Patents
Literature
60 results about "Safeguarding" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Safeguarding is a term used in the United Kingdom and Ireland to denote measures to protect the health, well-being and human rights of individuals, which allow people — especially children, young people and vulnerable adults — to live free from abuse, harm and neglect.
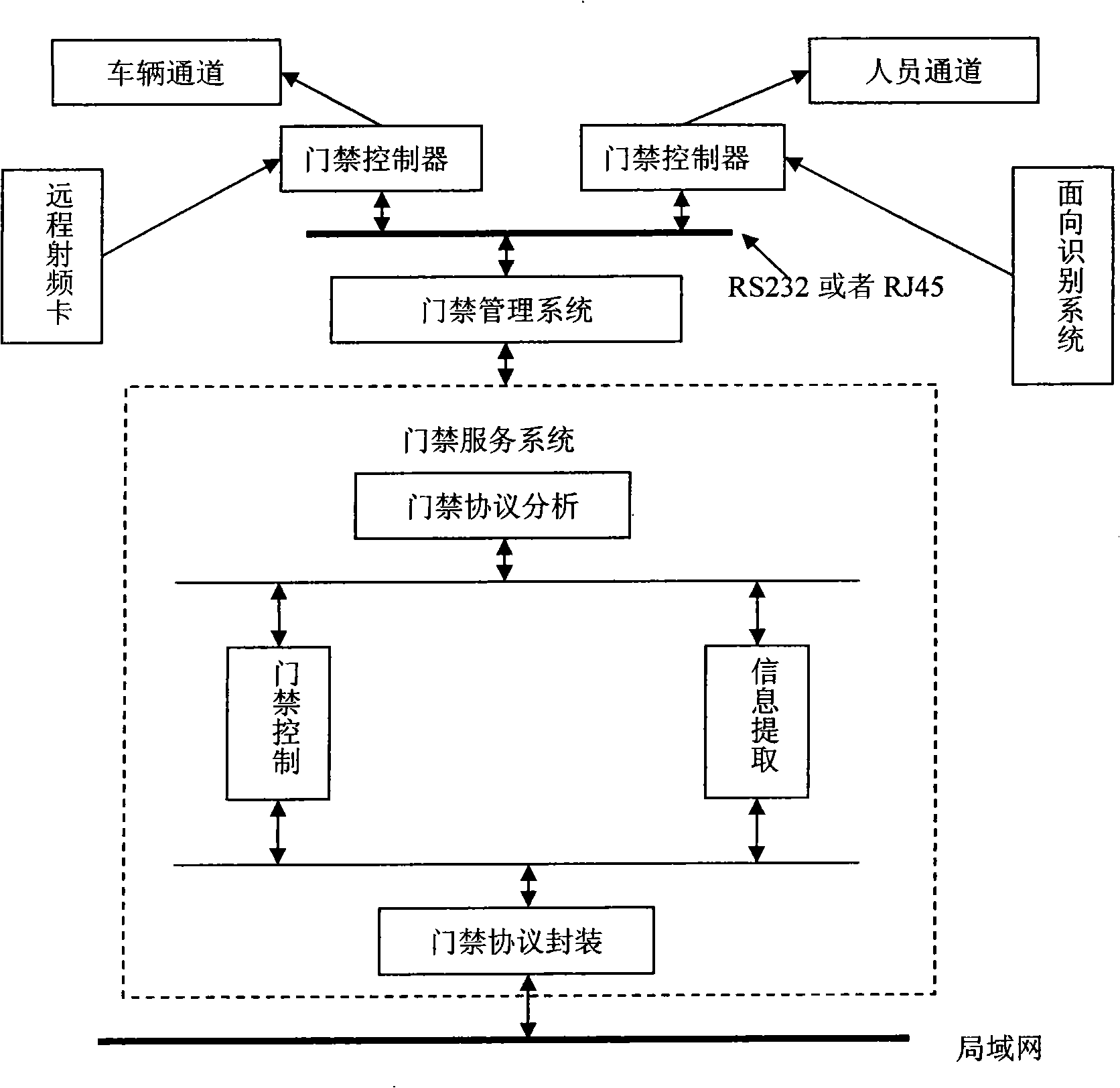
High integrity perception for machine localization and safeguarding
ActiveUS20100063651A1Autonomous decision making processDigital data processing detailsEngineeringHigh integrity
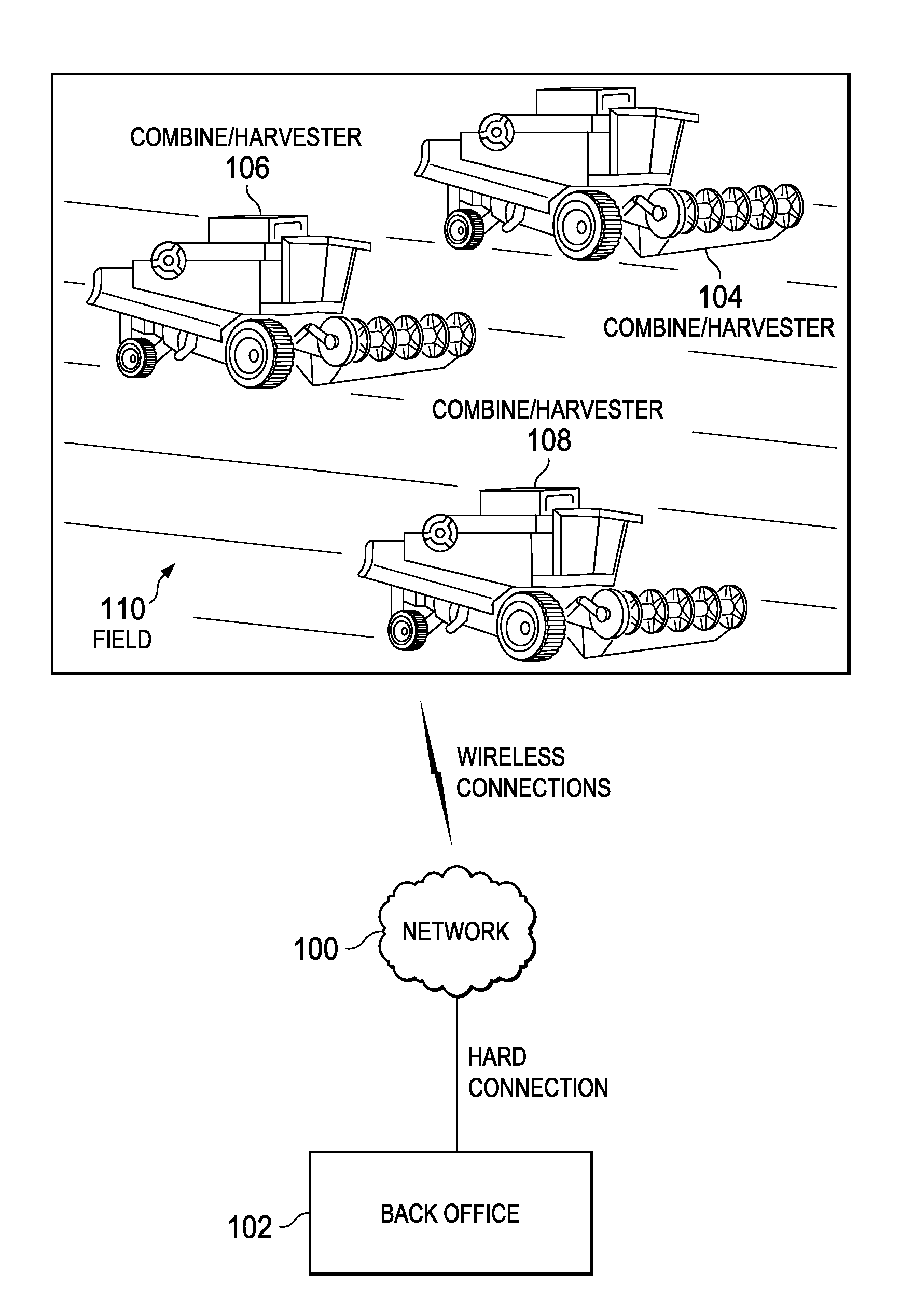
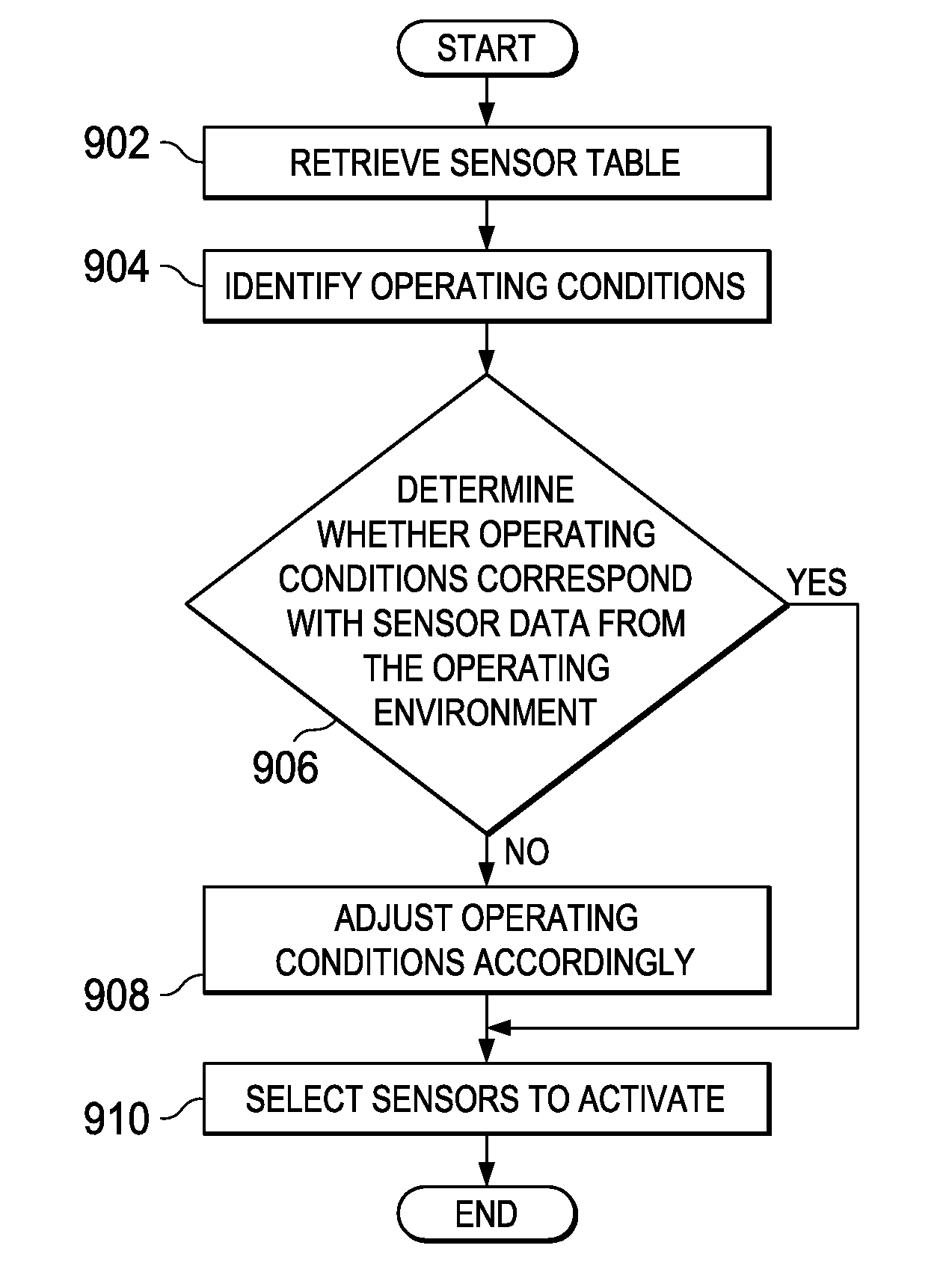
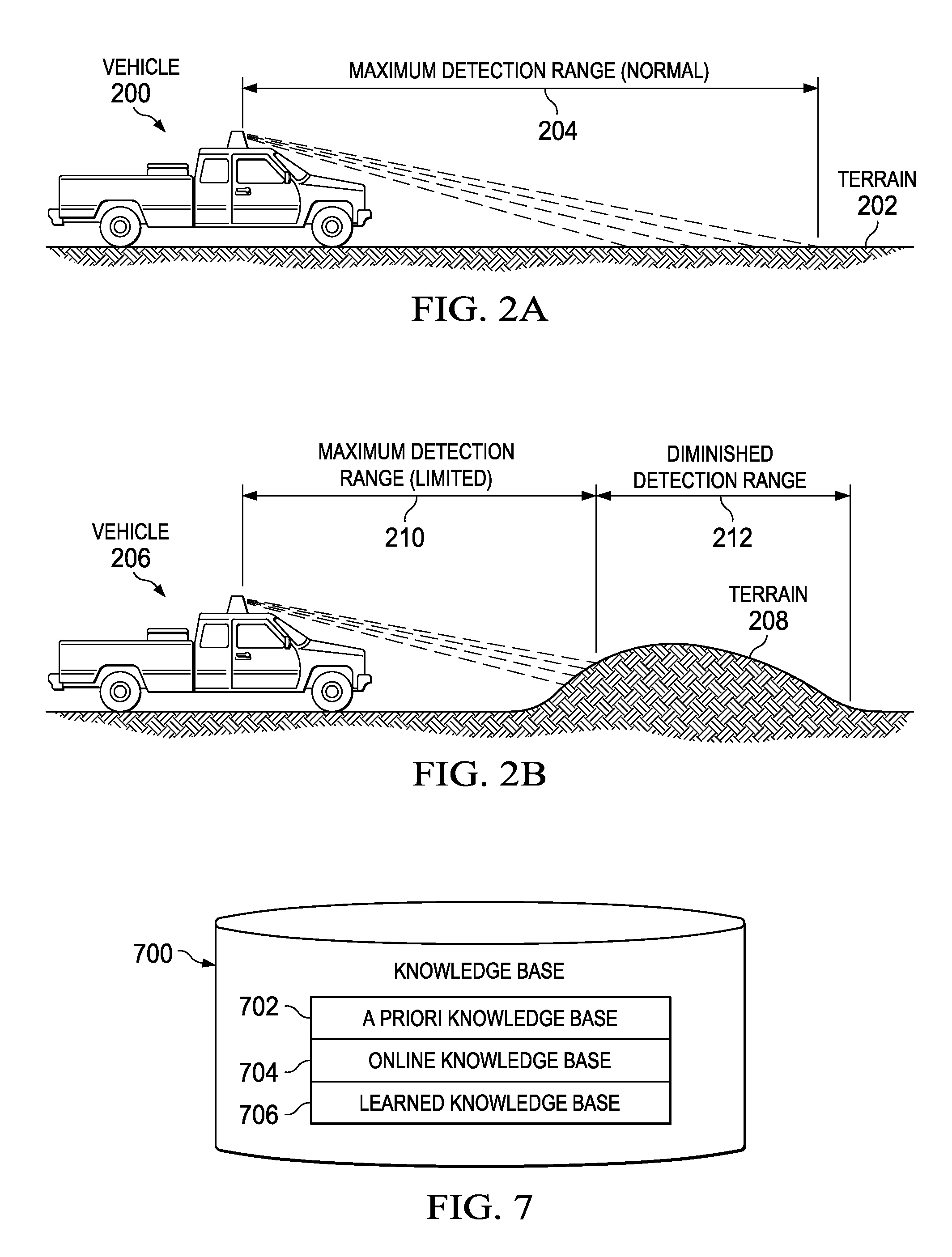
The illustrative embodiments provide a method for processing sensor data and controlling the movement of a vehicle. An operating environment around the vehicle is identified and sensor data is selected from a set of sensors. A dynamic condition is identified using a plurality of different types of sensors on the vehicle. In response to the dynamic condition being identified, the movement of the vehicle is controlled. Sensor data for a plurality of vehicles is managed by receiving sensor data at the plurality of vehicles, each with a plurality of sensors. In response to a selected vehicle within the plurality of vehicles being unable to obtain needed sensor data, collected sensor data from a number of other vehicles in the plurality of vehicles can be obtained to form alternate sensor data used to control the vehicle.
Owner:DEERE & CO
Method and system for safeguarding user access
ActiveCN101835156AImprove protectionNot vulnerableSecurity arrangementSelf-modifying codeNetwork-attached storage
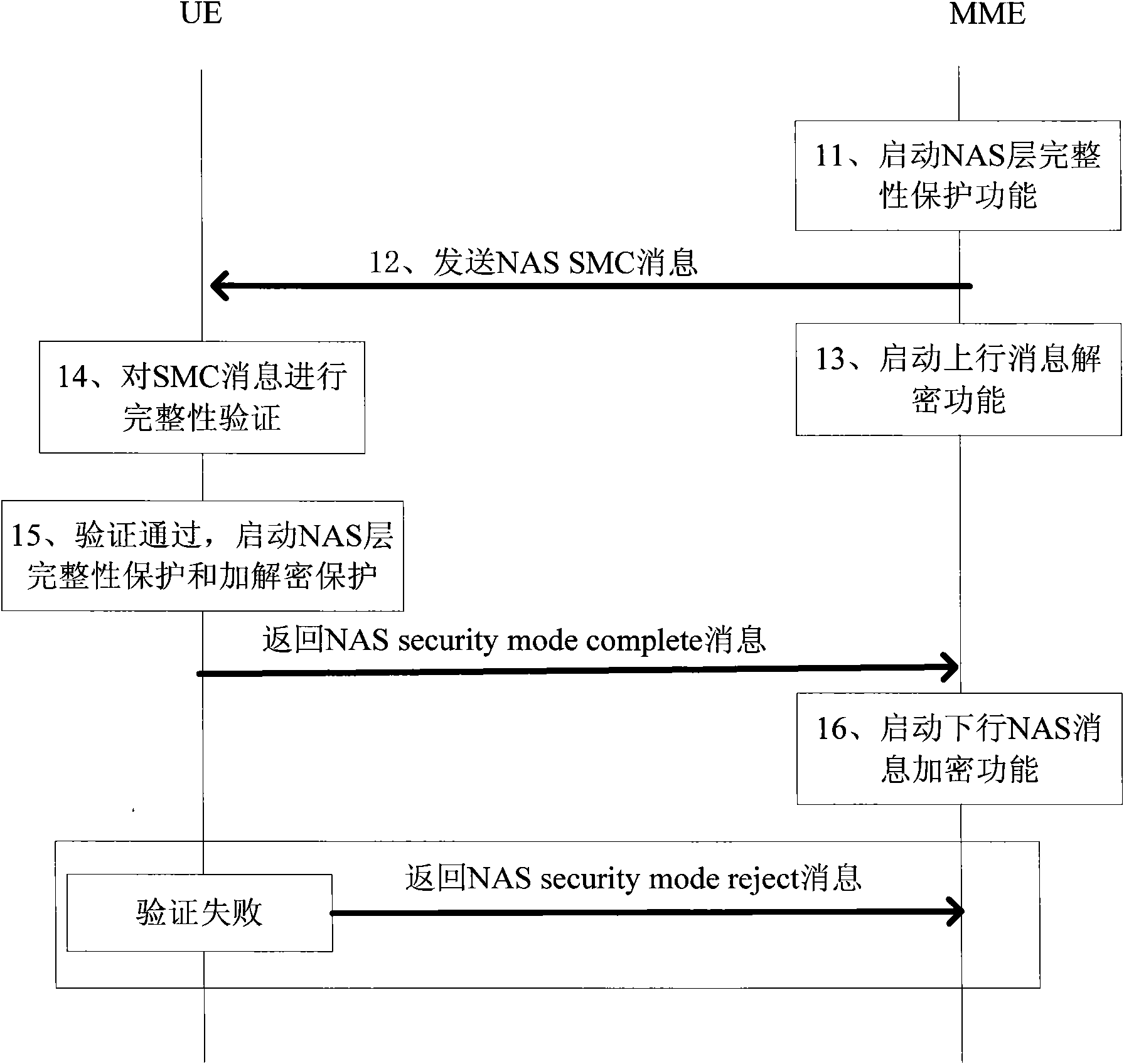
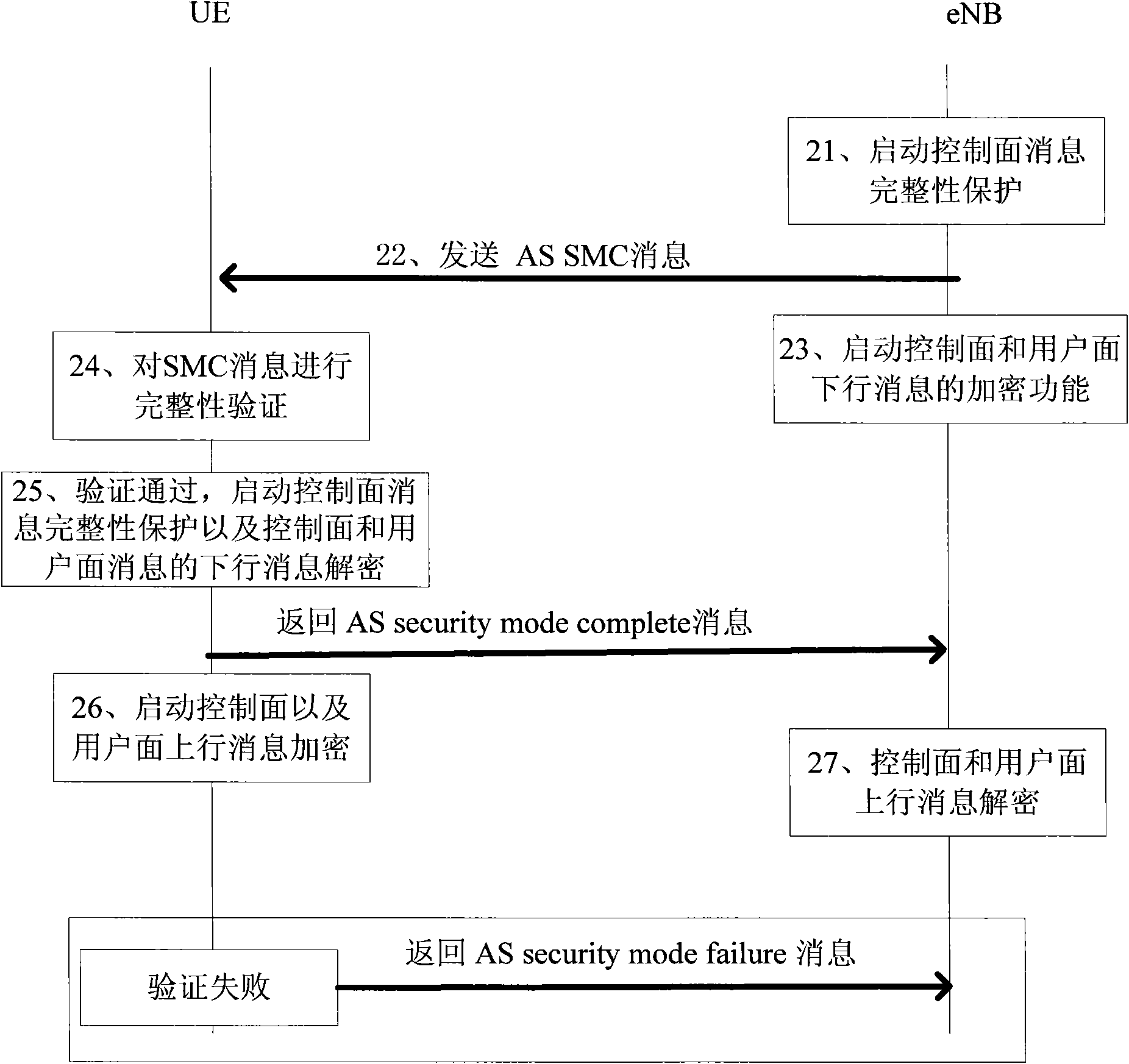
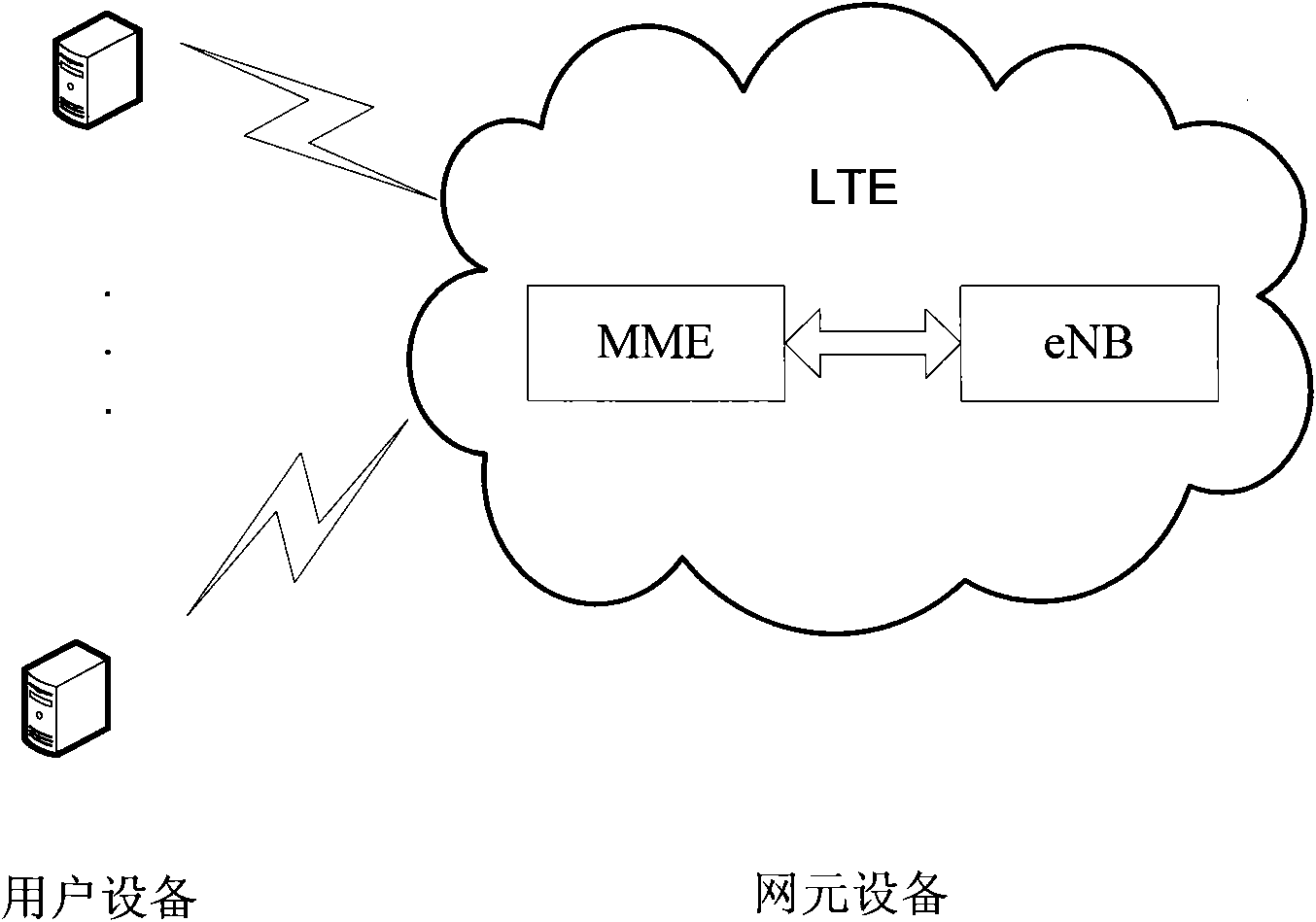
The invention provides a method and a system for safeguarding user access. The method is applied to an LTE (Long Term Evolution) system. UE accessing the LTE system issues an access safety activating command, verifies the integrity of a safe mode command message in an activating process and sends a verification failure message to a network side if verification fails, wherein preset discrimination information is added to the verification failure message, and the network side receives the verification failure message, detects whether the discrimination information is legal or not and restores the configuration before activation if the discrimination information is legal. In traditional NAS (Network Attached Storage) SMC (Self-Modifying Code) and AS SMC flows, the safeguarding of the verification failure message is enhanced so that the network side is hardly attacked by false messages.
