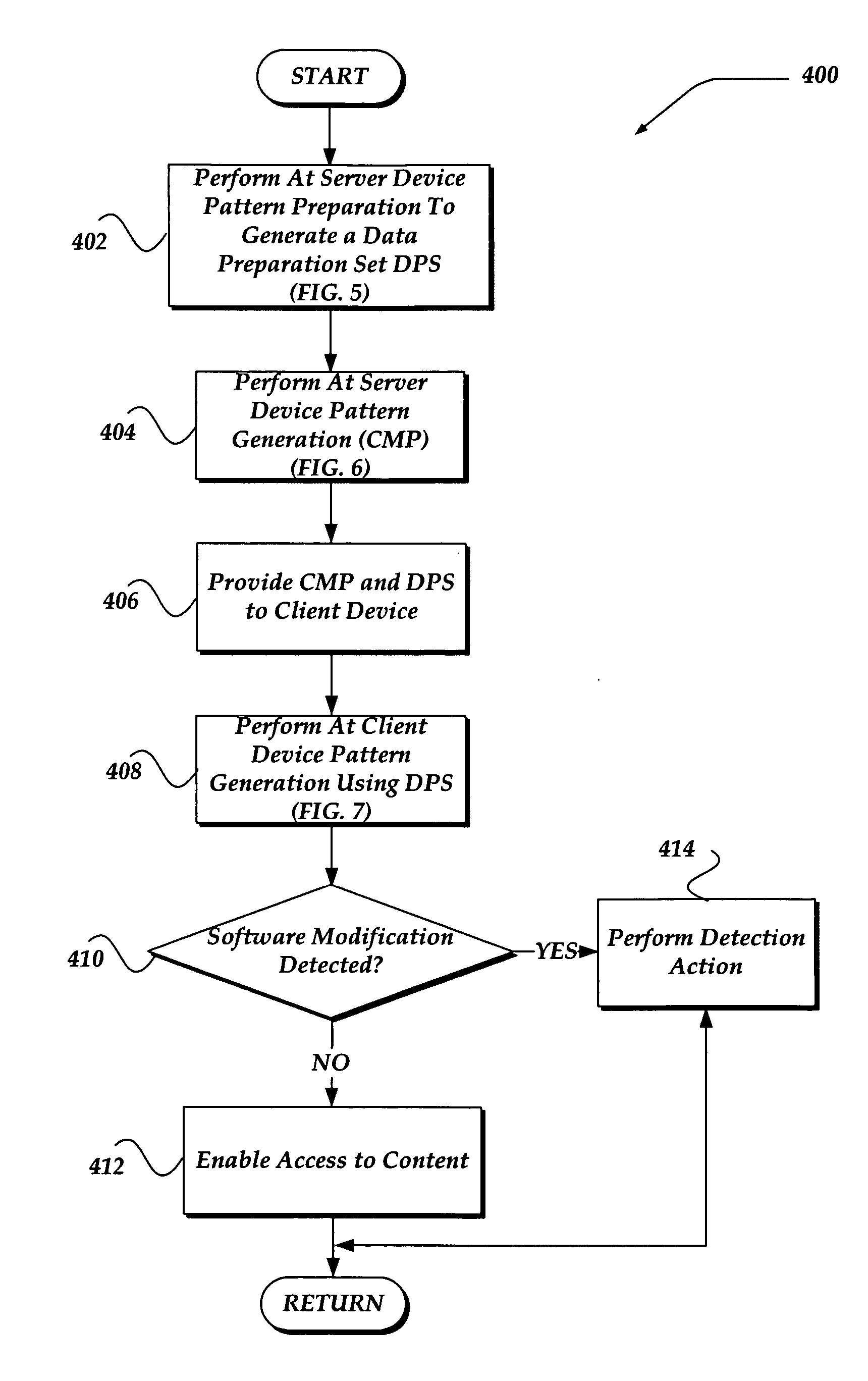
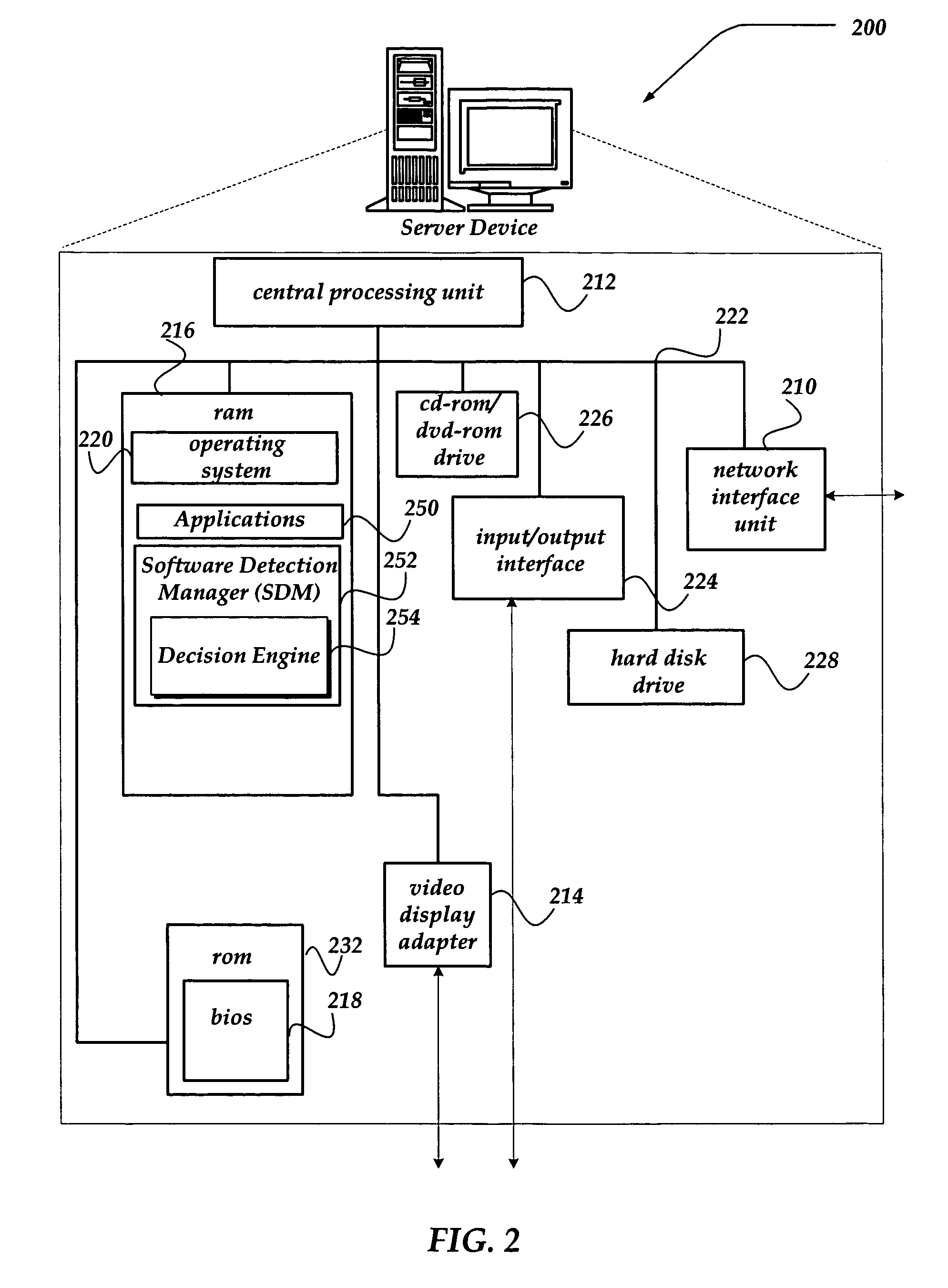
Patents
Literature
54 results about "Software integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Integrity Software are providers of the Evolution range of construction industry specific job costing and accounting software in the UK and Ireland.
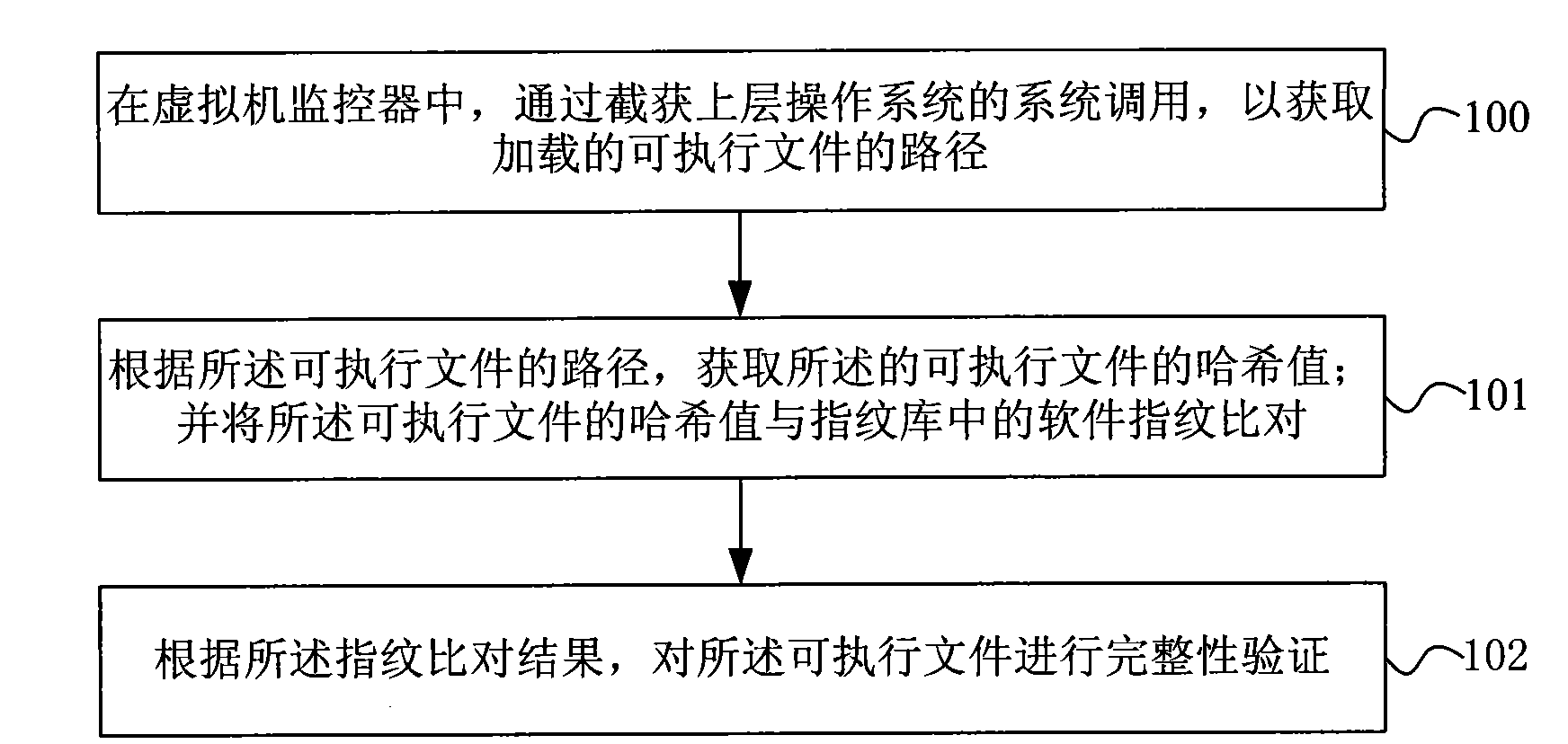
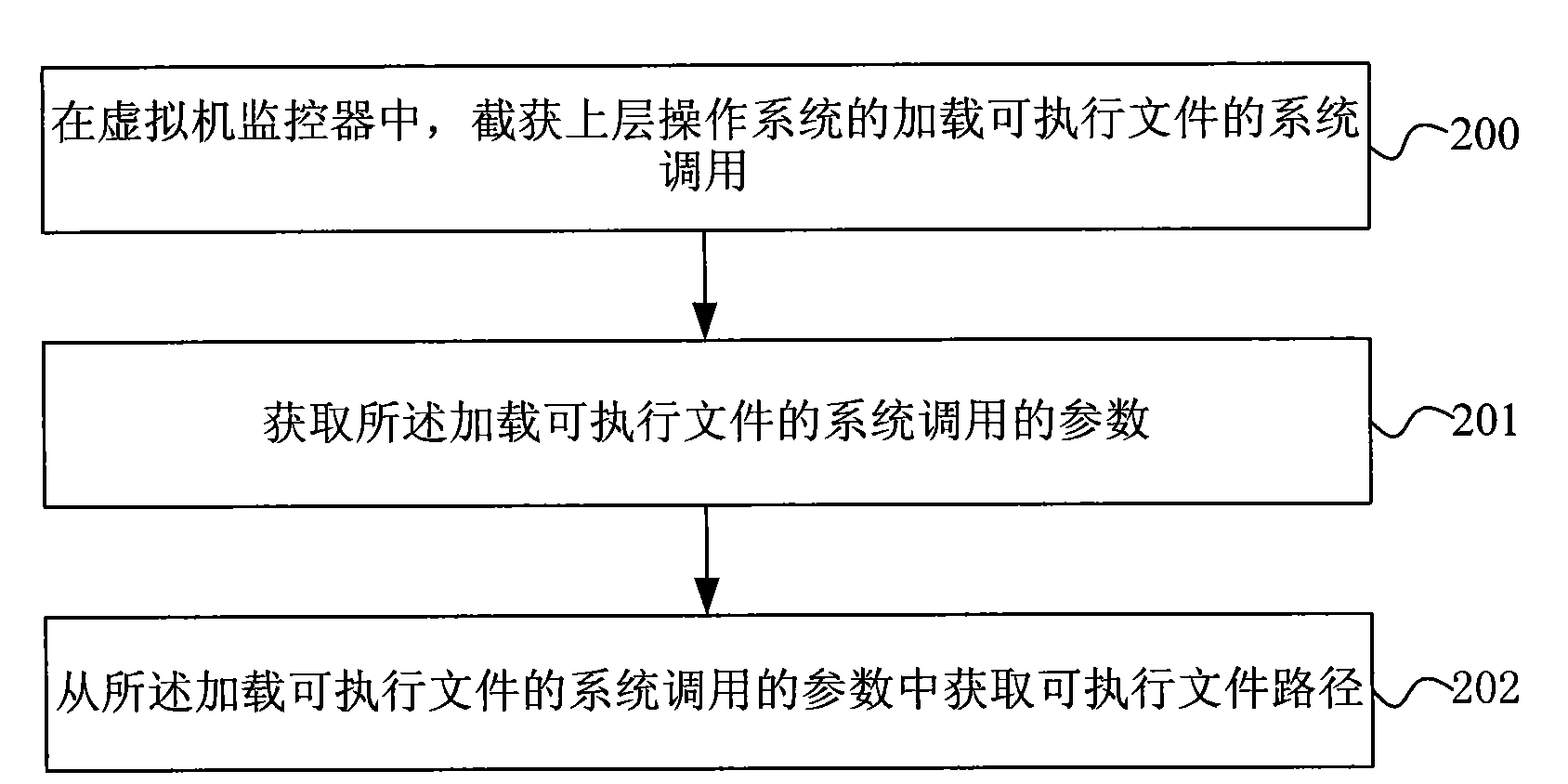
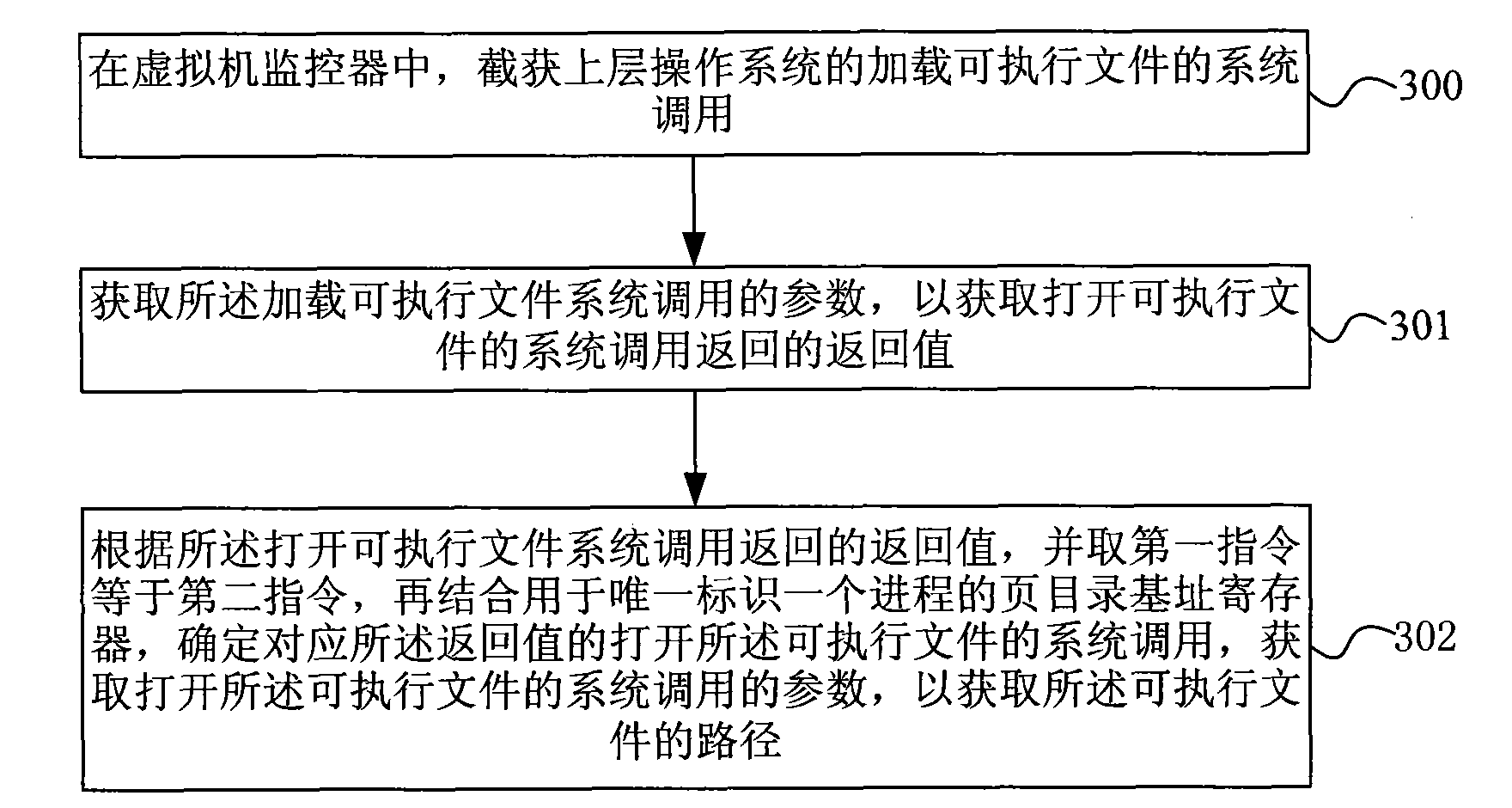
Method and system for verifying software completeness
InactiveCN101593259AImprove securityVersatilityPlatform integrity maintainanceOperational systemValidation methods
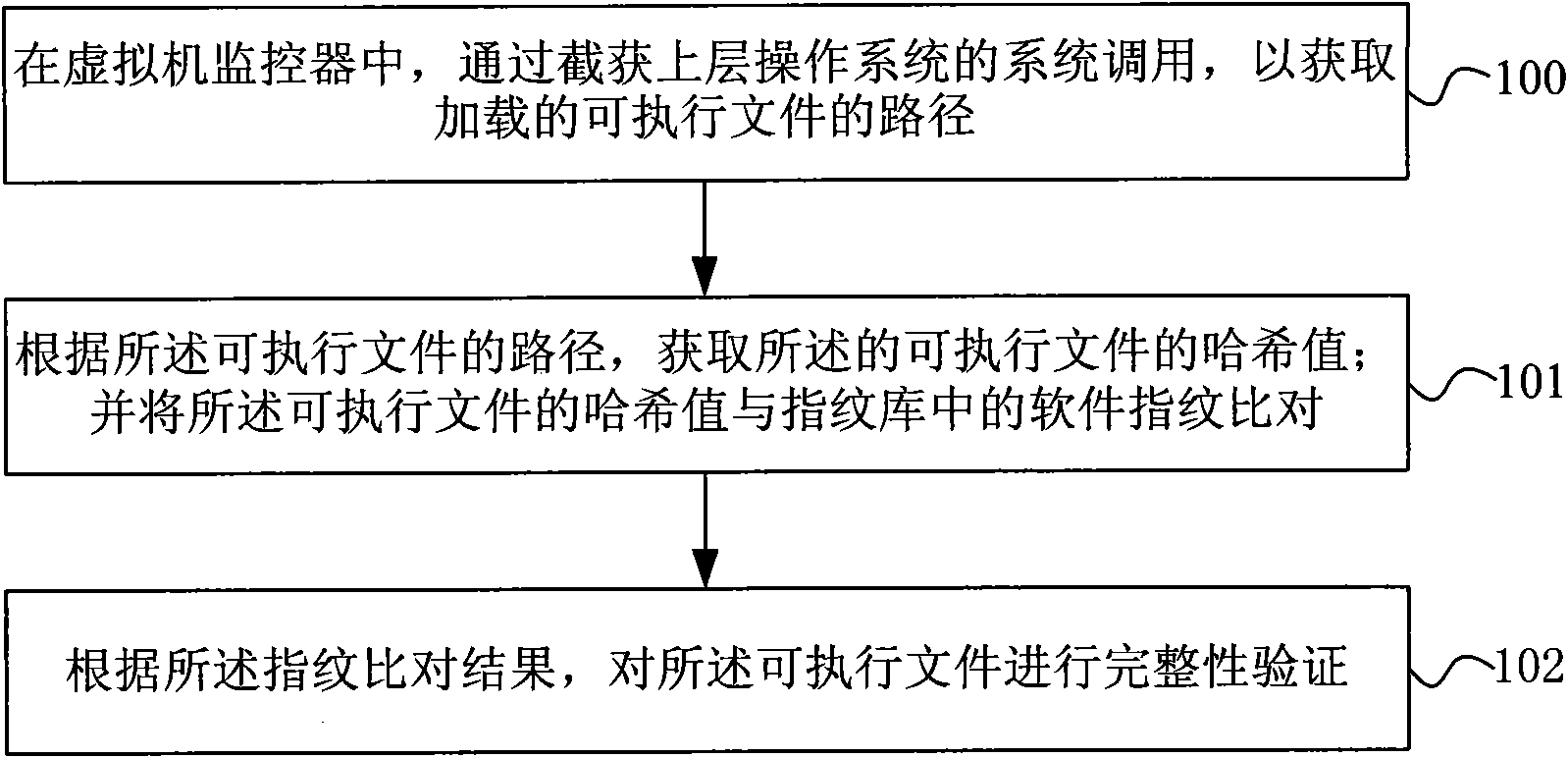
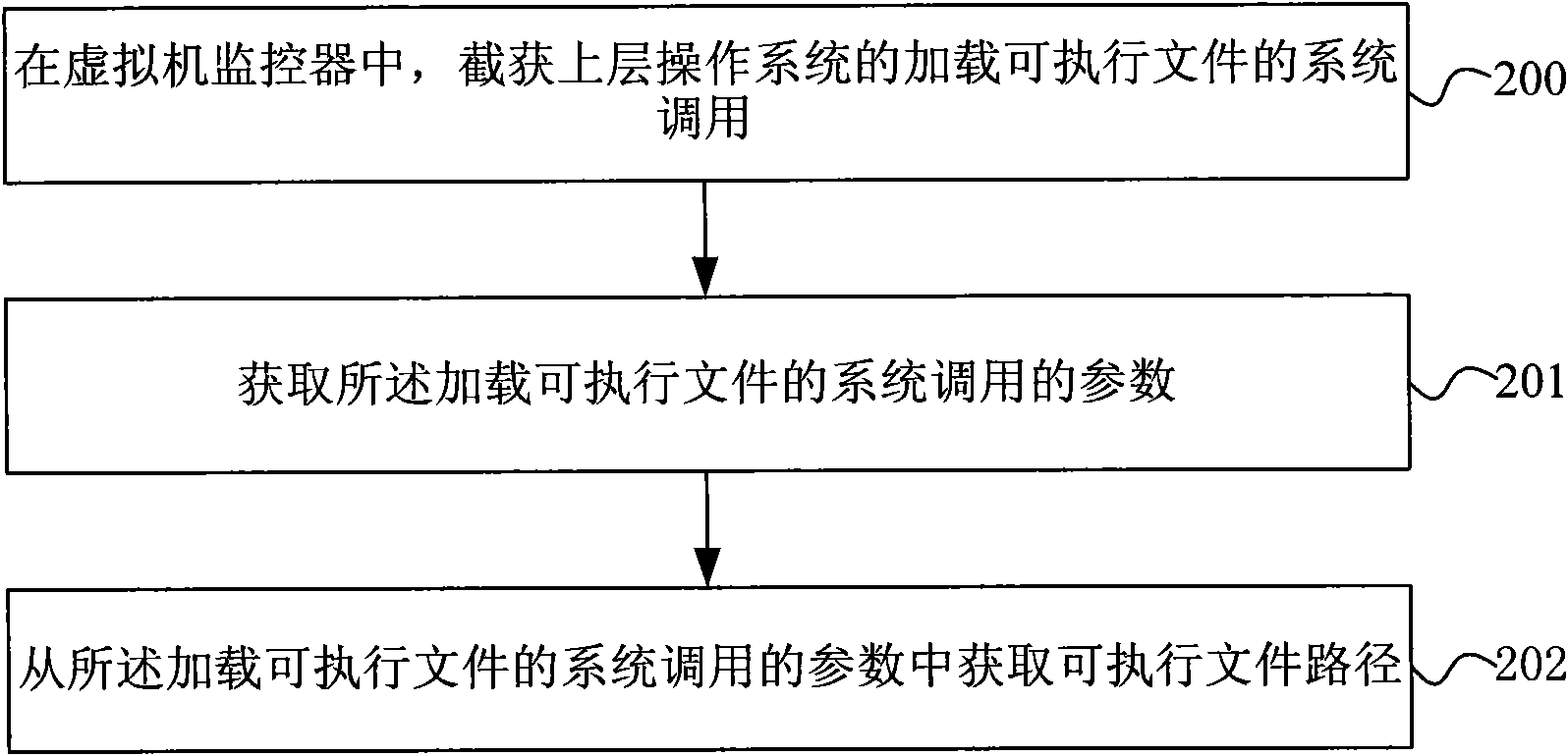
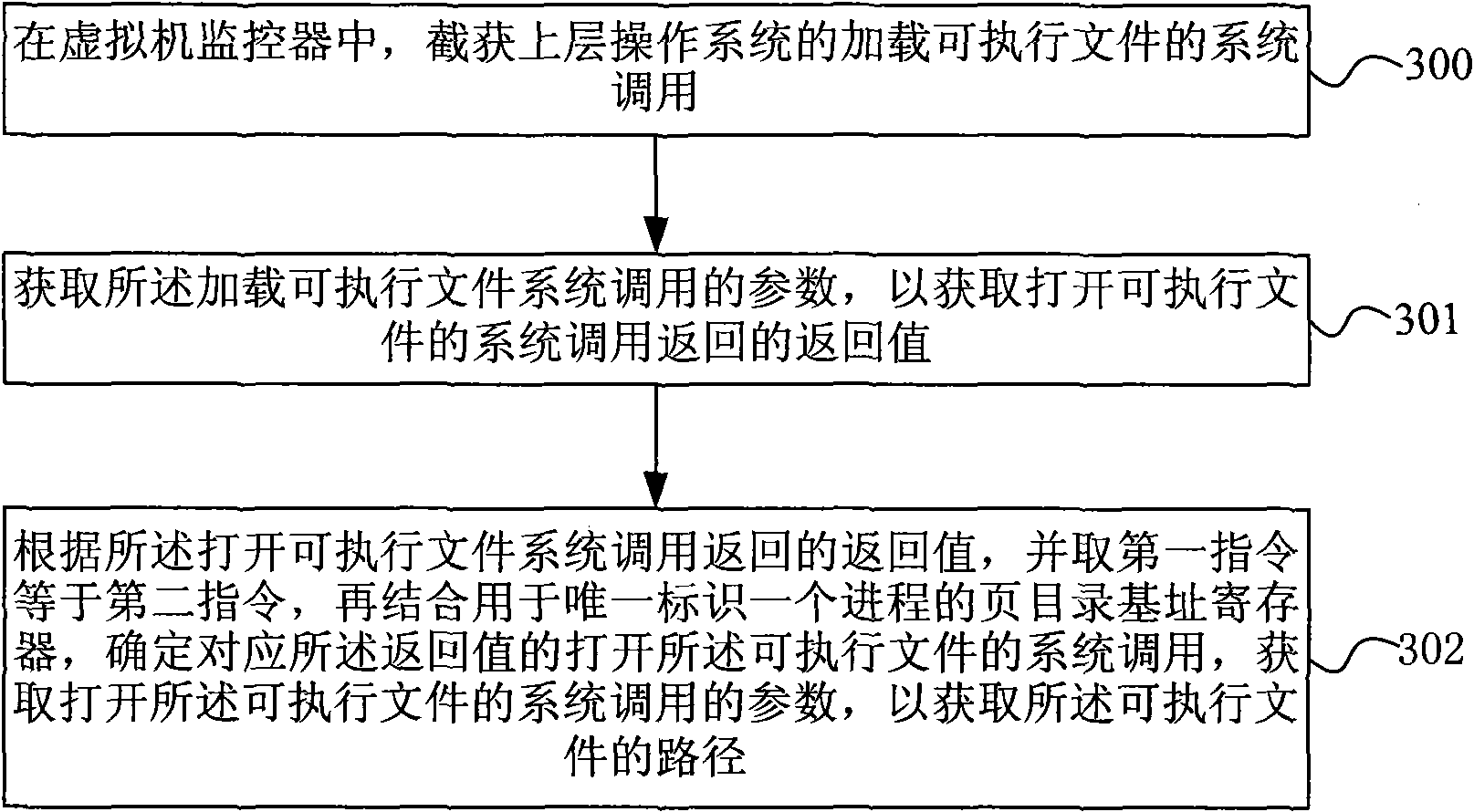
The invention discloses a method for verifying software completeness. The method comprises the following steps: acquiring path of a loaded executable file through capturing system call of an upper operation system in a virtual machine monitor; acquiring a Hash value of the executable file according to the path of the executable file; comparing the Hash value of the executable file with software