Patents
Literature
41results about How to "Accurate identity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
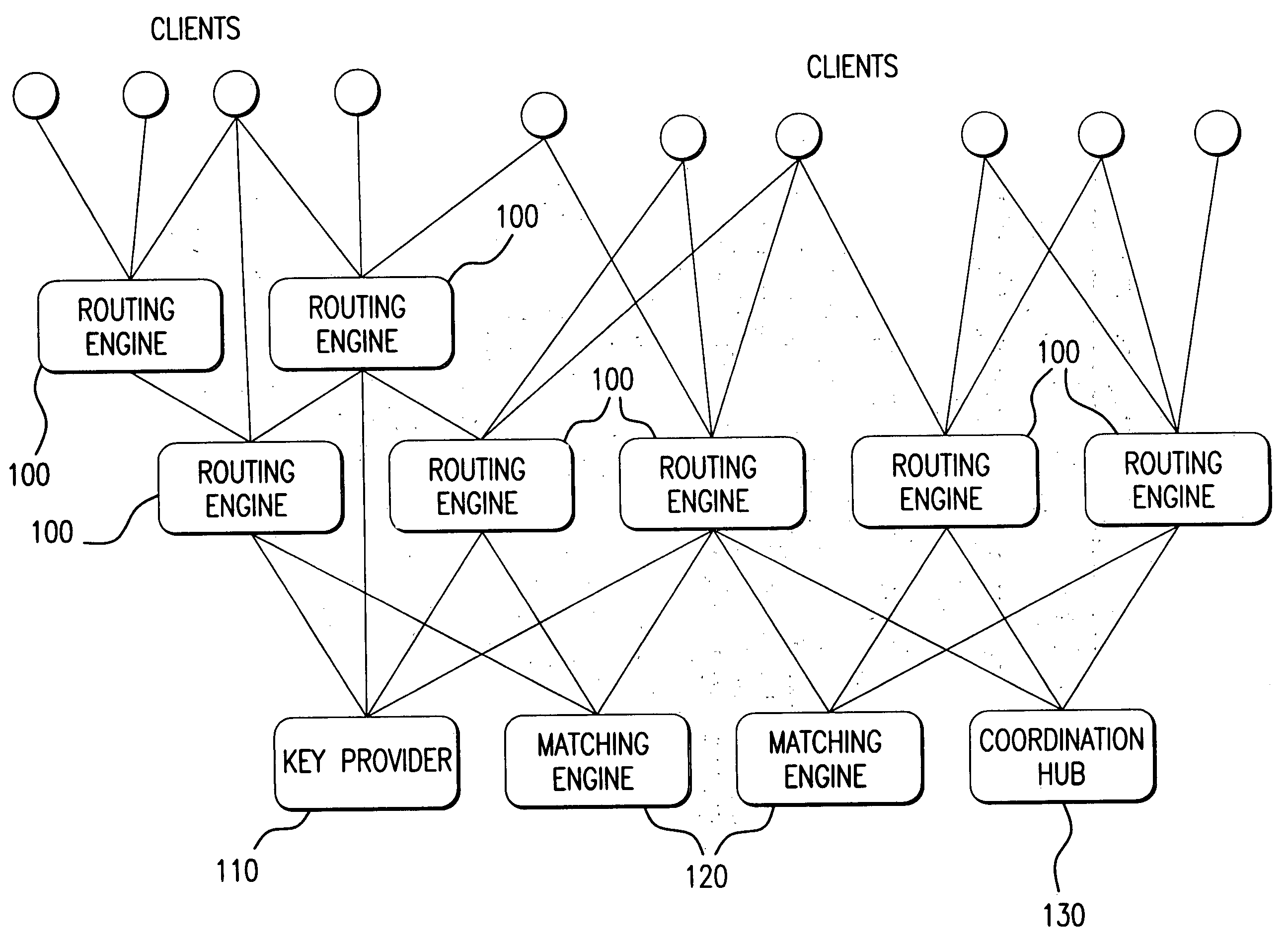
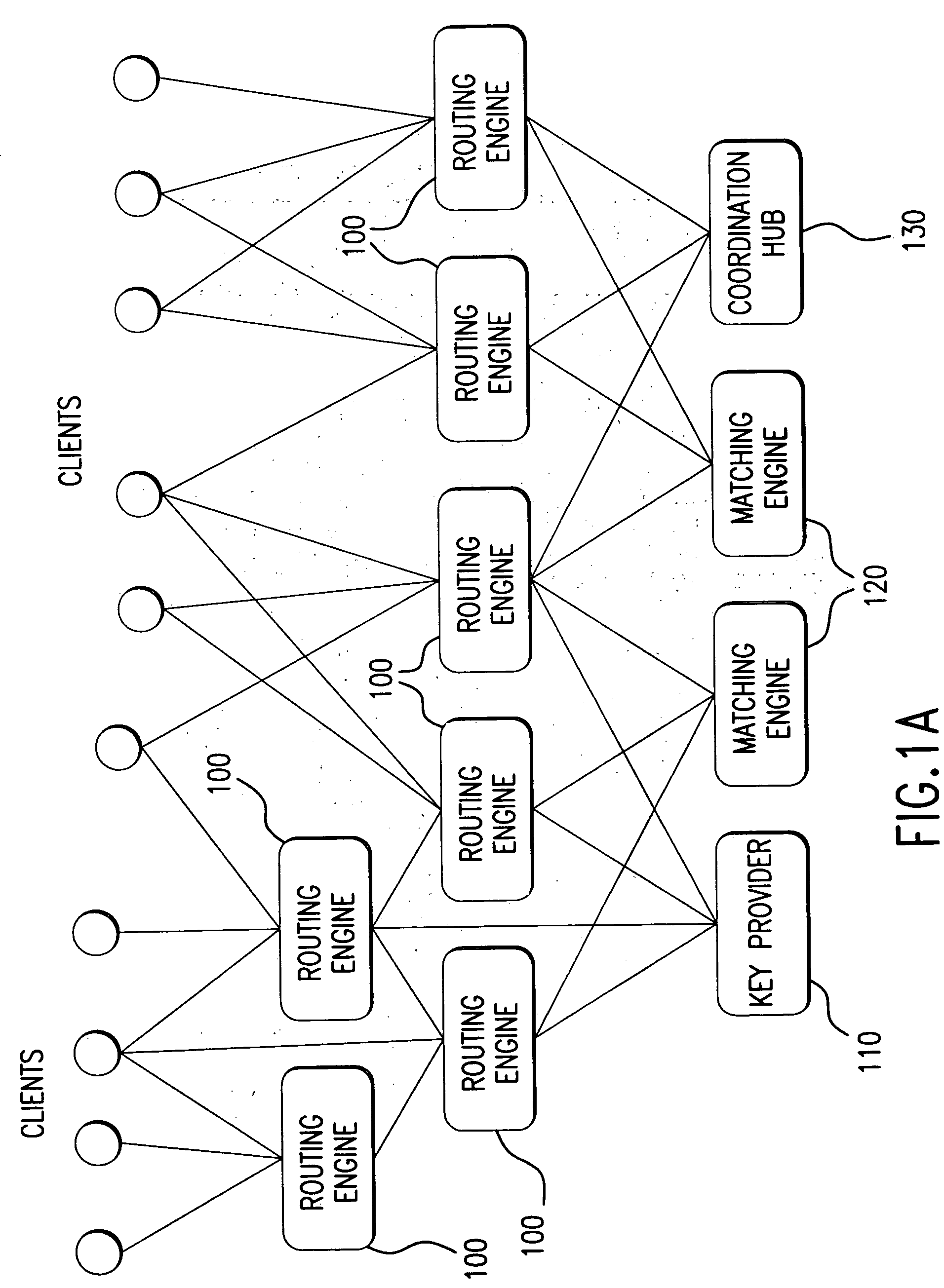
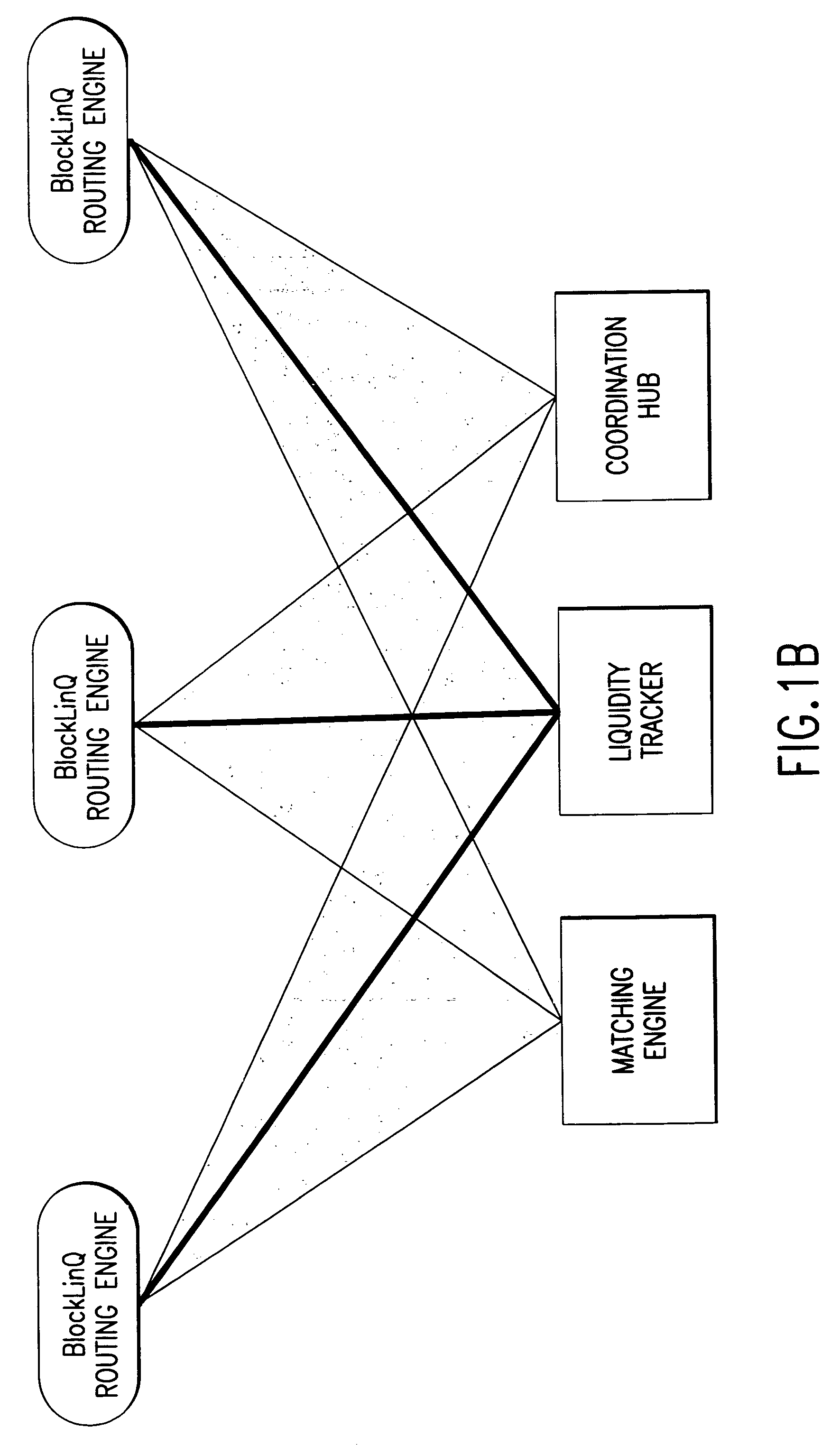
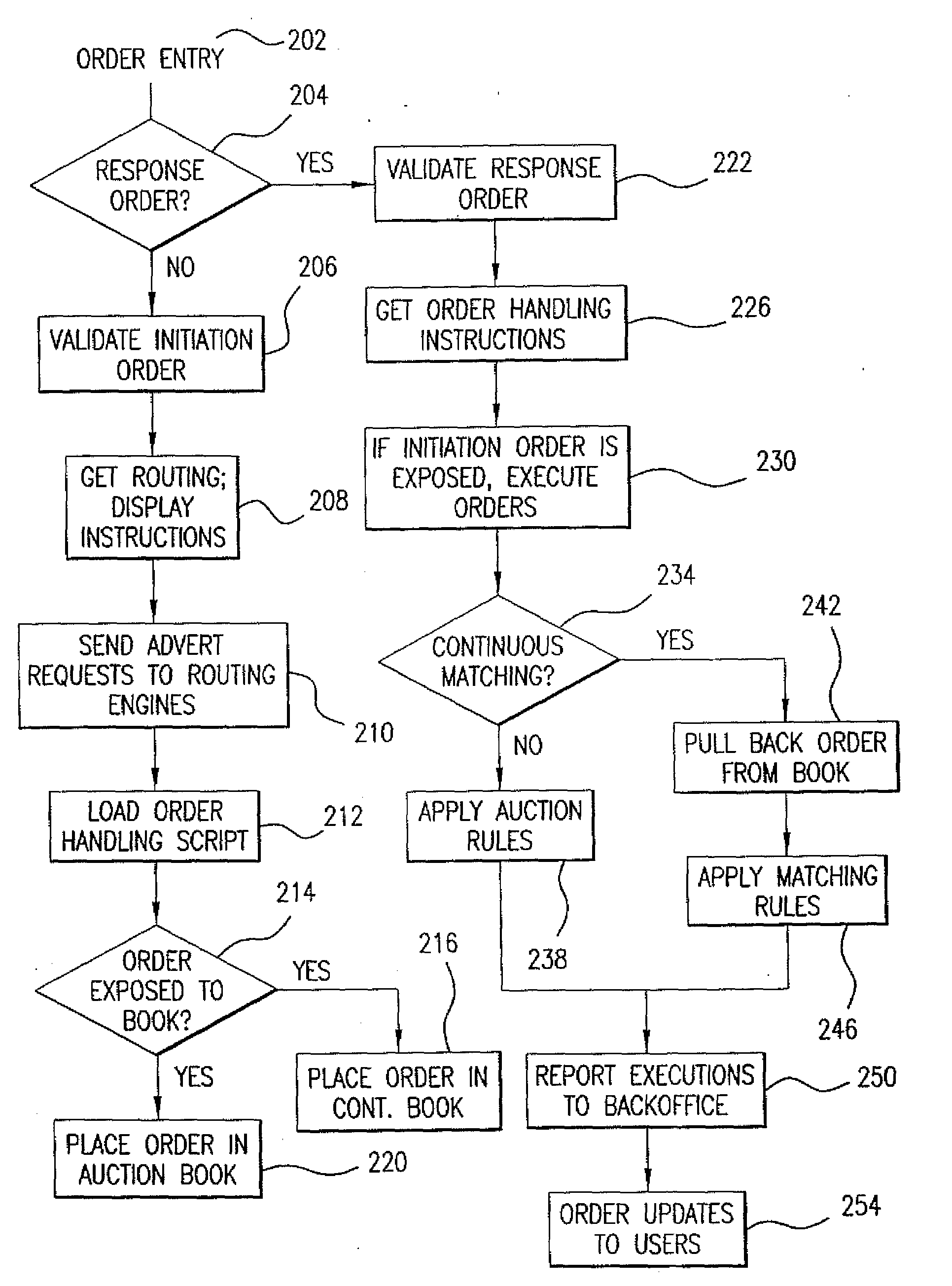
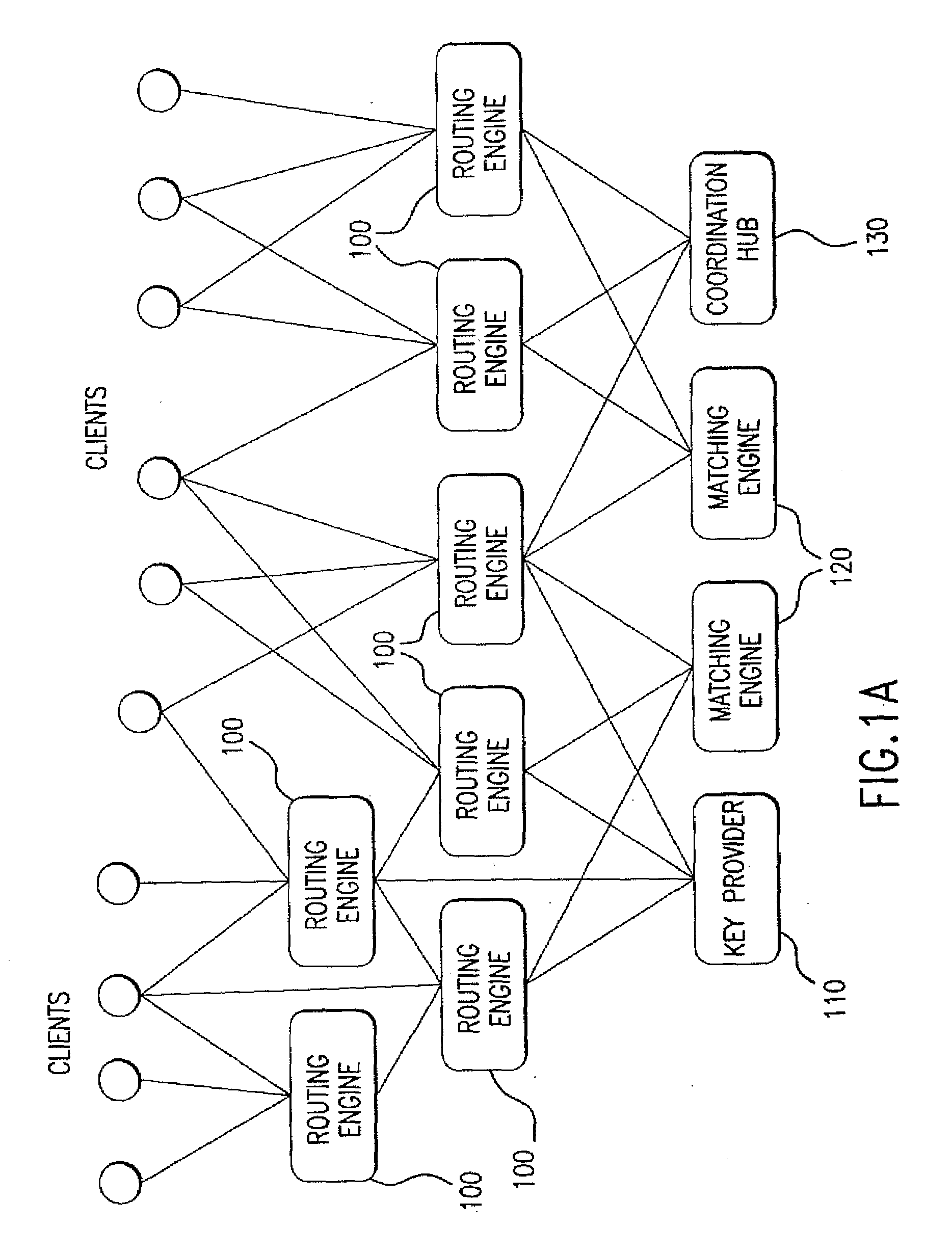
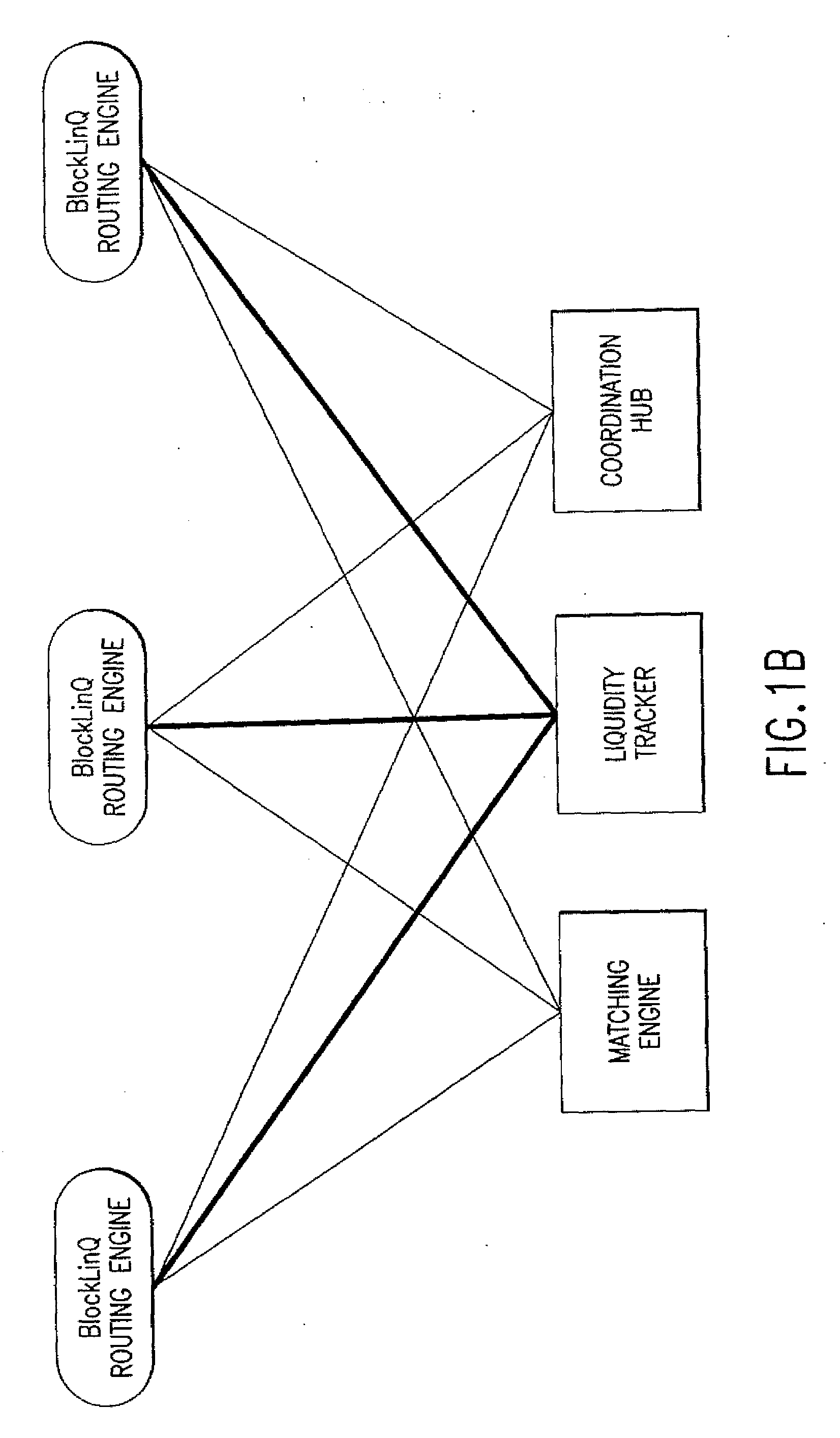
Method and system for managing distributed trading data
InactiveUS7565313B2Avoid misuseMaximizing internalization rateFinanceCommerceData providerTransaction data
In a preferred embodiment, the invention comprises a computer-implemented system and method of managing market information across a network of data providers, comprising the steps of: (a) electronically receiving first data including confidential information regarding market participants in a first system that protects said first data behind a firewall; (b) electronically receiving second data including confidential information regarding market participants in a second system that protects said second data behind a firewall; (c) electronically receiving an order and targeting parameters from a first market participant; (d) electronically issuing an advertisement request message to said first system and said second system, said advertisement message comprising display attributes of said order and comprising said targeting parameters; (e) electronically prompting said first system and said second system via the advertisement request message to each send a coordination request message to a Coordination Hub, said coordination request message comprising information deduced from said confidential information regarding market participants in said first and second systems, wherein the selection of the information that is sent to the Coordination Hub is based at least in part on said first market participant's targeting parameters; (f) electronically prompting based on the coordination request message said Coordination Hub to issue permissions to advertise the order to selected market participants, wherein market participants are selected based, at least in part, on said received information regarding market participants; and (g) electronically prompting based on the permission to advertise the order said first system and said second system to route information about said order from first participant to said selected market participants.
