Patents
Literature
42results about How to "Improper use" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
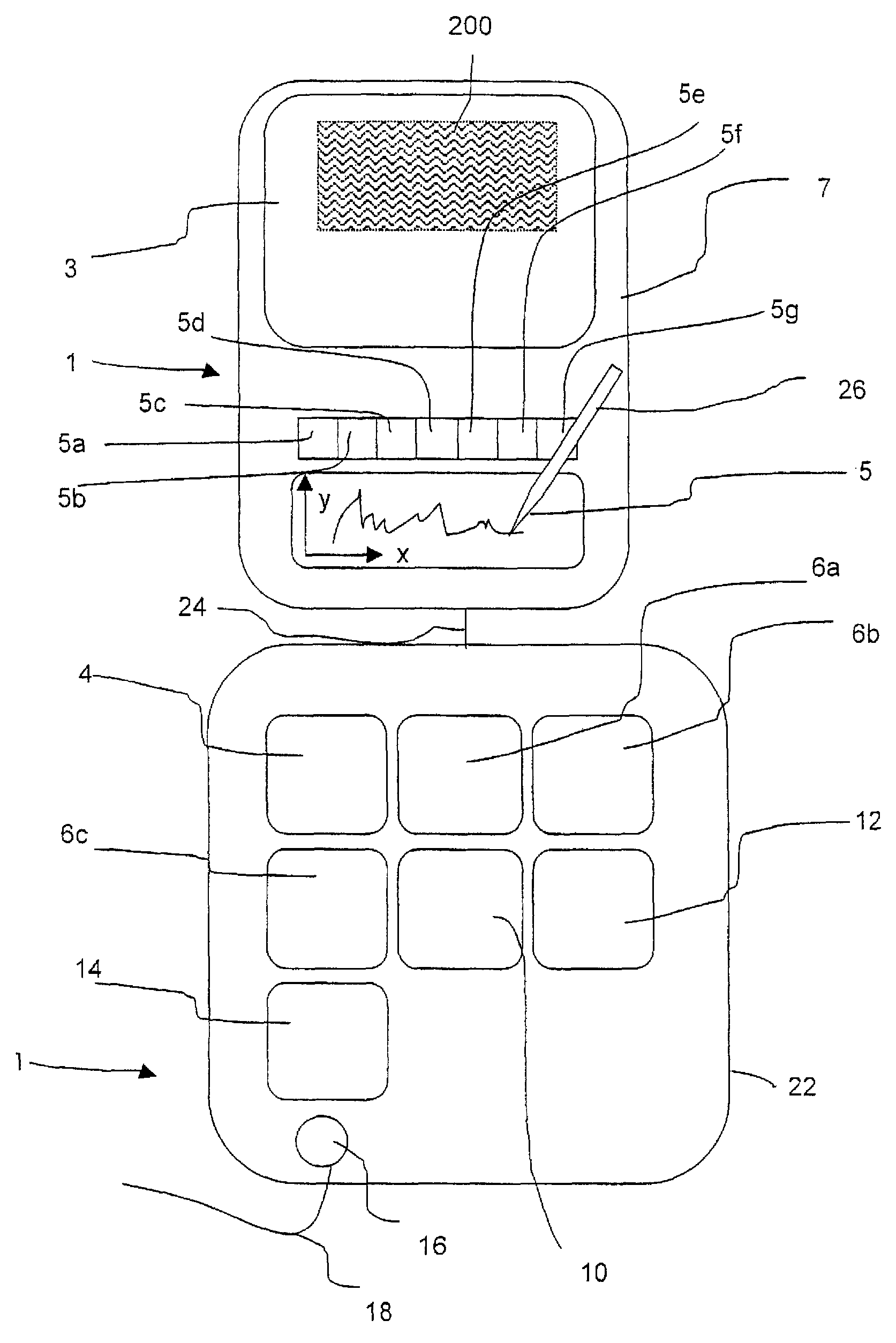
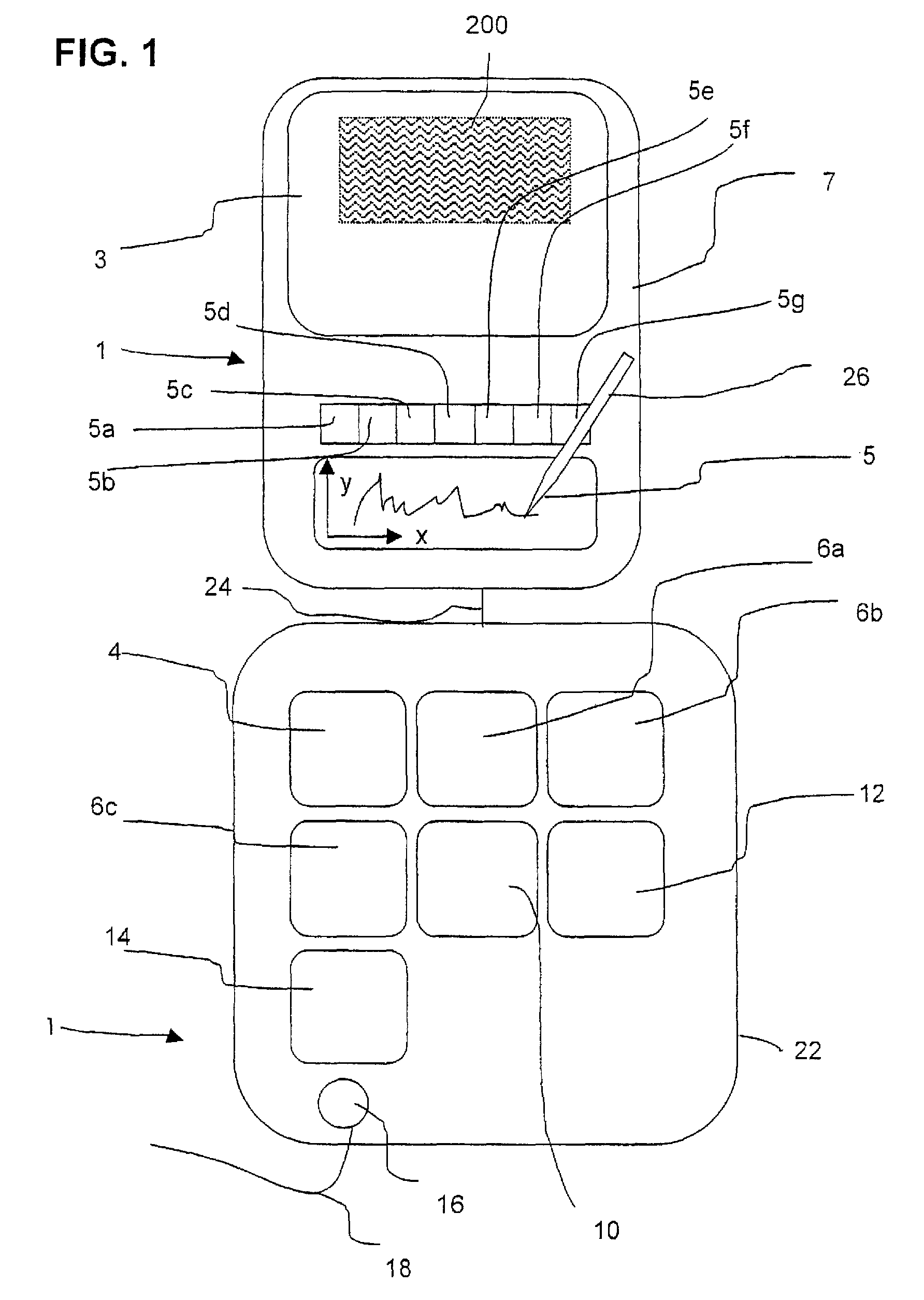
System to control content and prohibit certain interactive attempts by a person using a personal computer
InactiveUS6065056AReduce usageAvoid spreadingDigital data information retrievalMultiple digital computer combinationsPasswordWord search
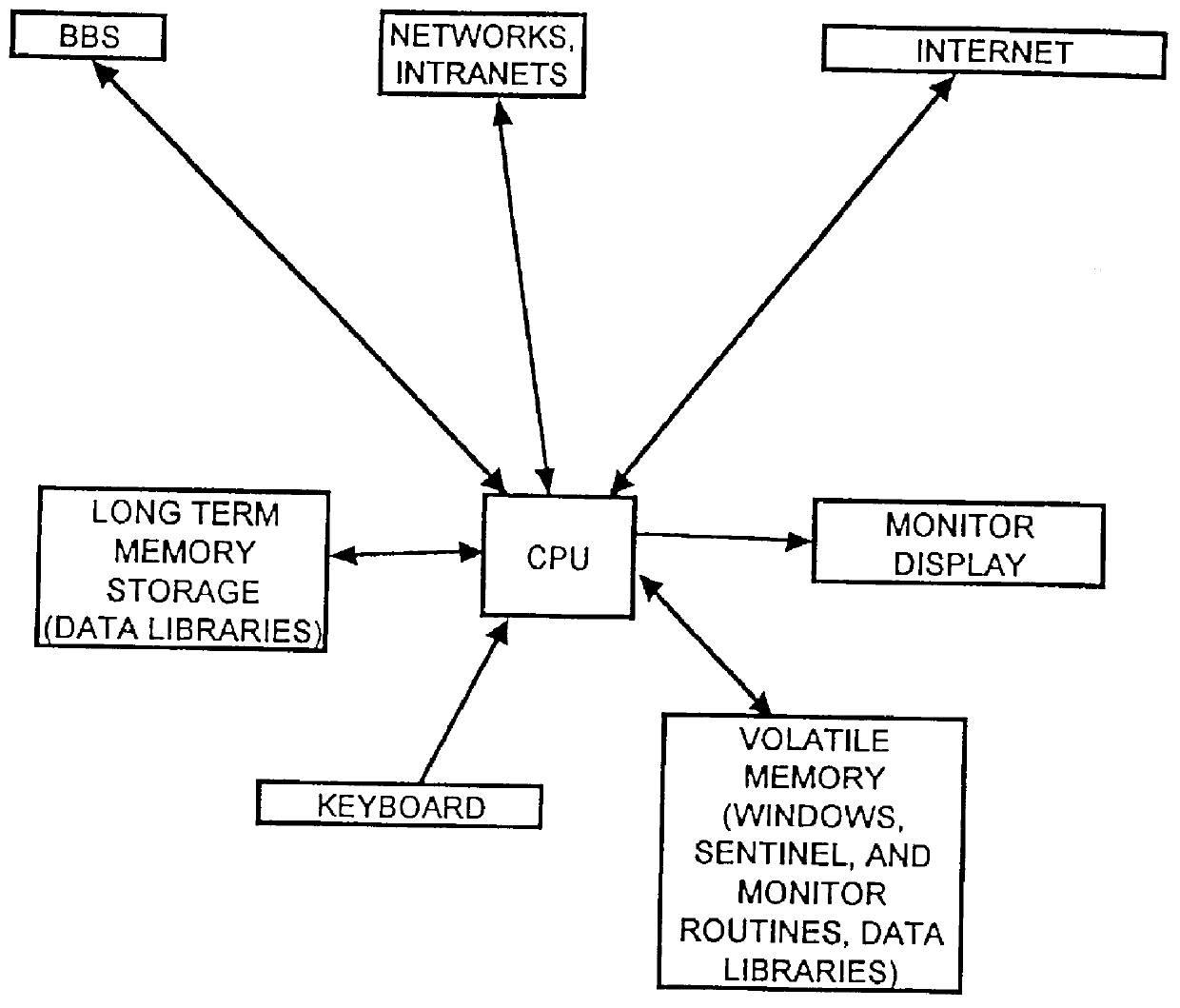
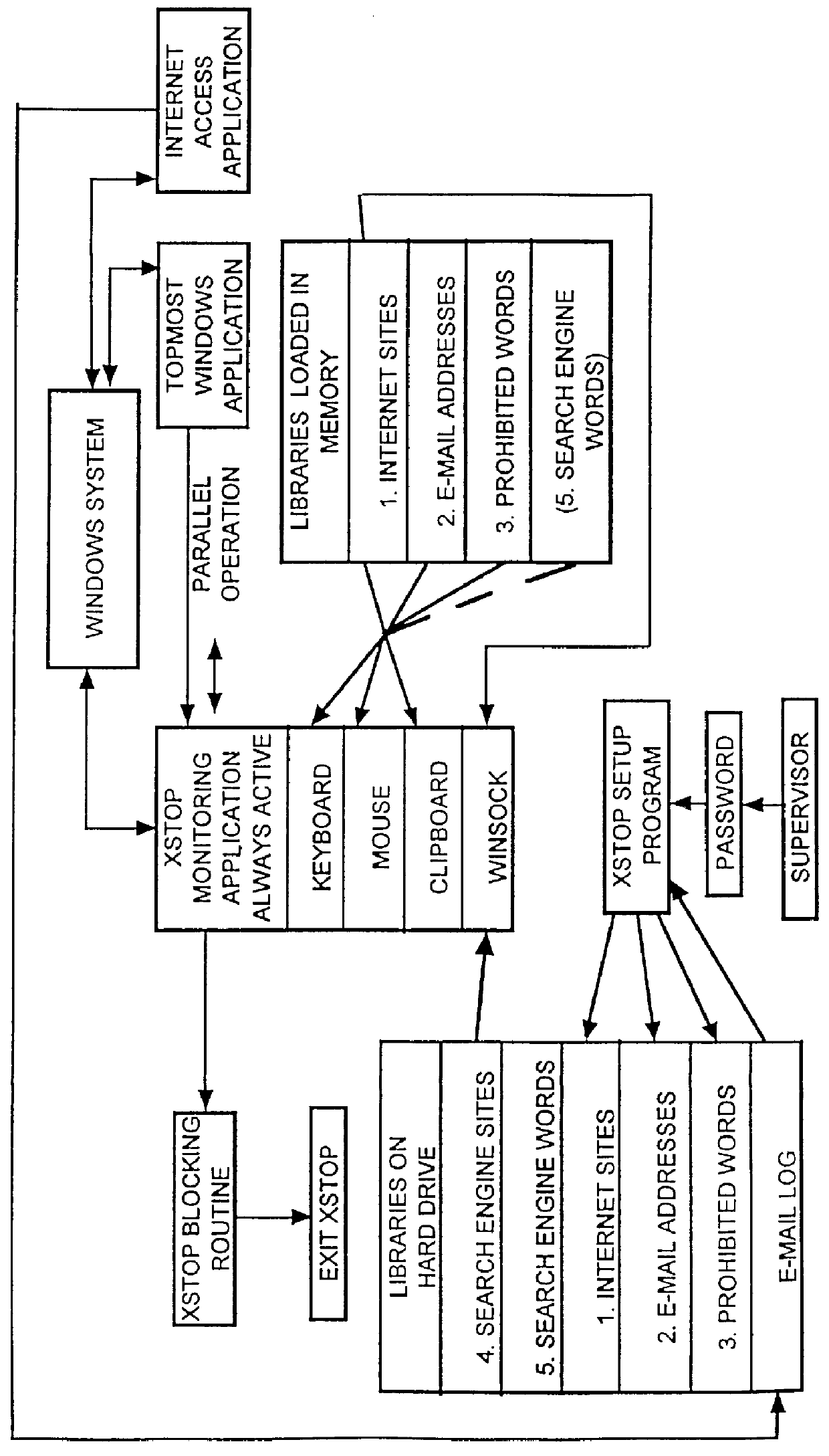
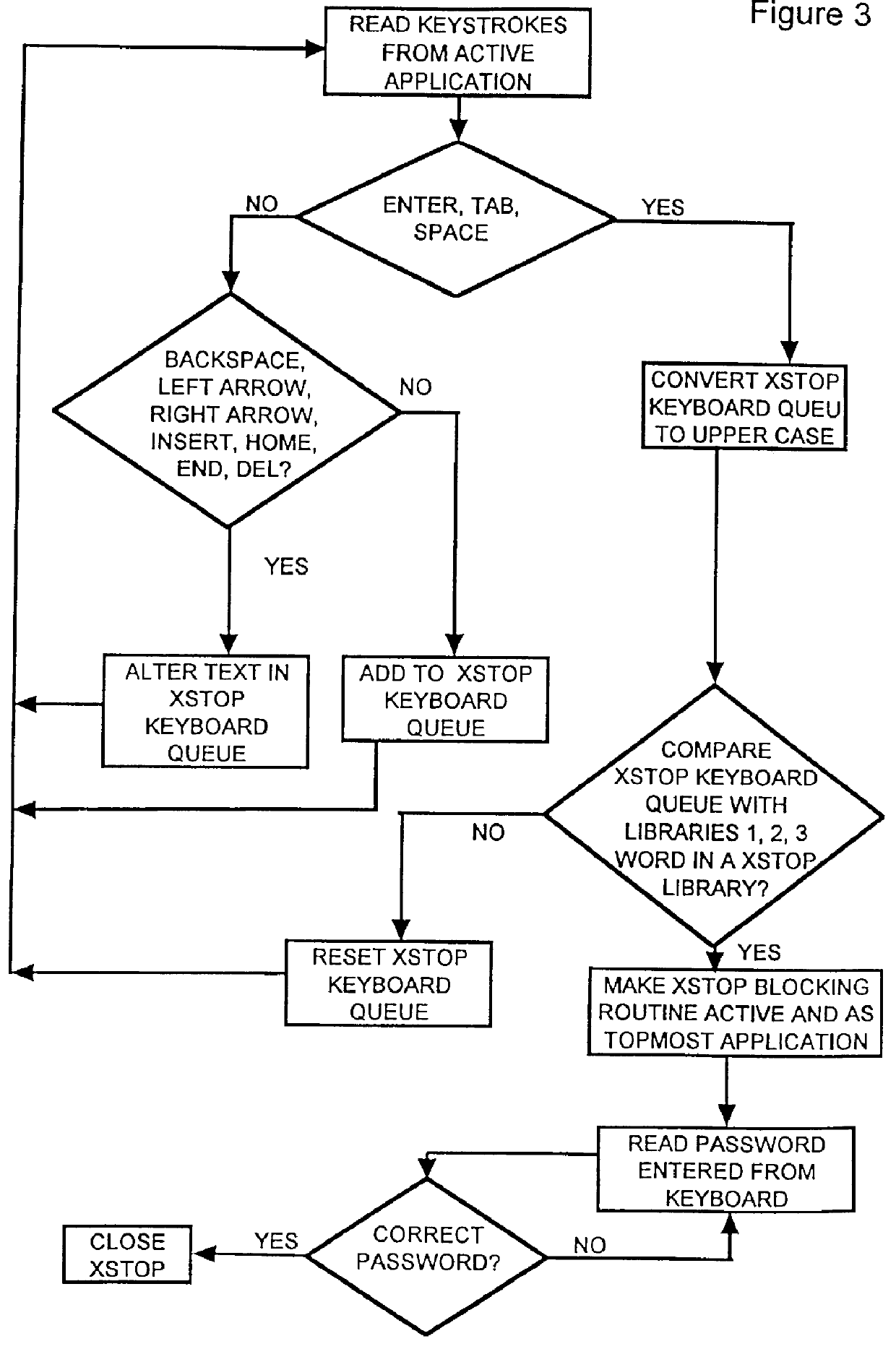
A computer, terminal and a method for blocking the use and creating of vulgar and pornographic material in a responsive and interactive matter that comprehensively monitors computer operations for creation or transmission of vulgar and pornographic material. Data created by the keyboard, data passing through the clipboard, data selected by the mouse pointer, and data passing through the Internet interface are monitored for content and further operation of the computer terminal is blocked. The computer terminal may only be unblocked by a supervisory intervention, such as by entering of a password, or by restarting or resetting the terminal. Key word searches, such as those in Internet search engines, are also monitored, but the terminal adapts to monitor not only for words of a profane and vulgar nature, but also for words that are behaviorally tested to produce lists containing vulgar and profane items, e.g., Internet sites. The computer terminal and method can be modified to block other forms of communication or computer operation, such as blocking transmission of secret business data, blocking execution or opening of certain programs or files, and the like.
Owner:TW SECURITY CORP
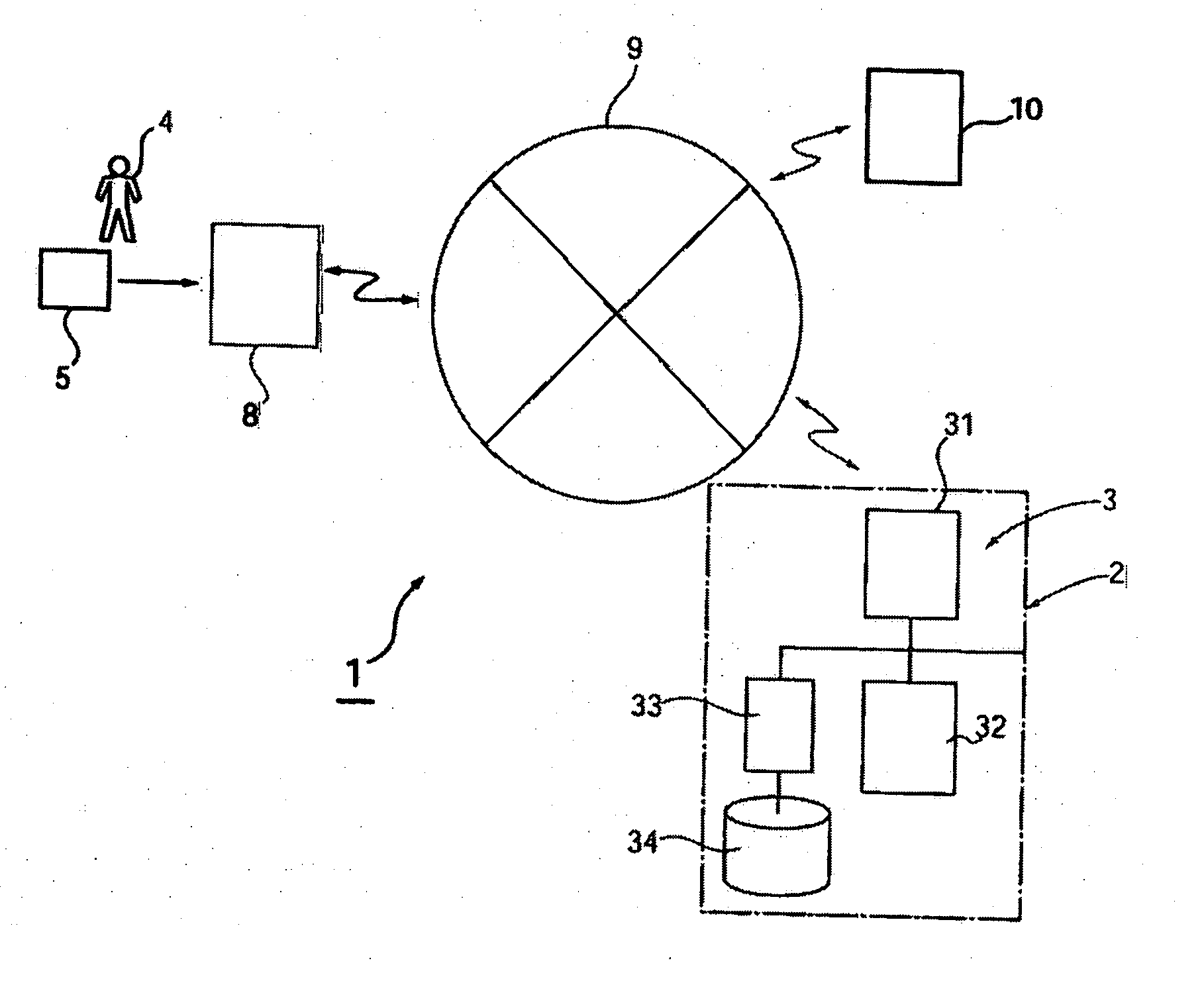
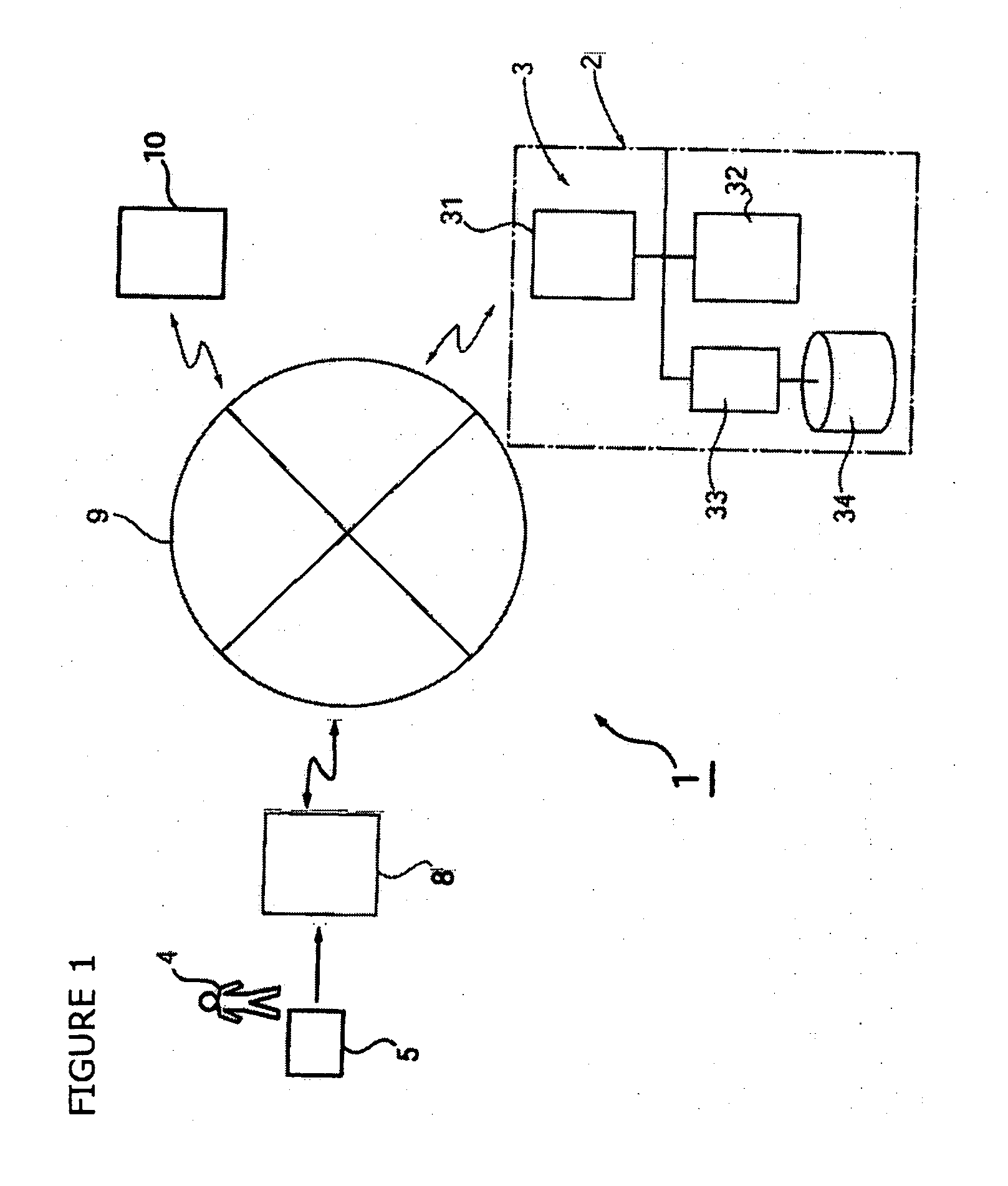
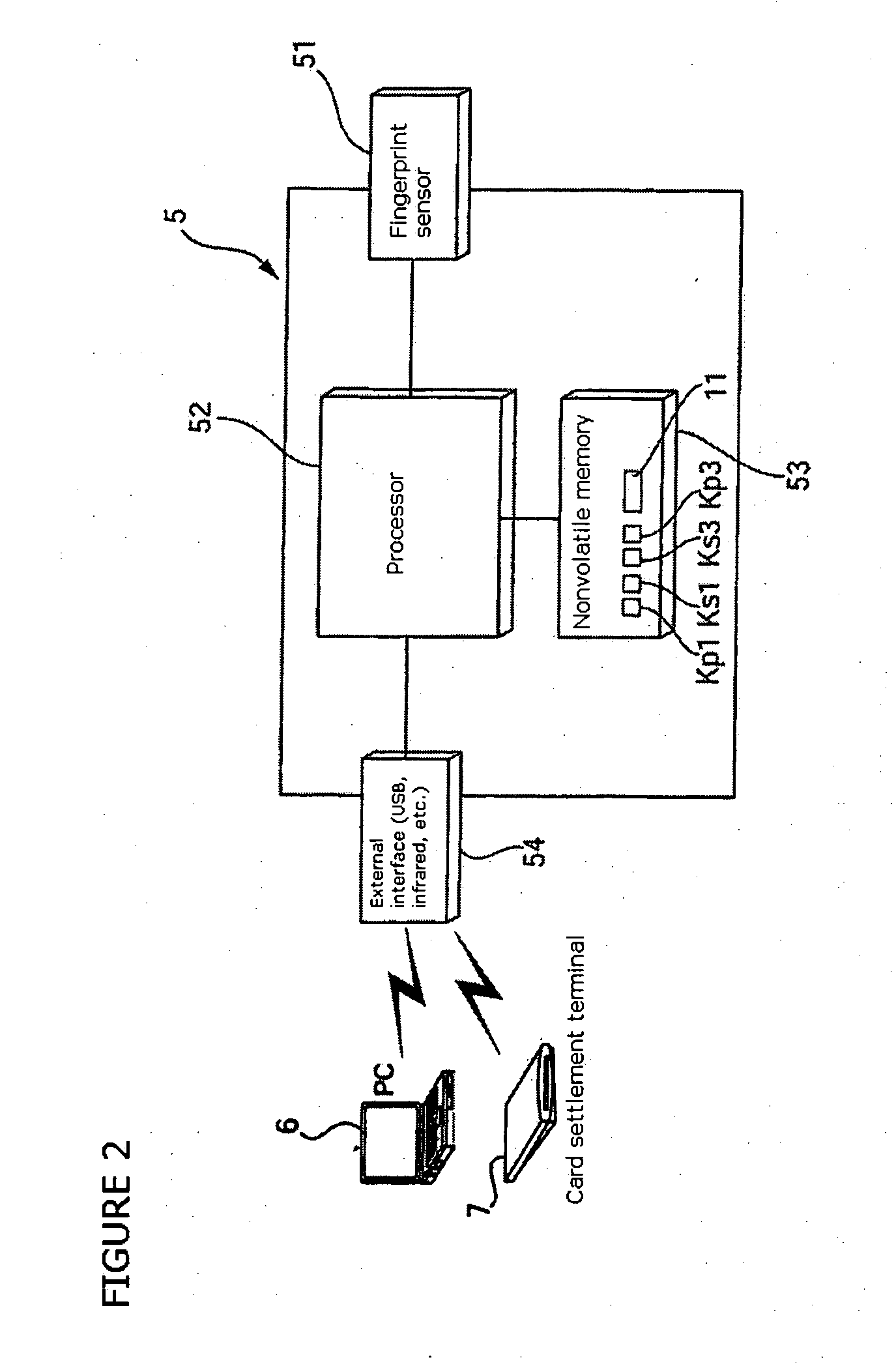
Card settlement method using portable electronic device having fingerprint sensor
InactiveUS20060229988A1Improper useEnsure confidentialityComputer security arrangementsIndividual entry/exit registersFingerprintComputer hardware
In a card settlement system using a portable electronic device having a fingerprint sensor, a credit card and a portable electronic device (5) having a fingerprint sensor are issued to a person who has made application. To this electronic device (5), card information (12), a storage public key Kp1, and
Owner:PARA3
Device to deploy a resilient sleeve to constrict on body tissue
InactiveUS20060212046A1Convenient treatmentContainment leakSurgical pincettesProsthesisEngineeringBody tissue
The preferred embodiment of the invention contemplates a device configured to prepare and deploy a resilient sleeve on to a portion of body tissue. The device expands the resilient sleeve, uses a vacuum system to draw the body tissue in to the resilient sleeve, and releases the resilient sleeve from the expanded state so that it captures and constricts the body tissue.
