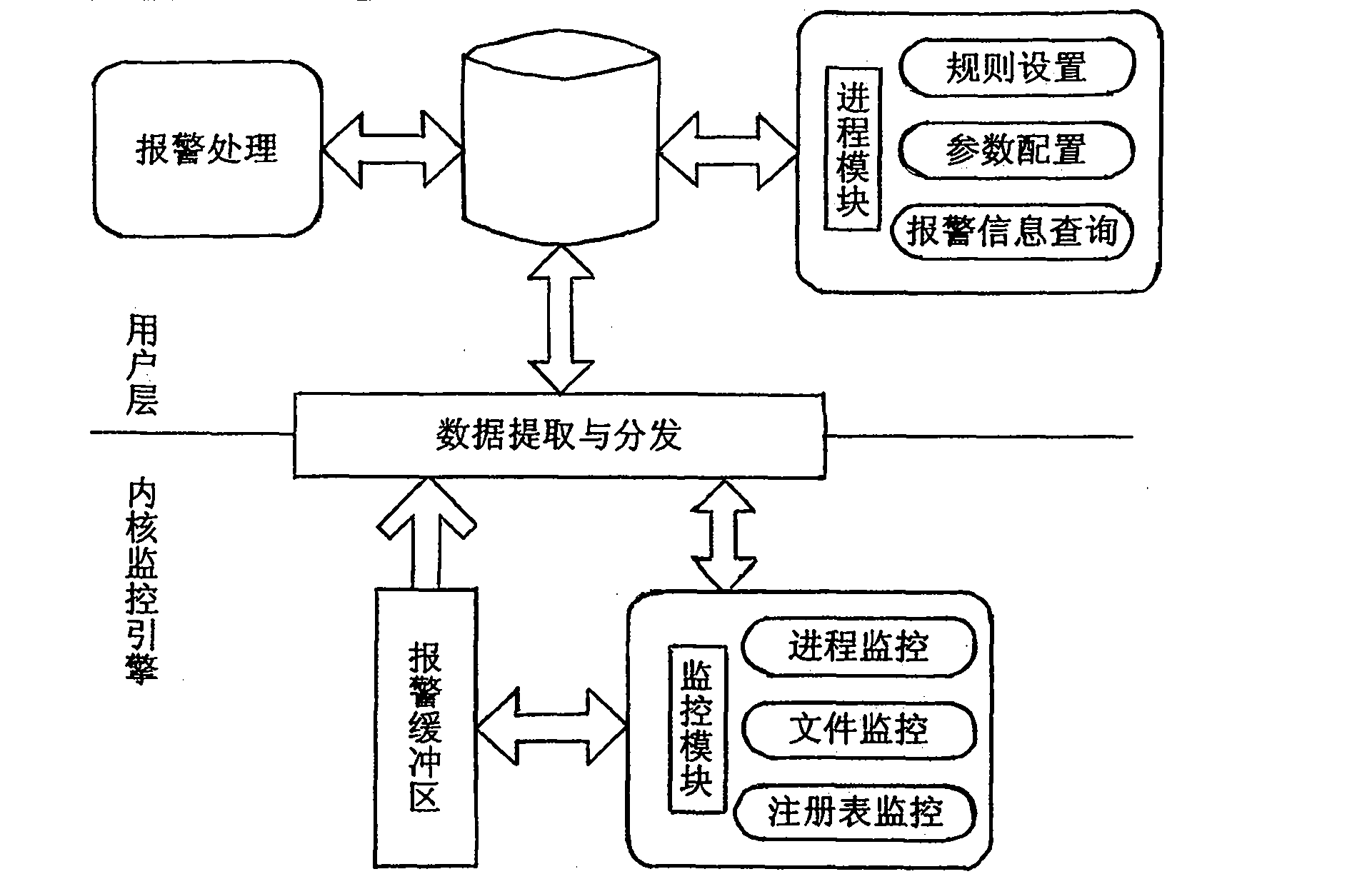
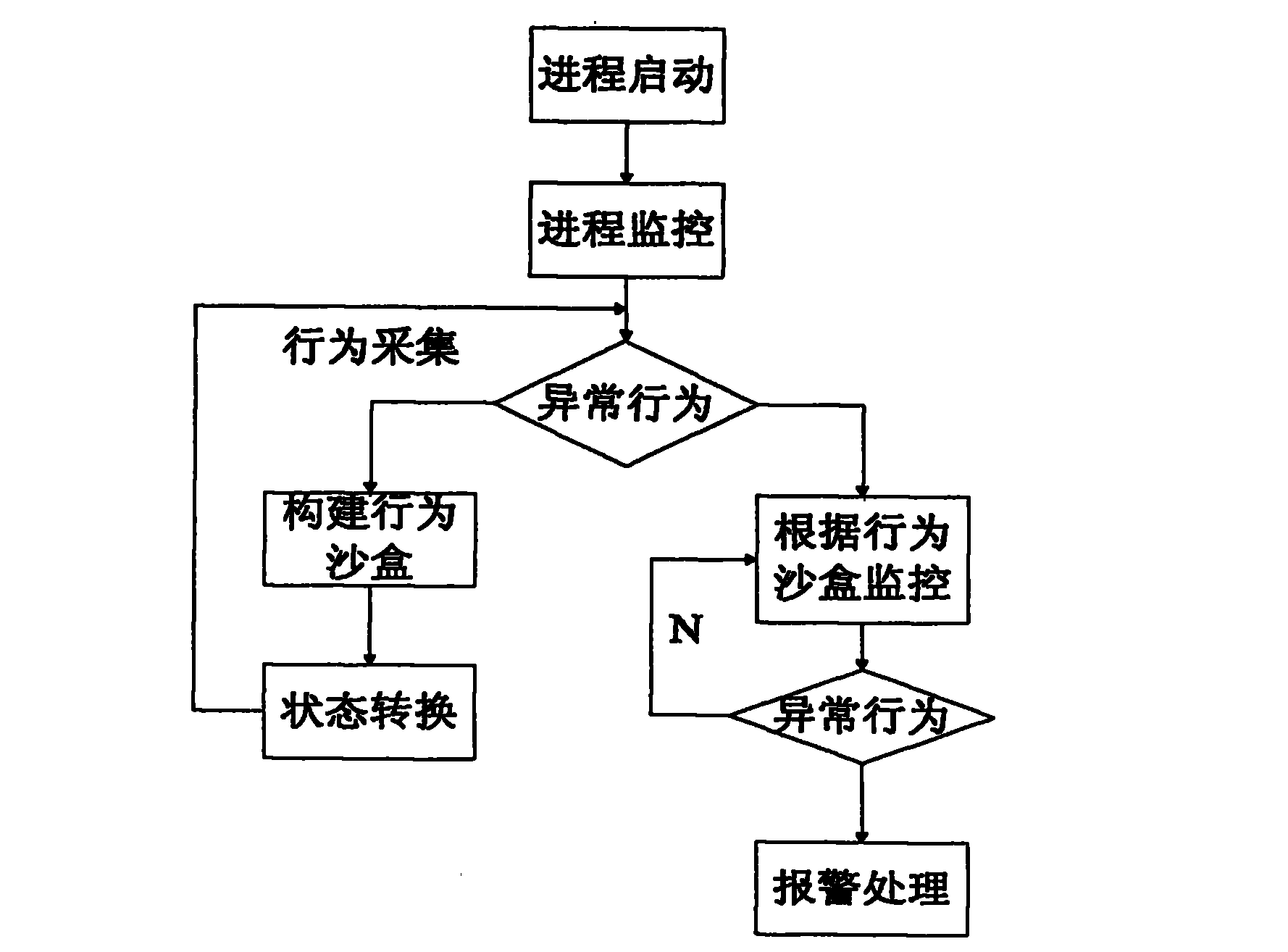
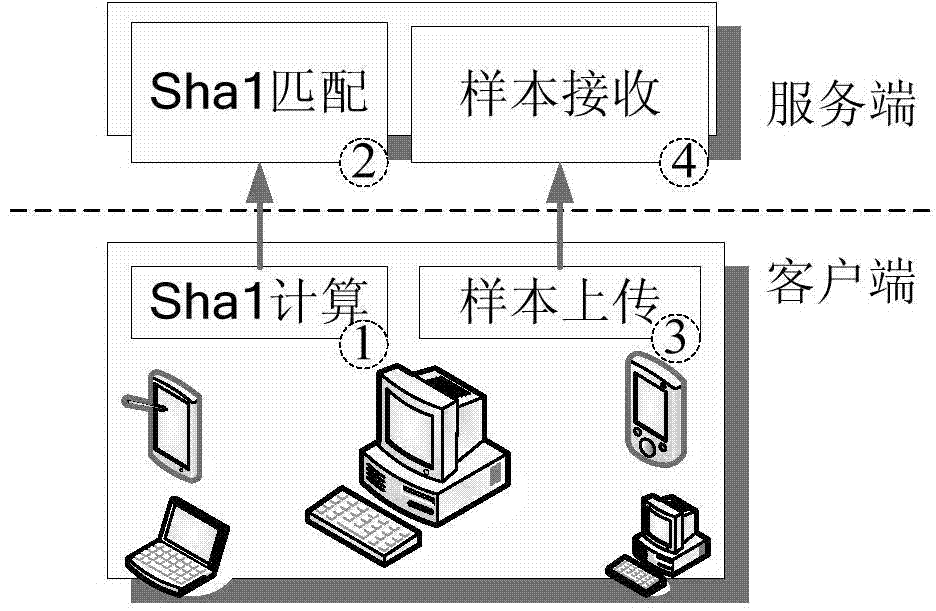
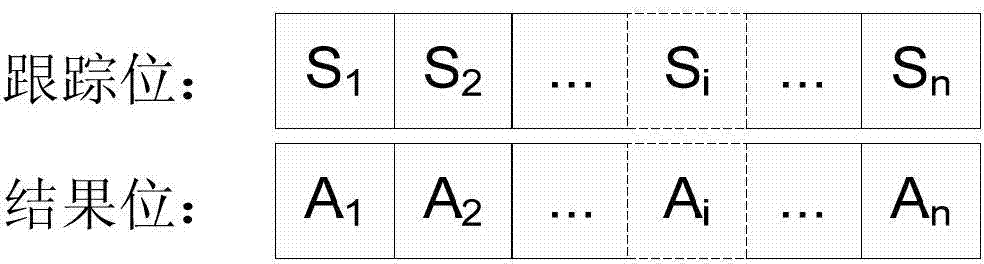
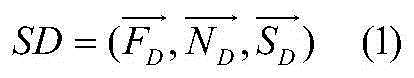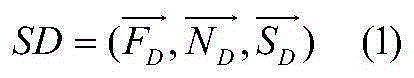Patents
Literature
180 results about "Software behavior" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
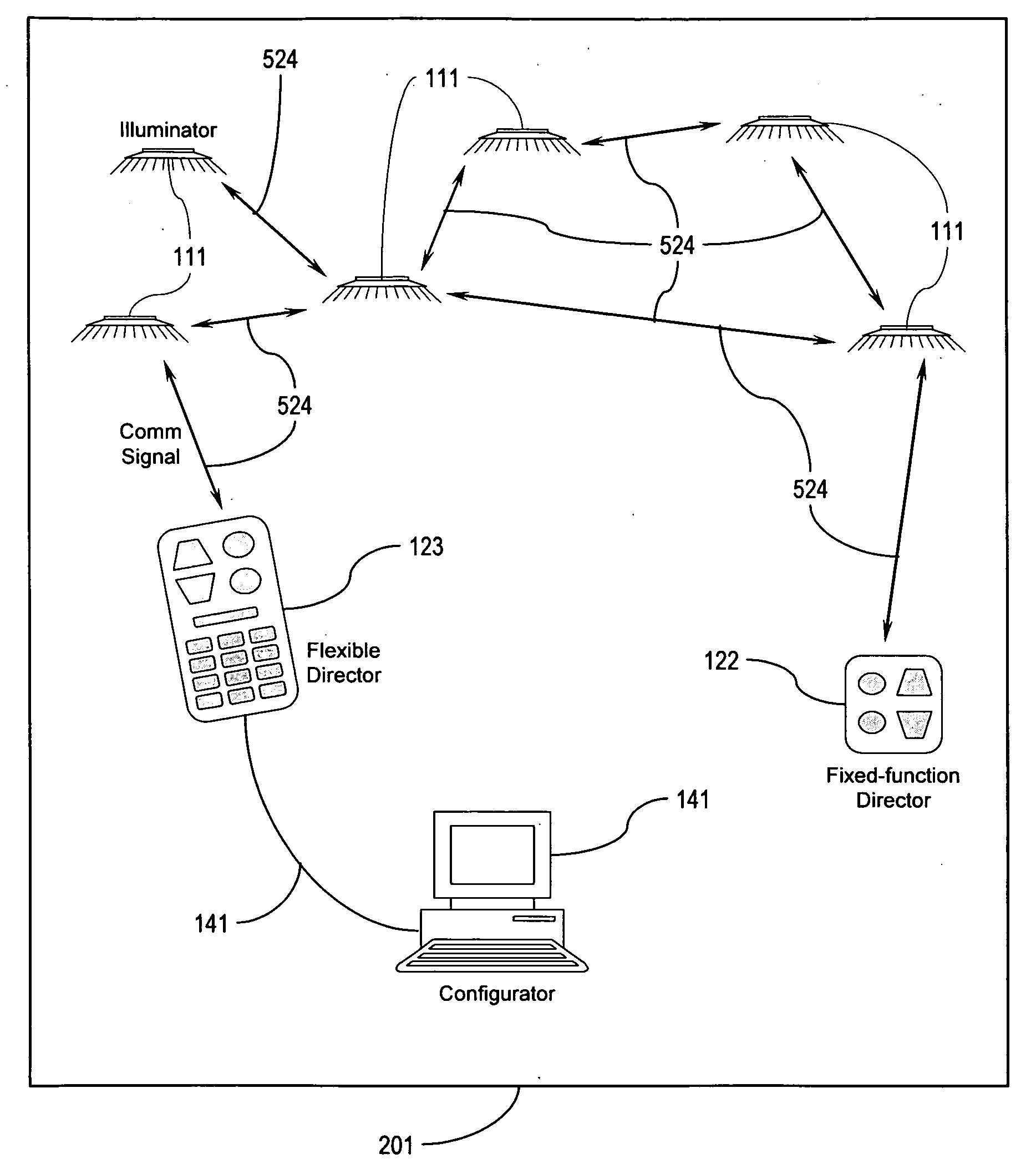
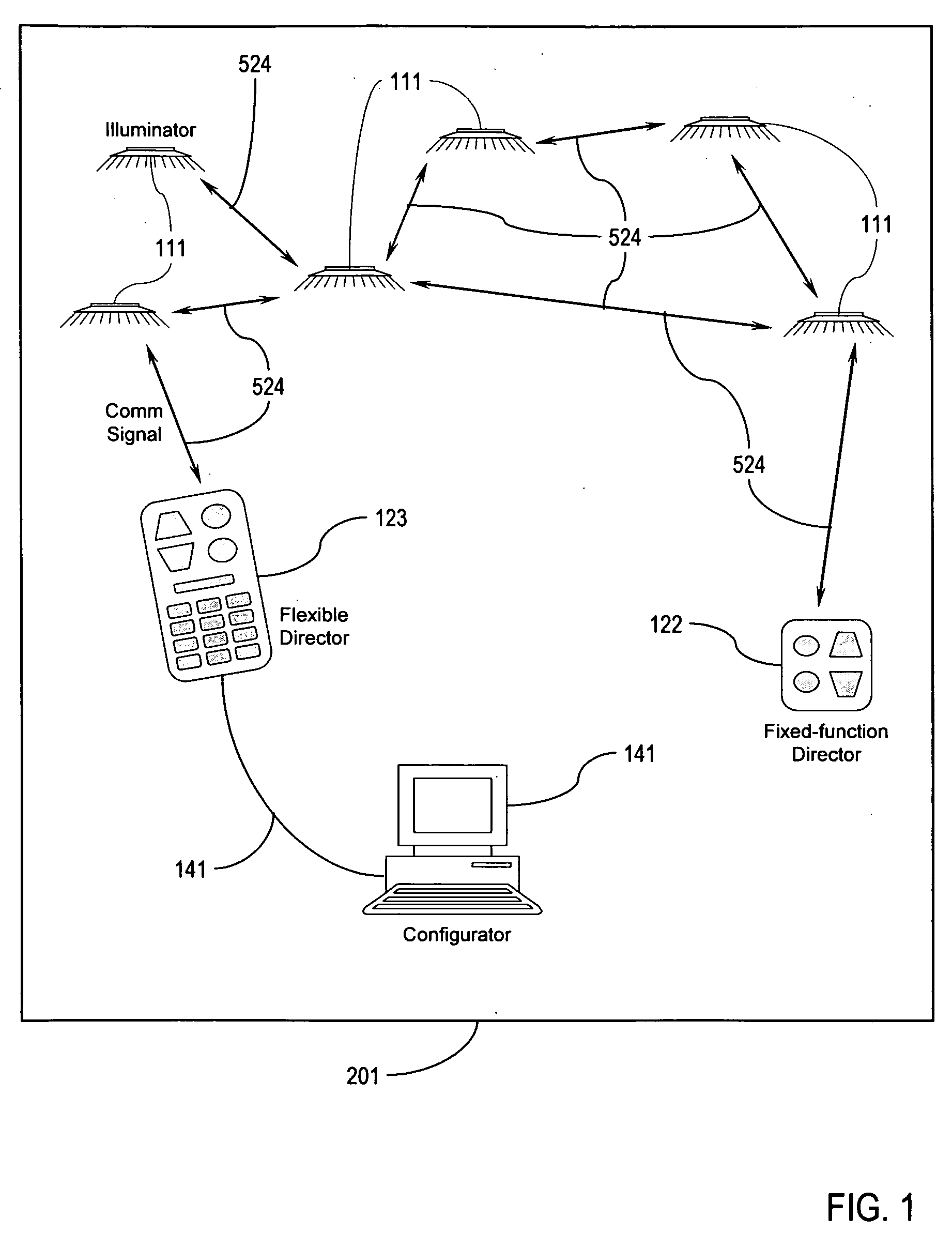
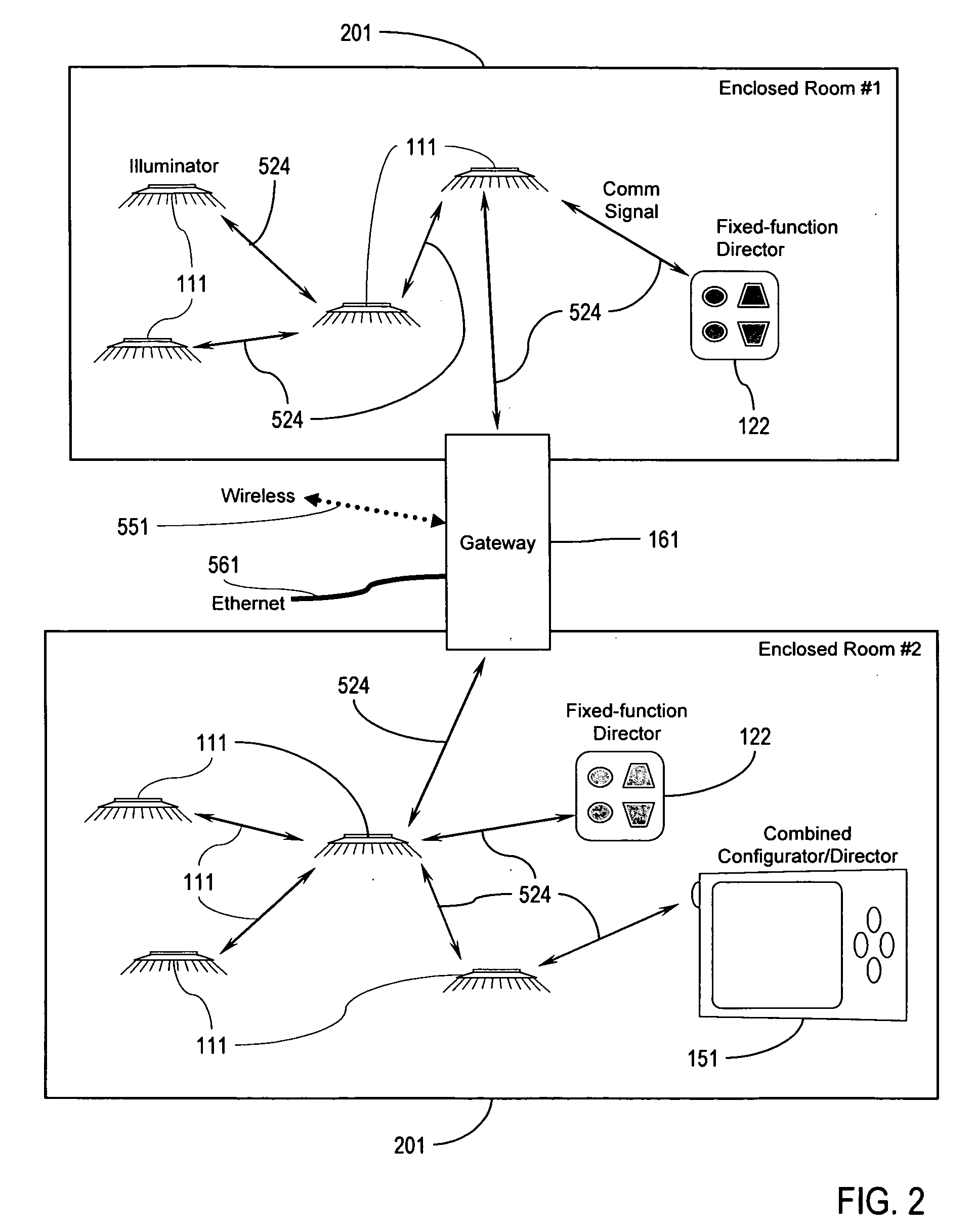
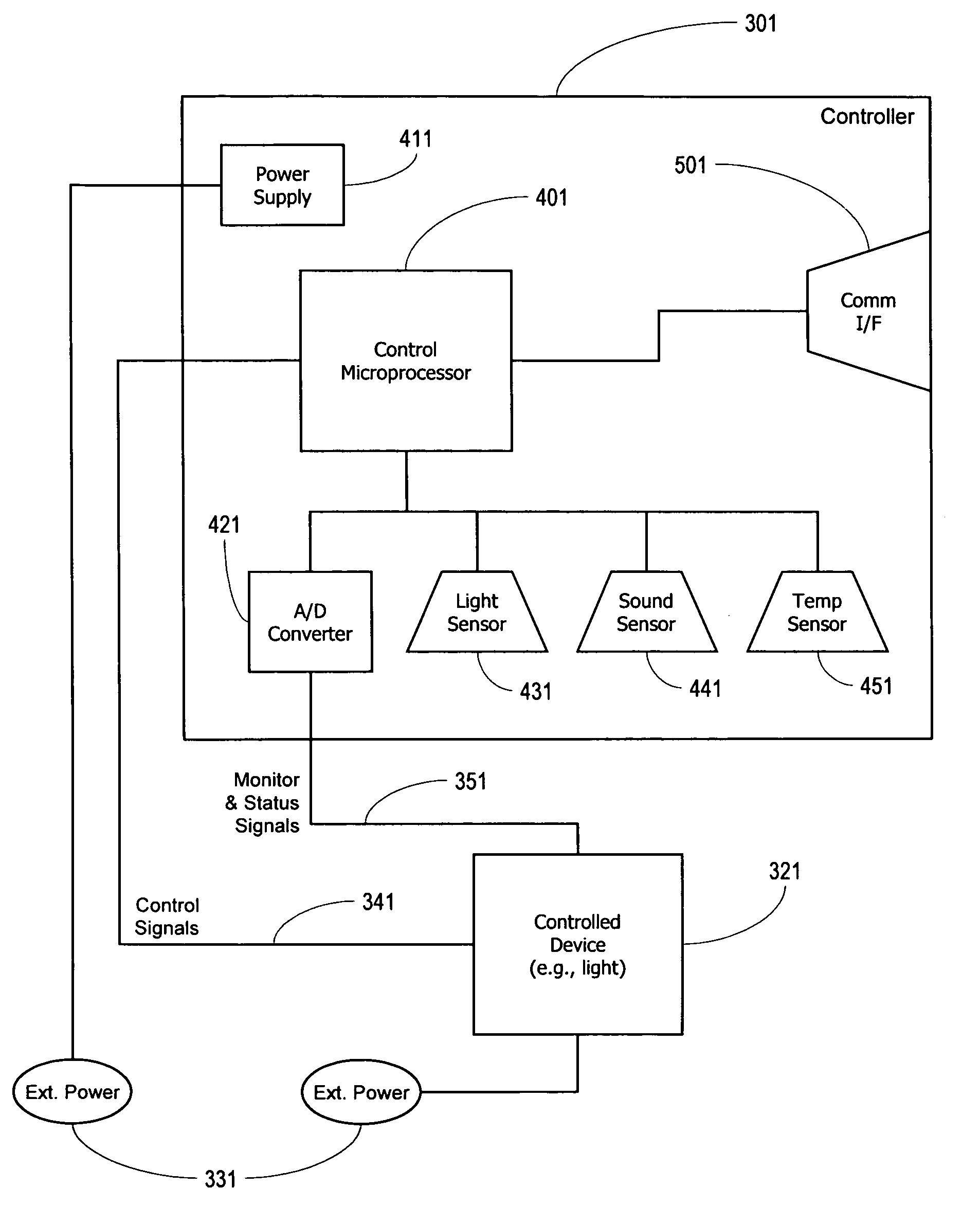
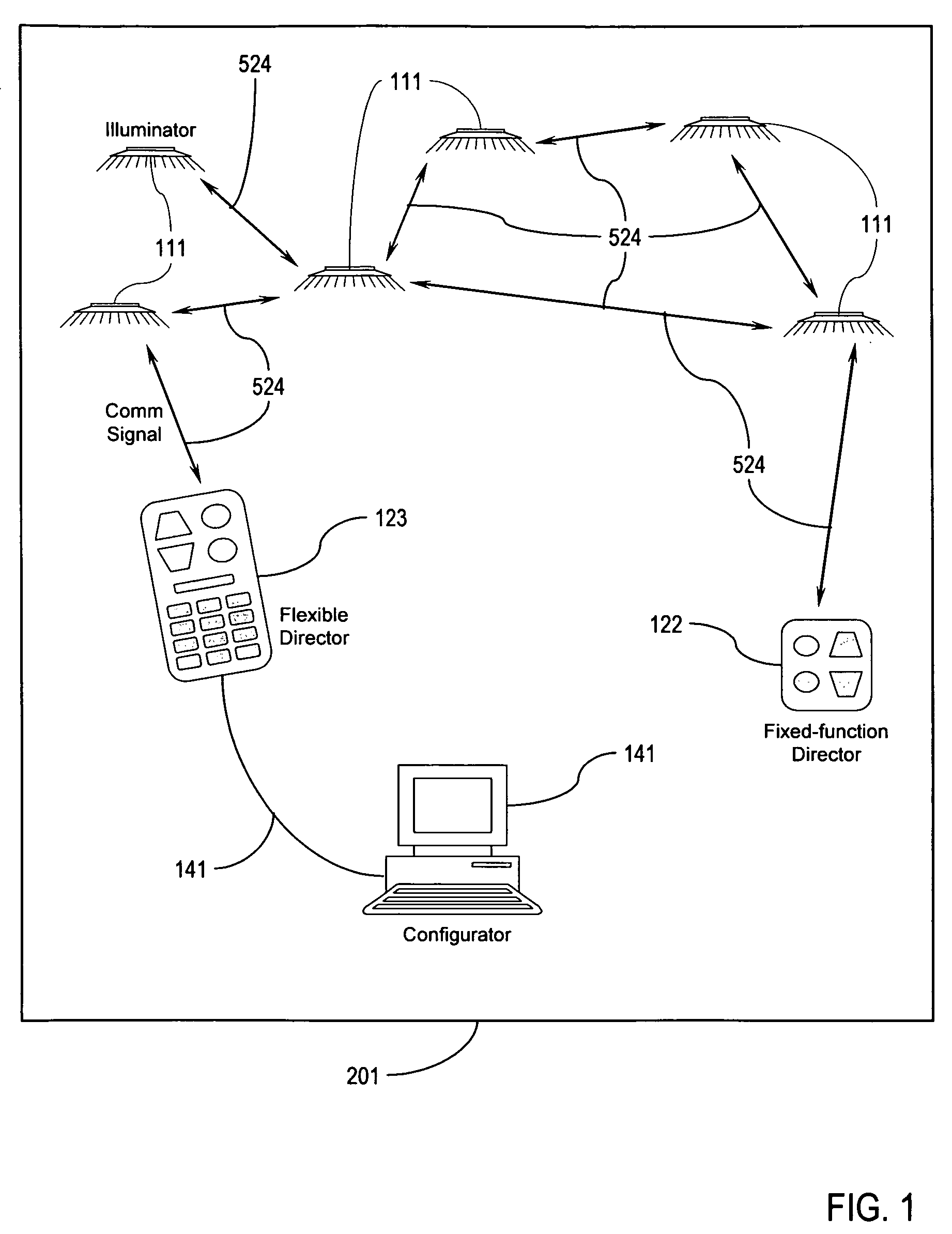
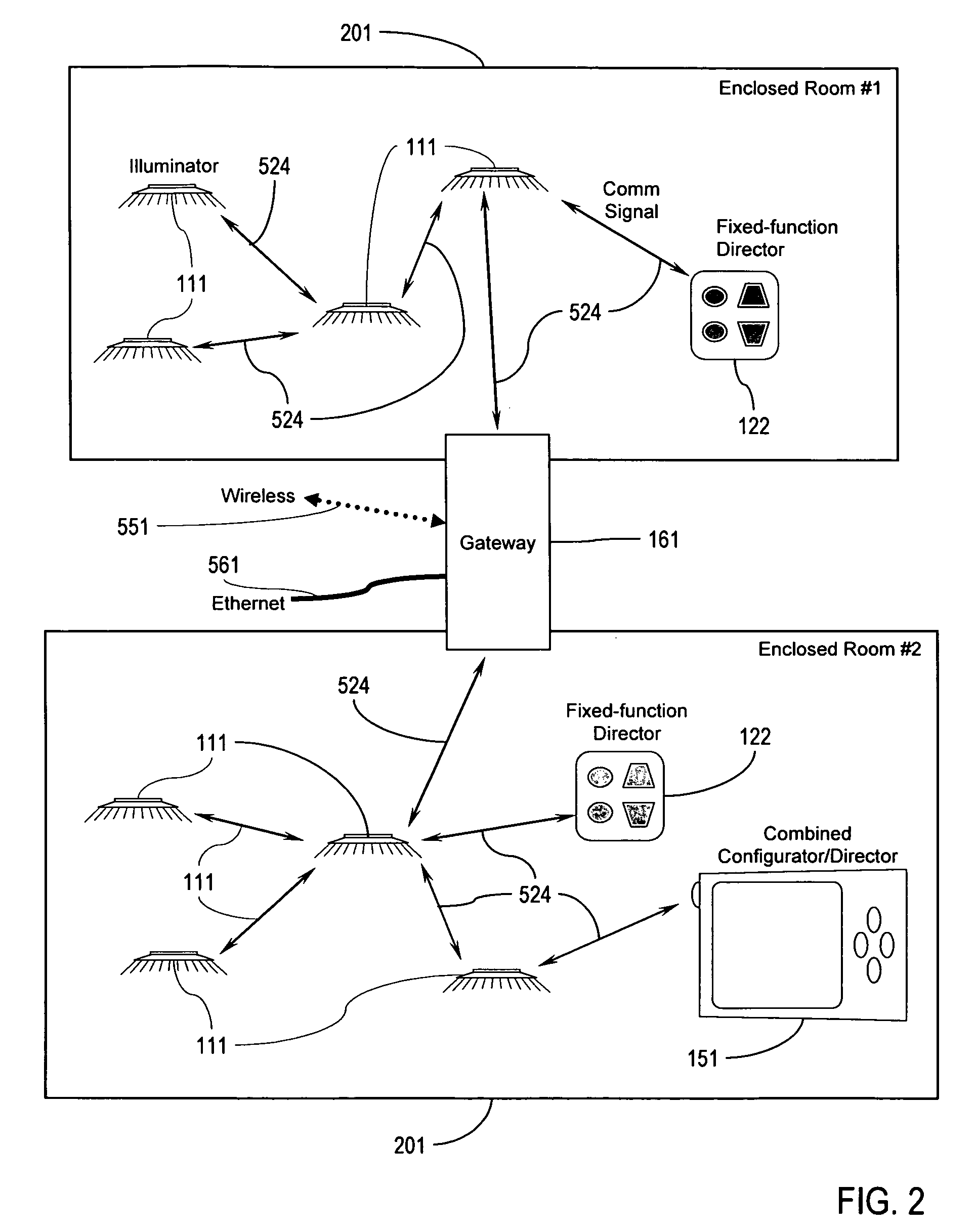
Illumination control network
ActiveUS20080265799A1Easy to adjustCost-effectiveElectrical apparatusElectric light circuit arrangementNetwork controlMovement control
The present invention addresses the problem of providing illumination in a manner that is energy efficient and intelligent. In particular, the present invention uses distributed processing across a network of illuminators to control the illumination for a given environment. The network controls the illumination level and pattern in response to light, sound, and motion. The network may also be trained according to uploaded software behavior modules, and subsets of the network may be organized into groups for illumination control and maintenance reporting.