Owner:ITG SOFTWARE SOLUTIONS INC
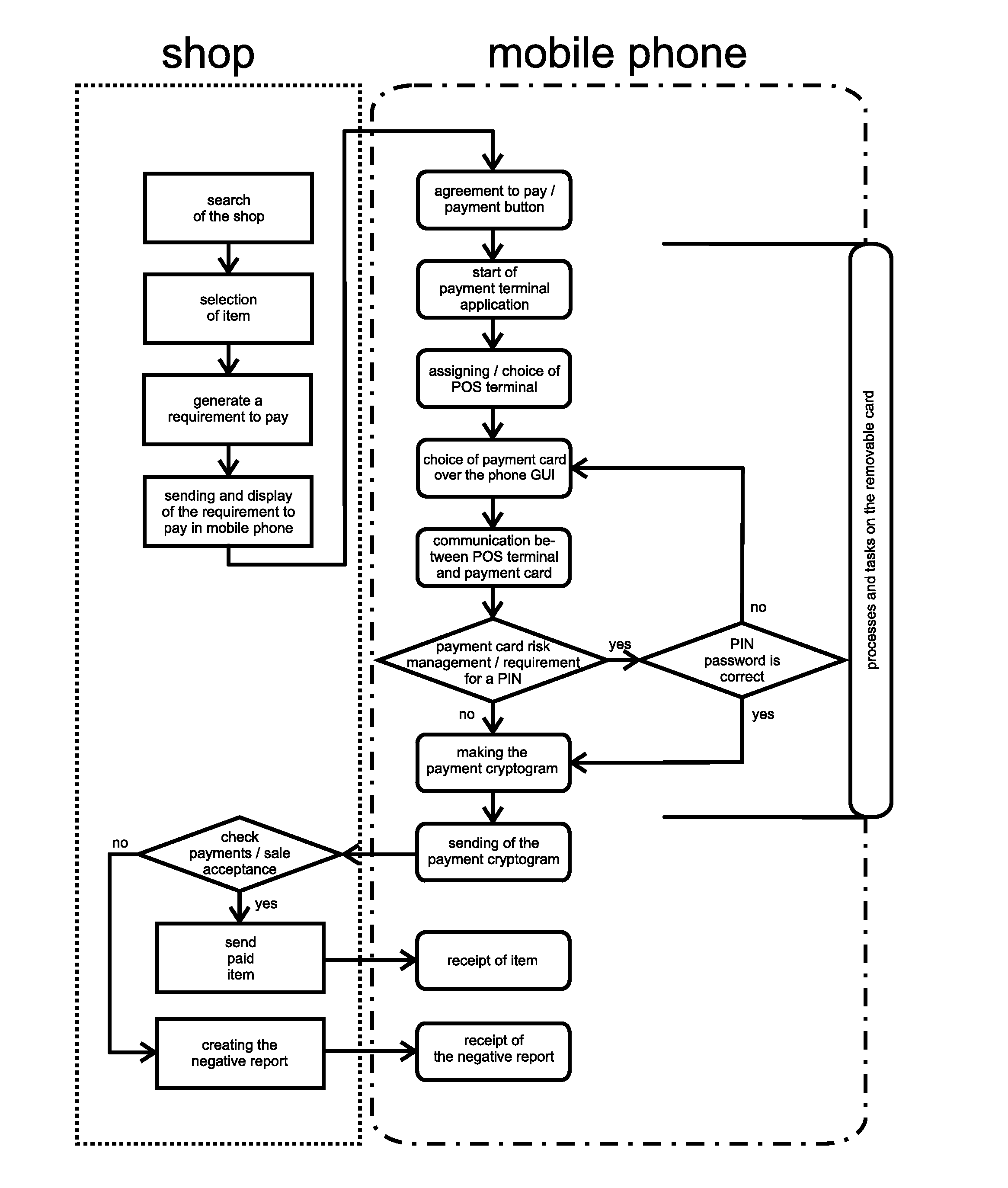
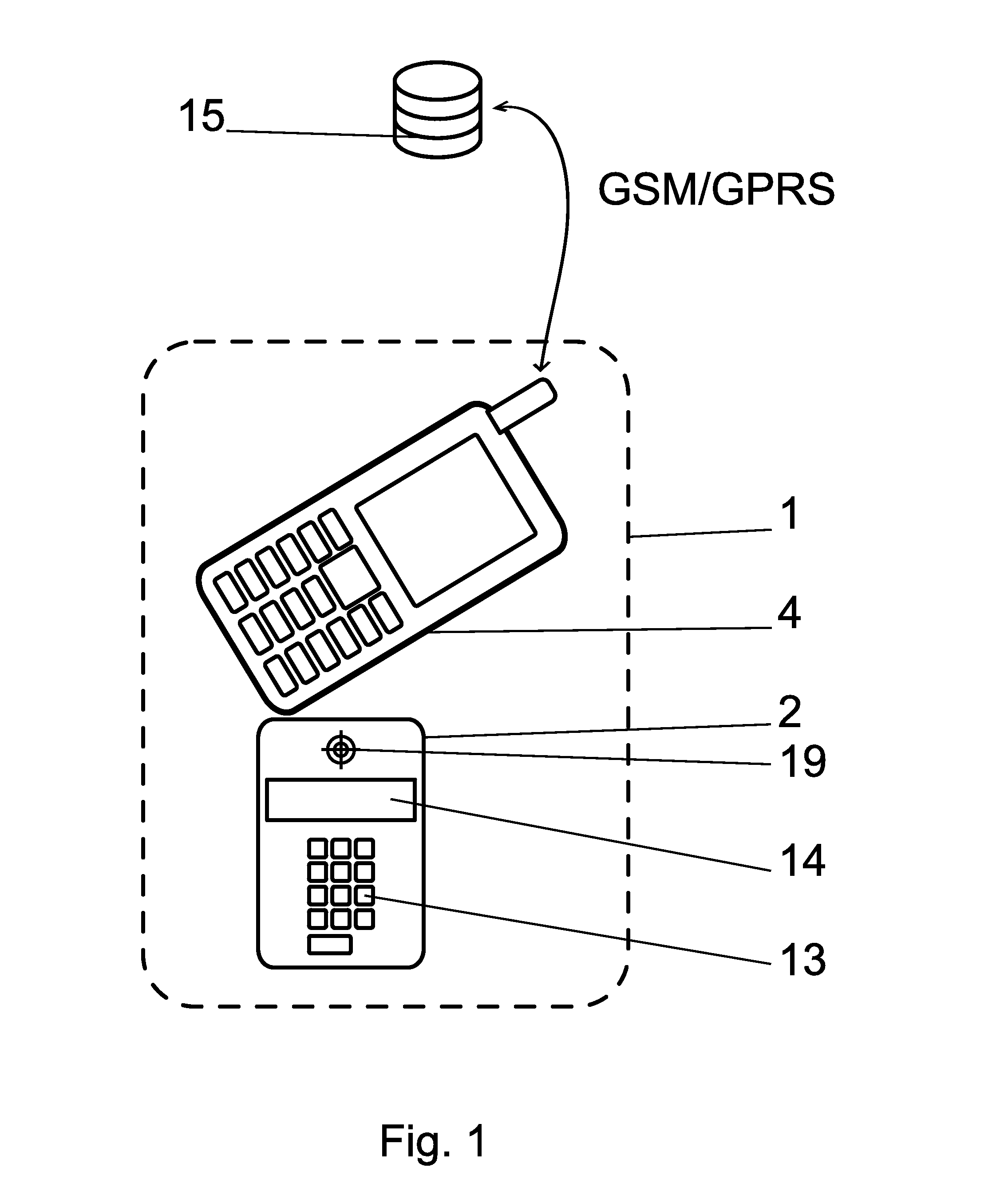
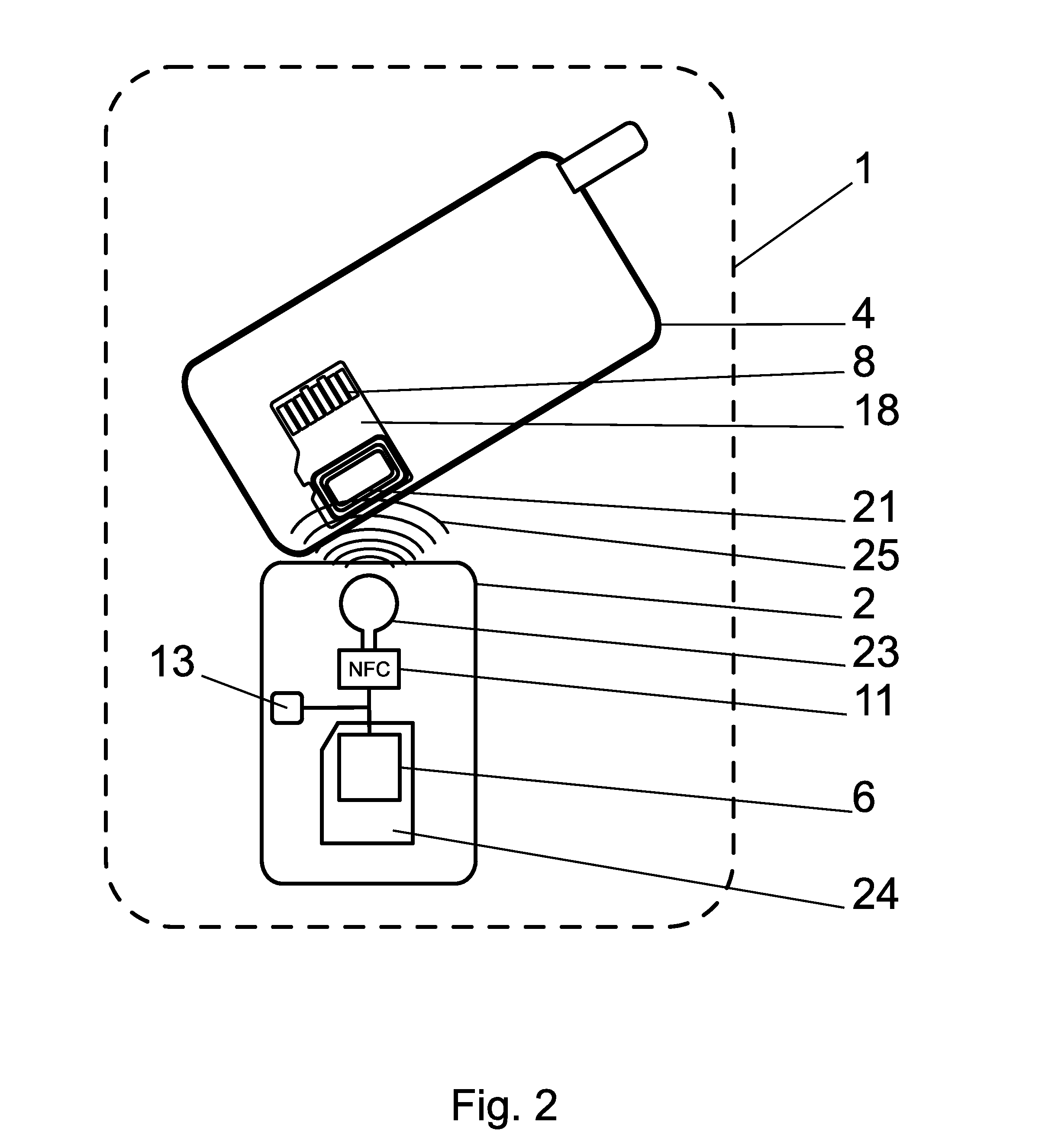
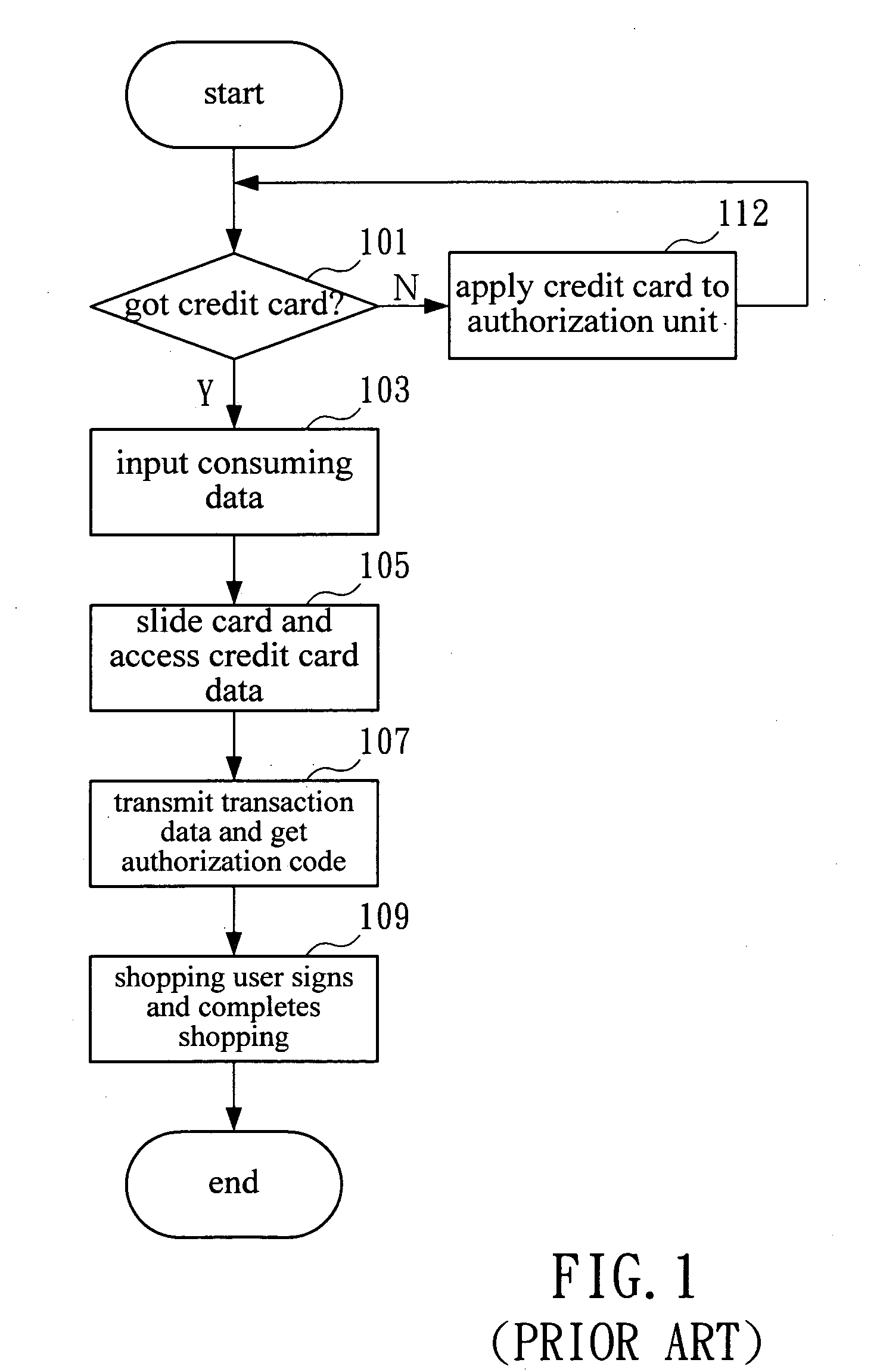
POS payment terminal and a method of direct debit payment transaction using a mobile communication device, such as a mobile phone
InactiveUS20110112968A1Solve insufficient capacityImprove security levelAcutation objectsAccounting/billing servicesDirect debitPayment transaction
A payment terminal using a mobile communication device (4), such as a mobile phone, is located on a removable memory card (1), e.g. type microSD card, which is adjusted in such a way so it can be inserted into an additional hardware slot, e.g. memory slot. A payment POS terminal application runs on a removable memory card (1), which contains at least one payment card. The payment card's unit (7) with the card's payment application is located in the secured part of the memory, separately from the terminal's configuration data unit (6). The configuration data of the terminal's selected identity and the payment card's data are located in the separate parts of the secure element or in completely independent secure elements or they can also be localized in the Sales Device of the merchant and there e.g. within the ICC card (29) or SAM card (42).
Owner:SMK CORP
Distributive access controller
ActiveUS20040025052A1Provide securityConvenient access controlDigital data processing detailsUnauthorized memory use protectionComputer resourcesComputerized system
A device for securely controlling communications among or within computers, computer systems, or computer networks, comprising: (a) a primary access port to which an "owner" computer program, computer, computer system, or computer network is connectable to access shared computer resources; (b) a secondary access port to which a non-owner computer program, computer, computer system, or computer network is connectable to access the shared computer resources; (c) a transfer port to which a shared computer resource is connectable to provide controlled access to that computer resource from computer programs, computers, computer systems, or computer networks connected to the access ports; and (d) a separate physical communication path to and from each access port and each transfer port, where access permissions and restrictions for each communication path are set by the owner of the device through the primary access port.
Owner:SECUREEDEN LLC
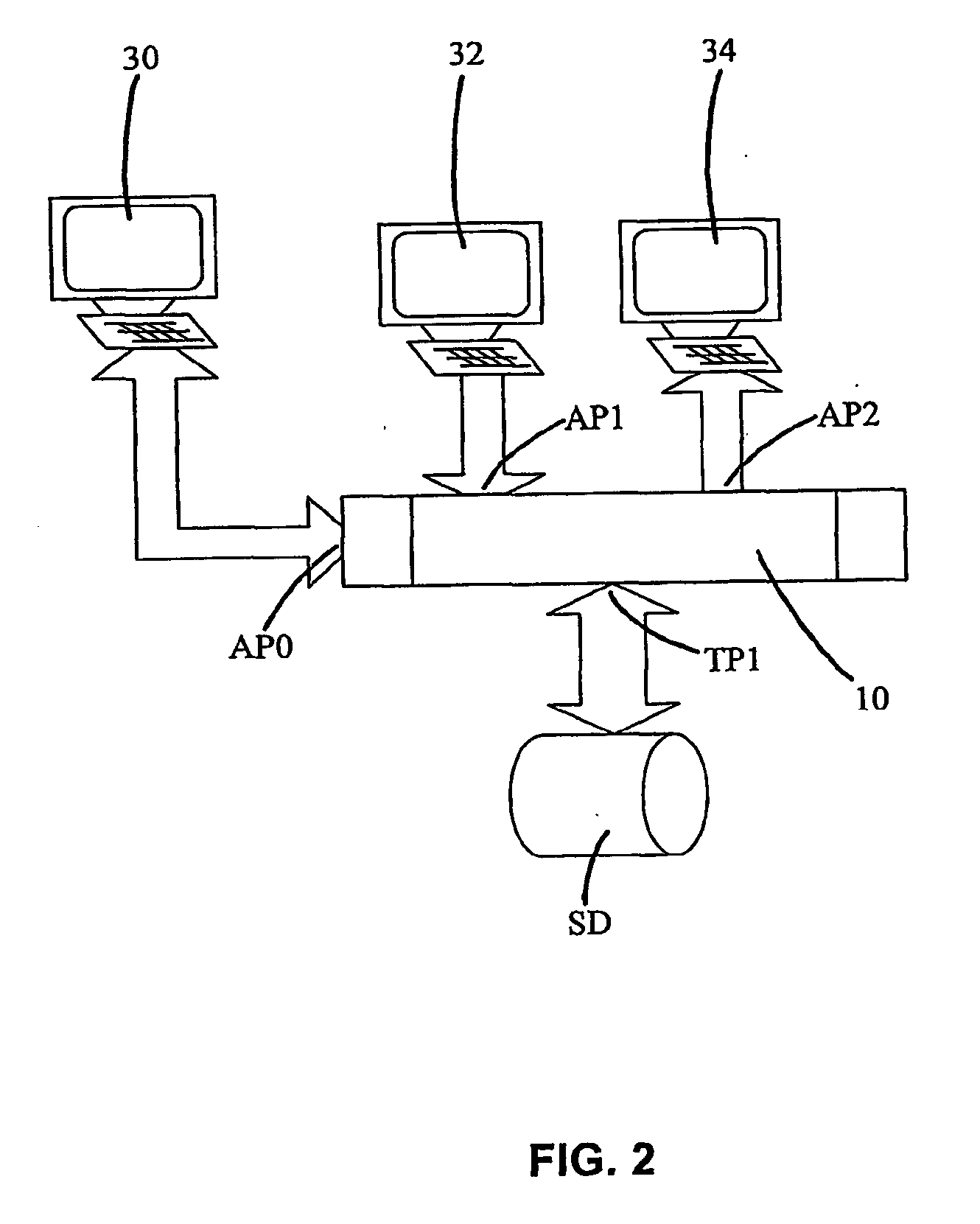
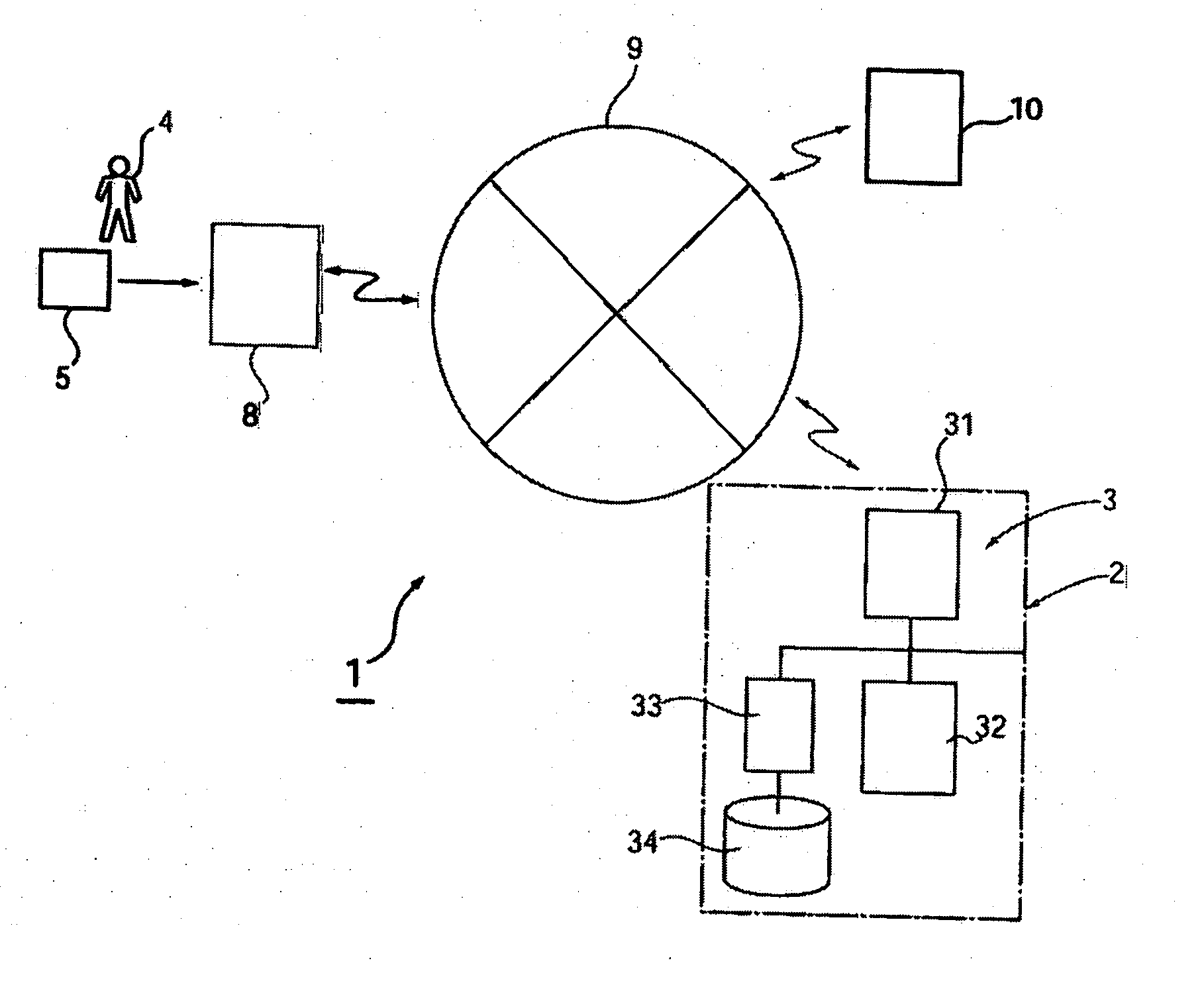
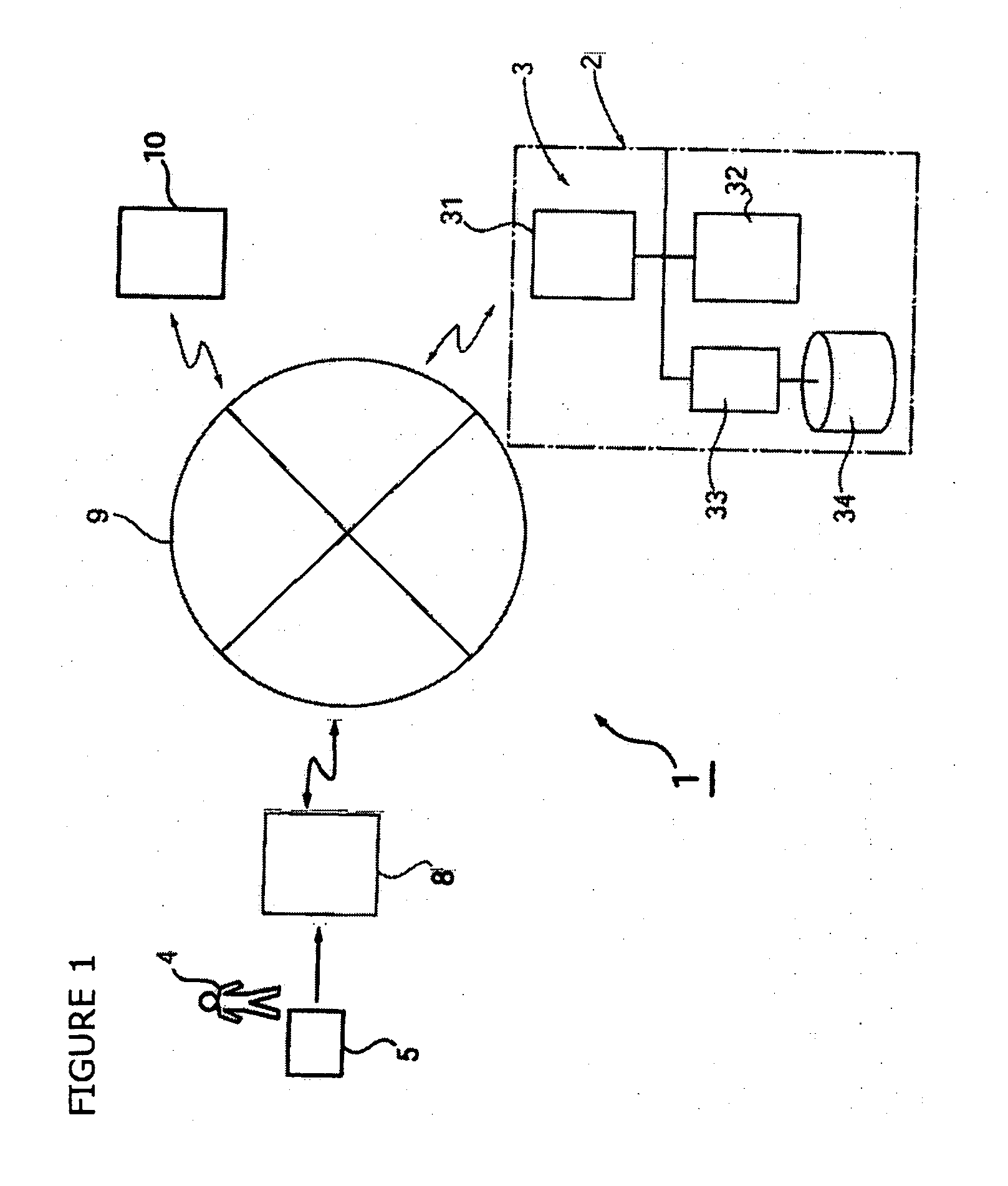
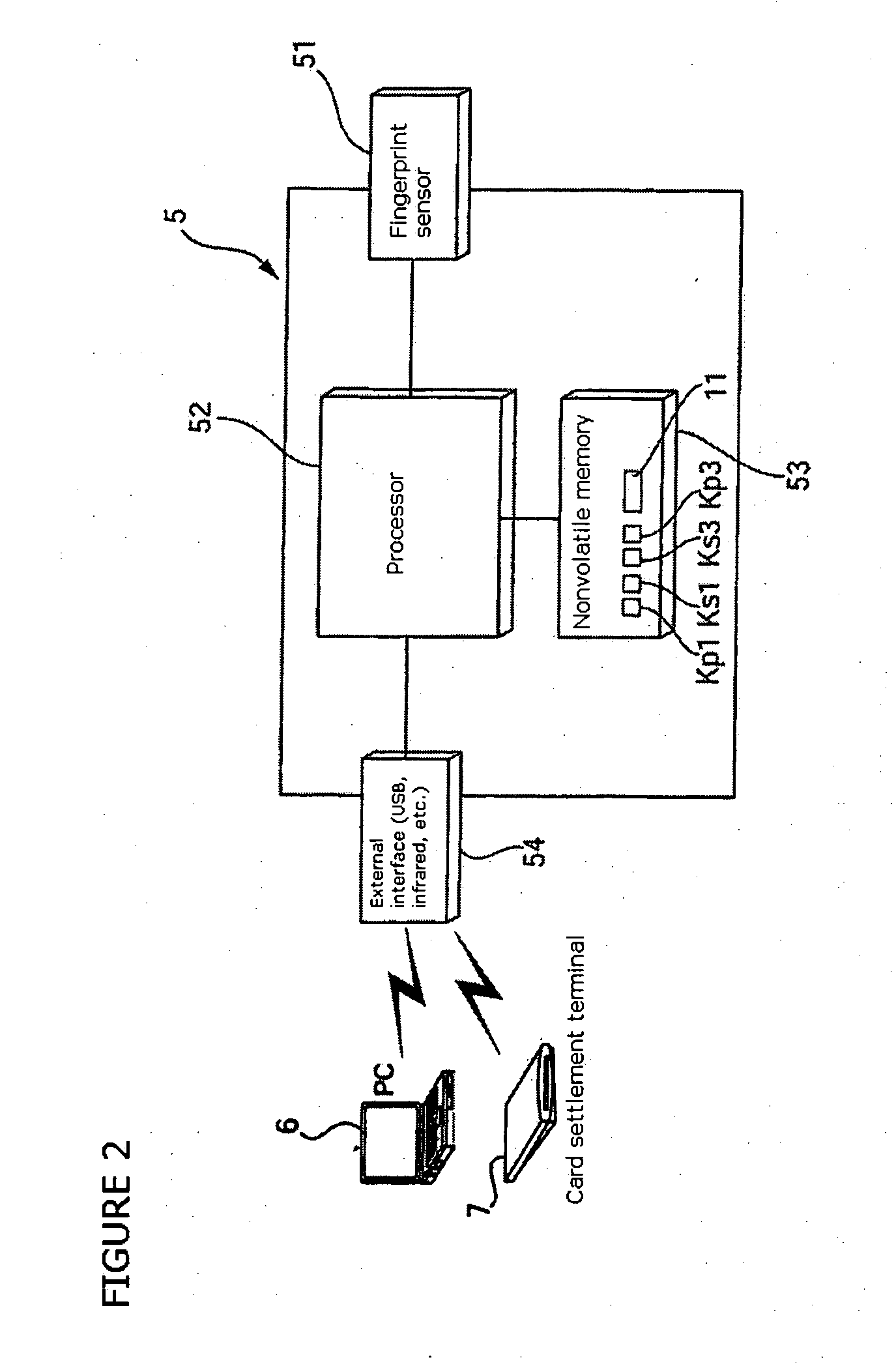
Card settlement method using portable electronic device having fingerprint sensor
InactiveUS20060229988A1Improper useEnsure confidentialityComputer security arrangementsIndividual entry/exit registersFingerprintComputer hardware
In a card settlement system using a portable electronic device having a fingerprint sensor, a credit card and a portable electronic device (5) having a fingerprint sensor are issued to a person who has made application. To this electronic device (5), card information (12), a storage public key Kp1, and
Owner:PARA3
Method for managing distributed trading data
InactiveUS20090281954A1Protect interestsAvoid misuseFinancePayment architectureData providerTransaction data
In a preferred embodiment, the invention comprises a computer-implemented system and method of managing market information across a network of data providers, comprising the steps of: (a) electronically receiving first data including confidential information regarding market participants in a first system that protects said first data behind a firewall; (b) electronically receiving second data including confidential information regarding market participants in a second system that protects said second data behind a firewall; (c) electronically receiving an order and targeting parameters from a first market participant; (d) electronically issuing an advertisement request message to said first system and said second system, said advertisement message comprising display attributes of said order and comprising said targeting parameters; (e) electronically prompting said first system and said second system via the advertisement request message to each send a coordination request message to a Coordination Hub, said coordination request message comprising information deduced from said confidential information regarding market participants in said first and second systems, wherein the selection of the information that is sent to the Coordination Hub is based at least in part on said first market participant's targeting parameters; (f) electronically prompting based on the coordination request message said Coordination Hub to issue permissions to advertise the order to selected market participants, wherein market participants are selected based, at least in part, on said received information regarding market participants; and (g) electronically prompting based on the permission to advertise the order said first system and said second system to route information about said order from first participant to said selected market participants.
