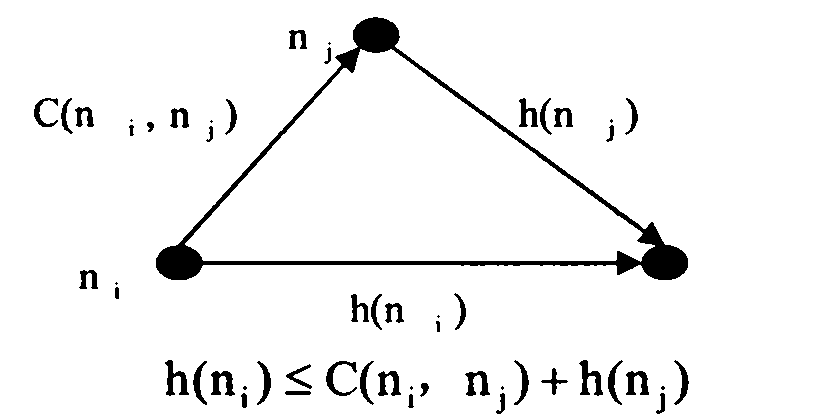Patents
Literature
396 results about "Analysis of algorithms" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
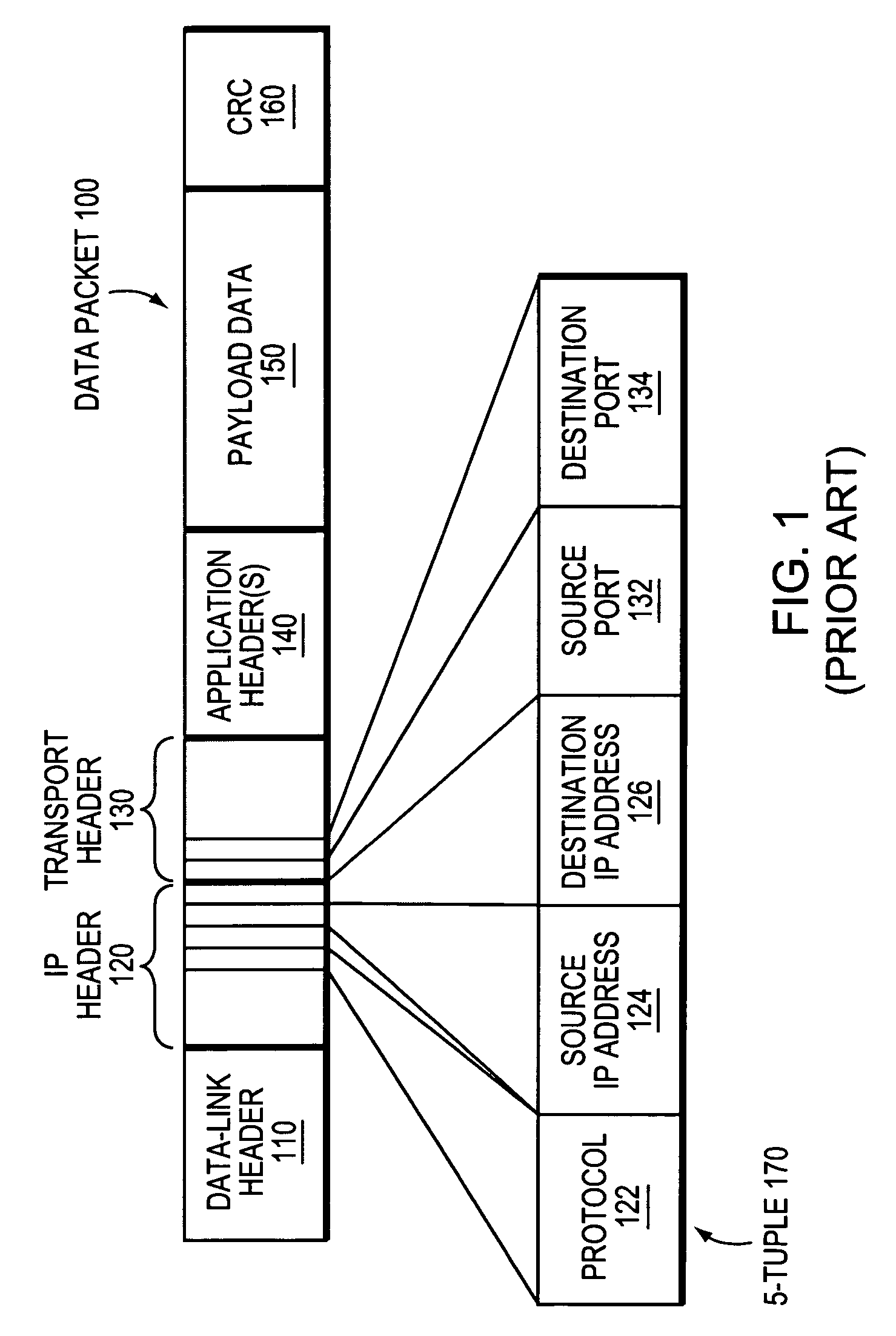
In computer science, the analysis of algorithms is the process of finding the computational complexity of algorithms – the amount of time, storage, or other resources needed to execute them. Usually, this involves determining a function that relates the length of an algorithm's input to the number of steps it takes (its time complexity) or the number of storage locations it uses (its space complexity). An algorithm is said to be efficient when this function's values are small, or grow slowly compared to a growth in the size of the input. Different inputs of the same length may cause the algorithm to have different behavior, so best, worst and average case descriptions might all be of practical interest. When not otherwise specified, the function describing the performance of an algorithm is usually an upper bound, determined from the worst case inputs to the algorithm.
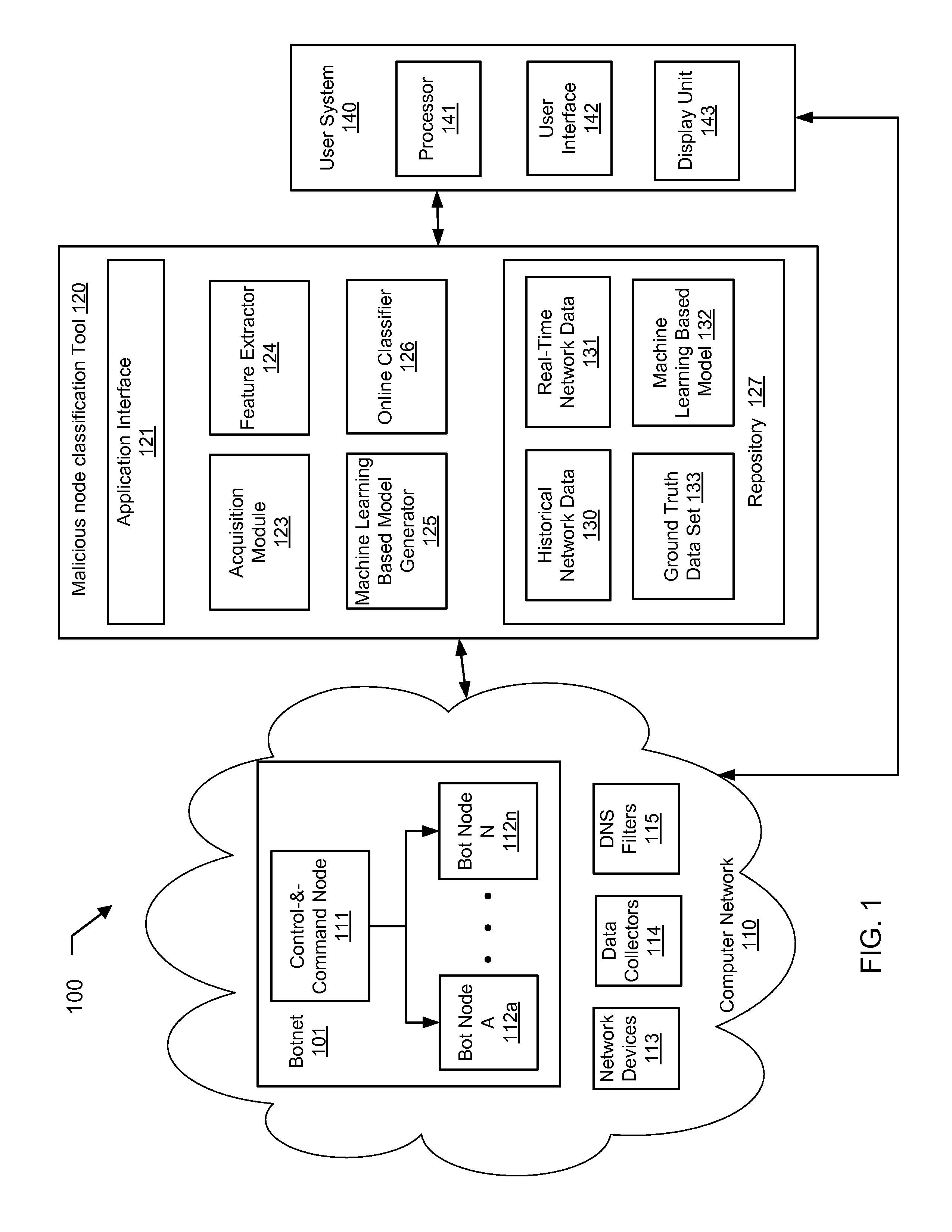
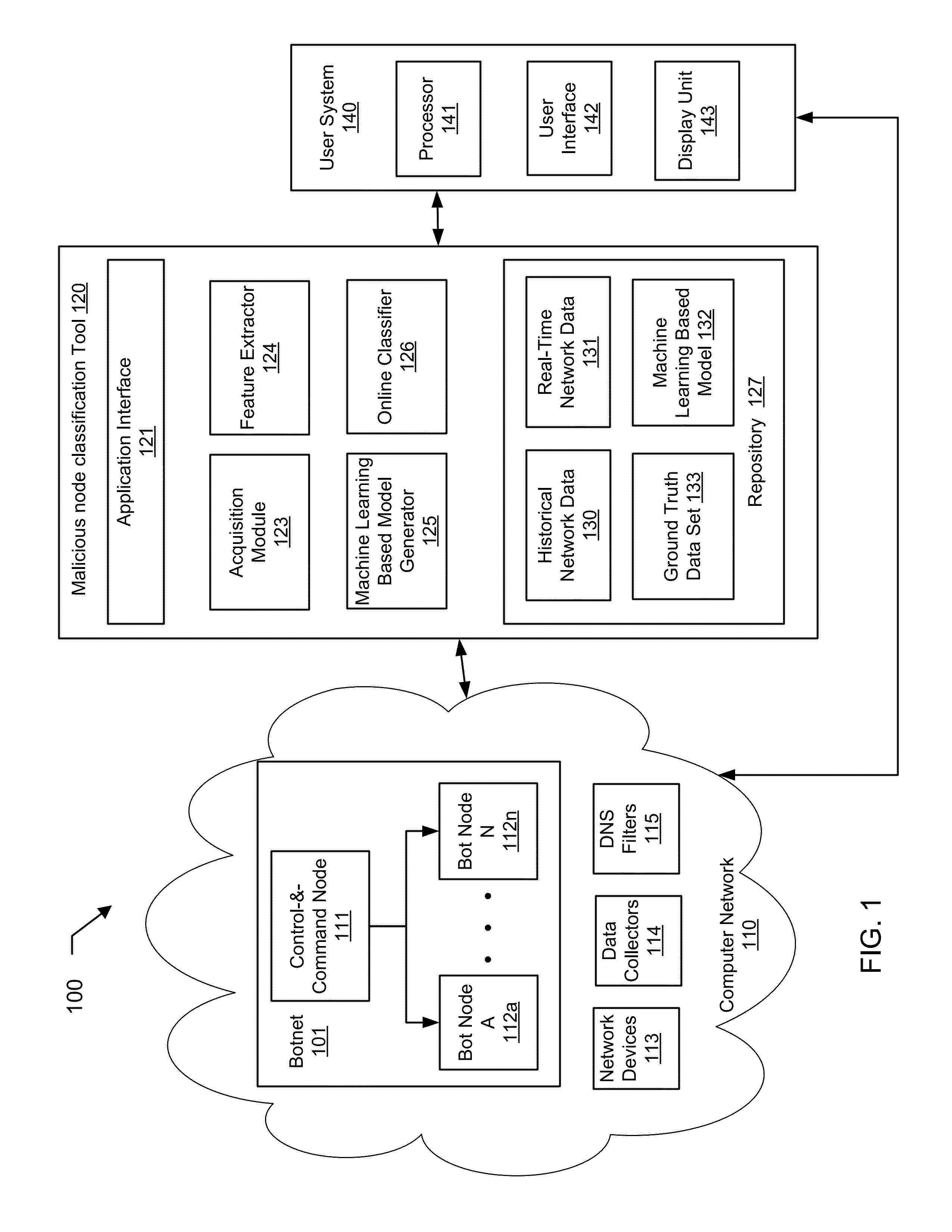
Machine learning based botnet detection using real-time extracted traffic features
ActiveUS8682812B1Digital computer detailsComputer security arrangementsLearning basedTraffic capacity
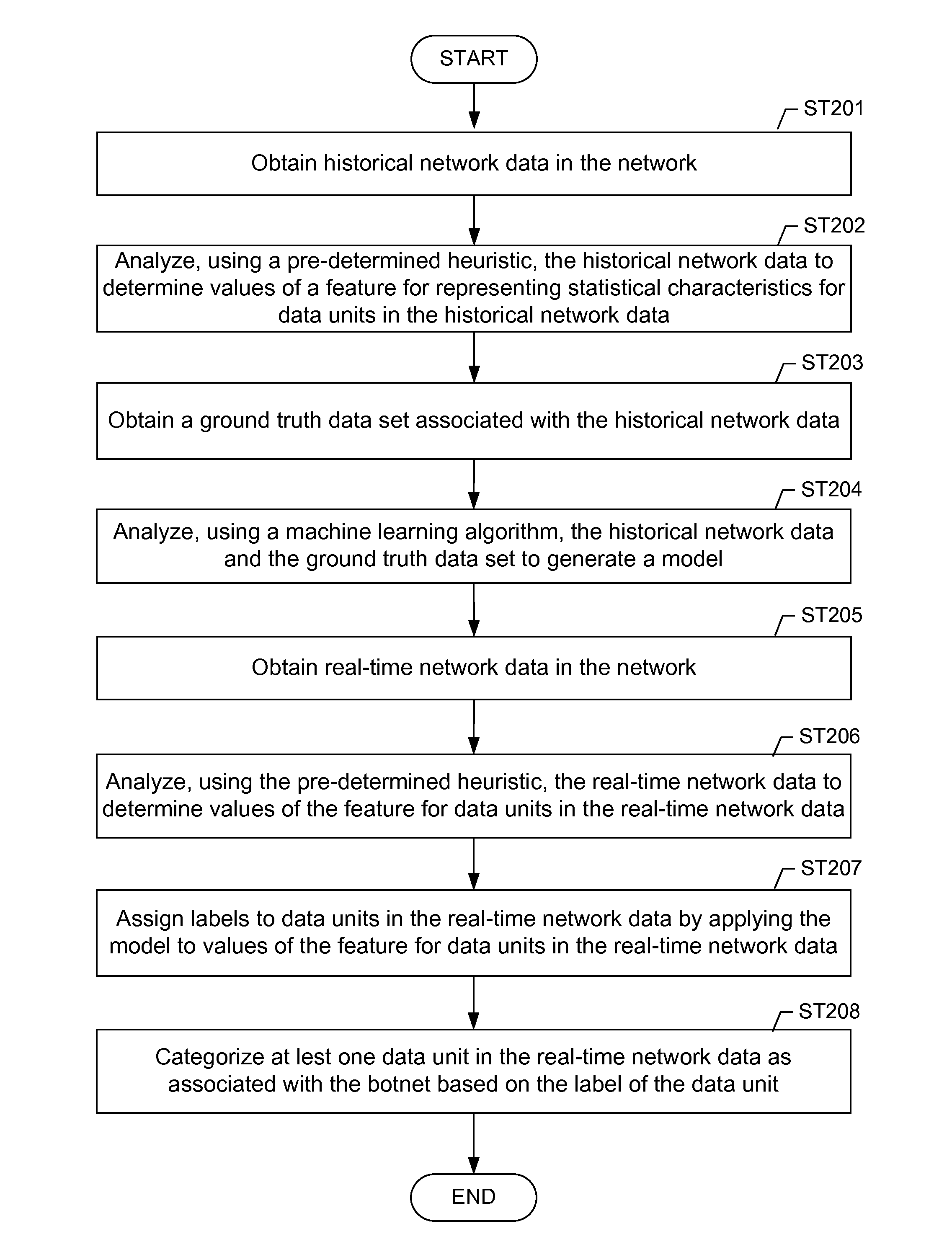
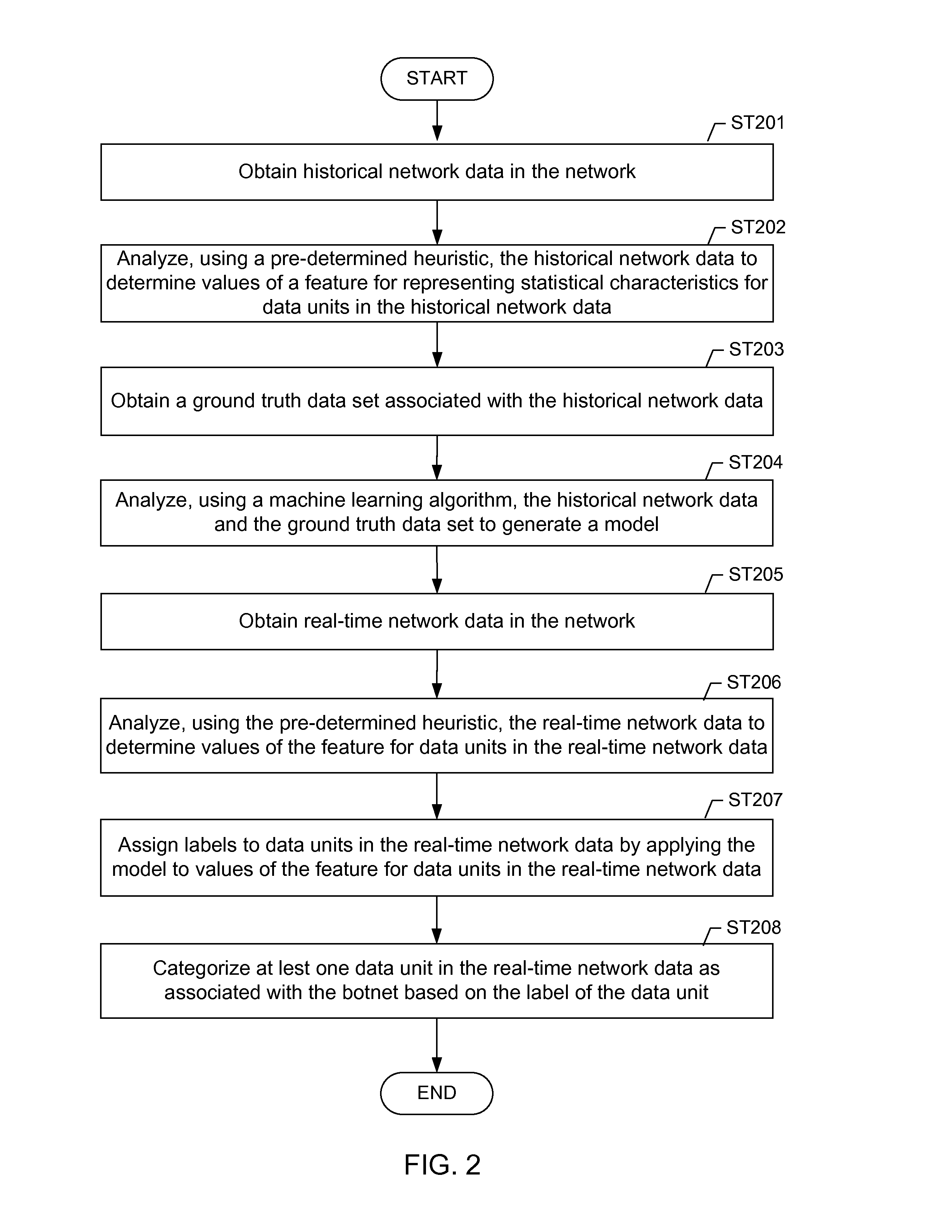
A method for identifying a botnet in a network, including analyzing historical network data using a pre-determined heuristic to determine values of a feature in the historical network data, obtaining a ground truth data set having labels assigned to data units in the historical network data identifying known malicious nodes in the network, analyzing the historical network data and the ground truth data set using a machine learning algorithm to generate a model representing the labels as a function of the values of the feature, analyzing real-time network data using the pre-determined heuristic to determine a value of the feature for a data unit in the real-time network data, assigning a label to the data unit by applying the model to the value of the feature, and categorizing the data unit as associated with the botnet based on the label.
Owner:THE BOEING CO
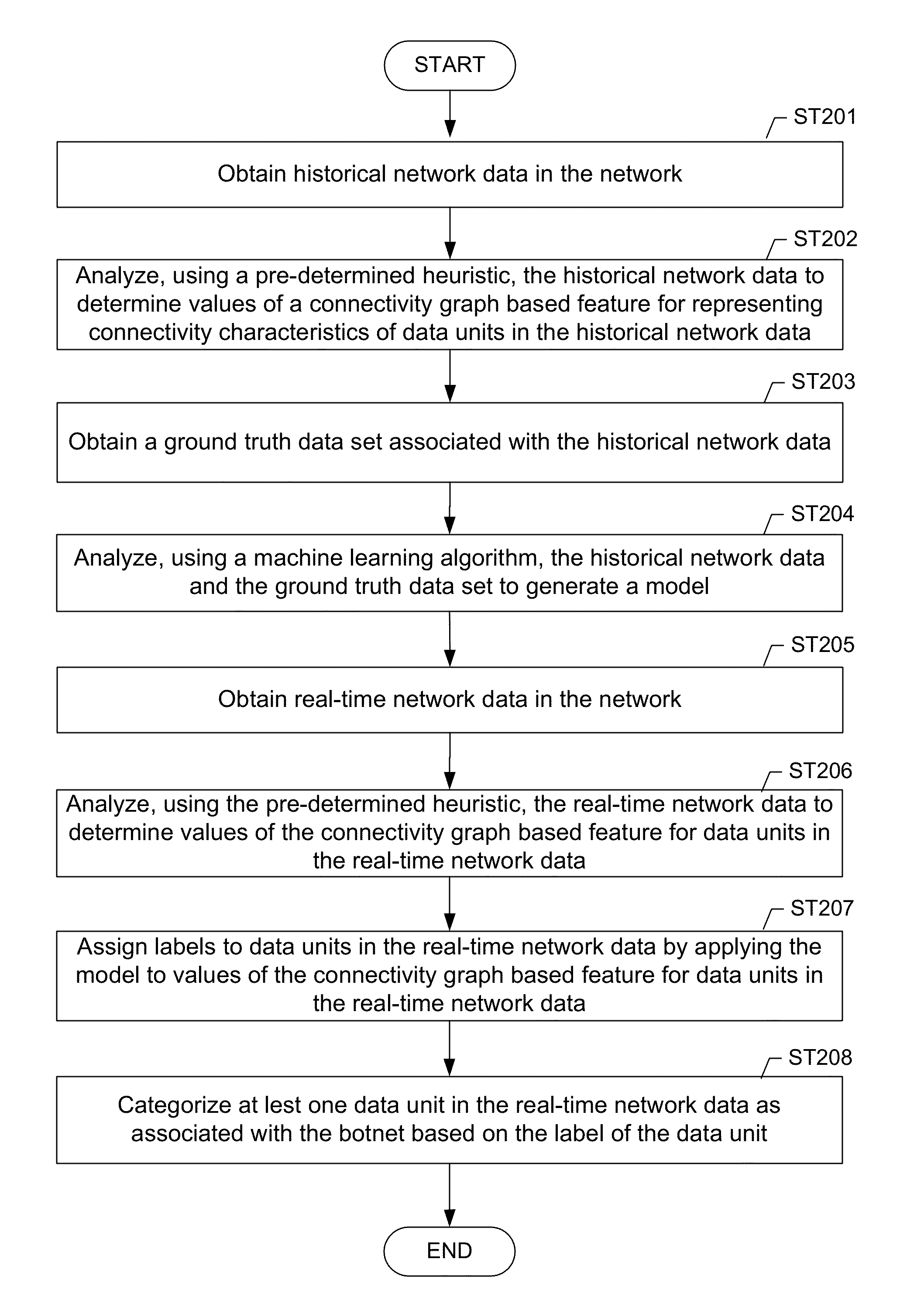
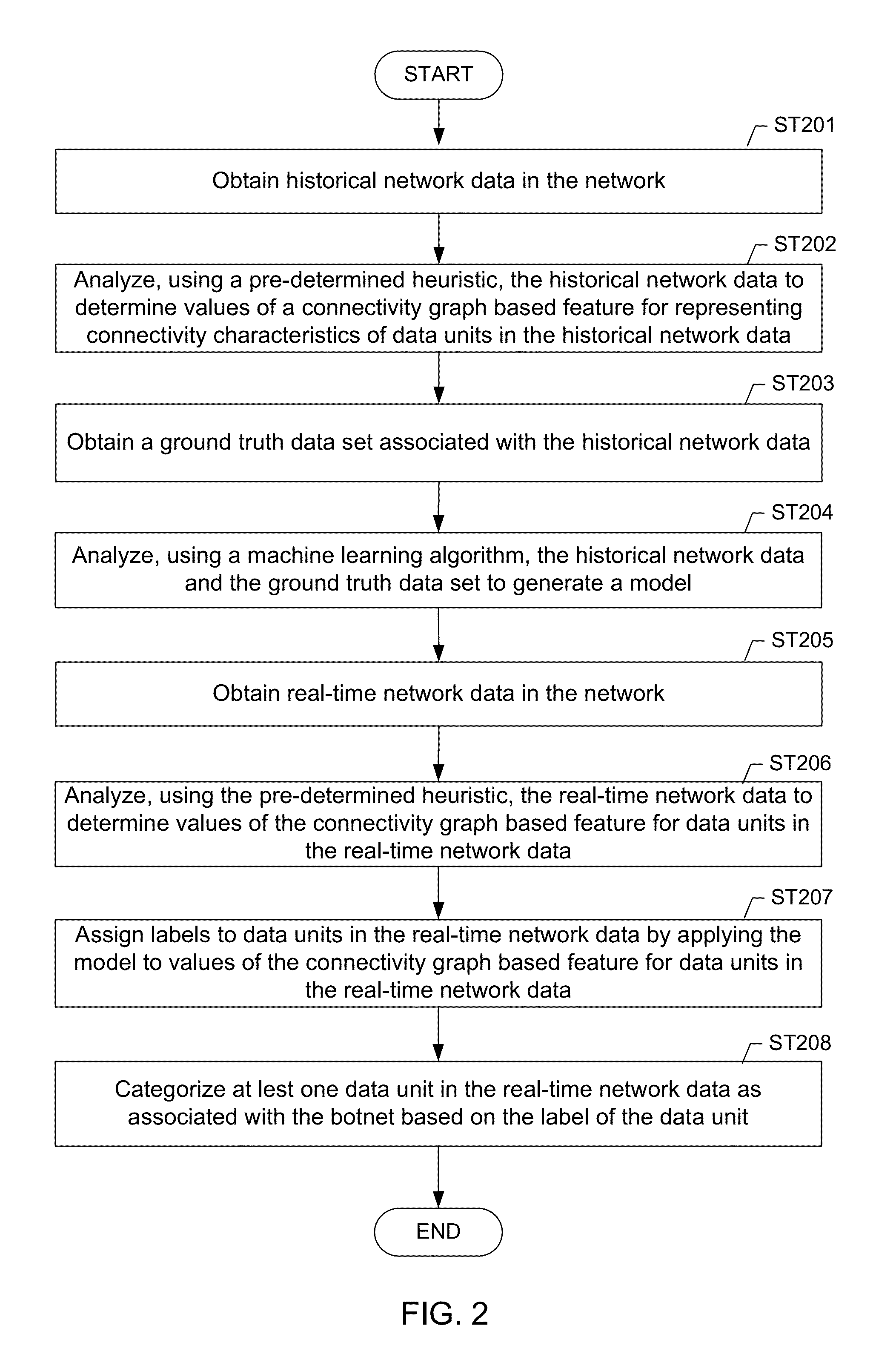
Machine learning based botnet detection using real-time connectivity graph based traffic features
A method for identifying a botnet in a network, including analyzing historical network data using a pre-determined heuristic to determine values of a connectivity graph based feature in the historical network data, obtaining a ground truth data set having labels assigned to data units in the historical network data identifying known malicious nodes in the network, analyzing the historical network data and the ground truth data set using a machine learning algorithm to generate a model representing the labels as a function of the values of the connectivity graph based feature, analyzing real-time network data using the pre-determined heuristic to determine a value of the connectivity graph based feature for a data unit in the real-time network data, assigning a label to the data unit by applying the model to the value of the connectivity graph based feature, and categorizing the data unit as associated with the botnet based on the label.