Owner:GYRUS ACMI INC (D B A OLYMPUS SURGICAL TECH AMERICA)
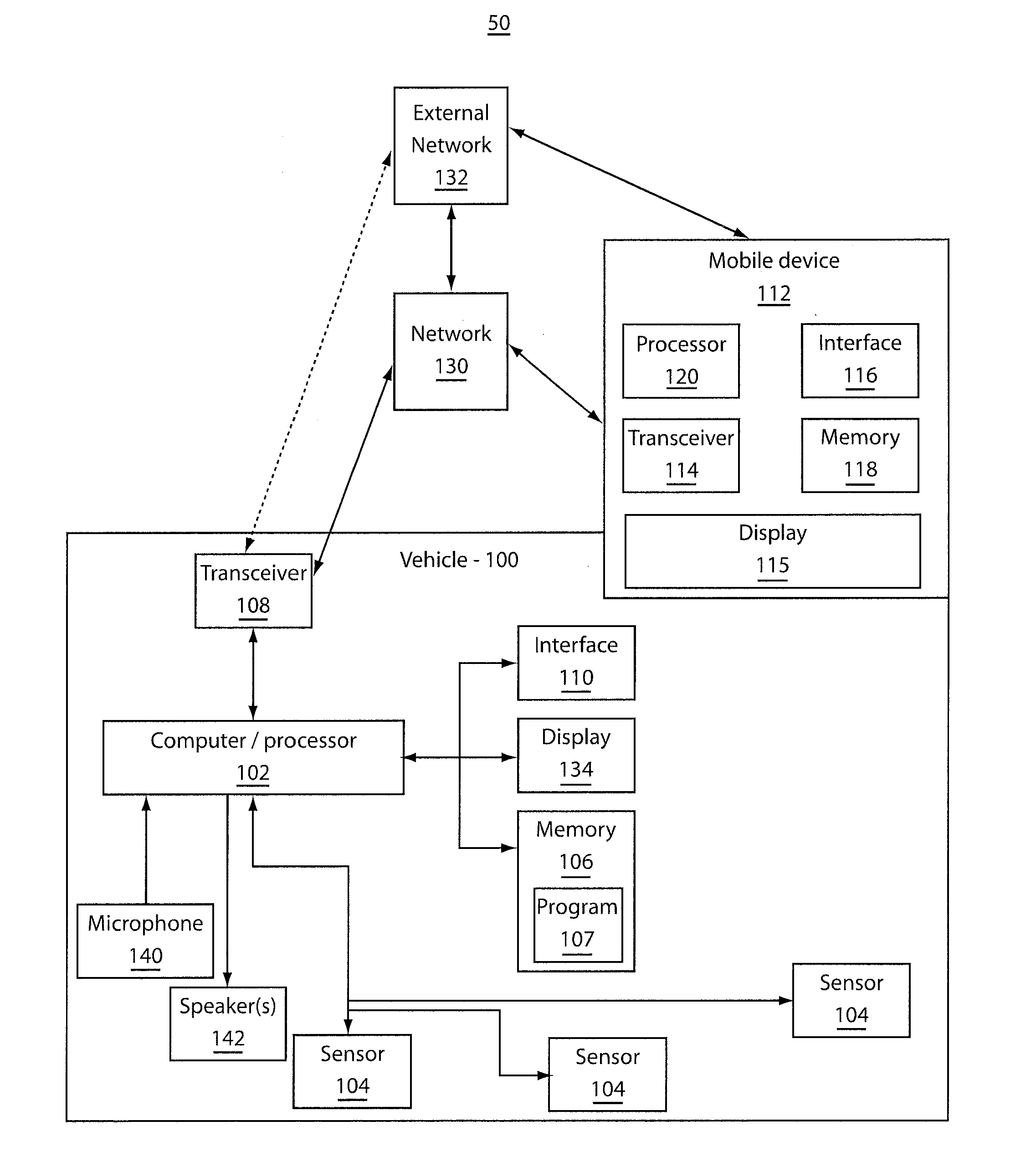
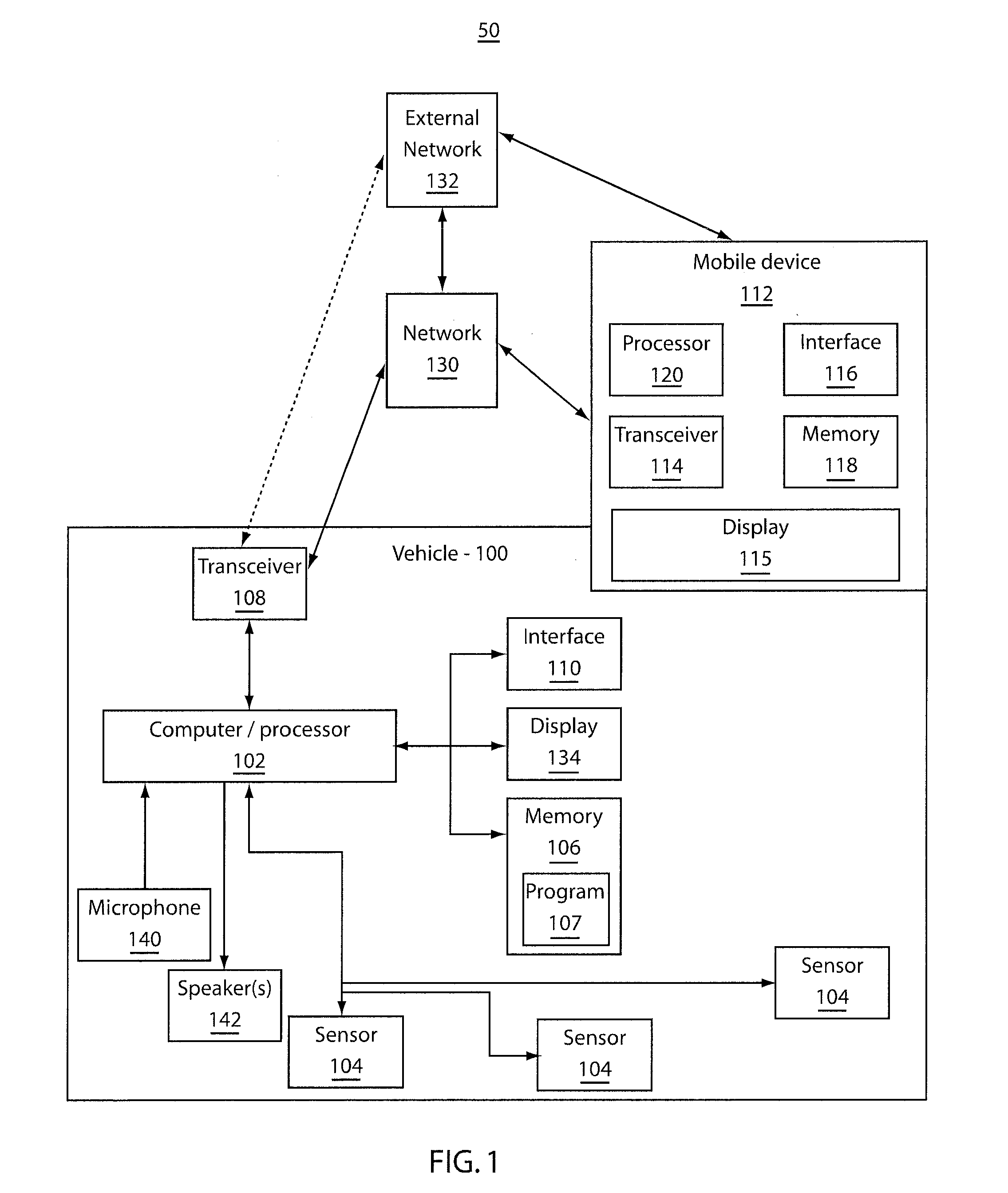
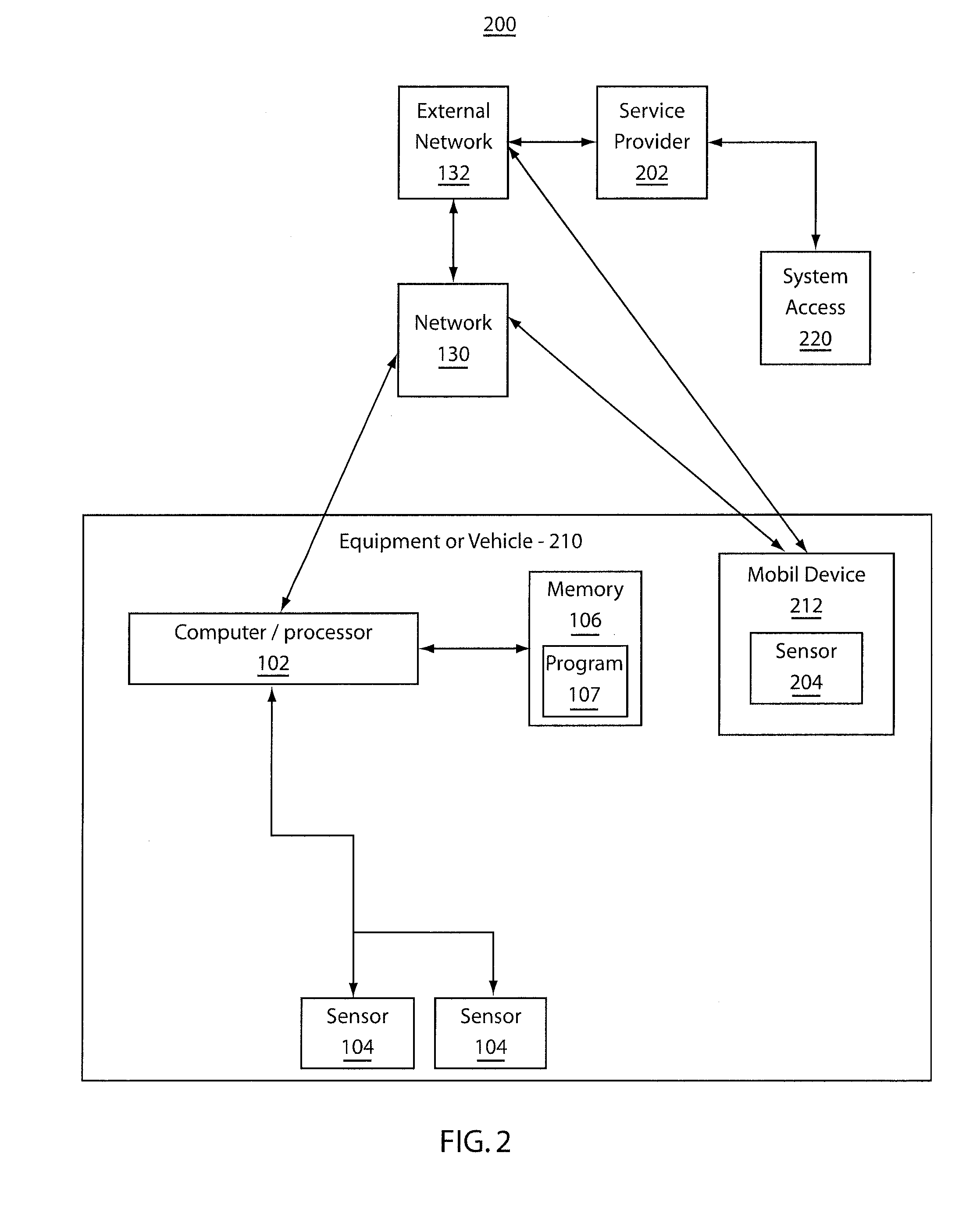
Prevention of texting while operating a motor vehicle
InactiveUS20120176232A1Improper useRegistering/indicating working of vehiclesDigital data processing detailsMobile vehicleComputer module
A system and method includes sensors configured to measure conditions of a vehicle. A monitoring module is configured to evaluate the conditions input thereto from the sensors. The monitoring module is further configured to determine a state of a mobile device located within the vehicle. Based upon a combination of the conditions of the vehicle and the state of the mobile device, a determination of improper use of the mobile device is made.
Owner:SLINGSHOT IOT LLC
Image processing system, image processing method, and image input system
InactiveUS7002709B1Avoid misuseImproper useDigitally marking record carriersDigital computer detailsColor imageImaging processing
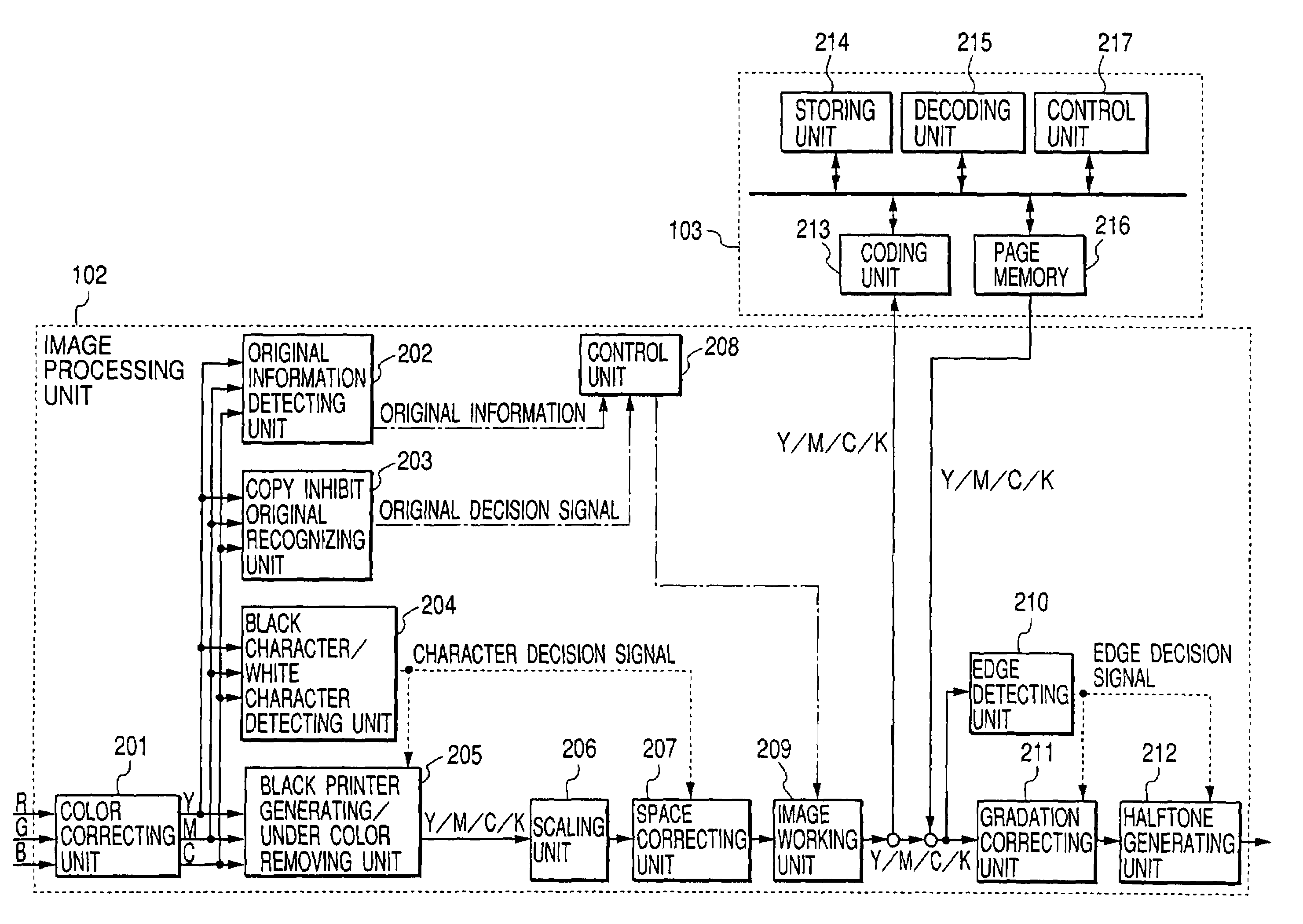
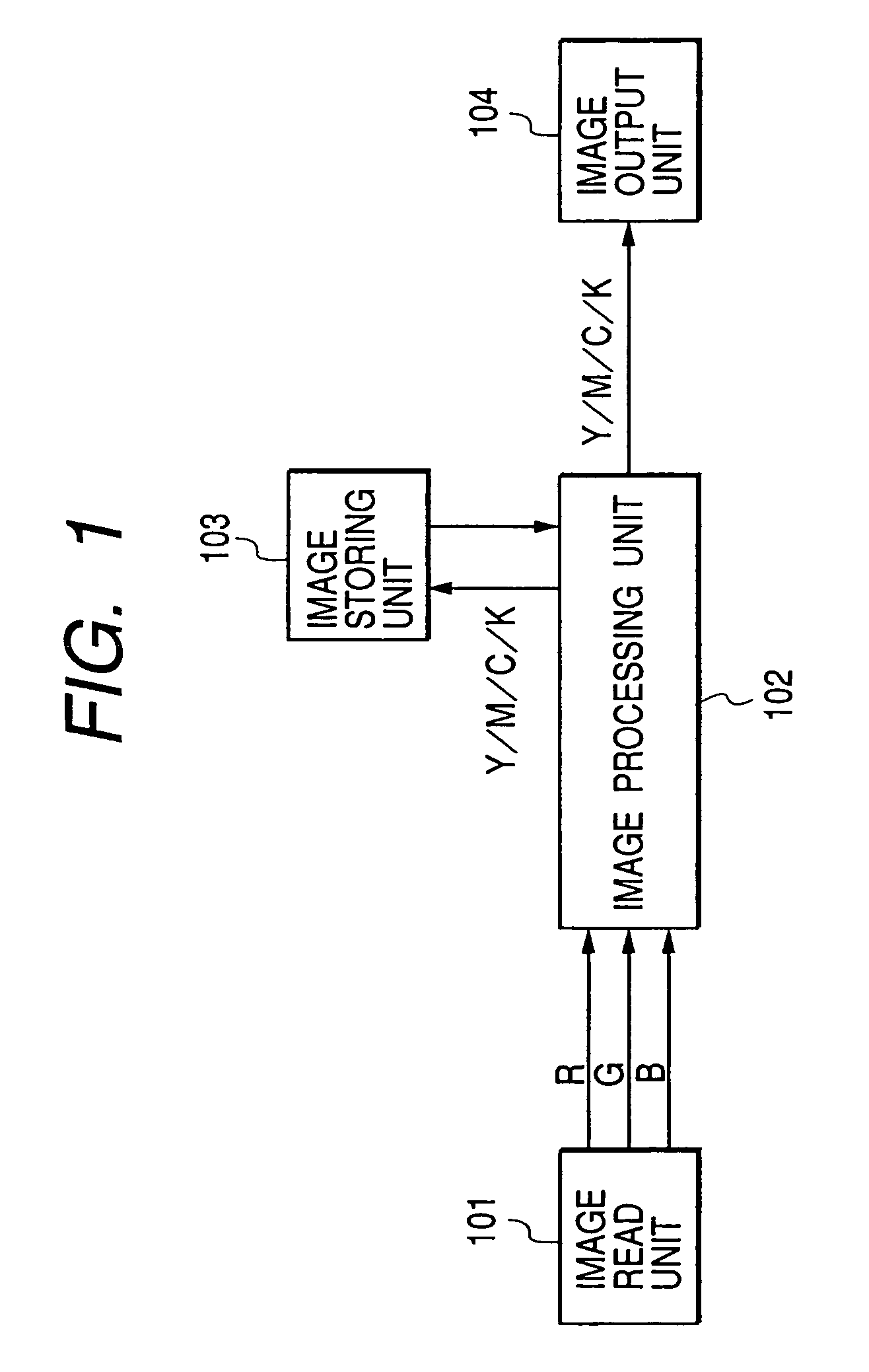
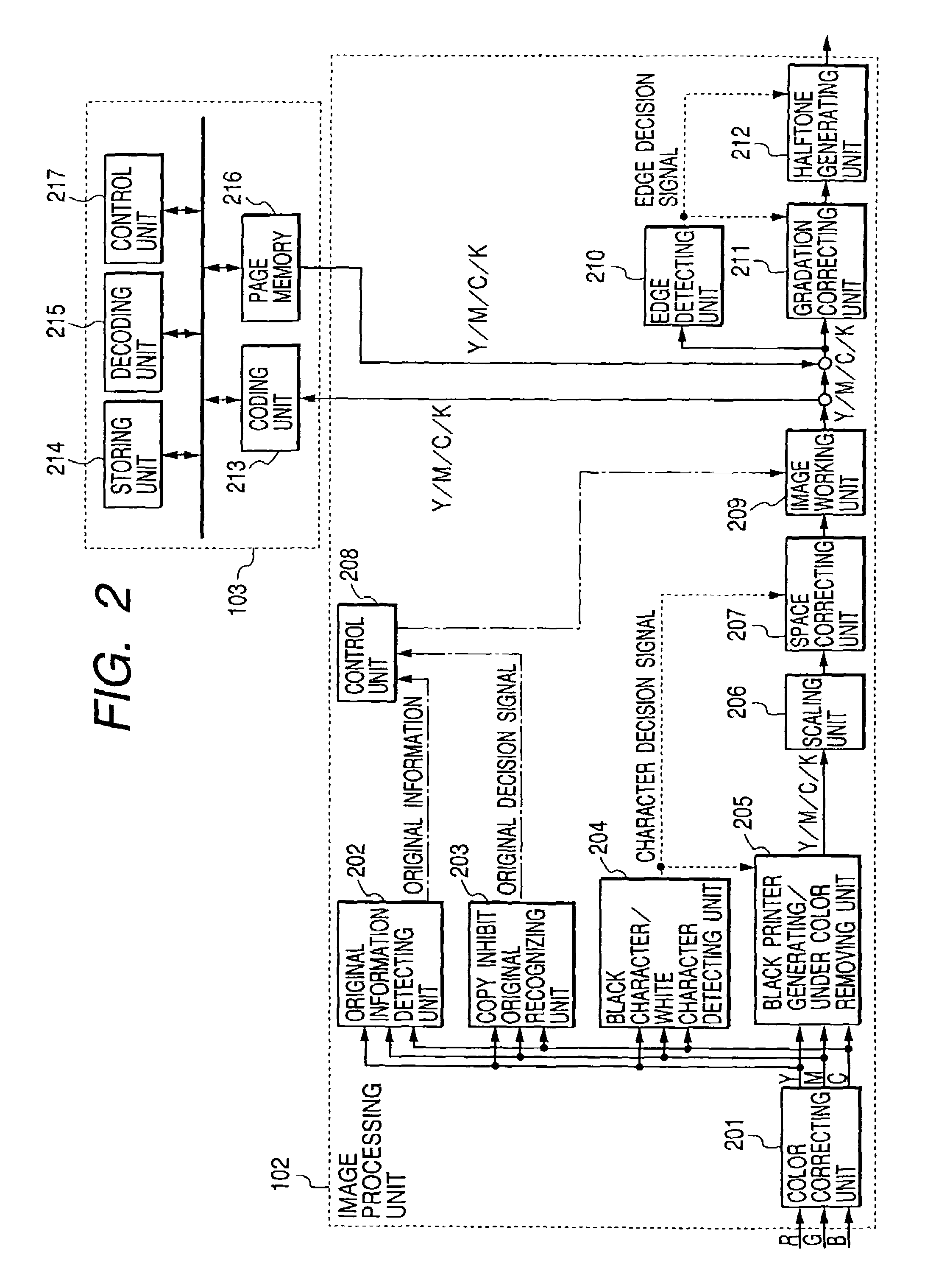
The reproduction of a copy inhibit image and the abuse of data through a network are to be prevented without sacrificing various page editing functions. An image read unit scans an original placed on an original carrying table and thereby generates RGB color image signals of multi-value. An image processing unit performs various image processing and, upon detection of a copy inhibit original, performs image working for preventing faithful reproduction of the copy inhibit original. An image storing unit temporarily stores page by page original images provided from the image processing unit. If a copy inhibit image is contained in the original images, the image working is performed by the image processing unit to prevent faithful reproduction and the images after the image working are stored in the image storing unit. An image output unit performs a printing operation in accordance with image data outputted from the image processing unit.
Owner:FUJIFILM BUSINESS INNOVATION CORP
Device to deploy a resilient sleeve to constrict on body tissue
Owner:GYRUS ACMI INC (D B A OLYMPUS SURGICAL TECH AMERICA)
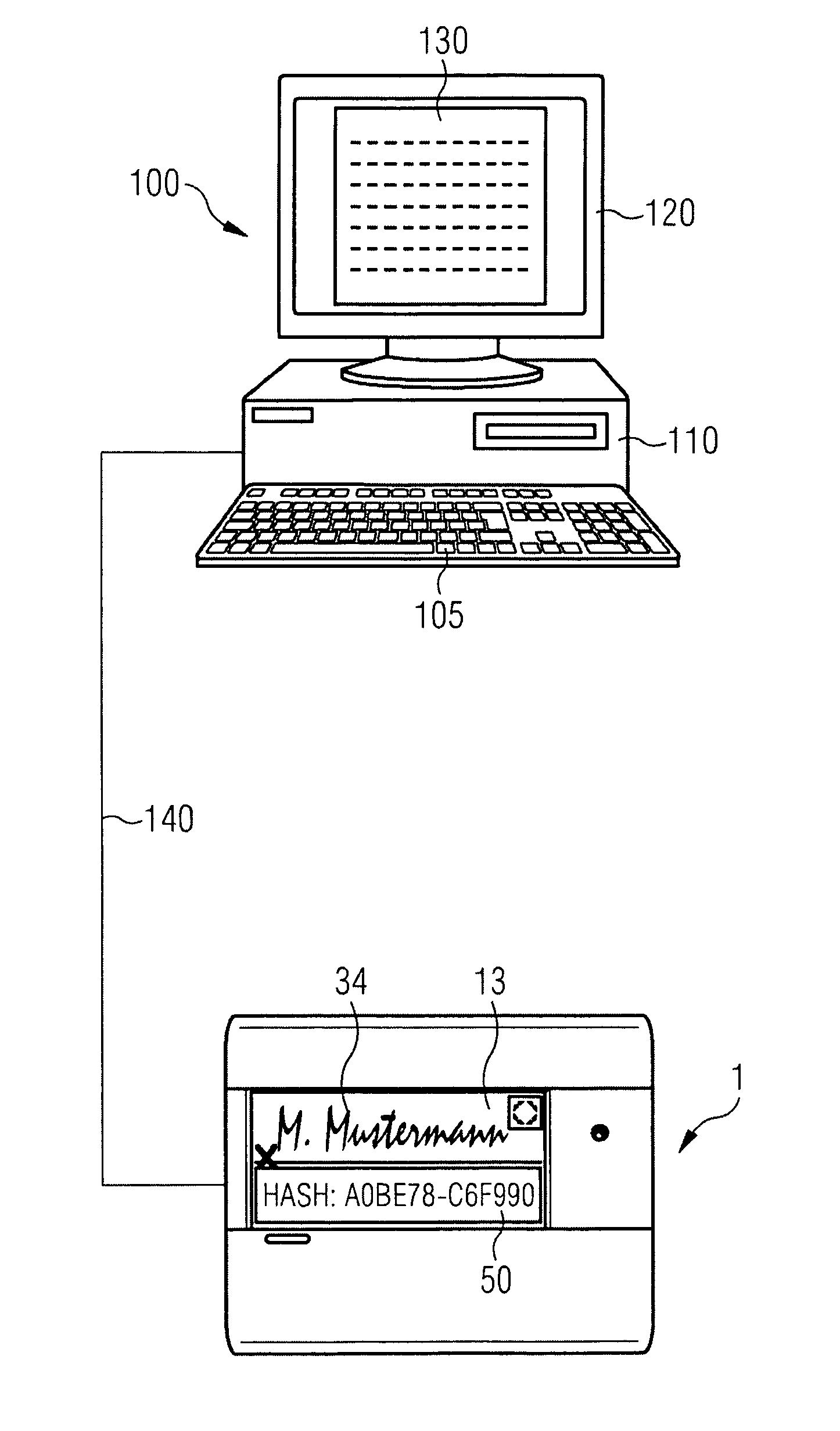
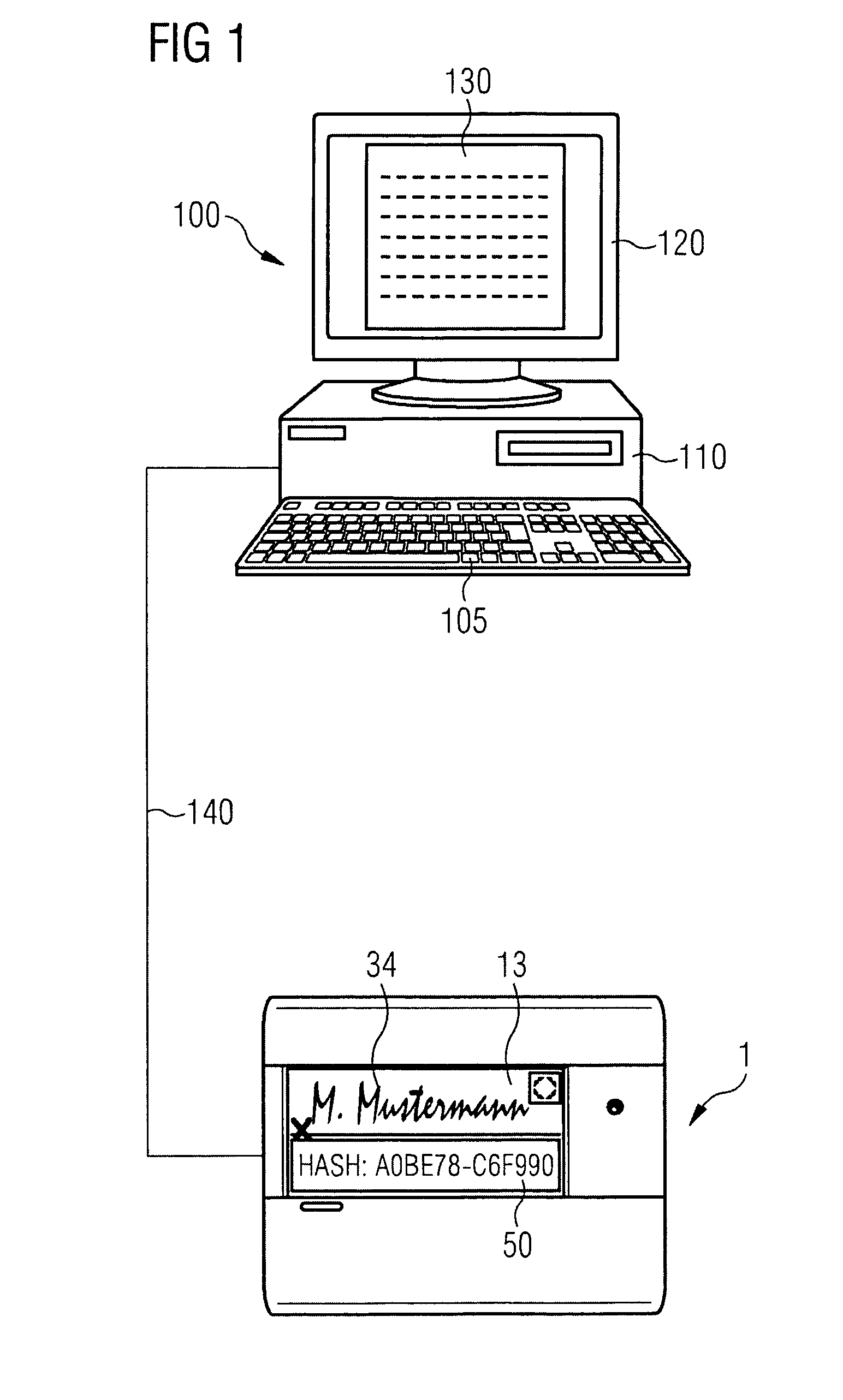
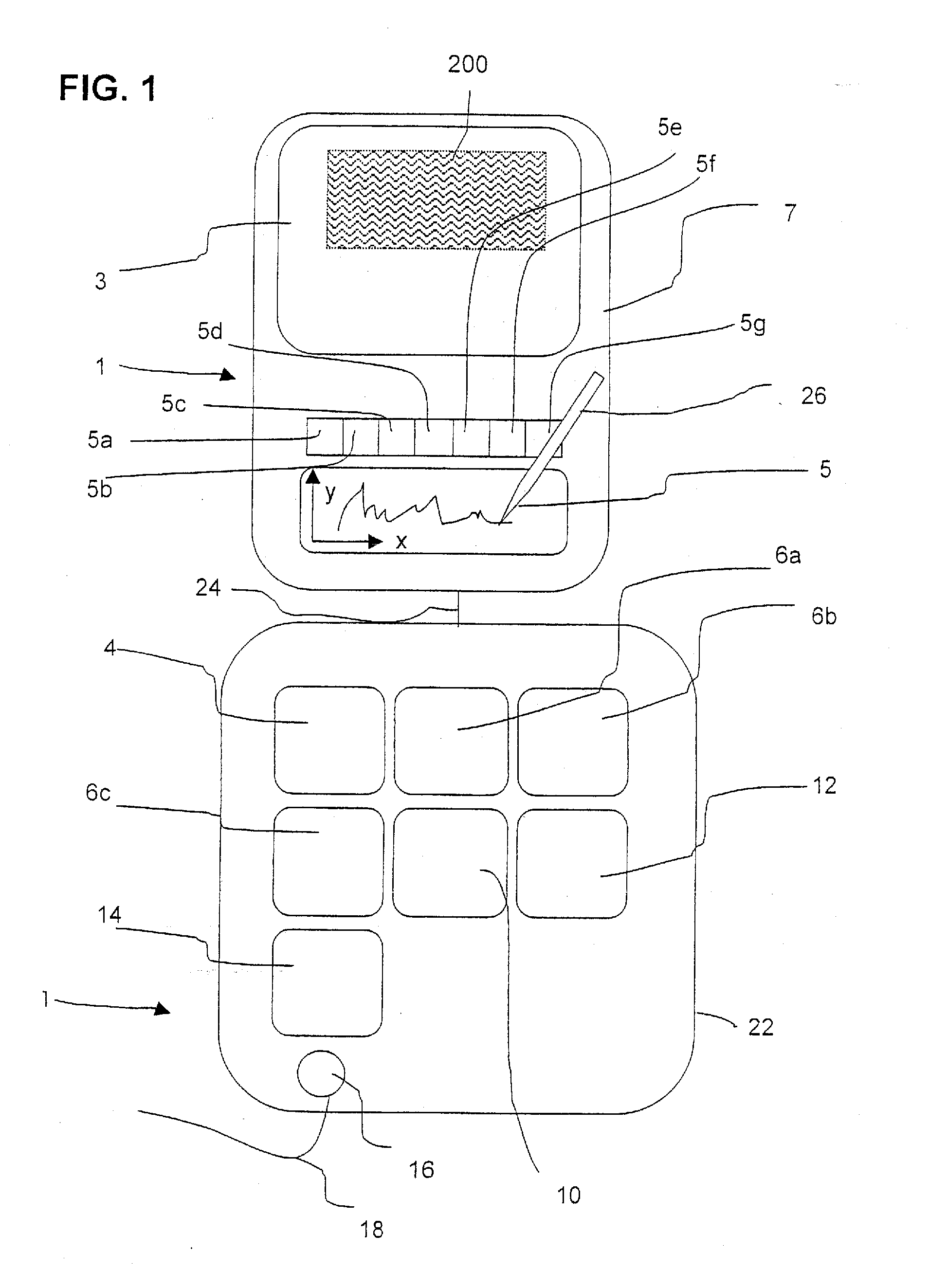
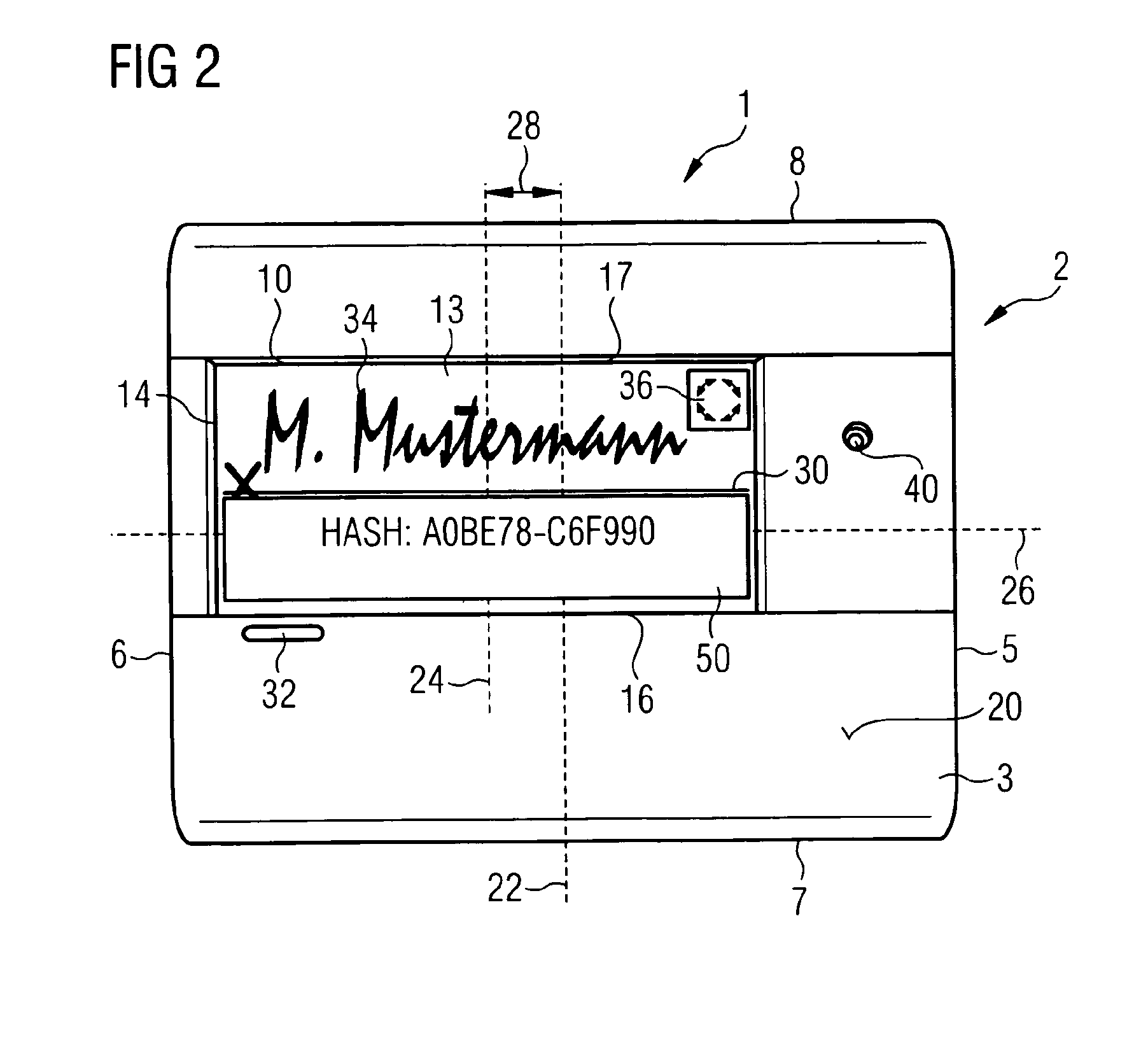
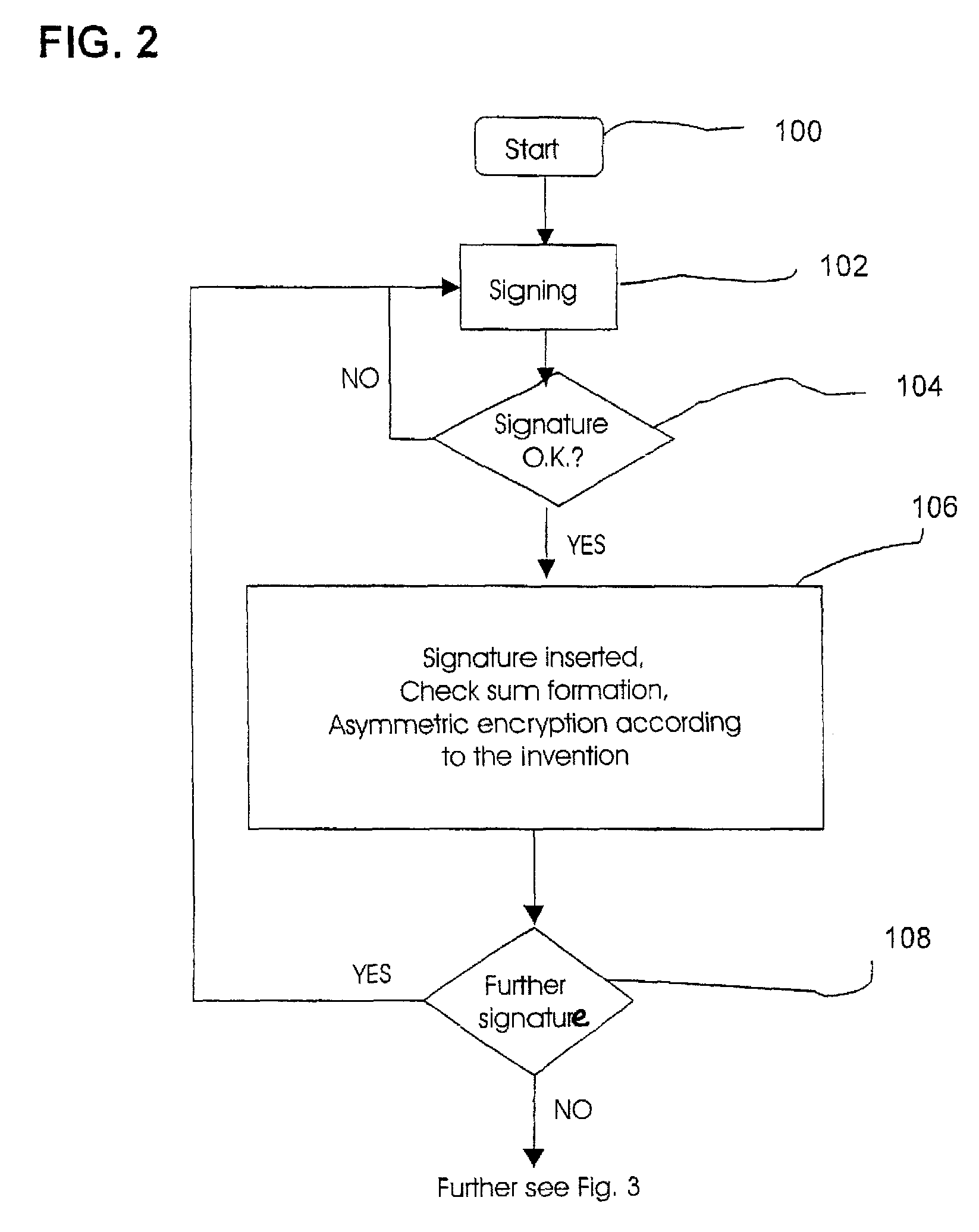
Method and device for electronically capturing a handwritten signature using embedding technique
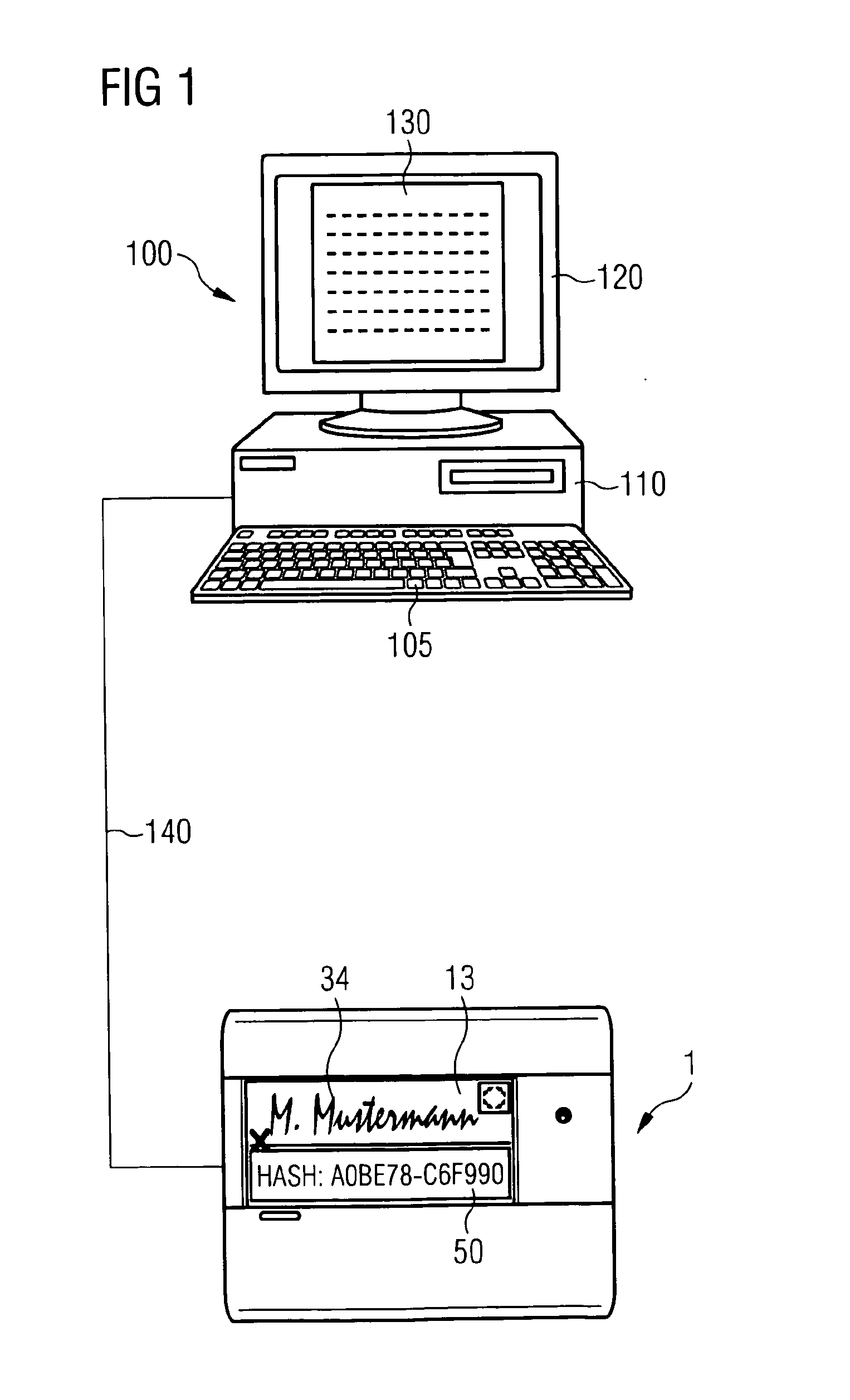
ActiveUS8700905B2Improper useUser identity/authority verificationUnauthorized memory use protectionElectronic documentDigital signature
A method and apparatus for encrypting an electronic document involves a computer having a first monitor and a signature capture apparatus configured to capture a handwritten signature on a second monitor. A hash sum of the electronic document generated in the computer is transmitted to the signature capture apparatus. The electronic document and the first hash sum thereof are displayed on the first monitor. The first hash sum is also displayed on the second monitor. After electronically capturing the handwritten signature, the signature data are encrypted using the first hash sum. A digital signature image is generated in the signature capture apparatus and the first hash sum is embedded therein. The embedded first hash sum is then extracted in the computer. If the extracted hash sum is identical to the first hash sum generated in the computer apparatus, the encrypted signature data and the signed document are stored.