Owner:SIBERT JULIE CLAIRE +1
Illumination control network
ActiveUS8035320B2Easy to adjustCost-effectiveElectrical apparatusElectric light circuit arrangementNetwork controlComputer module
The present invention addresses the problem of providing illumination in a manner that is energy efficient and intelligent. In particular, the present invention uses distributed processing across a network of illuminators to control the illumination for a given environment. The network controls the illumination level and pattern in response to light, sound, and motion. The network may also be trained according to uploaded software behavior modules, and subsets of the network may be organized into groups for illumination control and maintenance reporting.
Owner:SIBERT JULIE CLAIRE +1
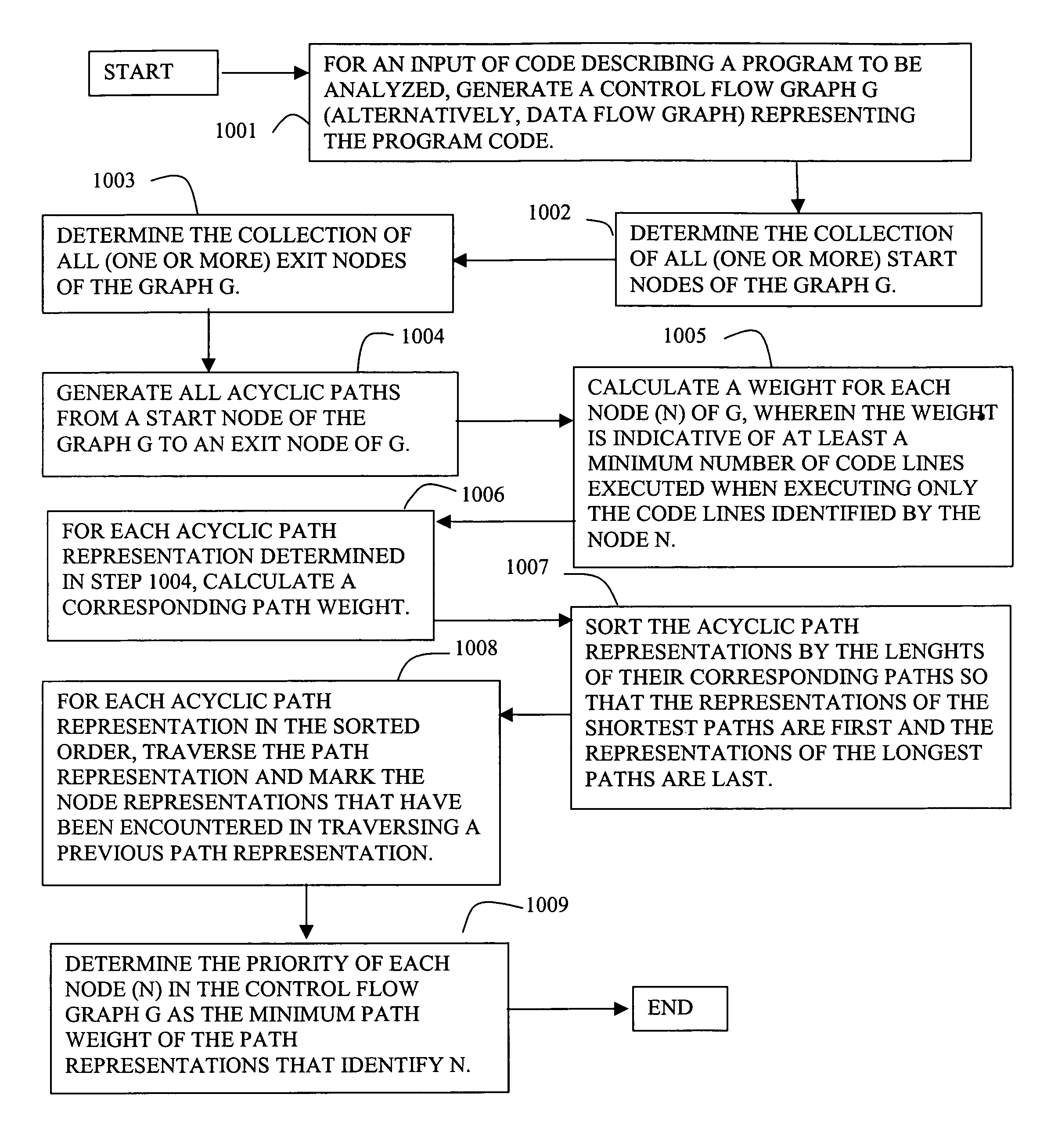
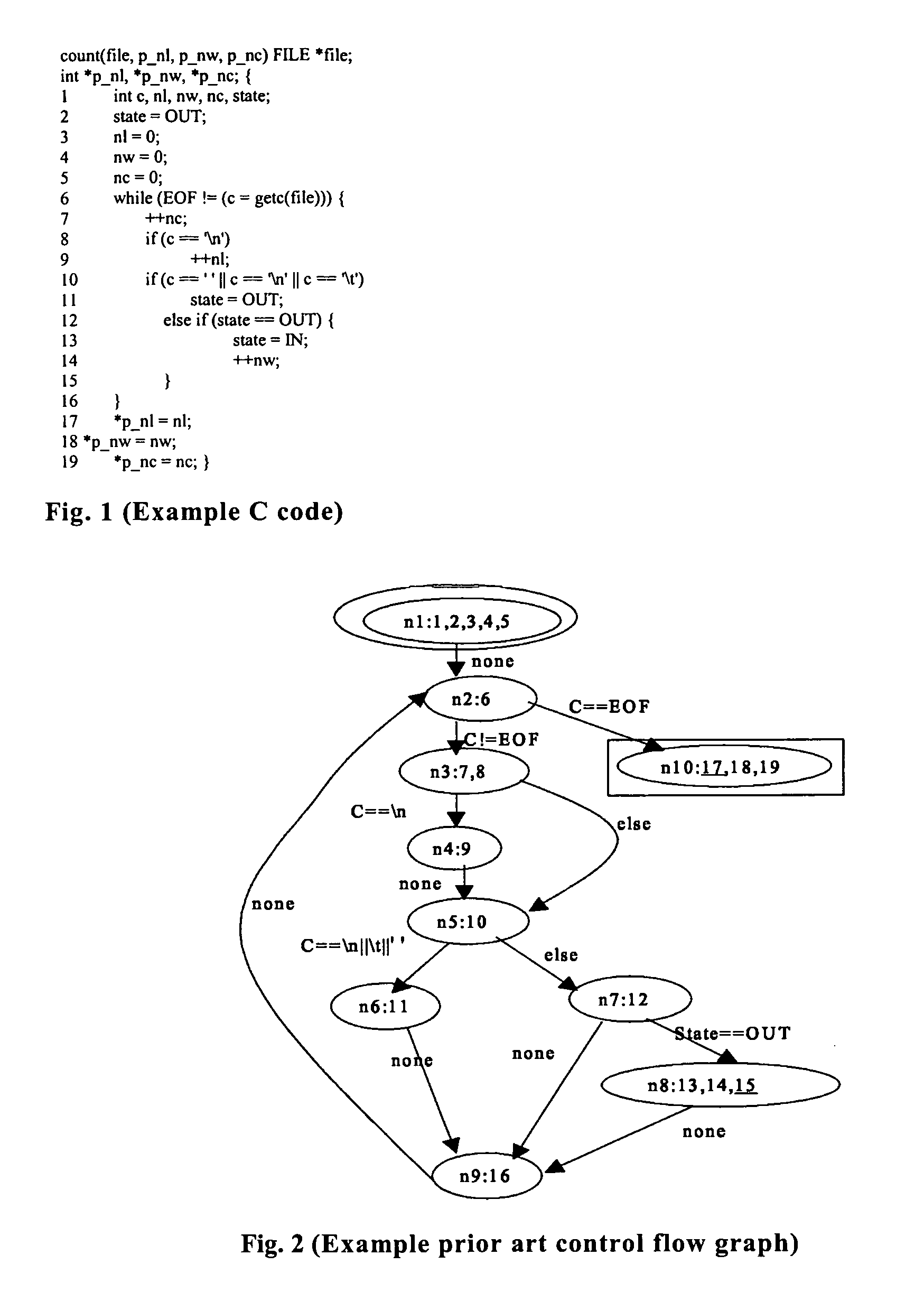
Handling loops in programs and examining feasible software behavior for detecting malicious code
InactiveUS7945898B1Reduce in quantityLess resourcesError detection/correctionAnalogue computers for electric apparatusNODALSoftware system
The present invention is directed to automatically analyzing software systems for identifying faults or bugs and / or detection of malicious code. In various embodiments, the present invention measures code coverage for high priority invocable program elements, uses a relaxed coverage estimation technique that, instead of guaranteeing which code units will be executed, guarantees that at least a certain number of code units will be executed, determines and solves constraints in code to identify infeasible paths containing one or more selected nodes, determines, for a composite data type, a range of values for each of at least two non-composite data fields, and / or translates, prior to code analysis complex code into simpler code having fewer operators.
Owner:AVAYA INC
Malicious software detection system based on P2P dynamic cloud and malicious software detection method
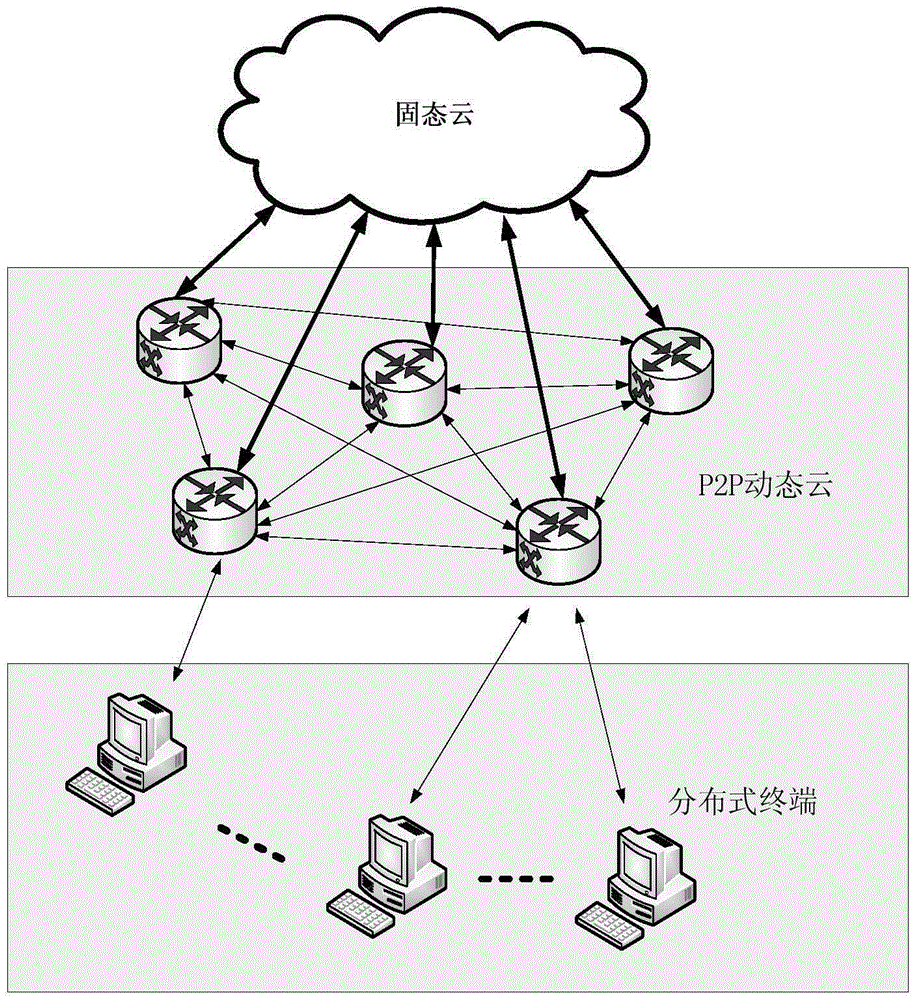
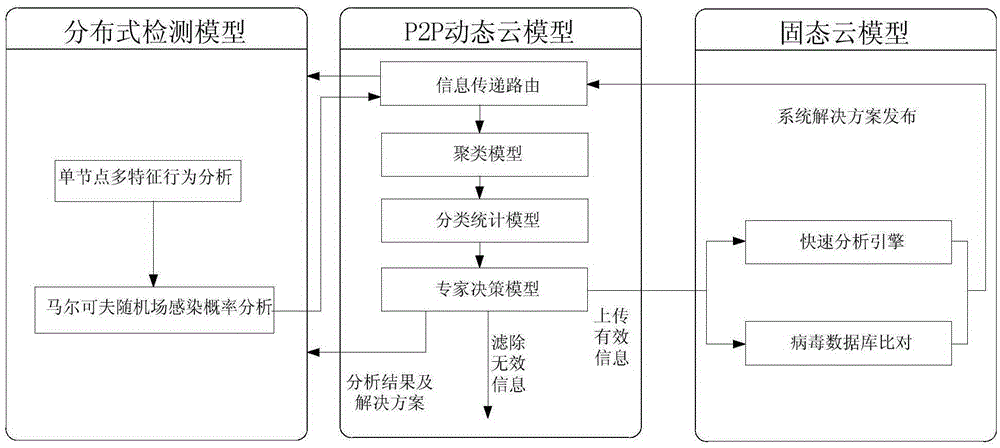
The invention relates to a malicious software detection system based on P2P dynamic cloud and a malicious software detection method. The system comprises a single solid cloud server, multiple dynamic cloud servers and multiple distributed terminals, wherein the multiple dynamic cloud servers form a P2P network, the single solid cloud server and the multiple dynamic cloud servers form a C / S network, the dynamic cloud servers and the distributed terminals form a C / S network, the distributed terminals are used for monitoring abnormality of software behaviors in the network to acquire abnormal behavior characteristics, and the abnormal behavior characteristics are uploaded to the dynamic cloud servers, the dynamic cloud servers are used for analyzing the abnormal behavior characteristics and feeding back the analysis result to the distributed terminals or the solid cloud server, and the solid cloud server is used for carrying out further analysis on the abnormal behavior characteristics uploaded by the dynamic cloud servers and feeding back the analysis result to the distributed terminals through the dynamic cloud servers. Through the system, load of the cloud servers is mitigated, a speed of response to a client request is improved, and precision of detection on the malicious software is improved.
