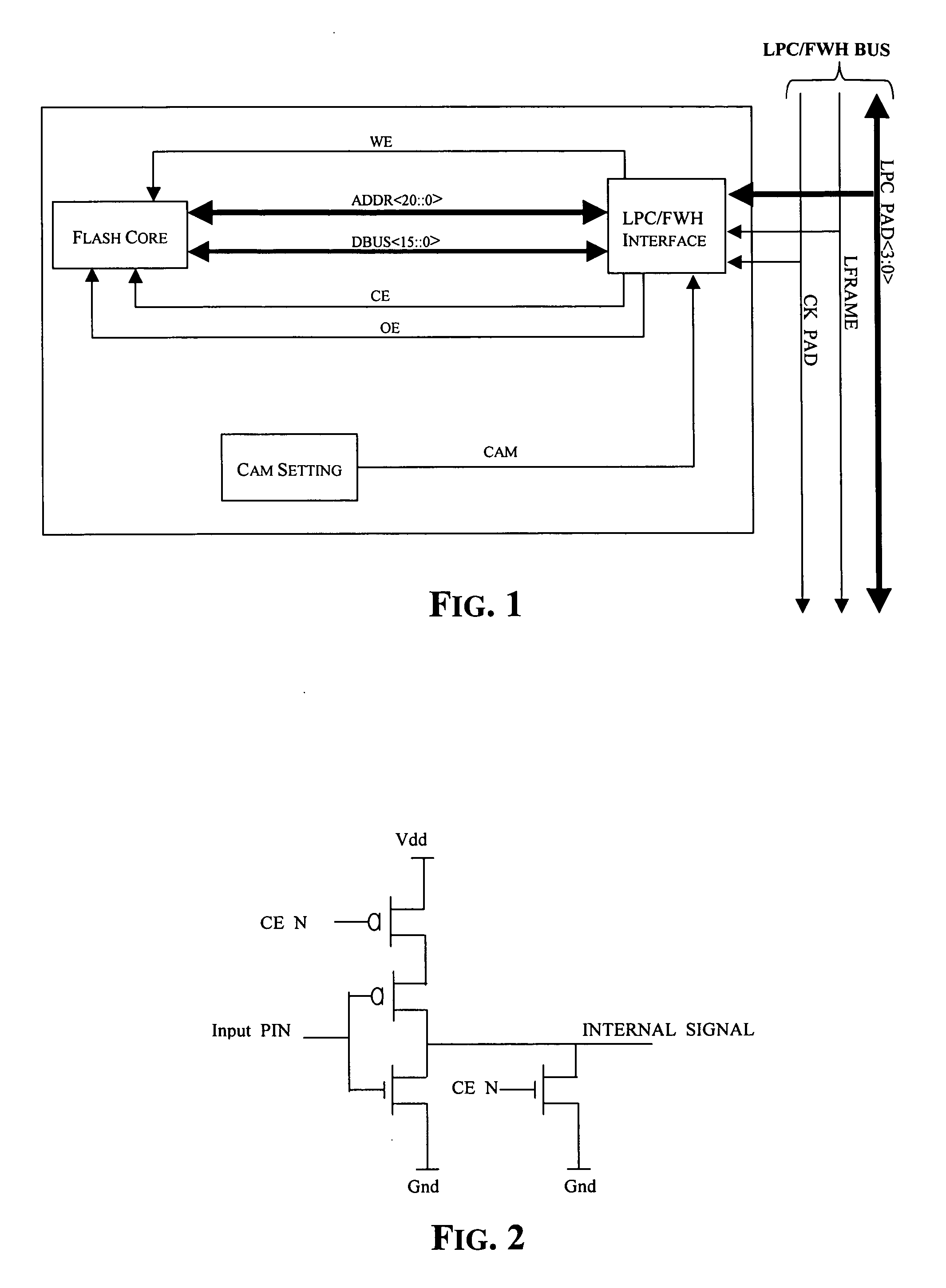
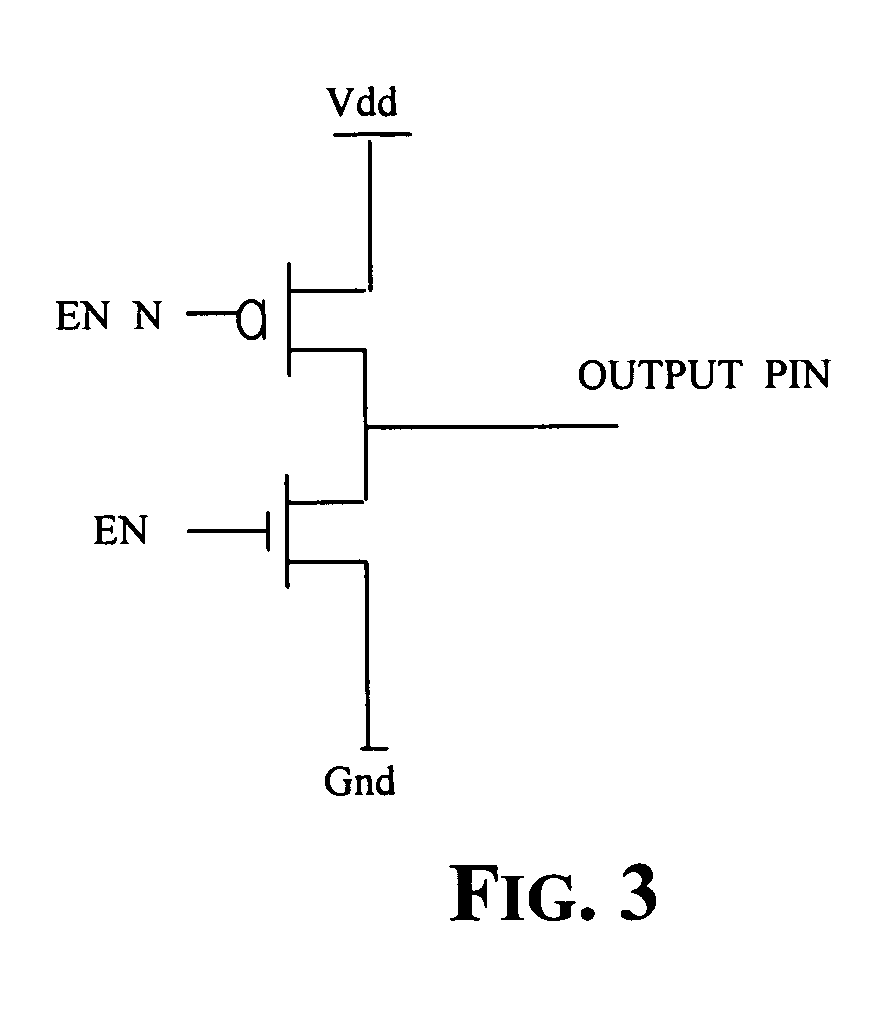
Method of generating an enable signal of a standard memory core and relative memory device
A memory device is configured for communicating with one of two different serial protocols, respectively an LPC or an SPI protocol, as well as with a parallel communication protocol through a multi-protocol interface while requiring only a single additional pin as compared to a standard memory device accessible with a parallel communication protocol. This result is achieved by exploiting the same pin for providing a timing signal for serial mode communications or an address multiplexing signal for parallel mode communications. The additional pin is used for conveying a start signal of an A / AMUX parallel communication protocol. The interface includes logic circuits that generate an enable signal for the standard memory core of the memory device.
Owner:MICRON TECH INC
Information processing apparatus and method, and program
InactiveUS20070239641A1Easy and efficientEasily and efficiently teachingProgramme-controlled manipulatorComputer controlInformation processingLearning unit
Teaching to a robot for an action on an external object can be made easily and efficiently. According to the present invention, there is provided an information processing apparatus including a learning unit for learning a predetermined time-series pattern, an output unit for outputting a time-series pattern corresponding to the result of learning by the learning unit, and an adjusting unit supplied with a time-series pattern obtained from an action made by an action unit on the basis of a time-series pattern supplied from the output unit and external teaching for the action to adjust a time-series pattern supplied from the output unit correspondingly to the input time-series pattern, the learning unit learning the time-series pattern supplied from the output unit and adjusted by the adjusting unit.
Owner:SONY CORP +1
Maximal frequent sequential pattern mining method based on distributed log
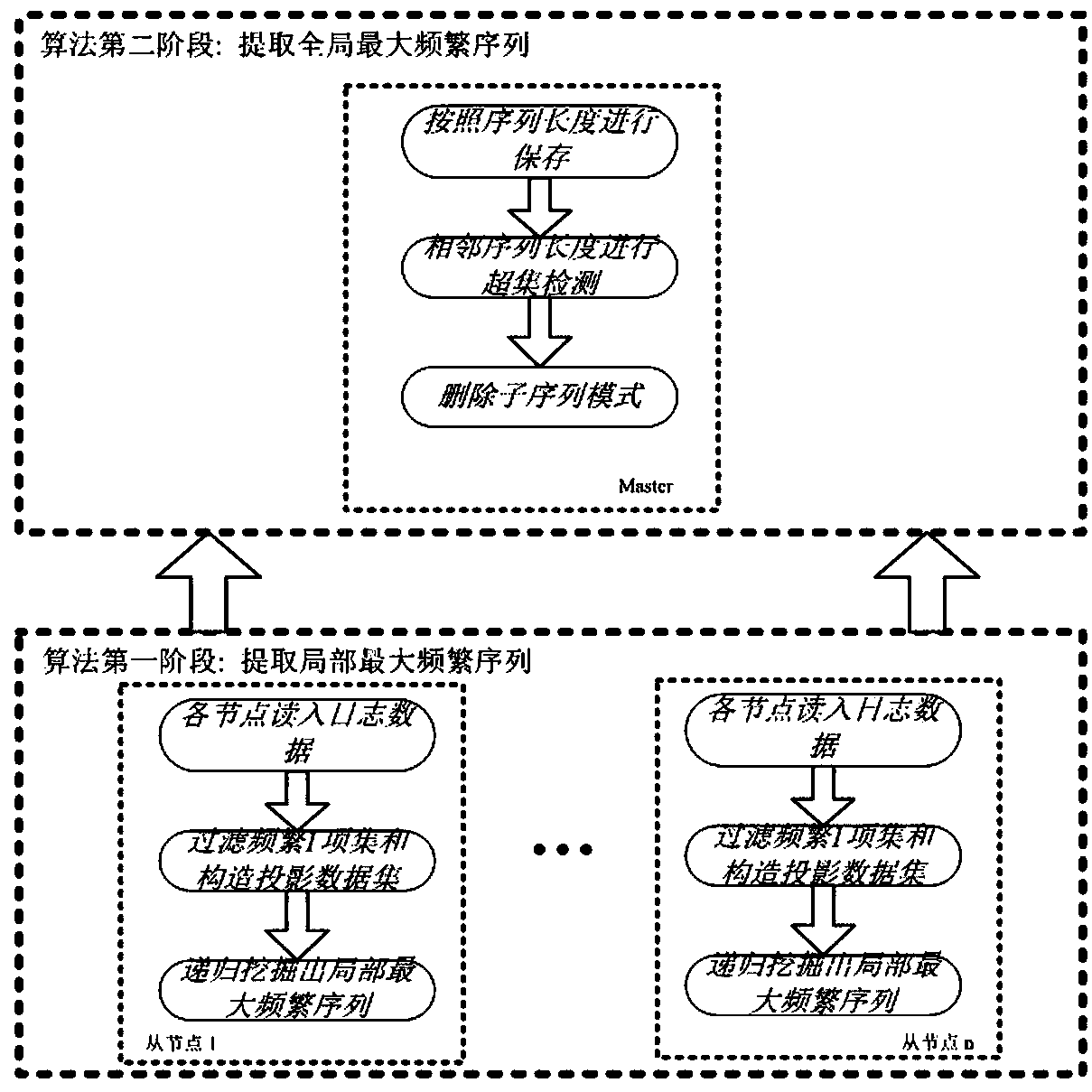
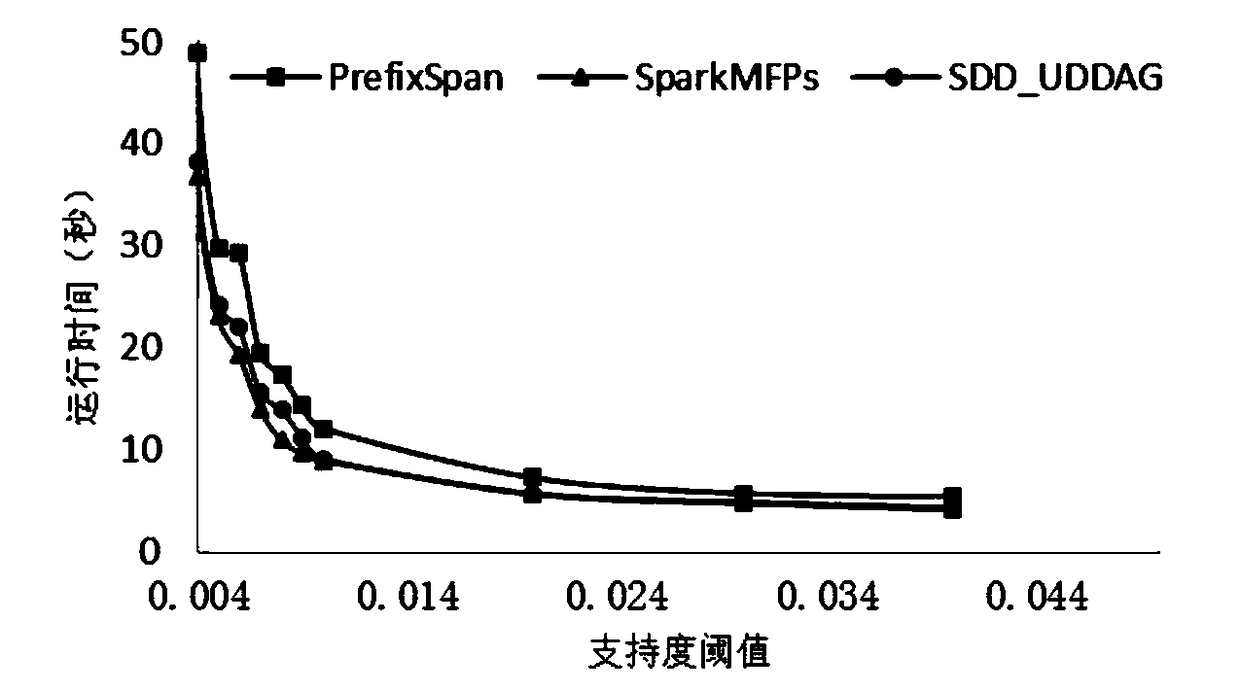
ActiveCN108874952AImprove scalabilitySolve mining problemsSpecial data processing applicationsData setSerial pattern
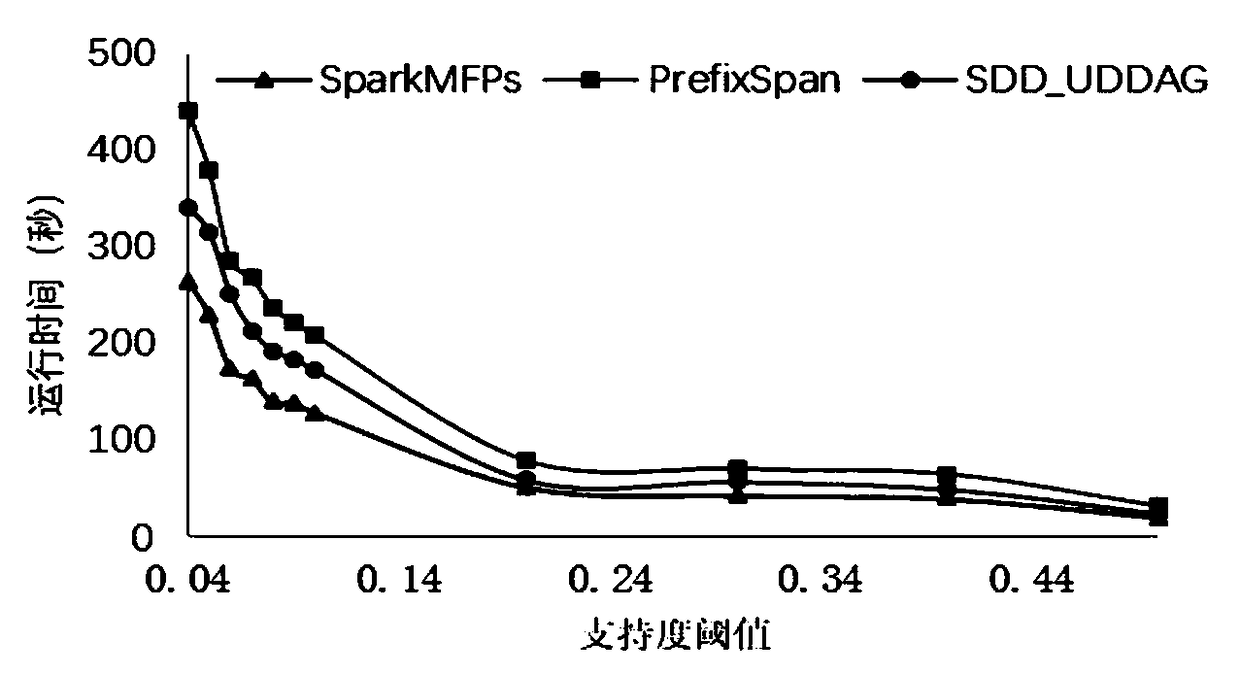
The invention relates to a maximal frequent sequential pattern mining method based on a distributed log.The method comprises the following steps that: on the basis of a Spark distributed computation framework, extracting a local maximal frequent sequence; utilizing prefix projection to divide search space, and carrying out recursive extraction on the local maximal frequent sequence, wherein a first frequent sequence deletes infrequent items in a log sequence dataset, a database scanning scale is lowered, and meanwhile, a corresponding relationship between the frequent sequential pattern and the maximum frequent sequential pattern is used for reducing a candidate sequence number; extracting a global maximum frequent sequence; storing the local maximal frequent sequence according to different lengths, and carrying out superset detection on the sequential pattern of adjacent lengths to judge whether a superset relationship is in the presence or not; and if the superset relationship is inthe presence, deleting a redundant sequence, and extracting a global maximum frequent sequence. The maximal frequent sequential pattern mining method based on the distributed log has higher efficiency, and supports the mining of larger-scale event sequence data.