Owner:E XCHANGE ADVANTAGE
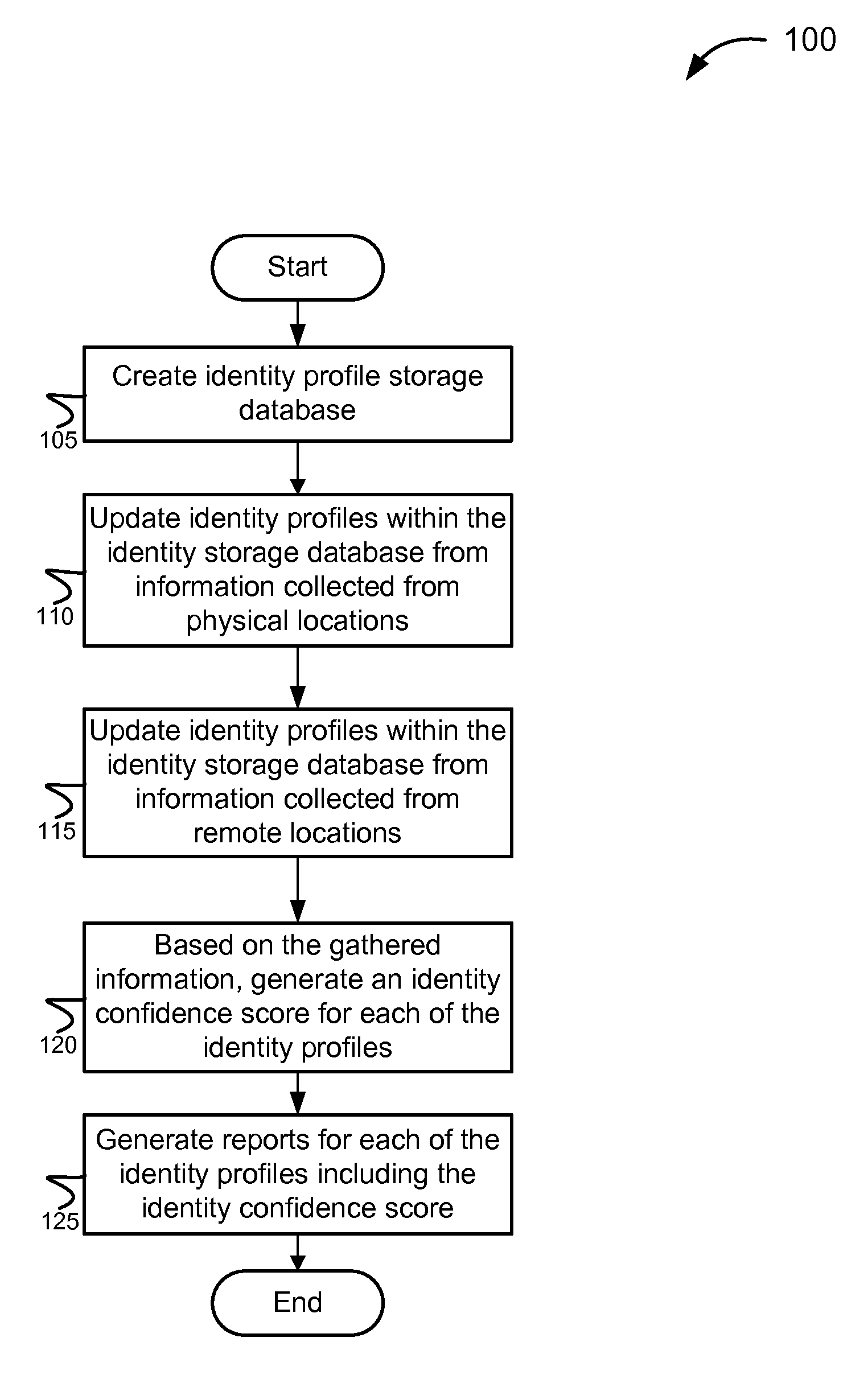
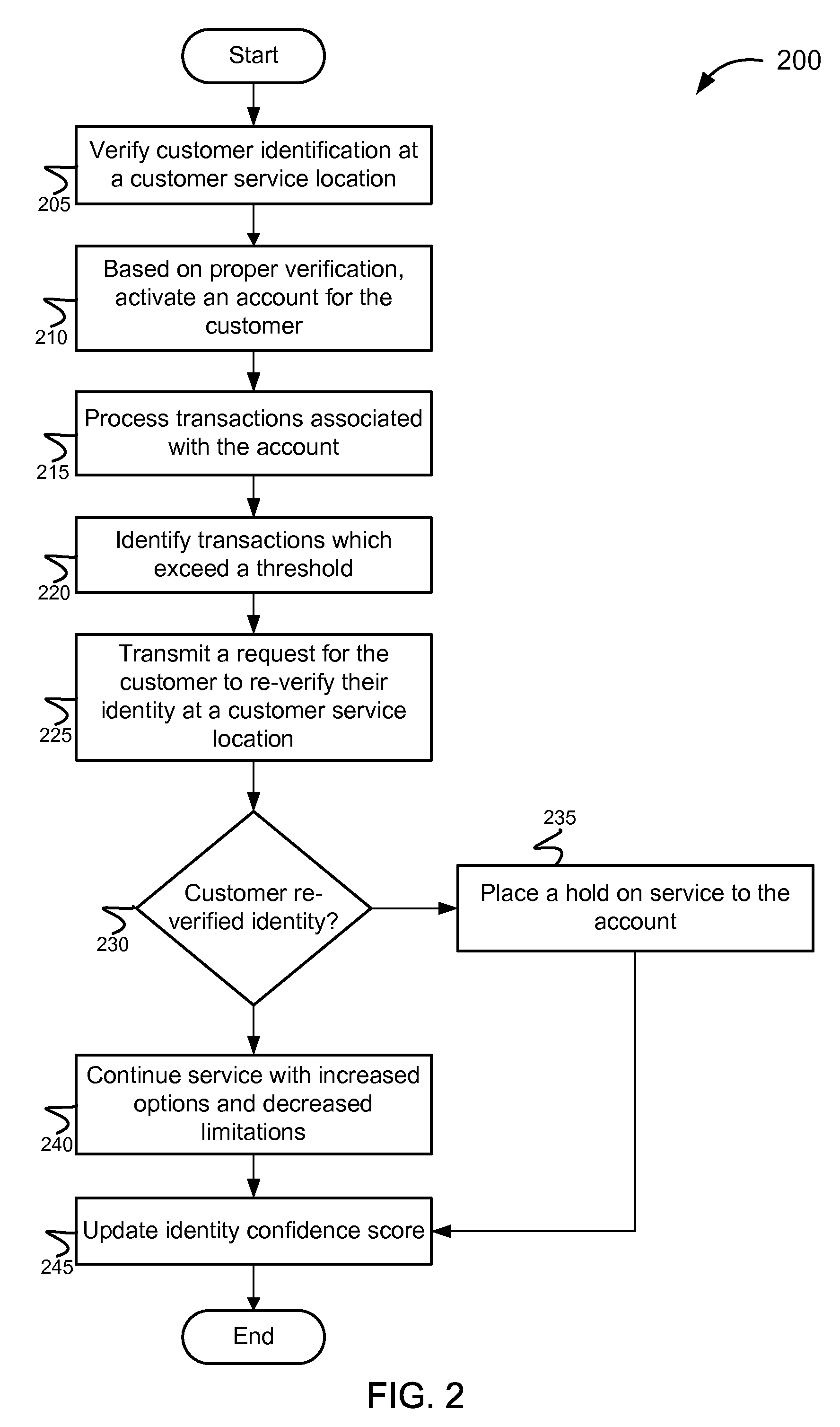
Methods and systems for establishing an identity confidence database
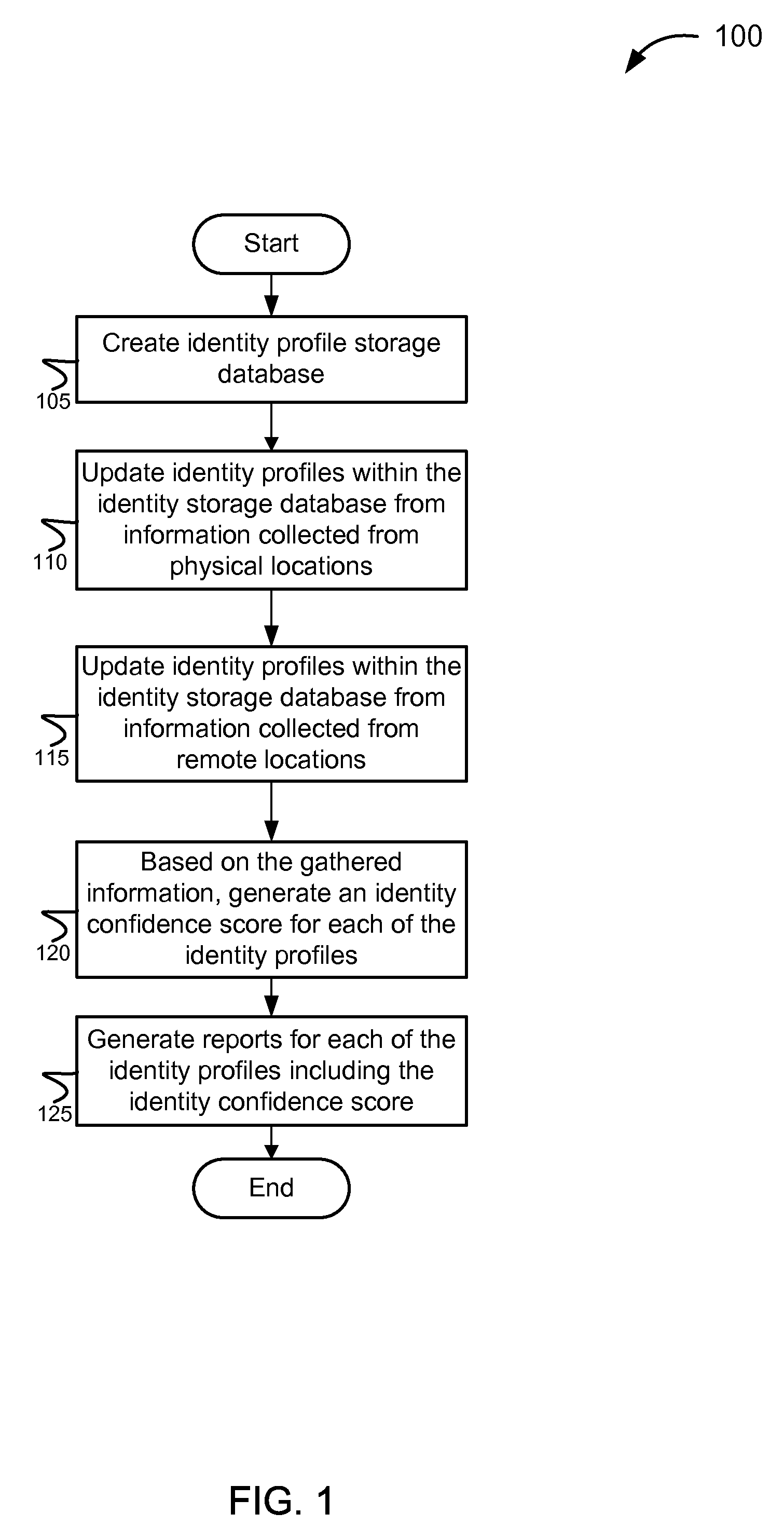
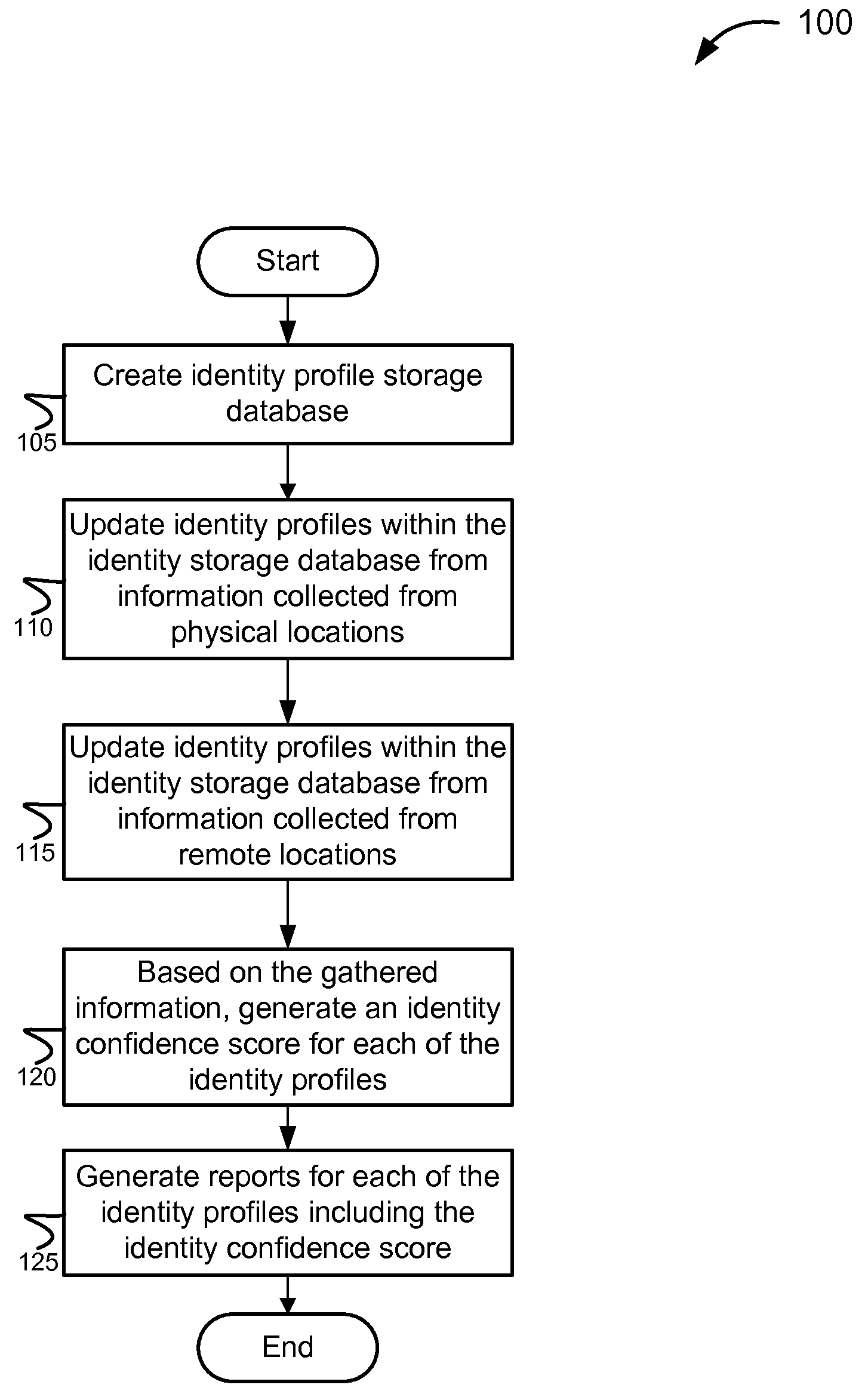
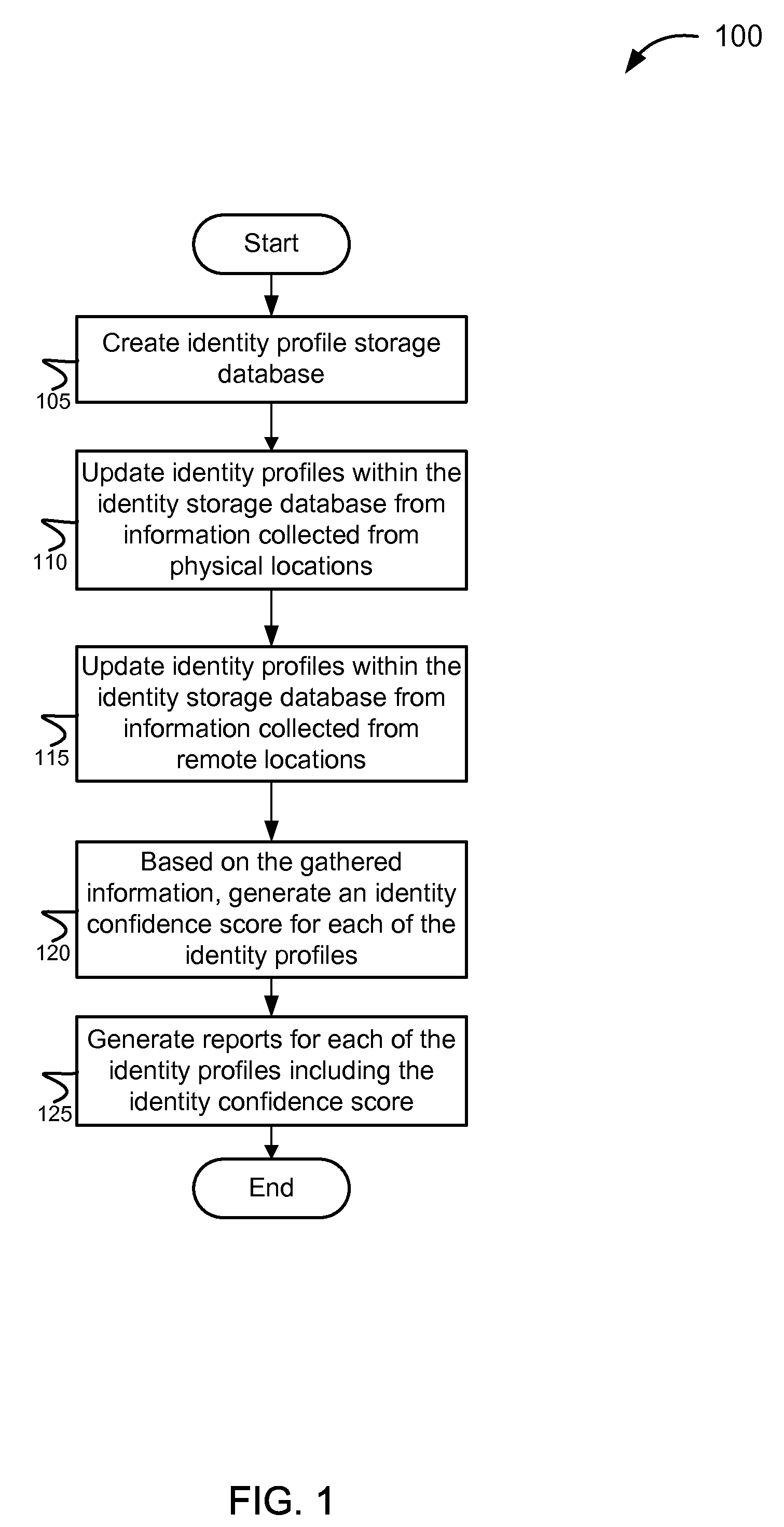
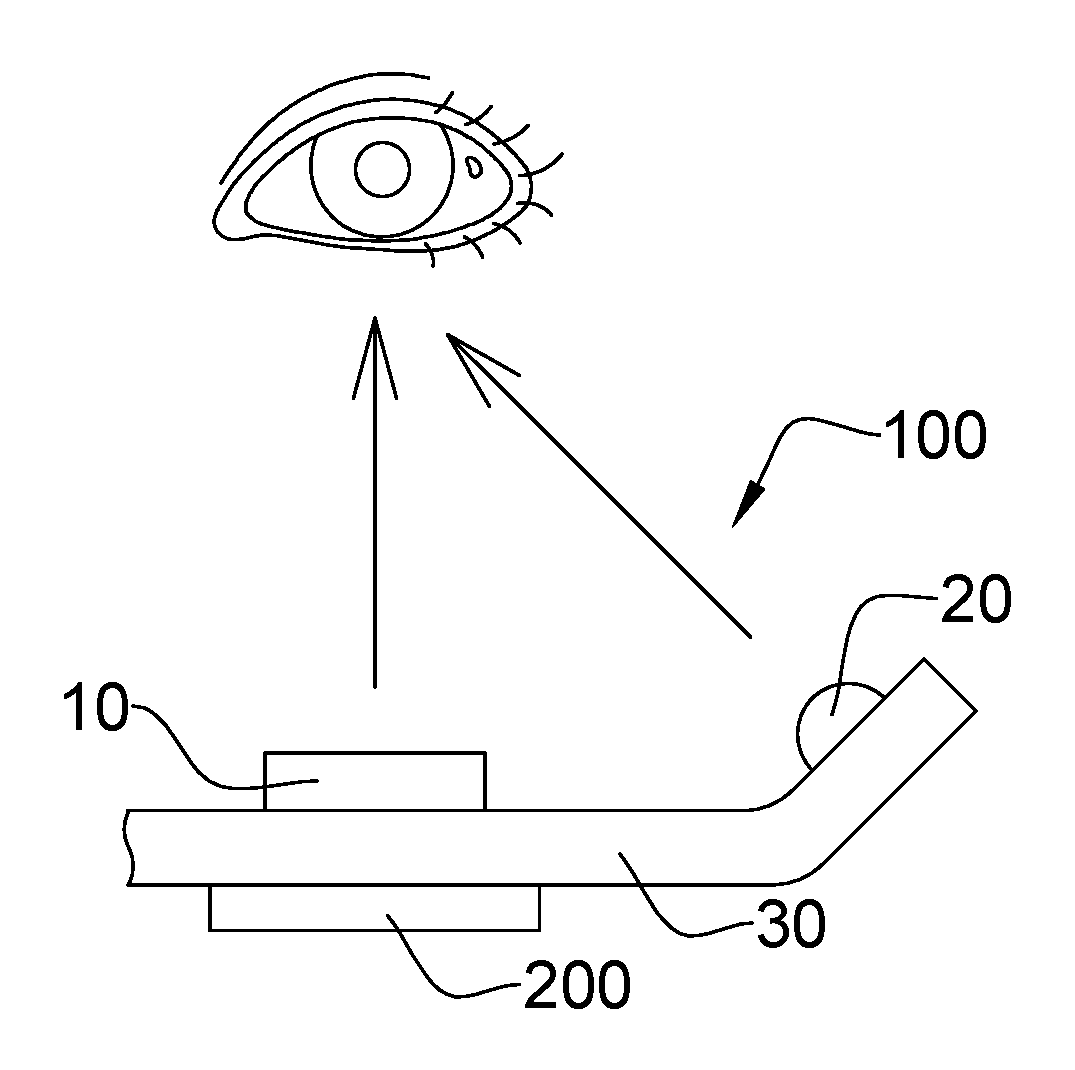
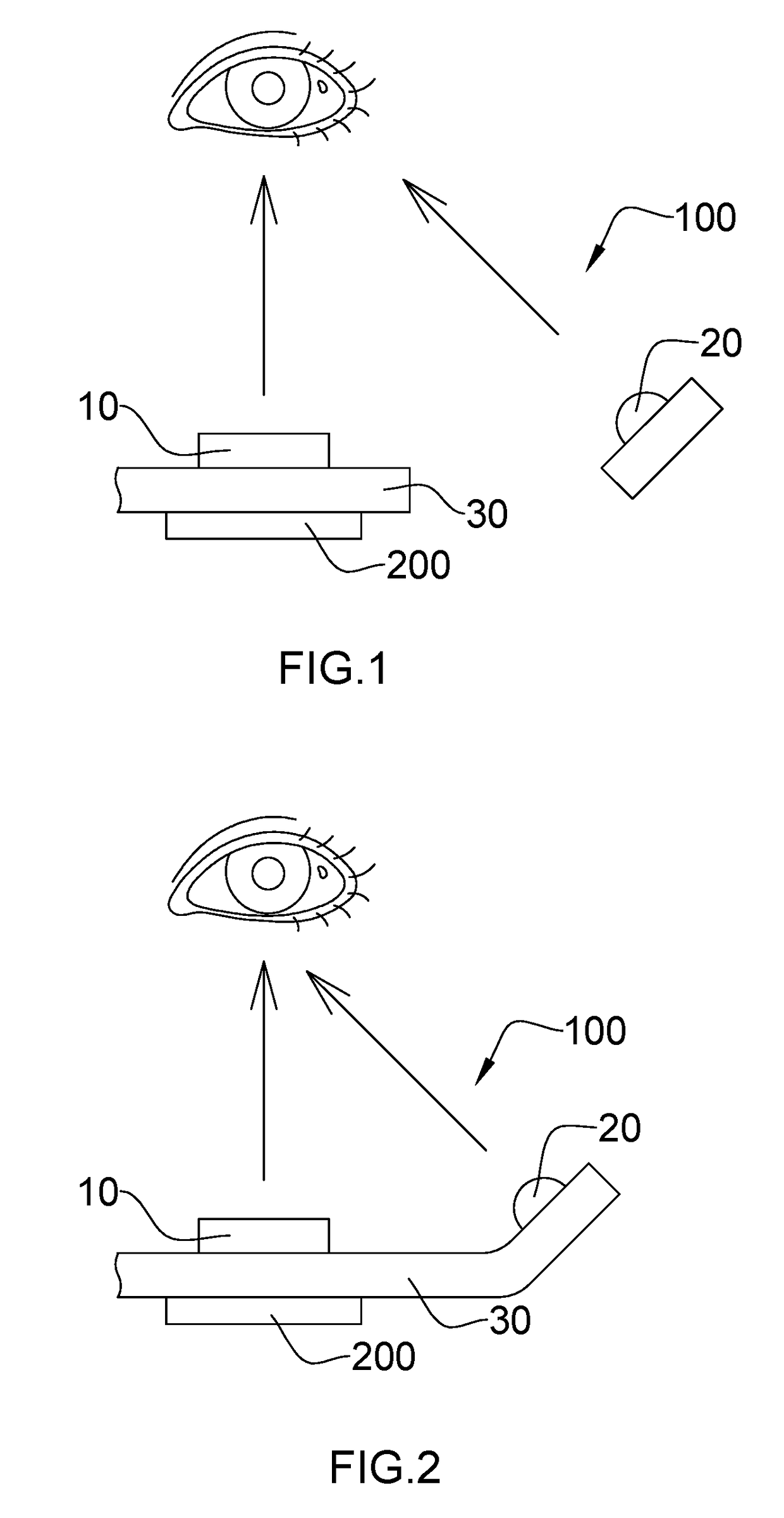
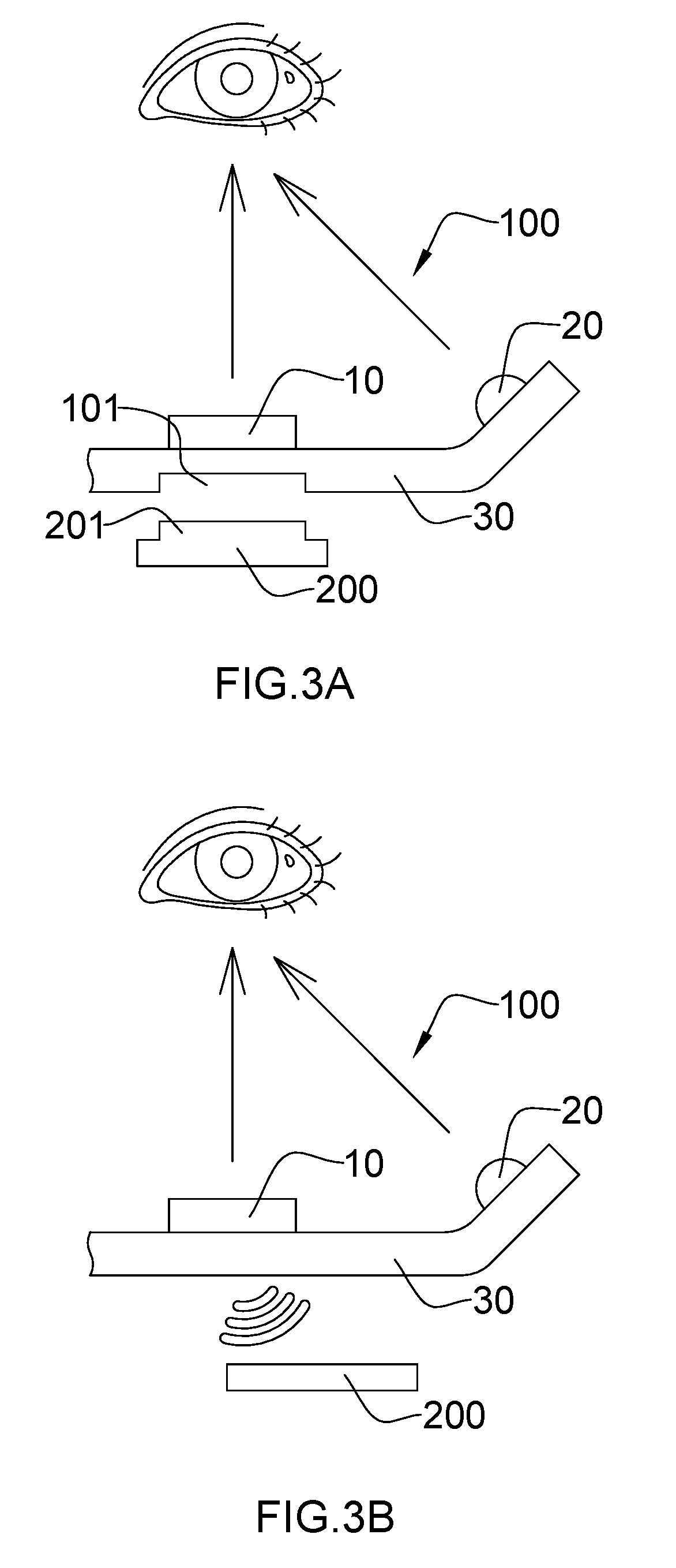
ActiveUS8762288B2Accurate identityConfidenceComplete banking machinesFinanceDatabaseConfidence score
The invention provides various systems and methods for establishing an identity confidence scoring system. The method includes gathering identity information about the customers from physical locations and from remote locations. The method updates the identity profiles with the gathered identity information, and based on the gathered identity information, generates an identity confidence score associated with each identity profile.