Owner:重庆巴陆科技有限公司
Invading detection method and system based on procedure action
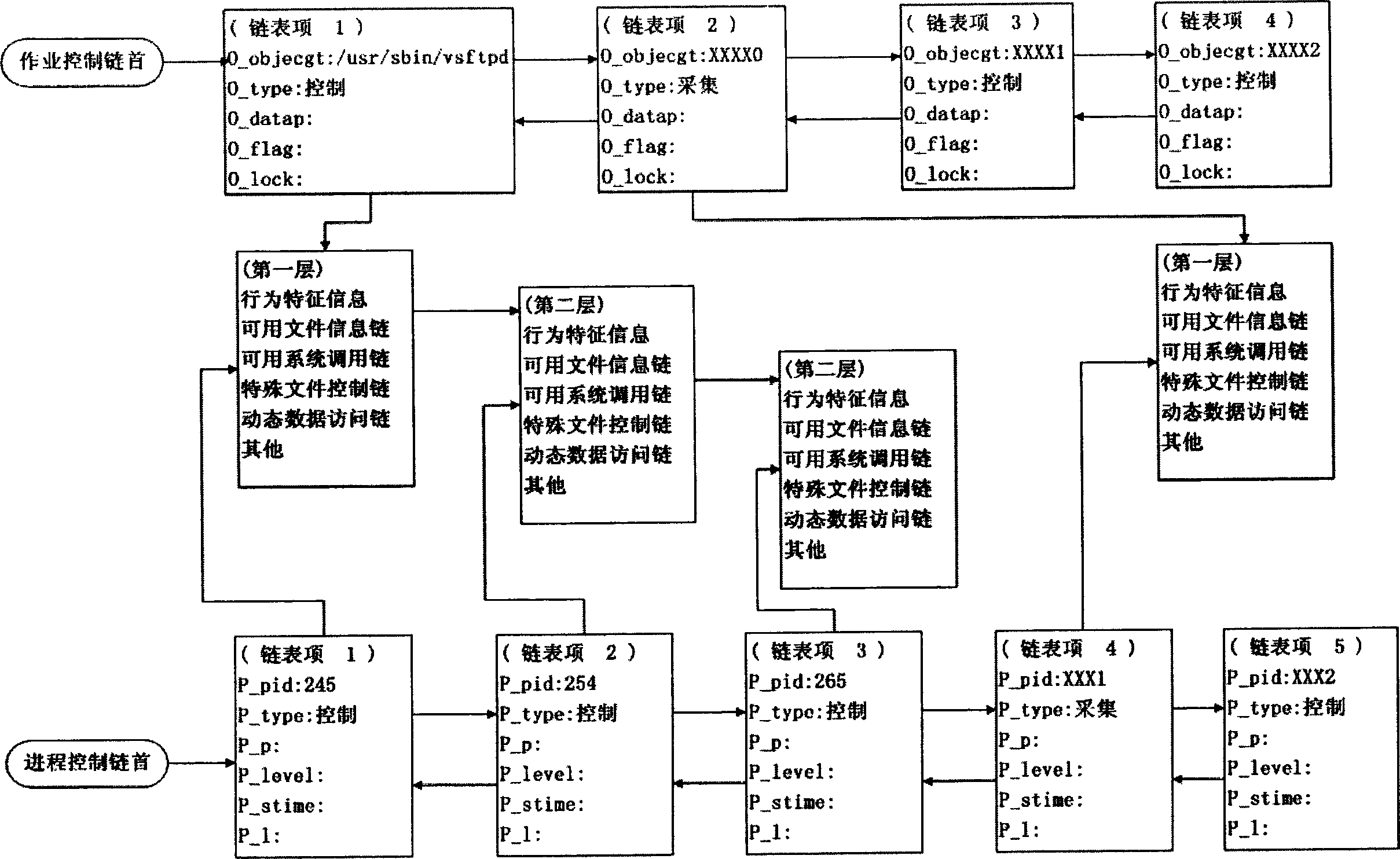
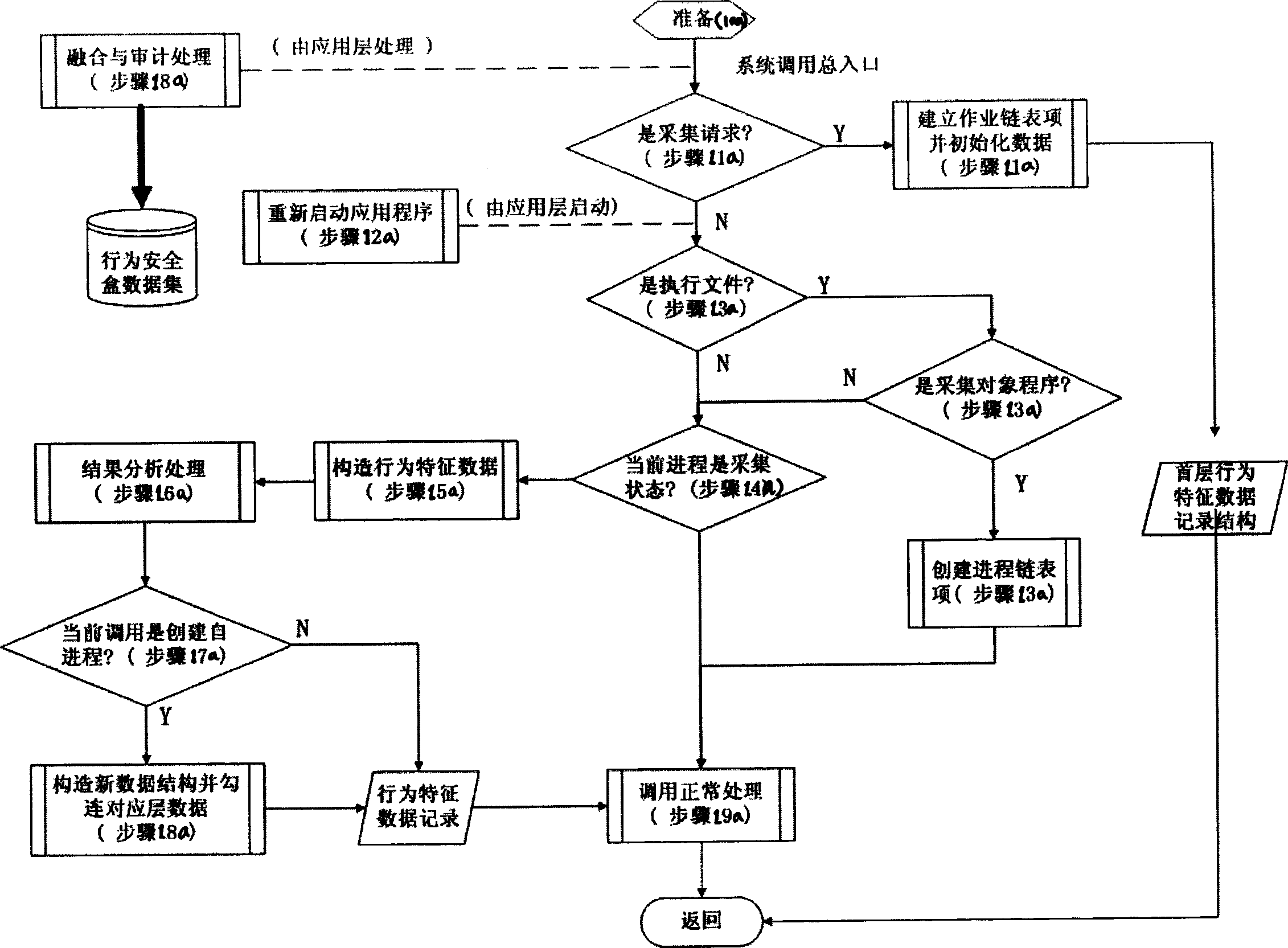
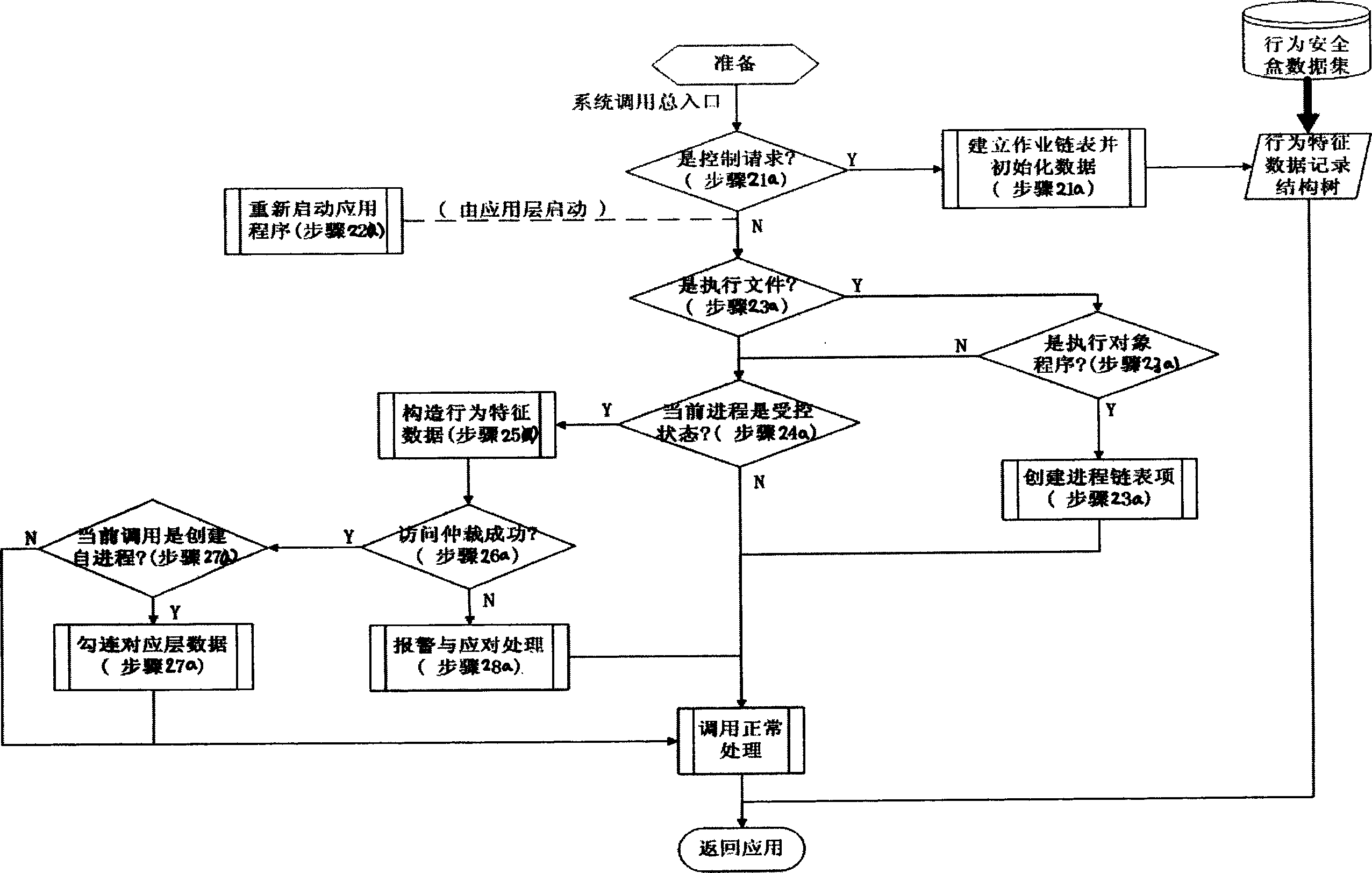
ActiveCN1794645AImprove security defense performanceClear processData switching networksClose couplingNetwork security policy
This invention discloses a method for testing inbreak, which obtains the information of software behavior characters of a program, a structure access model and acts it on the program to prevent abnormal behavior so as to protect the entire network server system to avoid network inbreak including the following basic processes: collecting and processing a behavior security box to monitor the software behavior timely and a protection system suitable for the above mentioned method is also disclosed to realize the close coupling control to the behavior of the applied program.
Owner:上海浦东软件园信息技术股份有限公司
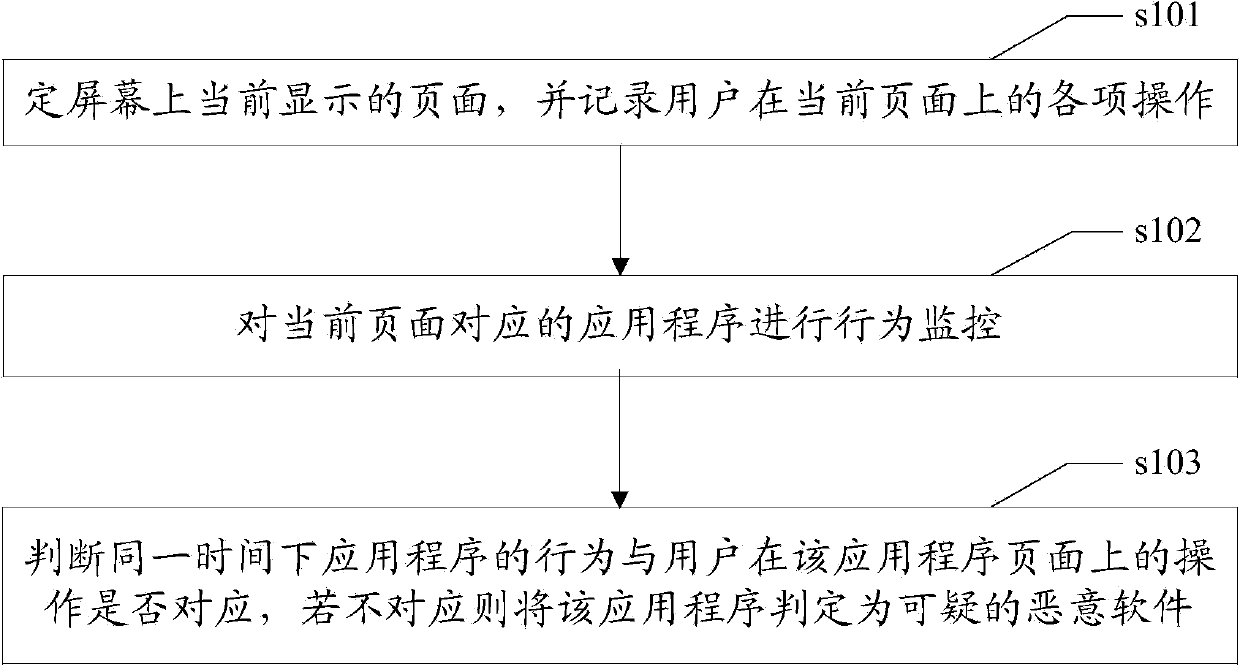
Method and device for detecting malicious software of intelligent mobile terminal
ActiveCN104217164AEasy to identifyImprove versatilityPlatform integrity maintainanceRemote controlMalware
The invention discloses a method and a device for detecting malicious software of an intelligent mobile terminal. The user operation is compared with a software behavior and according to behavior characteristics, the malicious software is identified. For continuously emerging new viruses or virus mutations, compared with a conventional detection method, the method and the device do not depend on a malicious code section feature library and a malicious function calling sequence feature library and are also limited to known malicious software, and thus, the method and the device have high universality and high detection rate, malicious behaviors such as malicious charging, privacy stealing and remote control can be well identified and reliable guarantee is provided for safety use of the intelligent mobile terminal.
Owner:FIFTH ELECTRONICS RES INST OF MINIST OF IND & INFORMATION TECH
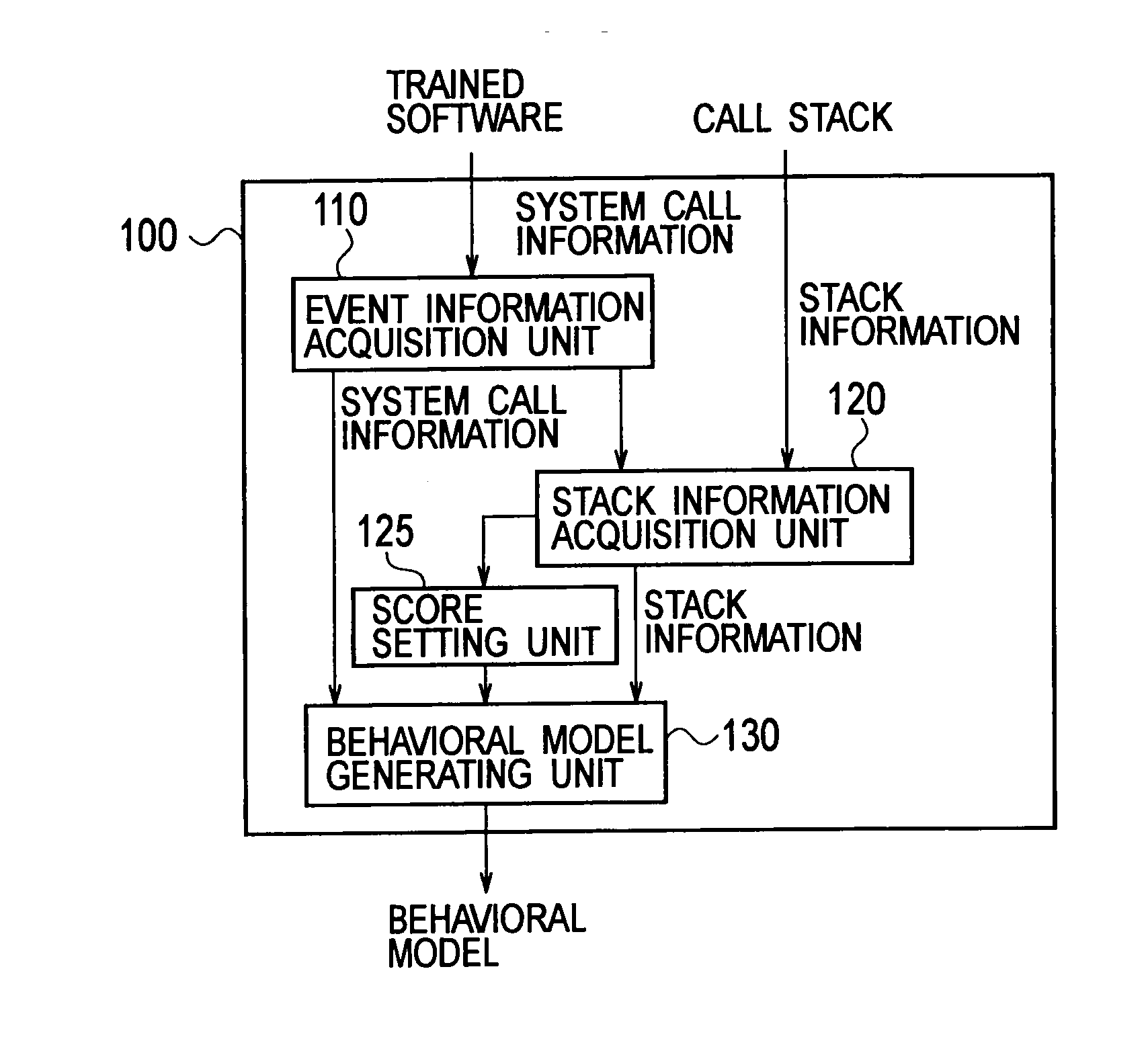
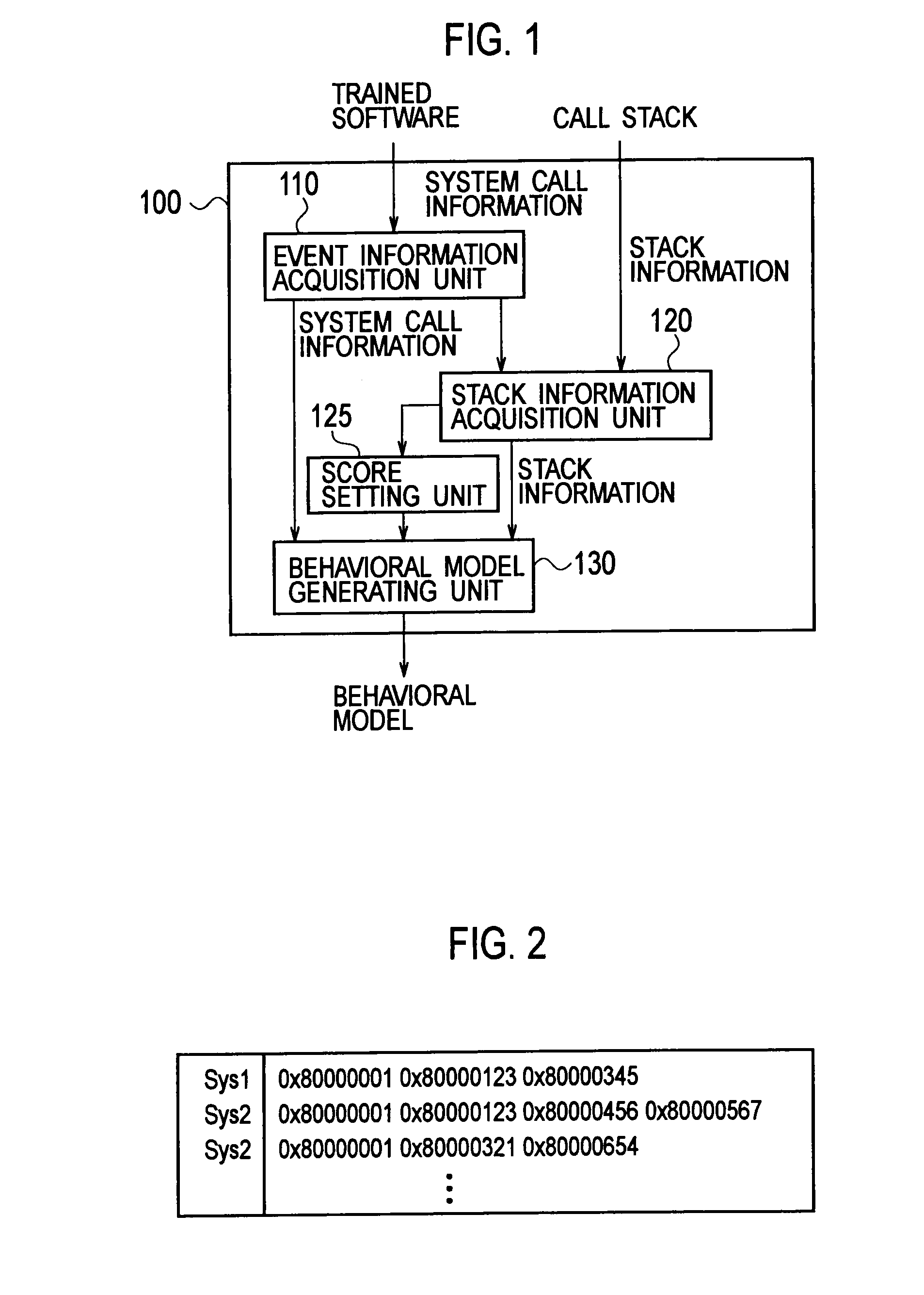
Software behavior modeling device, software behavior modeling method, software behavior verification device, and software behavior verification method
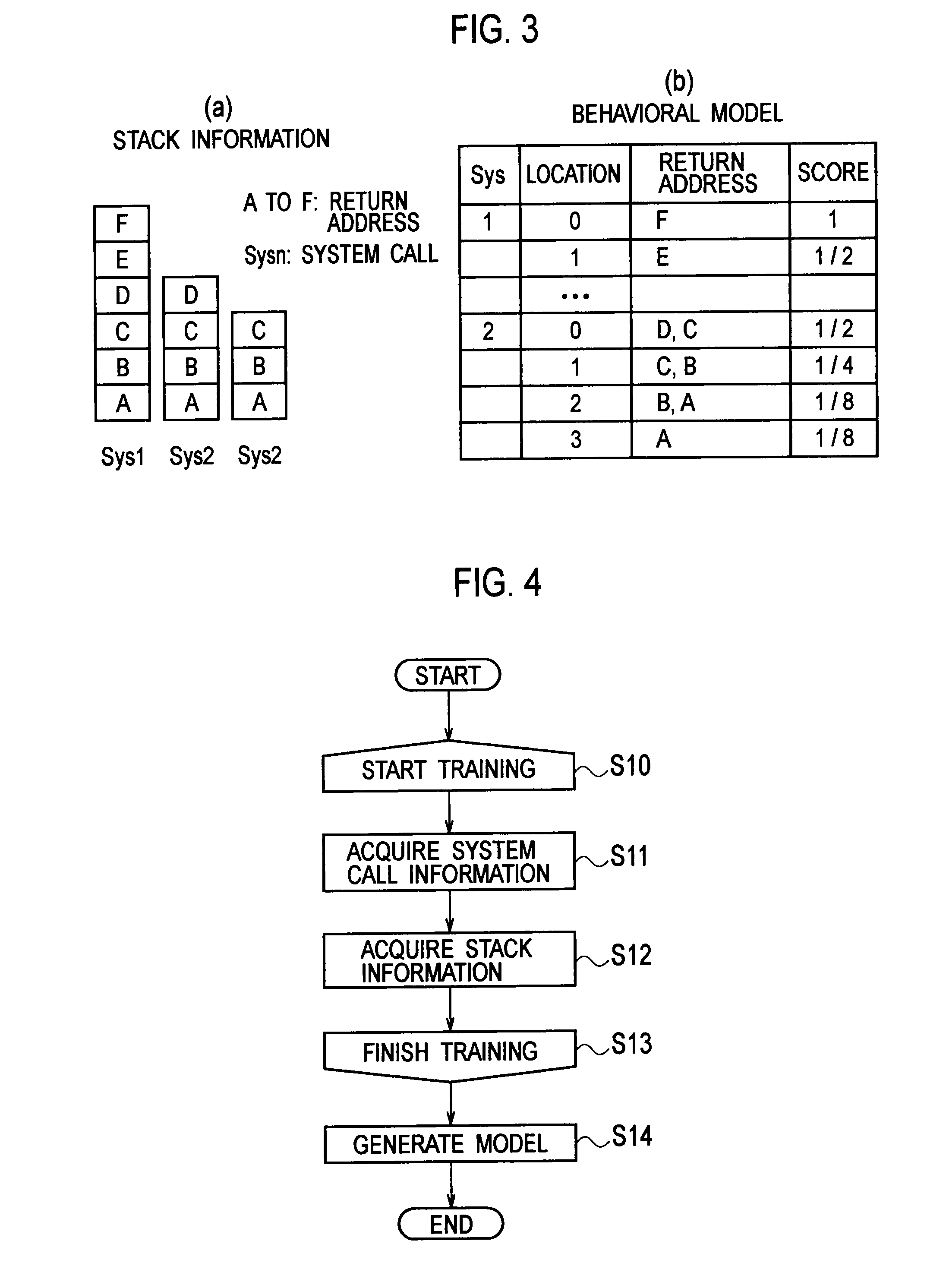
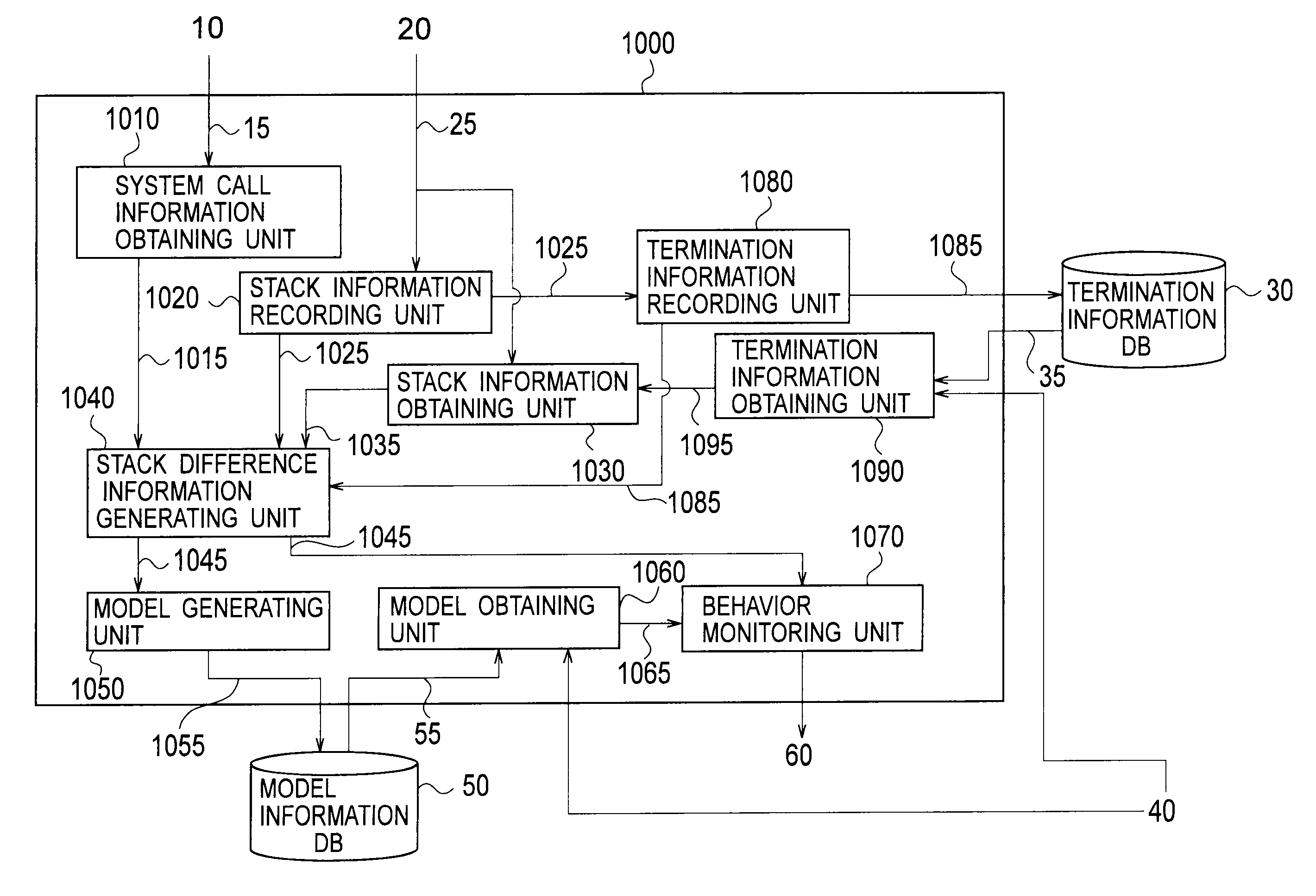
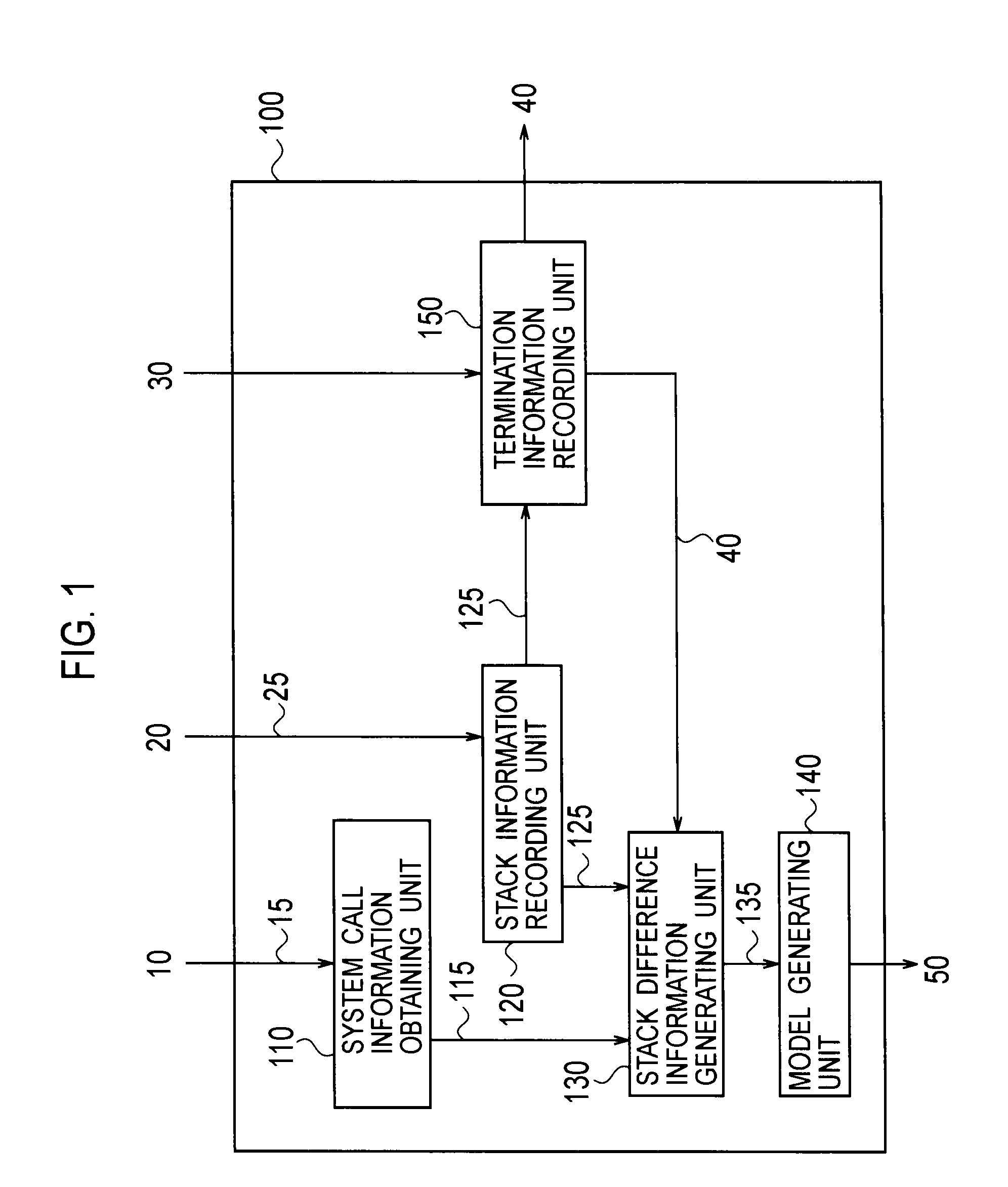
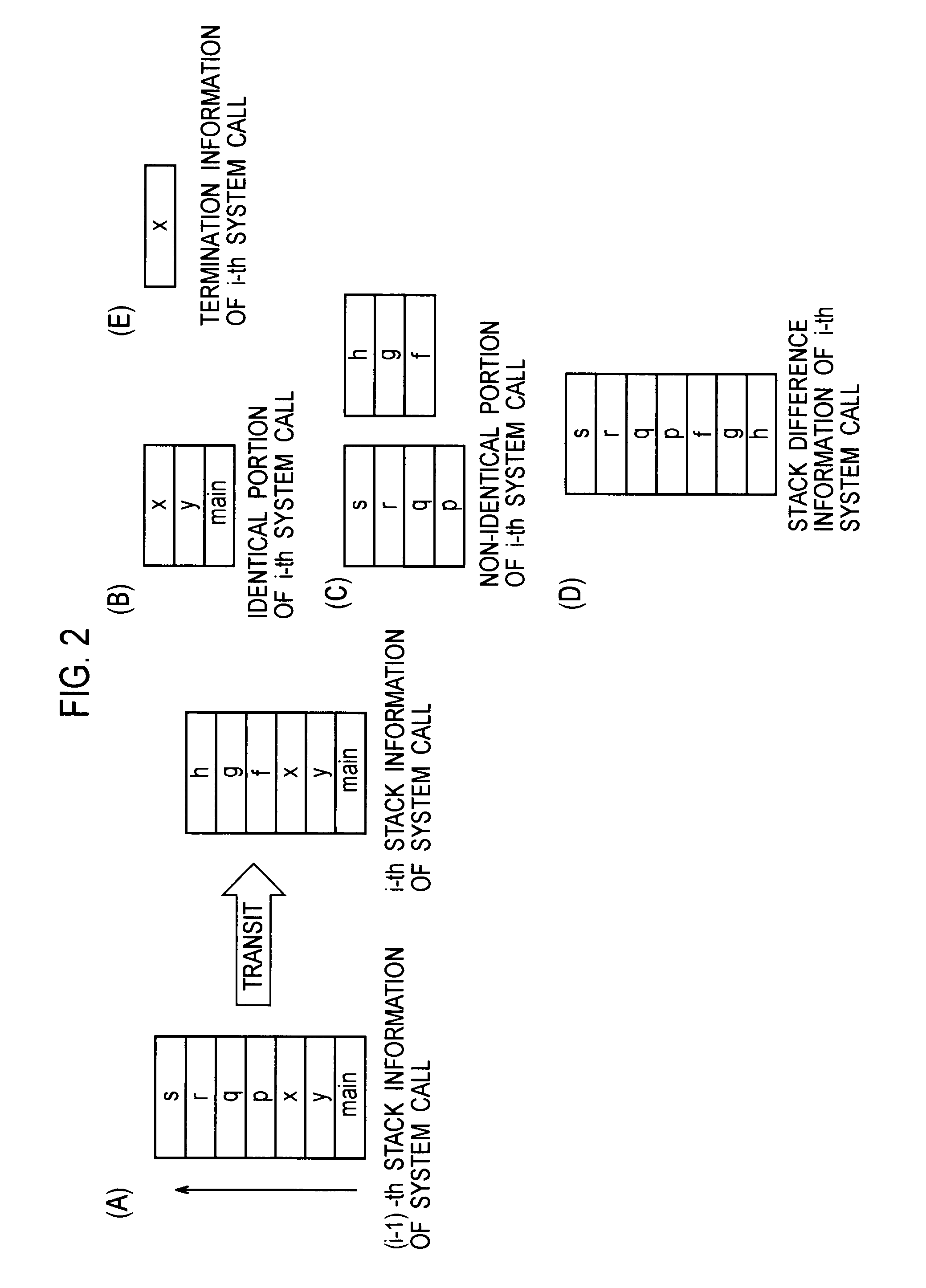
InactiveUS20110154487A1Improve accuracyReduce processing loadMemory loss protectionError detection/correctionCall stackSoftware engineering
A software behavior modeling device which forms a model of a behavior of software includes; an event information acquisition unit configured to acquire event information indicating a specific event which occurs during execution of the software; a stack information acquisition unit configured to acquire stack information stored in a call stack at a time of occurrence of the specific event; a score setting unit configured to set a score in accordance with a storage location in which each element included in the stack information is stored in the call stack; and a model generating unit configured to form a model of a relationship between the specific event and the element by using the score, and to generate a behavior model of the software.
