Database safeguarding method based on data stream restoration technology
A technology of security protection and data flow, applied in electronic digital data processing, special data processing applications, instruments, etc., can solve the problems of lack of database security enhancement products, inability to effectively defend against malicious attacks on database servers, and database security without protection methods, etc. To achieve the effect of preventing security vulnerabilities and preventing SQL injection attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be further described below in conjunction with accompanying drawing.
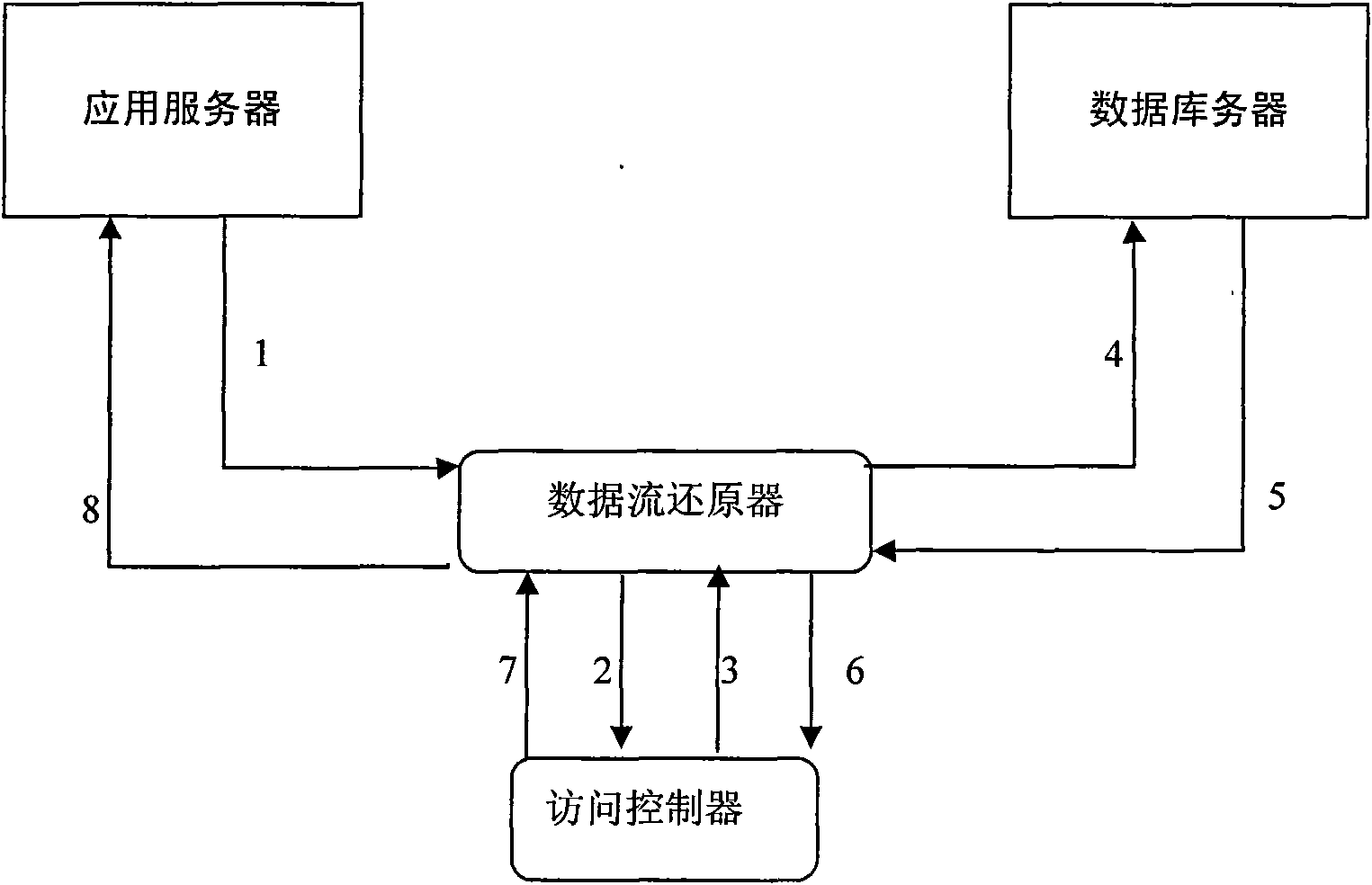
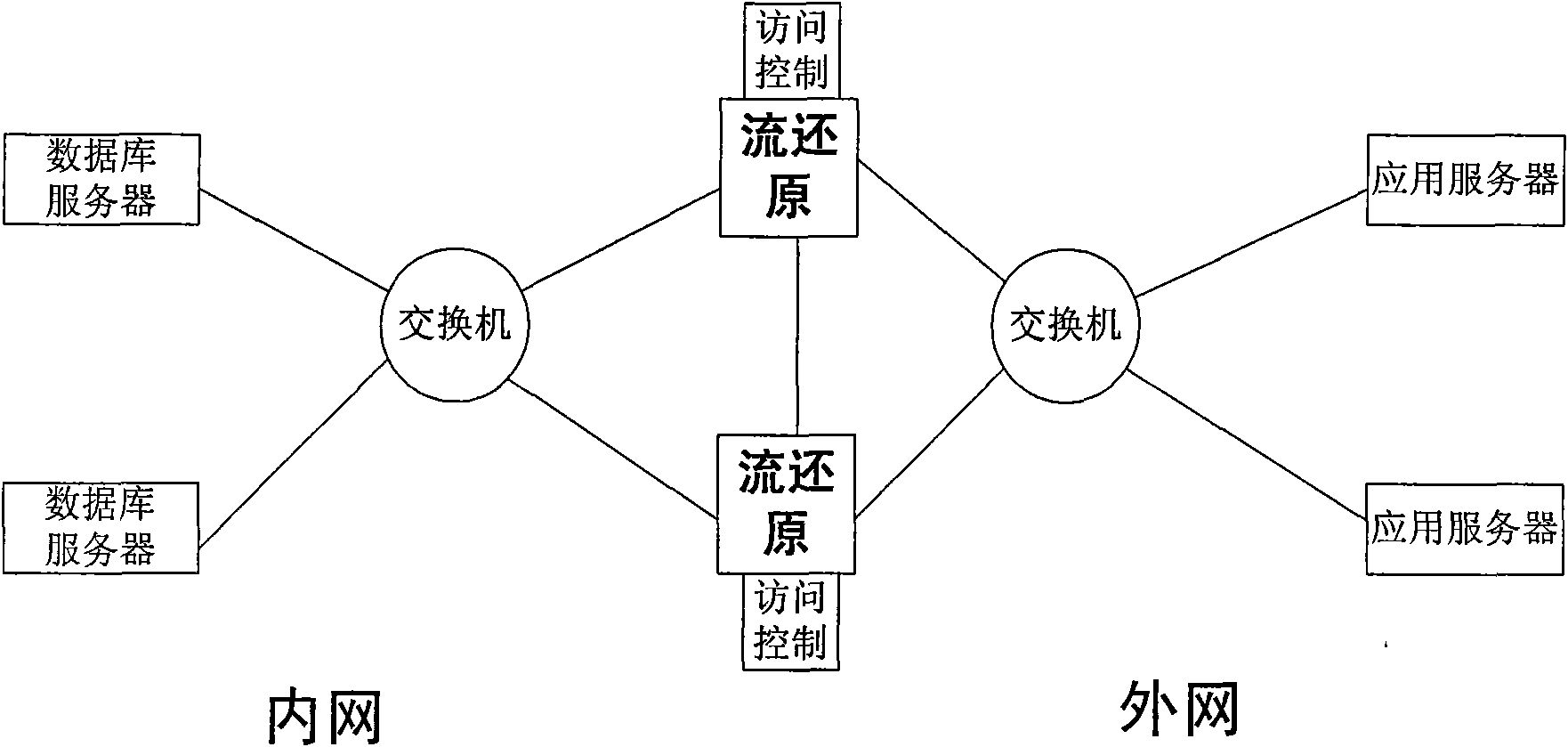
[0043] The data flow restorer of the method is serially connected between the application server and the database server, and can restore all operations of the application server to the database server. The access controller checks the restored operations, rejects the operations that do not conform to the defined rules, and cuts off the corresponding TCP link.
[0044] Configure basic IP, MAC and other access information in the data flow restorer to avoid IP address forgery and unauthorized application server access to the database.
[0045] For the corresponding operation of the corresponding database, the authority controller will perform the following operations:
[0046] 1) Check the legality of operations such as the corresponding network address, network card hardware address, and application port.
[0047] 2) Check the legitimacy of the login authentication informa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com