Owner:FUJIAN NORMAL UNIV
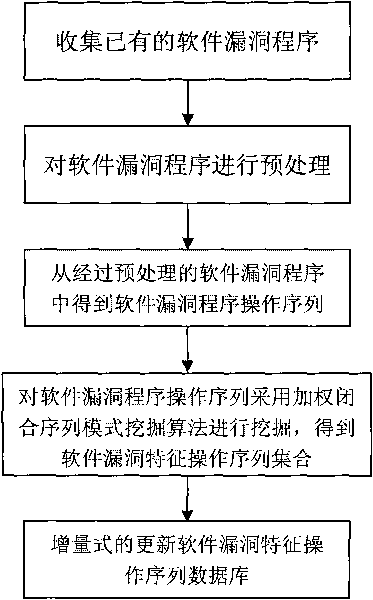
Method for extracting operation sequence of software vulnerability characteristics
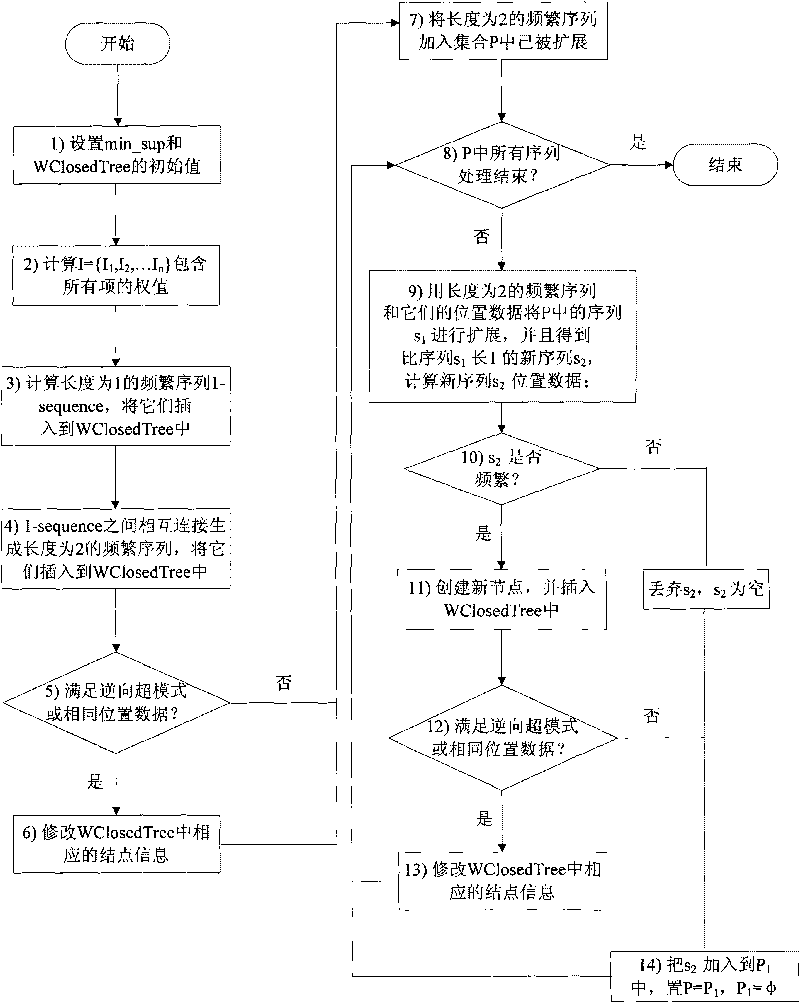
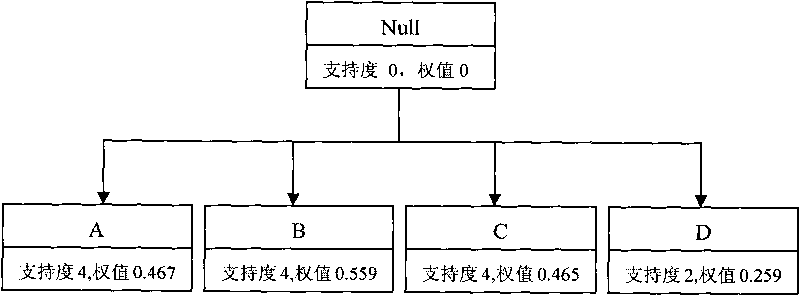
InactiveCN101727391AImprove analysis efficiencyImprove extraction efficiencySoftware testing/debuggingSerial patternSoftware engineering
The invention relates to a method for extracting an operation sequence of software vulnerability characteristics, in particular to a method for extracting an operation sequence of software vulnerability characteristics mined based on a close sequence mode, and belongs to the technical field of information safety. According to the method, a software vulnerability procedure is processed by using a function call relationship analysis technique and is abstracted as a data mode of the operation sequence of the software vulnerability procedure; and a weighted closed sequence is mined by adopting a weighted closed sequence mode mining algorithm, so that the extracting efficiency for the operation sequence of software vulnerability characteristics is increased.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
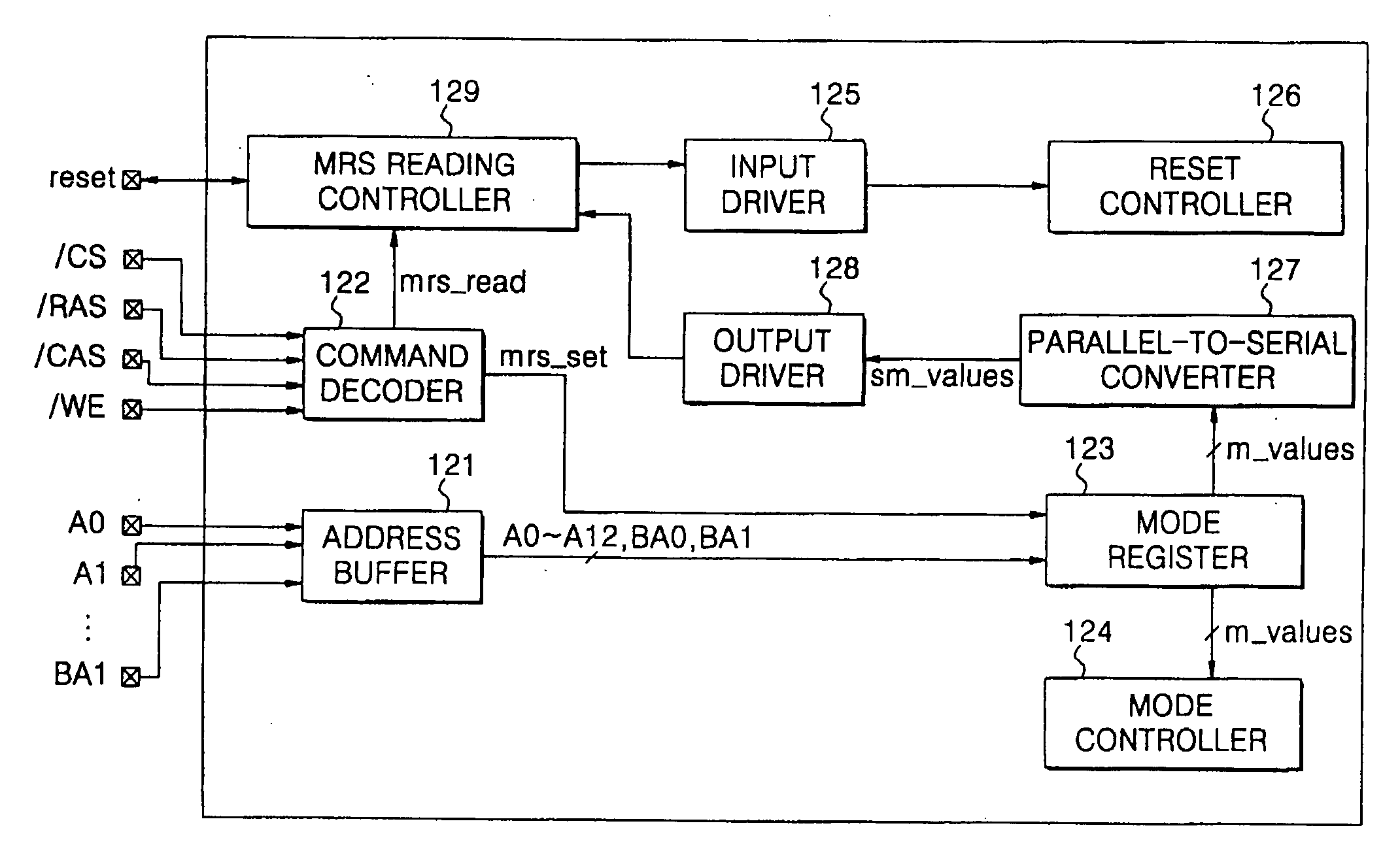
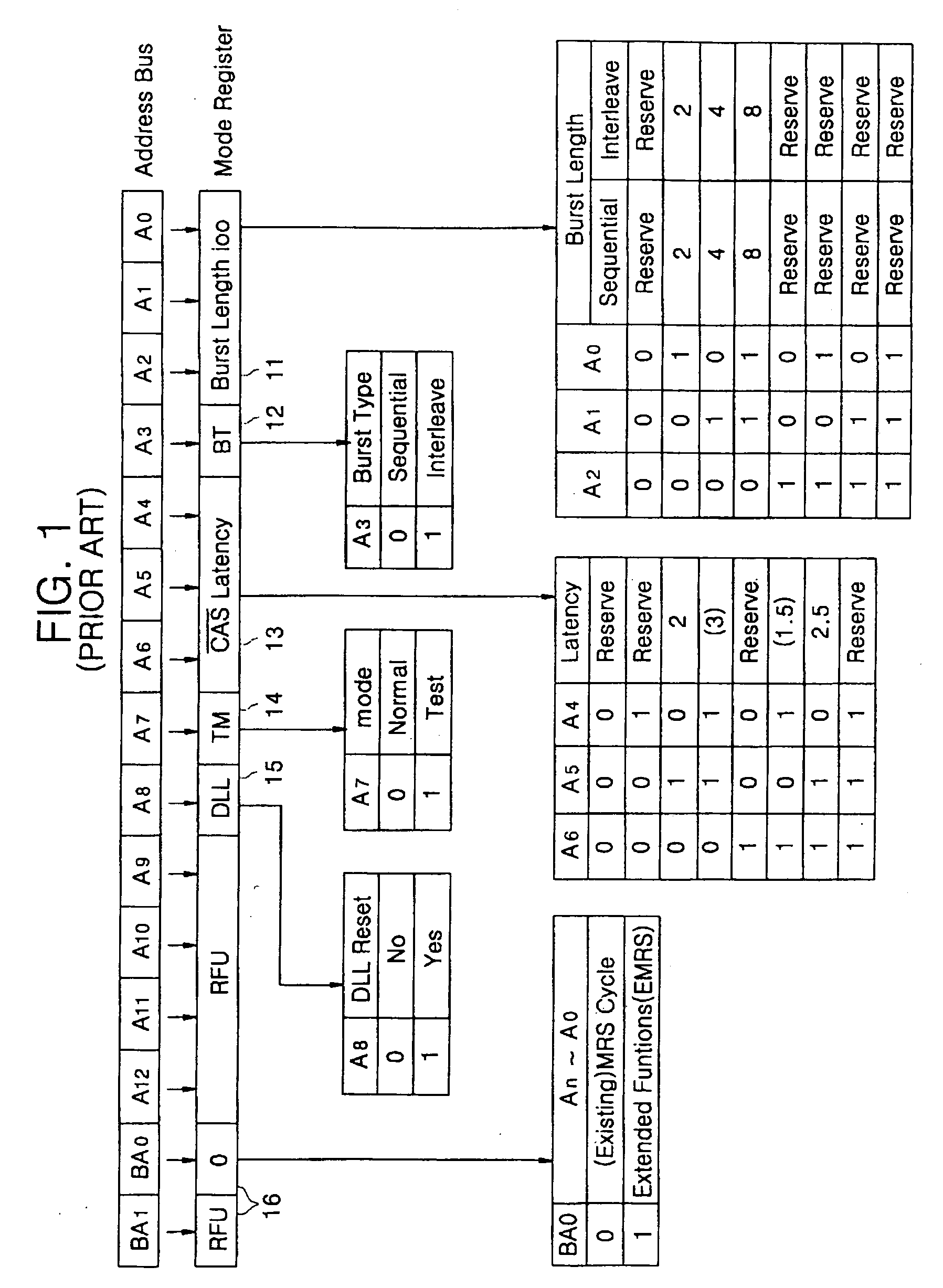
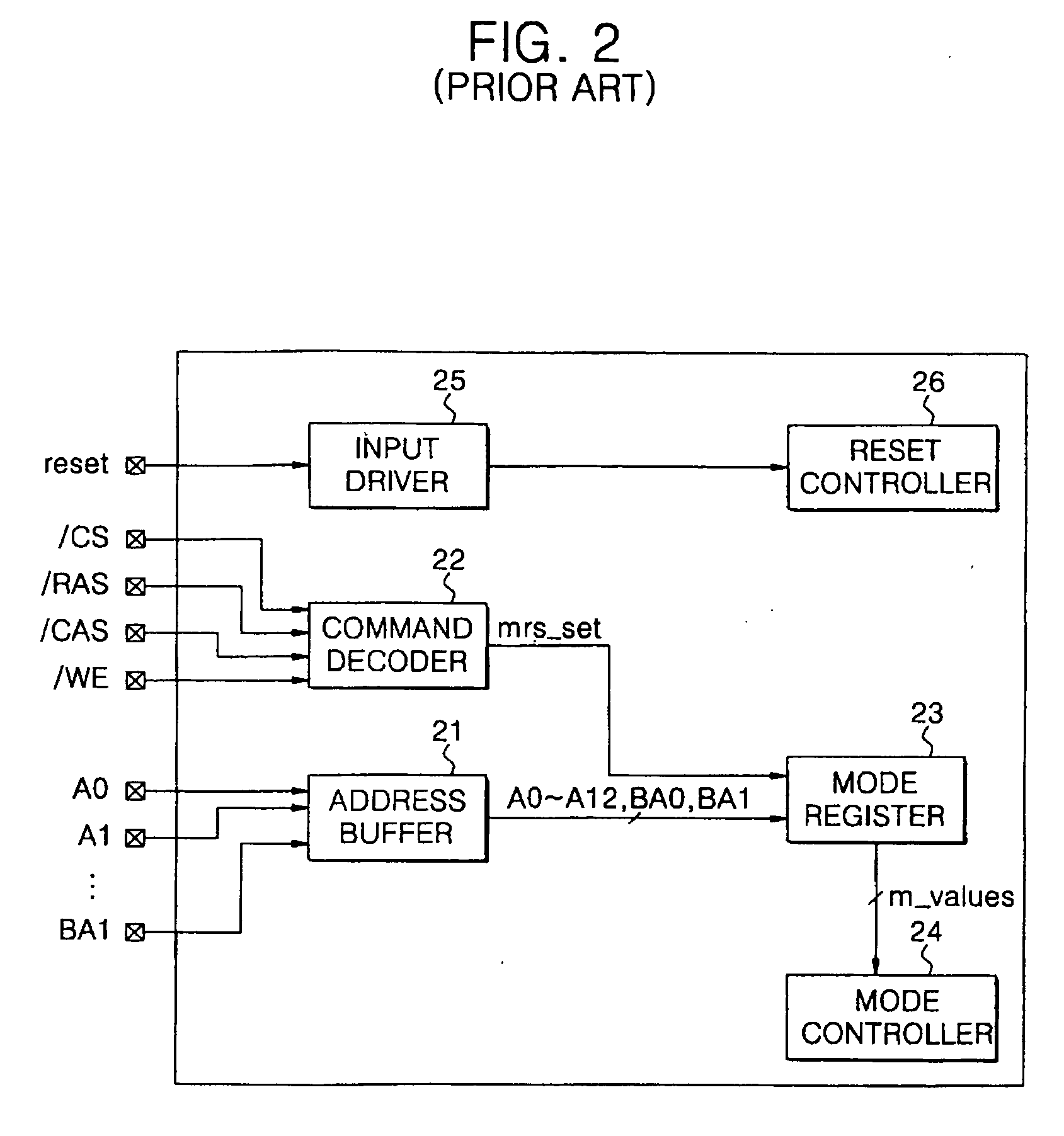
Semiconductor memory devices including mode registers and systems including the same
Semiconductor memory devices are provided. The semiconductor memory device includes a command decoder, a code converter and a code outputting unit. The command decoder is configured to receive a plurality of command signals from an external source, decode the plurality of command signals and generate a mode register reading signal responsive to the decoded plurality of command signals. The code converter is configured to receive mode setting codes generated based on the decoded plurality of command signals and convert the mode setting codes to serial mode setting codes. The code outputting unit is configured to receive the serial mode setting codes and output the serial mode setting codes to the external source responsive to the mode register reading signal. Systems including the semiconductor memory devices are also provided.