Owner:STEPOVER
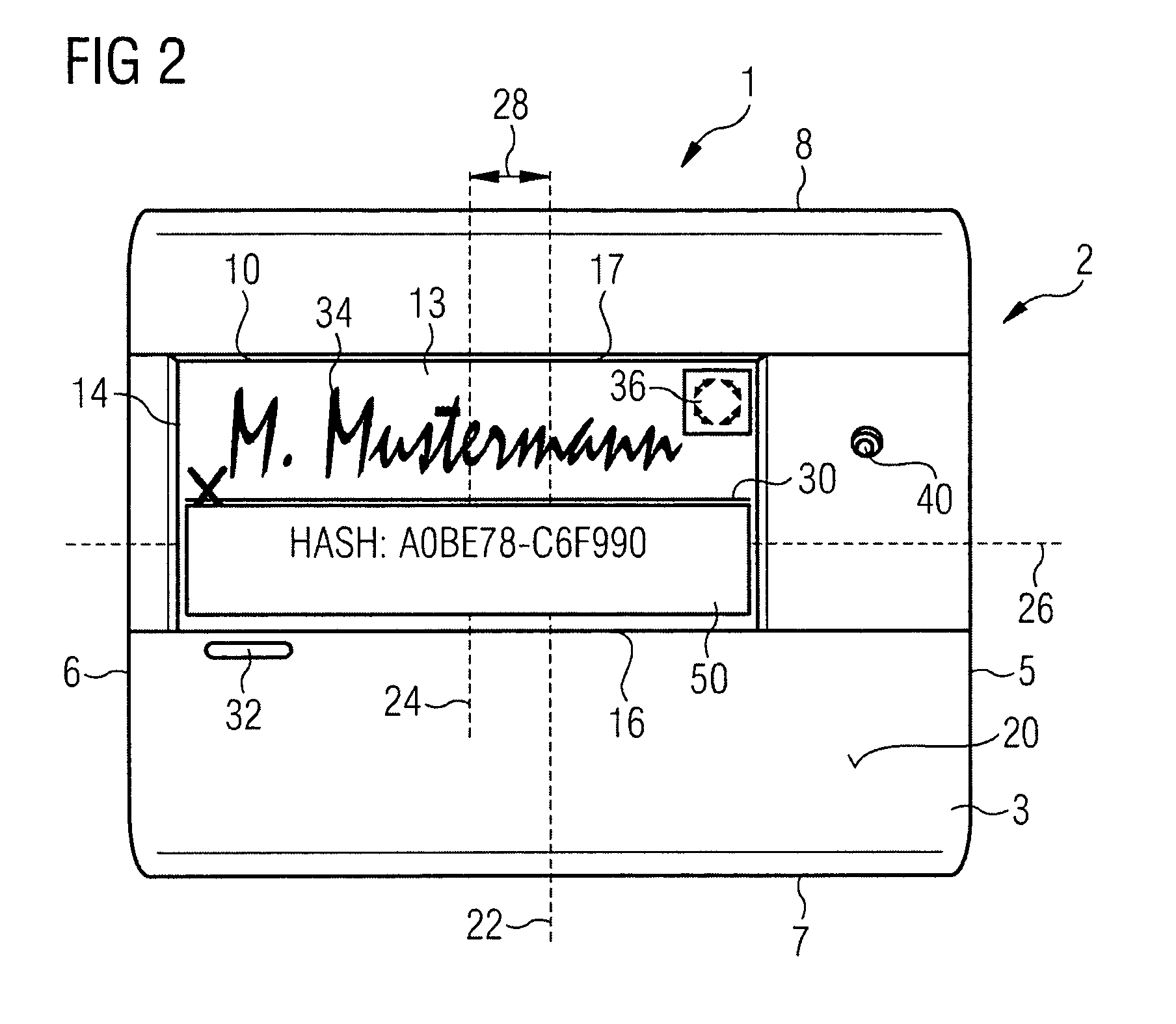
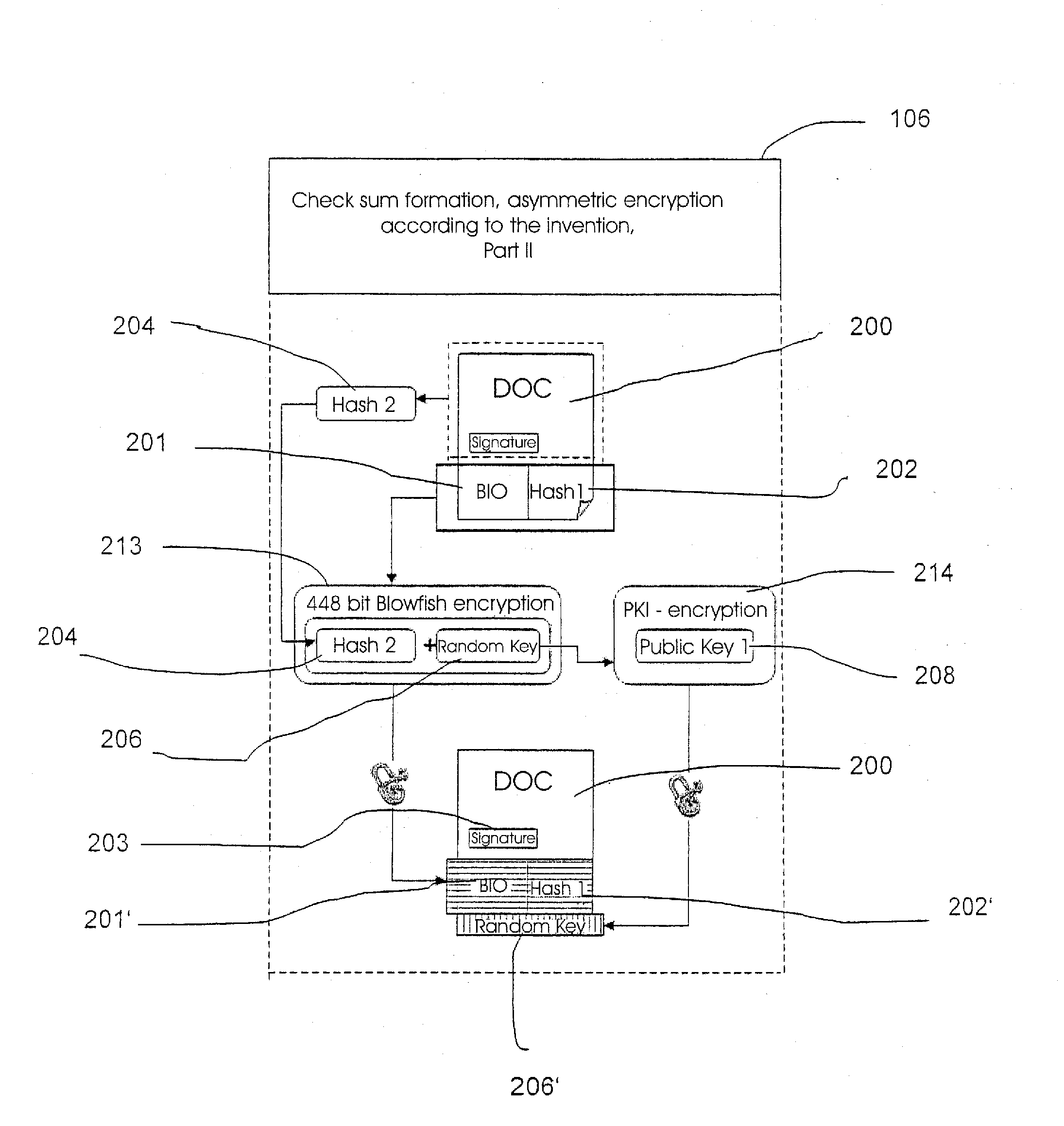
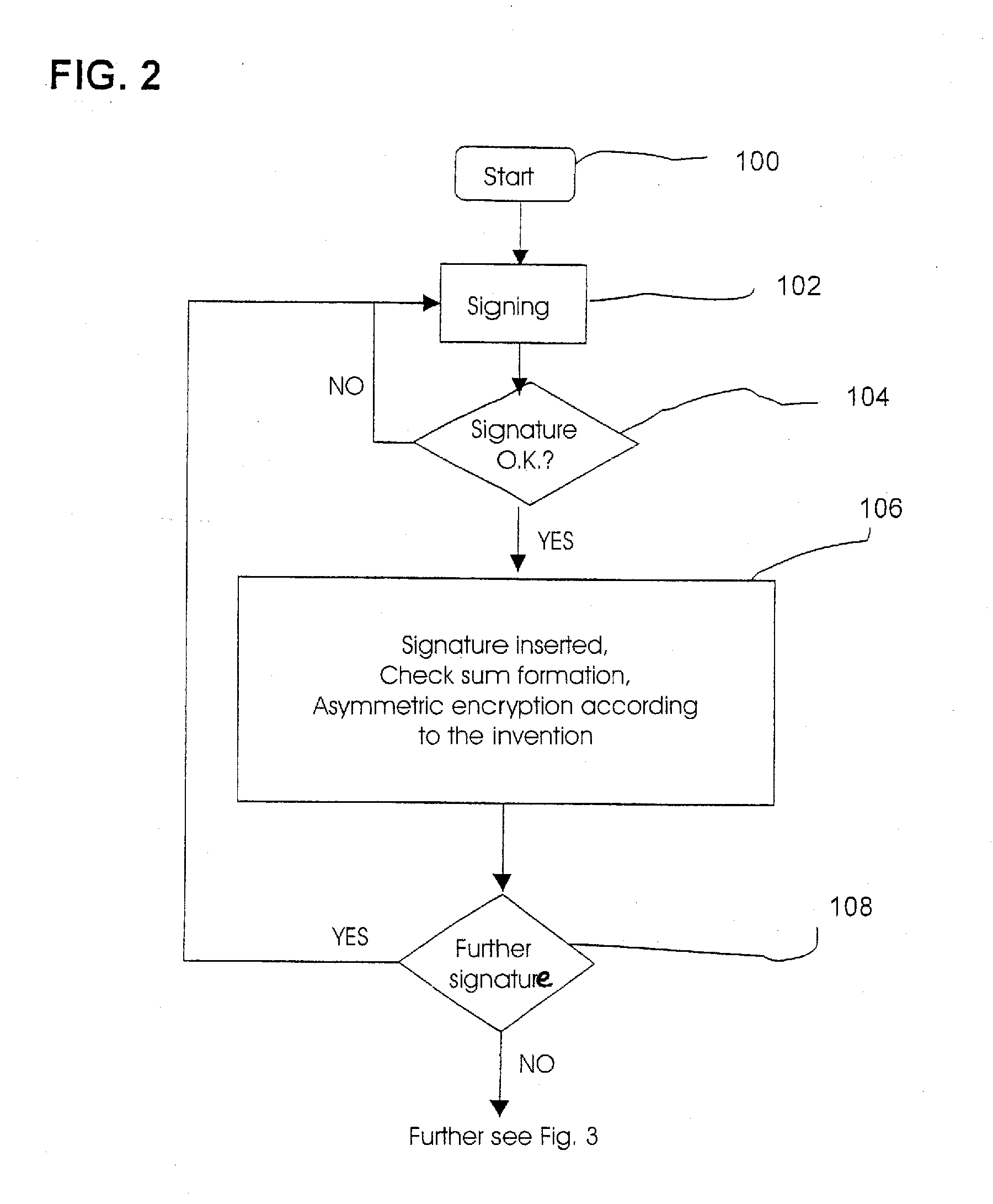
Method and Device for Safeguarding of a Document with Inserted Signature image and Biometric Data in a Computer System
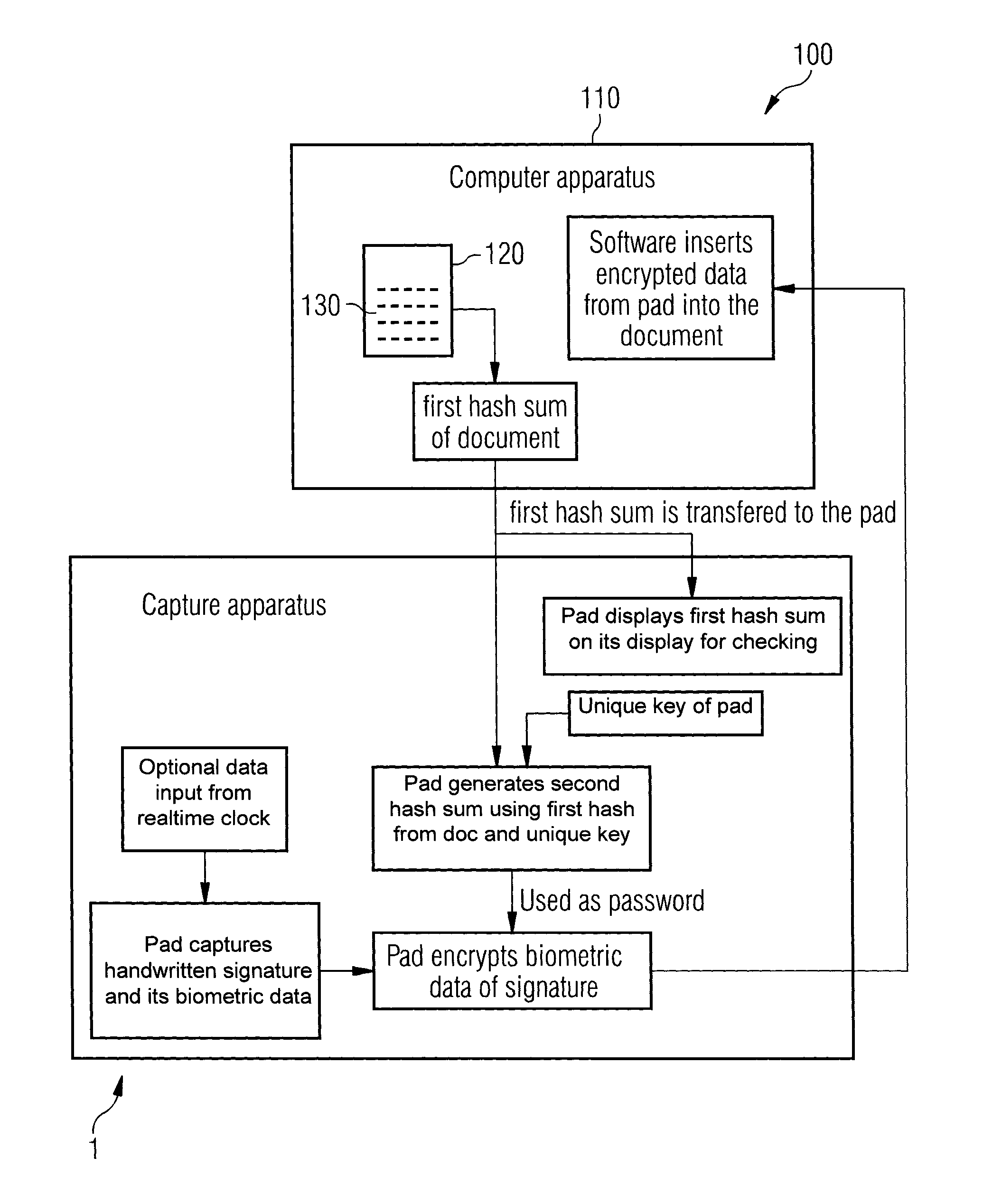
ActiveUS20100106973A1Improper useConfidenceDigital data processing detailsUser identity/authority verificationElectronic documentHash function
A method for safeguarding an electronic document includes inserting at least one digital signature image into the electronic document and generating a first check sum for the electronic document, with or without optionally-inserted biometric signature data, using a first hash function. A second check sum is then generated using a second hash function. The first check sum and the biometric data, if provided, are then symmetrically encrypted using a key that is the sum of the second check sum and a generated random value. The symmetrically-encrypted first check sum is attached to the document. The random value is then asymmetrically encrypted using a first public key of a first key pair and the asymmetrically-encrypted random value is added to the document.
Owner:STEPOVER
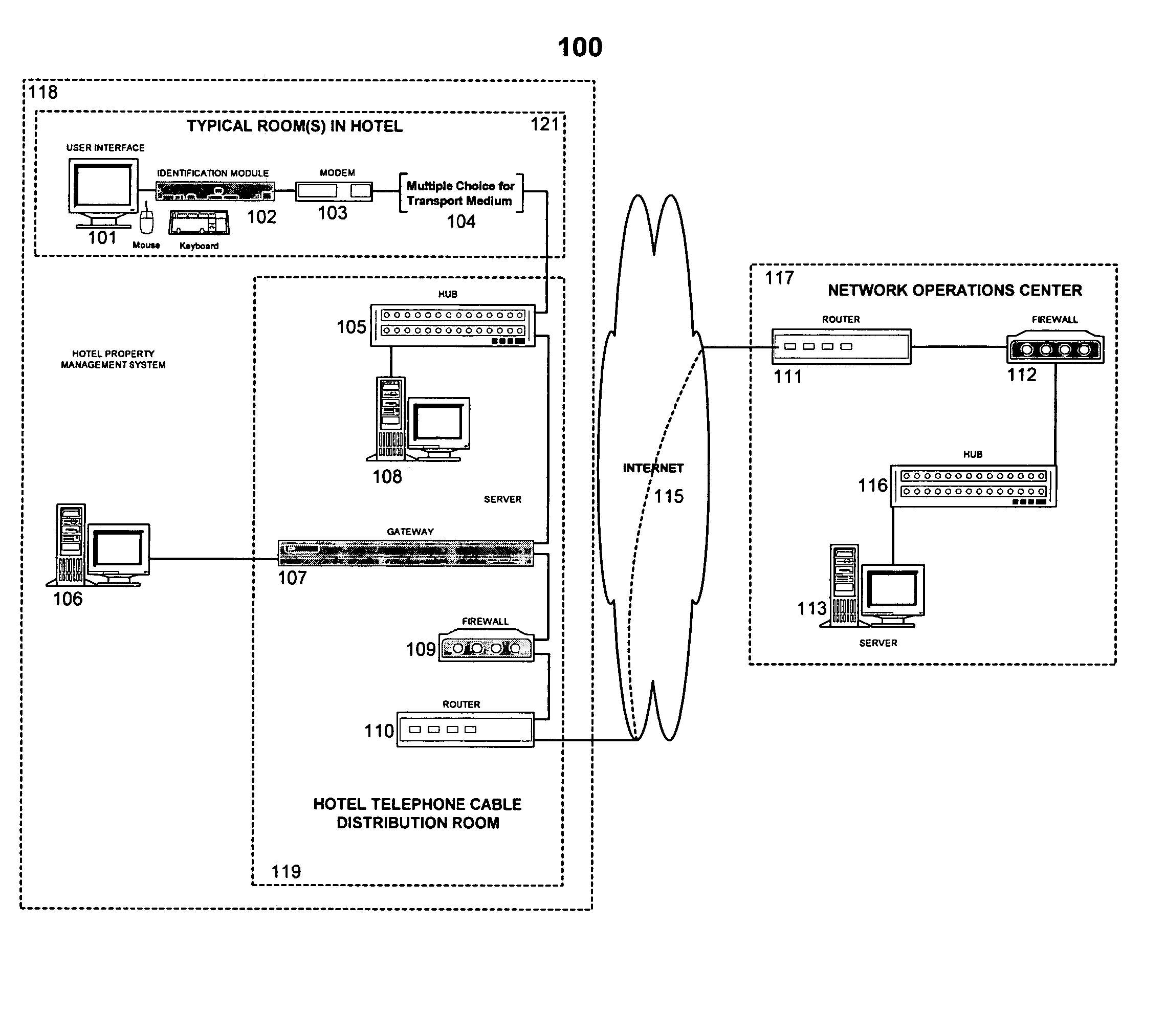
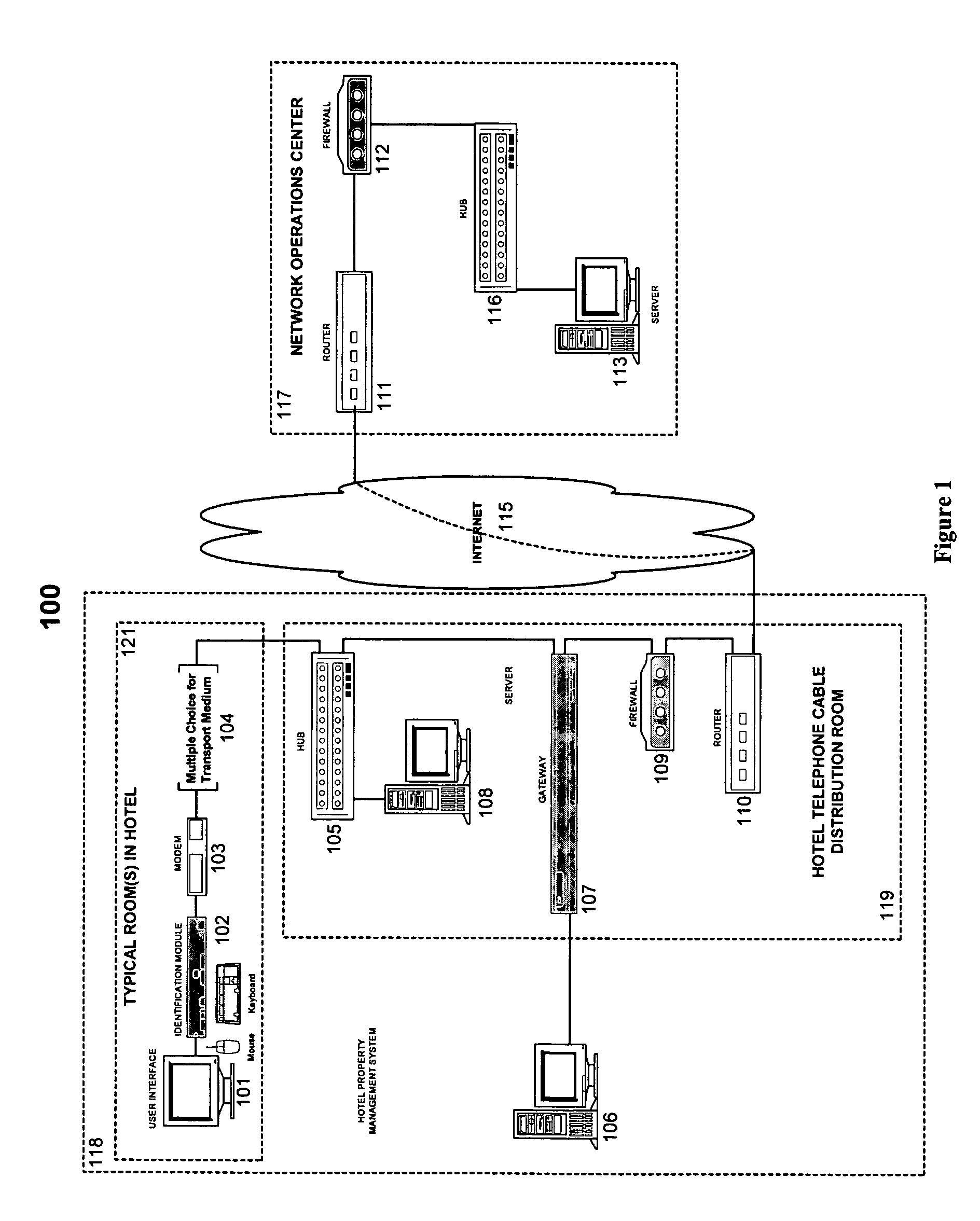
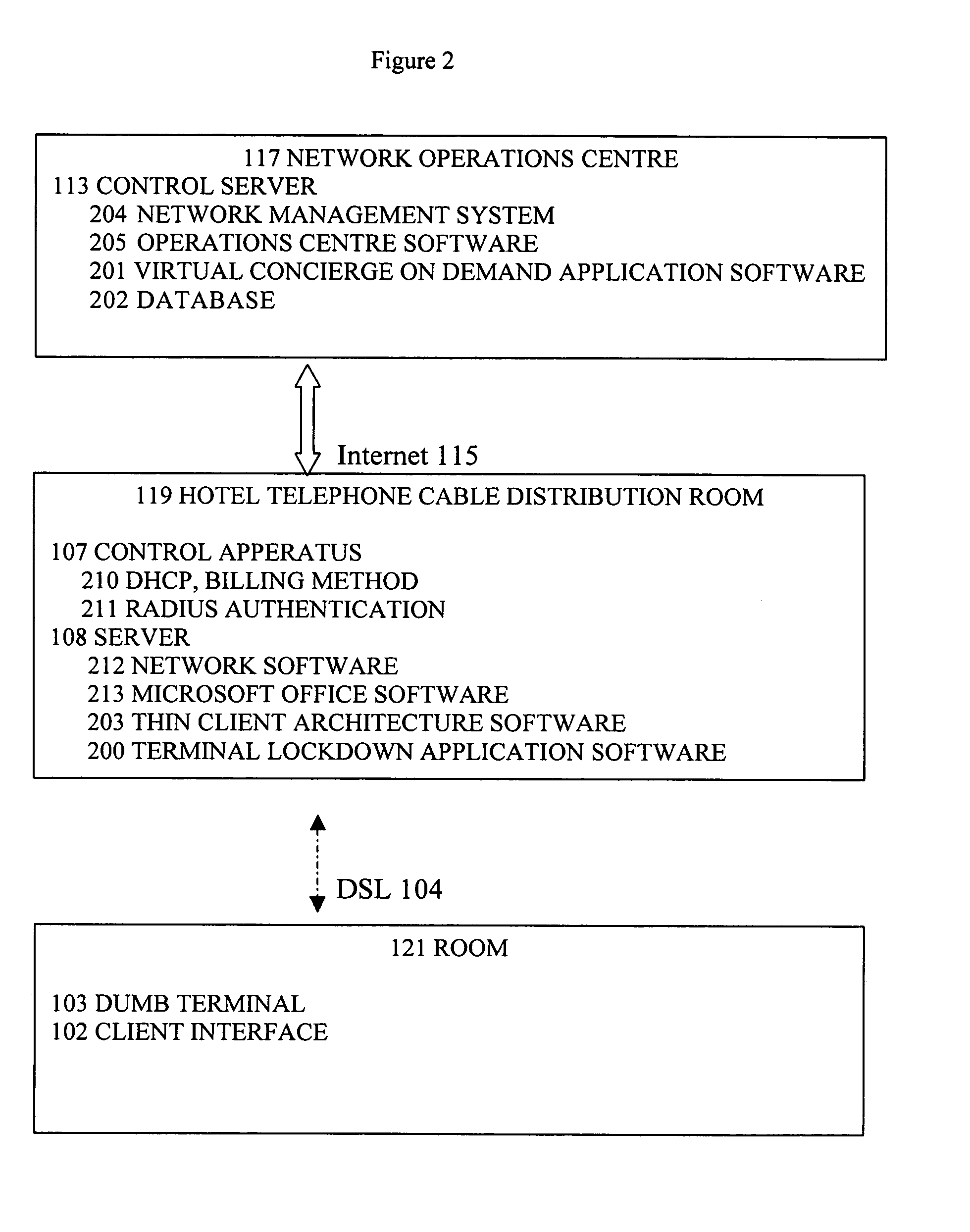
System and method for providing services across a network
InactiveUS20050154736A1Eliminate needEliminate requirementsMetering/charging/biilling arrangementsCommerceClient-sidePersonalization
The invention provides a thin-client system and method that enables users to interact with a remote server in order to eliminate local computer systems being required within private and semi-private spaces such as hotel rooms. The system enables secure and personalized short term access to high-speed services and enables an operator to deliver personalized information services to different users.