fingerprints in a fingerprint bank; and carrying out completeness verification on the executable file according to the result of fingerprint comparison. The invention also discloses a software completeness verification system. The method and the system for software completeness verification realize software completeness verification in the virtual monitor, is independent of the operation system without depending on completeness of the operation system, improves security of the system, and has universality and compatibility. The technical proposal belongs to completeness verification of software in loading period, reduces verification cost without support of auxiliary hardware, reduces cost and improves performance compared with the method for verifying completeness of a file system.
Owner:BEIHANG UNIV
High-reliability computing platform
InactiveCN101877040AEnsure crediblePrevent potential safety hazardsInternal/peripheral component protectionOperational systemPassword
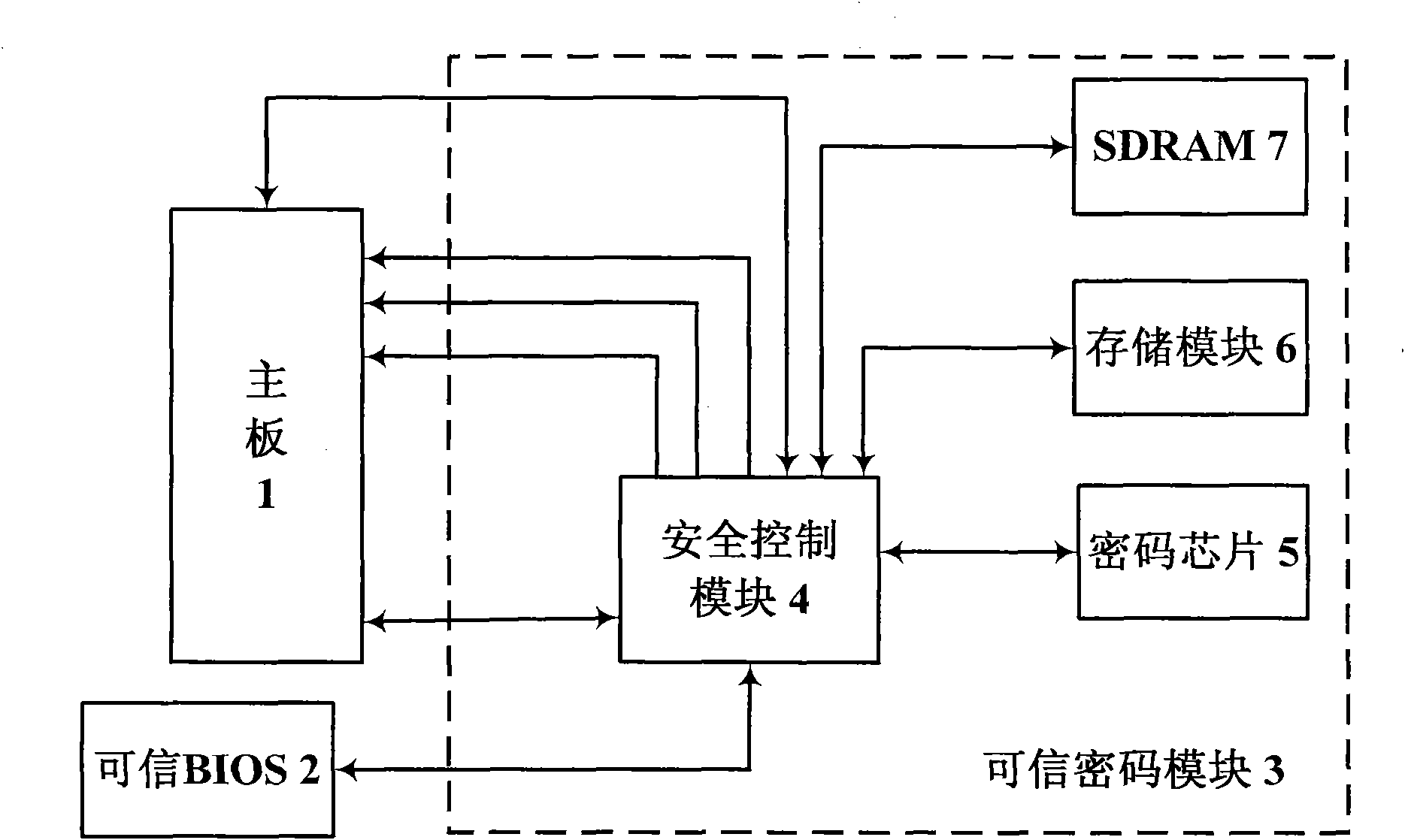
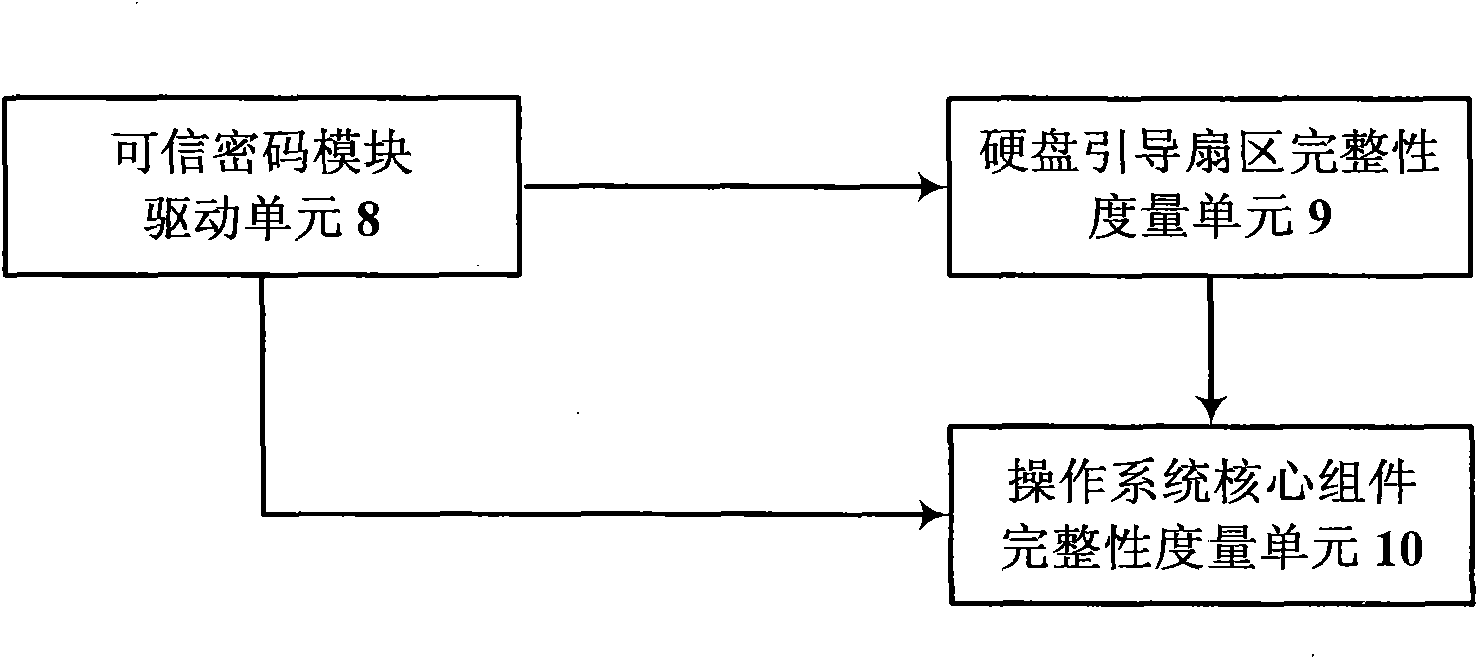
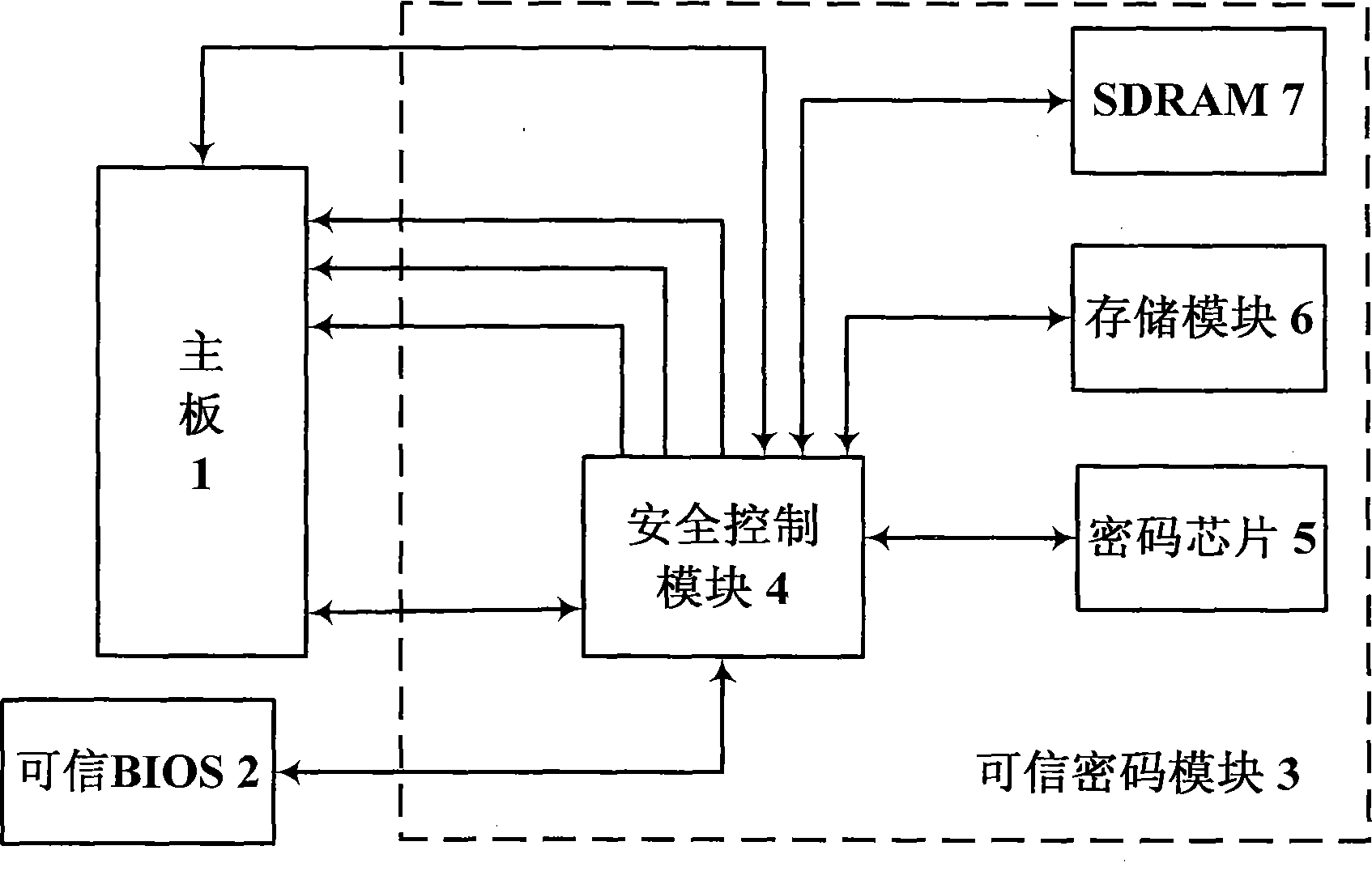