Owner:THE BOEING CO
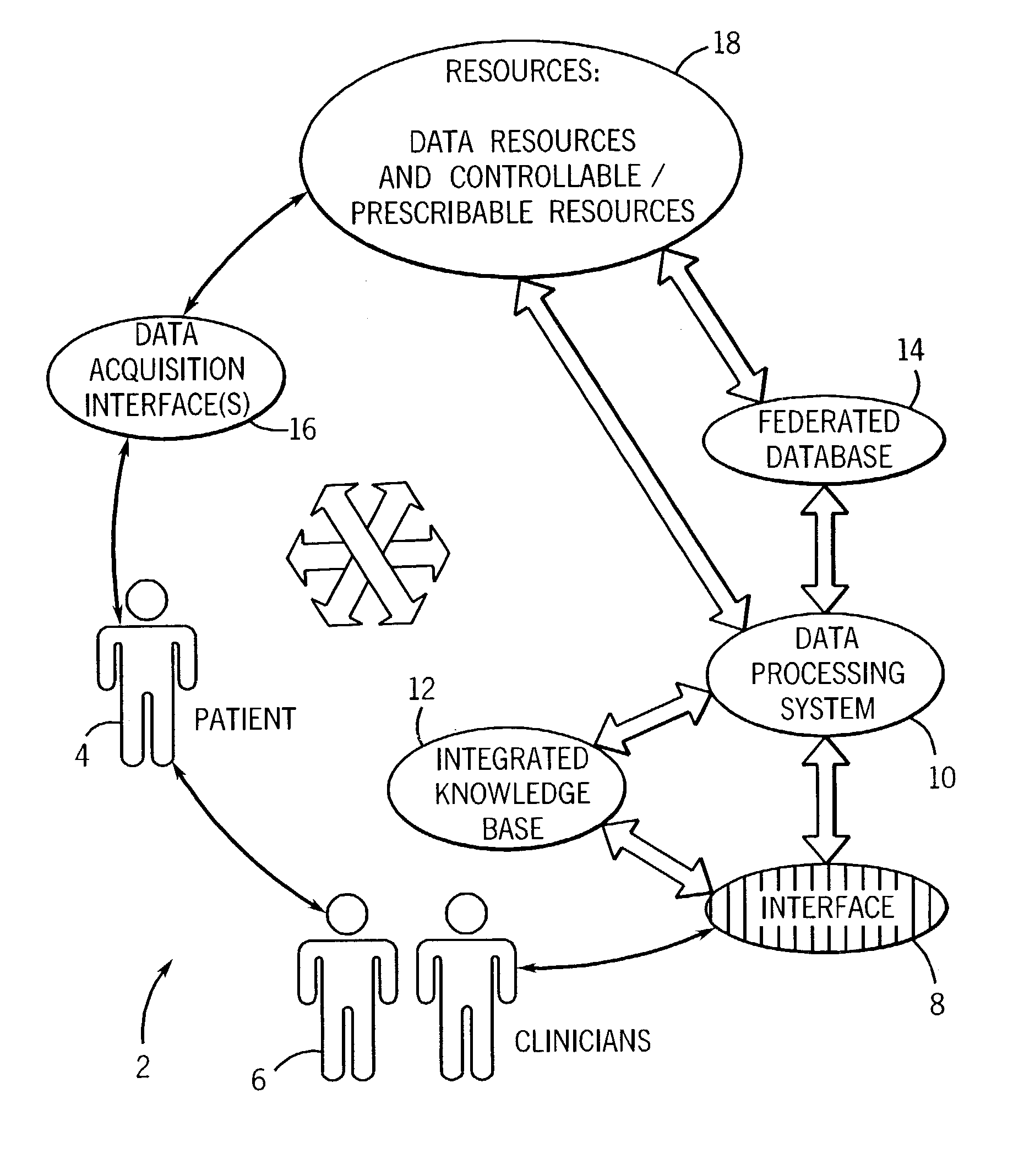
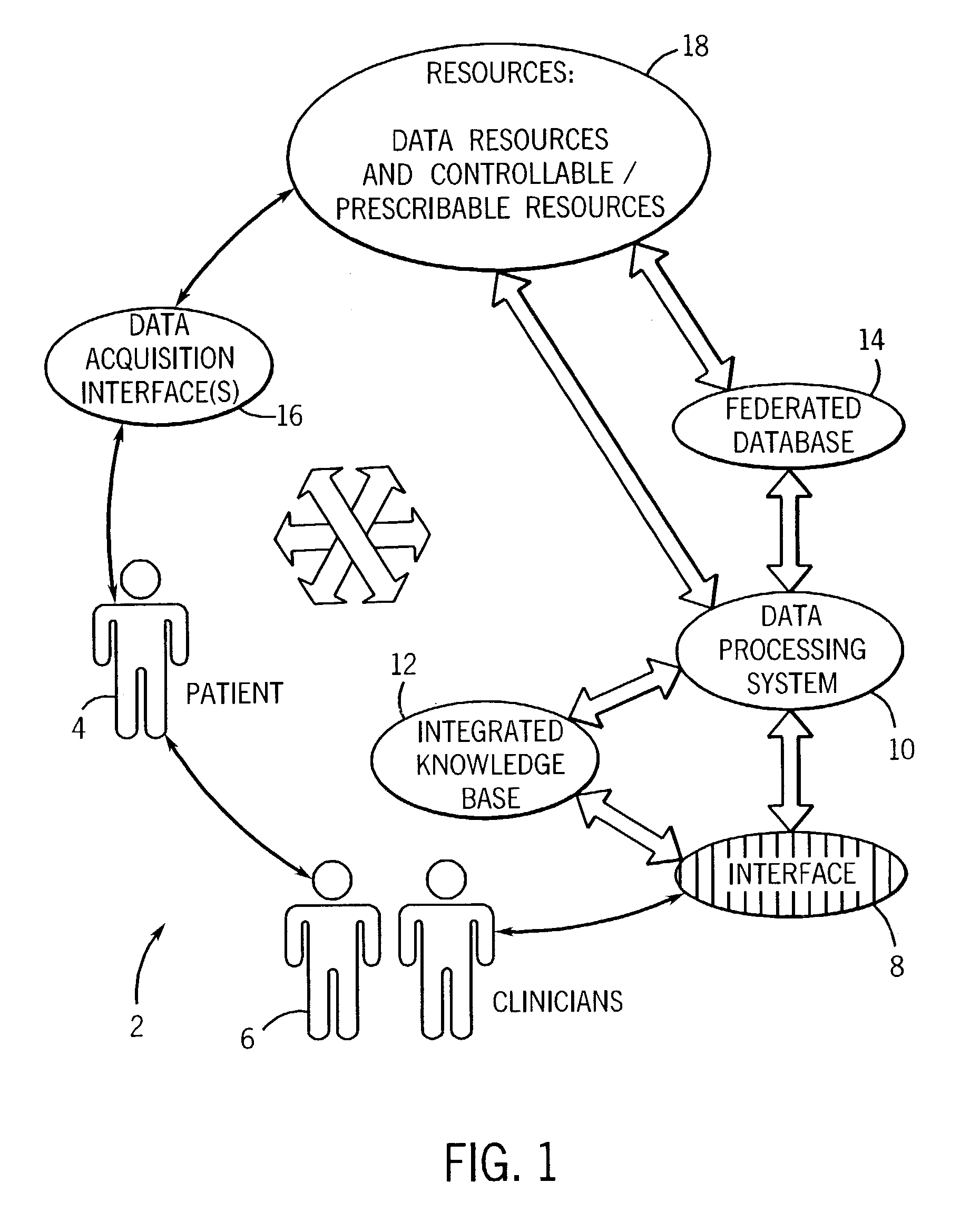
Data processing and feedback method and system
ActiveUS7187790B2Patient care can be improvedQuick identificationCharacter and pattern recognitionOffice automationComputer-aidedHuman operator
A technique is provided for offering feedback, including feedback for patient care and for training purposes for medical professionals and human operators. The technique includes accessing data, such as image data, for evaluation by a human operator. The data is then analyzed via a computer-assisted data operating algorithm, and the analysis may further include analysis of supplemental data accessed from an integrated knowledge base. Based upon the analysis feedback is provided to the operator, such as for completing or complementing the evaluation, correcting analysis by the human operator, or otherwise informing the human operator of similarities or differences between the analyses.
Owner:GE MEDICAL SYST GLOBAL TECH CO LLC
Alert system and method for geographic or natural disasters utilizing a telecommunications network
InactiveUS6914525B2Avoid lostLow costFrequency-division multiplex detailsTime-division multiplexCommunication unitTelecommunications network
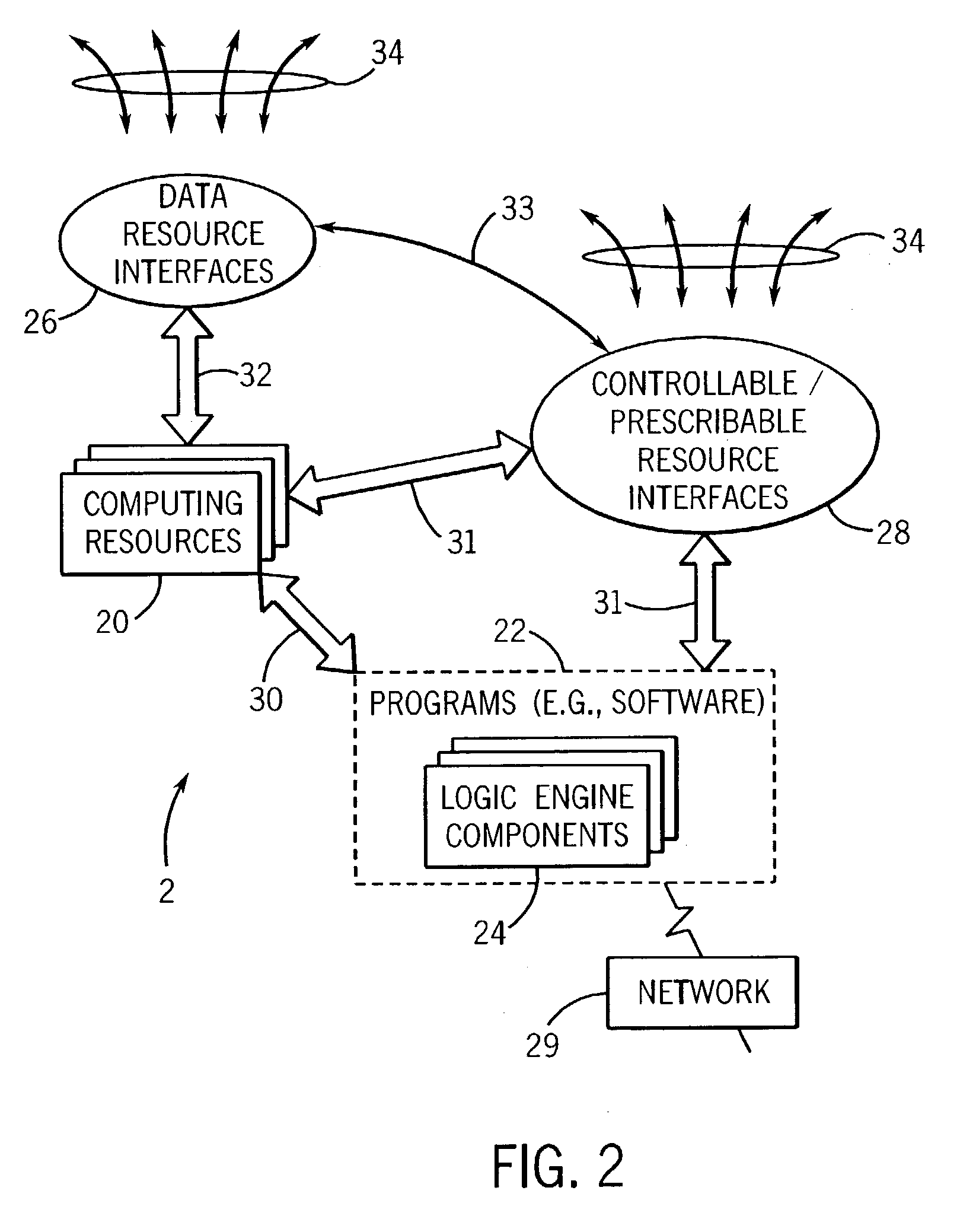
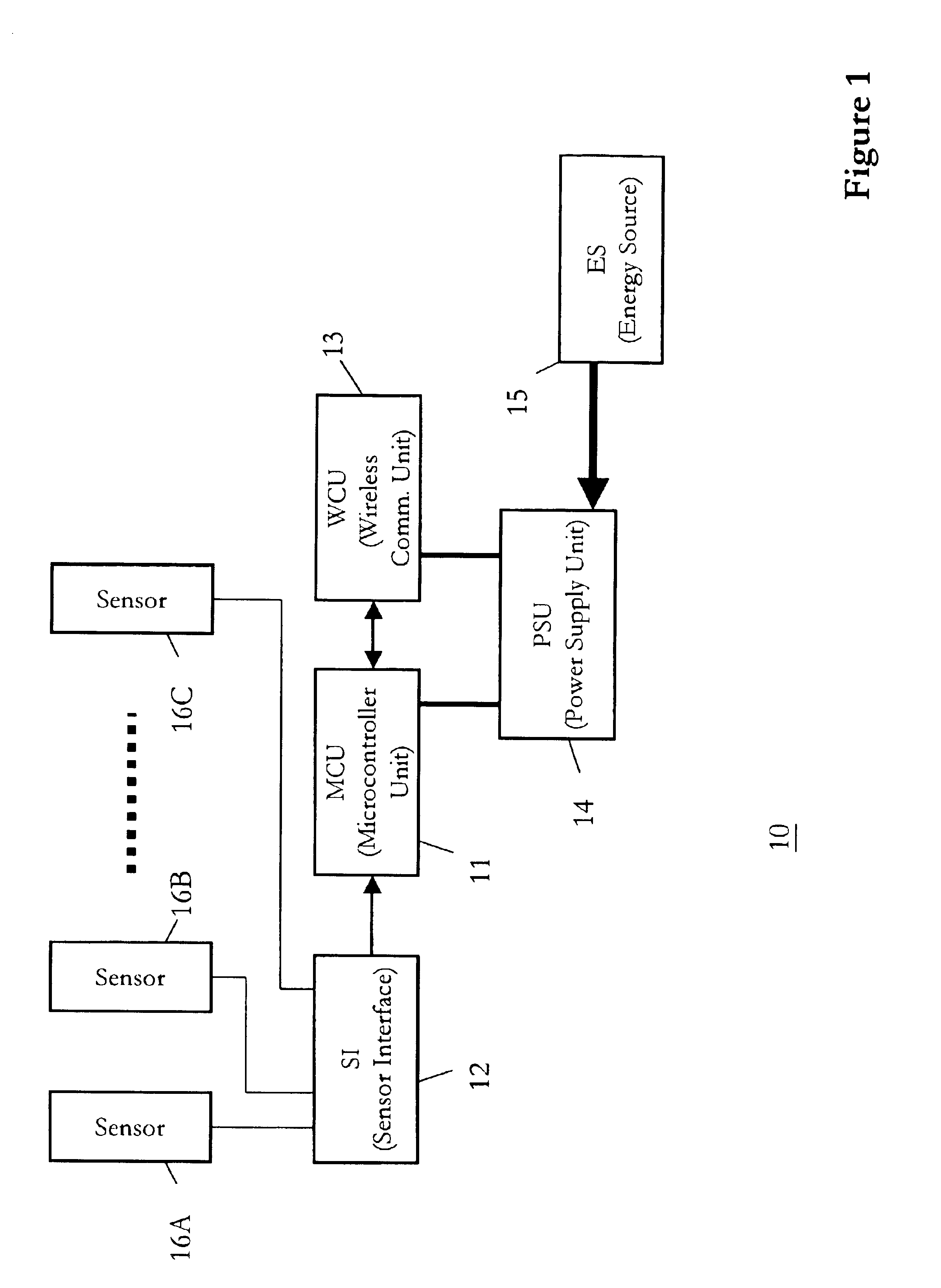
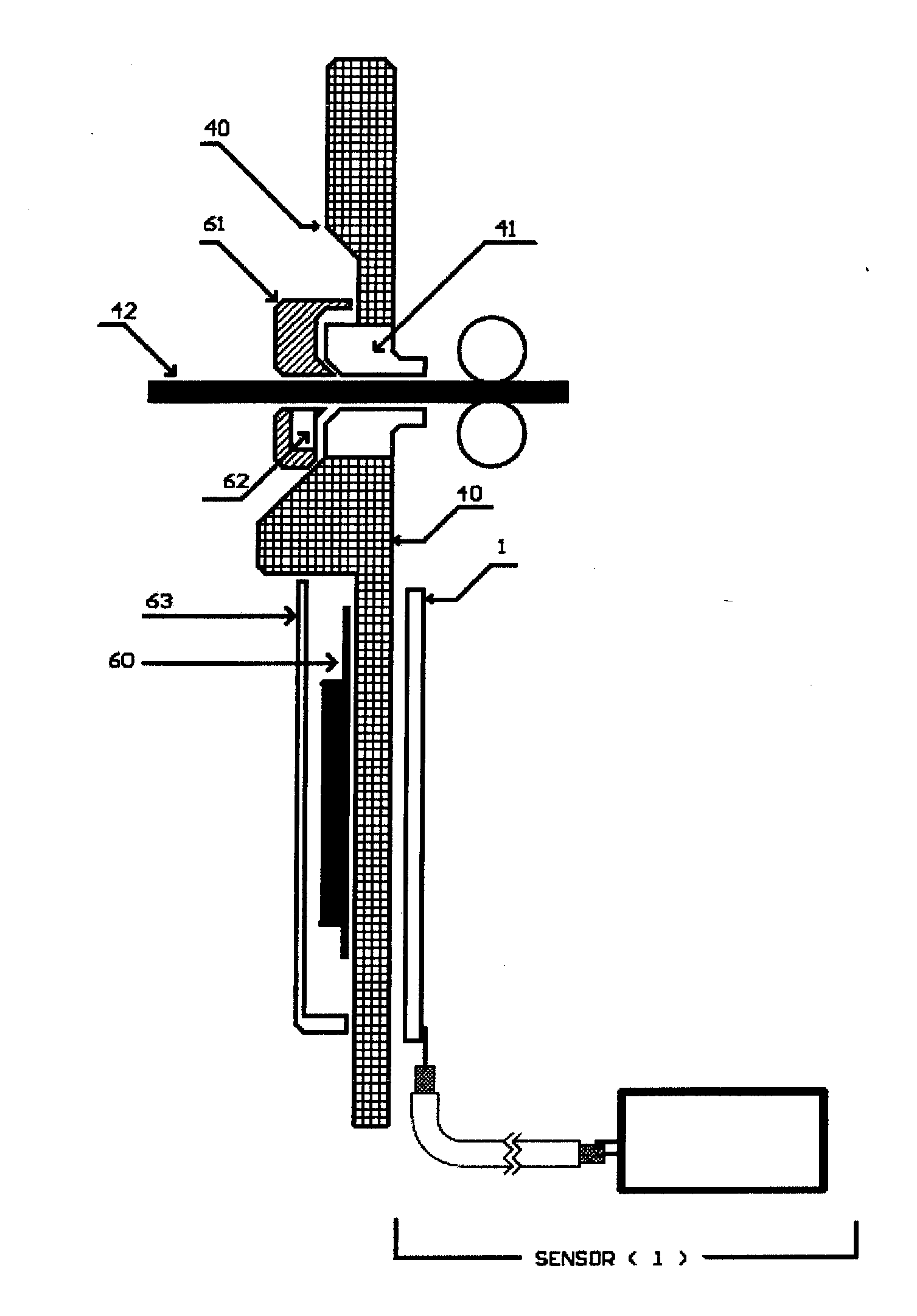
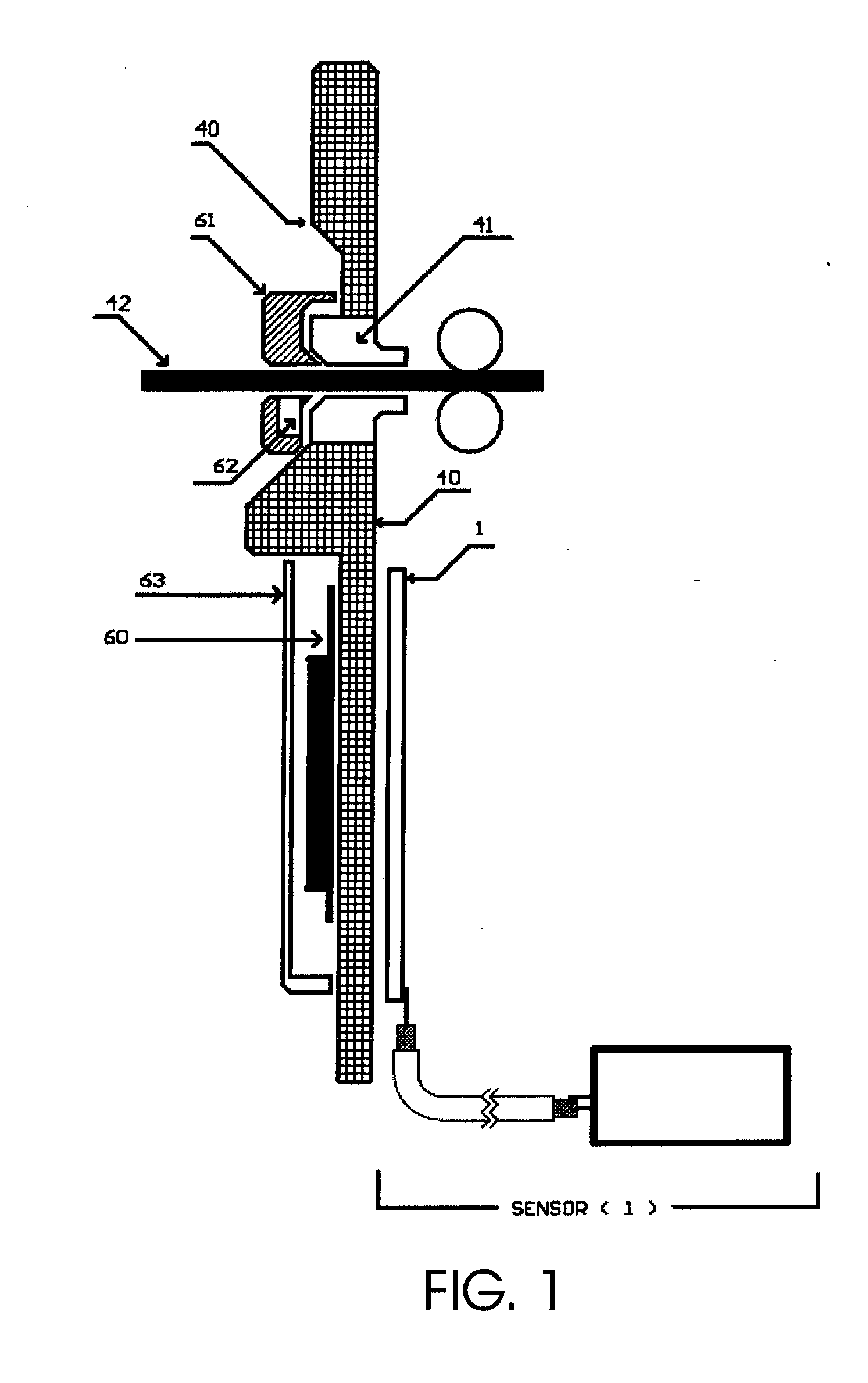
The invention advantageously provides an alert system and method for geographic or natural disasters that utilize a telecommunications network for monitoring geographic data in disaster-prone areas and accordingly issuing warnings against potential disasters to people inside the monitored area. An alert system according to a preferred embodiment of the invention comprises a telecommunications service network, one or more wireless sensor modules and a control center. The telecommunications network according to this particular embodiment includes service coverage over the monitored areas. The wireless sensor modules are installed to selected locations inside monitored areas. Each of the sensor modules further comprises at least one sensor for collecting geographic or geodetic data and a wireless communications unit for sending collected geographic data to the control center via the telecommunications network. The control center then receives and processes the monitored geographic or geodetic data sent by the wireless sensor modules for further algorithmic analysis. The control center accordingly issues alerts for imminent geographic or natural disasters if the processing of the geographic or geodetic data produces adverse results.