Owner:MEIKLEHAM DANIEL MCNEILL +2
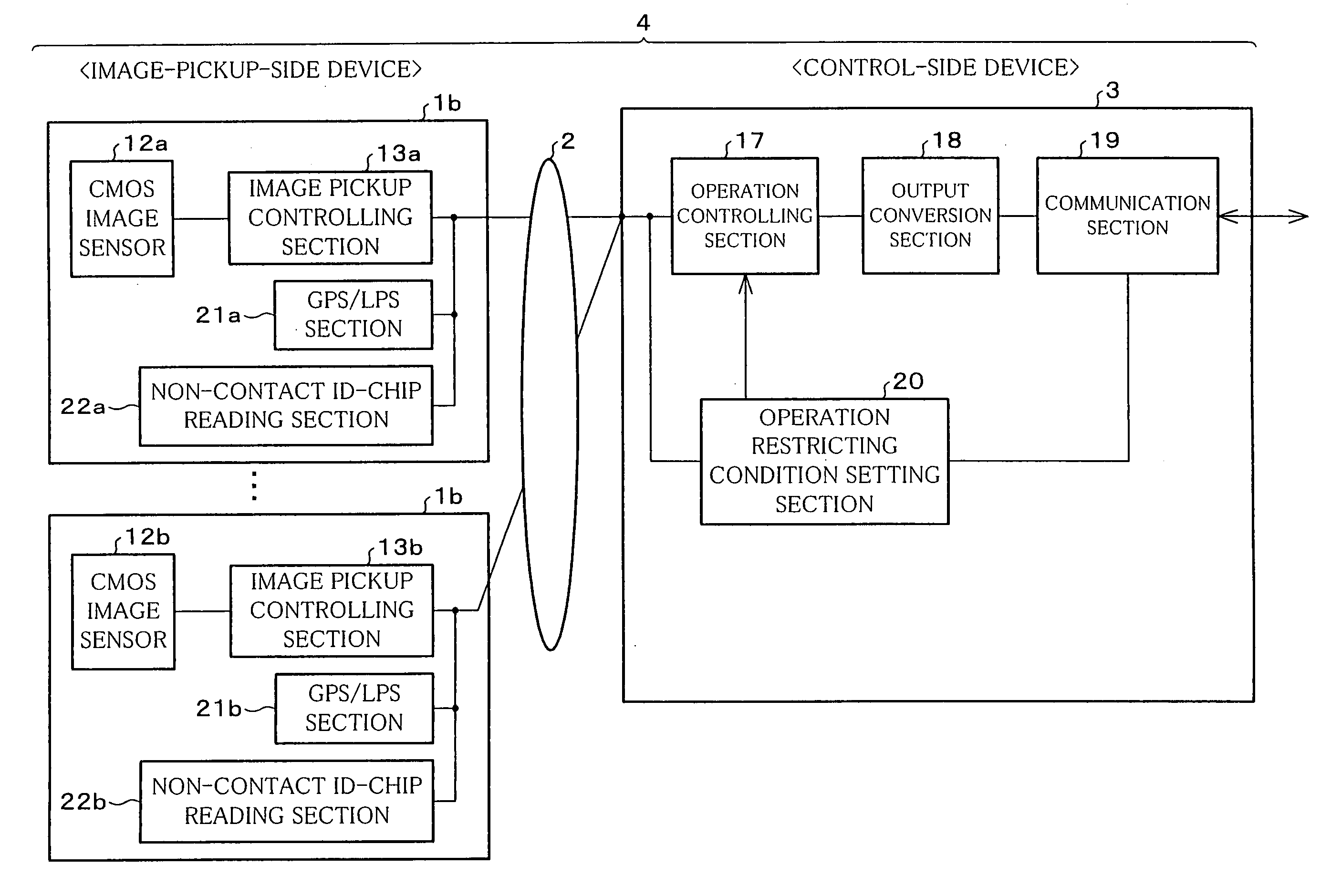
Imaging apparatus, imaging system, imaging apparatus control method and control program, and recording medium in which the same program has been recorded
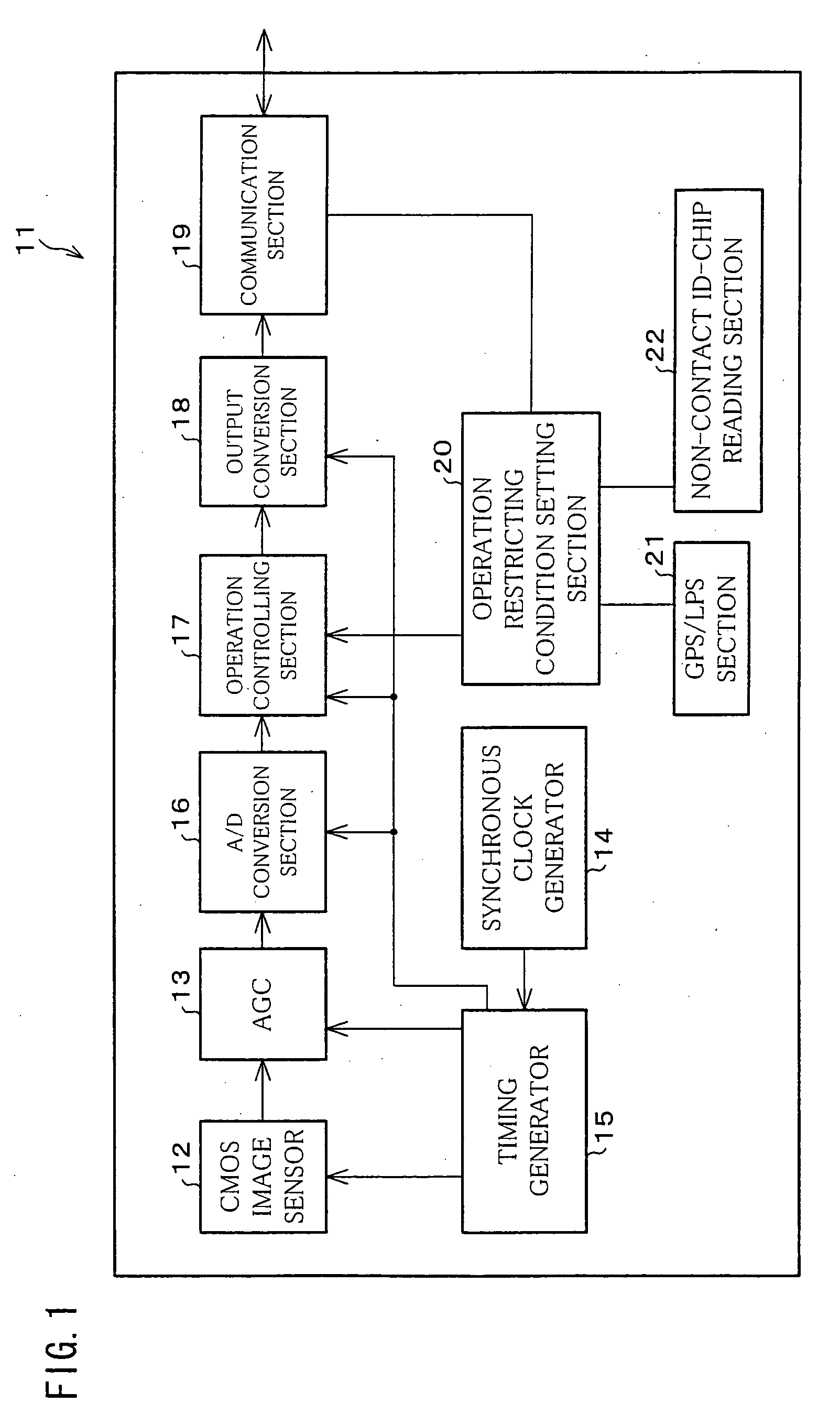
InactiveUS20050231357A1Avoid misuseRisk of improperTelevision system detailsColor television detailsCMOS sensorImaging equipment
A camera (11) includes: a CMOS image sensor (12) which converts input light so as to obtain image data; a GPS / LPS section (21) or a non-contact ID-chip reading section (22), which detects the location of the camera itself; an operation restricting condition setting section (20) which determines whether or not the detected location is inside of a predetermined area; and an operation controlling section (17). If it is determined that the location of the camera itself is outside of the predetermined area, the operation controlling section (17) restricts the image pickup operation in the CMOS sensor (12).
Owner:ORMON CORP
Method and device for electronically capturing a handwritten signature and safeguarding biometric data
ActiveUS20110185184A1Improper useSecure transmissionUnauthorized memory use protectionHardware monitoringElectronic documentBiometric data
A method and apparatus for encrypting an electronic document involves a computer having a first monitor and a signature capture apparatus configured to capture a handwritten signature on a second monitor. A hash sum of the electronic document generated in the computer is transmitted to the signature capture apparatus. The electronic document and the first hash sum thereof are displayed on the first monitor. The first hash sum is also displayed on the second monitor. After electronically capturing the handwritten signature, the signature data and the first hash sum are encrypted in the signature capture apparatus and then transmitted to the computer. The encrypted signature data, the first hash sum and the signed document are stored on a computer-readable medium.
Owner:STEPOVER
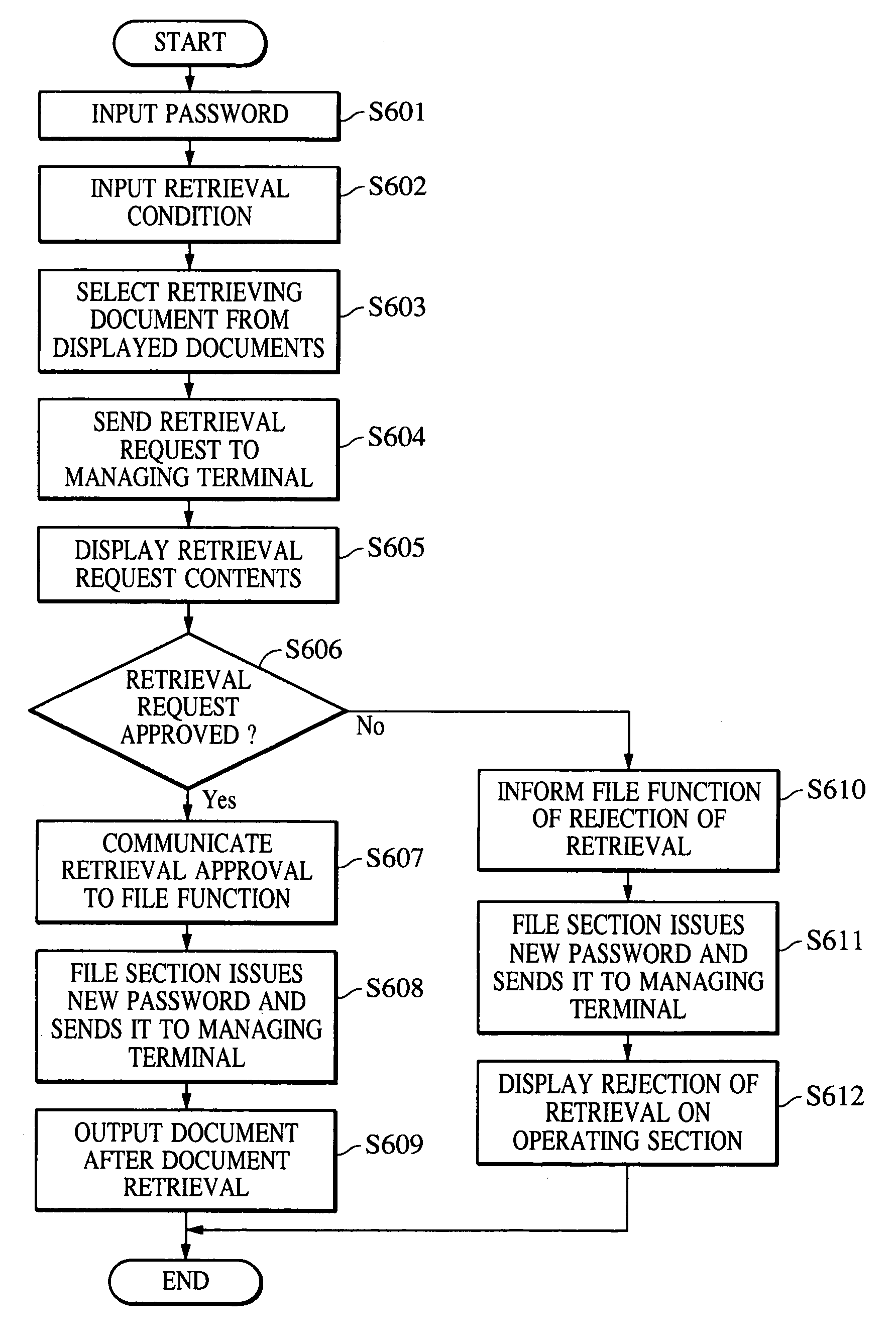
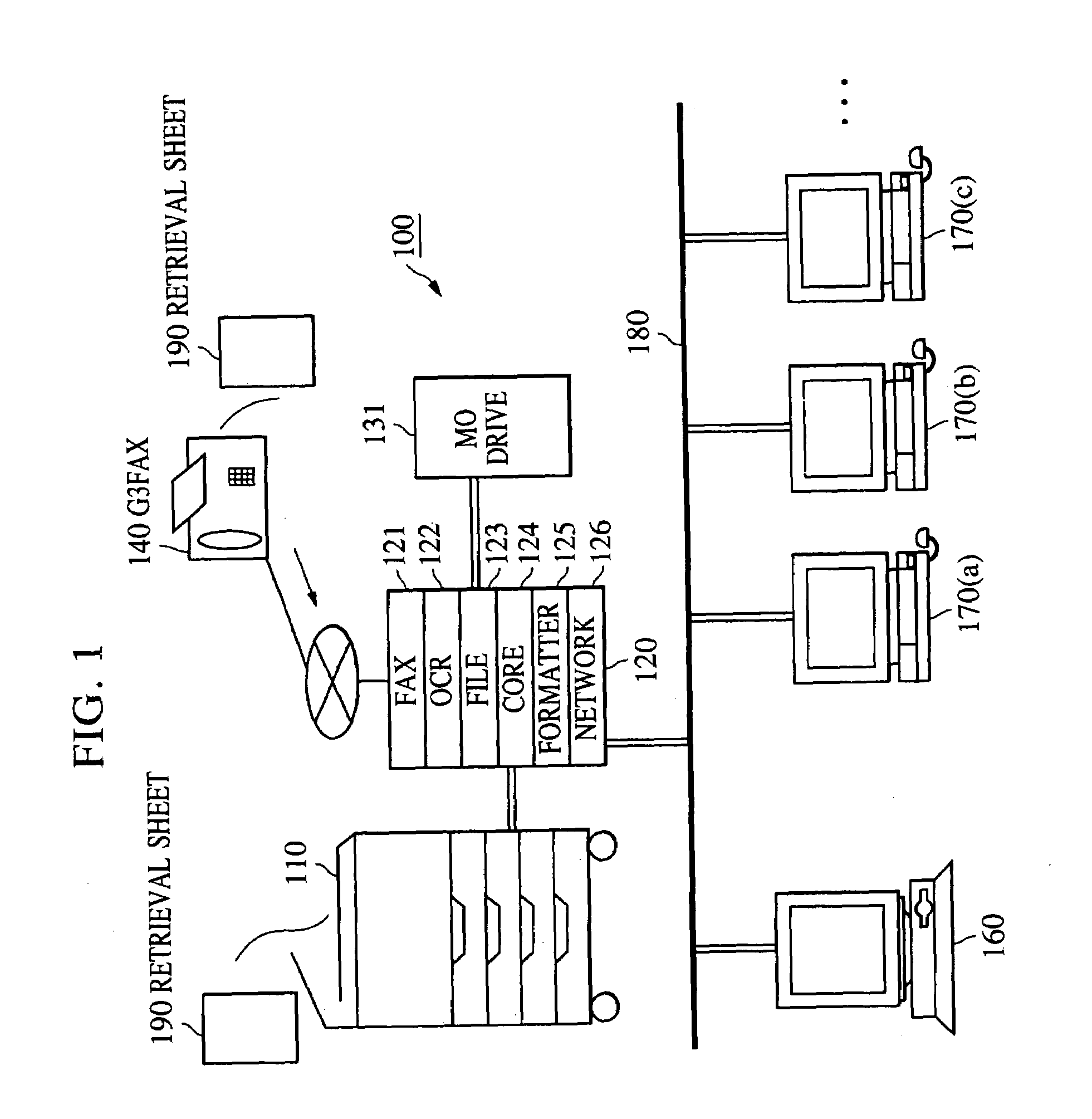
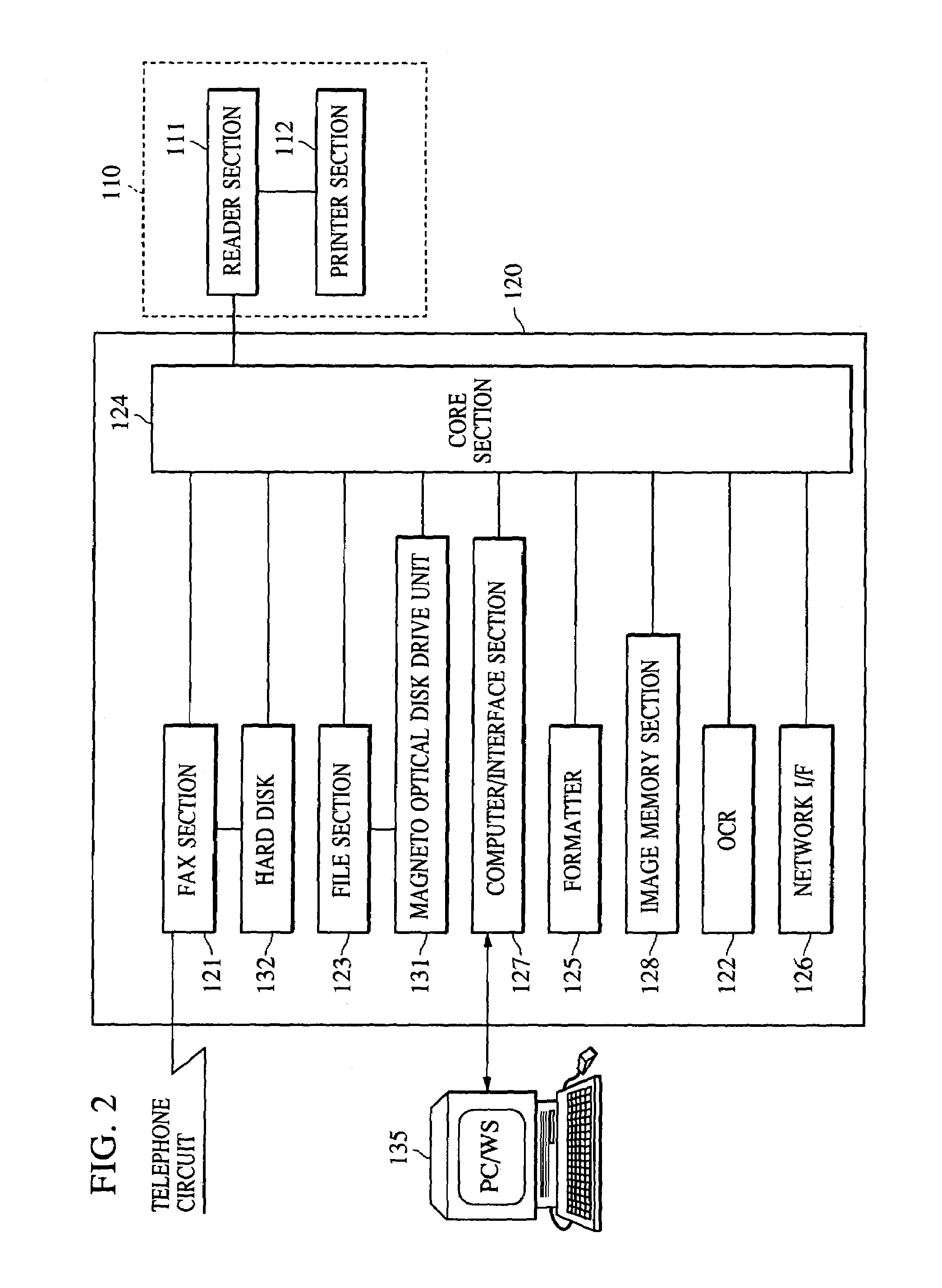
Apparatus for retrieving document data
InactiveUS6950202B1Reliably preventing improper or illegal outward flowDrawback can be obviatedDigital data processing detailsDigital computer detailsPasswordDigital copy
An information input / output system capable of reliably preventing improper leakage of information and of keeping confidential information secret. The information input / output system provides a digital copying machine compositely having a plurality of functions, such as a filing function, an OCR function, a facsimile function and a network function. The digital copying machine performs an information retrieval on the basis of a password from a user in response to an information retrieval requirement (information retrieval request) made through its operating section, an information retrieval requirement made by a information retrieval sheet sent from the external through the use of a facsimile or an information retrieval requirement made through a personal computer on a network. After the completion of the information retrieval, the digital copying machine issues a new password (for example, at random) and makes the previously used password invalid.
Owner:CANON KK
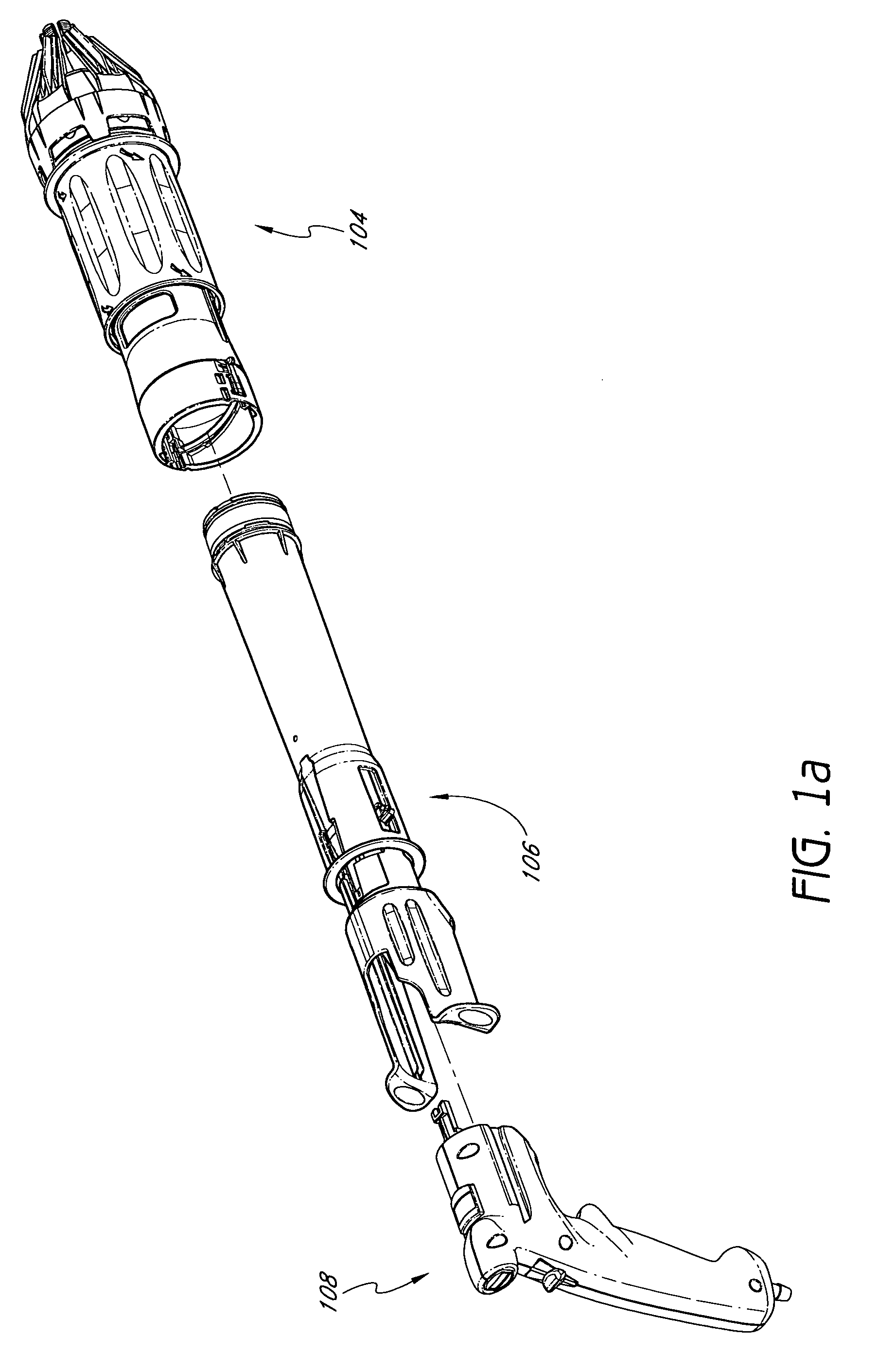
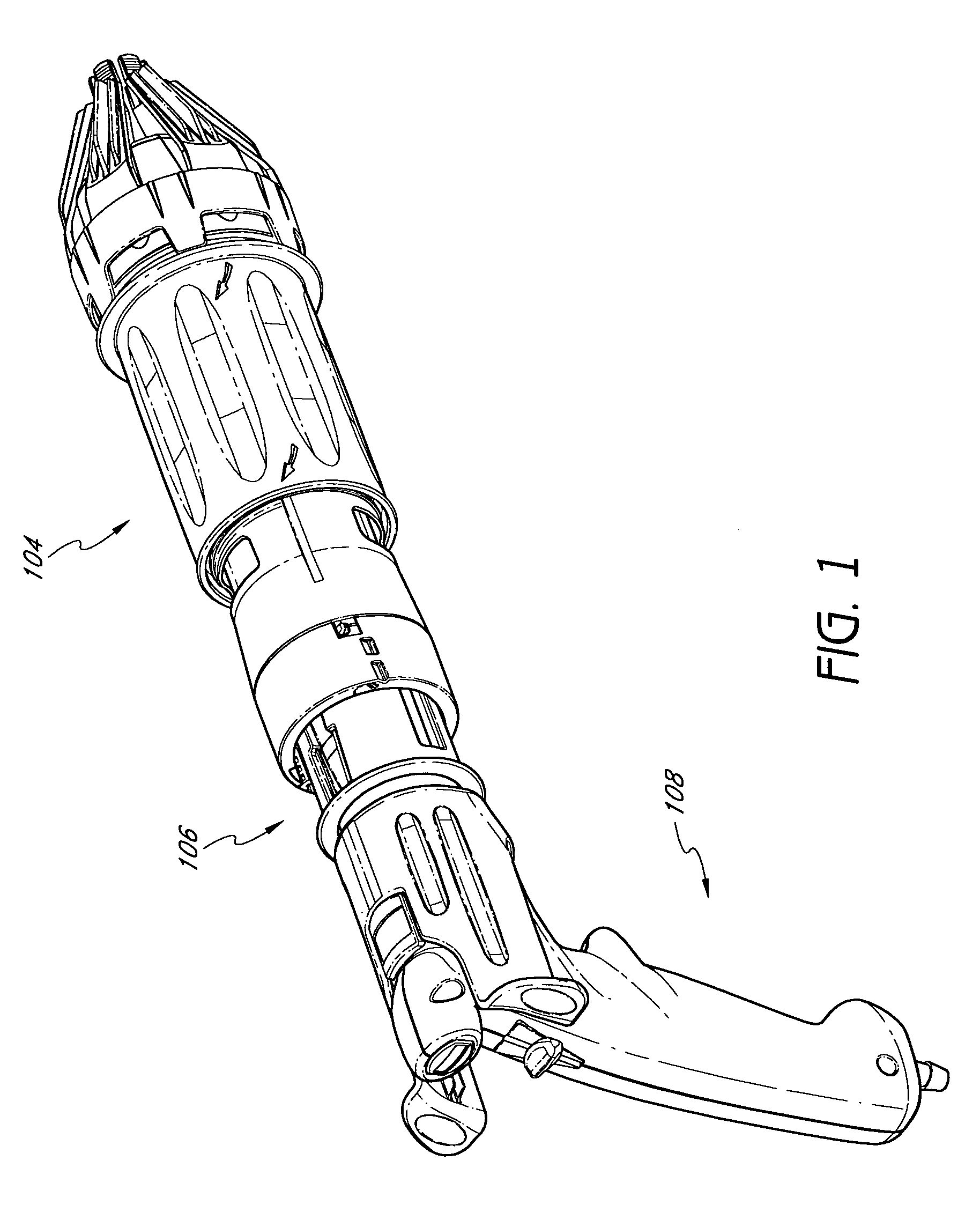
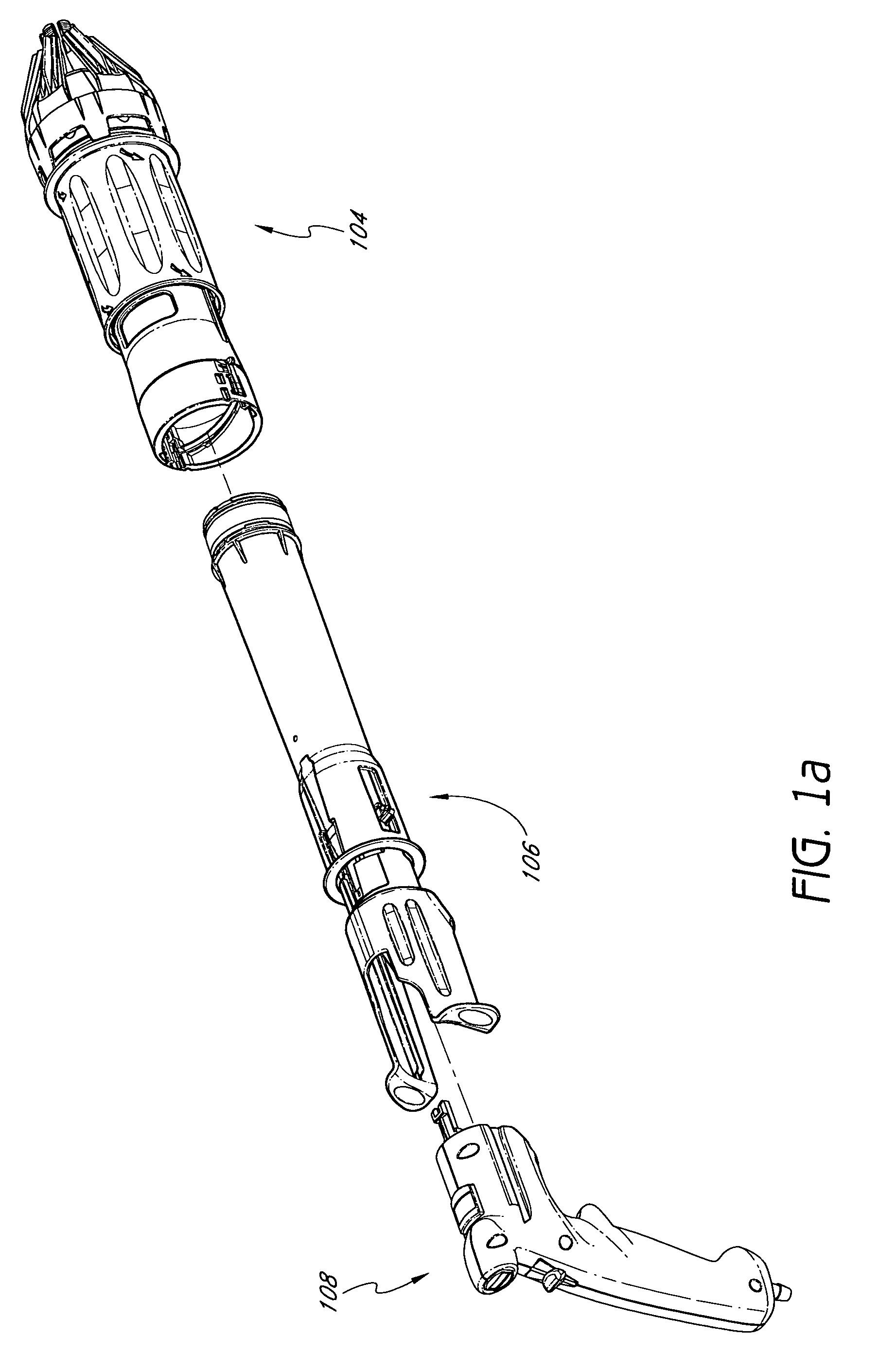
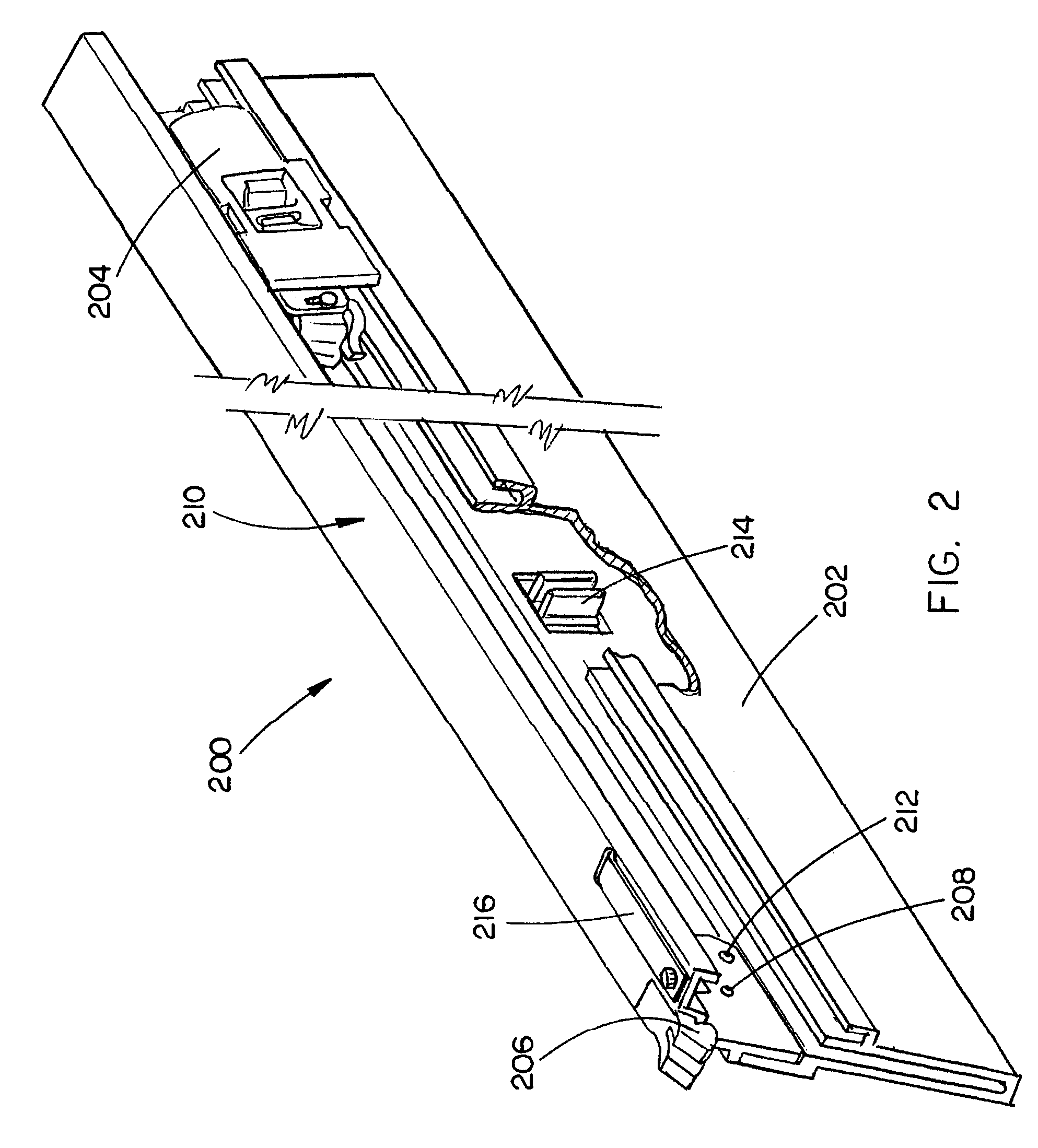
Articulating pusher assembly
InactiveUS20060108390A1Decrease riskReduce riskStapling toolsNailing toolsBiomedical engineeringConstant pressure
An articulating pusher assembly, disposed within a nail loading assembly, includes an articulating pusher coupled to an adapter, the articulating pusher for engaging a nail. The adapter may be further coupled with a casing which engages a spool assembly to provide a constant pressure on the articulating pusher assembly to advance the nail down the length of the nail loading assembly. The articulating pusher is enabled to accommodate the use of a variety of nail types and collation angles of nail strips within the nail loading assembly.