The invention discloses a high-reliability computing platform, which comprises a mainboard (1), a reliable BIOS (3) and a reliable password module (2) connected through a bus. A computer is electrified, and then the reliable password module (2) is electrified at first; the mainboard (1) is kept at a reset state by controlling a power, a clock and reset signal line, meanwhile a safety control module (4) starts a BIOS integrity measuring mechanism to ensure the reliability of the BIOS and then releases the power, the clock and the reset signal; the mainboard (1) directly accesses the BIOS chip through an LPC bus and loads the reliable BIOS (3) for normal start; the reliable BIOS (3) sequentially loads a hard disk boot sector integrity measuring unit (9) and an operating system core component integrity measuring unit (10) therein to finish the software integrity measurement; and after the measurement is successful, the operating system is normally loaded and operated. The invention ensures the safety and reliability during the computer starting process.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
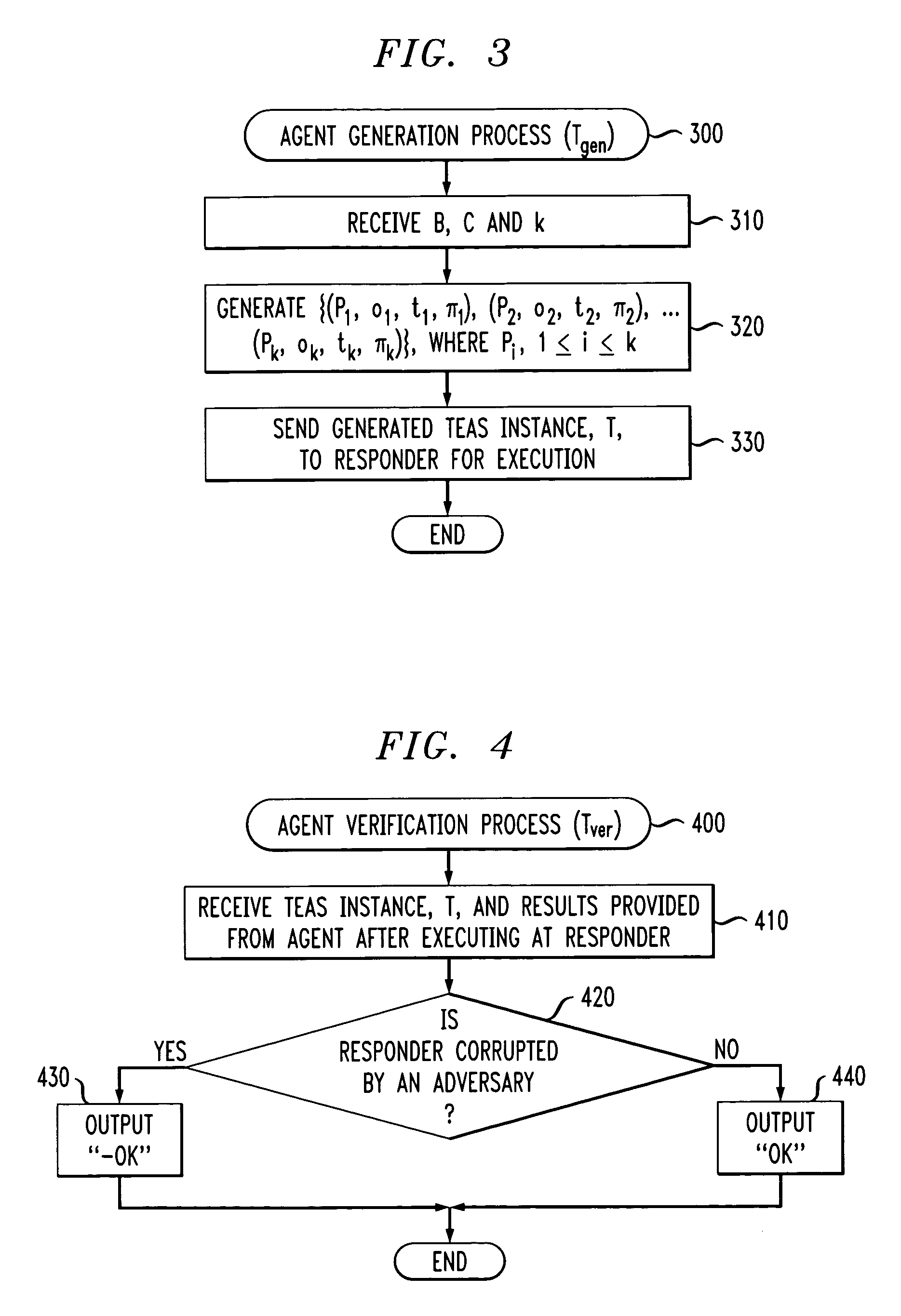
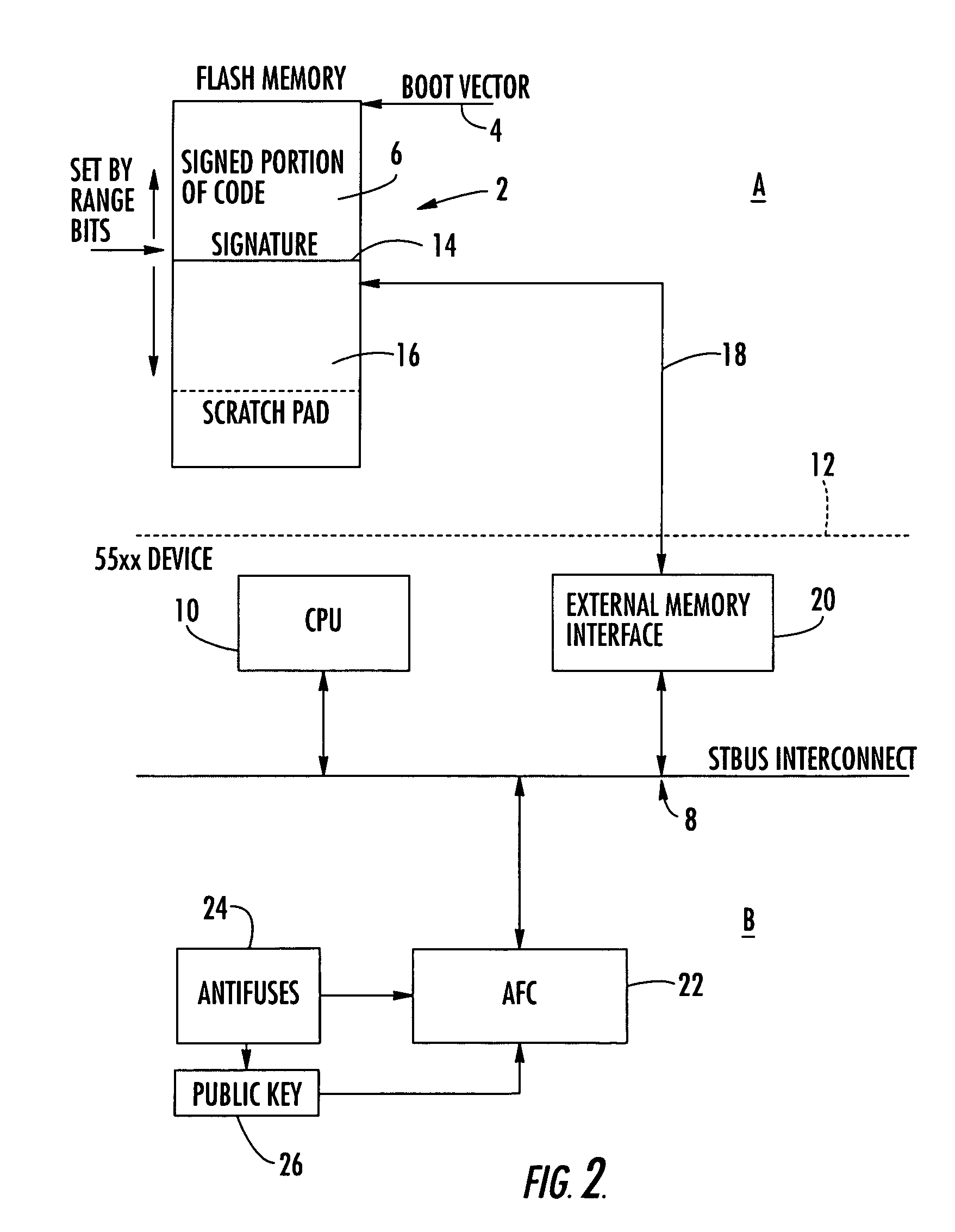