Owner:FAR EASTONE TELECOMM
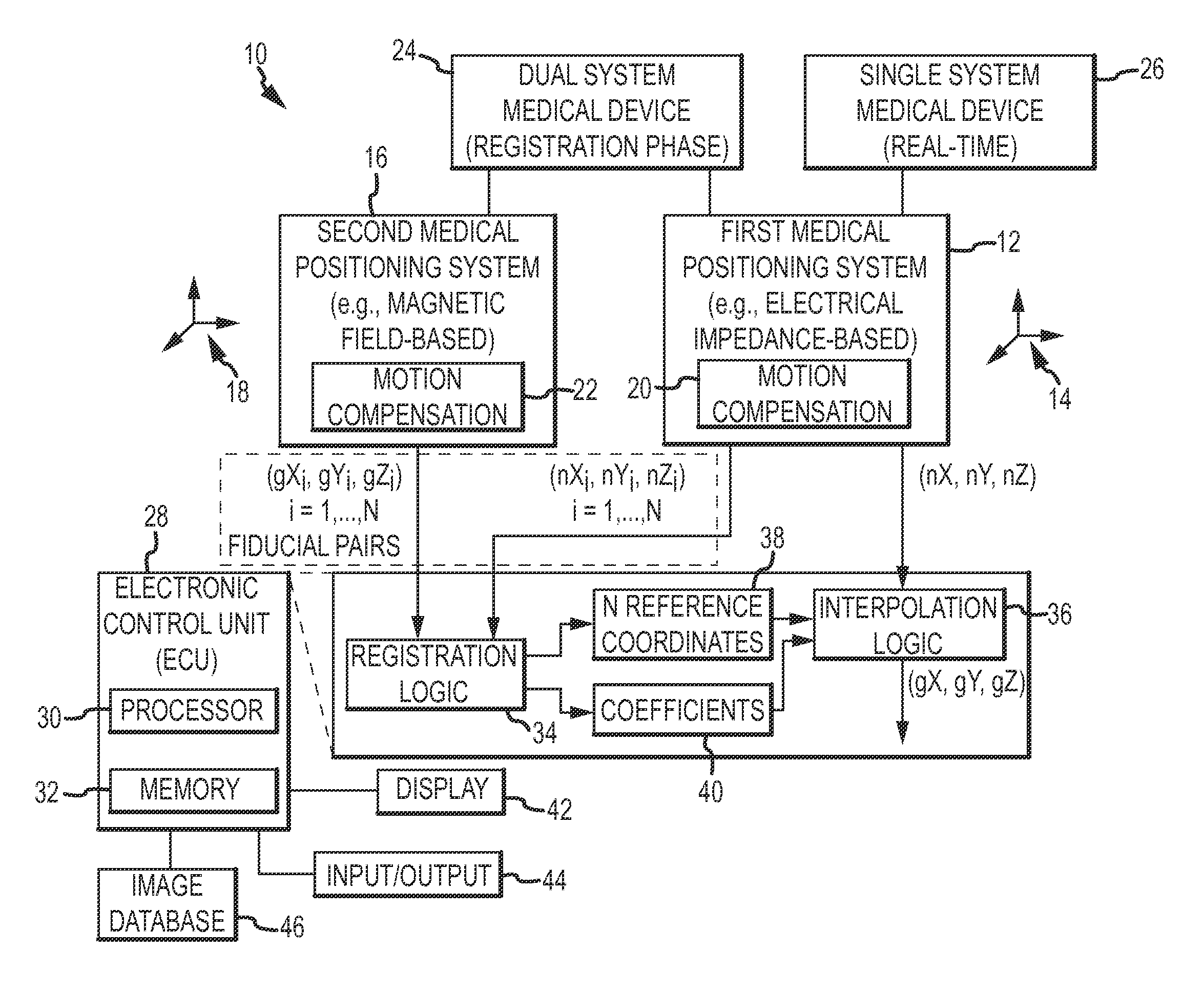
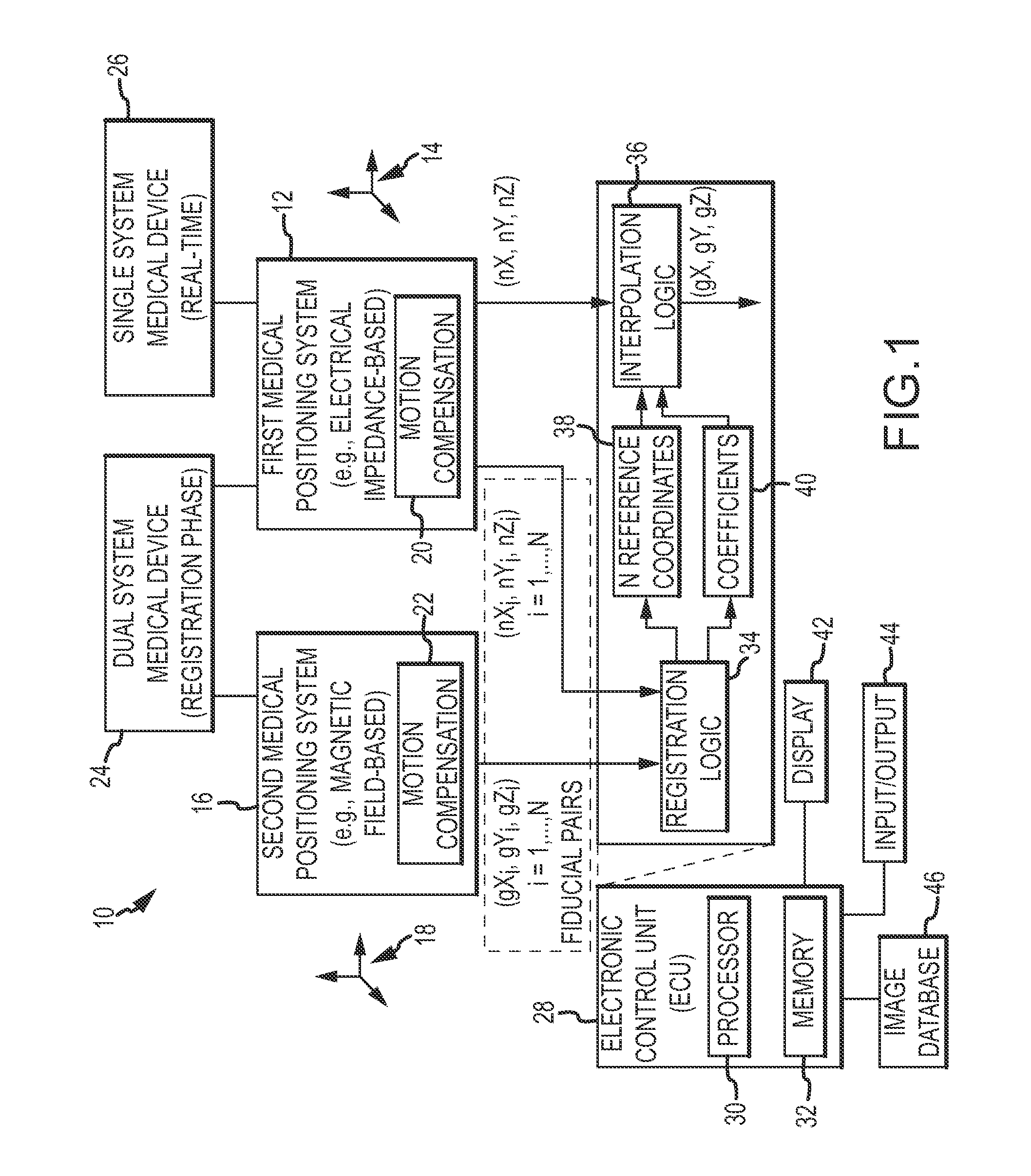
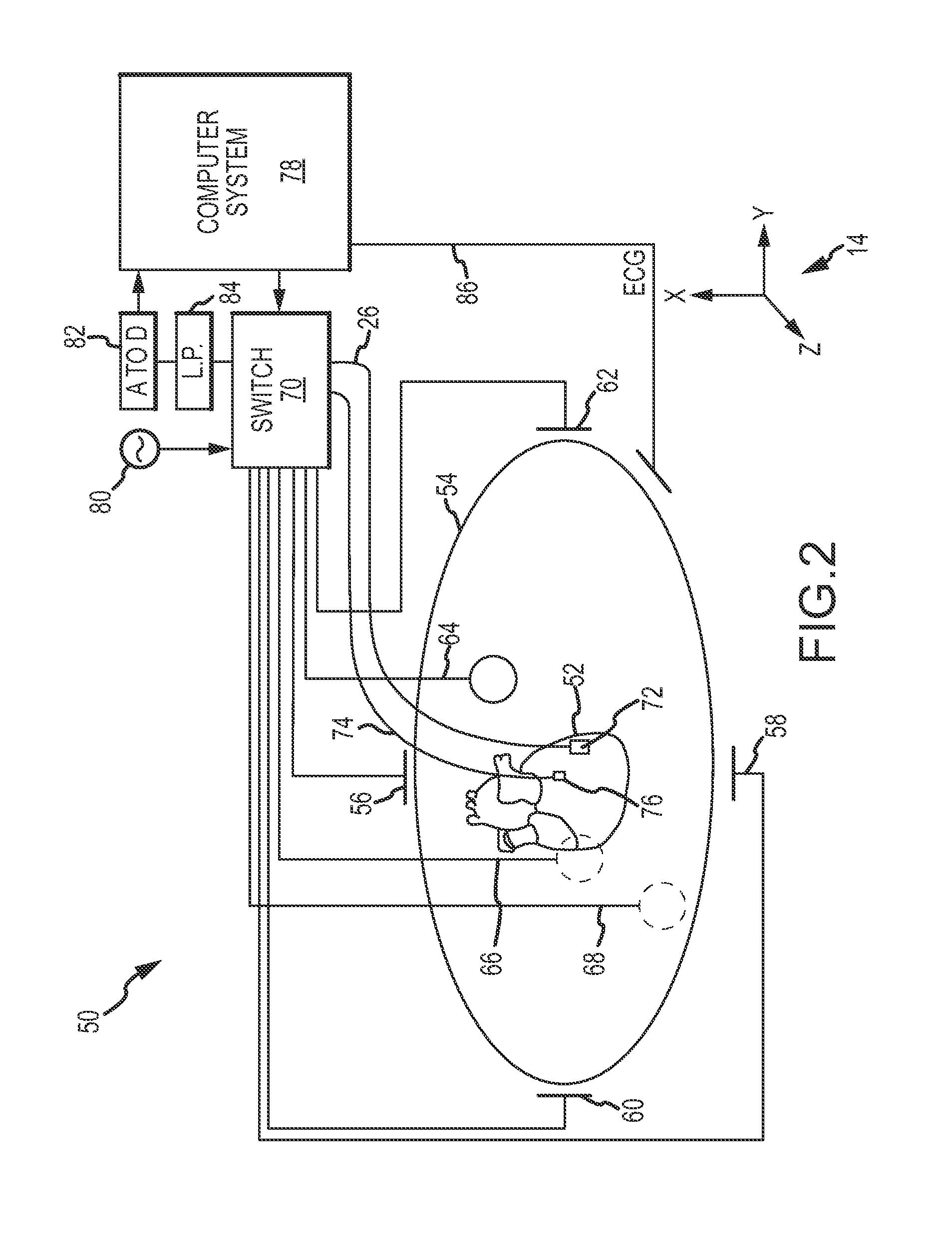
Catheter navigation using impedance and magnetic field measurements
ActiveUS20130066193A1Surgical navigation systemsCatheterThree-dimensional spaceAnalysis of algorithms
A method of operating a positioning system by registering a first coordinate system of a first positioning system in a second coordinate system of a second positioning system includes determining an interpolation function configured to register the first, non-orthonormal coordinate system in the second, orthonormal coordinate system. Fiducial pairs are collected by the respective positioning systems, each of which contain a respective coordinate in the respective coordinate system, both of which refer to the same physical point in three dimensional space. Establishing a working interpolation function involves an analysis of the fiducial pairs using a thin-plate spline algorithm. The method further includes repeatedly obtaining a first coordinate in the first coordinate system and determining a corresponding second coordinate in the second coordinate system in accordance with the interpolation function.
Owner:ST JUDE MEDICAL ATRIAL FIBRILLATION DIV
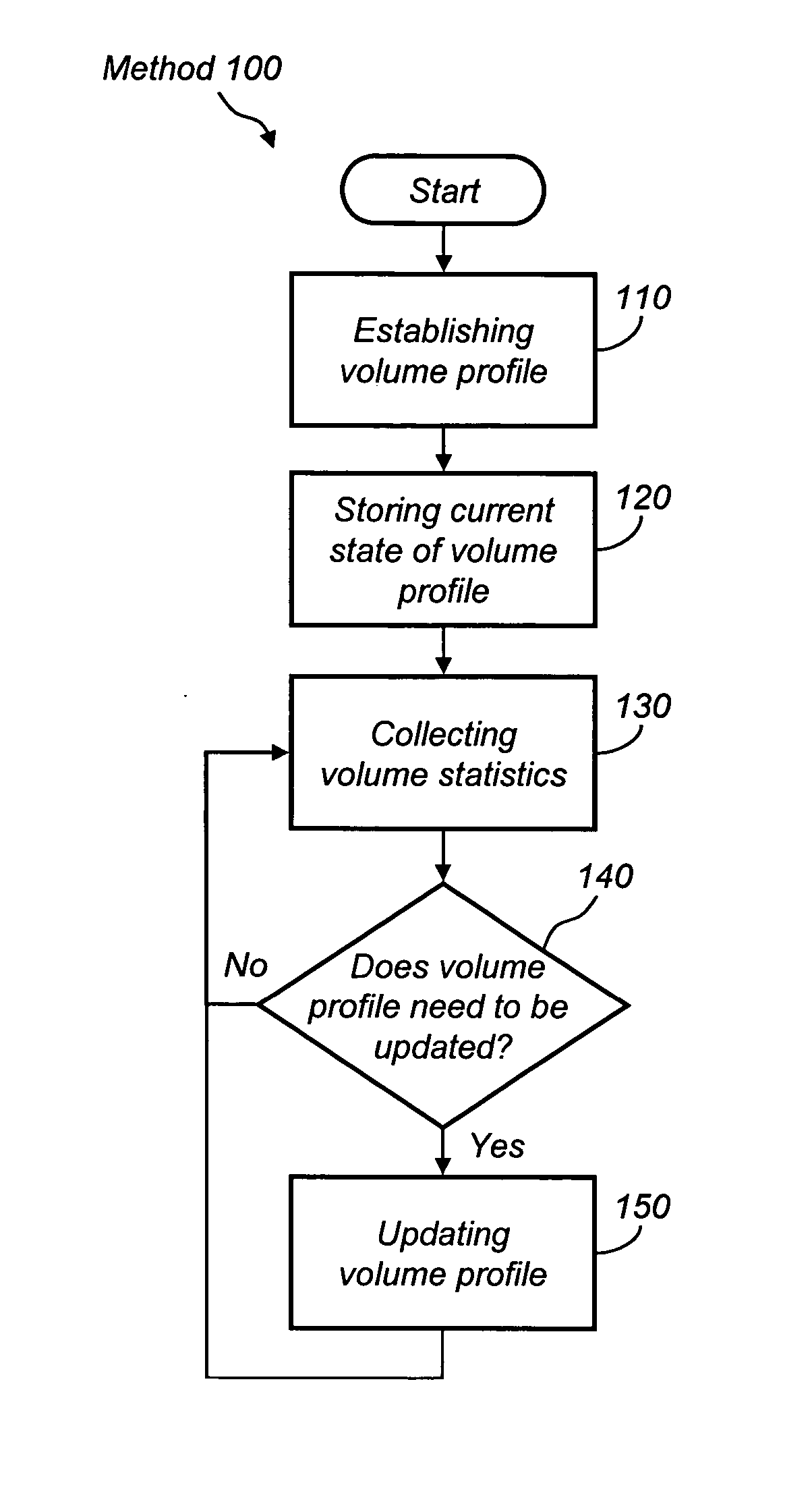
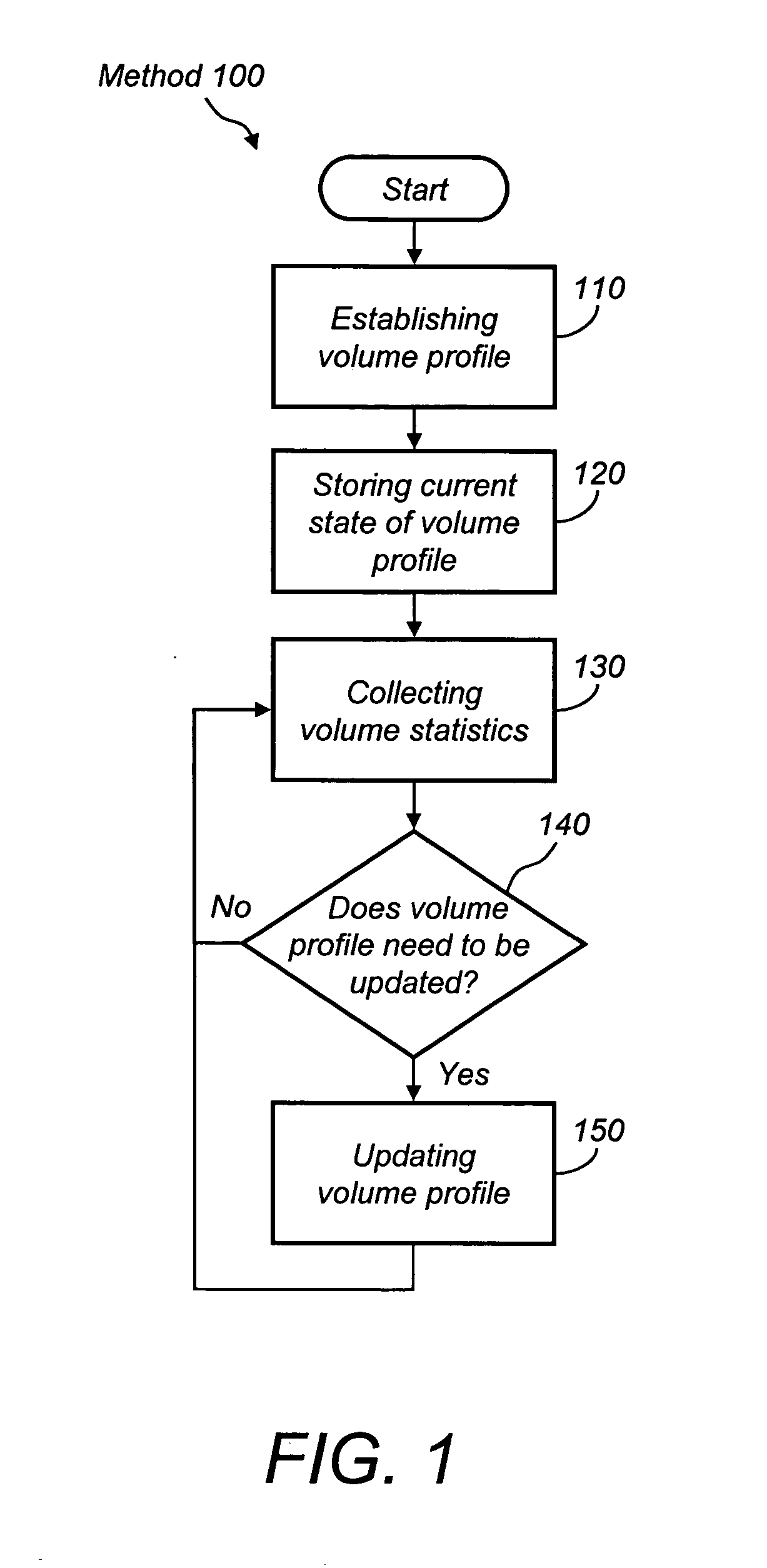
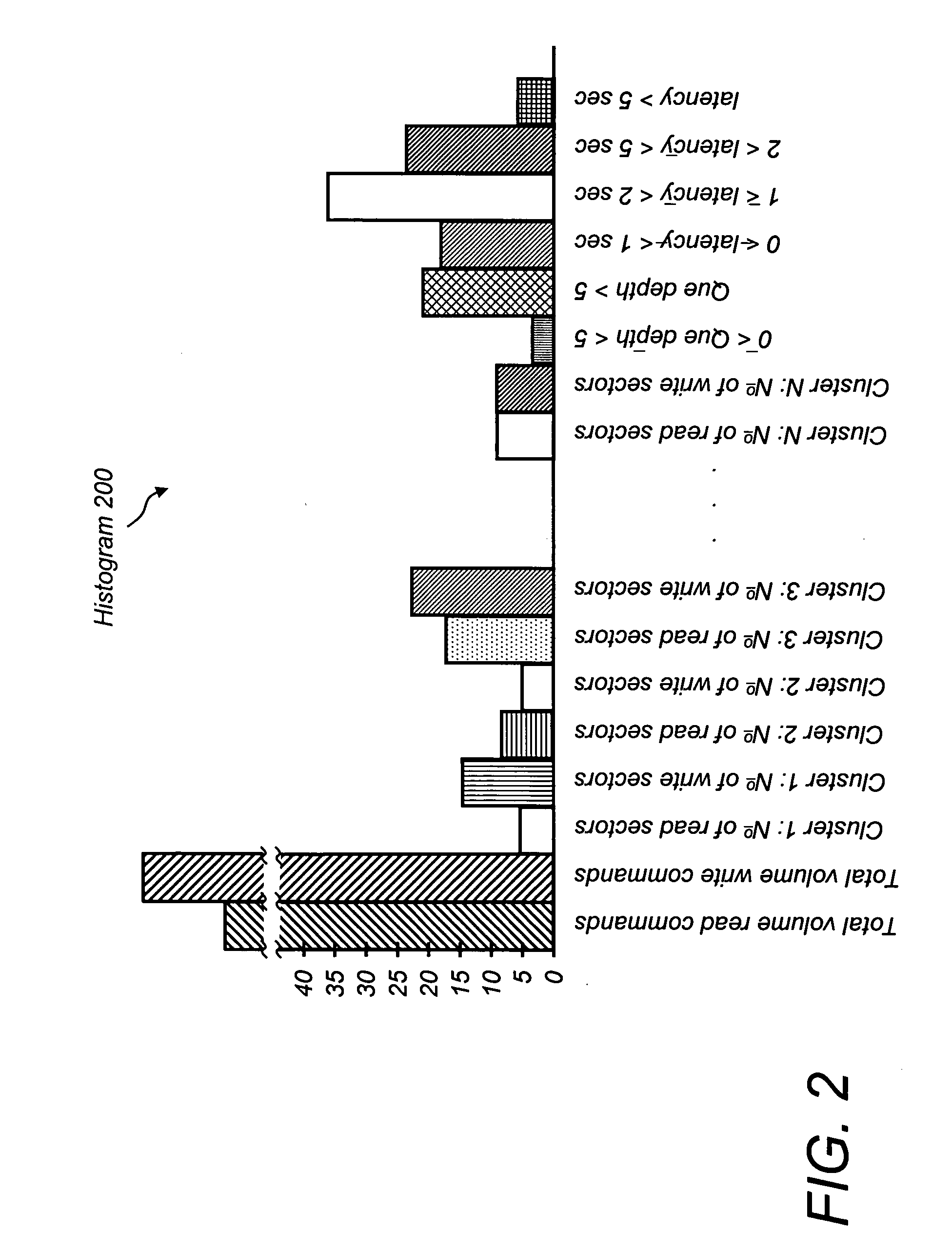
System and method of establishing and reconfiguring volume profiles in a storage system
InactiveUS20050050270A1Improve performanceInput/output to record carriersMemory systemsAnalysis of algorithmsReal-time computing
A method of predictive baseline volume profile creation for new volumes in a networked storage system and a system for dynamically reevaluating system performance and needs to create an optimized and efficient use of system resources by changing volume profiles as necessary. The system gathers statistical data and analyzes the information through algorithms to arrive at an optimal configuration for volume clusters. Clusters are then reallocated and reassigned to match the ideal system configuration for that point in time. The system continually reevaluates and readjusts its performance to meet throughput requirements specified in the quality of service agreement
Owner:ADAPTEC
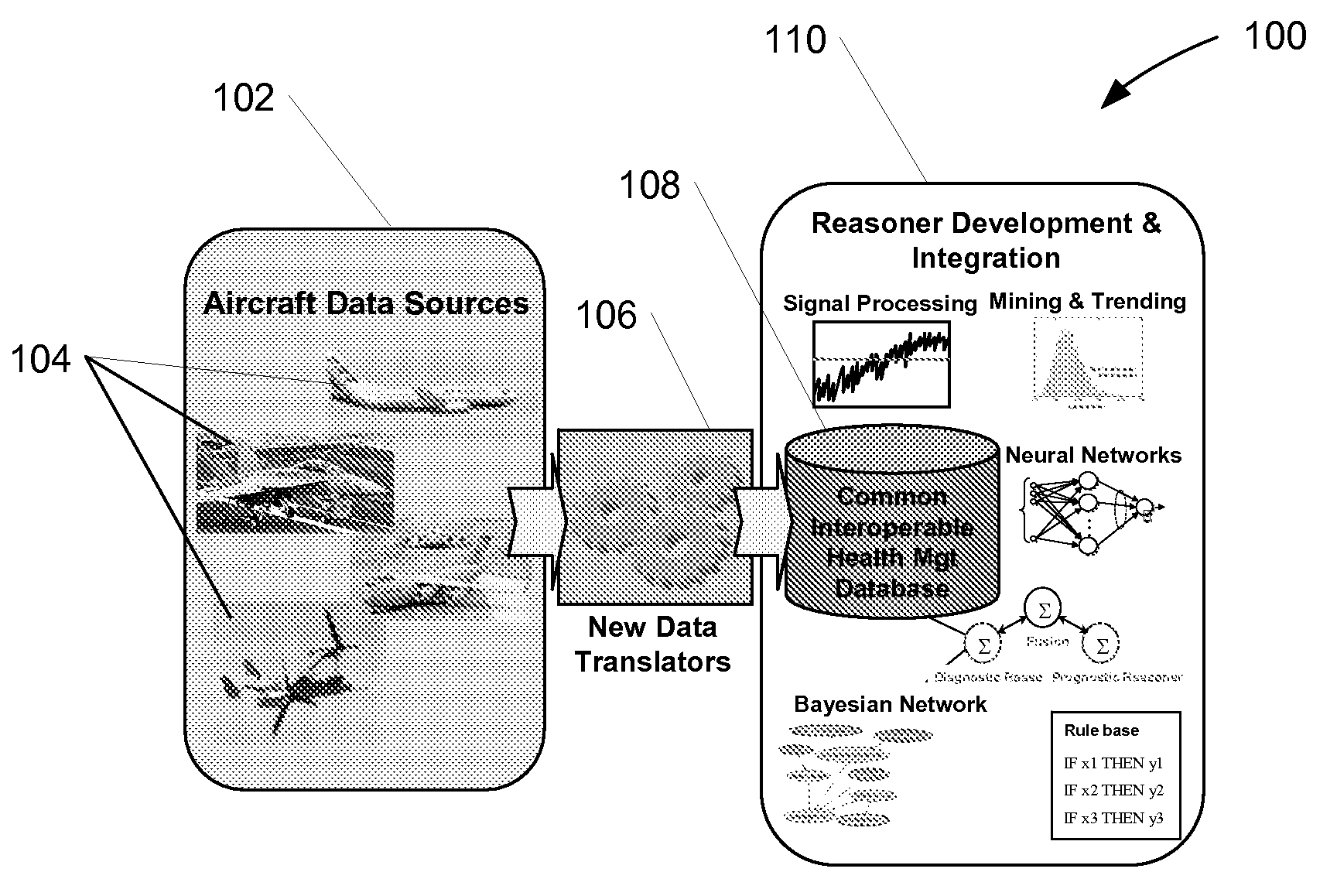
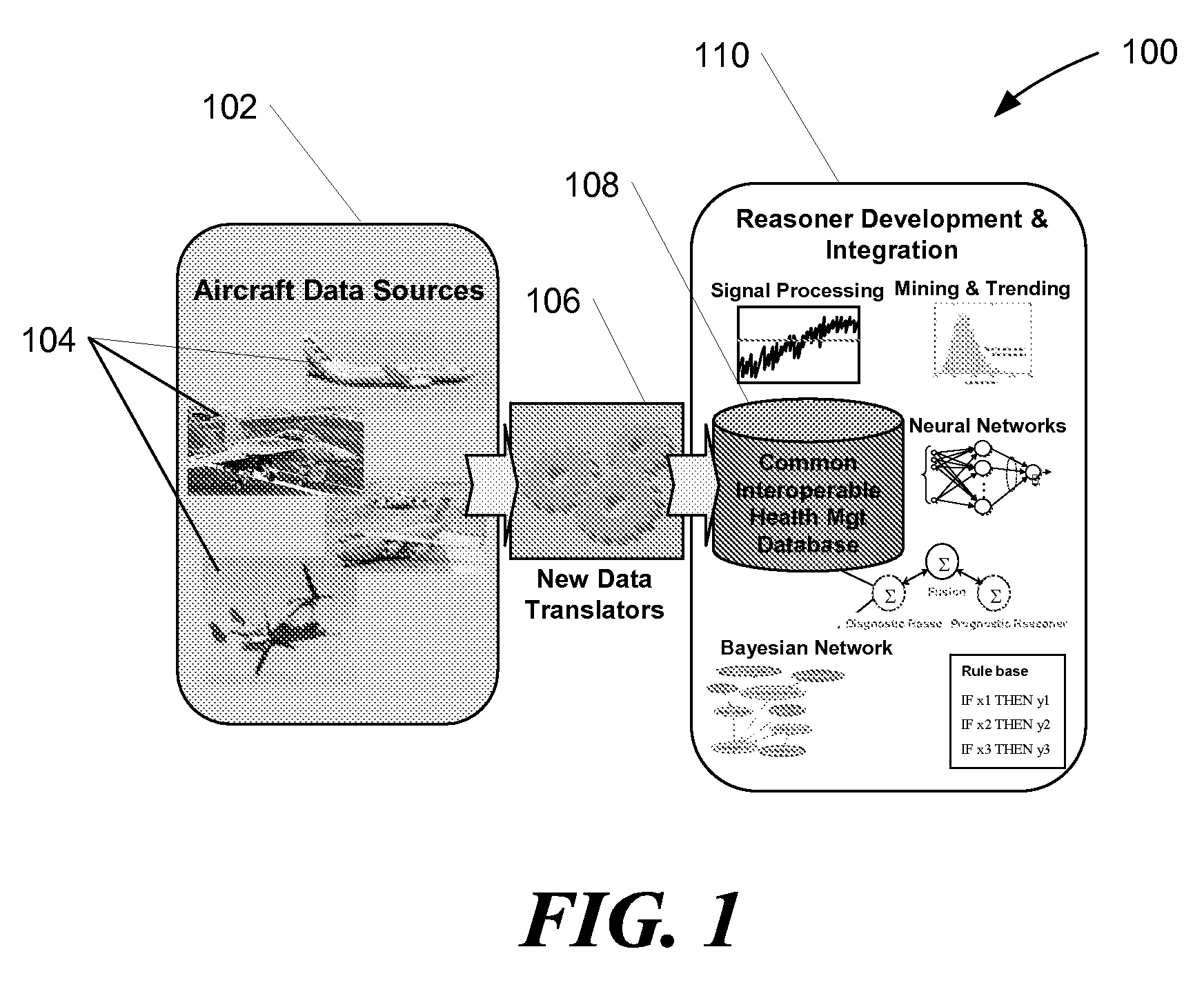
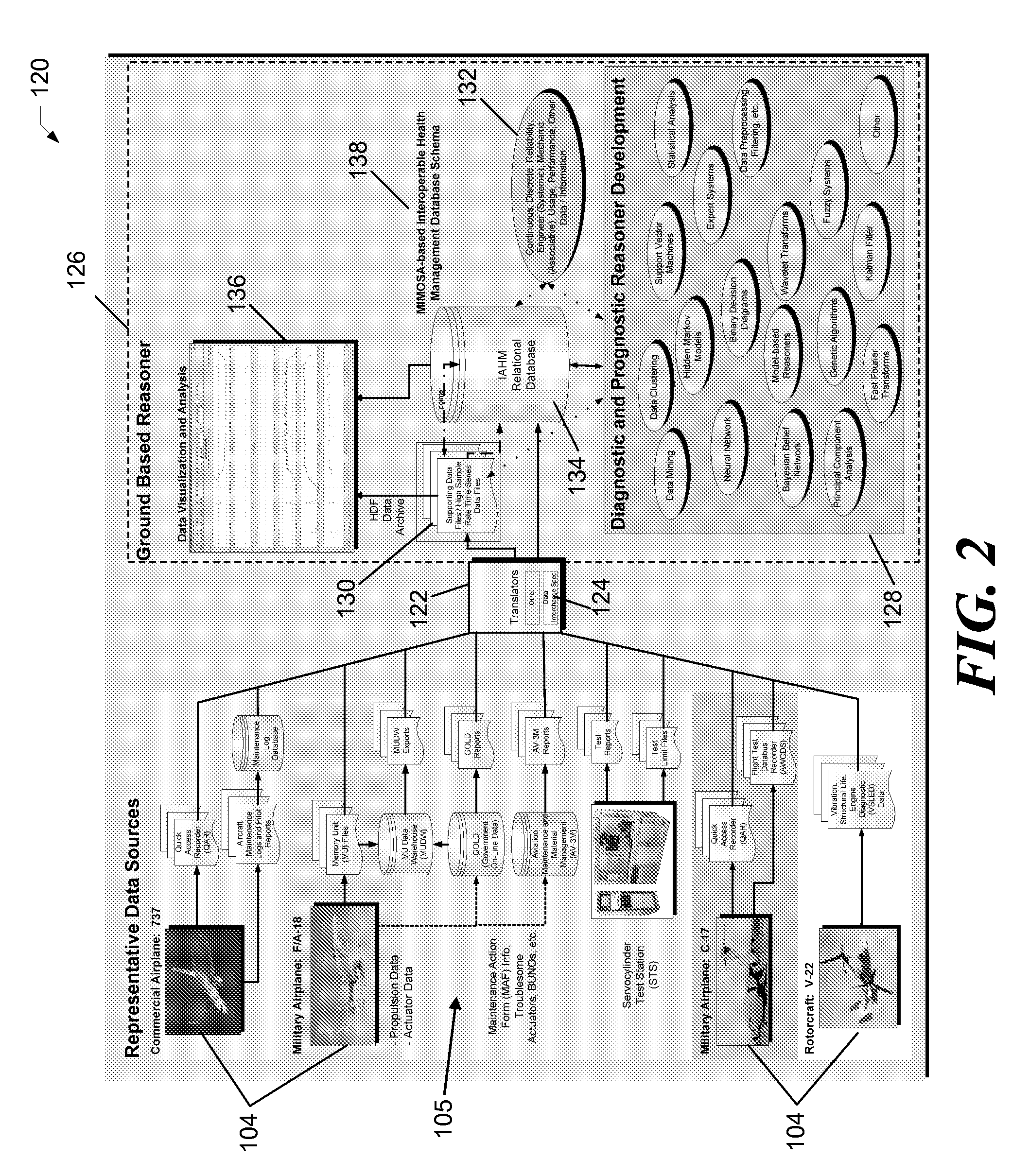
Systems and Methods for Health Management of Single or Multi-Platform Systems
InactiveUS20080040152A1Improve maintainabilityImprove securityData processing applicationsTesting/monitoring control systemsMulti platformAnalysis of algorithms