Owner:ZTE CORP
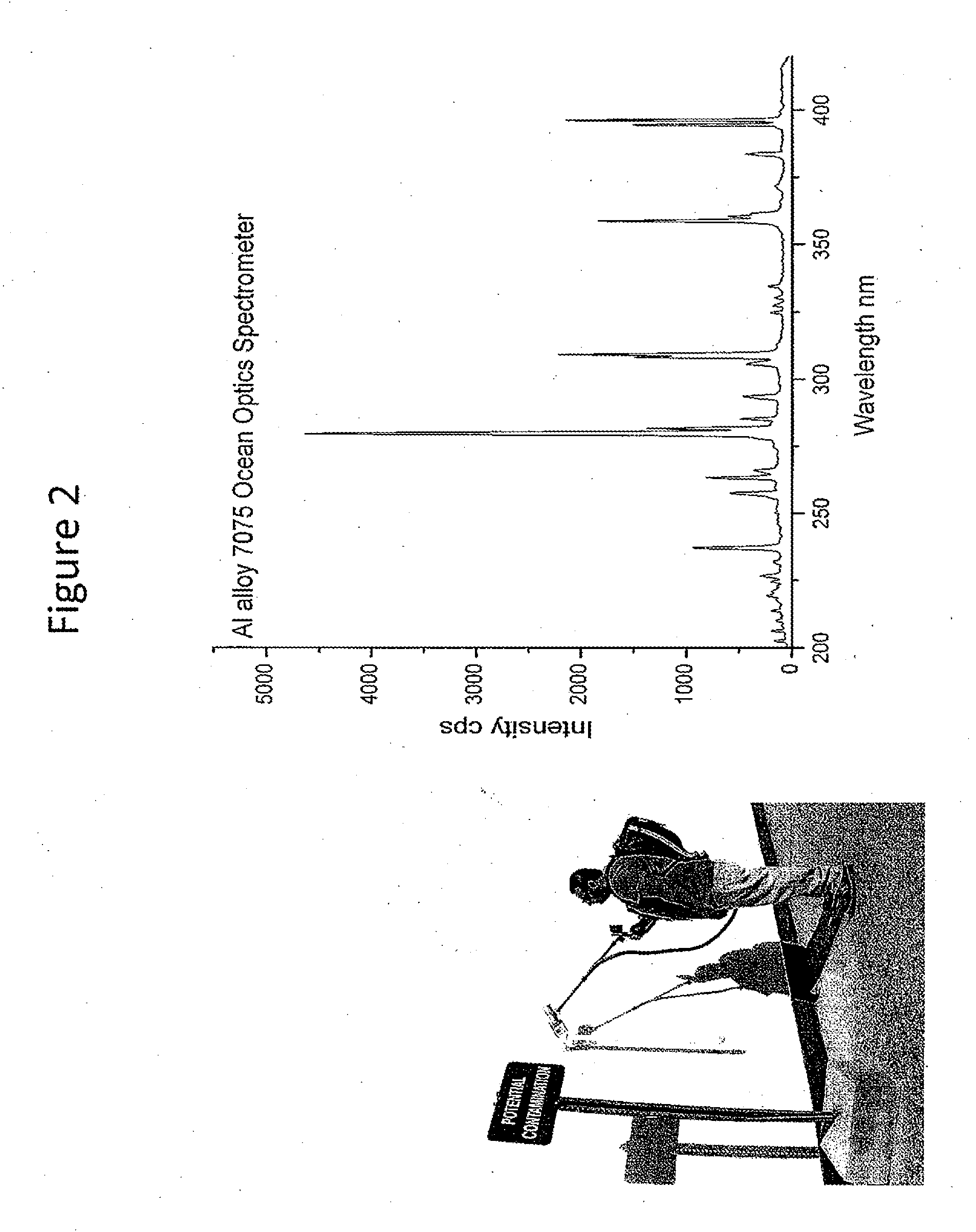
Laser induced breakdown spectroscopy instrumentation for real-time elemental analysis
InactiveUS20120033212A1Radiation pyrometrySpectrum investigationElemental analysisLaser-induced breakdown spectroscopy
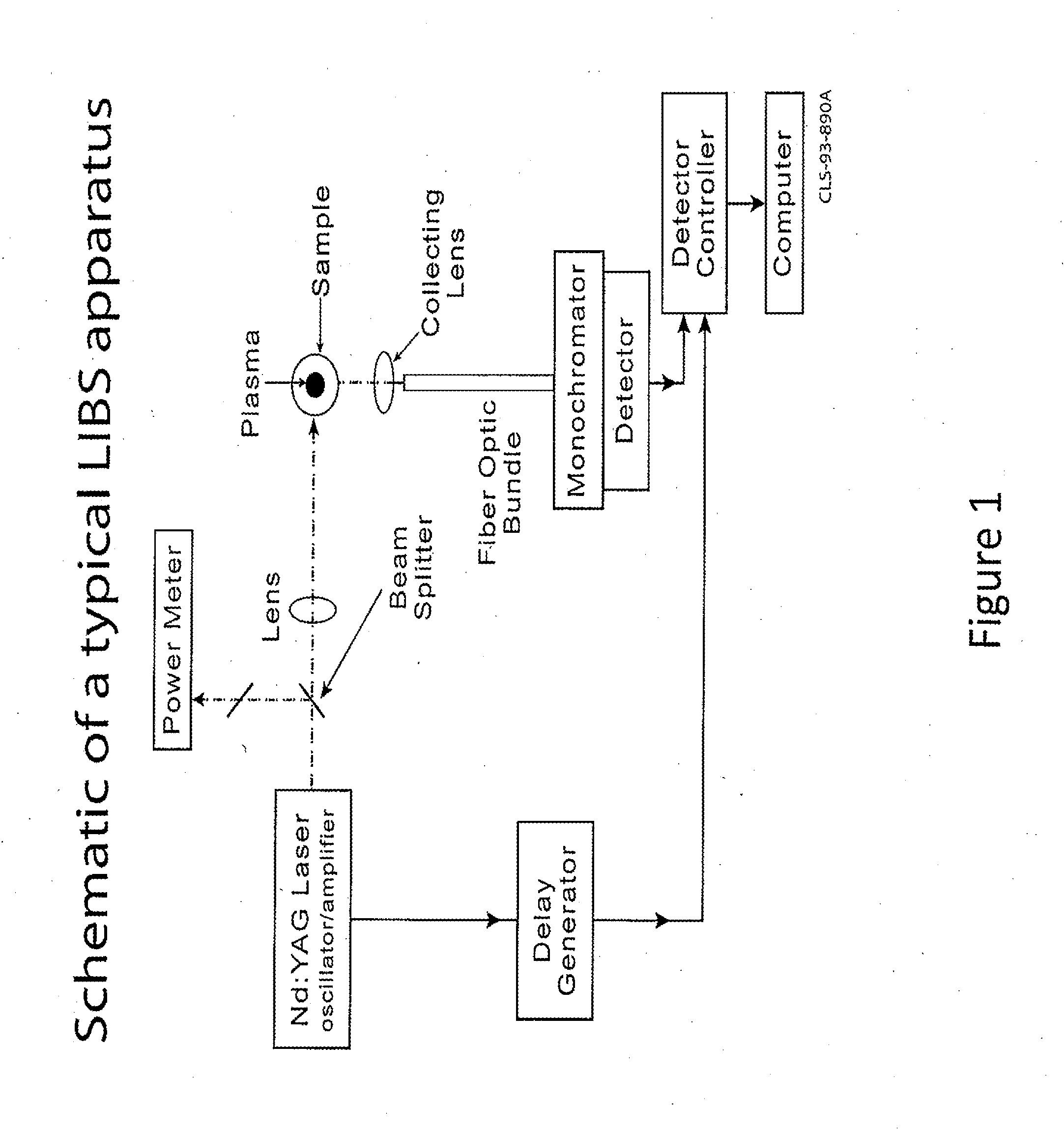
A backpack laser-induced breakdown spectroscopy LIBS system to provide rapid in-field elemental analysis of environmental samples important to the safeguarding of special nuclear materials.
Owner:LOS ALAMOS NATIONAL SECURITY
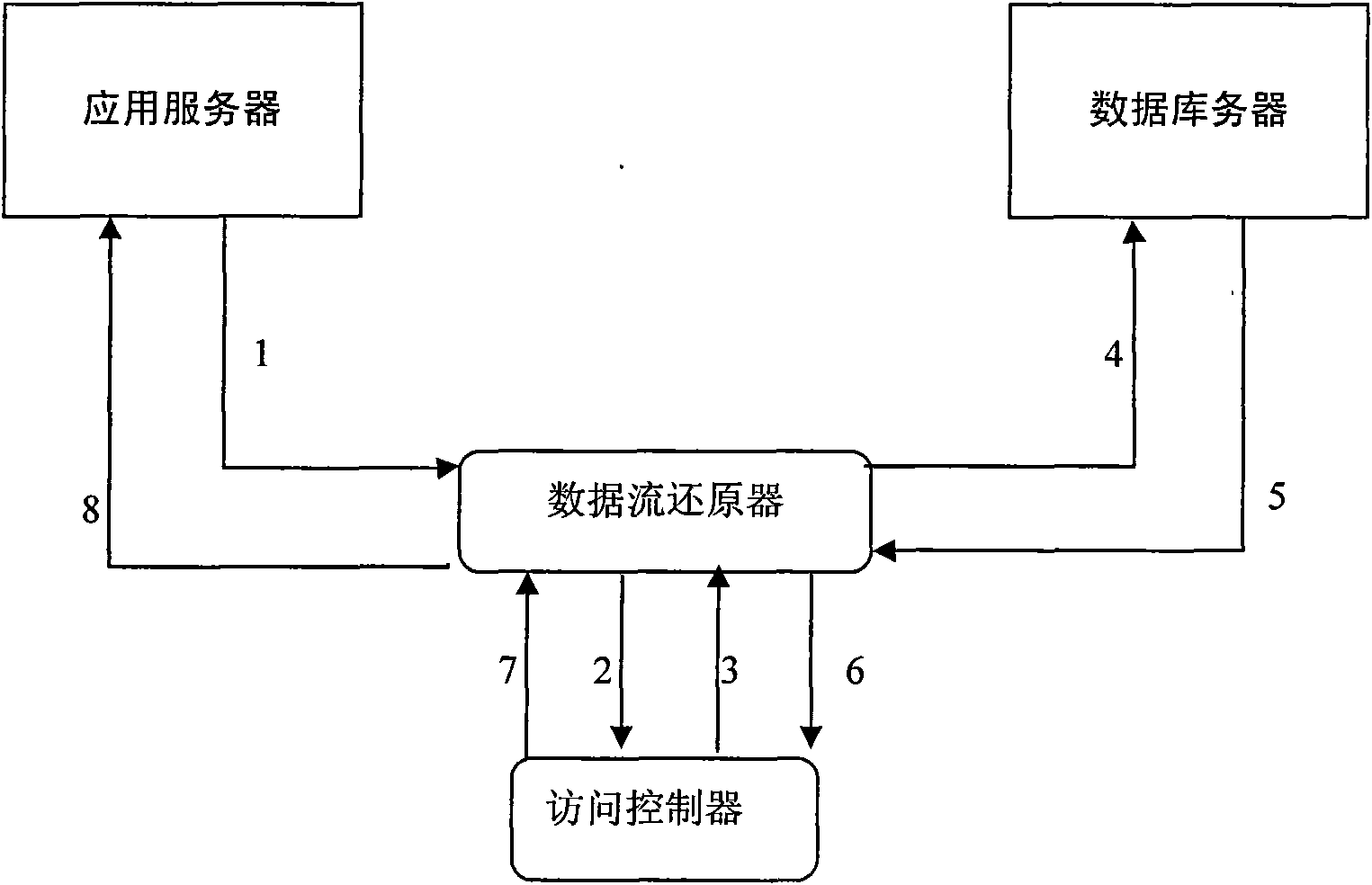
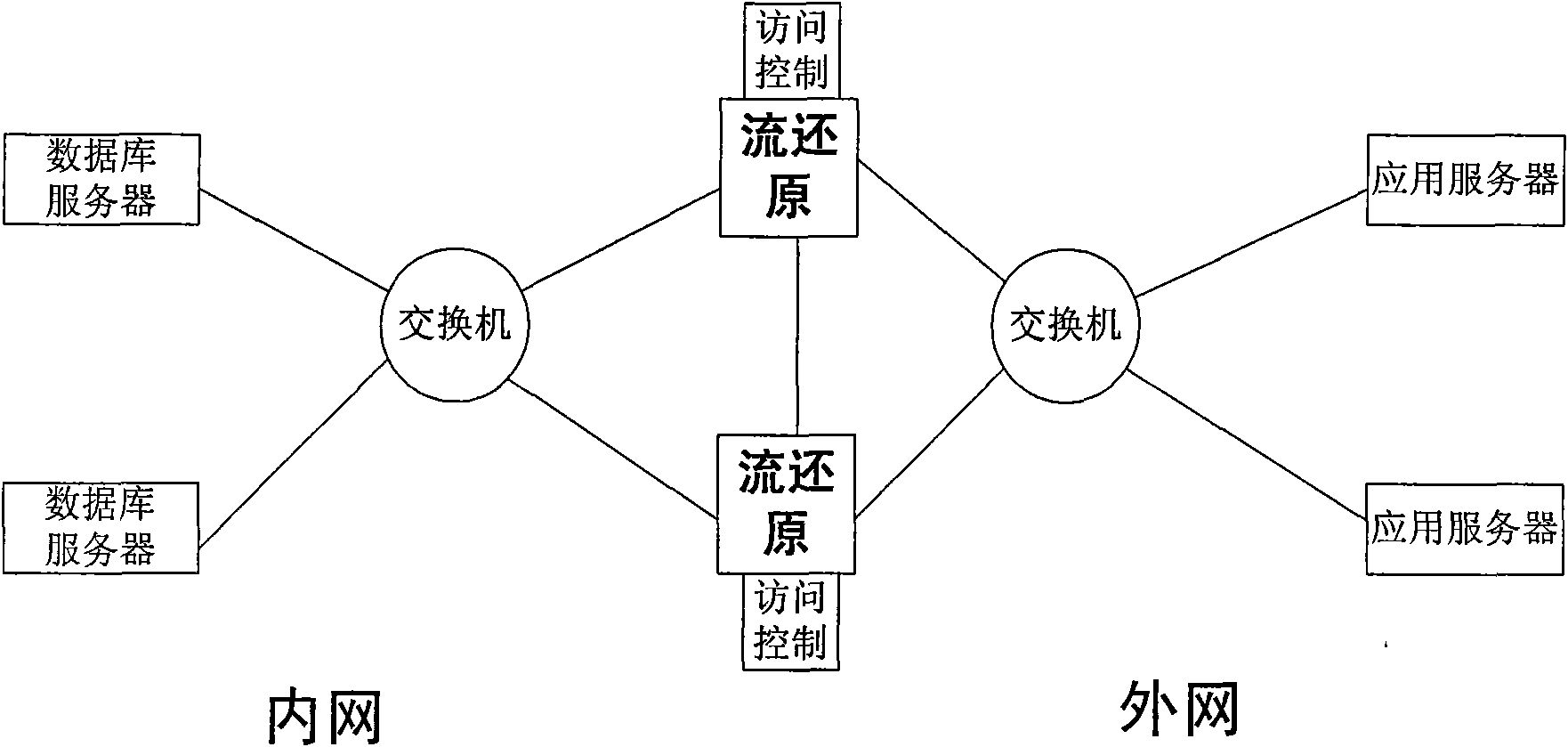
Database safeguarding method based on data stream restoration technology
InactiveCN101610271AAchieve securityAvoid attackTransmissionSpecial data processing applicationsData streamApplication server
The invention discloses a database safeguarding method based on data stream restoration technology, for purpose of protecting the safety of key databases. A system of the method is connected between an application server and a database server in series and mainly consists of a data stream restorer and an access controller. A message transmitted by the application server to a database is intercepted and captured by the data stream restorer. The data stream restorer buffers the message, restores the message into a corresponding TCP data stream, restores SQL sentences from the data stream and submits the SQL sentences to the access controller for safety examination. After passing the safety examination, the message is forwarded to the database server, and an execution result sequentially undergoes restoration and examination and then is forwarded to the application server. Due to the database safeguarding method, the fine-grained safety examination and isolation of the existing application and database communication can be carried out, thereby greatly enhancing the safeguarding capability of the database.
Owner:STATE GRID ELECTRIC POWER RES INST +1
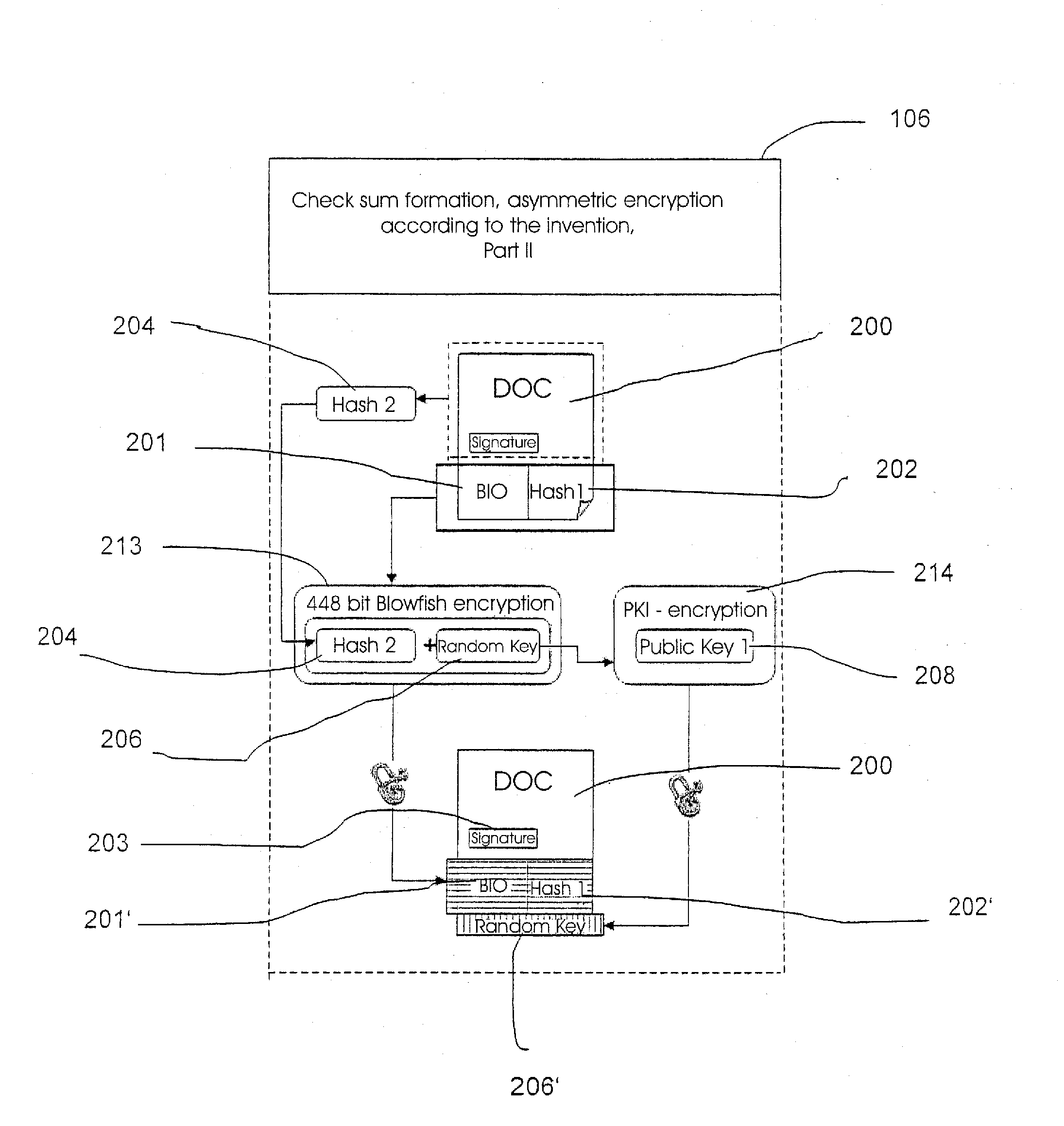
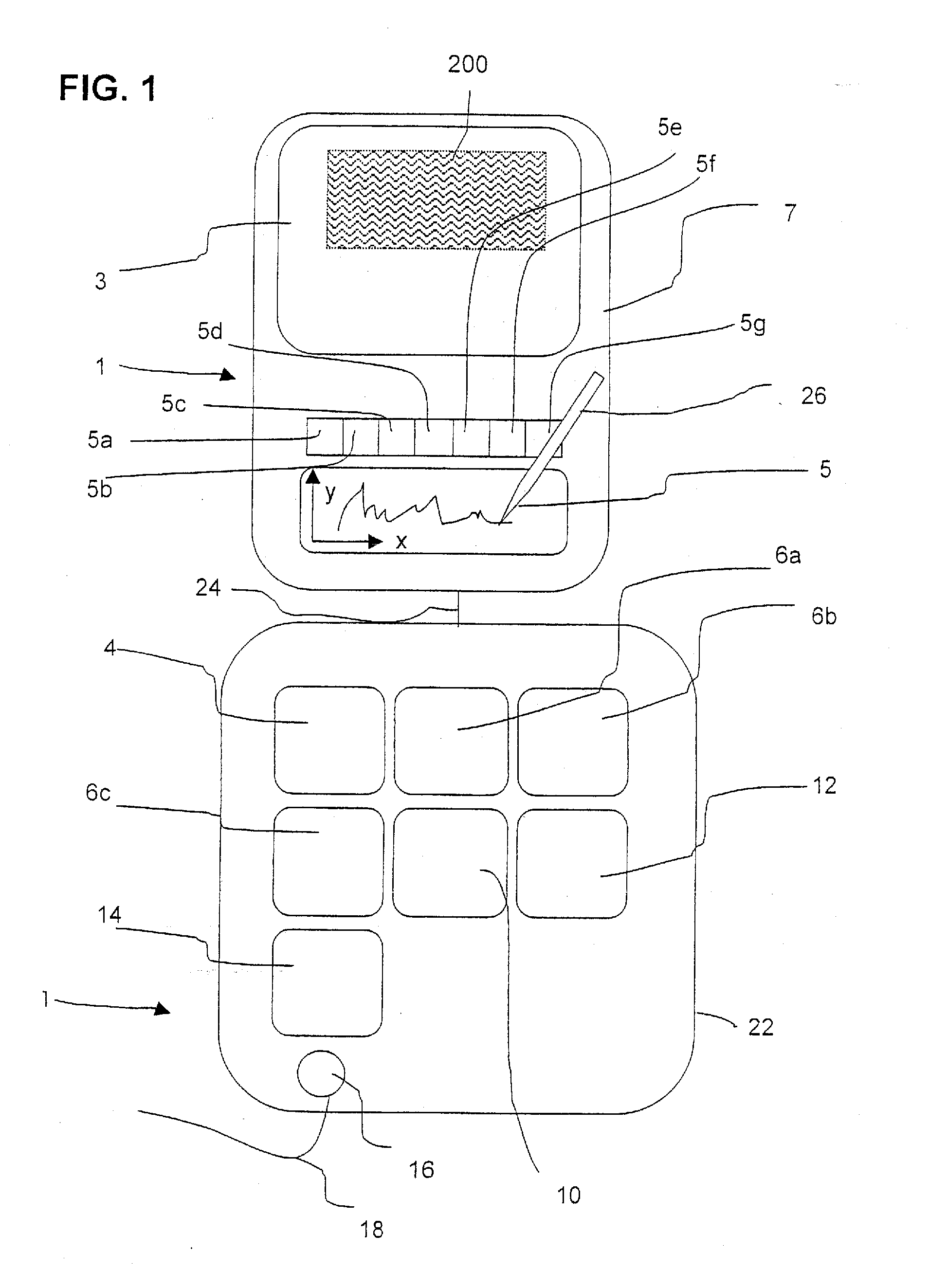
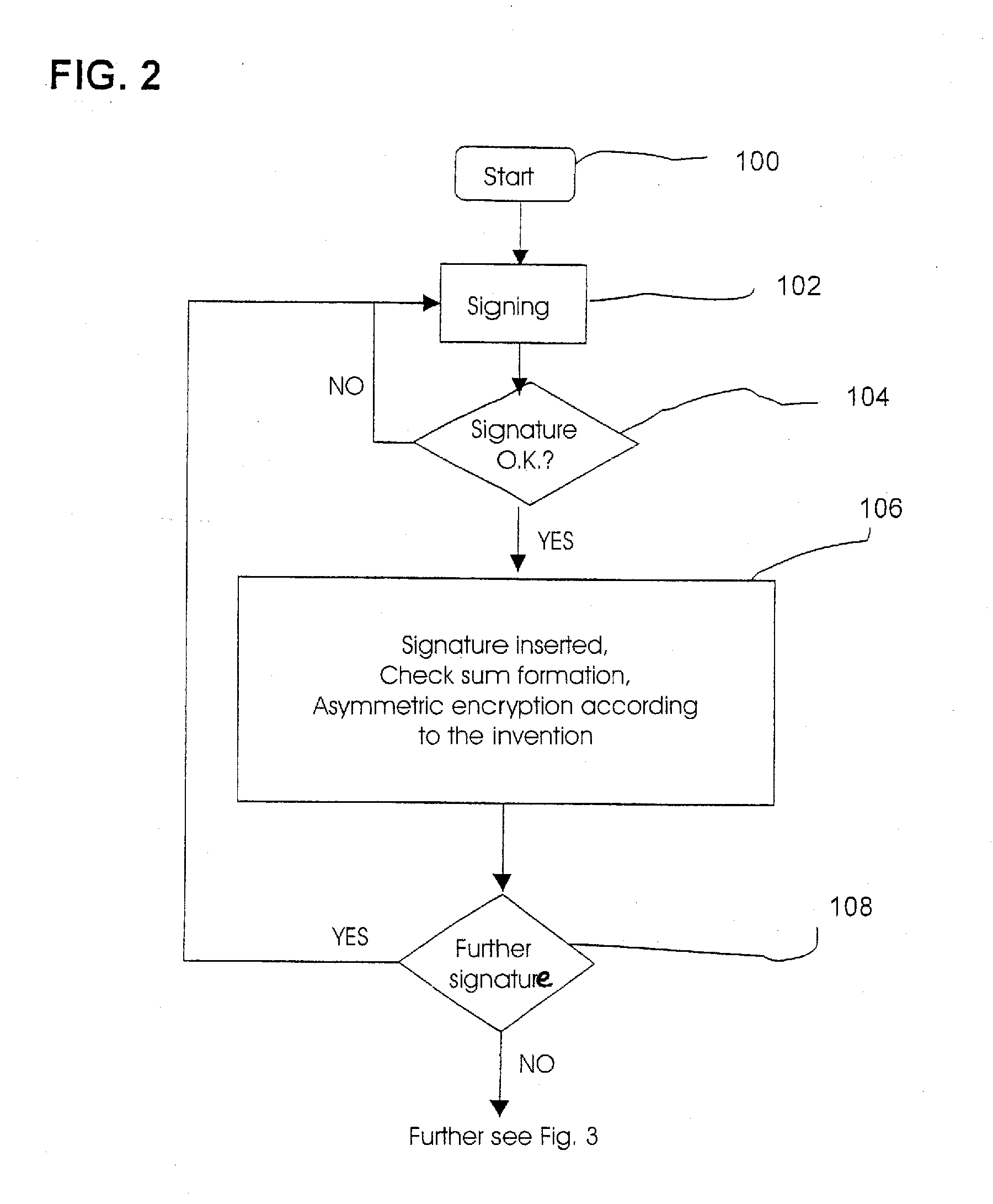
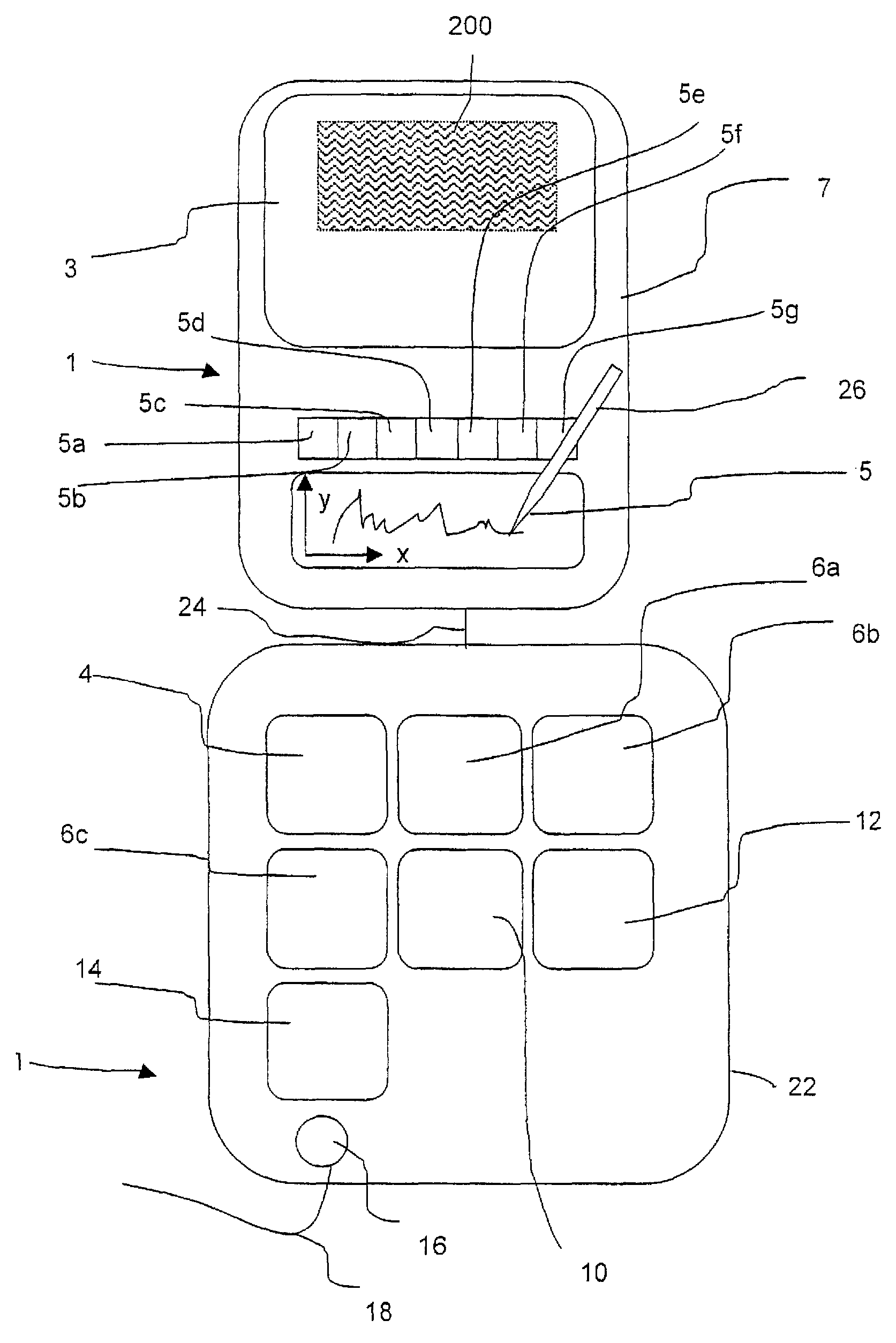
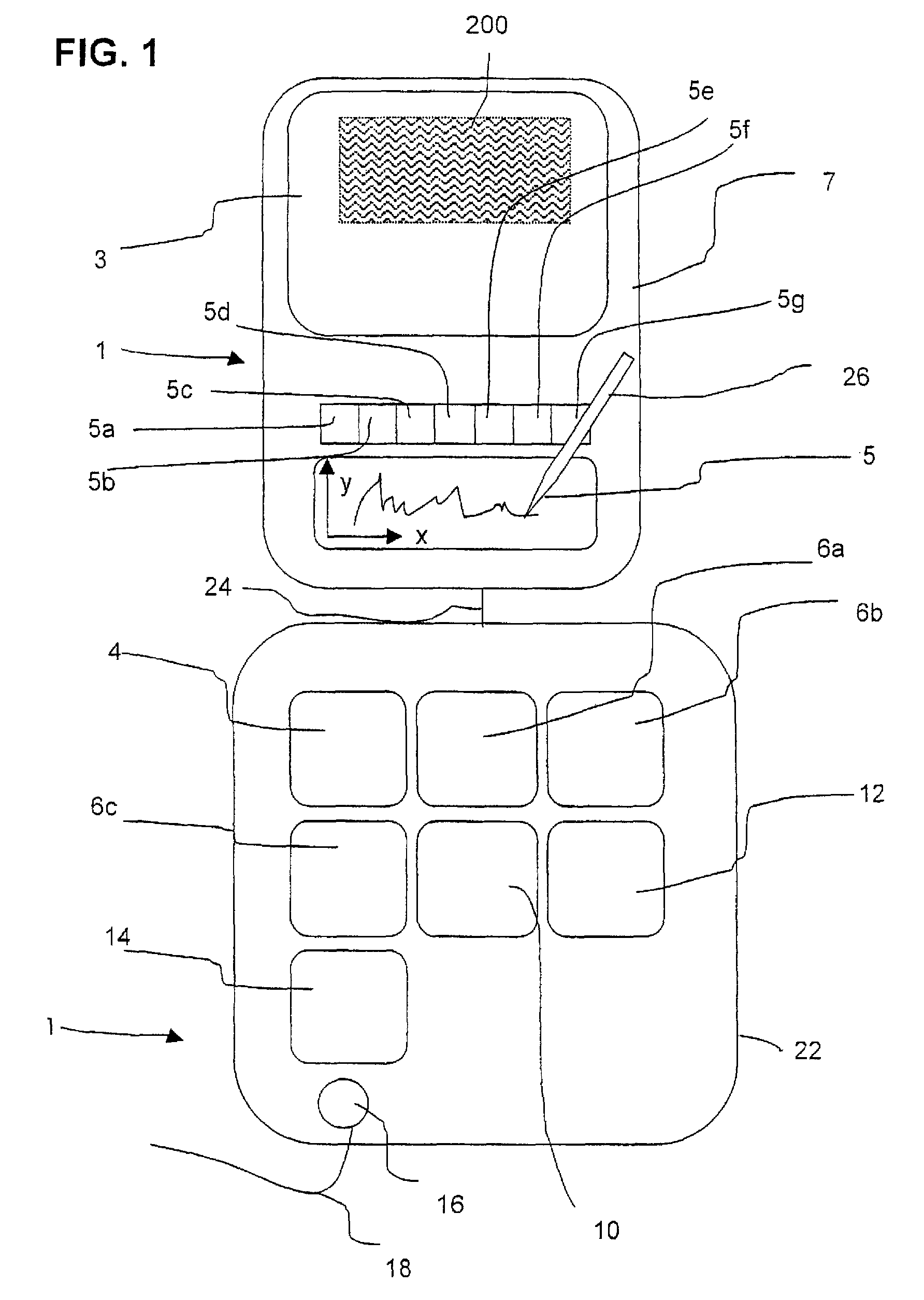
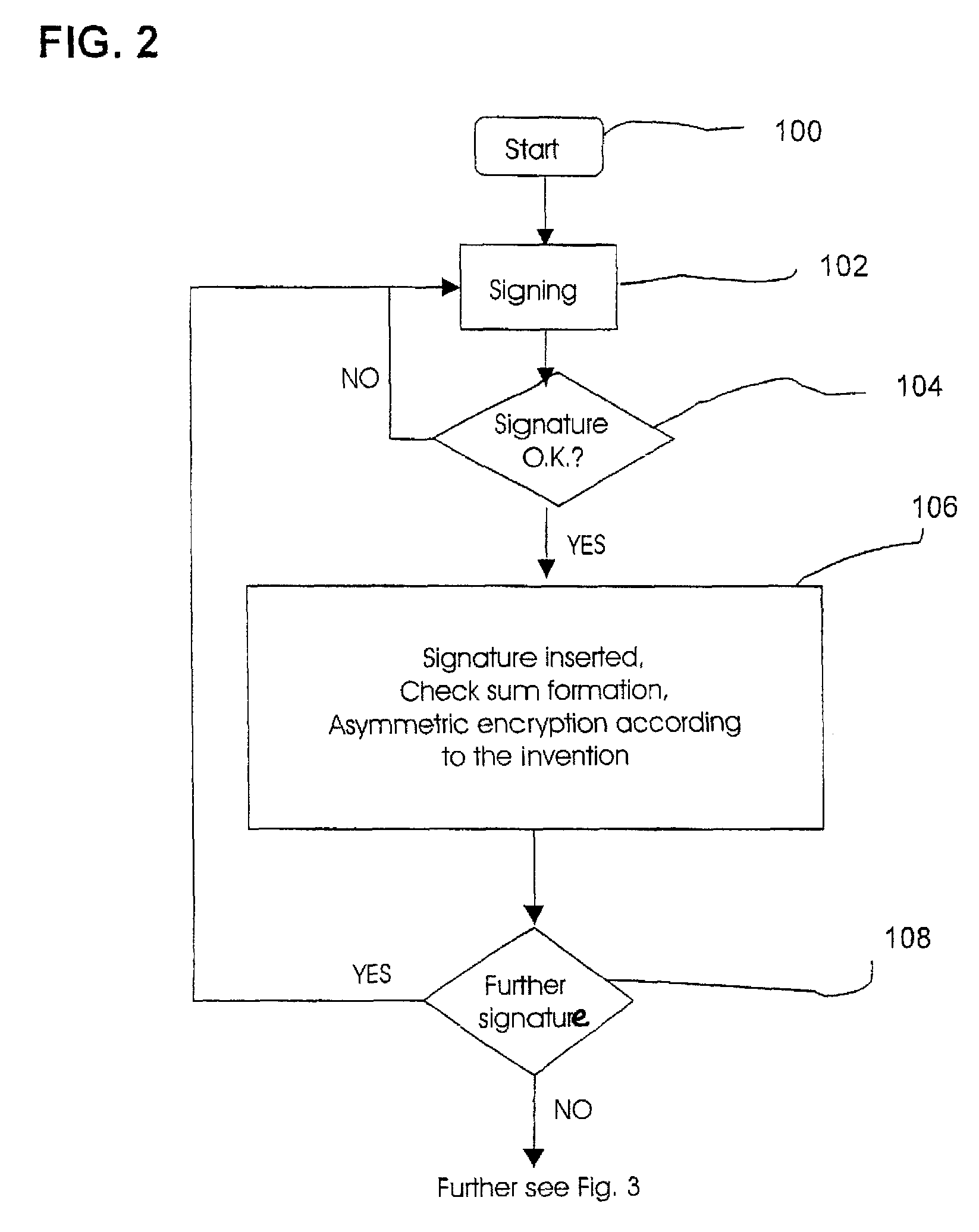
Method and Device for Safeguarding of a Document with Inserted Signature image and Biometric Data in a Computer System
ActiveUS20100106973A1Improper useConfidenceDigital data processing detailsUser identity/authority verificationElectronic documentHash function
A method for safeguarding an electronic document includes inserting at least one digital signature image into the electronic document and generating a first check sum for the electronic document, with or without optionally-inserted biometric signature data, using a first hash function. A second check sum is then generated using a second hash function. The first check sum and the biometric data, if provided, are then symmetrically encrypted using a key that is the sum of the second check sum and a generated random value. The symmetrically-encrypted first check sum is attached to the document. The random value is then asymmetrically encrypted using a first public key of a first key pair and the asymmetrically-encrypted random value is added to the document.