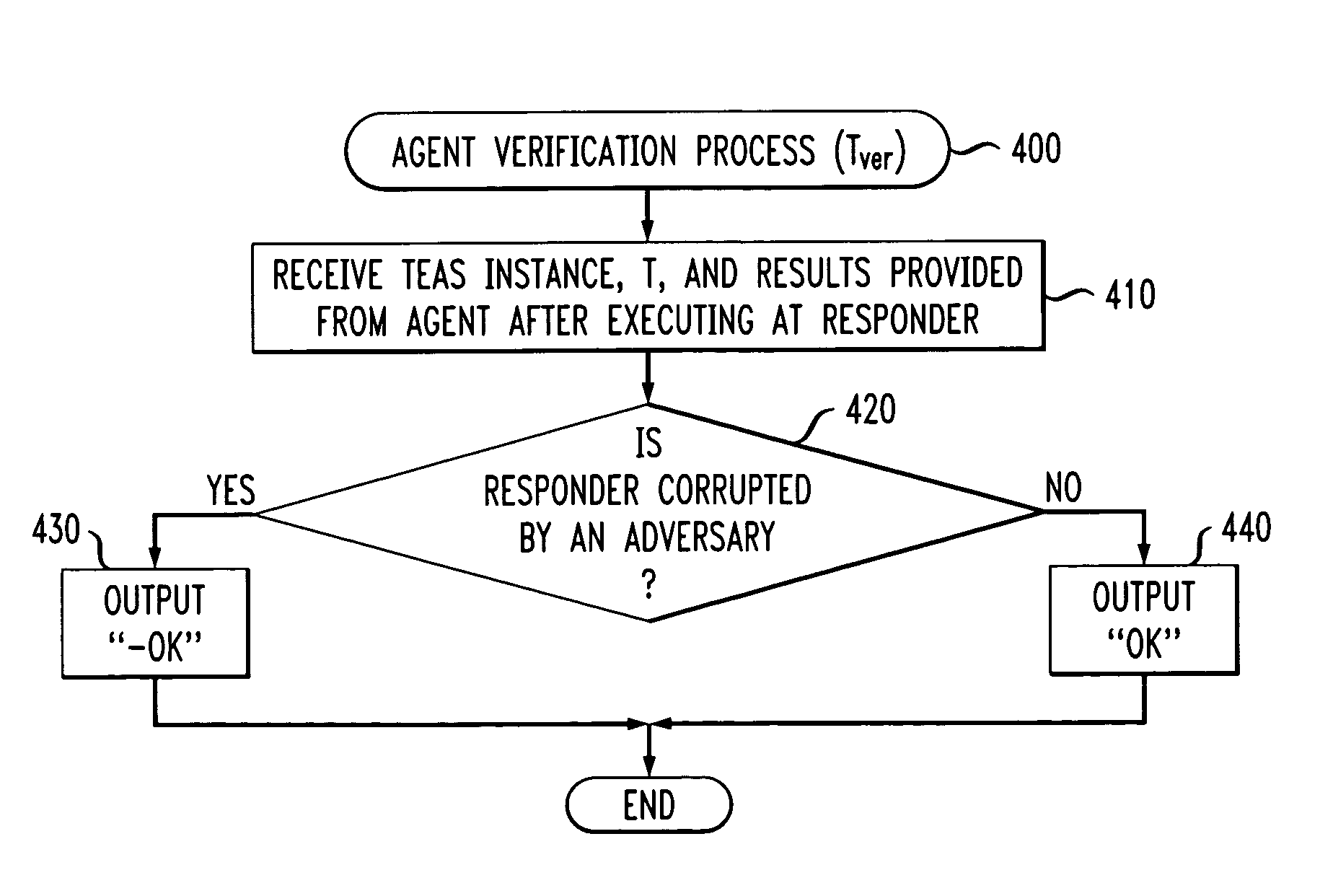
Method and apparatus for software integrity protection using timed executable agents
ActiveUS20060090209A1Digital data processing detailsAnalogue secracy/subscription systemsClient-sideBlind technique
A method and apparatus are disclosed for evaluating the security of at least one client. An executable program is executed by the client being evaluated. A result is received from the executable program and an evaluation of the result indicates whether the client has been corrupted. The executable program is one of a plurality of possible programs. The result may be evaluated based on an elapsed time between when the executable program is provided to the client and when the result is received. The executable program may include at least one function that writes to a memory of the client. A program blinding technique is also disclosed to generate executable programs.
Owner:WSOU INVESTMENTS LLC
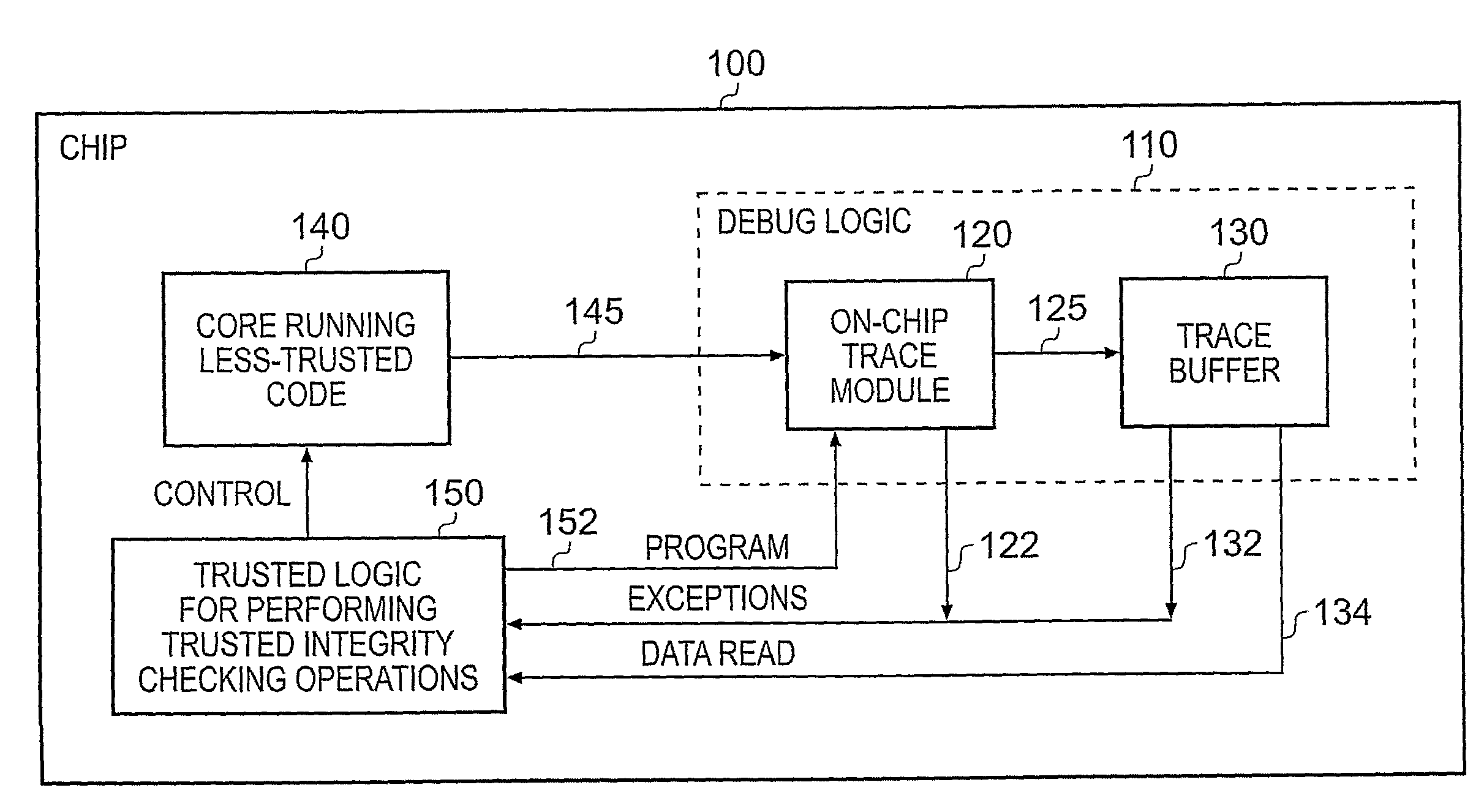
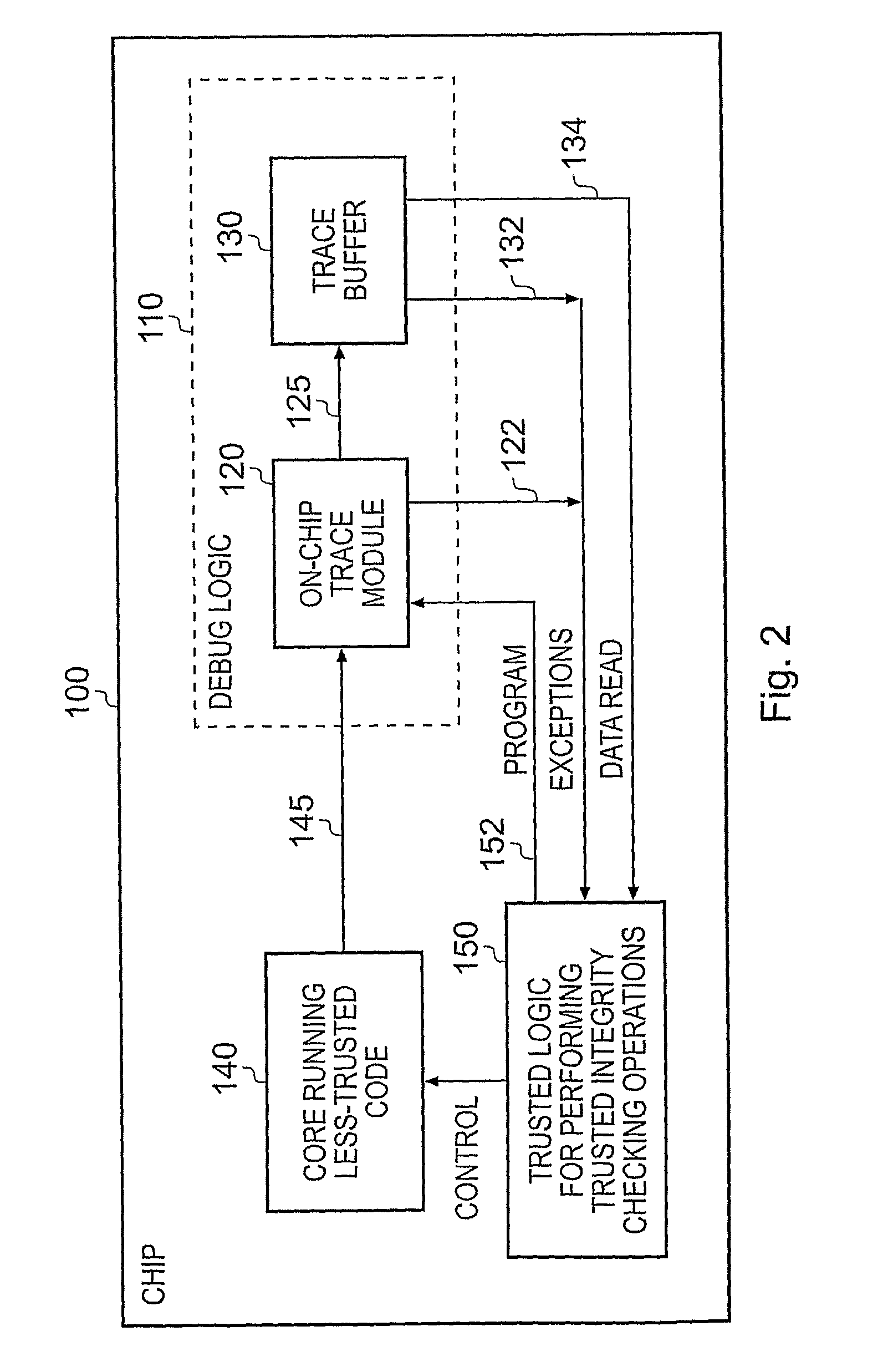
Apparatus and method for performing integrity checks on sofware
InactiveUS20090307770A1Low implementation costFacilitate strong and robust integrity checking processMemory loss protectionUnauthorized memory use protectionProgramming languageControl register
An apparatus and method are provided for performing integrity checking of software code executing on a processing unit of the apparatus. The apparatus further includes debug logic used when debugging program code executed by the processing unit, and trusted logic for performing trusted integrity checking operations on less-trusted program code executed by the processing unit. The debug logic has an interface via which the trusted logic can program one or more control registers, that interface not being accessible by the less-trusted program code. The trusted logic programs the control registers so as to cause the debug logic to be re-used to detect one or more activities of the processing logic during execution of the less-trusted program code, and the trusted integrity checking operations performed by the trusted logic are influenced by the activities detected by the debug logic. Such an approach has been found to provide an efficient and secure technique for performing run-time integrity checking of program code.
