A block chain anonymous transport protocol based on ring signature
An anonymous transmission and data transmission protocol technology, applied in the field of blockchain anonymous transmission protocol, can solve the problems of poor transmission efficiency, low transmission security, low source reliability and data security, etc., to improve efficiency and efficiency. The effect of communication transmission, increasing source credibility and data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
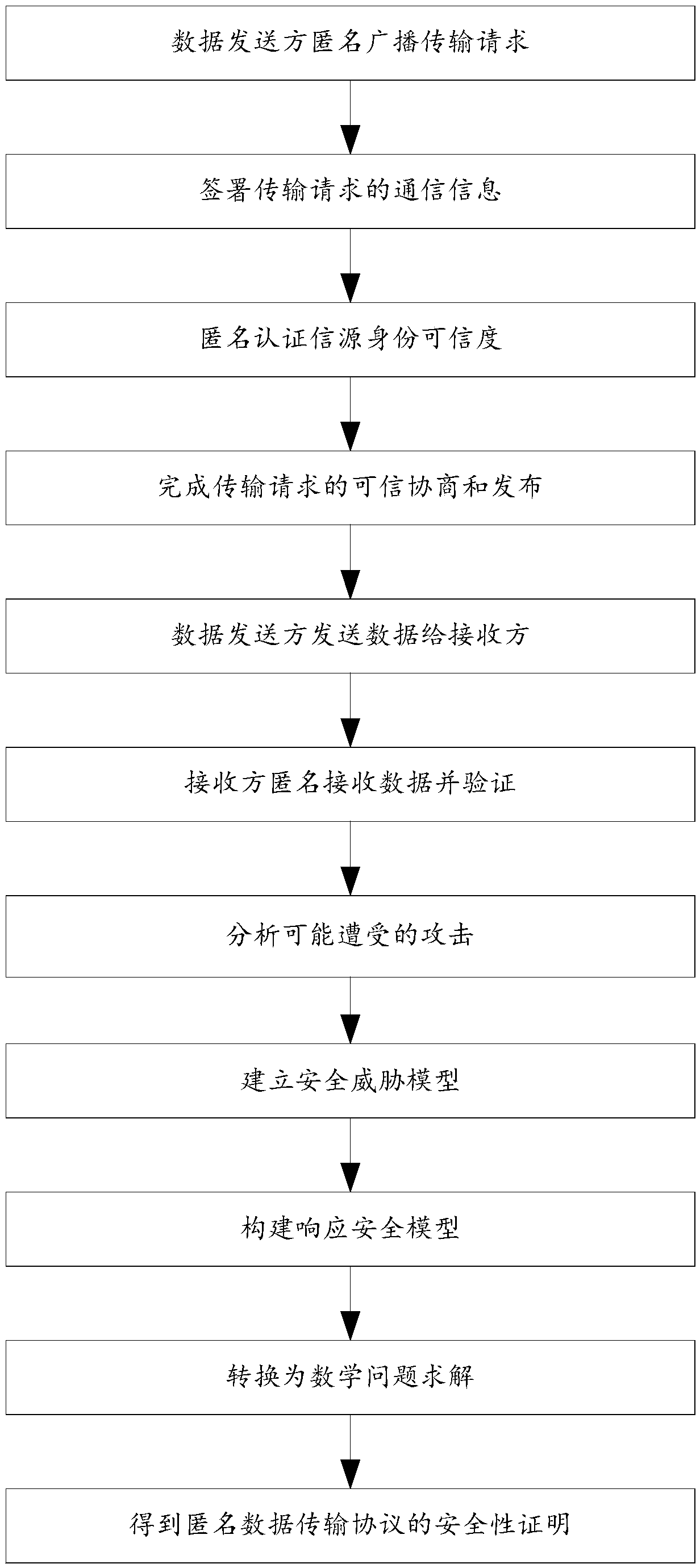
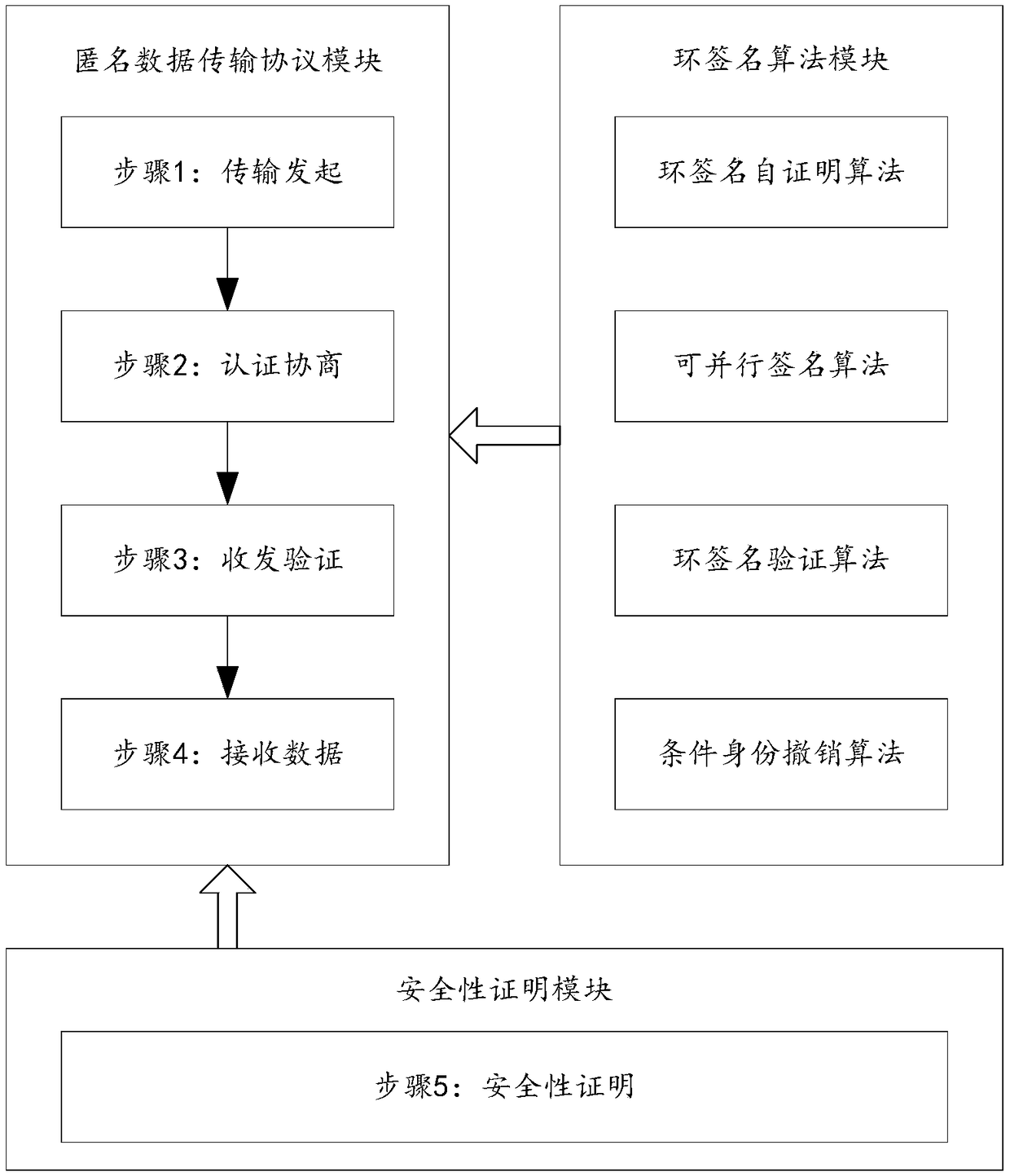
[0046] A ring-signature-based block chain anonymous transmission protocol provided by a preferred embodiment of the present invention includes the following steps:
[0047] Step 1: The data sender anonymously broadcasts the transmission request;
[0048] Step 2: Sign the communication information of the transmission request, then anonymously authenticate the source identity credibility of the data sender, obtain the credible mechanism and parameters of the transmission request, and issue the transmission request;
[0049] Step 2.1: Sign the communication information of the transmission request through the ring signature self-certification algorithm and the parallel signature algorithm;
[0050] Step 2.2: Use the ring signature verification algorithm to anonymously authenticate the source identity credibility of the data sender;
[0051] Step 2.3: If a rebellious or malicious node is found during the transmission process, the identity of the rebellious node is traced and revok...
Embodiment 2
[0062] On the basis of Embodiment 1, the preferred embodiment of the present invention further includes
[0063] Step 5: Prove the security of the anonymous data transmission protocol;
[0064] Step 5.1: Analyze the types of on-chain or off-chain adversaries, attack conditions, attack forms, attack processes, and attack effects that nodes on the blockchain may face during data transmission;
[0065] Step 5.2: According to the possible attacks analyzed in step 5.1, establish corresponding security threat models respectively, and comprehensively and accurately simulate the environment under attack;
[0066] Step 5.3: After converting the security threat model in step 5.2 into a formal description of attacks in the blockchain environment, construct a challenge response security model for each security target. The security model describes multiple different layers, different objects and different Blockchain attacks for security requirements, and corresponding mathematically diffi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com