Owner:STEPOVER
Synthetic intelligent safety prevention system based on area safety
InactiveCN101303777AReach exchangeAchieve sharingCo-operative working arrangementsData switching by path configurationPersonalizationTime information
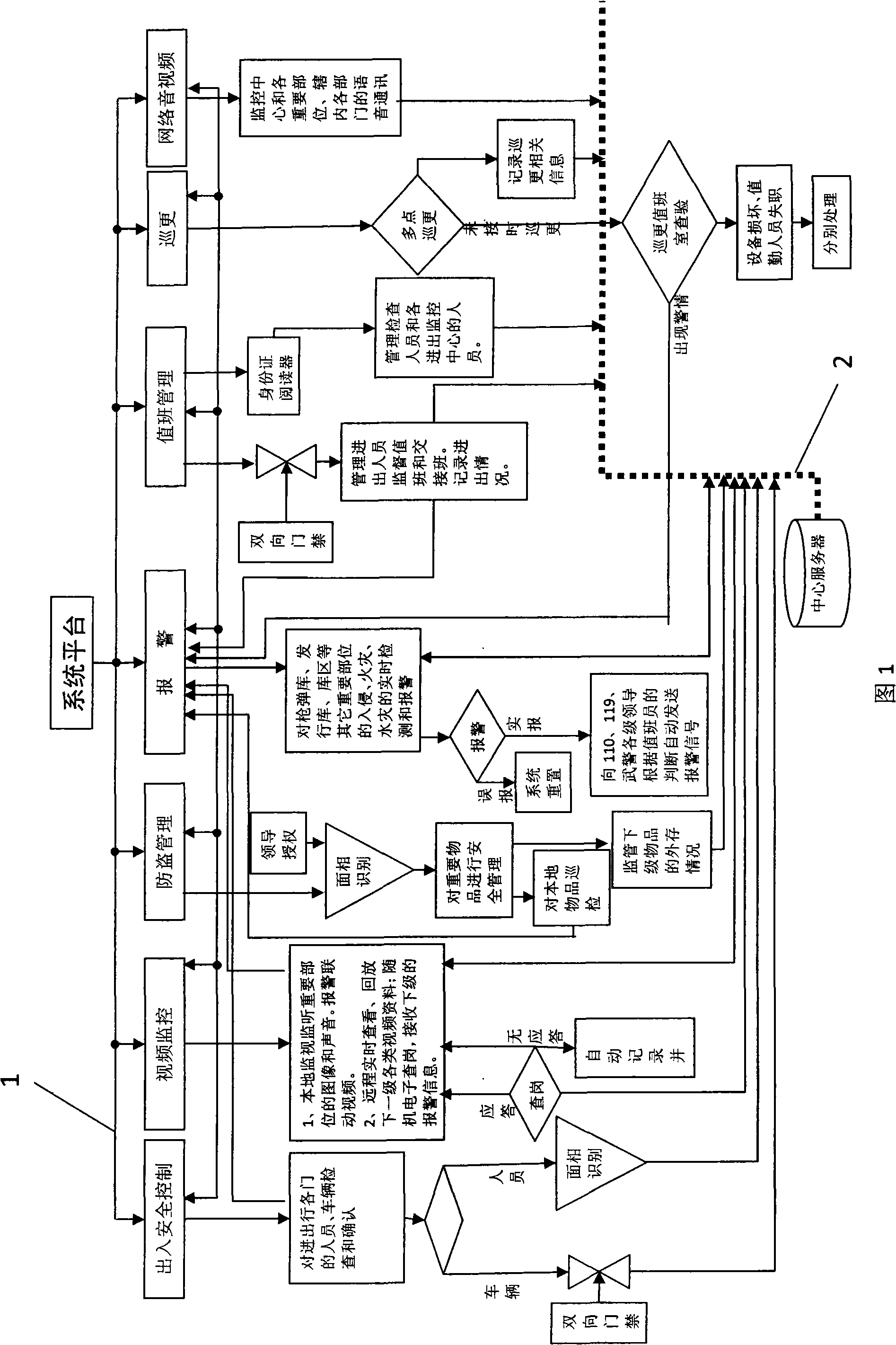
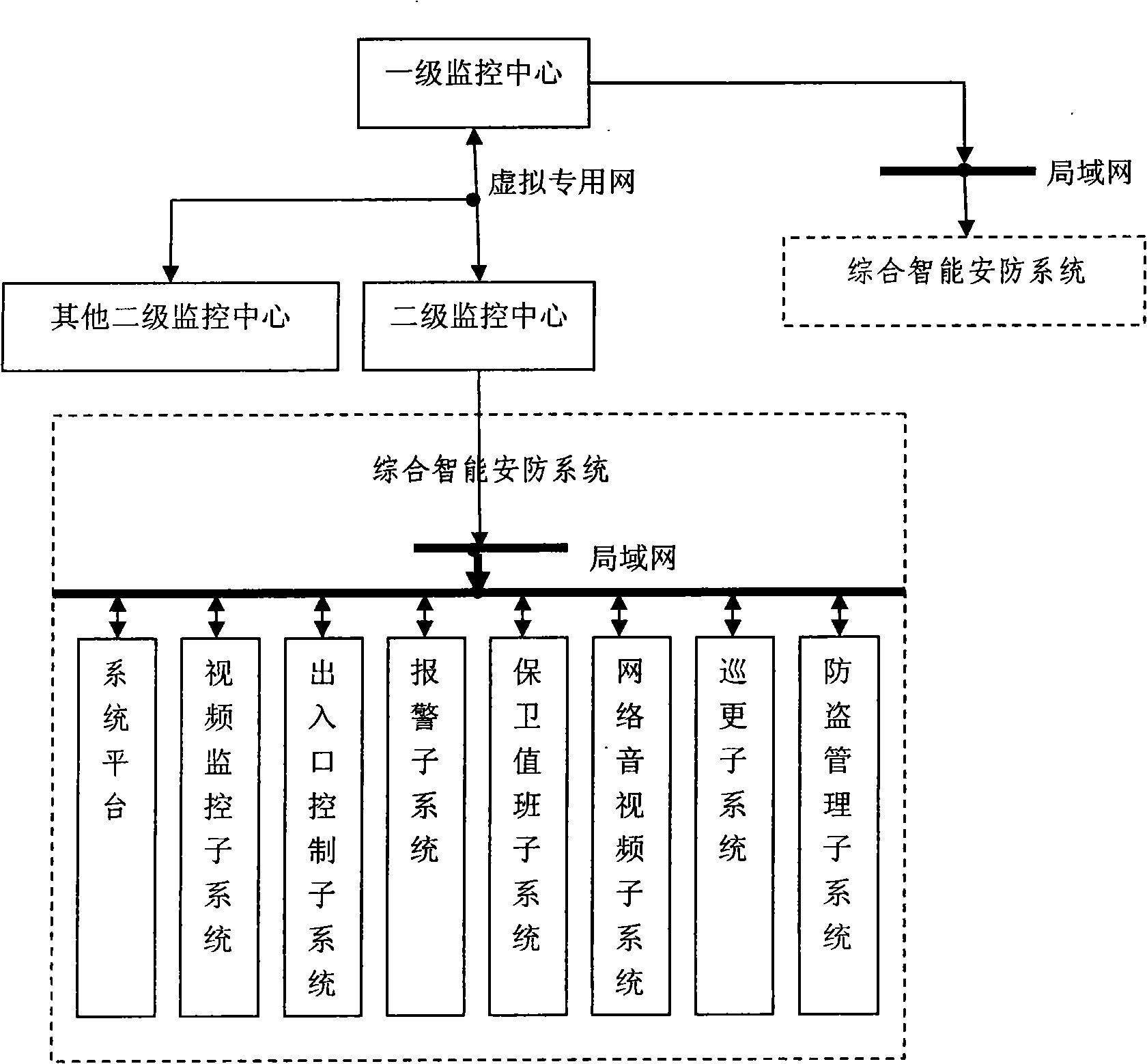
The invention discloses an integral intelligent security system based on the regional safety, which remotely controls and manages separate system by means of a TCP / IP network; not only video, access control, and alarm are included, but also the administration of the daily work of patrol, antitheft, and security guard personnel are brought into the system; the individualized target detecting technologies such as the RFID technology, the biometric identification technology, and the like, are additionally applied. The invention is a 'network system' of hierarchical network version and meets requirements for multi-level and multi-monitoring centers. The invention is highly practical , can provide real-time information to a user; meanwhile and provide a plurality of emergency solutions according to the collected real-time information. Therefore, the invention is applicable to overall regional safeguarding or security guard in some important places. The integral intelligent security system has very high compatibility and expansibility, can perform the regional networking from a point to a line and a point to a surface so as to ultimately form a multi-level safety guarding and emergency response system among regions.
Owner:INFORMATION RES INST OF SHANDONG ACAD OF SCI +1
High integrity perception for machine localization and safeguarding
ActiveUS8818567B2Autonomous decision making processAnalogue computers for trafficHigh integrityPattern perception
The illustrative embodiments provide a method for processing sensor data and controlling the movement of a vehicle. An operating environment around the vehicle is identified and sensor data is selected from a set of sensors. A dynamic condition is identified using a plurality of different types of sensors on the vehicle. In response to the dynamic condition being identified, the movement of the vehicle is controlled. Sensor data for a plurality of vehicles is managed by receiving sensor data at the plurality of vehicles, each with a plurality of sensors. In response to a selected vehicle within the plurality of vehicles being unable to obtain needed sensor data, collected sensor data from a number of other vehicles in the plurality of vehicles can be obtained to form alternate sensor data used to control the vehicle.
Owner:DEERE & CO
Auto-counting and safeguard component of punching machine
InactiveCN104923586ARealize effective statistical functionsRealize security protection functionShaping safety devicesMetal working apparatusPunch pressControl circuit
The invention discloses an auto-counting and safeguard component of a punching machine. The auto-counting and safeguard component comprises an automatic counting device, a photoelectric protector and a control cabinet. The automatic counting device comprises a photoelectric proximity switch and a flexible support connected with each other. The photoelectric protector comprises a circular shell and a plurality of photoelectric protective units provided within the circular shell. Each photoelectric protective unit comprises an infrared transmitting end, an infrared receiving end and a control circuit; the infrared transmitting end and the infrared receiving end are co-directional and both connected with the control circuit; the control cabinet comprises an independent power supply, a counter and a plurality of relays connected in parallel; the independent power supply is connected with both the counter and the relays; the counter is electrically connected with the photoelectric proximity switch; the relays and the control circuits are connected in one-to-one correspondence. The automatic counting device is made to adapt to the processing modes of traditional punches, and a safeguard device is made to adapt to the processing modes of the traditional punches to allow safeguarding.
Owner:CHENGDU DIANSHI CREATIVE TECH
System security method and apparatus
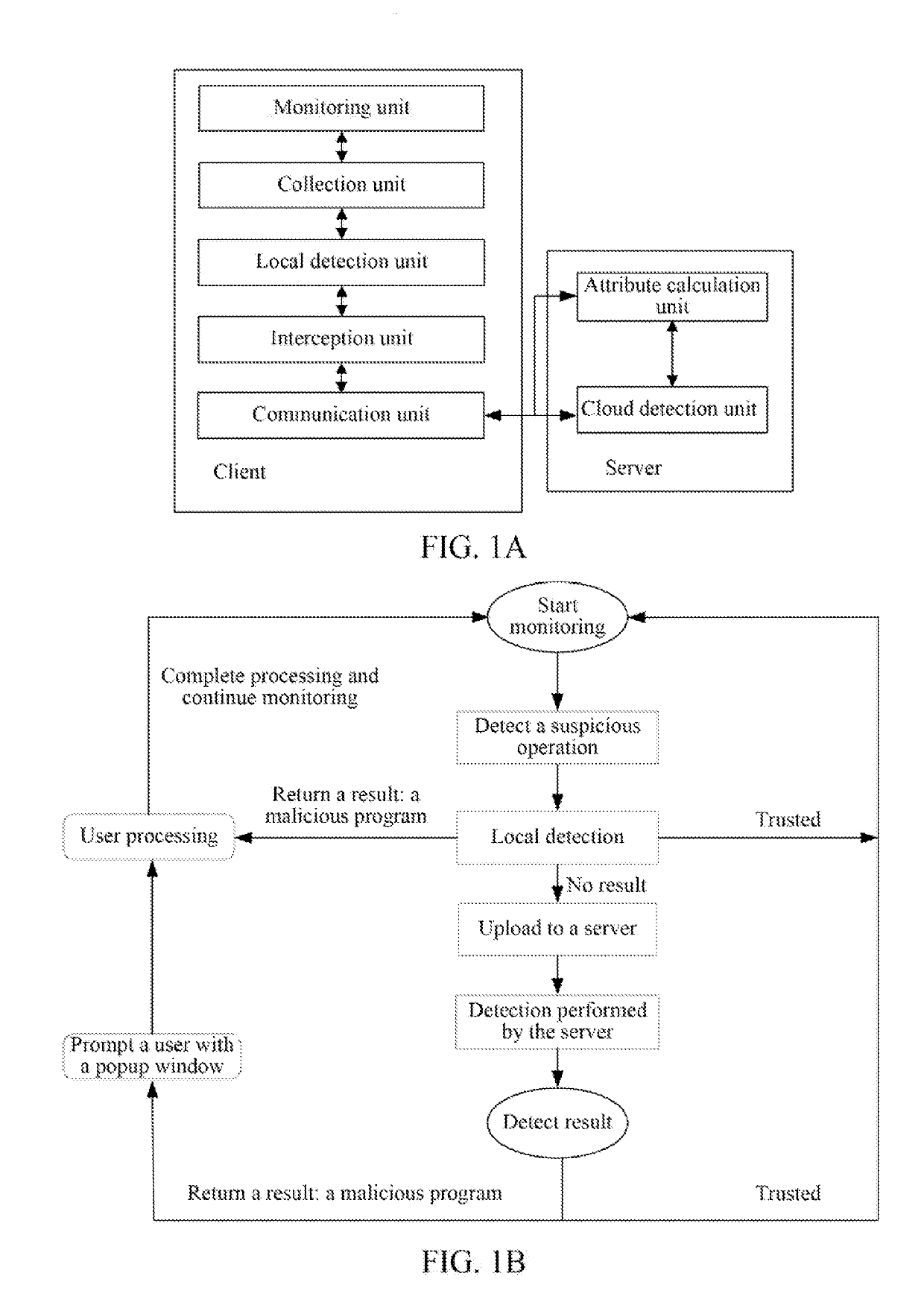
ActiveUS20190318089A1Easy to distinguishFlexible settingsEnsemble learningCharacter and pattern recognitionSystemic approachOperating system
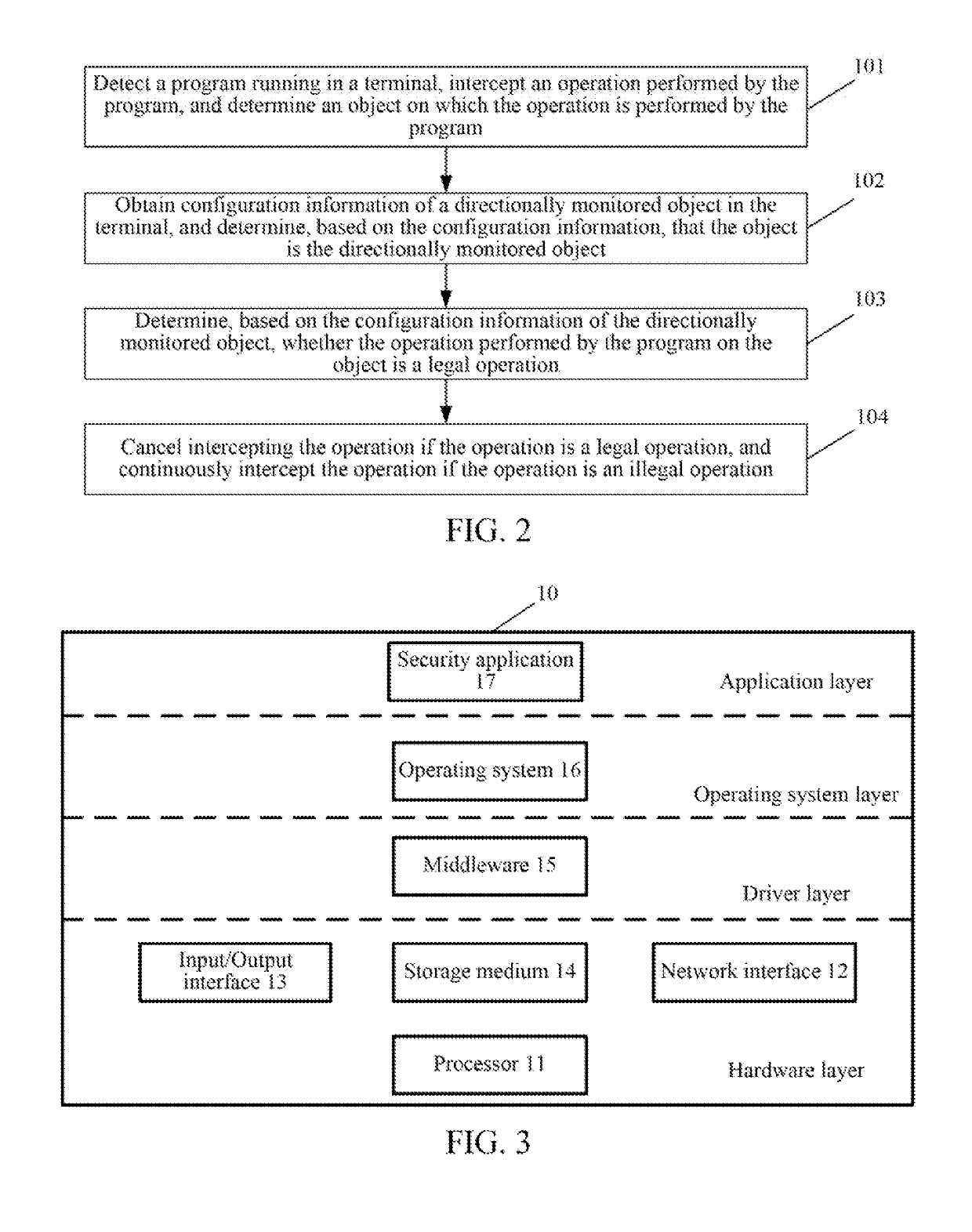
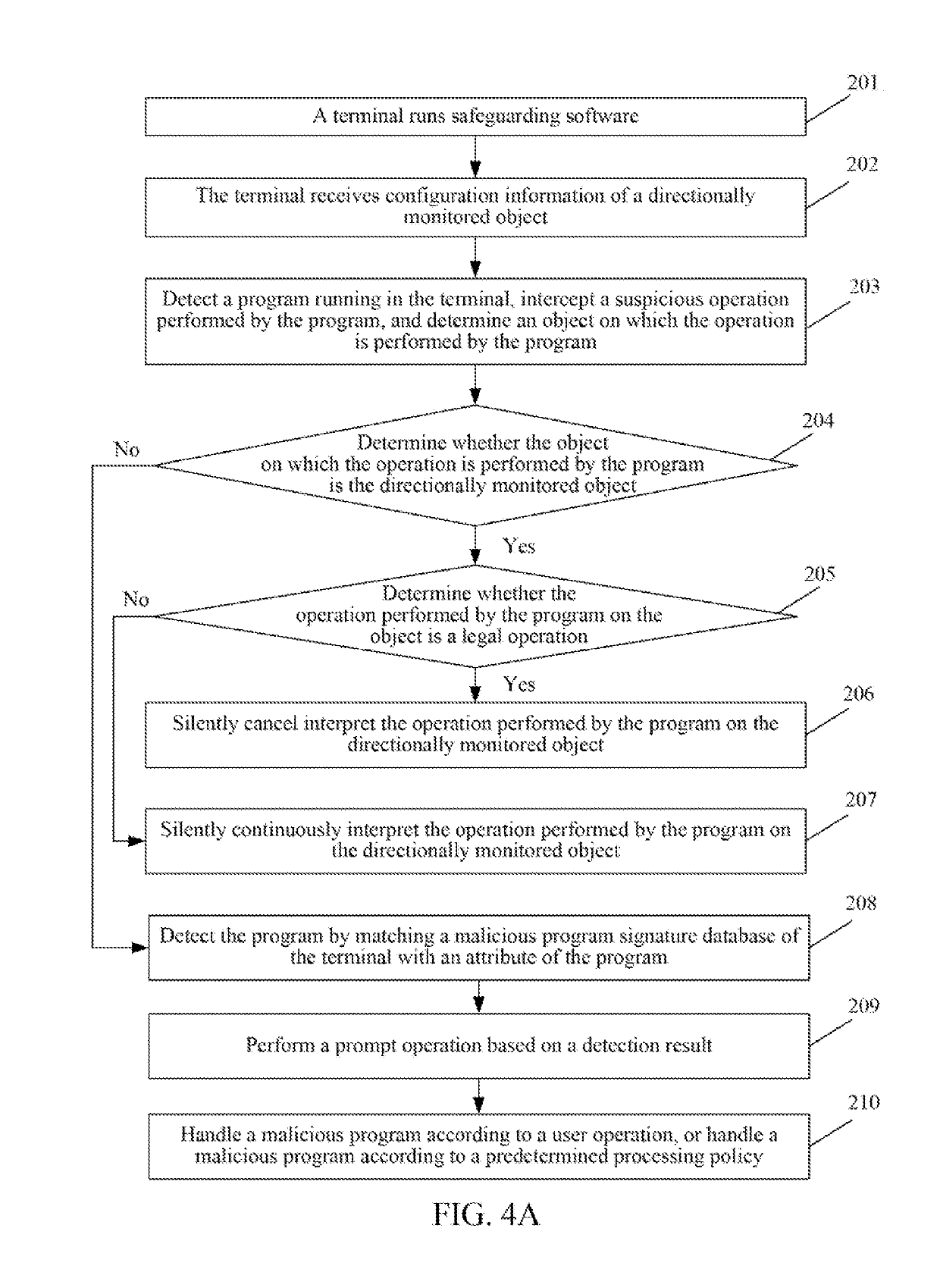
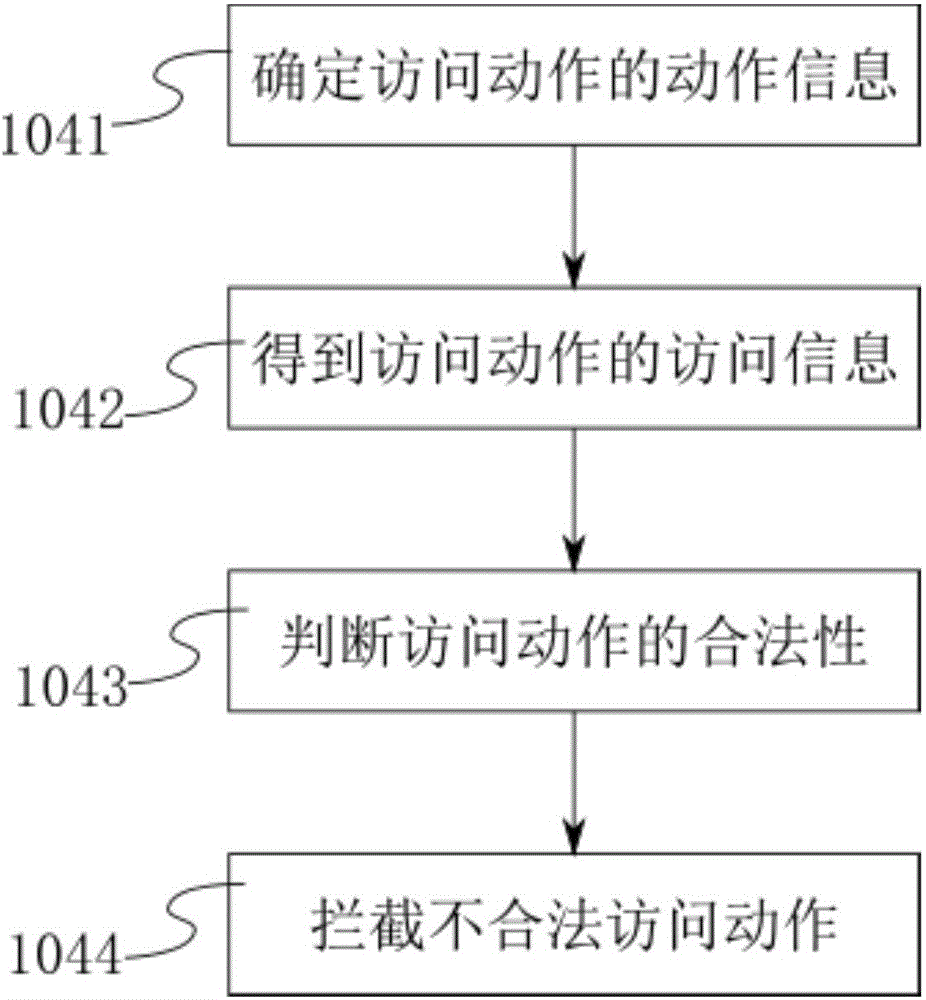
A safeguarding method, a safeguarding apparatus, and a computer storage medium are provided. The method includes detecting a program operating on a terminal, and intercepting an operation performed by the program; identifying an object on which the program performs the operation; obtaining configuration information of the object on the terminal, and determining, based on the configuration information, that the object is a targeted monitored object. The method further includes determining, based on the configuration information of the targeted monitored object, whether the operation performed by the program on the object is a legitimate operation; and canceling intercepting the operation if the operation is a legitimate operation, and continuously intercepting the operation if the operation is an illegitimate operation.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Self-service store system and self-service shopping method
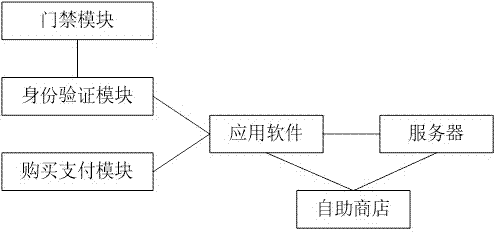
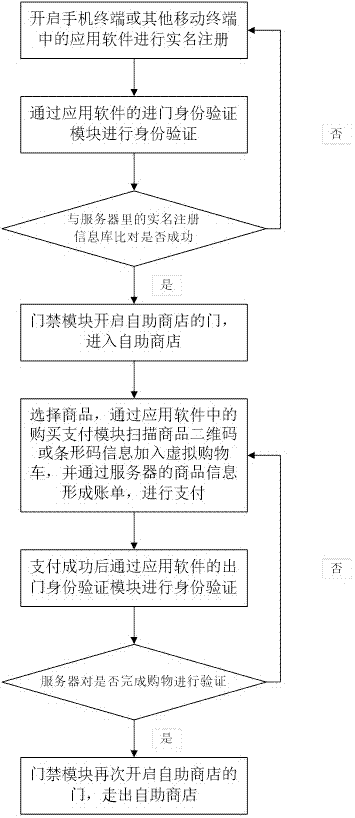
InactiveCN107025552ARealize offline purchase and online paymentSave human effortPayment architectureIndividual entry/exit registersPaymentBarcode
The present invention discloses a self-service store system, which includes a server, an application software, a self-service store and a door control module. The server is used for storing the real-name registration information and the commodity information, and judging whether the shopping information is completed or not. The application software is installed in a mobile phone. The application software comprises an identity authentication module and a purchase and payment module. The application software is in wireless connection with the server. The self-service store is used for displaying commodities provided with two-dimensional codes or barcodes. The door control module is arranged on the door of the self-service store and is used for controlling the opening / closing of the door through identity authentication. The door control module is in wireless connection with the identity authentication module. The identity authentication module comprises a door-entering identity authentication module used for authenticating whether the real-name registration is completed or not, and a door-exiting identity authentication module used for authenticating whether the shopping is completed or not. Based on the system, the mall queuing can be avoided, and the functions of on-line payment and offline purchase are realized. The manpower is saved. The system can be in operation for 24 hours, so that the system is very convenient to use. The subsequent return and right-safeguarding is facilitated. The system is simple to use. By adopting the real-name system, the safety of the self-service store is actively maintained.