Owner:SAMSUNG ELECTRONICS CO LTD
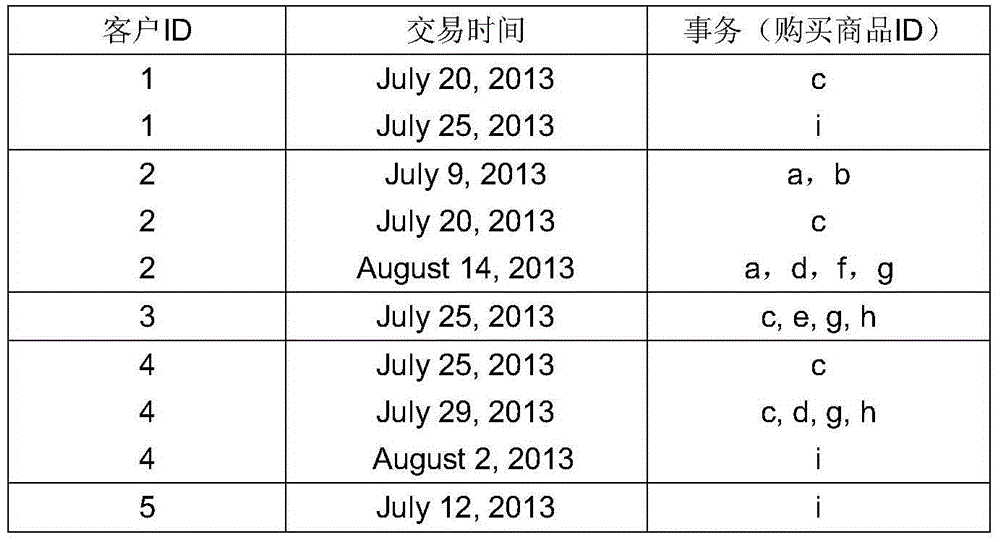
Method for quickly applying negative sequence mining patterns to customer purchasing behavior analysis
PendingCN104574153AIncrease trading opportunitiesIncrease loyaltySpecial data processing applicationsMarketingBehavioral analyticsSerial pattern
The invention provides a method for quickly applying negative sequence mining patterns to customer purchasing behavior analysis. A fast algorithm named as f-NSP is proposed to efficiently mine the negative sequential patterns. According to the main idea of the algorithm, firstly, a positive sequential pattern is obtained through a positive sequential pattern mining algorithm, and as for all frequent positive sequences, an efficient bitmap storage structure is used for storing data sequences including the frequent positive sequences; secondly, negative candidates are generated through a method which is the same as e-NSP and is used for generating negative candidate sequences; finally, data bitmaps are subjected to and operation, or operation and xor operation by means of a formula, the support degree of the negative candidates is quickly calculated, the negative sequential pattern meeting the minimum support degree is mined, and a database does not need to be scanned again. Purchasing behaviors of customers are analyzed through screened sequential patterns so that a seller can predict subsequent commodity buying and selling conditions according to current commodity buying and selling conditions; as a result, the seller can arrange placement of commodities better, and the sale quantity of the commodities can be increased.
Owner:QILU UNIV OF TECH
Multi-track malicious program feature detecting method based on data mining
ActiveCN105138916AImprove accuracyHigh precisionPlatform integrity maintainanceFeature extractionSerial pattern
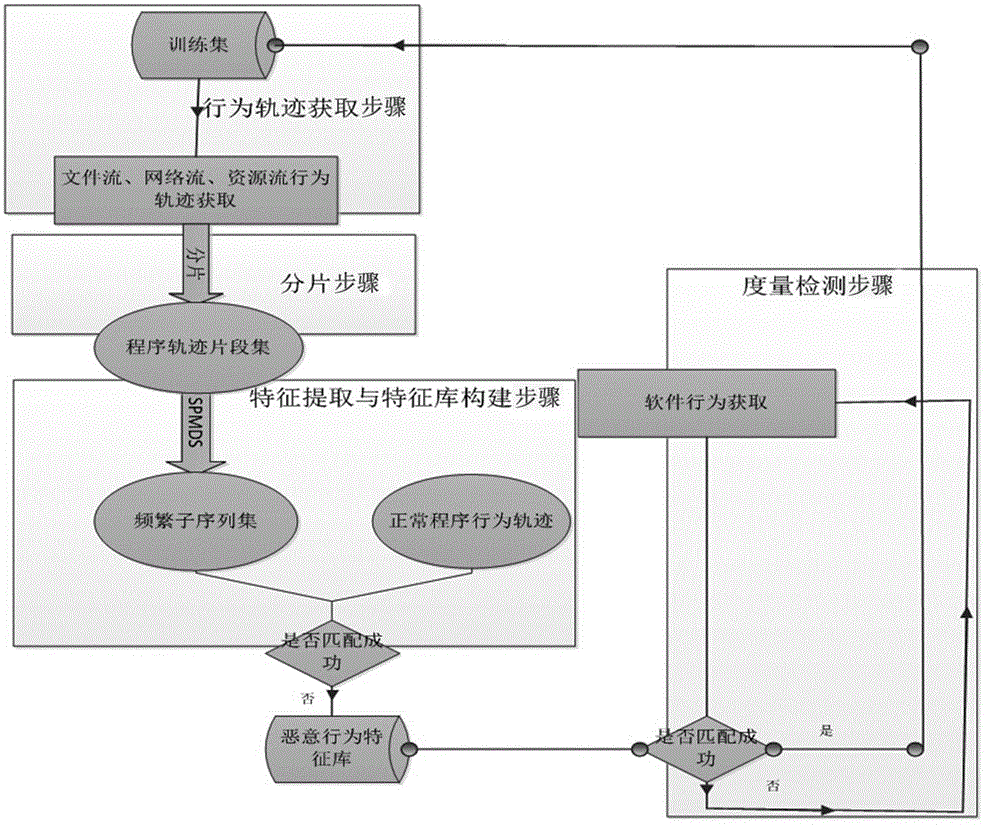
The invention relates to a multi-track malicious program feature detecting method based on data mining. The multi-track malicious program feature detecting method comprises the step of behavior track acquiring, the step of zone partitioning, the step of feature extracting and feature library establishing and the step of magnanimity detecting. In the step of behavior track acquiring, a dynamically-operating system calling sequence of a program is obtained; in the step of zone partitioning, zone portioning is carried out on obtained software behavior tracks so as to adapt to the needs of the mining process; in the step of feature extracting and feature library establishing, a sequence mode mining algorithm improved in data mining is adopted for acquiring a data flow, network flow and resource flow behavior frequent subsequence set, removing normal program behavior track fragments and structure a malicious behavior feature library; in the step of magnanimity detecting, magnanimity detecting is carried out on a program operating in real time according to the structured three-dimensional feature library. The multi-track malicious program feature detecting method based on data mining is high in detection accuracy.
Owner:THE PLA INFORMATION ENG UNIV
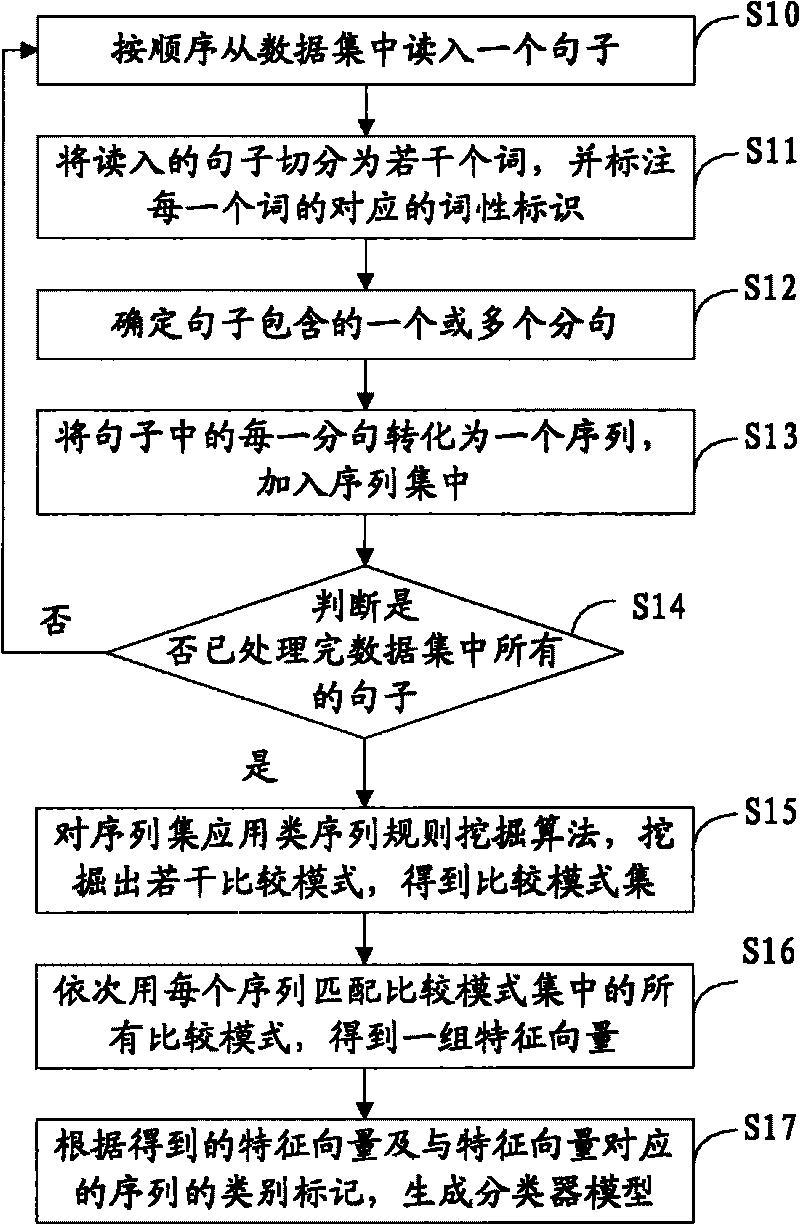
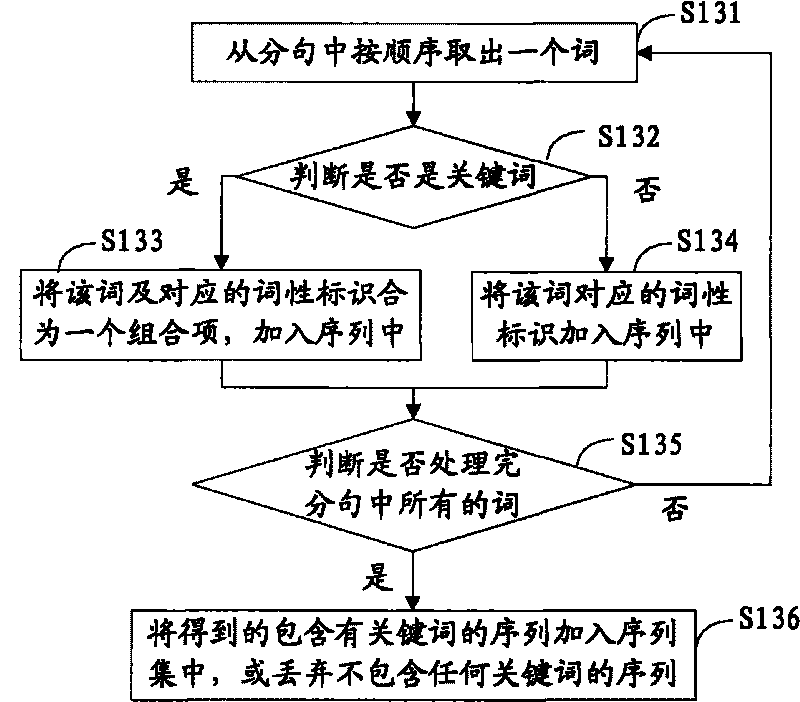
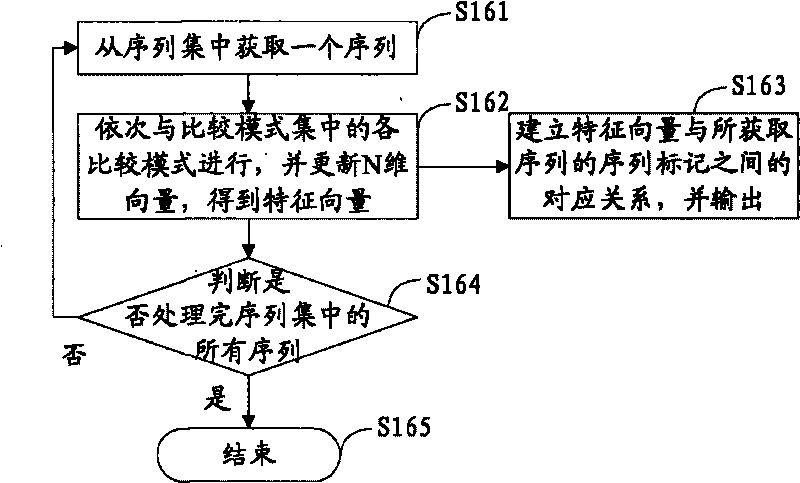
Method and device for generating Chinese comparative sentence sorter model and identifying Chinese comparative sentences
The invention discloses a method and a device for generating a Chinese comparative sentence sorter model and identifying Chinese comparative sentences. The method comprises the following steps: converting each clause containing set comparative keywords in each sentence of a data set into a sequence, and establishing a category tag as the same as the sentence of a corresponding clause for the sequence; obtaining a sequence set; mining a plurality of comparative modes from the sequence set by a sequence mode mining algorithm, and forming a comparative mode set; matching each comparative mode in the comparative mode set with each sequence one by one, and according to the matching result and the total number of the comparative modes, obtaining a group of characteristic vectors corresponding to each sequence; generating a sorter model according to the characteristic vectors and the corresponding category tag of the sequence; and then identifying a read-in sentence with unknown category through the obtained comparative mode set and the sorter model, and determining whether the sentence is a comparative sentence. By automatically learning the mode characteristics of the comparative sentences, the sorter model is generated and can automatically and effectively identify the comparative sentences in a text.
Owner:PEKING UNIV +2
Integral frequency bias and fine synchronization method and apparatus of receiver
InactiveCN101312447AImprove estimation performanceEstimated range is largePulse modulation television signal transmissionMulti-frequency code systemsSerial patternComputer science
The invention discloses an integer frequency bias estimation and fine synchronization method of a receiver and discloses a device thereof, for processing integer frequency bias estimation on the received signals of different frame head sequence modes and carrier frequency bias. The method comprises that: (1) a receiver first processes synchronous capture on the received signals, to attain the coarse synchronization positions and the frame head modes of the received signals; (2) the receiver processes decimal frequency bias estimation on the received signals and then processes decimal frequency bias compensation on the received signals; (3) the receiver attains the real phase of the pseudo random sequence of the frame head with the frame head mode having phase rotation; (4) according to the coarse synchronization position, the frame head mode and the phase of the frame of the received signals, the receiver processes integer frequency bias estimation on the received signals after the decimal frequency bias compensation. The invention can realize integer frequency bias estimation on the receiver of a DTMB system, having better estimation performance and large estimation range.