Owner:ARM LTD
System and method for software tamper detection
A method, system, and apparatus are directed towards detecting unauthorized modification of software, such as virtual smart card software. An analysis is performed on the software to generate a unique pattern that is based on the integrity of the software. The pattern is generated using various portions of the software code. In one embodiment, matrix manipulations that involve a sequence of randomly selected matrix operations are performed on extracted portions of the software code. Sample sizes of the software code, sizes of the matrices, and other initialization parameters may be selected based on a desired security level. The resulting pattern may then be compared to a known normal pattern for the software to detect unauthorized modification. In one embodiment, however, the resulting pattern may be algorithmically combined with another value. The resulting combination may be used to decrypt content, if the software has not been modified.
Owner:GOOGLE LLC
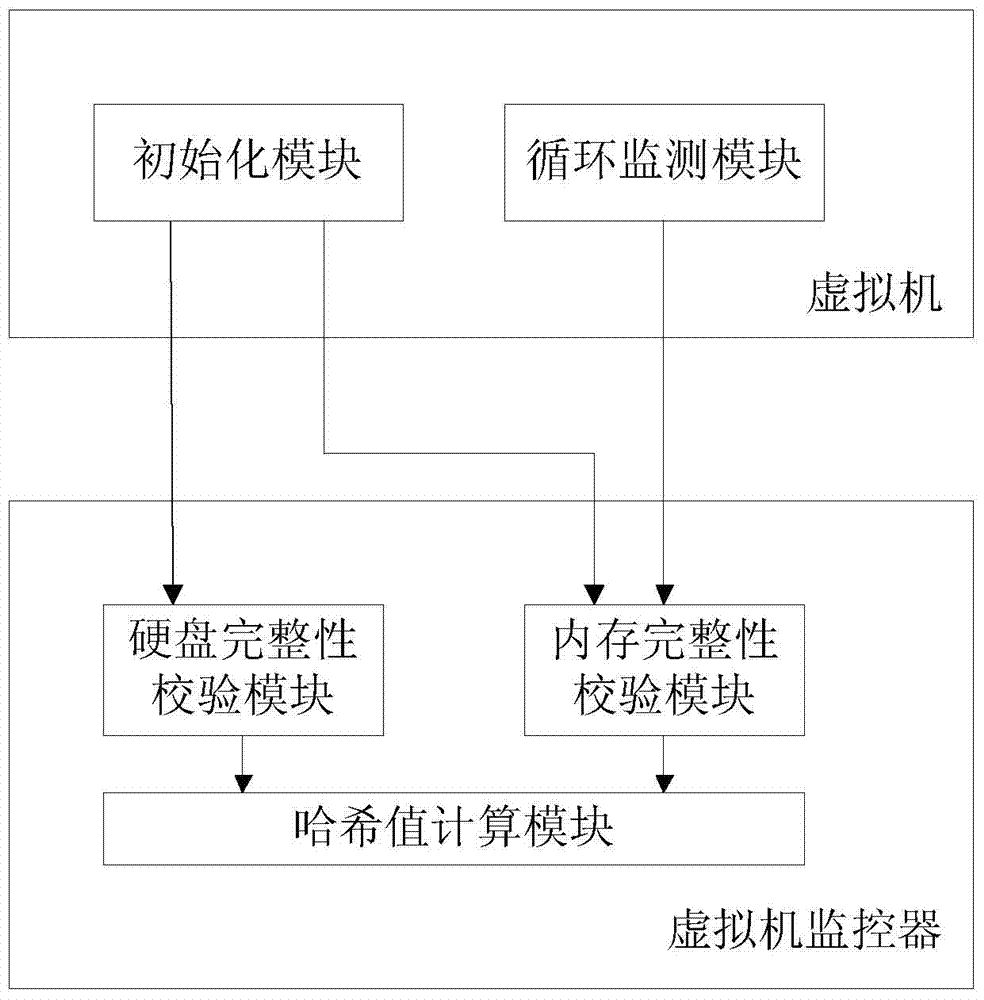
Software integrity verifying system and method based on VMM (virtual machine monitor)
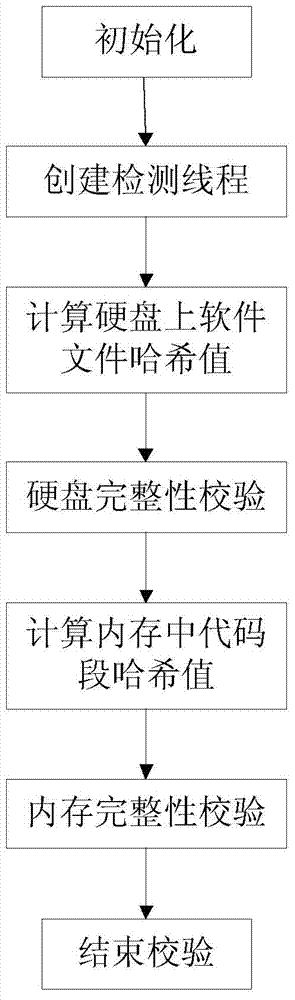
ActiveCN103593617AReduce performance overheadReduce overheadPlatform integrity maintainanceInternal memoryComputer module
The invention discloses a software integrity verifying system and method based on a VMM (virtual machine monitor). The system comprises a virtual machine and the VMM. The virtual machine comprises an initial detecting module and a circulating detecting module. The VMM comprises a hard disk integrity verifying module, an internal memory integrity verifying module and a hash value calculating module. The method includes: initiating, creating a detecting thread, calculating the hash value of the software file in a hard disk, verifying hard disk integrity, calculating the hash value of the code segment in an internal memory, verifying internal memory integrity, and finishing software integrity verification. The system and the method has the advantages that integrity verification can be performed efficiently by actively being caught into the VMM, and internal memory integrity monitoring is achieved by creating a circulating detecting thread; the system and the method can be used for detecting software's malice modification of an executable file, crack prevention of software, and detecting internal memory patch's modification of the software image in the internal memory.
Owner:XIDIAN UNIV
System and method of verifying integrity of software
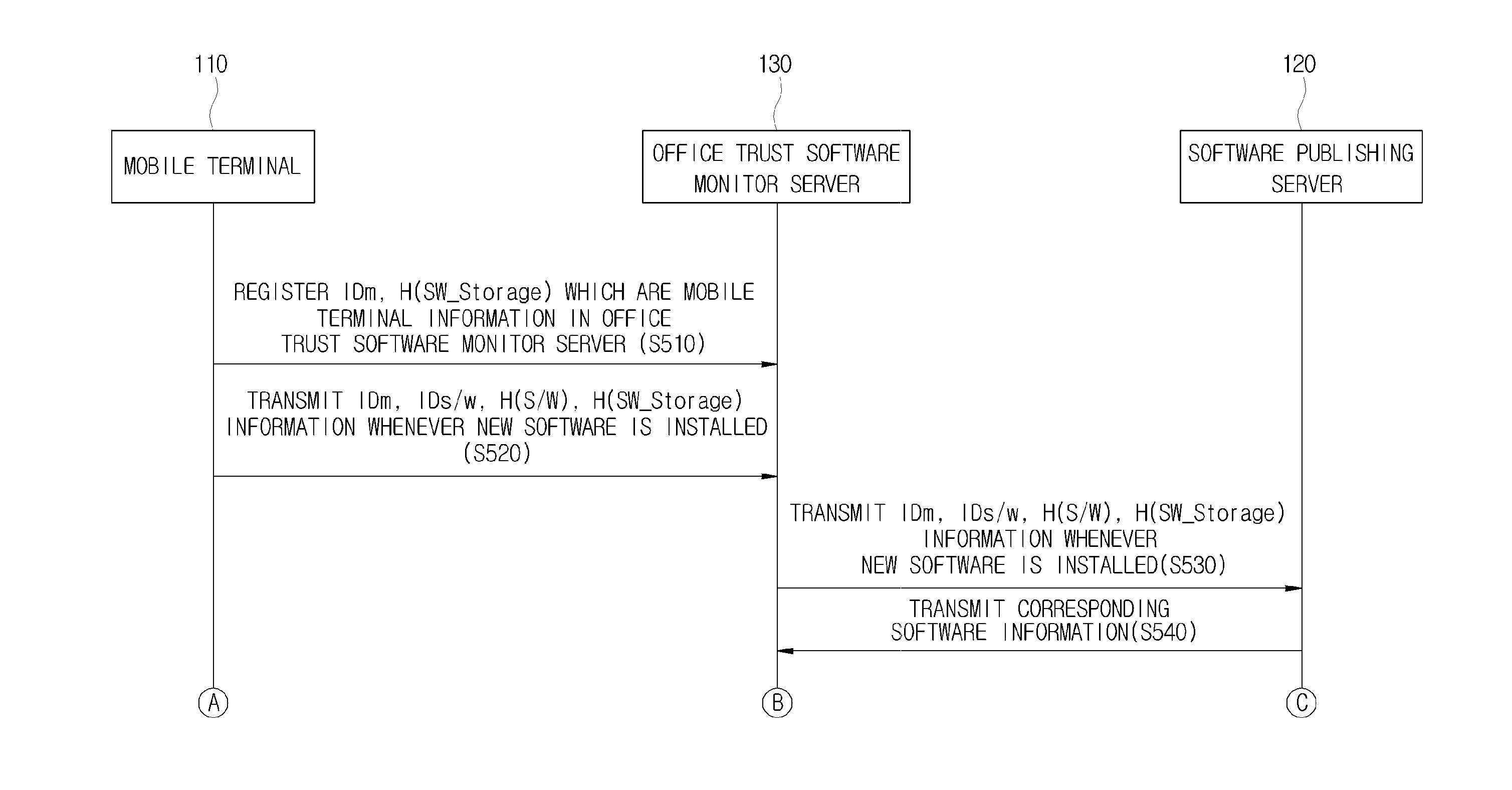
InactiveUS20150271679A1Service provisioningUser identity/authority verificationComputer hardwareComputer terminal
A system and method of verifying integrity of software for verifying the integrity of software installed on a mobile terminal is provided. The system includes the mobile terminal configured to transmit mobile terminal information including a first software hash value and a software identification (ID) with respect to the software, and an office trust software monitor server configured to transmit the software ID transmitted from the mobile terminal to a software publishing server, receive a second software hash value with respect to the software corresponding to the software ID from the software publishing server, compare the first software hash value and the second software hash value, and verify the integrity of the software.
