Patents
Literature
825 results about "Event triggered" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A triggering event is a tangible or intangible barrier or occurrence which, once breached or met, causes another event to occur. Triggering events include job loss, retirement, or death and are typical for many types of contracts. These triggers help to prevent, or ensure, that in the case of a catastrophic change,...
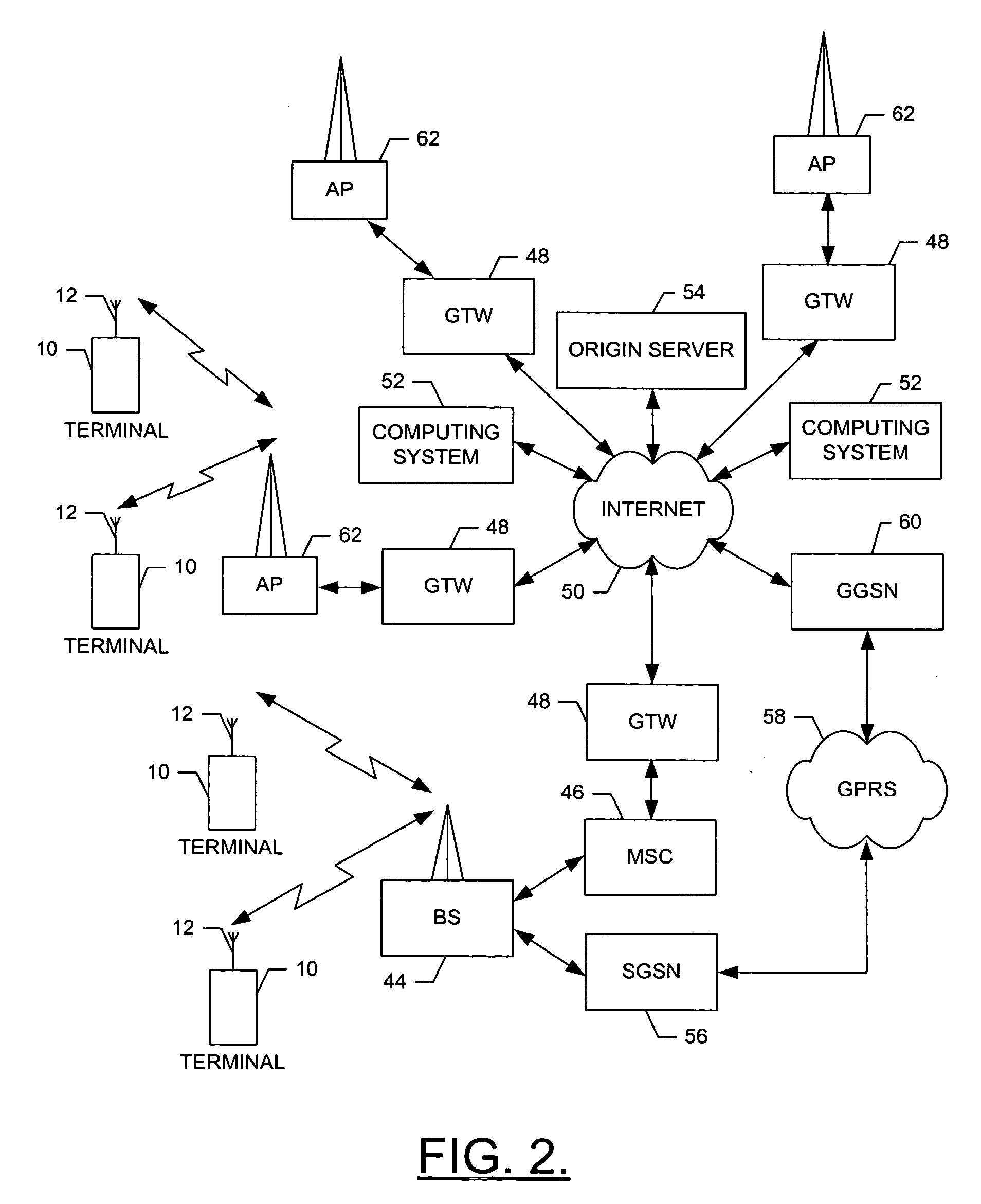
Billing system and method for micro-transactions
ActiveUS20060276171A1Metering/charging/biilling arrangementsFinanceEvent triggeredCustomer identification
Billing a customer through an intermediary billing system for a transaction by receiving, at the intermediary billing system, a transaction request associated with a transaction amount and a customer identification code, validating, in the intermediary billing system, the transaction request by determining whether the customer identification code corresponds to a customer that is registered with the intermediary billing system, and sending, in the case that the transaction request is valid, a billing event trigger associated with the customer identification code to an external billing mechanism, the billing event trigger representing the transaction amount.
Owner:SMS AC INC
Event-triggered data collection
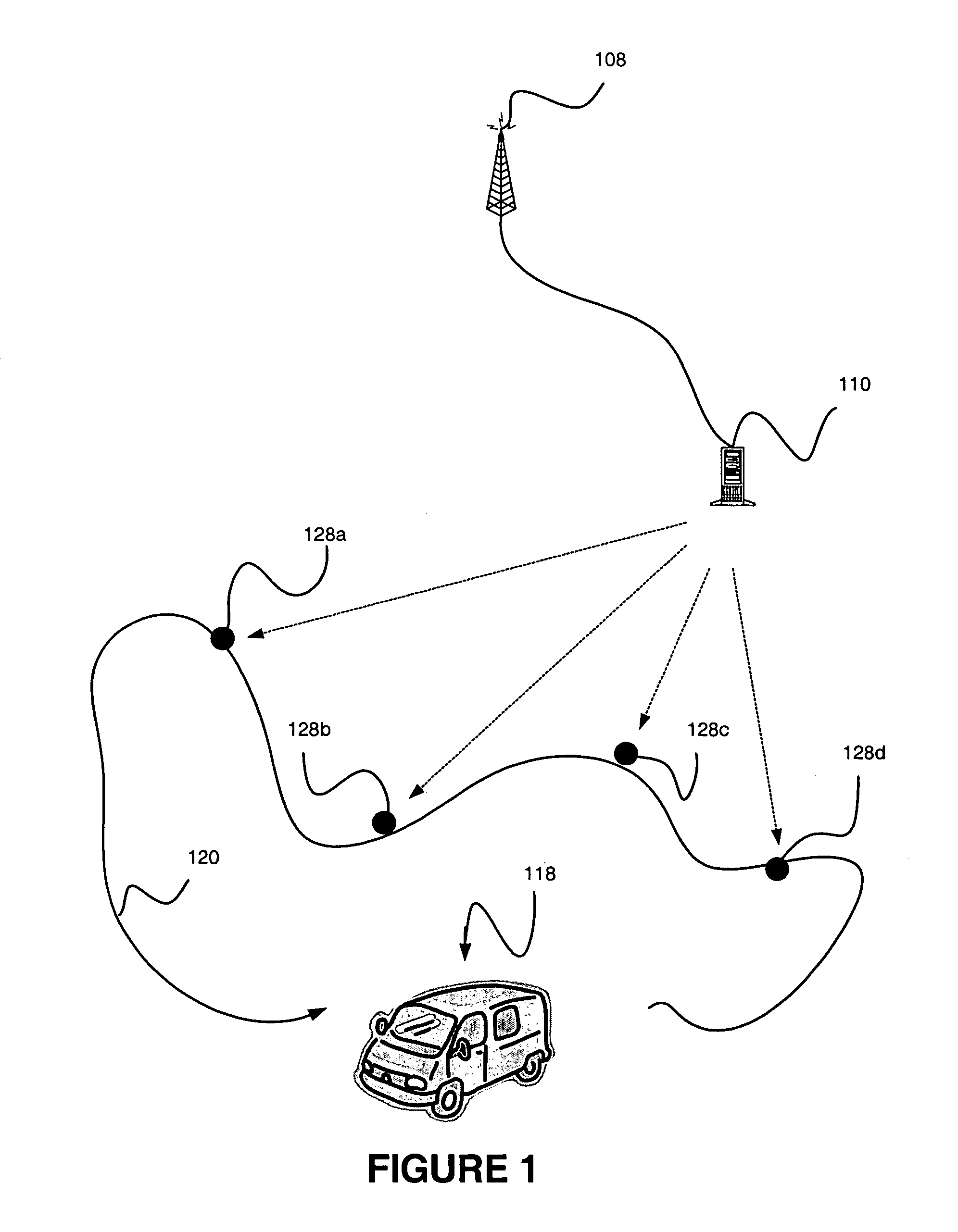
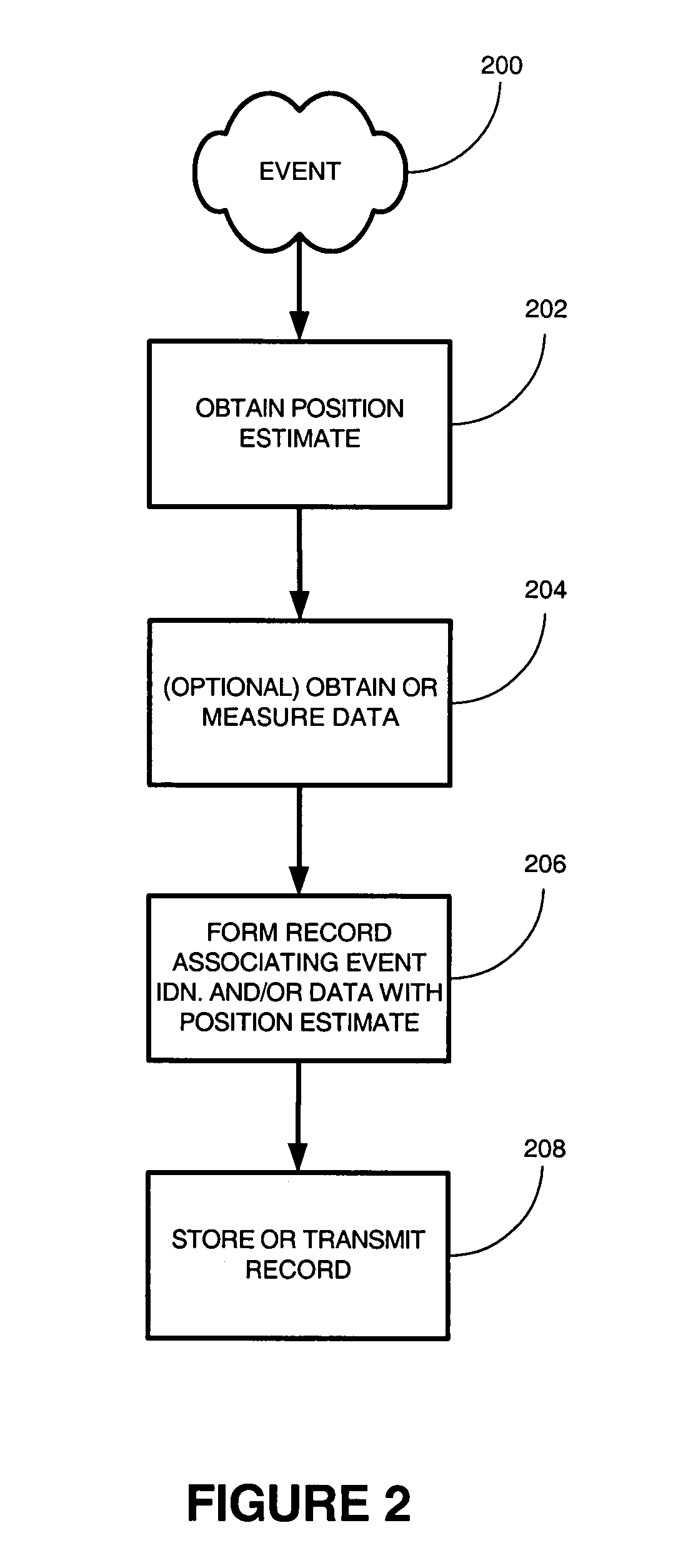
A method of obtaining data useful for one or more network applications is described. The method is performed responsive to a triggering event, such as a dropped call, a position fix, or even expiration of a timer. A position estimate for a subscriber station is obtained responsive to the event. A record is then formed associating the position estimate for the subscriber station with an identifier of the triggering event and / or data measured or obtained responsive to the event, such as the strength of one or more pilots visible to the subscriber station. The record is either stored locally or transmitted to a remote location. In one implementation, the record is transmitted to a remote location, and stored in a database holding like records relating to other subscriber stations.
Owner:QUALCOMM INC
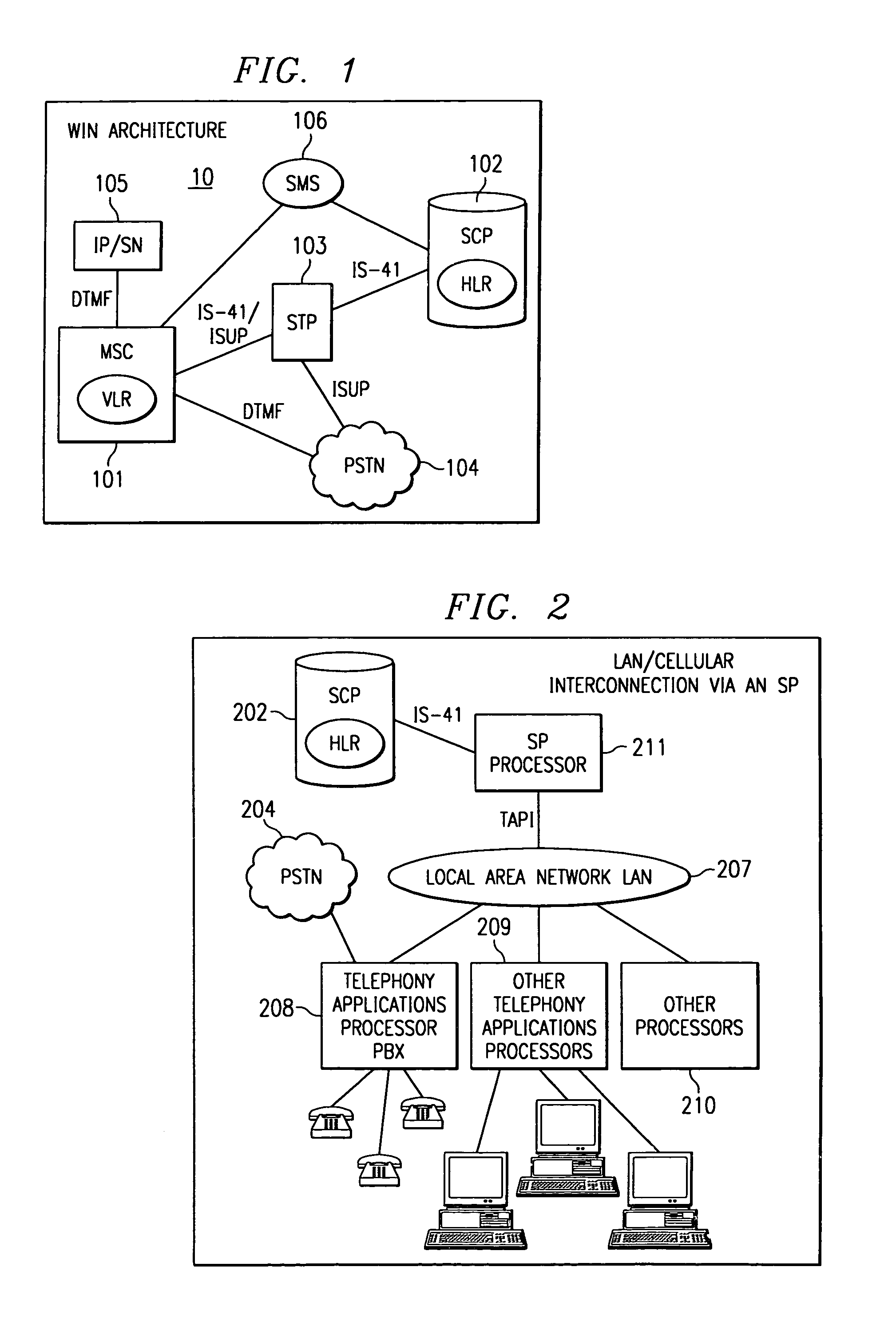
Mobility extended telephone application programming interface and method of use
InactiveUS7359720B2Low implementation costChange is minimalIntelligent networksInterconnection arrangementsApplication programming interfaceProcessor register
A system and method of for exchanging information between a wireless network and an external system is disclosed. The wireless network detects trigger events related to communications with wireless subscribers. Certain event triggers cause the wireless system to create a message to send to the external system. In response the external system may send information to the wireless system. The wireless system may create messages upon detection of handoff, origination, status, registration or other activity by the wireless subscriber. The invention may also detect trigger events related one mass media broadcasts. An interface translates between the different protocols of the wireless and the external or wireline networks to allow for automatic call redirection. The application can be utilized between many networks and facilitates the utilization of the architecture of a wirelined network and the home location register of the wireless network for various applications on the wireless network.
Owner:UNWIRED PLANET
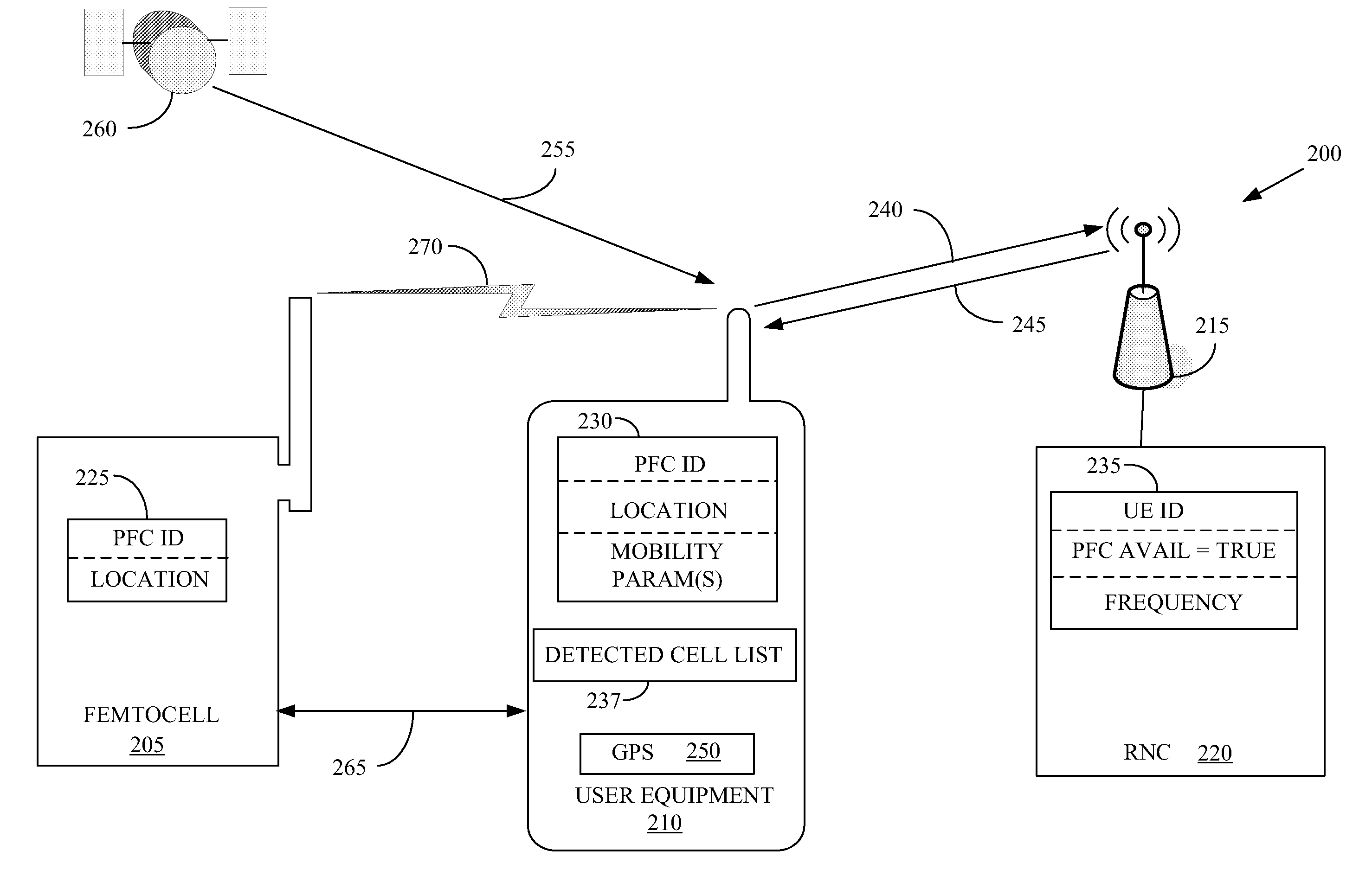
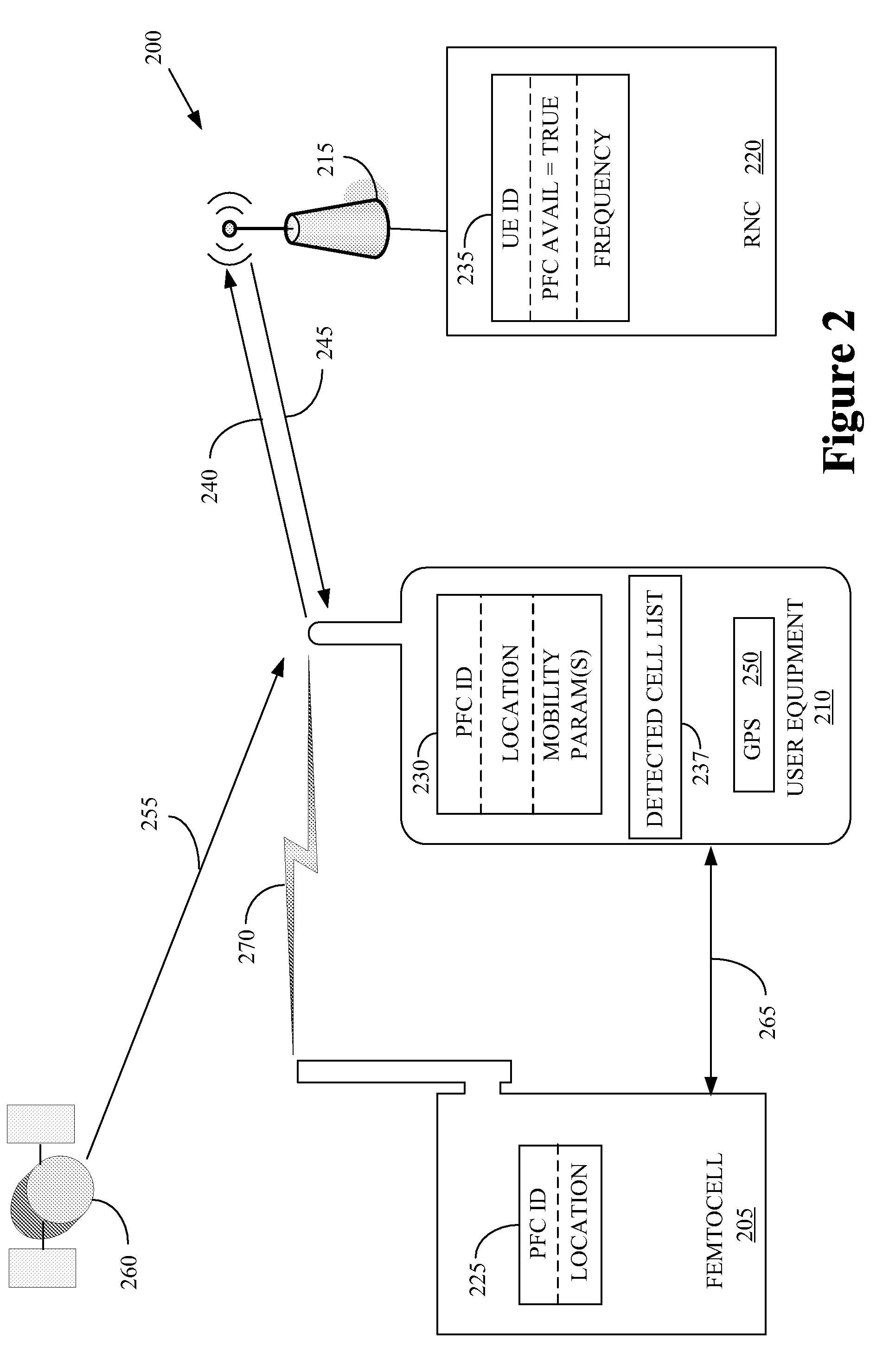
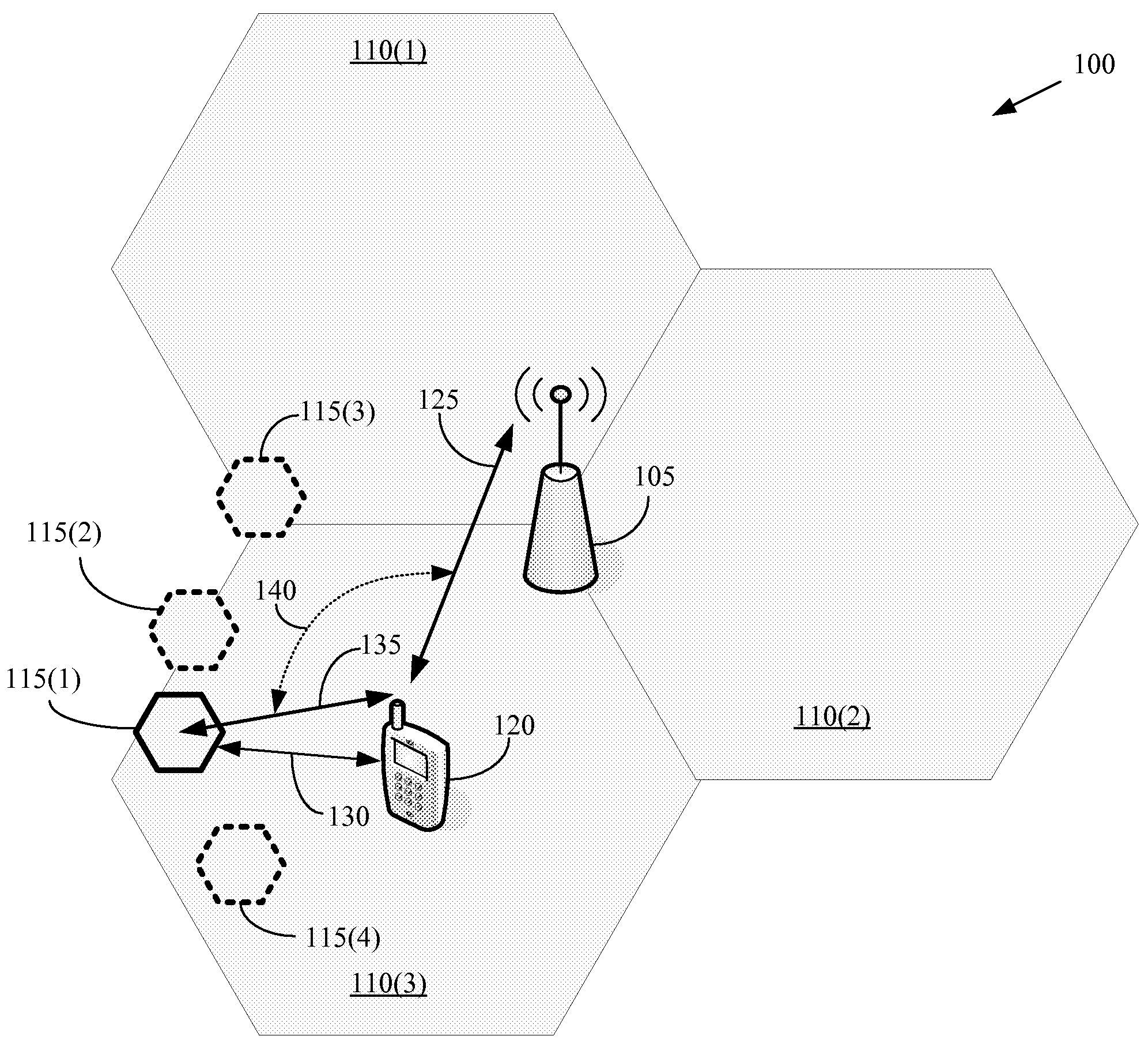
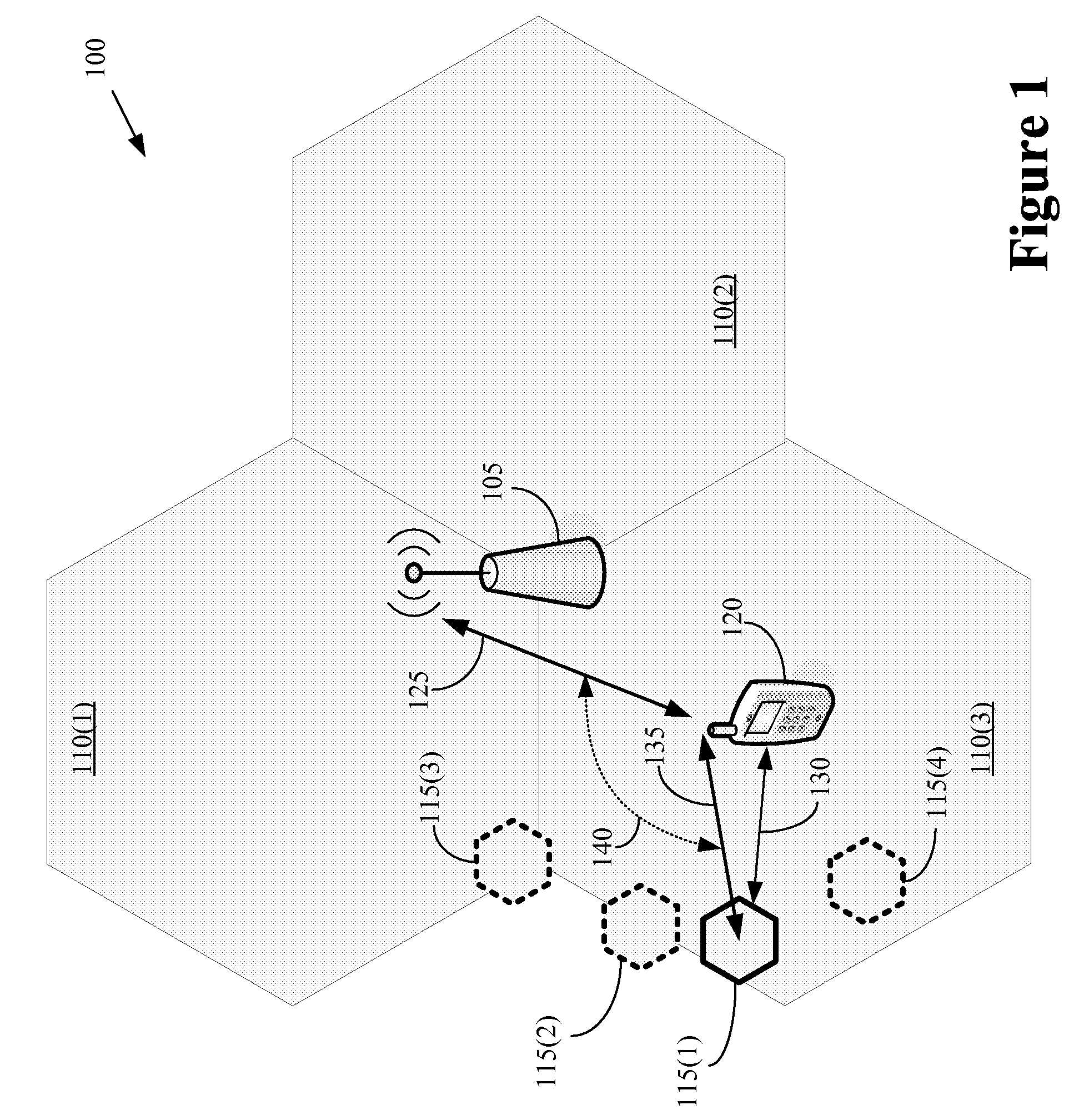
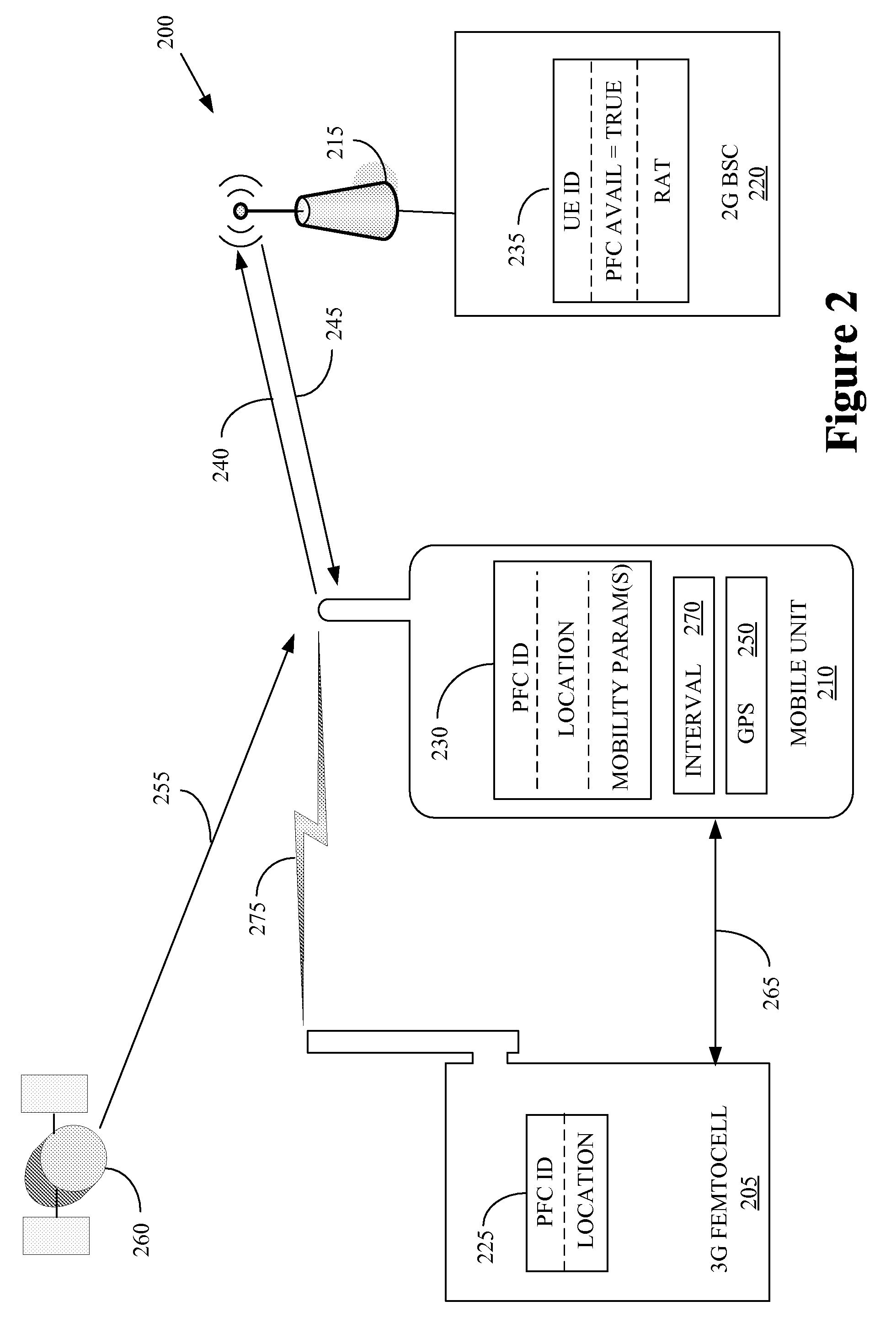
Location-based handovers from a macrocell to a femtocell using event-triggered measurement reporting
The present invention provides a method for implementation in user equipment that is configured to communicate with a wireless communication system that comprises one or more macro-cells and one or more femtocells. The method includes comparing, at the user equipment, a location of the user equipment and a location of one or more femtocells. The method also includes transmitting, from the user equipment to the macrocell(s), a first measurement report, with a location-based event, when the comparison indicates that the user equipment is within a selected range of the femtocell(s).