Owner:INNOFIDEI TECHNOLOGIES INC
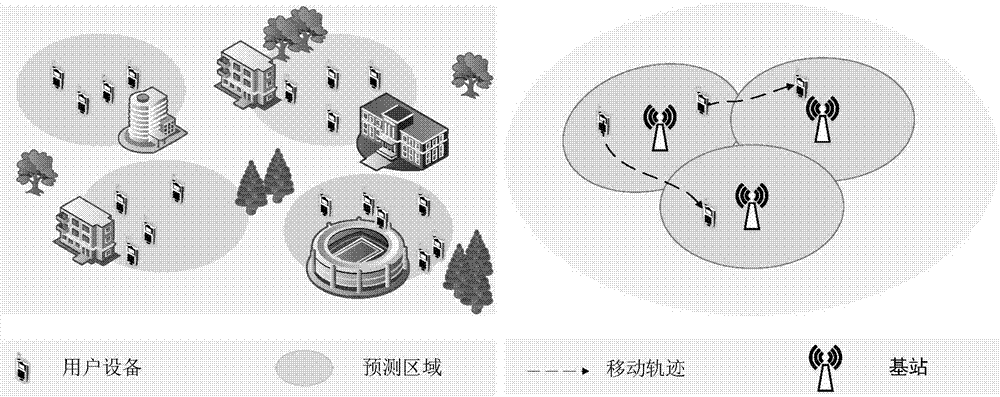
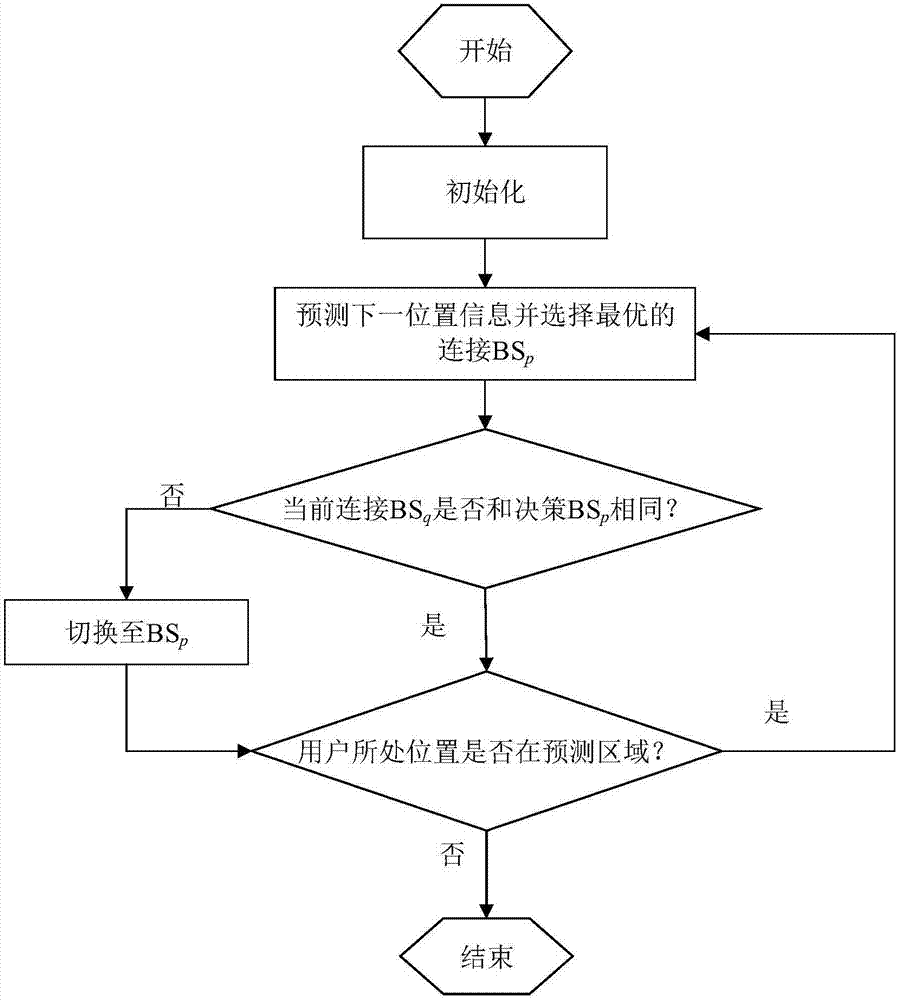
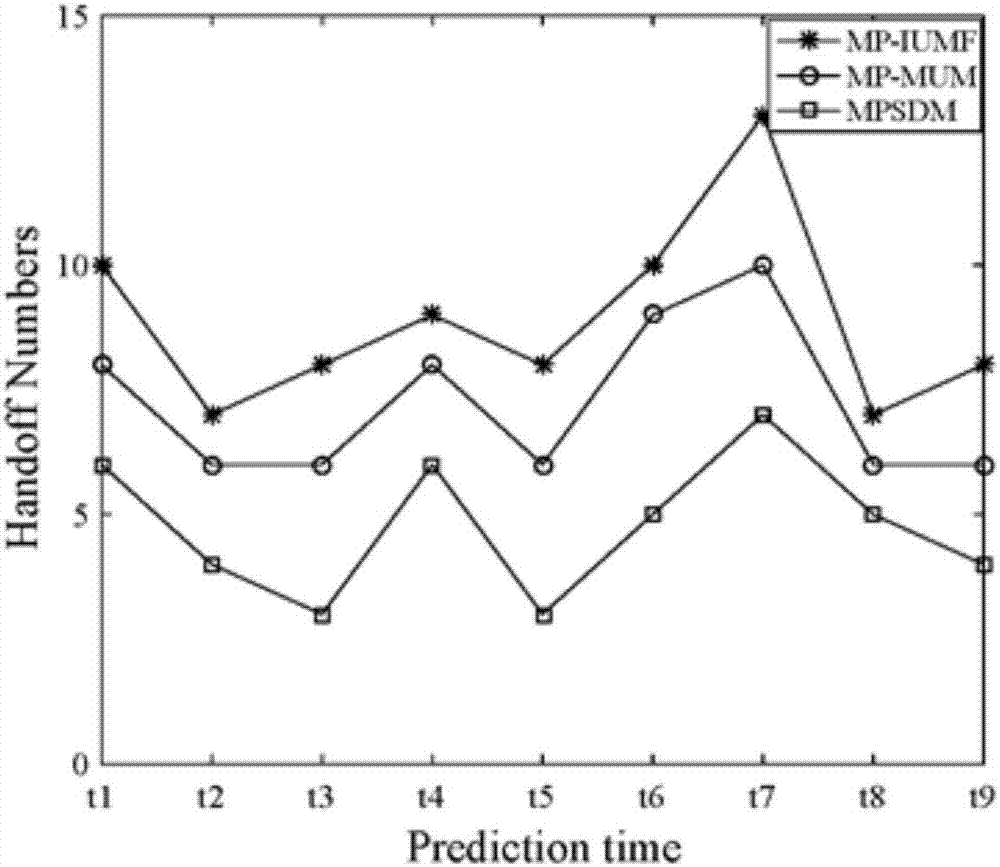
Mobility prediction method based on fuzzy clustering in outdoor crowded places
ActiveCN107426703AAccurate prediction of movement trajectoryGuaranteed continuous communication serviceLocation information based servicePattern sequenceSerial pattern
The invention provides a mobility prediction method based on fuzzy clustering in outdoor crowded places, and belongs to the field of mobile communication technology. The scene is divided into several prediction regions, and the prediction time is divided into several time periods, user moving trajectories are divided into different groups within each prediction region according to the prediction time, irregular trajectories are removed in a sequence mode, a sequence in a frequency mobility mode is found, the position of the next position is predicted by matching the user moving trajectories with a historical user moving trajectory, and thus the prediction accuracy is improved. By adoption of the mobility prediction method, the continuous communication service of the users in the outdoor crowded places is guaranteed, the unnecessary switching times are effectively reduced, and the user residence time is prolonged. According to the mobility prediction method, the user moving trajectories in the outdoor crowded places are analyzed and modeled to help to analyze and solve other related user behavior problems in the outdoor crowded places.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Similar hydrologic process searching method using user interaction
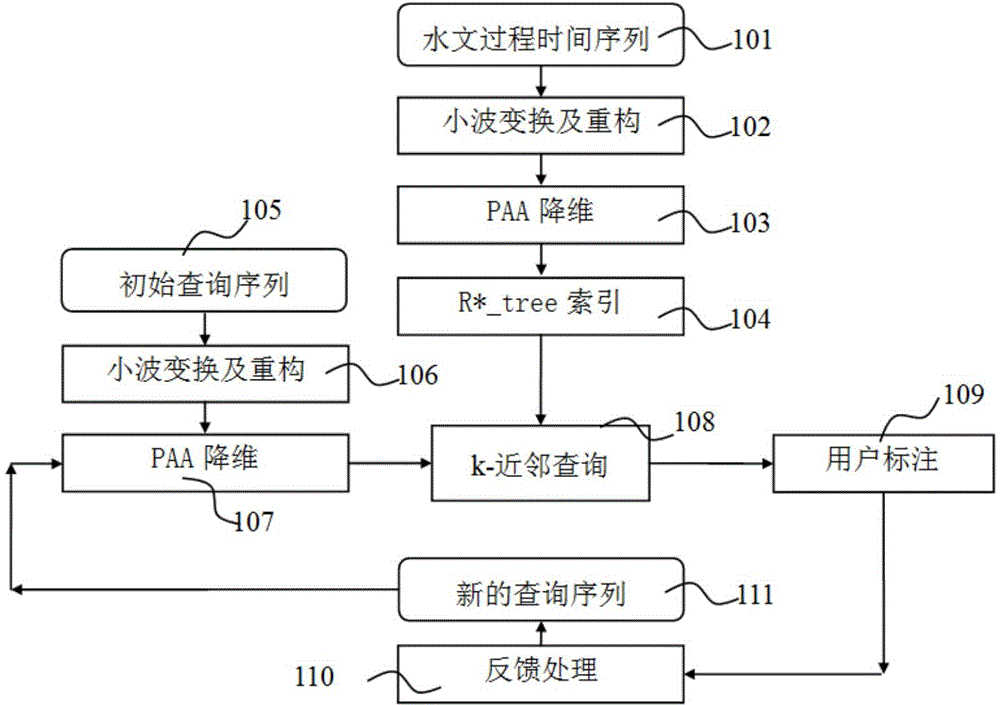
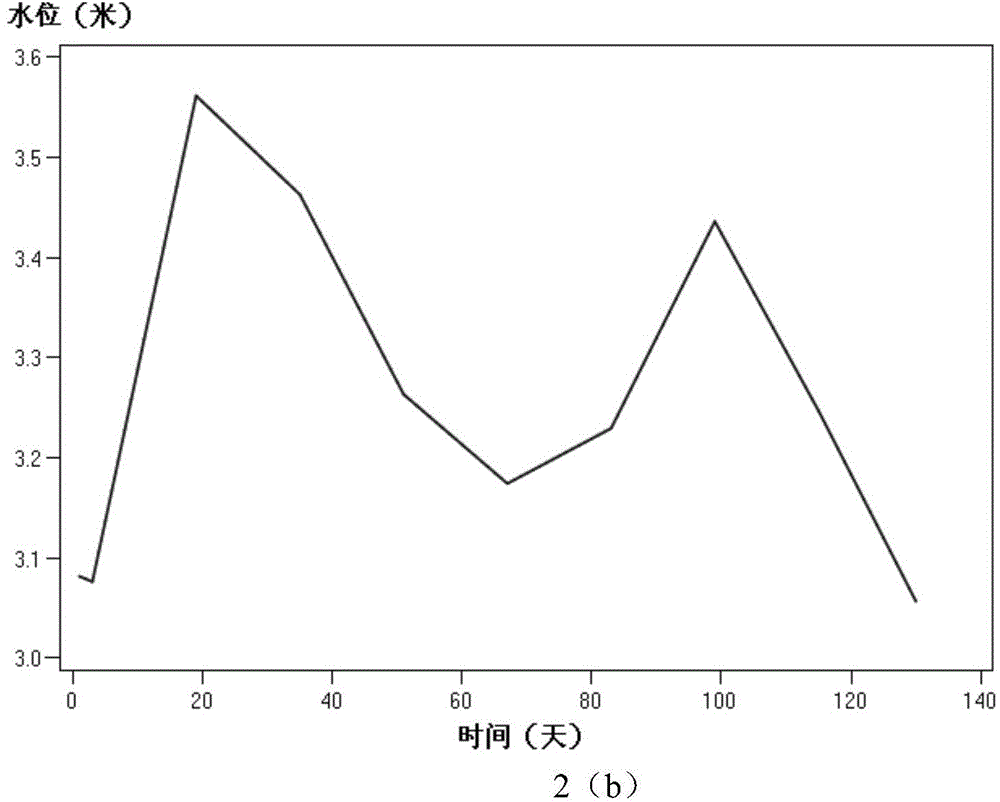
InactiveCN104794153AImprove accuracyEasy to extract and calculateSpecial data processing applicationsSerial patternData mining
The invention discloses a similar hydrologic process searching method using user interaction. An Euclidean distance with weight is used as similar measurement, similar searching is conducted on a search sequence designated by a user, the user conducts marking on a search result, and similar level or dissimilar level is set on the search result according to the understanding of the user on a search sequence mode; the similar or dissimilar sequence properties are combined by an algorithm, the weight is regulated, so that a search sequence better meeting requirements of the user is generated, search is conducted circularly until the user terminates the search process. According to the similar hydrologic process searching method using user interaction, the user interaction is used for regulating the search sequence and the weight, the search accuracy is improved, and the accuracy of the hydrologic sequence similar search is improved.
Owner:HOHAI UNIV
Program -class operating system debug method based on serial mode excavation
InactiveCN101308473APrecise positioningRapid positioningSoftware testing/debuggingOperational systemSerial pattern
The invention discloses a program-level operating system debugging method based on sequential pattern mining, comprising the following steps: to find all the frequent system calling sequential patterns through sequential pattern mining; to compute all the parameters in a hidden Markov model to identify abnormal system calling sequences. The method makes use of the sequential pattern mining method to carry through pattern mining to the system calling sequence set in the desktop operating system to find all the frequent sequence set, and also makes use of the frequent sequence set to train the hidden Markov model so as to eventually identify the abnormal system calling sequences through the Markov model to accurately and quickly target the bug location of the entire desktop operating system to help the user to improve the operating system.
Owner:ZHEJIANG UNIV
Semiconductor integrated circuit
InactiveUS20060225139A1Reduce power consumptionEasy to processEnergy efficient ICTDigital data processing detailsSerial patternSemiconductor
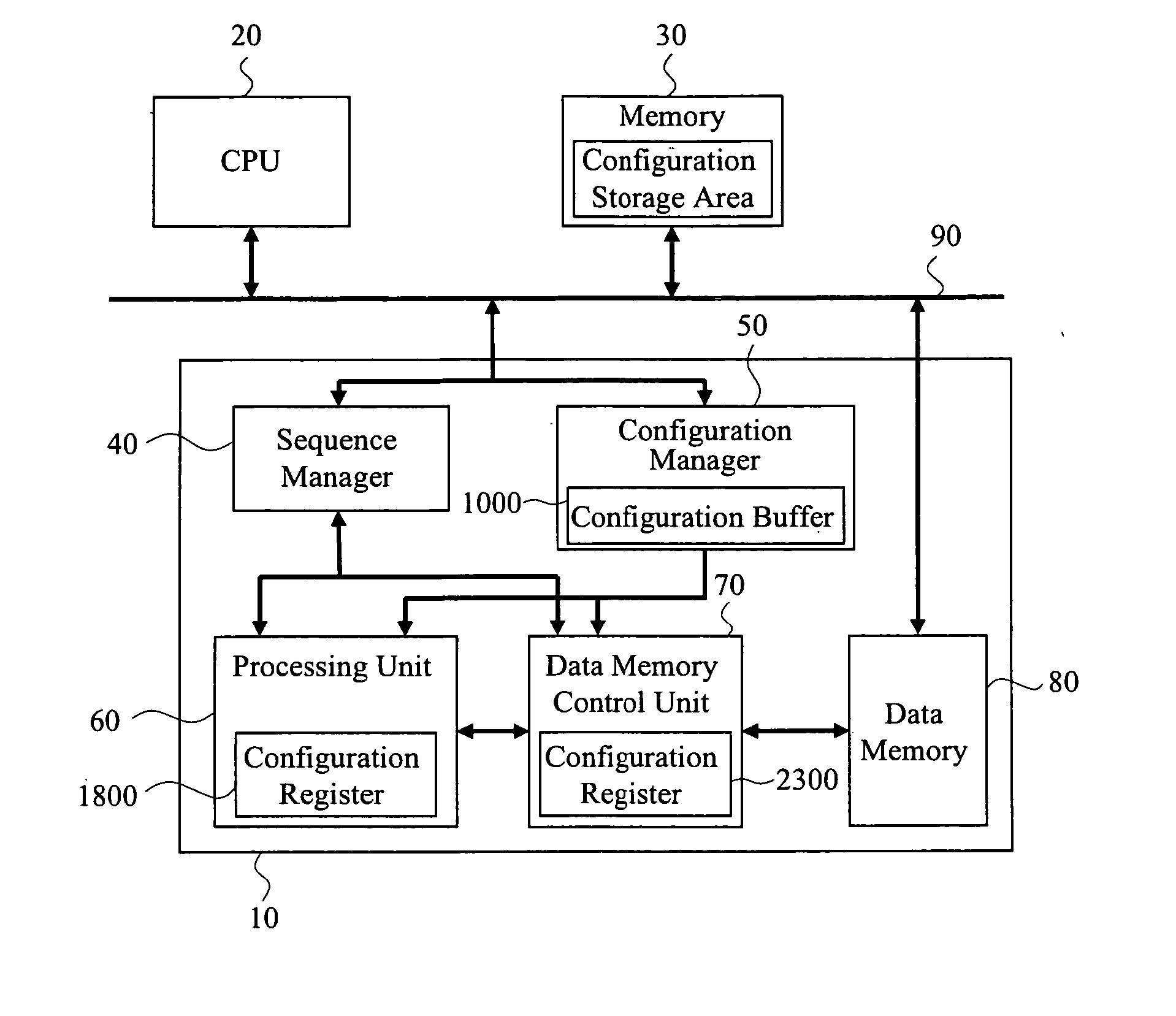
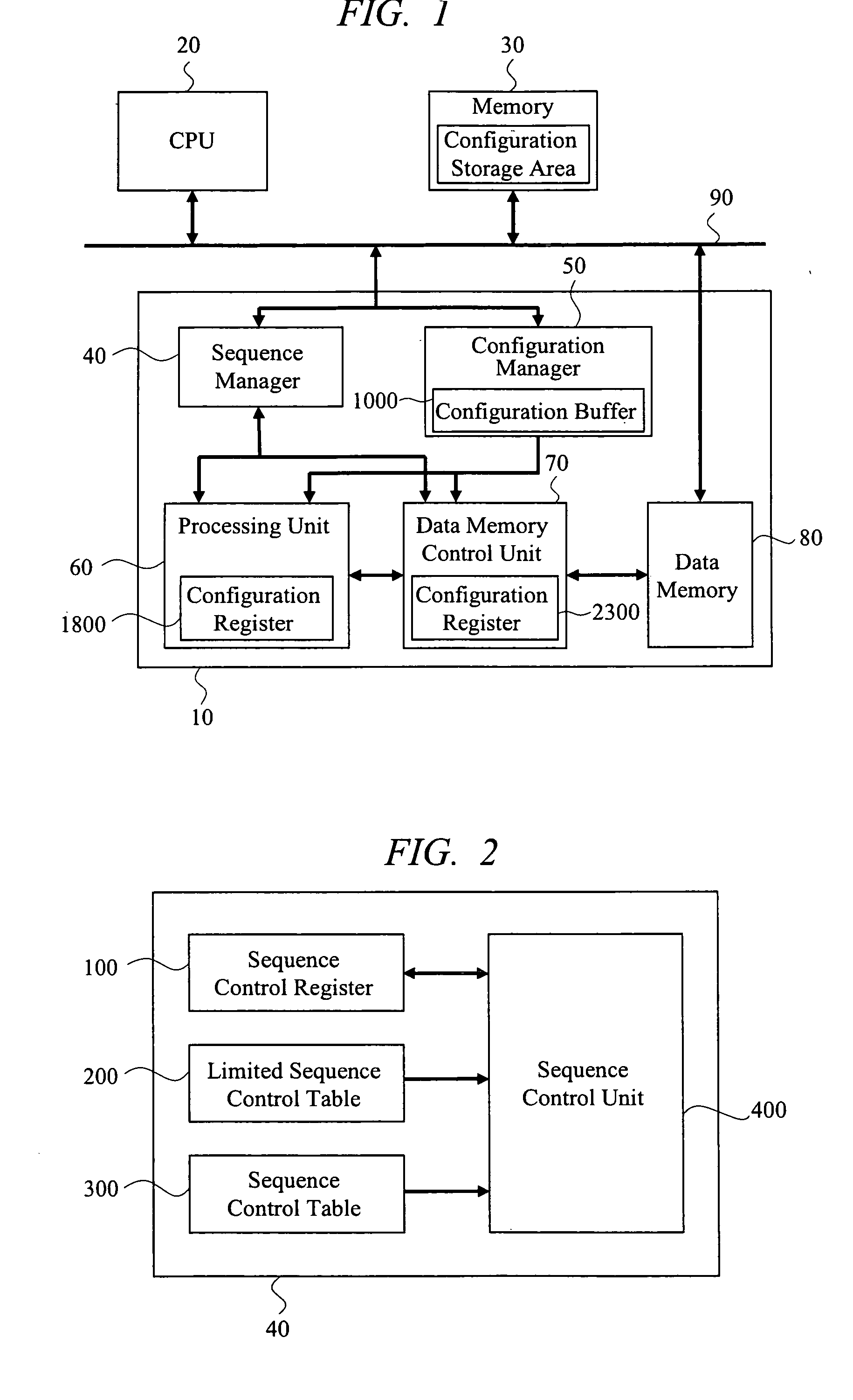
In a dynamic reconfigurable processor, a mechanism for effectively storing configuration data with a small hardware scale and improving processing performance is provided. Also, a sequence mechanism that is easy to be implemented with flexibility and a high operating frequency being both achieved is provided. The configuration data is hierarchically stored, and without suspending a process in a processing unit, configuration data required for subsequent processing is transferred in advance from a first storage area to a second storage area. Also, with a plurality of sequence modes, a condition determination process is performed on different sequence conditions.