Owner:BLACK & DECKER INC
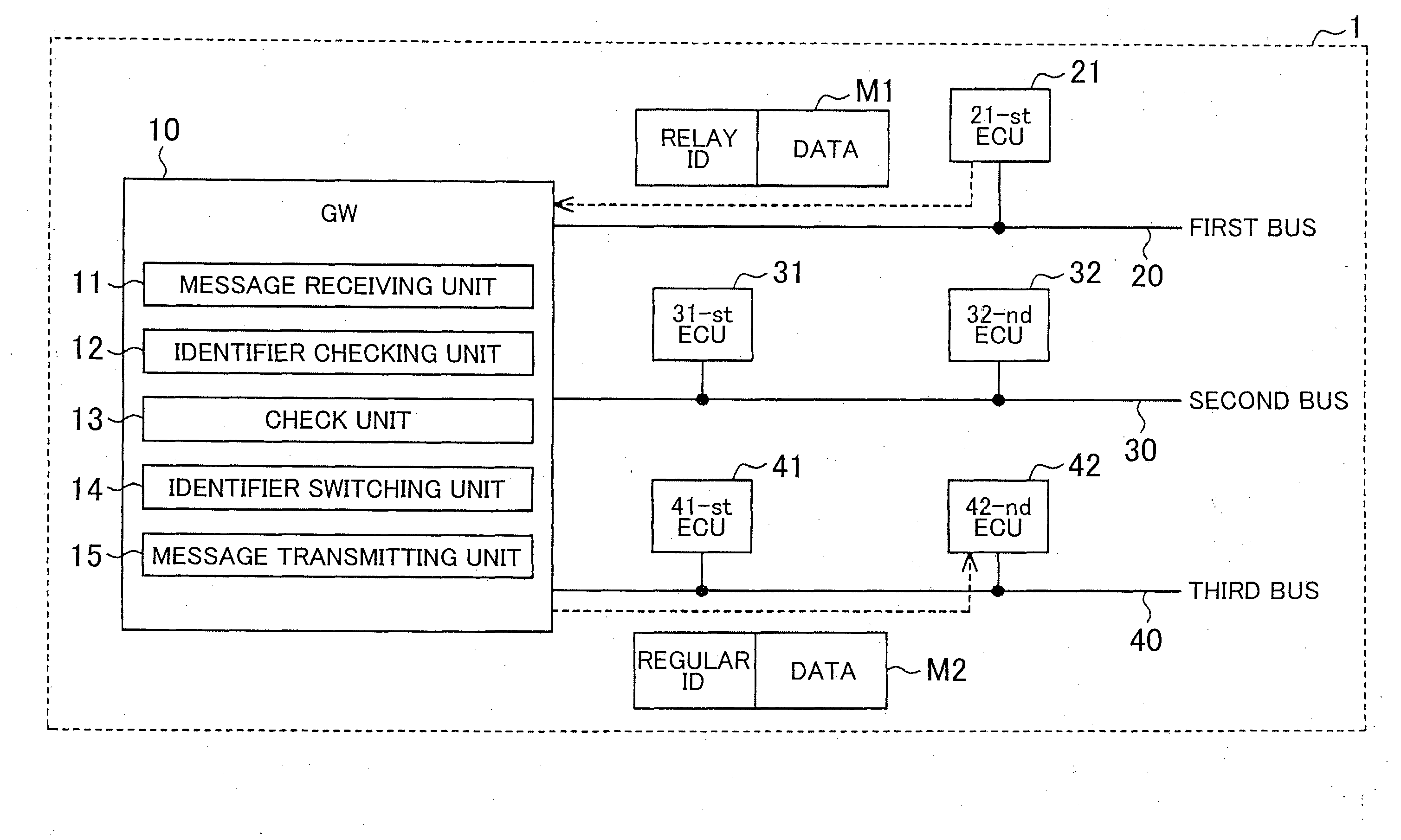
Communication system and communication method
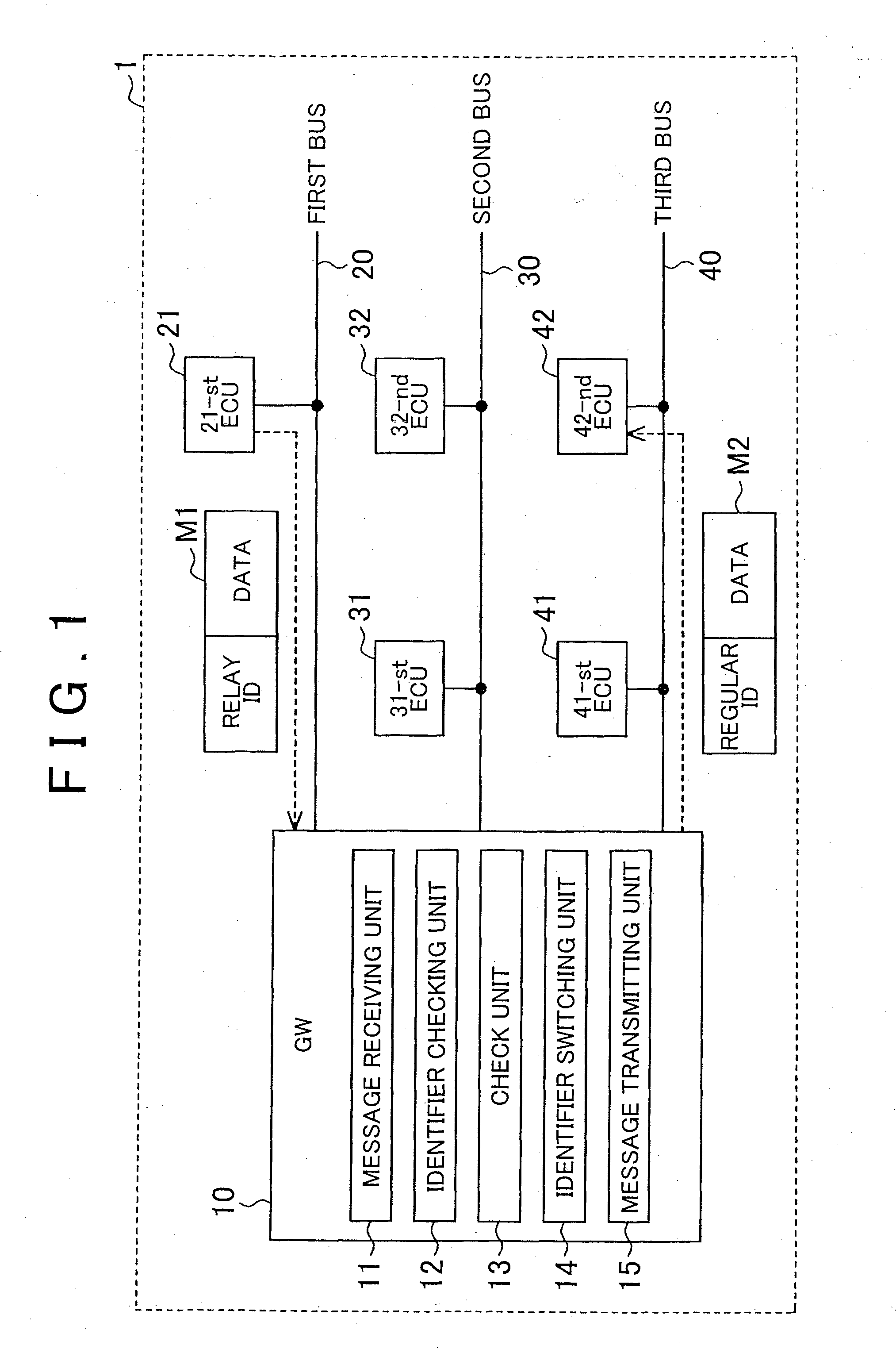
InactiveUS20160234037A1Improve communication securityImprove versatilityRepeater/relay circuitsLocation information based serviceCommunications systemData storing
A communication system includes: a communication device that is connected to a communication line and that performs communication via the connected communication line using a communication message including a data area in which data is stored and an identifier area in which a communication identifier determined to correspond to the data is stored; and a gateway that is connected to a plurality of the communication lines and that relays a communication message among the plurality of communication lines. The communication device transmits a communication message, in which user data and a communication identifier corresponding to the user data are stored in the data area and a relay identifier for allowing the gateway to specify a communication line through which the user data stored in the data area is transmitted in the identifier area, to the gateway.
Owner:TOYOTA JIDOSHA KK
Control for the display device for a communication terminal
InactiveUS20090017871A1Convenient operationOperation of appliances with display devices more economic and more convenientPower managementEnergy efficient ICTEmbedded systemAuthorization
There is described a method for operating a device comprising a display device, a communication device and a communication system. According to said method, the display device is activated once a user enters a near field of the device, and the display device is deactivated once a user leaves the near field of the device. The display device comprises OLEDs or other components that have a short service life and / or a high power requirement. Activation and / or deactivation are controlled by a transponder, e.g. an RFID-TAG to be carried by the user, which responder is detected in the near field of the device. Temporary deactivation of the display device can prolong the service life of the display device and / or save power and the use of contactless RFID-TAGs increases ease of operation. The technology can also be used for other purposes, e.g. user authorization.
Owner:SIEMENS AG
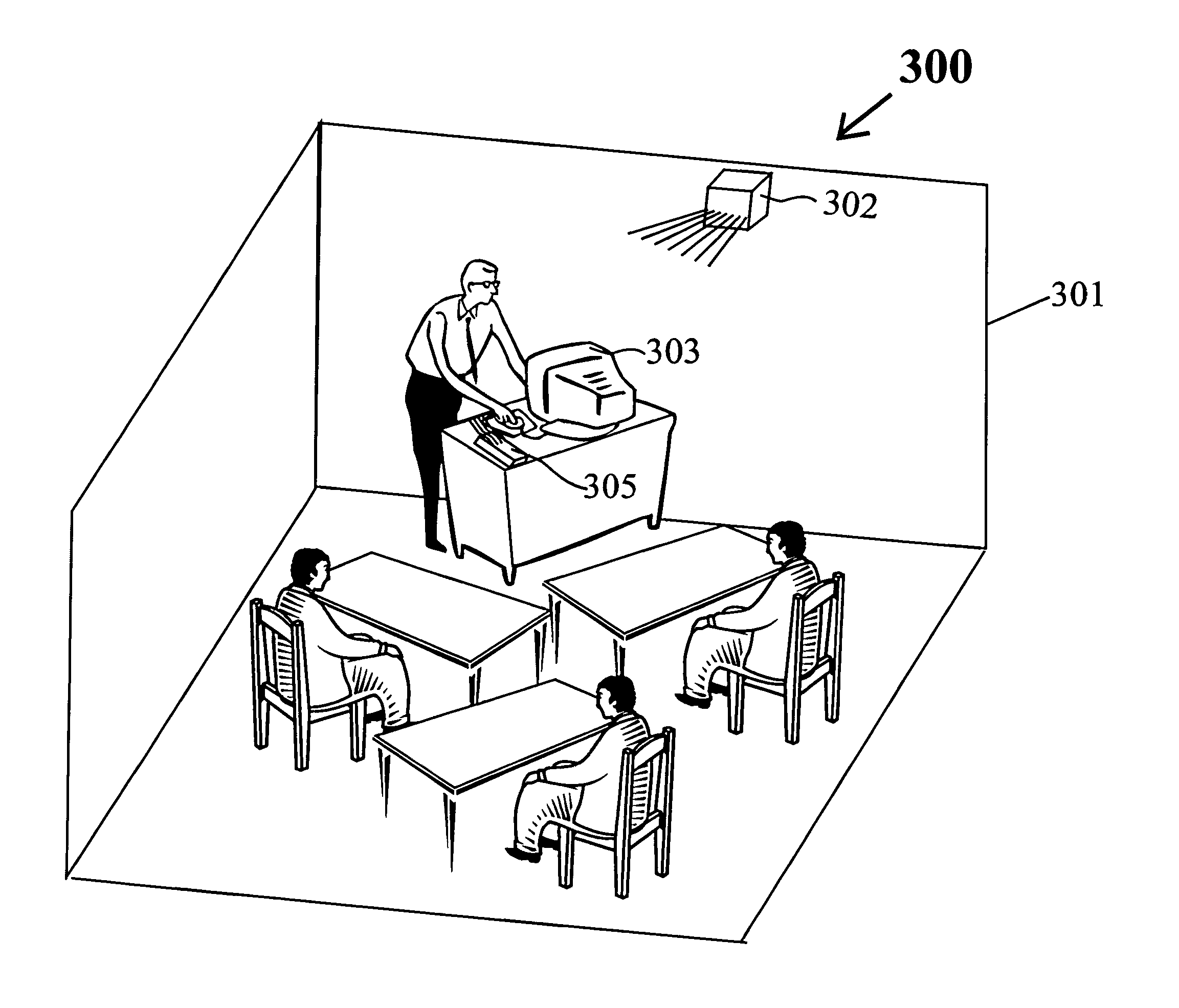
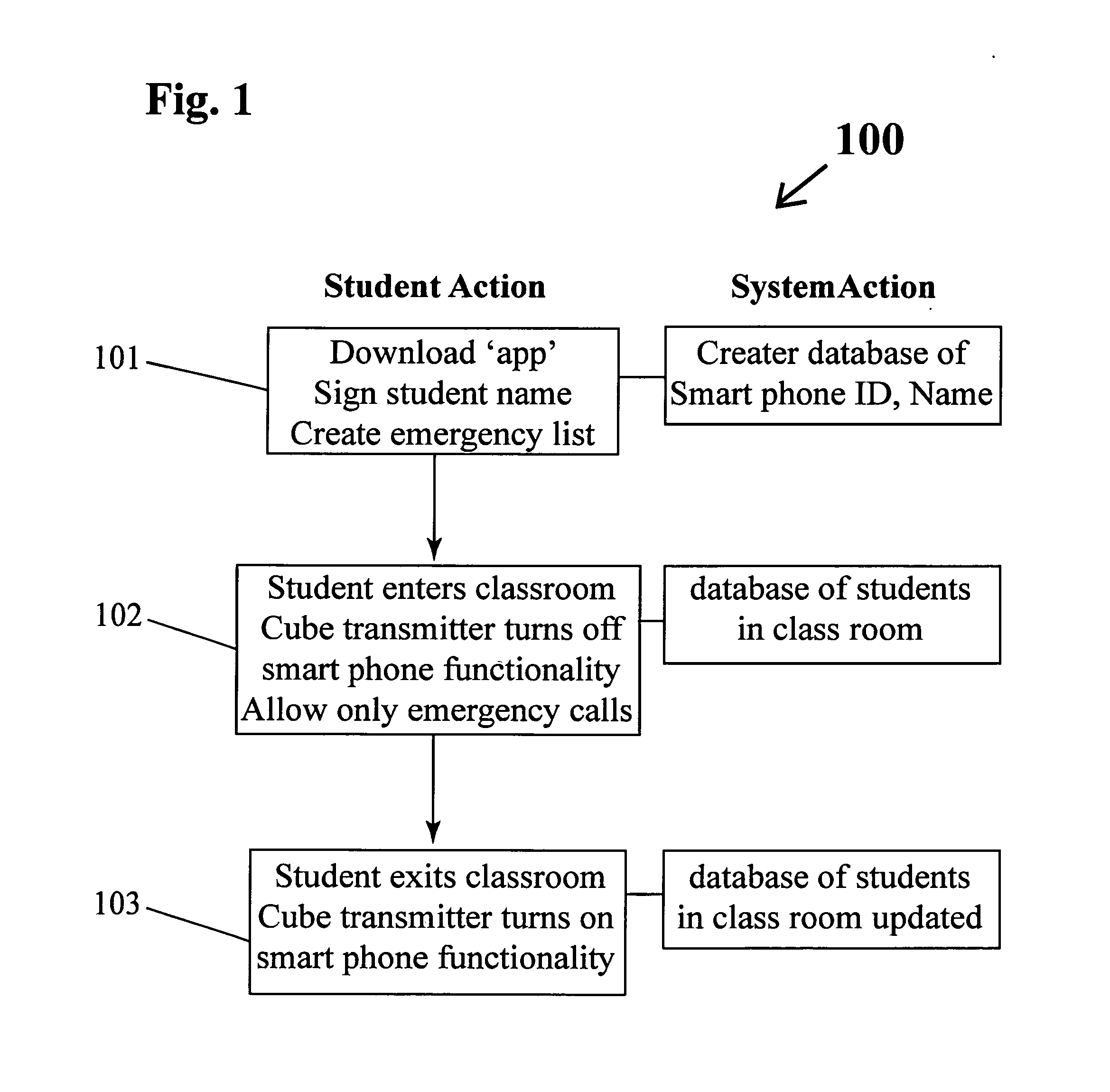
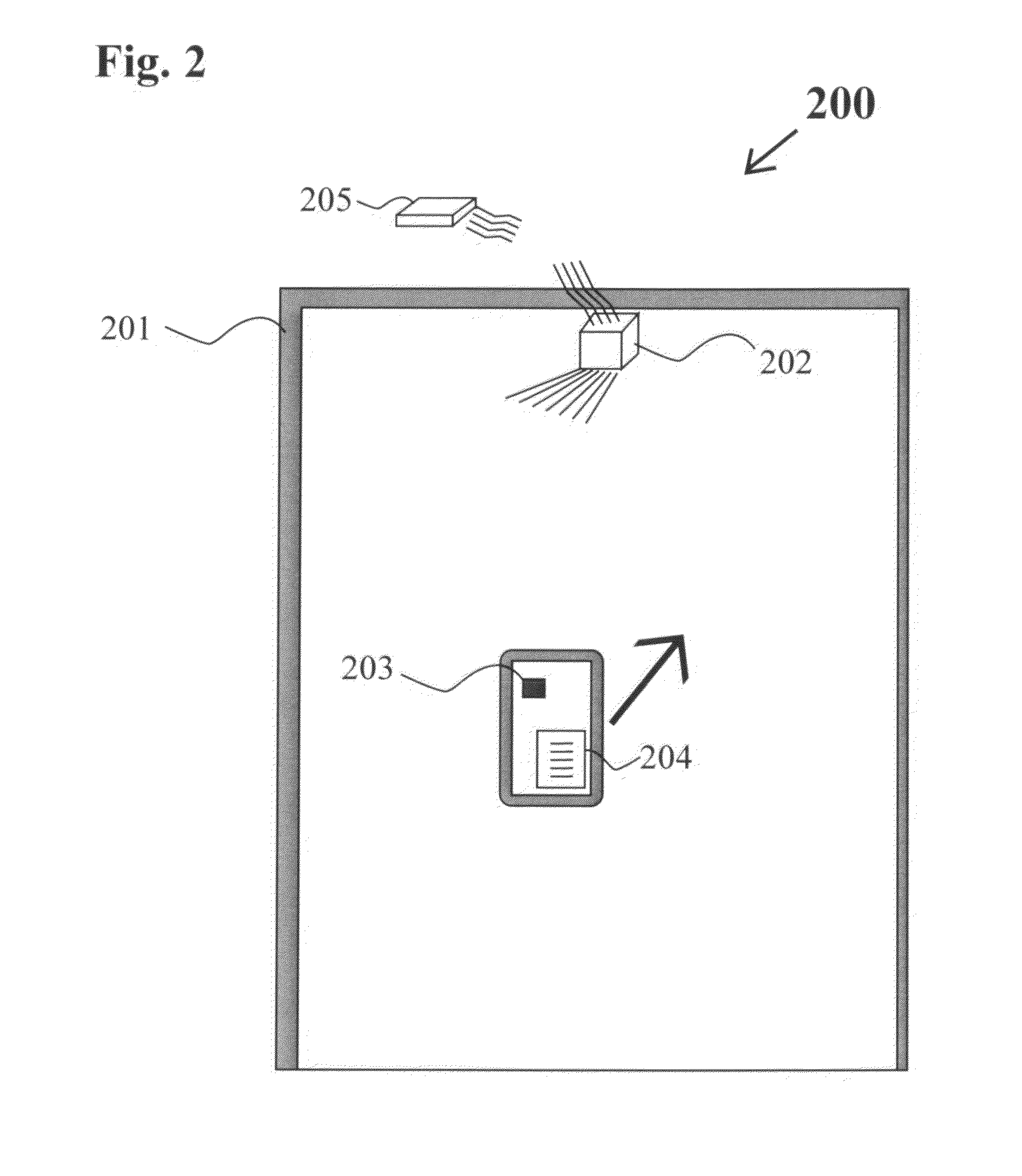
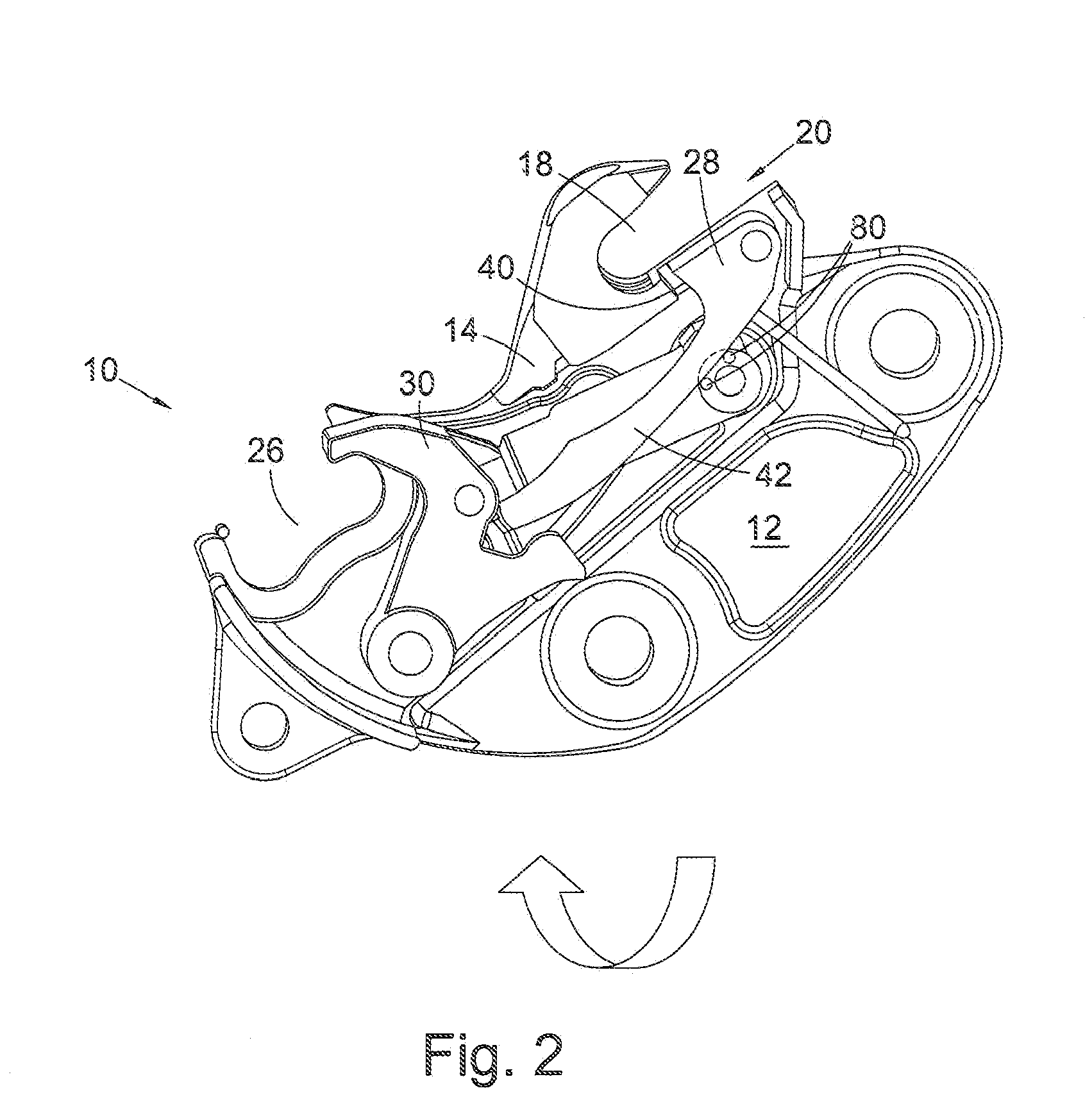
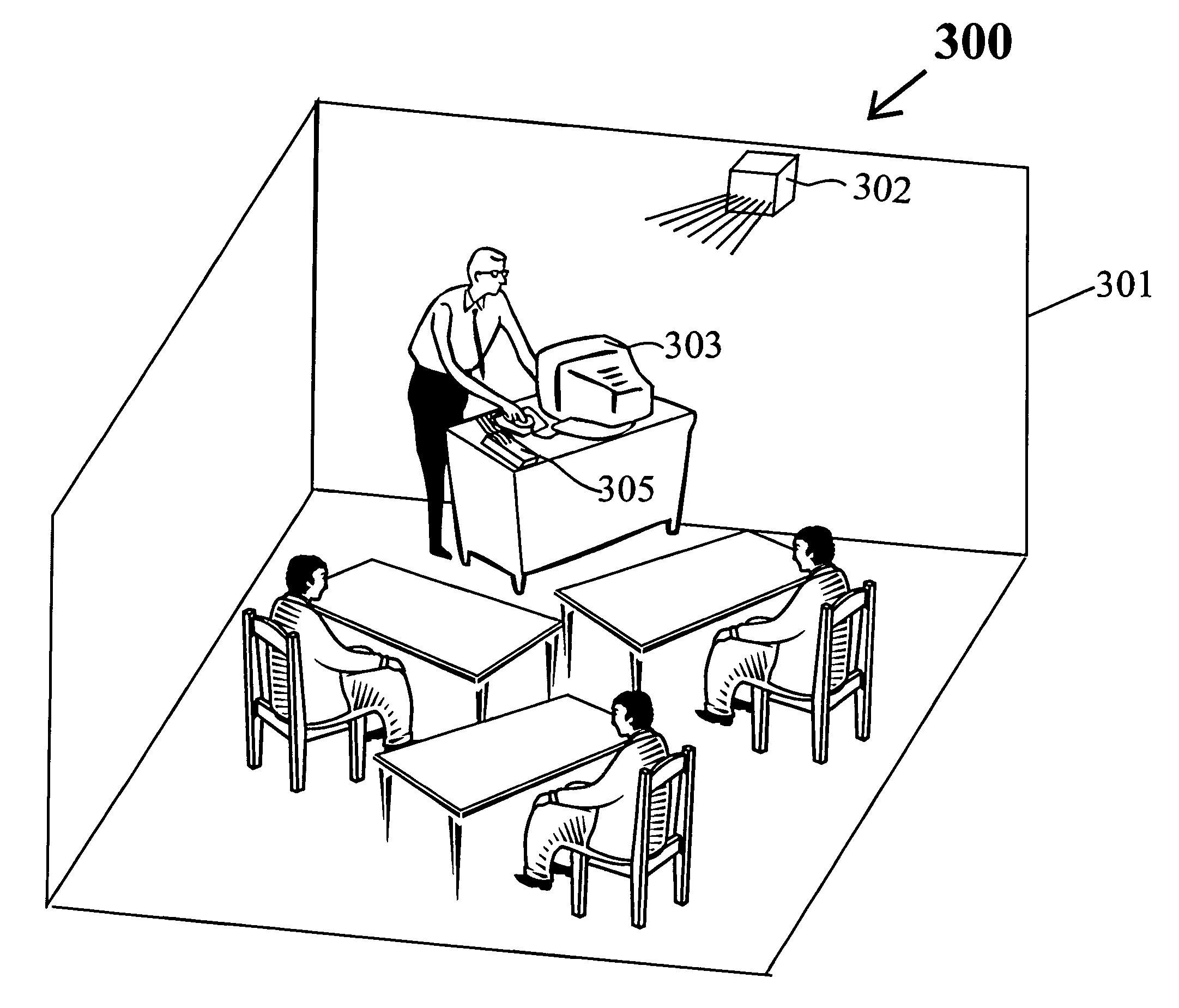
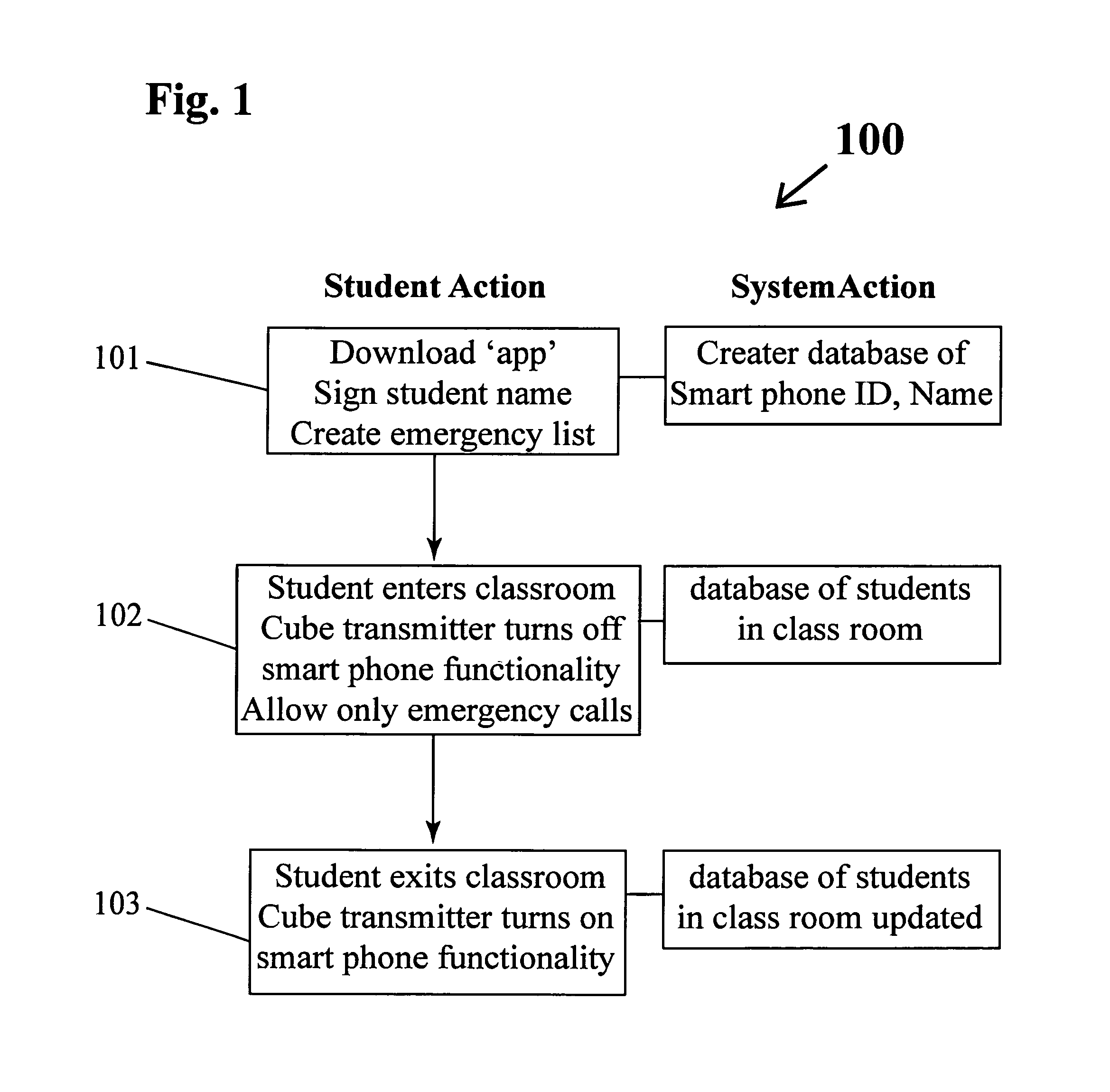
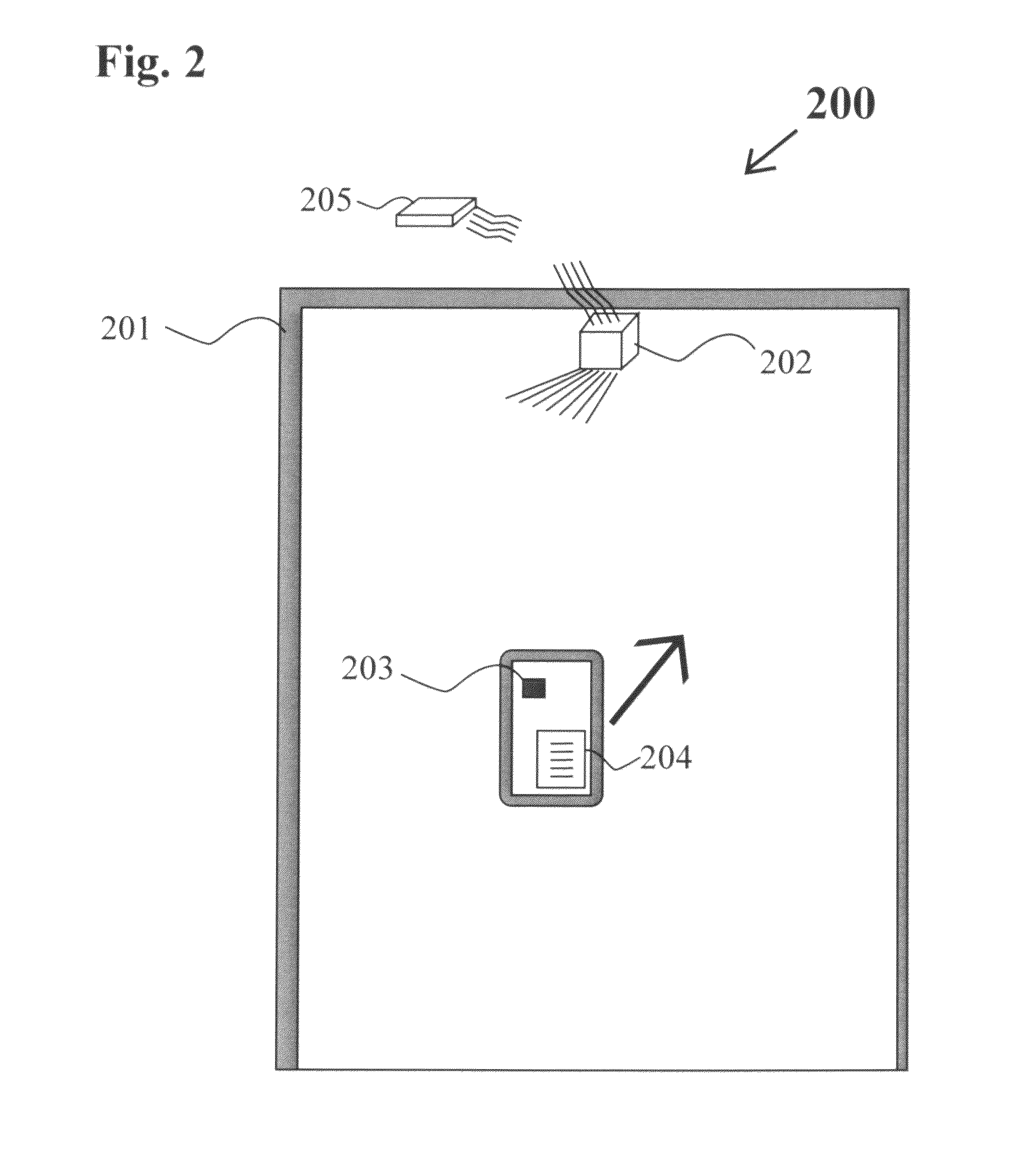
Learning guard system
InactiveUS20150319293A1Improve abilitiesBlock usage and distractionAssess restrictionSubstation equipmentInternet accessComputer science
A Learning Guard System protects the attention of students in a classroom by requiring the student to download an ‘app’ from the Learning Guard website. During installation the ‘app’ requires the student to provide their name and a list of emergency contacts which are stored in the memory of the smart phone and by the Learning Guard cloud database. When a student enters a classroom doorway cube transmitter mounted thereon interacts with the ‘app in the smart phone to thereby acquire the smart phone ID and turn off the smart phone functionality, including voice, text communication, Internet access, playing music and videos. This prevent communication of the student with others, excepting emergency contacts both public and private. The cube transmitter communicates the smart phone ID to a base station linked to the Learning Guard cloud database, which creates a database of students in the classroom. When the student exits the classroom through the doorway, all of the previously extant smart phone functionalities are turned on.
Owner:CERDA ANTHONY
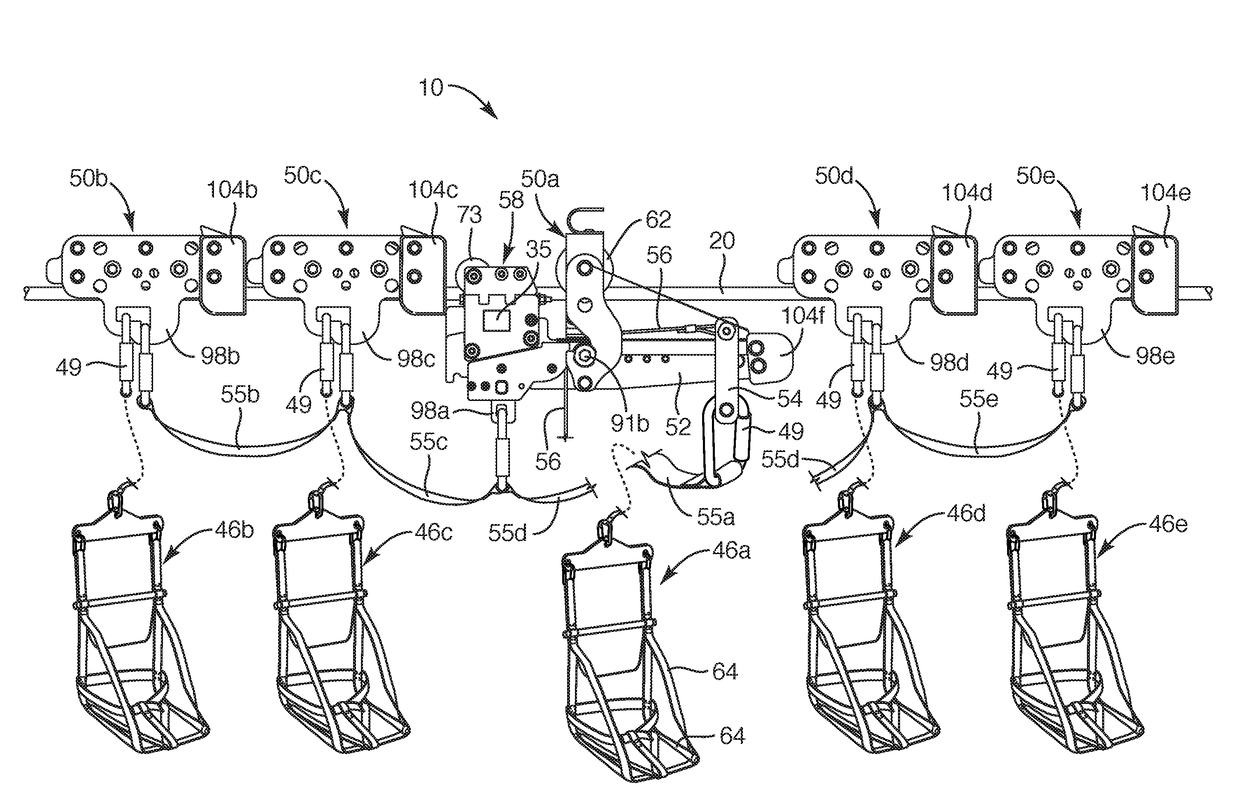
Unattended, self-guided, zip-line, tour system and method
ActiveUS20160046305A1Simplify operating proceduresSimple processBrakes for specific applicationsDigital data processing detailsEngineeringSelf guided
A canopy tour system may include multiple track lines extending between associated upper and lower stations for loading, launching, receiving, and unclipping, respectively, riders of trolleys on the zip lines. A system of mechanical and electronic interlocks provides safety for users in remote locations, enabling individual riders to operate trolleys, including attaching and dis-attaching the trolleys from various track lines, unattended by other workers or employees of the canopy tour operation. Mechanical interlocks assure that a trolley cannot be properly engaged with a launch block on a track line until all such interlocks are properly closed. A master computer may communicate through a network, with all stations to verify and identify times and locations of users.