Systems and methods for health data management are disclosed. In one embodiment, a method of monitoring health information for a multi-platform system includes receiving health information from one or more subsystems of a plurality of platforms, and analyzing the health information using one or more reasoner algorithms configured to predict a potential failure of the one or more subsystems. Upon prediction of a potential failure, the method includes providing a prognostic characteristic of the one or more subsystems. In alternate embodiments, the method may further include translating at least some of the health information for each of the one or more subsystems into a common format, and storing the translated health information into a database for subsequent analysis.
Owner:THE BOEING CO
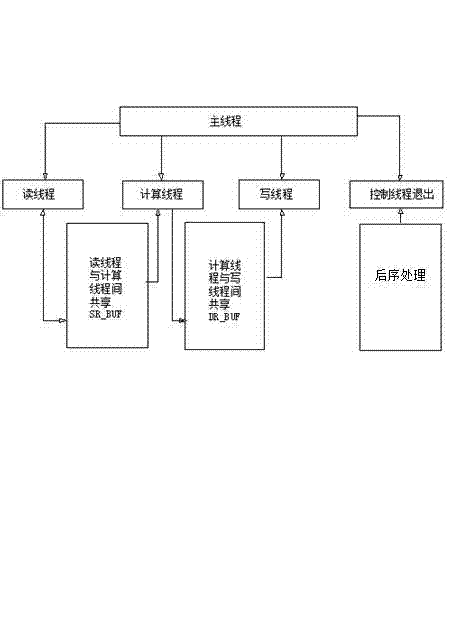
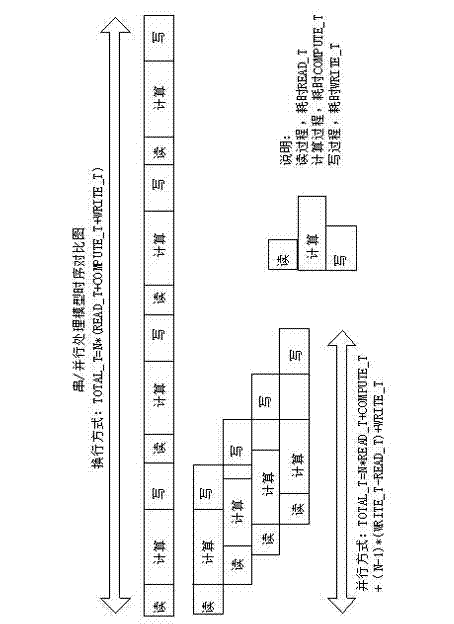
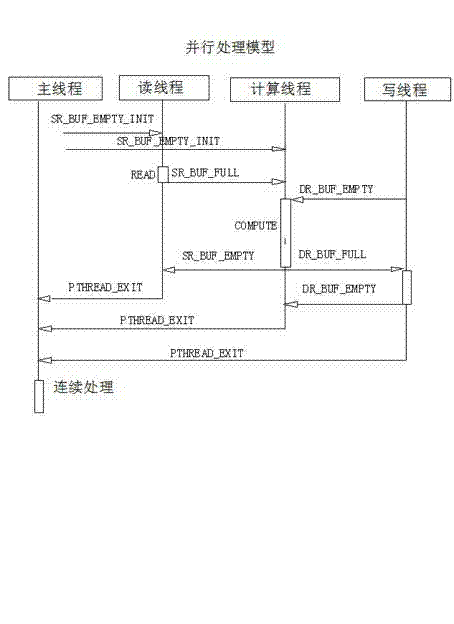
Software performance optimization method based on central processing unit (CPU) multi-core platform
ActiveCN103049245AImprove performanceReduce running timeResource allocationConcurrent instruction executionCache optimizationResource utilization
The invention provides a software performance optimization method based on a CPU multi-core platform. The method comprises software characteristic analysis, parallel optimization scheme formulation and parallel optimization scheme implementation and iteration tuning. Particularly, the method comprises application software characteristic analysis, serial algorithm analysis, CPU multi-in / thread parallel algorithm design, multi-buffer design, design of communication modes among threads, memory access optimization, cache optimization, processor vectorization optimization, mathematical function library optimization and the like. The method is widely applicable to application occasions with multi-thread parallel processing requirements, software developers are guided to perform multi-thread parallel optimization improvement on prior software rapidly and efficiently with short developing periods and low developing costs, the utilization of system resources by software is optimized, data reading and computing and mutual masking of write-back data are achieved, the software running time is shortened furthest, the hardware resource utilization rate is improved apparently, and the software computing efficiency and the software whole performance are enhanced.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
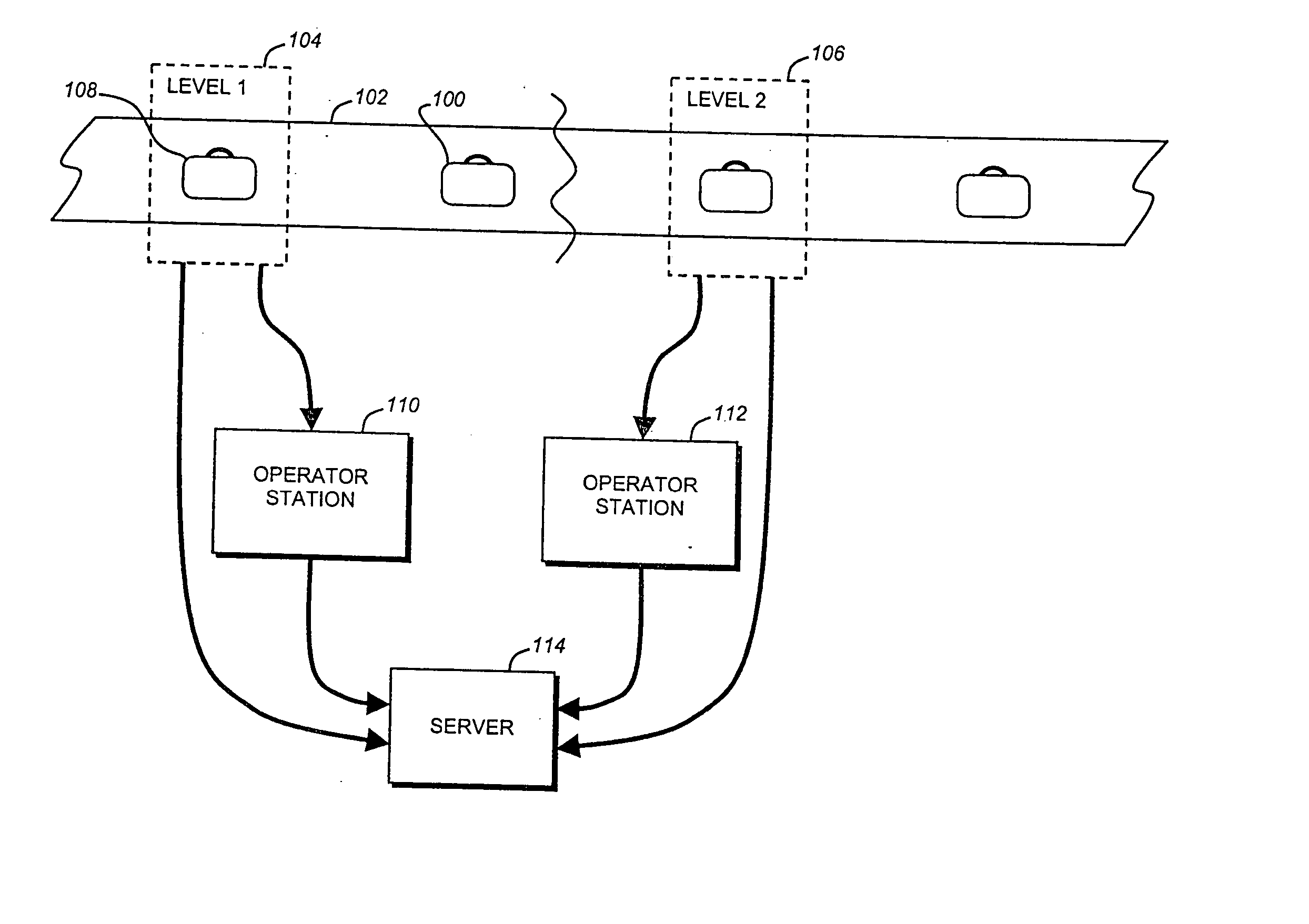
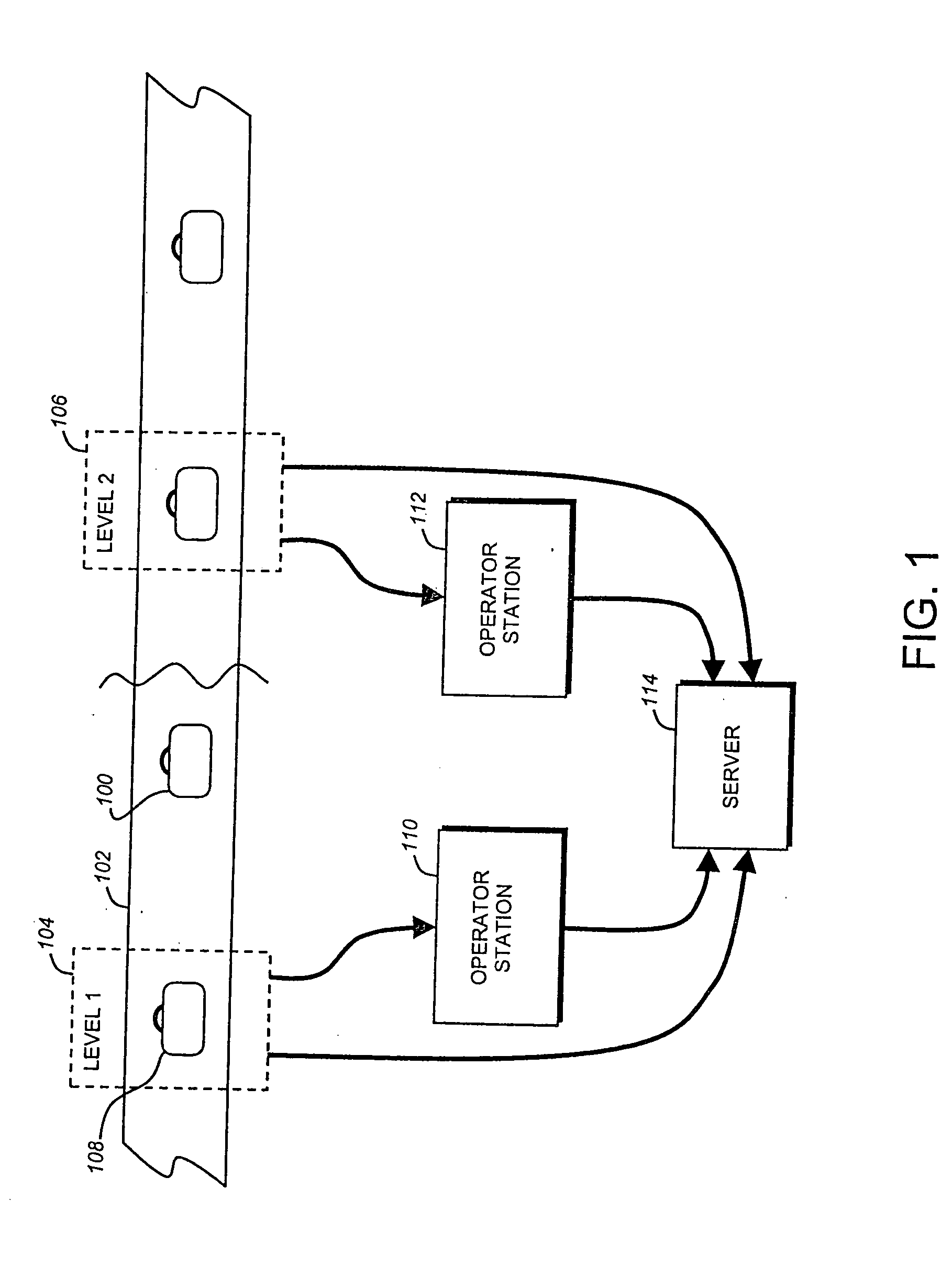
Remote baggage screening system, software and method
A method of advance baggage screening includes steps of transmitting a threat file corresponding to an item under inspection to a processing center, analyzing the threat file according to a detection algorithm at the processing center to determine a screening result for the item under inspection, and transmitting the screening result to a remotely located operator interface for access by an operator.