Owner:RENESAS TECH CORP
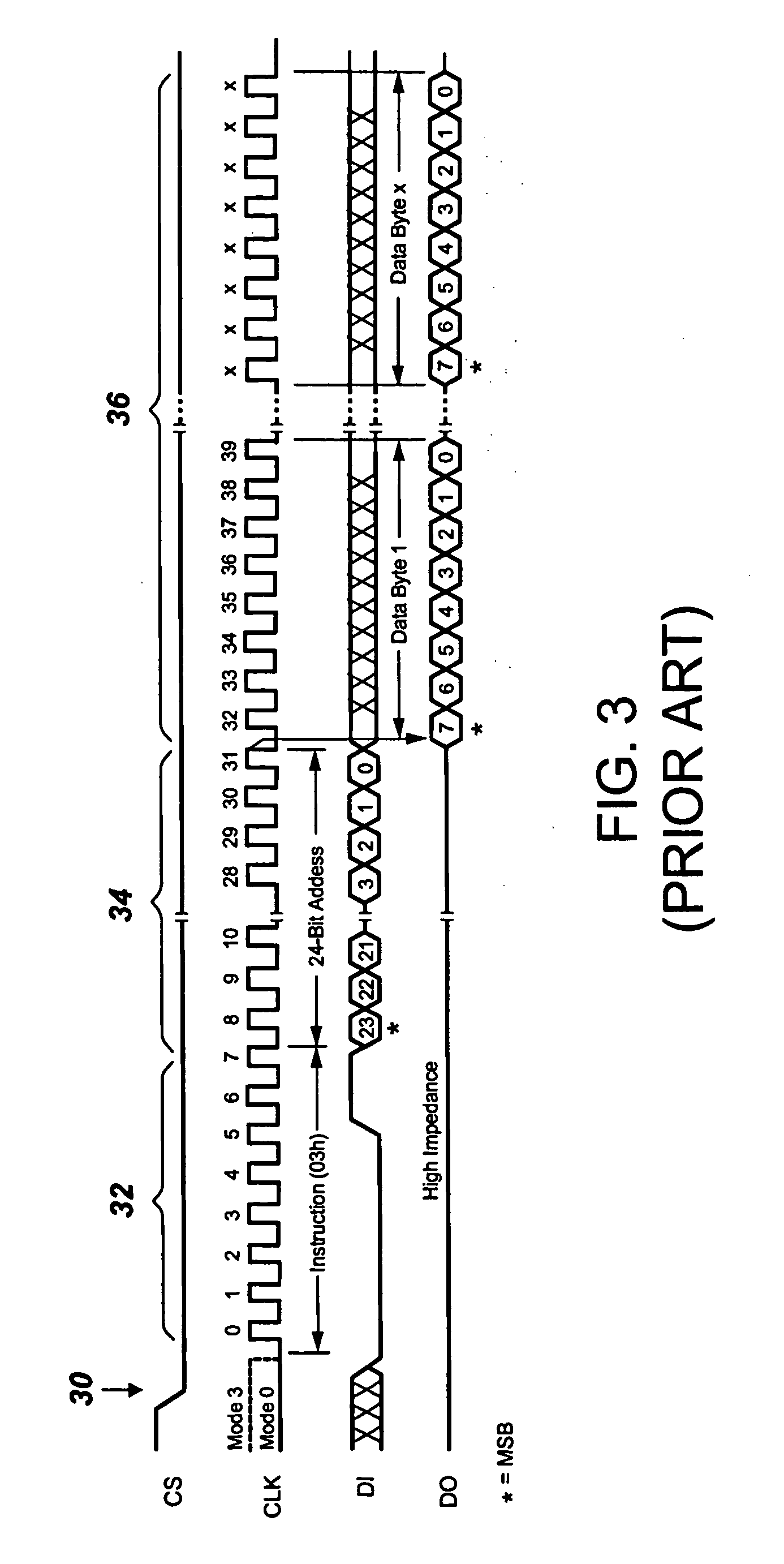
Serial flash semiconductor memory
InactiveUS20100049948A1Reduced pin countImprove rendering capabilitiesMemory adressing/allocation/relocationRead-only memoriesSerial patternLow Pin Count
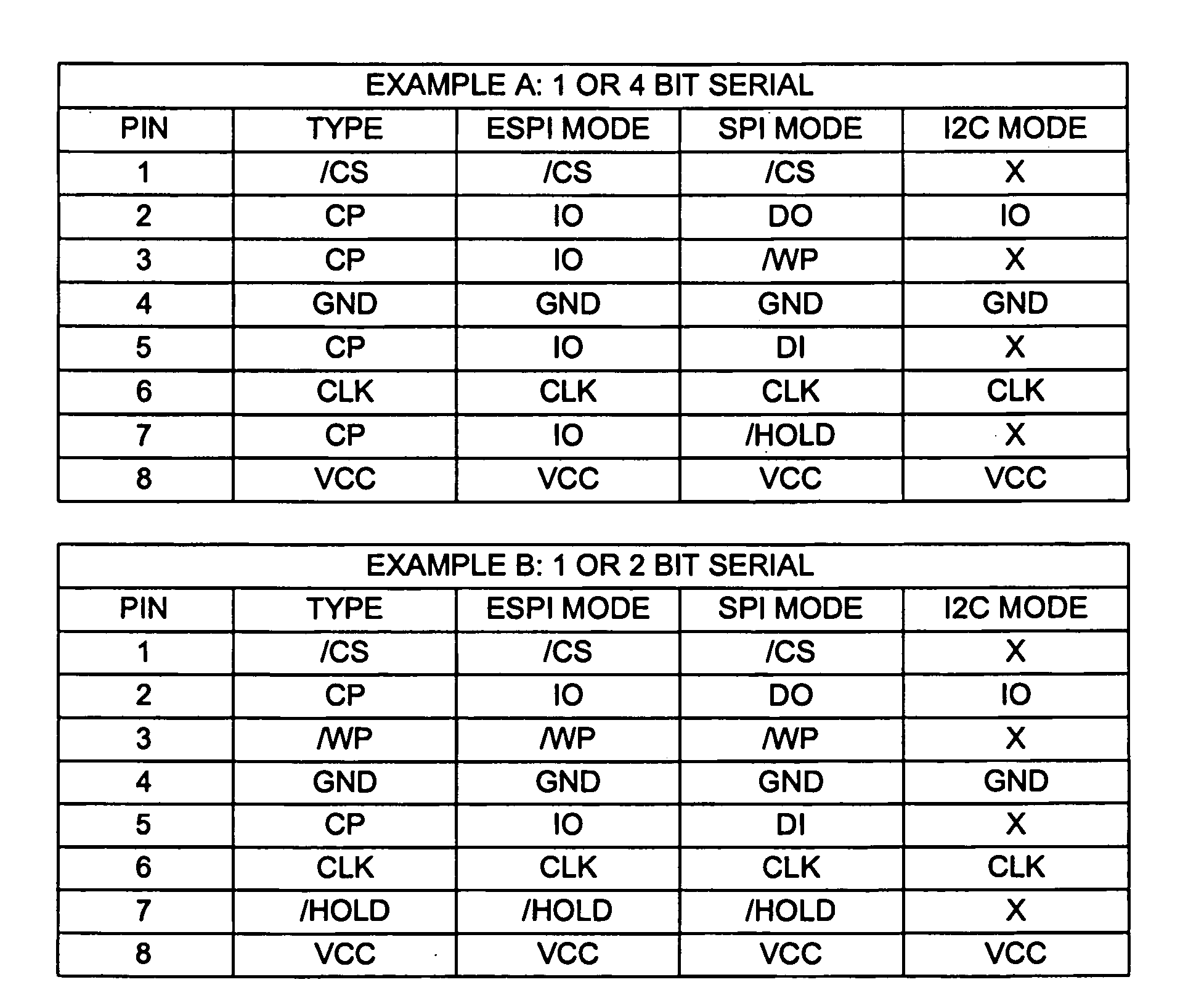
A serial flash memory is provided with multiple configurable pins, at least one of which is selectively configurable for use in either single-bit serial data transfers or multiple-bit serial data transfers. In single-bit serial mode, data transfer is bit-by-bit through a pin. In multiple-bit serial mode, a number of sequential bits are transferred at a time through respective pins. The serial flash memory may have 16 or fewer pins, and even 8 or fewer pins, so that low pin count packaging such as the 8-pin or 16-pin SOIC package and the 8-contact MLP / QFN / SON package may be used. The availability of the single-bit serial type protocol enables compatibility with a number of existing systems, while the availability of the multiple-bit serial type protocol enables the serial flash memory to provide data transfer rates, in systems that can support them, that are significantly faster than available with standard serial flash memories.
Owner:WINBOND ELECTRONICS CORP
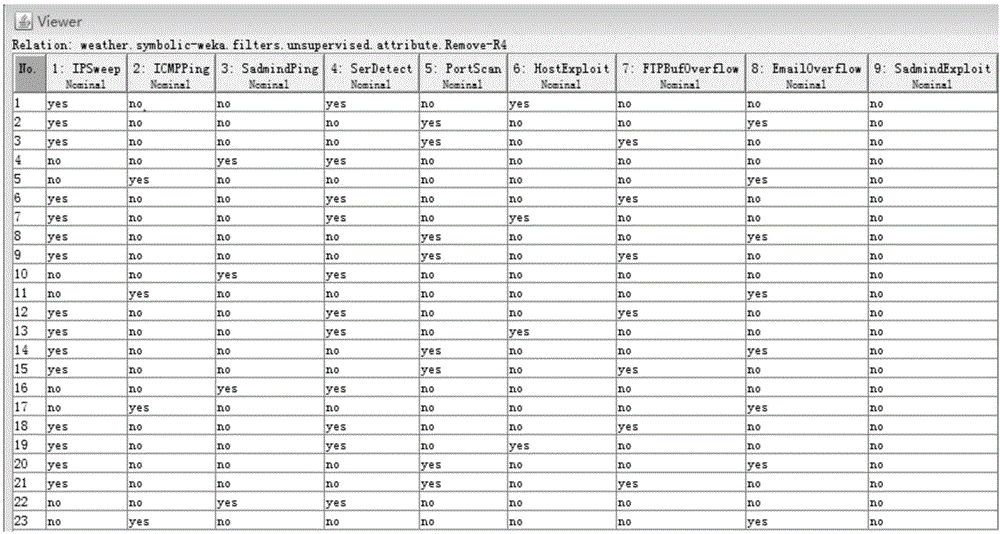
Multi-step attack prediction method based on cause-and-effect Byesian network
ActiveCN106411921AImprove attack prediction capabilitiesOptimized multi-step attack prediction methodTransmissionSerial patternNetwork attack
The invention relates to a multi-step attack prediction method based on a cause-and-effect Byesian network. First of all, a multi-step attack mode in an attack scene sample is mined by use of a frequent mode, the multi-step attack mode is depicted through a cause-and-effect Byesian network mode, based on this, a probability of future attacks is calculated through attack evidence, and thus next-step attack behaviors of network multi-step attacks and attack intensions of attackers can be predicted. According to the invention, a multi-step attack prediction method of manually constructing a network attack structure graph is optimized, the multi-step attack mode is mined automatically based on a frequent sequence mode, by means of the cause-and-effect Byesian network mode, the attack mode is depicted, network parameters are learnt, next-step attacks and the attack attentions are predicted, the attack prediction capability for unknown changing multi-step attack modes is improved, next-step attack means and a final attack attention of the multi-step attacks can be rapidly and accurately predicted, and the method has great realistic significance for safeguarding network and computer information security.
Owner:THE PLA INFORMATION ENG UNIV
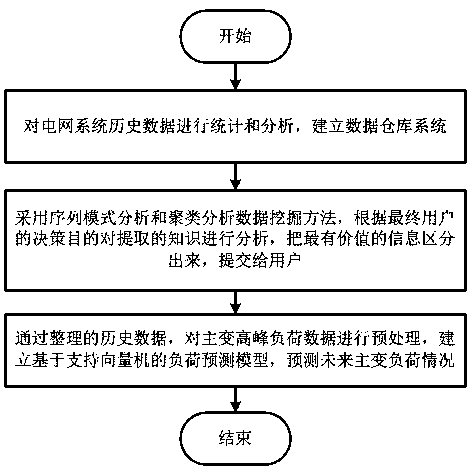
Electric power big data-based main transformer peak load prediction method and data warehouse system
InactiveCN107918639AAccurate extractionFast and accurate prediction of main transformer peak loadForecastingMulti-dimensional databasesAnalysis dataData warehouse
The invention relates to the technical field of electric power systems, and in particular to an electric power big data-based main transformer peak load prediction method and a data warehouse system.The method comprises the following steps of: S1, carrying out statistics and analysis on history data of a power grid system, so as to establish the data warehouse system; S2, analyzing an extracted knowledge according to a decision purpose of a final user by adoption of a sequence mode analysis and clustering analysis data mining method, distinguishing most valuable information and submitting theinformation to the user; and S3, preprocessing main transformer peak load data through the arranged history data, and establishing a support vector machine-based load prediction model to predict thefuture main transformer load condition. According to the electric power big data-based main transformer peak load prediction method, the data warehouse system is established, the data mining method isestablished, and the support vector machine-based method is adopted to predict the main transformer load change condition, so that correct and reliable main transformer peak load prediction is realized, and systems are reasonably scheduled to ensure safe and economic operation.