Owner:ZIP HLDG
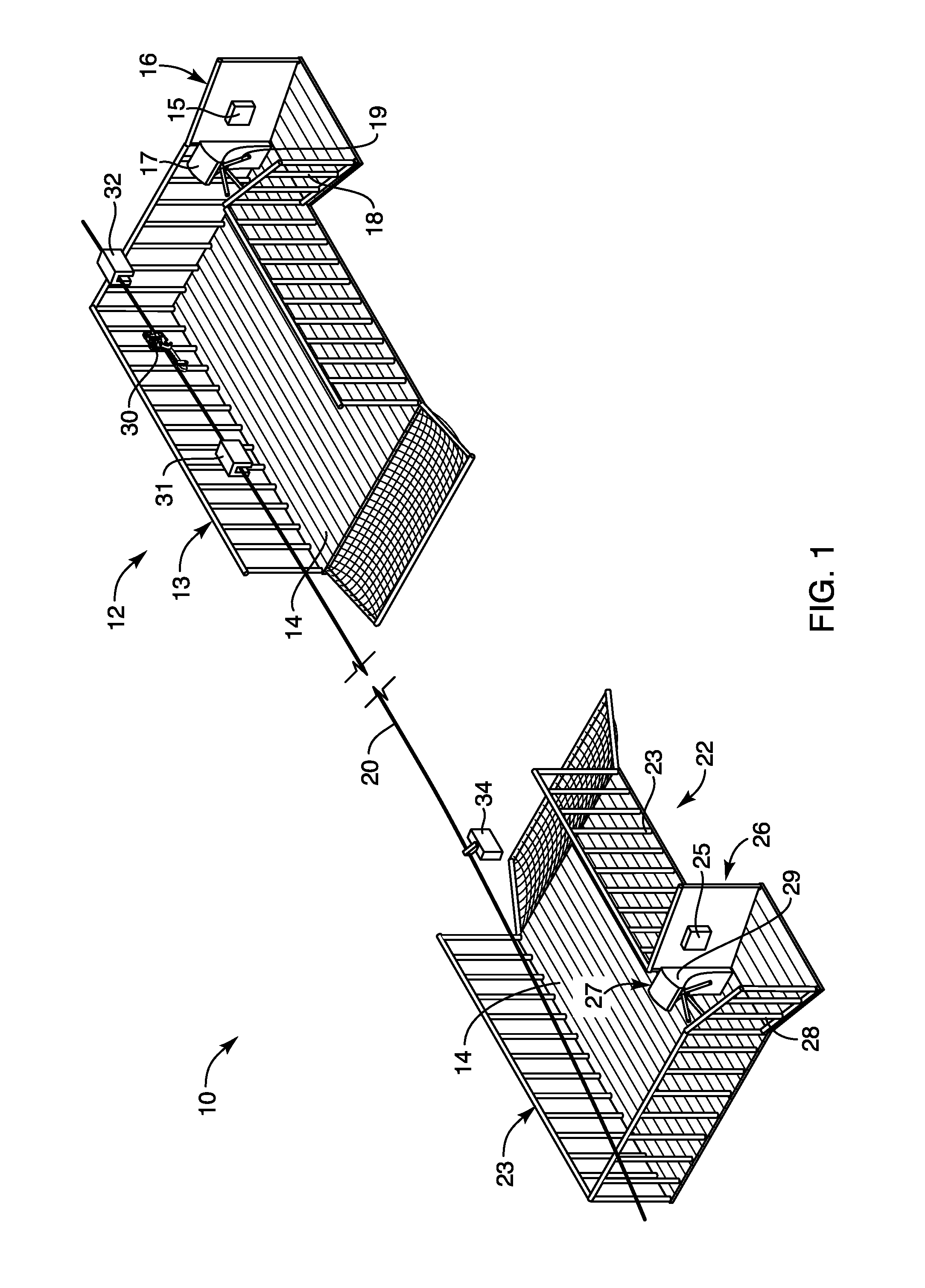
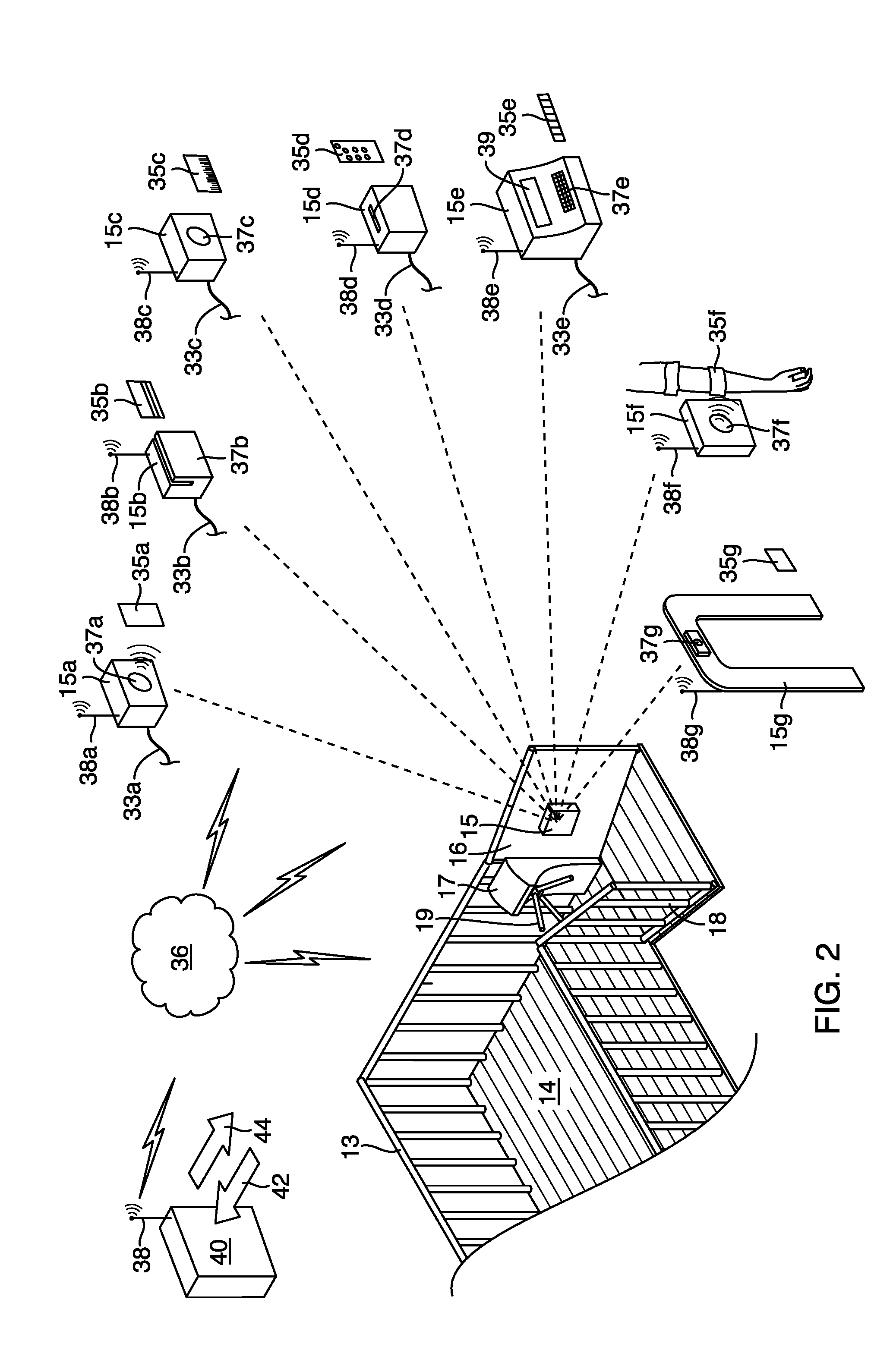
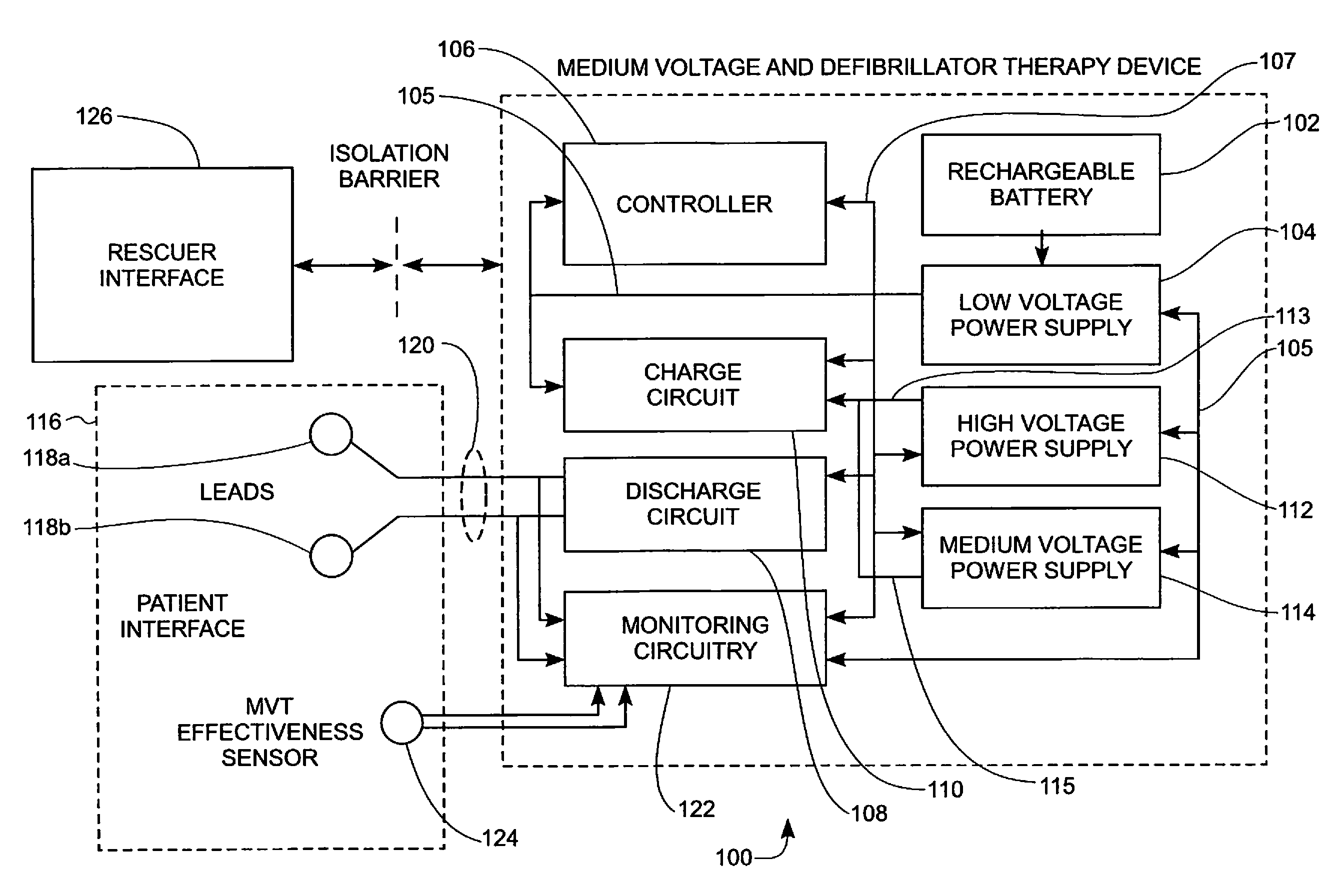
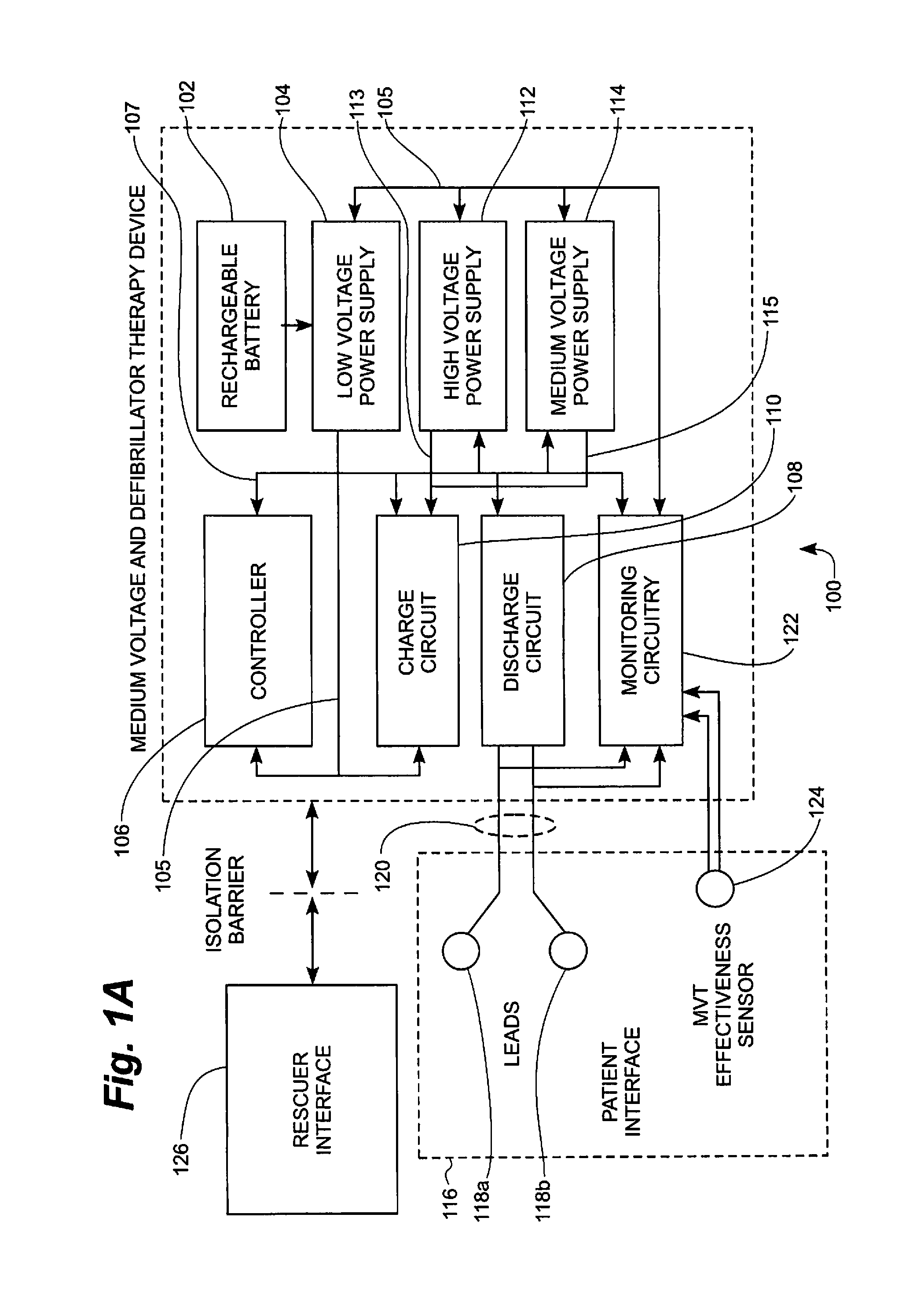
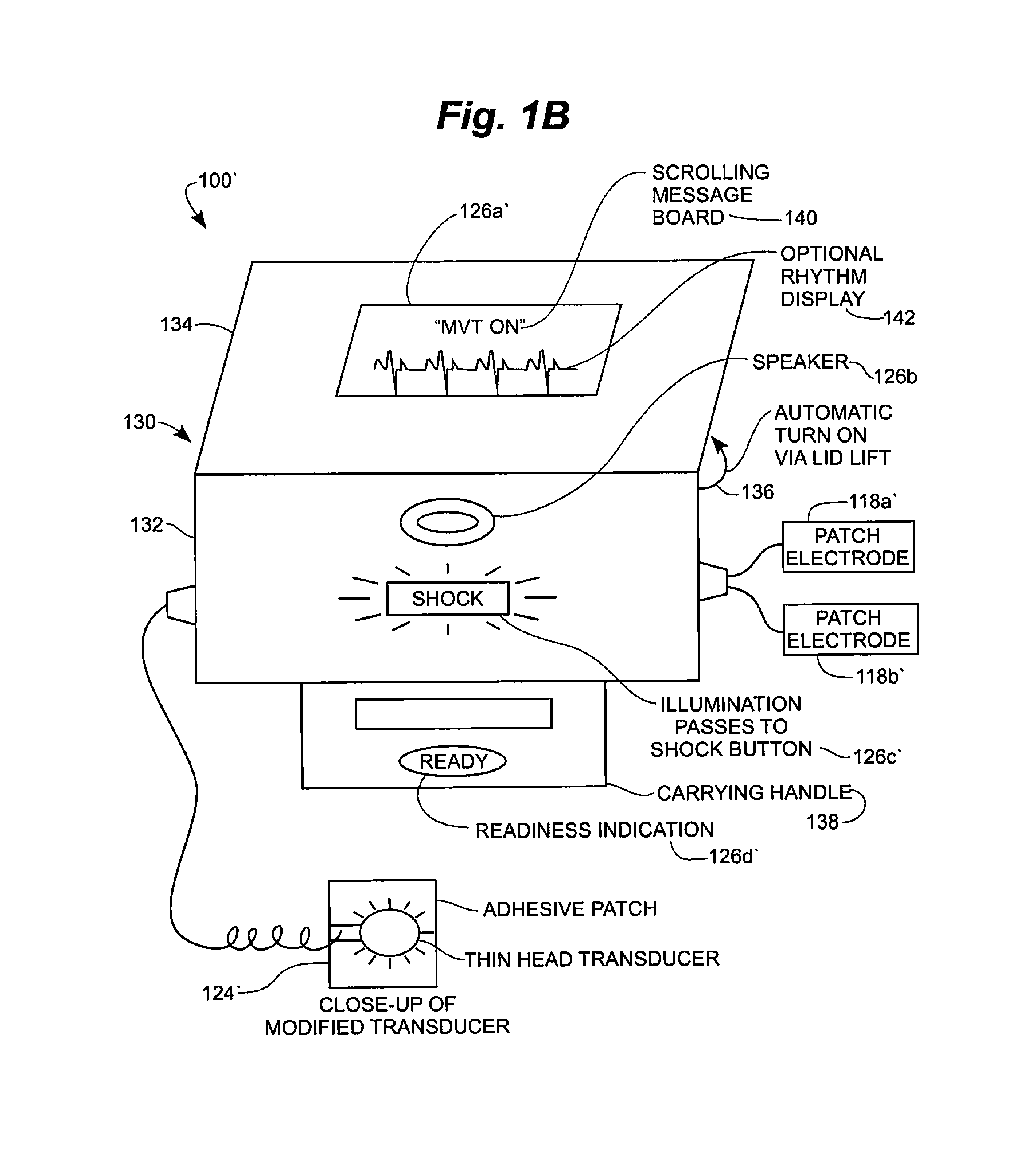
Medium voltage therapy applications in treating cardiac arrest
ActiveUS8401637B2Work comfortablyImproper useHeart defibrillatorsElectricityCardiorespiratory arrest
A method and system for treating an individual experiencing cardiac arrest using an automatic external defibrillator (AED) includes placing a first and a second electrode of the AED in electrical communication with an exterior surface of the individual. A need to apply a high voltage defibrillation signal to the individual is automatically determined. The method also includes automatically causing the AED to apply a medium voltage therapy (MVT) signal through the first and the second electrodes to the individual. The MVT signal is applied to induce a hemodynamic effect in the individual. Alternatively, or additionally, the MVT signal is applied to induce a respiratory effect in the individual. Optionally, the MVT signal is applied before determining the need to apply the defibrillation signal.
Owner:GALVANI
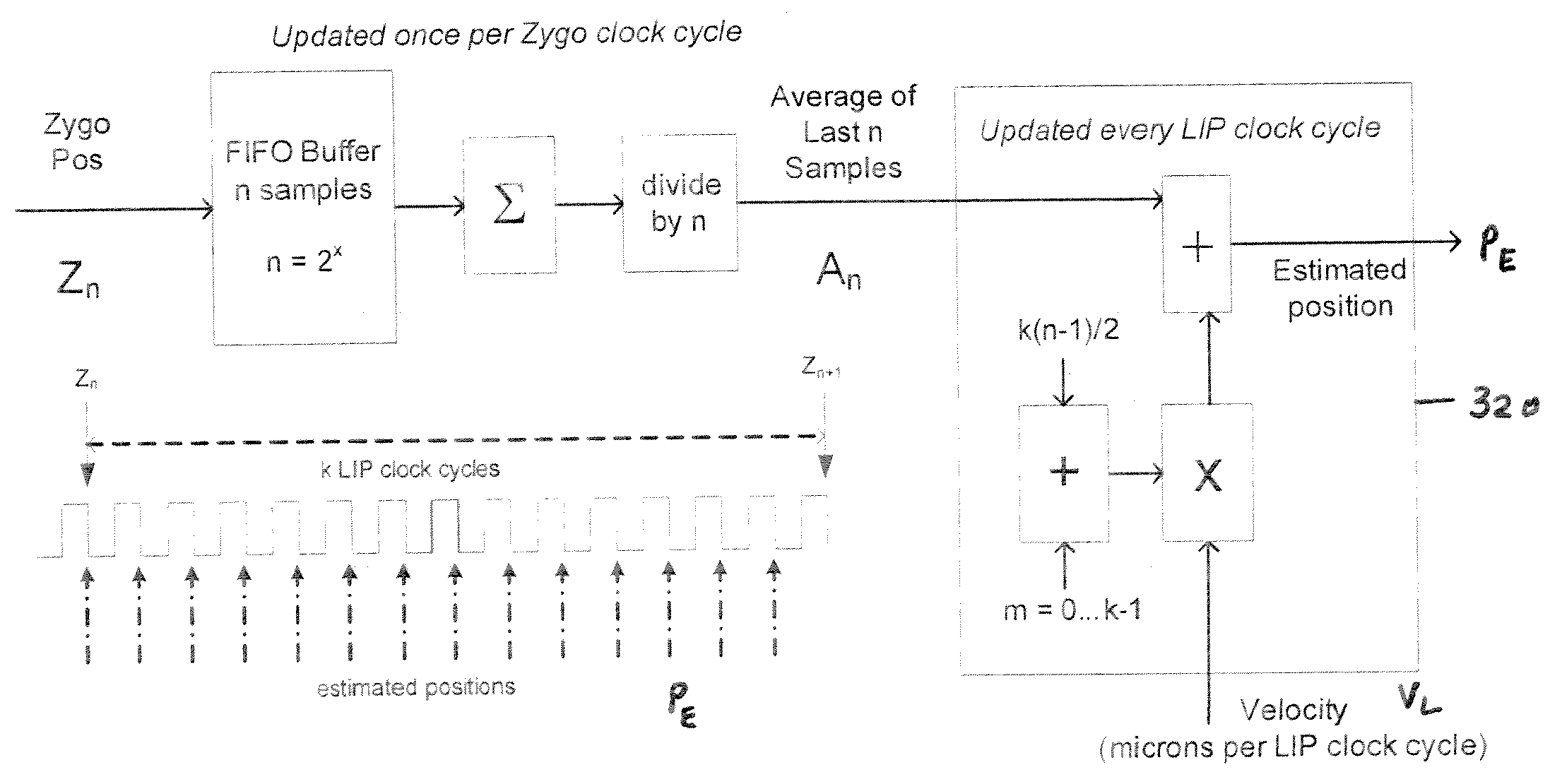
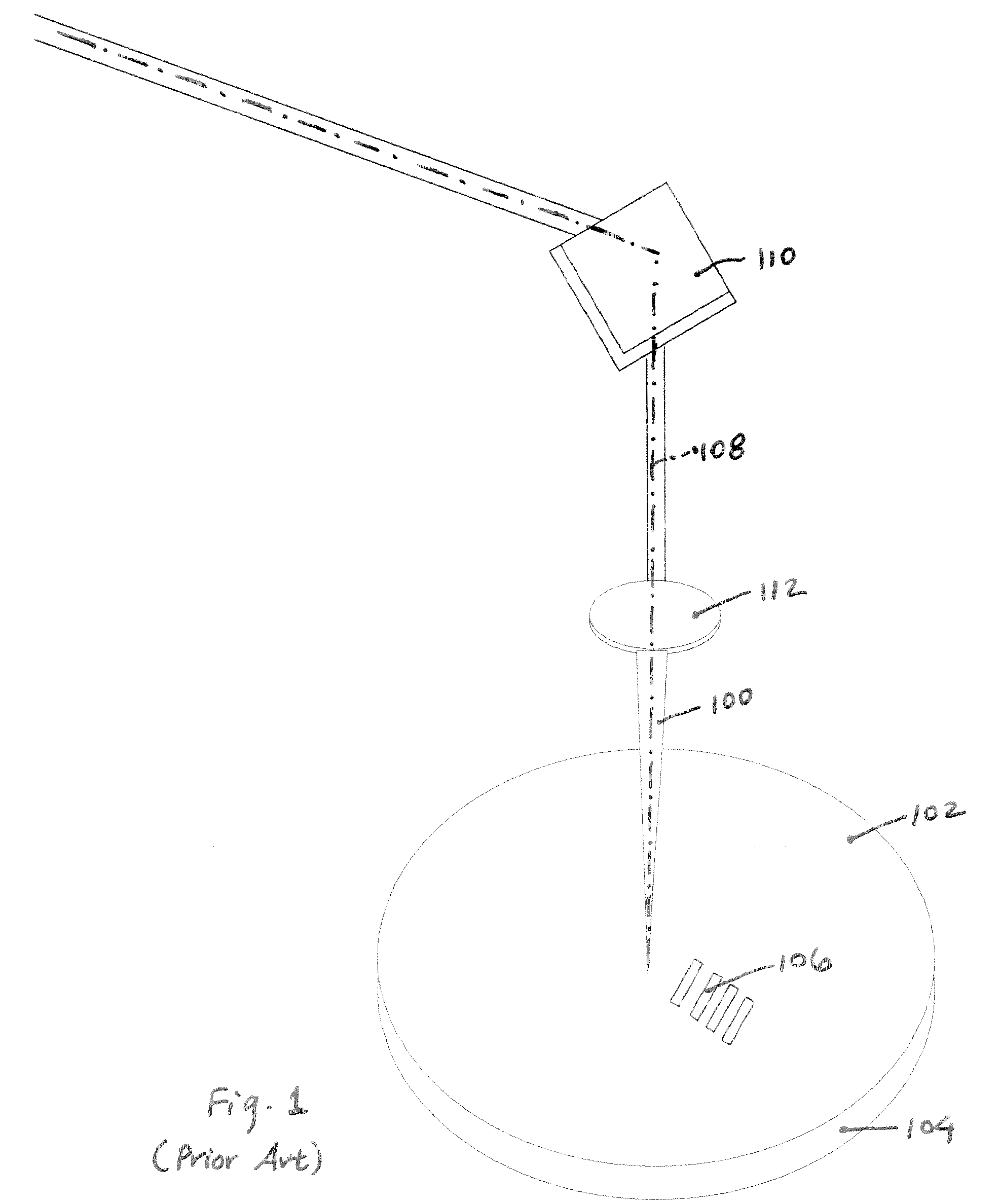
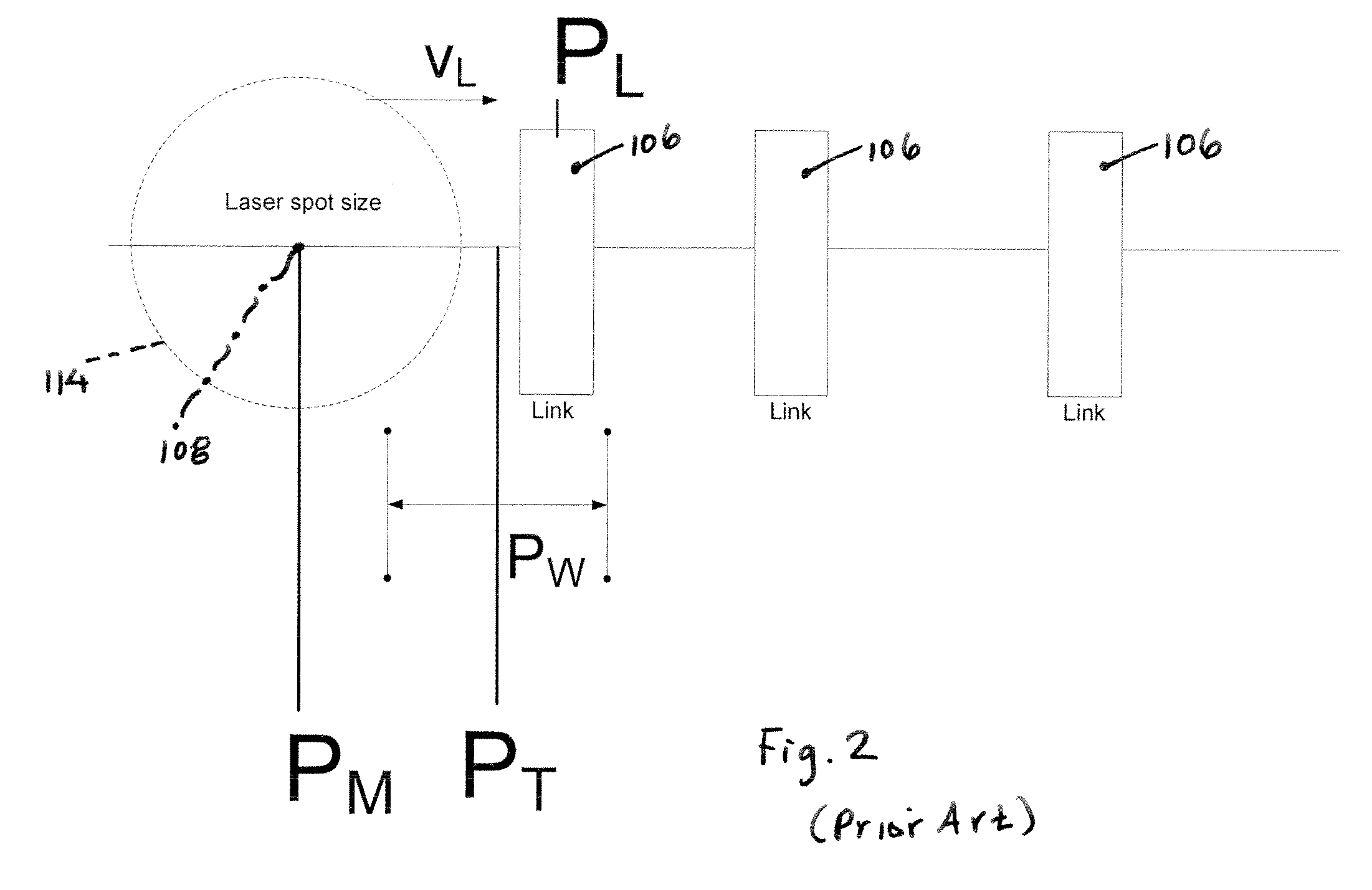
Use of predictive pulse triggering to improve accuracy in link processing
InactiveUS20080223837A1Improve system accuracyImproper useLaser detailsWelding/soldering/cutting articlesRelative motionOptoelectronics
A predictive pulse triggering (PPT) method enables precise triggering of a laser beam in a link-processing system. The PPT method entails triggering the laser beam based on estimated relative motion parameters of the target and laser beam axis. The PPT method allows for a six-fold improvement in laser positioning accuracy over the conventional, entirely measurement-based method.