Owner:THE WESTERN UNION CO
Methods and systems for establishing an identity confidence database
ActiveUS20100274597A1Building confidenceAccurate identityComplete banking machinesFinanceConfidence factorDatabase
The invention provides various systems and methods for establishing an identity confidence scoring system. The method includes gathering identity information about the customers from physical locations and from remote locations. The method updates the identity profiles with the gathered identity information, and based on the gathered identity information, generates an identity confidence score associated with each identity profile.
Owner:THE WESTERN UNION CO
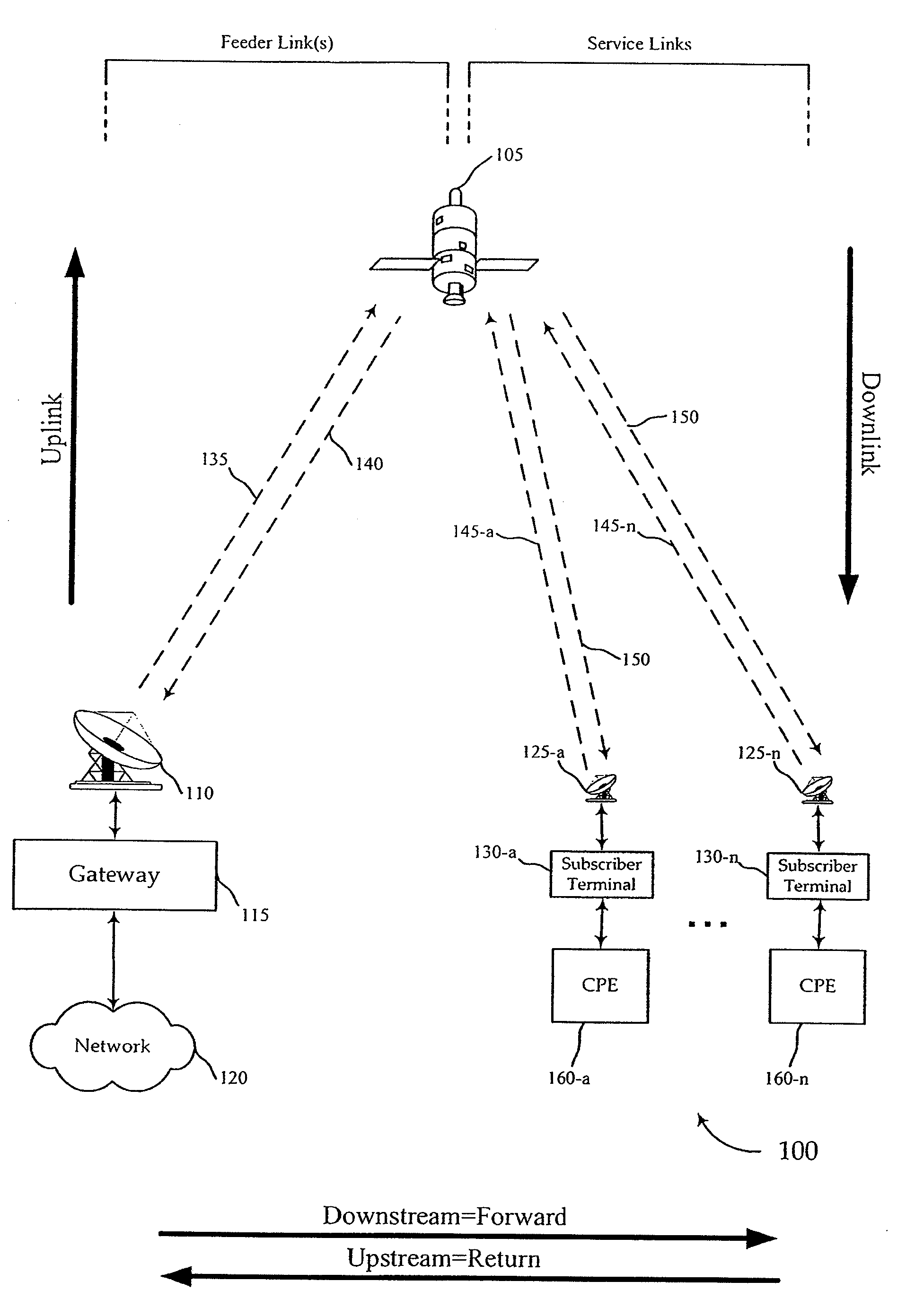
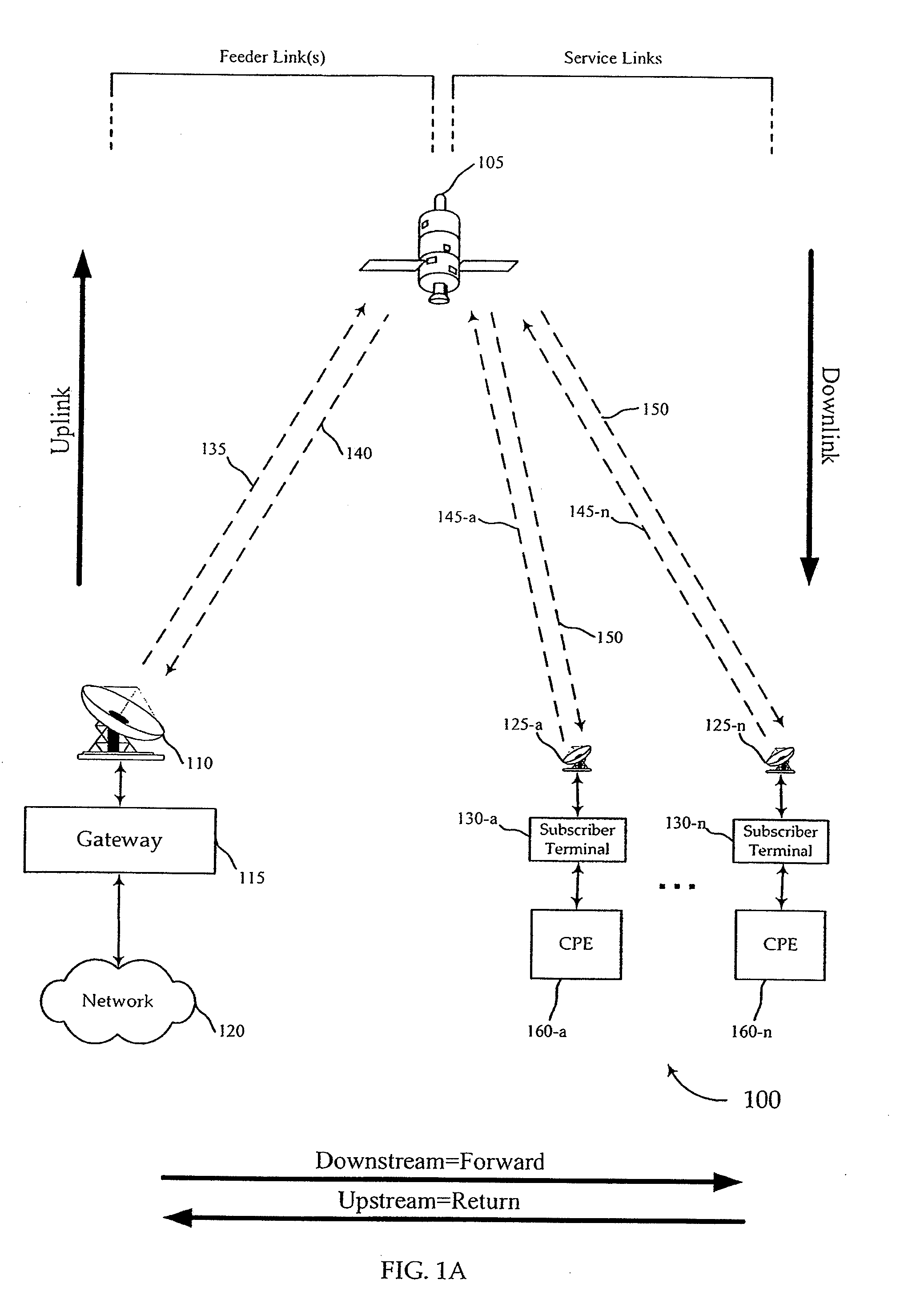
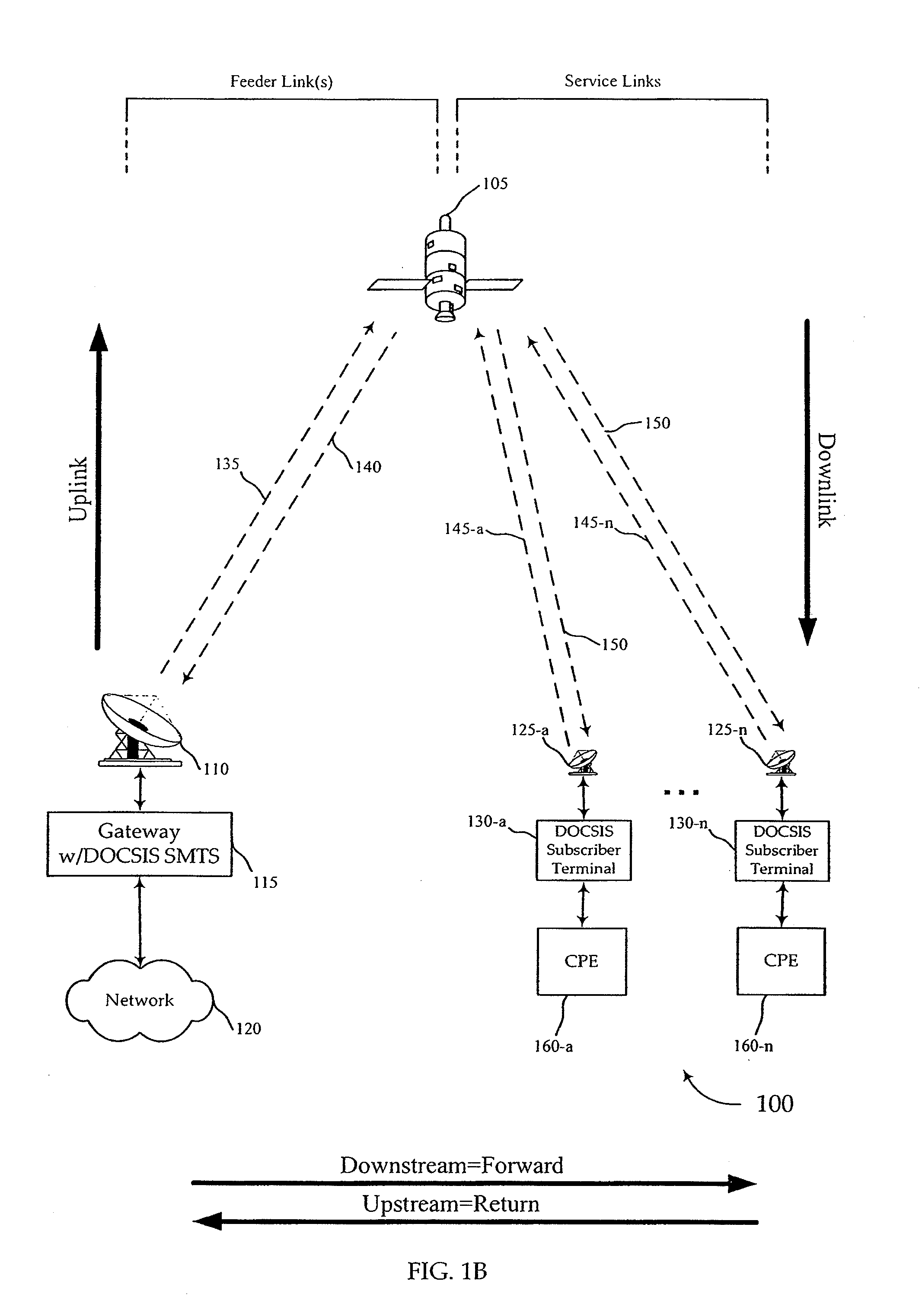
Multi-service provider authentication
InactiveUS20100037308A1Accurate identityUser identity/authority verificationMultiple digital computer combinationsEmbedded securityModem device
Network access providers implement interactive procedures and subscriber terminals employ embedded secure authentication structures and procedures to ensure that a satellite modem at the subscriber terminal accurately verifies the identity of a satellite modem terminal system at the location of the network access provider gateway facility during the satellite modem initialization process so that the satellite modem will only attempt to acquire satellite resource from the appropriate (authenticated and authorized) satellite modem termination system. In a virtual downstream channel environment, diverse downstream channel feeds are distinguished by authentication procedures. The present invention differs from standard theft of service prevention because theft of subscriber prevention is in a virtual channel environment, where subscriber terminals have access to a plurality of virtual channels by the nature of the signal.
Owner:VIASAT INC
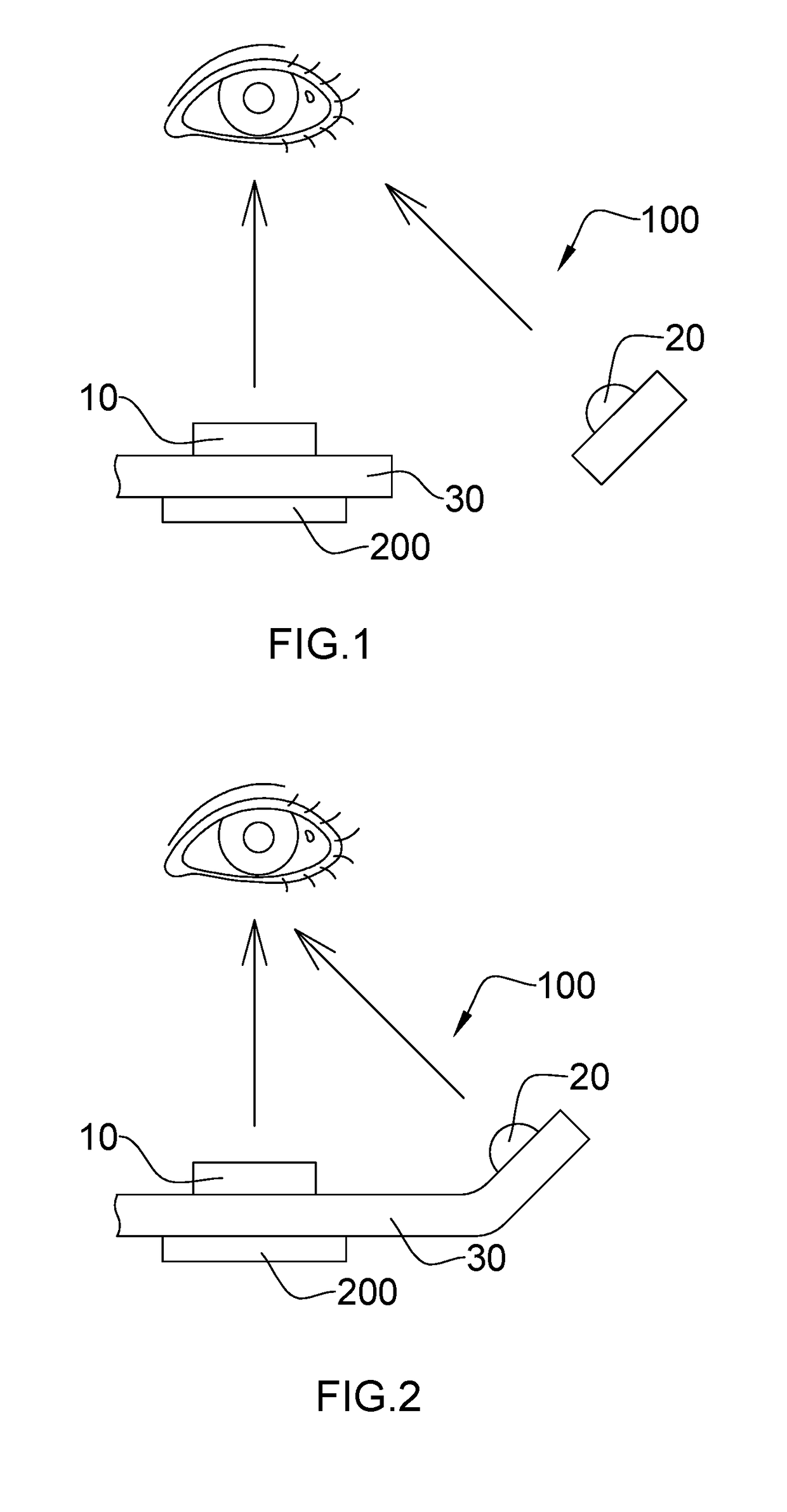
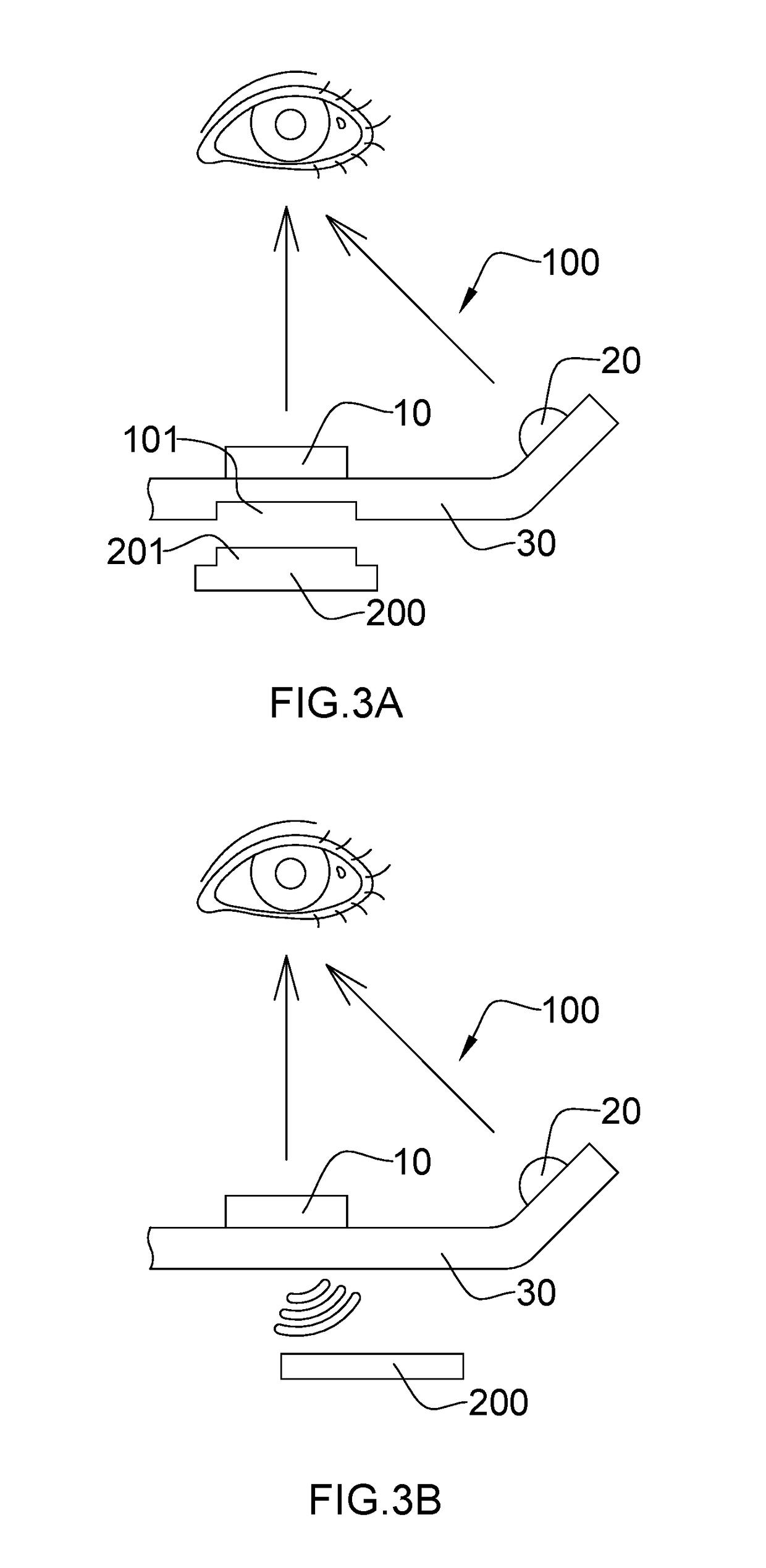
Iris Recognition Device, Manufacturing Method Therefor and Application Thereof
ActiveUS20170124392A1High precisionReduces consumed user identification timeTelevision system detailsAcquiring/recognising eyesLight sourcePupil
The iris recognition device includes an iris camera module used for collecting iris characteristics of a user, and at least one fill light component used for providing a supplementary light source for the iris camera module. When the iris recognition device is used for collecting the iris characteristics of the user, the supplementary light source provided by the fill light component reduces reflective spots on the iris or make reflective spots in areas other than iris such as sclera and pupil, thereby improving precision of the collected iris characteristics of the user.