Owner:广东电网有限责任公司云浮供电局
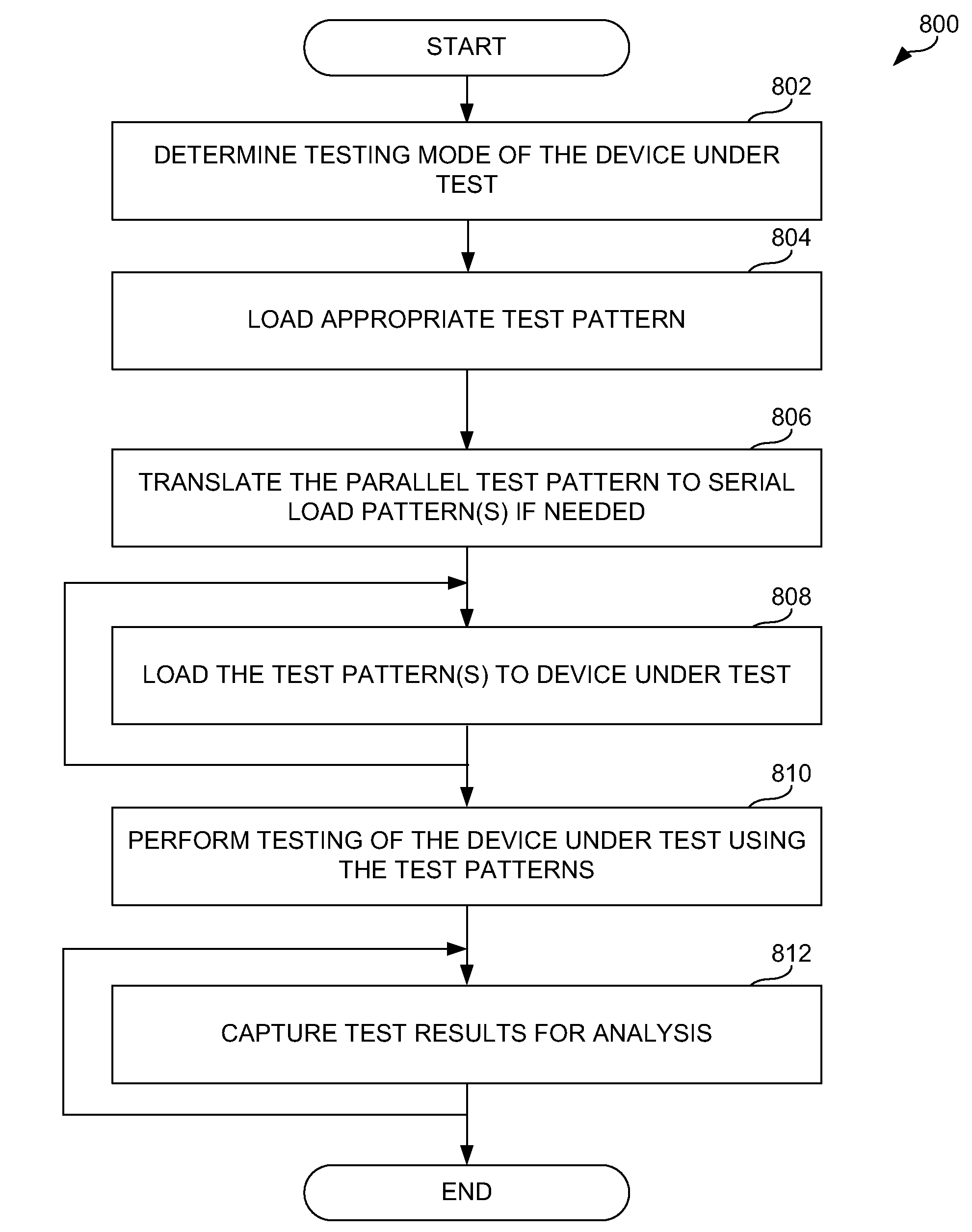
Serial test mode of an integrated circuit (IC)
InactiveUS20100100786A1Reduce in quantityElectronic circuit testingError detection/correctionComputer hardwareSoftware engine
A methodology to perform testing of integrated circuits (IC) wherein a reduced number of Input / Output (IO) pins may used to load testing patterns and capture test results from test structures after an IC has been installed in its intended application is provided. This methodology utilizes a software engine that receives and translates a parallel test pattern into serial data patterns operable to be provided on the reduced number of I / O pins. A serial process loader then loads the serial data patterns to the test structures within the IC. The IC receives the serial patterns and in turn translates them into parallel test patterns in order to apply the test patterns to the appropriate test structures. The results are captured and then translated into a serial format for communication from the IC to a test unit for analysis.
Owner:IBM CORP
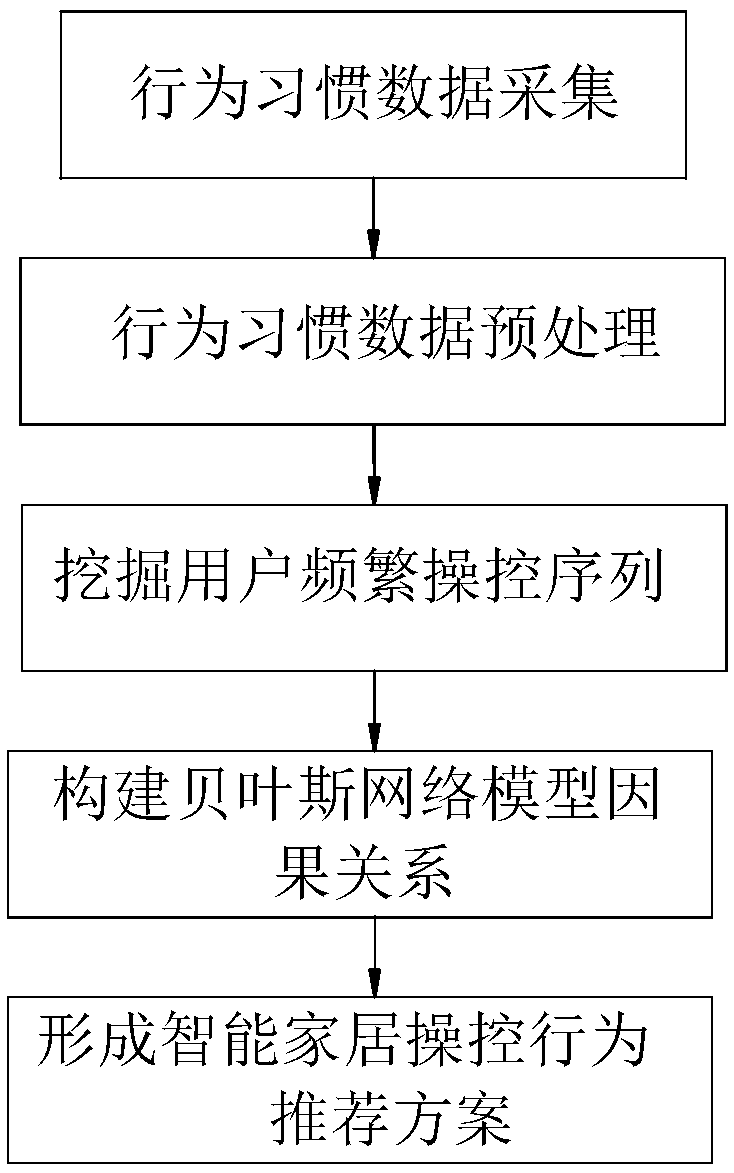
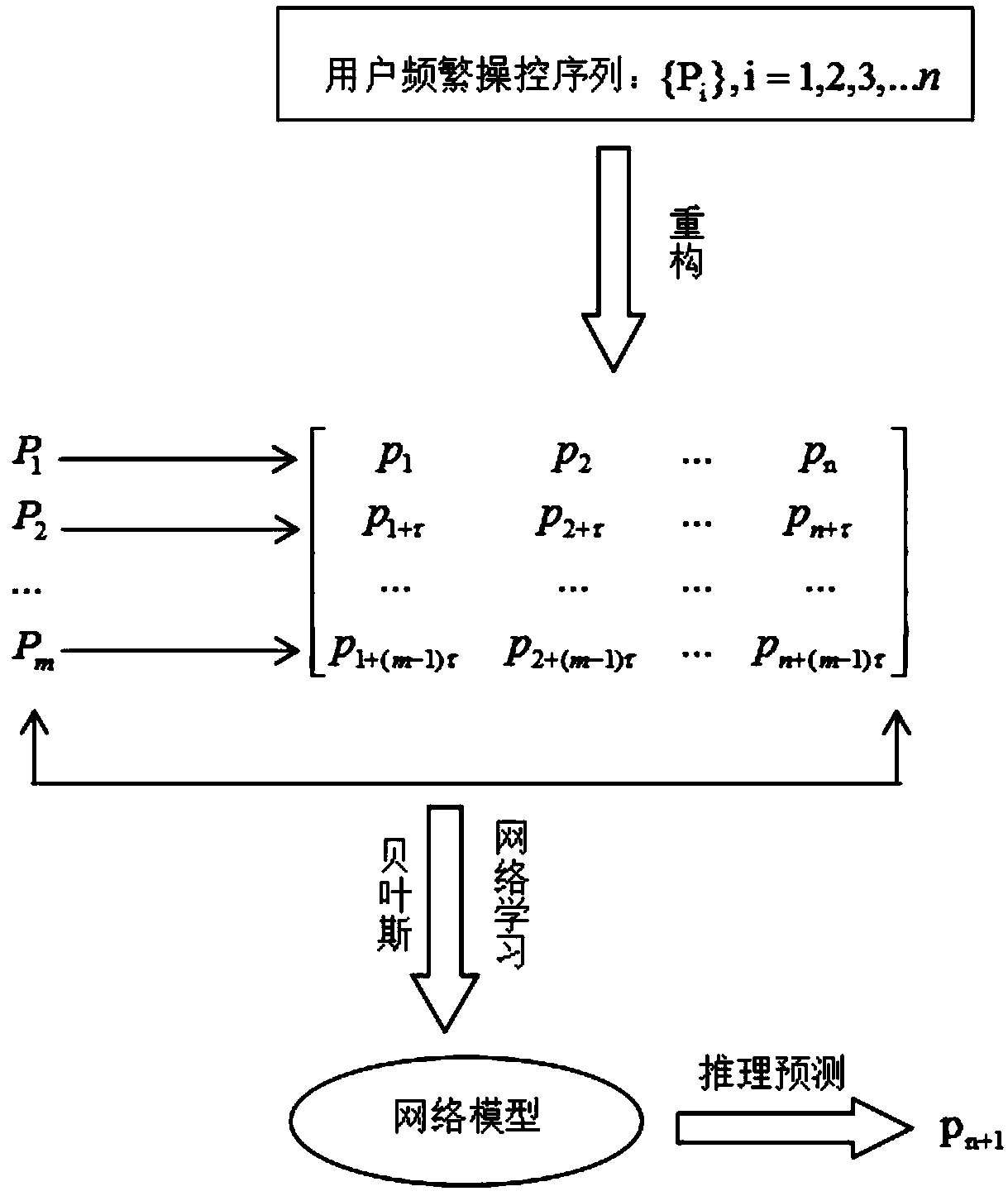
Smart home user manipulation behavior recommendation method based on temporal causality analysis
ActiveCN109542944AReduce noiseEnhancing strong temporal correlationDigital data information retrievalCharacter and pattern recognitionComputation complexityData set
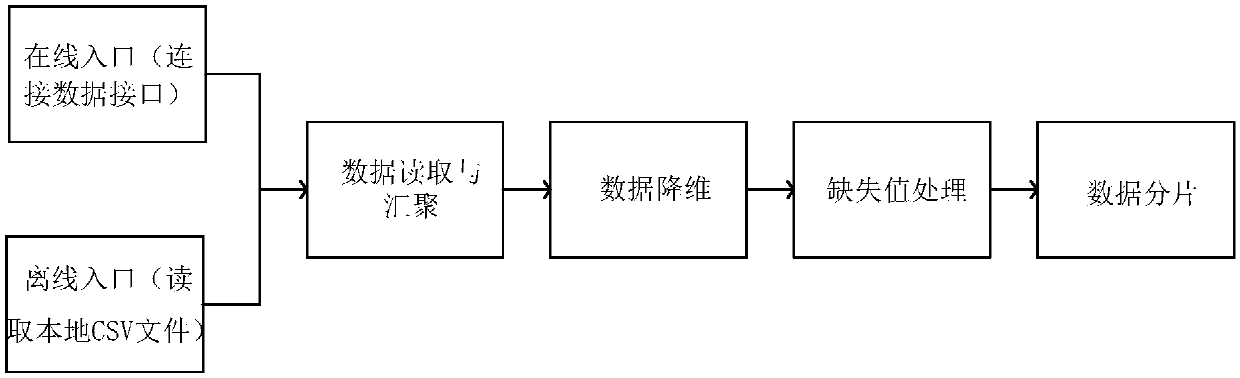
The invention relates to a smart home user manipulation behavior recommendation methodbased on temporal causality analysis. A large number of user behavior habit data are segmented, and then the sequence of frequent user operations is extracted from the data by a sequential pattern mining algorithm. Based on the sequence of frequent user operations, the causal relationship between the mining sequences of Bayesian network is constructed, so as to construct the process of intelligent home manipulation behavior recommendation scheme. The invention combines the advantages of a pattern mining algorithm and a Bayesian model, reduces the entire data set to a selected set of frequently manipulated sequences through pattern mining, greatly reduces the computational complexity and the noise in the causal relationship computation, which is conducive to more efficient formation of a more user-friendly smart home manipulation behavior recommendation scheme, and at the same time enhances the strongtime correlation between each device of the smart home manipulation behavior recommendation scheme, and fills in the shortcomings of the traditional algorithm.
Owner:GUANGDONG UNIV OF TECH
Software-action description, fetching and controlling method with virtual address space characteristic
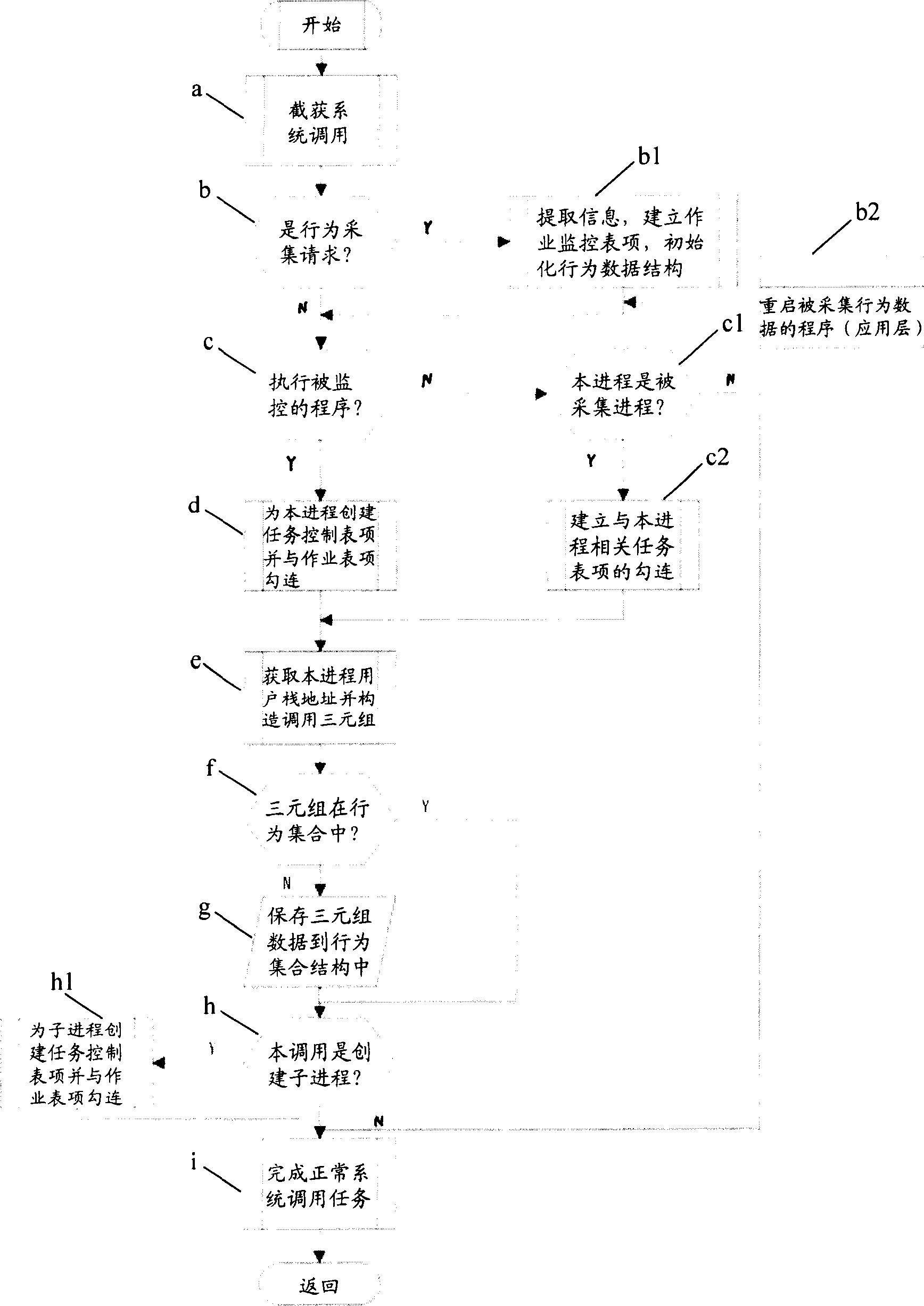
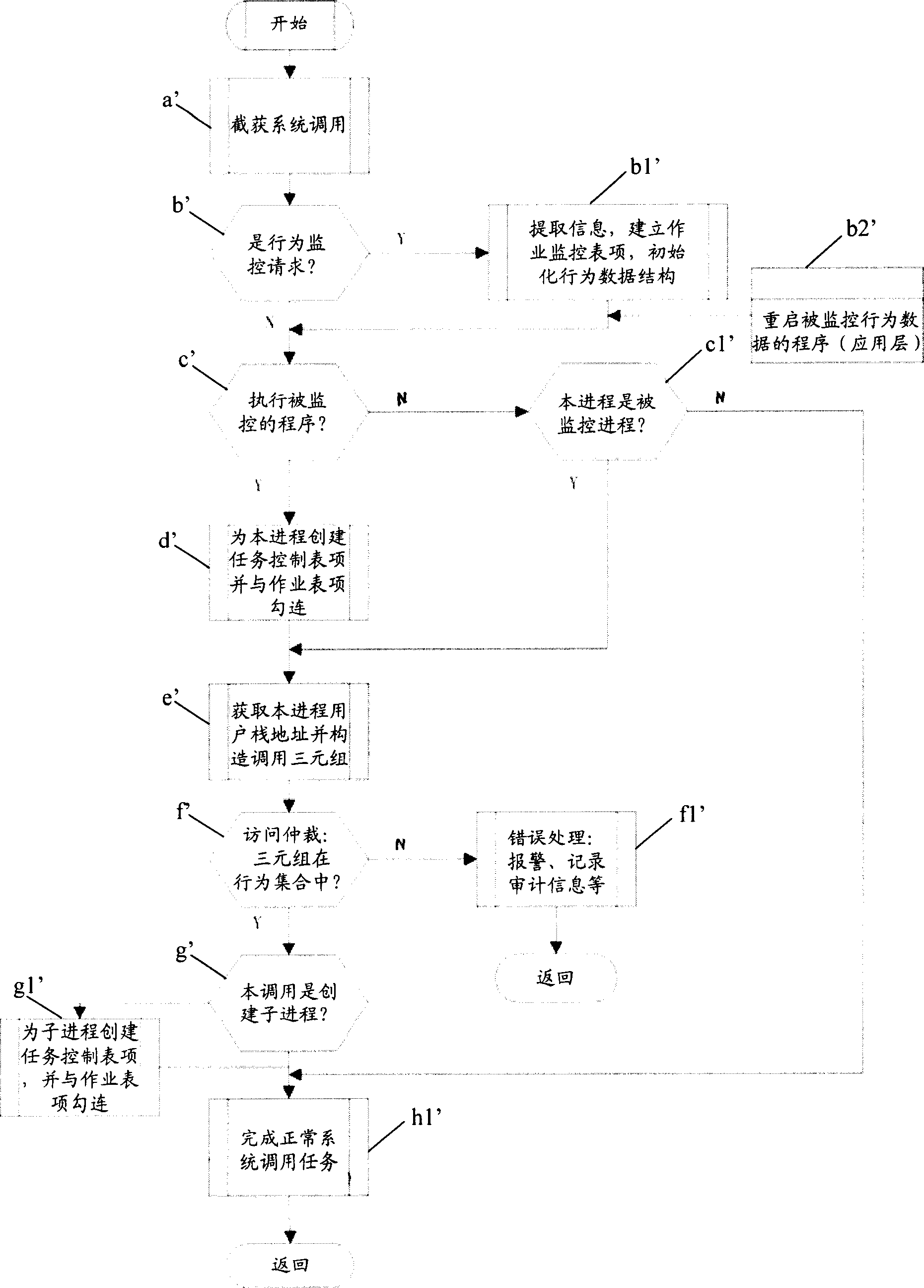
ActiveCN1892615AEasy to detectEasy to controlSoftware testing/debuggingPlatform integrity maintainanceSerial patternVirtual space
Said invention discloses software behavioural abnormality detection and protecting means. It contains obtaining one software behaviour and address attribute and establishing characteristic of correspondence data integration; using said established characteristic data integration detecting and protection software abnormal behavior, wherein characteristic data integration having virtual space address attribute. Said invented method can restrict software behaviour track without error, capable of raising detecting accuracy, greatly raising identifying efficiency and convenient execution. It can independently use and conjunctively use with other data, for example short sequence, status attribute, and resource attribute. Said invention can realize real time detecting with controlling to application program behaviour, capable of being used in main unit information system safety protection and network information system invasion protection etc field.