Owner:L3 COMMUNICATIONS SECURITY & DETECTION SYSTEMS CORPORATION
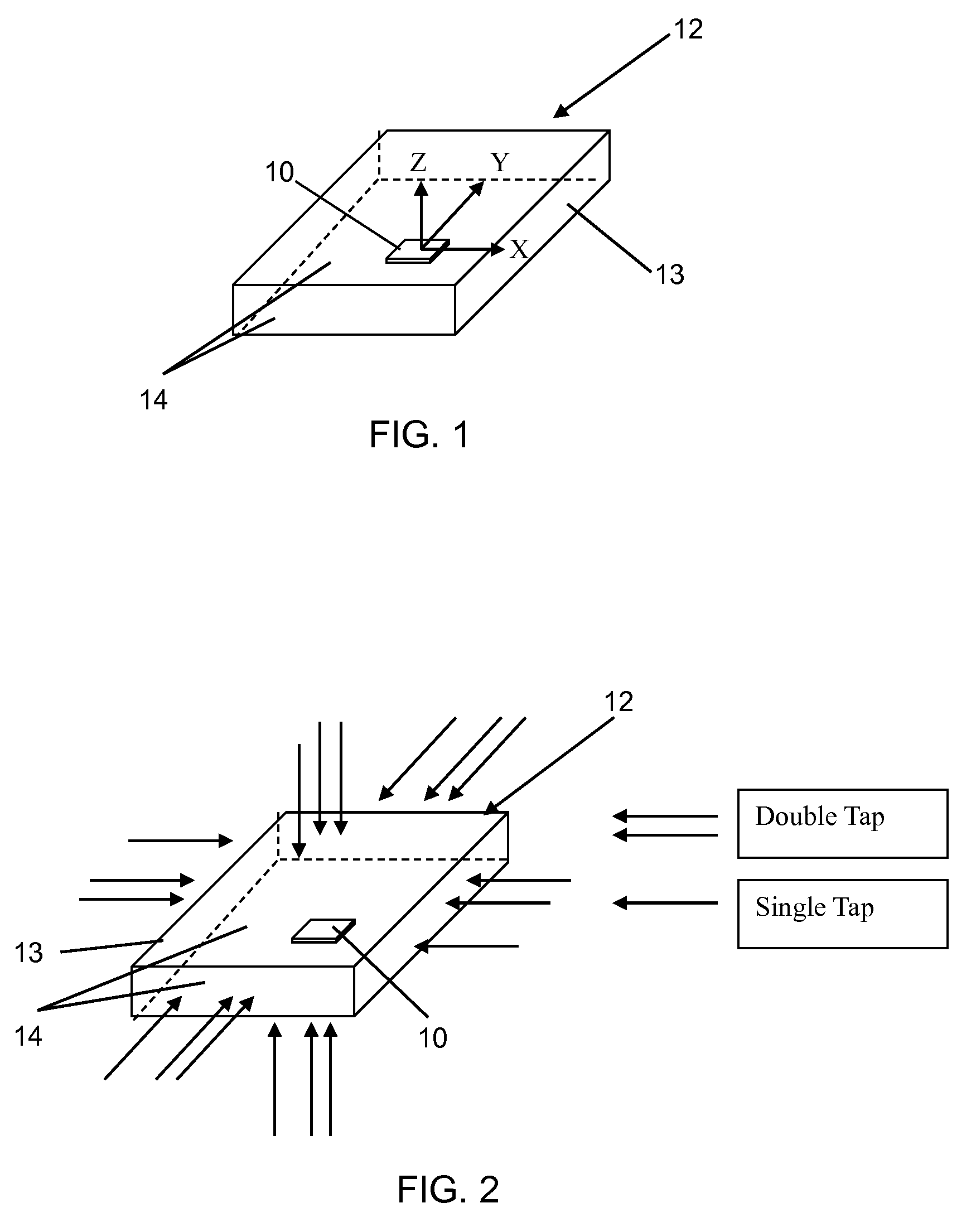
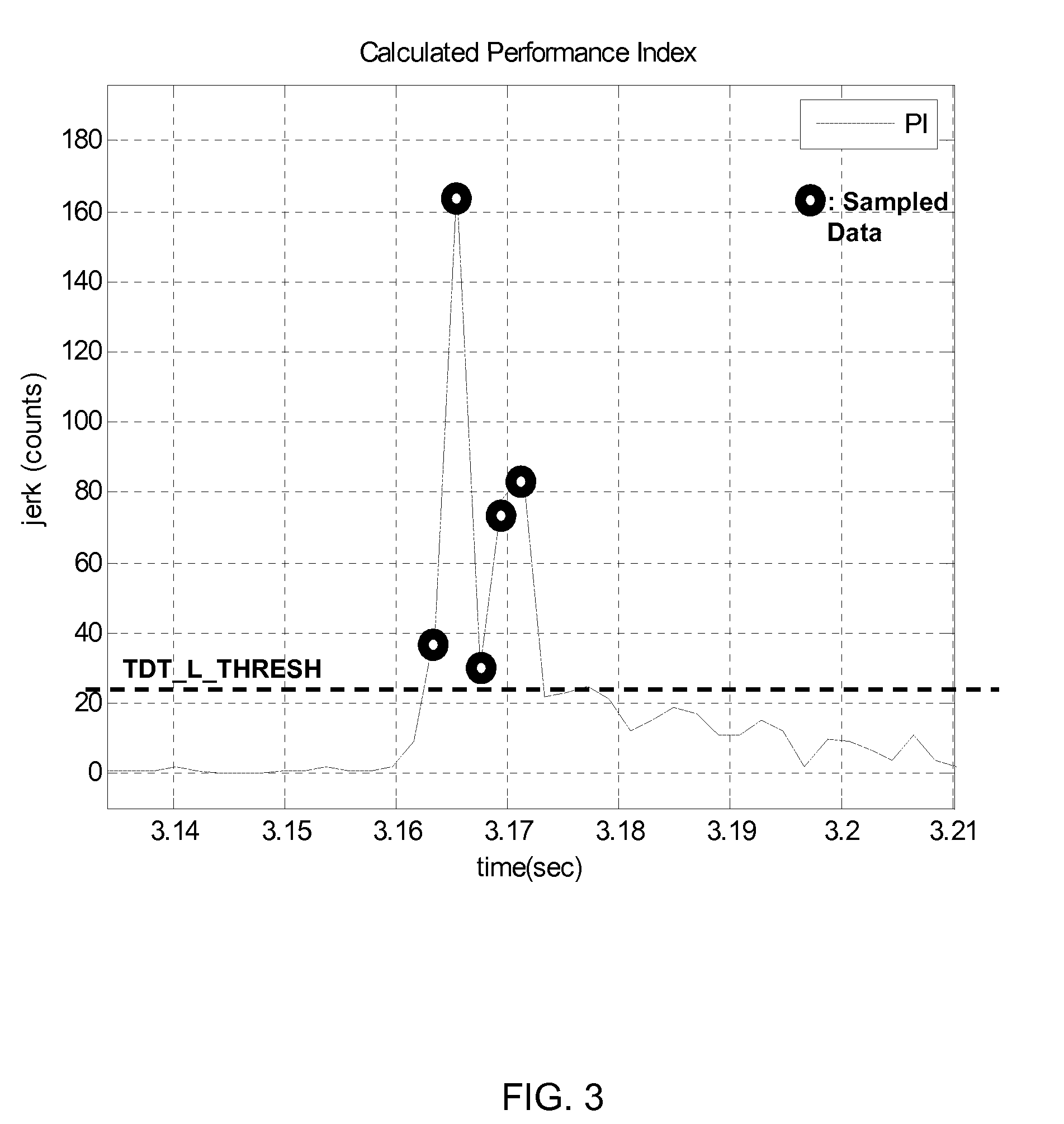
Directional tap detection algorithm using an accelerometer
ActiveUS20100256947A1Increase the number ofForce measurementAcceleration measurementTriaxial accelerometerPerformance index
A directional tap detection algorithm and a single tri-axis accelerometer (10) are employed to extend the number of unique button less input commands available for a small mobile electronic device (12) such as a cell phone or a MP3 player. The algorithm analyzes acceleration data from the tri-axis accelerometer (10) to detect the direction and number of taps imparted to any of the six sides (14) of a housing (13) of the device (12), yielding 12 unique inputs. The algorithm employs a parameter referred to as the performance index (PI) to identify tap induced movements. The PI is determined by calculating the time derivative of each acceleration signal for each axis and then calculating the sum of the absolute values of the calculated acceleration derivatives. A tap is determined to have occurred if the sum exceeds a threshold value for a predetermined amount of time. If a second tap is detected within a predetermined time after the first tap, then a double tap is determined to have occurred.
Owner:KIONIX CORP
Method for detecting activity information of user and electronic device thereof
InactiveUS20170046503A1Physical therapies and activitiesData processing applicationsRecognition algorithmAnalysis of algorithms
An electronic device is provided. The electronic device includes a communication module, a memory configured to store multiple recognition algorithms for analyzing user activities, and a processor configured to acquire activity schedule information related to a user activity; select at least one recognition algorithm among the multiple recognition algorithms, at least based on the acquired activity schedule information; and analyze activity information related to the user activity, using the at least one recognition algorithm, thereby providing activity guide information related to the user activity.
Owner:SAMSUNG ELECTRONICS CO LTD
Image processing system for predicting ovulation
InactiveUS6960170B2Stimulates saliva productionAnalysis using chemical indicatorsSurgerySaliva sampleBristle
An image processing system for predicting ovulation using a test channel for collecting saliva sample and a miniature camera for capturing the image of the saliva at dried state for analyzing the crystalline patterns for ovulation prediction. A rotary bristle element is attached to the drive head and a notch-like test channel traverses the width of the drive head. A conductivity sensor is mounted on a wall of the test channel for detecting filling and drying of the saliva sample. An algorithm in the microprocessor analyzes the image of the dried saliva and calculates the characteristic line length of line segments of connected saliva dots. A ferning index is also defined and calculated based on the percentage of area coverage of line segments which are exceeding the threshold line length. Trend curves are established based on the daily saliva analysis in a woman's menstrual cycle for predicting days from the ovulation.
Owner:KUO YOUTI
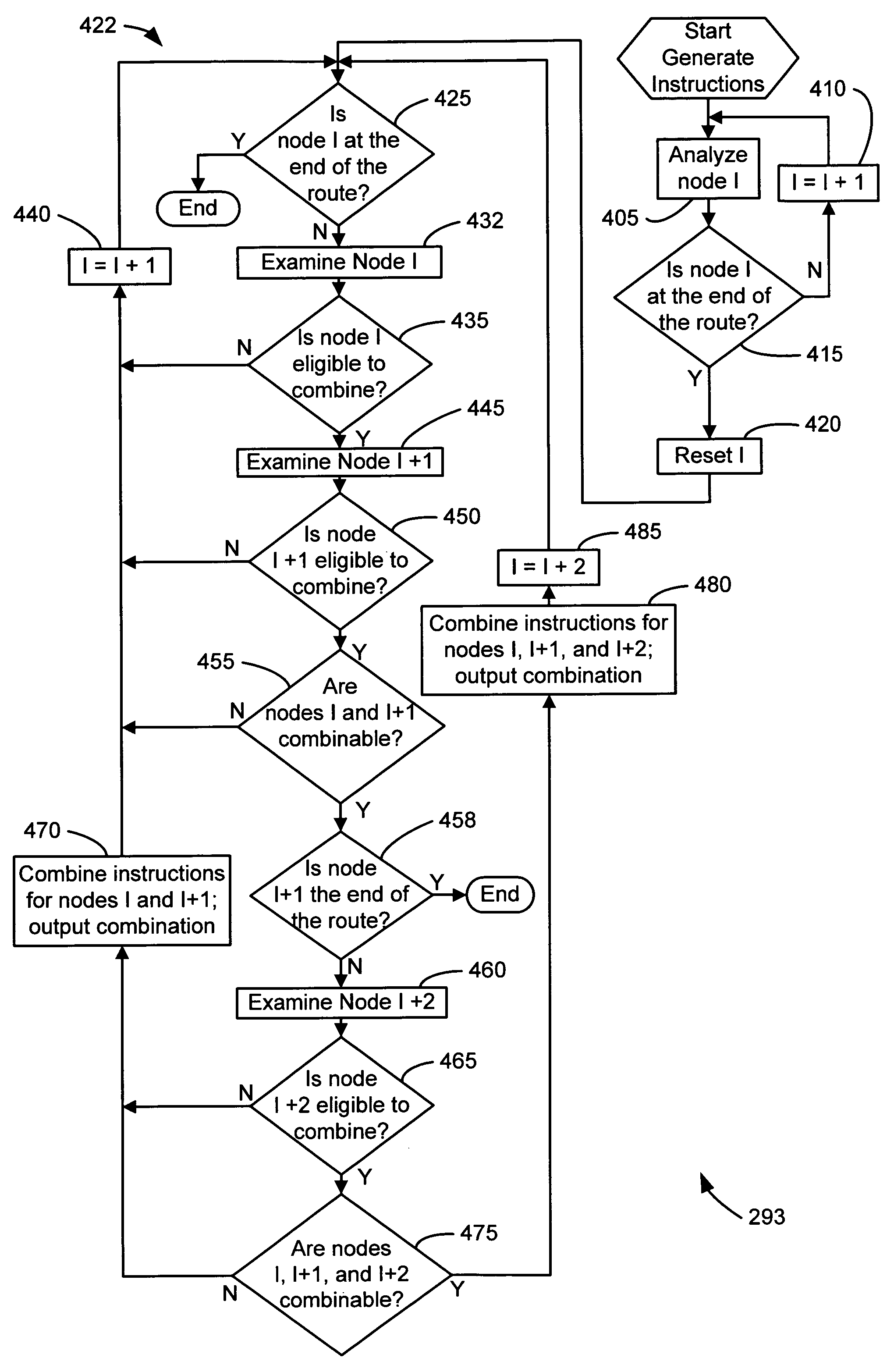
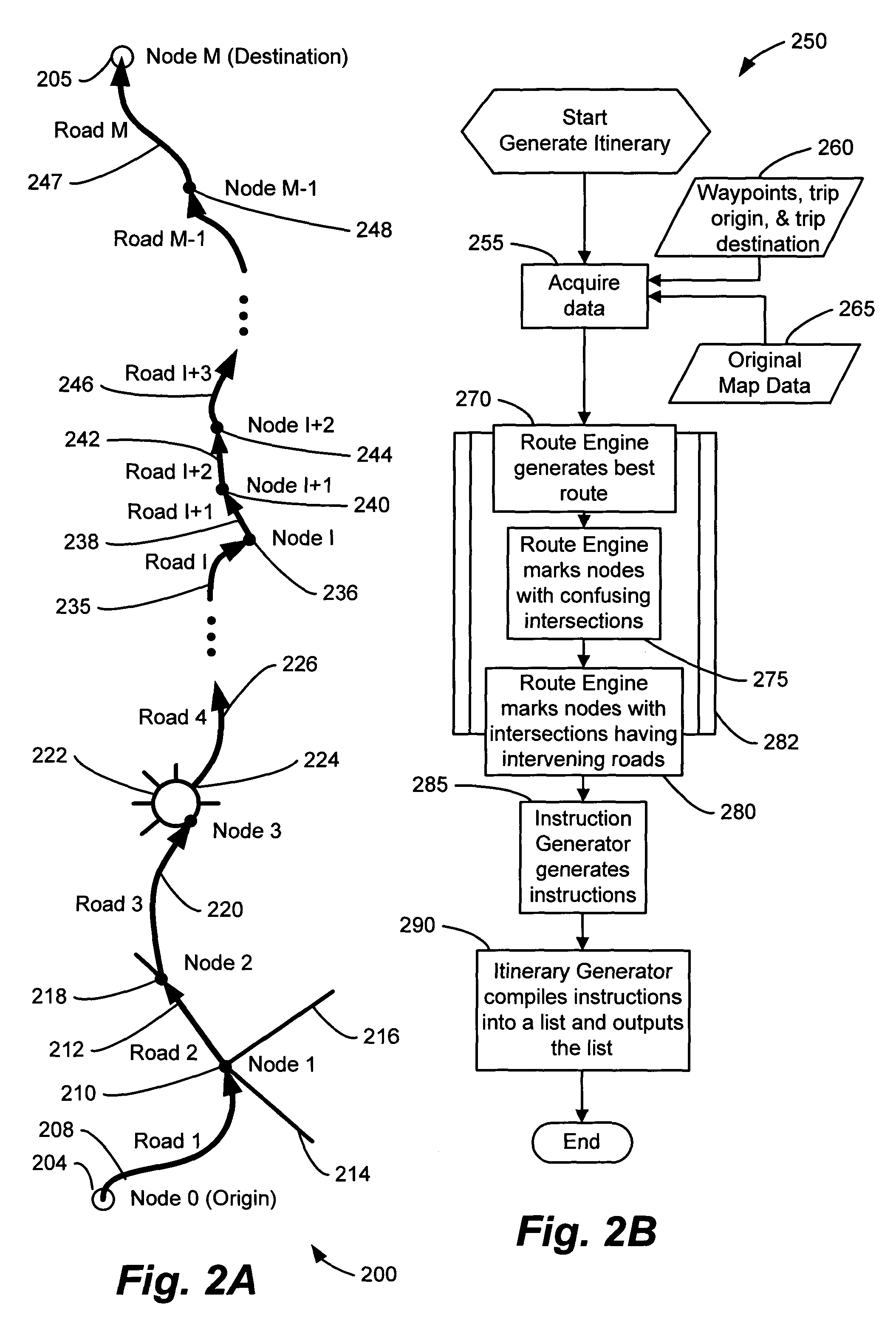
Method and system for generating driving directions
ActiveUS7054745B1Effective guidanceInstruments for road network navigationRoad vehicles traffic controlComputer-based instructionDriver/operator
A method and system for generating driving directions composes computer-based instructions that emulate a human driving perspective. Language-based instructions guide a driver along a route that encompasses a sequence of roads and intersections. An algorithm applies rules based on human perception to route components. The algorithm diagnoses road name changes so that instructions are clear and concise. The algorithm analyzes road and intersection geometry at confusing areas, such as road forks, roundabouts, ferry crossings, cloverleaf interchanges, and ramps, to generate instructions that conform to a driver's natural perspective. The algorithm analyzes the configuration of an intersection with respect to a driver's field of view to compose a clear and concise instruction. When appropriate, the algorithm produces compound instructions for adjacent intersections.
Owner:MICROSOFT TECH LICENSING LLC
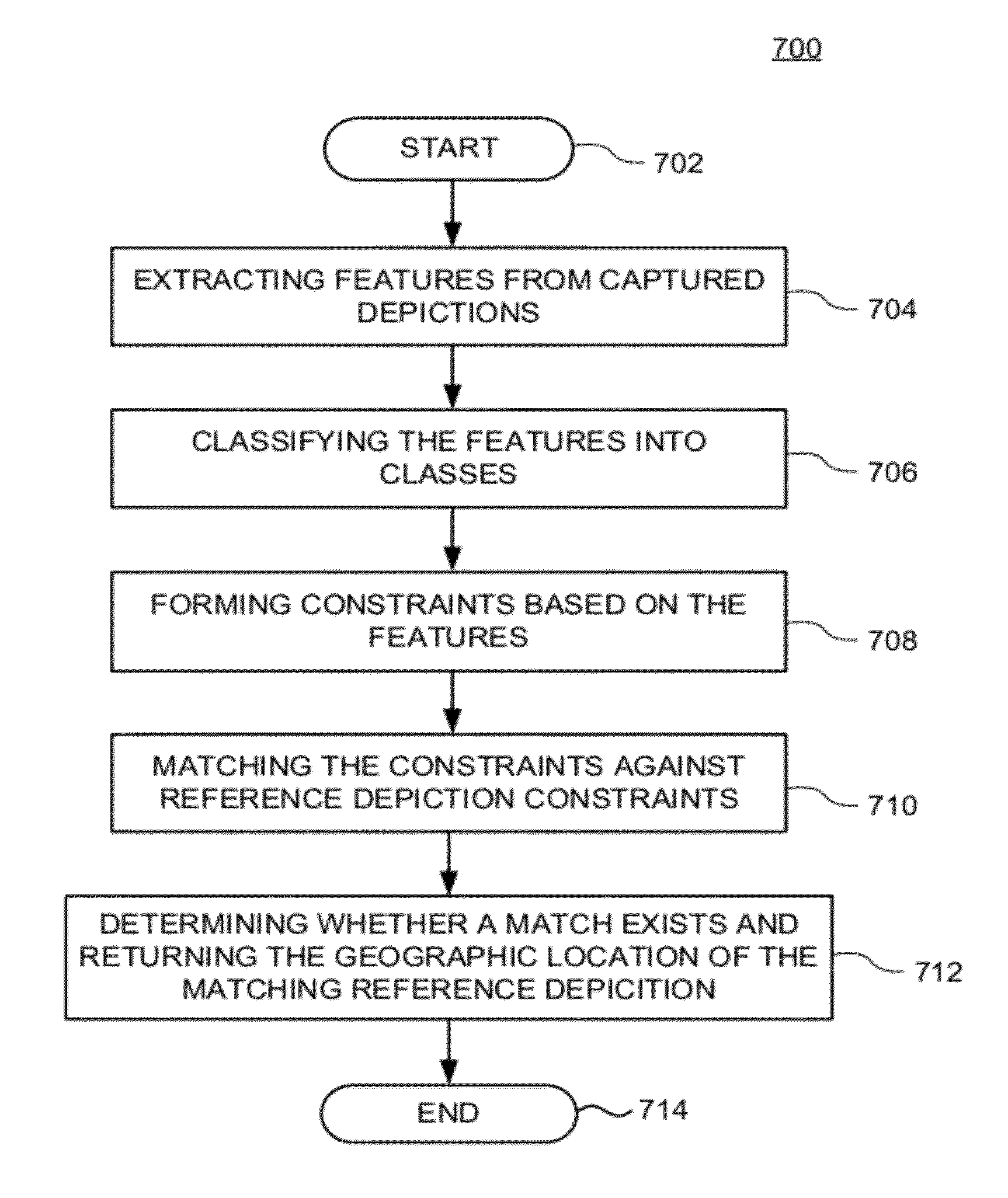
Method and apparatus for inferring the geographic location of captured scene depictions
Owner:SRI INTERNATIONAL
Image capture apparatus and image capture method
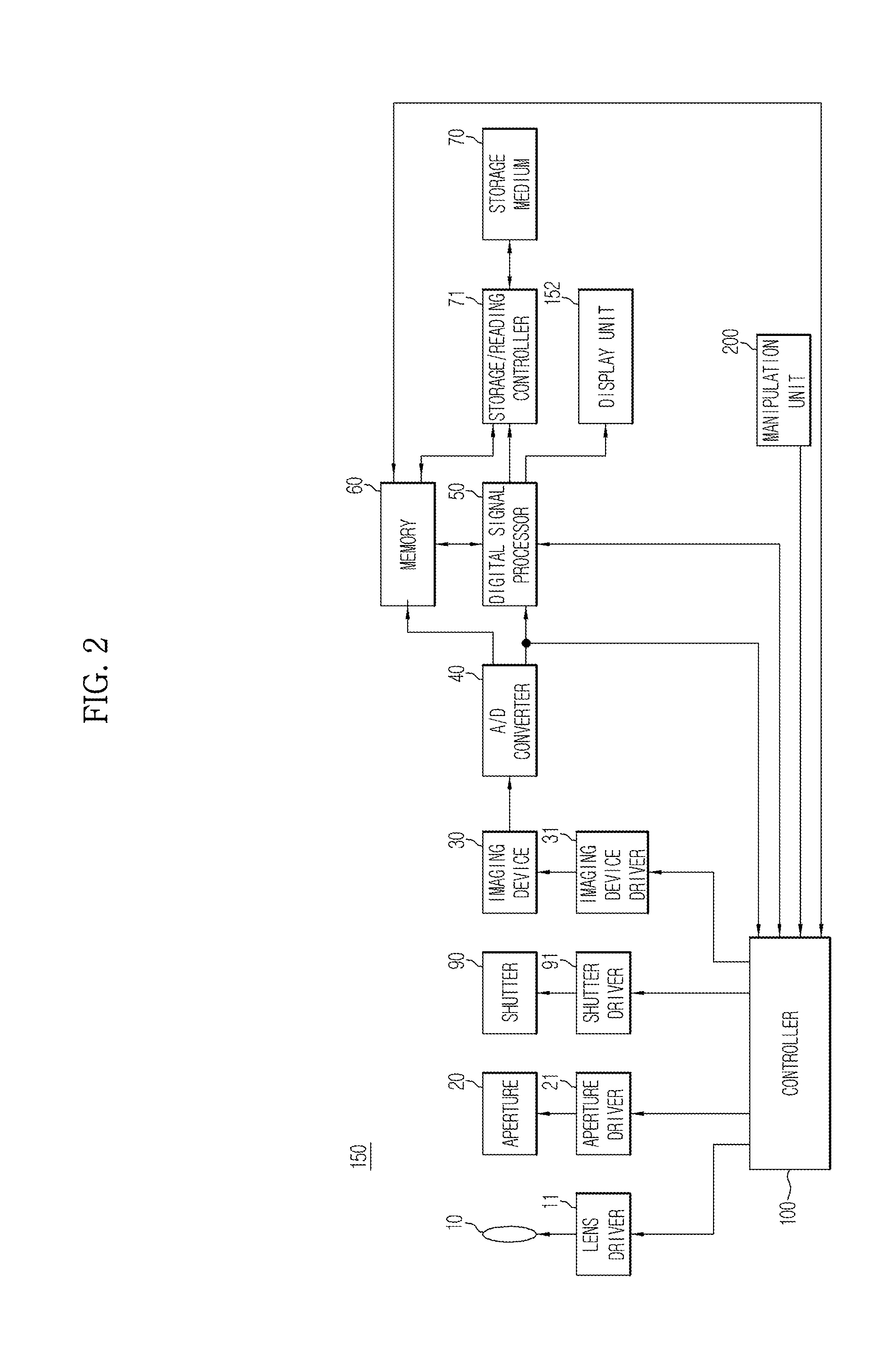
InactiveUS20140043517A1Television system detailsColor television detailsImaging processingComputer graphics (images)
An image capture apparatus automatically sets an image capture mode based on a subject or surrounding, and a user changes set values of image processing options of the set image capture mode as needed, thereby providing convenience and flexibility. The image capture apparatus includes a scene mode selection unit that analyzes a live view image according to a predetermined scene selection algorithm and selects a scene mode based on the analysis result, a display unit that displays a user interface to select an image processing option related to the selected scene mode and to change a set value of the selected image processing option, and a controller that receives the changed set value of the selected image processing option before an image is captured in the selected scene mode, applies the changed set value to the selected scene mode, and captures the live view image in the selected scene mode.