Owner:ALCATEL LUCENT SAS
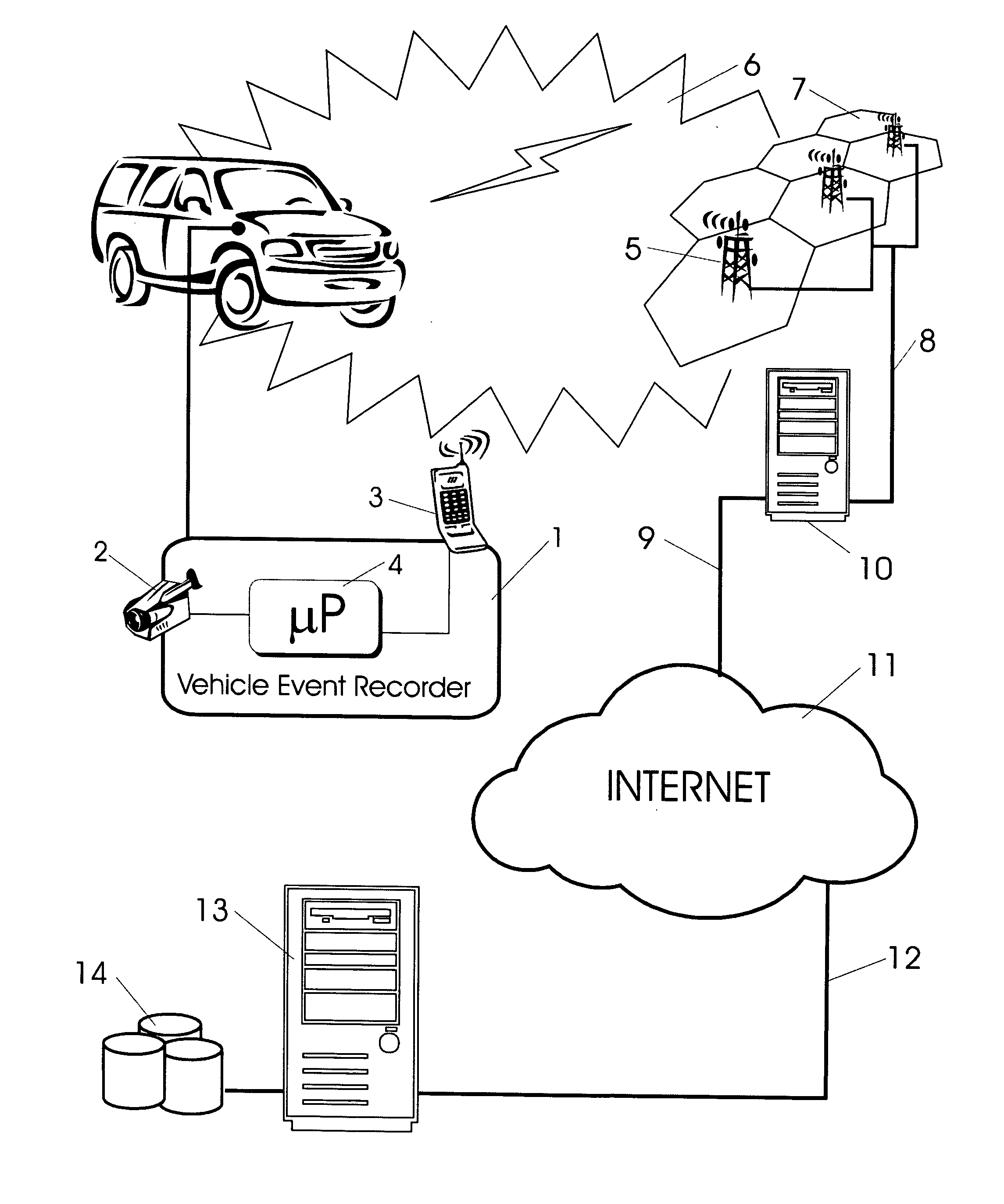
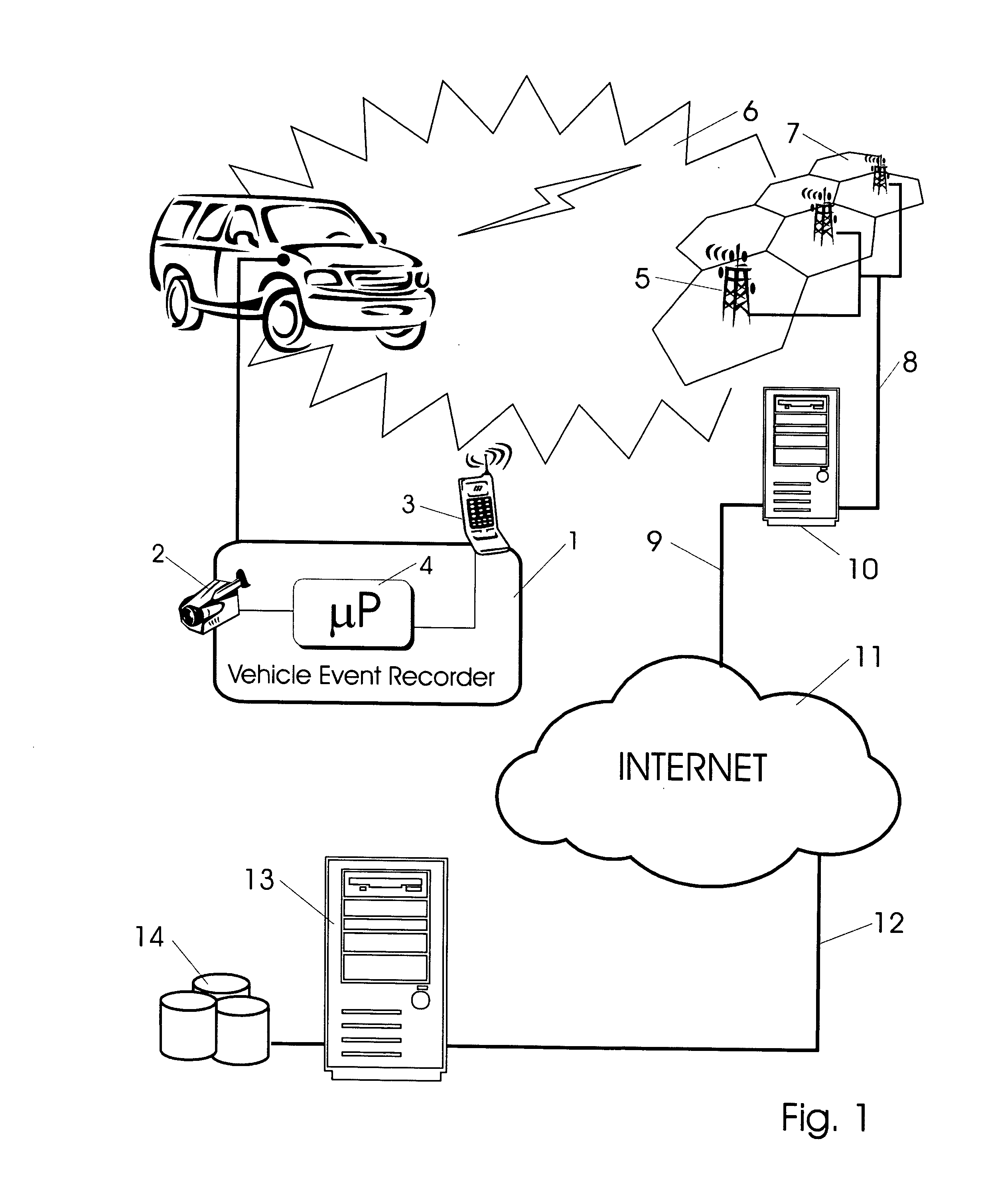
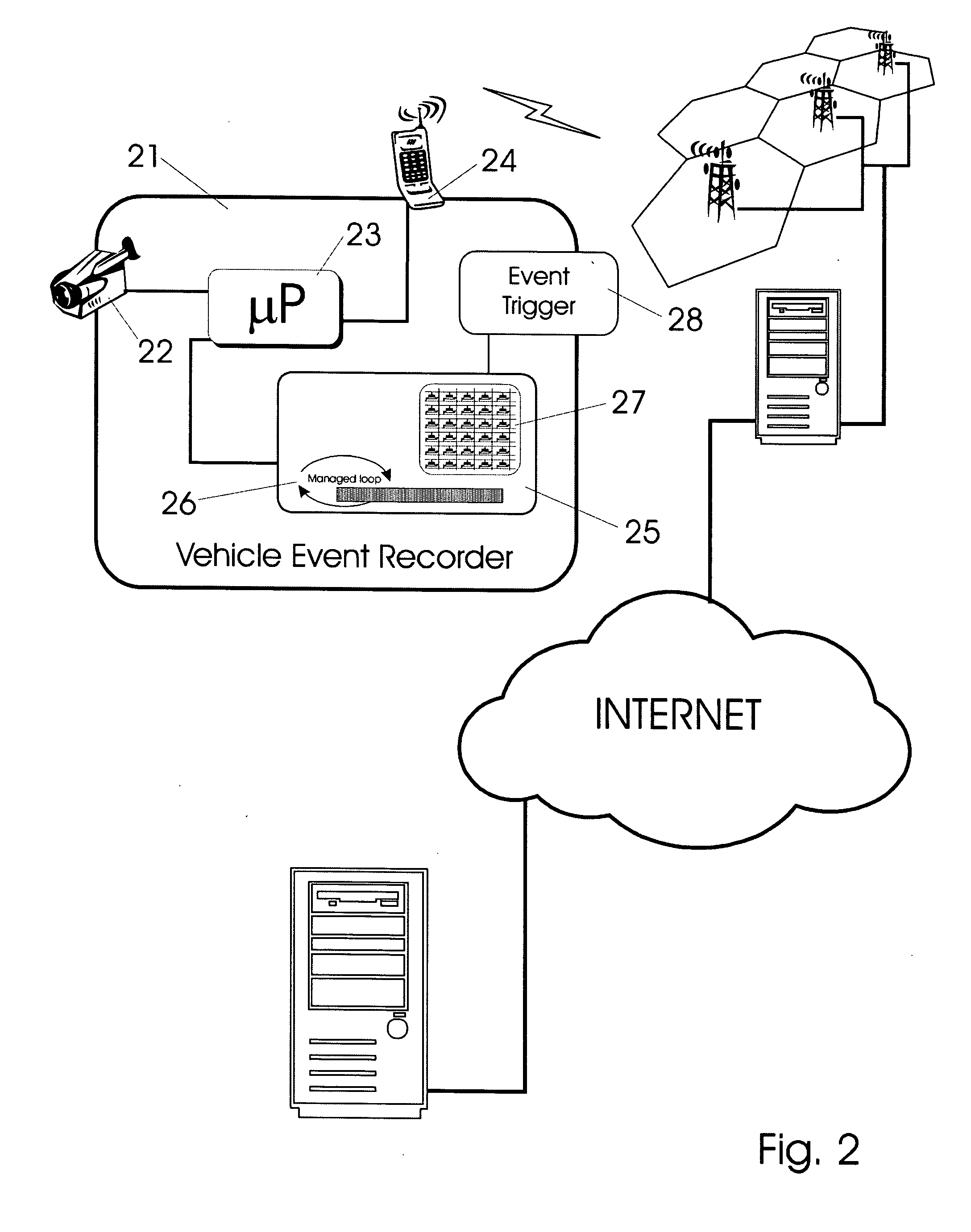
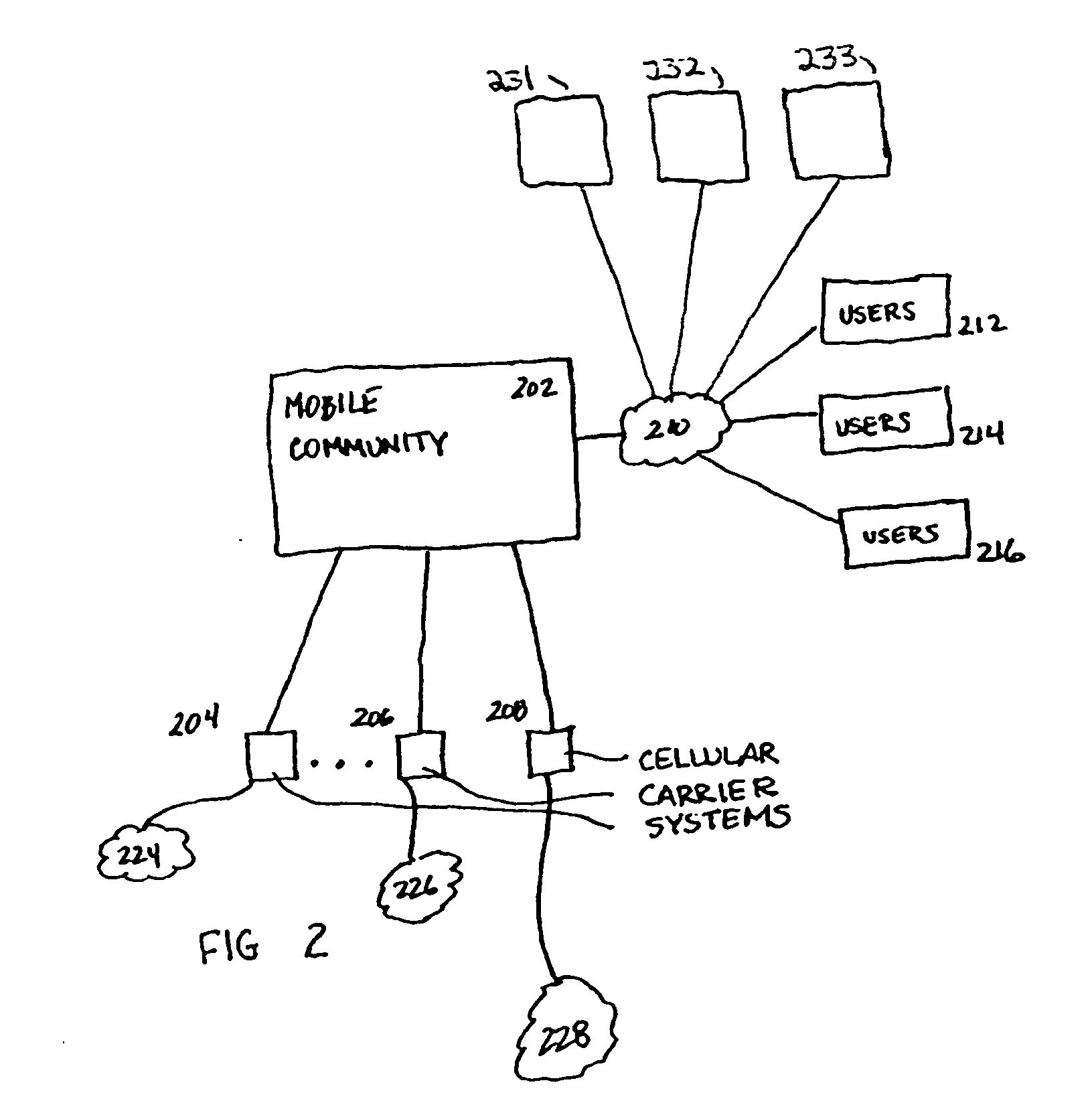
Vehicle event recorder systems and networks having integrated cellular wireless communications systems
ActiveUS20070219686A1Transmission easilyHigh bandwidthVehicle testingRegistering/indicating working of vehiclesTransceiverThe Internet
Owner:SMARTDRIVE SYSTEMS
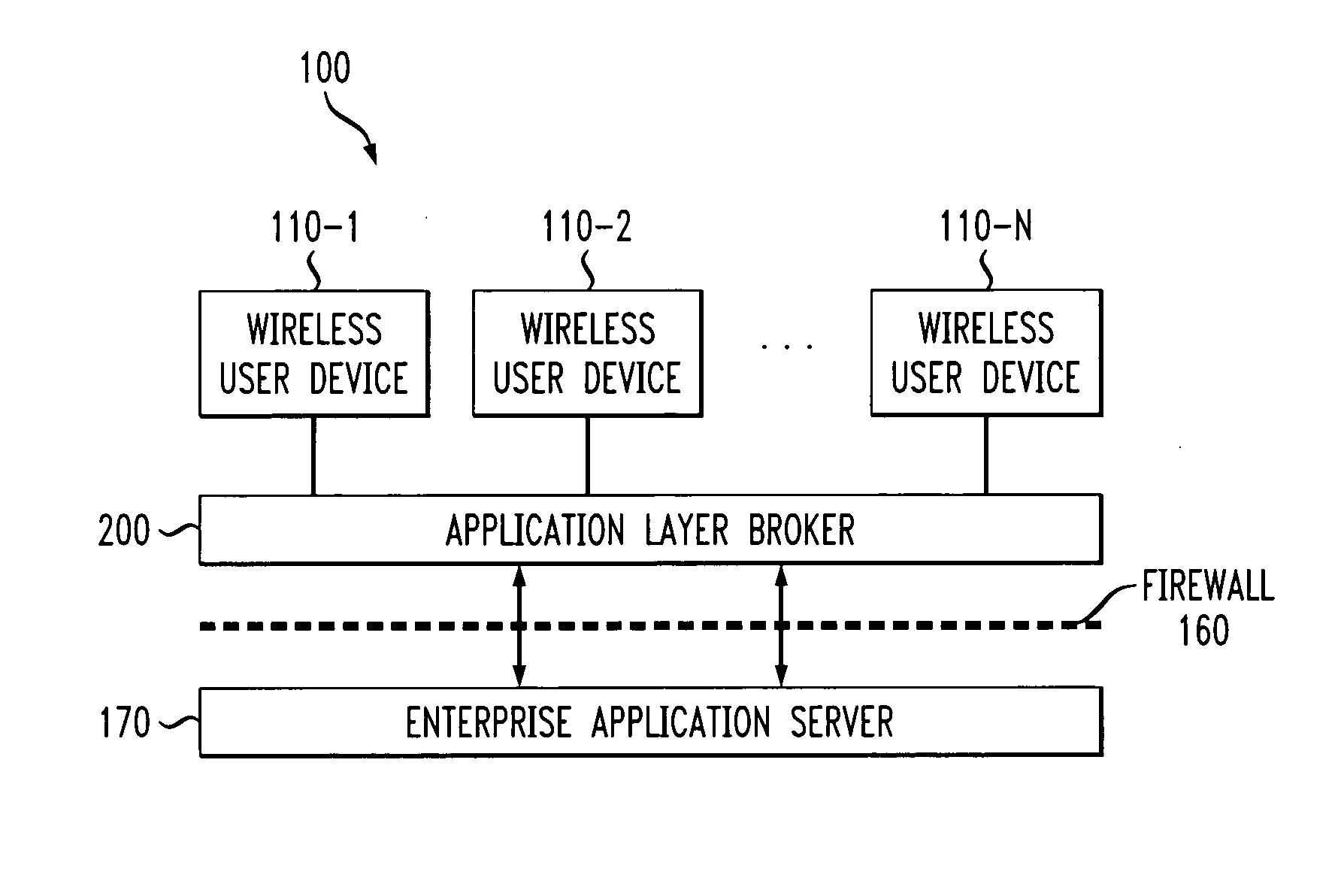
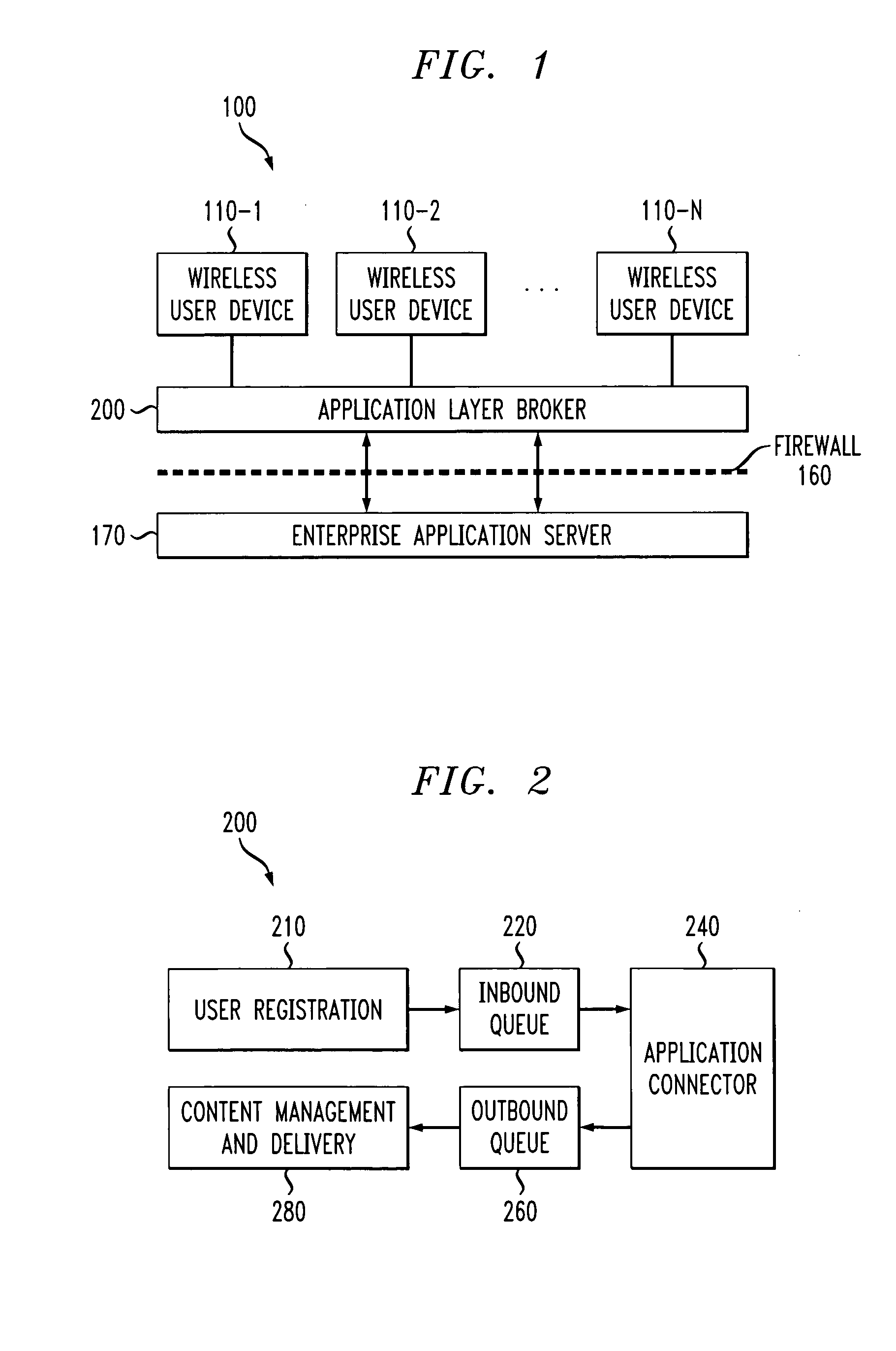
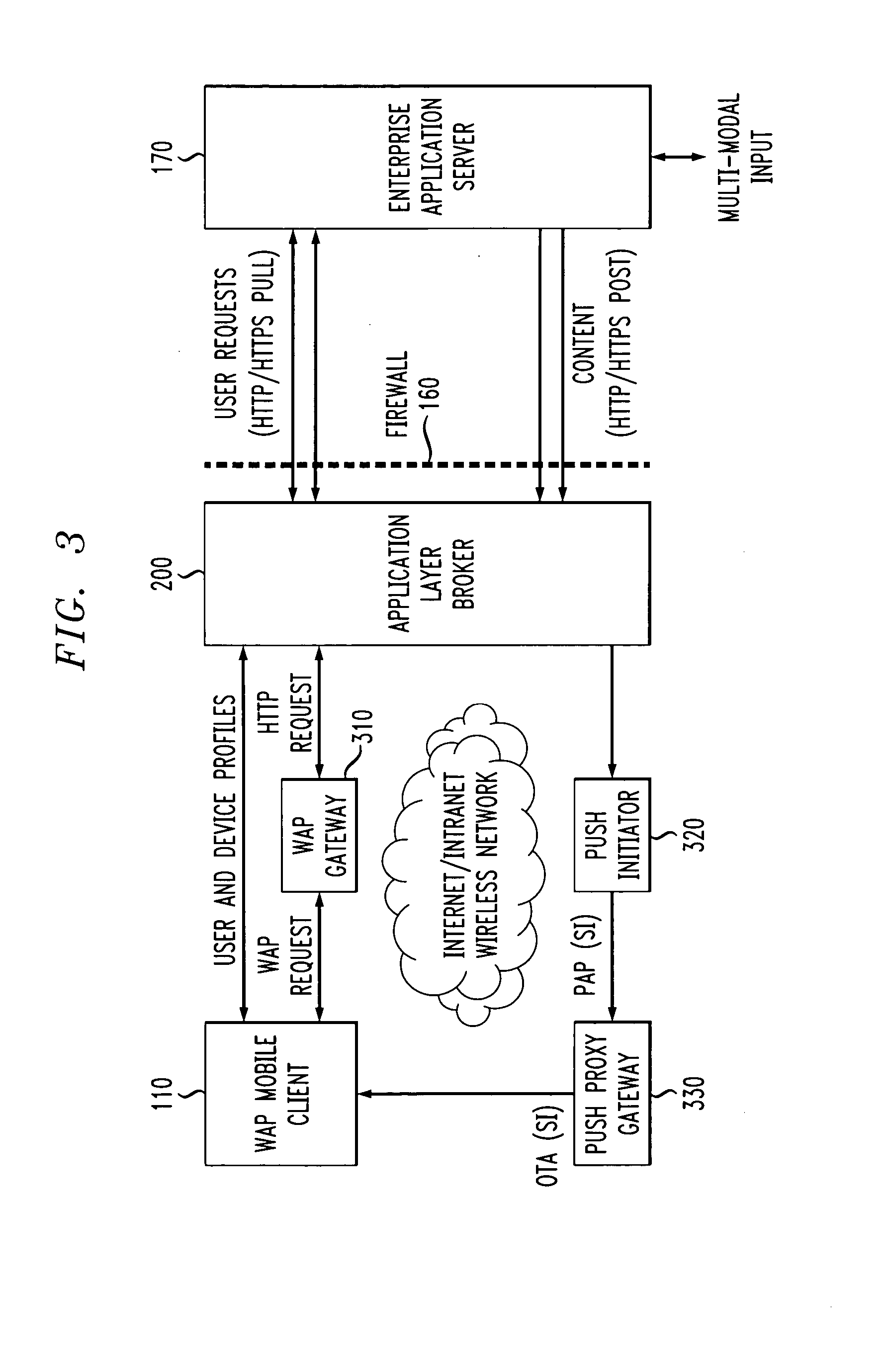
Method and apparatus for secure wireless delivery of converged services
ActiveUS20050071674A1Digital data processing detailsUnauthorized memory use protectionApplication serverService control
A method and apparatus are provided for the secure delivery of converged services to users of wireless devices in a wireless environment. An application layer broker is position between the user devices and the application server to provide an indirect coupling between the enterprise application server and the wireless user devices. The application layer broker links the wireless environment to the enterprise application server through an event triggered content delivery mechanism without providing a direct link between the wireless user device and the enterprise application server. Delivered content can only be accessed by the intended user and the authorized device. The application layer broker provides adaptation to various user devices and the various capabilities associated with each user device. Wireless devices can be upgraded independently from upgrades to the application server. The decoupling performed by the application layer broker separates the service control, such as user registration from the service delivery.