Owner:上海浦东软件园信息技术股份有限公司
Apparatus and method for detecting sequential pattern
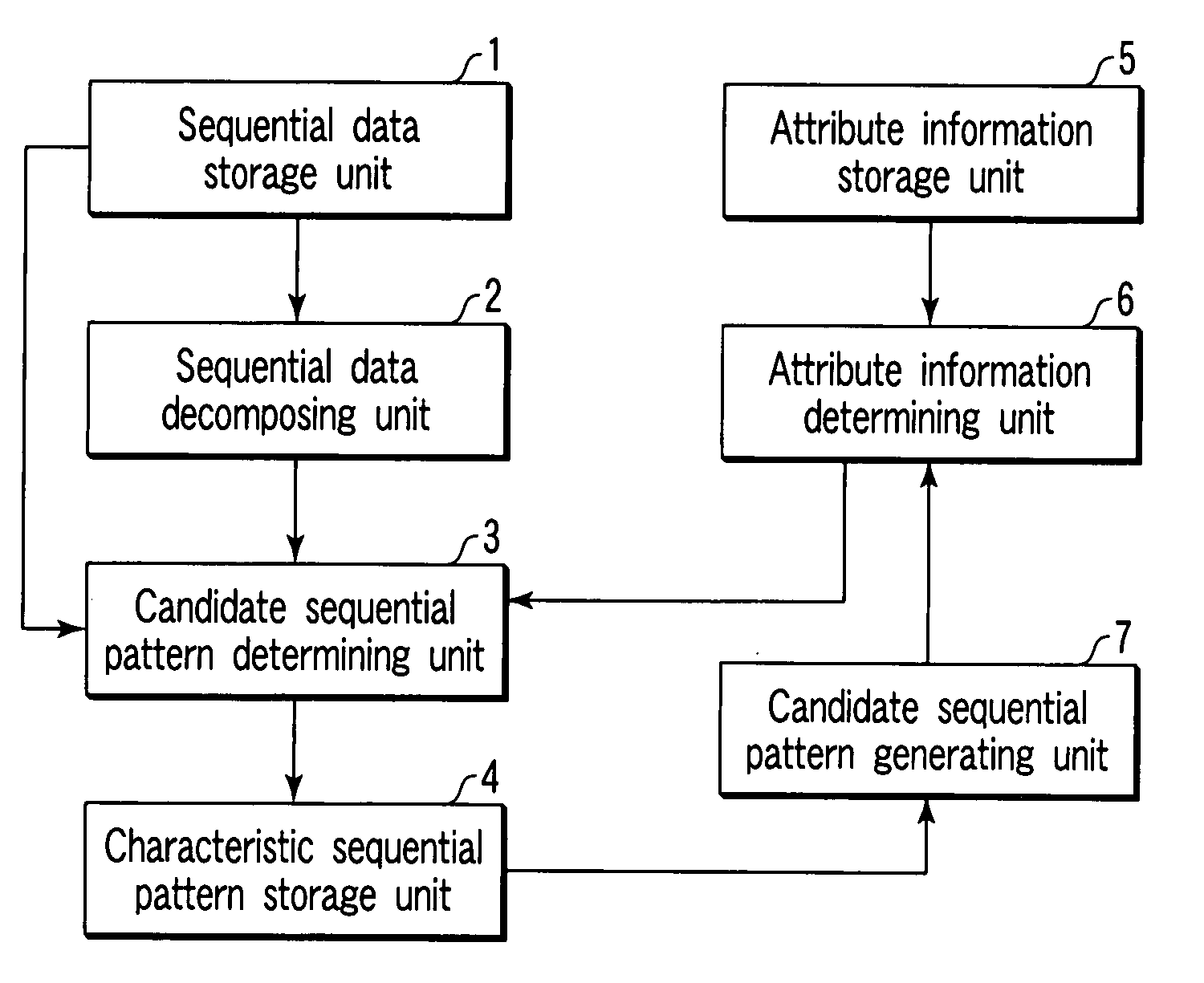
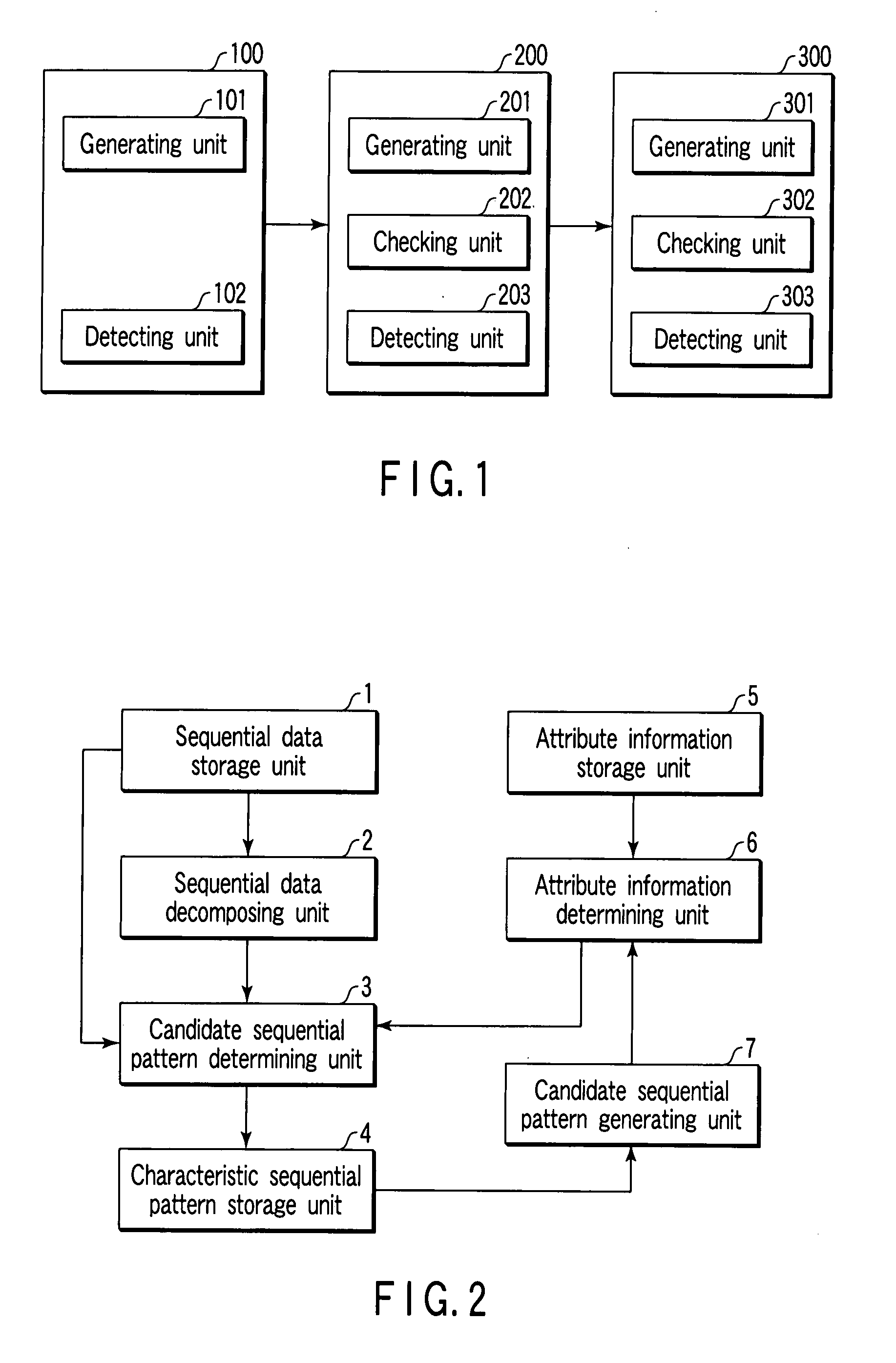
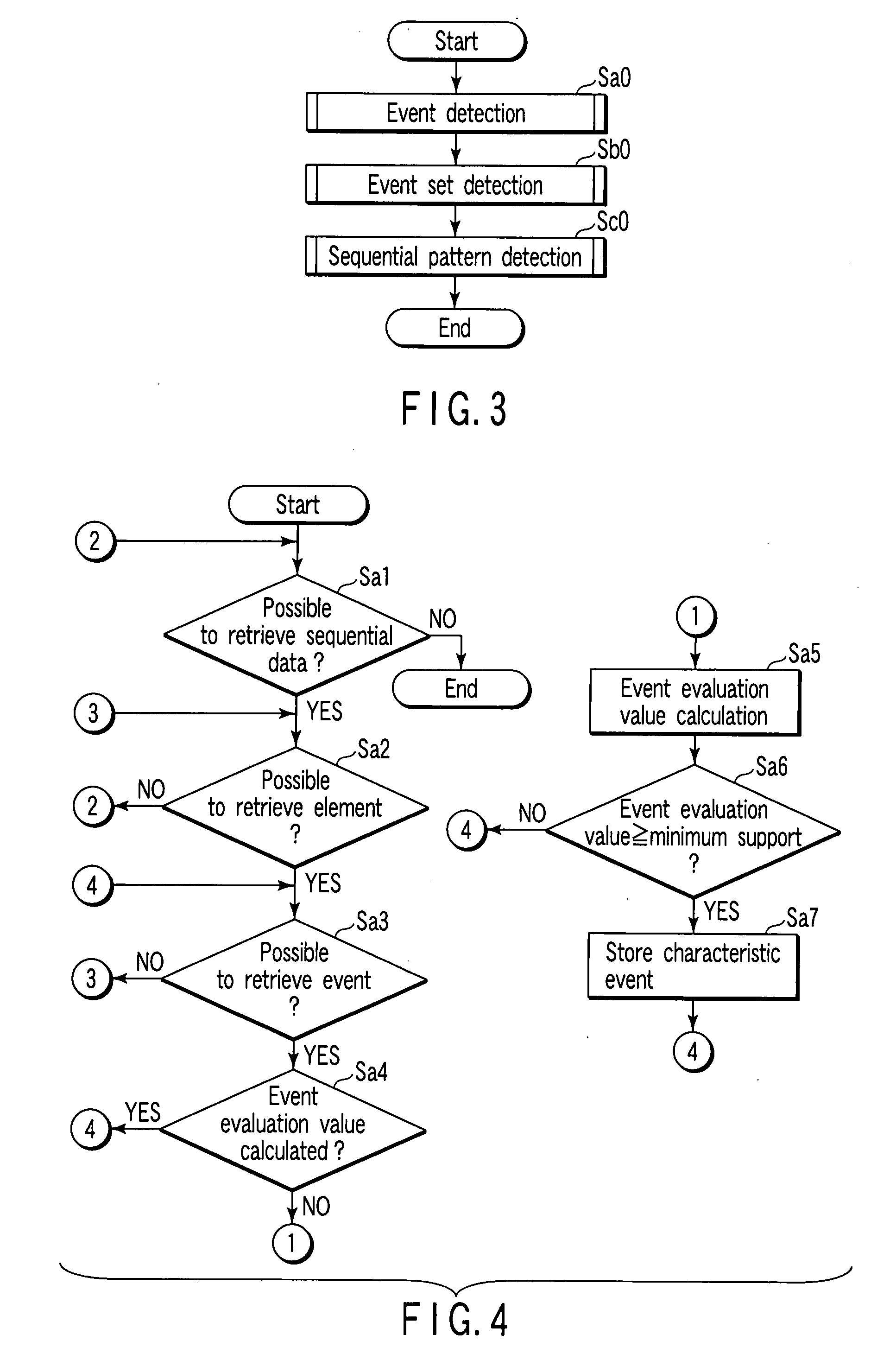
InactiveUS20080033895A1Data processing applicationsDigital data information retrievalSerial patternPattern detection
A sequential pattern detecting apparatus includes a first combining unit configured to combine a plurality of characteristic event sets detected from sequential data containing elements which comprise a plurality of events and which are arranged in sequential order, to generate a characteristic primary sequential pattern with a sequence size of “1”, a second combining unit configured to combine a plurality of characteristic ith-length (i=1, 2, . . . ) sequential patterns with a sequence size of “i” to generate a candidate (i+1)th-length sequential pattern, a checking unit configured to check validity of the candidate (i+1)th-length sequential pattern on the basis of the attributes to detect valid (i+1)th-length sequential patterns, and a detecting unit configured to detect a characteristic (i+1)th-length sequential pattern from the valid (i+1)th-length sequential patterns with reference to the sequential data.