Owner:NINGBO SUNNY OPOTECH CO LTD
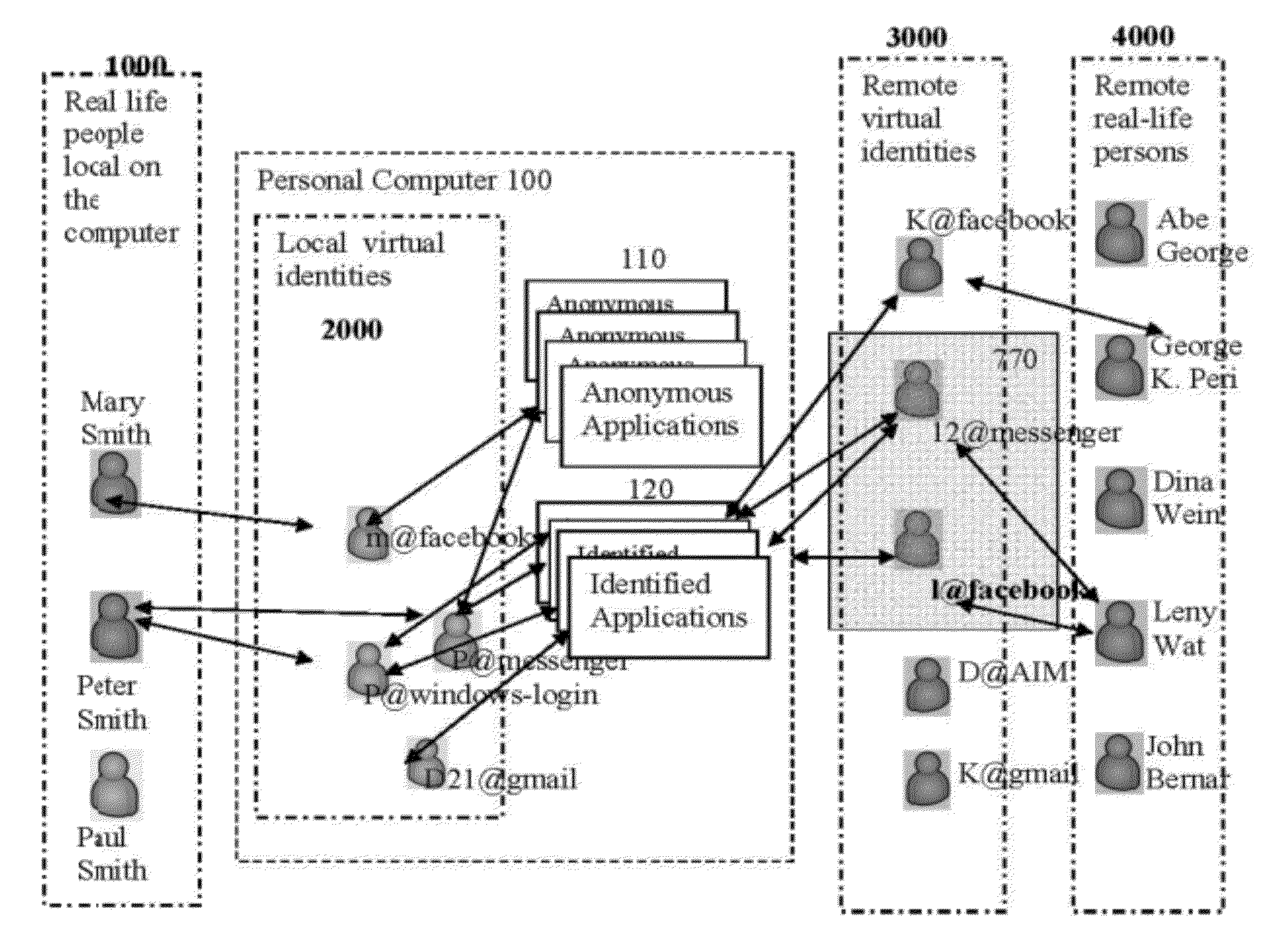
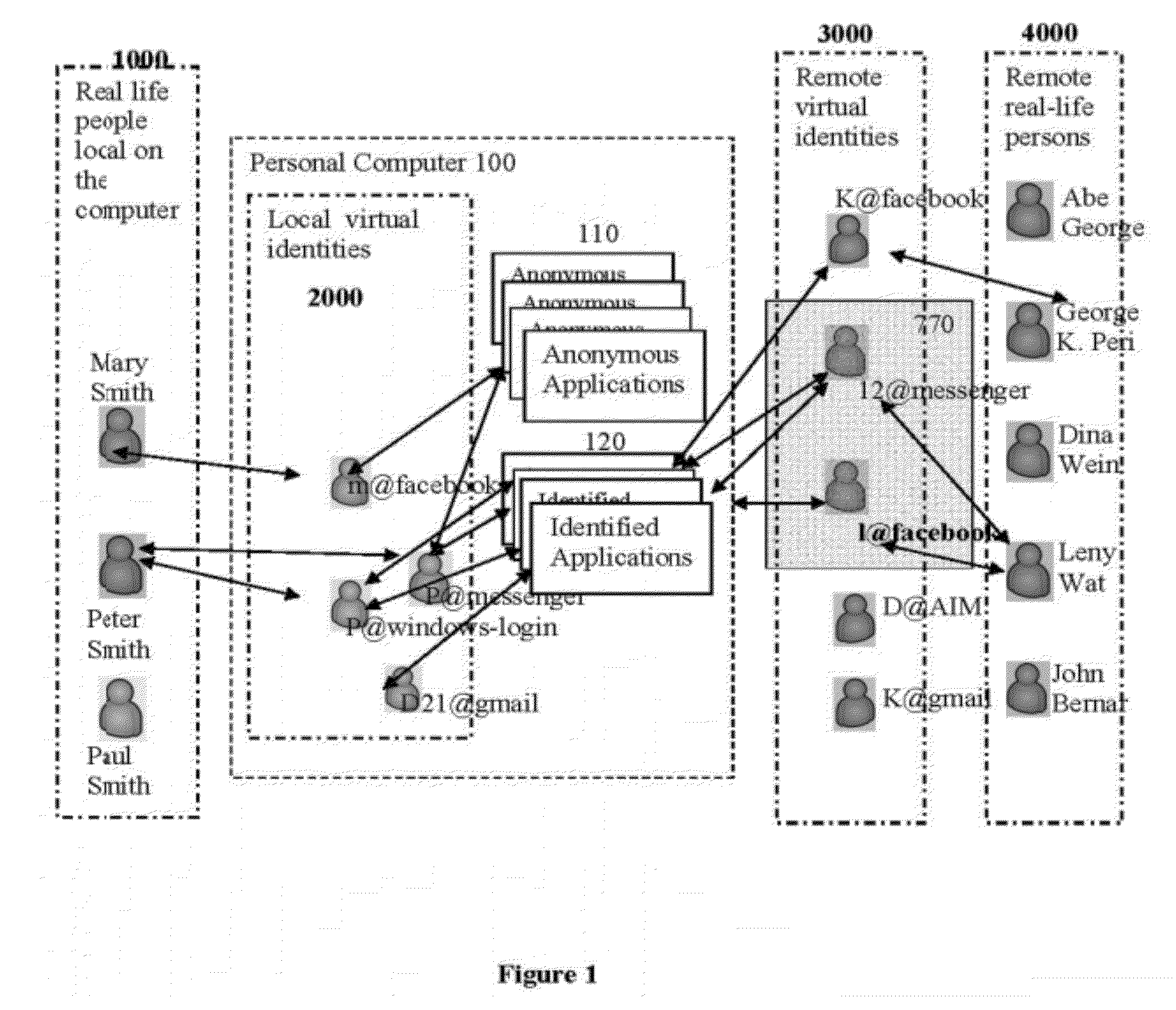
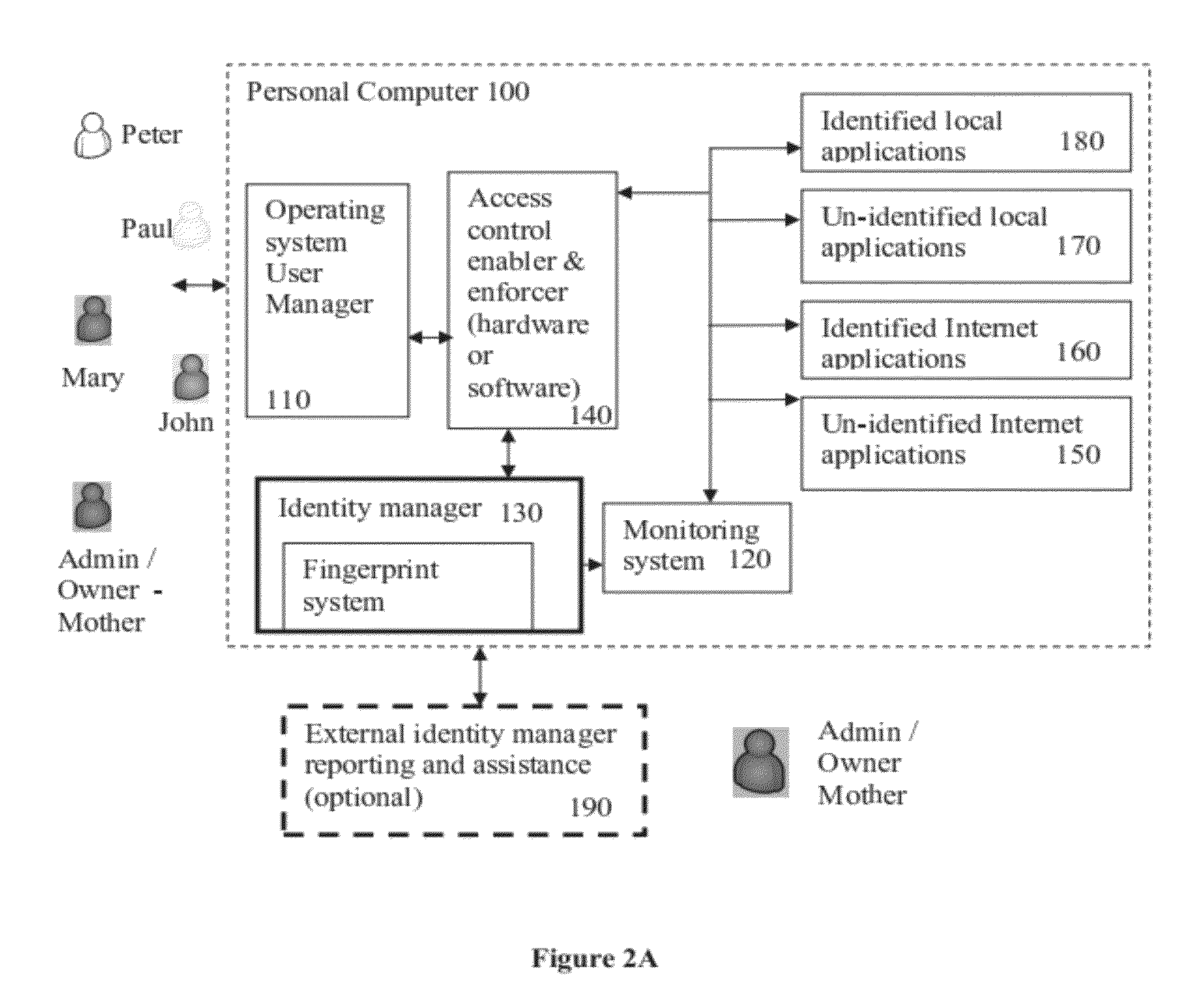
Methods and systems for managing virtual identities
InactiveUS20120317217A1Accurate identityMultiple digital computer combinationsDigital data authenticationHuman–computer interactionCurrent user
A method of monitoring a plurality of user generated interaction sessions. The method comprises providing a list of a plurality of defined users, where each defined user is associated with at least one response to a user-application interaction of a respective defined user with one of a plurality of defined applications accessible via a client terminal, identifying a current user of the client terminal from the plurality of defined users and at least one current interacted application from the plurality of defined applications, selecting a at least one respective response according to the at least one current interacted application and the current user, and triggering the at least one respective response.
Owner:UNITED PARENTS ONLINE
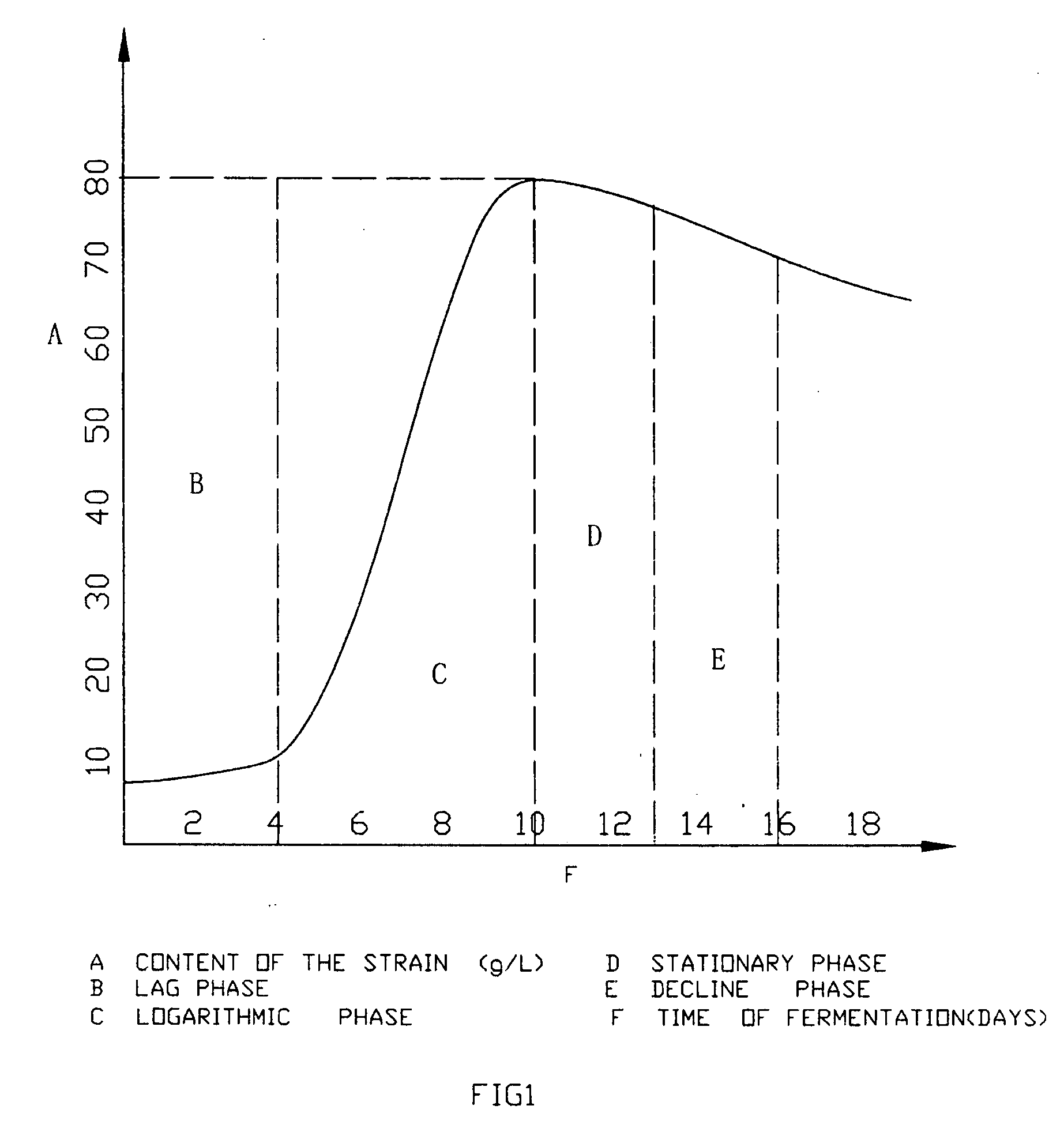
Industrial fermenting production process of Hirsutella hepiali Chen & Shen of anamorphic fungi related to Chinese Cordyceps Sinensis
InactiveUS20070004022A1Wide market prospectYield of the hyphae has been upgradedFungiImmunological disordersBiotechnologyIndustrial fermentation
The present invention discloses a fermenting production process of Hirsutella hepiali Chen & Shen for industrial purpose. It contains steps: a. Isolating new stain from original source; b. identifying whether the stain can grow stroma or not; c. culturing the strain in solid medium for rejuvenescence purpose; d. Secondly culturing the strain in liquid culture medium; e. fermenting. Said method provides a fermenting production process, which can continually identify whether the anamorphic fungi related to Chinese Cordyceps sinensis change or not, whether it retains the property of original strain or not. It also can be modified continually. According to these processes, the quality of the obtained product will be stable and the property will be retained stable for quite a long time. Therefore this method overcome the problems exist in the art that change of the strain, instability of quality of the product and so on.
Owner:SHEN NANYING
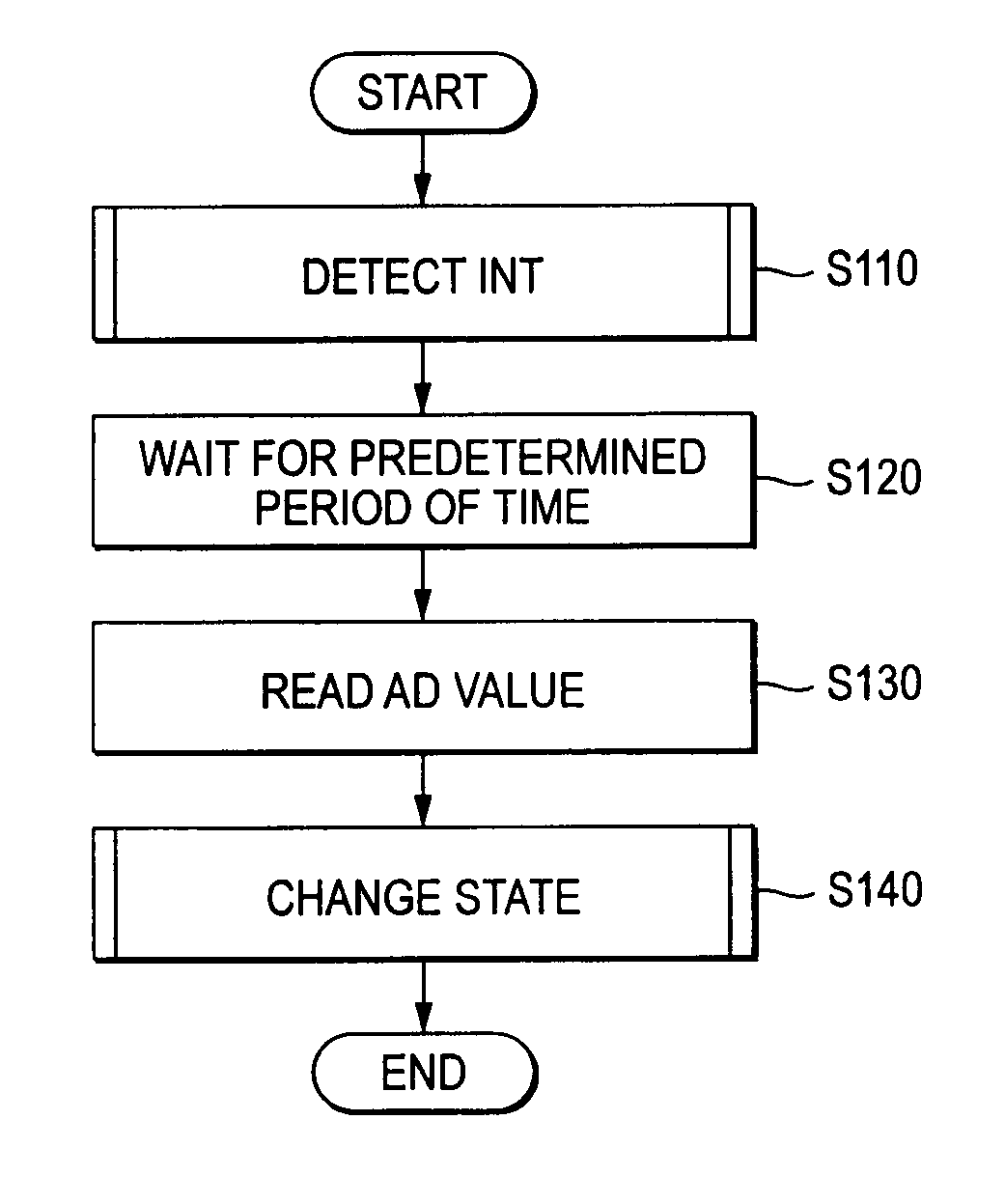
Electronic machine, connected machine identifying method for electronic machine and control system
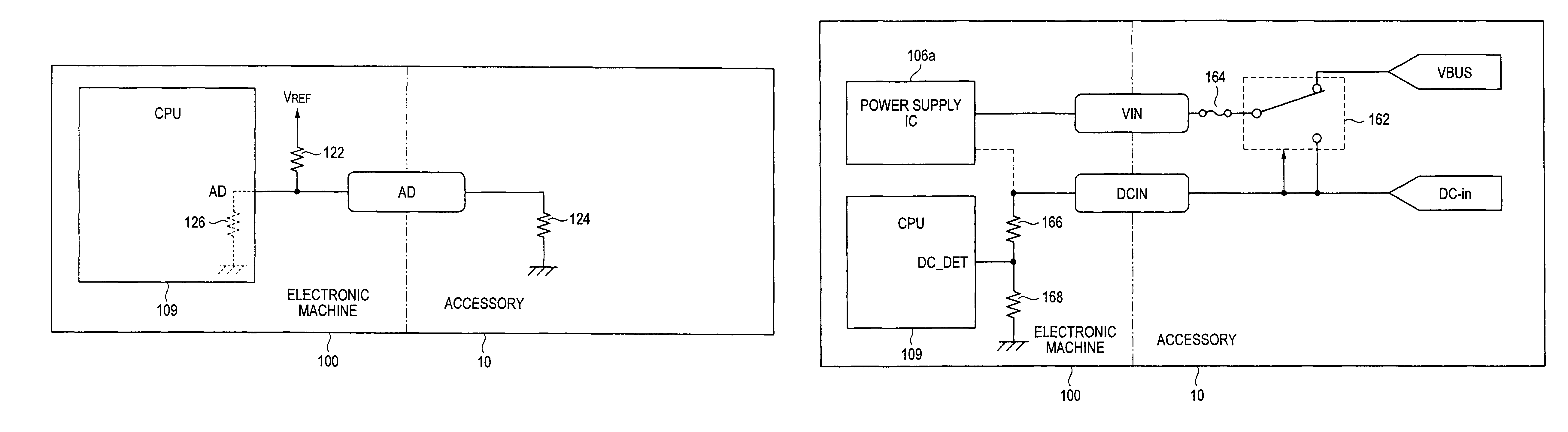
InactiveUS20080246581A1Accurate detectionAccurate identityResistance/reactance/impedenceElectric testing/monitoringElectrical resistance and conductanceControl system
An electronic machine connectable to a different apparatus is disclosed. The electronic machine includes a resistance, a connector to be connected to the different apparatus, and a detecting section that detects one state from multiple states based on the resistance value of the resistance and the resistance value of a resistance included in the different apparatus connected to the connector and controls multiple parameters based on the detected one state.
Owner:SONY CORP
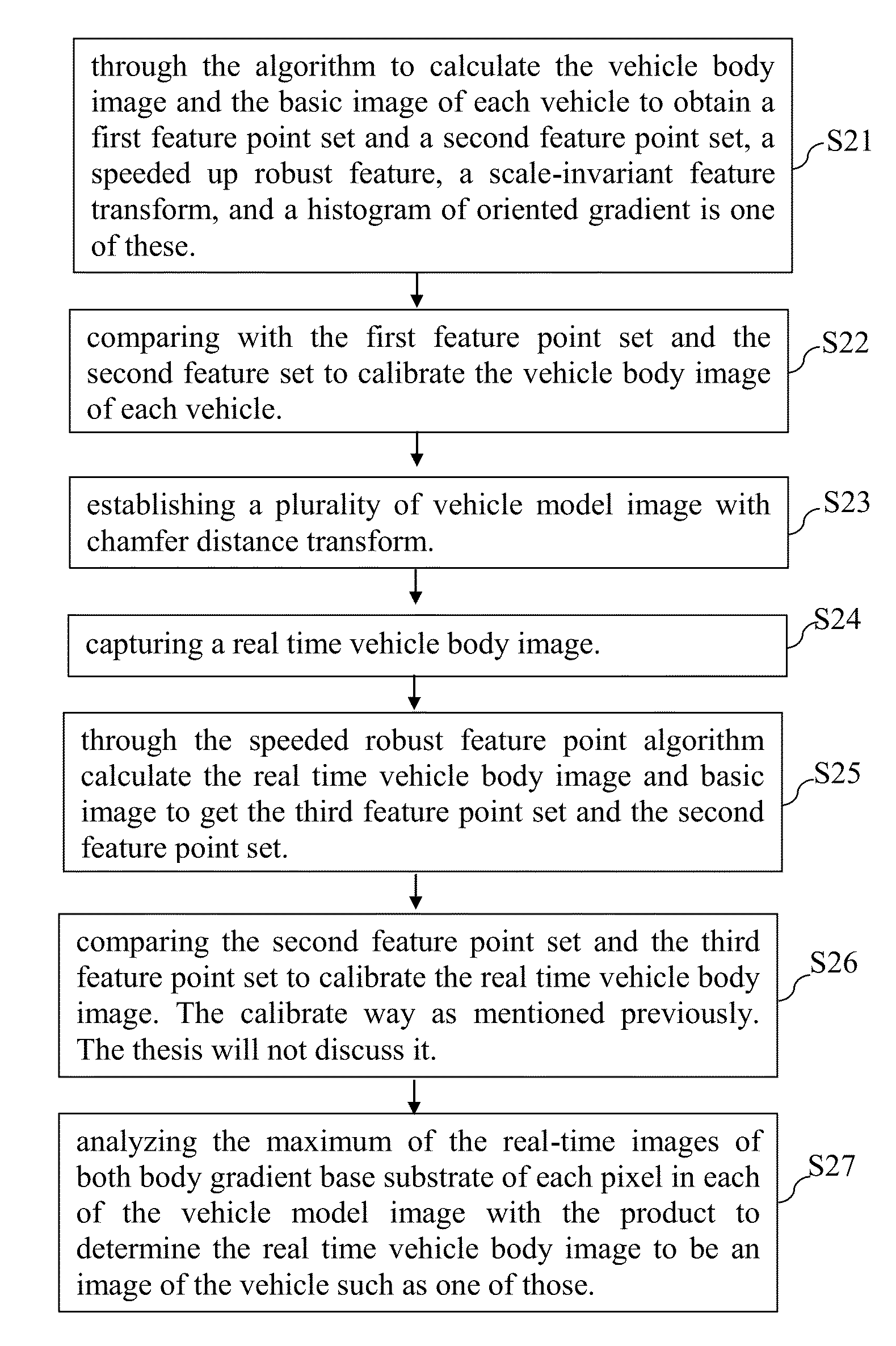
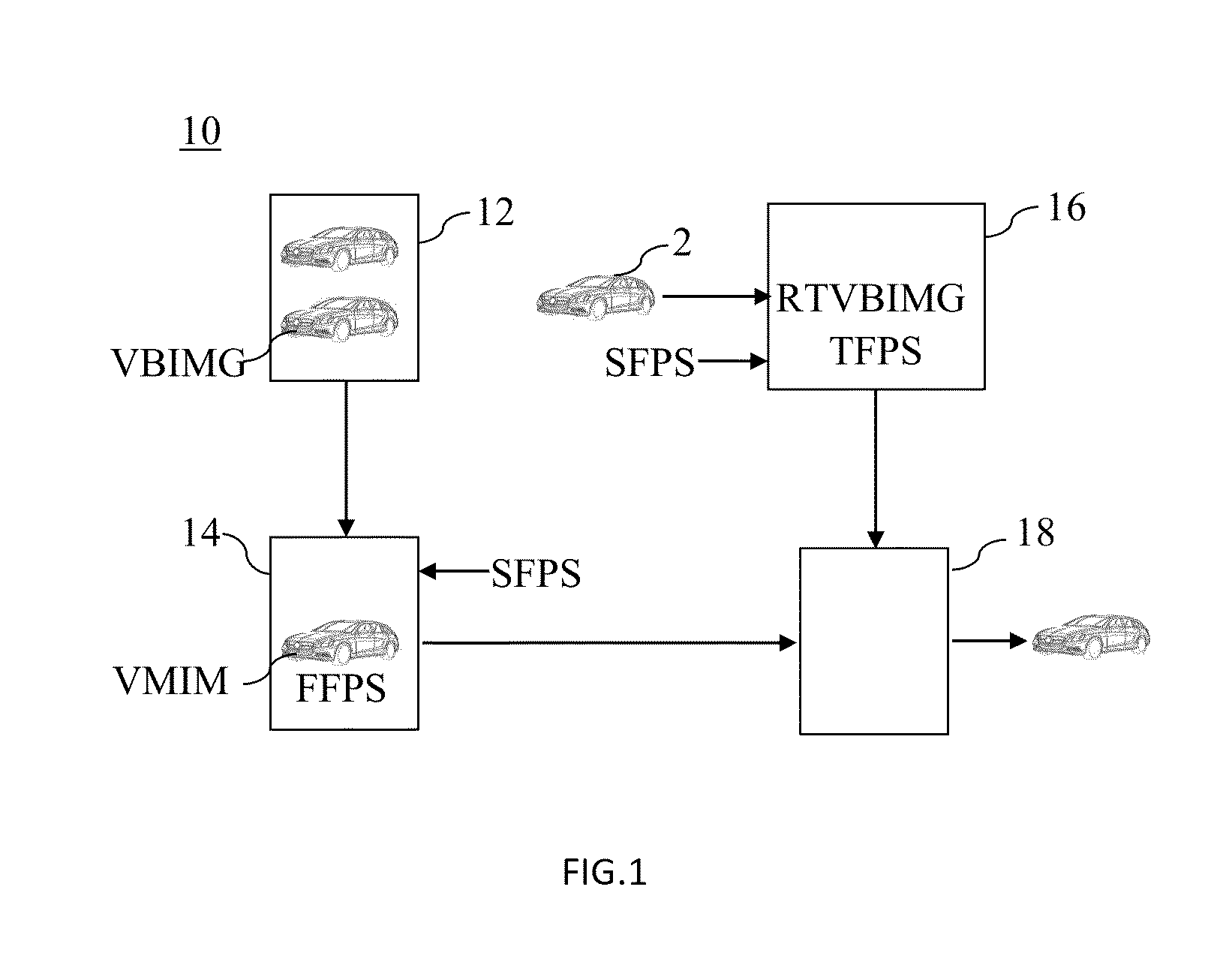
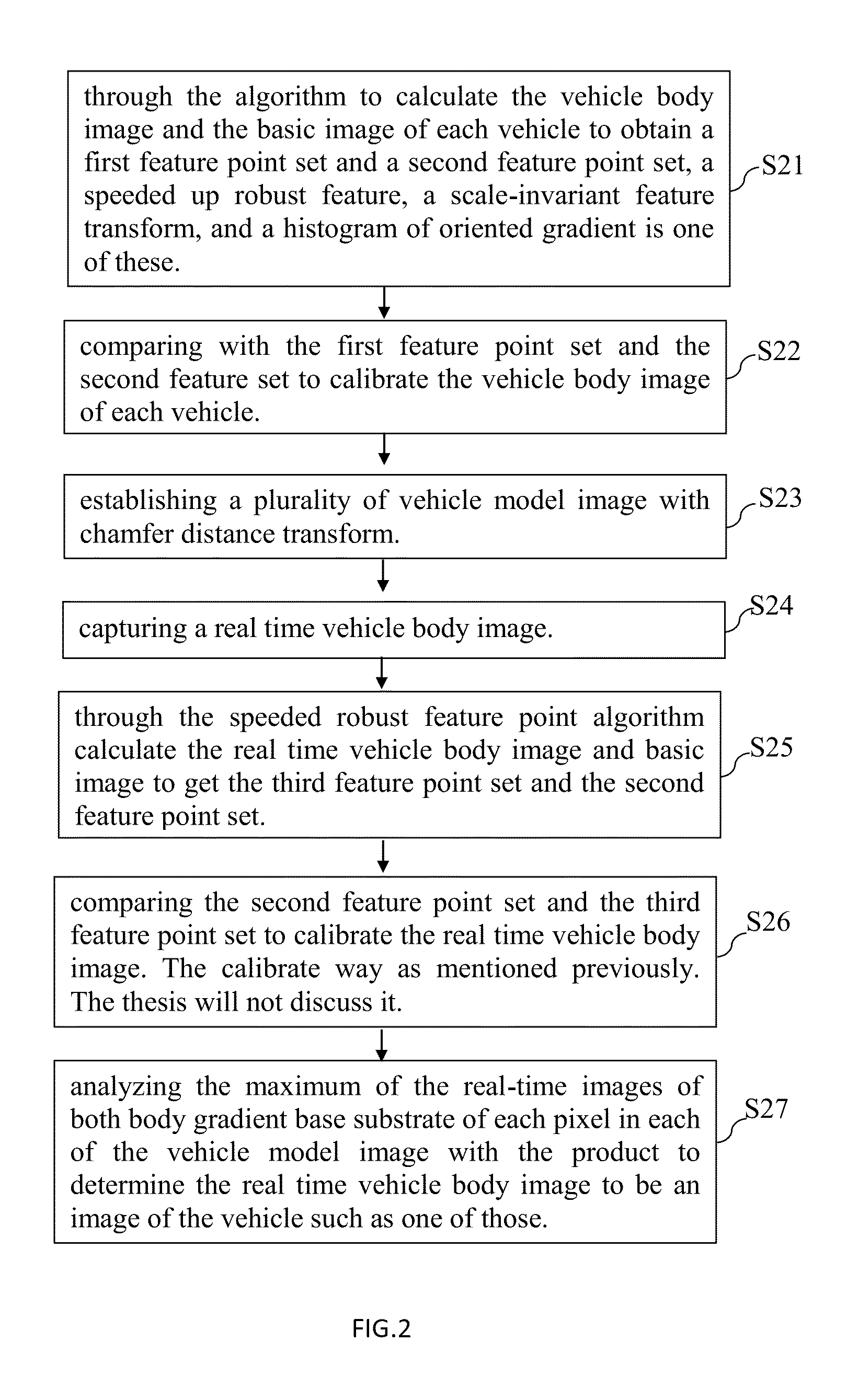
Method and system for vehicle identification
ActiveUS20150269190A1Accurate identityDigital data information retrievalCharacter and pattern recognitionReference imageBody images
A vehicle identification system and method comprising (a) Calculating vehicle image and reference image of each vehicle by algorithm, in order to obtain respectively the first feature point set and second feature point set. (b) Comparing first feature point with second feature point to calibrate the vehicle image of each vehicle. (c) Establishing plurality of vehicle model image with a gradient bevel distance of the base of the conversion of such vehicles. (d) Capturing instant image of the vehicle. (e) Calculating instant image and reference image by algorithm to obtain respectively the third feature point and the second feature point. (f) Comparing the second feature point and the third feature point to calibrate the instant vehicle image. (g) The instant judgments greatest body image and the gradient of each pixel in each of the base vehicle model for each pixel of the image of the product to determine the real-time vehicle body image should compare of the vehicle model image of one of them.
