Front-background related auditing method and system for Web server
A front-end, back-end and server technology, applied in the field of information security, can solve problems such as the inability to detect the time series relationship of database access events, the inability to identify the relationship, etc., to achieve the effect of accurate and real relationship and improve accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
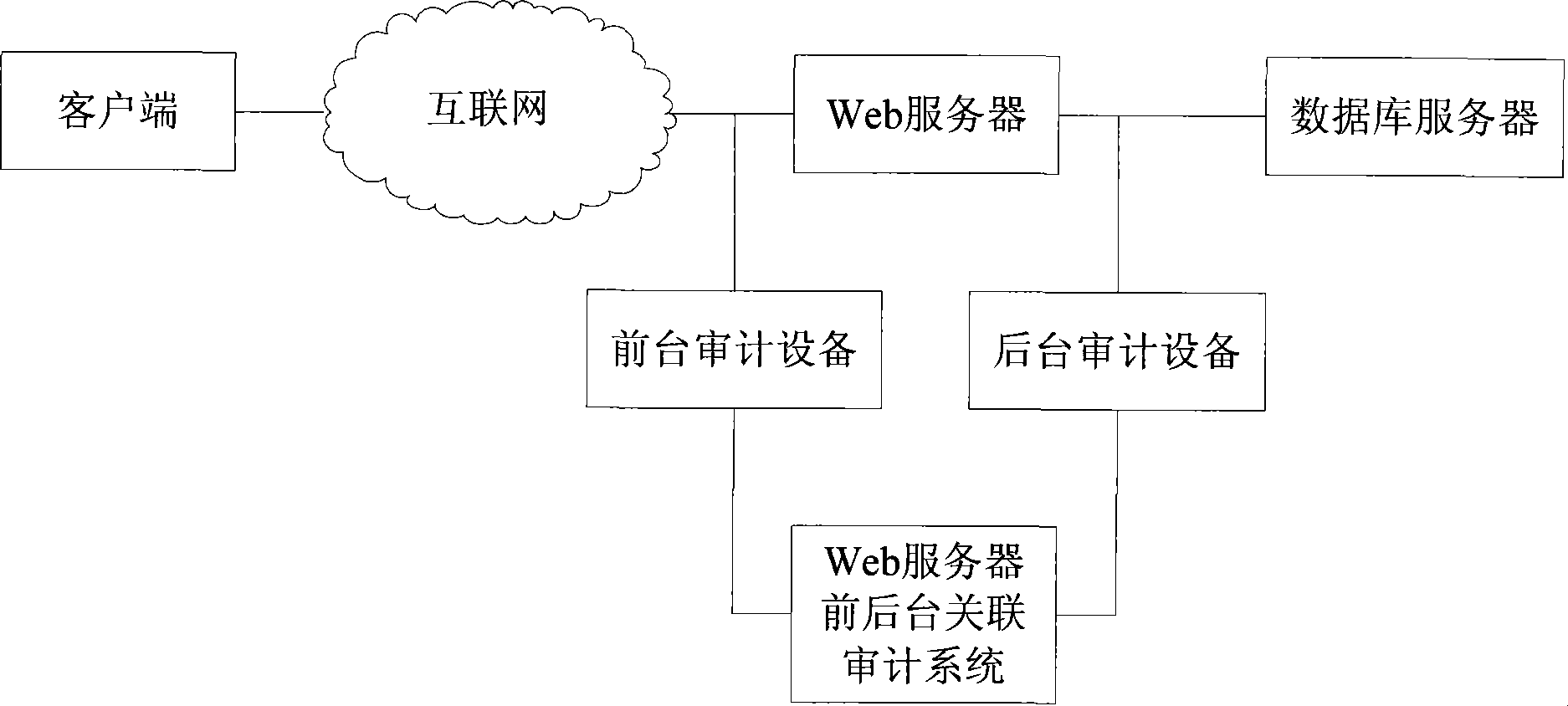
[0043] This embodiment is the deployment mode of the Web server front and back related audit system, such as figure 1 shown. In the figure, the foreground audit device observes the http access events from the client to the Web server, and the background audit device observes the database access events from the Web server to the database server, and both of them send the observed access events to the front-end and back-end associated audit systems of the Web server .