Owner:罗星星
Take-out food monitoring system
PendingCN109151378AIncrease motivationImprove hygieneCo-operative working arrangementsClosed circuit television systemsQuality levelFood safety
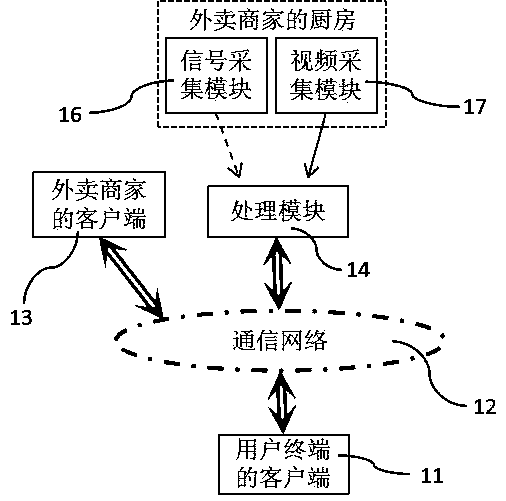
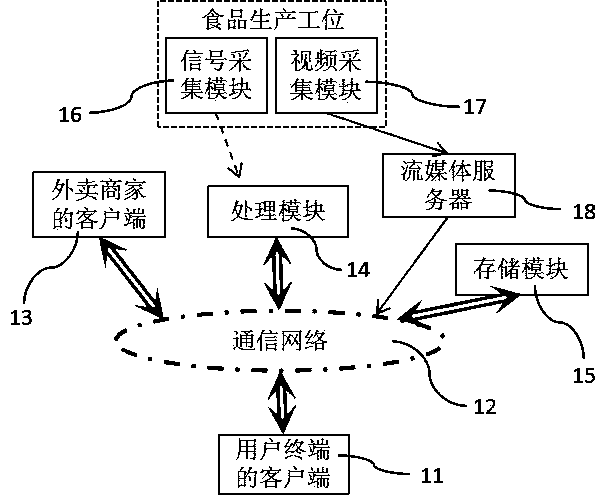
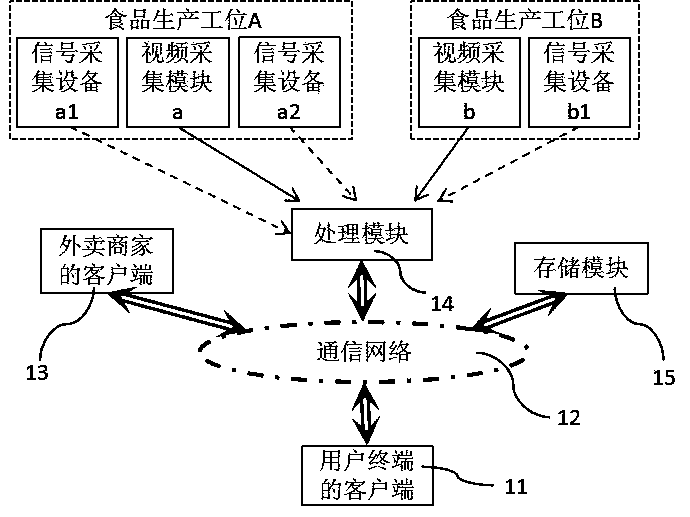
The invention discloses a take-out food monitoring system. A consumer is able to watch a real-time monitoring video of a take-out merchant kitchen by a client (11) of a user terminal and thus select atake-out merchant based on the environment of the take-out merchant kitchen and the freshness of the food. After the customer finds out a satisfied take-out merchant and satisfied food, ordering andpayment are carried out by the client (11) of the user terminal; the take-out merchant will send information to inform the consumer when carrying out food production; and when not being busy, the consumer can watch the live broadcasting video of the take-out food processing process at the client (11) of the user terminal and download the video into the user terminal for tracing and legal right safeguarding. Therefore, the take-out live broadcasting entertainment and interactivity are improved; the food safety is enhanced fundamentally; and thus the quality level of the take-out food is improved.
Owner:李志朋
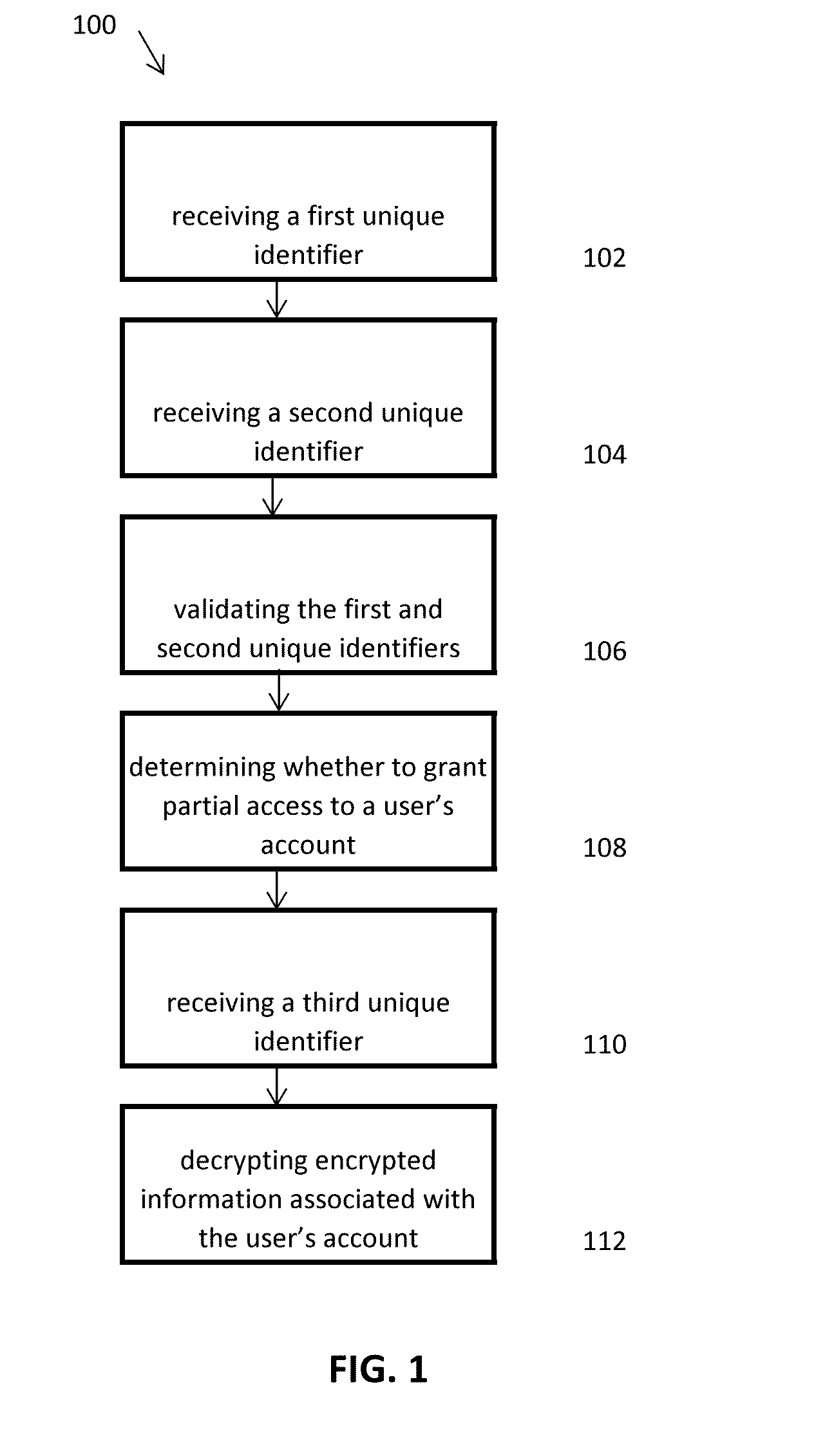
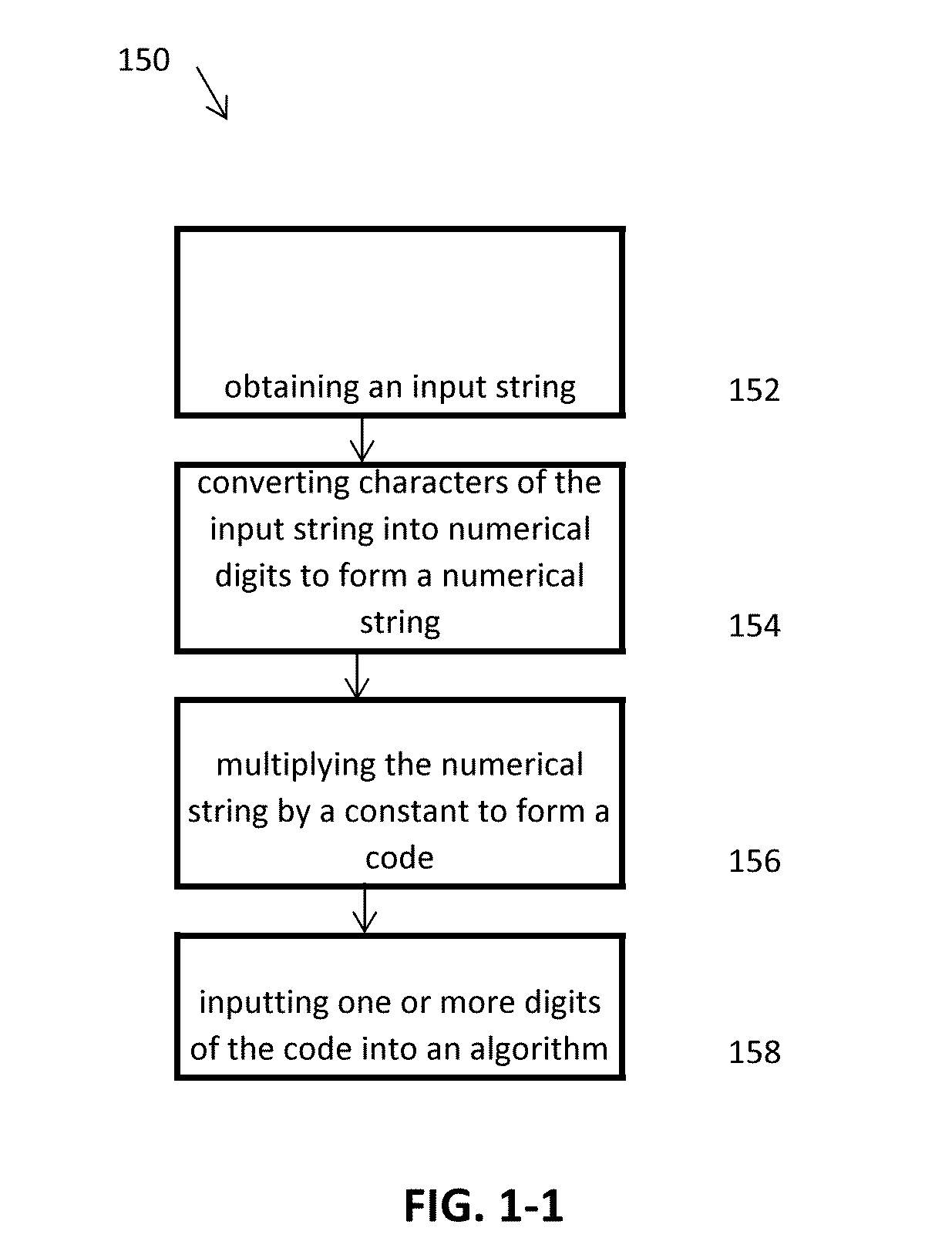
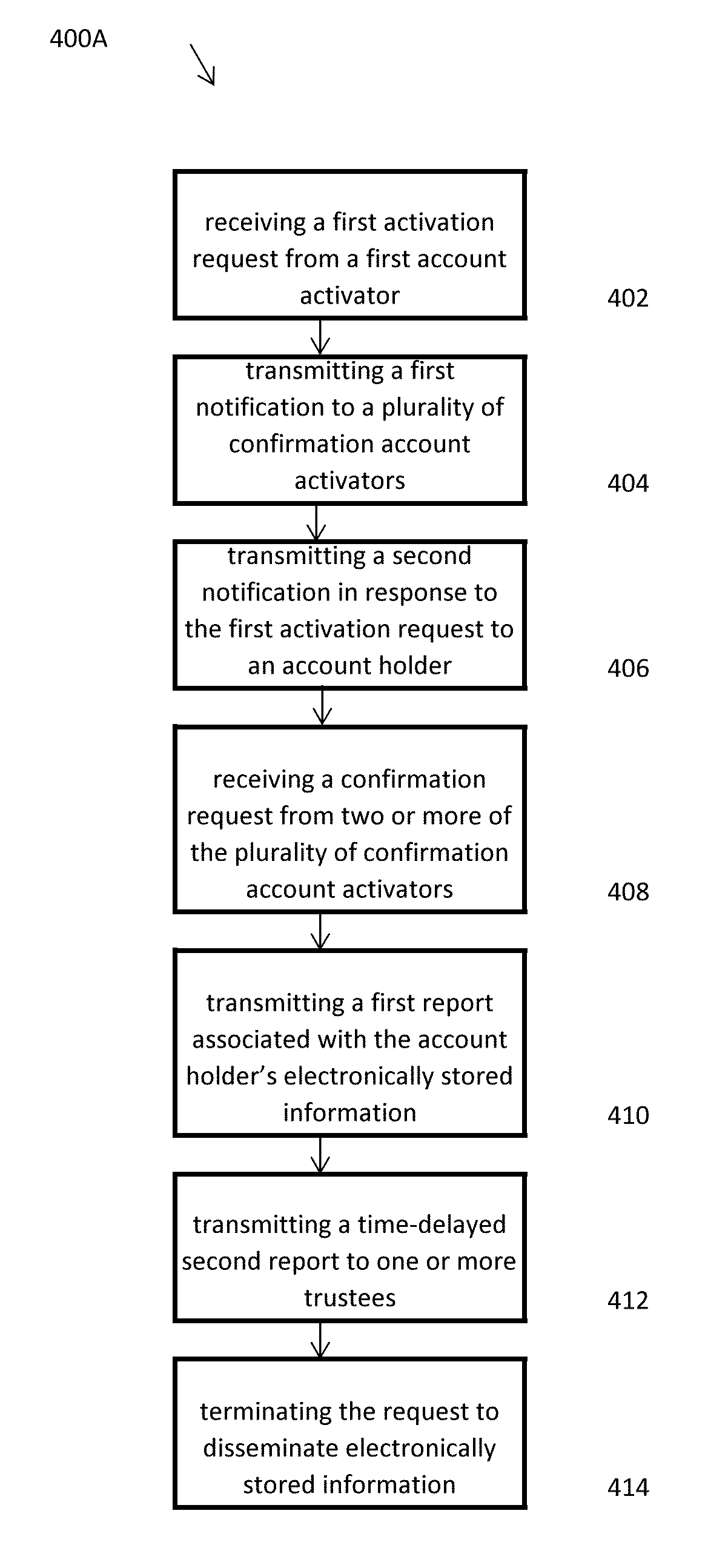
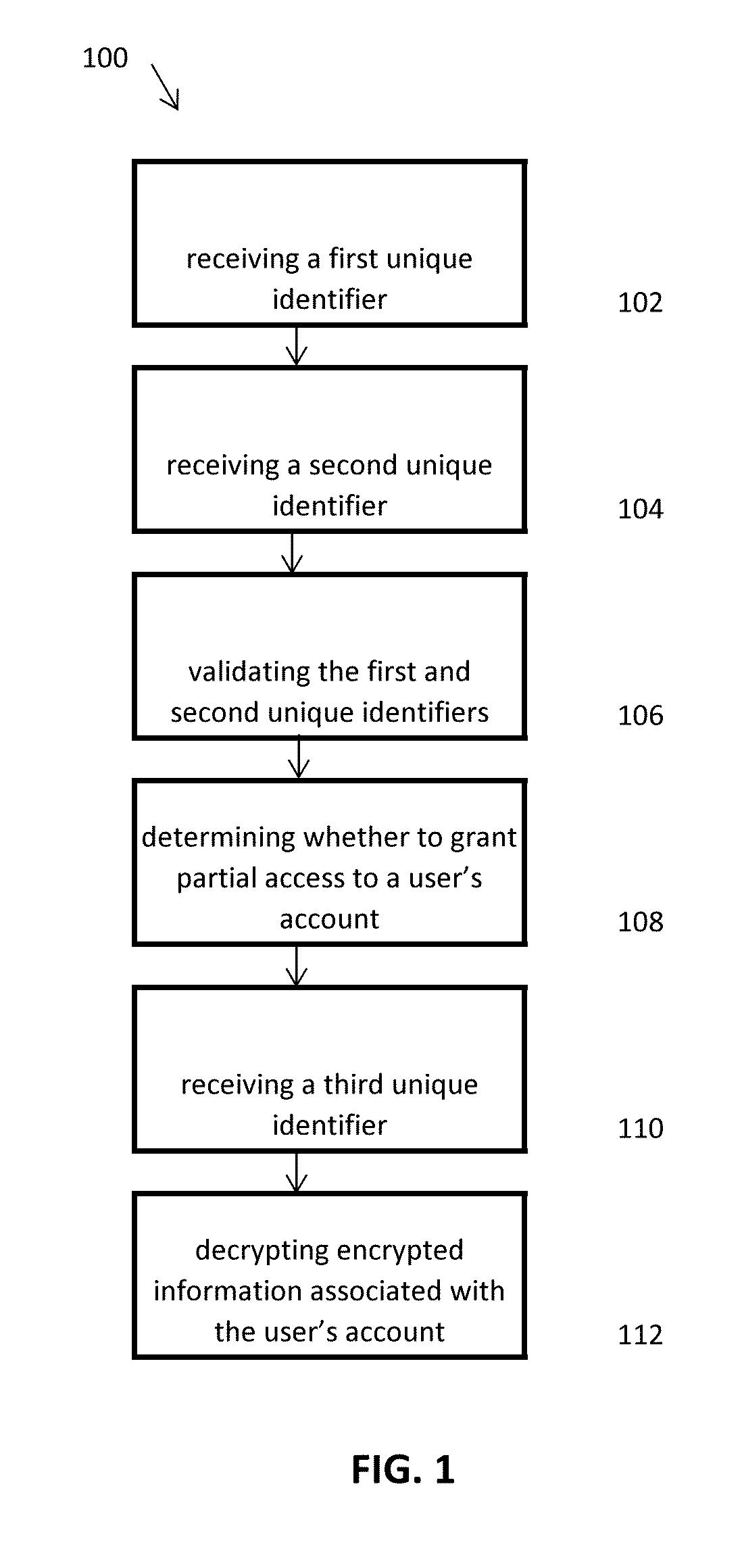
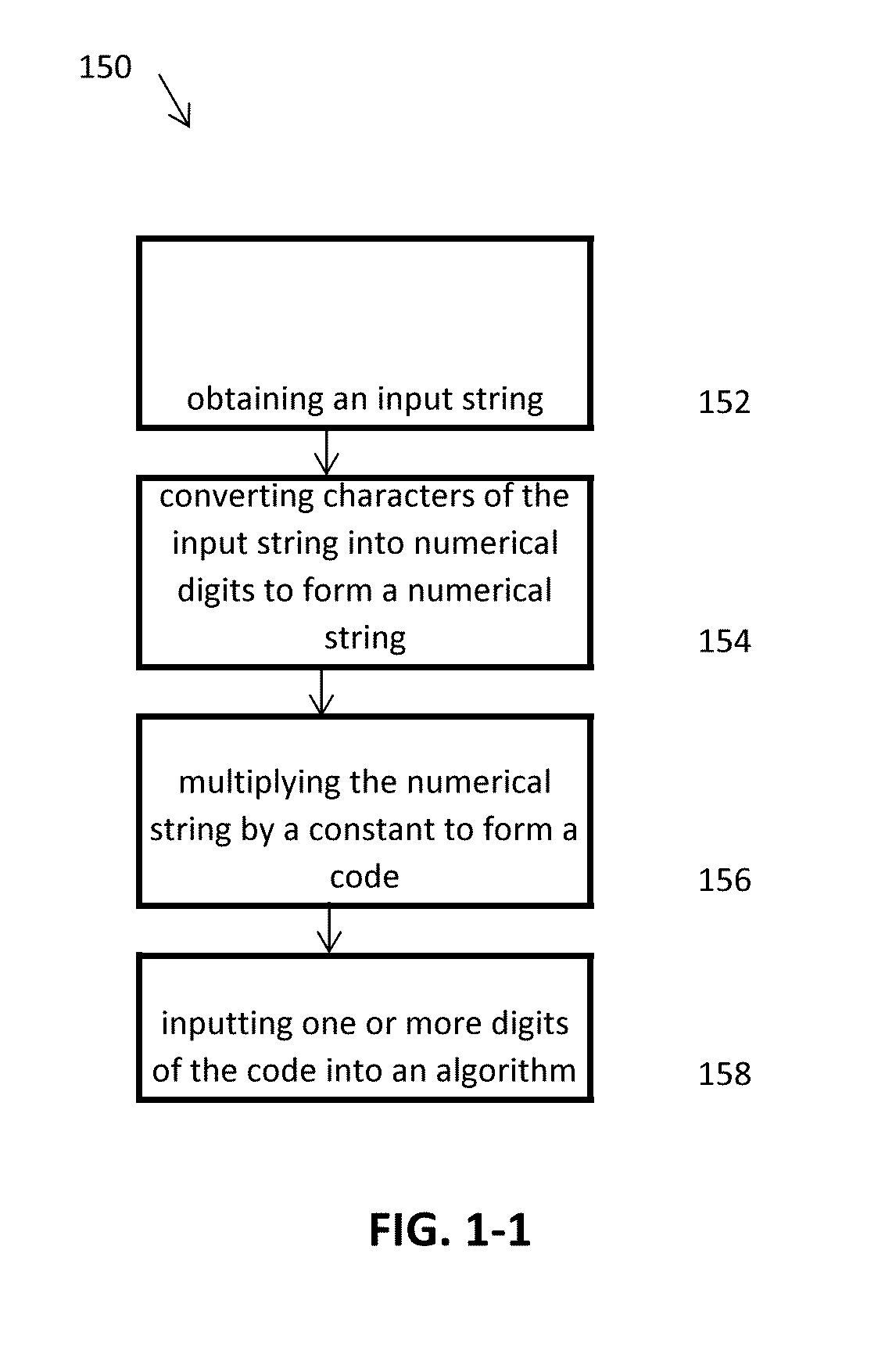
Methods, systems, and computer readable media for securely collecting, safeguarding, and disseminating electronically stored information
InactiveUS20140096267A1Good choiceEfficient managementDigital data processing detailsAnalogue secracy/subscription systemsInternet privacyComputer science
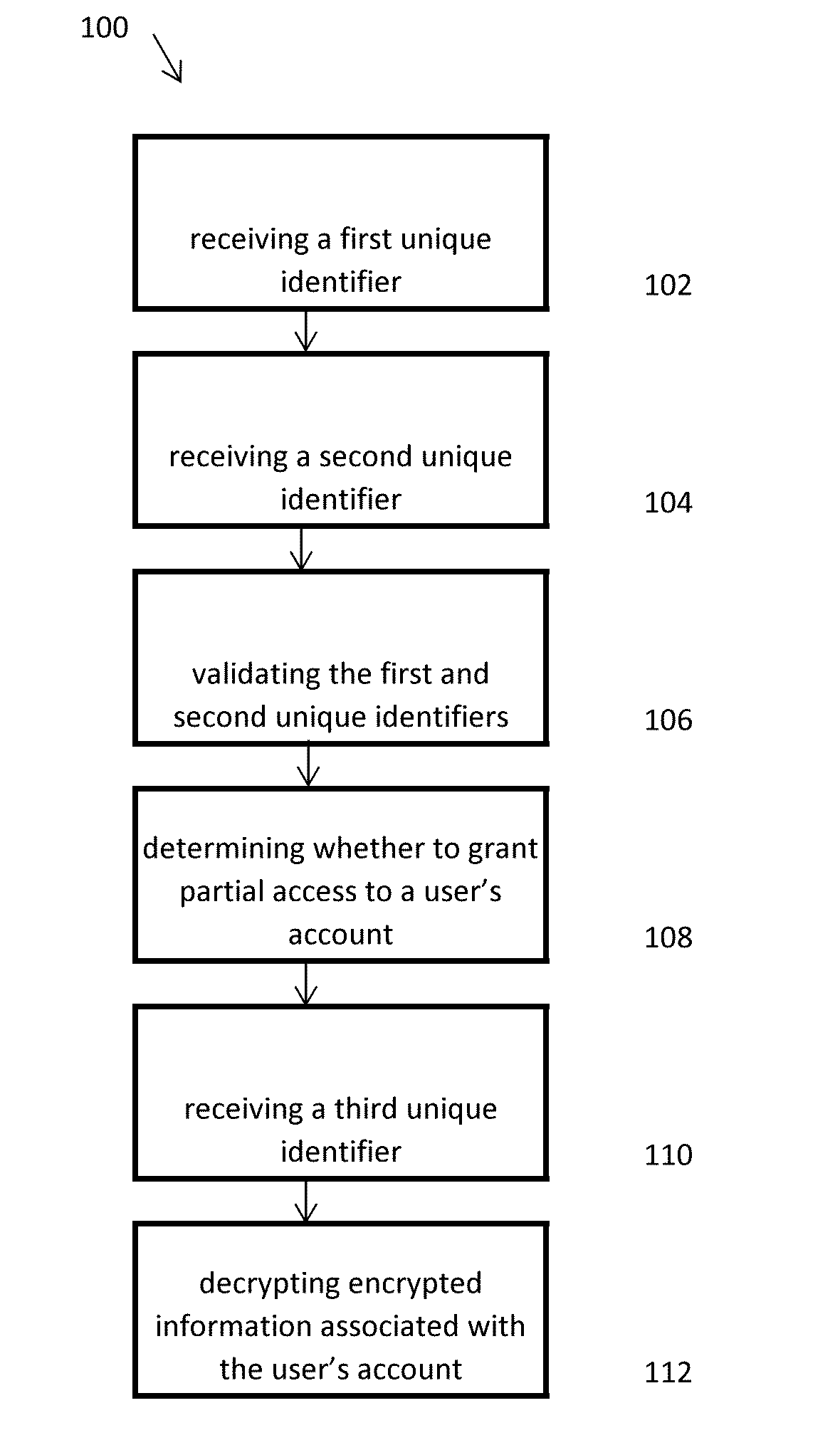
Applicant has created methods, systems, and computer readable media for securely collecting, safeguarding, and disseminating electronically stored information to facilitate an account owner's management of her personal, private, business, and legal documents. The method for safeguarding can include a double authentication process that only grants exclusive access to an account owner's encrypted information through the use of a uniquely generated security key. The method for collecting information can include a real-time encryption process to permit an account holder to securely upload and store electronic media in category-based compartmentalized locations. Further, the method can include a process for generating category-based advertisements through an integrated marketing platform with geo-fencing capabilities to facilitate the account owner's selection of a variety of services related to the stored information. Finally, the method for disseminating information can include authenticating a request to disseminate the stored information to one or more trustees.
Owner:CASSO ROBERTO M
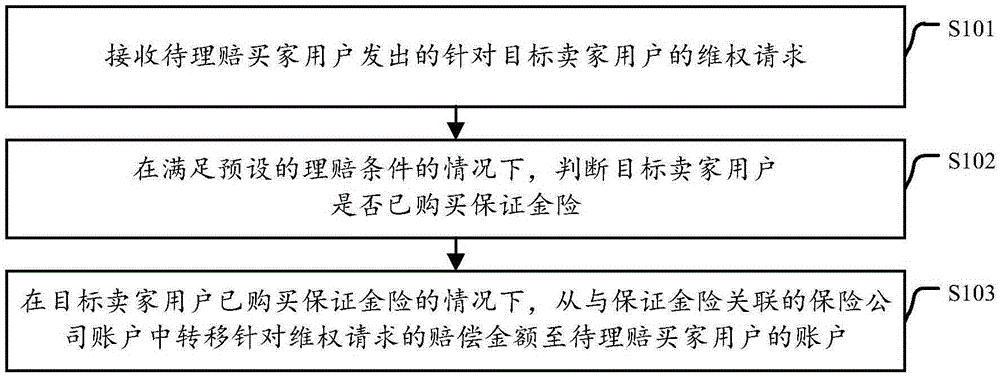
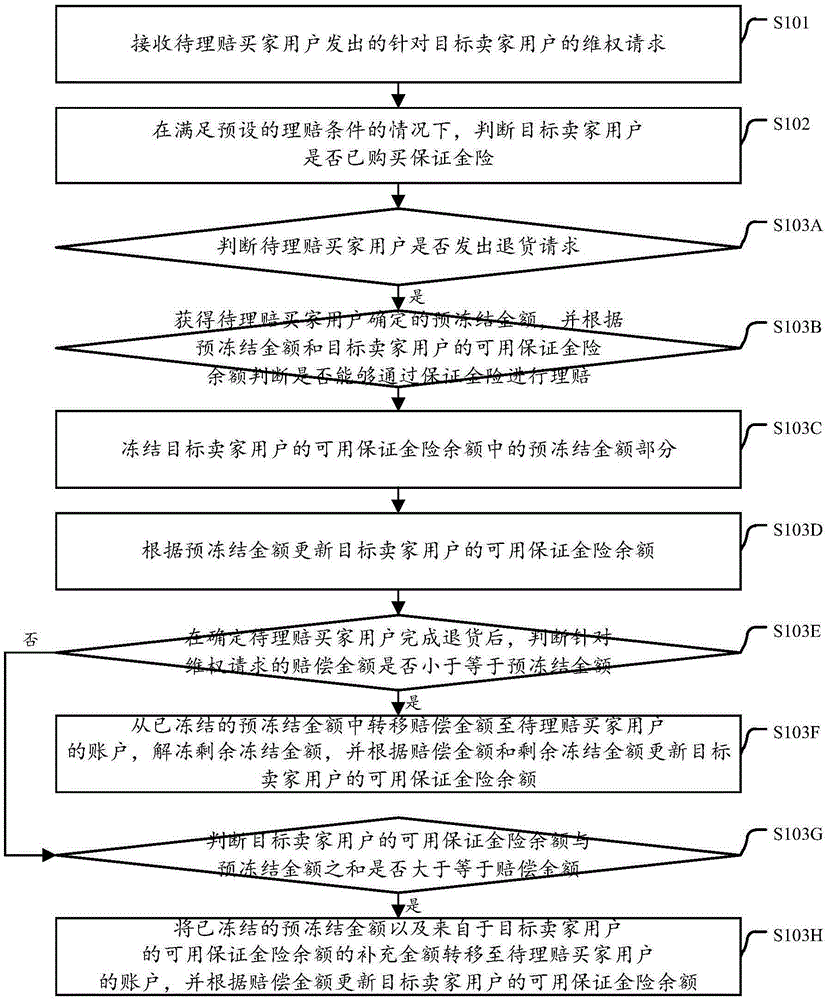
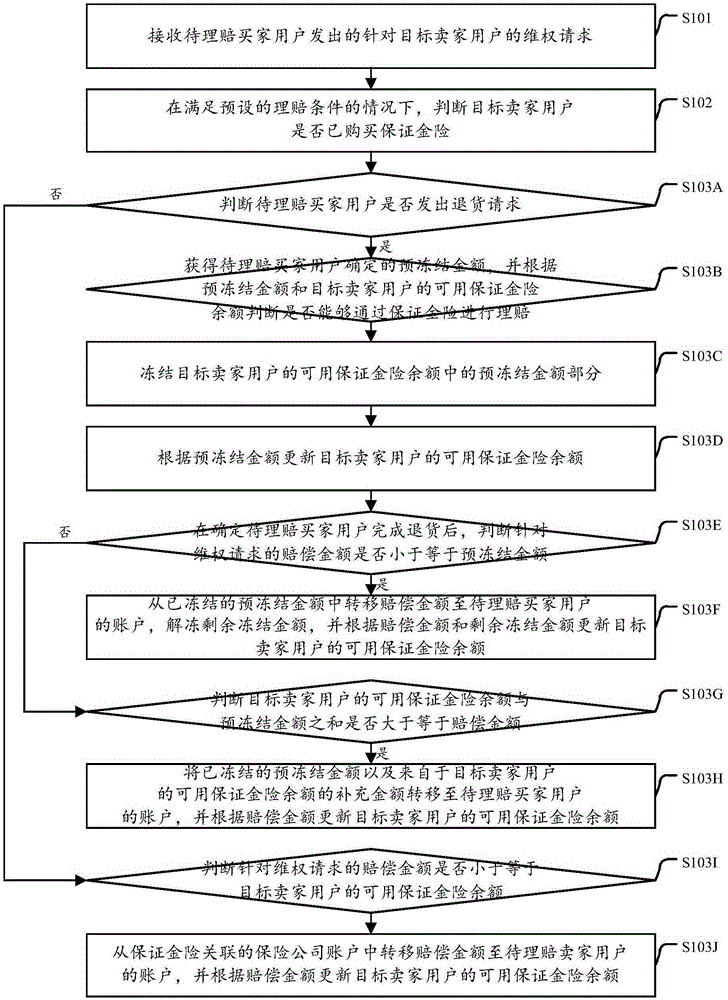
Online transaction settlement processing method and device
InactiveCN106600353AIncrease flexibilityGood reputationBuying/selling/leasing transactionsComputer scienceDatabase
The invention discloses an online transaction settlement processing method and a device. The online transaction settlement processing method comprises the steps of receiving a right safeguarding request sent from a to-be-settlement buyer user and aiming at a target seller user; on the condition that a preset settlement condition is met, judging whether target seller user already purchases a deposit insurance or not, wherein the deposit insurance is an insurance that is paid in advance by an insurance company associated with the deposit insurance when the seller user has no available funds; on the condition that the target seller user already purchases the deposit insurance, transferring the amount of compensation specified in the right safeguarding request to the account of the to-be-settlement buyer user from the account of the insurance company associated with the deposit insurance. According to the embodiments of the present invention, the claim processing process is conducted and the operation cost is reduced. The flow flexibility of funds is improved.