Owner:YUAN ZE UNIV
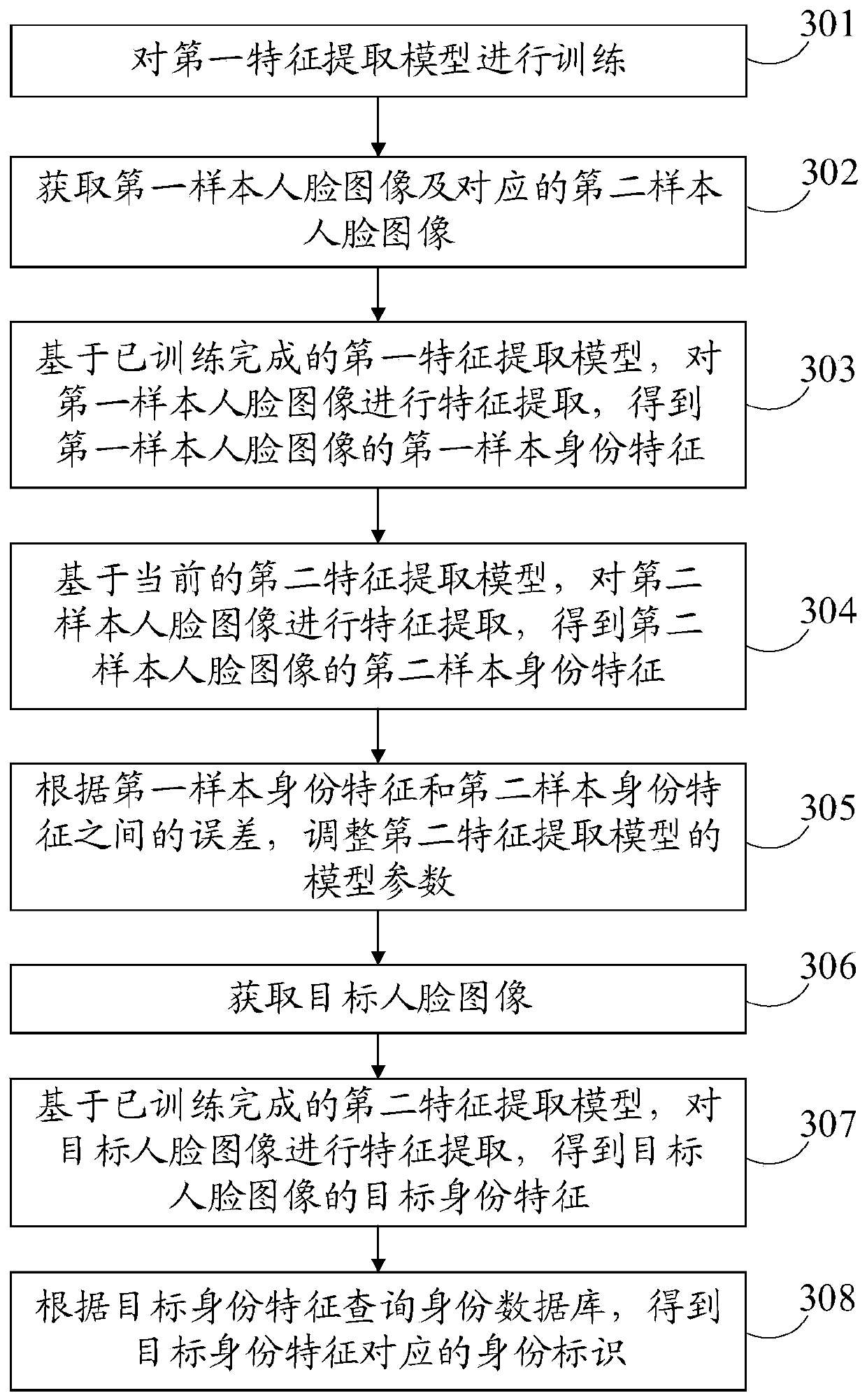
Face image processing method and device and storage medium
ActiveCN110059652AEasy to handleAccurate identityCharacter and pattern recognitionEnergy efficient computingFeature extractionImaging processing
The embodiment of the invention discloses a face image processing method and device and a storage medium, and belongs to the technical field of image processing. The method comprises the steps of obtaining a first sample face image and a corresponding second sample face image; based on the trained first feature extraction model, performing feature extraction on the first sample face image to obtain a first sample identity feature of the first sample face image; based on a current second feature extraction model, performing feature extraction on the second sample face image to obtain a second sample identity feature of the second sample face image; and adjusting model parameters of the second feature extraction model according to an error between the first sample identity feature and the second sample identity feature. According to the method, the second feature extraction model can learn the relation between the face image and the corresponding identity feature, a more accurate featureextraction model can be trained, the identity feature extracted by the second feature extraction model is more accurate, and the accuracy is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Providing identity-related information and preventing man-in-the-middle attacks
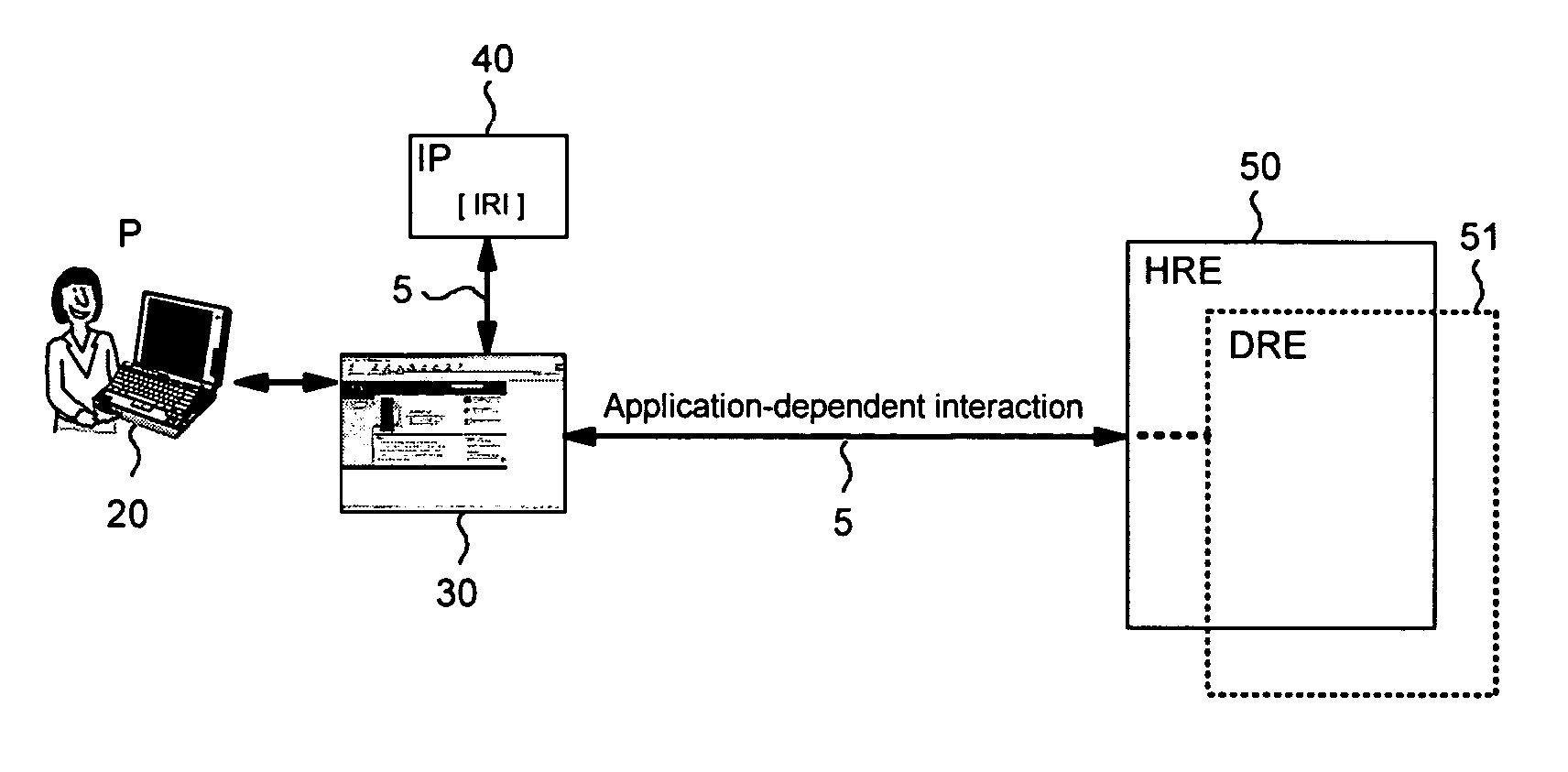
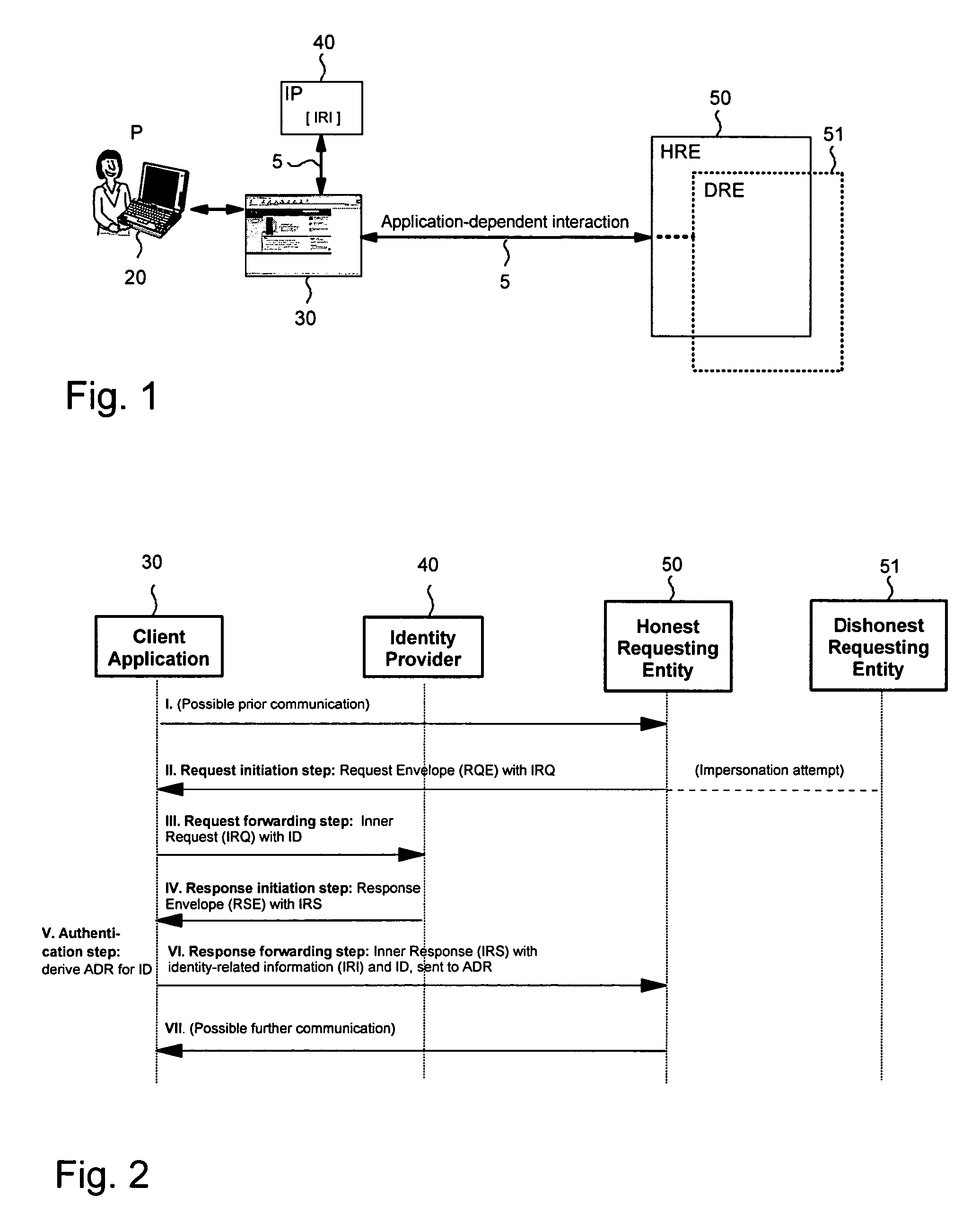
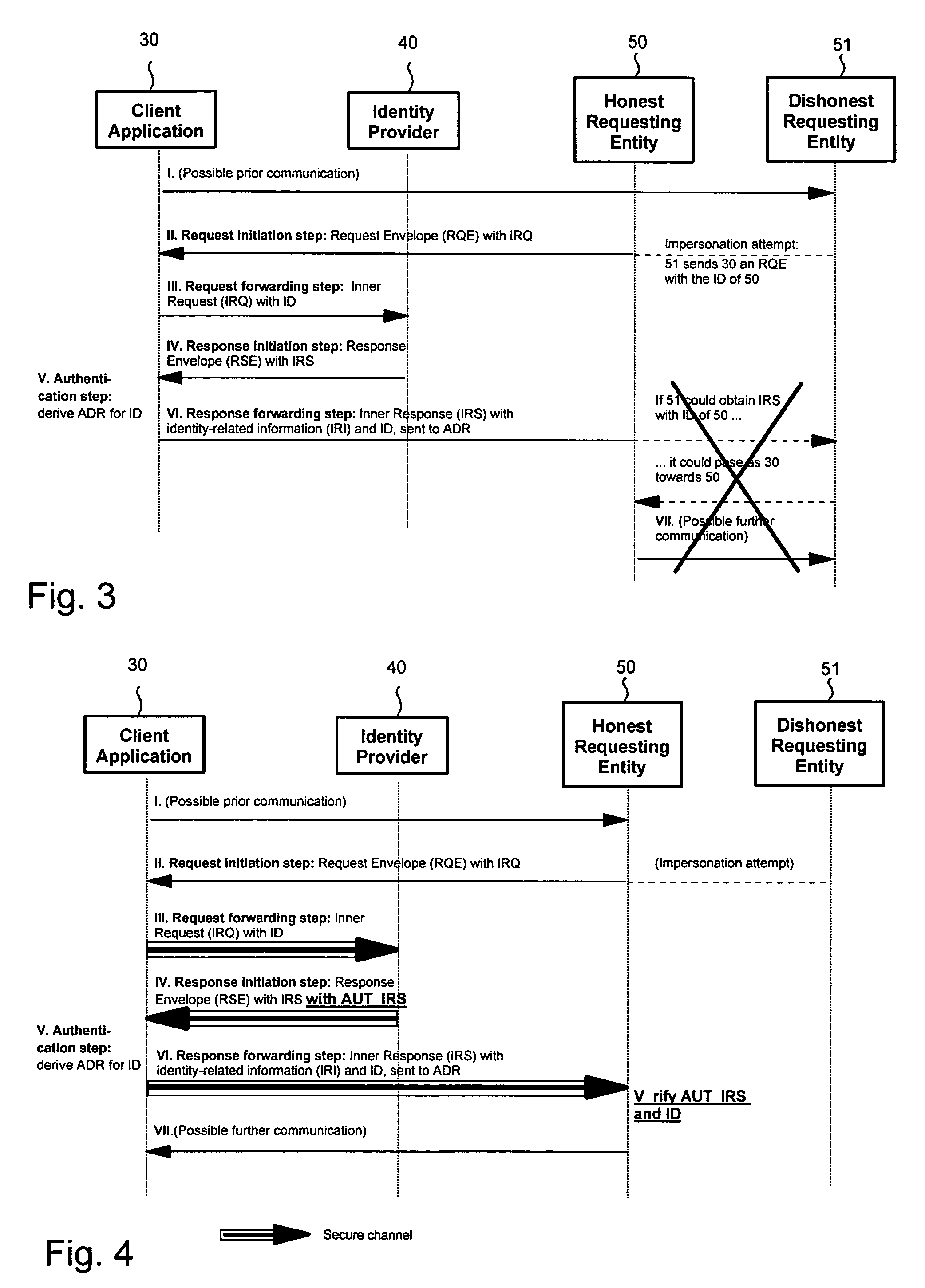
InactiveUS7240362B2Avoid attackAccurate identityUser identity/authority verificationData resettingMan-in-the-middle attackIdentity provider
This invention provides identity-related information about a client application to an honest requesting entity, ensuring identity of client applications and preventing man-in-the-middle attacks. An example method comprises transferring identity-related information hosted on an identity provider about a client application to an honest requesting entity by: the client application receiving from a particular entity a request to forward an inner request comprising an identifier of the honest requesting entity to an identity provider selected by the client application; the client application forwards the inner request to the identity provider holding the identity-related information; the client application receives from the identity provider a response envelope instructing the client application to forward an inner response comprising the identity-related information requested in the inner request and the identifier; the client application derives an address of the honest requesting entity having the identifier; and the client application forwards the inner response to the derived address.
Owner:IBM CORP
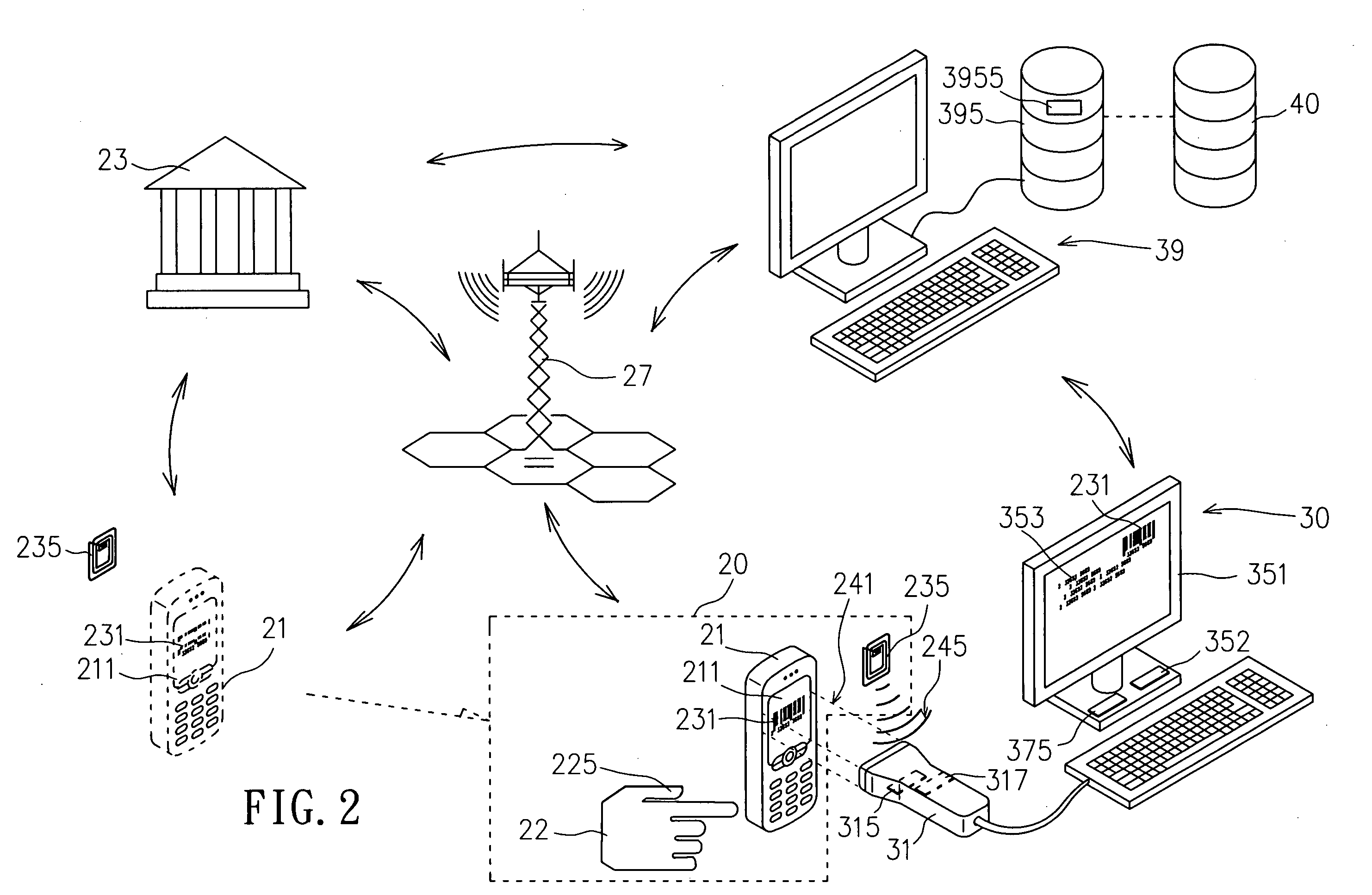
Data reading device with multiple verification functions and verifications system thereof
InactiveUS20060287951A1Avoids risk of creditReduce riskTicket-issuing apparatusFinanceRadio frequency signalData storing
A data accessing device with multiple verification functions and a verification system are provided. The device comprises an electronic certificate reader and a radio frequency signal reader in an outer housing. The electronic certificate reader can access an electronic certificate displayed in a portable electronic device of a user through an optical path, while the radio frequency signal reader accesses a personal radio frequency identification label of a user through a radio frequency path. The electronic certificate data and personal radio frequency identification label data is sent to a verification system to be processed and compared with user data stored in a user database to determine whether the access electronic certificate and personal radio frequency identification label are correct or whether there is a corresponding relationship therebetween. Accordingly, comparison result data is generated which can be represented in a result review device to be benefit for an identity verification application system to know correct identity of the user or whether to continue proceeding the transaction.
Owner:SHOOTER DIGITAL +1
Iris recognition device, manufacturing method therefor and application thereof
ActiveUS10169651B2High precisionEfficient identificationTelevision system detailsAcquiring/recognising eyesCamera modulePupil
The iris recognition device includes an iris camera module used for collecting iris characteristics of a user, and at least one fill light component used for providing a supplementary light source for the iris camera module. When the iris recognition device is used for collecting the iris characteristics of the user, the supplementary light source provided by the fill light component reduces reflective spots on the iris or make reflective spots in areas other than iris such as sclera and pupil, thereby improving precision of the collected iris characteristics of the user.
Owner:NINGBO SUNNY OPOTECH CO LTD
Method for synchronizing status of ue in a communication network
InactiveUS20200267539A1Accurate identityAssess restrictionConnection managementComputer networkTelecommunications
The present disclosure relates to synchronizing a temporary identity in the UE and the network when the UE is RRC Inactive state over 3GPP access and temporary identity of the UE is changed over a Non-3GPP access in a scenario when the UE is connected to the same AMF via 3GPP and non-3GPP access.