Owner:AVAYA INC
Fixed Position Multi-State Interactive Advertisement
Owner:MICROSOFT TECH LICENSING LLC
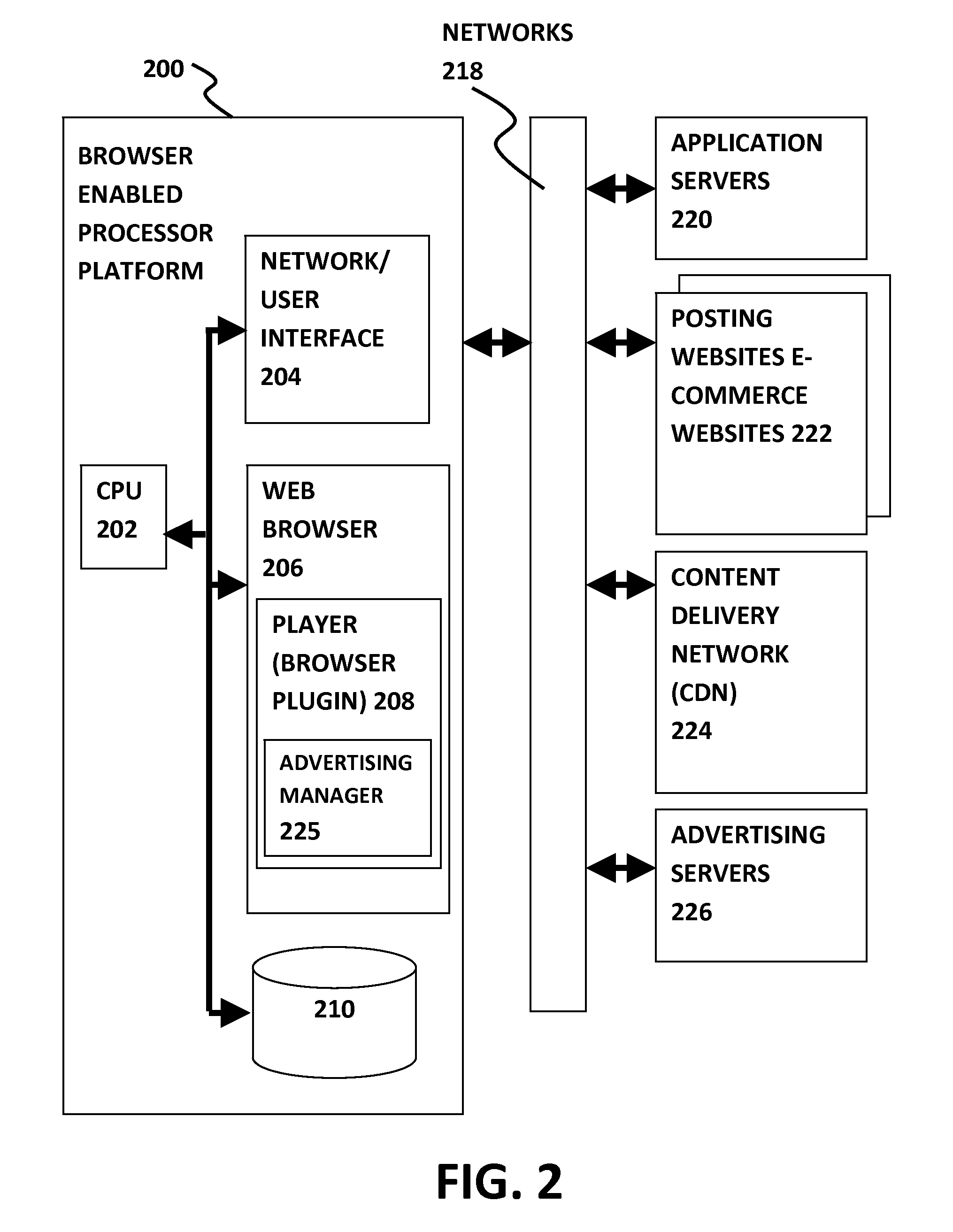
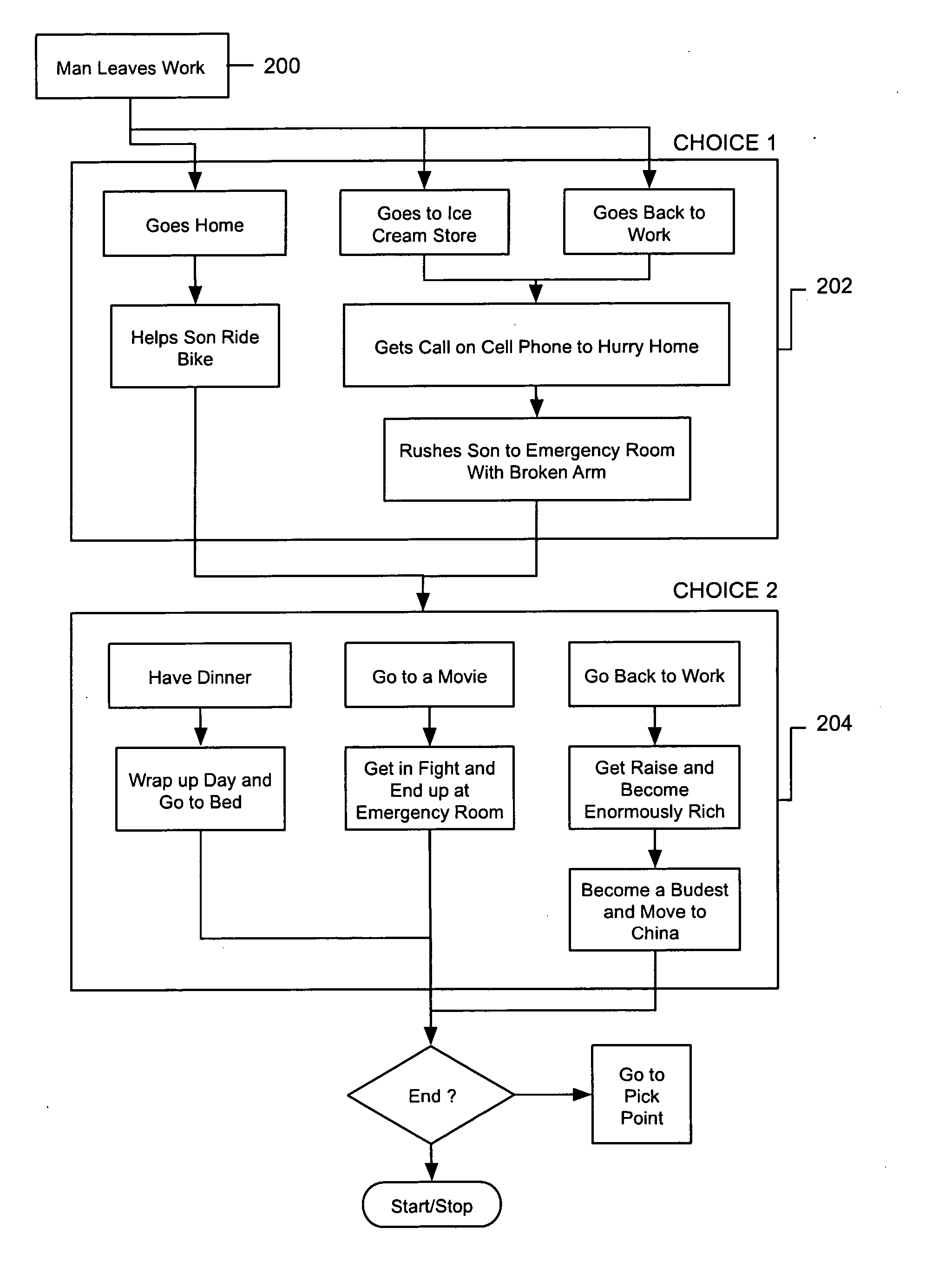
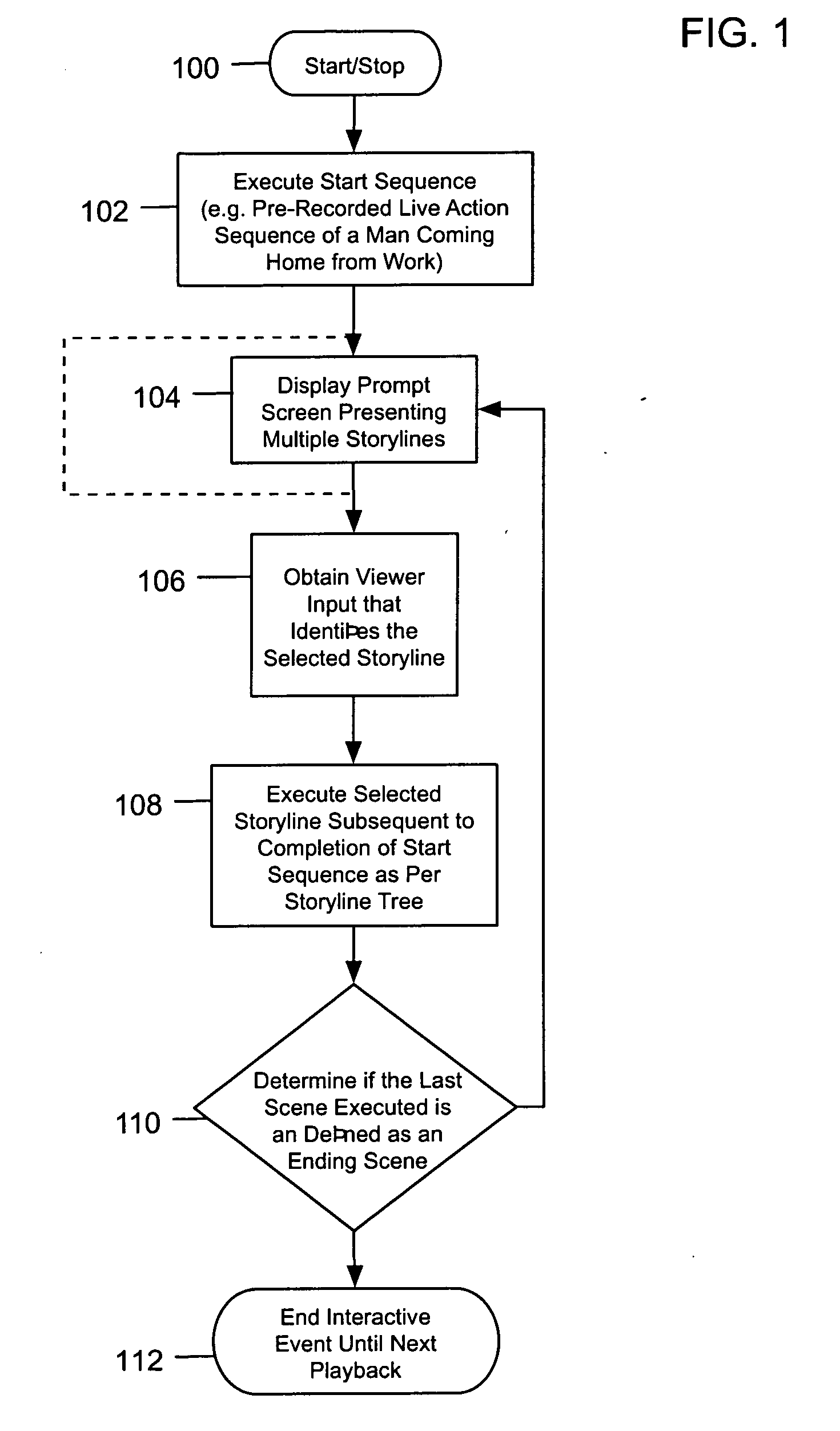
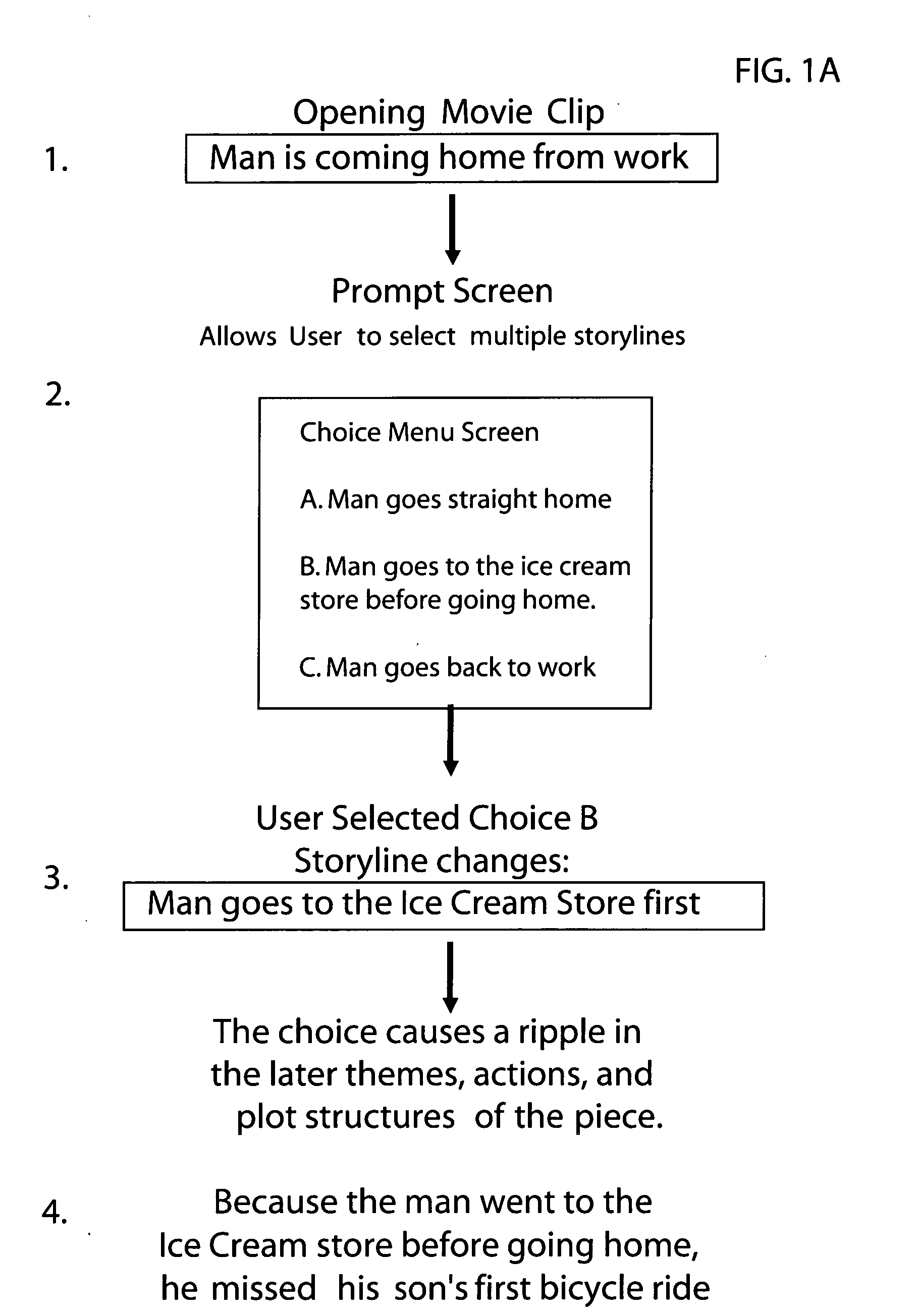
System and method for implementing an interactive storyline
InactiveUS20070099684A1Electronic editing digitised analogue information signalsRecord information storageEvent triggeredA domain
An interactive event that allows viewers to interact with a story in a video or film environment and change the story that is told based on input provided or obtained from the audience or other sources. For instance, an interactive event is created out of a movie storyline and given alternate endings, branching storylines, dead ends, advances, and regressions in the story. The system is designed to generate an interactive event out of a feature film by inserting menu prompts or branch points throughout the storyline allowing the player to navigate through the story based on input provided. The system allows the viewers to create different stories from the same situations. The events triggered may have a random component and thereby function much less like a pre-scripted story and more like real life where the story is always changing. The interactive storyline provides a domain wherein the participant experiences actions and conflicts along with their favorite characters with the goal of navigating to the end of the movie.
Owner:BUTTERWORTH EVANS
Location-based, event triggered inter-radio access technology handovers from a CDMA macrocell to a wcdma femtocell
ActiveUS20100124931A1Well formedAssess restrictionNetwork topologiesRadio access technologyCommunications system
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
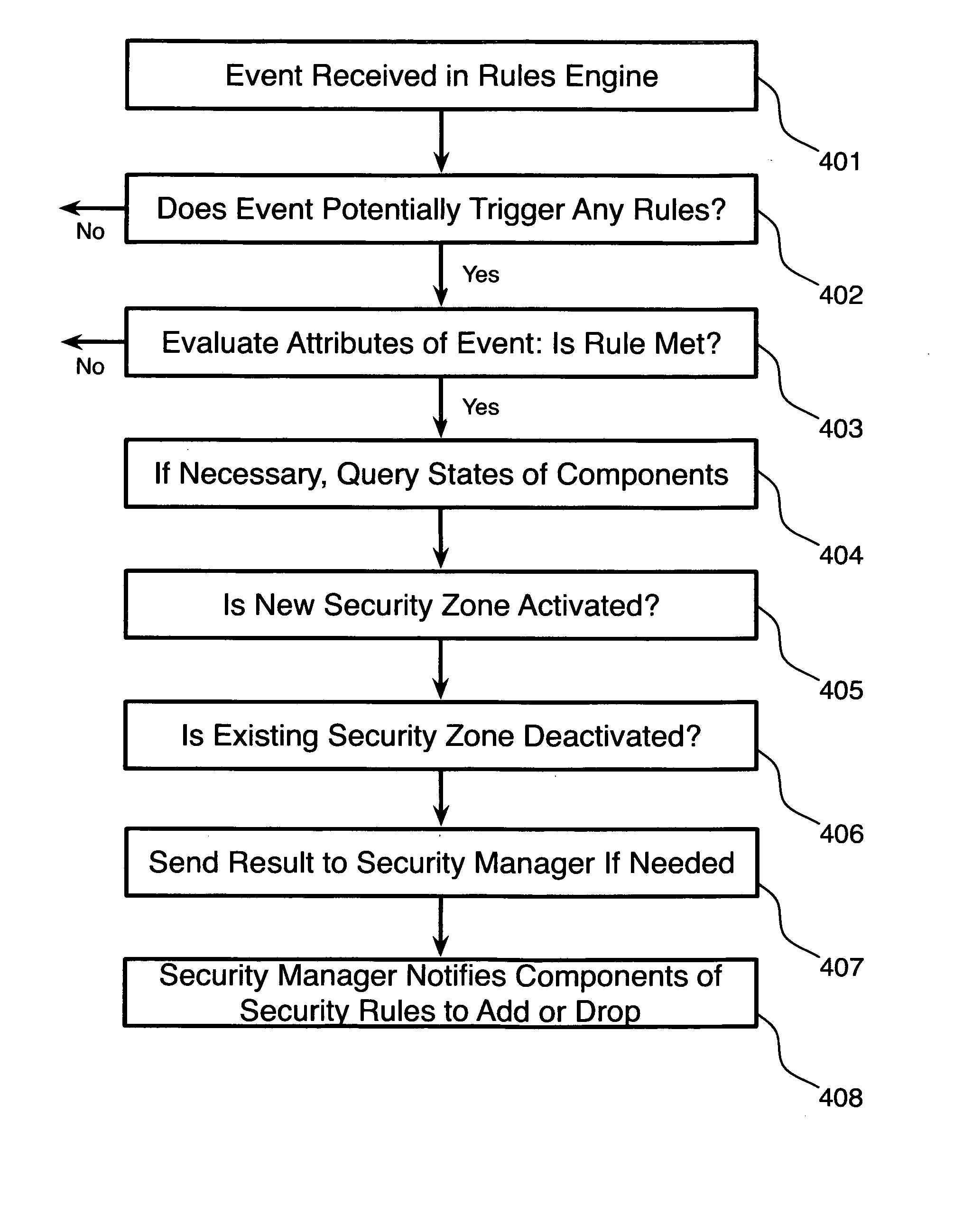
System and method for implementing adaptive security zones
A system for managing adaptive security zones in complex business operations, comprising a rules engine adapted to receive events from a plurality of event sources and a security manager coupled to the rules engine via a data network, wherein upon receiving an event, the rules engine determines what rules, if any, are triggered by the event and, upon triggering a rule, the rules engine determines if the rule pertains to security and, if so, sends a notification message to the security manager informing it of the triggered event, and wherein the security manager, on receiving a notification message from the rules engine, automatically establishes a new security zone based at least in part on the contents of the notification message, is disclosed
Owner:SERENOVA LLC
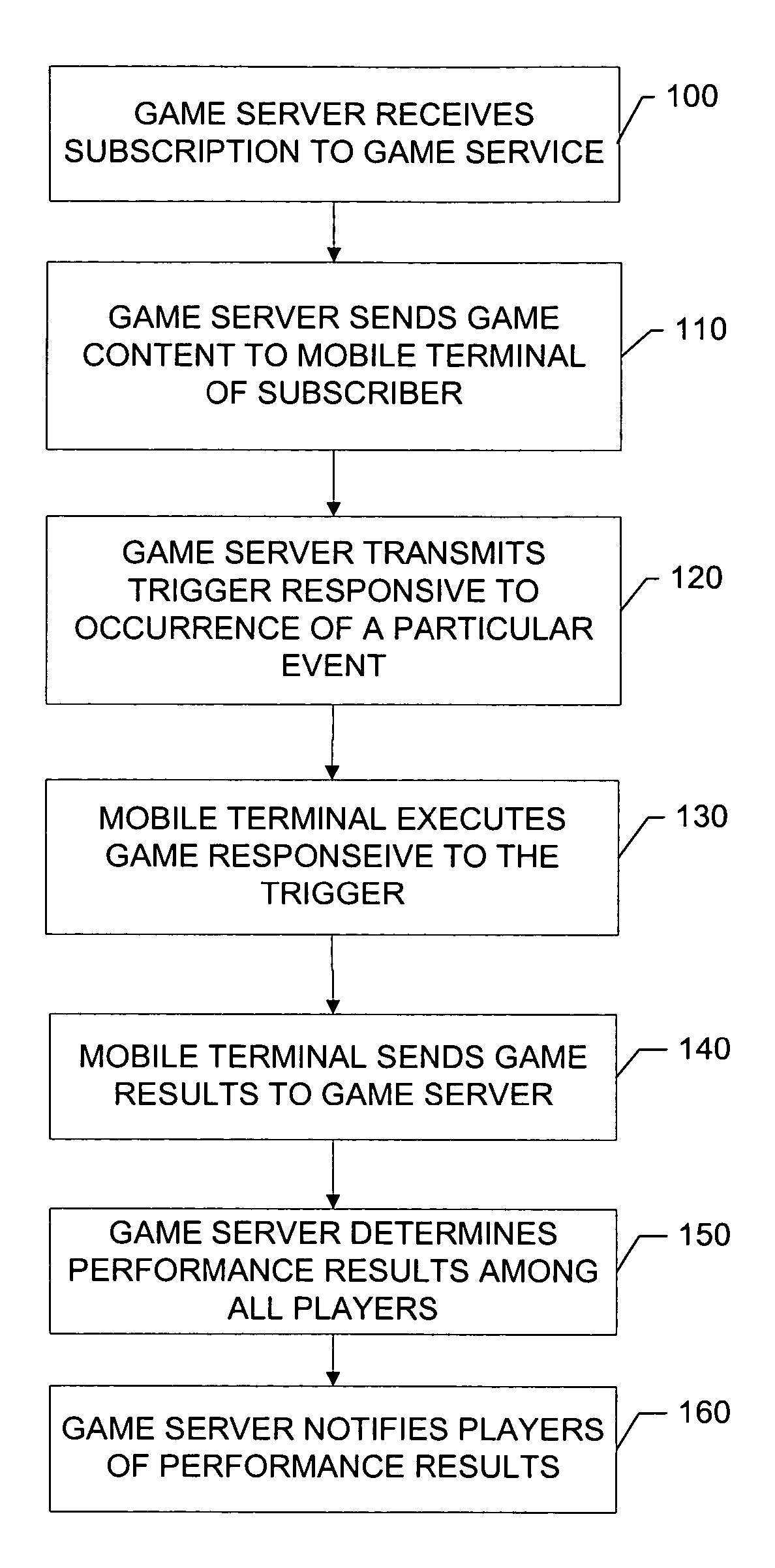
Method, apparatus, system and computer program product for event triggered games
A method of providing event triggered games includes operations of receiving a subscription to a game service from a subscriber, providing game content including a game to the subscriber, and enabling remote execution of the game responsive to receipt of a trigger associated with an occurrence of a predefined event of interest.
Owner:VRINGO INFRASTRUCTURE
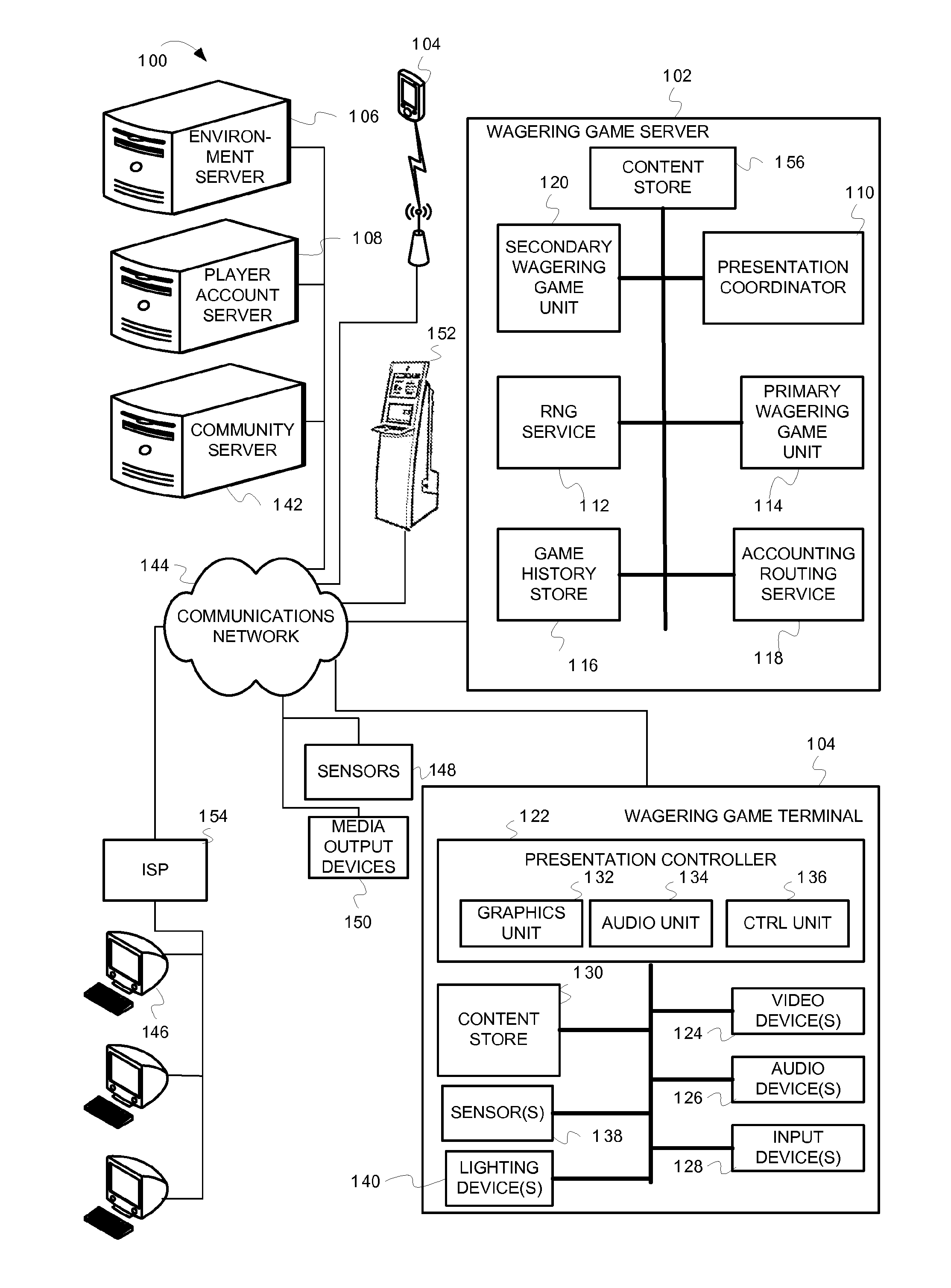
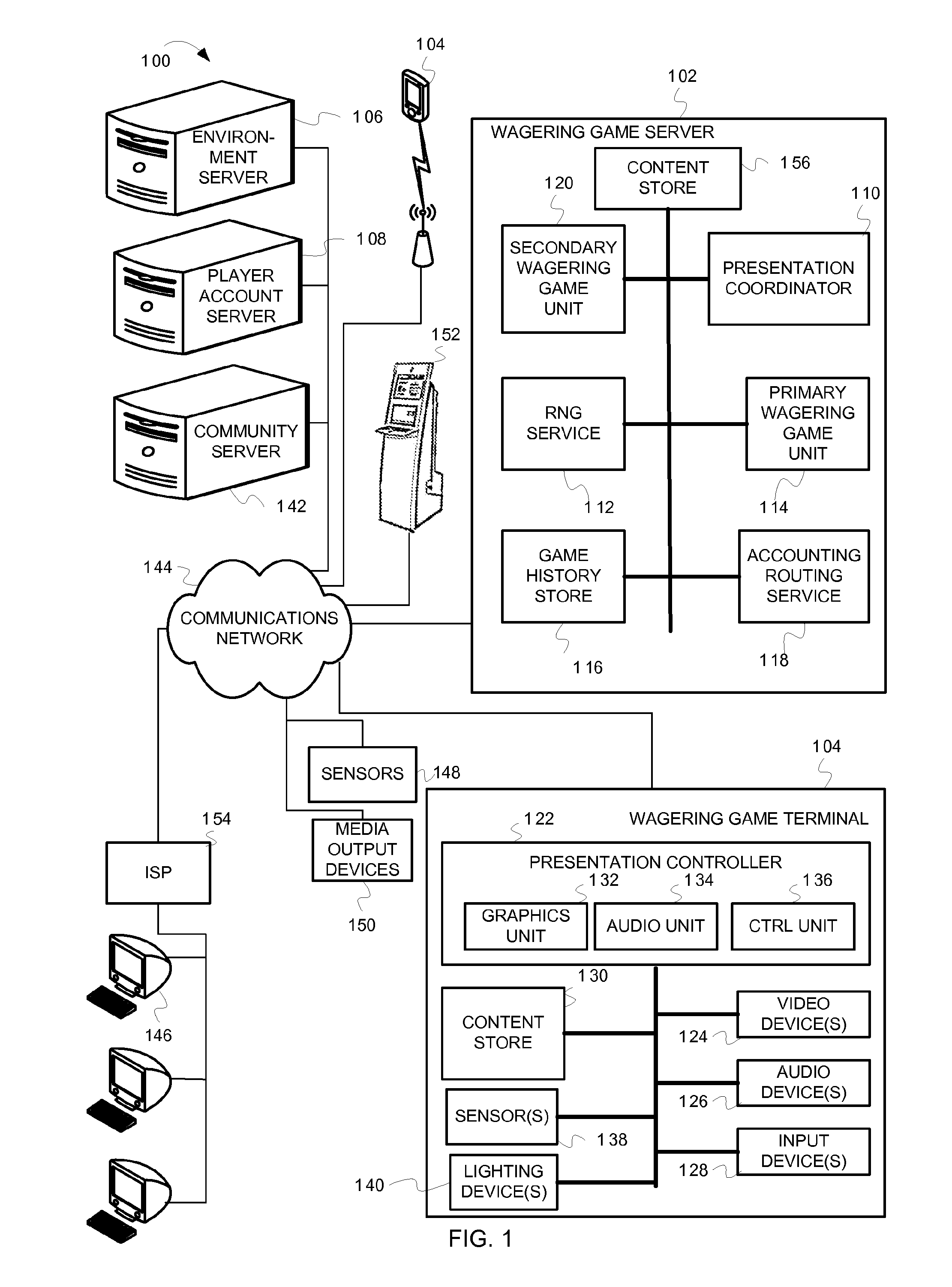
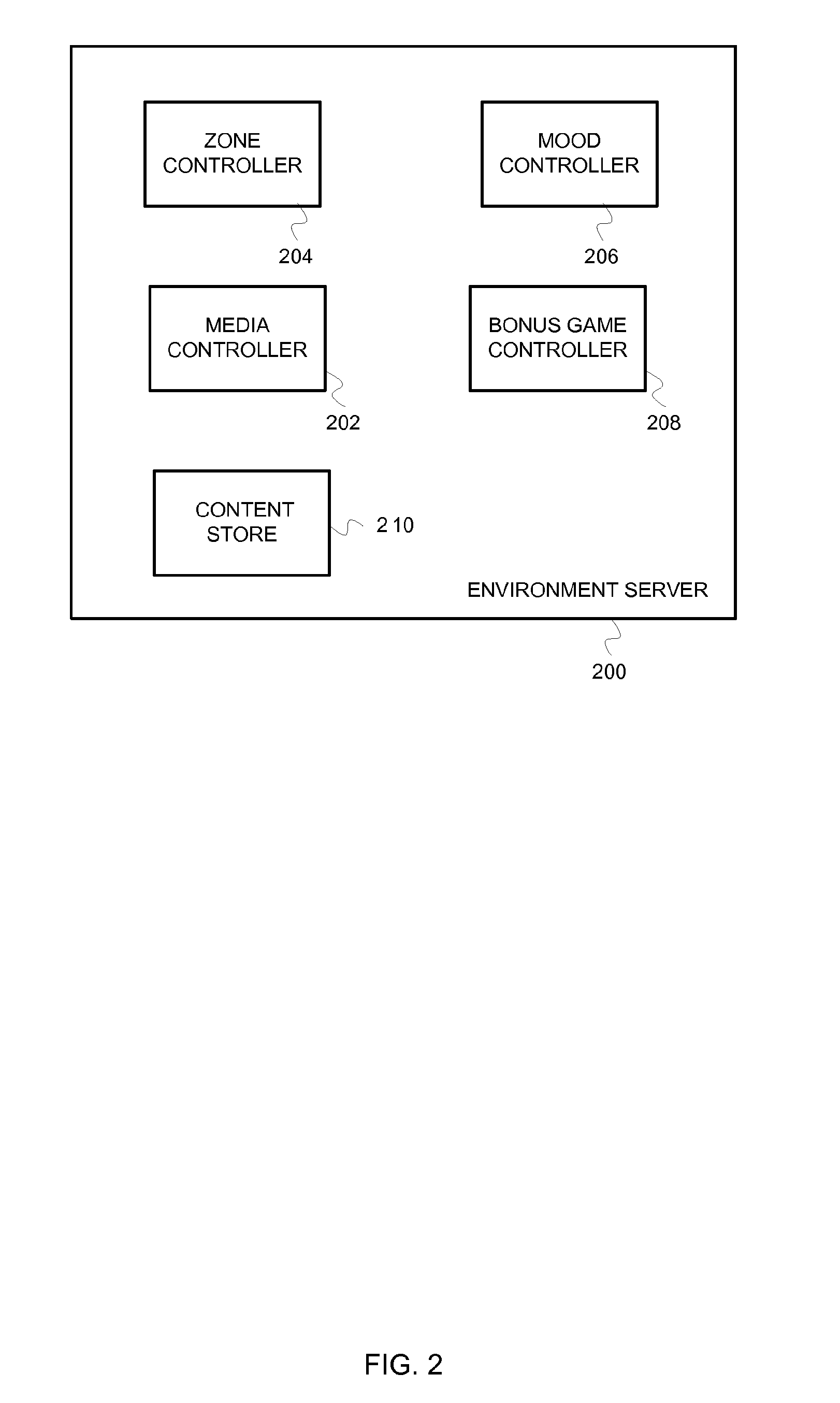
Creating casino experiences
Owner:LNW GAMING INC
Methods and systems for creating a dynamic call log and contact records
InactiveUS7839987B1Multiplex system selection arrangementsSpecial service for subscribersTelecommunicationsEvent triggered
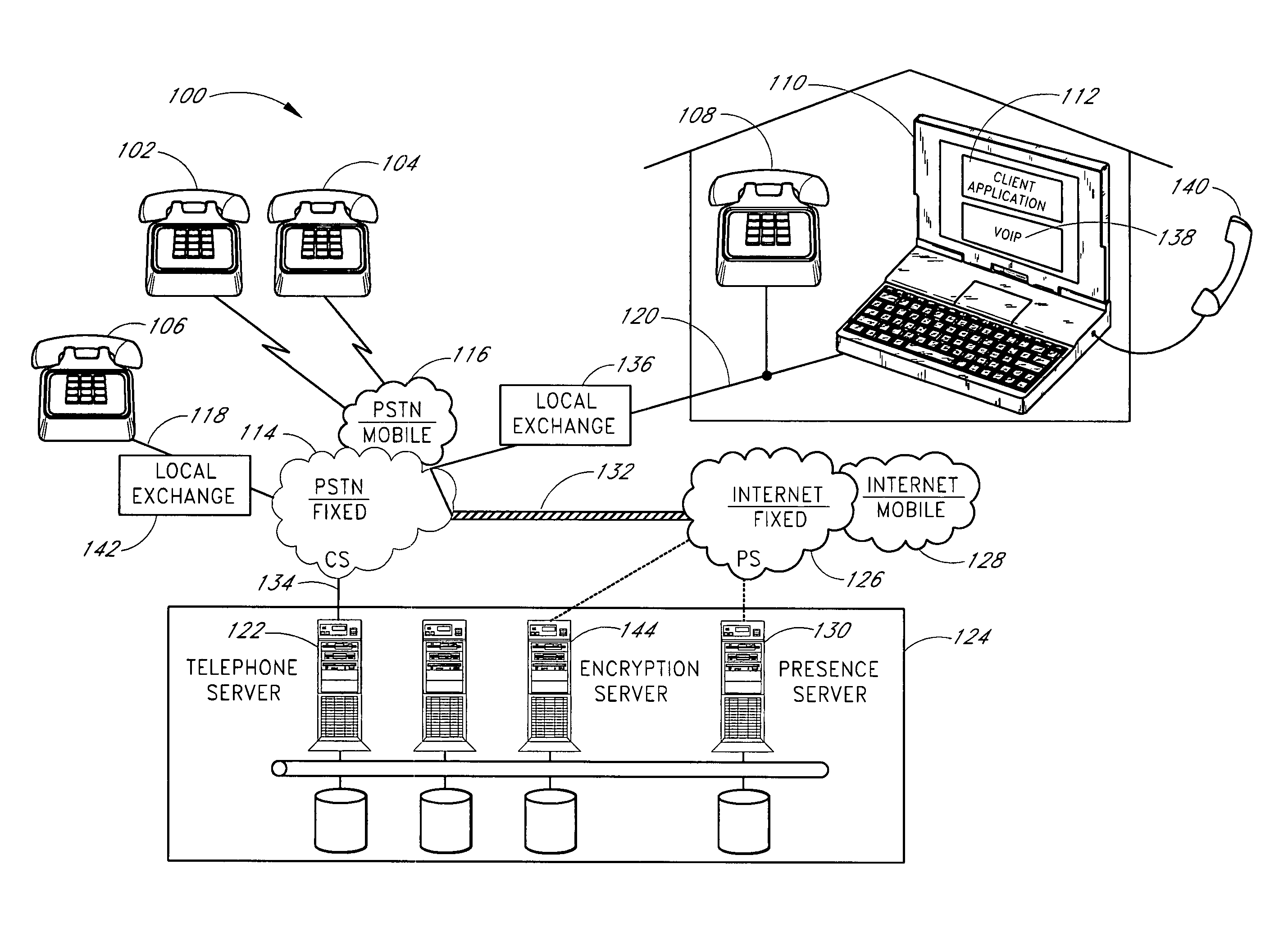
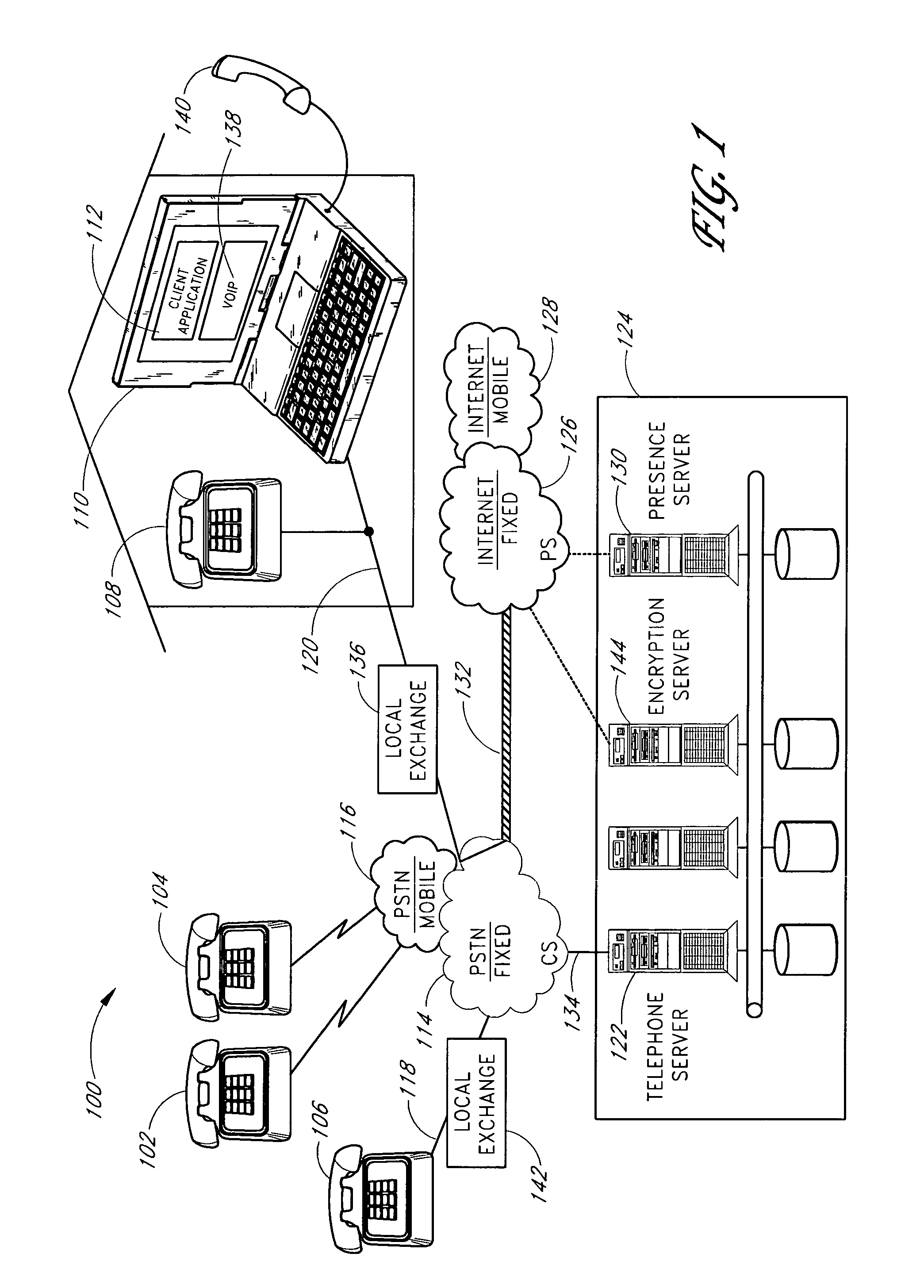
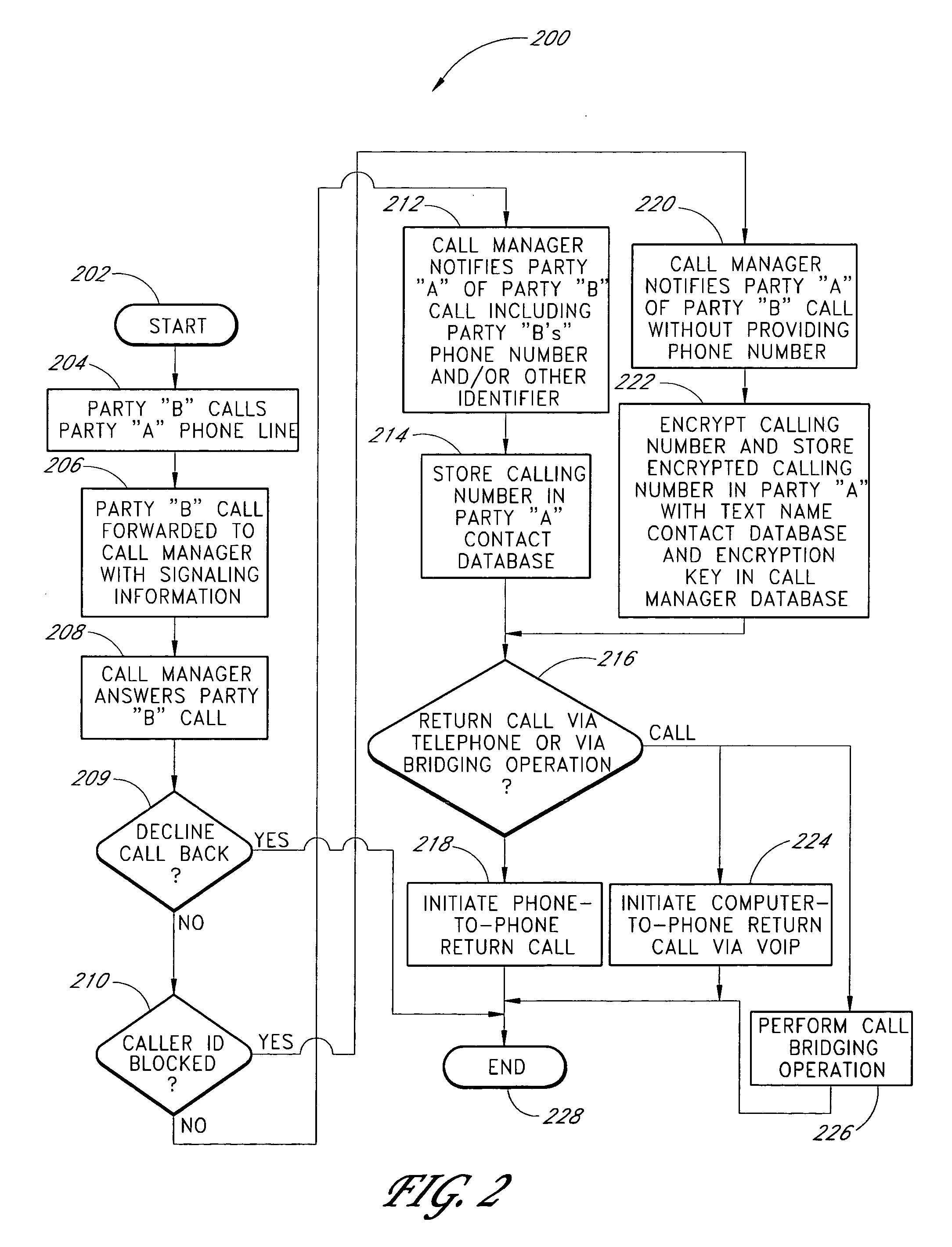