Owner:NTT DOCOMO INC
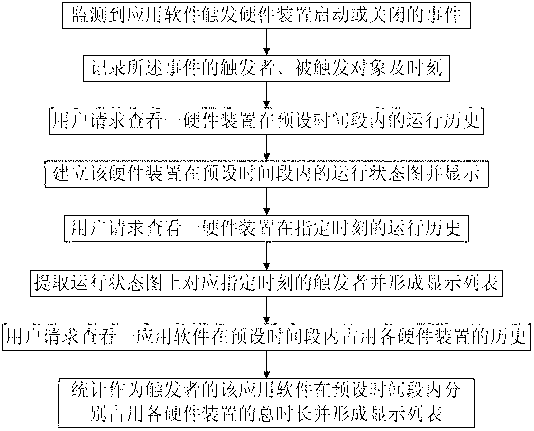
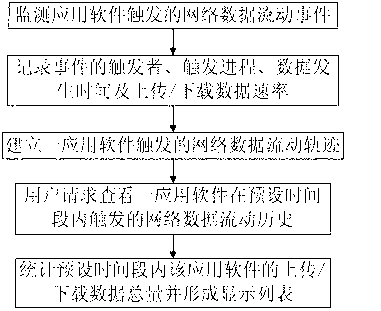
Data monitoring method and data monitoring system for software behavior of mobile terminal
ActiveCN103106130AReduce power lossEnergy efficient ICTHardware monitoringStaging operationState diagram
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
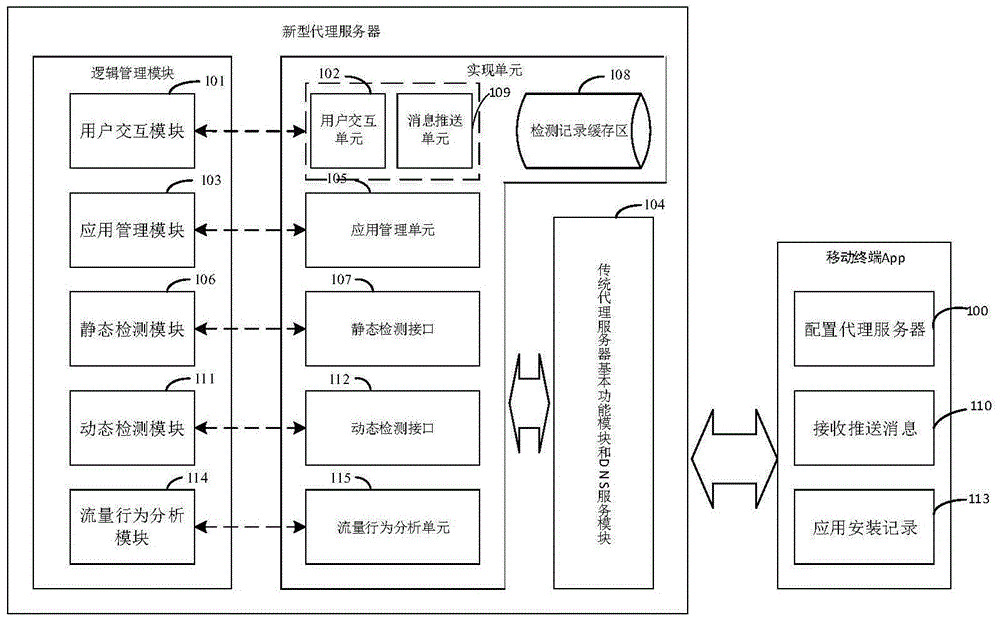
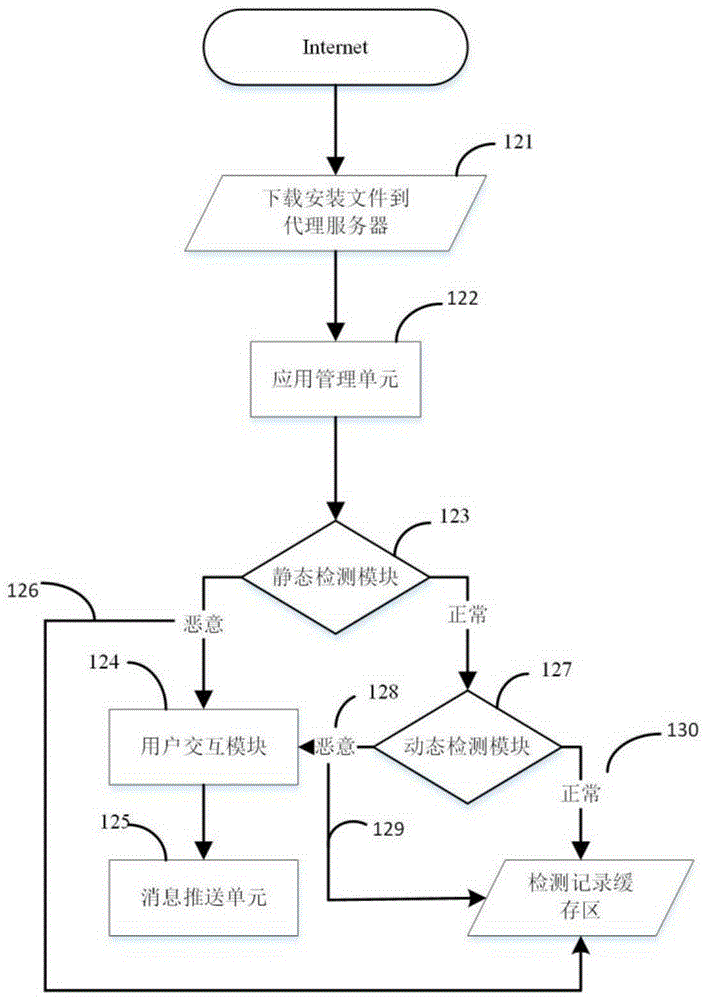
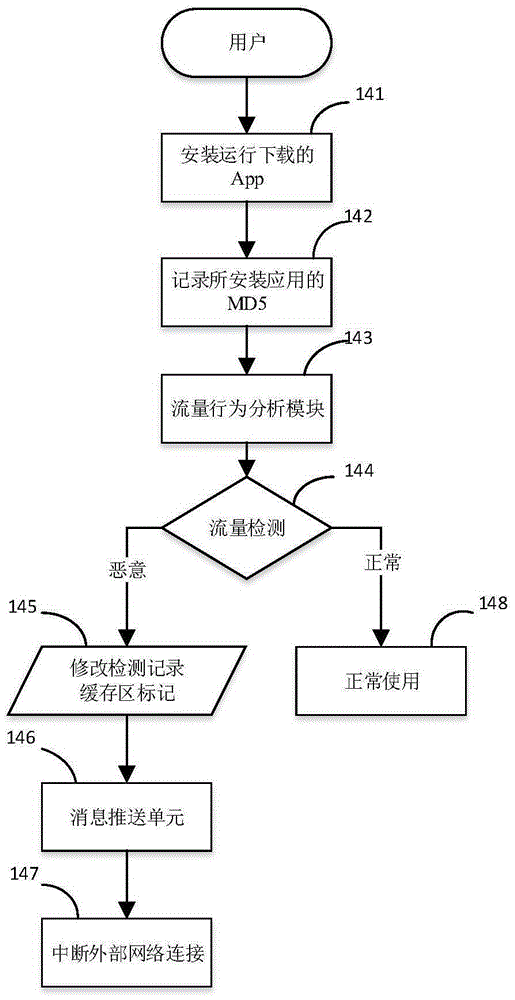
Proxy server having mobile terminal malicious software behavior detection capability and method
The invention discloses a proxy server having a mobile terminal malicious software behavior detection capability and a method. The proxy server comprises a static detection module, a dynamic detection module and a flow behavior analysis module, wherein the static detection module is used for performing static detection on downloaded mobile applications by calling a static detection interface; the dynamic detection module is used for performing secondary detection on the mobile applications which are detected to be normal by the static detection module by calling an API interface provided by a third-party dynamic detection service; and the flow behavior analysis module is used for processing flow of applications installed by a user and detecting whether flow behaviors are generated by malicious software or not through a flow detection service model. A novel proxy server having a triple detection capability is designed. Through primary and secondary detection, the security of the mobile applications installed by the user is basically ensured. Through tertiary flow detection, effective identification of malicious behaviors generated by the malicious software is ensured.
Owner:UNIV OF JINAN
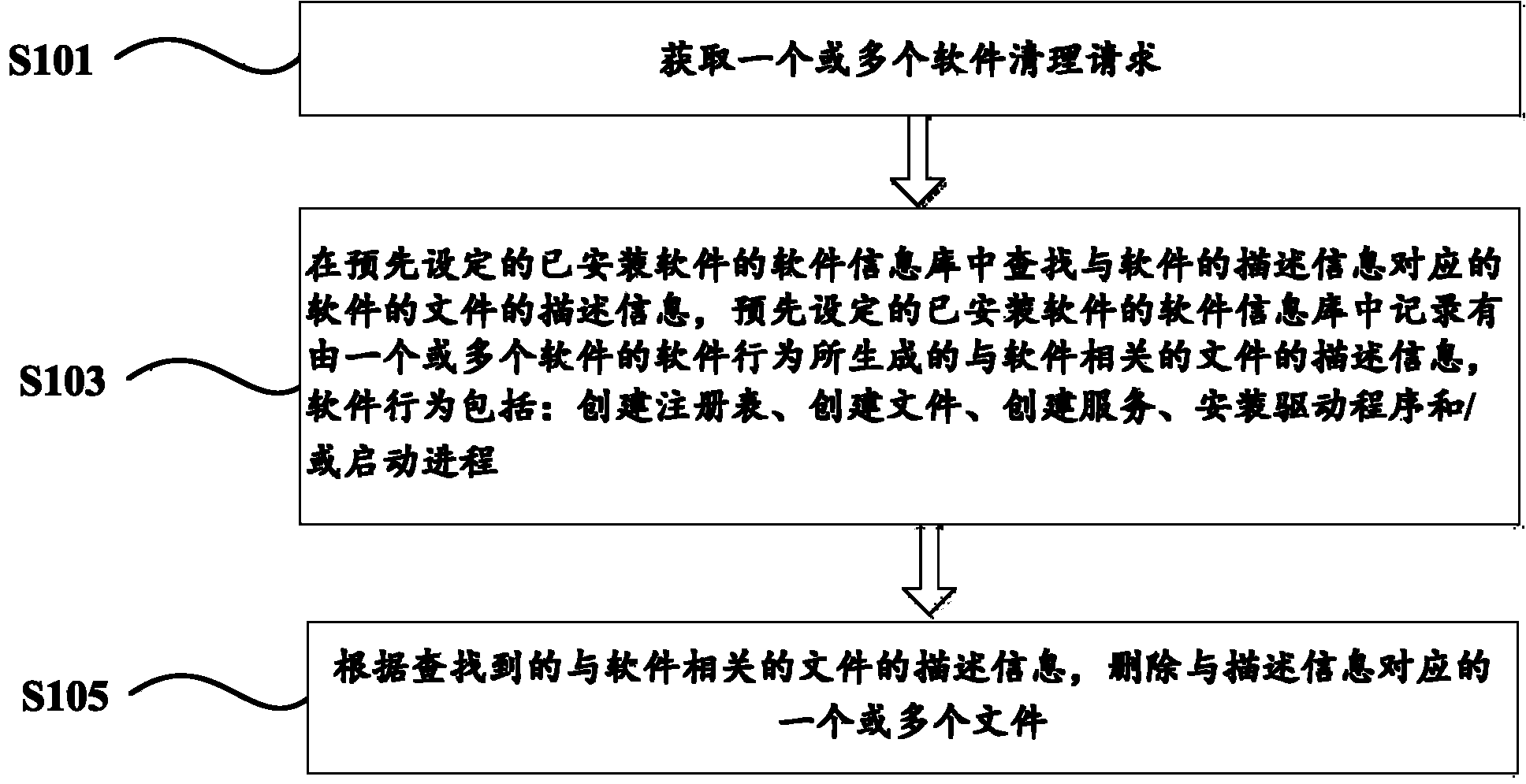
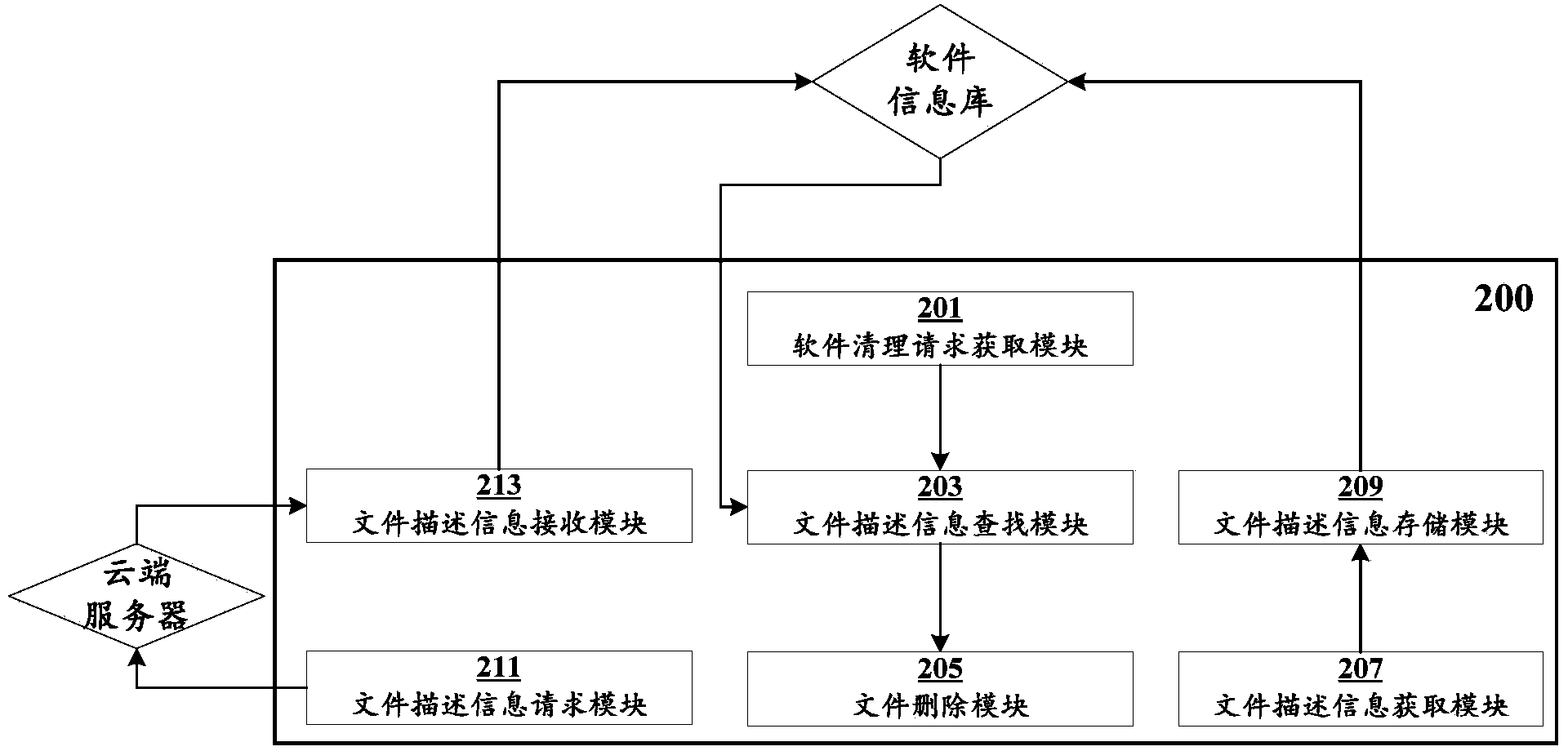
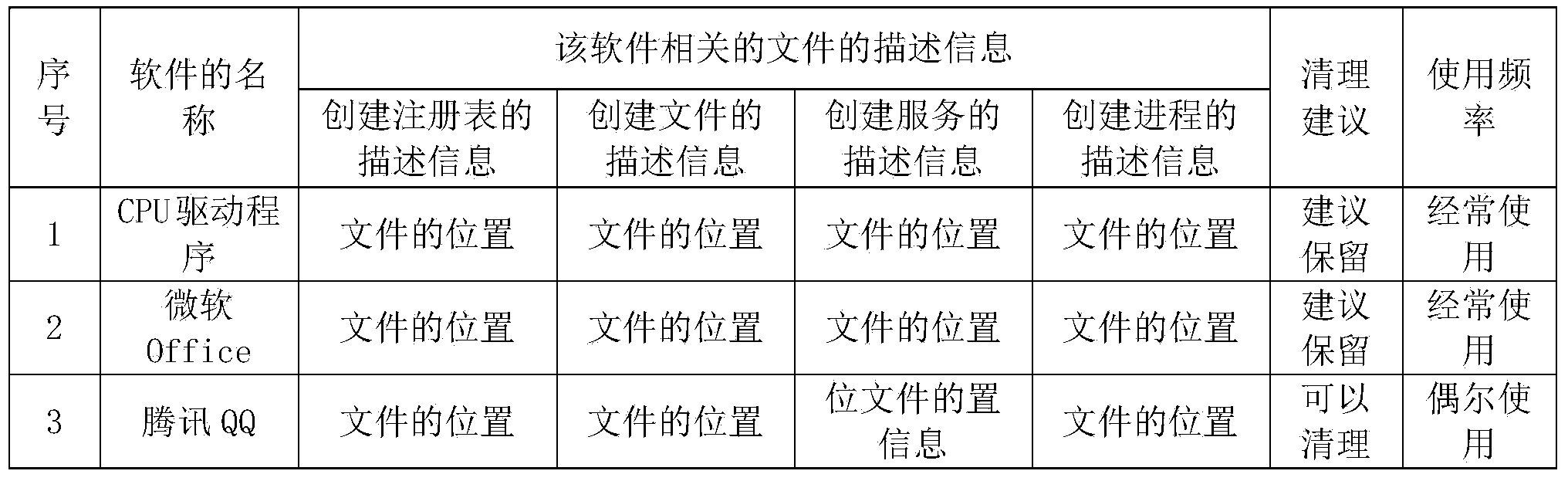
Software cleaning method and device
ActiveCN103645914ARealize one-click cleaningAvoid cumbersome uninstall operationsProgram loading/initiatingInformation repositorySoftware engineering
The invention discloses a software cleaning method and device. The software cleaning method comprises obtaining one or a plurality of software cleaning requirements which comprise software description information; searching software file description information which is corresponding to the software description information in a preset software information base with software installed, recording the file description information which is relevant to the software and generated through software behaviors of one or a plurality of software in the preset software information base with the software installed and deleting one or a plurality of files which are corresponding to the description information according to searched description information of the file which is relevant to the software. The software cleaning method has the advantages of solving the problem that in the prior art, part of residual files are left during a software uninstalling process and automatically achieving cleaning of the software when a user select the software to be cleaned, namely, achieving one-key cleaning of the software.