Owner:SAMSUNG ELECTRONICS CO LTD
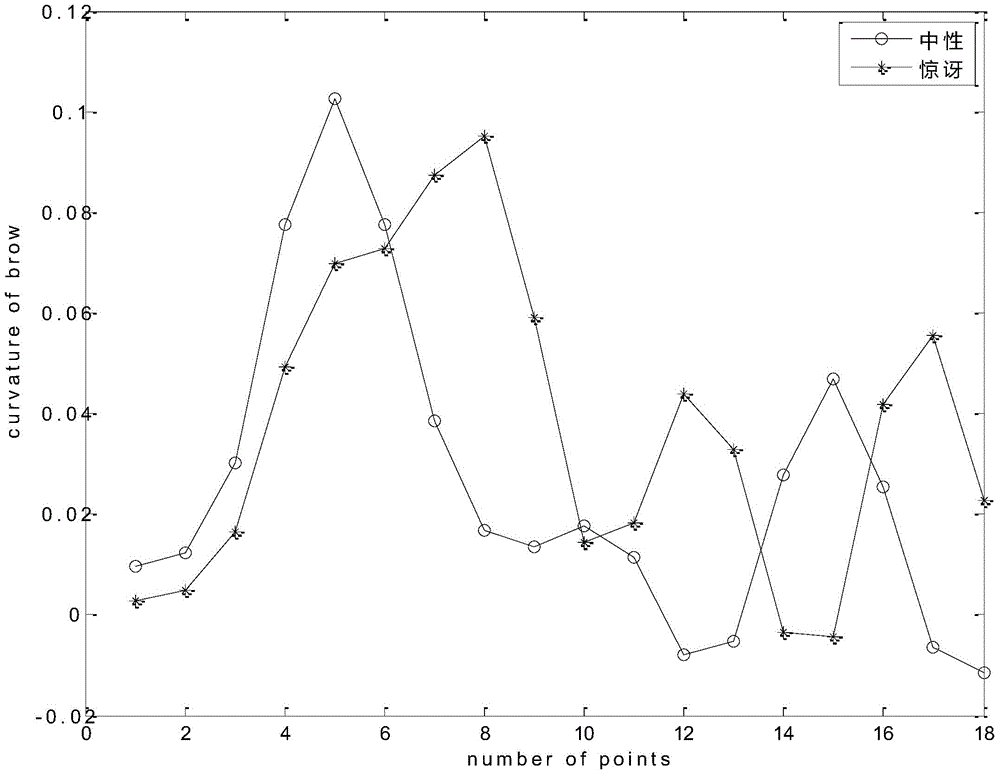
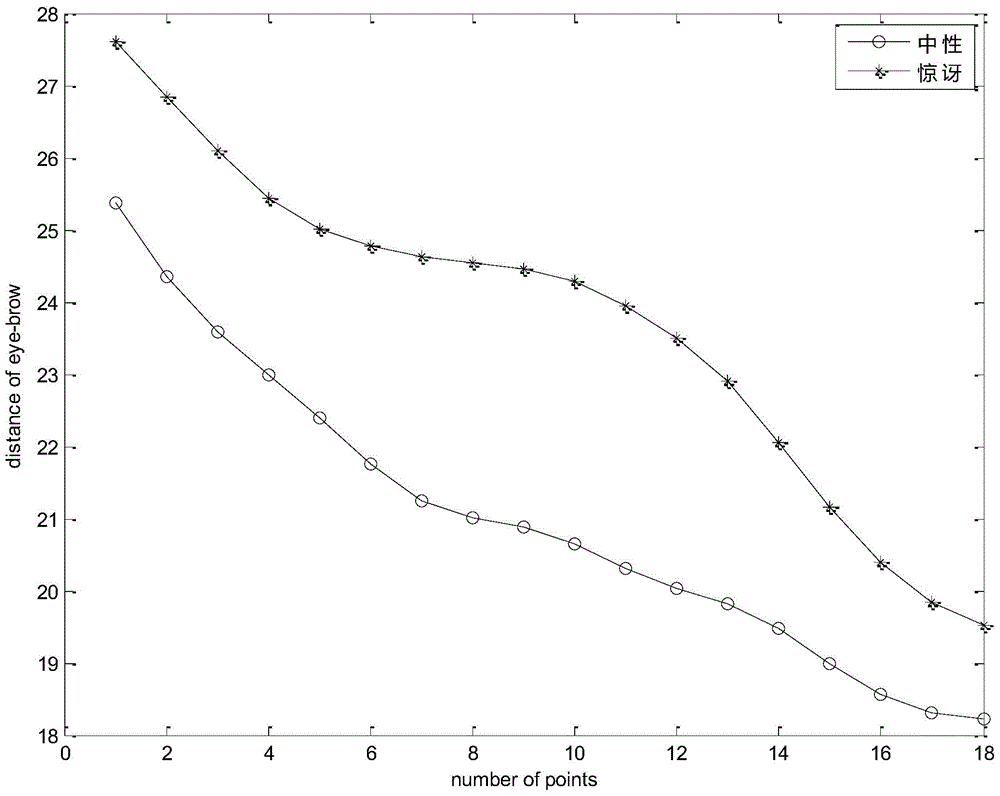
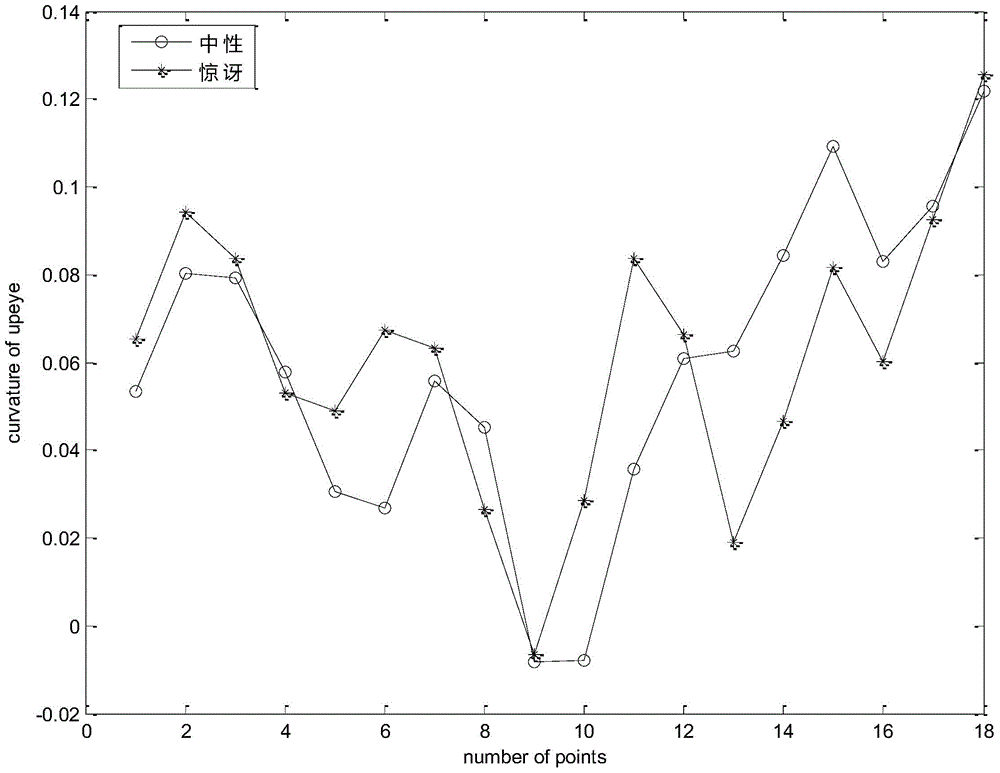
Active-shape-model-algorithm-based method for analyzing face expression
InactiveCN104951743ARealize expression recognitionVerify validityCharacter and pattern recognitionPattern recognitionNose
The invention relates to an active-shape-model-algorithm-based method for analyzing a face expression. The method comprises: a face expression database is stored or selected and parts of or all face expressions in the face expression database are selected as training images; on the basis of the active shape model algorithm, feature point localization is carried out on the training images, wherein the feature points are ones localized based on the eyebrows, eyes, noses, and mouths of the training images and form contour data of the eyebrows, eyes, noses, and mouths; data training is carried out to obtain numerical constraint conditions of all expressions; and according to the numerical constraint conditions of all expressions, a mathematical model of the face expressions is established, and then face identification is carried out based on the mathematical model.
Owner:SUZHOU UNIV
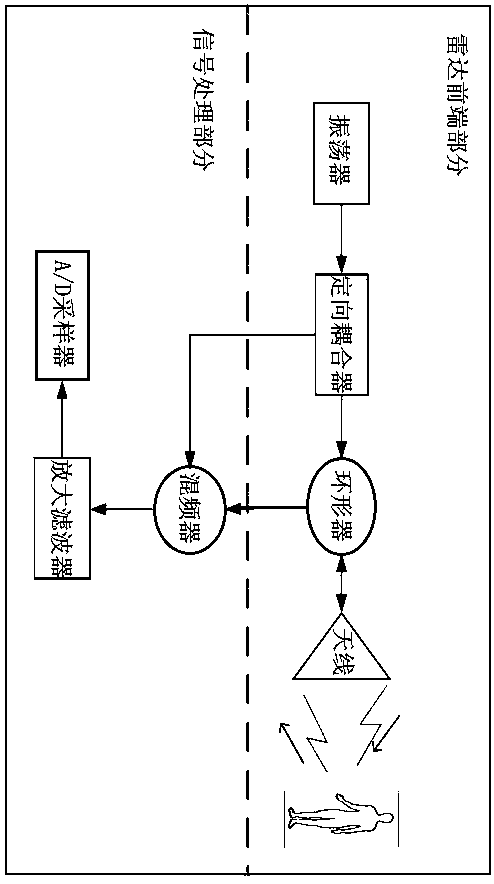
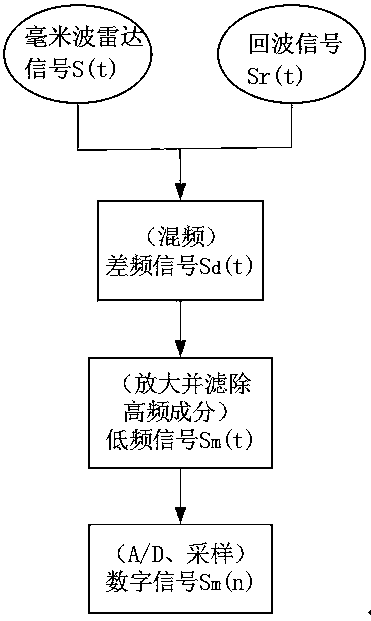
In-vehicle living body detection system and method based on millimeter-wave radar
InactiveCN110058225APrivacy protectionImprove featuresPedestrian/occupant safety arrangementAutomatic initiationsAnomaly detectionIn vehicle
The invention relates to the field of in-vehicle living body detection technologies and particularly discloses an in-vehicle living body detection system based on a millimeter-wave radar. The system comprises a front-end perception module, an algorithm analysis module and a control execution module, wherein the front-end perception module is connected with the algorithm analysis module and is usedfor transmitting a millimeter-wave radar signal, acquiring an echo signal reflected back by a target and preprocessing the echo signal; the algorithm analysis module is connected with the control execution module and is used for acquiring human micro-motion frequency parameters according to the preprocessed echo signal and obtaining a result of whether a living body or a living body sign anomalyexists in a vehicle or not through the human micro-motion frequency parameters; and the control execution module is used for controlling the vehicle to do a corresponding action according to the result obtained by the algorithm analysis module. Through the system, living body detection in a vehicle flameout state and detection of the in-vehicle living body sign anomaly during normal travel are realized, and vehicle safety is enhanced on another dimension.
Owner:HUIZHOU DESAY SV INTELLIGENT TRANSPORTATION TECH INST CO LTD
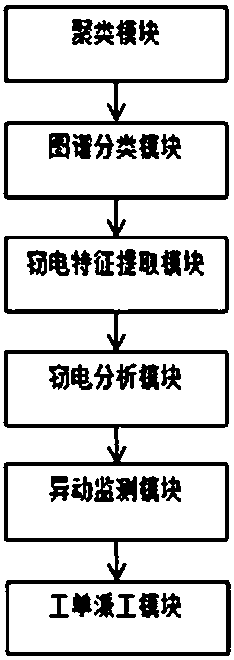
Power consumer electricity stealing behavior analysis method based on big data and machine learning
PendingCN109753989AImplement big data applicationsData processing applicationsCharacter and pattern recognitionData setUtilization behavior
The invention discloses a power consumer electricity stealing behavior analysis method based on big data and machine learning. The method comprises the following steps: 1, extracting a large amount ofuser electricity consumption data, and establishing an electricity consumption behavior pattern map by using a clustering algorithm; 2, analyzing a clustering result, and obtaining a normal electricity utilization behavior mode and a behavior mode to which an electricity stealing user belongs in combination with business experience and actual data; 3, on the basis of the behavior pattern to whichthe electricity larceny user belongs, extracting electricity consumption behavior characteristics of the user in the mode, and establishing an algorithm analysis model; 4, training and evaluating themodel by using the test data set and the training data set to obtain an optimal model; 5, monitoring the abnormal action of the user by combining line loss, metering abnormity and the like of the transformer area; and 6, tracking and monitoring the highly suspected electricity stealing user or generating an on-site patrol work order and a processing system. The invention discloses a correspondinganalysis processing system.
Owner:韩霞 +5
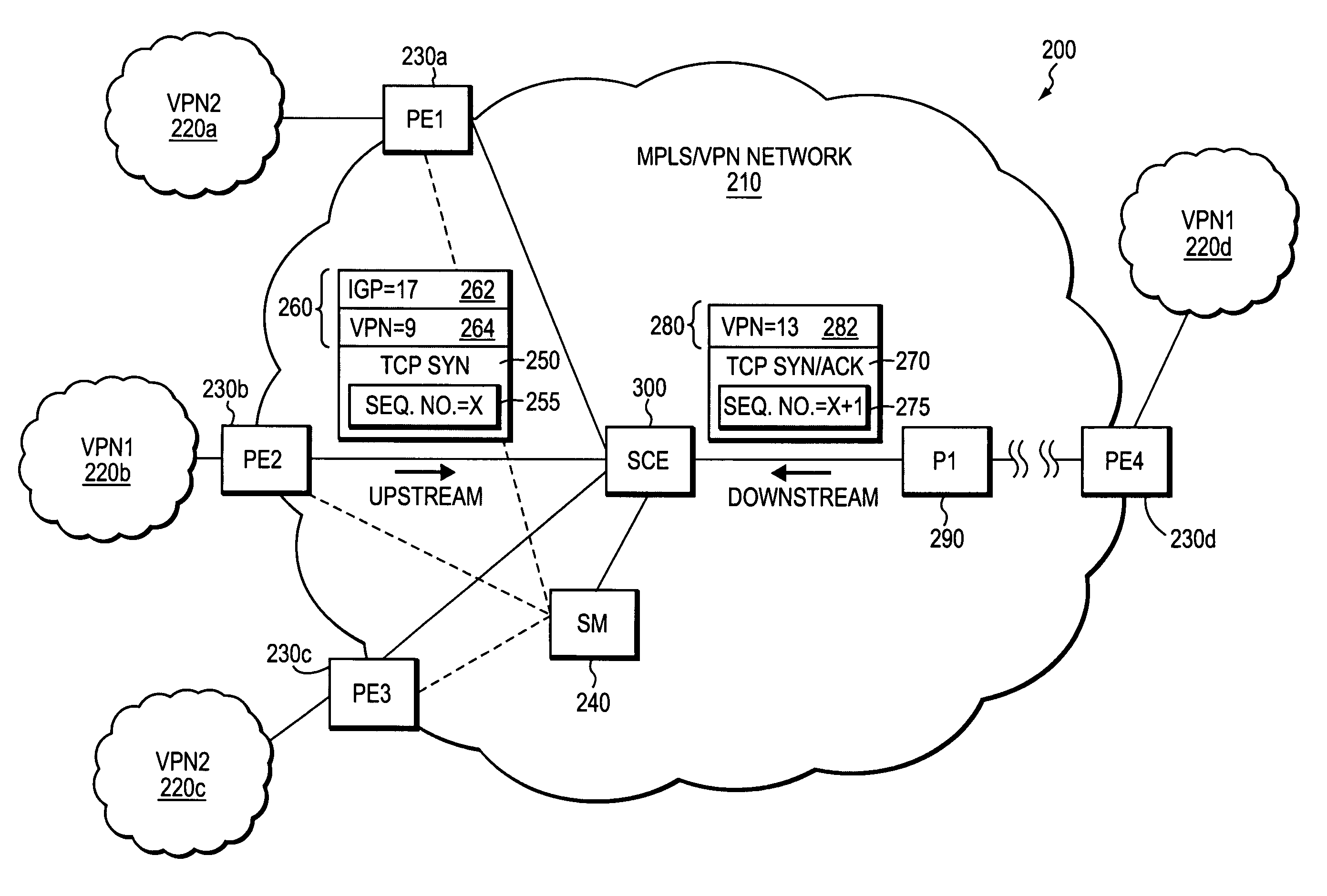
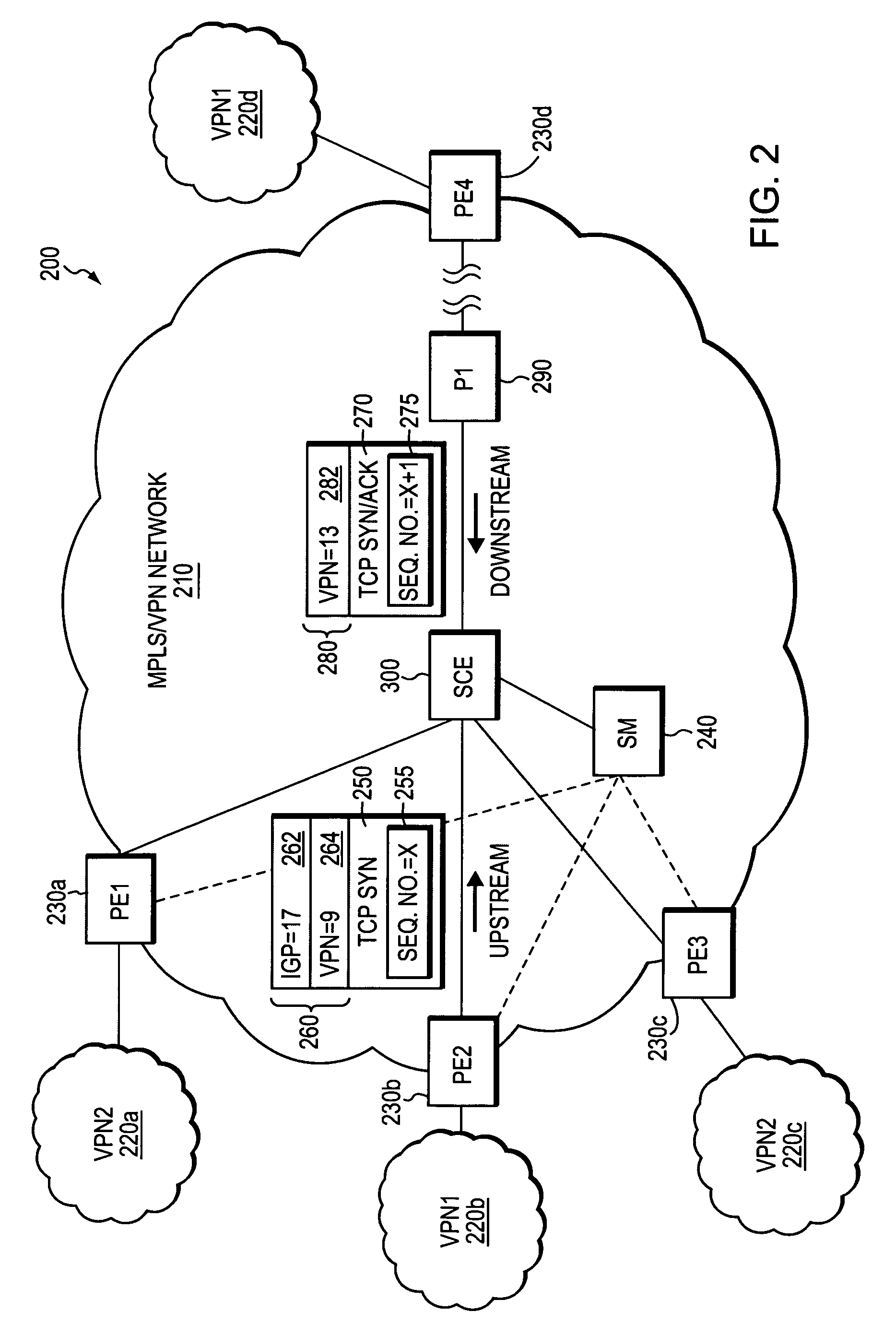
Method and apparatus for self-learning of VPNS from combination of unidirectional tunnels in MPLS/VPN networks
A technique is provided for implementing deep-packet inspection (DPI) services in a MPLS / VPN configured computer network. The technique employs a novel self-learning algorithm that analyzes data packets belonging to different unidirectional tunnels in the MPLS / VPN network and determines whether the analyzed data packets transport data in the same VPN. If so, the unidirectional tunnels containing the analyzed data packets are associated with a common layer-2 identification (L2ID) value. Unlike conventional flow-classification procedures, the inventive technique classifies a data packet by first associating the data packet with a L2ID value and then classifying the packet as belonging to a particular data flow based on a novel 6-tuple consisting of a conventional 5-tuple plus the packet's L2ID value. Because unidirectional tunnels corresponding to the same application data flow transport data packets having the same set of 6-tuple values, DPI services can apply application-level policies to classified data packets consistent with their 6-tuple flow classifications.
Owner:CISCO TECH INC
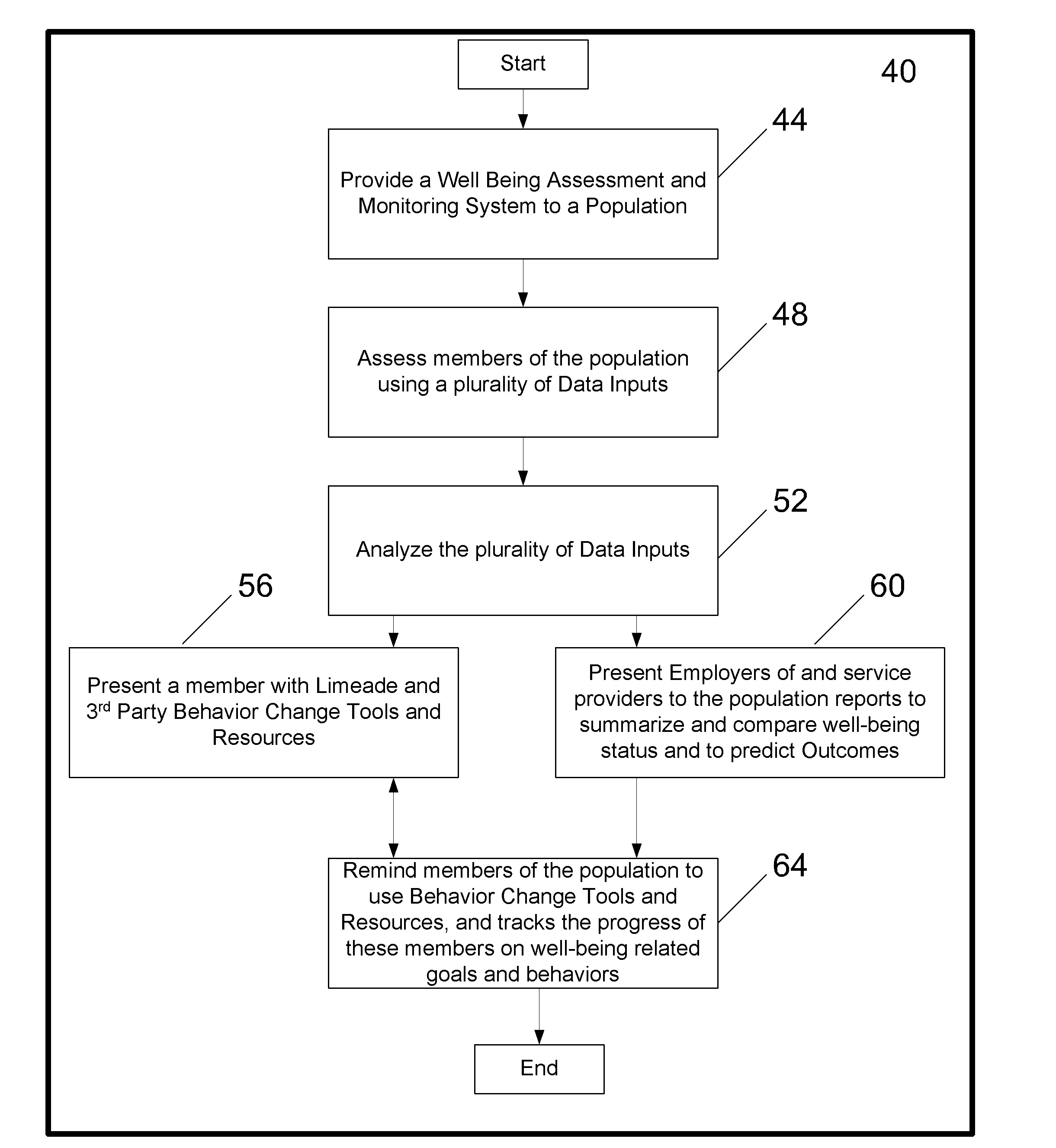
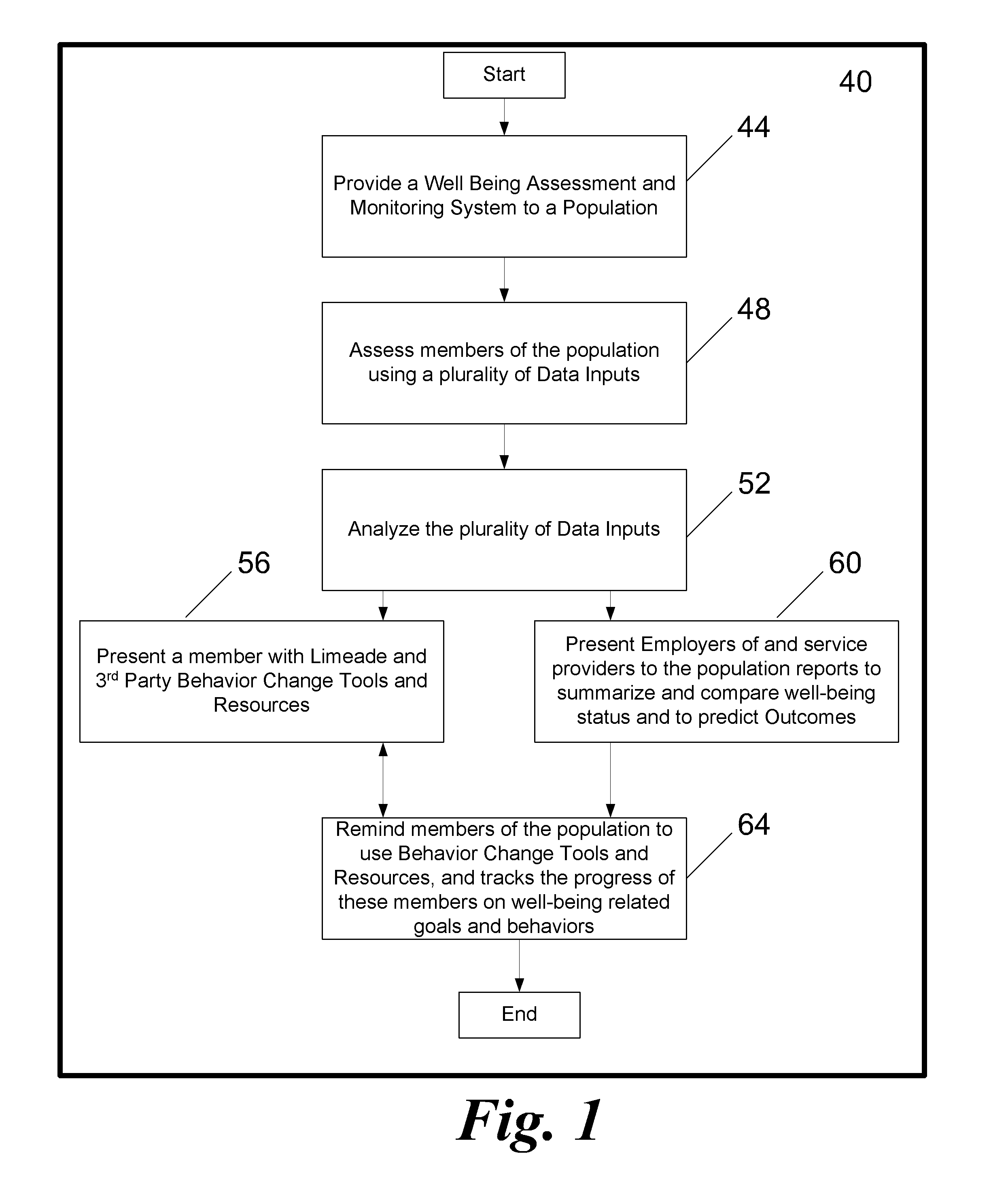
Systems and methods for a holistic well-being assessment
InactiveUS20090319347A1Epidemiological alert systemsComputer-assisted medical data acquisitionThird partyThe Internet
Systems and methods are described for an assessment tool built on a holistic well-being improvement model. The model consists of a series of assessments including, but not limited to a well-being improvement assessment, work productivity assessment, and a clinical health risk assessment. A member would complete these assessments through an internet site, on paper, on the phone, and / or on any other medium generally known in the art. After a member participates in the assessment, the assessment is analyzed based on a series of predefined algorithms. A member is then provided with system tools and access to third party behavior change tools and resources. Concurrently the data is compiled for the benefit of an employer and / or a provider in the form of an aggregate report in order to understand the status of the current population's well being and also providing the ability to predict future outcomes. The system further tracks the progress of a member on their well-being goals and behaviors.