The present invention is related to telecommunications, and in particular, to methods and systems for processing call signaling data. In an embodiment, a call processing system receives a first message from a switch while the switch is processing a call for a calling party, wherein the first message is initiated at least partly in response to a firing of a call event trigger configured within a switch. The first message includes call signaling information, including the calling party's phone number. The calling party's phone number is stored in the call processing system. A communication channel is established over a network between the call processing system and a computer associated with the called party. A message is transmitted to the networked computer, the message including the calling party's phone number, wherein the calling party's phone number is intended to be displayed on the networked computer associated with the called party.
Owner:CALLWAVE COMM
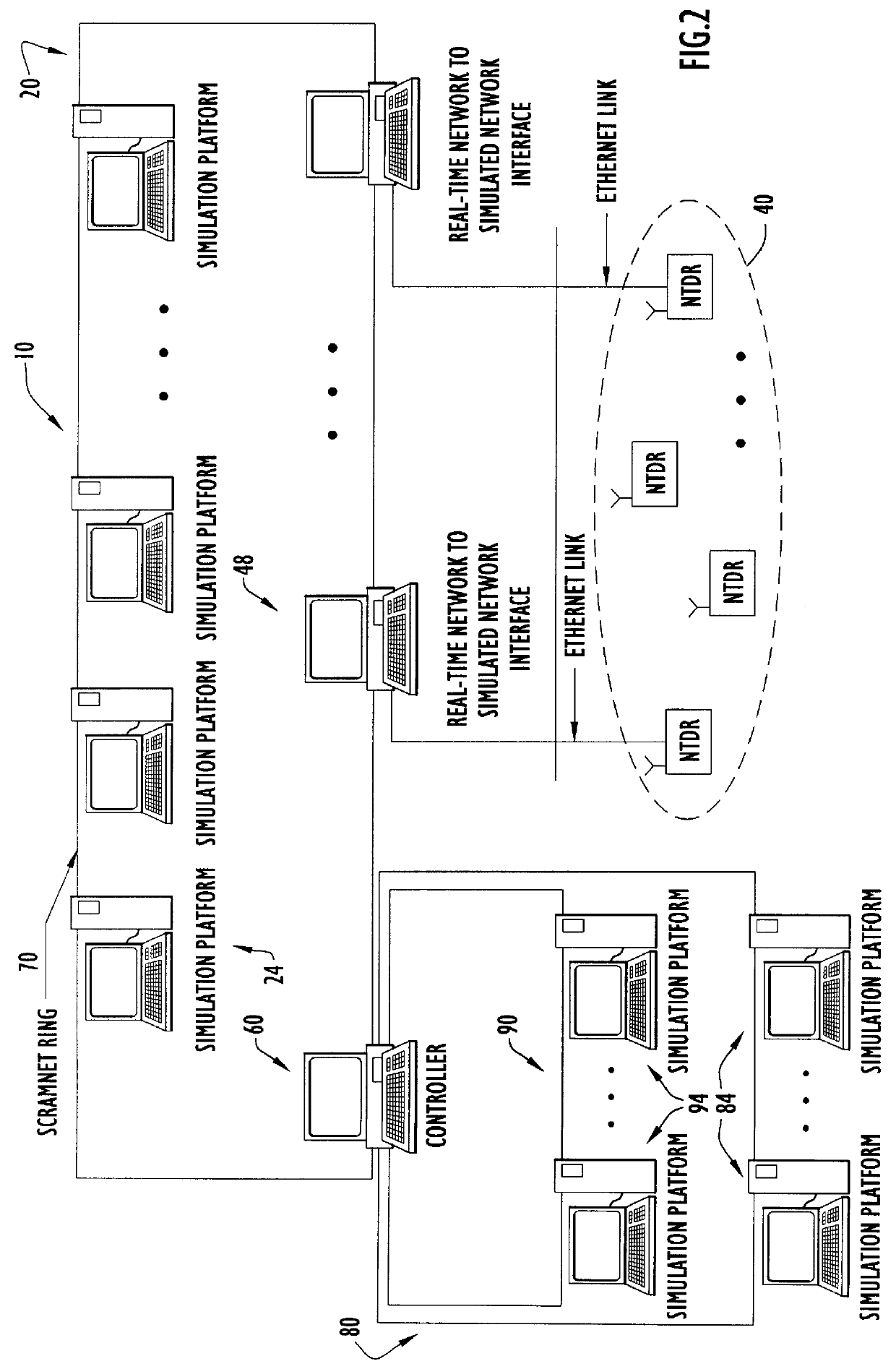
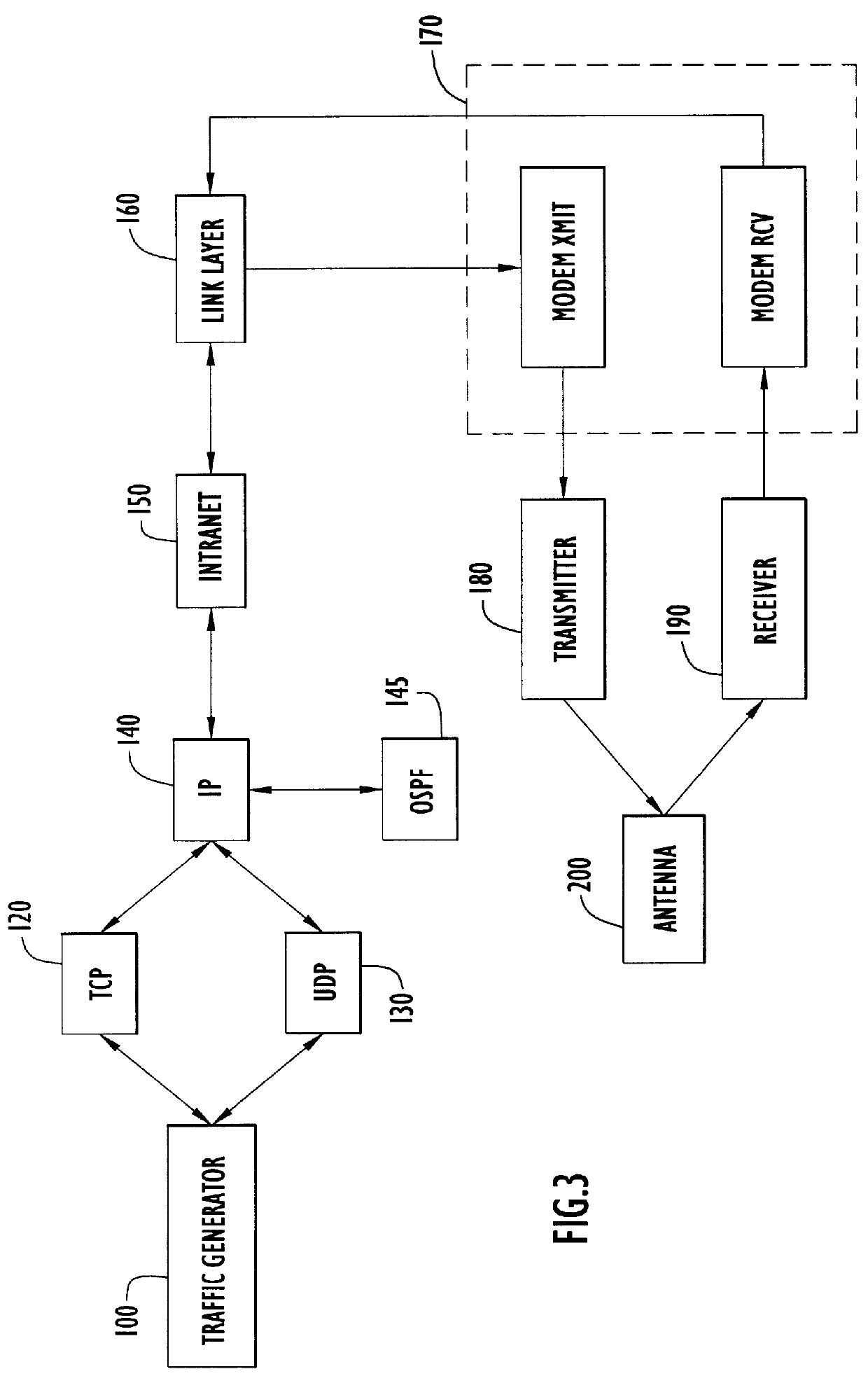
Large-scale network simulation method and apparatus
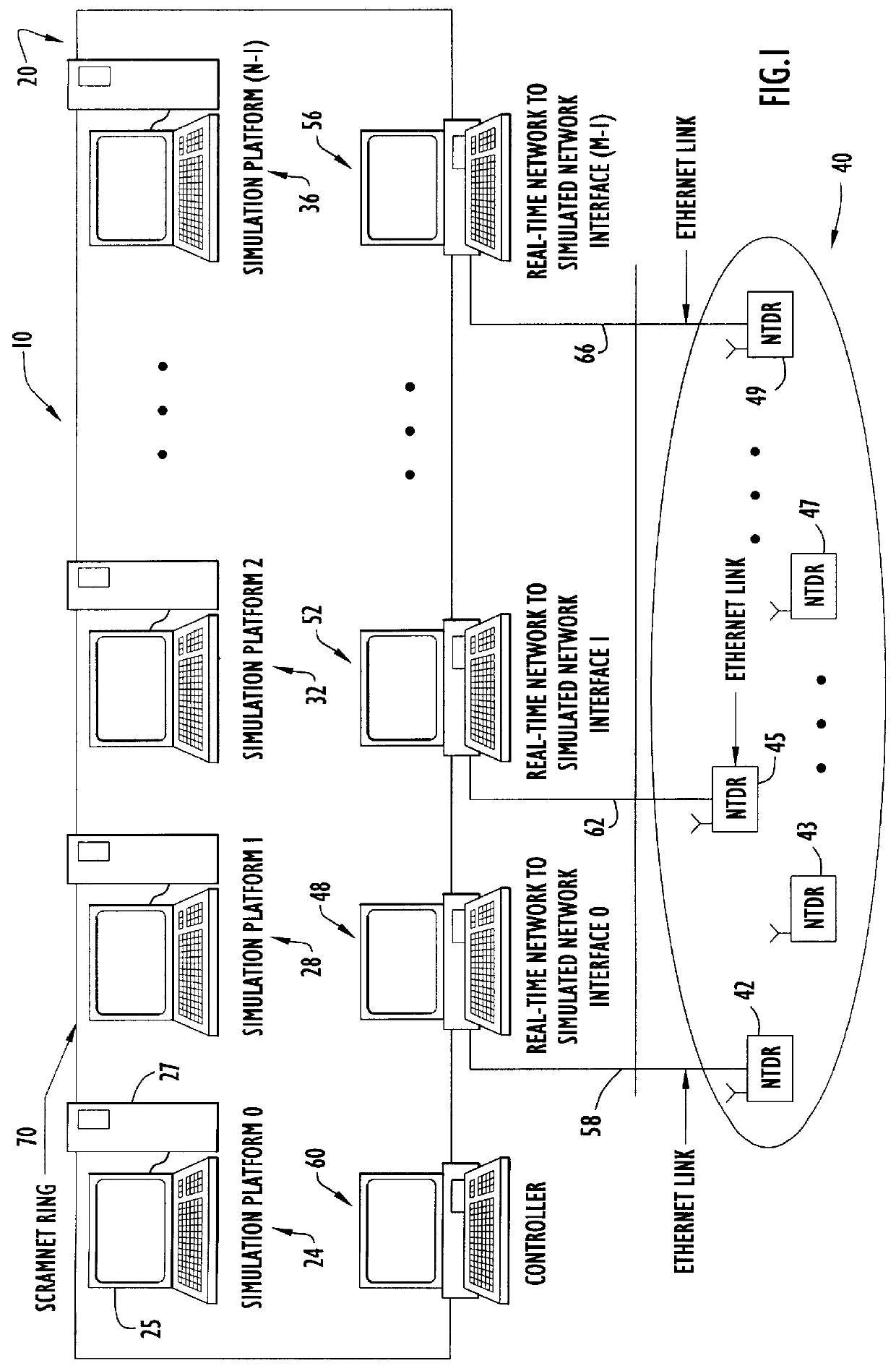
InactiveUS6134514AAnalogue computers for electric apparatusData switching networksTelecommunications linkChronological time
A distributed discrete-event simulation system operable for processing time-stamped events in chronological order for simulating a multinode communications network, the simulation system comprising a plurality of subsystem platforms (SPs) operable for transmitting message packets to other SPs for simulating node to node communications; and a system controller coupled via a communication link to the plurality of SPs for controlling synchronization and message packet processing associated with the plurality of SPs; wherein when a time-stamped event is received by one of the SPs, the receiving SP responsive to the time-stamped event triggers execution of tasks associated with the time-stamped event in the other SPs via the message packets to provide parallel task processing for the particular time-stamped event among the plurality of SPs.
Owner:HARRIS CORP
System and method for verification of identity for transactions
Billing a customer through an intermediary billing system for a transaction by receiving, at the intermediary billing system, a transaction request associated with a transaction amount and a customer identification code, validating, in the intermediary billing system, the transaction request by determining whether the customer identification code corresponds to a customer that is registered with the intermediary billing system, and sending, in the case that the transaction request is valid, a billing event trigger associated with the customer identification code to an external billing mechanism, the billing event trigger representing the transaction amount.
Owner:SMS AC INC
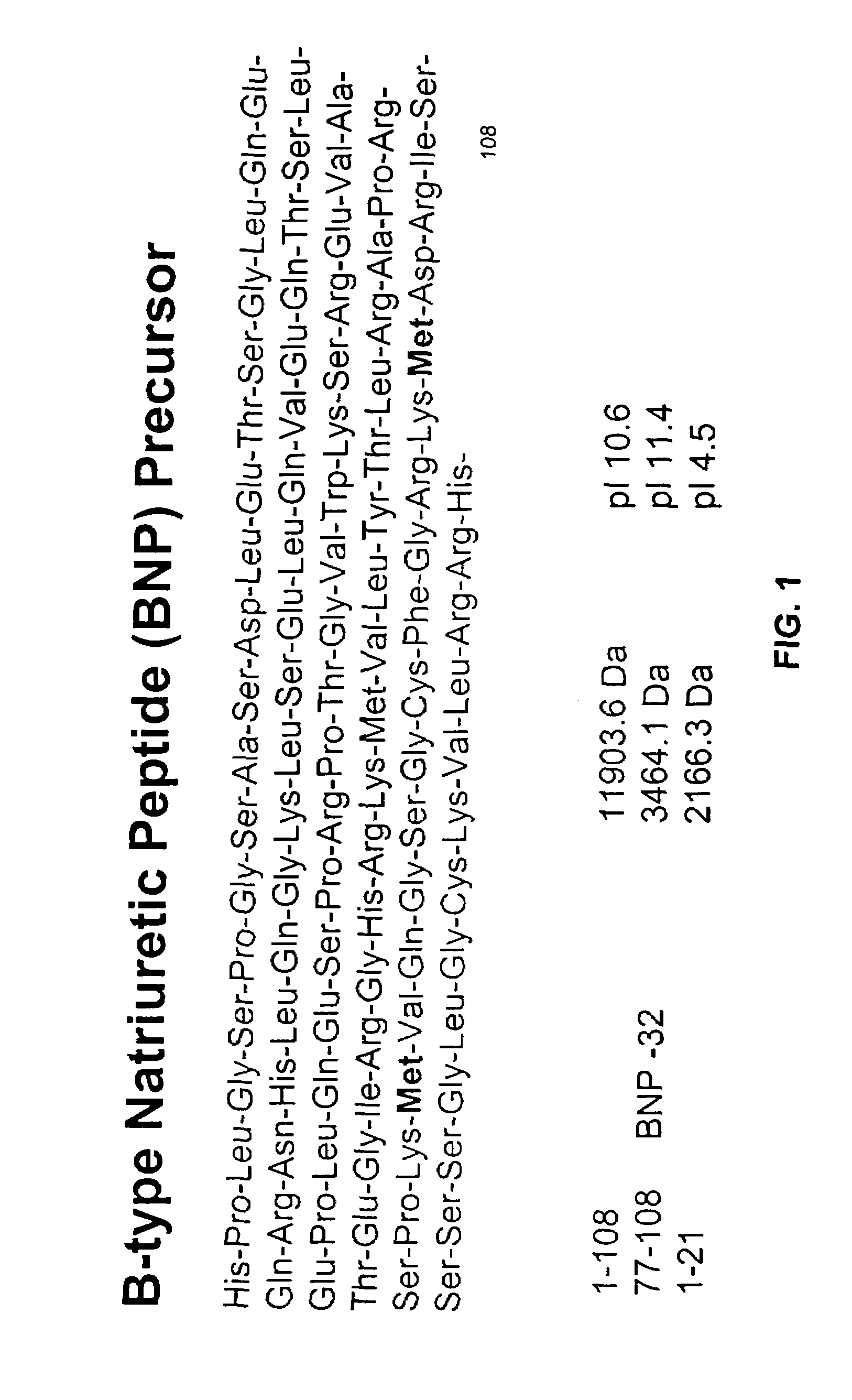
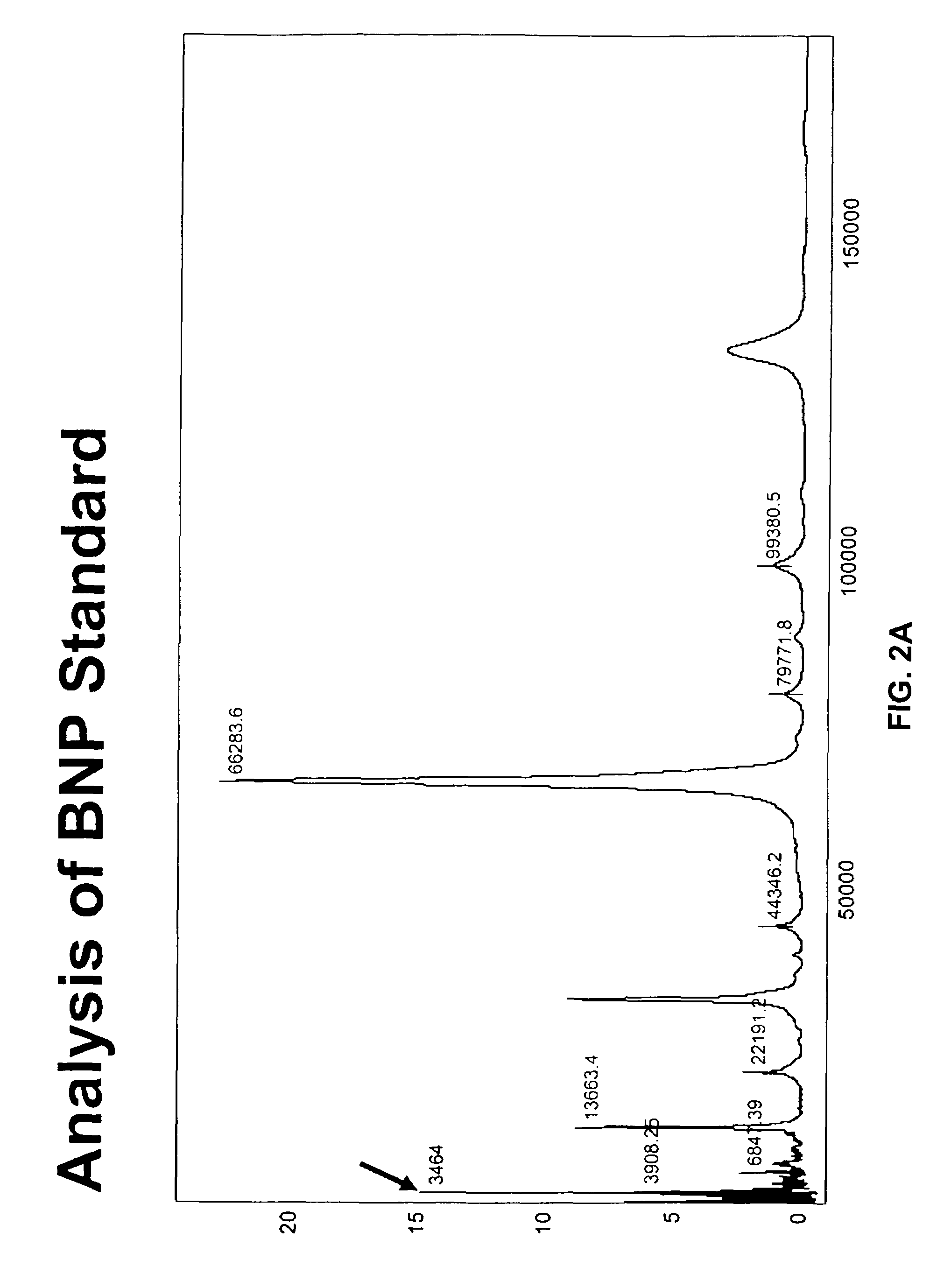
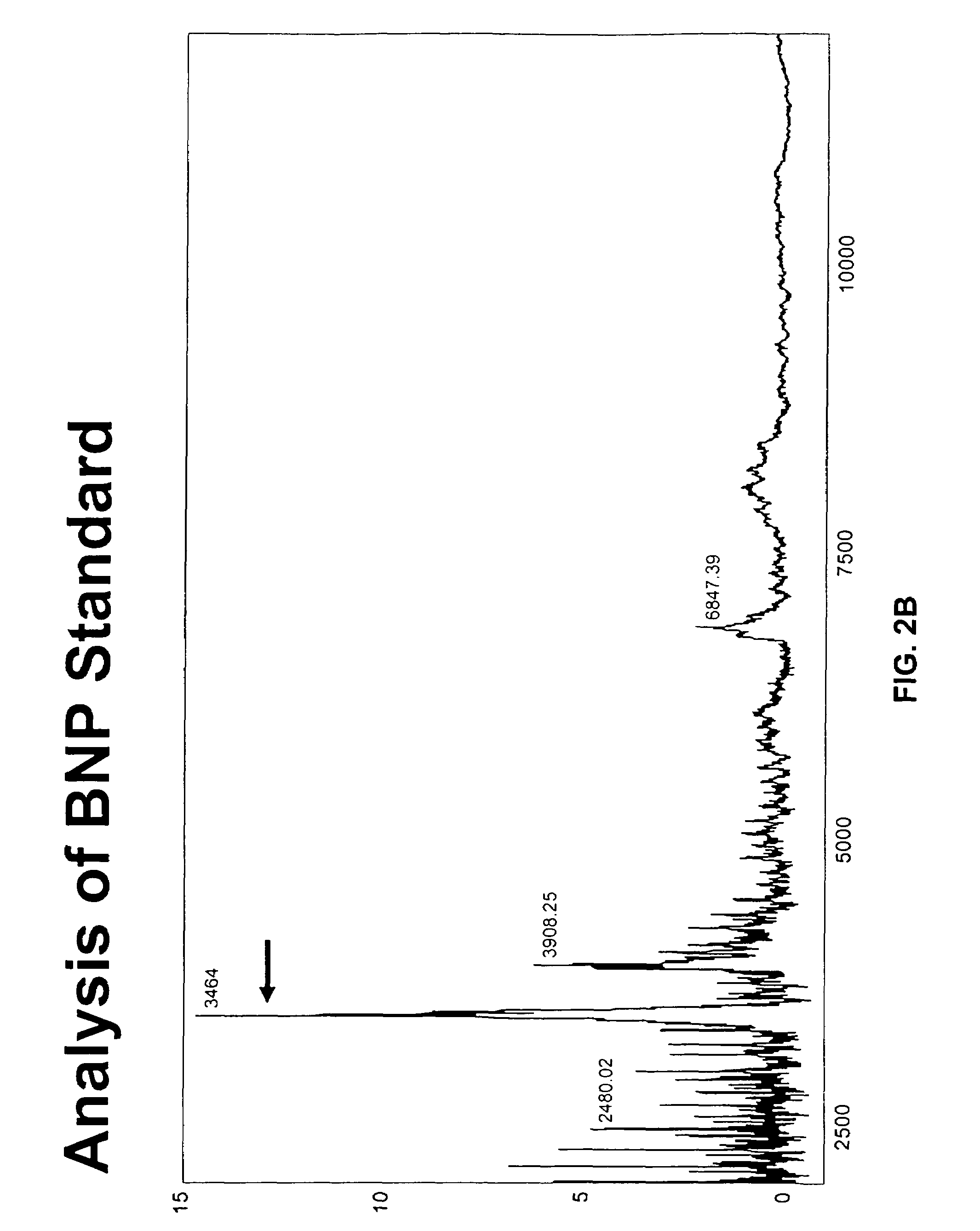
Polypeptides related to natriuretic peptides and methods of their identification and use
InactiveUS7341838B2Prevent degradationThe result is accurateCompound screeningApoptosis detectionTissue sampleEvent triggered
The present invention relates to the identification and use of polypeptides that bind to antibodies directed to a desired polypeptide of interest. Using natriuretic peptides and their precursors, and in particular BNP, as an example, the present invention describes a number of natriuretic peptides fragments produced in biological samples, most preferably blood-derived samples, that bind to antibodies directed to BNP. Because production of such fragments is an ongoing process that may be a function of, inter alia, the elapsed time between onset of an event triggering natriuretic peptide release into the tissues and the time the sample is obtained or analyzed; the elapsed time between sample acquisition and the time the sample is analyzed; the type of tissue sample at issue; the storage conditions; the quantity of proteolytic enzymes present; etc., such fragments may be used when both designing an assay for one or more natriuretic peptides, and when performing such an assay, in order to provide an accurate prognostic or diagnostic result.