Owner:BEIJING QIHOO TECH CO LTD
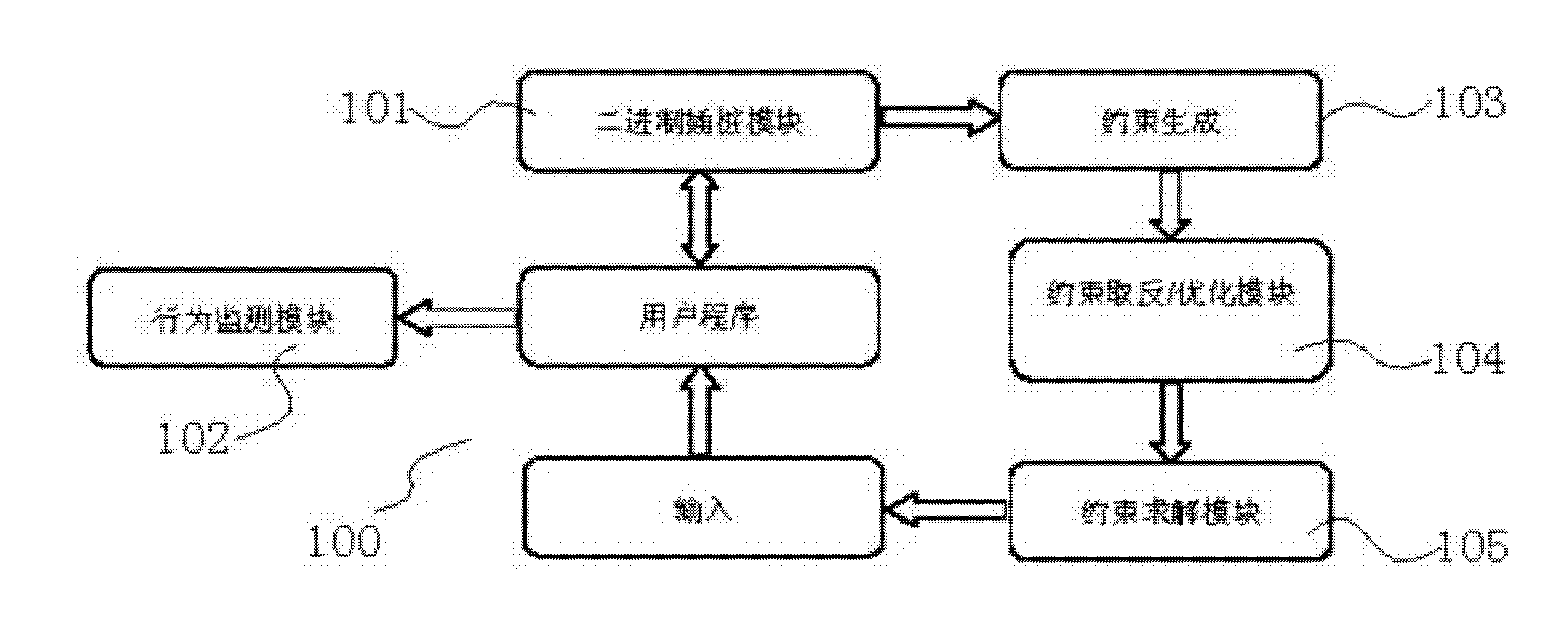
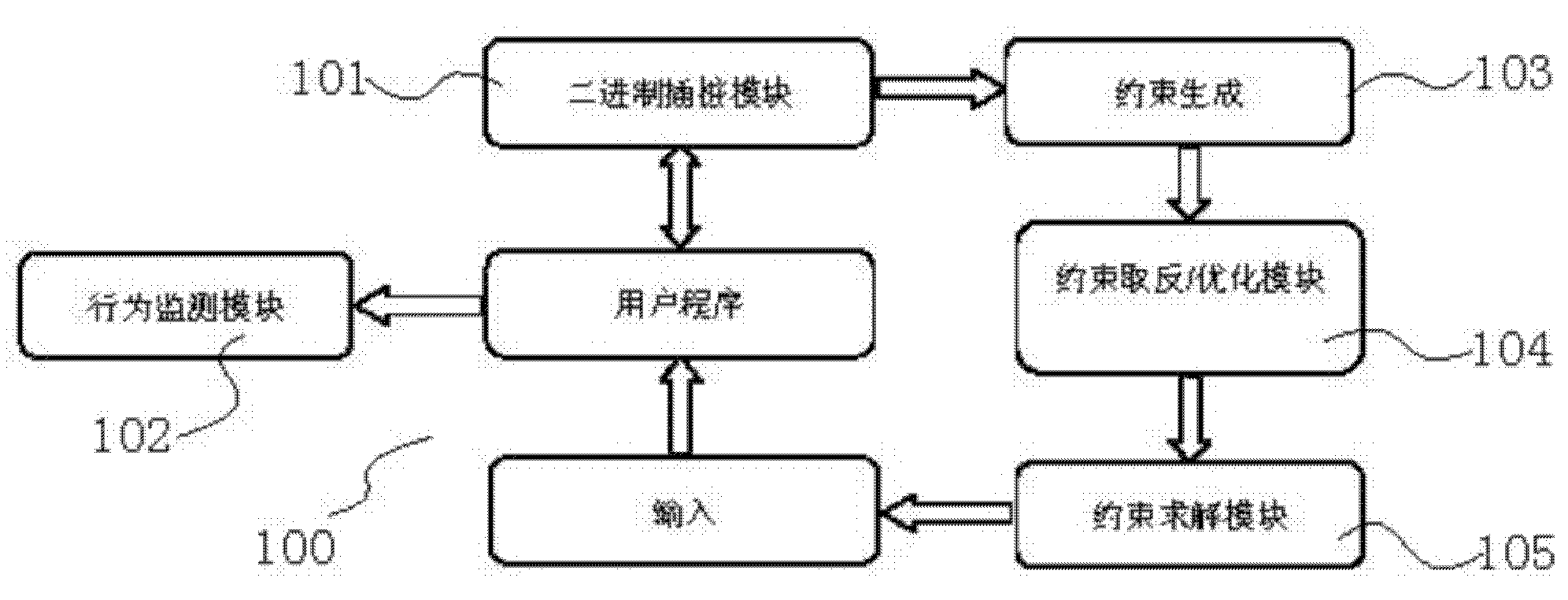
Software behavior detection system based on symbolic execution technology and detection method thereof
InactiveCN102222035AImprove accuracyIncrease diversityHardware monitoringSoftware testing/debuggingNegationTheoretical computer science
The invention discloses a software behavior detection system based on symbolic execution technology and a detection method thereof, wherein the detection system consists of a constraint generation module, a constraint negation / optimization module, a constraint solution module, a binary code pile pitching module and a behavior monitor module; and the method specifically comprises the following steps of: monitoring software behavior in the actual execution process of a program, collecting information relevant to the behavior, and providing certain essential data for behavior analysis; and simultaneously, collecting the constraint condition of the current path; after the program execution is finished, negating a certain constraint condition in the set of collected path constraint conditions so as to acquire a new patch constraint set, and solving the newly generated new patch constraint set by using a solver so as to determine whether a path can be achieved; and if the preconditions traversing the patch can be met, triggering a new software behavior by traversing the path. The system and the method can efficiently improve the precision and comprehensiveness of behavior detection.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
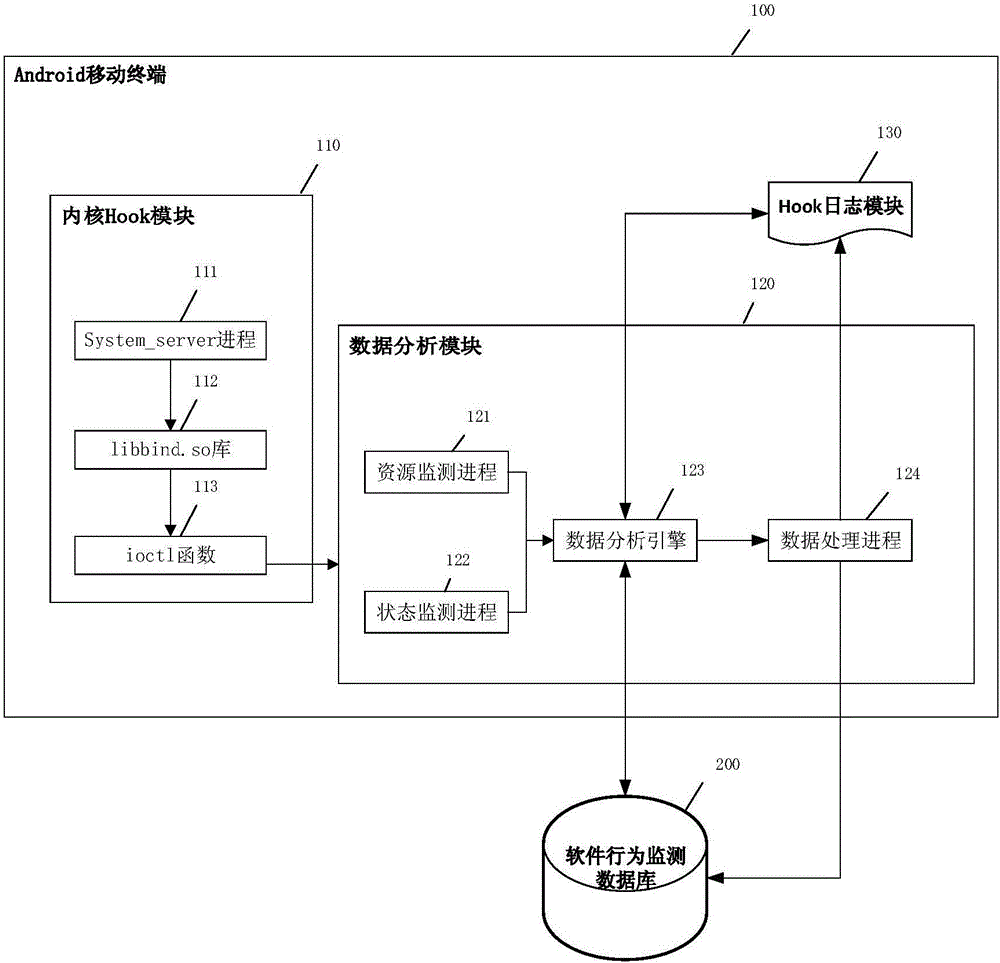
Abnormal behavior detection system of Android platform software
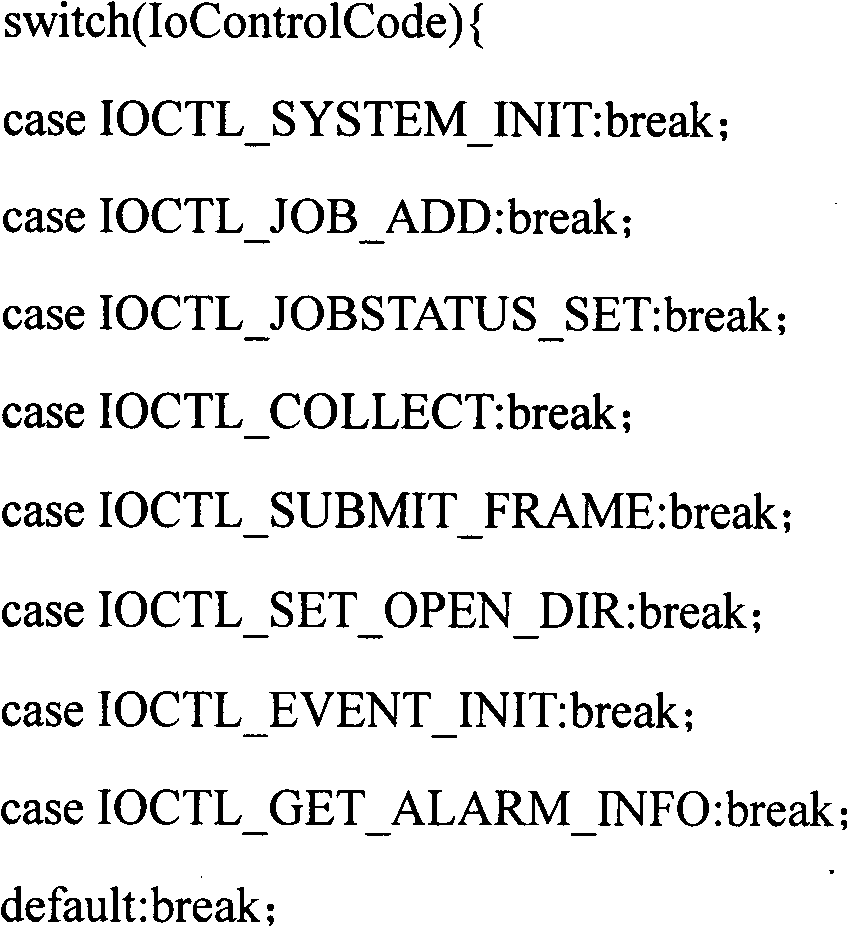
ActiveCN105956474AEffective Abnormal BehaviorEffectively identify abnormal behaviorPlatform integrity maintainanceOperational systemComputer module
The invention discloses an abnormal behavior detection system of Android platform software, and belongs to the technical field of the intelligent mobile terminal. The system comprises an Android mobile terminal and a software behavior monitoring database, wherein the Android mobile terminal and the software behavior monitoring database are mutually communicated; the Android mobile terminal comprises a kernel Hook module, a data analysis module and a Hook log module; the kernel Hook module comprises a System_server process, a libbind.so library and an ioctl function, wherein the System_server process, the libbind.so library and the ioctl function are successively interacted to realize the extraction of kernel Hook information; the data analysis module comprises a resource monitoring process, a state monitoring process, a data analysis engine and a data processing process, and carries out the definition writing of software behavior abnormality. The abnormal behavior detection system has the advantages of advancement, accuracy and comprehensiveness, combines the advantages of dynamic detection and static detection, effectively detects the abnormal behavior of app software through the Hook of a sensitive API (Application Program Interface) function, and effectively carries out statistics on the operating system behavior characteristics of the software.
Owner:WUHAN HONGXU INFORMATION TECH
Software hybrid measure method based on trusted computing
ActiveCN104517057AAchieve securityImplement Active MetricsPlatform integrity maintainanceTheoretical computer scienceTrusted Computing
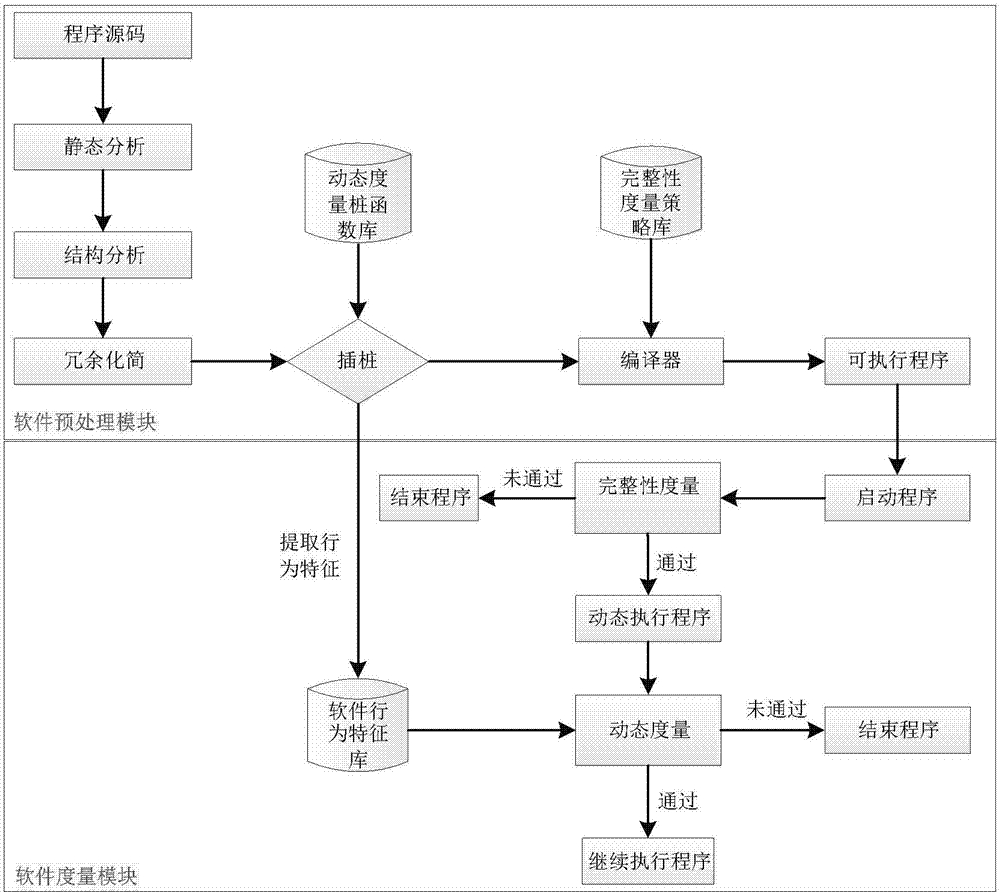
The invention relates to a software hybrid measure method based on trusted computing. The software hybrid measure method includes the steps: preprocessing software, analyzing and inserting program source codes, extracting behavior characteristics of the software, generating a software behavior characteristic library, embedding a software integrity measure strategy and generating an executable program to be measured; measuring the software, measuring integrity by a parallel optimization algorithm when starting the executable program to be measured according to the integrity measure strategy and the software behavior characteristic library, and dynamically measuring the executable program in real time in the running process. Static software measure and dynamic software measure can be simultaneously supported, software integrity measure and real-time dynamic behavior measure are combined by the aid of technologies such as parallel optimization, strategy embedding, inserting and system calling division, and the method has fine measure efficiency and low measure expenditure.
Owner:THE PLA INFORMATION ENG UNIV
Android software visualization safety analysis method based on module relations
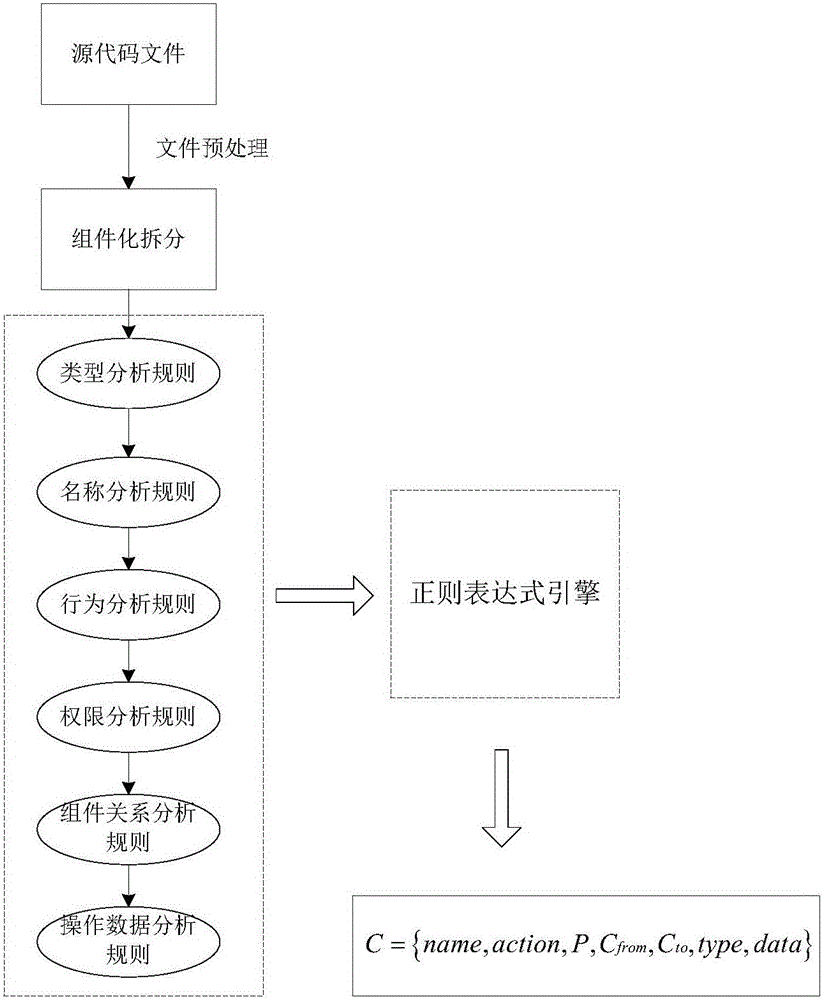
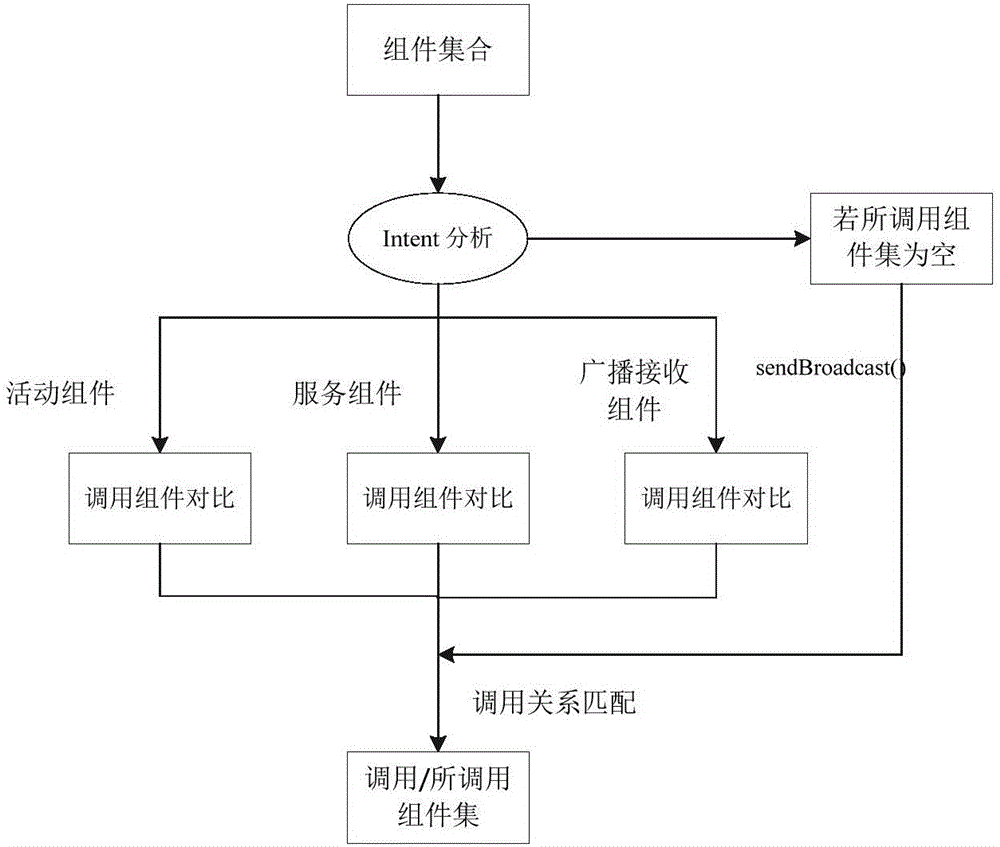
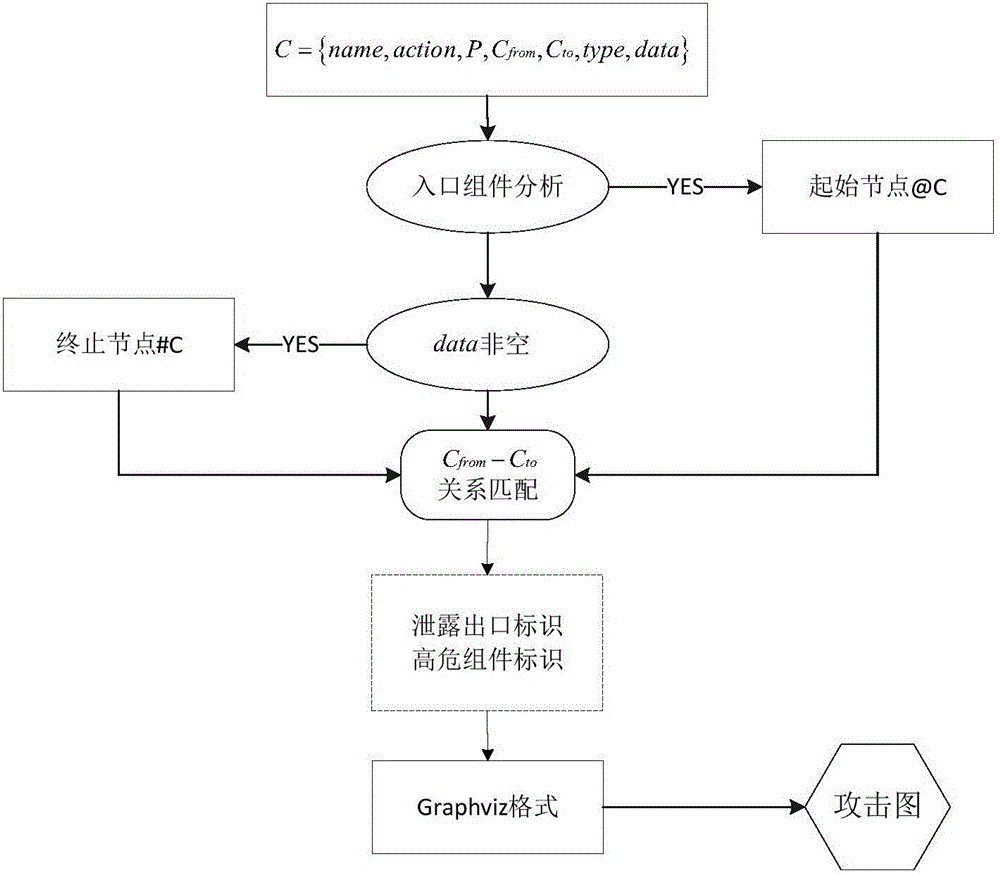
ActiveCN105787366AImprove understandingReduce false positive ratePlatform integrity maintainanceSoftware engineeringUser privacy
The invention provides an Android software visualization safety analysis method based on module relations.According to the method, module recognition is conducted on Android software source codes according to a standard module model, all Android modules are extracted, then all attributes of individual module are obtained through regulation matching engine analysis, automated module type modeling of Android software is achieved, software behavior is described in the modularized form, meanwhile, user privacy data serve as the core, privacy data and data leakage outlets are recognized, the weakness degree of each module is quantified, visualization description is conducted on possible privacy disclosure behavior of the software, module positions which is attacked by malicious applications possibly and the module calling relation, and visualization display of the software behavior with respect to safety is achieved.Artificial distinguishing of a user and a program analysis method are effectively combined, so that the user has more visualized knowledge about the software behavior related to privacy data, and the purpose of distinguishing safety of an application is achieved.