Owner:ELECTRO SCI IND INC
Protection module for data transmission connector
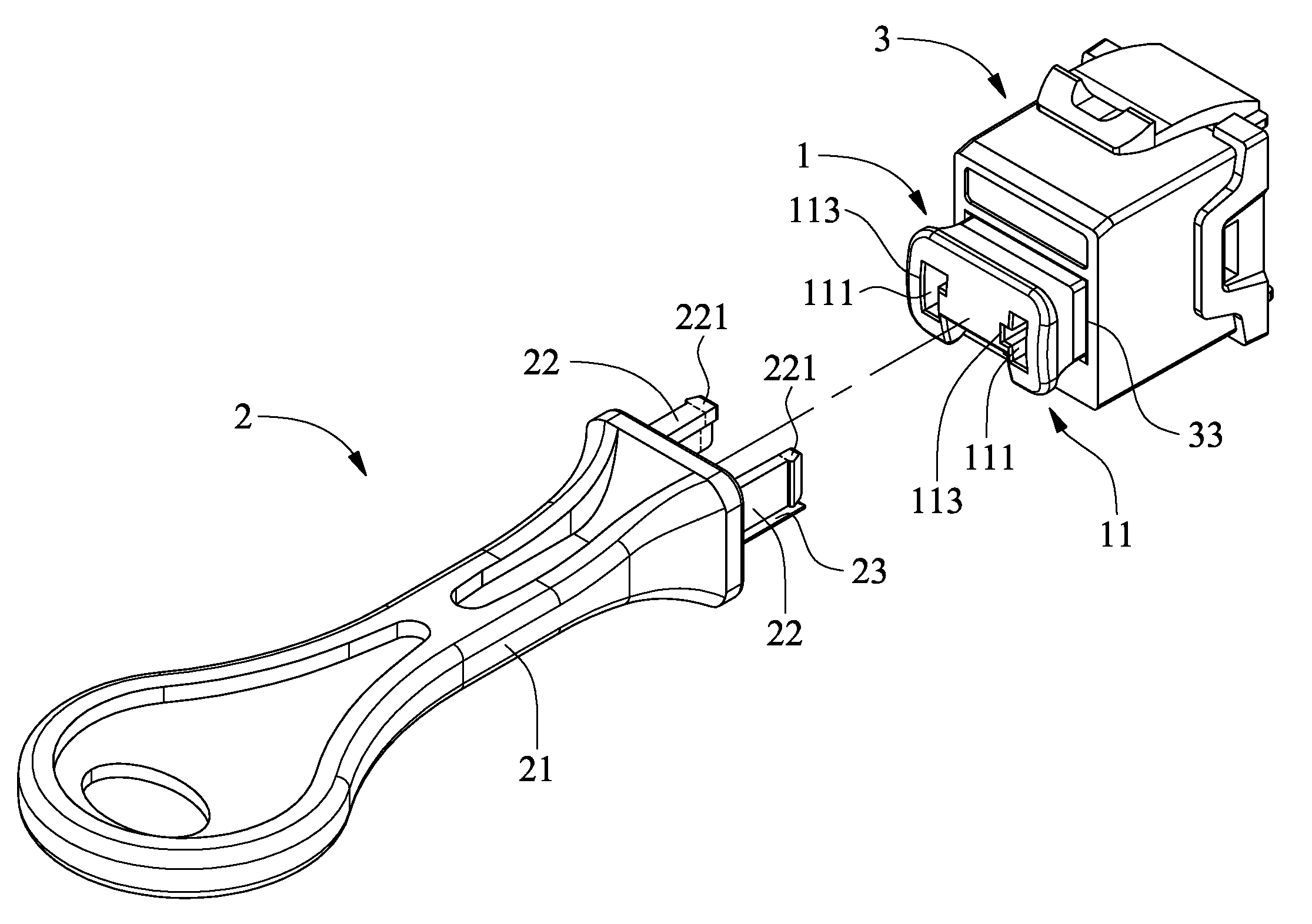
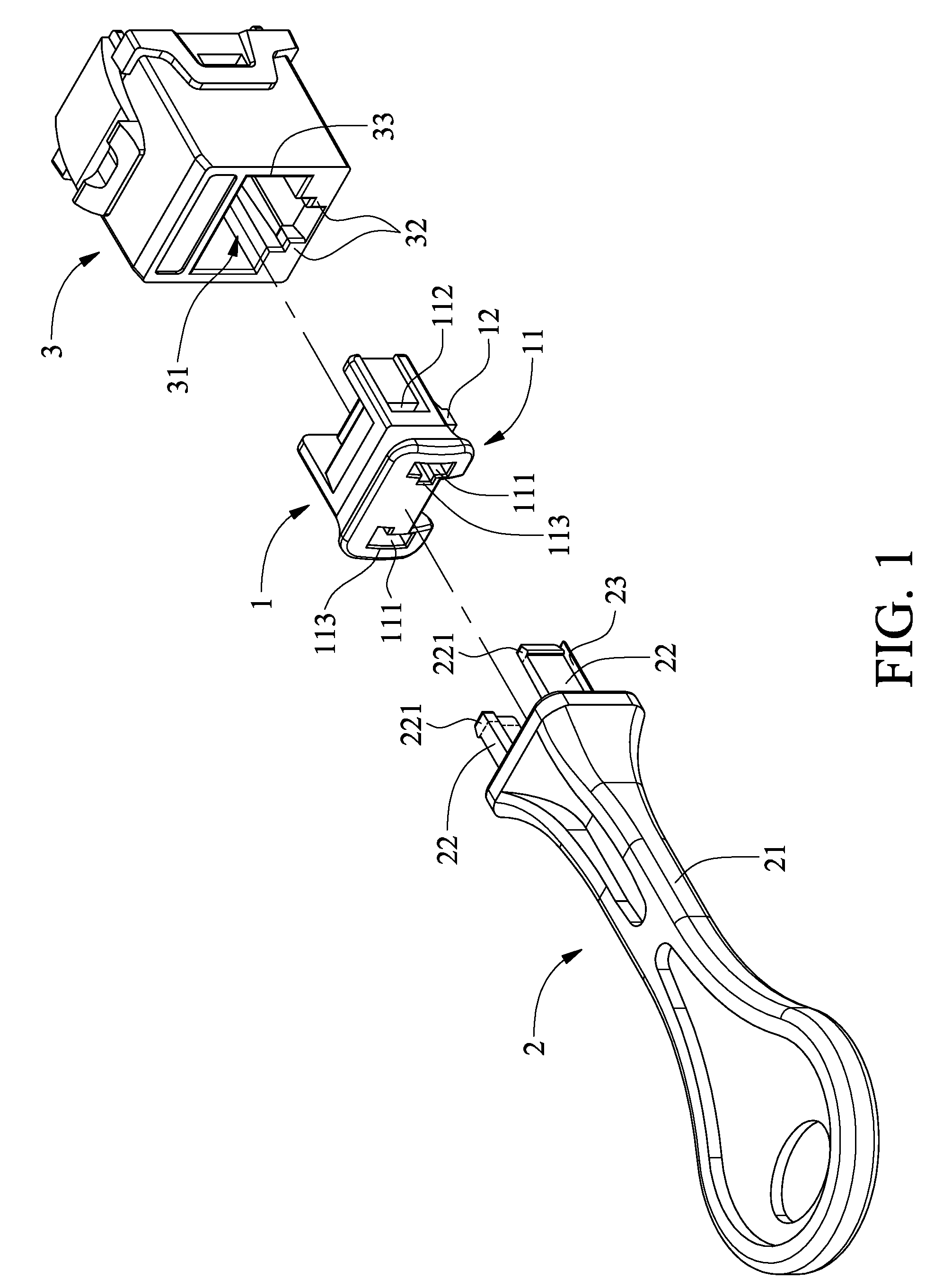
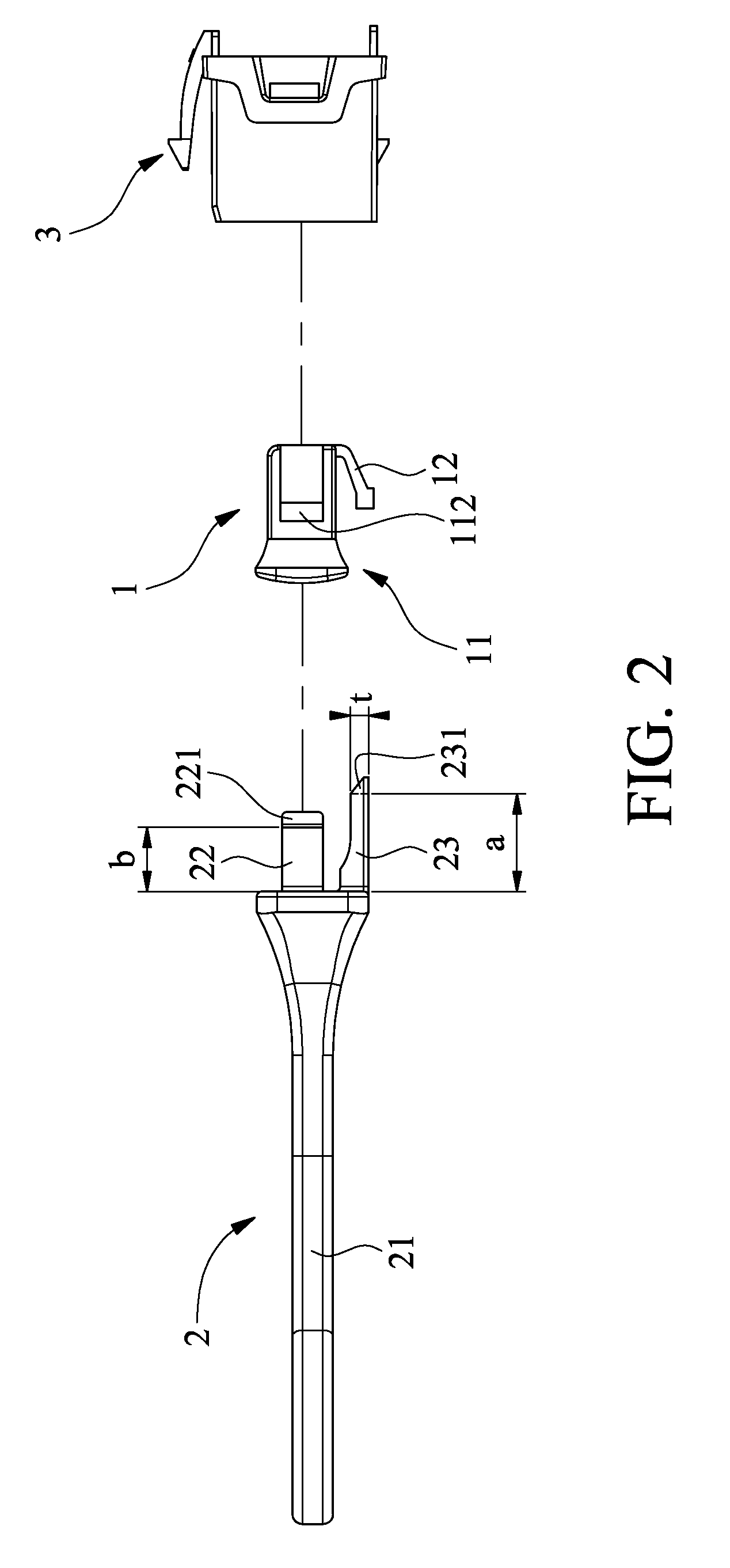
ActiveUS20130244459A1Improper useTwo-part coupling devicesLive contact access preventionData transmissionAcute angle
A protection module includes a protective cover having a first main body and an elastic arm, and a cover removing tool having a second main body, at least one elastic engaging pin and a release pin. The first main body has at least one engaging slot and a retaining slot; the elastic arm has a free front end with at least one beveled slot. The release pin is longer than the elastic engaging pin and has a thickness larger than a height of two raised portions in a socket of the data transmission connector, and has an acute-angled beveled free end. The elastic engaging pin has a cross-sectional shape corresponding to the engaging slot and has a free end with a retaining block. The protective cover is plugged into the data transmission connector for protecting the same against damages caused by maliciously applied force or improper use of it.
Owner:HSING CHAU INDAL
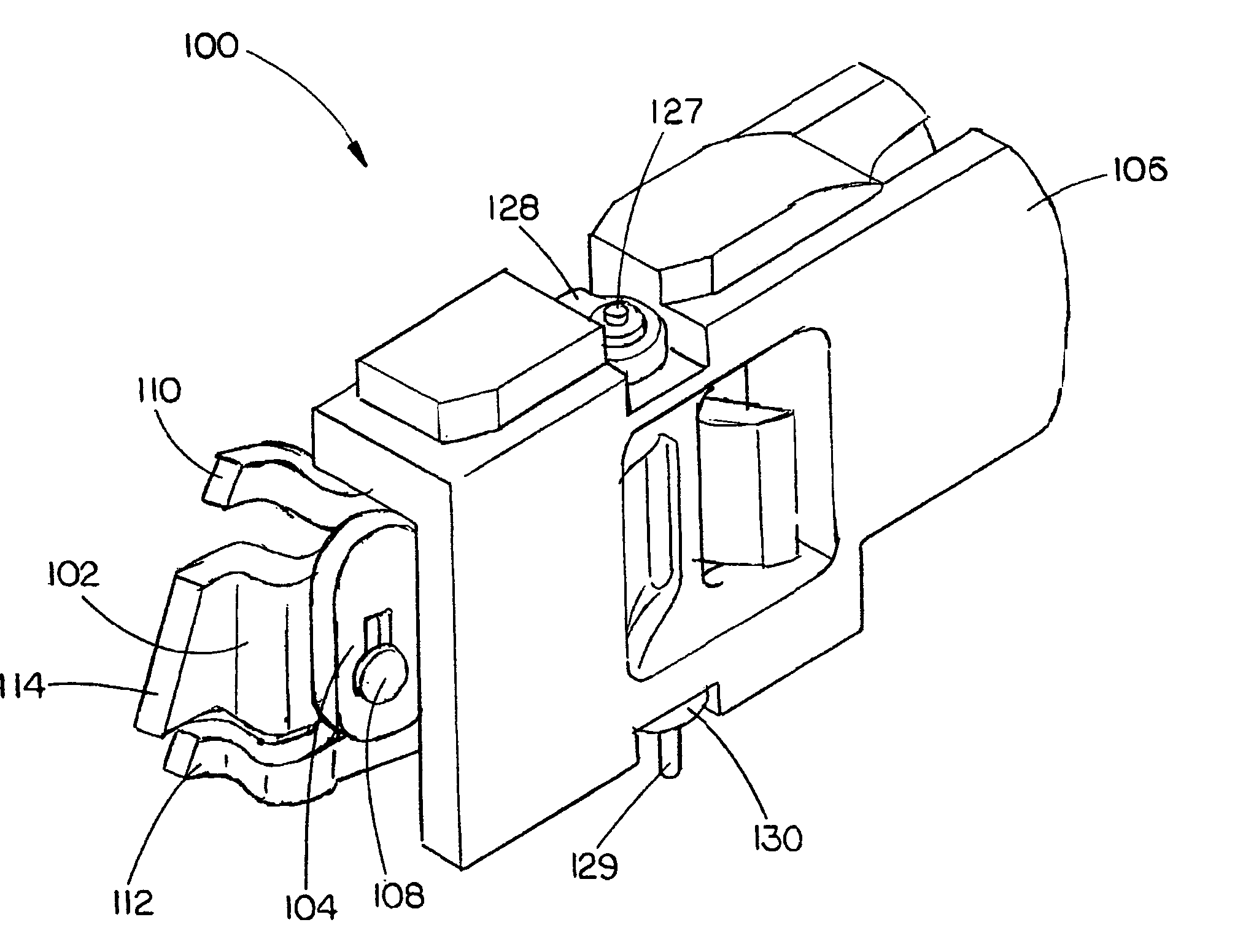
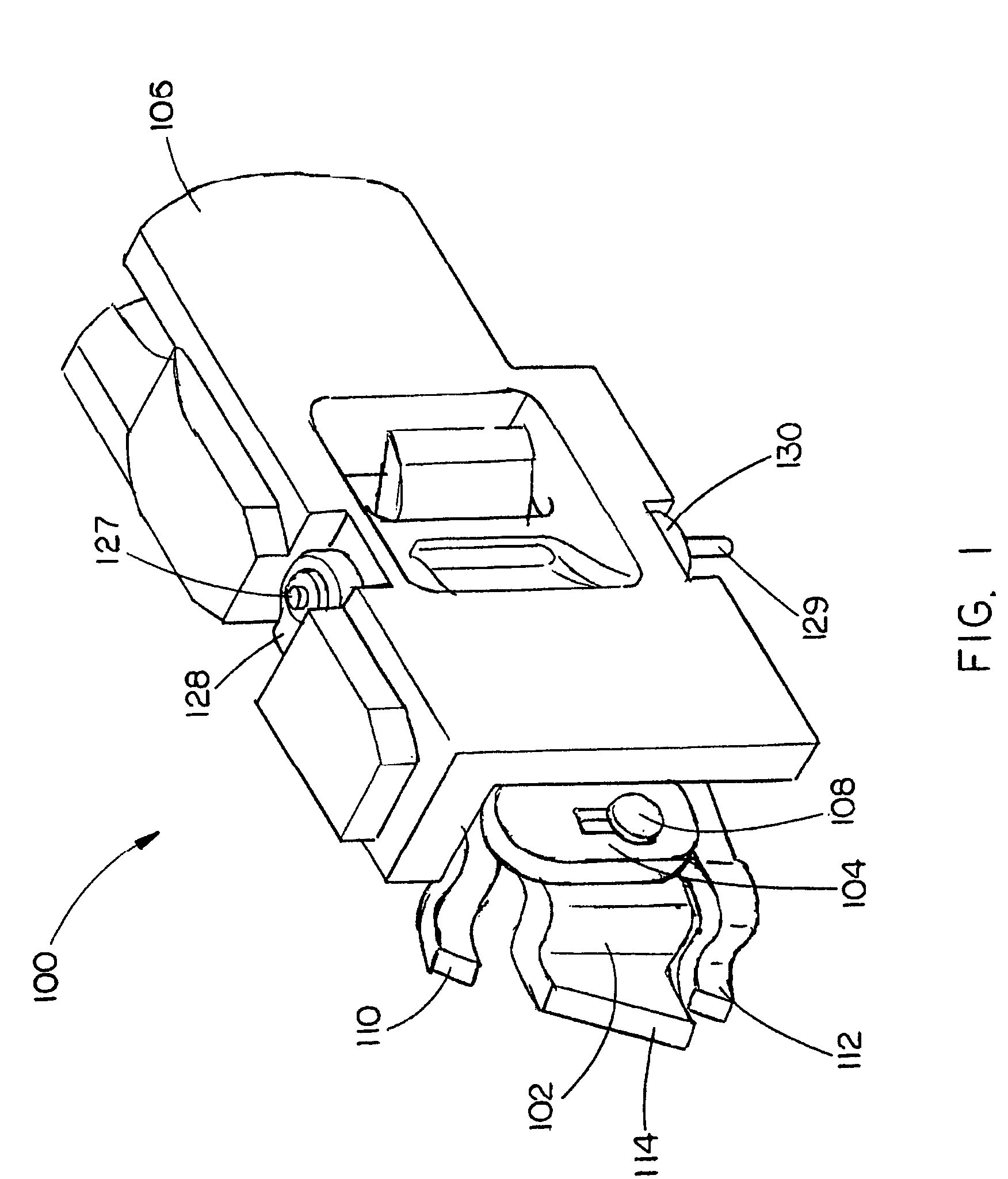
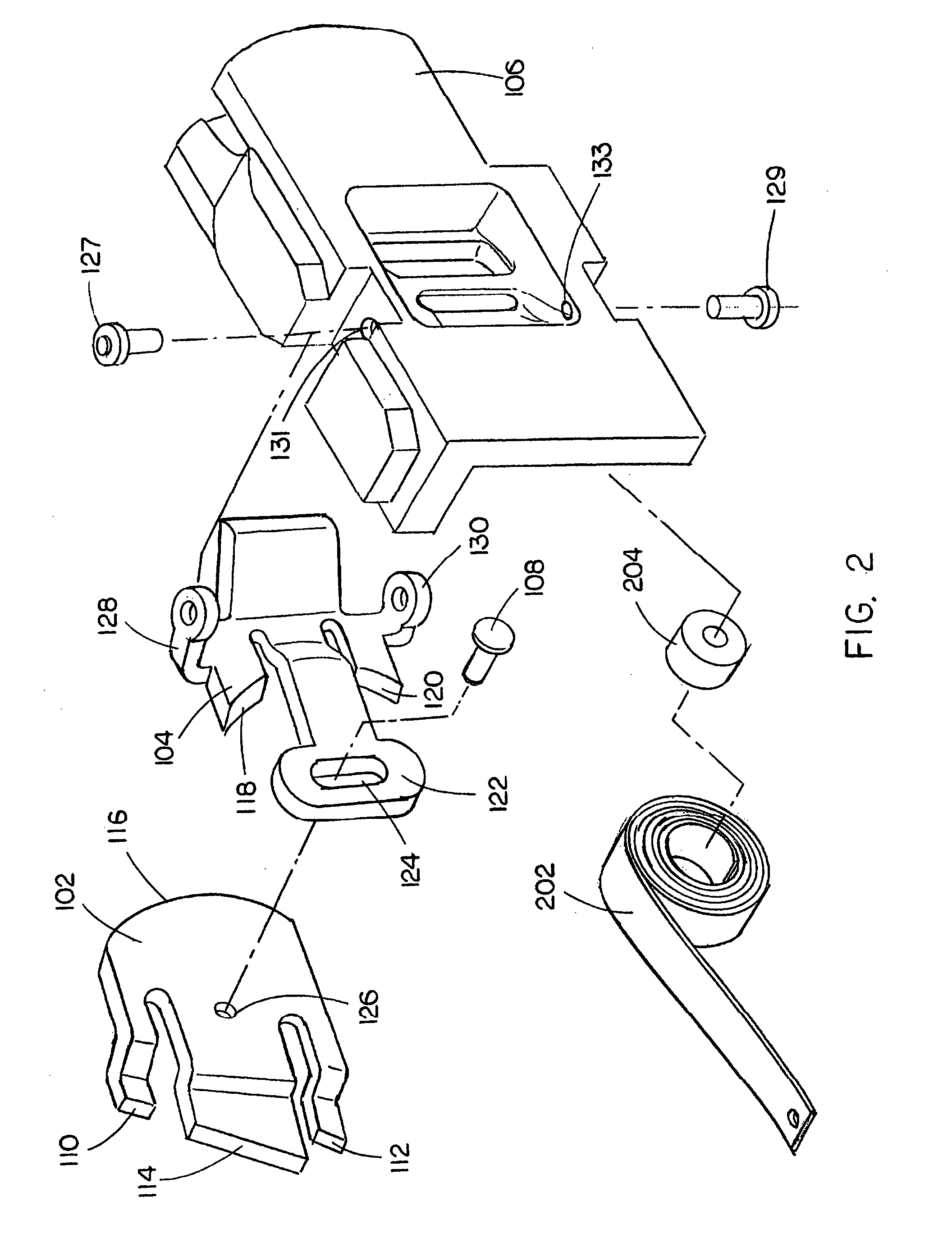
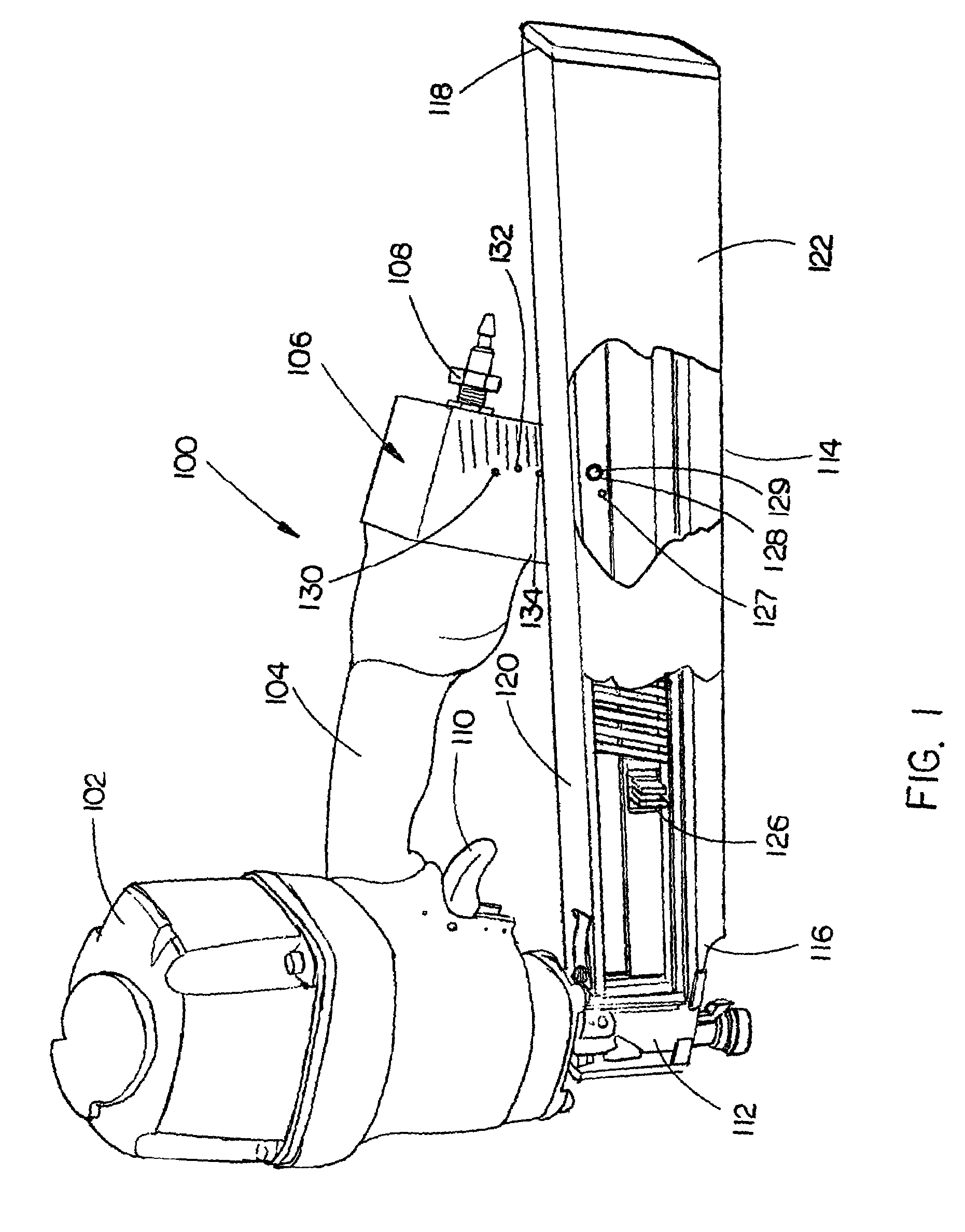
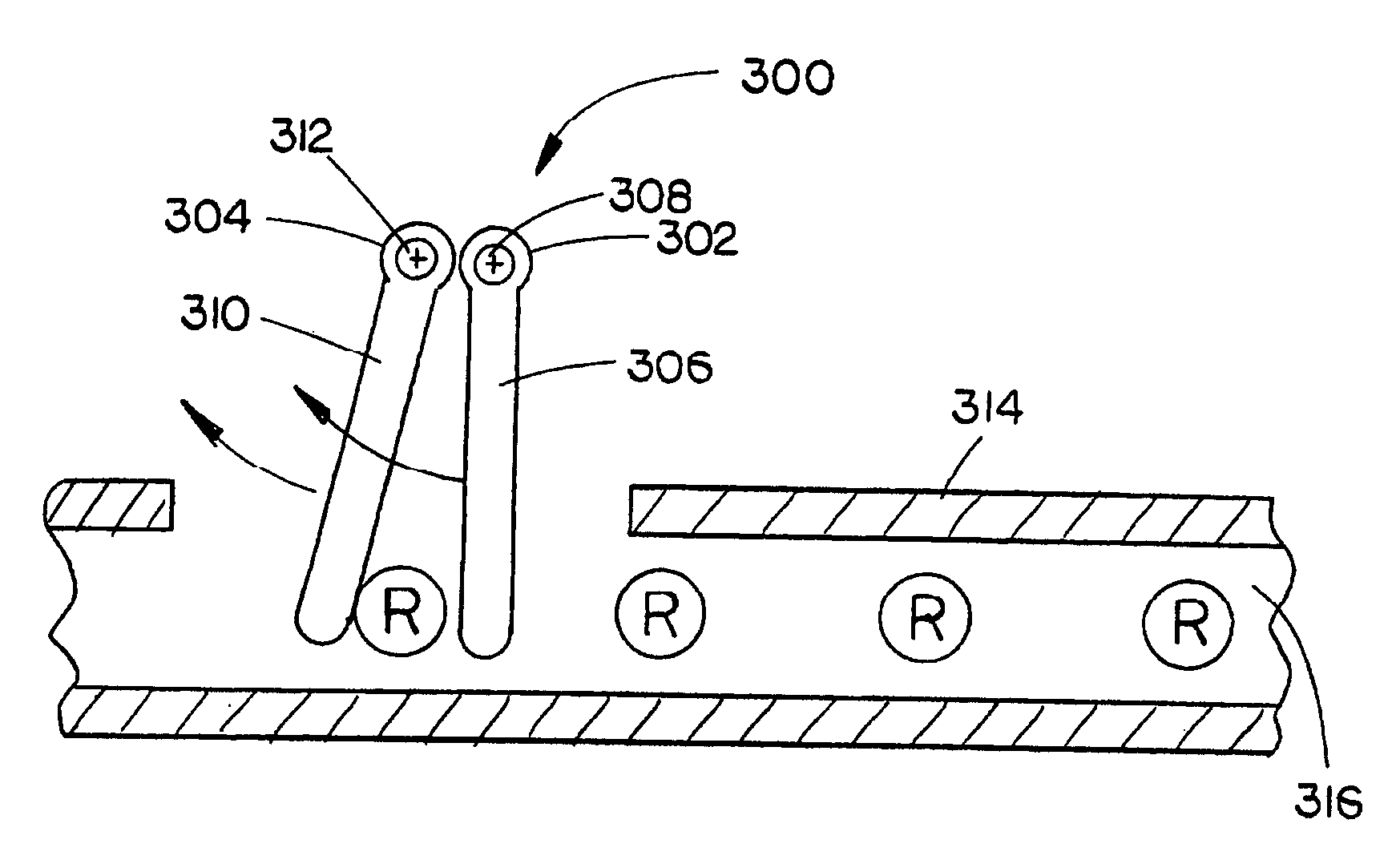
Nail spacing verification assembly
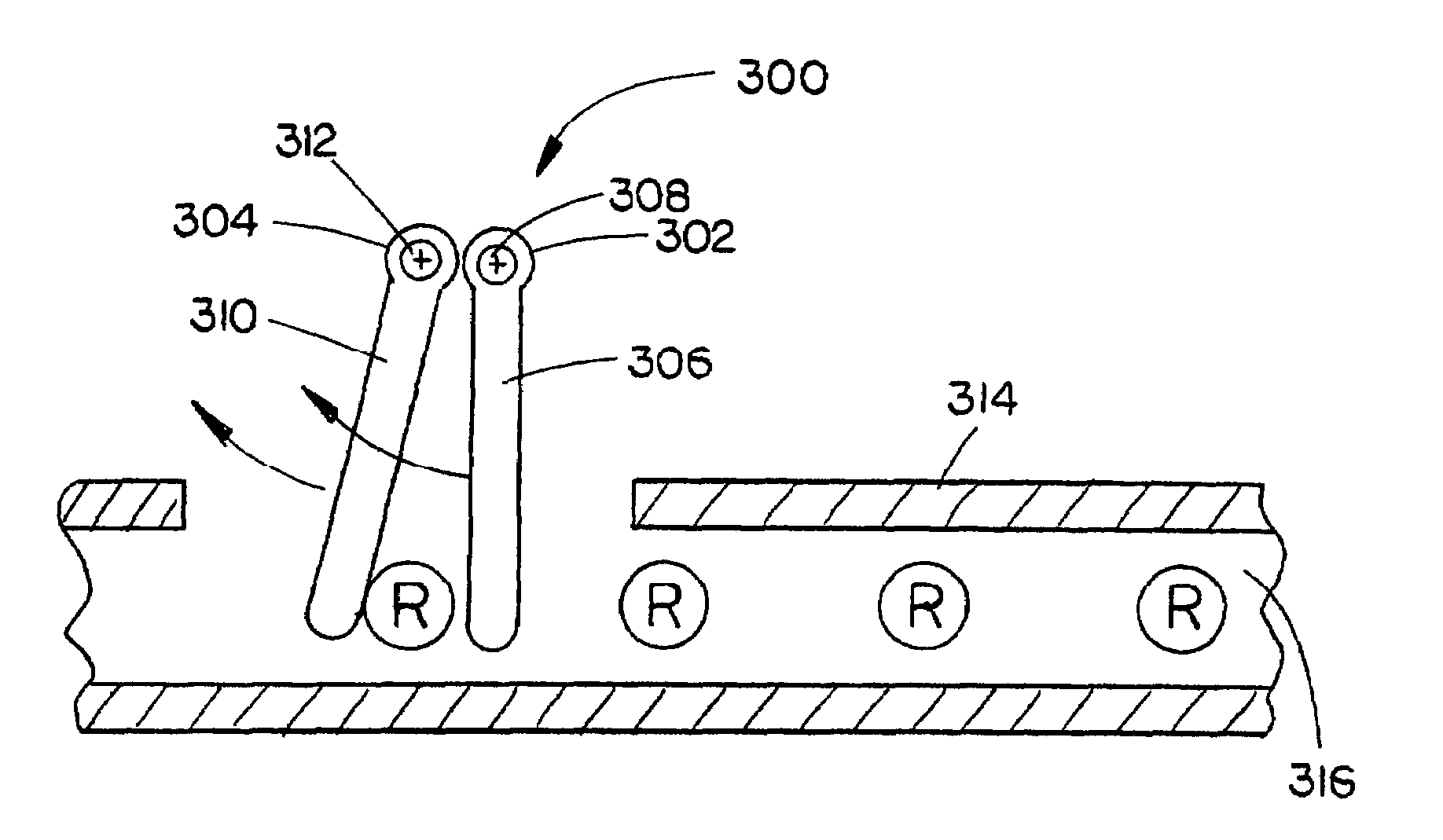
InactiveUS7143508B2Instances of nail misfire may be reducedDamage to improperStapling toolsAutomatic control devicesBiomedical engineeringNail gun
A nail spacing verification assembly is provided which enables the spacing between nails contained in a collated nail strip, the collated nail strip advancing down a nail loading assembly of a nail gun, to be verified before the nail is allowed to advance. A first and second probe are operationally coupled with each other. If nail spacing is correct, the first probe engages the second probe causing both probes to rotate and the nail to pass. If spacing is incorrect, the first probe does not engage the second probe and the nail is hindered from advancing down a nail loading assembly.
Owner:BLACK & DECKER INC
Method and device for safeguarding of a document with inserted signature image and biometric data in a computer system
ActiveUS7971063B2Improper useConfidenceDigital data processing detailsUser identity/authority verificationBiometric dataHash function
A method for safeguarding an electronic document includes inserting at least one digital signature image into the electronic document and generating a first check sum for the electronic document, with or without optionally-inserted biometric signature data, using a first hash function. A second check sum is then generated using a second hash function. The first check sum and the biometric data, if provided, are then symmetrically encrypted using a key that is the sum of the second check sum and a generated random value. The symmetrically-encrypted first check sum is attached to the document. The random value is then asymmetrically encrypted using a first public key of a first key pair and the asymmetrically-encrypted random value is added to the document.
Owner:STEPOVER
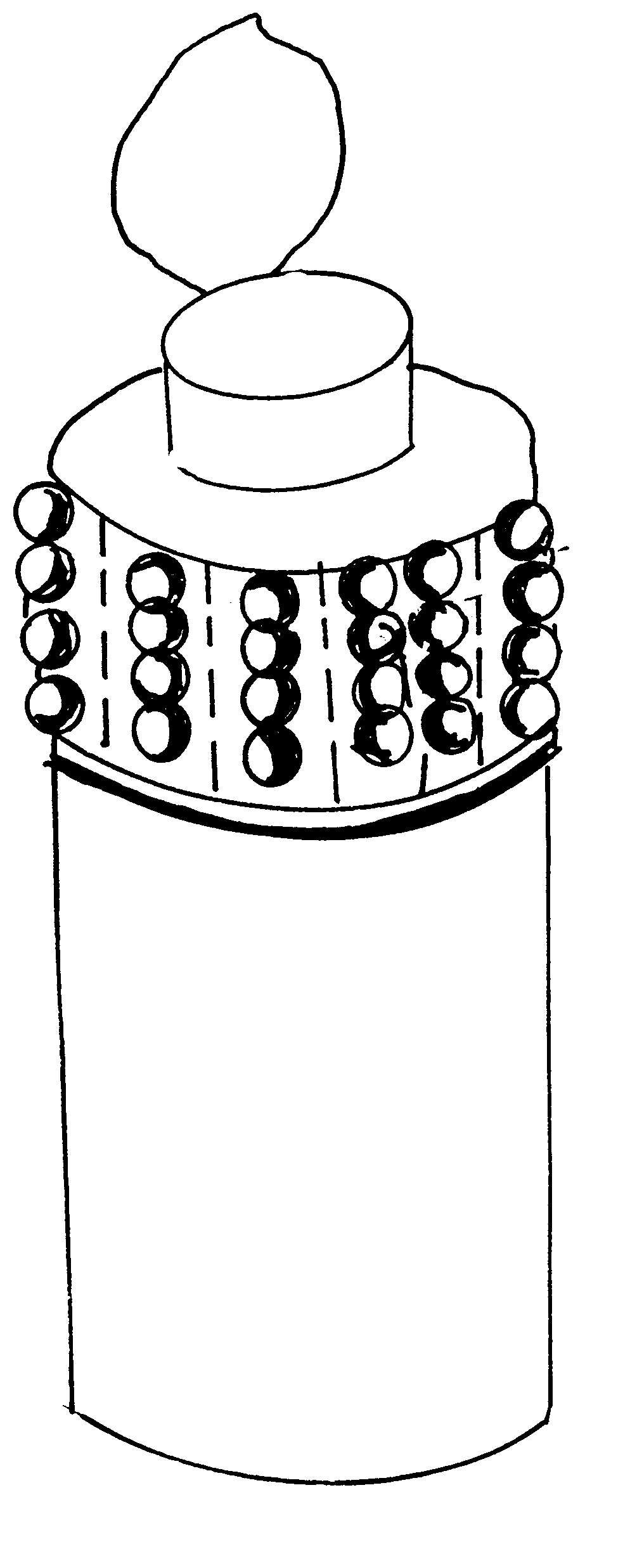
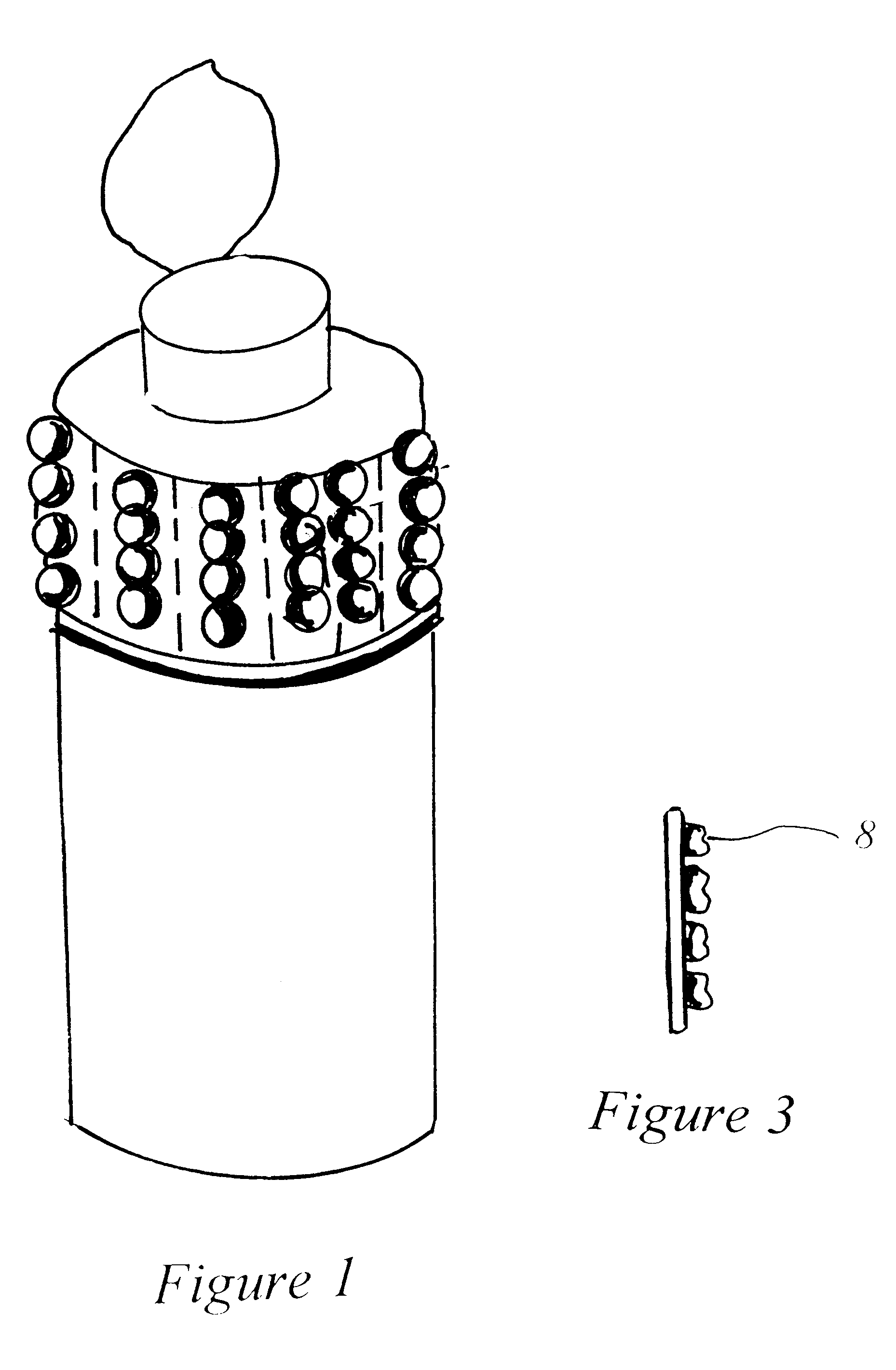
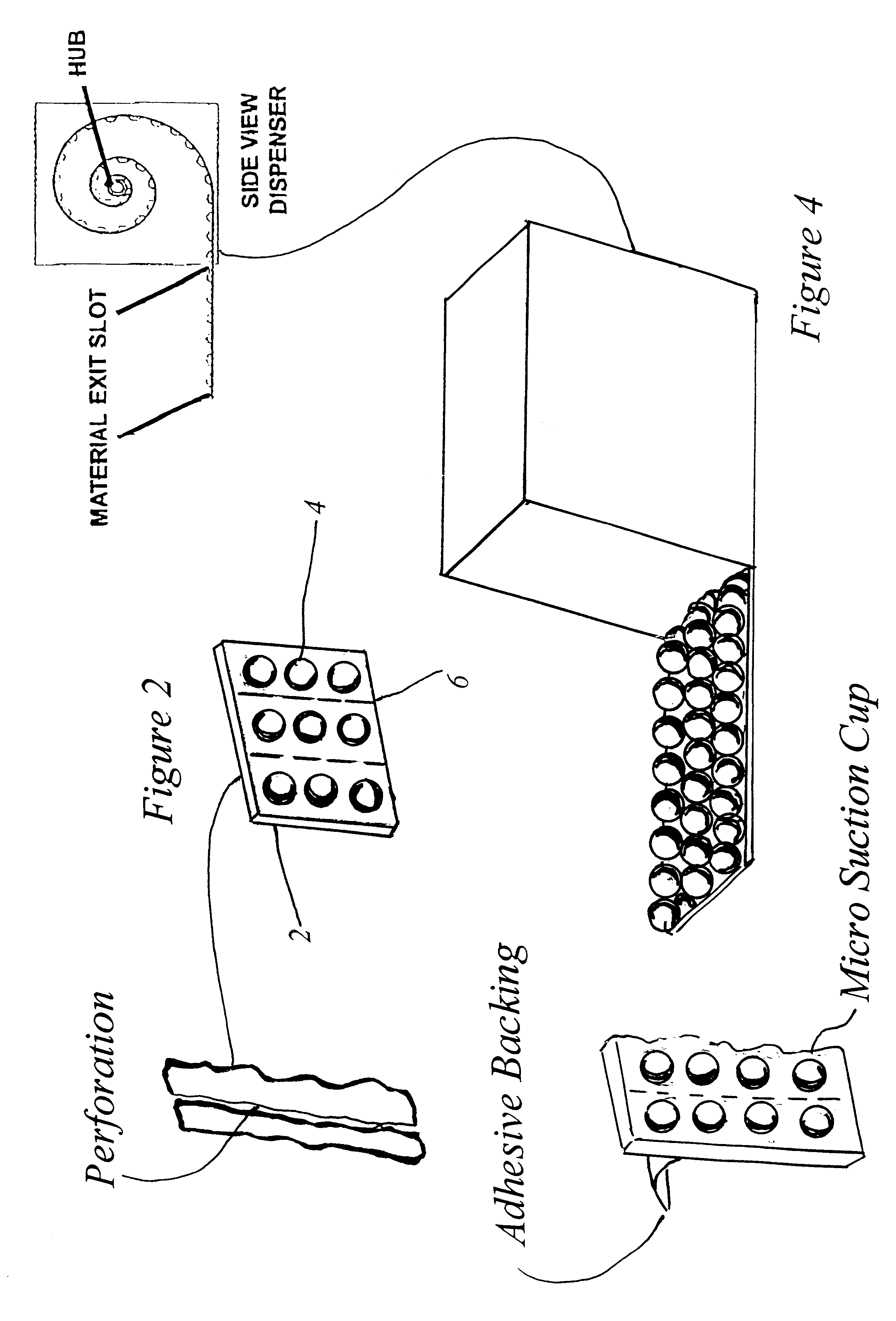
Universal shampoo indentification logo
InactiveUS6367185B1Assisted identificationEasy and efficient to manufactureStampsTeaching apparatusEngineeringBottle
The present invention is that of a new and improved apparatus for assisting a blind or visually impaired person in locating a shampoo bottle or other bottle located within a shower. The apparatus would be a plurality of small adhesive tags attached to each other but allowing a user to separate them by incorporated perforations. Each of the tags would have a plurality of incorporated raised bubbles on its front surface. The back surface would include a peel-away backing, which would cover a sticky coating on the back surface of the small adhesive tags until the small adhesive tags would be ready for use. Each bubble on each of the adhesive tags would be manufactured to include a micro-suction cup top-mounted on each bubble, providing the user with a more secure grip. The plurality of adhesive tags would be designed to come in a roll and would be packaged within a roll dispenser box, with the roll of adhesive tags connected to and surrounding a roller located inside the roll dispenser box. A roll dispenser box would include a slot opening to allow a plurality of small adhesive tags to be removed from the roll dispenser box and attached to a cylindrical object as needed.
