Electronic identity authentication method and authentication system
An electronic identity and identity authentication technology, applied in the field of identity authentication, can solve the problem that the access control system cannot guarantee the security of the shared office area, and achieve the effect of high reliability, rich means and strong flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
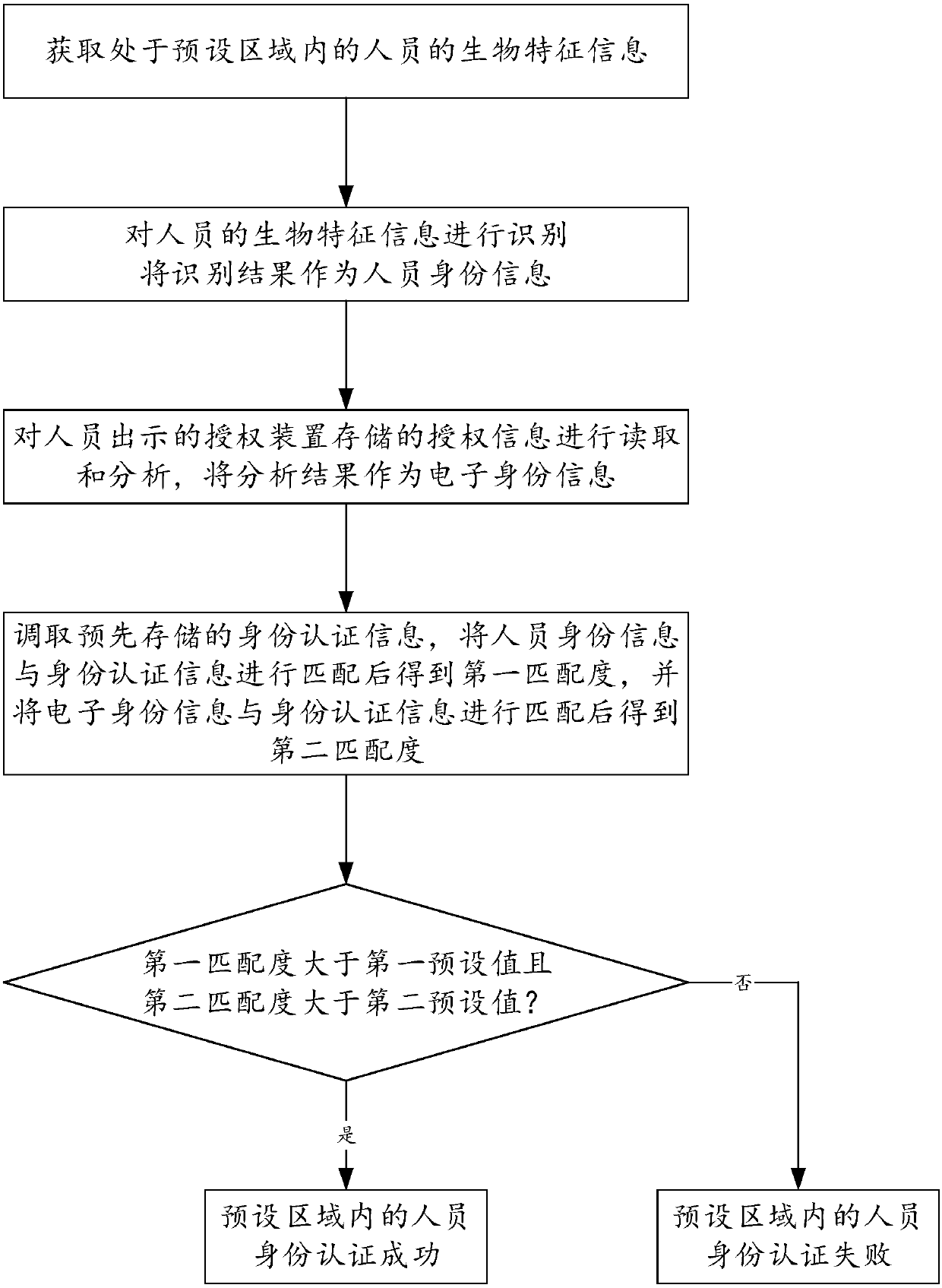
[0049] Such as figure 1 , 2As shown, this embodiment specifically discloses an electronic identity authentication method, which can be used to authenticate or verify the identity of a person entering a shared office area, thereby effectively avoiding problems such as maliciously entering the shared office area by pretending to be a person, and ensuring shared office space. The security of the office area fundamentally solves the security problem of "shared office" and makes the promotion and application of "shared office" possible; the method specifically includes the following steps.