Owner:SHANGHAI JIAO TONG UNIV
Software Behavior Modeling Apparatus, Software Behavior Monitoring Apparatus, Software Behavior Modeling Method, And Software Behavior Monitoring Method
InactiveUS20090187396A1Accurate detectionReduce overheadError detection/correctionSoftware designCall stackSoftware engineering
A software operation modeling device (100) includes: a stack information recording unit (120), an end information recording unit (150), a stack difference information generation unit (130) for generating information for generating stack difference information by concatenating a call stack upper node of stack information with information until the end information is detected by using the end information recorded by the end information recording unit (150), and a model generation unit (140) for generating a software operation model from the stack difference information.
Owner:NTT DOCOMO INC
Active defense system based on Android platform software behavior detection
InactiveCN103218566ALess storageLess calculationPlatform integrity maintainancePrincipal component analysisDimensionality reduction
The invention relates to an active defense system based on Android platform software behavior detection. The active defense system based on Android platform software behavior detection is used for actively defending mobile phone security threats. According to the active defense system, process data are collected by using a top command or a PS command, and ActivityManager.MemoryInfo () and ActivityManager.AppProcessInfo () which are provided by an API (Application Programming Interface) of Android; the collected data are analyzed by using a PCA (Principal Component Analysis) method, features which best reflect samples are extracted, and the samples are loaded to a neural network model; and partial samples are randomly selected for learning so as to obtain model parameters which serve as model parameters of an evaluation portion, thus, the samples to be detected are evaluated, whether the samples are normal or not is judged, and then, whether some process is abnormal or not is judged. According to the active defense system, PCA dimensionality reduction is introduced into mobile phones in a manner of being combined with a BP (Back Propagation) neural network, so that the traditional computation amount and memory capacity of the BP neural network are reduced, the active defense system can be excellently implemented on mobile devices with limited computing power and storage capacity, such as the mobile phones, and the security of the mobile phones is guaranteed.
Owner:JIANGNAN UNIV
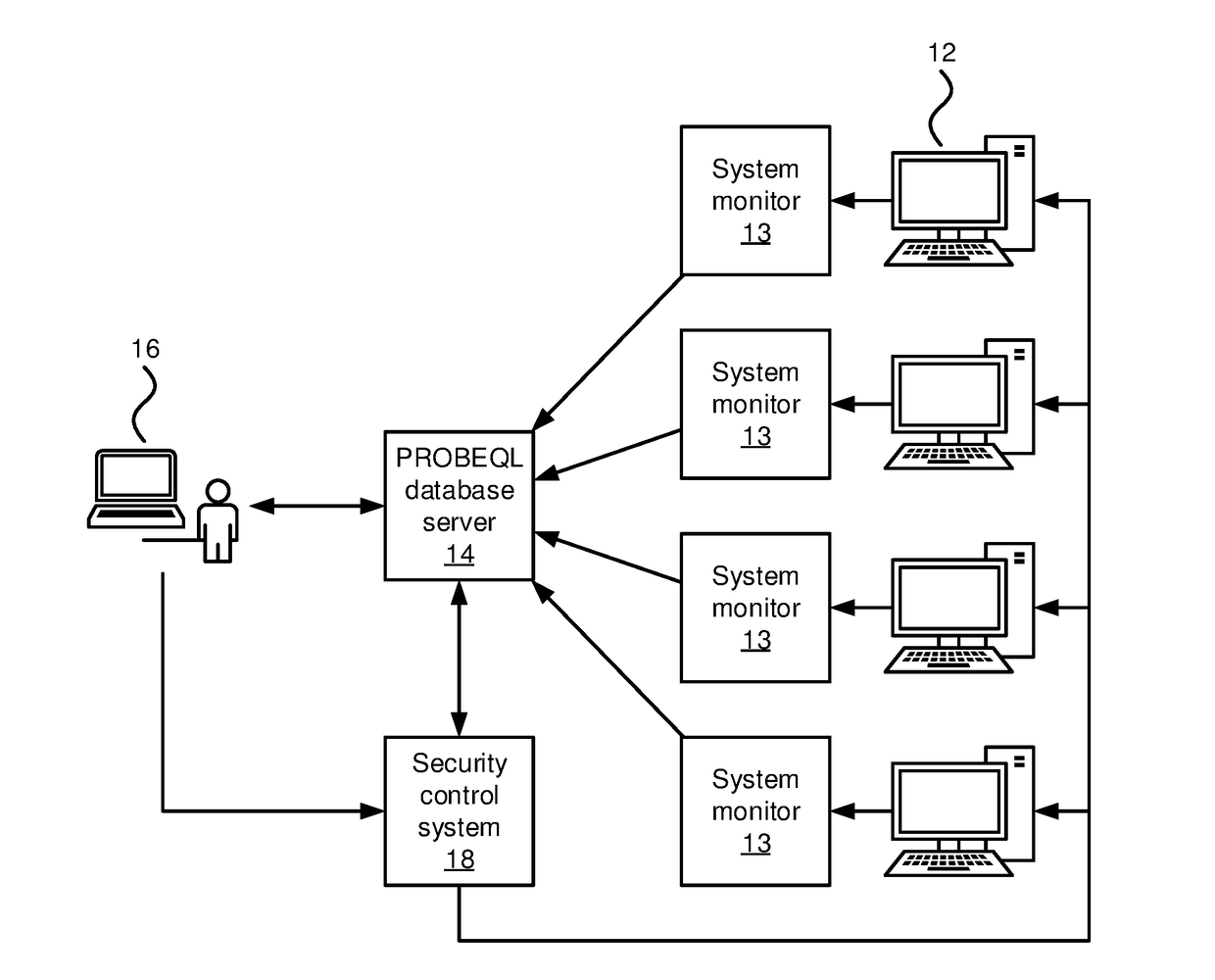
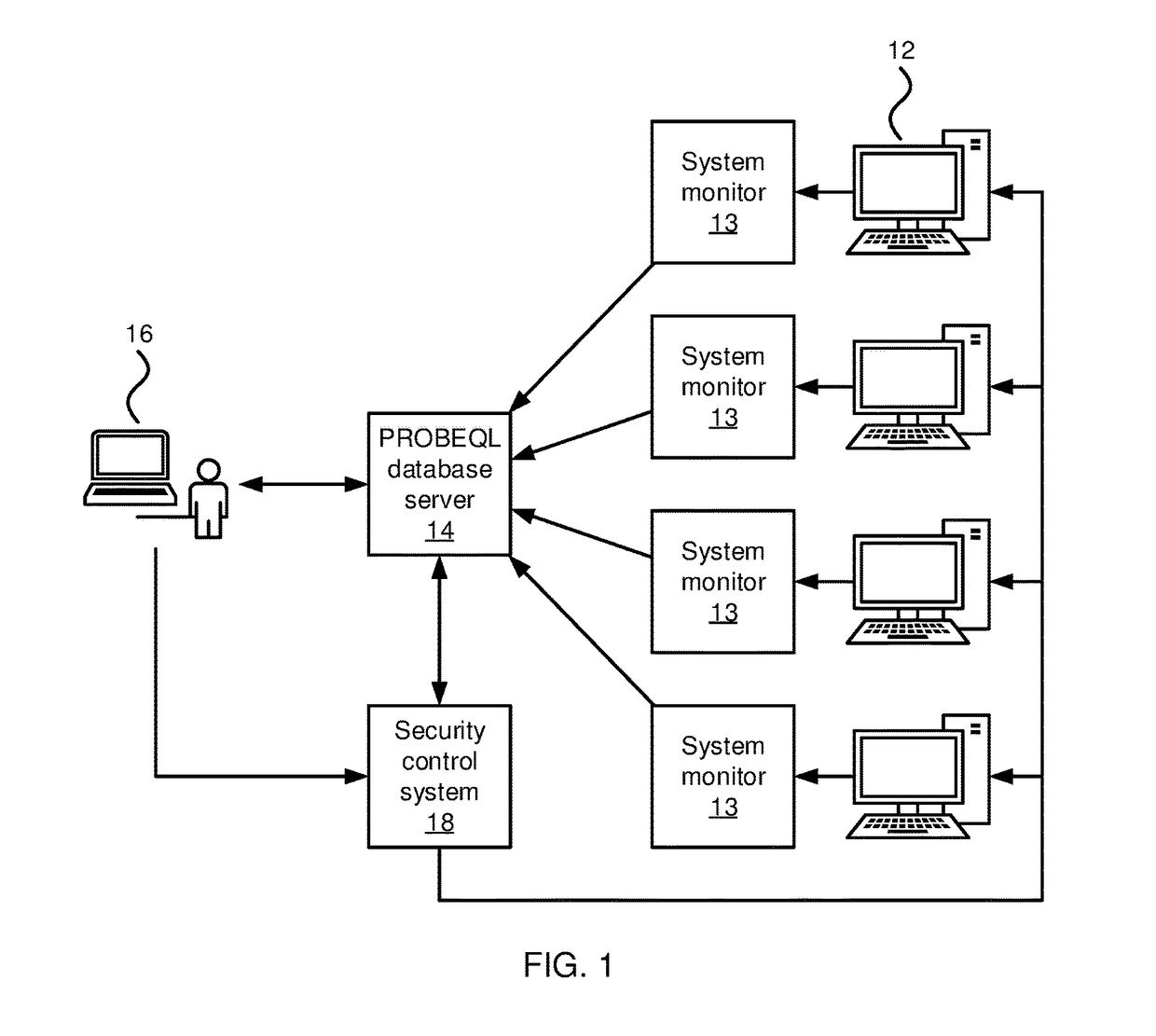
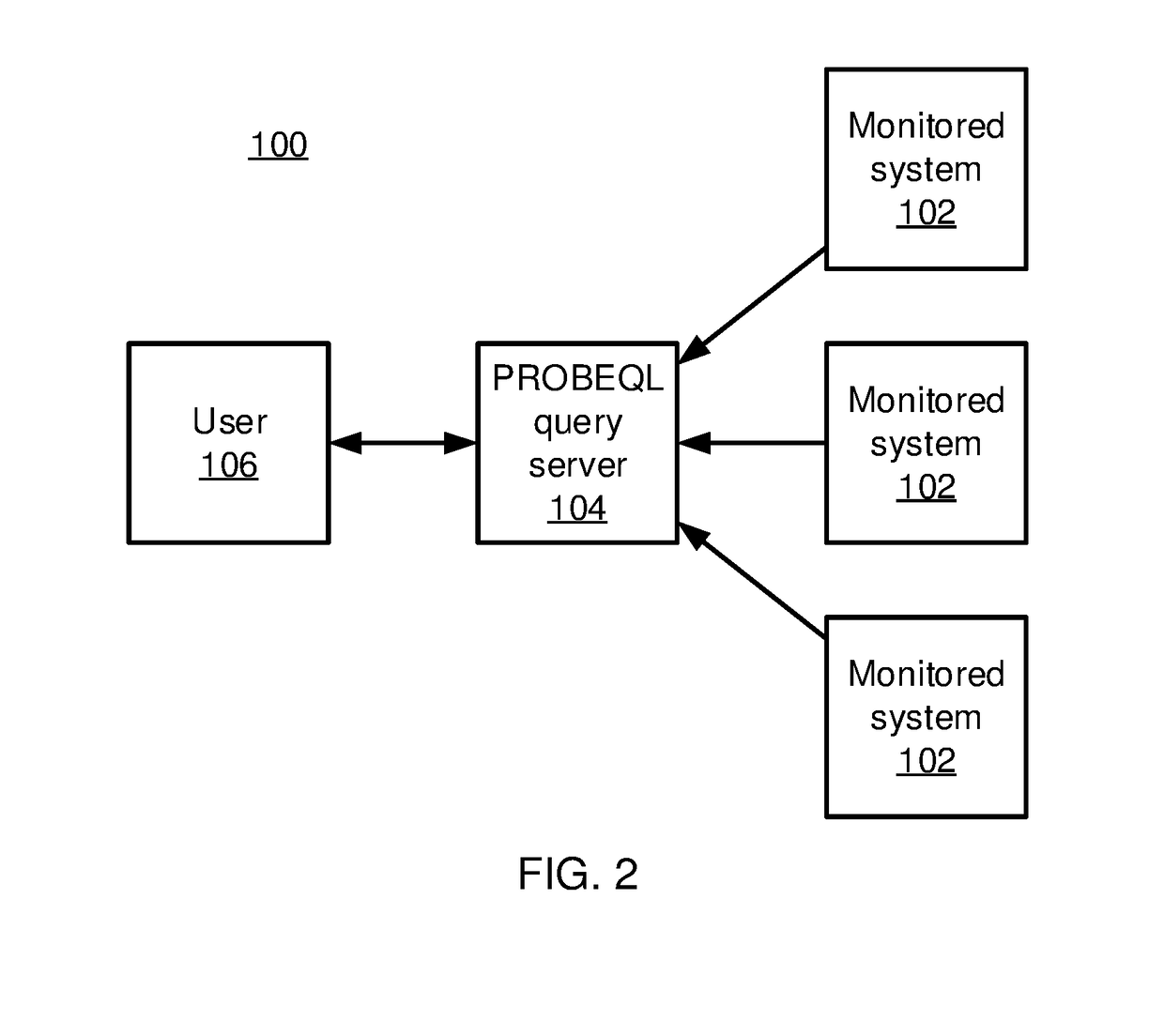
Security Monitoring with Progressive Behavioral Query Language Databases
ActiveUS20180060586A1Platform integrity maintainanceSpecial data processing applicationsDatabase queryQuery optimization
Automated security systems and methods include a set monitored systems, each having one or more corresponding monitors configured to record system state information. A progressive software behavioral query language (PROBEQL) database is configured to store the system state information from the monitored systems. A query optimizing module is configured to optimize a database query for parallel execution using spatial and temporal information relating to elements in the PROBEQL database. The optimized database query is split into sub-queries with sub-queries being divided spatially according to host and temporally according to time window. A parallel execution module is configured to execute the sub-queries on the PROBEQL database in parallel. A results module is configured to output progressive results of the database query. A security control system is configured to perform a security control action in accordance with the progressive results.
Owner:NEC CORP
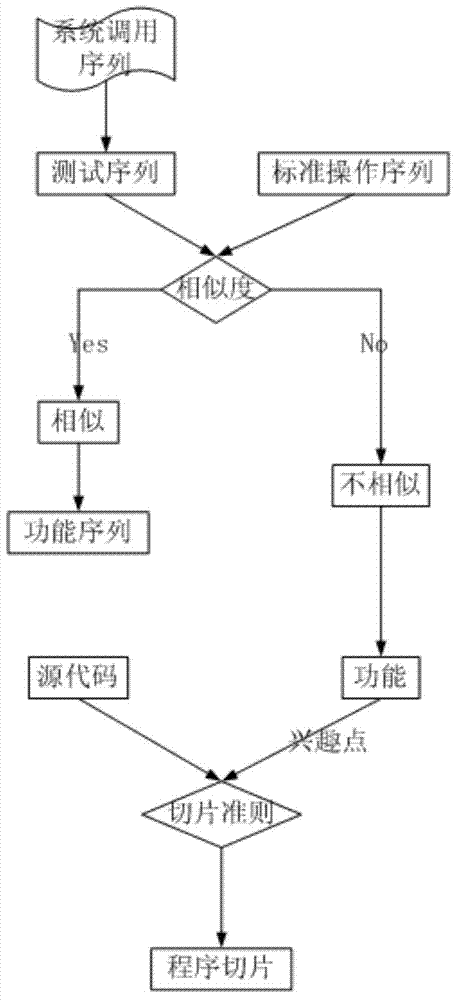
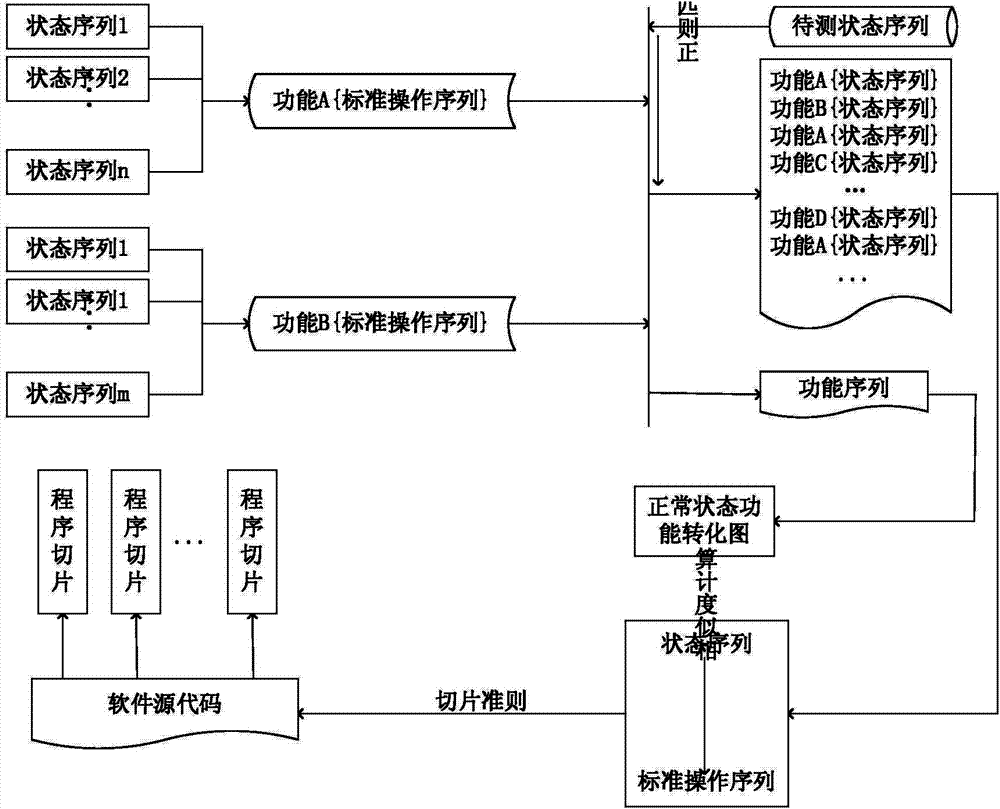
Method of tracing software abnormal behaviors based on software functional layer
InactiveCN103744786AAbnormal Behavior ResolutionSoftware testing/debuggingProgram slicingState model
Owner:BEIJING UNIV OF TECH
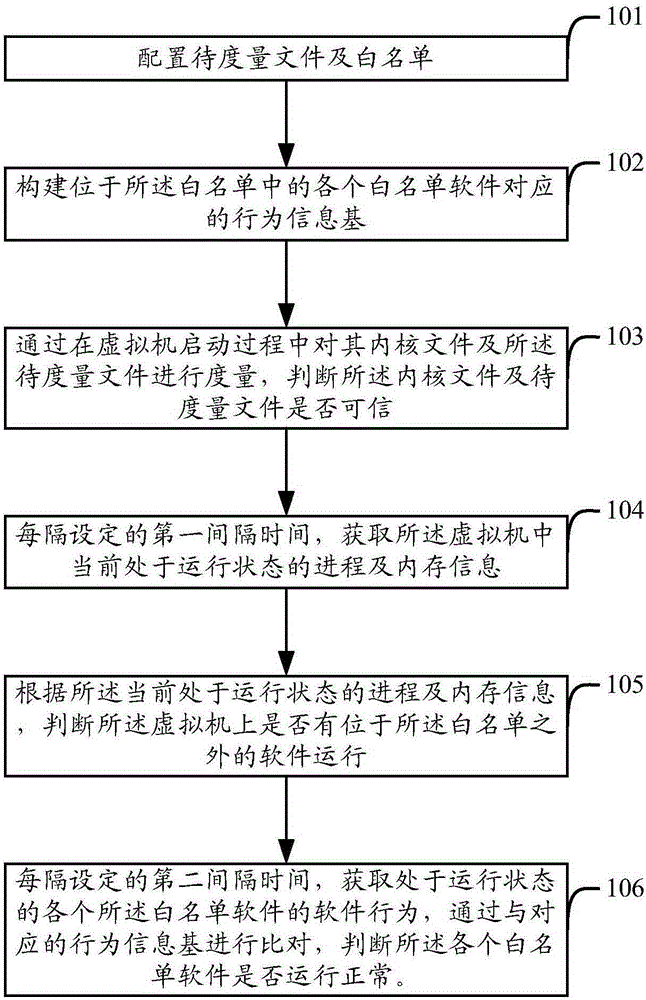
Virtual machine measurement method and apparatus
ActiveCN105159744AImplement static metricsImplement dynamic metricsPlatform integrity maintainanceSoftware simulation/interpretation/emulationSoftware behaviorVirtual machine
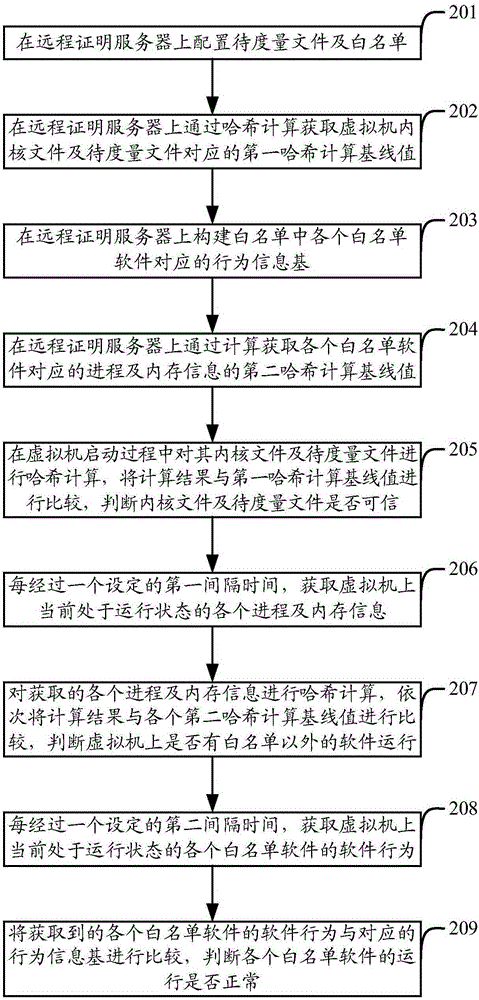
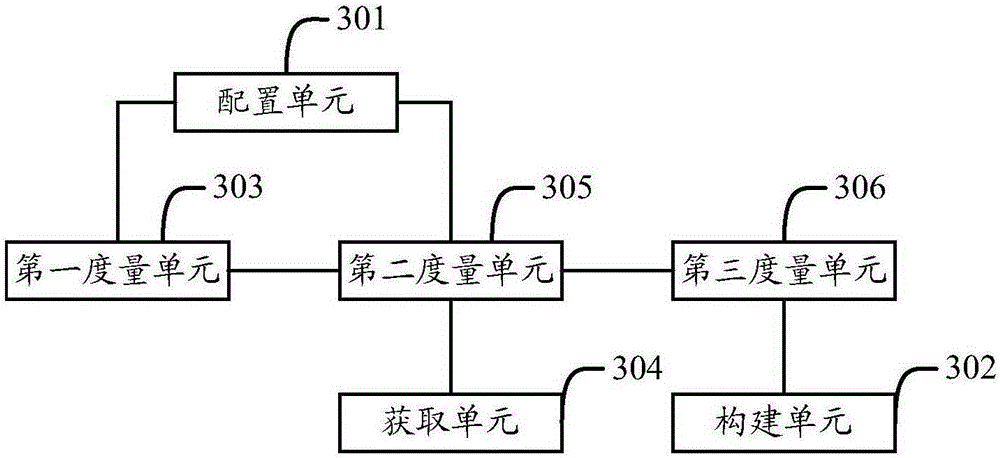
The invention provides a virtual machine measurement method and apparatus. The method comprises: configuring a to-be-measured file and a white list; constructing a behavior information base corresponding to each piece of white list software located in the white list; by measuring a kernel file and the to-be-measured file in a virtual machine starting process, judging whether the kernel file and the to-be-measured file are trusted; at a set first time interval, obtaining a process currently in a running state and memory information in a virtual machine; according to the process currently in the running state and the memory information, judging whether software located outside the white list runs in the virtual machine; and at a set second time interval, obtaining a software behavior of each piece of white list software in a running state, and by comparison with the corresponding behavior information base, judging whether each piece of white list software runs normally. The apparatus comprises a configuration unit, a construction unit, a first measurement unit, an acquisition unit, a second measurement unit and a third measurement unit. According to the scheme, the security of the virtual machine can be improved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
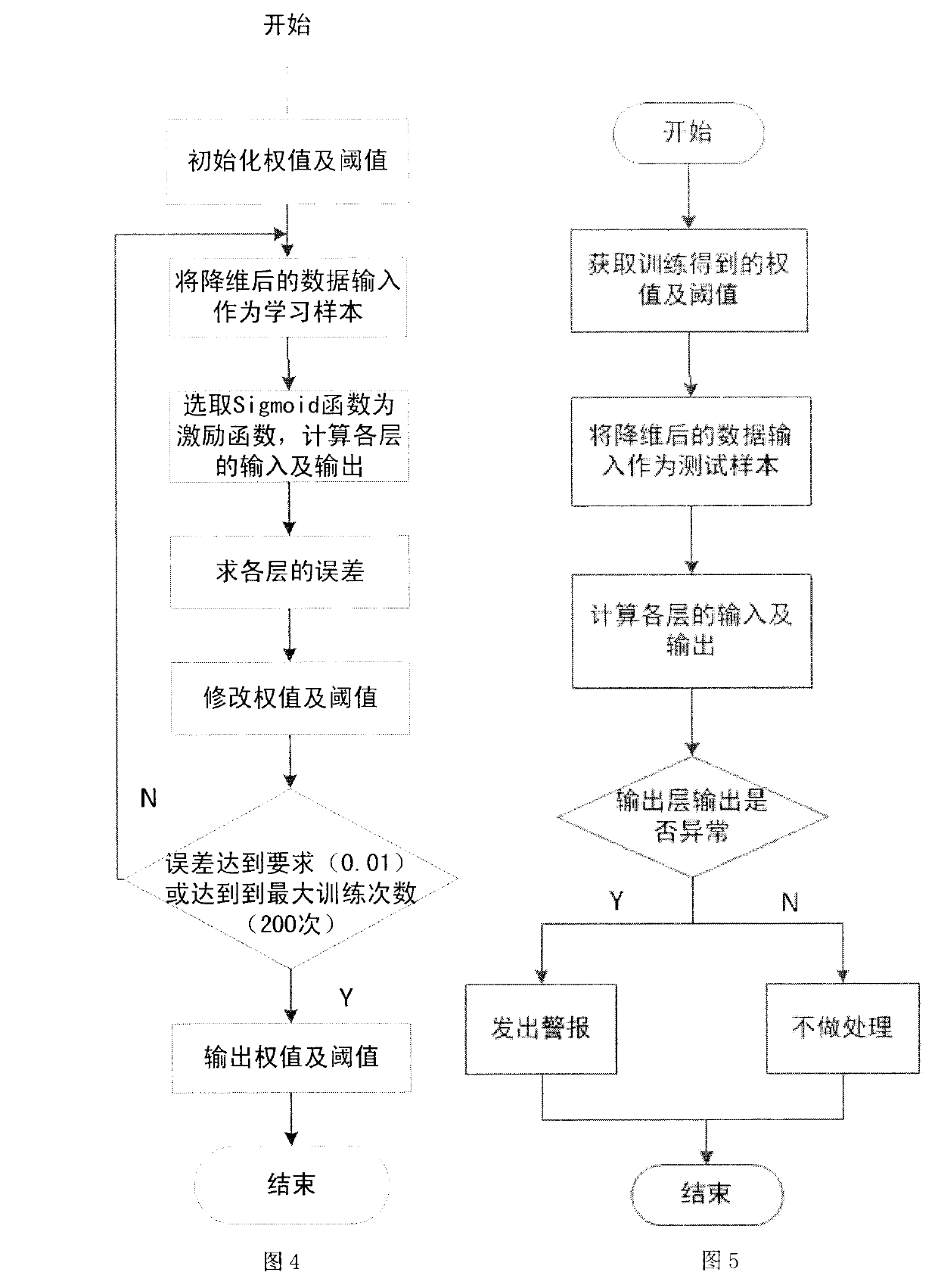
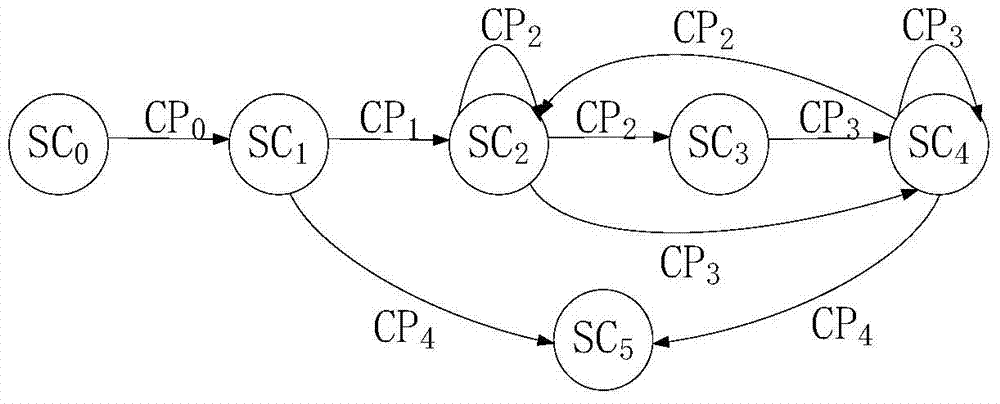
Software behavior credibility detecting method based on state transition diagram
ActiveCN102768638ARealize real-time monitoringThe detection system has a clear hierarchySoftware testing/debuggingSpecific program execution arrangementsState diagramSoftware behavior
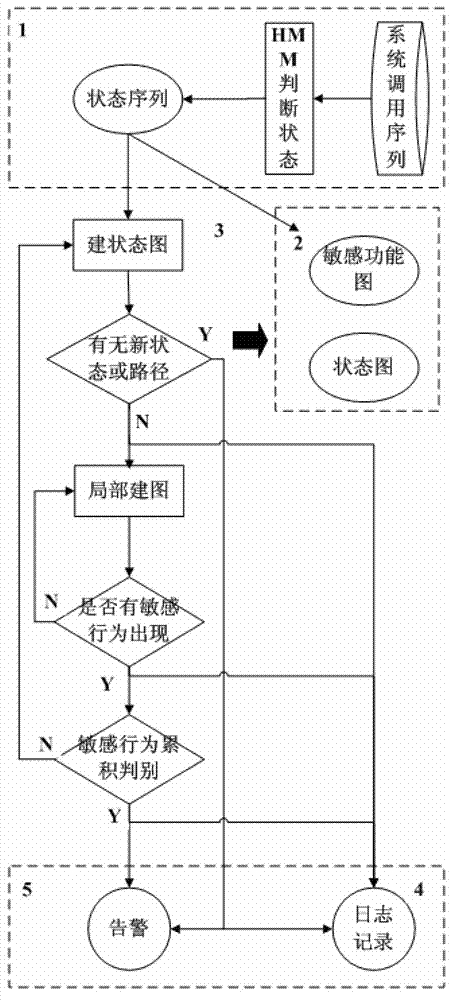
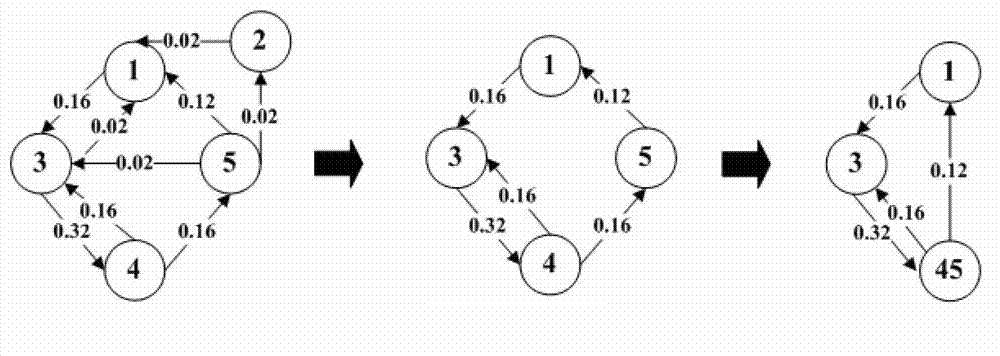