Owner:VERMILLION INC +1
Method and system for dynamically controlling overtime in electronic auctions
InactiveUS7152043B2Detect and prevent erroneousEasy to adjustFinanceBuying/selling/leasing transactionsEvent triggeredSpecific time
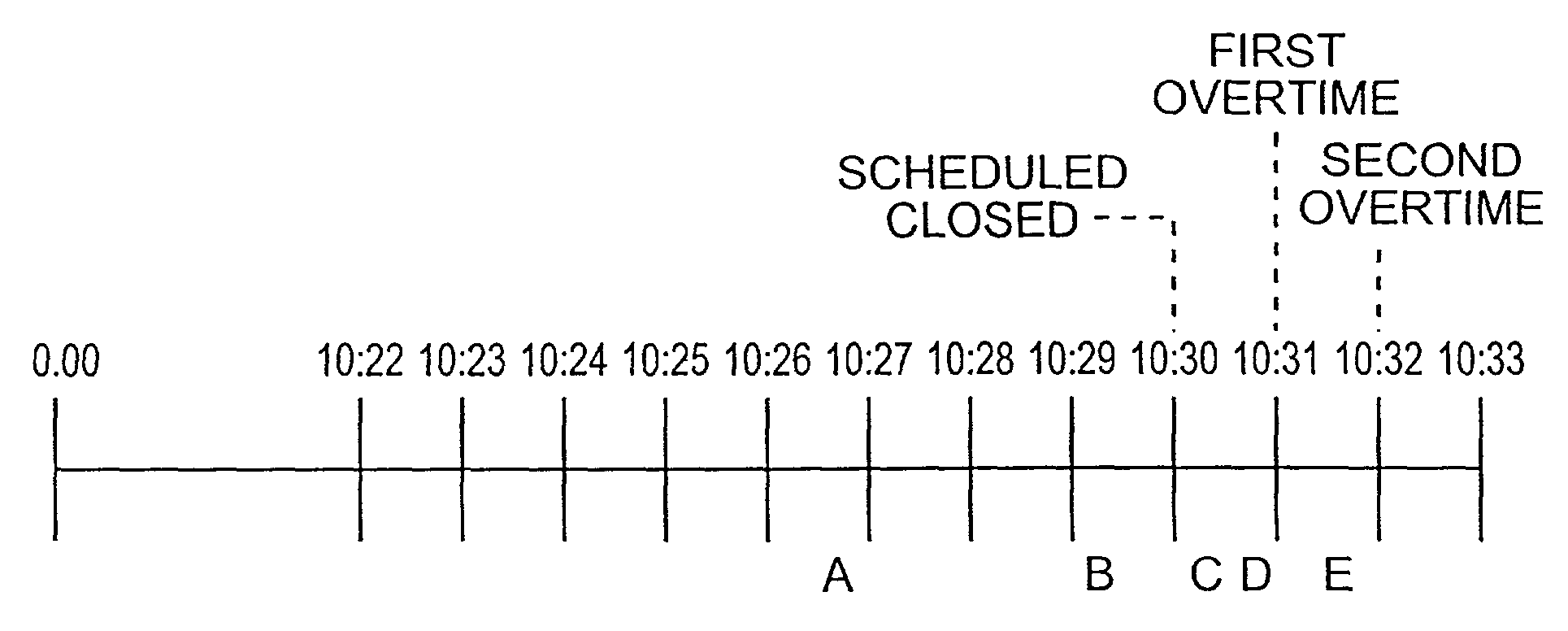
A method and system for conducting electronic auctions is described. A dynamic lot closing extension feature avoids collisions in closing times of multiple lots by dynamically extending the closing time of a subsequent lot if a preceding lot's closing time is extended to be too close to the subsequent lot's then-currently scheduled closing time. In one embodiment, scheduled closing times can be extended with a flexible overtime feature, in which the properties of the event triggering the extension and the duration of the overtime period(s) can be tailored to a particular auction, particular lots of products within an auction, and to the particular time within an auction process.
Owner:ARIBA INC
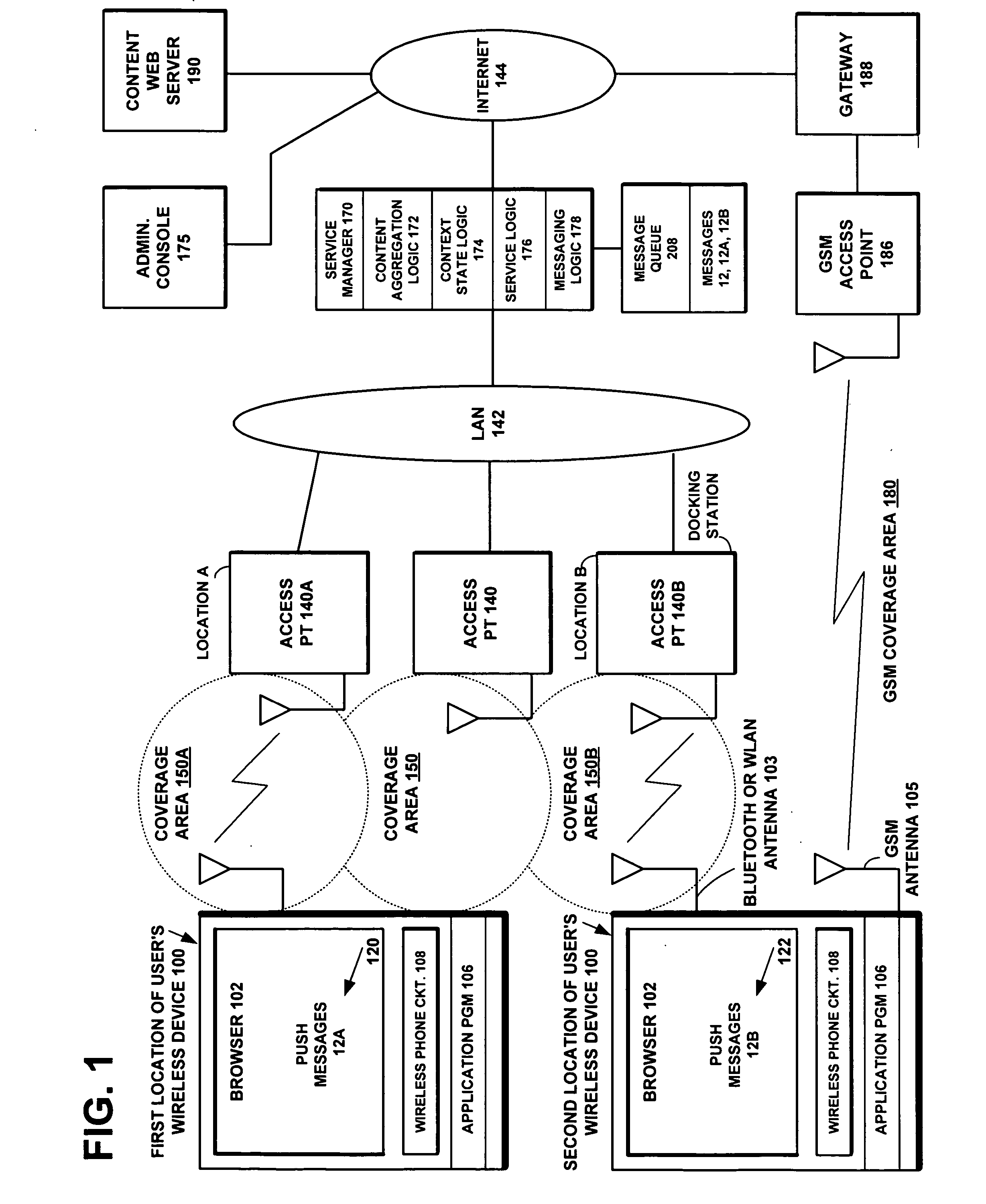
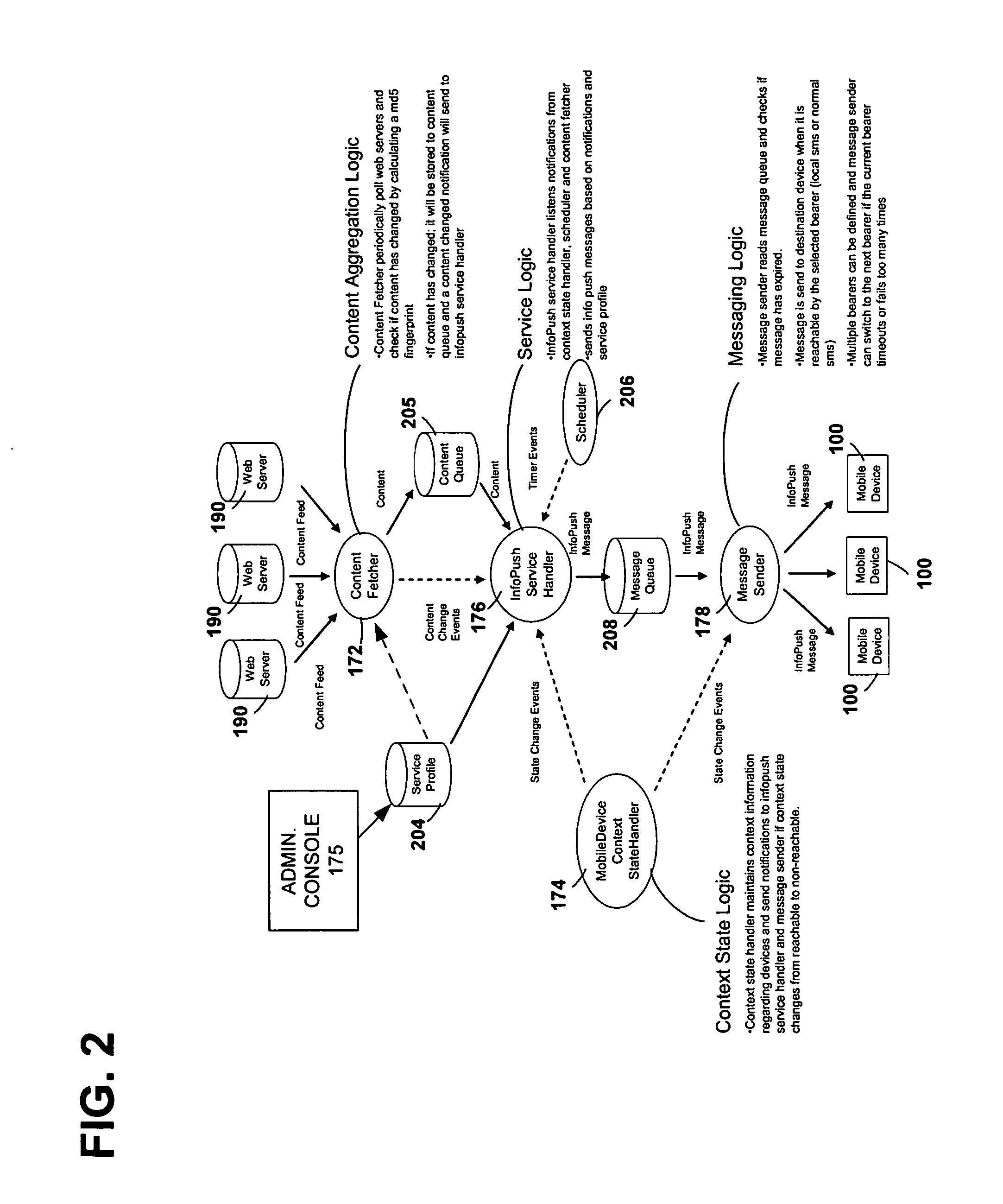
Method and system for controlling contextual information push services
InactiveUS20070214245A1Easy to createDigital computer detailsBroadcast service distributionMessage deliveryConfigfs
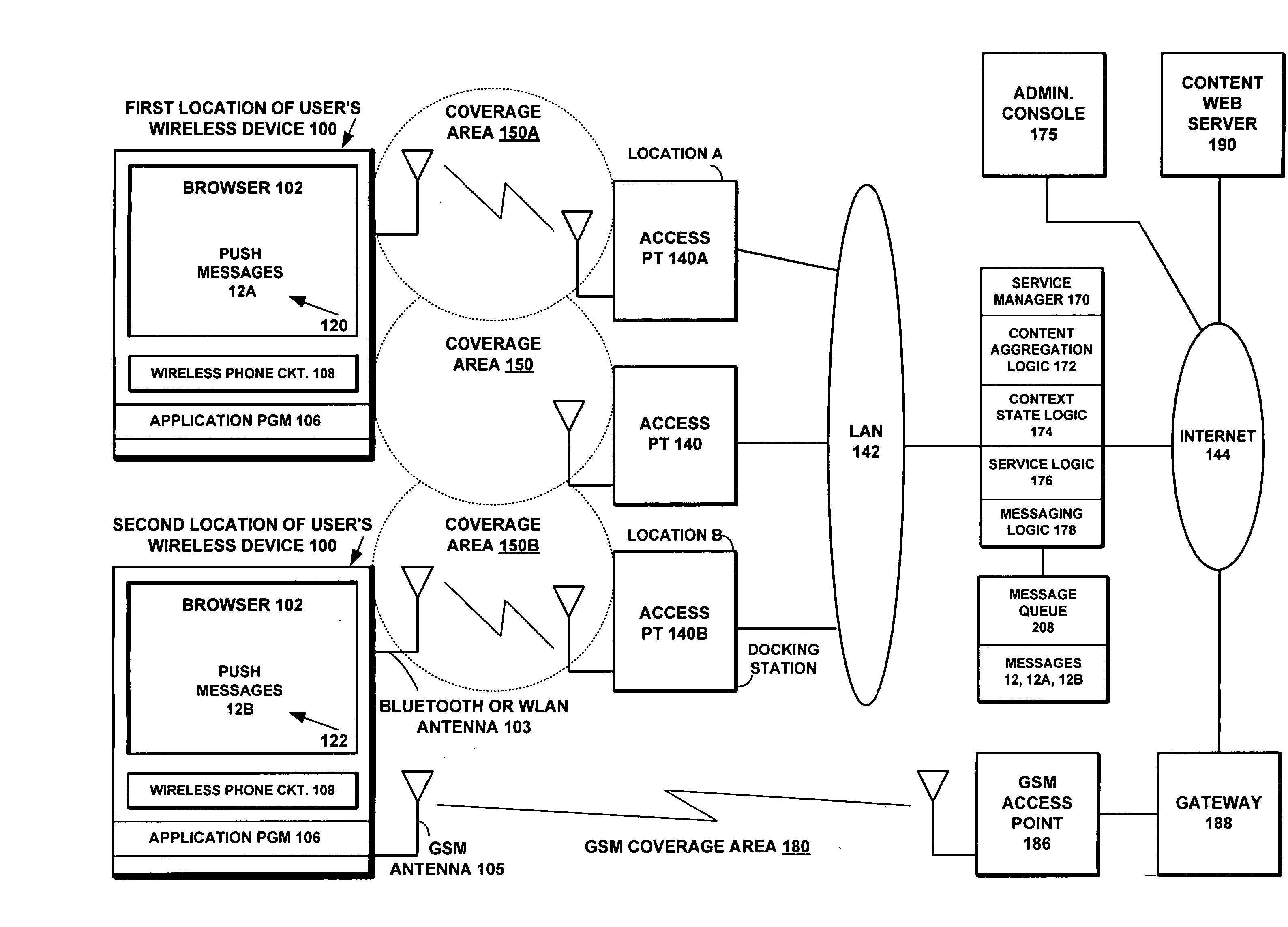
A system, server, method, and computer program product are disclosed for facilitating the creation of push messages pertaining to context dependent services and managing their delivery to mobile wireless devices having diverse routing, scheduling, and context or event-triggering requirements. A web-based interface is presented on an administrator console for defining profiles specifying content delivery characteristics for a plurality of mobile wireless devices. The profiles can include a recipient characteristic, a message delivery mode characteristic, and a bearer characteristic. A Service Manager is coupled to the web-based interface and to a plurality of access points, for pushing a message via a specified bearer, using a specified delivery mode, to one of the plurality of mobile wireless devices of a specified recipient satisfying one of the defined profiles of content delivery characteristics when the one device is located within a coverage area of one of the plurality of access points.
Owner:RPX CORP
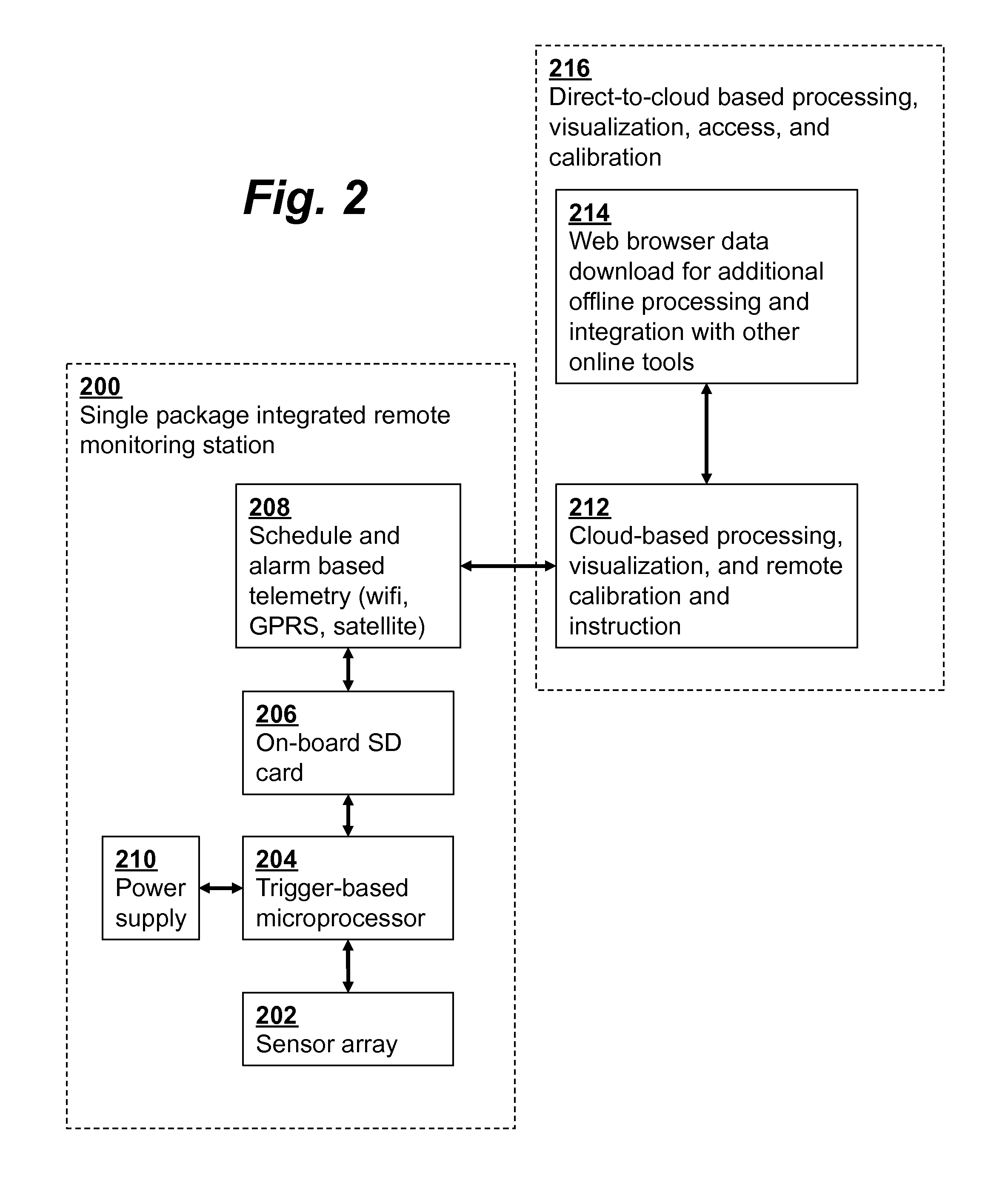
Distributed low-power wireless monitoring
ActiveUS20130317659A1Shorten the construction periodReduce power consumptionEnergy efficient ICTMechanical power/torque controlMonitoring systemEvent triggered
A distributed wireless monitoring system with low-power remote sensors includes data encoding / compression at sensors to reduce power use from transmission and storage, event activated operation / data logging, remote configuration of event triggering thresholds and correlation templates, distributed processing capabilities, and sensor clock synchronization from a network time service.
Owner:PORTLAND STATE UNIV +1
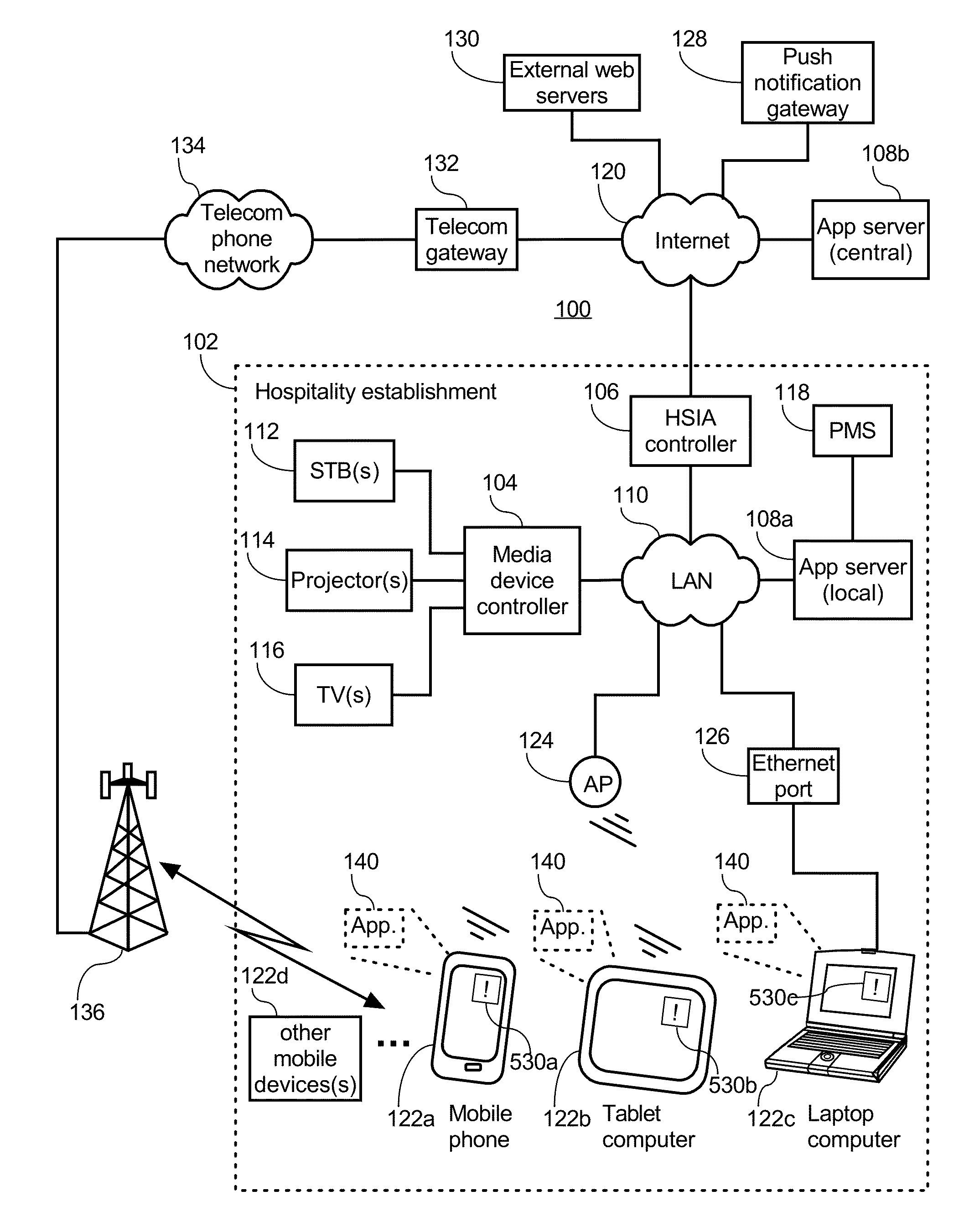
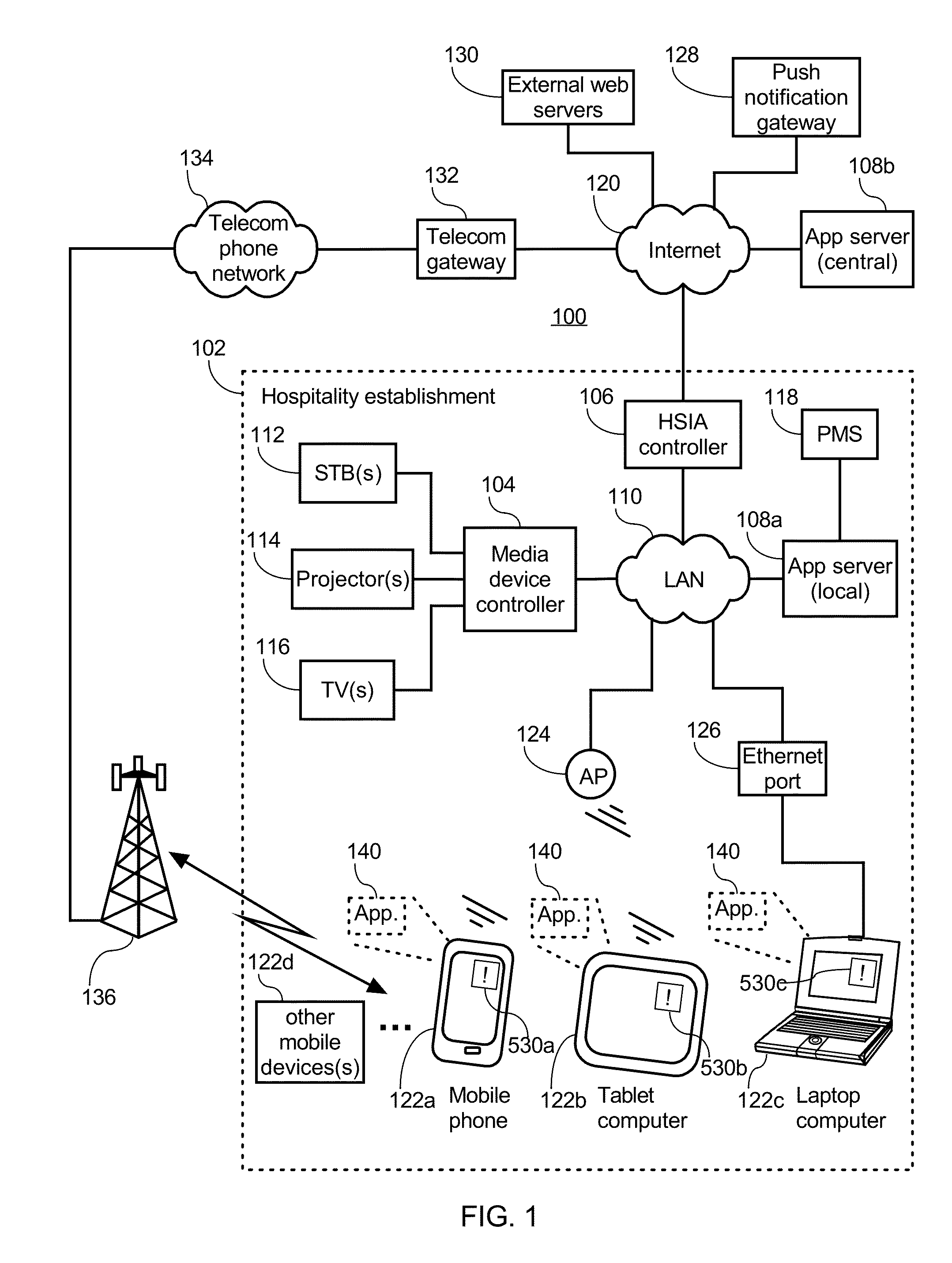
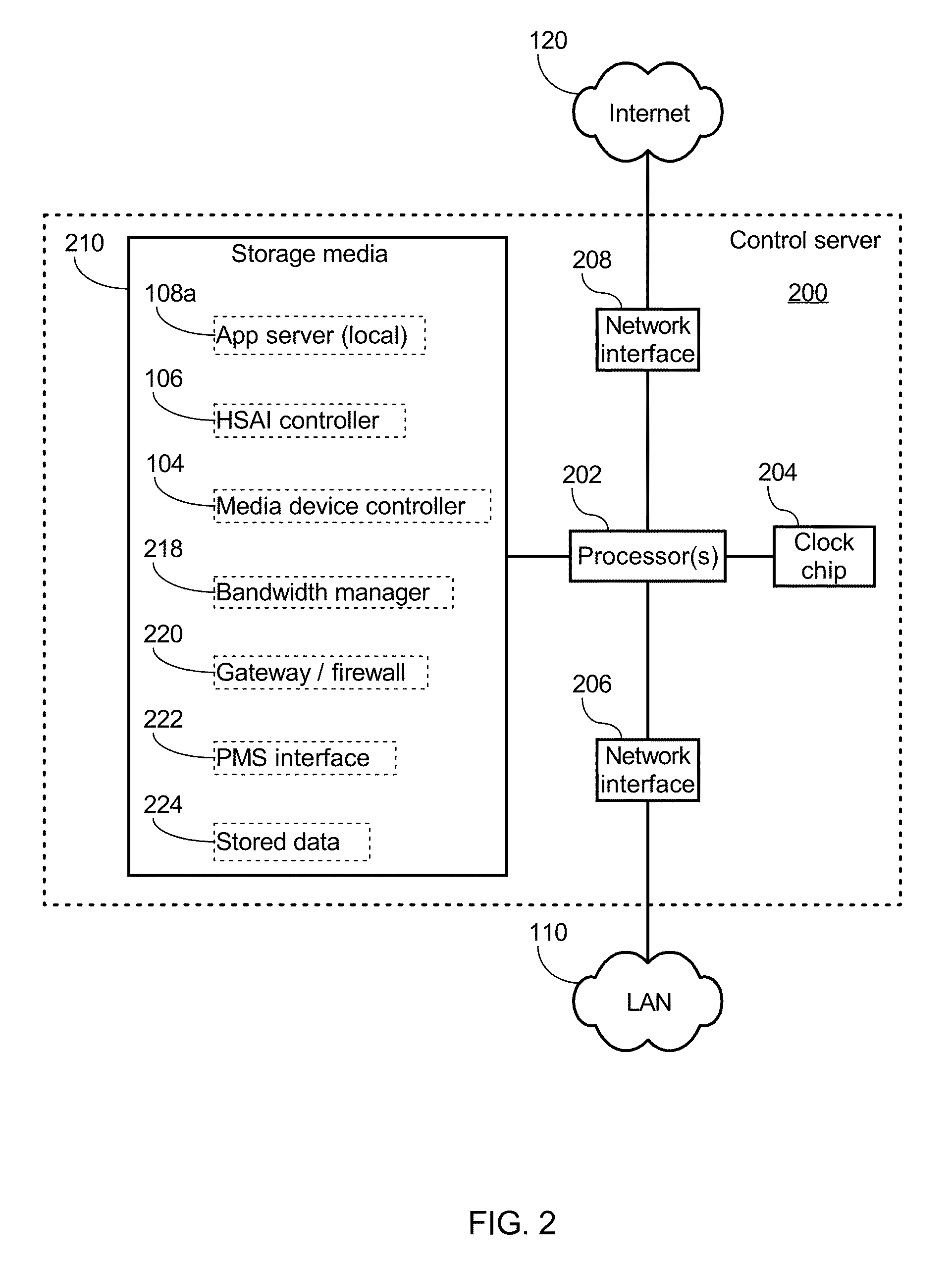
Event-triggered invitations to upgrade service offered by hospitality establishment
InactiveUS20150254726A1Good serviceRemove restrictionsService provisioningTransmissionDisplay deviceEvent triggered
An app server receives a device token from a software application on a mobile device. The device token identifies the mobile device for pushing notification messages of the software application to the mobile device via a push notification system. The mobile device is monitored while accessing the Internet in order to detect when the user may benefit from upgraded access to the Internet. The app server then sends one or more notification message(s) to the user such as by sending a message to the device token of the mobile device via the push notification system or to a display device associated with the user at the hospitality establishment. The notification message invites the user to upgrade their Internet access. The push notification system alerts the user to the notification message via the user interface of the mobile device even when the software application is not running on the mobile device.