Owner:ELECTRONICS & TELECOMM RES INST
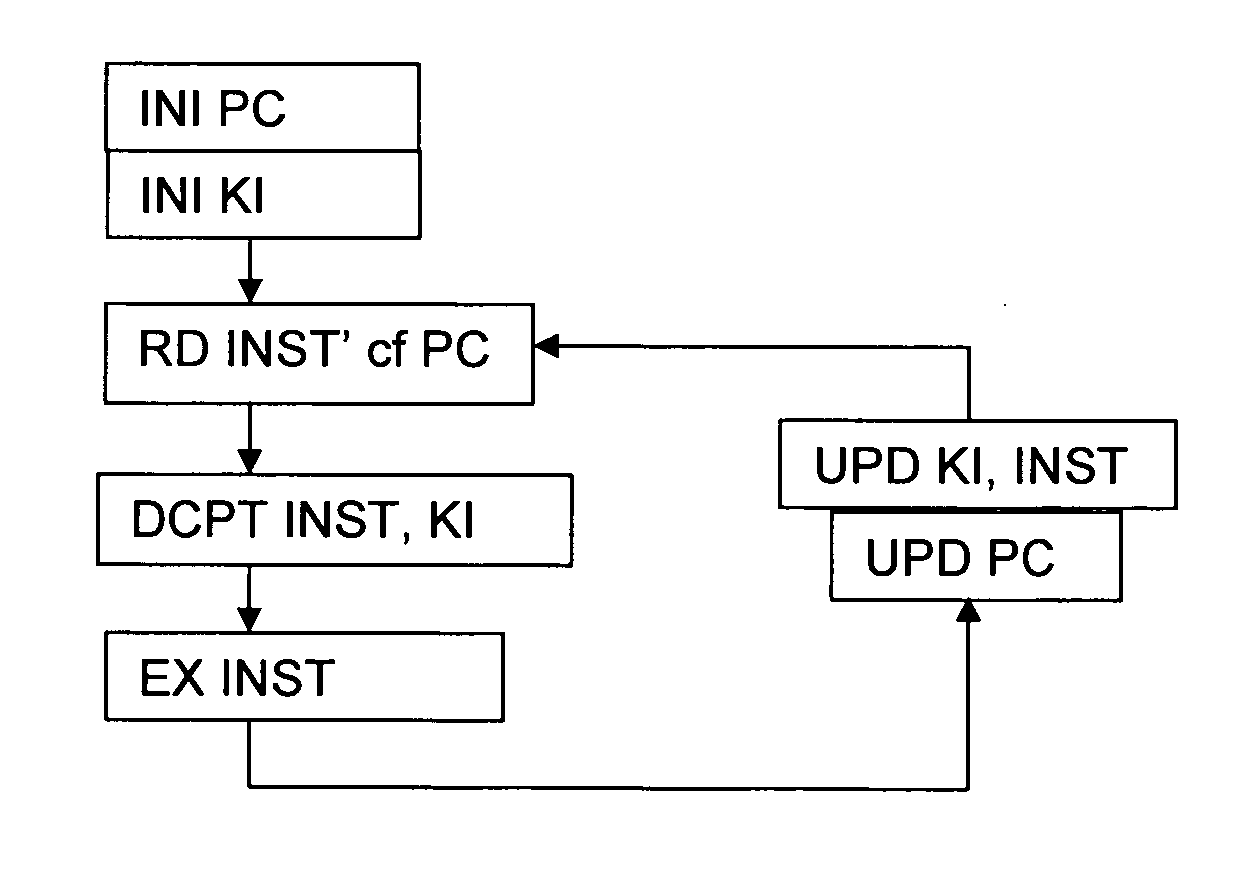
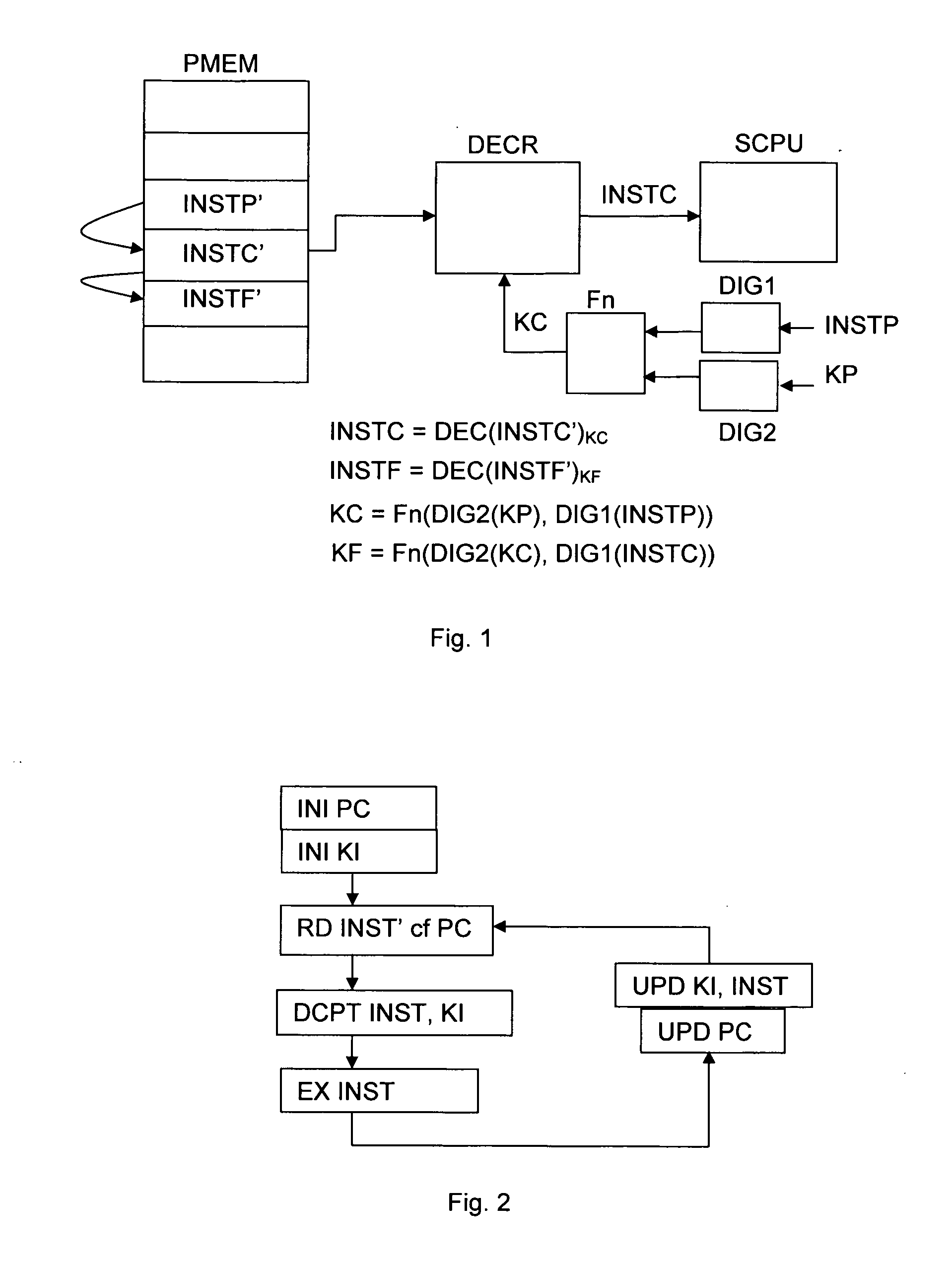
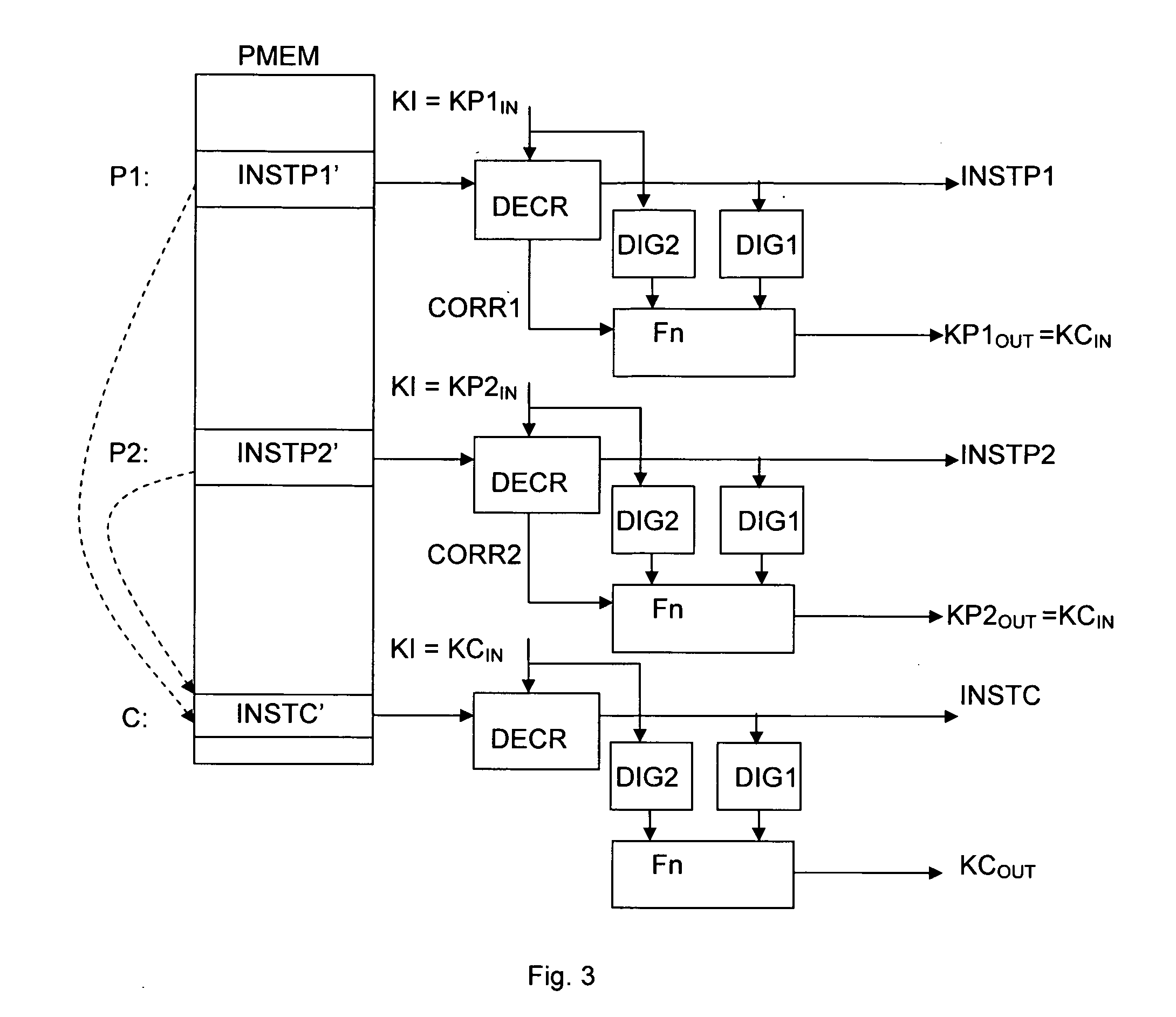
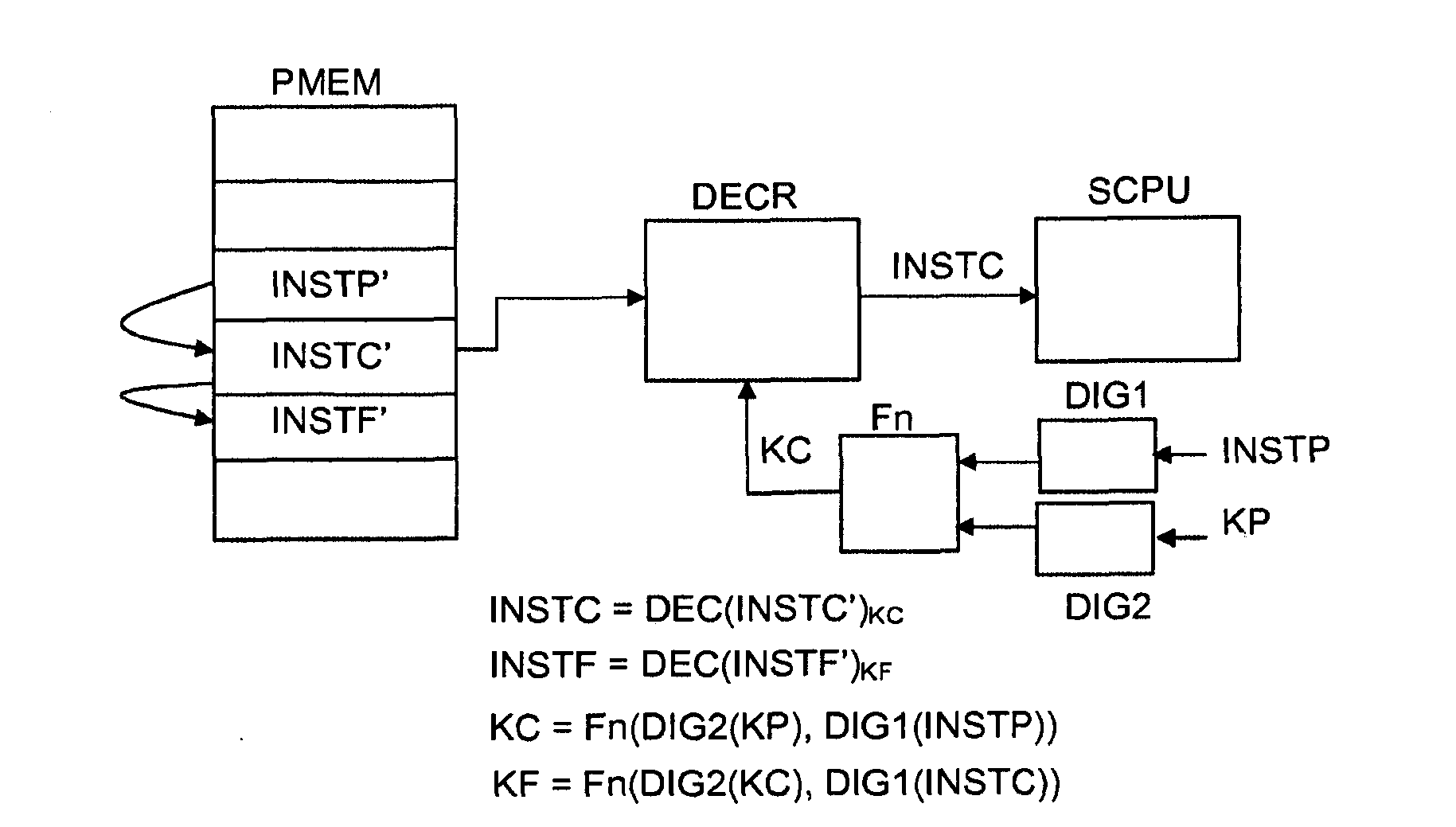
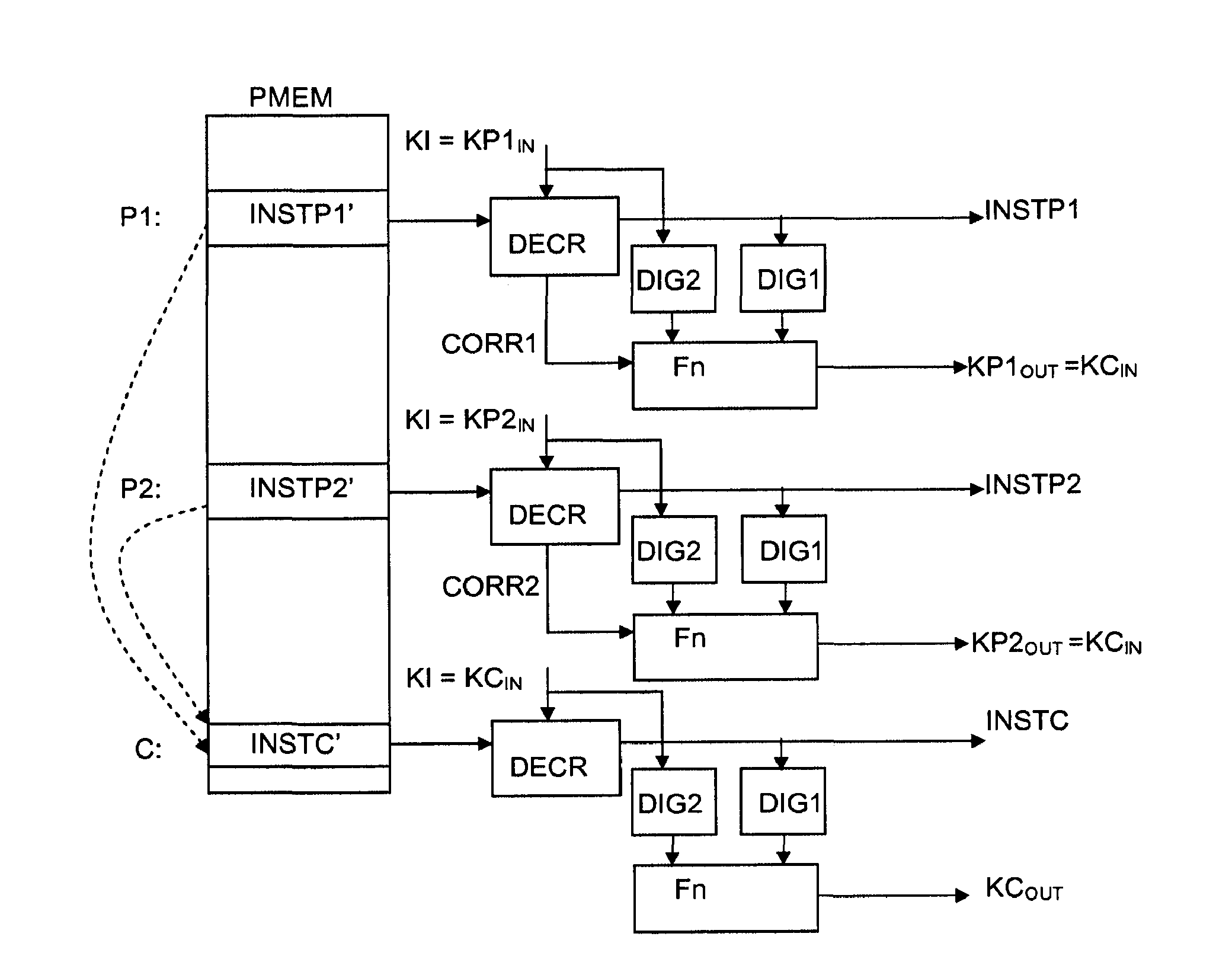
Processor-implemented method for ensuring software integrity
ActiveUS20110022854A1Rule out the possibilityMinimize overheadUnauthorized memory use protectionHardware monitoringThird partyComputer hardware
The present invention provides a solution to the problem of guaranteeing the integrity of software programmes by encrypting all or part of each instruction of a programme using a key based on all or part of one or a plurality of previous instructions, thus resulting in a different encryption key per instruction. The invention is applicable to software programmes whose structures are not necessarily tree-like in nature and is also applicable when the programme includes loops, jumps, calls or breaks etc. The invention allows for an exception to be flagged when an encrypted instruction is wrongly decrypted. There is no need for the first instruction to be in clear, since the instruction key may be appropriately initialised as required. The invention can be realised in software or entirely in hardware thereby eliminating the possibility of a third party intercepting a decrypted instruction or a decryption key.
Owner:NAGRAVISION SA
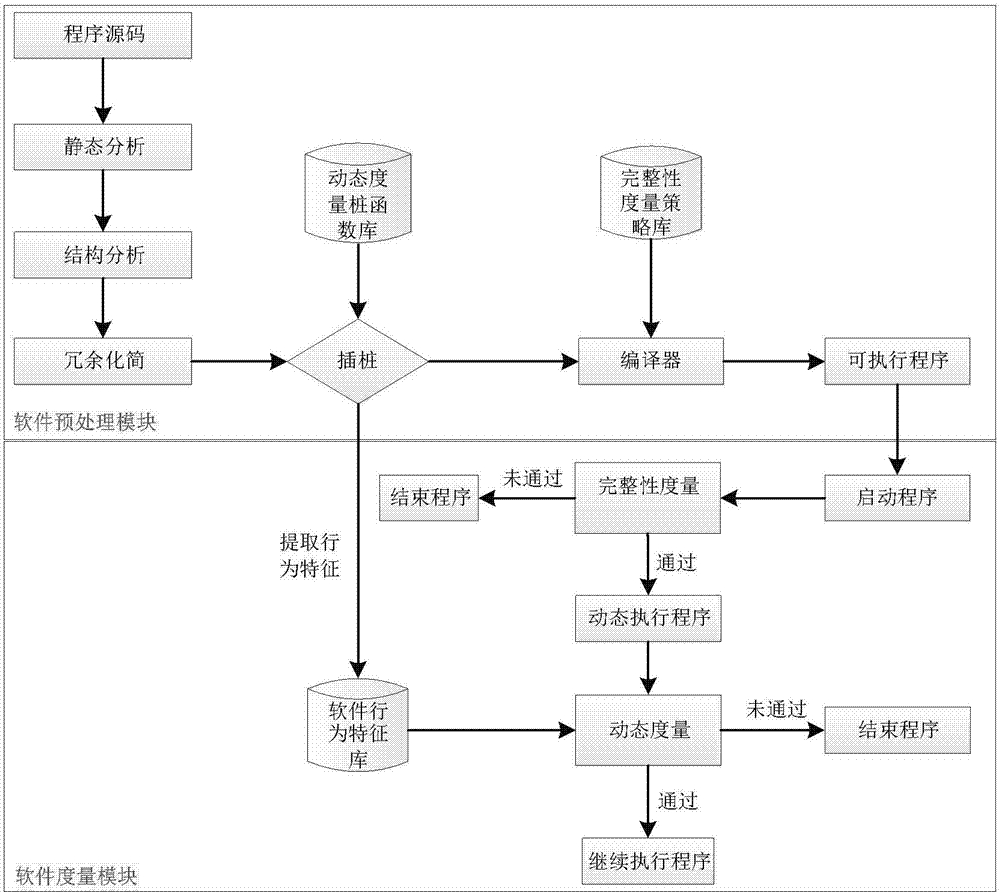