Owner:ALIBABA GRP HLDG LTD
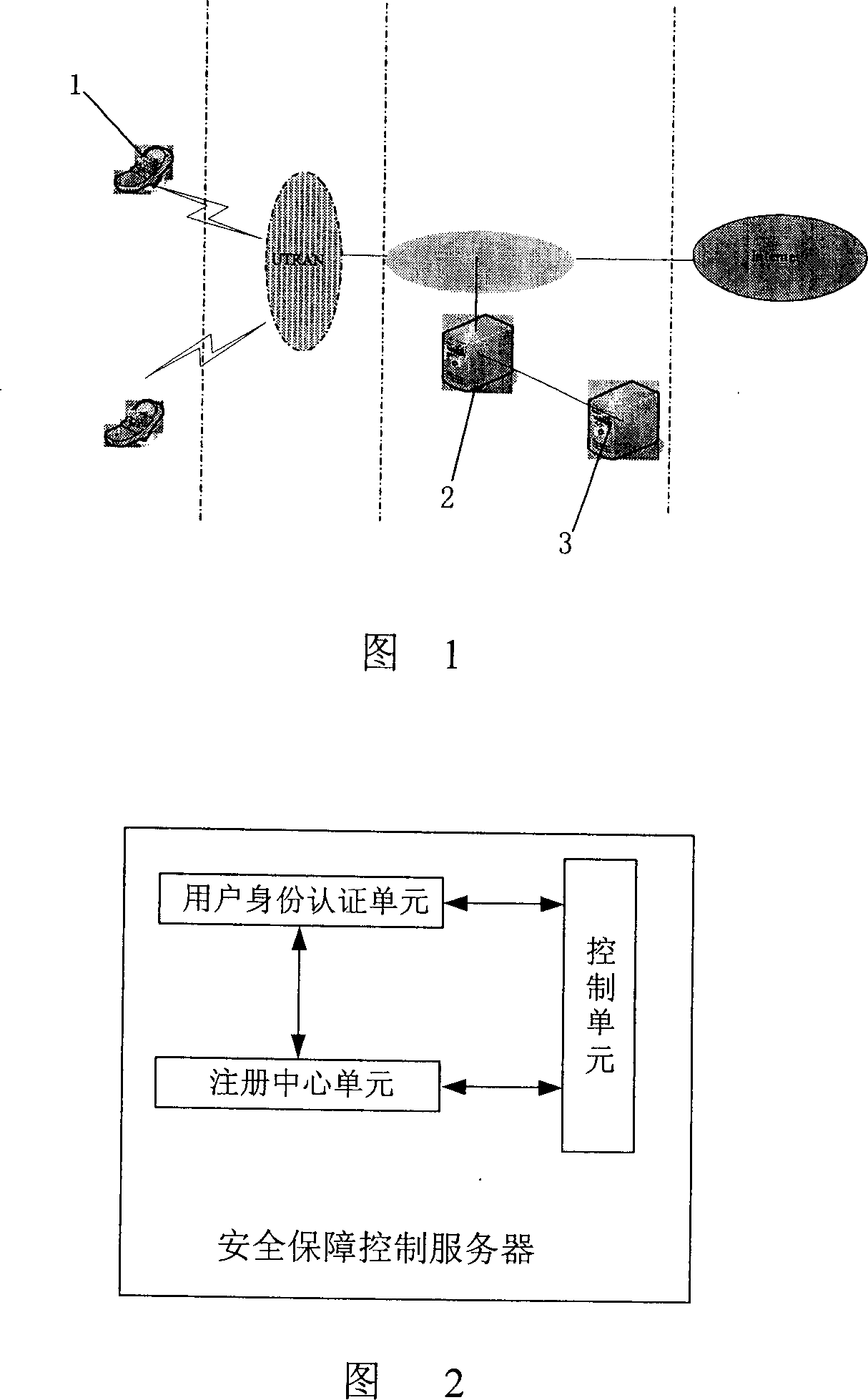
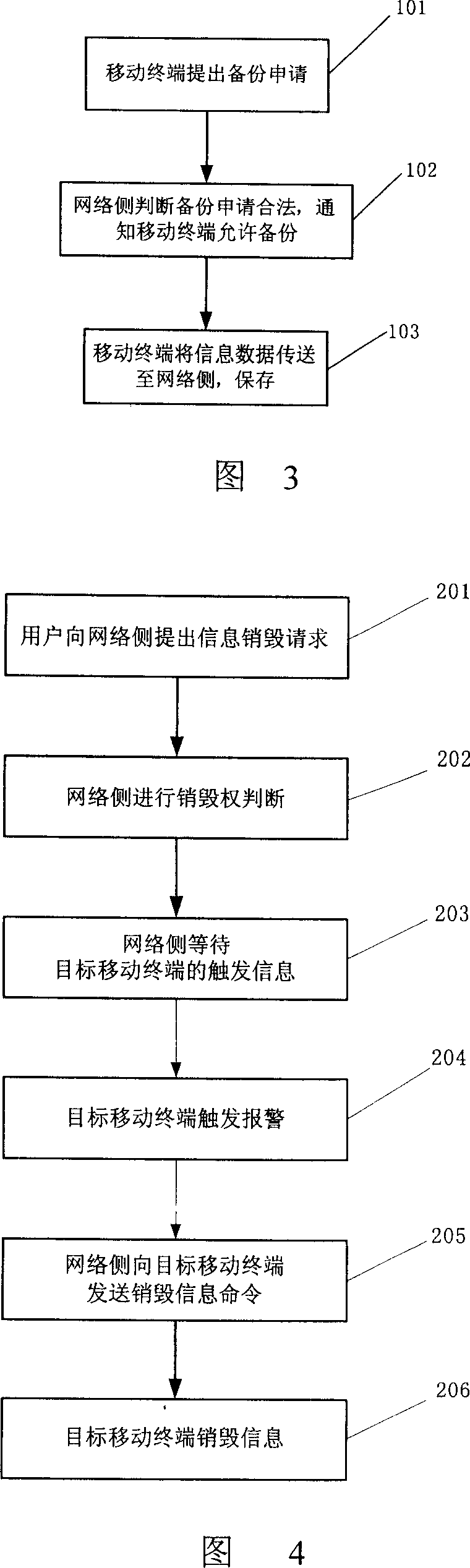
Mobile terminal information resource safety security control and realizing method
InactiveCN1980460AImplement backupAchieve destructionRadio/inductive link selection arrangementsSecurity arrangementComputer networkInformation resource
This system consists of mobile terminals (MT), the safeguard control server (SCS) and the net-side database (ND). SCS controls the MT info operation. SCS connects directly to ND. MTs connect with SCS via wireless accessing net. This invention also discloses a MT info resource safeguarding method to spare the MT info. After MT is lost, MT info can be restored or the info in MT can be auto destroyed. These reduce effectively the loss of info losing or info leakage due to losing the handset.
Owner:ZTE CORP
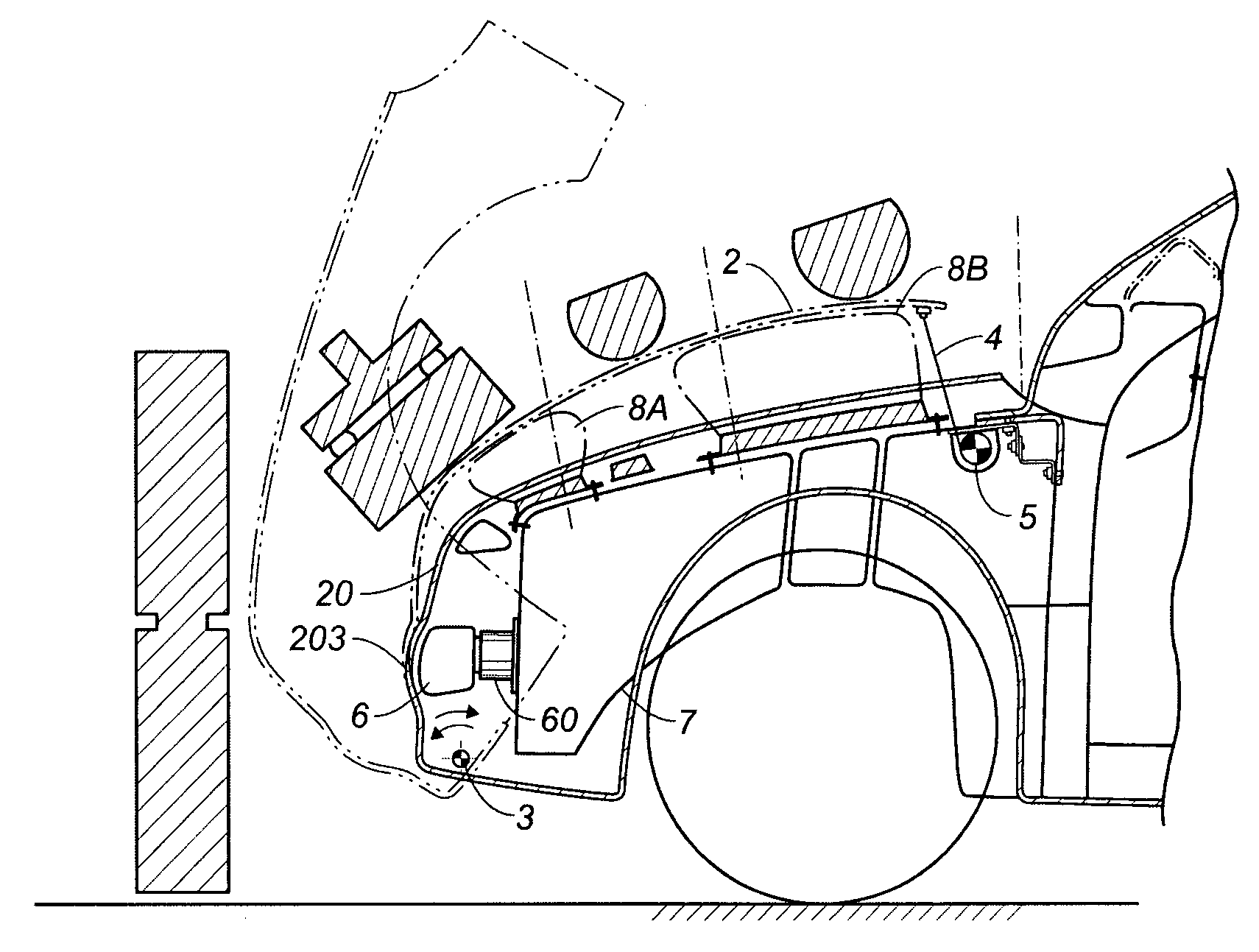
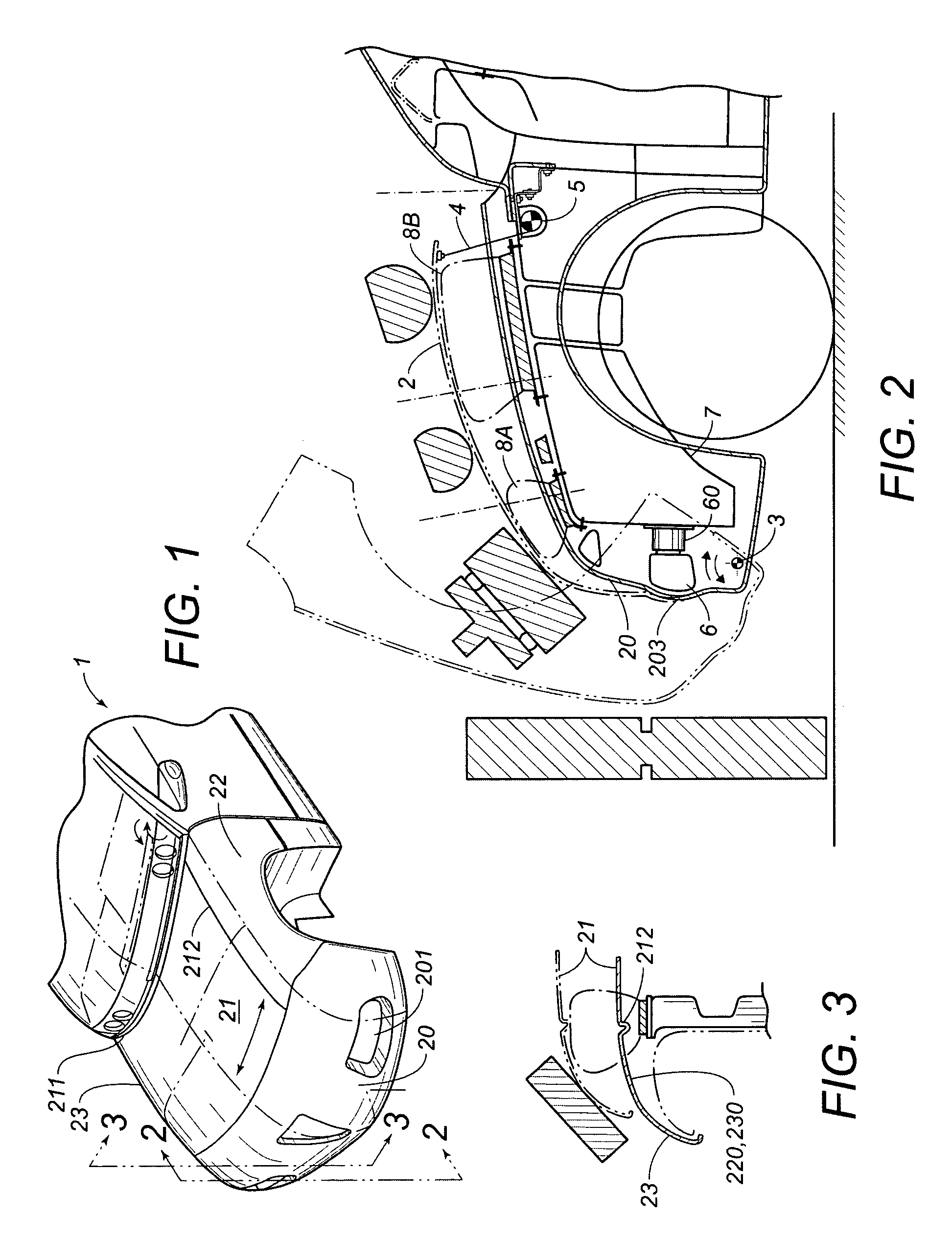
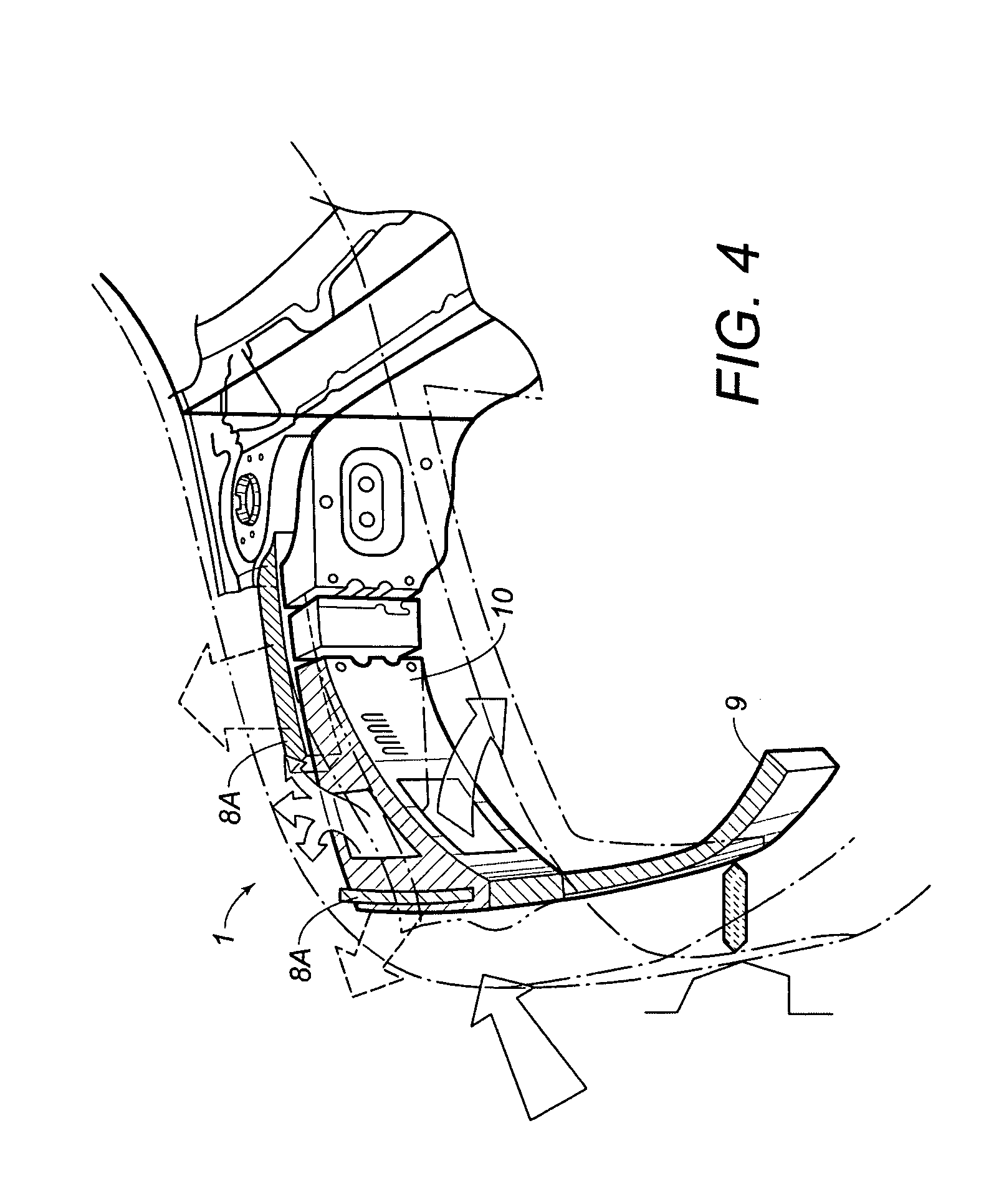
Structure for the front of a vehicle, of the type with control of the deformation for the safeguard of the pedestrian
InactiveUS7004532B2Vehicle seatsPedestrian/occupant safety arrangementEngineeringDeformation control
Structure for the front of a vehicle, of the type with deformation control for the safeguarding of pedestrians, cooperating with a sensor to detect approaching or actual impacts and including at least one air bag placed below the front bonnet component, and the front part of the vehicle having a “soft nose” shape The structure includes at least a frontal interchangeable pre-assembled module, made of a thermoplastic material that includes the motor bonnet covering, the bumper covering and the covering of the mudguards, respectively left and right, the pre-assembled module, in correspondence with the front side, is hinged underneath the front of the vehicle, and where at least on one side is deformable or capable of being raised by air bags placed under the module interacting with the sensor, while maintaining the rear portion coupled.
Owner:PLASTAL SPA
Down-hole danger-removing rescue capsule
InactiveCN101519974AHigh process feasibilityMature and reliable technical measuresSafety equipmentsHuman wasteCommunications system
The invention relates to a down-hole danger-removing rescue capsule, relating to the technical field of danger-removing rescue. The technical problem to be solved is to remove dangers in operation construction sites under mines. The danger-removing rescue capsule comprises a steel hollow sealing capsule, a passive life support system and a communication which can connect communication cables of a command center in communication equipment in the capsule; two ends of the capsule are provided with at least one unsealing capsule door; the capsule is internally provided with a fireproof insulating layer; the capsule is provided with at least one observing window; the bottom part of the capsule is provided with at least one group of rail wheels; the capsule is provided with a communication crossing capsule part; the capsule is externally provided with a lifting lug; and the passive life support system comprises an air regenerating device, a carbon monoxide removal device, an air purifying device, food, drinking water safeguarding articles, and a body excretion disposal device. The down-hole danger-removing rescue capsule has long period for removing dangers, low cost for manufacturing and operating, long service life and high cost performance.
Owner:蔡建 +1
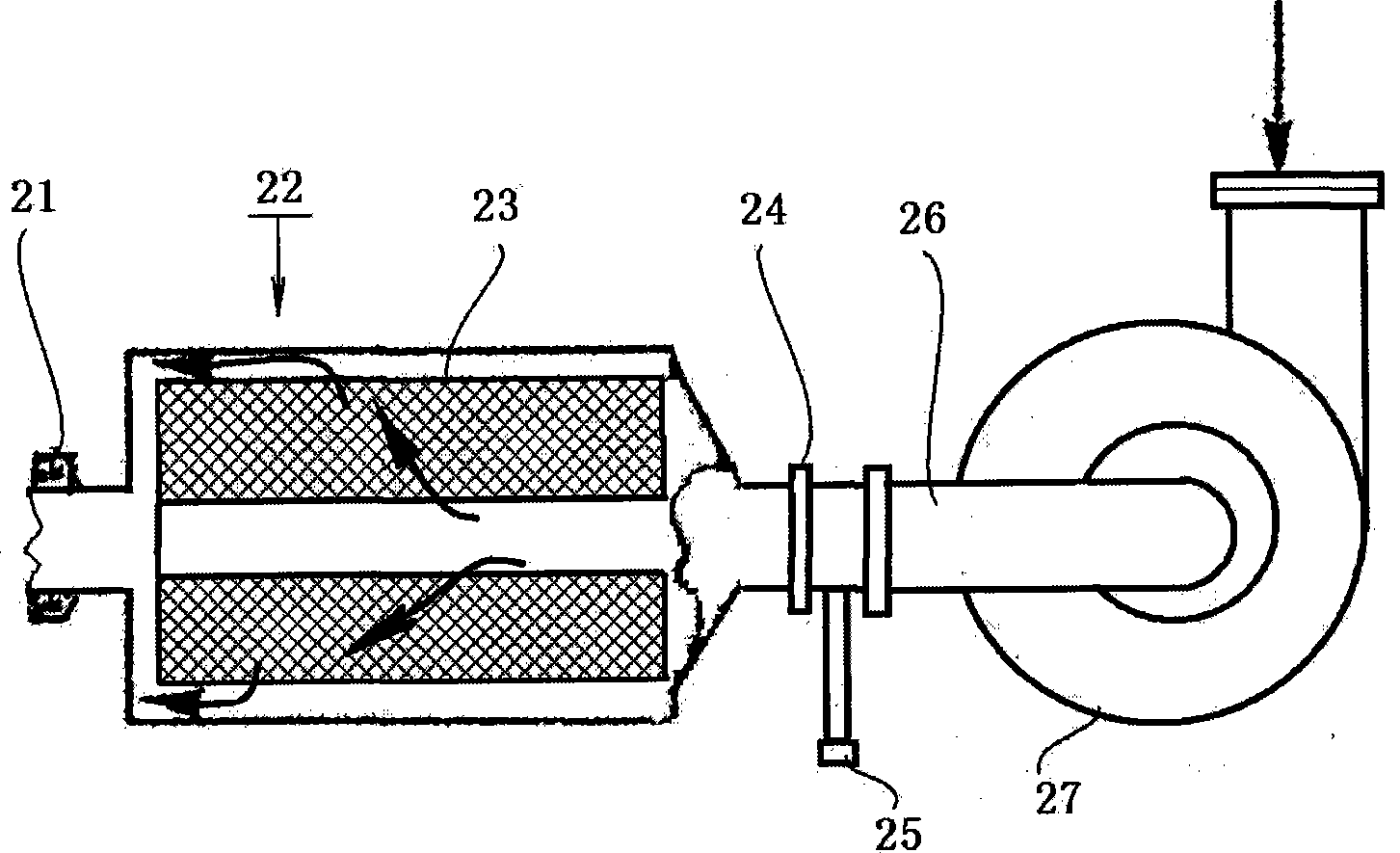
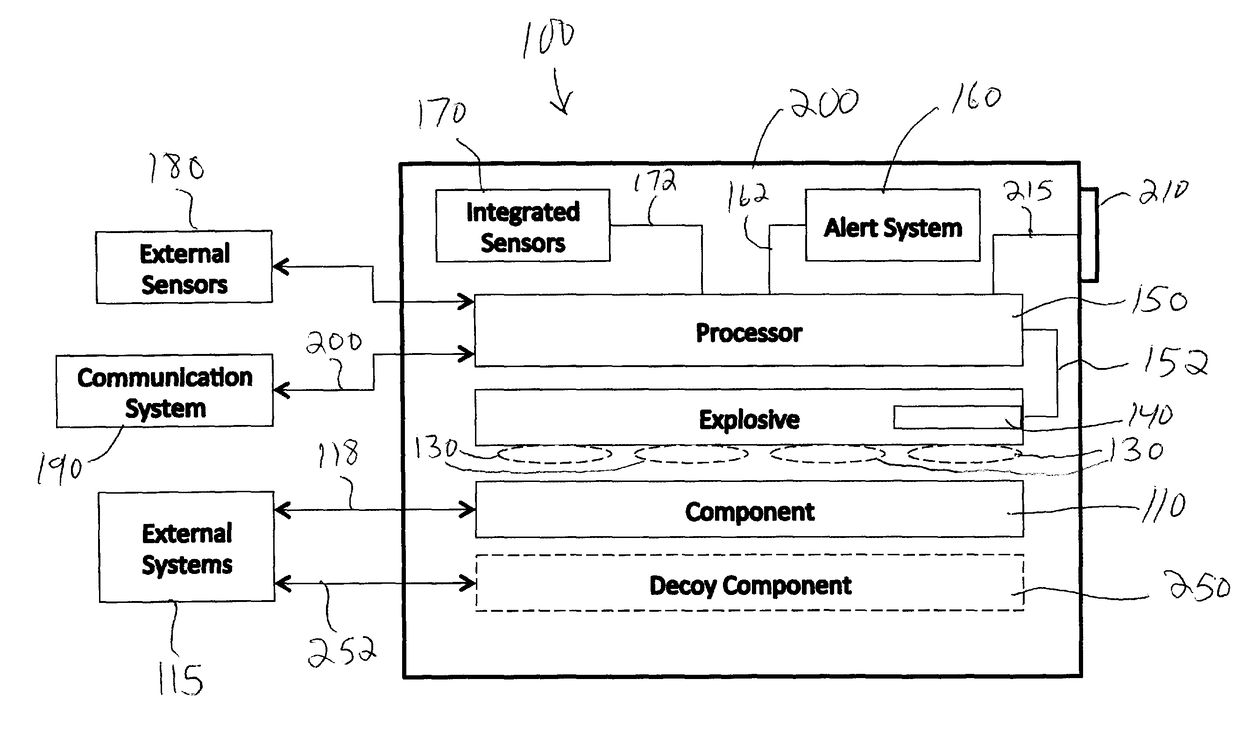
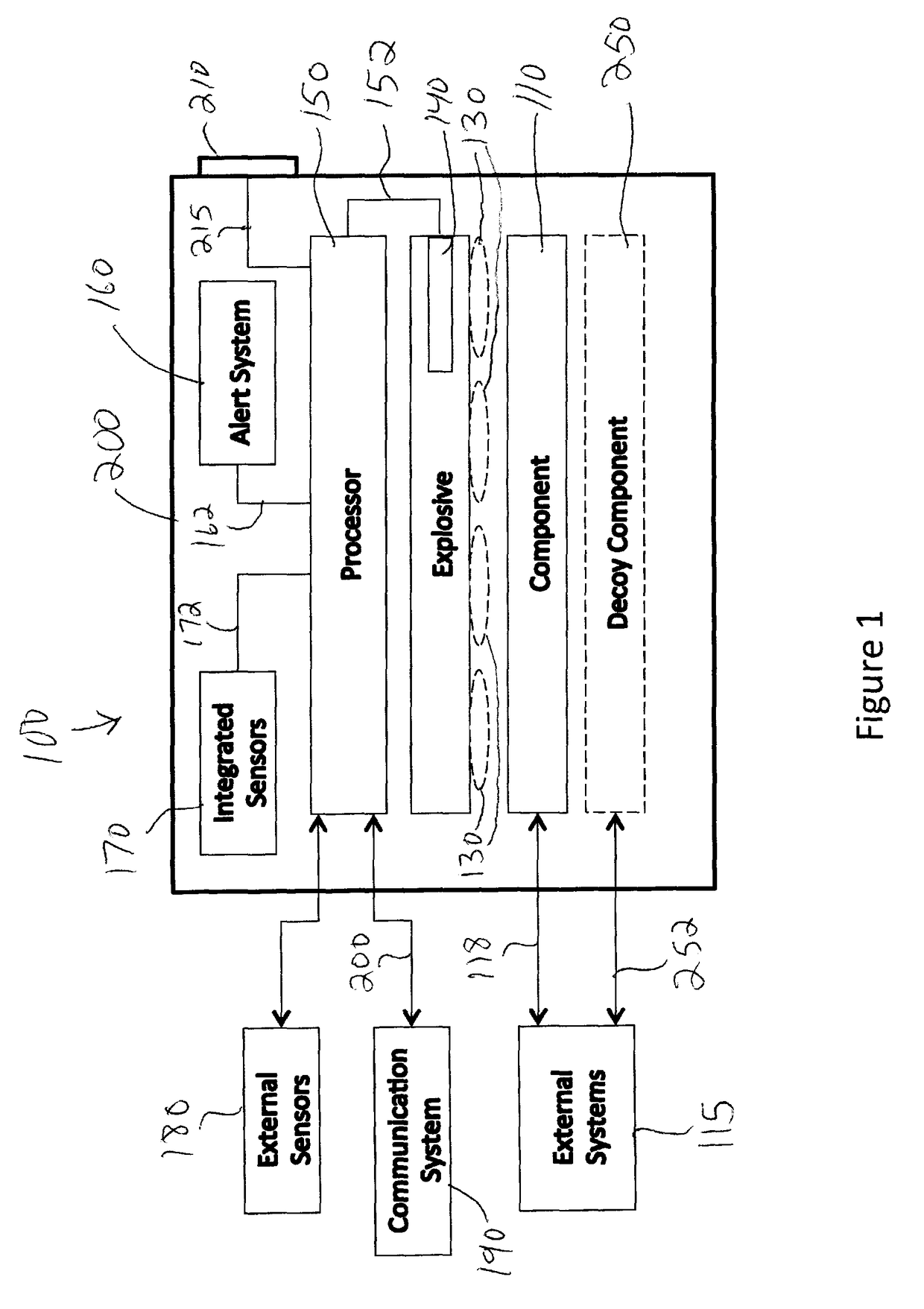
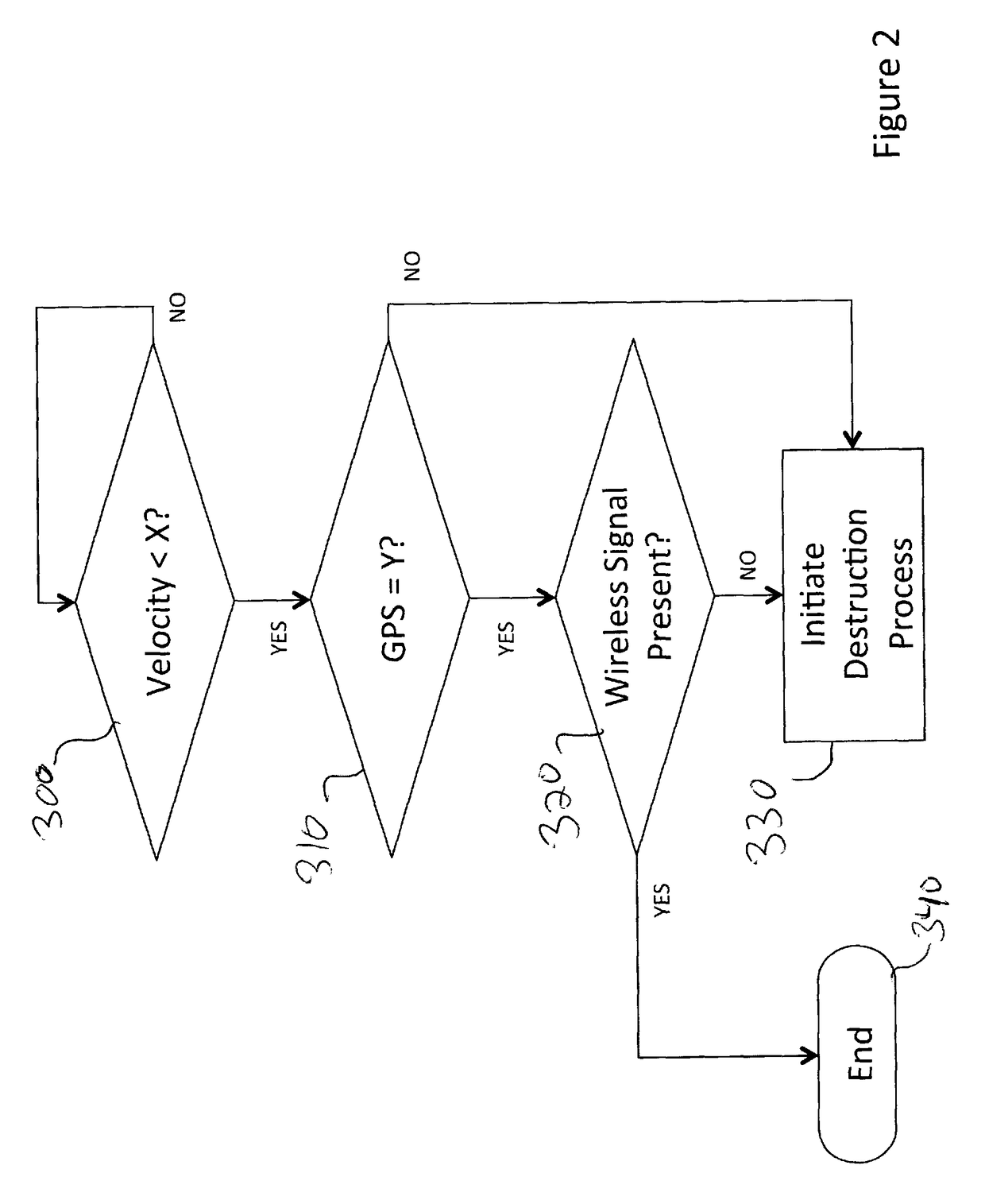
System and method for autonomous or remote controlled destruction of stored information or components
A system and method are provided for the destruction of electronically stored information and / or components that incorporated sensitive technology or that contain sensitive information upon the occurrence of one or more predetermined events. The system and method of the present invention is particularly suited for the safeguarding of electronically stored information and / or classified technology in systems deployed in an operational environment. The system and method of the present invention be incorporated into drones, full size aircraft, any type of vehicle, mines, missiles, torpedos, bombs, phones, cameras, robots, satellites or other spacecraft, computers, hard drives, thumb drives, switches, routers, bugs, brief cases, safes, and generally any device that utilizes components on which sensitive data is stored or components that utilize technology that should only be accessed by authorized personnel.