Owner:GUEST TEK INTERACTIVE ENTERTAINMENT
Enforcing secure internet connections for a mobile endpoint computing device
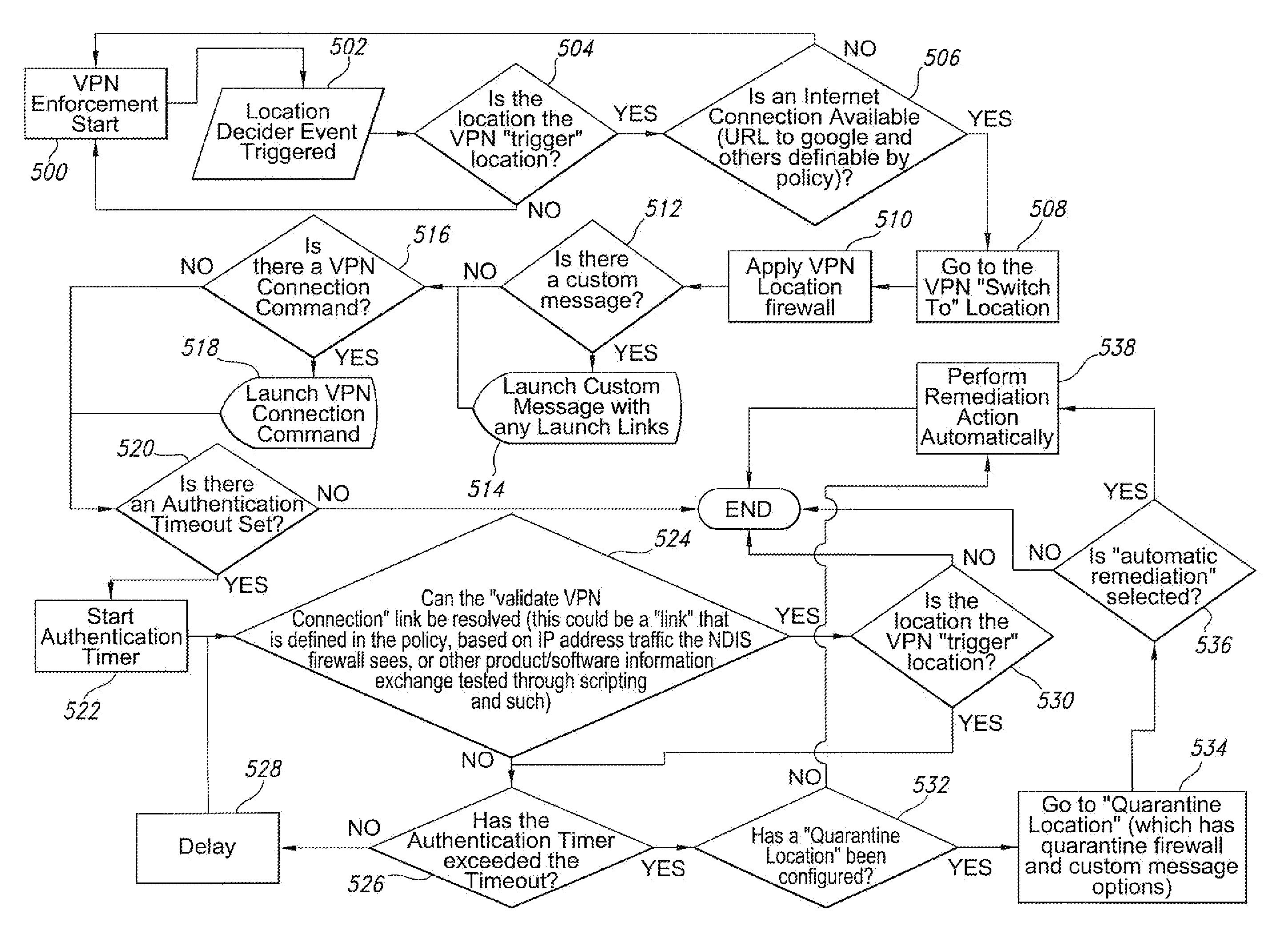
ActiveUS20100293610A1Low implementation costLow costComputer security arrangementsMultiple digital computer combinationsTraffic capacityTTEthernet
Methods and apparatus enforce a secure internet connection from a mobiles endpoint computing device. A security policy for the endpoint is defined based on its location. From that location, an internet connection is established and detected. This event triggers the launching of a full VPN tunnel connection including an NDIS firewall forcing packet traffic through a port of the endpoint computing device assigned by the security policy and / or MAC / IP addresses of a VPN concentrator. Thereafter, the packet traffic is monitored for compliance with the security policy. This includes determining whether packet traffic over the assigned port is observed within a given time or packet traffic is attempted over other ports. Monitoring occurs whether or not the protocol of the VPN tunnel connection is known. Other features contemplate quarantining for improper operation of the VPN tunnel, undertaking remediation, and computer program products, to name a few.
Owner:MICRO FOCUS SOFTWARE INC
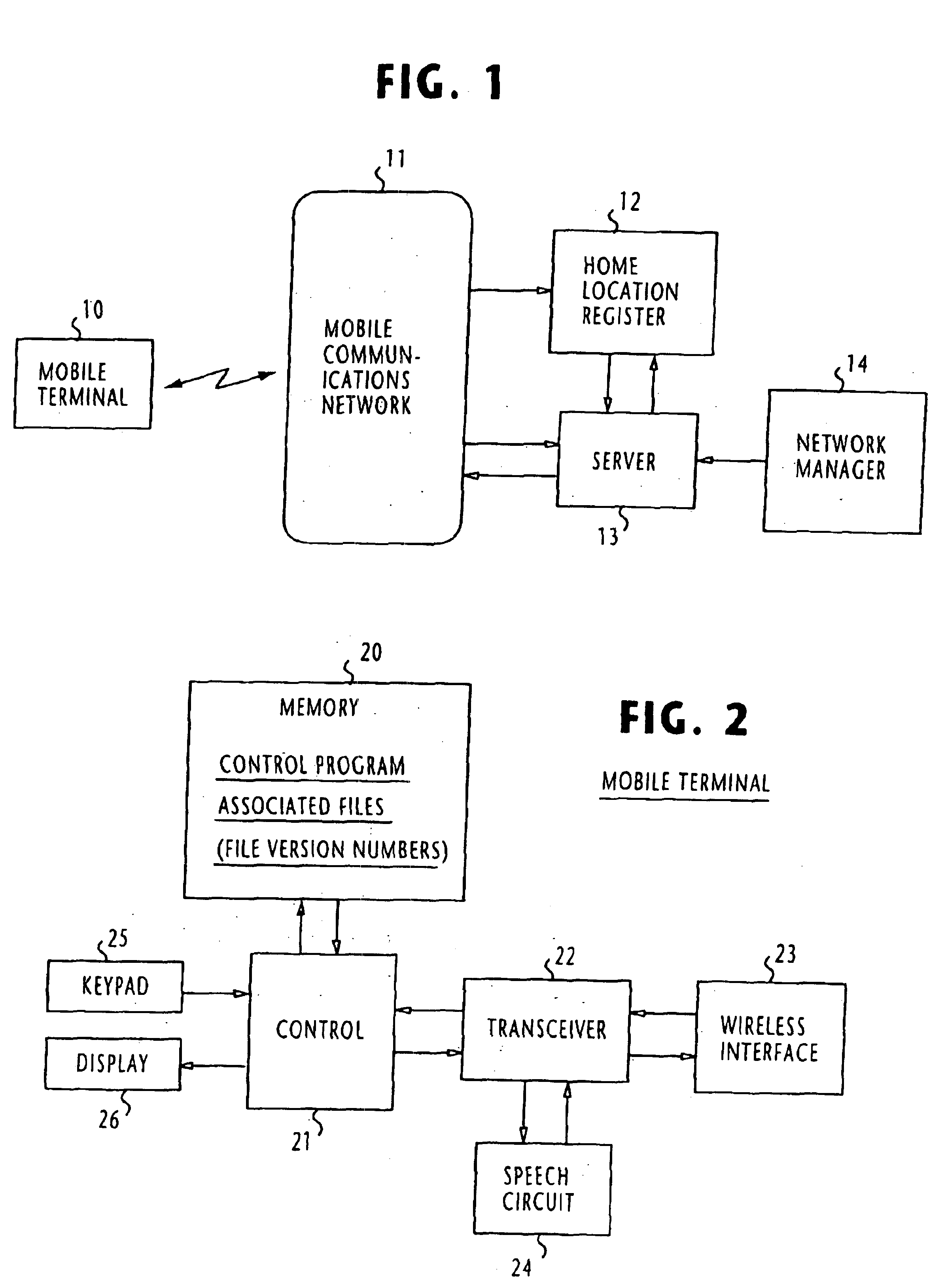
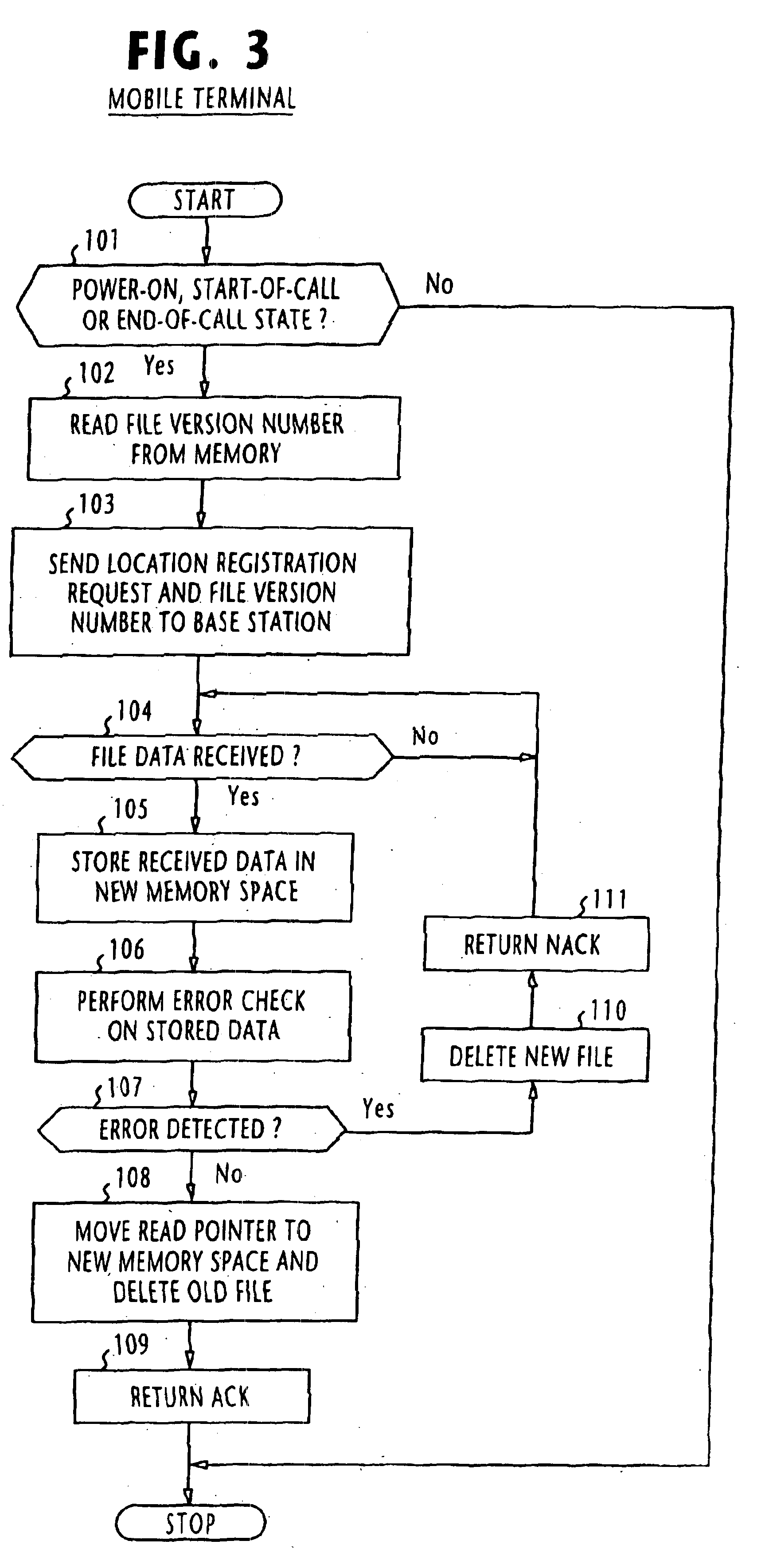
Method of updating client's installed data in response to a user-triggered event
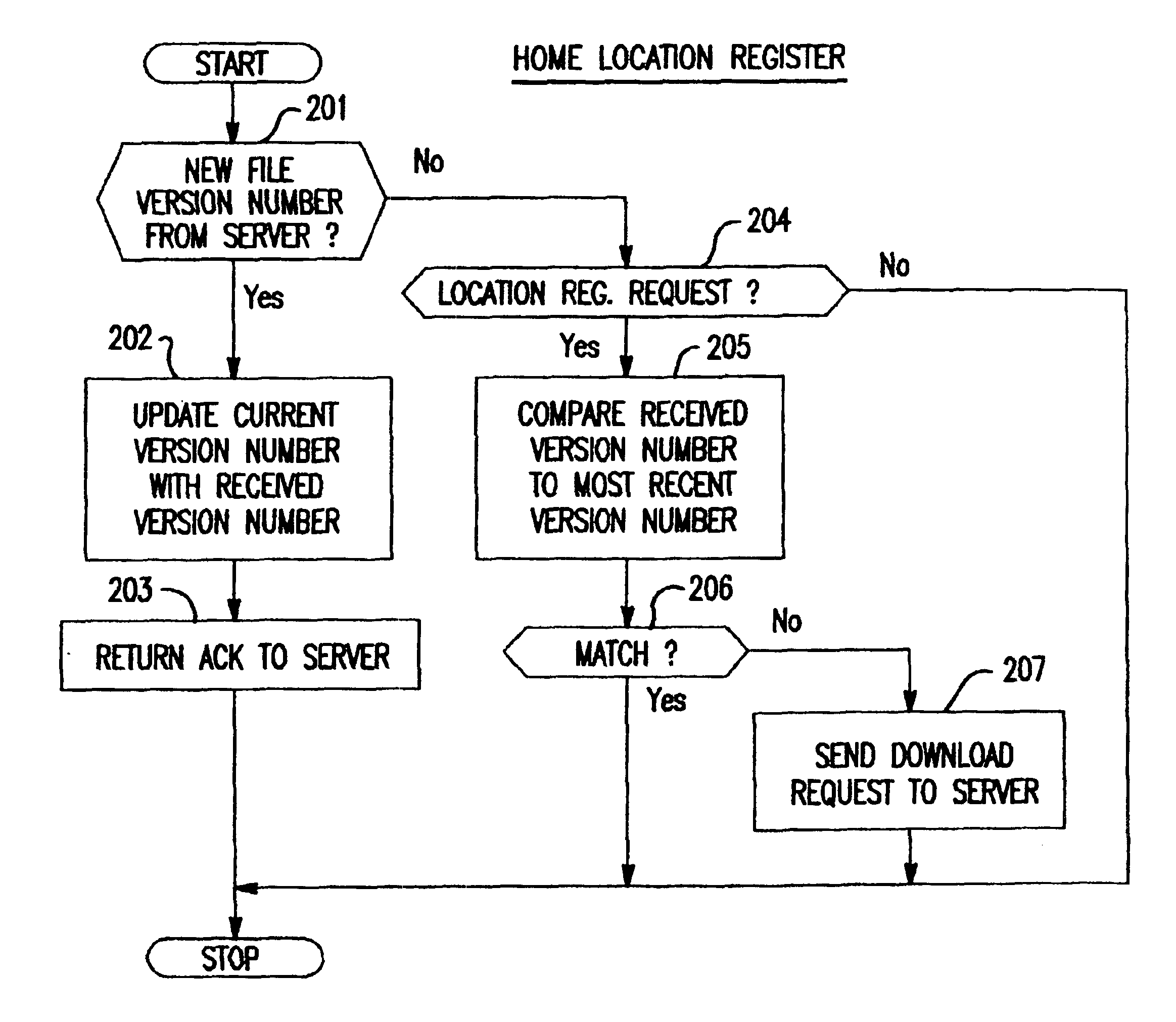
InactiveUS6877037B1Efficient methodData processing applicationsProgram control using stored programsComputer terminalEvent triggered
A client terminal, such as mobile terminal, stores a version number of its installed data or control program and transmits a request message to the server system via a communication network in response to an event triggered by a user of the client terminal, the request message containing the version number of the data and a phone number of the client terminal. The server system stores most recent data and a version number of the most recent data. When the server system receives the transmitted request, it compares the version number contained in the received request to the stored version number and transmits a copy of the most recent data and the version number of the most recent data to the client terminal via the communication network if there is a mismatch between the compared version numbers. The client terminal receives the copy of the most recent data and the version number from the server system and updates the installed data with the received copy and updates the stored version number with the received version number.
Owner:NEC CORP
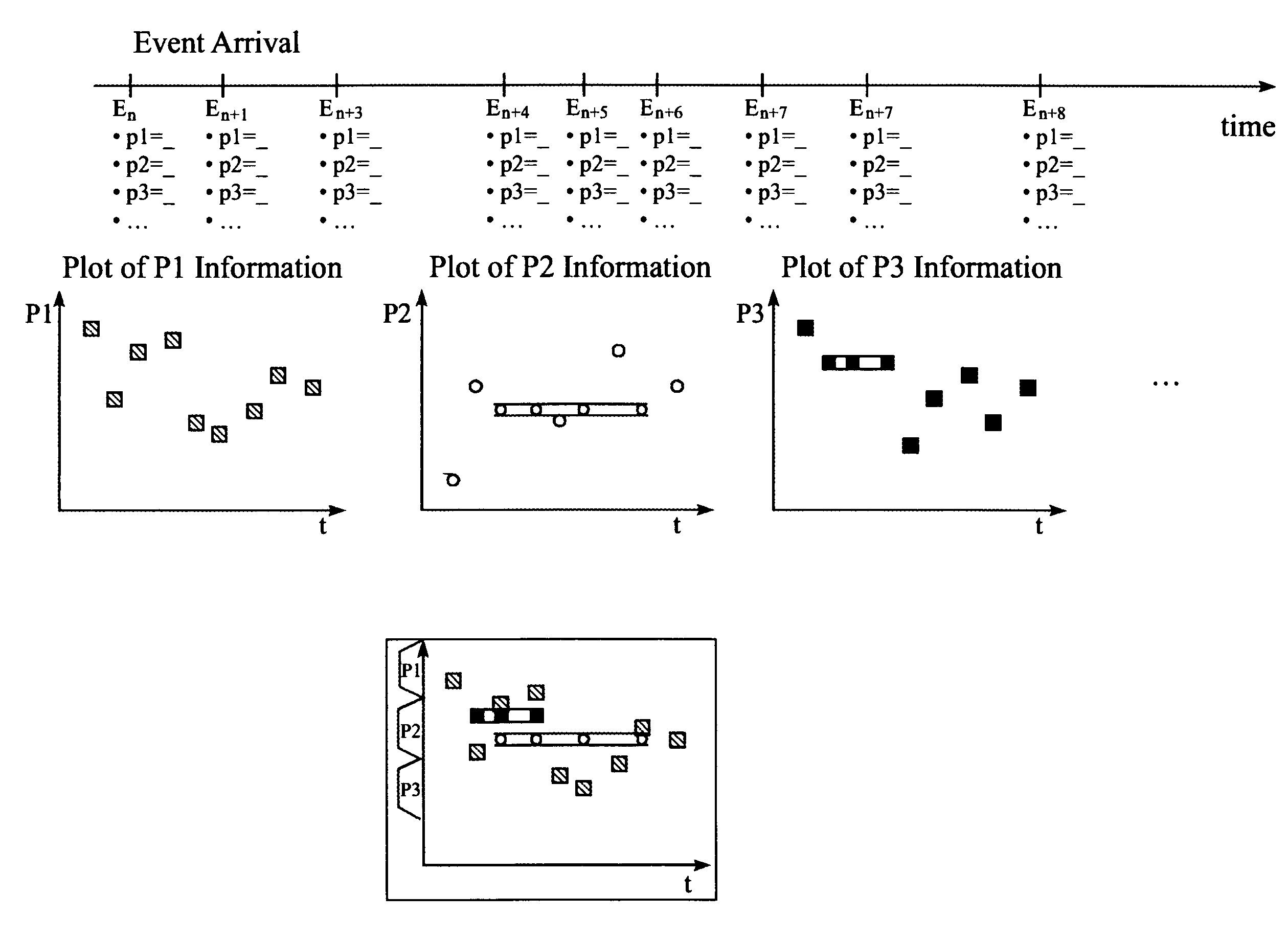
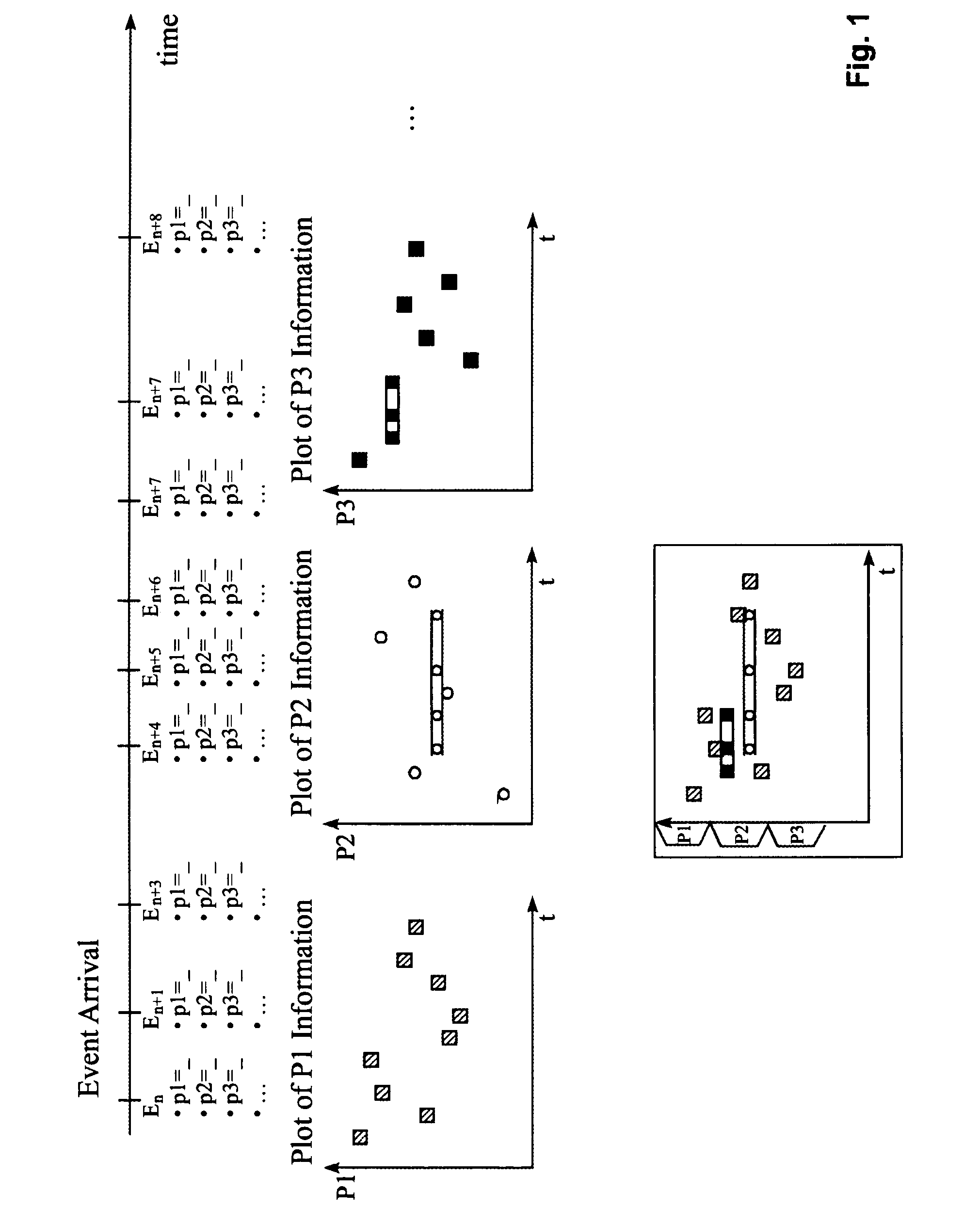
Monitoring events in a computer network
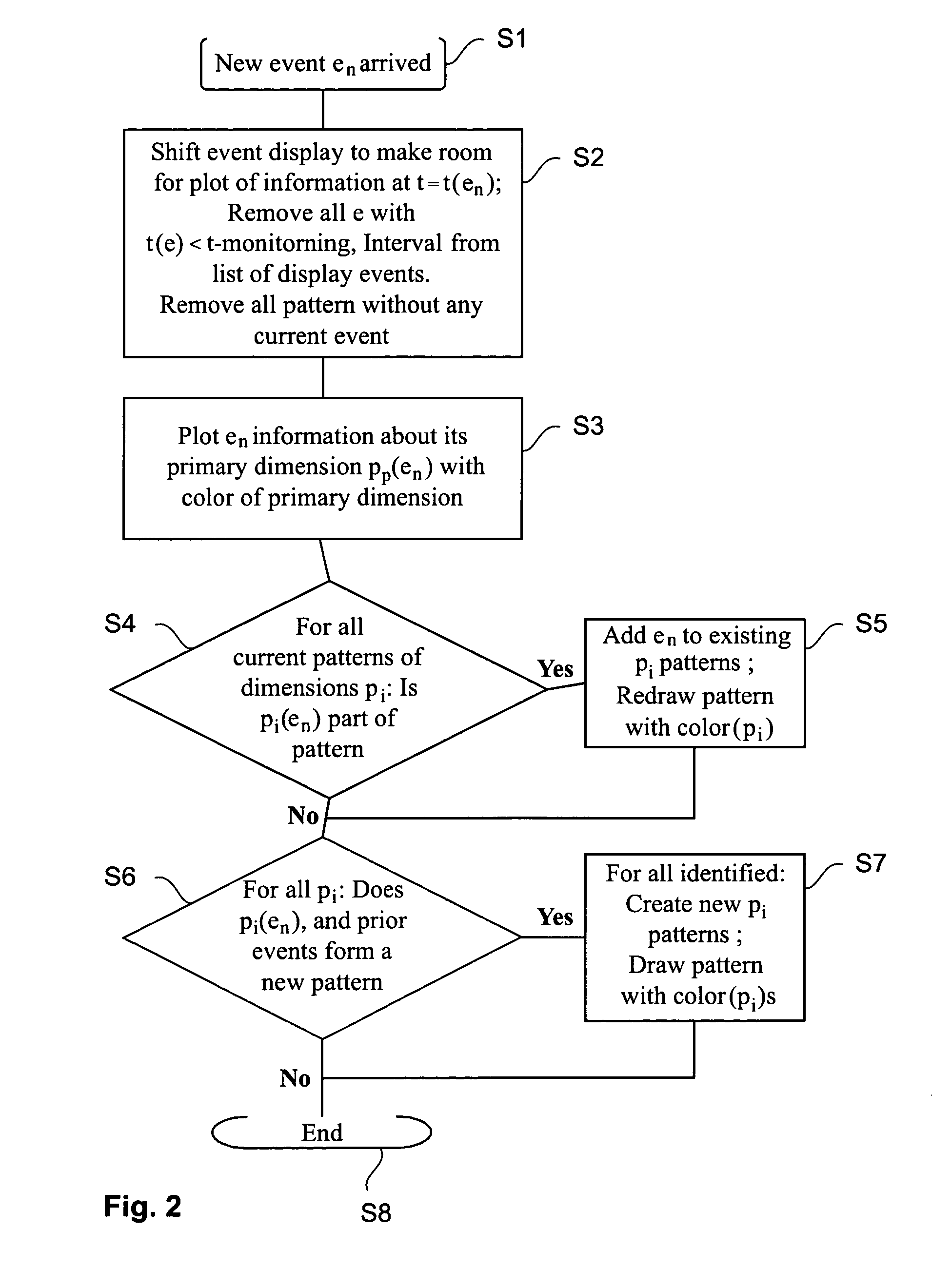
ActiveUS7324108B2Easy to switchQuick displayDrawing from basic elementsData processing applicationsMapping algorithmEvent triggered
Monitoring events triggered by a computer network. Each event being provided with attribute values allocated to a given set of attributes, and providing an event display, determining a primary attribute and a corresponding display label of the events selected from the given set of attributes presented with attribute values on a cross plot, providing a pattern algorithm to detect whether an arrived event is part of a given pattern, providing a mapping algorithm to map attribute values on the cross plot, allocating a second display label to the events indicating the attributes uncovered as part of the given pattern, plotting events arriving and including an attribute value allocated to a primary attribute into the cross plot, and plotting events arriving within the time period and detected by the pattern algorithm as part of the given pattern into the cross plot with the second display label indicating the given pattern.
