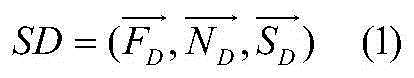Multi-track malicious program feature detecting method based on data mining
A malicious program and feature detection technology, applied in electrical digital data processing, instrument, platform integrity maintenance, etc., can solve problems such as defects that cannot be overcome in static detection, achieve optimization of mining efficiency, ensure system and data security, and improve accuracy degree of effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
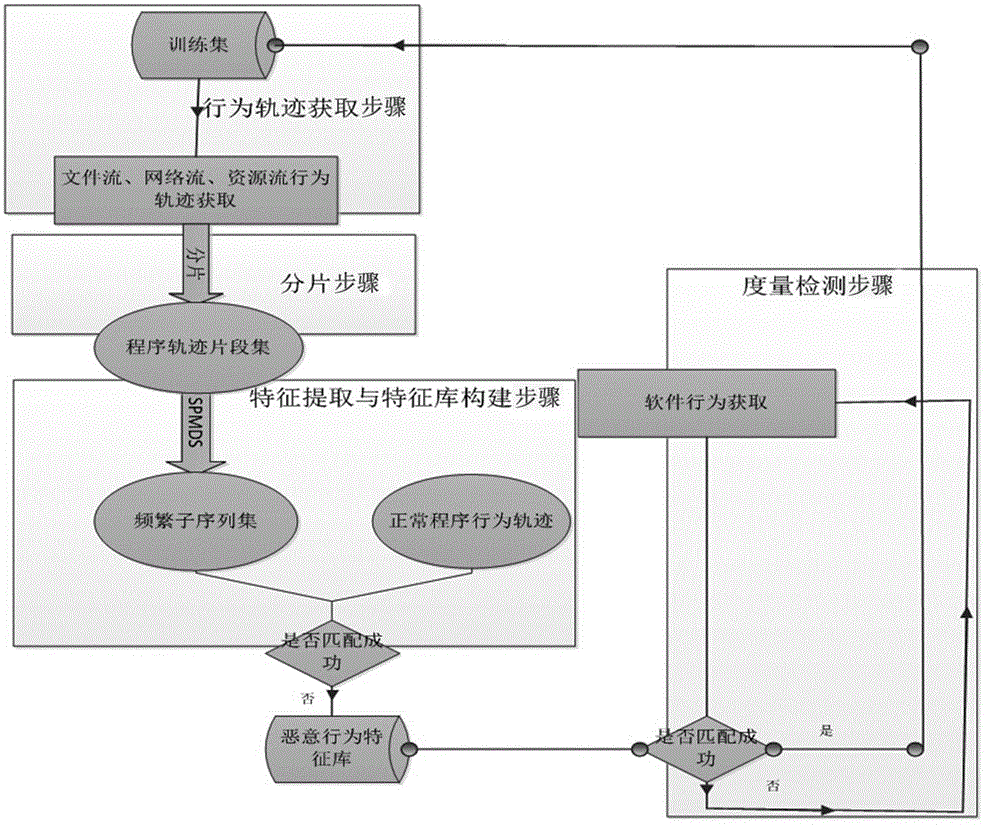
[0031] Multi-track malicious program feature detection method based on data mining (such as figure 1 Shown) contains the steps of acquiring behavior track, fragmentation step, feature extraction and feature library construction step, and measurement detection step;
[0032] The behavior trajectory acquisition step acquires the system call sequence of the program's dynamic operation, which is the basis of the model;
[0033] The fragmentation step fragments the obtained software behavior track to meet the needs of the mining process;
[0034] The feature extraction and feature library construction steps use the improved sequential pattern mining algorithm (prefixspan-x algorithm) in data mining to obtain frequent subsequence sets of file streams, network streams, and resource streams, and remove normal program behavior track segments to construct malicious behaviors. Feature Library;
[0035] The metric detection step performs metric detection on the real-time running program...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com