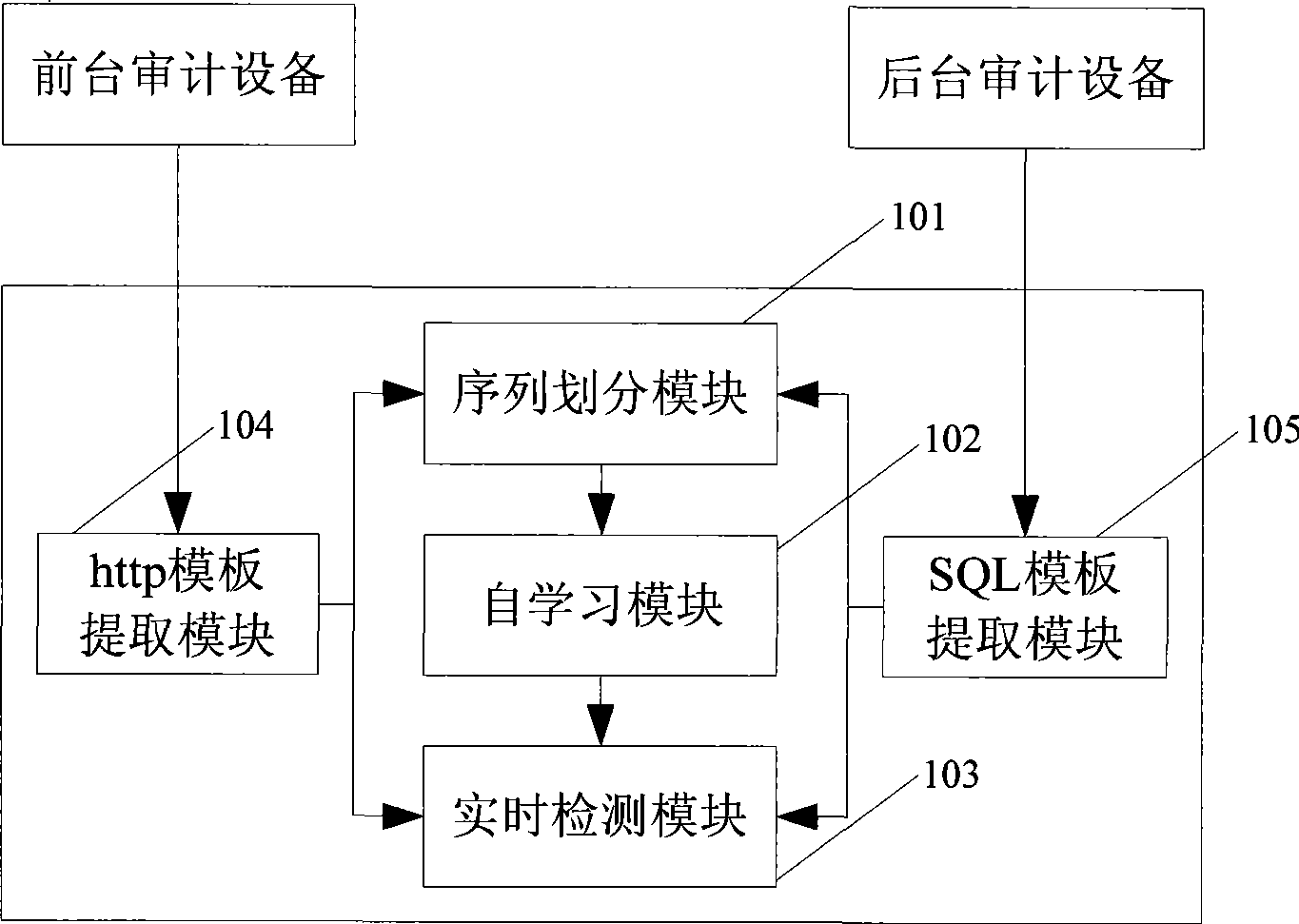
[0044] figure 2It is a schematic diagram of the structure of the front-end and back-end associated audit system of the Web server, and the connection relationship between the modules of the system is as follows:
[0045] The sequence division module 101 collects the output of the http template extraction module 104 and the SQL template extraction module 105, and according to the time window constraint and the matching constraint, a database access event triggered by an http access event is divided into the sam...