Owner:PAHMET
Computer network account number safety protecting method and serving system
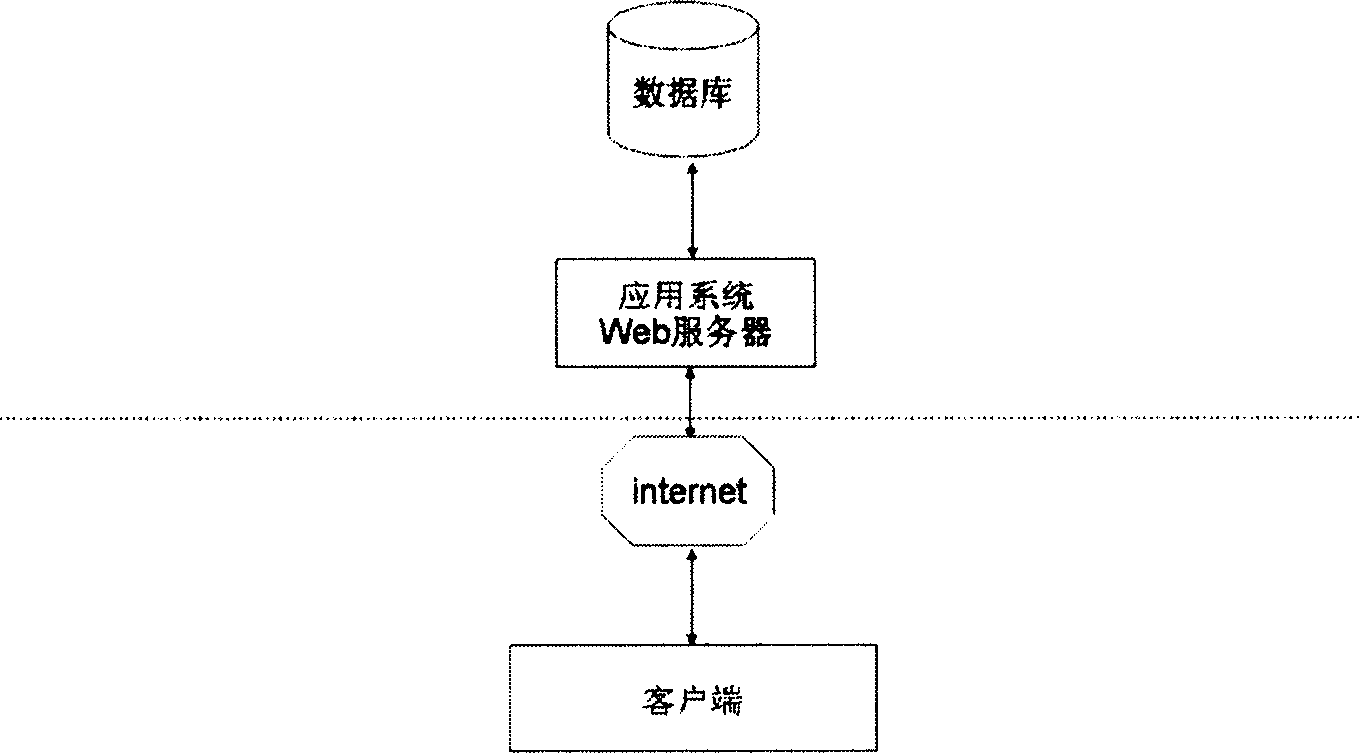
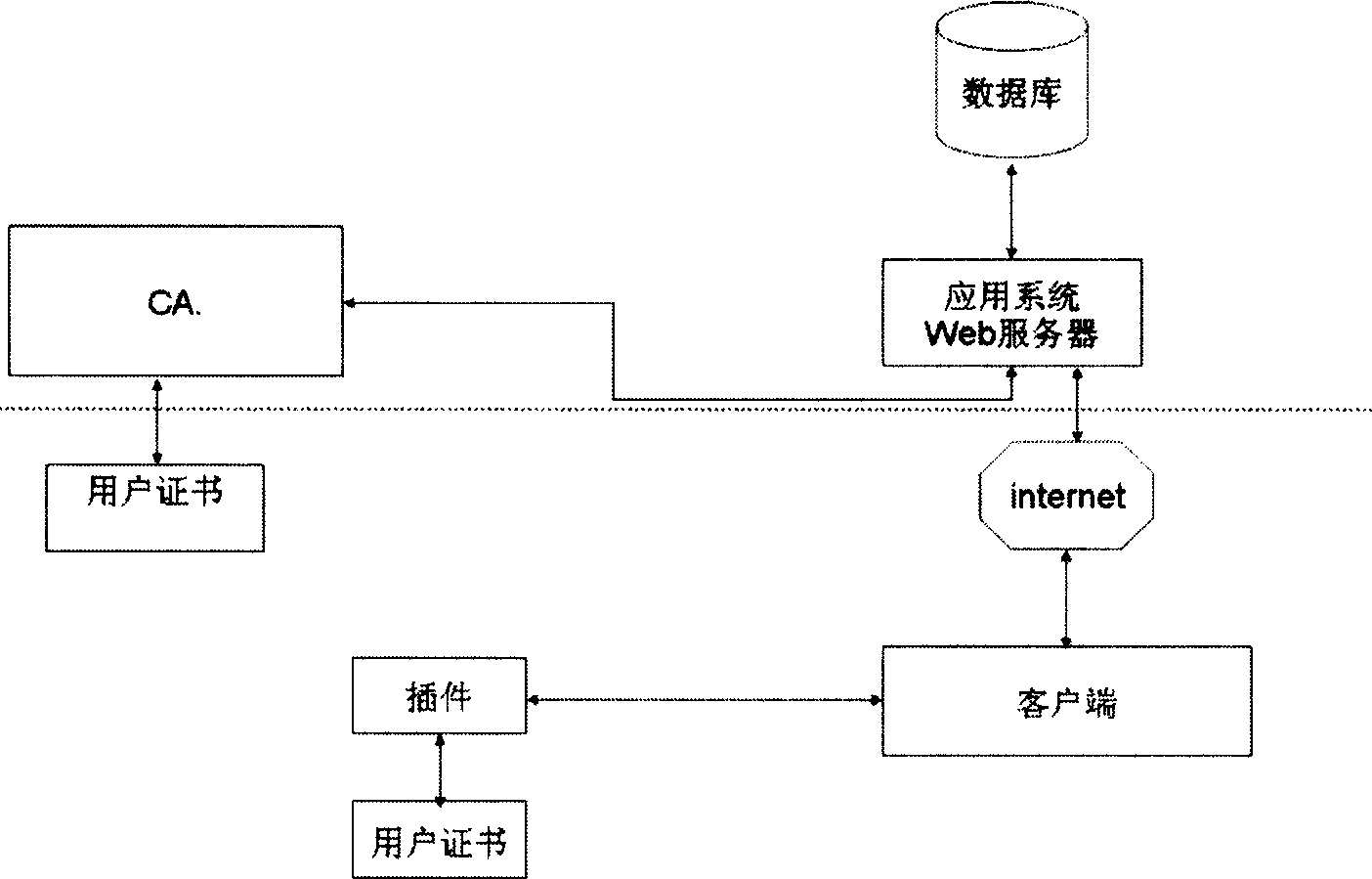
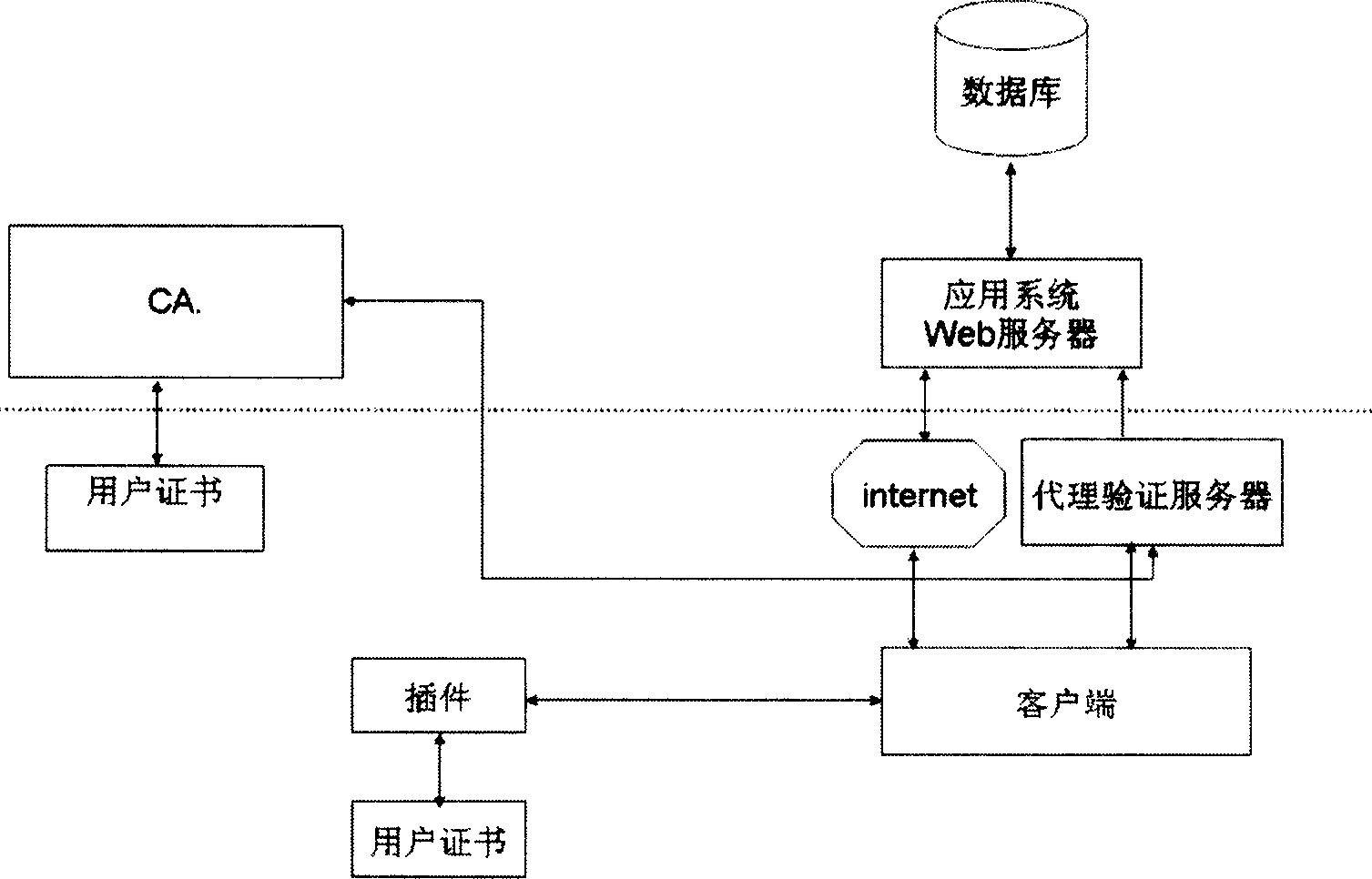
InactiveCN1905448AAvoid safety hazardsFilling in the gaps in safe usage questionsUser identity/authority verificationWeb serviceClient-side
The invention relates to a computer network account safeguarding method, comprising the steps of: at first use, modifying valid evidence at server end to verify user ID by an agent verifying server and storing the modified result into USB plug-in unit connected with user terminal; at later use, firstly verifying request of client end by the agent verifying server through other verifying method; when the request passes, the agent verifying server will send valid evidence to verifying user ID to the server end so as to implement user logon. And a service system for implementing the safeguarding method comprises: USB safety plug-in unit connected with user terminal, database and application system Web server, as well as agent verifying server for sending client end secret information and modifying secret information. And it radically prevents the possibility of sealing users valid evidences from client ends by illegal means.
Owner:代飞
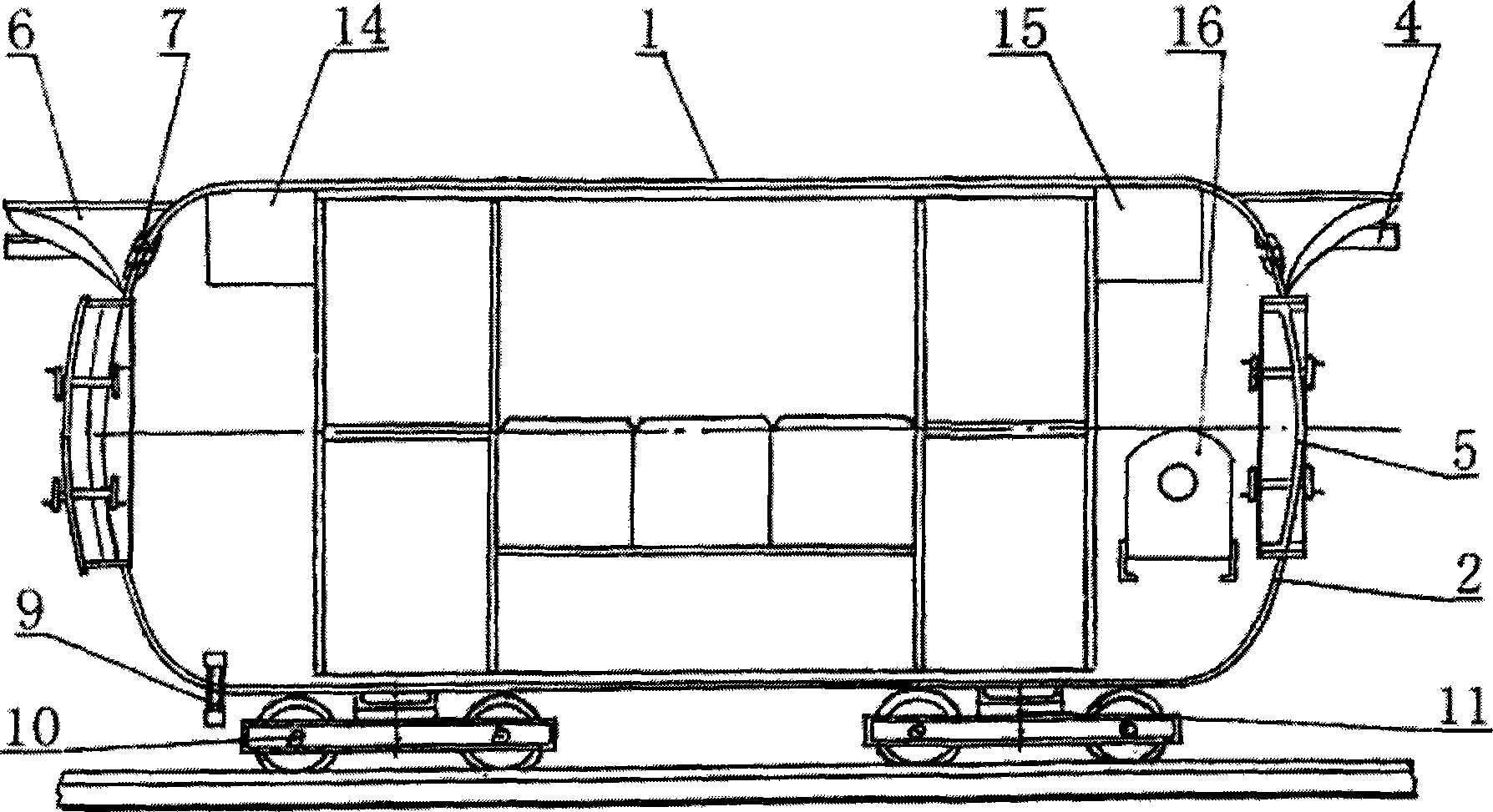
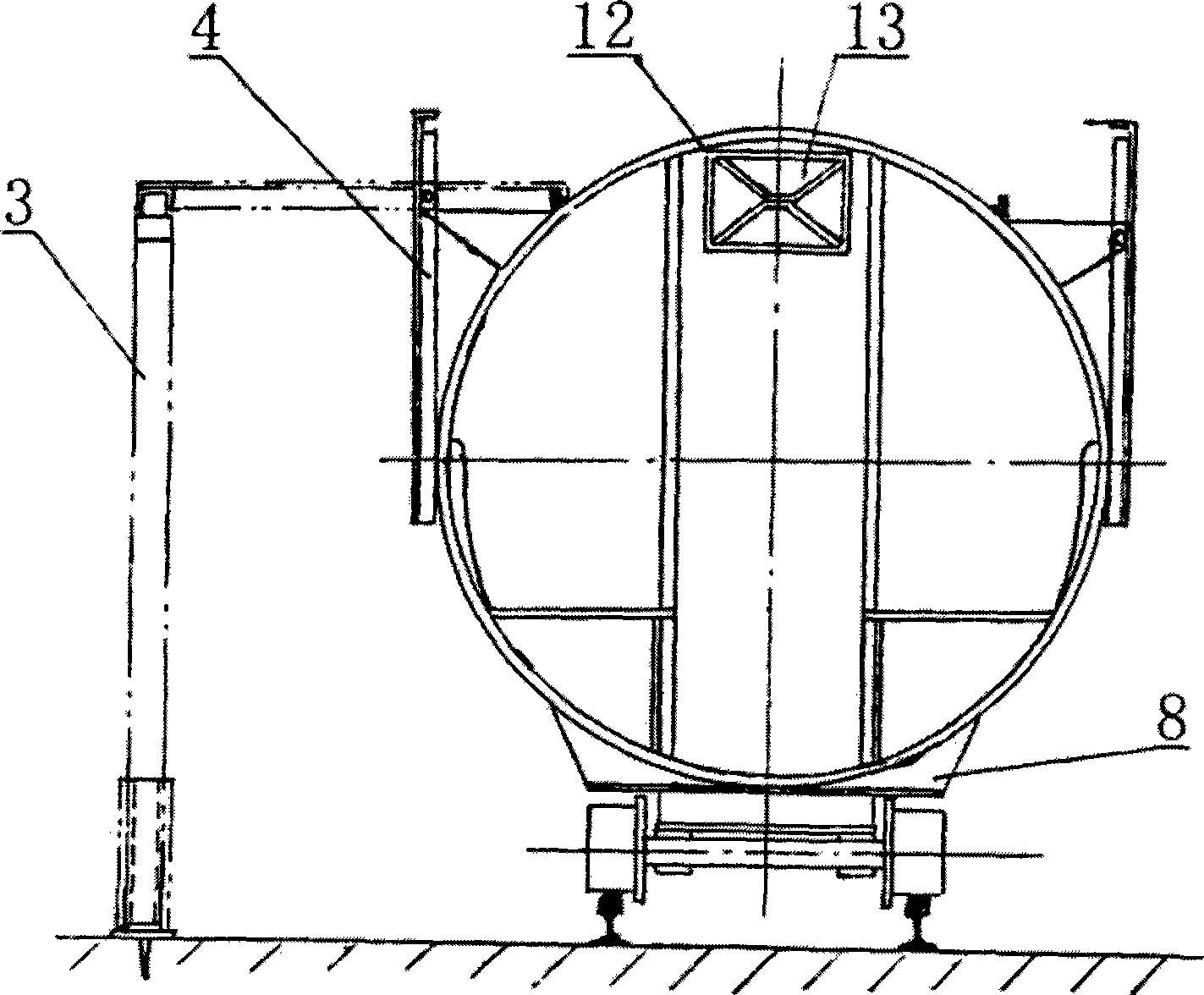
Helicopter trailer with lifting and safeguarding functions
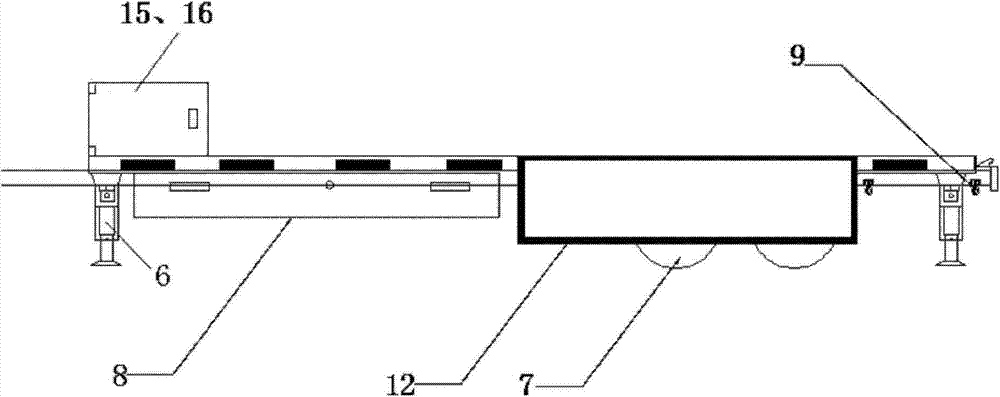
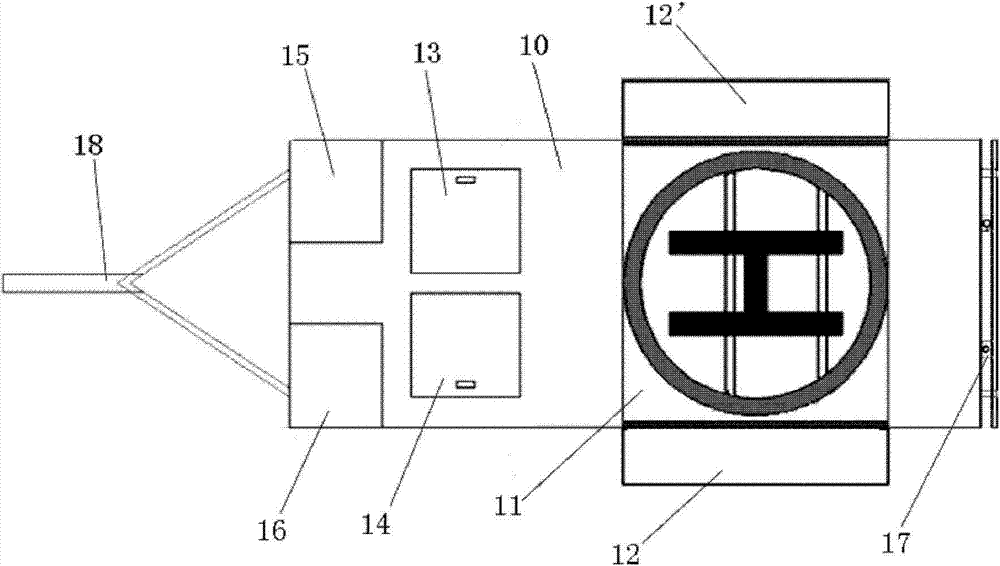
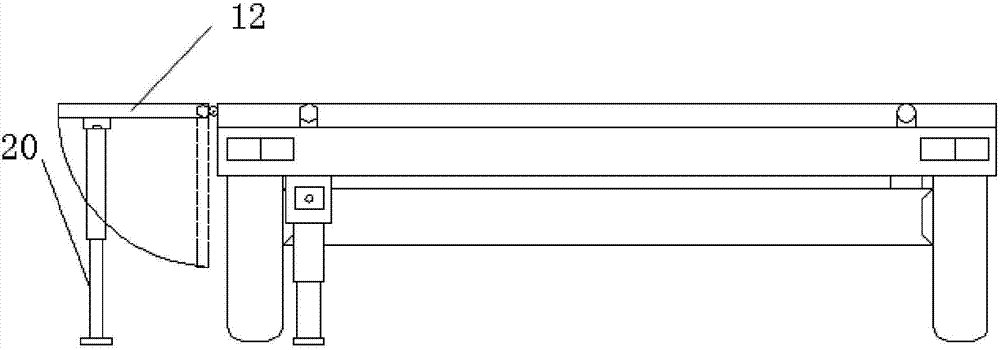
ActiveCN103832508AMeet the shock requirements for landingEasy to fixArresting gearVehiclesSafeguardingWheel and axle
The invention discloses a helicopter trailer with lifting and safeguarding functions. The helicopter trailer comprises a traction rod (18) and a trailer body connected with the traction rod (18), the trailer body comprises a trailer platform (10), two side-by-side wheel shafts (7) arranged below the trailer platform (10) and four supporting legs (6), each wheel shaft (7) comprises a bearing and wheels at the two ends of the bearing, and the bearings are triangle rubber damping bearings. The trailer platform (10) comprises a main landing platform (11) and foldable extending platforms (12 and 12') on the two sides of the main landing platform, and further comprises a plurality of helicopter safeguarding modules. The helicopter trailer has the complete safeguarding function and can conduct lifting, landing and conveying on a helicopter.