[0050] Step 1, first judge whether there is a person in the preset area, and if there is, after the first preset time period, obtain the biometric information of the person in the preset area; this step includes the step of adjusting the brightness of the preset area, To obtain more accurate biological feature information; in this embodiment, the biological feature information is face informat...
Embodiment 2
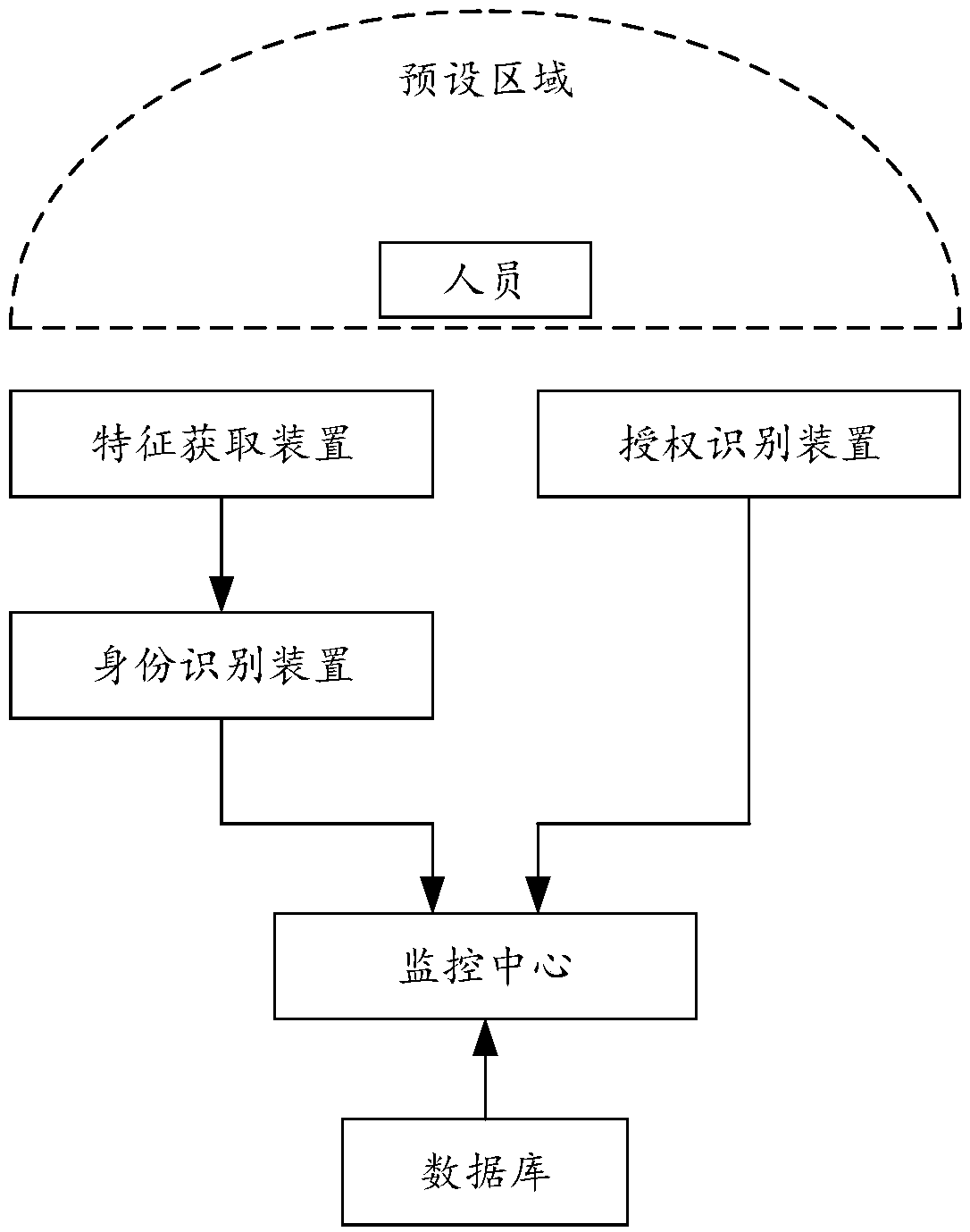
[0057] This embodiment is based on the same inventive concept as Embodiment 1. This embodiment specifically discloses an electronic identity authentication system, which includes a feature acquisition device, an identity identification device, an authorization identification device, a monitoring center, and a database. The feature acquisition device and The identification device is connected, the identification device is connected to the monitoring center by wired or wireless communication, the authorized identification device is also connected to the monitoring center by wired or wireless communication, and the monitoring center is connected to the database; specifically as figure 2 shown.
[0058] The feature acquisition device is used to acquire the biometric information of the person in the preset area; in this embodiment, the feature acquisition device includes a dimming module, a camera module, a start module and a delay module; the biometric information is face informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com