The invention relates to a software behavior credibility detecting method based on a diagram. A detecting system is divided into five modules including a data preprocessing module, a state diagram training module, a behavior detecting module, a real-time monitoring module and an abnormal warning module, wherein the data preprocessing module is in charge of processing preliminary data; the state diagram training module is used for training a normal behavior base; the behavior detecting module is in charge of detecting behaviors according to the built diagram, and the detection module is divided into two layers, the first layer is used for detecting states and paths, and the second layer is mainly used for detecting weights; the real-time monitoring module dynamically stores detection results in a log mode; and the abnormal warning module warns when the detecting module detects abnormal conditions, and stops running software. A detecting model can monitor software behaviors in real time, and detects behaviors which do not belong to the software, aggressive behaviors and illegal input.
Owner:BEIJING UNIV OF TECH
Static behavior analysis method of mobile smart terminal software
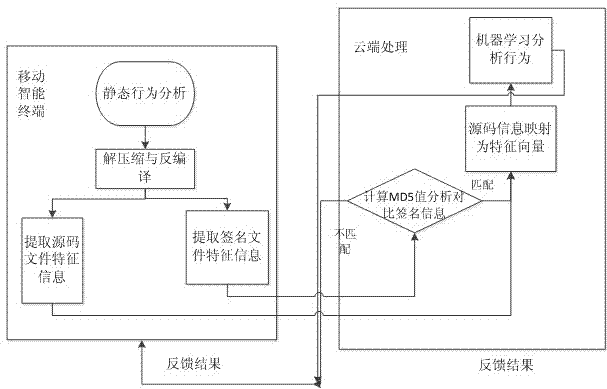
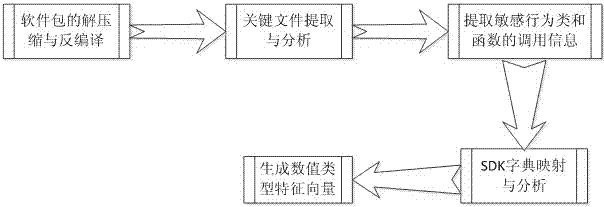
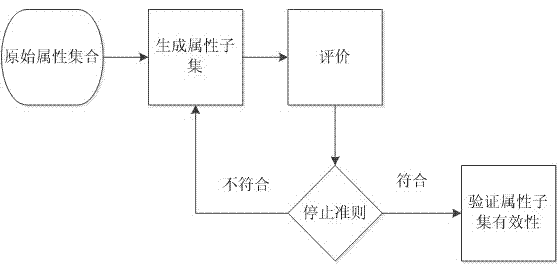
InactiveCN104751053AAvoid threatsStable and efficient analysisPlatform integrity maintainanceSoftware development processFeature vector
The invention discloses a static behavior analysis method of mobile smart terminal software. The static behavior analysis method includes steps of decompressing and decompiling to obtain software source codes by comparing signatures and machine learning concept, extracting kind function calling information and signature information, comparing the signature information at cloud and generating characteristic vectors of numeric types by an SDK (software development kit) dictionary, reducing Weka attribute to obtain behavior characteristics finally, and finally analyzing static behavior of the software by the machine learning algorithm. Accuracy and detecting rate are guaranteed while malicious software behaviors can be more precisely detected. Meanwhile, potential safety hazards during operating of the software are avoided and software behaviors of the mobile smart terminal can be more stably and efficiently analyzed.
Owner:CHANGSHU RES INSTITUE OF NANJING UNIV OF SCI & TECH
Mobile intelligent terminal malicious software analysis system
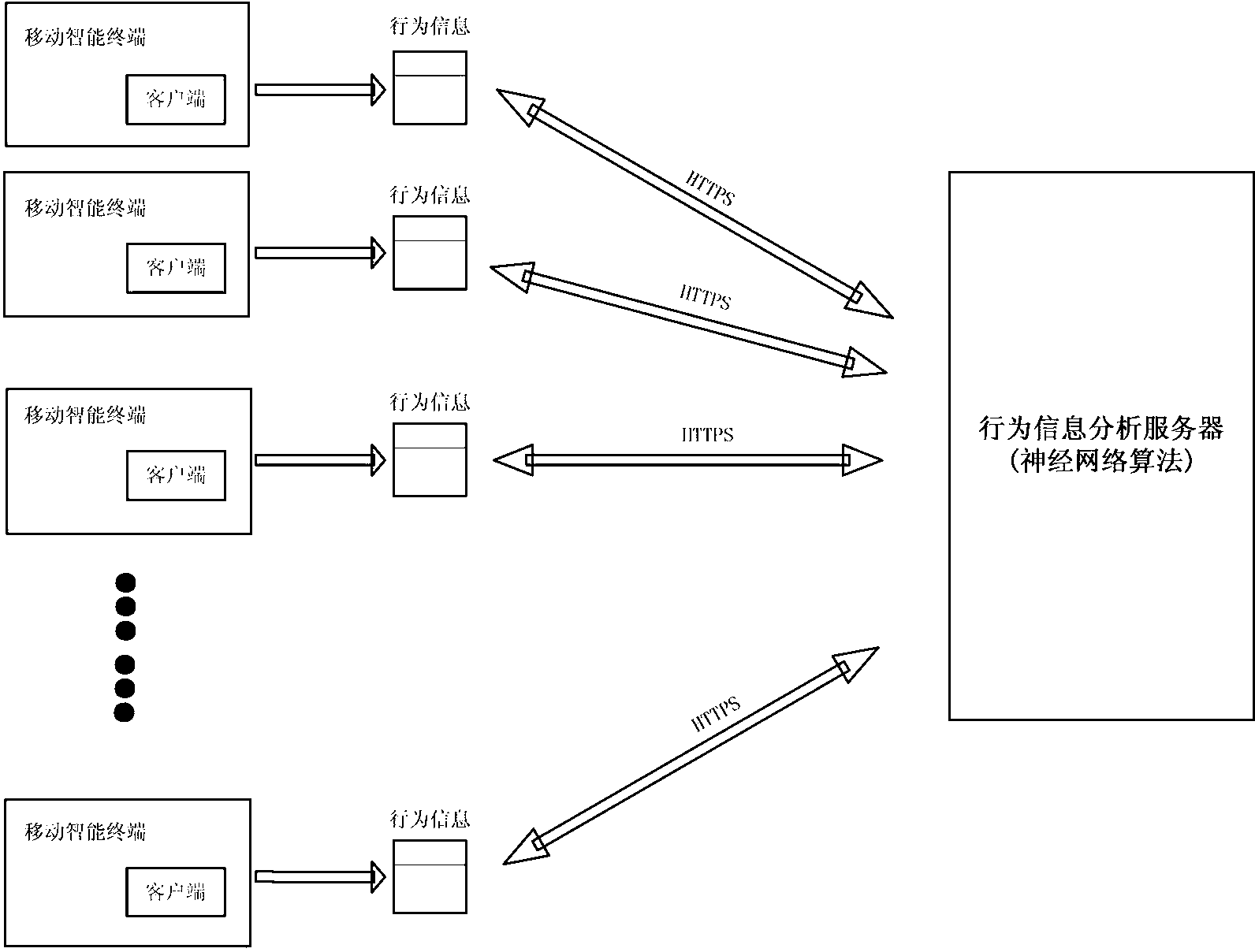
InactiveCN103136476AImprove detection efficiencyReduce overheadPlatform integrity maintainanceTransmissionInformation analysisSoftware analytics
A mobile intelligent terminal malicious software analysis system comprises a mobile intelligent terminal client program, a software behavior information analysis background server, a client-side and background server communication protocol, and a distributed operating environment, wherein the mobile intelligent terminal client program is used for collecting behavior information in software operation and sending the information to the background server; the software behavior information analysis background server adopts related algorithms to analyze software behavior information, judges whether software has malicious behaviors or not, and returns analysis results to a mobile intelligent terminal; the client-side and background server communication protocol is used for achieving data communication between a client-side and the background server; and the distributed operating environment is used for providing mass data of software behavior analysis. According to the mobile intelligent terminal malicious software analysis system, emerging malicious software can be effectively detected, and system resource overhead of the mobile intelligent terminal on malicious software detection is reduced.
Owner:SHENZHEN ZHENGTONG ELECTRONICS
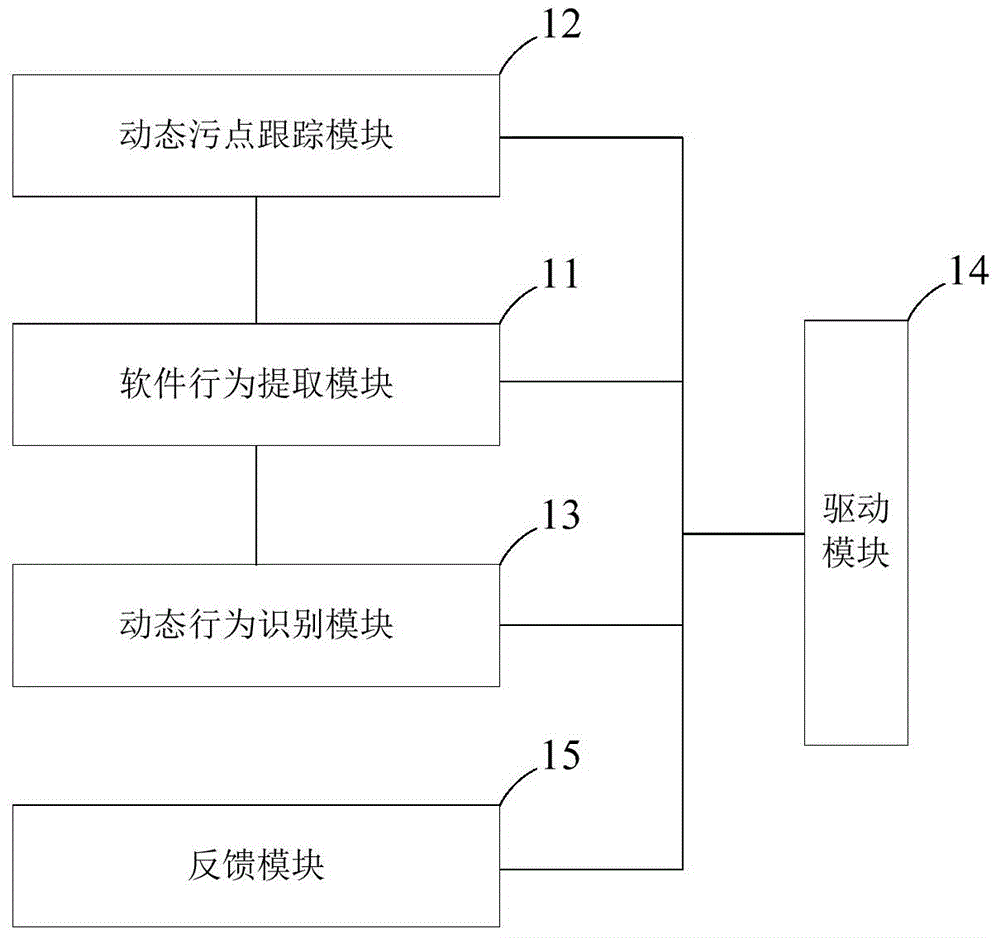
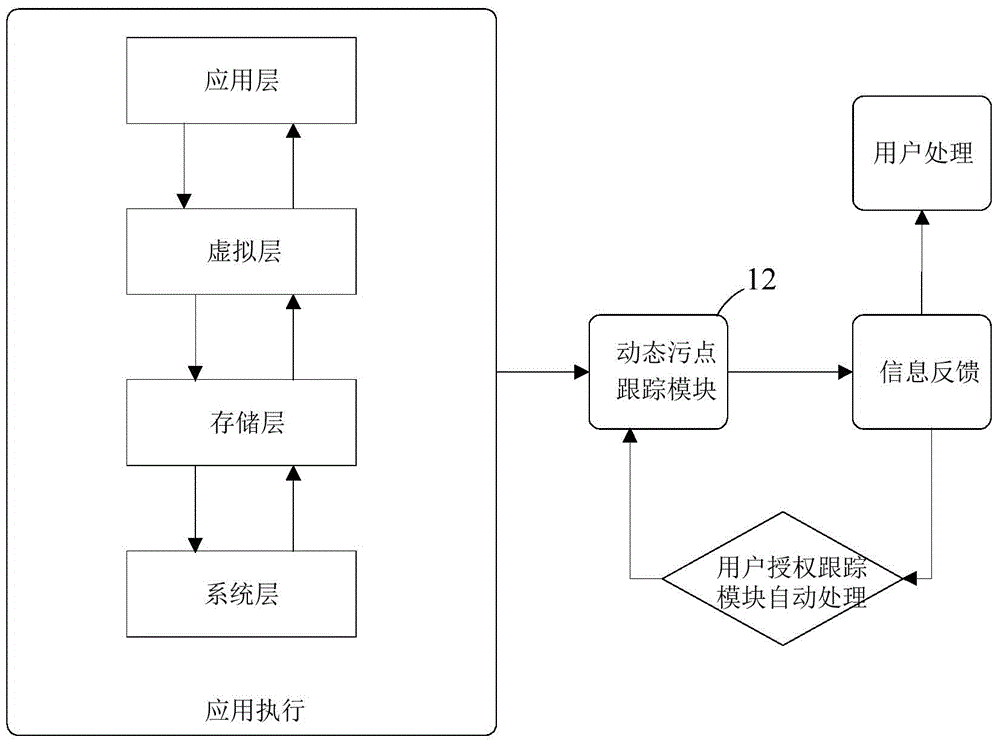
System and method for detecting dynamic malicious behaviors of application program in mobile terminal
ActiveCN104462973AImprove integrityEasy to detectPlatform integrity maintainanceSoftware systemSoftware engineering
The invention provides a system and method for detecting dynamic malicious behaviors of an application program in a mobile terminal. The system comprises a software behavior extraction module, a dynamic stain tracking module, a dynamic behavior recognition module and a driving module, wherein the software behavior extraction module dynamically extracts software behaviors of the application program running on the mobile terminal; the dynamic stain tracking module receives the software behaviors and monitors a data transmission behavior among the software behaviors to judge whether the data transmission behavior is a malicious behavior; the dynamic behavior recognition module receives the software behaviors and recognizes a software system calling behavior among the software behaviors to judge whether the software system calling behavior is a malicious behavior; the driving module receives judgment results of the dynamic stain tracking module and the dynamic behavior recognition module and conducts processing. By means of the system and method, a dynamic detection technology for the application program in the running process is provided, the ability of the system to detect malicious software is improved, and information security of users is guaranteed.
Owner:合肥小刺猬信息科技有限公司
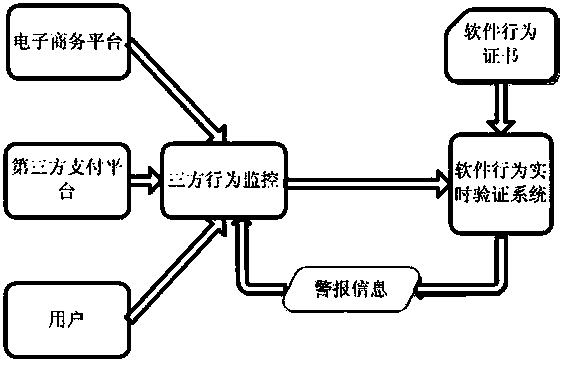
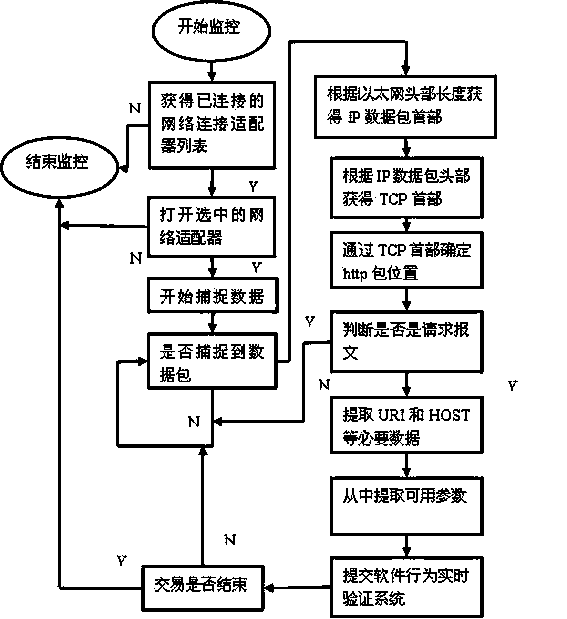
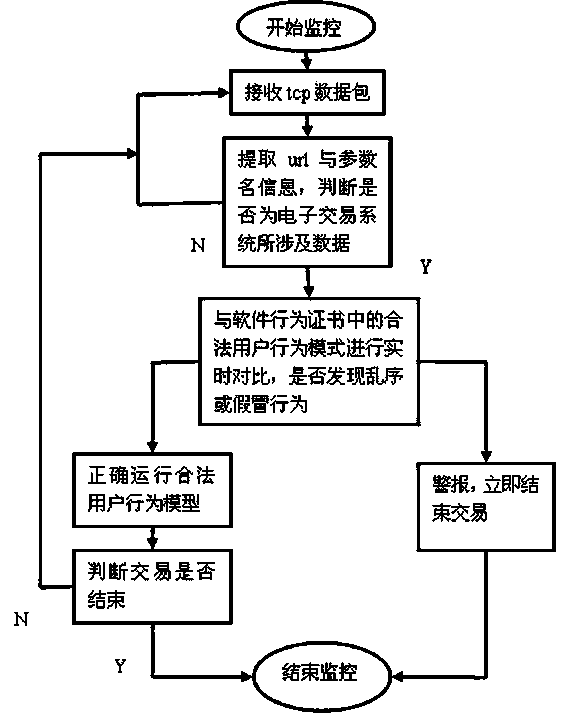
Software behavior monitor and verification system
ActiveCN103714456AFull monitoring of interactive processReal-time alertComputer security arrangementsTransmissionData packEngineering
The invention relates to a software behavior monitor and verification system which is composed of a soft behavior certificate, three-party software behavior monitoring units and a software behavior real-time verification system. The soft behavior certificate is a three-party communication data packet according to a user, an e-commerce website and a third-party payment platform in the correct transaction process. The three-party software behavior monitoring units are data packet monitor units installed on the e-commerce website, the third-party payment platform and a user client side. The software behavior real-time verification system receives transaction interaction information data packets submitted by the three-party monitoring units respectively and extracts and integrates key sequences and information in the transaction interaction information data packets, a user behavior interaction sequence and a software behavior model are compared in real time according to a global unique order number, and once the out-of-order phenomenon, fake identities and other illegal behaviors occur, an alarm is given out, and the transaction is closed. Three-party interaction url and other key parameters are used, the legal and normal transaction interaction process of the three parties is described, and the soft behavior certificate is provided.