Owner:KK TOSHIBA
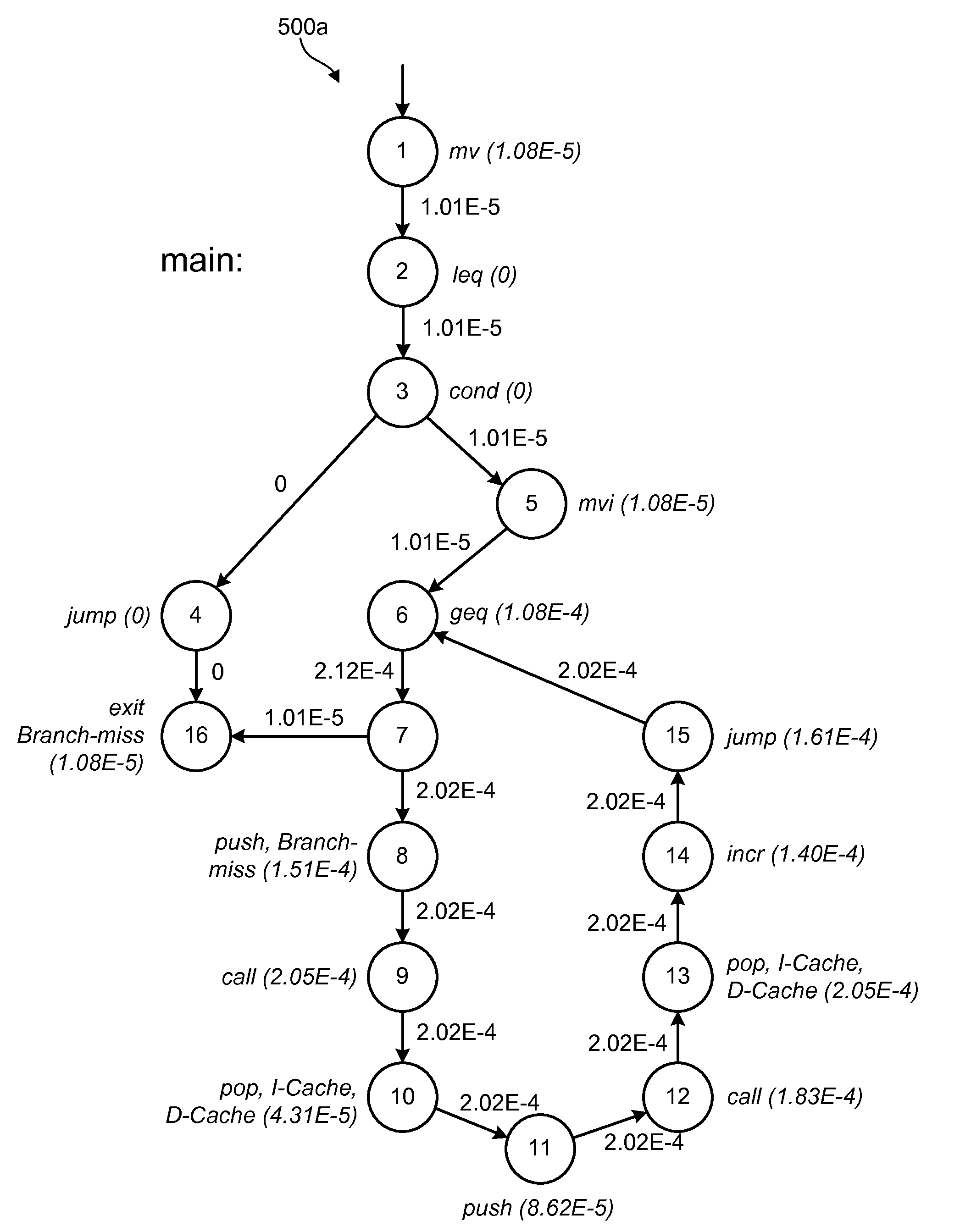
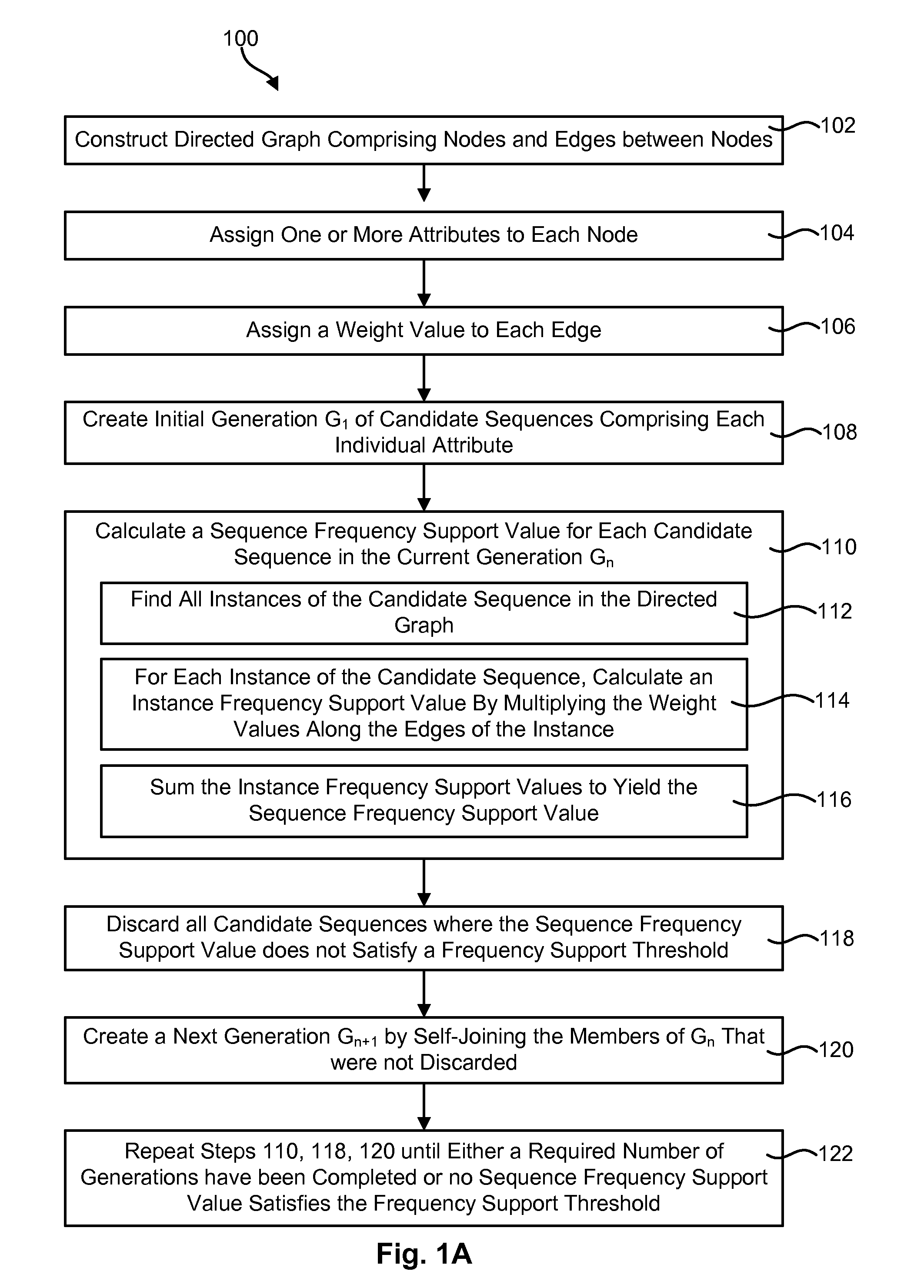
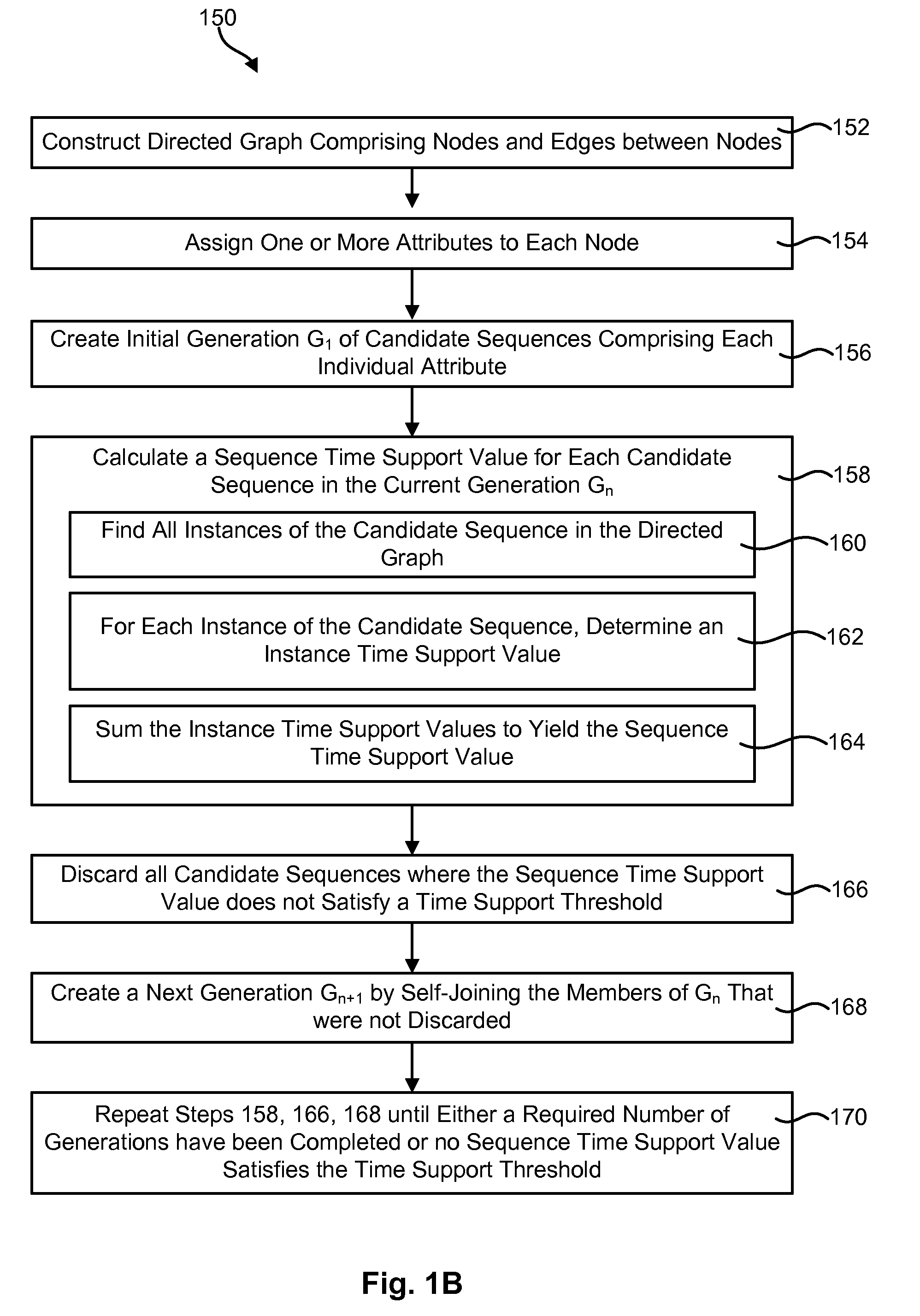
Mining sequential patterns in weighted directed graphs
InactiveUS20120197854A1Digital data processing detailsError detection/correctionDirected graphSerial pattern
A method for finding sequential patterns of attributes in a directed graph includes constructing a directed graph comprising multiple nodes and edges between the nodes. Each of the nodes may be assigned one or more attributes. Similarly, each of the edges may be assigned a weight value which may indicate the probably the edge will be traversed during traversal of the directed graph. The method may further include finding sequences of attributes in the directed graph that have some minimum amount of frequency and / or time support. In performing this step, the frequency support of each individual instance of a sequence of attributes may be calculated by multiplying the weight values along the edge or edges of the instance. A corresponding apparatus and computer program product are also disclosed and claimed herein.
Owner:INT BUSINESS MASCH CORP
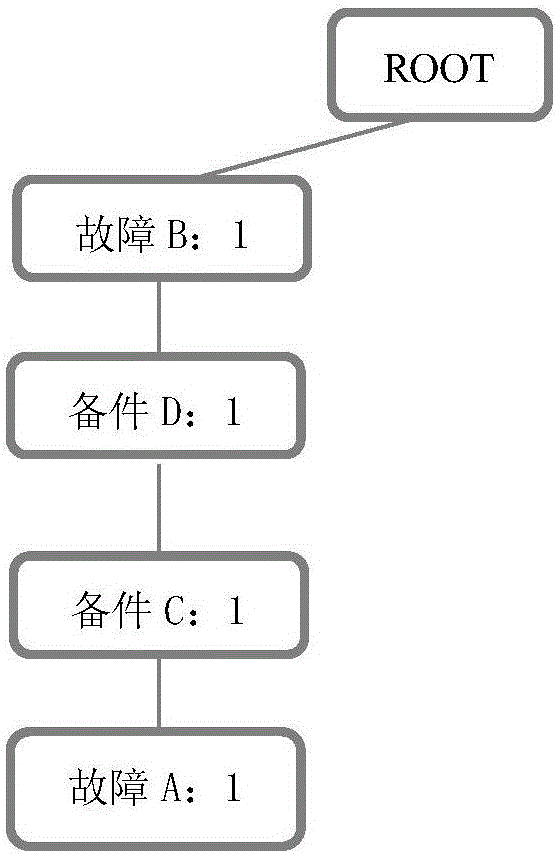
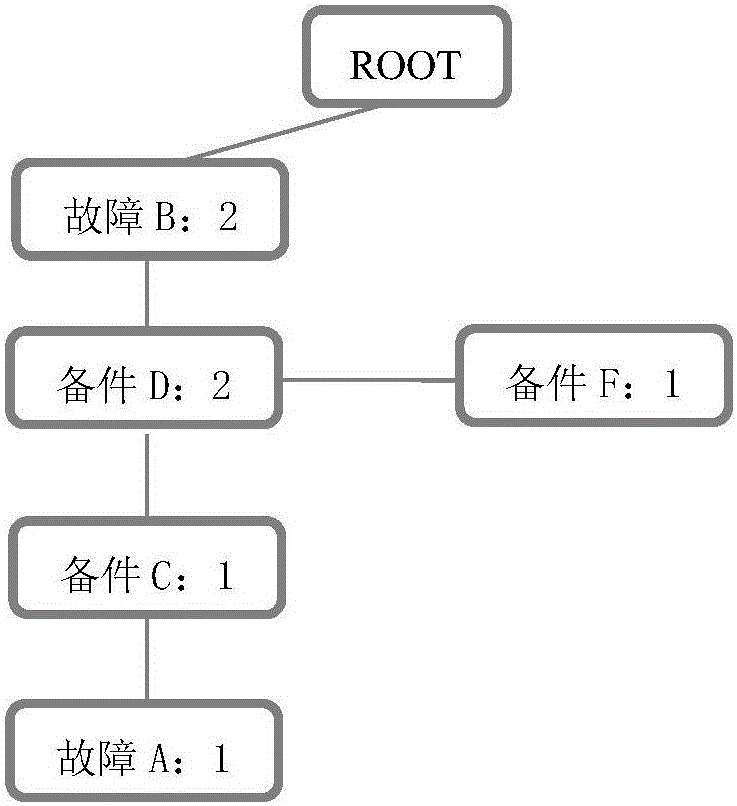
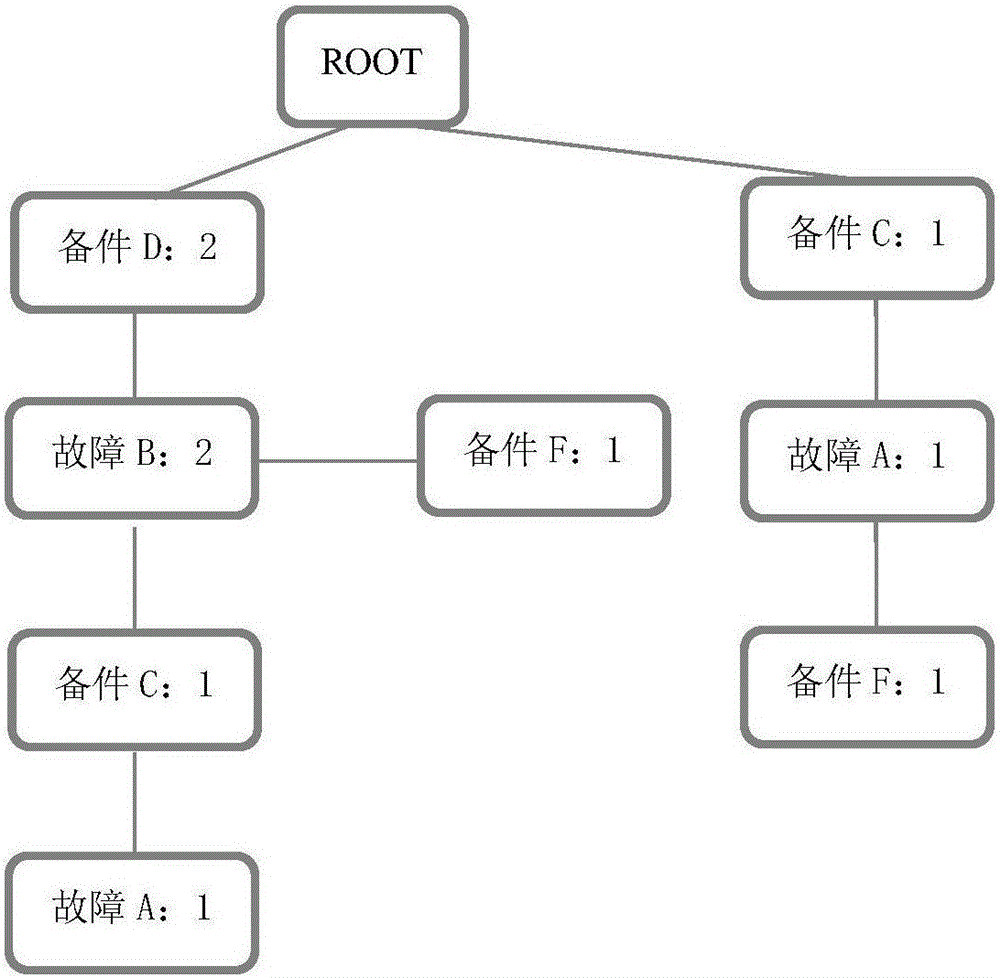
FP-Tree sequential pattern mining-based fault diagnosis and valuation platform
The invention discloses an FP-Tree sequential pattern mining-based fault diagnosis and valuation platform. The platform comprises a corresponding relationship module, a topologic search module and a solution module, wherein the corresponding relationship module creates a frequent item set of a corresponding relationship between a fault code and a replacement spare part through an FP-Tree algorithm according to a transactional database; the topologic search module performs a topologic search by utilizing a topologic relationship between the position of the spare part and an ECU position where a fault is located, and selects the frequent item set; and the solution module obtains a complete solution of the spare part corresponding to the fault code and a repair item according to a corresponding relationship established by the spare part and the repair item. According to the diagnosis and valuation platform, the corresponding relationship is searched for through the frequent item set algorithm FP-Tree and the sequential pattern mining algorithm; the two algorithms are fused for use; the platform is suitable for the possibility of parallel solving of multiple faults in addition to a single fault; the spare part needed to be repaired and the item are judged by remotely estimating the fault code of the vehicle; the complete solution is provided; and a reference is provided for vehicle repair.
Owner:DALIAN ROILAND SCI & TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com