Owner:LIMEADE
VMM-based intrusion detection system
InactiveUS8719936B2Memory loss protectionError detection/correctionPattern recognitionOperational system
An intrusion detection system collects architectural level events from a Virtual Machine Monitor where the collected events represent operation of a corresponding Virtual Machine. The events are consolidated into features that are compared with features from a known normal operating system. If an amount of any differences between the collected features and the normal features exceeds a threshold value, a compromised Virtual Machine may be indicated. The comparison thresholds are determined by training on normal and abnormal systems and analyzing the collected events with machine learning algorithms to arrive at a model of normal operation.
Owner:NORTHEASTERN UNIV
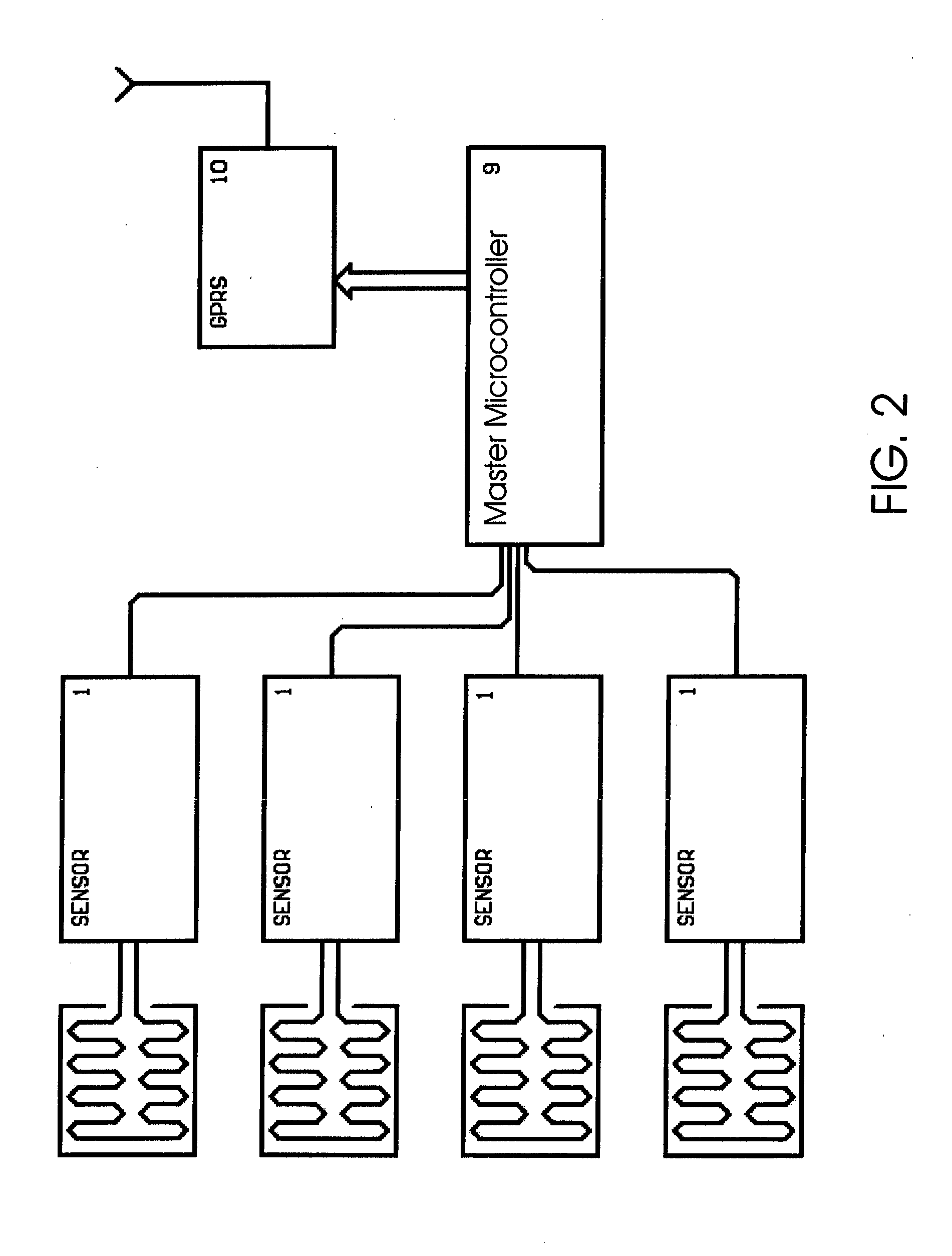
Method, device, sensor and algorythm for detection of devices stealing information from ATM devices
InactiveUS20150091547A1Complete banking machinesFrequency measurement arrangementMicrocontrollerEngineering
Method for detection of skimming devices comprising detecting electromagnetic emissions by sensors of the invention located inside of ATM. Electromagnetic emission is monitored in broad band of 10 kHz to 30 MHz and narrow band, and only one determined frequency is passed through filters in the narrow band, and sensors' output is analyzed and processed according to algorithm of the invention. Alarm signal is generated upon achieving pre-assigned threshold chosen so that discriminating between useful signal and interference is not obstructed. The method is implemented by device comprising sensors for detecting electromagnetic emissions, microcontroller for controlling the sensors, master microcontroller for processing of sensors' output, and notifying module for sending signals to control center. According to the invention sensor is provided for detecting electromagnetic emissions comprising receiving, regulating, filtering and converting parts.
Owner:VASILEV VASIL STEFANOV +1
Optimizing and dispatching method of energy consumption of flexible flow shop with associated adjustment time and sequence
InactiveCN104391488AHigh energy consumptionLow costEnergy industryProgramme total factory controlMathematical modelHeuristic
The invention discloses an optimizing and dispatching method of energy consumption of a flexible flow shop with associated adjustment and sequence. The method comprises the following steps: S1, searching on the dispatching problem of the flexible flow shop having adjustment time associated with sequence, wherein the adjustment time is defined into one associated with workpiece sequence and the other one associated with workpiece sequence and machines; S2, establishing the following mathematic models; S3, using the minimum overall energy consumption as a target and providing three heuristics algorithms with respect to a problem existing in the problems resolved with an NEH algorithm; S4, verifying the above three algorithms, providing two lower bounds of the problem and designing one simulation experiment based on a split block experiment; S5, analyzing factors, algorithms, lower bounds and CPU operational time according to the simulation results. According to the optimizing and dispatching method of energy consumption of the flexible flow shop with associated adjustment and sequence, the energy consumption is optimized and the cost is saved.
Owner:GUANGDONG UNIV OF TECH
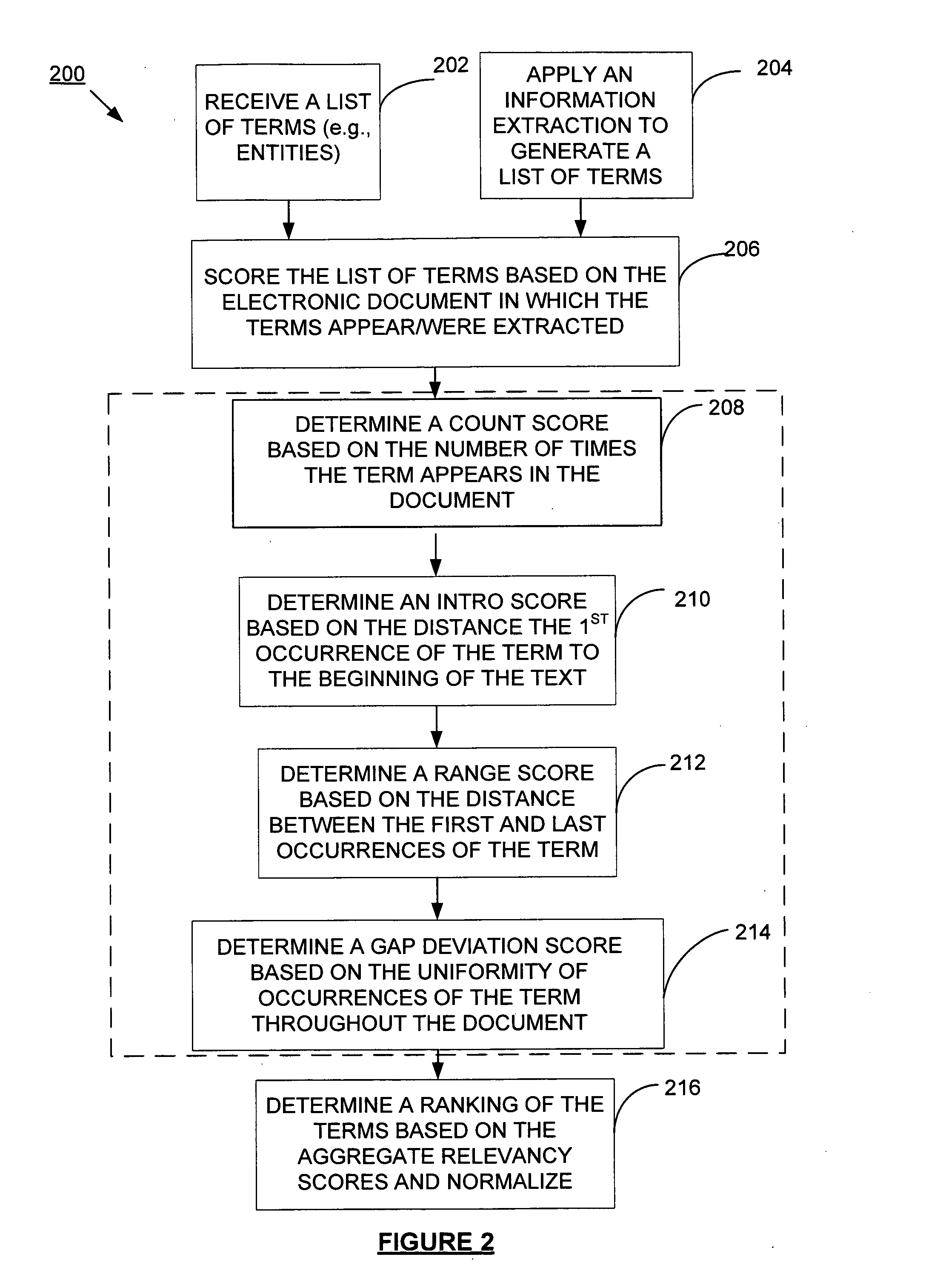
Method and system for determining relevance of terms in text documents
ActiveUS20110004606A1Digital data information retrievalDigital data processing detailsScoring algorithmSubject matter
The present invention provides a corpus-independent method for determining relevancy of terms to content of text appearing in a document by analyzing the document itself. Conventional information extraction, or other methods, may be applied to a document to generate a list of terms. The invention analyzes the document using relevancy scoring algorithms to determine a term relevancy score representing the term's relevance to the text contained in the document. The scores, including an aggregate score, may be normalized in the process. Based on relevancy scoring, terms are then ranked and further processed. In this manner relevancy is determined based on the subject document itself and by analyzing the occurrences and locations of the terms within the document. Additional techniques may be applied to relate the relevancy scores generated by the present invention to a corpus or collection of documents.
Owner:REFINITIV US ORG LLC
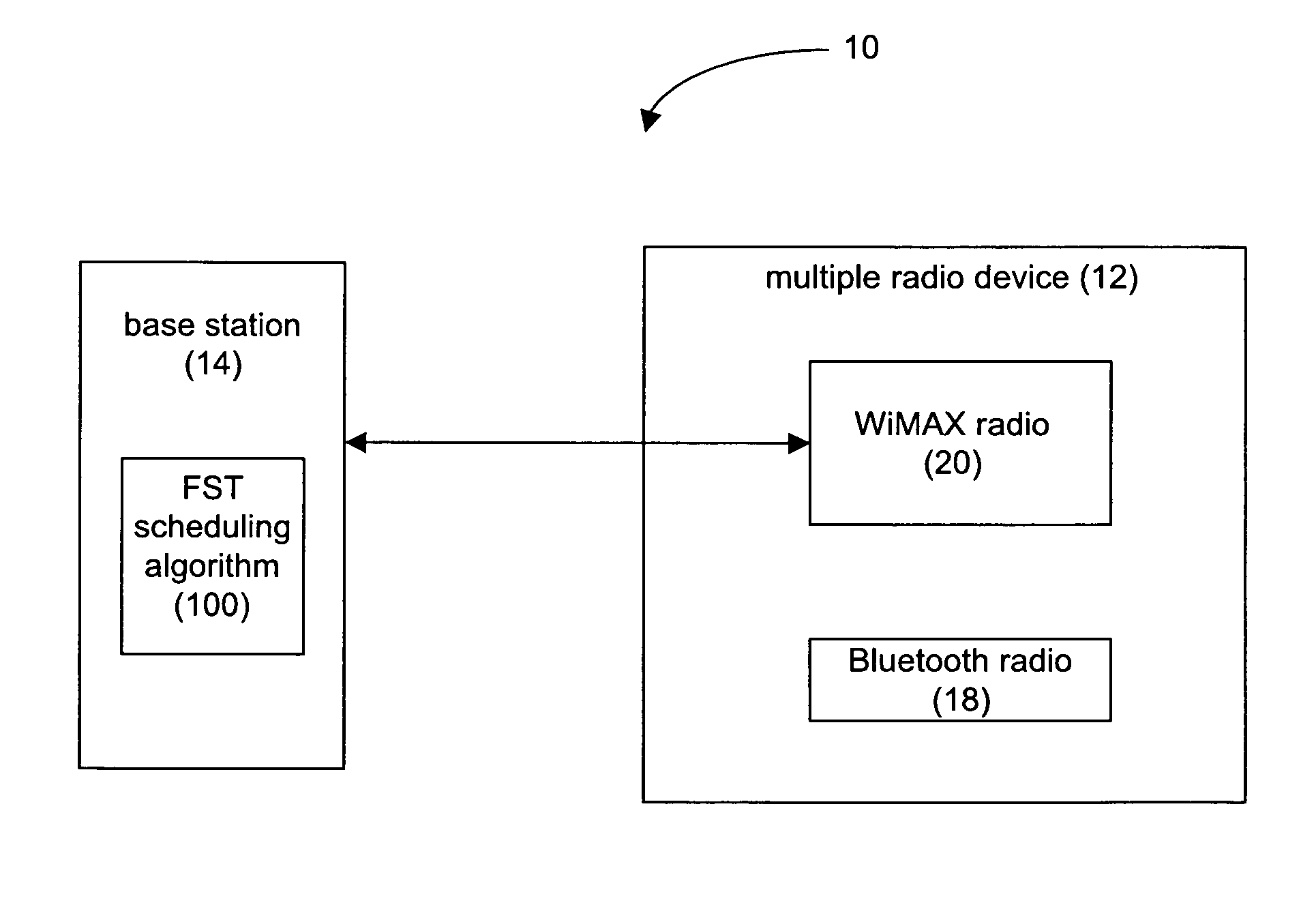
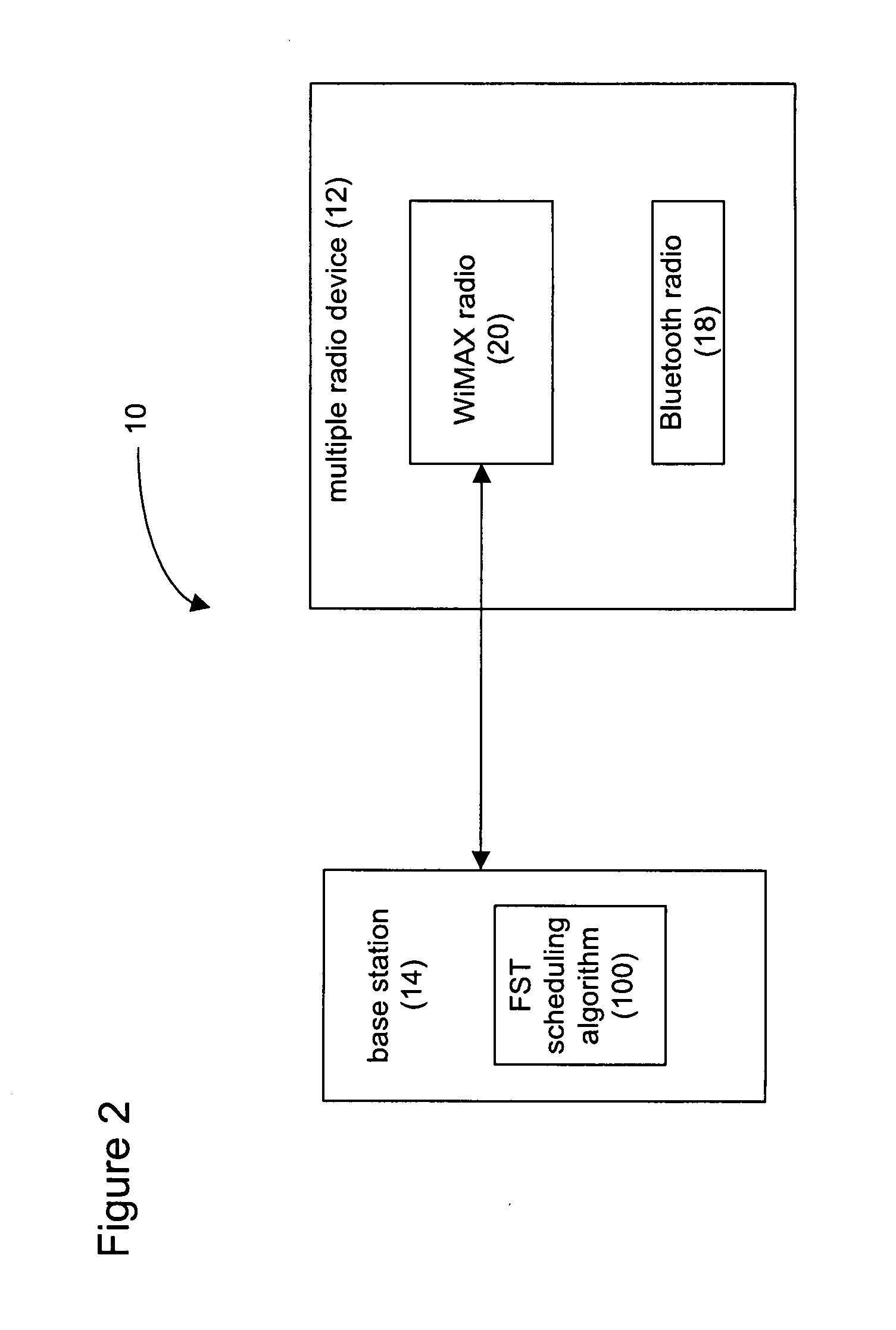
Flexible starting time scheduling algorithm for bitmap coexistence protection
A flexible start time (FST) scheduling algorithm operable at a base station is disclosed, to allocate resource in the time domain based on coexistence period bitmap (CBP) feedback gathered from multi-radio user terminals. The algorithm analyzes traffic load distribution in the wireless neighborhood and determines an optimum starting time of the CBP operation for the current user.