Owner:NEC CORP
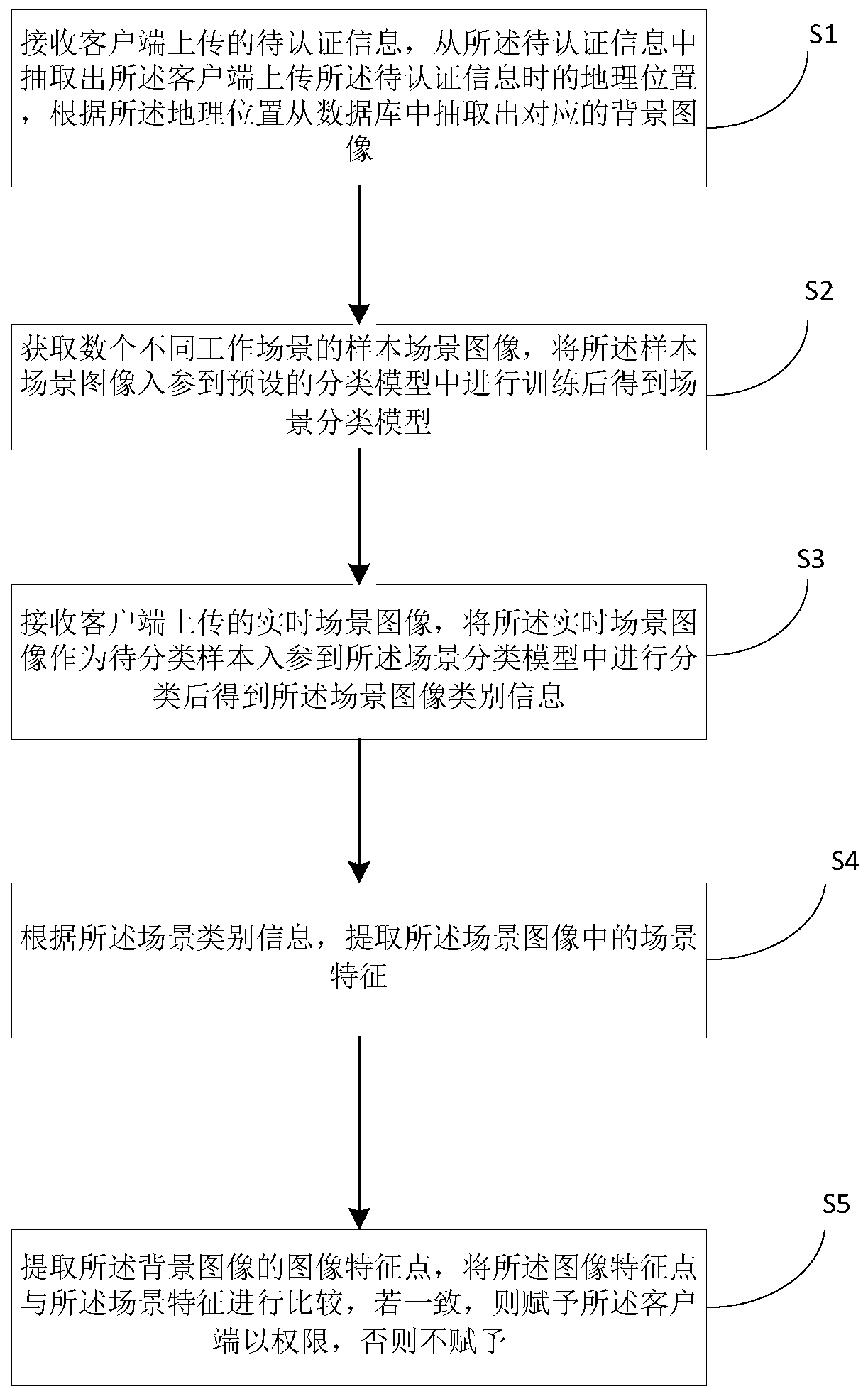
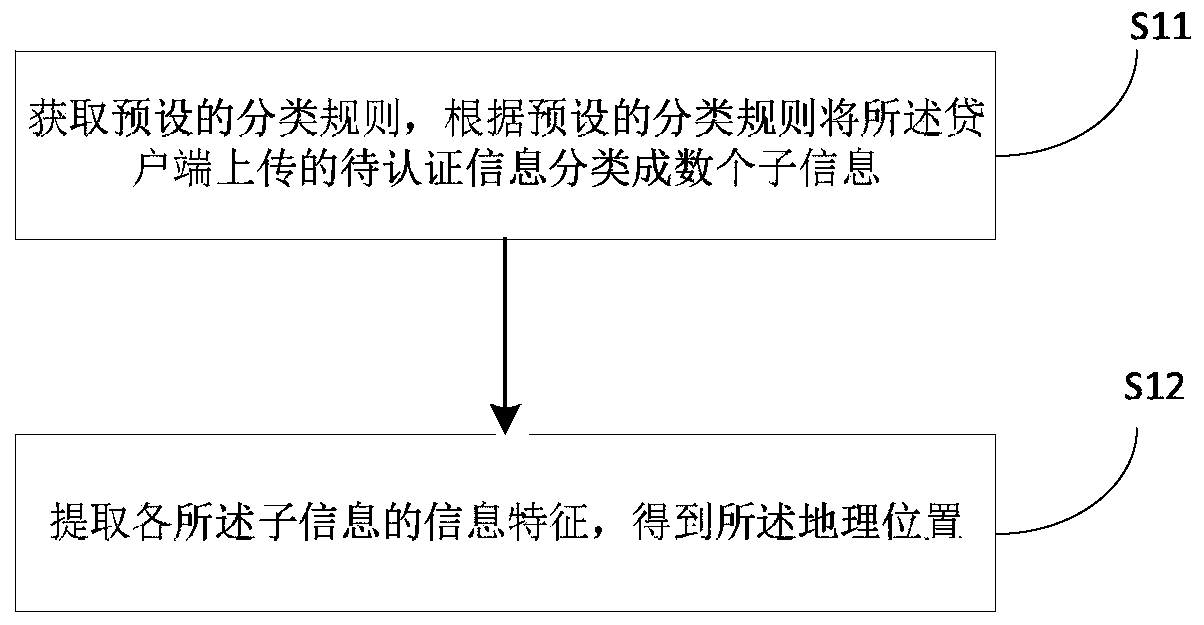
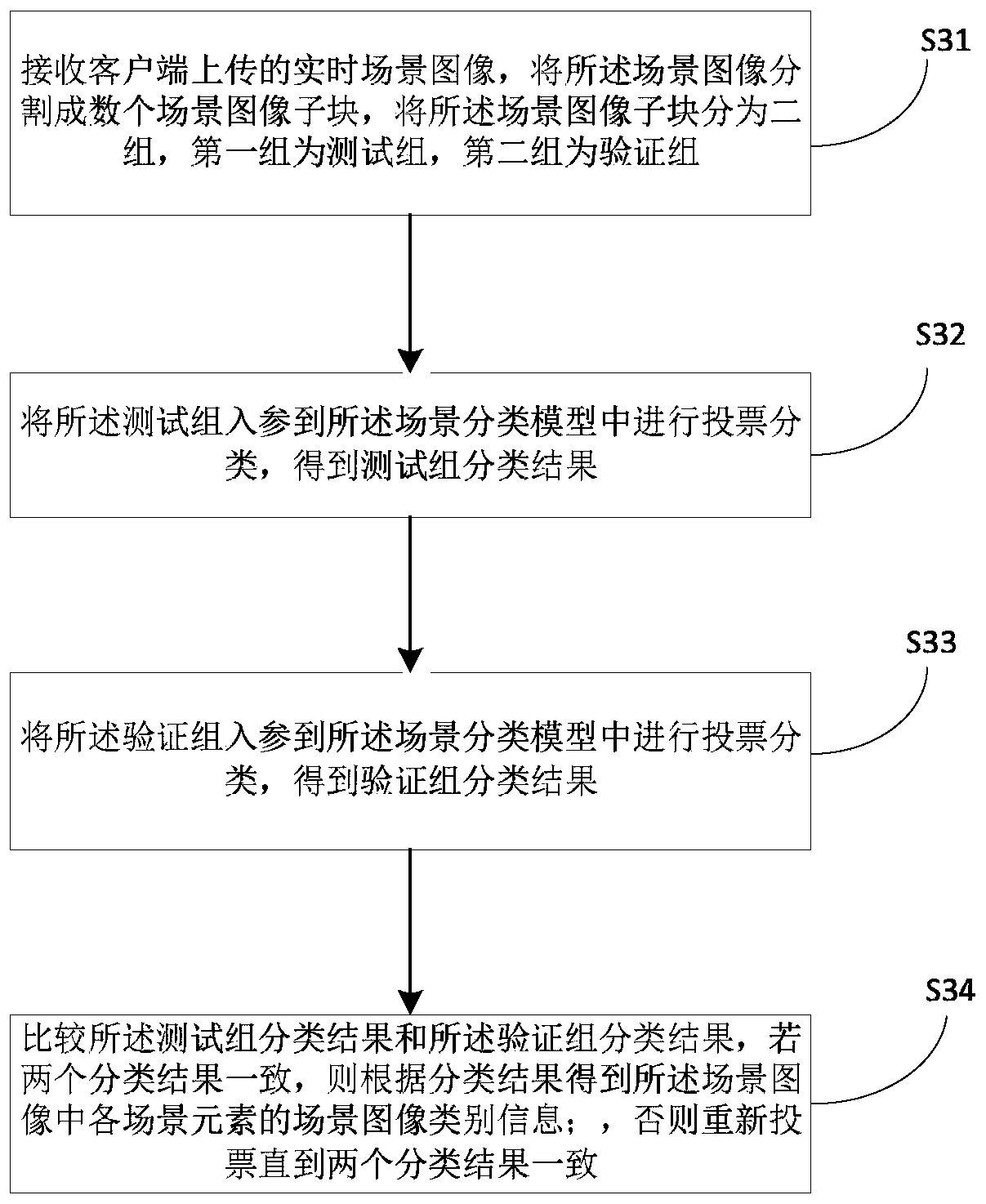
Information identification method based on deep learning and related equipment
The invention relates to the technical field of image classification and recognition, in particular to an information identification method based on deep learning and related equipment, and the methodcomprises the steps: extracting a geographic position from to-be-authenticated information, and extracting a corresponding background image from a database according to the geographic position; acquiring a plurality of sample scene images of different working scenes, and adding the sample scene images into a convolutional neural network model for training to obtain a scene classification model; taking a real-time scene image as a to-be-classified sample, and adding the to-be-classified sample into the scene classification model for classification to obtain scene image category information; extracting scene features in the scene image; and extracting image feature points of the background image, and comparing the image feature points with the scene features. According to the application, scene information verification is introduced when the loan qualification of the loaner is audited, so that the problem that the loaner obtains the loan application qualification through the virtual working condition is avoided.
Owner:PING AN TECH (SHENZHEN) CO LTD
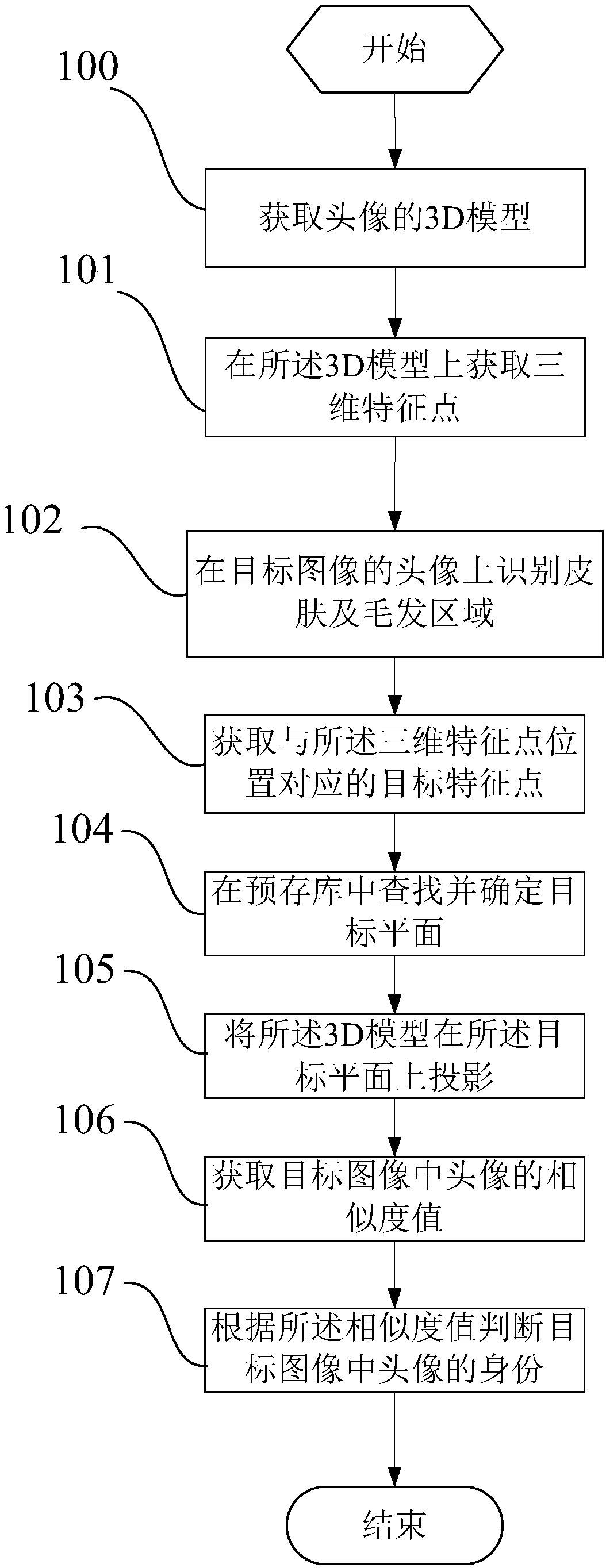
Face recognition method based on 3D imaging and terminal
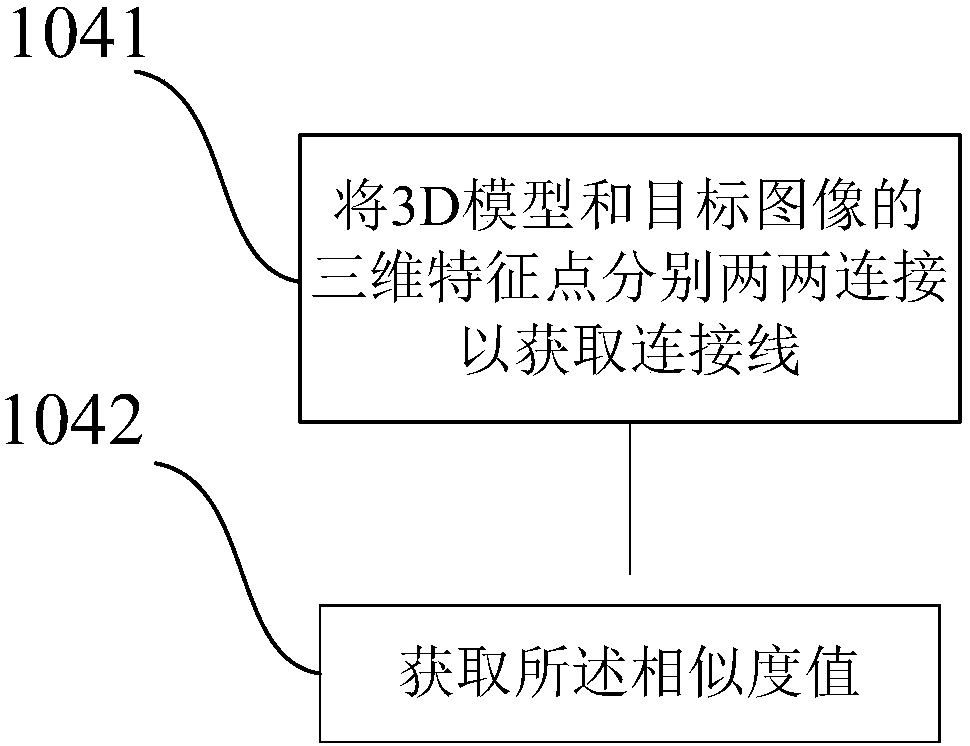
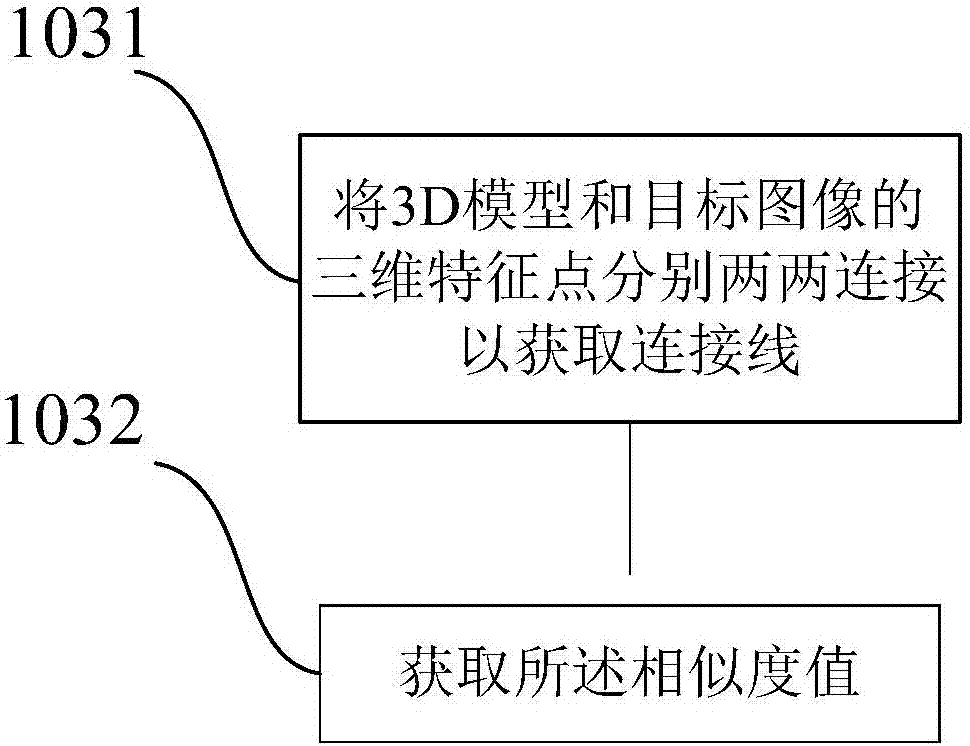
InactiveCN108197549ARich varietyAccurate identityImage enhancementImage analysisPattern recognitionIdentity recognition
The invention discloses a face recognition method based on 3D imaging and a terminal. The face recognition method comprises the steps that a 3D model of an icon is acquired; three-dimensional featurepoints are acquired from the 3D model; a skin and hair area is recognized on the icon of a target image; target feature points corresponding to the three-dimensional feature points in position are acquired from the skin and hair area; the three-dimensional feature points and the target feature points are compared to acquire a similarity value of the icon in the target image; and the identity of the icon in the target image is judged according to the similarity value. Through the face recognition method and the terminal, recognition of the identity in the image is more accurate, more types of recognition images are available, the recognition range is wider, and more application environments are available for identity recognition.
Owner:UNRE SHANGHAI INFORMATION TECH CO LTD
Method and system to identify metal alloys
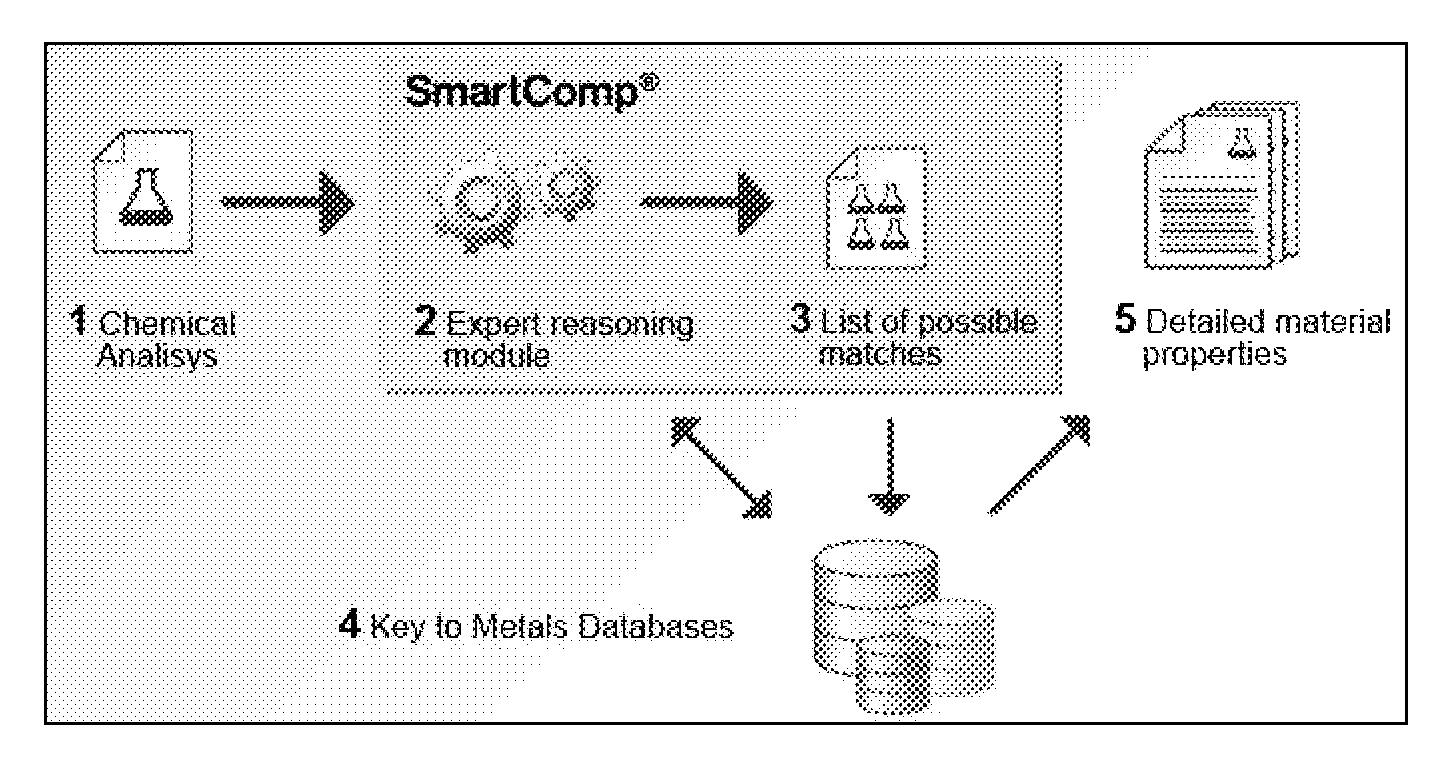
ActiveUS8918290B2Accurate identificationAccurate identitySpecial data processing applicationsChemical methods analysisCorrelation factorChemical composition
A method and system to identify an unknown metal alloy based on its chemical composition is provided in the present application. The chemical elements contained in the alloy are separated into key elements and trap elements. Then a similarity factor between a relative amount of each key element and a threshold value of said key elements is determined and a correlation factor is formed based on the similarity factors.
Owner:KEY TO METALS
Virtual network management method of data center and data center system
PendingCN114371912AAccurate identityAvoid data transfer clutterSoftware simulation/interpretation/emulationVirtual network topologyNetwork management
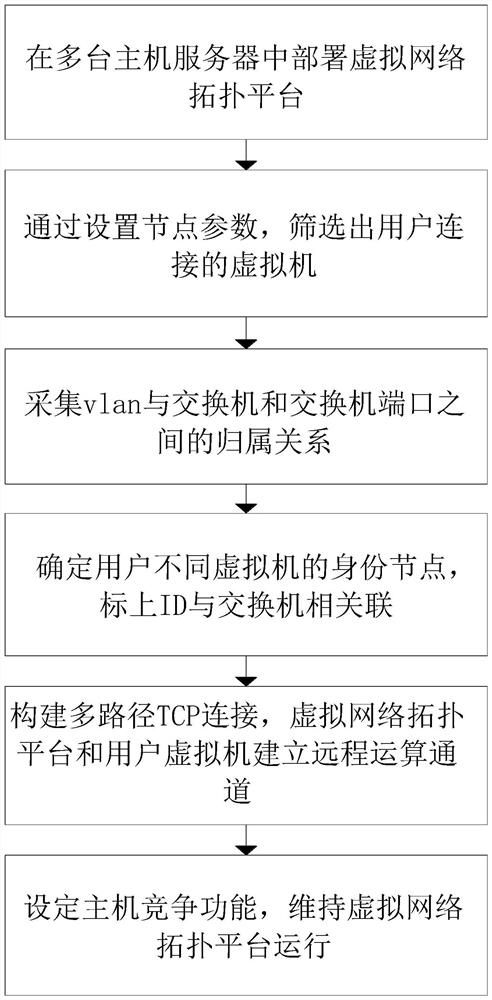
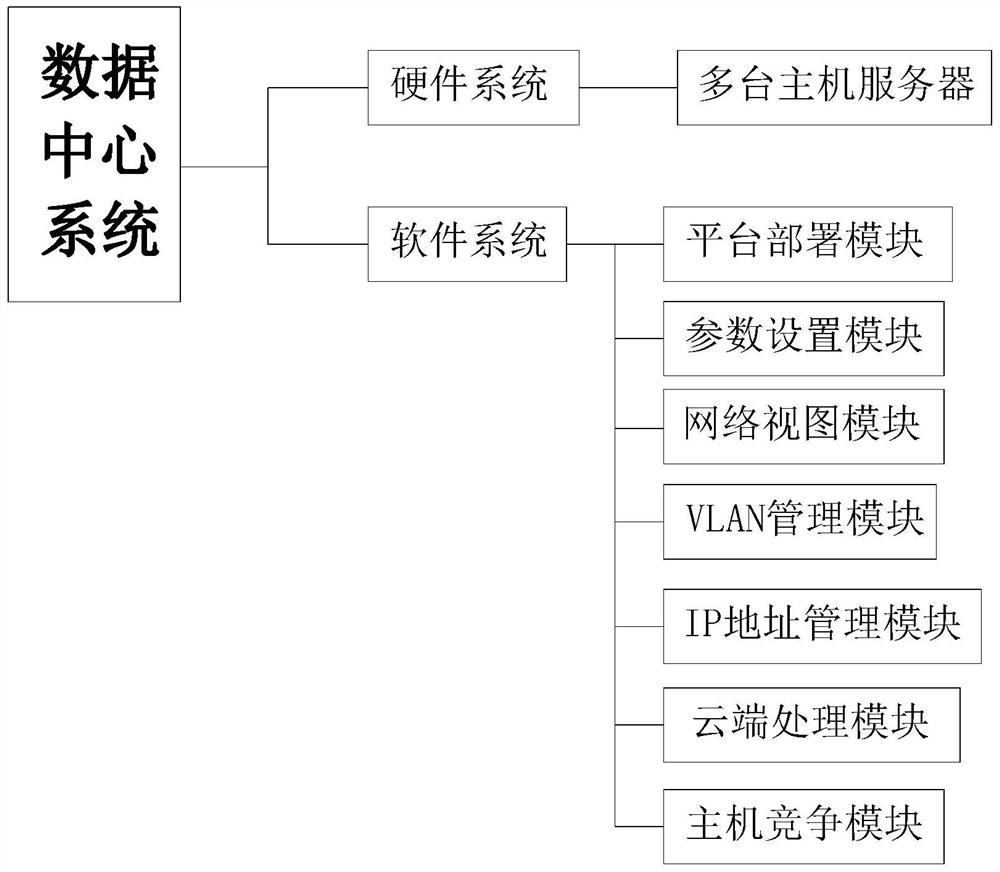
The invention provides a virtual network management method of a data center and a data center system, and relates to the technical field of network management, and the method comprises the following steps: deploying a virtual network topology platform in a plurality of host servers, and deploying configuration to meet application operation requirements; through setting node parameters, configuration information of physical network nodes and port connection links between the physical network nodes are identified, so that virtual machines connected by users are screened out; according to the method, node parameters are set, configuration information of physical network nodes and port connection links between the physical network nodes are identified, virtual machines connected with users are screened out, the affiliation relation between the vlan and a switch and the affiliation relation between the vlan and a switch port are collected, and relation data of an IP and an MAC in each physical network node are stored; iDs are marked to be associated with a switch, so that the identity accuracy of the virtual machines of the user is ensured, and disordered data transmission is avoided.