Owner:TREND MICRO INC
System and method for correlating events in a pluggable correlation architecture
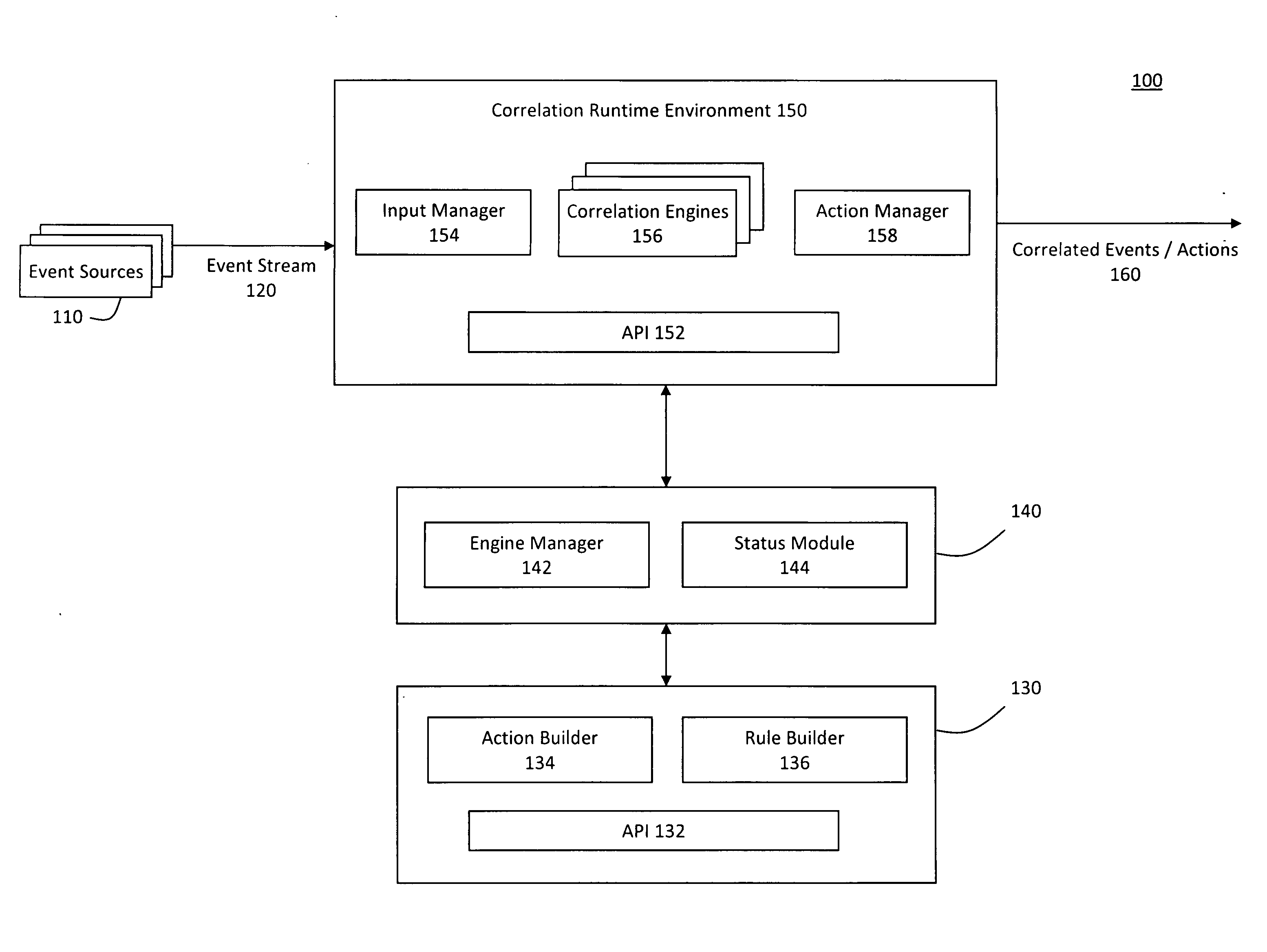
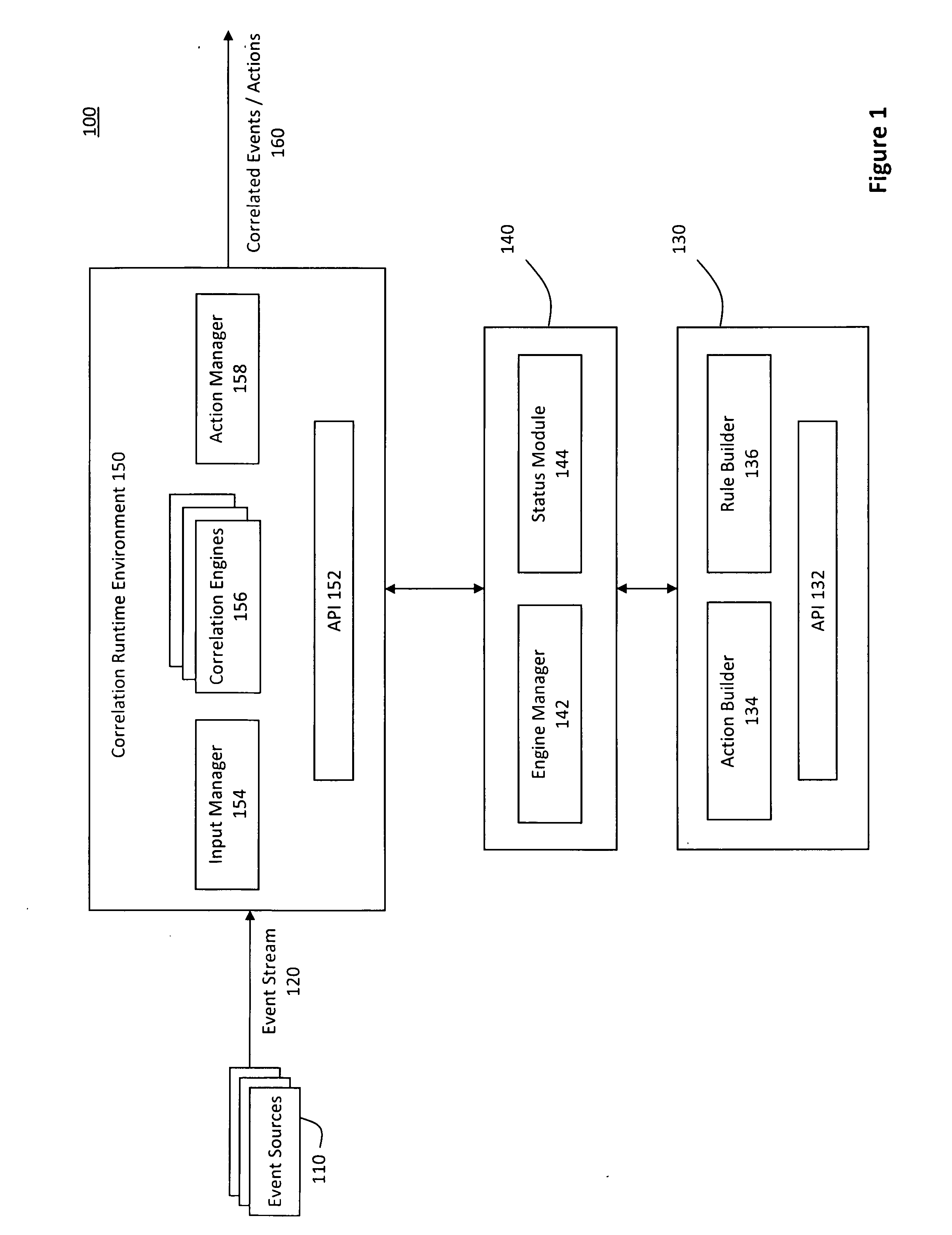
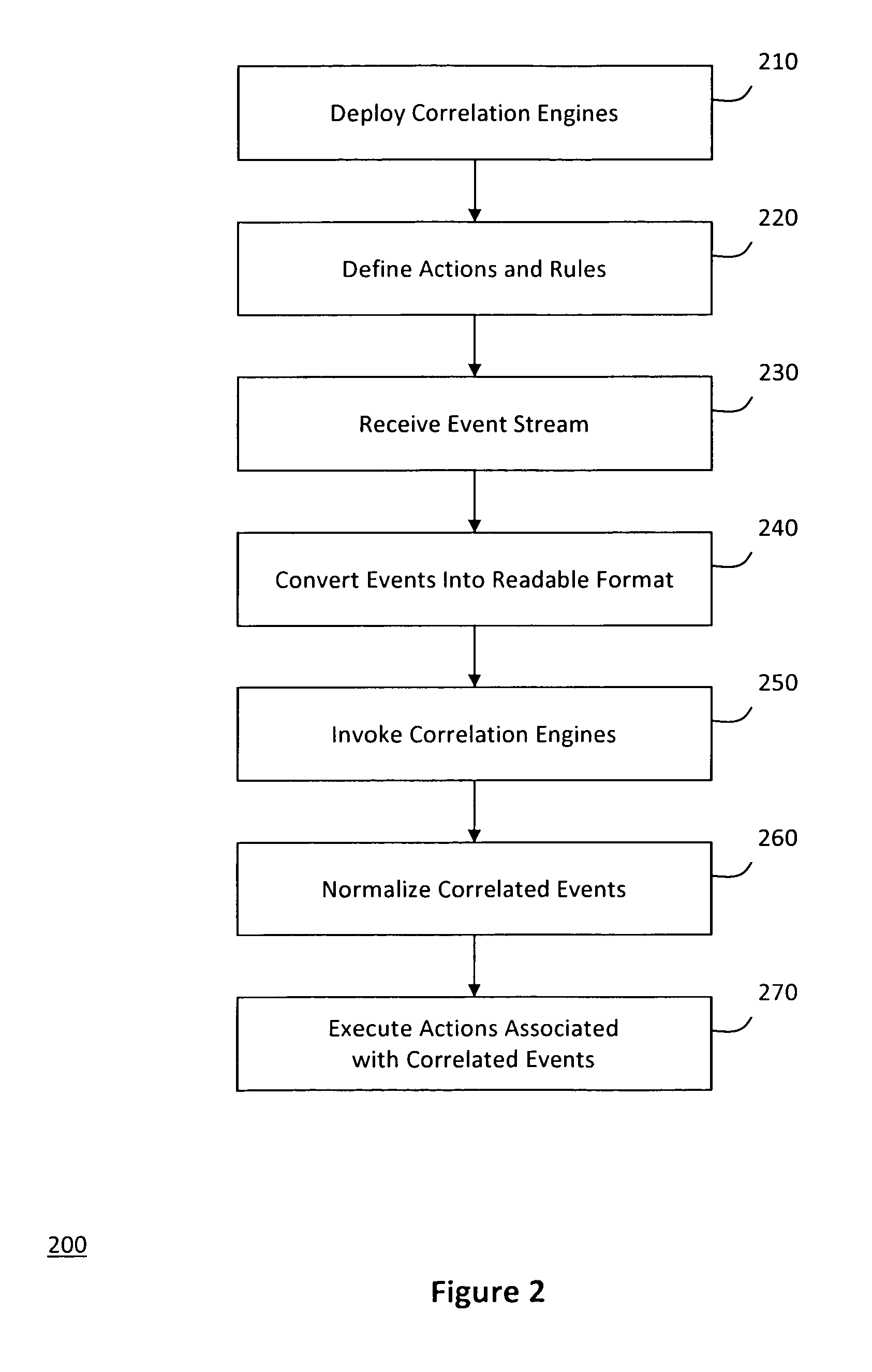
ActiveUS20090265288A1Improve incident managementImprove remediationKnowledge representationSpecial data processing applicationsRemedial actionEvent triggered
A system for pluggable event correlation may include an input manager that receives a plurality of events and converts the events into a format compatible with one or more of a plurality of correlation engines. The correlation engines may then evaluate the converted events using various rules and generate correlated events when the evaluated events trigger at least one of the rules. An action manager may execute remedial actions when the correlation engines generate the correlated events. Moreover, extensibility may be provided by enabling a user to define rules to be triggered when events occur in a predetermined pattern, and actions to be executed when a predetermined rule triggers a correlated event. Further, to plug a new correlation engine into the system, adapters may be deployed to handle input and output, while the user-defined rules may be validating according to semantic requirements of the new correlation engine.
Owner:EMC IP HLDG CO LLC
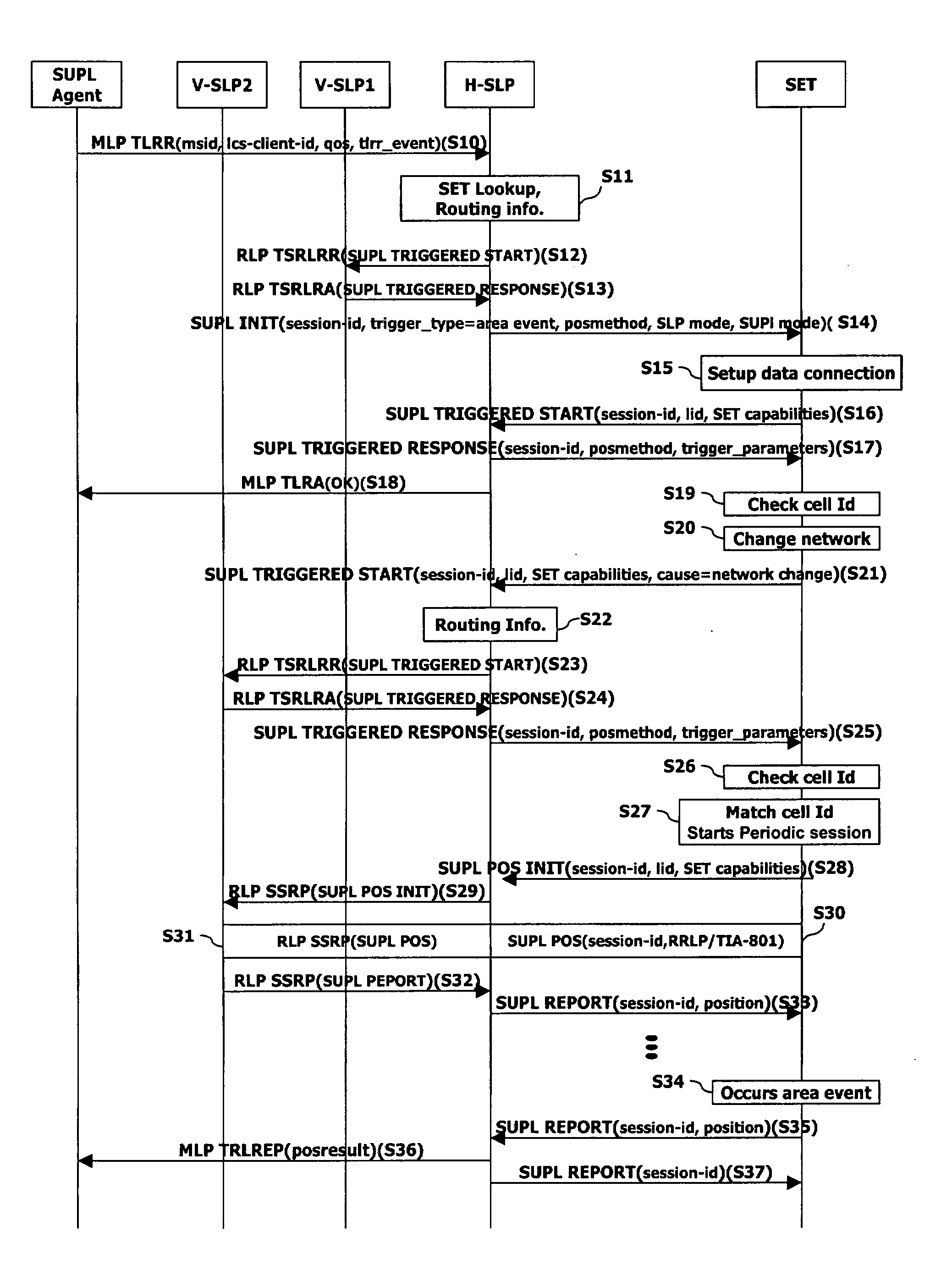
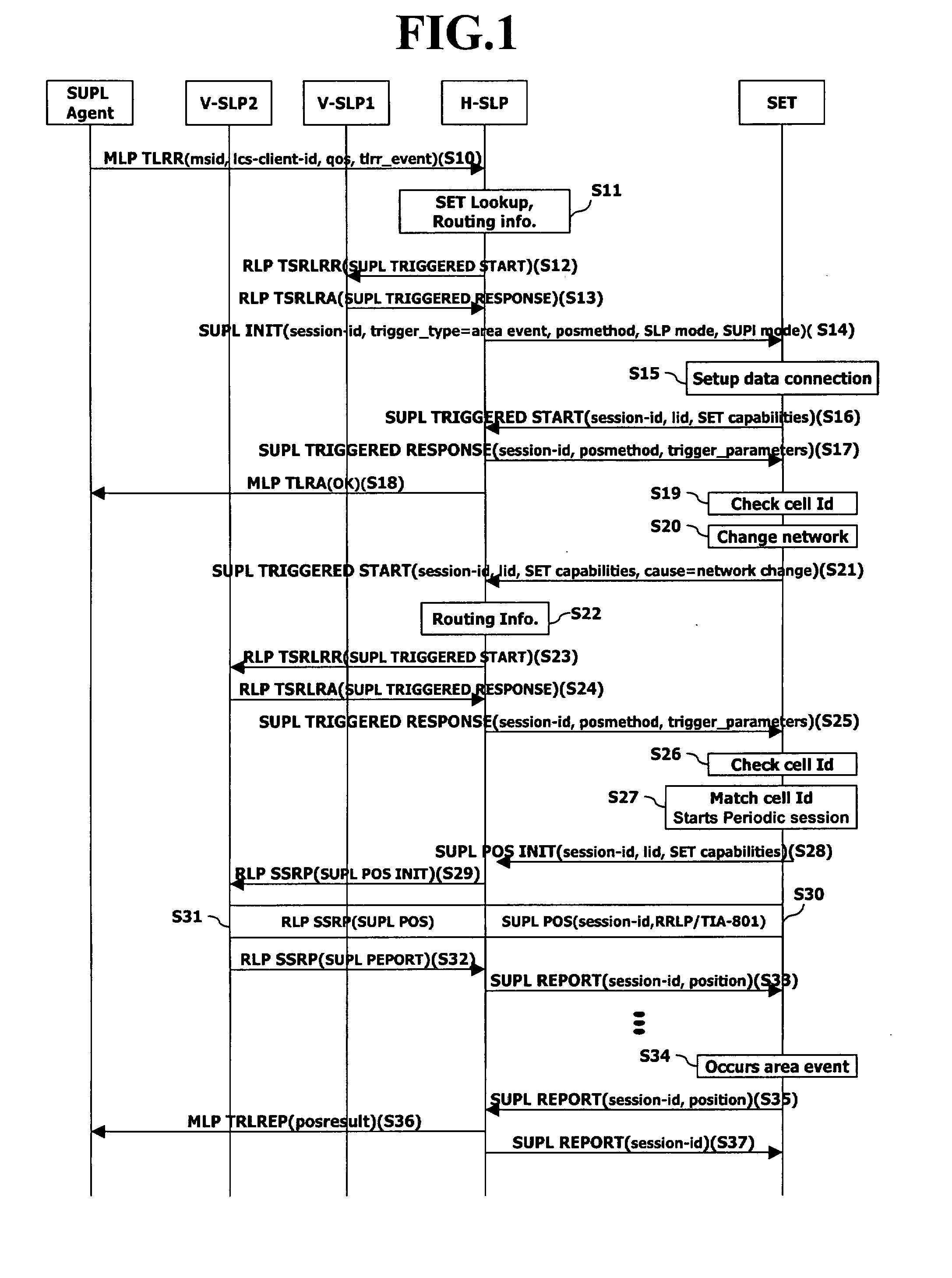
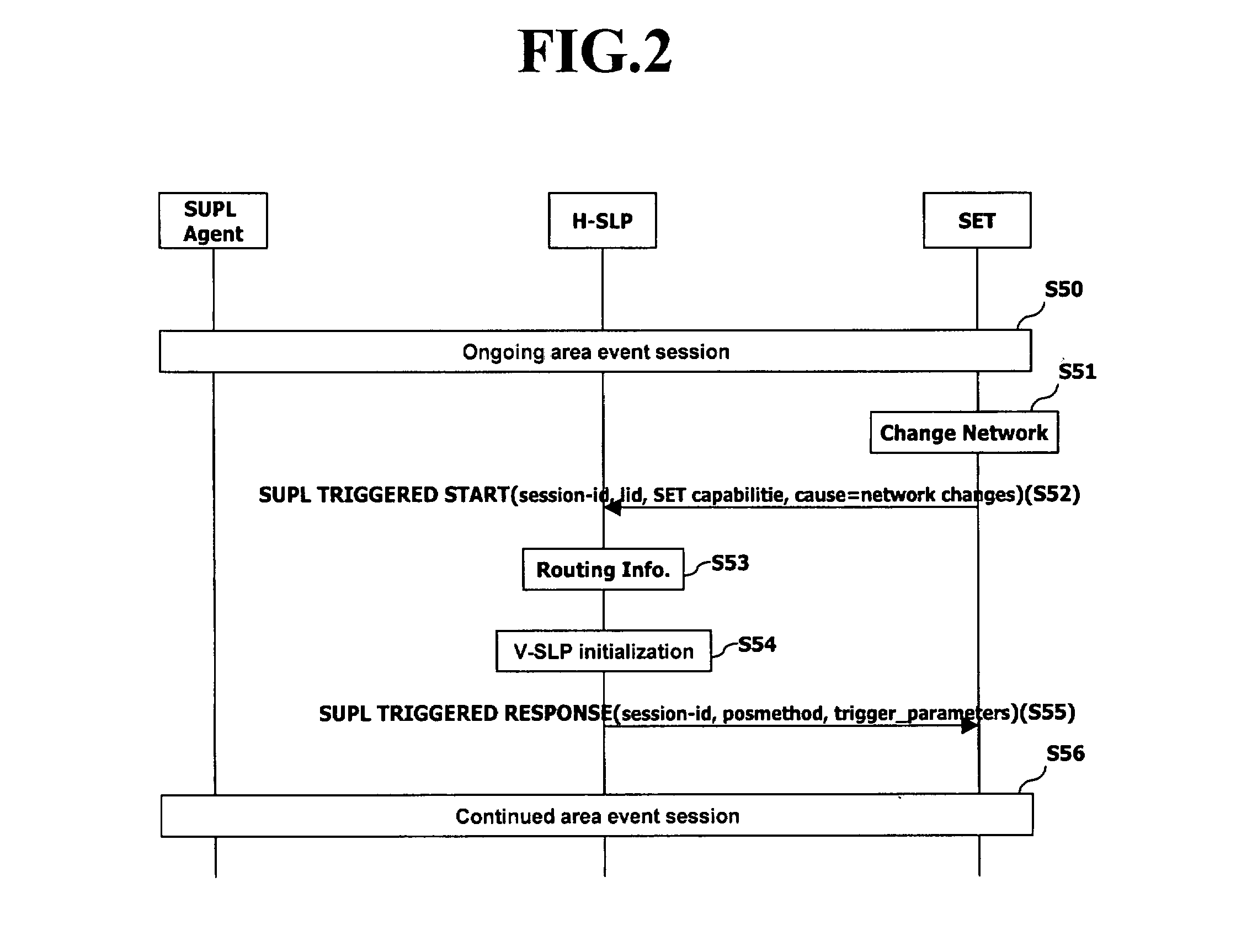
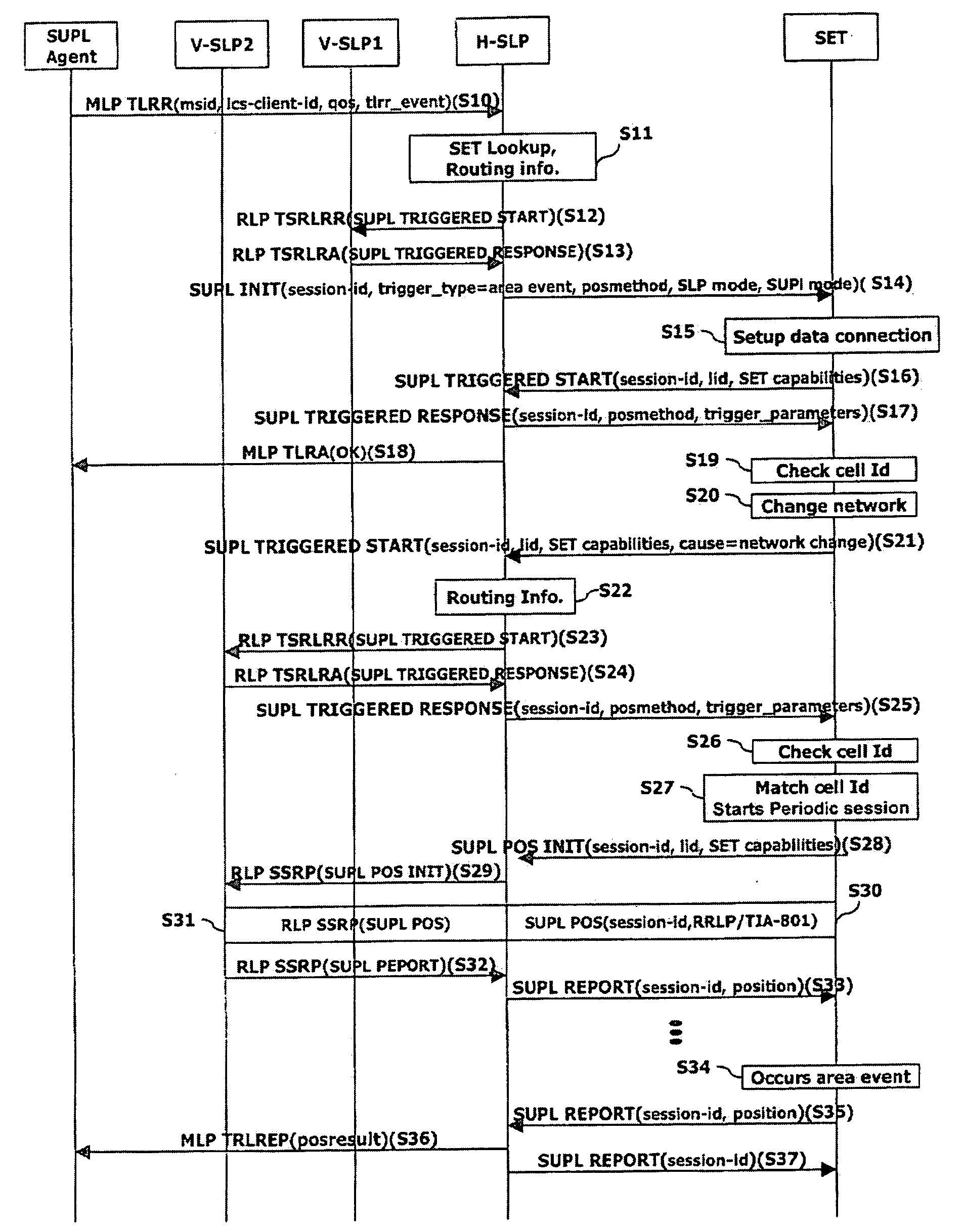
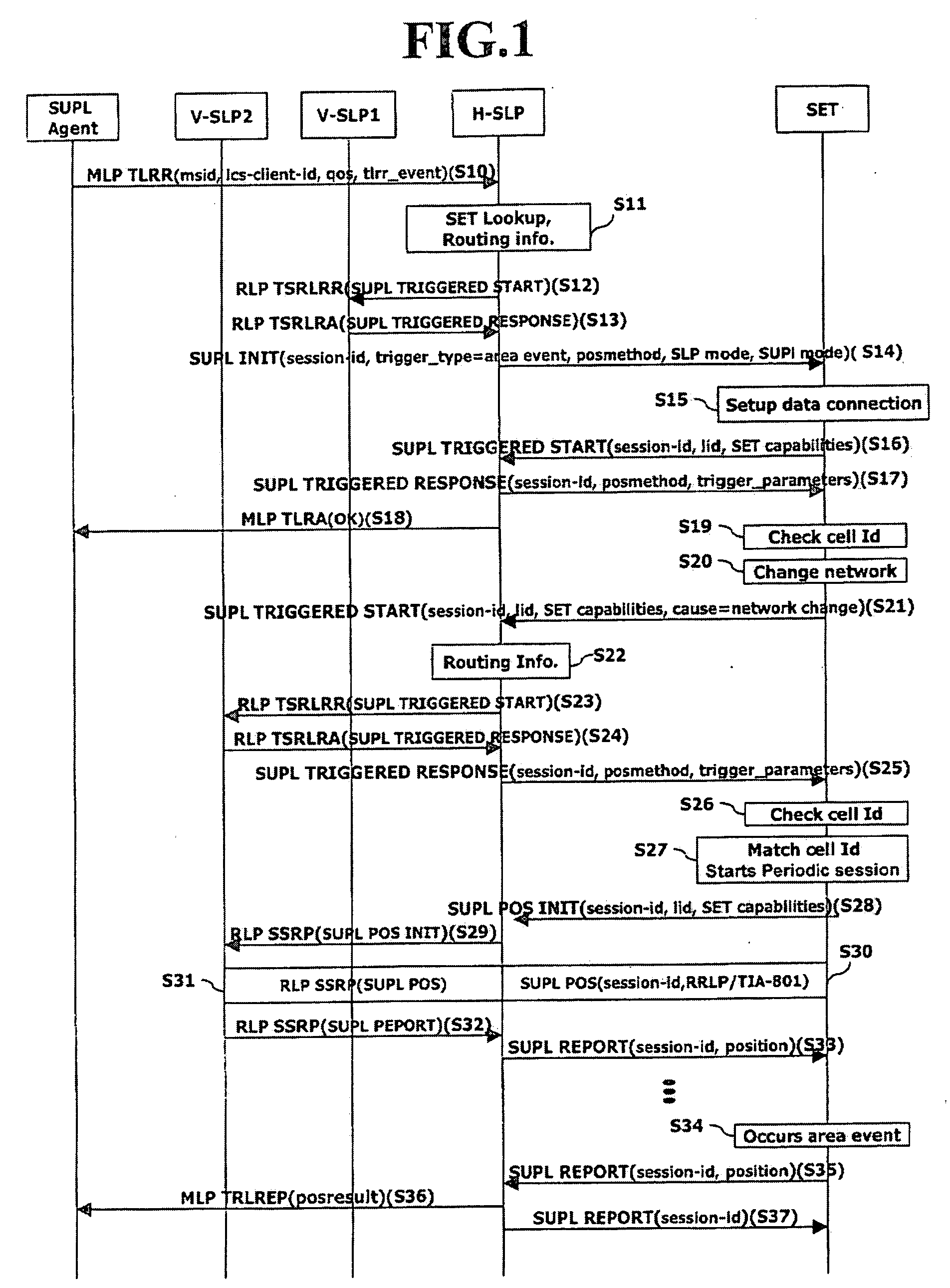
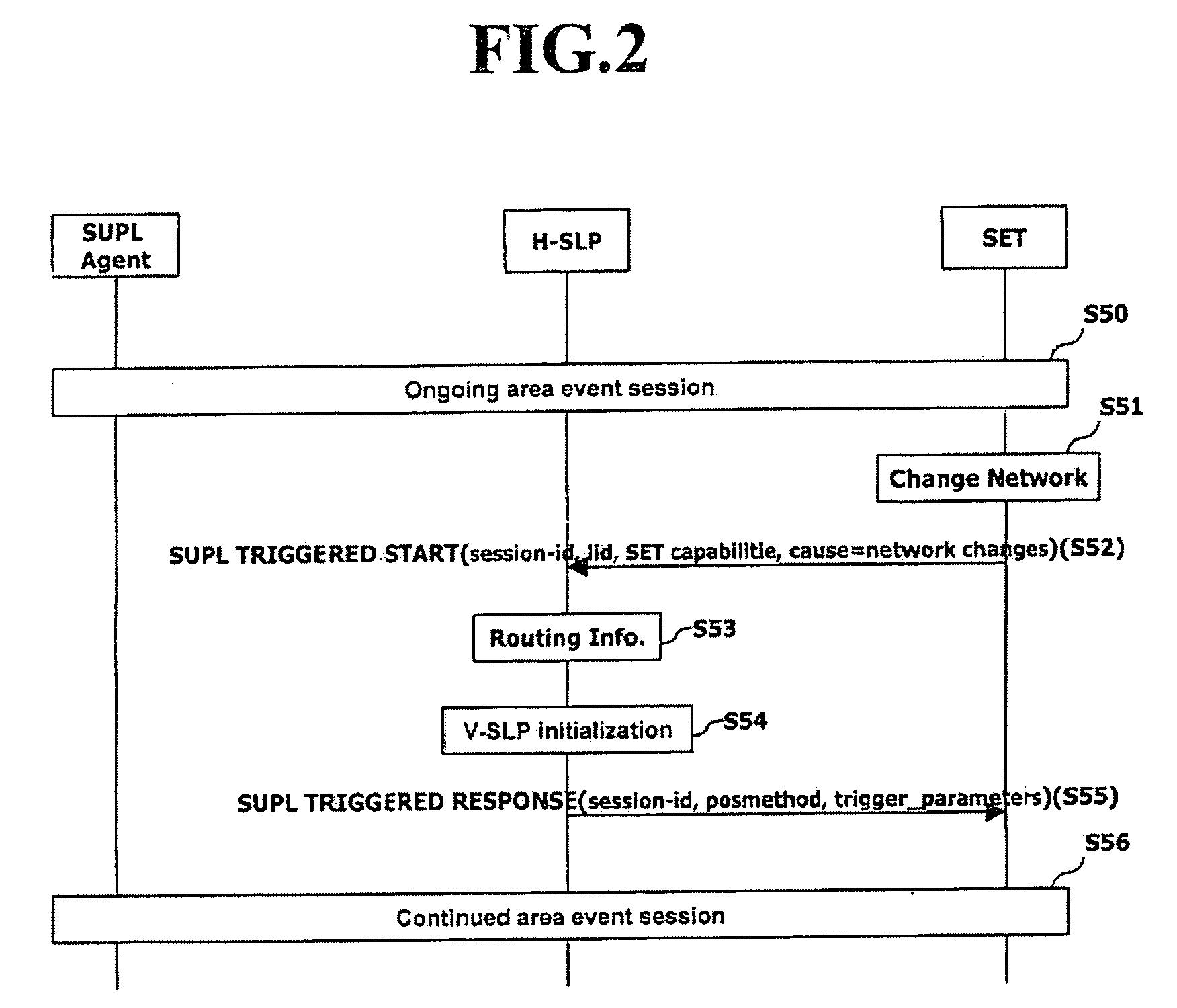
Location positioning method in handover between networks
ActiveUS20070243885A1Efficient executionServices signallingRadio/inductive link selection arrangementsEvent triggeredFamily network
Disclosed is a location information system based upon a SUPL(Secure User Plane Location) architecture, and more particularly, to a location positioning method based on an area event in handover between networks. The method comprises: if a network is changed or if a terminal is outside of the coverage area of a serving network while an area event is ongoing, requesting, by the terminal, new event trigger parameters to a home network through a first message; determining, by the home network, a serving network of the terminal by using location identifier included in the first message; receiving, the home network, the location identifier of a target area for which the positioning is requested from the determined serving network; and transmitting, the home network, the new event trigger parameters including the area identifier to the terminal through a second message.