Owner:FRASER ANN
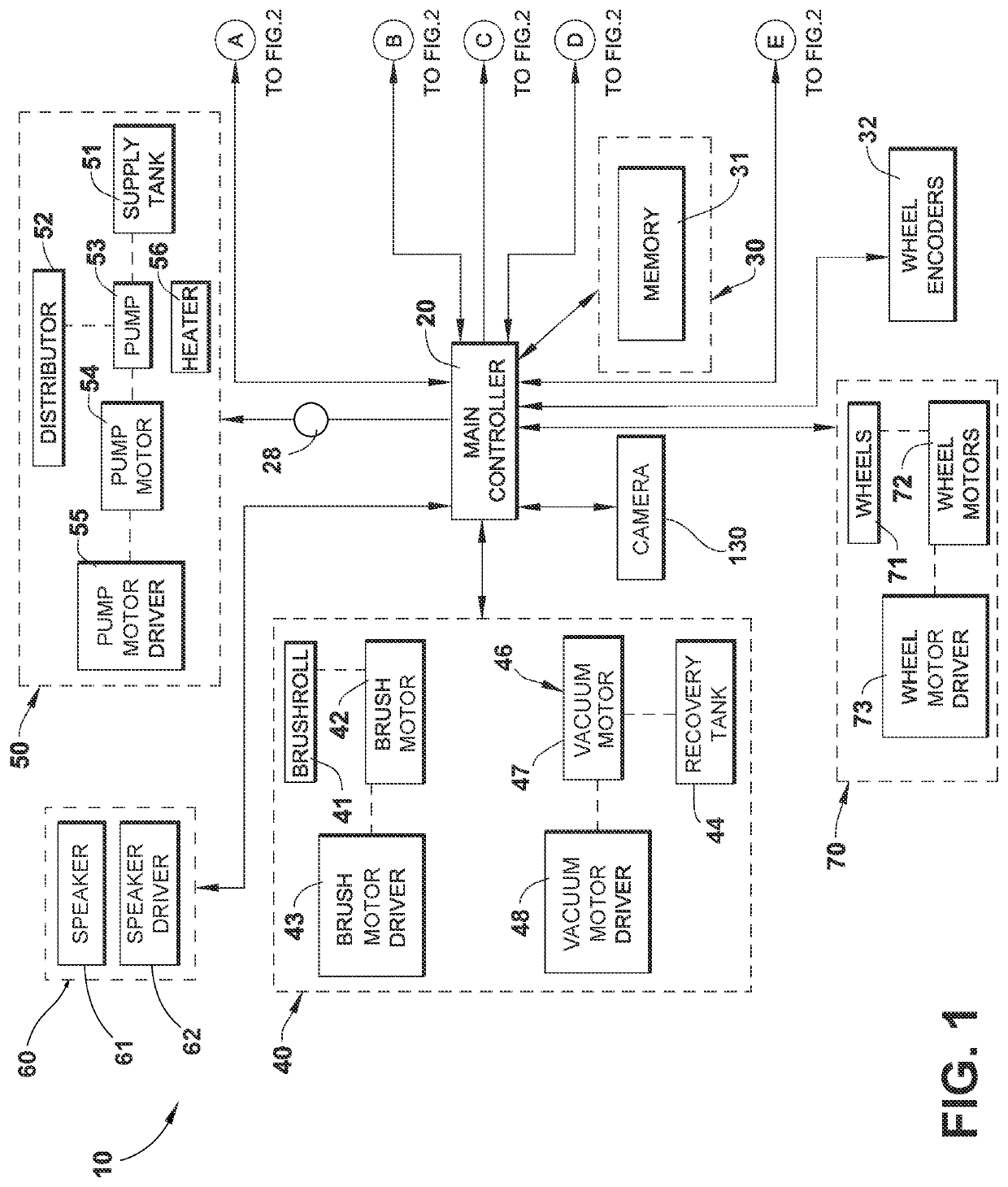
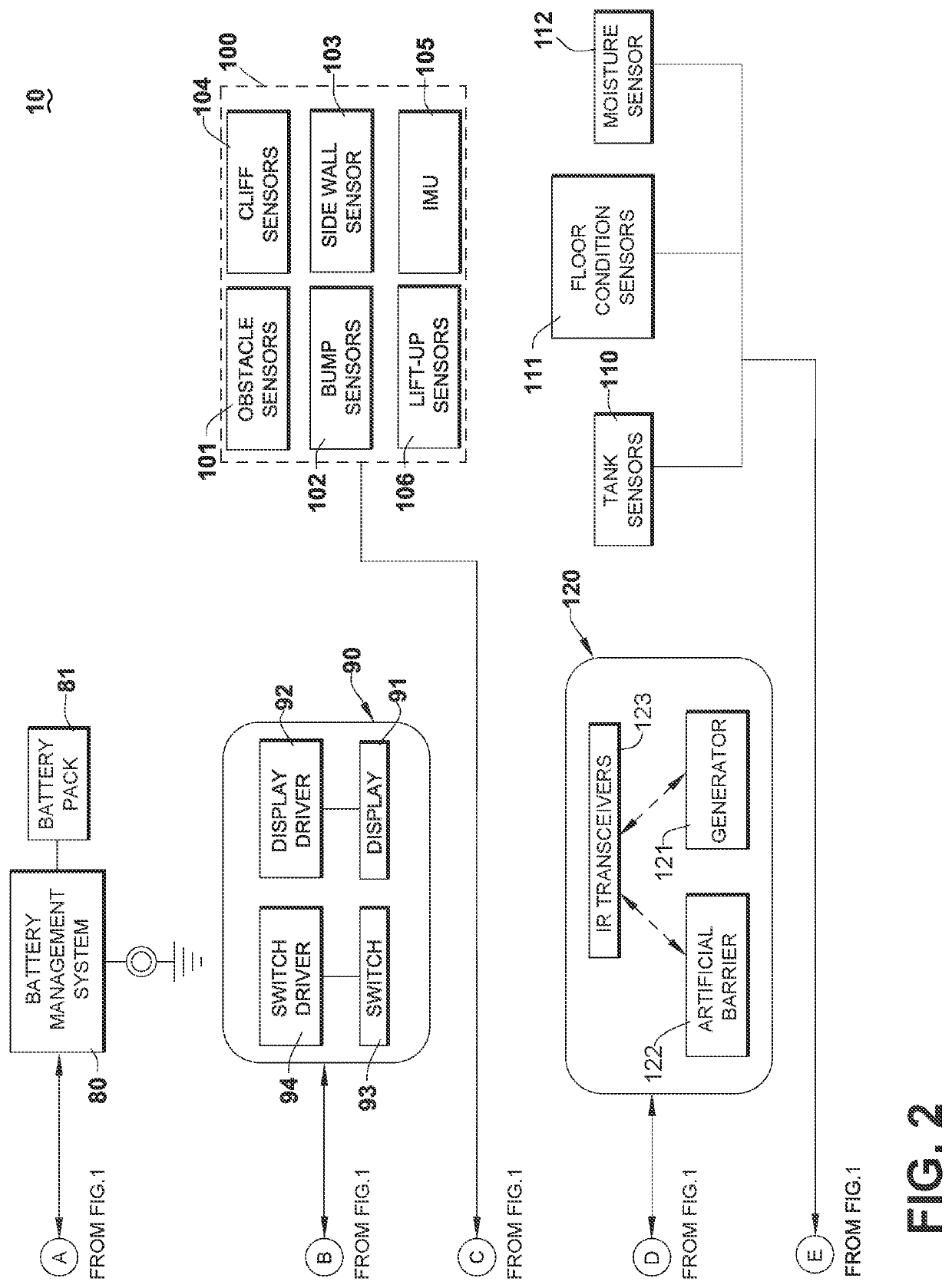
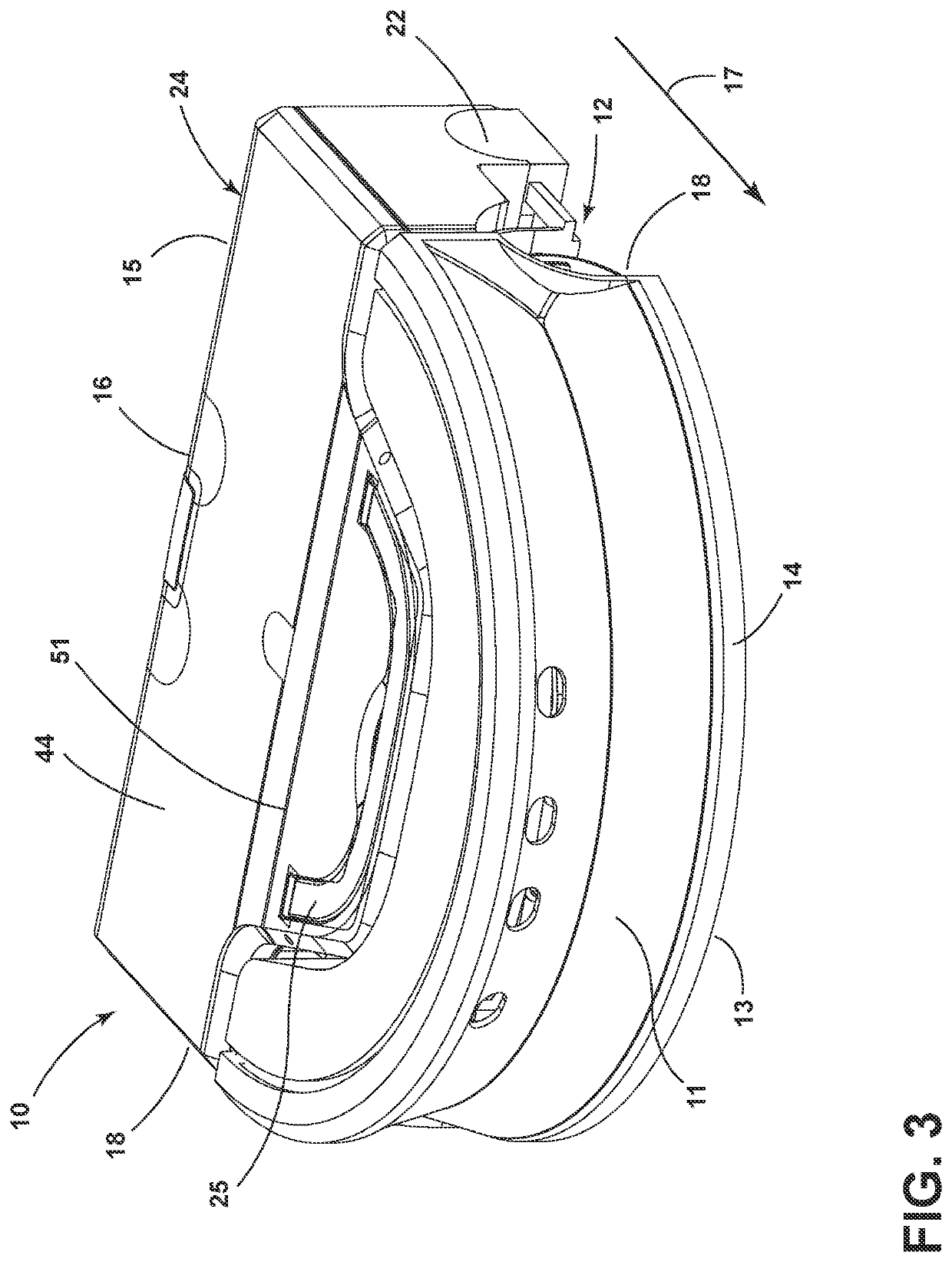
Autonomous floor cleaner with audible warning
ActiveUS20210169296A1Improper useAccurate conditionAutomatic obstacle detectionTravelling automatic controlCleanserFloor Cleaning Agent
An autonomous floor cleaner can include a housing, a drive system for autonomously moving the housing over the surface to be cleaned, a controller for controlling the operation of the autonomous floor cleaner, and warning system for issuing an audible warning based on an orientation or operational condition of the robot. Methods for issuing an audible warning are disclosed.
Owner:BISSELL INC
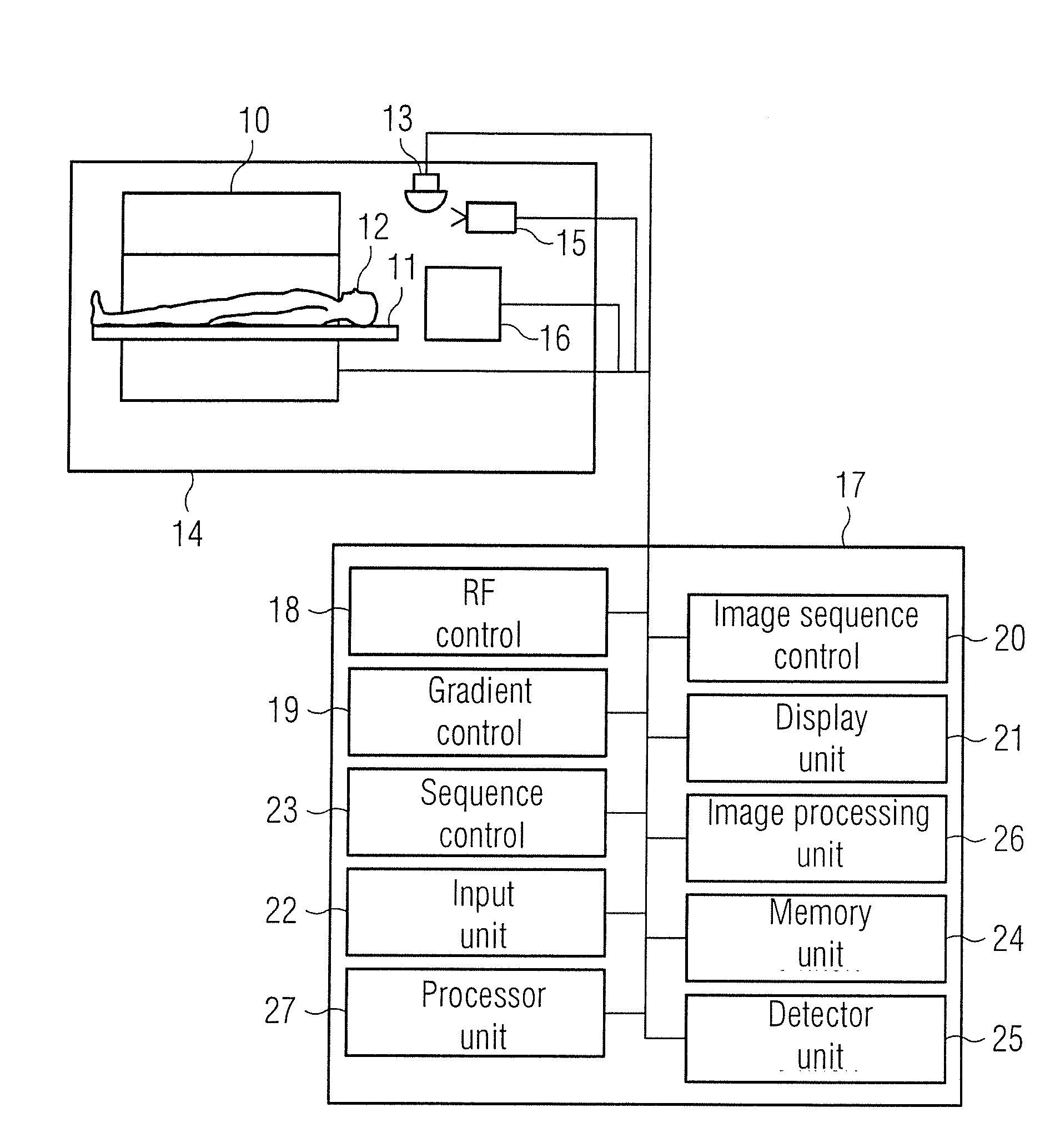
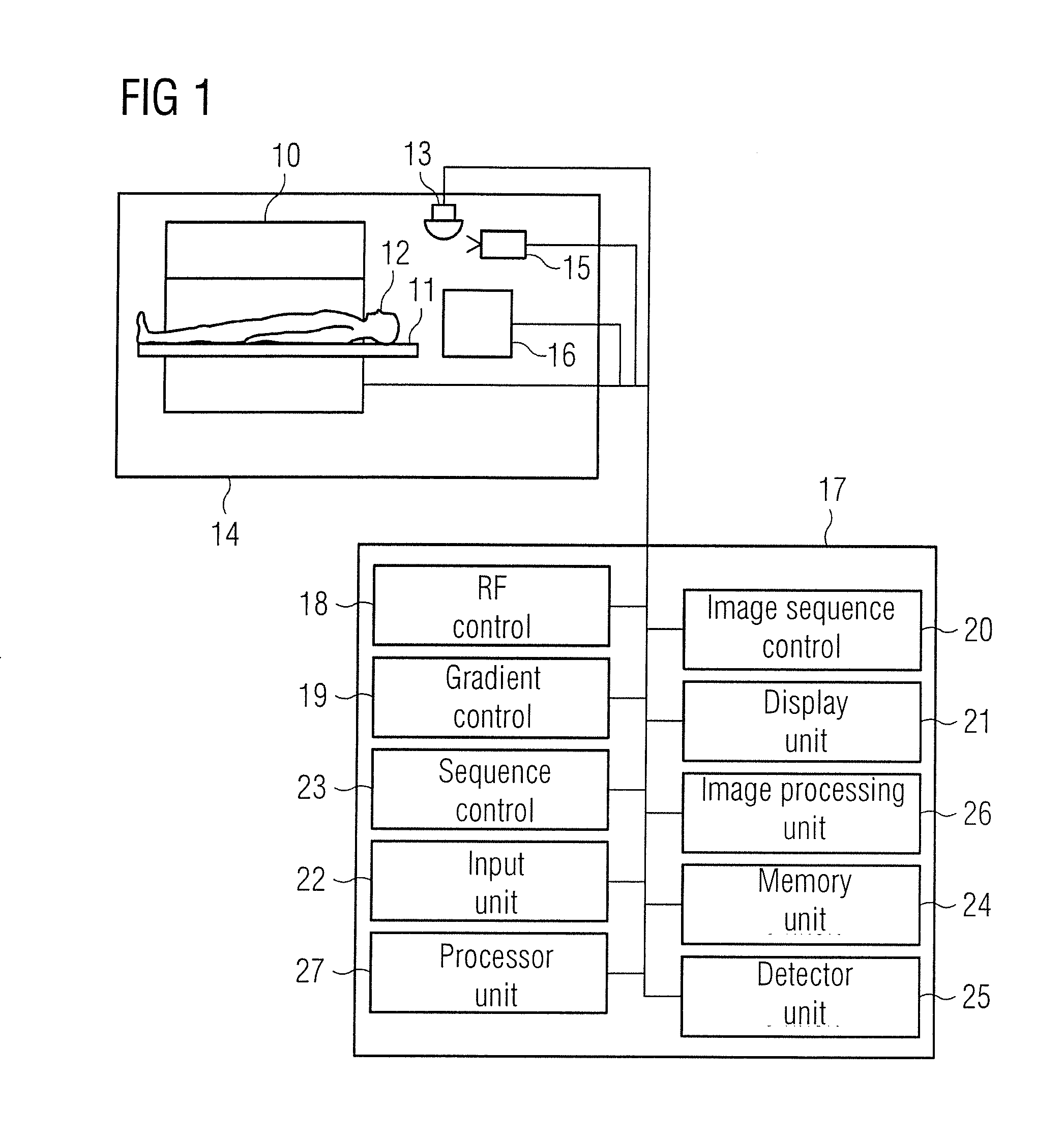
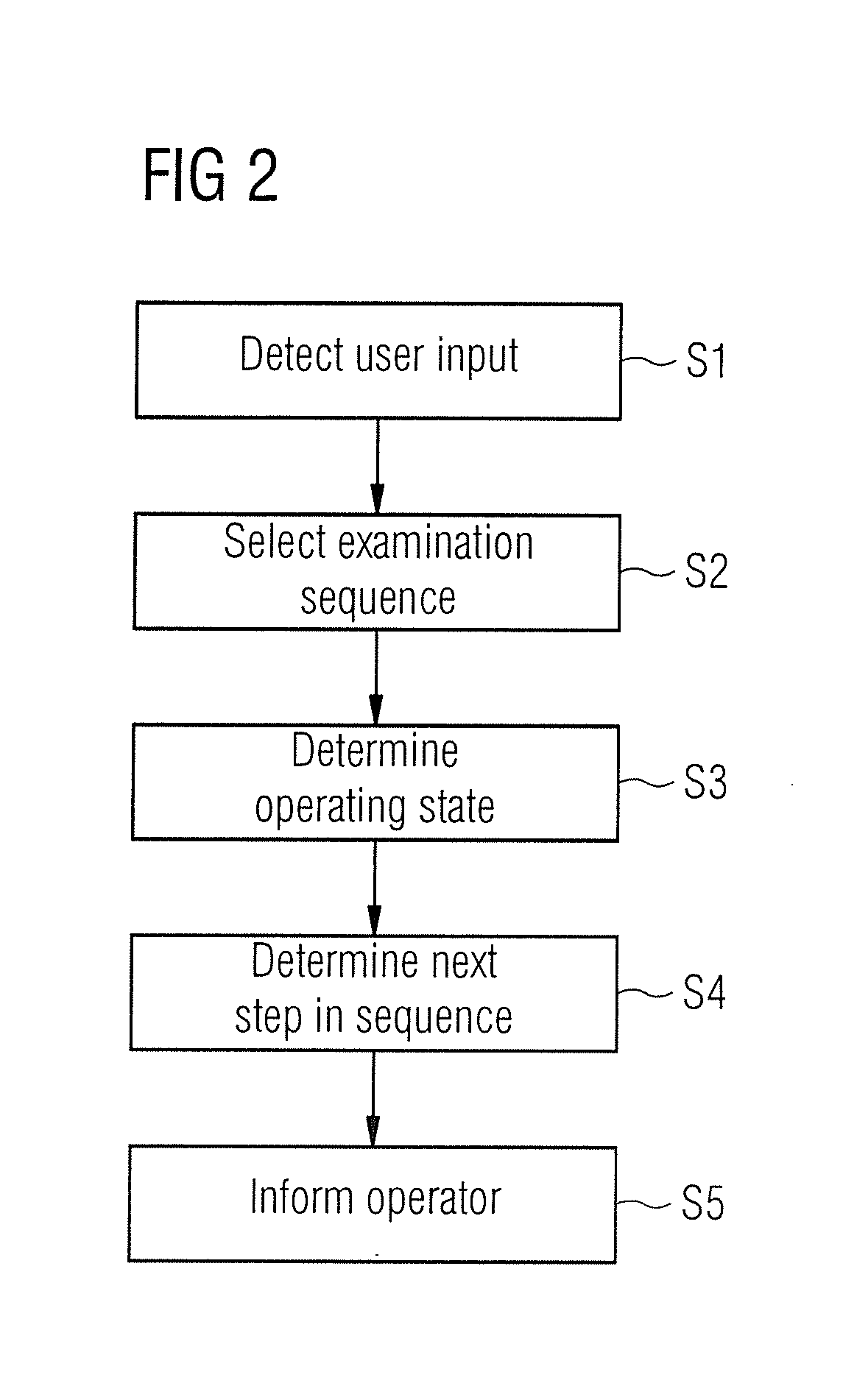
Medical imaging apparatus with optimized operation
ActiveUS20150362566A1Easy to operateImprove securityMeasurements using NMR imaging systemsMedical equipmentMedical imagingComputer science
In a method for operating a medical imaging apparatus in which an examination object is situated, information is detected indicating that at least one image of the examination object is to be created by the medical device. Next, a selection of an examination sequence is made from multiple stored, predefined examination sequences, and subsequently a detection occurs as to the step in the selected examination sequence at which the medical device is currently operating. Thereafter, a specification of the next step to be undertaken from the selected examination sequence is presented to a person operating the medical imaging apparatus.
Owner:SIEMENS AG
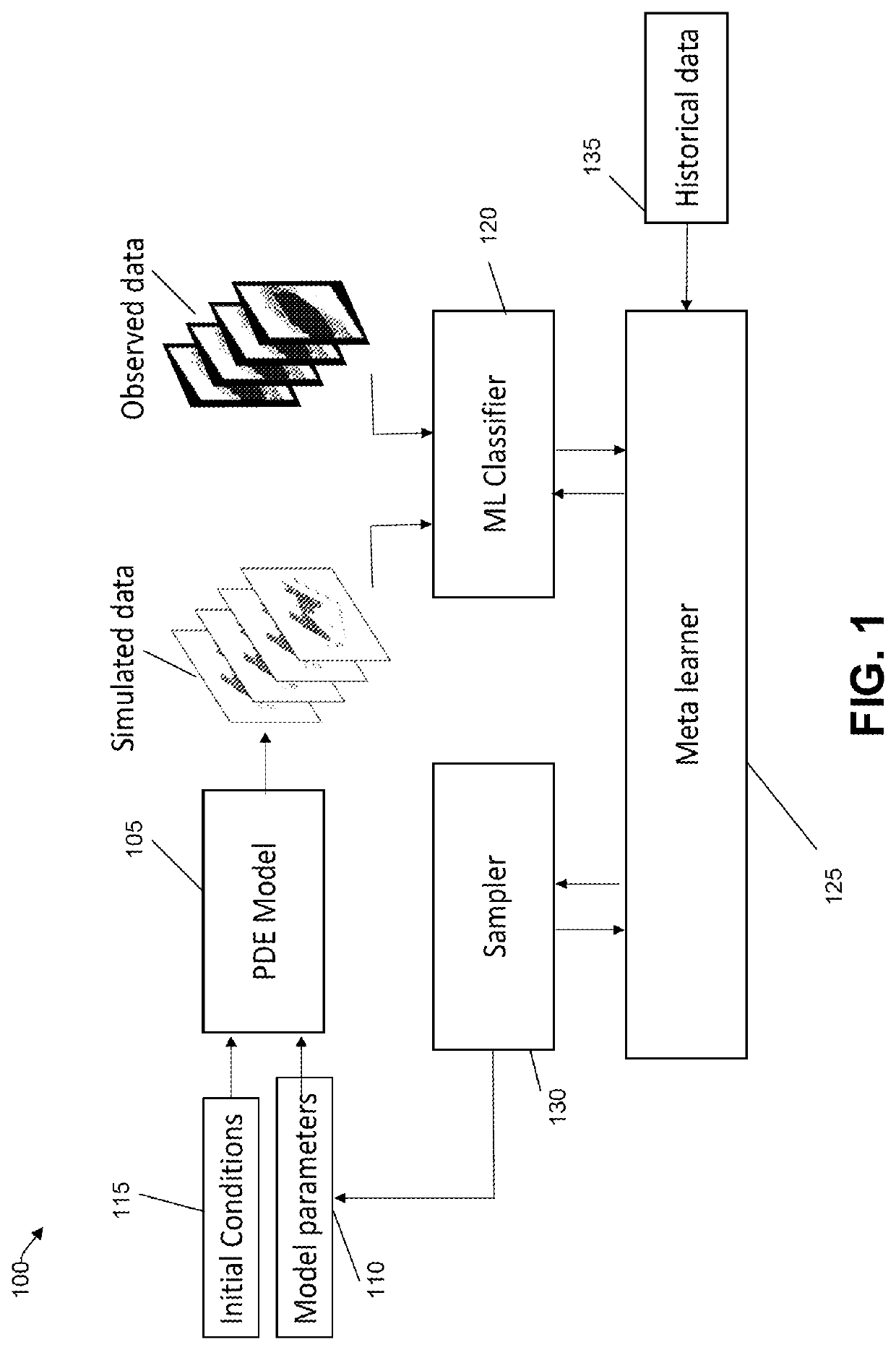
System for continuous update of advection-diffusion models with adversarial networks
PendingUS20220198278A1Improve data accuracyImprove accuracyMathematical modelsNeural architecturesAlgorithmEngineering
A computing device configured for automatic selection of model parameters includes a processor and a memory coupled to the processor. The memory stores instructions to cause the processor to perform acts including providing an initial set of model parameters and initial condition information to a model based on historical data. A model generates data based on the model parameters and the initial condition information. After determining whether the model-generated data is similar to an observed data, updated model parameters are selected for input to the model based on the determined similarity.
Owner:IBM CORP
Tandem-trolley, zip-line system and method
InactiveUS20170144678A1Simplify operating proceduresSimple processBrakes for specific applicationsRope railwaysSimulationSingle line
A canopy tour system follow a route including multiple legs of track line, and may run multiple track lines in parallel along each leg, establishing the route of descent. Each leg extends between an associated upper station and lower station, used for loading, launching, receiving, and unclipping, respectively, riders of trolleys on the zip lines. A system of mechanical and electronic interlocks provides safety for users in remote locations, enabling individual riders to operate trolleys, including attaching and dis-attaching the trolleys from various track lines, unattended by other workers or employees of the canopy tour operation. Multiple trolleys may travel simultaneously and in close proximity to one another as a group on a single line. Each group traveling together is controlled by a single braking trolley ahead, behind, or in the midst of the group.
Owner:ZIPHLDG
Coupler with Magnet
InactiveUS20120230760A1Easy to useAvoid positioningMechanical machines/dredgersRopes and cables for vehicles/pulleyEngineeringFlange
A coupler includes first and second attachment pin jaws. A first latching mechanism is associated with the first jaw. The first latching mechanism has an arm connected to and extending away from a latching member. A second latching mechanism is associated with the jaw. The first and second latching mechanisms are adapted to latch the first and second attachment pins of an accessory in or on the first jaw and the second jaw, respectively. The second latching mechanism is powered for movement between a latching position and a non-latching position. The first latching mechanism is operatively connected to, or connectable with, the second latching mechanism to allow it to selectively operate the first latching mechanism between latching and non-latching positions by means of a groove or flange or finger on the second latching mechanism. A magnet is provided to ensure a correct disengagement of the first latch latching mechanism.
Owner:MILLER INT
Learning guard system
InactiveUS9325836B2Block usage and distractionImproper useAssess restrictionSubstation equipmentInternet accessComputer science
A Learning Guard System protects the attention of students in a classroom by requiring the student to download an ‘app’ from the Learning Guard website. During installation the ‘app’ requires the student to provide their name and a list of emergency contacts which are stored in the memory of the smart phone and by the Learning Guard cloud database. When a student enters a classroom doorway cube transmitter mounted thereon interacts with the ‘app in the smart phone to thereby acquire the smart phone ID and turn off the smart phone functionality, including voice, text communication, Internet access, playing music and videos. This prevent communication of the student with others, excepting emergency contacts both public and private. The cube transmitter communicates the smart phone ID to a base station linked to the Learning Guard cloud database, which creates a database of students in the classroom. When the student exits the classroom through the doorway, all of the previously extant smart phone functionalities are turned on.
Owner:CERDA ANTHONY
Nail spacing verification assembly
InactiveUS20060102684A1Improve efficiencyIncrease productivityStapling toolsAutomatic control devicesBiomedical engineeringNail gun
A nail spacing verification assembly is provided which enables the spacing between nails contained in a collated nail strip, the collated nail strip advancing down a nail loading assembly of a nail gun, to be verified before the nail is allowed to advance. A first and second probe are operationally coupled with each other. If nail spacing is correct, the first probe engages the second probe causing both probes to rotate and the nail to pass. If spacing is incorrect, the first probe does not engage the second probe and the nail is hindered from advancing down a nail loading assembly.
Owner:BLACK & DECKER INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com