Method and device for detecting hijacking of DNS (Domain Name Server)
A DNS server and legitimacy verification technology, applied in the field of DNS server hijacking detection, can solve problems such as terminal access address errors, errors, threats to terminal or user information security, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0028] An embodiment of the present disclosure provides a method for detecting DNS server hijacking, see figure 1 , the method flow includes:
[0029] In step 101, according to the first domain name system DNS server address set in the terminal, a domain name resolution request carrying a first domain name is sent to the first DNS server. The first domain name is a domain name that does not exist in the network. The method of this embodiment used in the terminal;
[0030] In step 102, the resolution result of the first domain name returned by the first DNS server is received, and if there is a first address list corresponding to the first domain name in the resolution result of the first domain name, then the address list carrying the second domain name is sent to the first DNS server. The domain name resolution request, the second domain name is the domain name that exists in the network that needs to be accessed by the target application, and the method of this embodiment i...
Embodiment 2
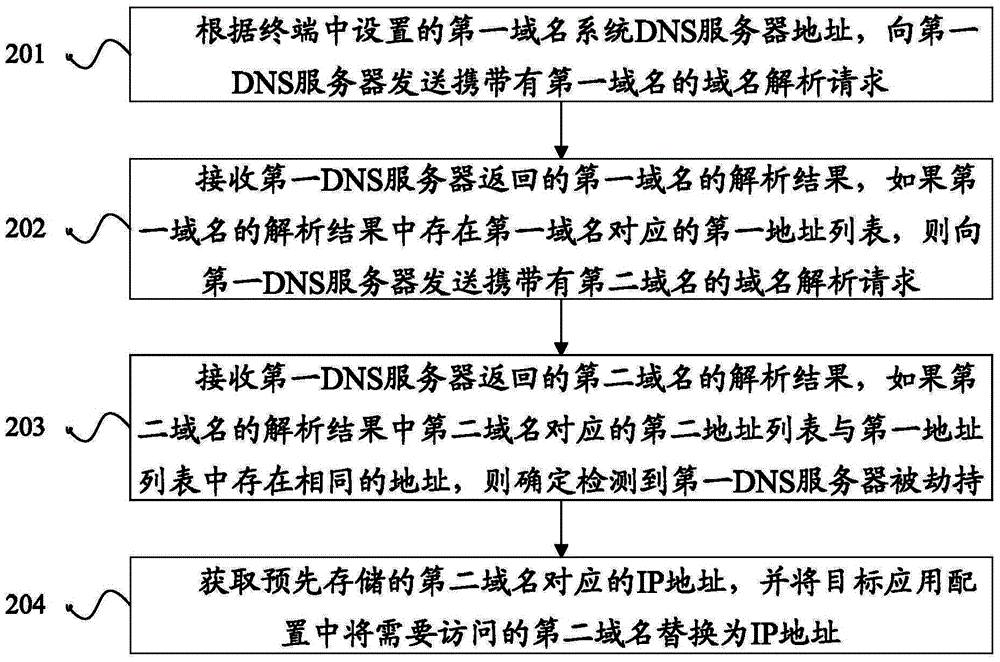
[0034] An embodiment of the present disclosure provides a method for detecting DNS server hijacking, see figure 2 , the method flow includes:
[0035] In step 201, according to the first domain name system DNS server address set in the terminal, a domain name resolution request carrying a first domain name is sent to the first DNS server. The first domain name is a domain name that does not exist in the network. The method of this embodiment used in the terminal.
[0036] Wherein, the first domain name is a domain name that does not exist in the network in the embodiment of the present disclosure, and the first domain name is a preset determination factor for determining whether the DNS server is hijacked. For example: the first domain name can be "www.zhegeyumingbucunzai123456789.com". Normally, the DNS server cannot obtain the IP address corresponding to the first domain name after analyzing the first domain name.
[0037] The purpose of setting the first domain name and...
Embodiment 3
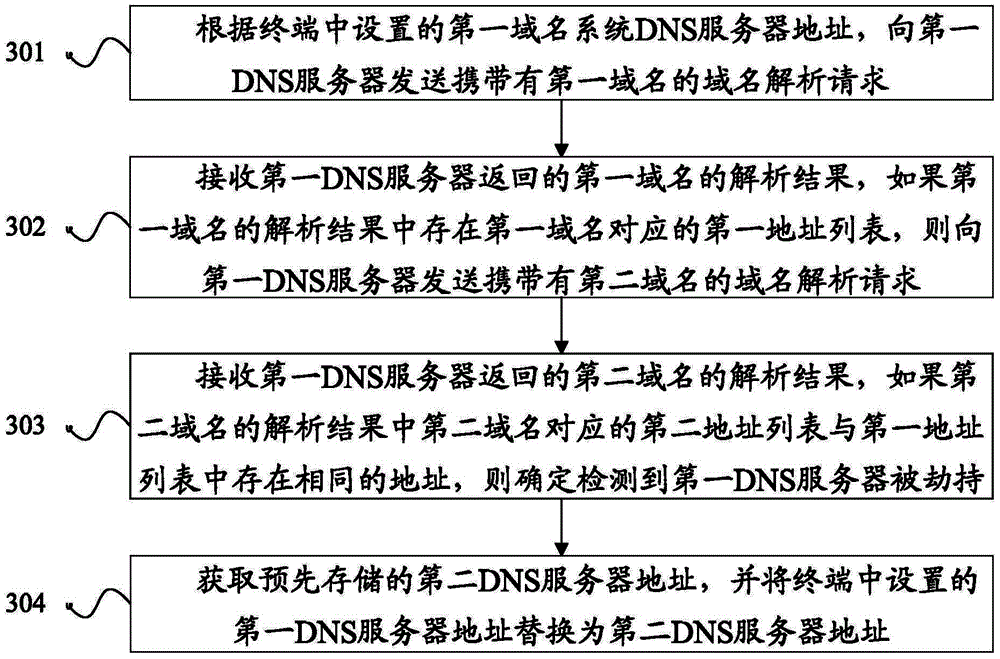
[0056] An embodiment of the present disclosure provides a method for detecting DNS server hijacking, see image 3 , the method flow includes:
[0057] In step 301, according to the first domain name system DNS server address set in the terminal, a domain name resolution request carrying a first domain name is sent to the first DNS server. The first domain name is a domain name that does not exist in the network. The method of this embodiment used in the terminal.
[0058] Wherein, the first domain name is a domain name that does not exist in the network in the embodiment of the present disclosure, and the first domain name is a preset determination factor for determining whether the DNS server is hijacked. For example: the first domain name can be "www.zhegeyumingbucunzai123456789.com". Normally, the DNS server cannot obtain the IP address corresponding to the first domain name after analyzing the first domain name.
[0059] The purpose of setting the first domain name and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com