Owner:LG ELECTRONICS INC
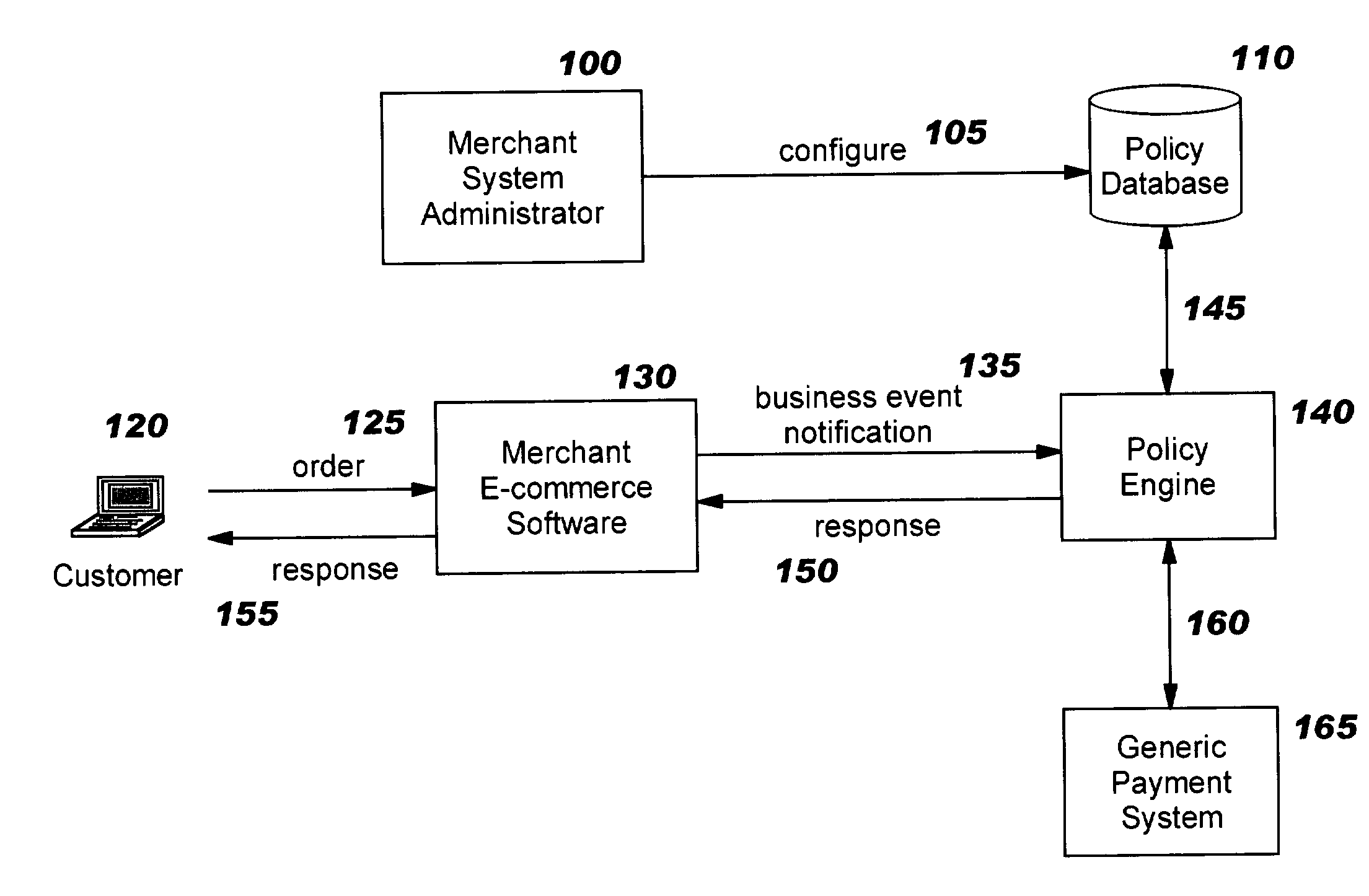
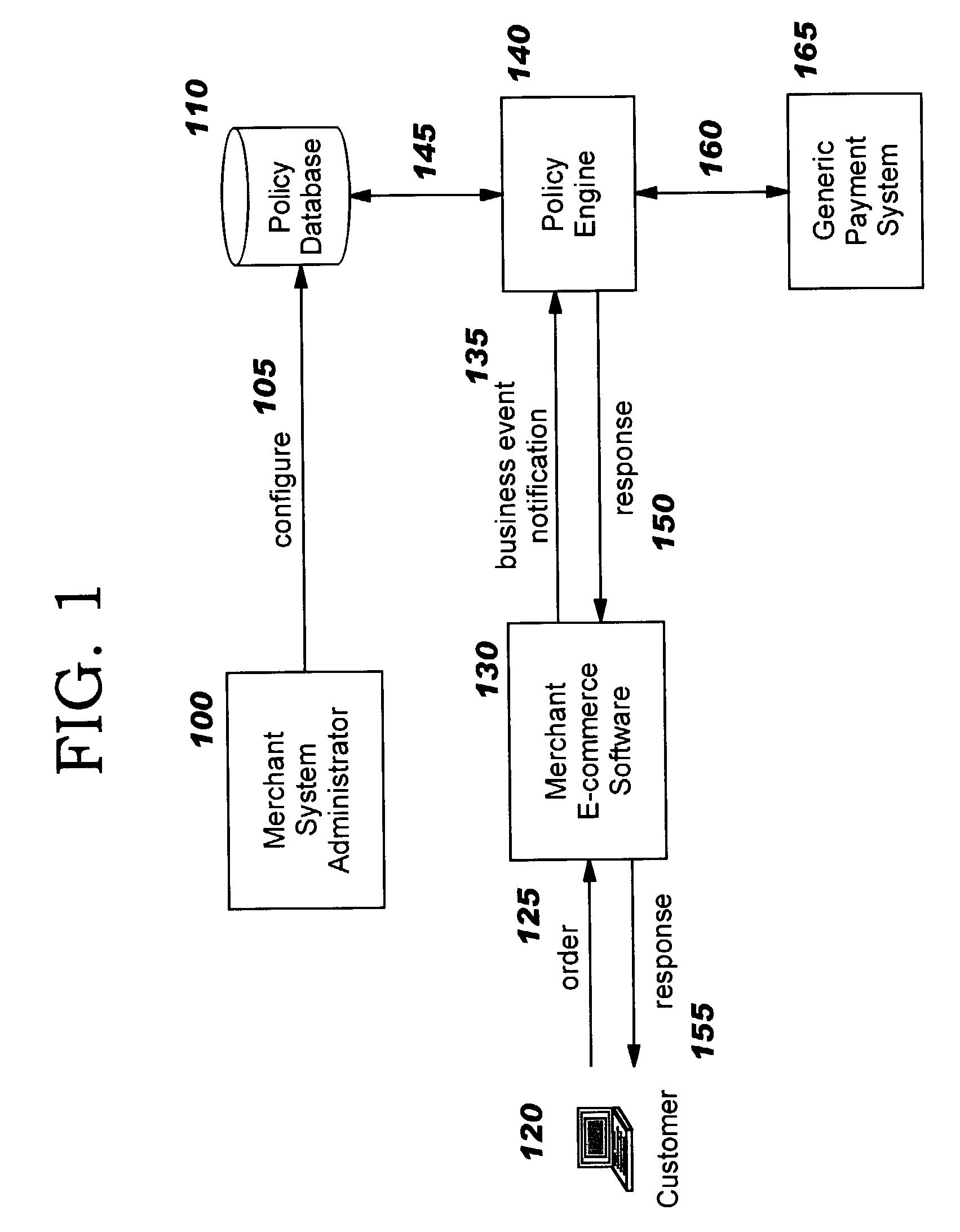
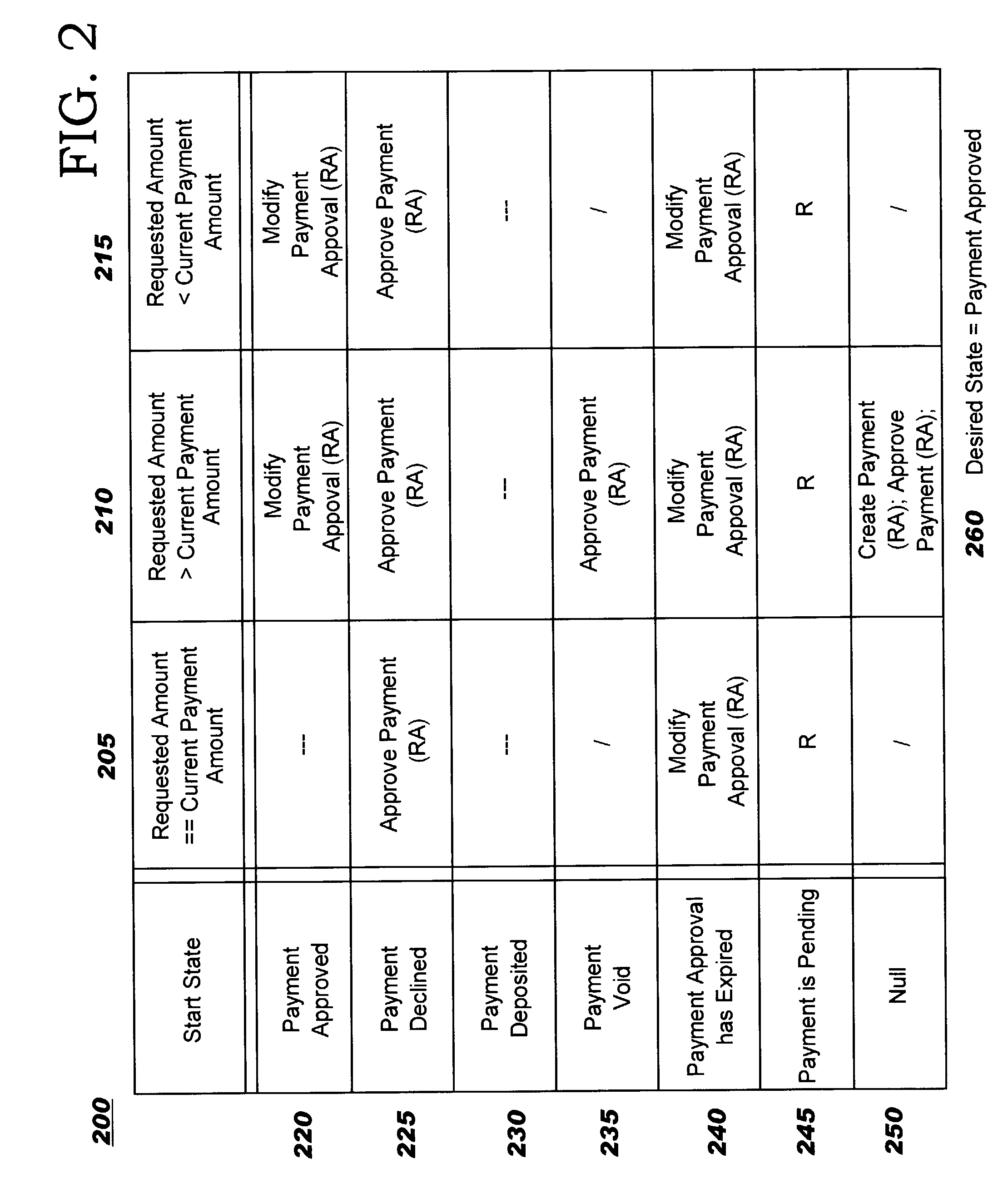
Business event triggered, policy-driven payment management
Techniques are disclosed for using business events as triggers to drive payment processing for electronic commerce. As the business logic of a merchant's c-commerce software application reaches various stages that impact payment considerations, it issues a corresponding event notification. According to preferred embodiments, these event notifications are processed by a policy engine, which locates policy information or rules previously configured for that event. Actions are then carried out, based on the configured policy. The merchant e-commerce application is therefore shielded from the details of the underlying payment processing. New payment types can be provided, and existing payment types can be modified if necessary, by adding / modifying policies; the merchant's e-commerce application does not need to change. This event-driven model allows application developers to focus on creating software for the merchant's key business requirements, and makes it easier to maintain the software.
Owner:IBM CORP
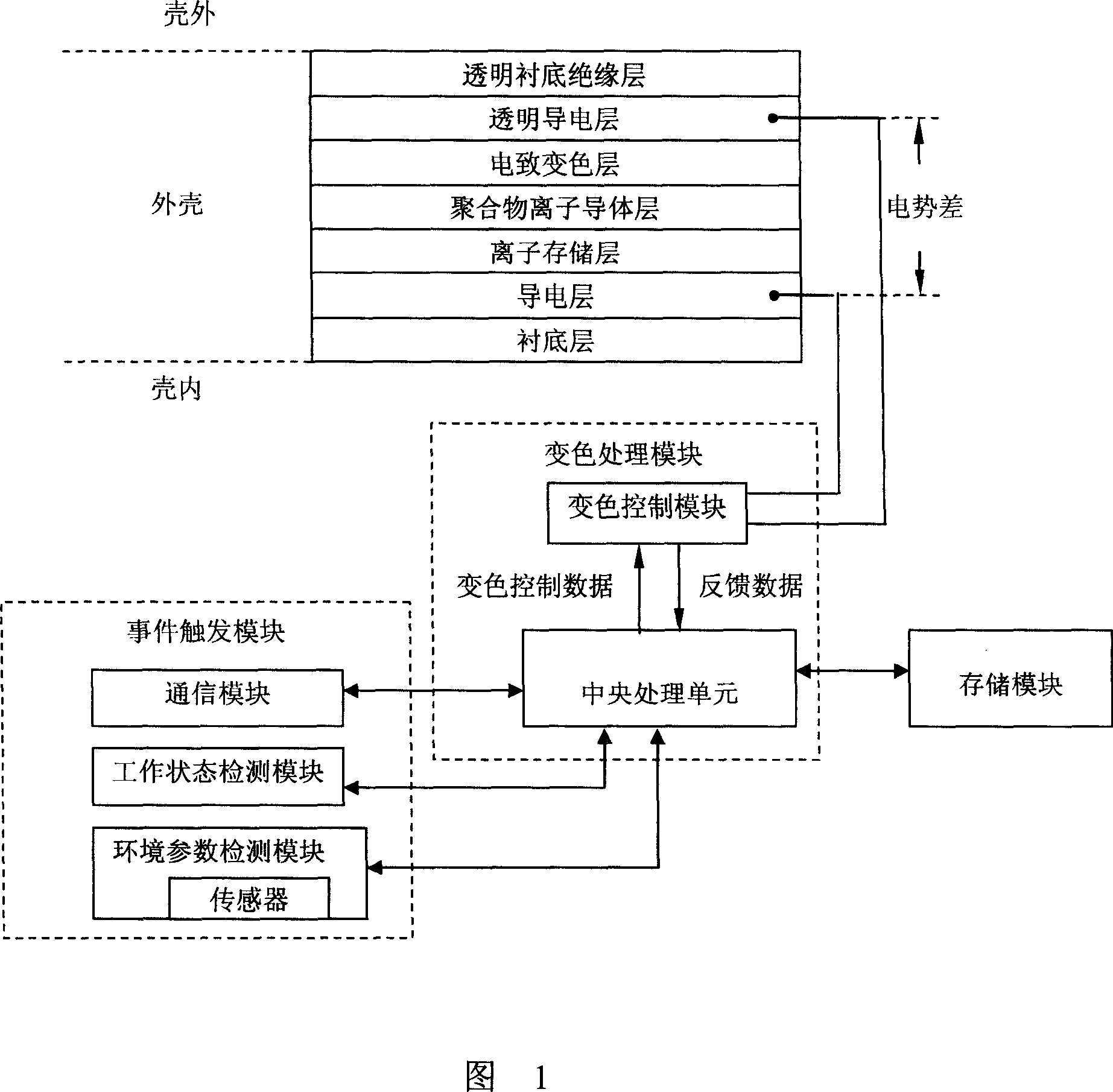
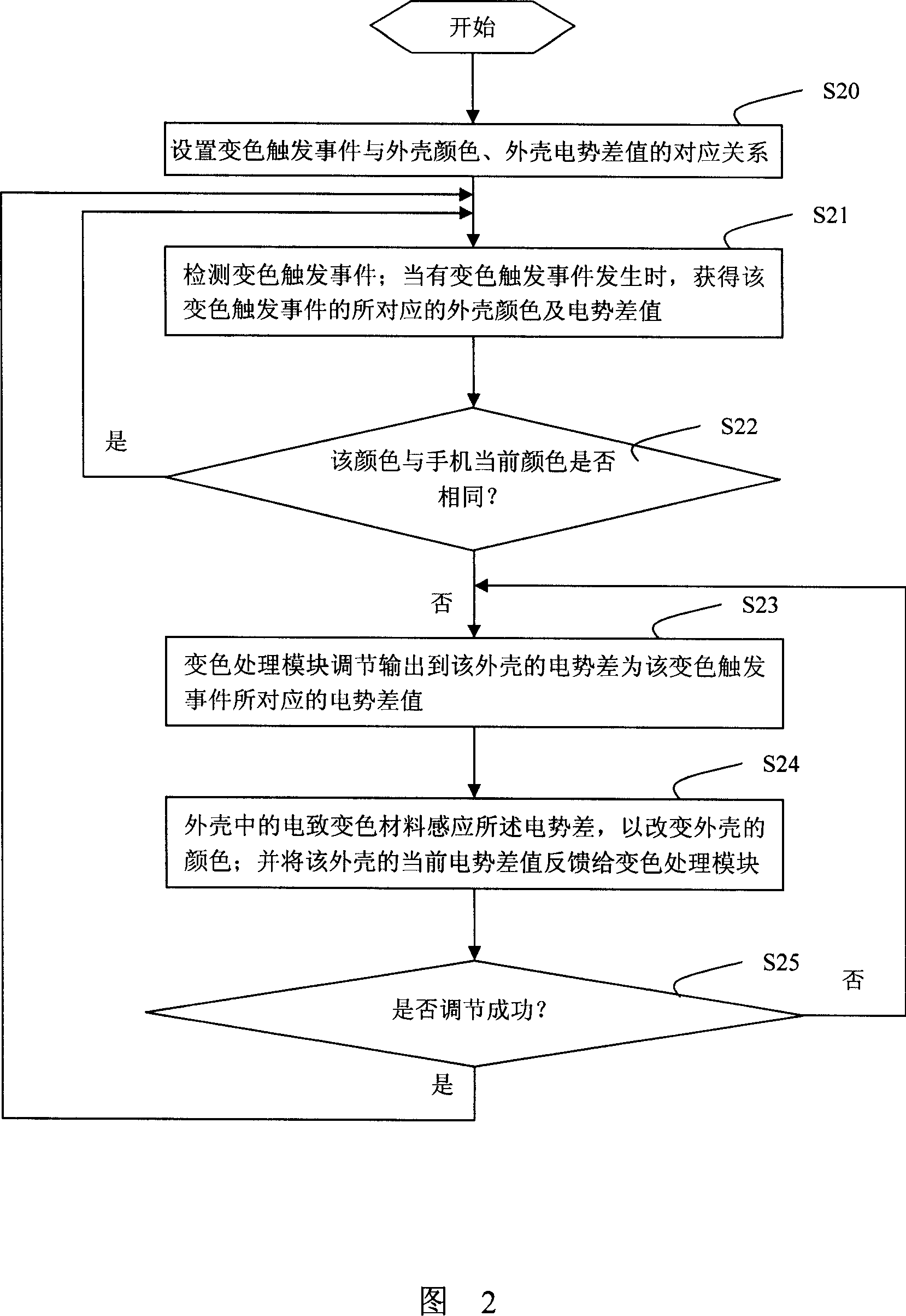
Electronic device and method for controlling electronic device casing coloring
InactiveCN101030161AImprove performanceAesthetic performanceHardware monitoringRadio/inductive link selection arrangementsElectricityComputer module
An electronic device is prepared as receiving discoloration trigger event by event trigger module and sending said event to discoloration processing module being used to obtain potential D-value corresponding to discoloration trigger event and being used to control potential D-value on shell to be corresponded shell potential D-value, setting electrochromism layer between partial shell and substrate and electric-connecting said electrochromism to discoloration processing module. The method for controlling shell discoloration of electronic device is also disclosed.
Owner:HUAWEI TECH CO LTD
Location positioning method in handover between networks
ActiveUS20080200182A1Efficient executionServices signallingRadio/inductive link selection arrangementsEvent triggeredHandover
Disclosed is a location information system based upon a SUPL (Secure User Plane Location) architecture, and more particularly, to a location positioning method and terminal based on an area event in handover between networks. The method according to one embodiment includes: if a network is changed or if a terminal is outside of the coverage area of a serving network while an area event is ongoing, requesting, by the terminal, new event trigger parameters to a home network through a first message; determining, by the home network, a serving network of the terminal by using location identifier included in the first message; receiving, the home network, the location identifier of a target area for which the positioning is requested from the determined serving network; and transmitting, the home network, the new event trigger parameters including the area identifier to the terminal through a second message.
Owner:LG ELECTRONICS INC
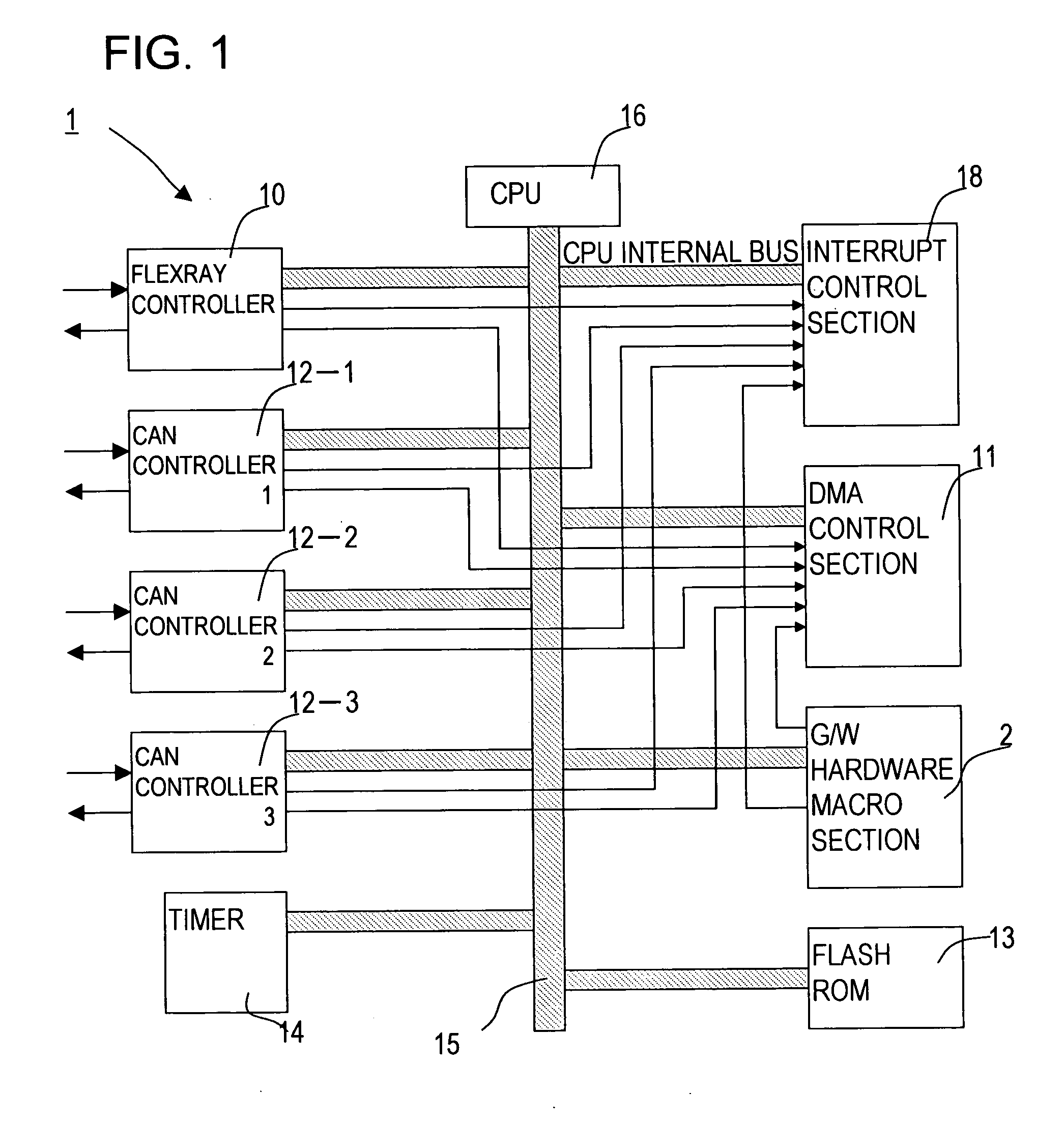
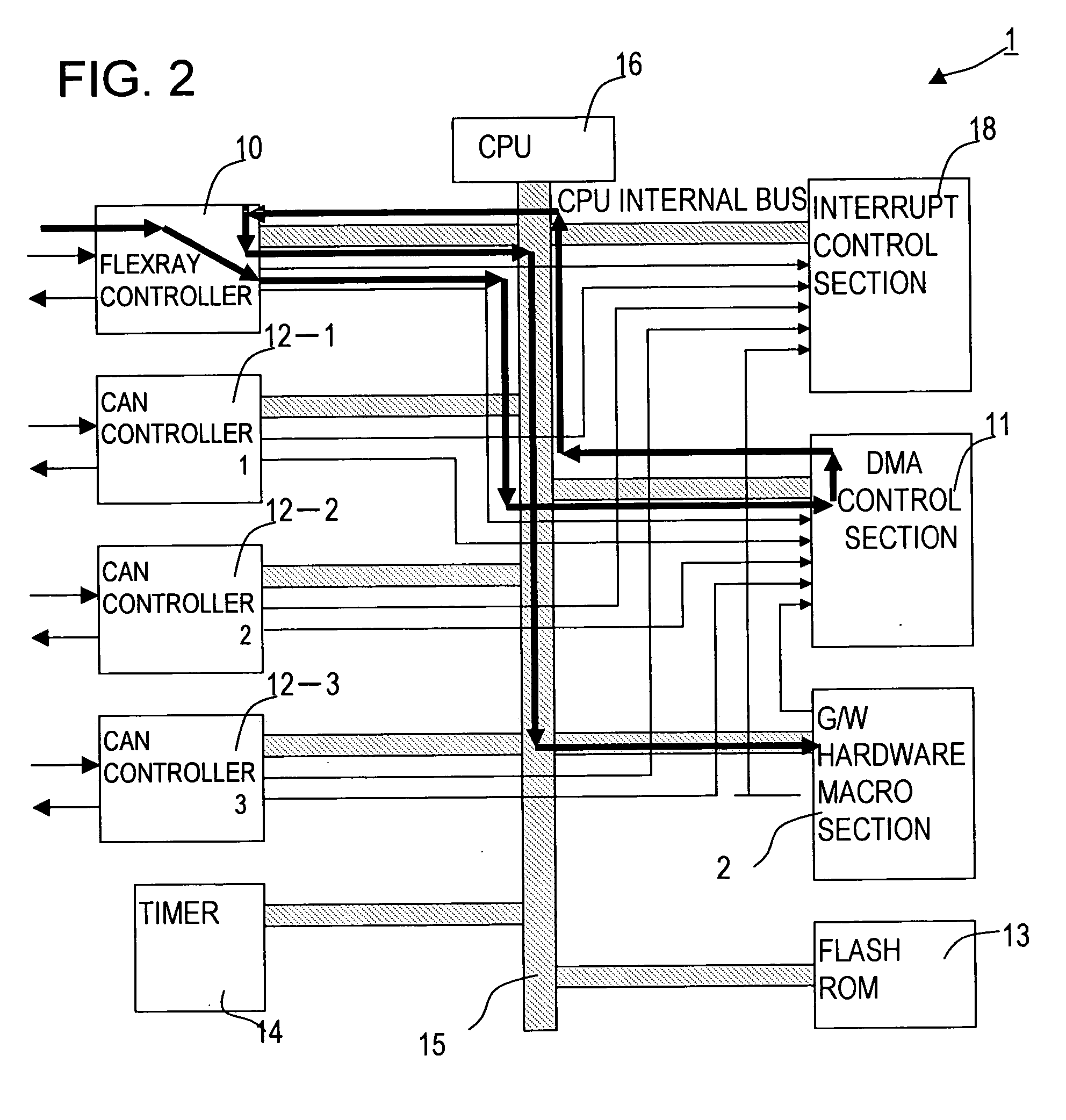
Communication message conversion apparatus and communication message conversion method
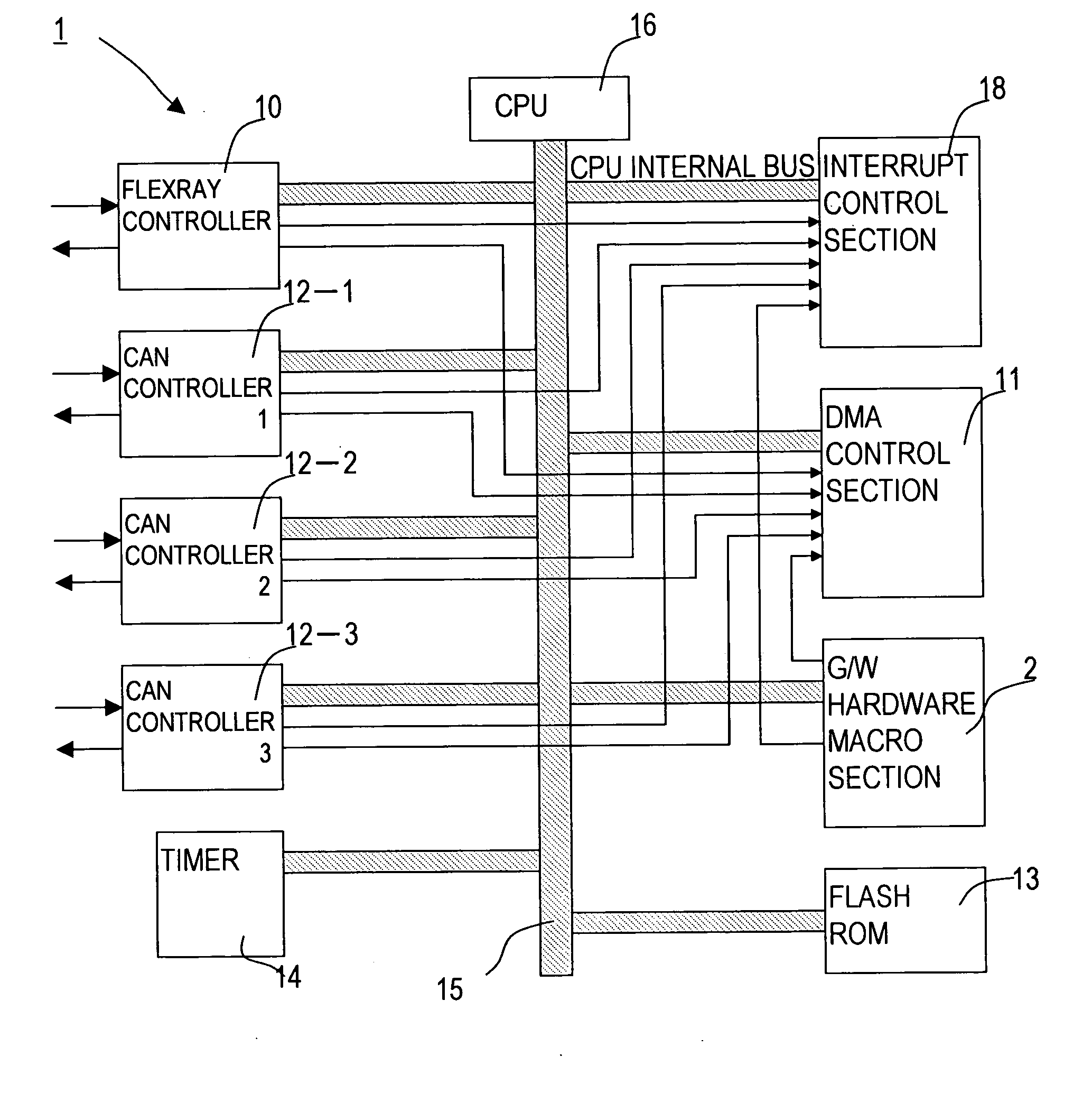
InactiveUS20070140294A1Easy to identifyIncrease speedTime-division multiplexNetworks interconnectionTime scheduleEvent triggered
A communication conversion apparatus achieve efficient conversion without conversion delay and converts messages that effect communication with different communication protocols and schedules. In a message conversion apparatus that performs message conversion of different communication protocols, a routing circuit and a scheduler circuits that perform scheduling of the different communication protocols are separately provided. And time-triggered scheduling and event-triggered scheduling are separately performed. Conversion of FlexRay and CAN messages can be efficiently implemented.
Owner:FUJITSU GENERAL LTD
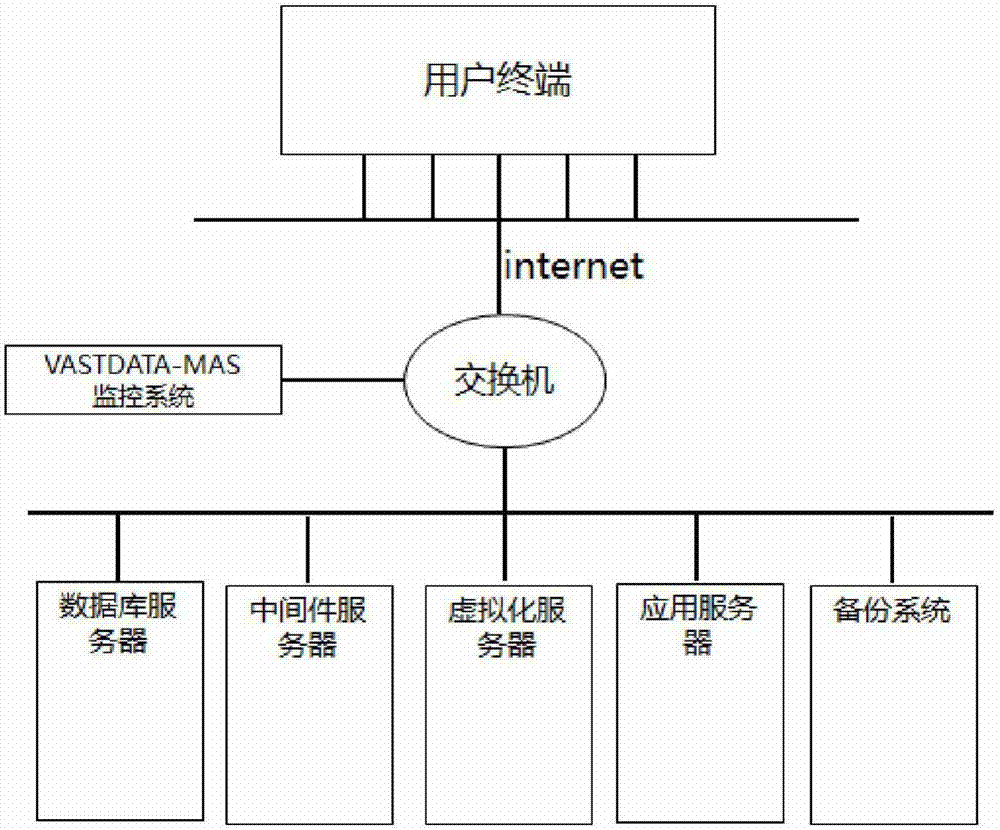
System monitoring method based on cloud platform
The invention discloses a system monitoring method based on a cloud platform and belongs to the computer technology field. Two ways such as 'Automatic discovery' and by-hand input are used for configuring configuration parameters of monitored objects in data acquisition of managed resources, and performance data is acquired by multiple acquisition ways such as SNMP Agent, Telnet, Vast data-MAS Agent, Http (Hyper Text Transport Protocol), ICMP (Internet Control Messages Protocol), TCP (Transmission Control Protocol) and IDBC (Internet Data Base Connection) via an active turning mechanism; warning messages and data from a third-party managing tool and a private user system are integrated and received by multiple ways; data is collected by a VASTDATE-MAS collecting and scheduling module and compared with a preset system threshold, and perfect event triggering, inquiring, informing, processing, and statistic analysis functions can be provided by the VASTDATE-MAS event and an informing module; the system monitoring method is easy to deploy, can realize plug and play and one-touch application.
Owner:BEIJING VASTDATA TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com