Embodiment 2
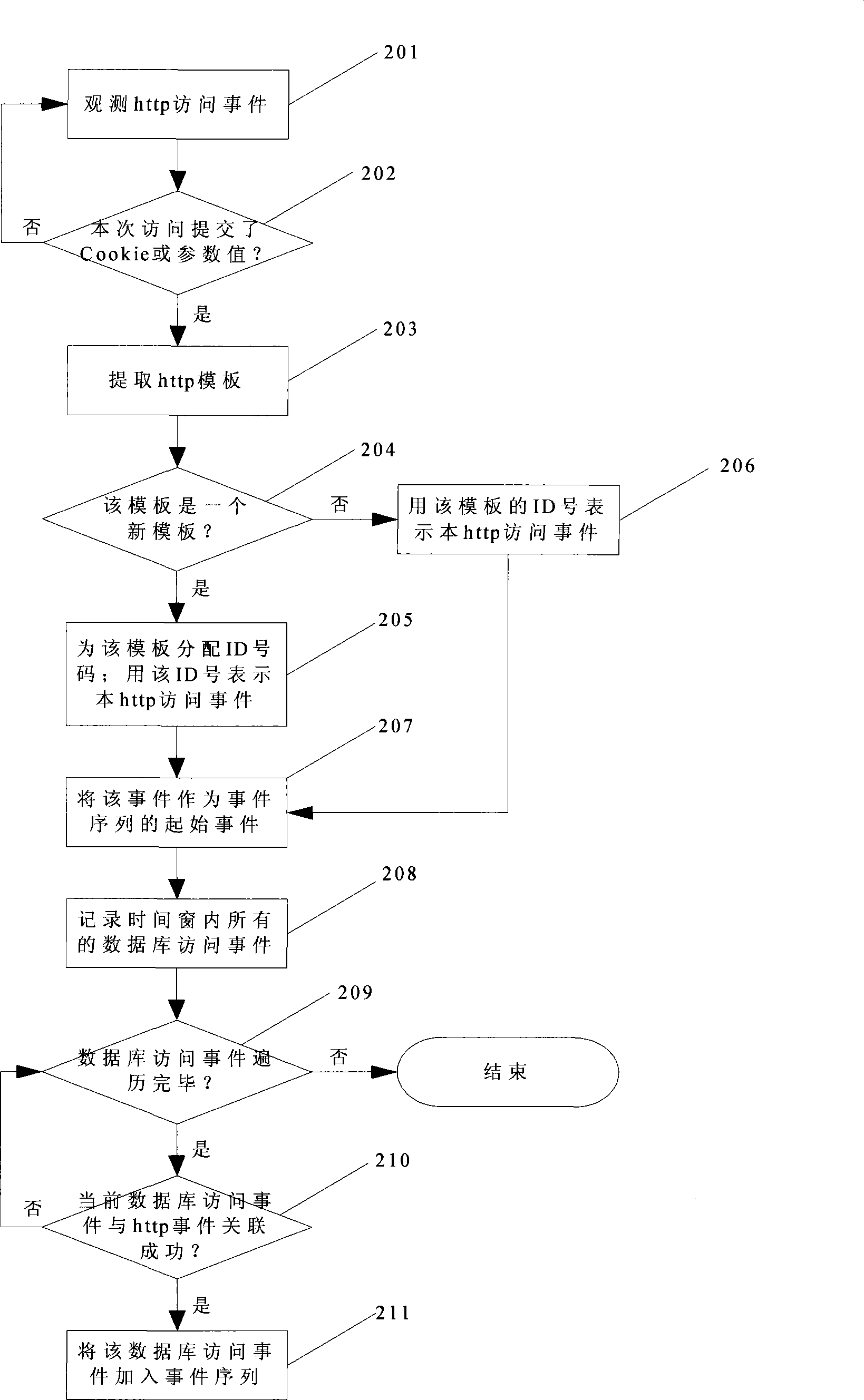
[0049] In this embodiment, the sequence is divided into stages, such as figure 2 shown, including the following steps:
[0050] Step 201: observe the http access event at the foreground;
[0051] Step 202: judge whether this visit has submitted cookies value or parameter value, if submitted, go to step 203, otherwise go to step 201;
[0052] Step 203: extract the http template from the http access event;
[0053] Step 204: Determine whether the template is a new template. If it is a new template, go to step 205, otherwise go to step 206;
[0054] Step 205: assign an ID number mark for the new template, and represent the http access event with the mark;
[0055] Step 206: represent the http access event with the ID number of the template;
[0056] Step 207: generate a new event sequence, use the http access event as the initial event of the event sequence;
[0057] Step 208: according to the time window of setting, observe from the time of foreground http access event, a...
Embodiment 3
[0062] This embodiment is an association process between a database access event and an http access event, such as image 3 shown, including the following steps:
[0063] Step 301: extract SQL template and parameter value from database access event;
[0064] Step 302: Determine whether the SQL template is a new template. If yes, go to step 303, otherwise go to step 304.
[0065] Step 303: assign an ID number mark for the new template, and use the mark to represent the database access event;
[0066] Step 304: then the ID number of this template represents this database access event;
[0067] Step 305: compare the parameter value in the database access event with the parameter value in the http access event. If the degree of matching between the two exceeds the preset threshold, the association is successful; otherwise, go to step 306 . The calculation method of the matching degree is as follows: assuming that the database access event contains n parameter values, m of whi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com