Owner:INTEL CORP
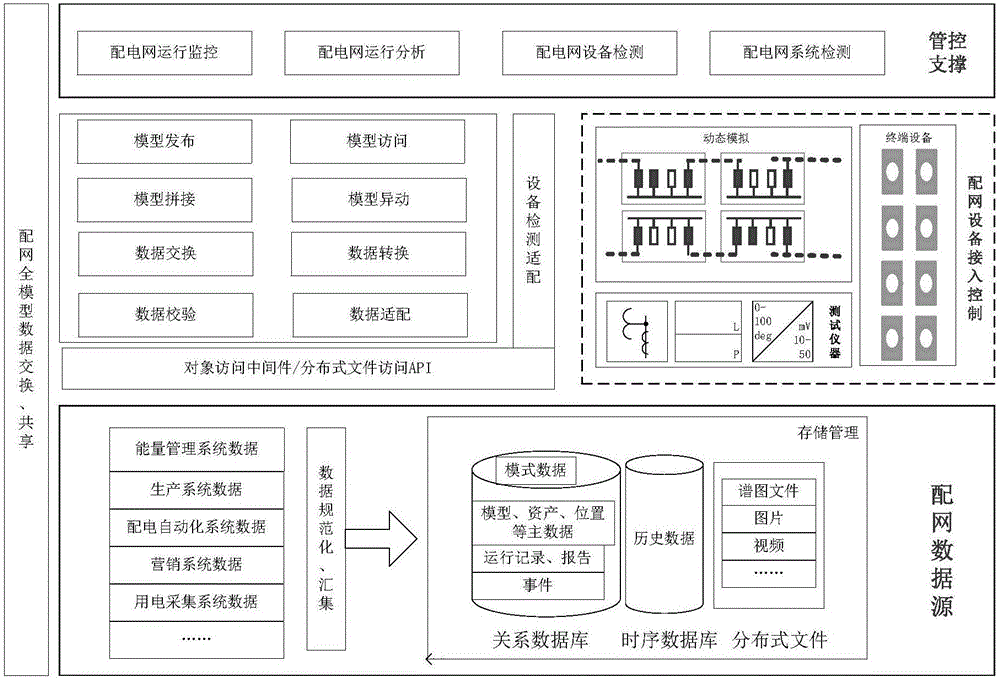
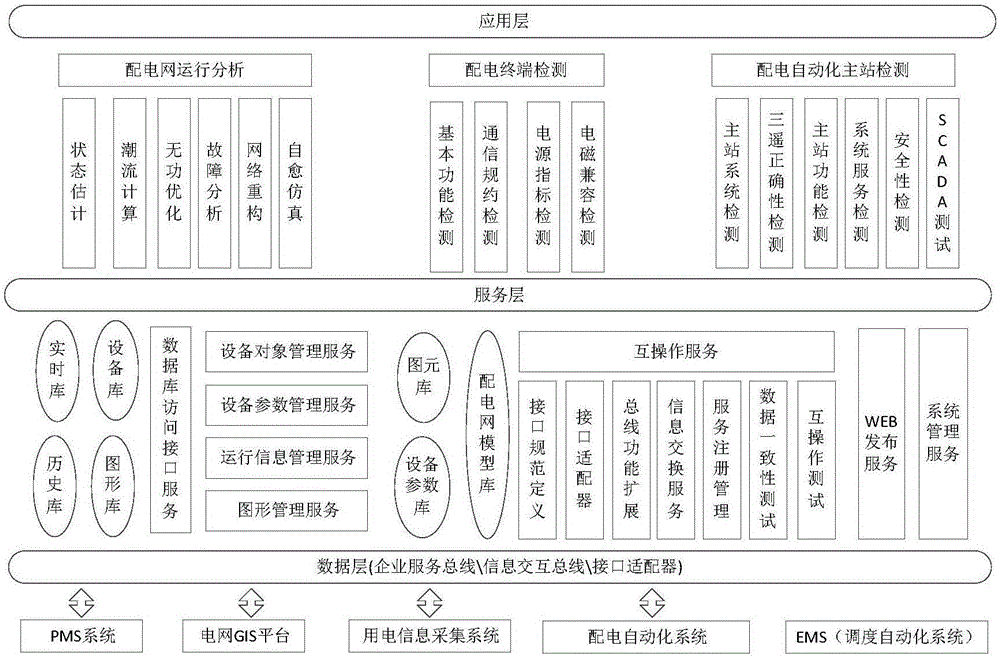
Integrated support system and method for management and control of power distribution network
The invention discloses an integrated support system and method for management and control of a power distribution network. A data layer comprises a data access processing unit for integrating and standardizing the collected data associated with the distribution network according to the common information model to form the pattern data, the historical data and the document data, and store respectively in the relational database, a sequential database and a distribution database. A service layer comprises a digital simulation model, a distribution terminal detection model and a distribution automation master station system test model called by an application layer, and the service layer realizes data interaction of all distribution models and assessing control of distribution equipment by equipment detection and matching and object accessing middleware / distributed file accessing middleware. The application layer comprises a distribution network operation analysis unit, a distribution network terminal detection unit and a distribution automation main station system detection unit, wherein the distribution network operation analysis unit calls a digital simulation model and uses a distribution network digital simulation algorithm to analyze the current network running states by combining with the distribution network related information in the data layer.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY +2
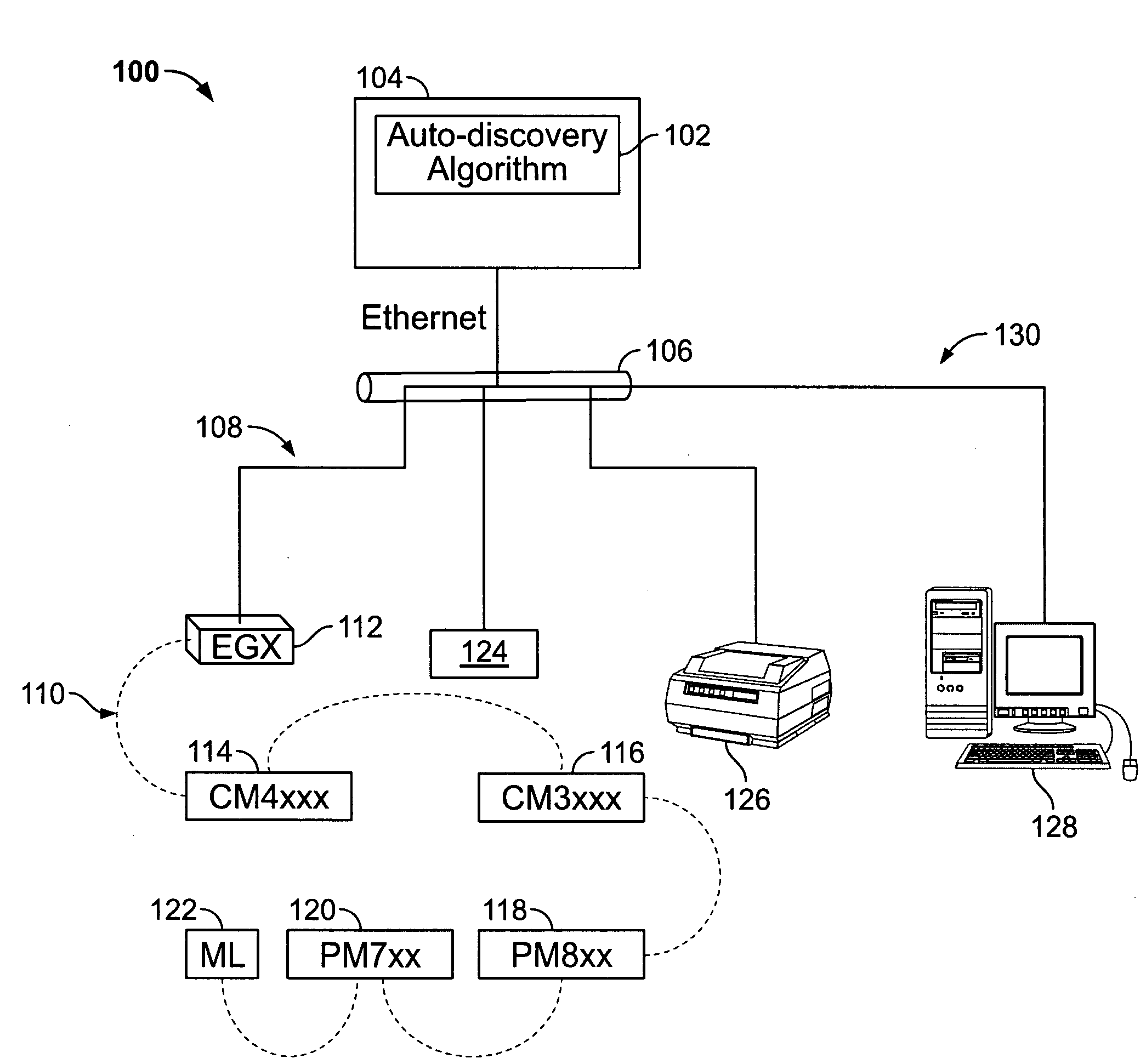
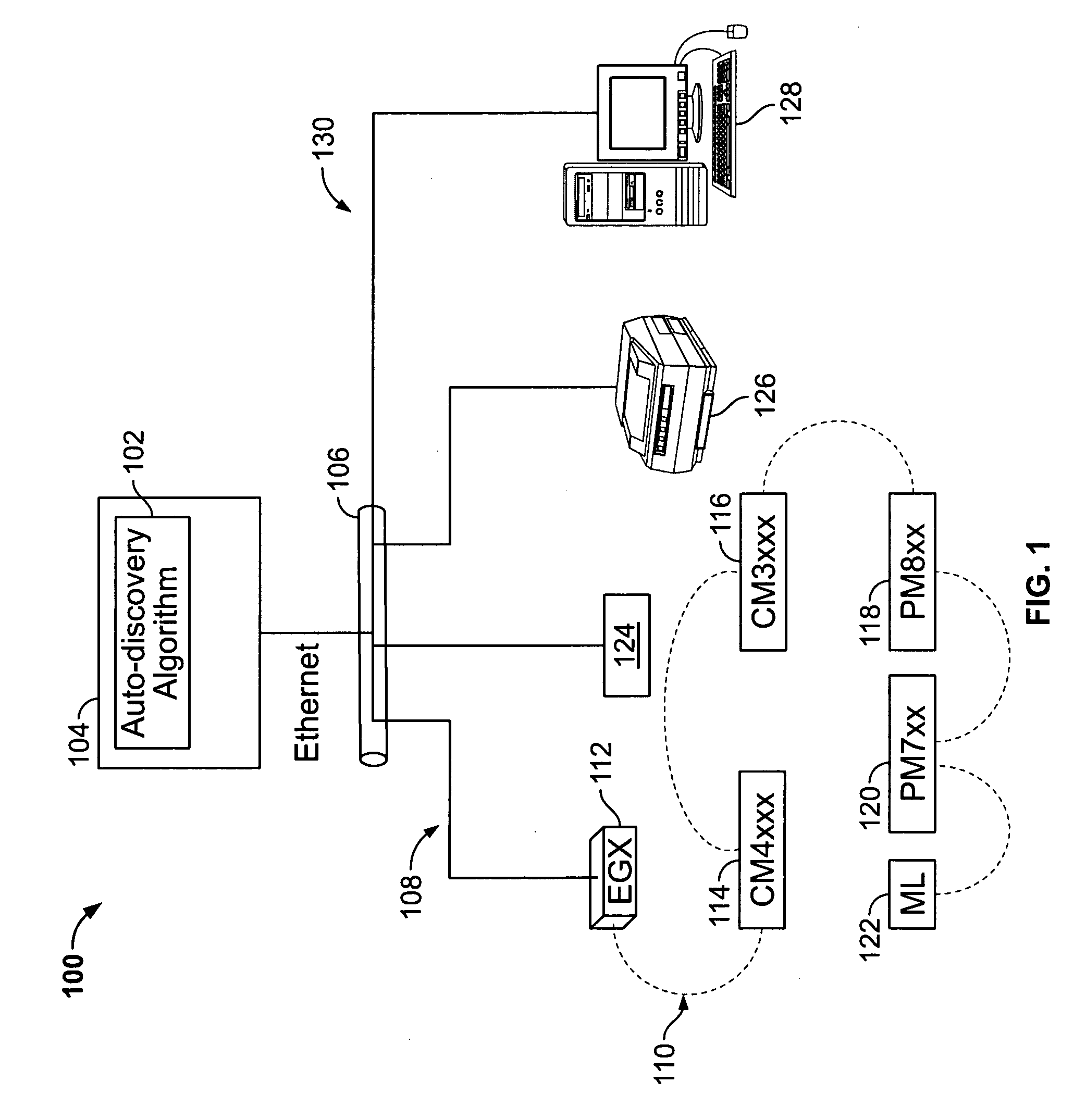
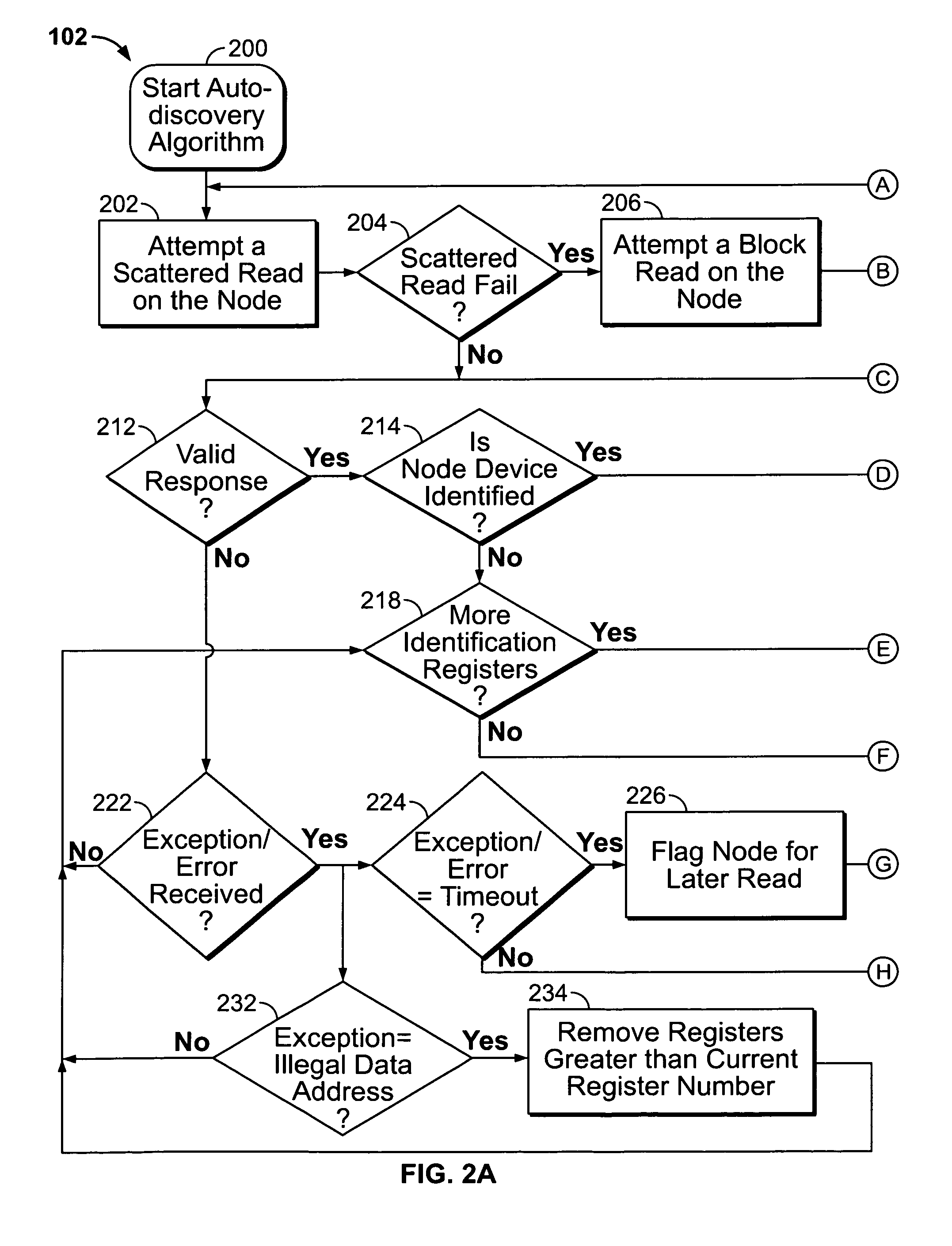
Automated discovery of devices in large utility monitoring systems
InactiveUS20090287803A1Increase opportunitiesReduce in quantityElectric devicesTariff metering apparatusProcessor registerMonitoring system
An auto-discovery algorithm attempts a scattered-read of register addresses of a device in a utility monitoring system whose identity is unknown to a computer system. If the scattered read is successful, and data from the device includes a device ID code that is matched against a lookup table of devices. If unsuccessful, the algorithm attempts a block-read, and if unsuccessful, iteratively checks each register against the lookup table to determine whether a match exists until either one is found or the device reports an illegal data address exception, whereupon the algorithm stops attempting to read from subsequent addresses. The algorithm analyzes the response from the communications driver of the computer system to determine whether the response is valid, and if not, what type of exception is reported. If a timeout occurs, the algorithm flags the device for a later retry scan, and moves on to attempt to discover the next device.
Owner:SQUARE D CO
An industrial data intelligent analysis system
InactiveCN109739922ARealize intelligent analysisMining potential valueDatabase management systemsSpecial data processing applicationsData accessAnalysis of algorithms
The invention discloses an industrial data intelligent analysis system, which belongs to the technical field of intelligent analysis and comprises an industrial data access DA, an interactive visual IV and an intelligent analysis AI. The method comprises the following steps: step 1, adopting a data access + big data underlying analysis platform + application layer Web visualization architecture mode by the whole industrial data intelligent analysis system; 2, adding a data source; 3, collecting data, and storing and integrating the data; 4, preprocessing the data; 5, realizing algorithm analysis and task development: modeling the data after data preprocessing according to a business scene, adopting intelligent analysis AI, providing analysis algorithm configuration of a bottom layer, customizing a task flow in a draggable manner, and carrying out periodic or immediate processing configuration on the task; and 6, carrying out operation management and display. The method has the beneficial effects that intelligent analysis of a large amount of industrial data is realized, and the potential value of the industrial data is mined; and abundant graphs explore a visual interface, and one-stop service is provided.
Owner:徐工汉云技术股份有限公司
Heuristic route segment path-finding method for ship route design
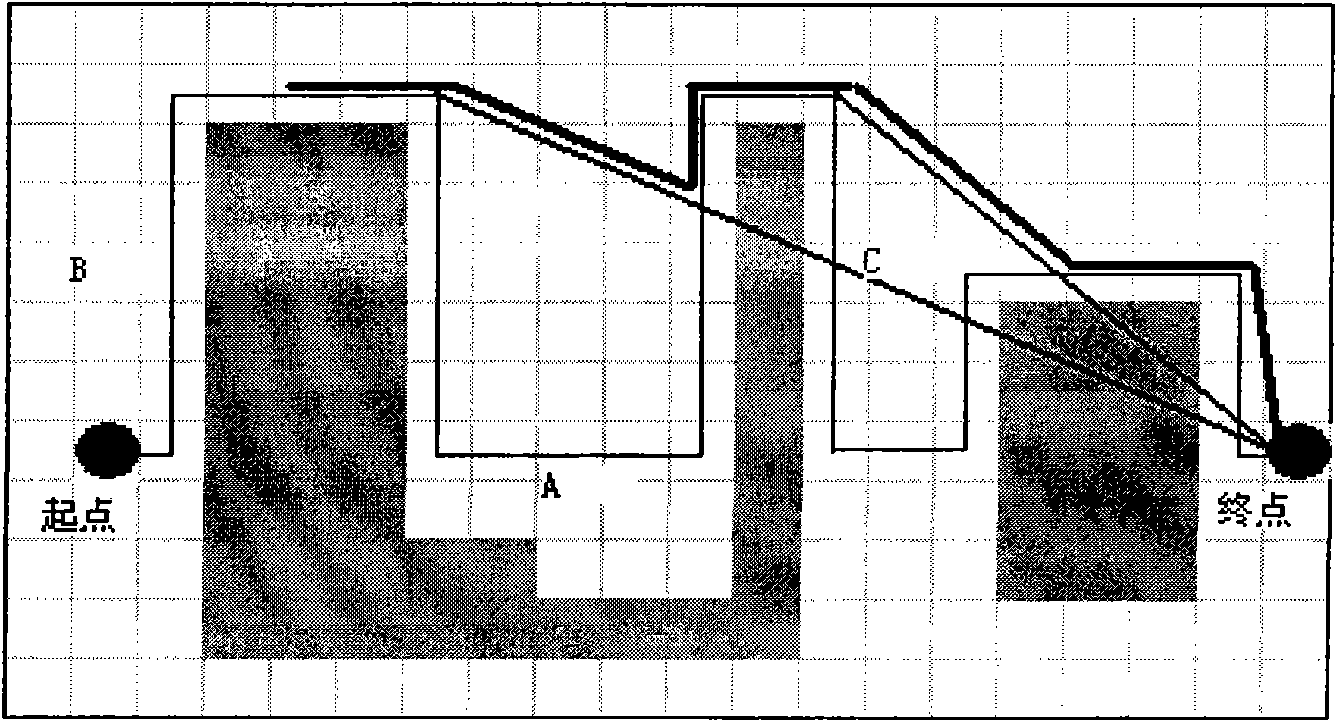
InactiveCN101833699AReduce search timeImprove accuracyForecastingSpecial data processing applicationsShort path algorithmAnalysis method
The invention discloses a heuristic route segment path-finding method for ship route design, comprising heuristic search, a heuristic shortest route segment path-finding algorithm analysis method, an A* algorithm heuristic principle and an improved shortest path algorithm, wherein the heuristic route segment path-finding algorithm puts forwards a method establishing a navigable path tree to reduce meaningless path searching time by being based on a point to point navigable line algorithm and combining with the A* algorithm heuristic principle. By analyzing the particularity of the route segment path-finding algorithm based on a vector diagram in the ship route design, the route segment path-finding algorithm is improved according to an analysis result, the accuracy of a generated route segment path is enhanced and the path-finding efficiency is further increased. Lands, islands and other barriers positioned on a map of the world are expressed by polygons in the vector diagram, and route segment path-finding is to finally find an optimal route segment from communicated paths which are generated between the two outer points of the polygons without passing through the polygons.
Owner:BEIJING BOMAOYITONG SCI & TECH
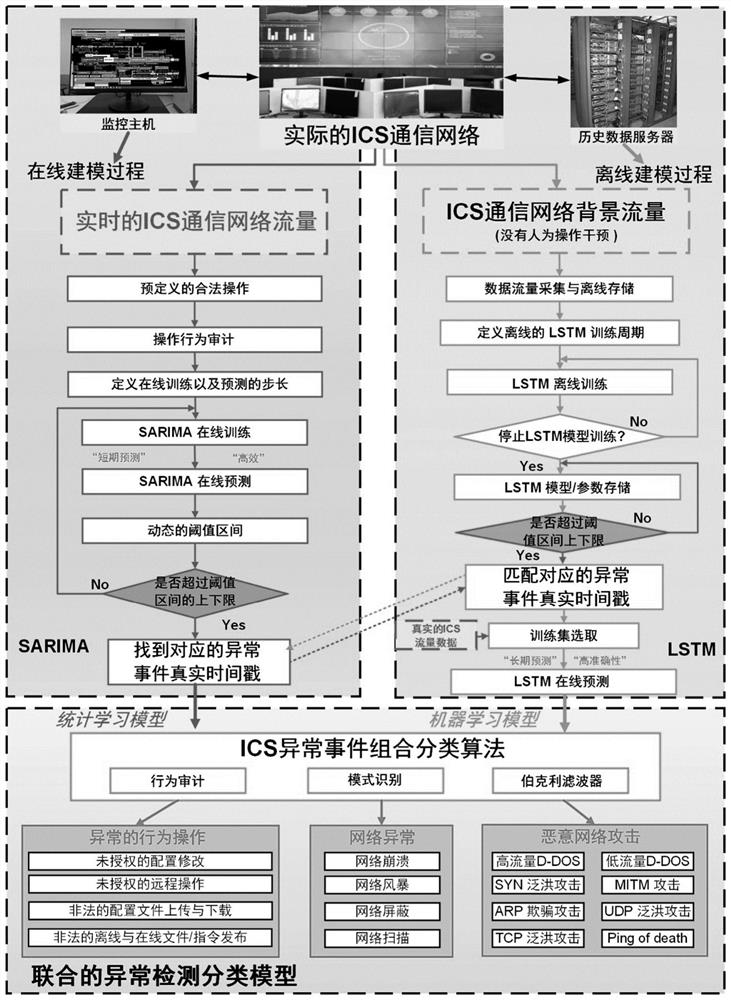
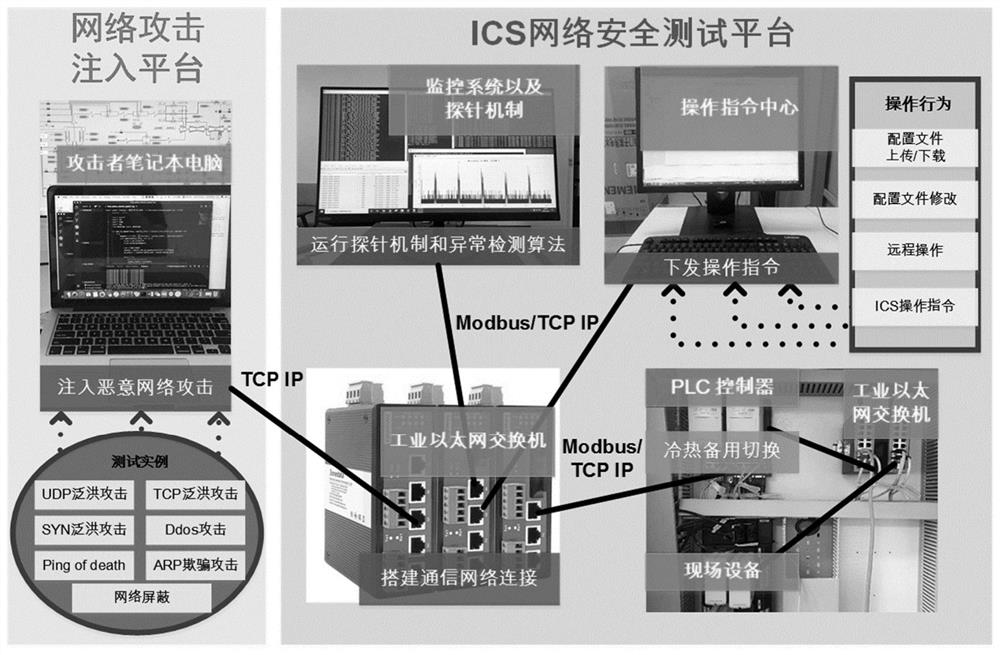
Industrial control system communication network anomaly classification method based on statistical learning and deep learning
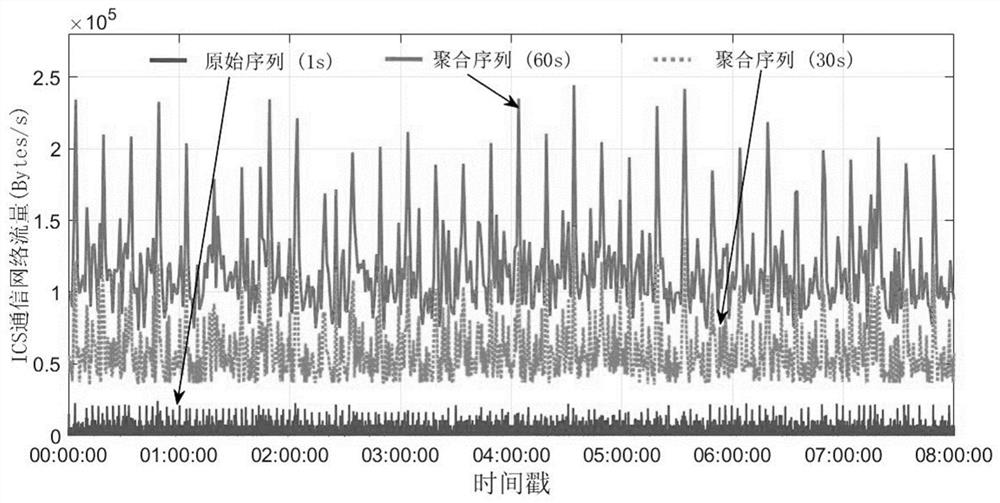
ActiveCN112202736AAccurate source locationMeet intrusion detectionTesting/monitoring control systemsCharacter and pattern recognitionClassification methodsEngineering
The invention discloses an industrial control system (ICS) communication network anomaly classification method based on statistical learning and deep learning. According to the invention, the method comprises the steps: designing LSTM deep learning structure parameters on the basis of the flow of a large-data-volume industrial control system communication network during normal operation, and performing modeling analysis; designing a correlation algorithm to analyze a numerical relationship between background traffic and real-time traffic by analyzing a real-time communication traffic data threshold generated based on a SARIMA online statistical learning model in the early stage; and carrying out specific classification on the ICS communication network anomaly according to an ICS network anomaly event classification algorithm. According to the invention, experimental analysis is carried out by using a target range test board combining industrial control safety virtuality and reality inZhejiang Province; meanwhile, a physical simulation platform is built in a laboratory environment to carry out a verification experiment, and detailed examples are given to verify the reliability andaccuracy of the algorithm.
Owner:ZHEJIANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com