Owner:HAIFENG NAVIGATION TECH
Host safeguarding method and device
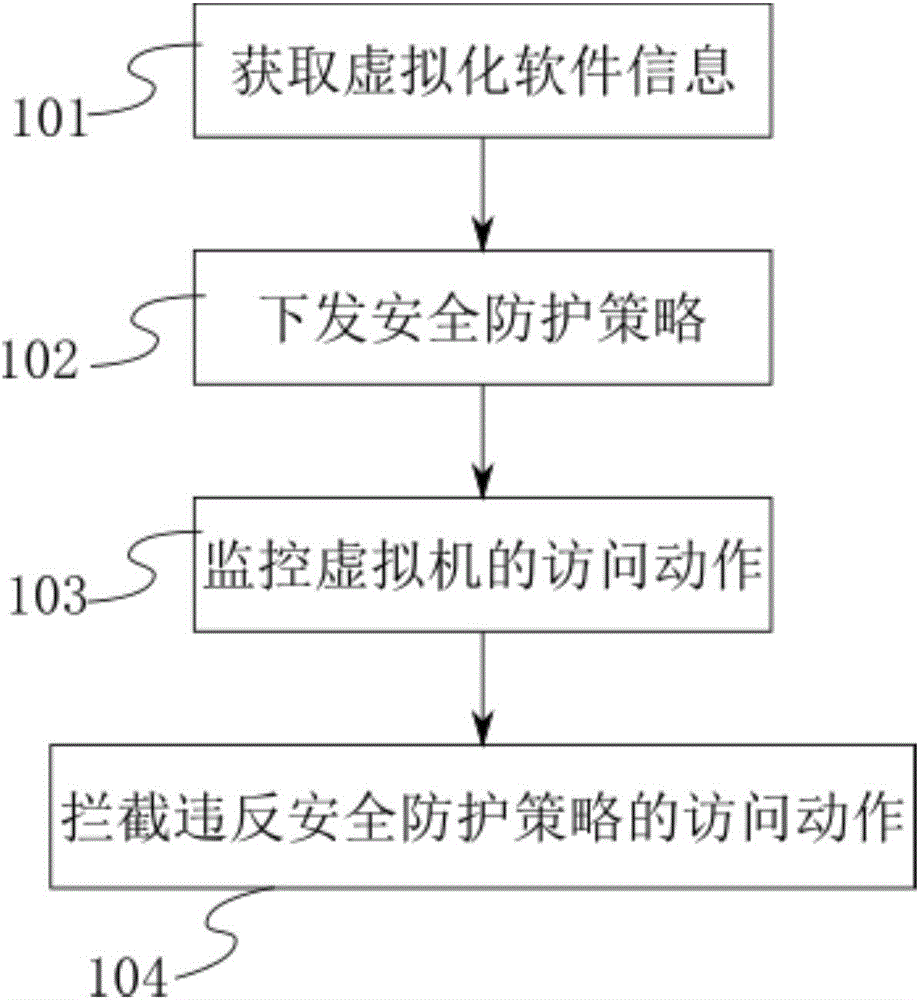
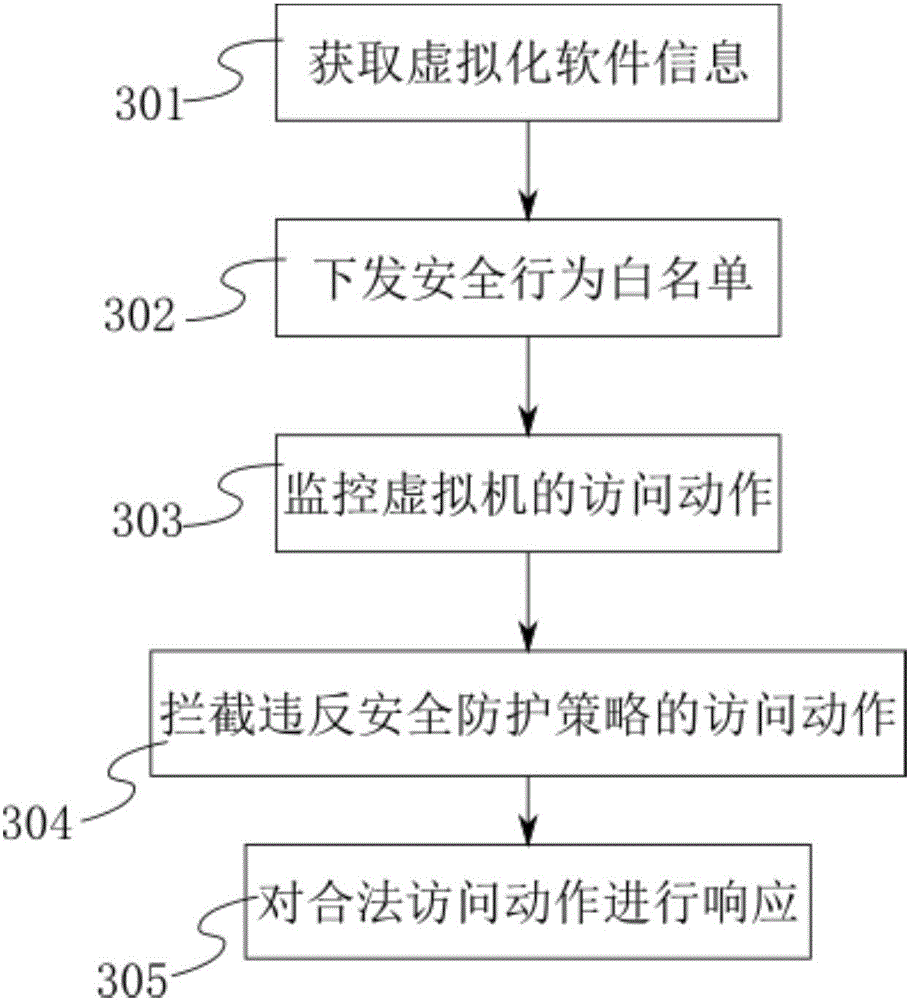
InactiveCN106778258AEnsure safetyEasy maintenancePlatform integrity maintainanceSoftware simulation/interpretation/emulationVirtual machineSoftware
The invention discloses a host safeguarding method and device and belongs to the technical field of virtualization; the host safeguard method comprises: acquiring information of virtualization software, issuing a safeguard strategy, monitoring access actions of a virtual machine, intercepting illegal actions, and other steps. The access actions of the virtual machine are correlated to the type and version of virtualization software, whether the actions are secure or not is judged by monitoring the actions of the virtual machine, and unsecure actions are intercepted in time; the host safeguarding method and device have the advantages of good logic simplicity, ease of implementation and good result reliability, comprehensive safeguarding can be provided for a host and virtualization software without changing existing Hypervisor code, and the host safeguarding method and device are a new path compared to the prior art and belong to a major modification to the prior art.
Owner:BEIJING CHINA POWER INFORMATION TECH +3
Comprehensive operation control system and method for battery energy storage system in high-permeability photovoltaic distribution network
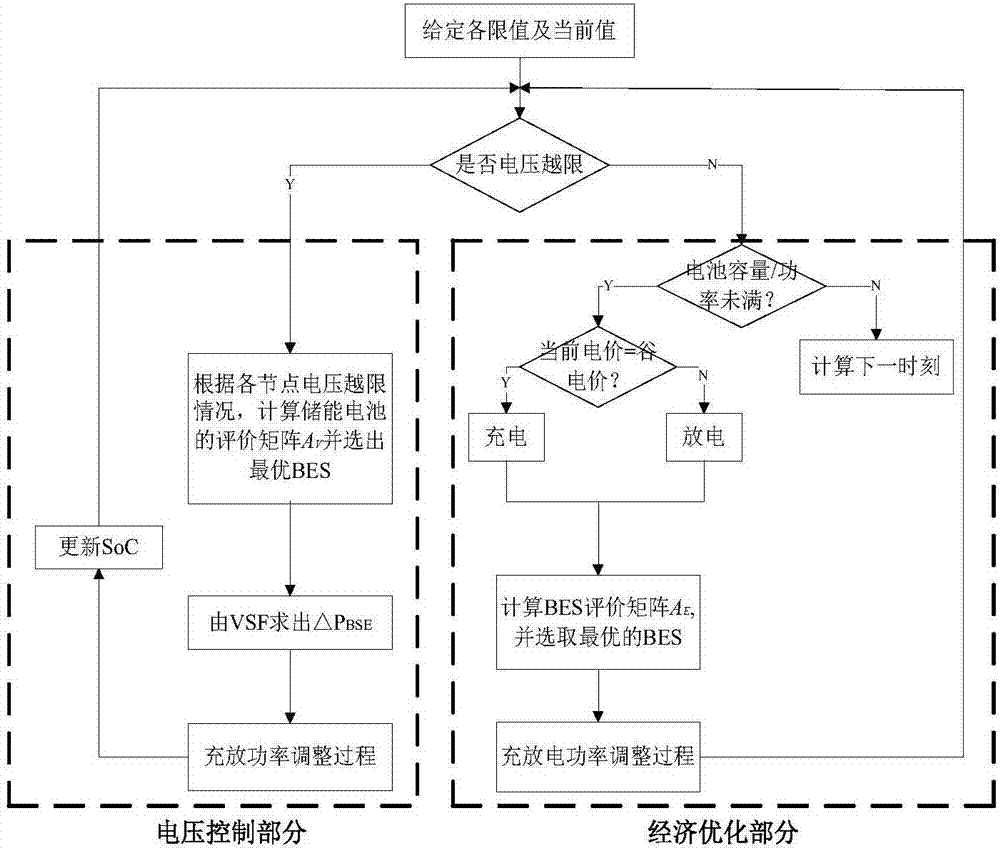
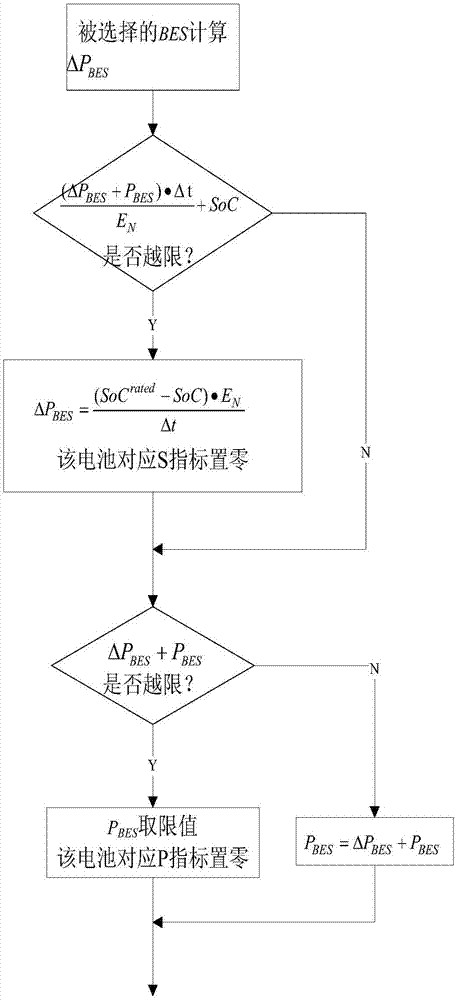
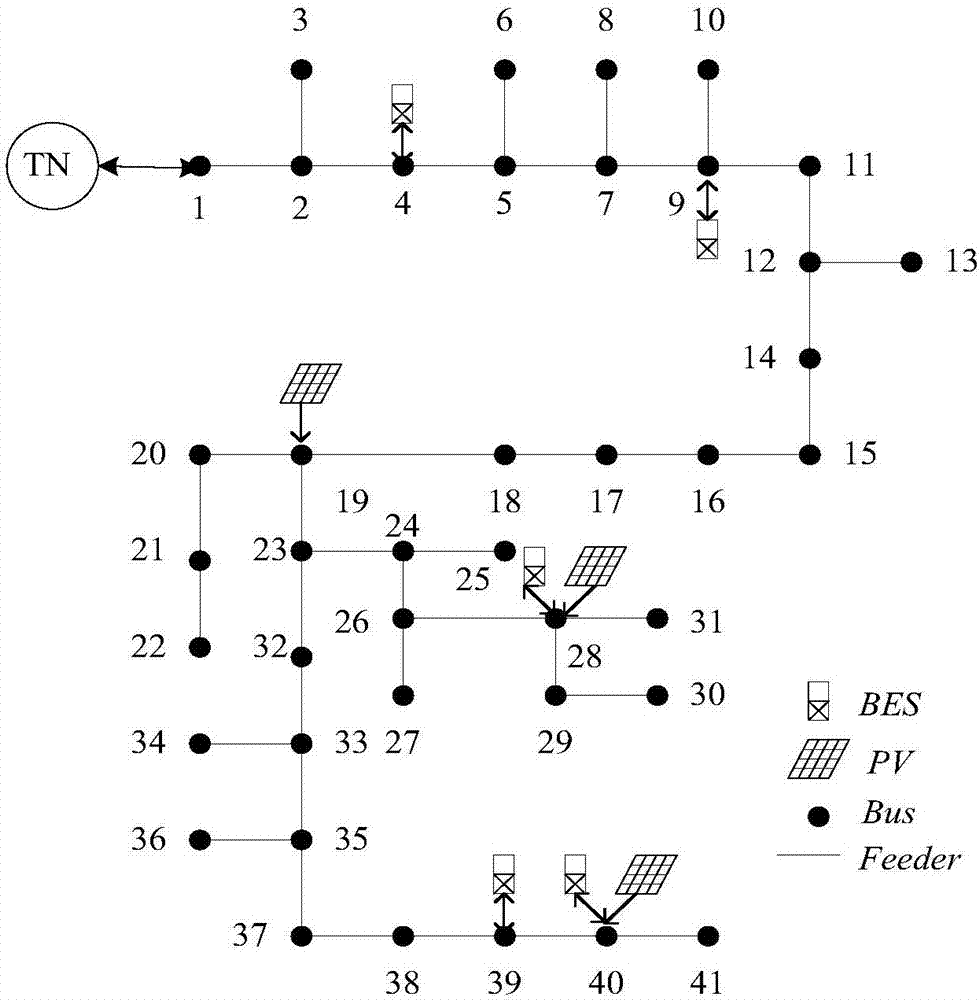
ActiveCN107370172ABalanced UtilizationExtended service lifeFlexible AC transmissionEnergy storageElectricity priceEngineering
The invention discloses a comprehensive operation control system and method for a battery energy storage system. The comprehensive operation control method comprises two sub strategies of voltage control and economic optimization, wherein voltage control, by taking voltage out-of-limit prevention as the target, comprises the steps of establishing an evaluation matrix comprising battery residual life, SoC state, voltage sensitivity characteristic, operational expenditure and the like, and selecting one with the maximum comprehensive index for controlling; economic optimization, by taking safeguarding of voltage safety as the premise, comprises the steps of reducing influence of battery action to a node voltage as far as possible by combination with power utilization peak and valley electric charges, and selecting one with the minimum of voltage sensitivity factor and operational expenditure and the best battery state for controlling. By adoption of the method, the problem of voltage out of limit caused by high-permeability photovoltaic and overhigh power utilization peak load can be solved; and in addition, peak clipping and valley filling is realized, the safety of the power distribution network is improved, profits is realized under the policy of time-of-use electricity price, and benefits of energy storage installation users are improved.
Owner:SHANDONG UNIV
Method and device for safeguarding of a document with inserted signature image and biometric data in a computer system
ActiveUS7971063B2Improper useConfidenceDigital data processing detailsUser identity/authority verificationBiometric dataHash function
A method for safeguarding an electronic document includes inserting at least one digital signature image into the electronic document and generating a first check sum for the electronic document, with or without optionally-inserted biometric signature data, using a first hash function. A second check sum is then generated using a second hash function. The first check sum and the biometric data, if provided, are then symmetrically encrypted using a key that is the sum of the second check sum and a generated random value. The symmetrically-encrypted first check sum is attached to the document. The random value is then asymmetrically encrypted using a first public key of a first key pair and the asymmetrically-encrypted random value is added to the document.
Owner:STEPOVER
Concealed target positioning method for single building wall corner
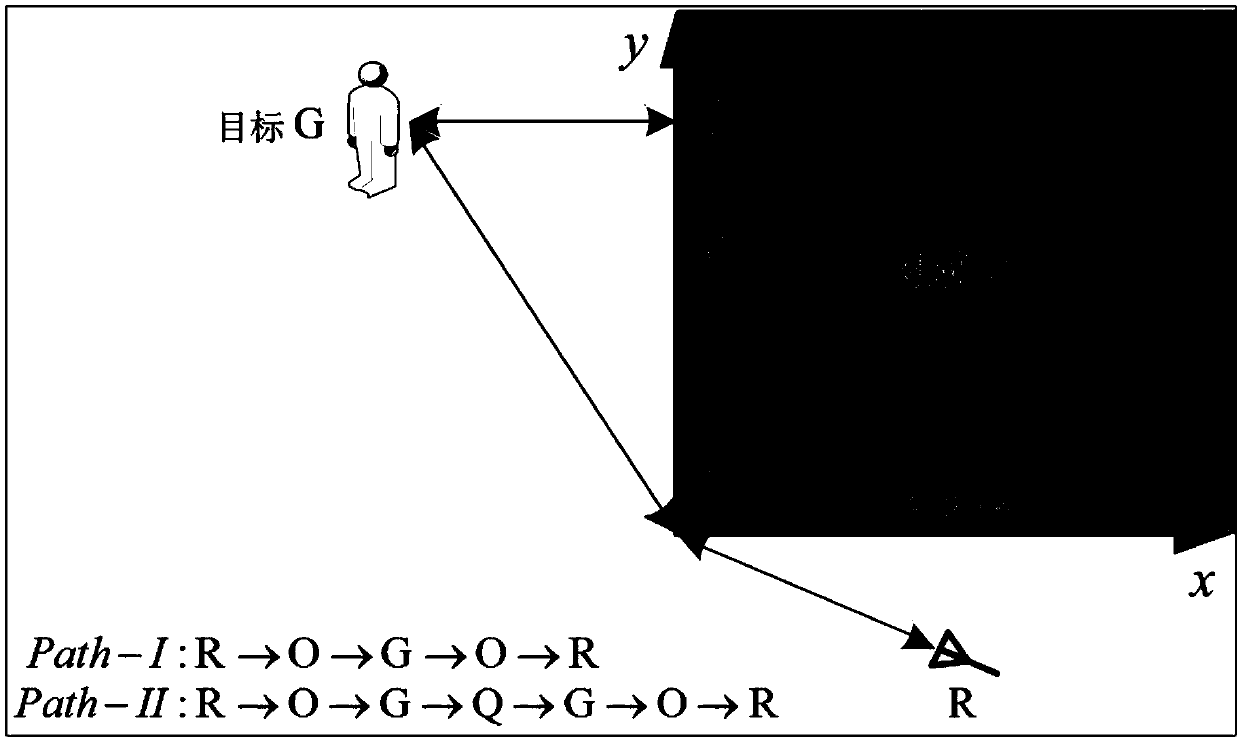
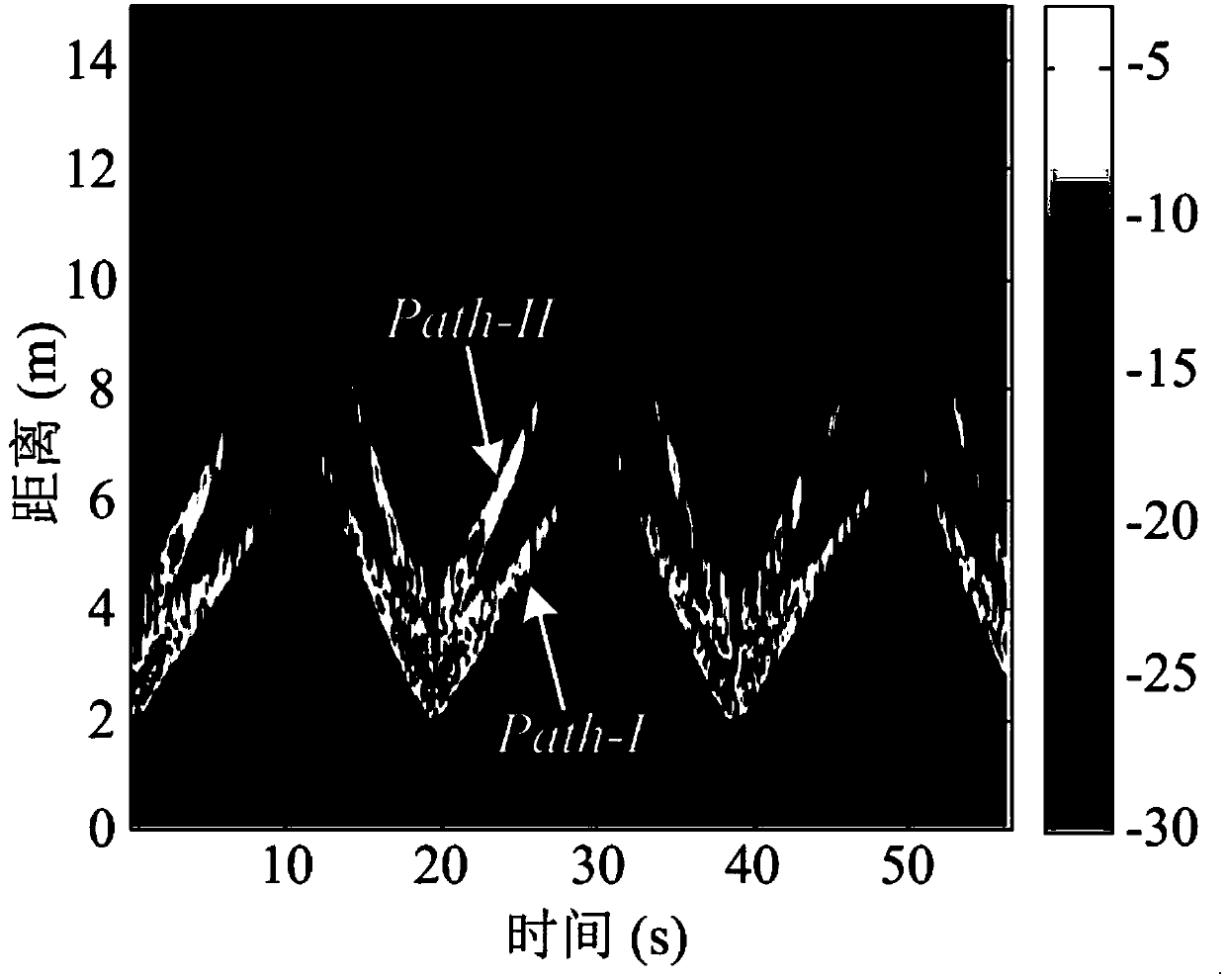
ActiveCN109655827ASimple calculationImprove practicalityRadio wave reradiation/reflectionRadarPeak value
The invention discloses a concealed target positioning method for a single building wall corner based on an ultra-wide band multi-path utilization radar. The main aim is to realize positioning for a non-direct-viewing target in a city environment. The multi-path diffraction feature of electromagnetic waves is used for positioning a concealed target behind the corner, firstly, a moving target display technology is adopted for background compensation to restrain strong background clutters, a median filtering algorithm is used for conducting smooth denoising processing on compensated echo signals, then by the utilization of unit average constant false alarm detection, peak values corresponding to a direct diffraction path and a side wall reflection path are extracted from the echo signals, according to the geometrical relation of the two paths, in combination with the clear position of the radar and building layout information, the position of the target is worked out, and finally alpha-beta filtering method is introduced to improve the positioning precision of the moving target. The concealed target positioning method has the advantages that the realizing process is simple, the wholeprocess of obtaining the position of the target is small in calculation amount, and the high positioning precision for the target is realized. The concealed target positioning method can be applied to the fields of city street fighting, terrorism combating, stability safeguarding, disaster rescue and others.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
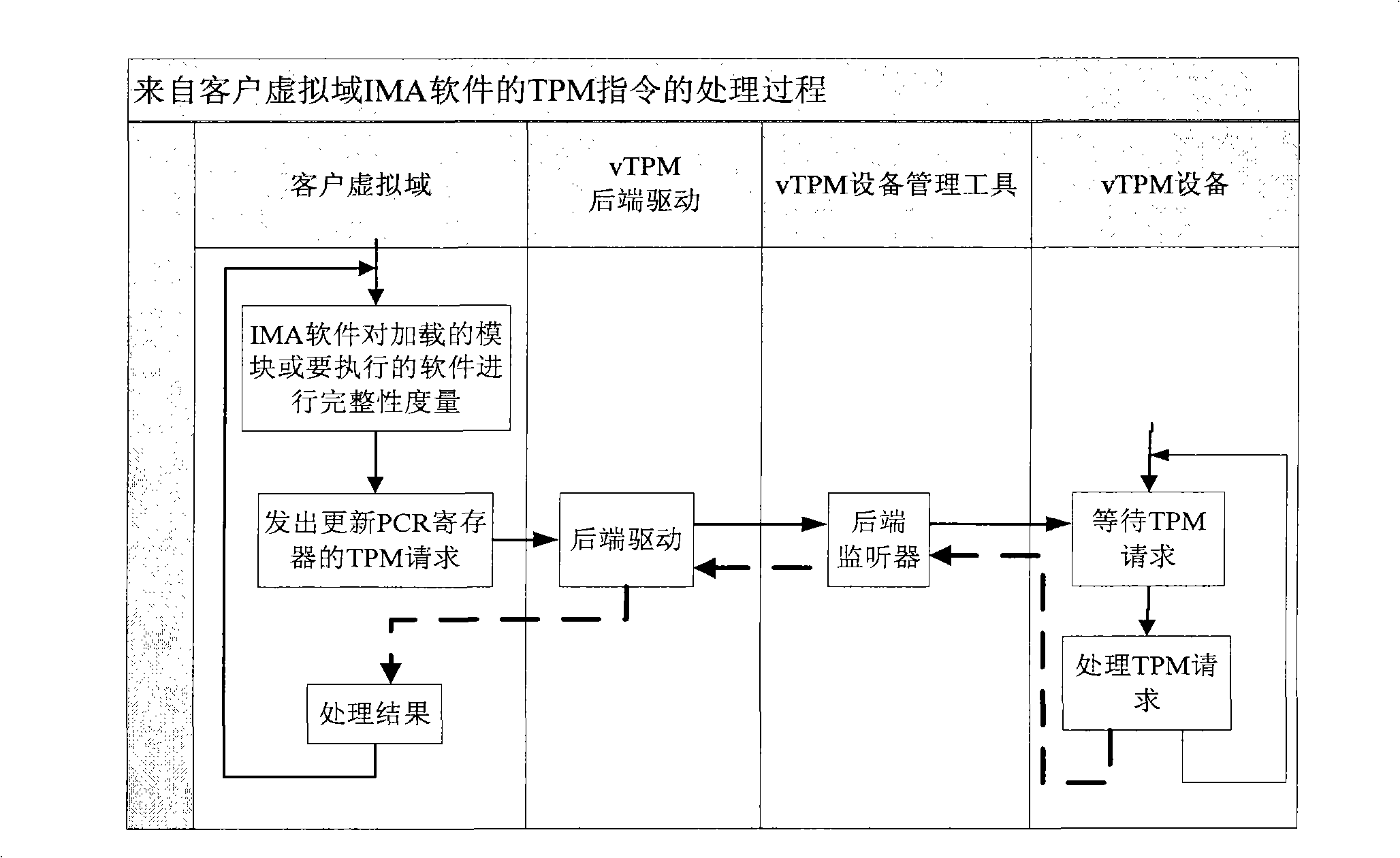
Method for self adaptedly safeguarding the normal starting of credible client virtual domain
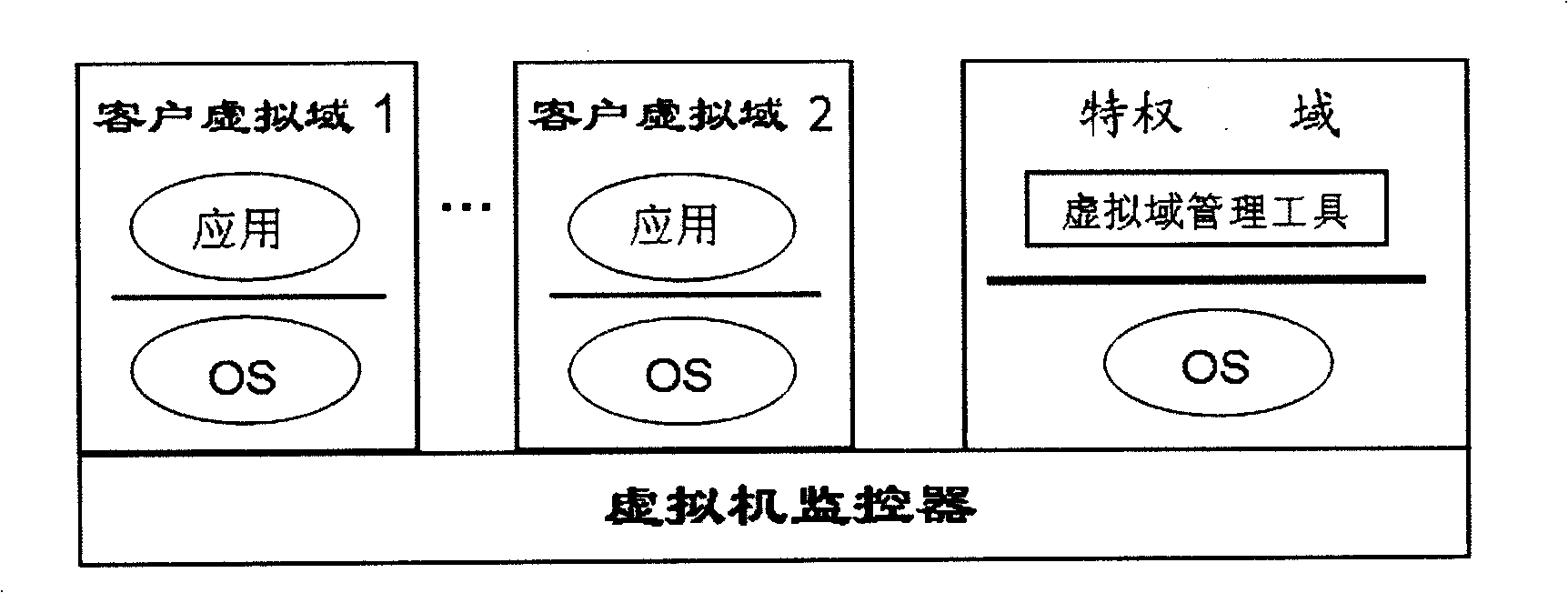
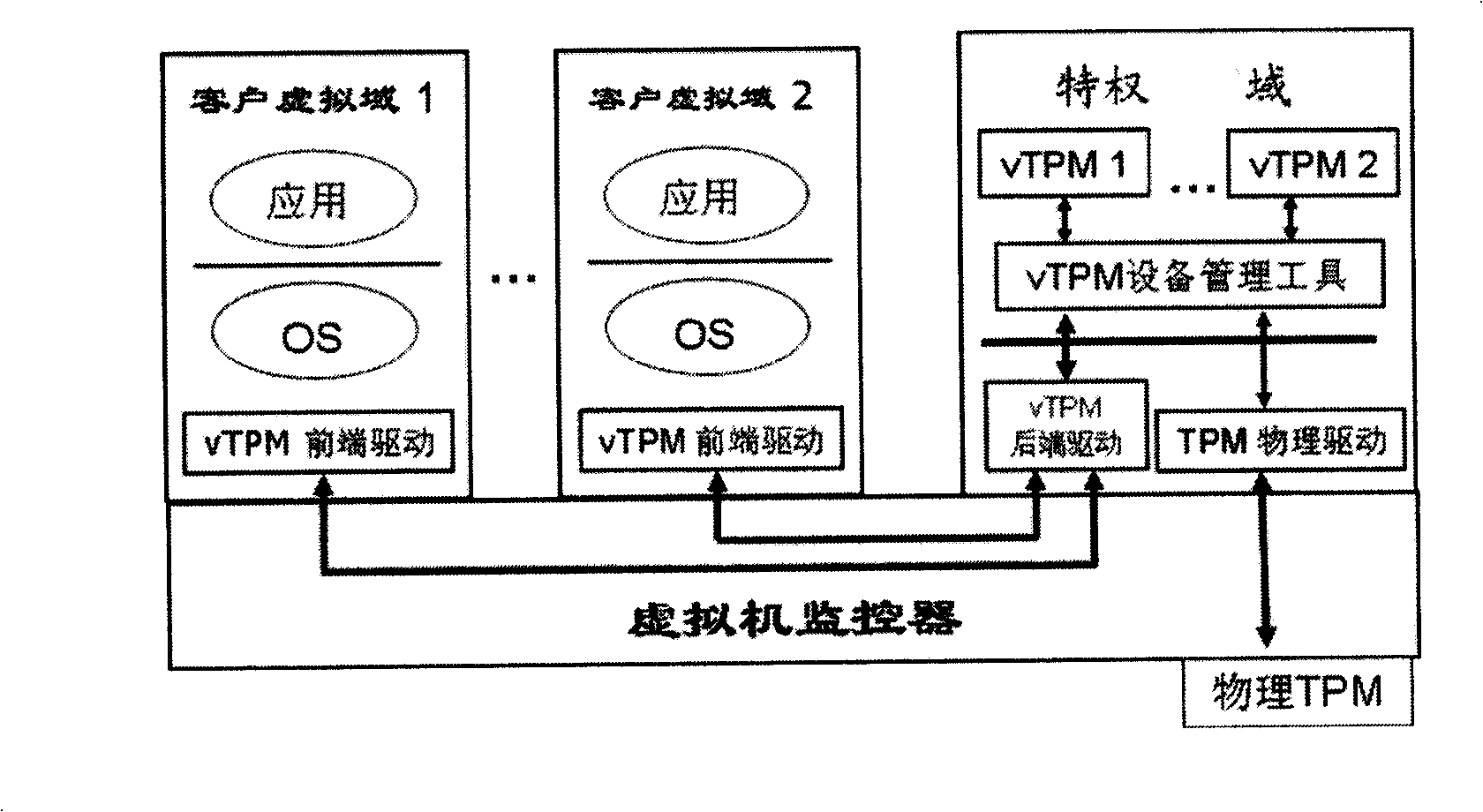
InactiveCN101539864ASolve the speed problemSolve resource problemsProgram initiation/switchingProgram loading/initiatingTrusted Platform ModuleSoftware engineering
The invention relates to a method for self adaptedly safeguarding the normal starting of a credible client virtual domain. The method realizes the safeguarding by increasing the functions of the existing virtual trusted platform module and the integrity measurement software. In the method, the integrity measurement software is loaded by the client virtual domain and then enters into the sleep mode so as to suspend the system starting; until the virtual trusted platform module of a privilege domain comes into operation, the integrity measurement software is aroused and the virtual domain system continously starts. The method not only can safeguard that the credible client virtual domain does not collapse owing to the slow establishment process of the virtual trusted platform module, but only maintains that the original system makes the best of system resources on one hand and maintains the response speed of the original system on the other hand by adopting an event driving operating mode and postponing the suspending of the starting process of the virtual domain before the initializing part of the virtual domain software of a first access virtual trusted platform module.