Owner:江苏先云信息技术有限公司
Electronic identity authentication method and authentication system
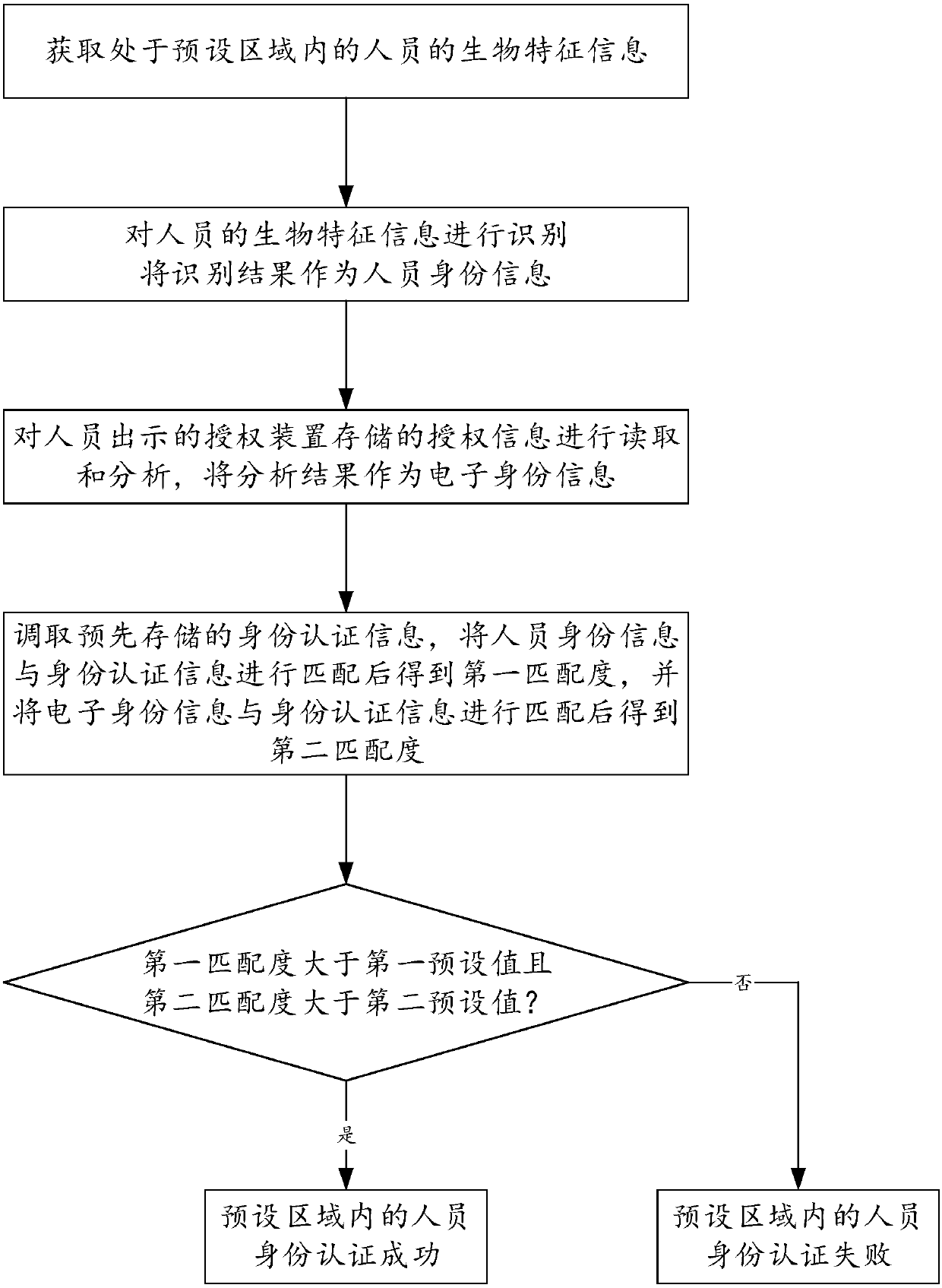
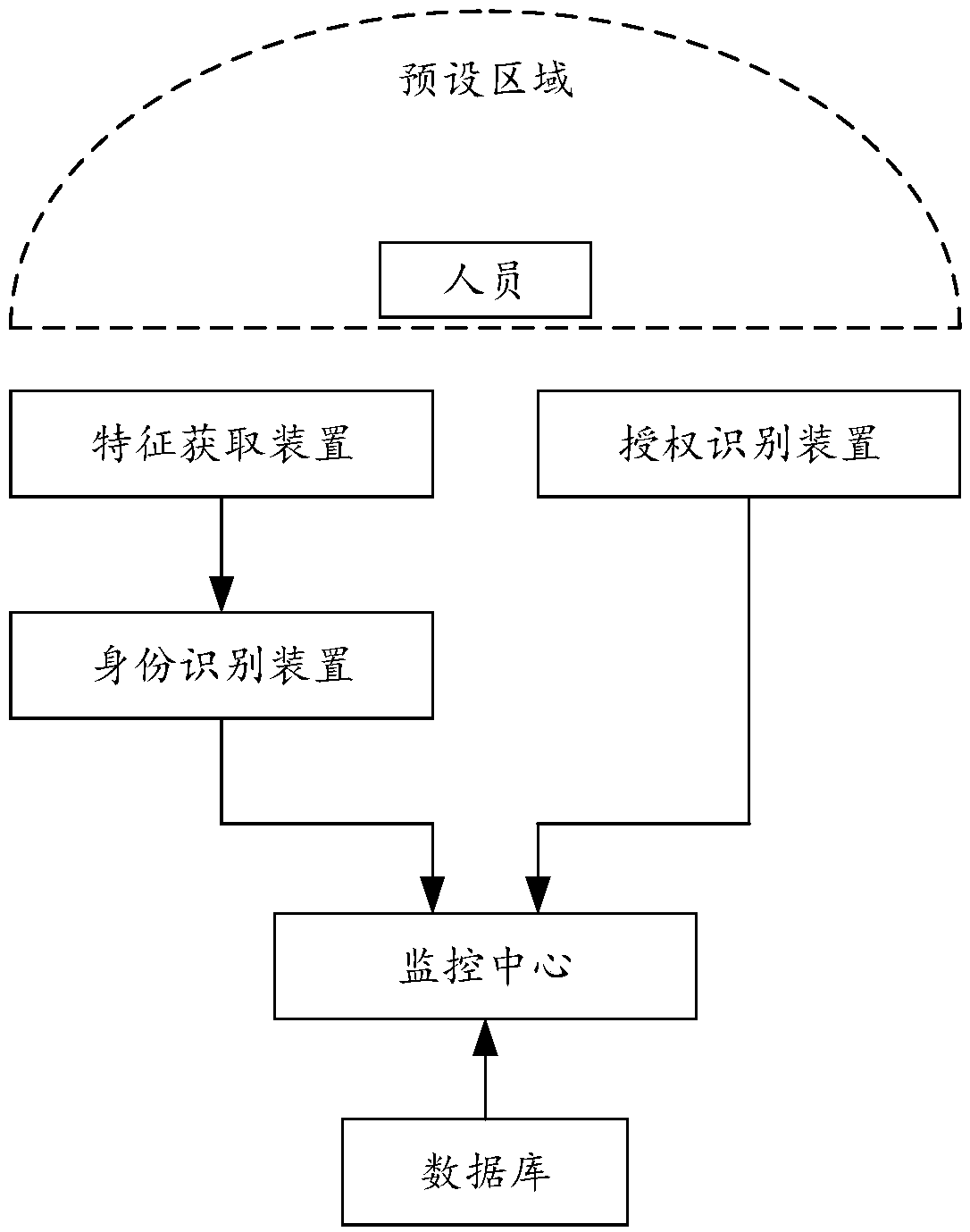
InactiveCN110097662AAccurate identityAvoid problems entering coworking areasIndividual entry/exit registersIdentification deviceAuthentication system
The invention discloses an electronic identity authentication method and authentication system. The method comprises the steps: acquiring biological characteristic information of a person and identifying the biological characteristic information of the person to obtain the identity information of the person; reading and analyzing authorization information that is stored by an authorization deviceand is shown by the person to obtain electronic identity information; and matching the identity information of the person with the identity authentication information to obtain a first matching degree, matching the electronic identity information with the identity authentication information to obtain a second matching degree, and authenticating the identity of the person based on the first and second matching degrees. In addition, the system includes a feature acquiring device, an identity identifying device, an authorization identifying device, a monitoring center, and a database. According to the invention, the electronic identity authentication method and authentication system based on dual information acquisition are employed innovatively, so that the high security of the shared officearea is ensured and thus a problem that the impostor enters the shared office area maliciously is solved.
Owner:TERMINUSBEIJING TECH CO LTD
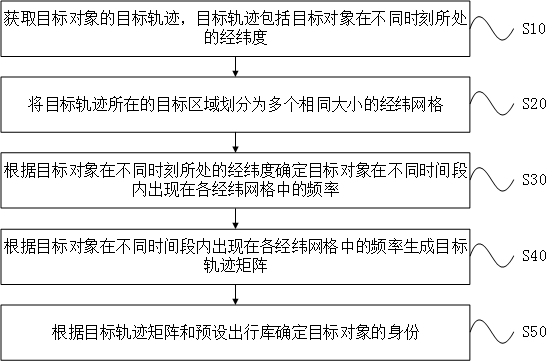
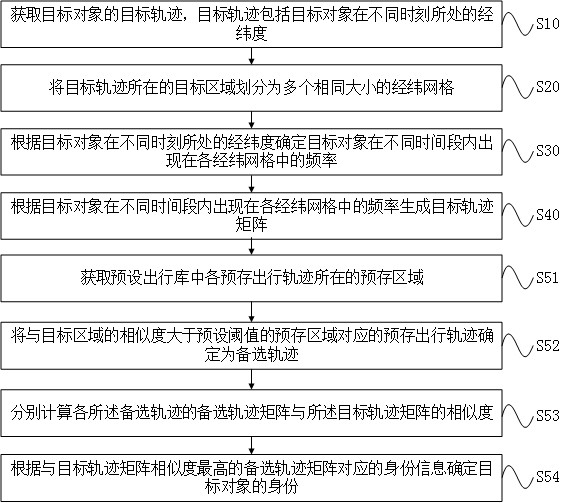
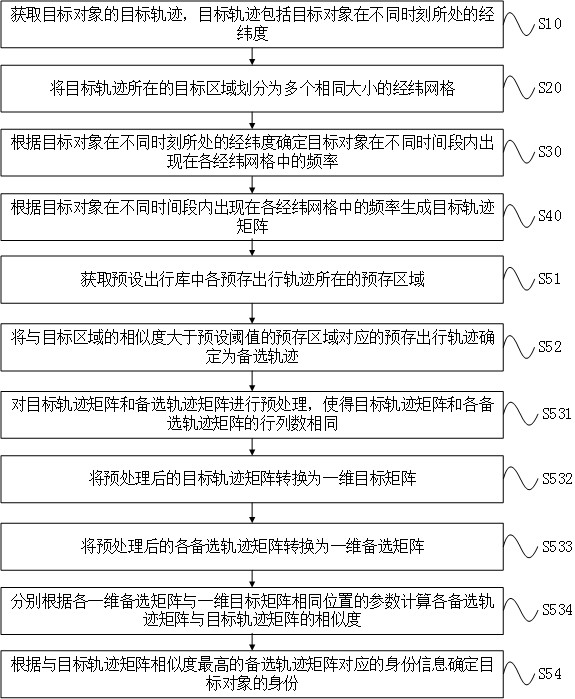
Target object identification method and device
InactiveCN111814914AAccurate identityFlexible adjustmentCharacter and pattern recognitionPhysicsComputer graphics (images)
The invention provides a target object identification method and device, and the method comprises the steps: obtaining a target track of a target object, wherein the target track comprises the longitude and latitude of the target object at different moments; dividing a target area where the target track is located into a plurality of longitude and latitude grids with the same size; determining thefrequency of the target object appearing in each longitude and latitude grid in different time periods according to the longitude and latitude of the target object at different moments; generating atarget trajectory matrix according to the frequency of the target object appearing in each longitude and latitude grid in different time periods; and determining the identity of the target object according to the target trajectory matrix and a preset travel library, wherein the preset travel library comprises a plurality of pre-stored travel trajectories and identity information corresponding to each pre-stored travel trajectory. By implementing the method, the identity of the target object can be determined through the target track, and the target track matrix is flexibly determined through the target track so that the identity of the target object can be determined more accurately.
Owner:ZHUHAI DAHENGQIN TECH DEV CO LTD
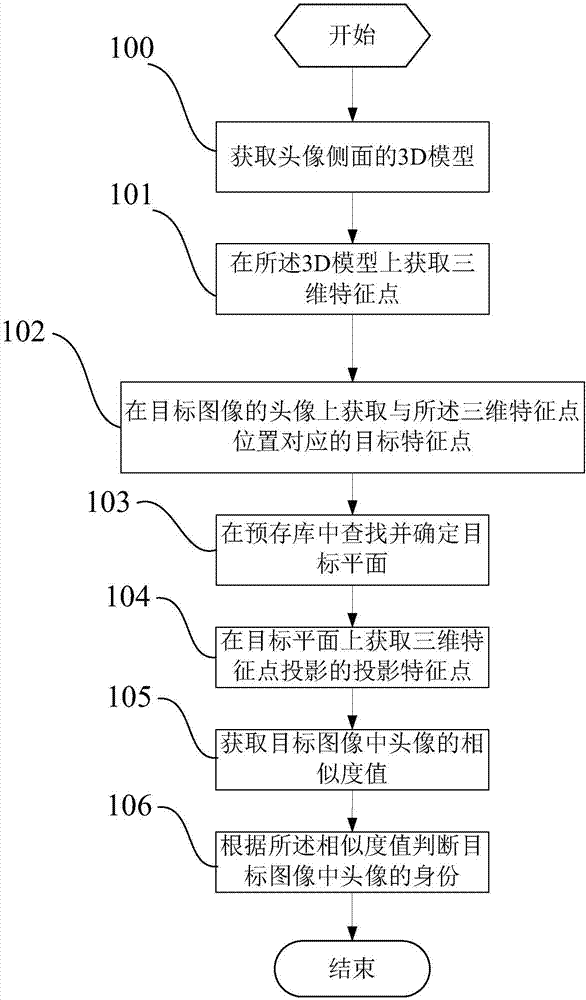
Identity recognition method and terminal based on 3D imaging
InactiveCN108009532AAccurate identityRich varietyCharacter and pattern recognitionApplication Context3 d imaging
The invention discloses an identity recognition method and terminal based on 3D imaging. The identity recognition method comprises: acquiring a 3D model of the side of a portrait; acquiring a three-dimensional feature point on the 3D model; acquiring a target feature point corresponding to the position of the three-dimensional feature point from the portrait in a target image; comparing the three-dimensional feature point with the target feature point so as to obtain the similarity value of the portrait in the target image; and determining the identity of the portrait in the target image according to the similarity value. The identity recognition method and terminal can accurately recognize the identity in the image, can recognize various types of images, and have a wide recognition range,and various identity recognition application environments.
Owner:UNRE SHANGHAI INFORMATION TECH CO LTD
Electronic machine, connected machine identifying method for electronic machine and control system
InactiveUS7804311B2Accurate detectionAccurate identityResistance/reactance/impedenceInput/output processes for data processingElectrical resistance and conductanceControl system
An electronic machine connectable to a different apparatus is disclosed. The electronic machine includes a resistance, a connector to be connected to the different apparatus, and a detecting section that detects one state from multiple states based on the resistance value of the resistance and the resistance value of a resistance included in the different apparatus connected to the connector and controls multiple parameters based on the detected one state.
Owner:SONY CORP
Access identity authentication system and authentication method thereof
InactiveCN107025707AAccurate identityAvoid enteringIndividual entry/exit registersAuthentication systemCharacter analysis
The invention relates to an access identity authentication system and an authentication method thereof, and belongs to the technical field of electronic management. An image acquisition module is used for acquiring an image of a human face and sending the acquired image to an identification module; the identification module is used for identifying the human face in the image of the image acquisition module and identifying identity information of a person; the identity information of the person is sent to a monitoring center; a card reading module reads a chest card of the person and conducts location identification and character analysis to obtain chest card information, and then the chest card information and positioning information are sent to the monitoring center; the identity information of the person, and the chest card information are correspondingly compared with associated data of staff identity-chest card stored in a database through the monitoring center. According to the access identity authentication system and the authentication method thereof, double information is acquired and is compared with storage data of the monitoring center to ensure that the identity of the entry person is accurate, and prevent an impostor from using a copied card or other person's card to entry a control area.
Owner:SHENZHEN RUIRONGCHUANG ELECTRONICS TECH CO LTD
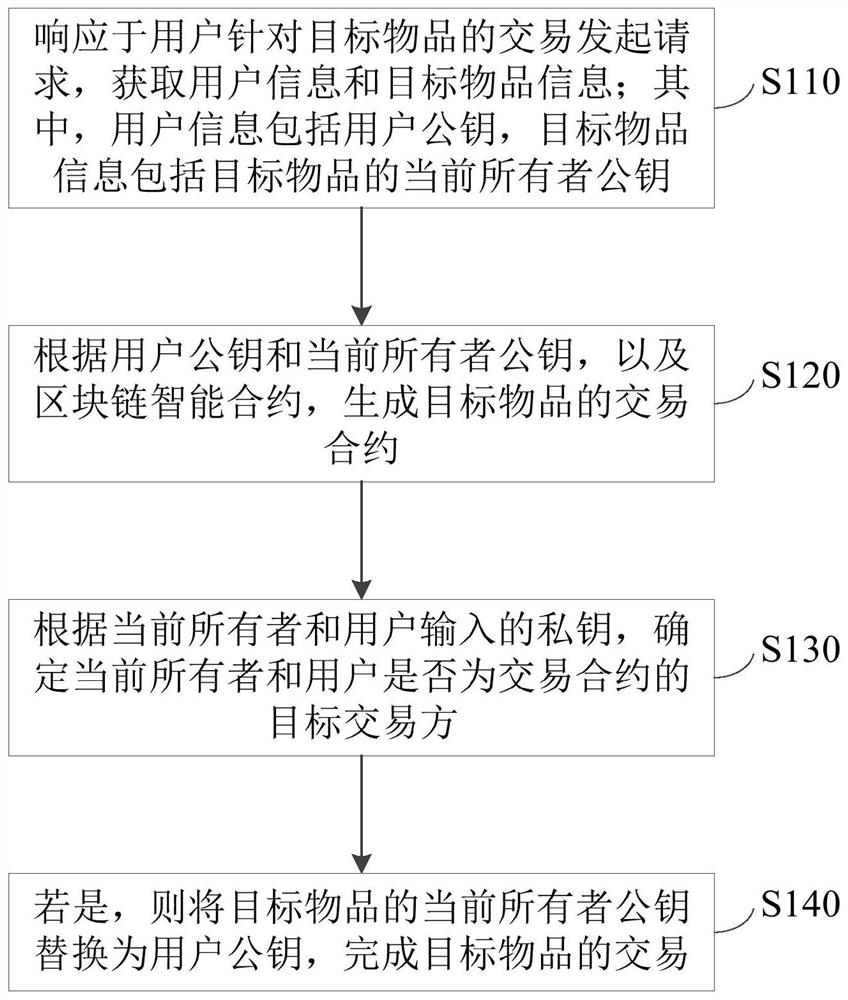
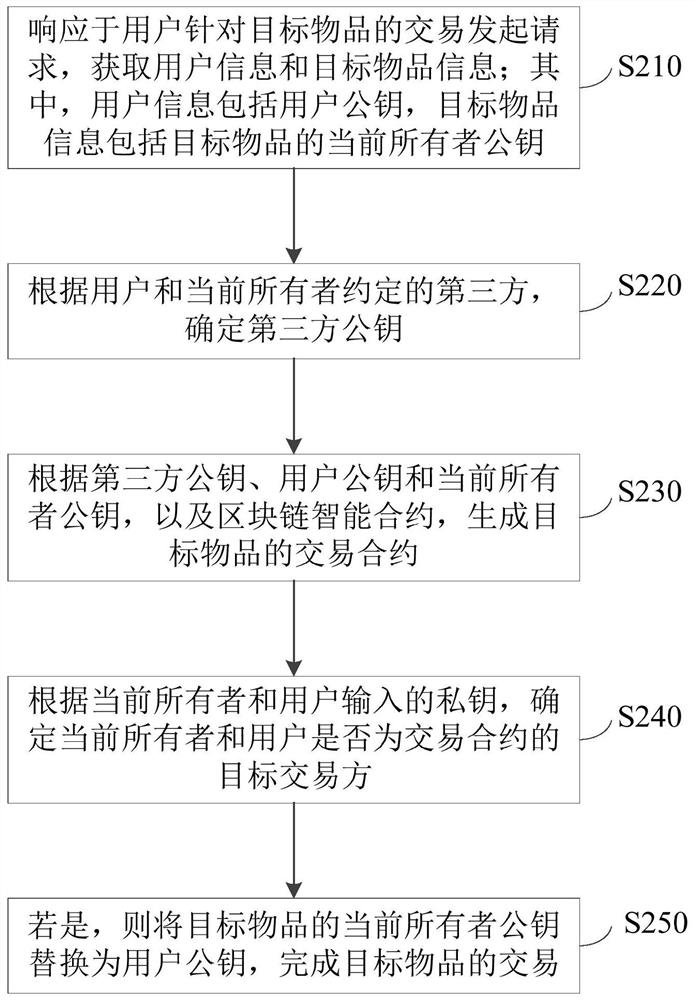
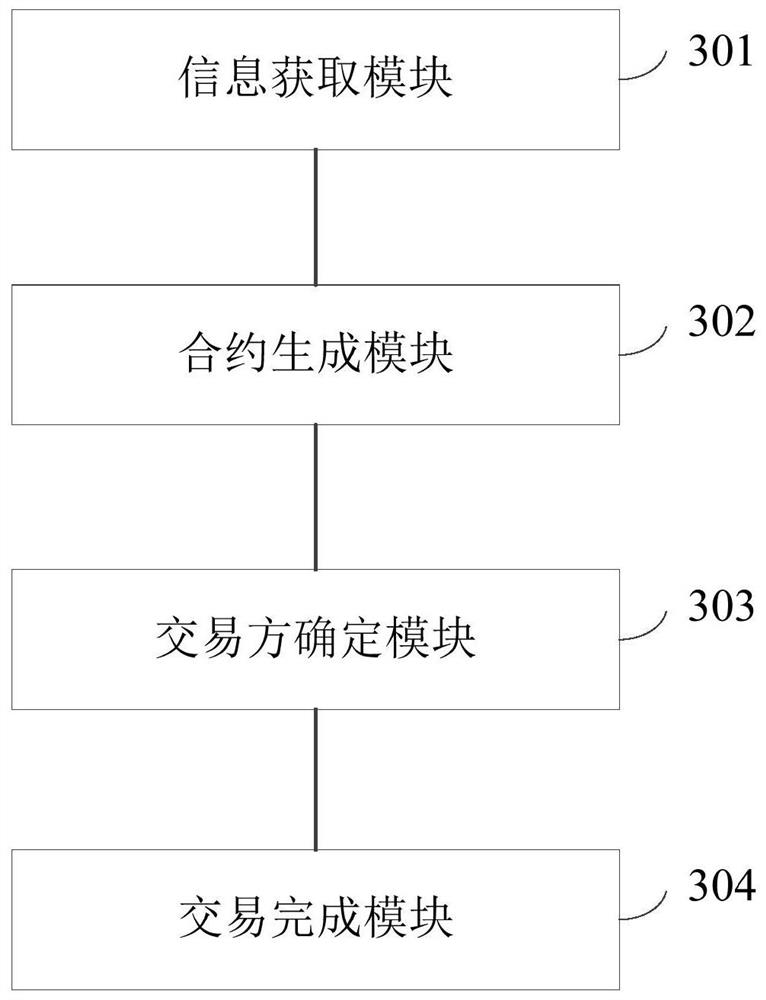
Transaction processing method, apparatus and device, and storage medium
PendingCN112037056ASolve the problem that items cannot be traded through the blockchainAccurate identityFinanceTransmissionEngineeringFinancial transaction
The embodiment of the invention discloses a transaction processing method and device, equipment and a storage medium. The method comprises the steps of obtaining user information and target article information in response to a transaction initiation request of a user for a target article, wherein the user information comprises a user public key, and the target article information comprises a current owner public key of a target article; generating a transaction contract of the target object according to the user public key, the current owner public key and a blockchain smart contract; determining whether the current owner and the user are target transaction parties of the transaction contract or not according to the current owner and a private key input by the user; and if so, replacing the current owner public key of the target article with the user public key to complete the transaction of the target article. The transaction between two transaction parties on the blockchain is realized, the transaction information is prevented from being tampered at will, and the security of the transaction is ensured.
Owner:SHENZHEN UNIV
Medical identity recognition wrist strap
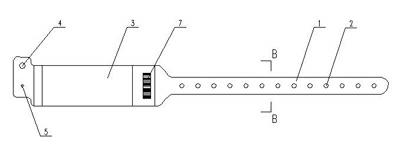
InactiveCN102610160ANo malleabilityNot easy to fall offStampsIdentification meansInformatizationIdentity recognition
The invention discloses a medical identity recognition wrist strap which is convenient to use, accurate in identity recognition and high in informatization management level. The medical identity recognition wrist strap comprises a wrist strap portion, a plurality of wearing holes arranged on the wrist strap portion, an information writing portion connected with one end of the wrist strap portion, a male button portion and a female button portion, wherein the male button portion and the female button portion are connected with the wrist strap. A high polymer material writing layer and a main bar code are arranged on the information writing portion, waterproof film layers are arranged on the high polymer material writing layer and the main bar code, a bar code strip portion is connected to the wrist strap portion, a plurality of identical bar codes which are adhered in a peelable mode and provided with unique information.
Owner:JIANGSU GAOJU IDENTIFICATION TECH CO LTD
Wireless radio frequency identification reader-writer of campus verification system
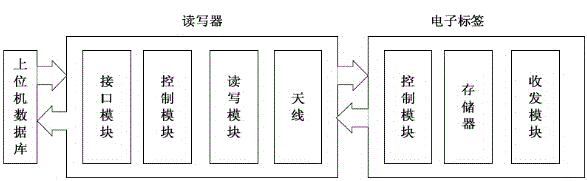
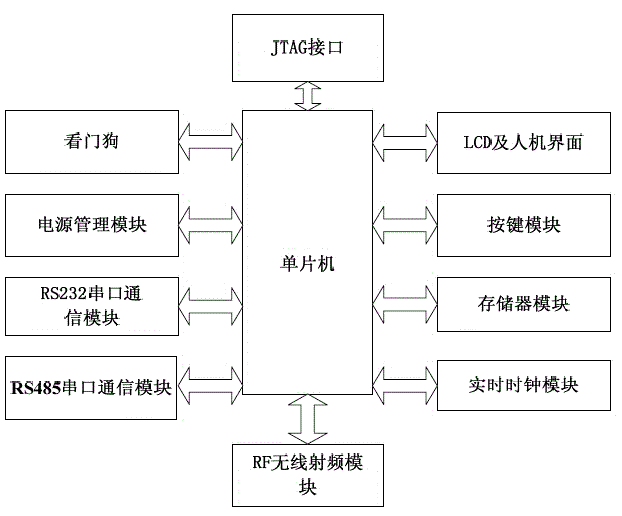
InactiveCN105989379AAccurate identityQuick identificationCo-operative working arrangementsReader writerMemory module
The present invention discloses a wireless radio frequency identification reader-writer of a campus verification system. The wireless radio frequency identification reader-writer is composed of a single-chip microcomputer, an external data memory module, a keyboard module, a Chinese liquid crystal display module, a radio frequency module, a real-time clock module, a power supply management module, a serial port communication module and the like. The wireless radio frequency identification reader-writer provided by the present invention applies an automatic identification technology, a miniature computer software / hardware technology, a radio frequency technology and an information safety technology and can realize a function of acquiring various campus information. A reader-writer system has the advantages of being portable and intelligent, being small in size and low in cost and power consumption, etc.
Owner:CHENGDU ZHONGJIE LIANKONG TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com