Owner:TONGJI UNIV
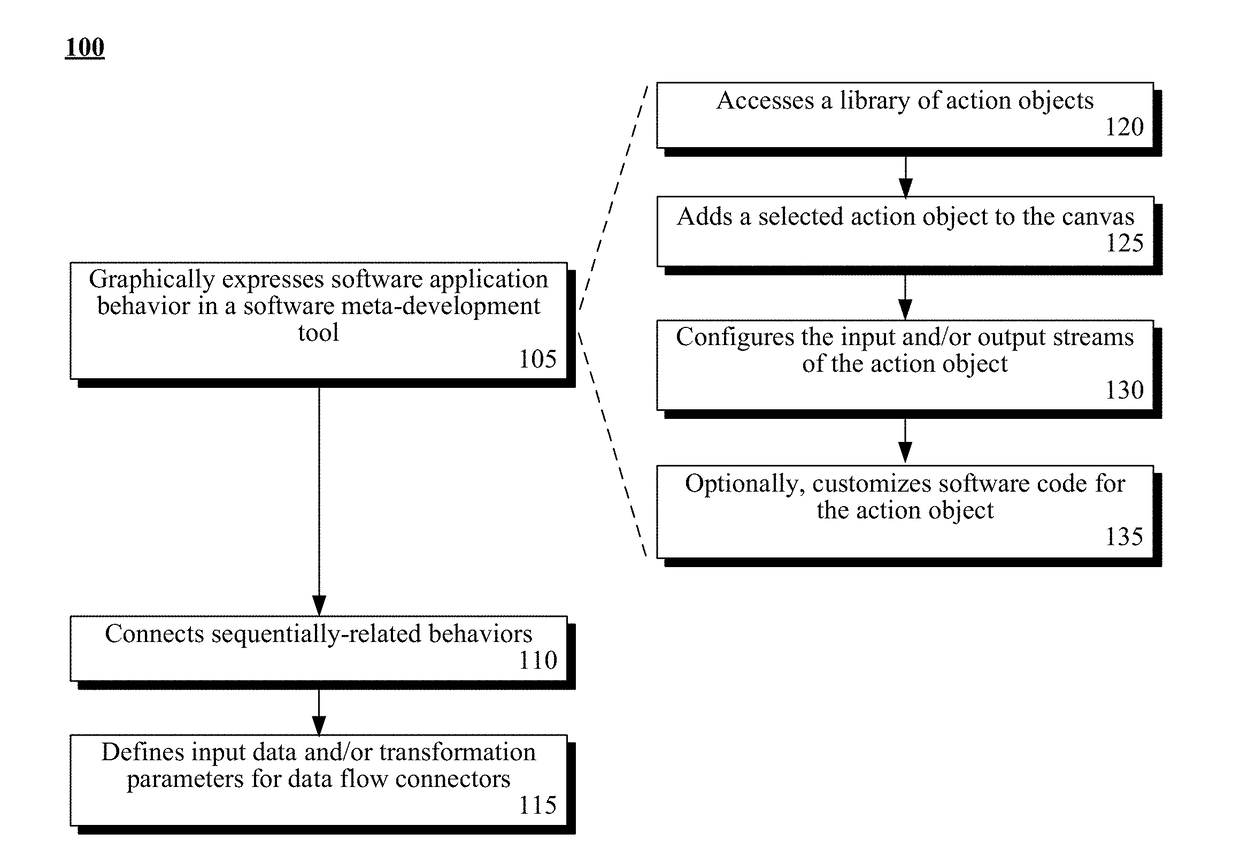
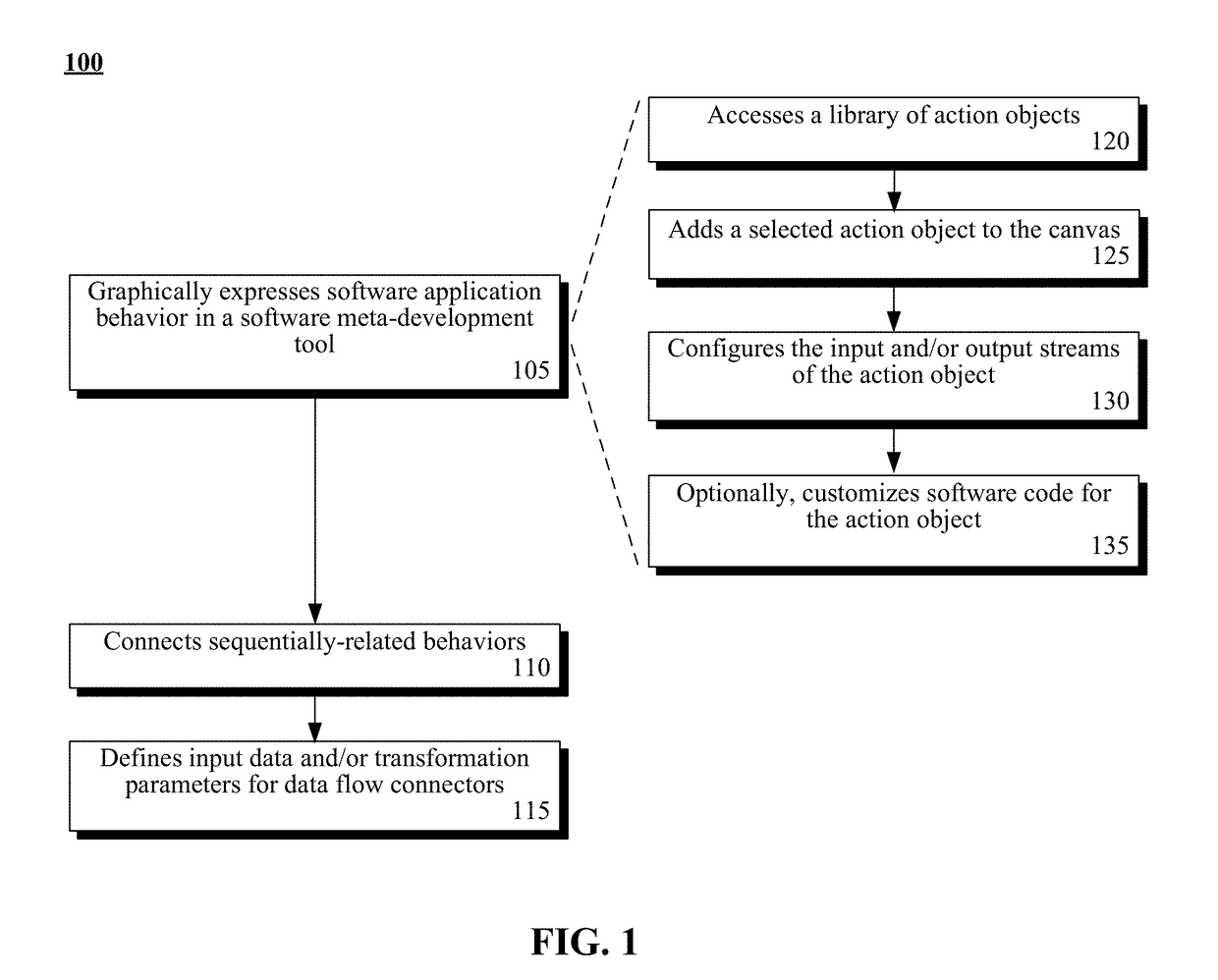
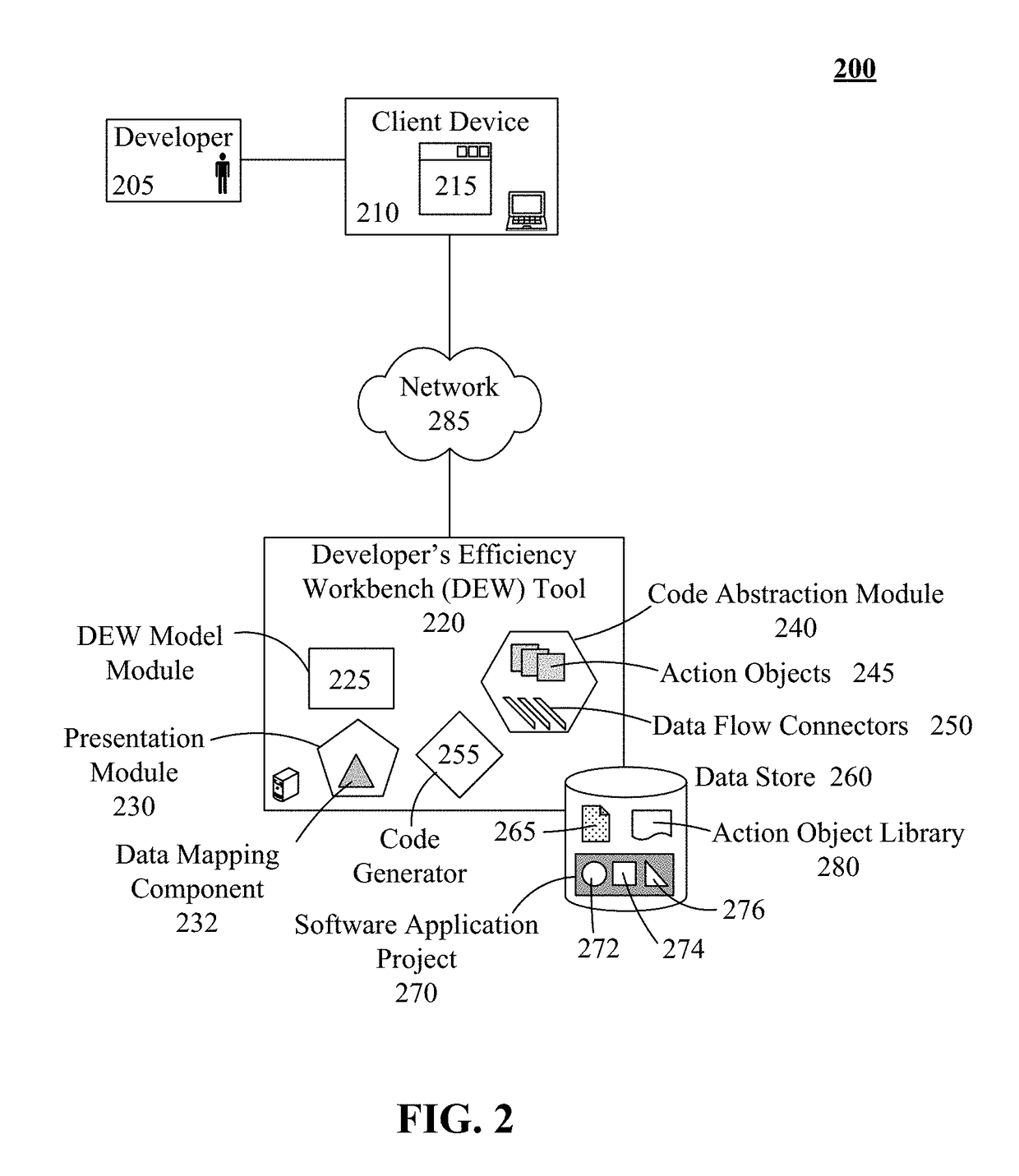
Application development tool using graphic objects to bind object sets of different distinct divisions of a design pattern
A code abstraction can be created within a software meta-development tool as a platform and programming language independent representation of a software application. The code abstraction can be comprised of action objects and data flow connectors. An action object can be a graphical placeholder representing software code that implements software behavior. Each action object can have an input and an output stream that are unconstrained by data type. A data flow connector can connect the output stream of one action object to the input stream of another sequentially-related action object. The data flow connector can graphically express a directional relationship and can define input data and transformation parameters. The data flow connector can implicitly represent the operations necessary to convert the input data in accordance with the transformation parameters. Authoring of the software code associated with the code abstraction by a user of the software meta-development tool can be unnecessary.
Owner:TECHREV LLC
Function call based dynamic detection method for buffer overflow vulnerability
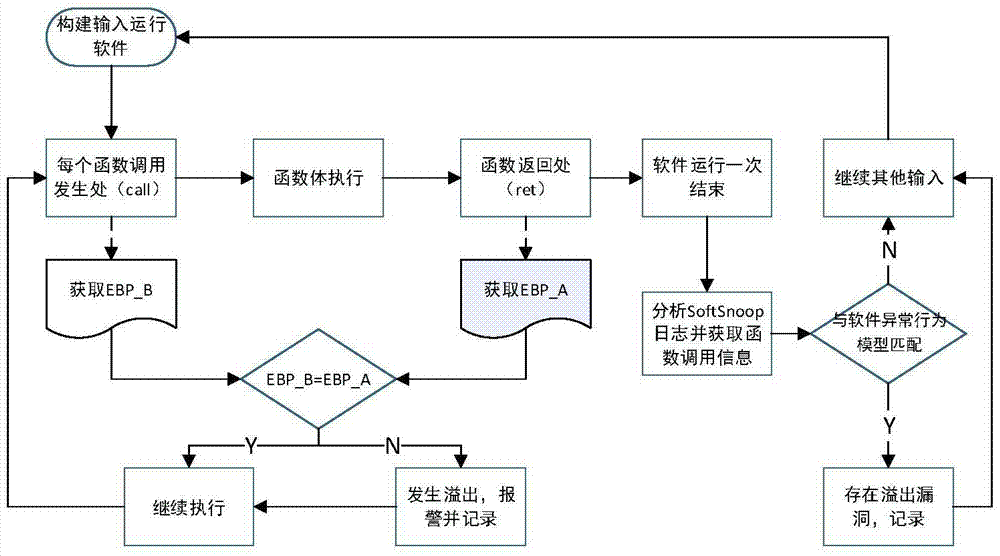
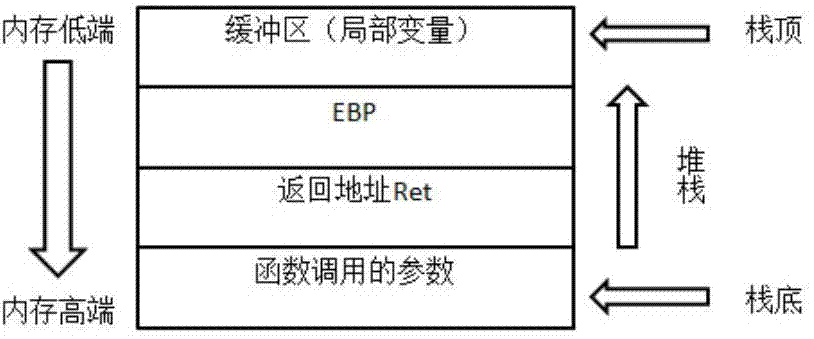
ActiveCN104766015AMake up for the shortcomings of high false negative rateHigh measurement accuracyPlatform integrity maintainanceProcessor registerBuffer overflow
The invention discloses a function cell based dynamic detection method for buffer overflow vulnerability. The method comprises the steps of acquiring a function call instruction address and a return instruction address of a detected program; building input parameters, and operating the detection program; in case of function call occurs, acquiring the value EBP_B in a base register; acquiring the value EBP_A of the base register when the function call is finished; if EBP_B is not equal to EBP_A, recording the vulnerability and alarming; if EBP_B is equal to EBP_A, determining that no vulnerability occurs; repeating the process until the detection program finishes the operation; continuously acquiring the function call information of the current operation; matching with an abnormal software behavior model; if matching, recording the possible vulnerability; if not matching, determining that the behavior of the program under the current input is free of the feature showing the buffer overflow vulnerability. The method is that a large number of inputs are built for repeated detection. The method can perform dynamic detection and improve the detection efficiency.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Multi-track malicious program feature detecting method based on data mining
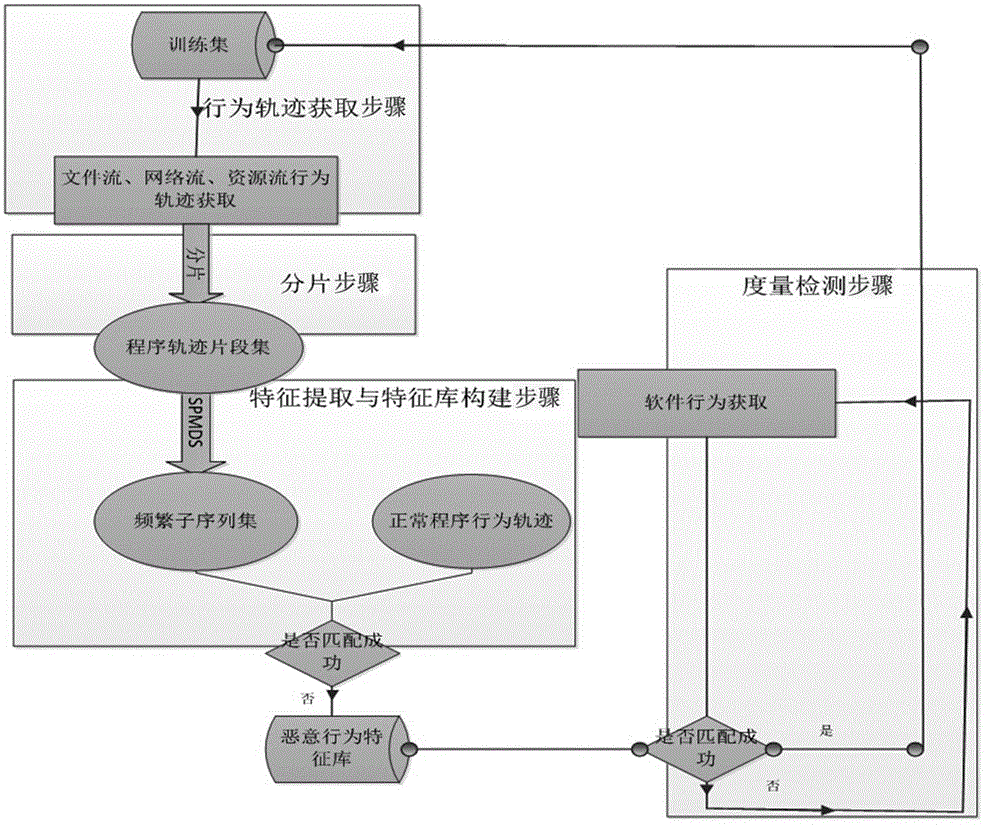
ActiveCN105138916AImprove accuracyHigh precisionPlatform integrity maintainanceFeature extractionSerial pattern
The invention relates to a multi-track malicious program feature detecting method based on data mining. The multi-track malicious program feature detecting method comprises the step of behavior track acquiring, the step of zone partitioning, the step of feature extracting and feature library establishing and the step of magnanimity detecting. In the step of behavior track acquiring, a dynamically-operating system calling sequence of a program is obtained; in the step of zone partitioning, zone portioning is carried out on obtained software behavior tracks so as to adapt to the needs of the mining process; in the step of feature extracting and feature library establishing, a sequence mode mining algorithm improved in data mining is adopted for acquiring a data flow, network flow and resource flow behavior frequent subsequence set, removing normal program behavior track fragments and structure a malicious behavior feature library; in the step of magnanimity detecting, magnanimity detecting is carried out on a program operating in real time according to the structured three-dimensional feature library. The multi-track malicious program feature detecting method based on data mining is high in detection accuracy.
Owner:THE PLA INFORMATION ENG UNIV
Method for controlling software behavior based on least privilege principle
InactiveCN102208004AAvoid crossing the lineAvoid destructionPlatform integrity maintainanceFiltrationProcess behavior
Owner:江苏云木养老科技有限公司
Attack tree model based Android software hybrid detection method
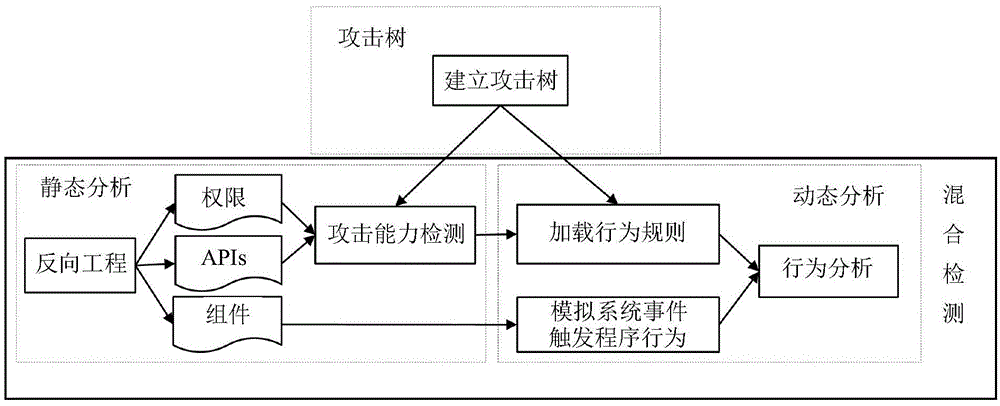
The present invention discloses an attack tree model based Android software hybrid detection method comprising the steps of: using an attack tree model to analyze attack types of various malware, and making a series of dynamic behavior detection rules for each attack path; then, performing hybrid detection including static analysis and dynamic analysis, wherein the static analysis realizes attack ability detection of to-be-tested software, and an analog system event in the dynamic analysis triggers to-be-tested software behaviors of a program; selecting a detecting point during software running by the dynamic analysis according to a result of the attack ability detection of the to-be-tested software, and loading and combining behavior rules; and according to to-be-tested software behaviors of an event trigger program of a component information analog system, forcing the to-be-tested-software to run fully, and performing to-be-tested-software behavior detection according to the behavior rules so as to identify malware. In contrast to the prior art, the attack tree model based Android software hybrid detection method organically combines static analysis and dynamic analysis methods to realize effective detection of malware threatening.
Owner:TIANJIN UNIV
Online virus detection method based on assembly of multiple detectors
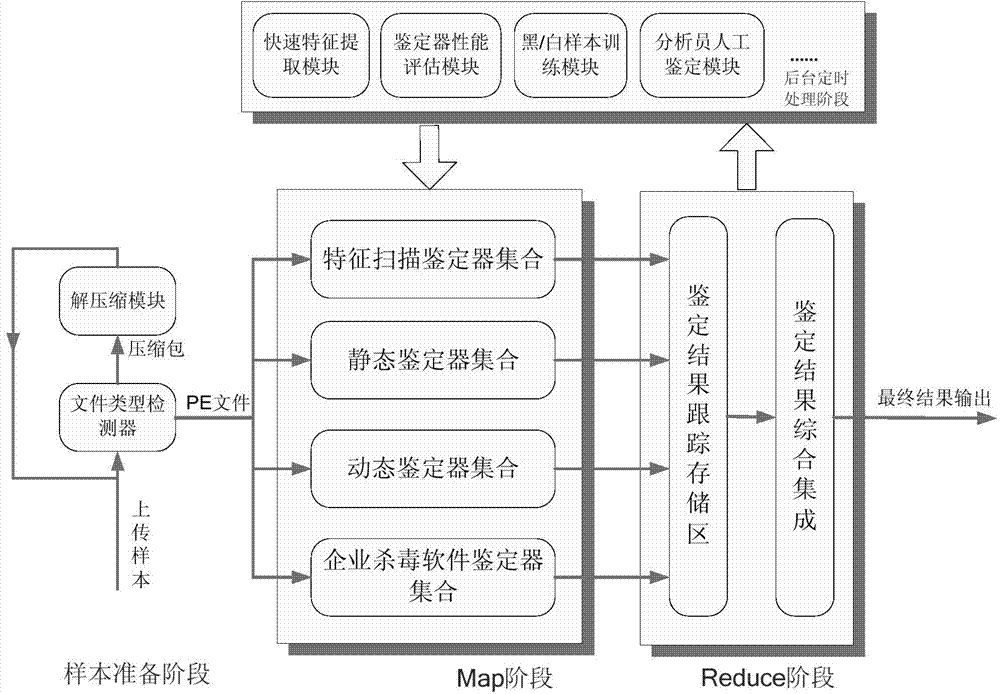
The invention discloses an online virus detection method based on assembly of multiple detectors and relates to computer virus detection. The method includes the sample preparation stage, the Map stage, the Reduce stage, the background timed processing stage. Based on a Hadoop distributed computing frame, a security system, namely an online virus detection model, aiming at defense of the whole Internet is provided. The Map stage and the Reduce stage are achieved by means of the Hadoop distributed computing frame. The online virus detection model intergrates parallel processing, grid computing, unknown virus behavior judgment and other emerging technologies and concepts and performs abnormity monitoring on software behaviors in the Internet through a large number of reticular clients, latest information about viruses, the Trojan horse and other malware in the Internet is obtained and transmitted to a server to be automatically analyzed and processed, and then the solutions to the viruses and the Trojan horse are distributed to all the clients.
Owner:XIAMEN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com