Multi-step attack prediction method based on cause-and-effect Byesian network
A Bayesian network and Bayesian attack graph technology, applied in electrical components, transmission systems, etc., can solve the problem of not being able to adapt to the dynamic changes of network attack patterns, and achieve network and computer information security, high reliability, etc. The effect of reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
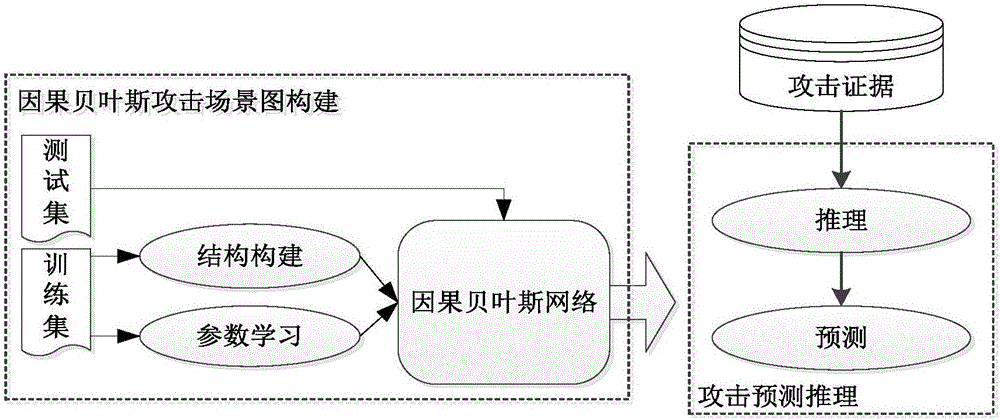
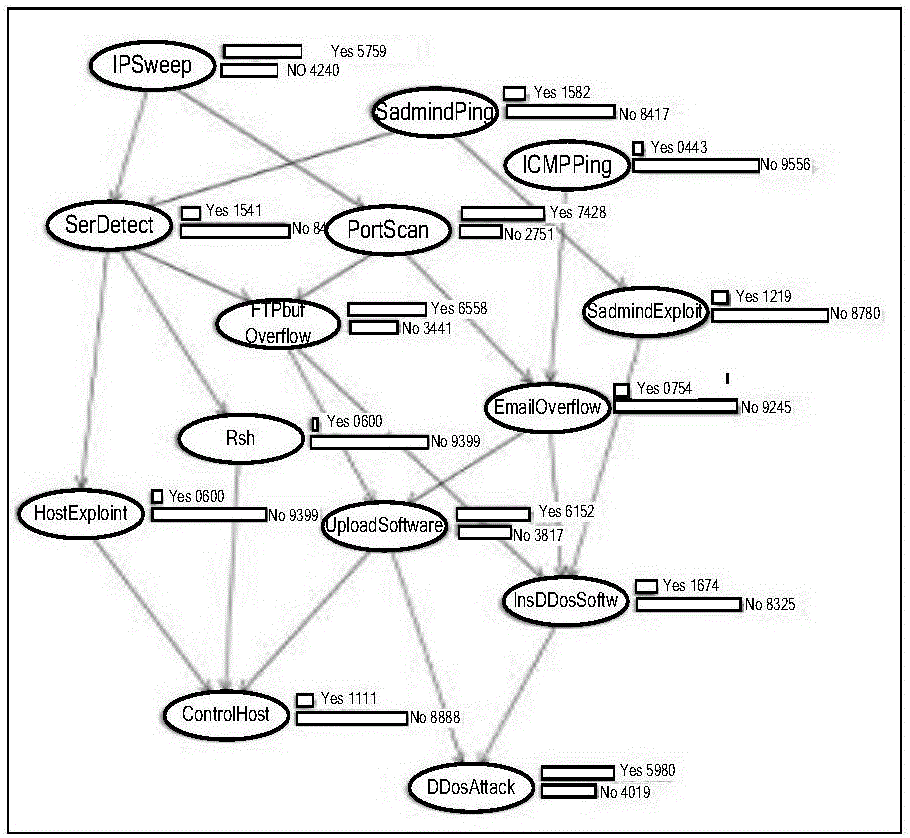
[0031] Embodiment one, see figure 1 As shown, a multi-step attack prediction method based on causal Bayesian network includes the following steps:
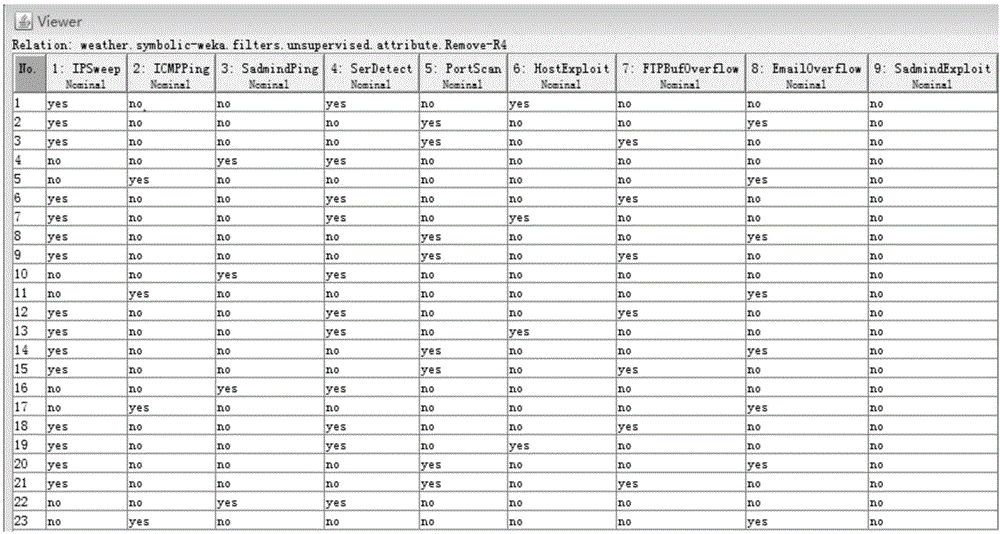
[0032] Step 1. Collect known attack scene data, of which, part of the data is used as a training data set, and the other part of the data is used as a test data set;
[0033] Step 2. Using the attack steps in the multi-step attack scenario in the training data set as attack evidence, perform parameter probability inference on the causal Bayesian attack graph, calculate the occurrence probability of unknown attacks in the causal Bayesian attack graph, and predict the network multi-step The next attack behavior of the attack and its attack intention;
[0034] Step 3. Based on the causal Bayesian attack graph, the unknown attack probability is calculated through the attack evidence, and the next attack behavior and attack intention of the network multi-step attack are predicted.
[0035] The present invention uses frequent patterns...
Embodiment 2
[0036] Embodiment two, see Figure 1~4 As shown, a multi-step attack prediction method based on causal Bayesian network, including the following content:
[0037] Step 1. Collect known attack scene data, of which, part of the data is used as a training data set, and the other part of the data is used as a test data set;
[0038] Step 2. Scan the training data set to find all frequent items in the training data attack sequence set, each frequent item corresponds to an attack step, and obtain the frequent item set, wherein the frequent item set contains n frequent items; according to the frequent item set, Obtain a sequence pattern set with a length of 1 prefixed by each frequent item, which is recorded as a frequent sequence subset, wherein the set of all suffixes contained in all sequence patterns prefixed by a frequent item is called the projection database of the prefix, On the projection database corresponding to different prefixes, execute repeatedly until no new sequence...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com