Owner:BEIJING JIAOTONG UNIV
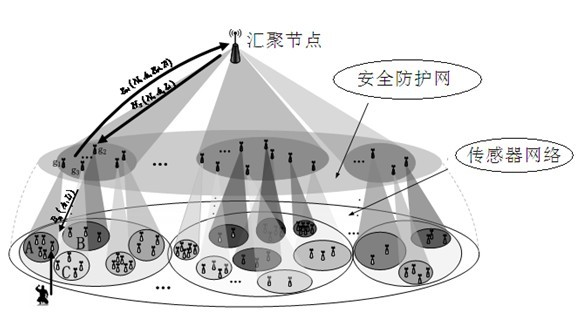
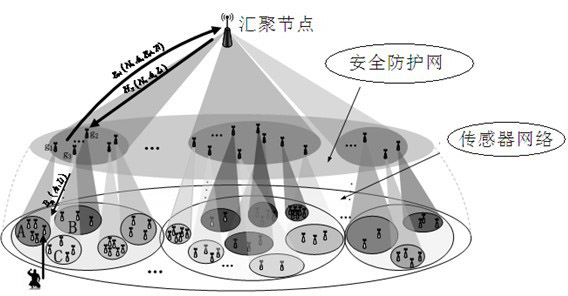
Safeguarding method for wireless sensor network
ActiveCN102665199AImprove securityImprove security detection capabilitiesNetwork topologiesTransmissionMobile wireless sensor networkWireless mesh network
The invention provides a safeguarding method for a wireless sensor network. Security functions designed in the wireless sensor network strengthen special guard nodes, a safeguarding network logically independent from the sensor network is constructed on the basis, network security includes a plurality of levels, the security levels of sensor regions in the sensor network can be provided by the safeguarding network, cryptographic algorithms are evolved by regions according to the security levels, and data guard measures of the corresponding strength are taken so that a network security mechanism capable of safely and effectively saving resources is formed. By the aid of the method, safeguarding capability of the wireless sensor network is improved, network security response time is shortened, flexibility of the network coping with security threats is improved, network security resources are saved, and cryptographic algorithm modification cost is reduced.
Owner:鸣飞伟业技术有限公司
Methods, systems, and computer readable media for securely collecting, safeguarding, and disseminating electronically stored information
InactiveUS20140096262A1Good choiceEfficient managementDigital data processing detailsAnalogue secracy/subscription systemsInternet privacyEncryption
Applicant has created methods, systems, and computer readable media for securely collecting, safeguarding, and disseminating electronically stored information to facilitate an account owner's management of her personal, private, business, and legal documents. The method for safeguarding can include a double authentication process that only grants exclusive access to an account owner's encrypted information through the use of a uniquely generated security key. The method for collecting information can include a real-time encryption process to permit an account holder to securely upload and store electronic media in category-based compartmentalized locations. Further, the method can include a process for generating category-based advertisements through an integrated marketing platform with geo-fencing capabilities to facilitate the account owner's selection of a variety of services related to the stored information. Finally, the method for disseminating information can include authenticating a request to disseminate the stored information to one or more trustees.
Owner:CASSO ROBERTO M
Multi-target correlation degree division processing method for buoy data
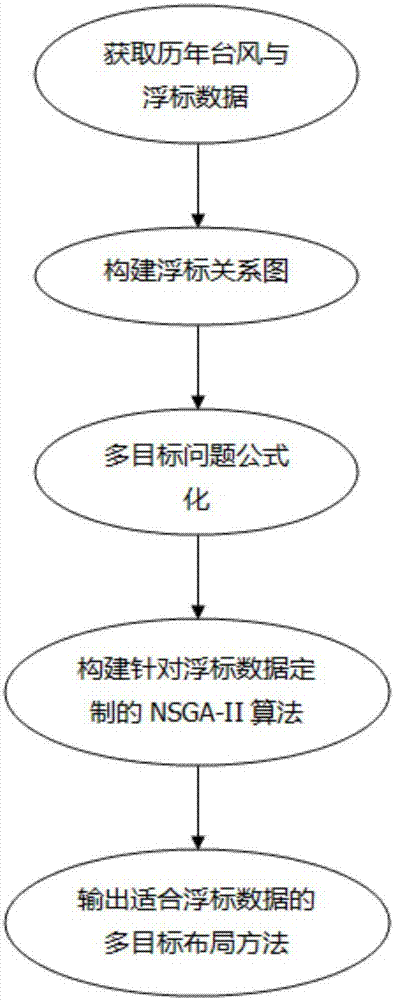
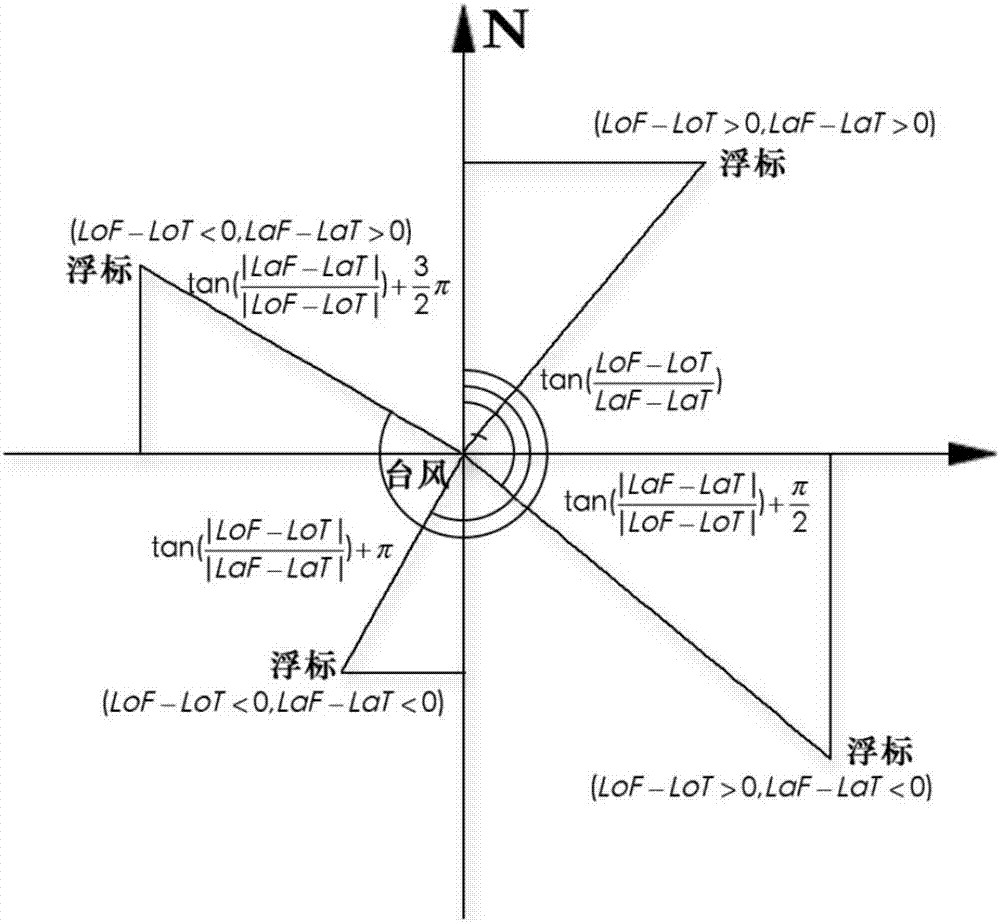
ActiveCN106919783AImprove forecast accuracyQuality improvementSpecial data processing applicationsInformaticsRelation graphGenetic algorithm
The invention relates to a multi-target correlation degree division processing method for buoy data. The multi-target correlation degree division processing method for the buoy data comprises the following steps of obtaining typhoon and buoy data over the years; constructing a buoy relation graph; performing multi-target problem formulation; constructing an NSGA-II algorithm (a non-dominated sorting genetic algorithm with an elite-preservation strategy) customized for the buoy data; and outputting a multi-target layout method suitable for the buoy data. The method has the advantages that all buoys in a sea area form the graph, and buoy distribution is partitioned into regions for storage; the buoy data correlation in micro-areas is maximized, the correlation between the micro-areas is minimized, the cross-micro-area communication time is minimized, and micro-area loads are balanced; an efficient retrieval mode is provided for ocean emergency early warning, forecast and typhoon data analysis, and the forecast precision is improved; and the quality of operational conventional forecast, the numerical model assimilation effect, correct making of disaster prevention and reduction and emergency forecast decisions, and guarantee capabilities of maritime activities such as rights safeguarding, law enforcement and the like are facilitated.
Owner:SHANGHAI OCEAN UNIV
Transparent Silicone Cover for the Safeguarding of Glass Pharmaceutical Vials
InactiveUS20160194114A1Improve securityAvoid partial crackingPackage recyclingBottlesClinical settingsBarcode
A transparent silicone cover and accompanying transparent silicone securing bands that safeguard a glass pharmaceutical vial from shattering or cracking as a result of handling by automated dispensing units, patients, or medical or veterinary staff while simultaneously allowing inspection and reading of an enclosed vial, its contents and all labels in their entirety, as well as scanning of barcodes in the clinical setting. The main body provides a cylindrical lumen for the vial to rest in securely while effectively protecting the vial's sidewalls and base. One side of the main body has a narrow slit from top to base which also extends inwardly partially across the base, allowing the main body to flex open, offering easy insertion and removal of a vial. The transparent silicone securing bands fit tightly over the main body to further safeguard the enclosed vial. The entire assemblage is autoclavable, hypoallergenic, microbe resistant, removable and reusable.
Owner:LUNA ANDREW ISAAC
Organizing-defense monitoring method capable of expanding safety prevention arrangement
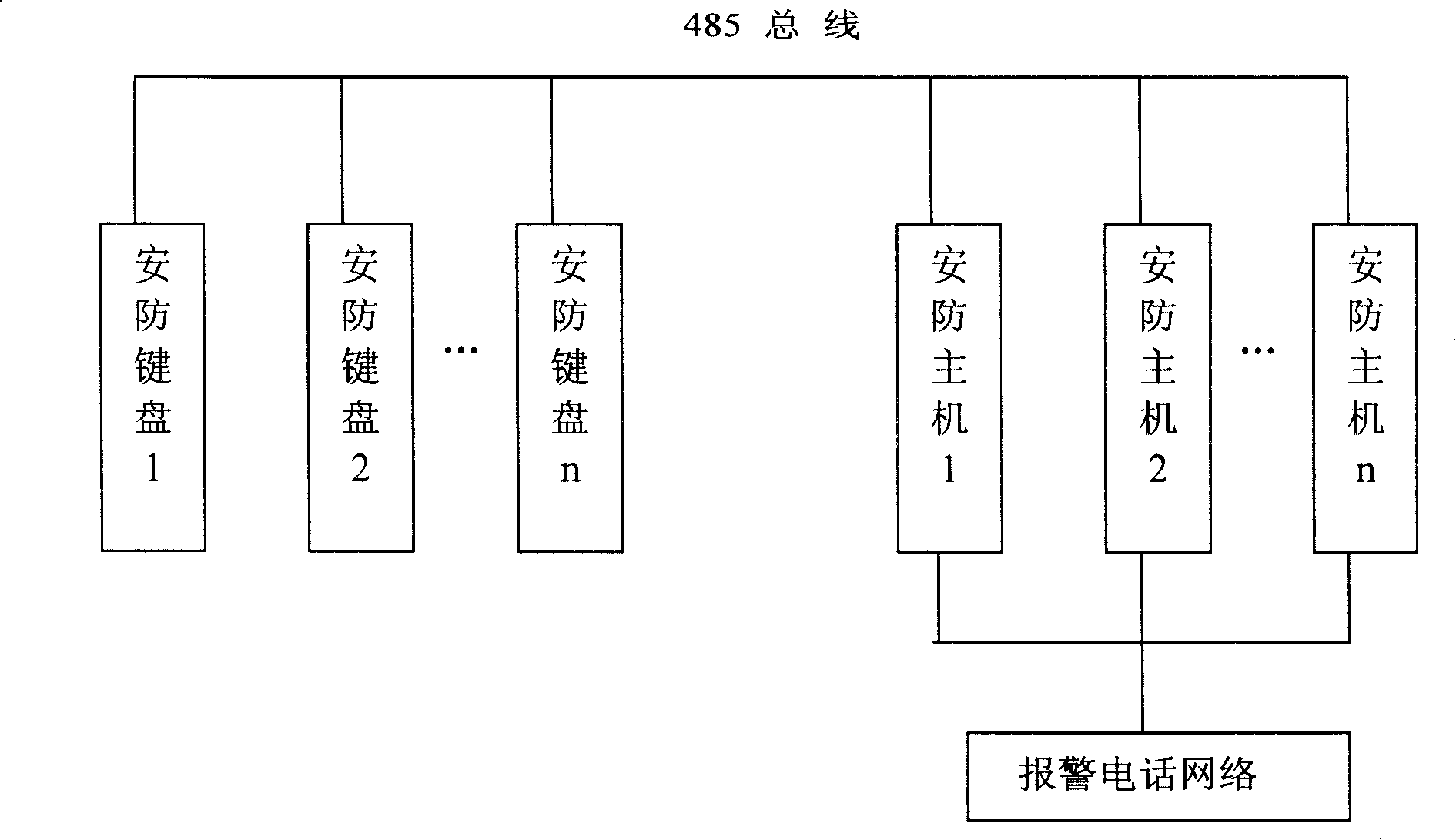
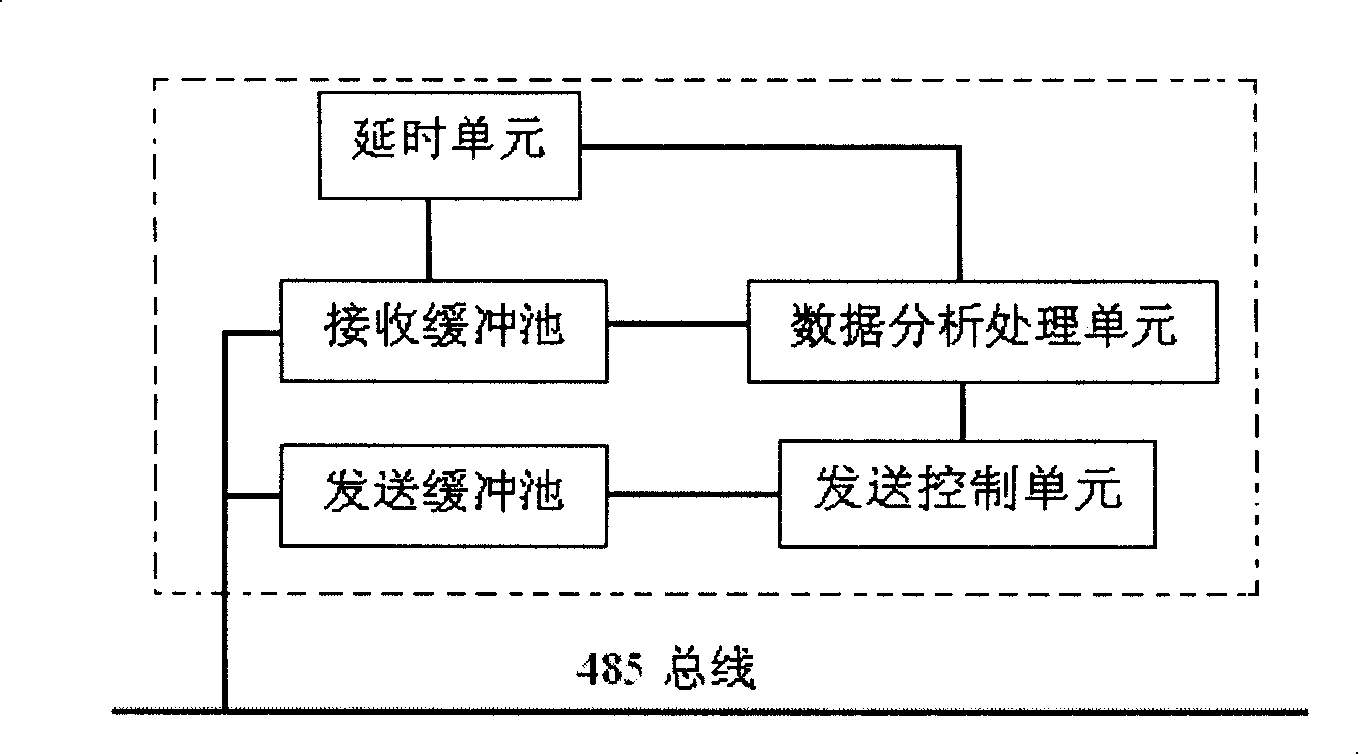
The invention discloses a defense-setting and monitoring method which can expand safeguarding arrangement, which employs two or more safeguarding main machines and two or more safeguarding keyboards. Detecting heads are connected with the corresponding safeguarding main machines, logical control units used for monitoring circuit state, slowly storing data, controlling the process of receiving and sending are arranged on each safeguarding main machine and each safeguarding keyboard, a safeguarding control group is formed by using bus structure to connect, time-delay is set by monitoring whether the free state of the bus is conflictive with the data to finish the sending of data and control order. The invention can effectively realize the expansion of the connecting number of the safeguarding detecting heads, reduce the wiring pressure of the safeguarding system, simultaneously facilitate the user to set and operate the safeguarding system.
Owner:GUANGDONG TRI SUN ELECTRONICS TECH +1
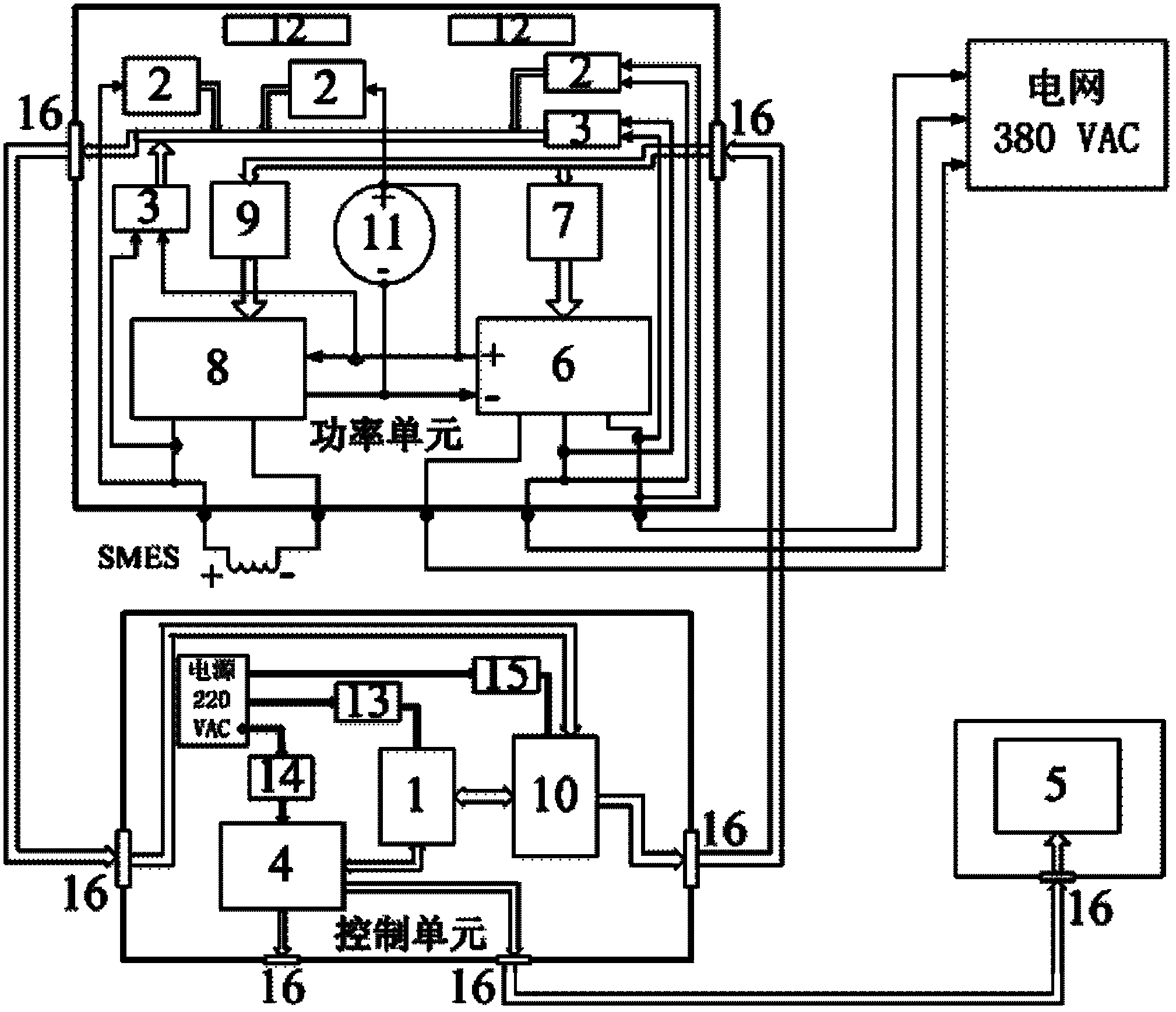
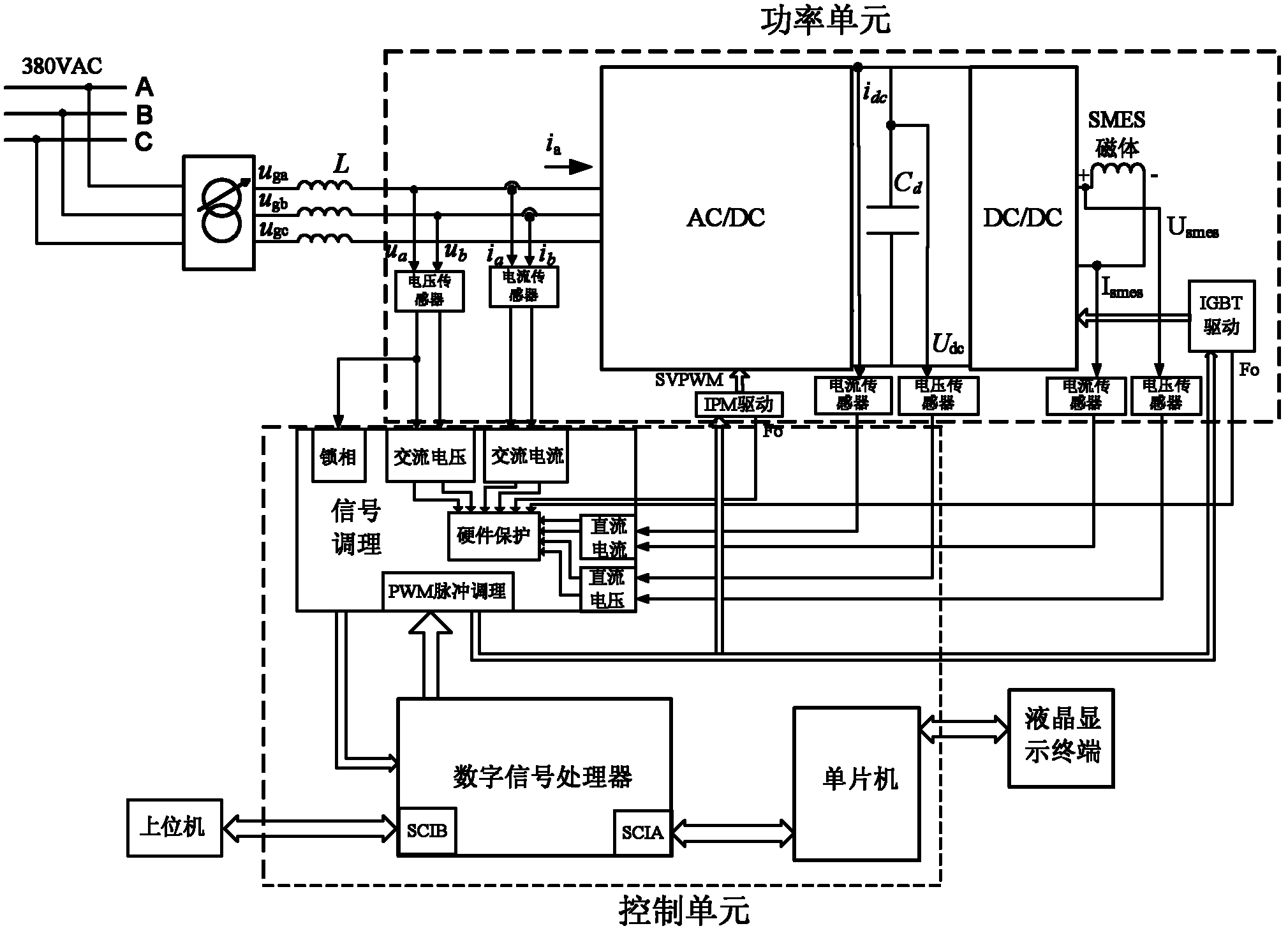
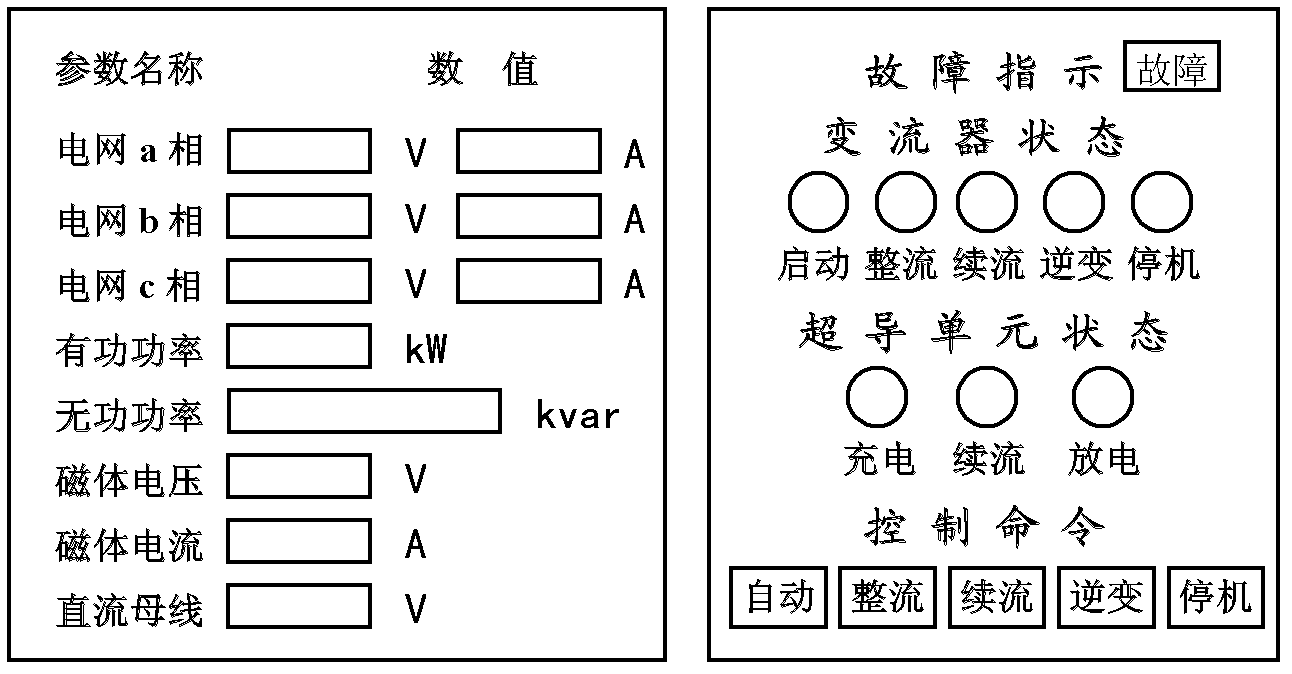
Grid-connected full digital monitoring system for controllable high-temperature superconducting magnetic energy storage (SMES) system
ActiveCN102222935ASimple and user-friendly operationLow costFlexible AC transmissionSingle network parallel feeding arrangementsMicrocontrollerOperation mode
The invention relates to a grid-connected full digital monitoring system for a controllable high-temperature superconducting magnetic energy storage (SMES) system. The grid-connected full digital monitoring system adopts a dual-processor form based on a microcontroller and a digital signal processor (DSP) to realize the monitoring on the high-temperature SMES system in a grid-connected operation mode. A full digital man-machine interaction interface can display an instantaneous operating parameter and operating conditions of a power grid, an SMES magnet and a power regulator, and can display various fault information on a liquid crystal terminal interface for fault location and removal when the SMES system is failed in the grid-connected process. The digital man-machine interaction interface has a control command touch key for field personnel to control, namely, the touch key can be touched to control the operating condition of the power regulator; and meanwhile, remote control of an upper computer is supported. The invention comprehensively takes the conditions of the SMES system, the power grid and the power regulator and a necessary safeguarding technology into consideration. The grid-connected visual monitoring system with a man-machine interaction function for the SMES system can effectively ensure safe operation for the SMES units.
Owner:CHINA ELECTRIC POWER RES INST +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com