Static behavior analysis method of mobile smart terminal software
A mobile intelligent terminal and behavior analysis technology, applied in the direction of platform integrity maintenance, etc., can solve problems such as seldom considering terminal characteristics and little behavior analysis, and achieve the effect of preventing threats, stable and efficient analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
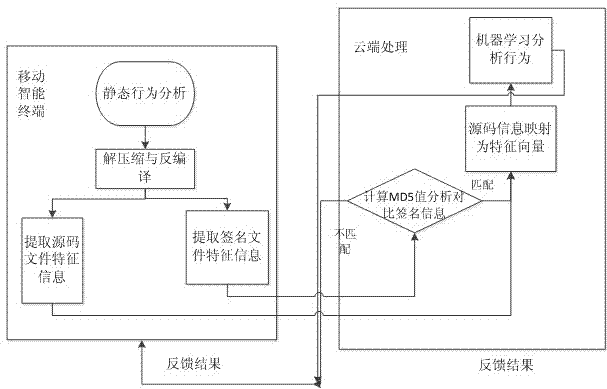
[0021] combine figure 1 , the present invention relates to a static behavior analysis method of mobile intelligent terminal software, the steps are as follows:
[0022] The first step is to obtain the software package by decompression, and then use reverse engineering and other means to obtain the source code of the software. Extract the software signature information, and compare the signature information by calculating the MD5 value.
[0023] 1. Extraction of signature information:
[0024] By extracting the MD5 check code of the signature file in each software package, and using the file name to form a key-value pair, the signature information is compared and analyzed one by one, so as to determine whether the software has been modified.
[0025] 2. Implementation method of software package signature comparison:
[0026] Analyze and obtain the information in the software package by observing and analyzing the software source code.
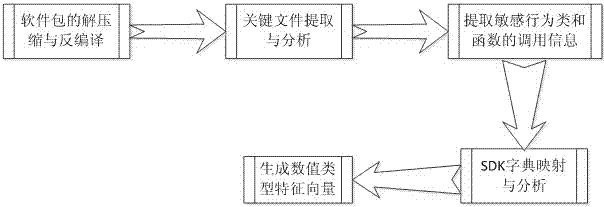
[0027] The second step,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com