Software hybrid measure method based on trusted computing
ActiveCN104517057AAchieve securityImplement Active MetricsPlatform integrity maintainanceTheoretical computer scienceTrusted Computing
The invention relates to a software hybrid measure method based on trusted computing. The software hybrid measure method includes the steps: preprocessing software, analyzing and inserting program source codes, extracting behavior characteristics of the software, generating a software behavior characteristic library, embedding a software integrity measure strategy and generating an executable program to be measured; measuring the software, measuring integrity by a parallel optimization algorithm when starting the executable program to be measured according to the integrity measure strategy and the software behavior characteristic library, and dynamically measuring the executable program in real time in the running process. Static software measure and dynamic software measure can be simultaneously supported, software integrity measure and real-time dynamic behavior measure are combined by the aid of technologies such as parallel optimization, strategy embedding, inserting and system calling division, and the method has fine measure efficiency and low measure expenditure.
Owner:THE PLA INFORMATION ENG UNIV
Method of Maintaining Software Integrity
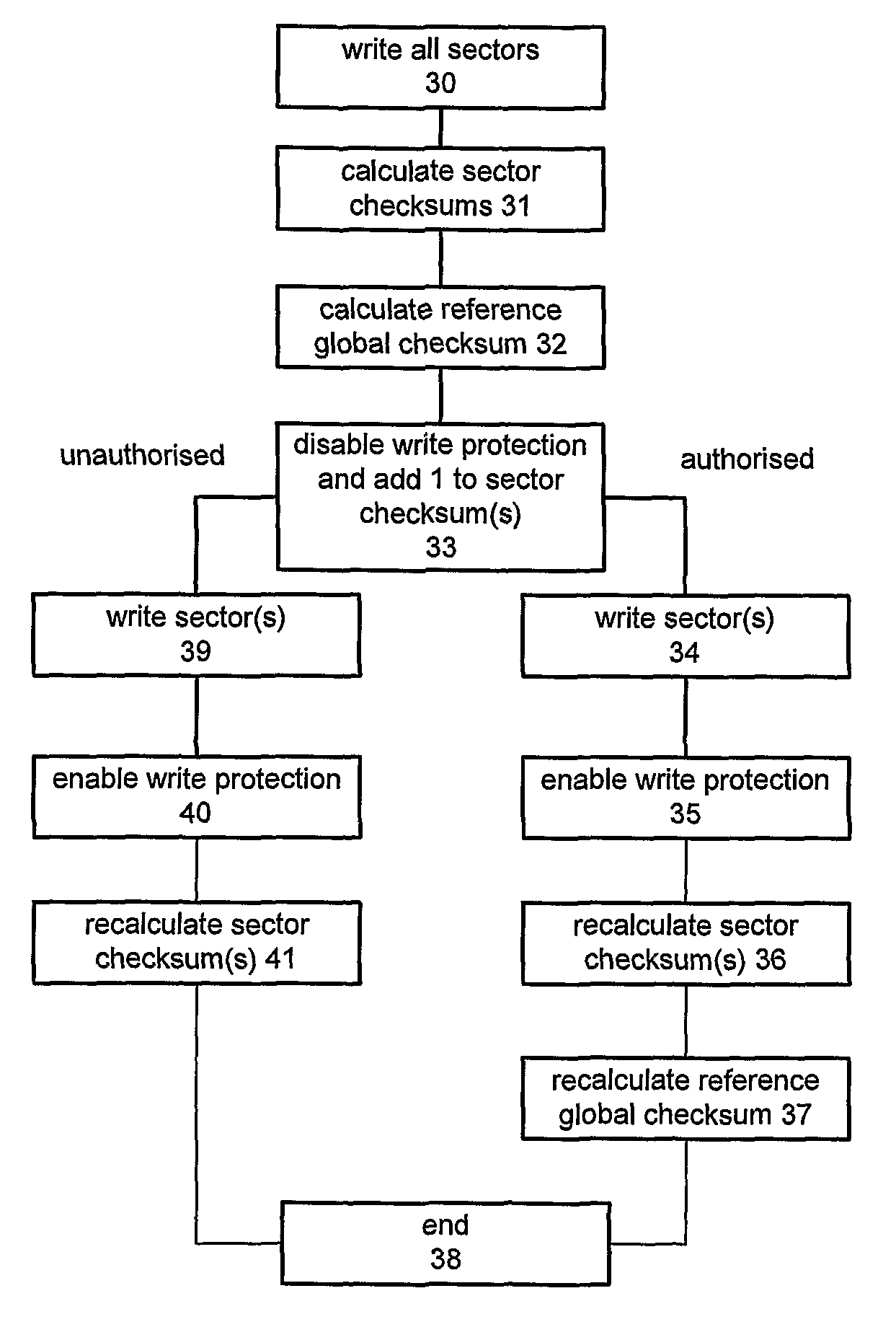
InactiveUS20090055656A1Difficult to calculateShorten the timeUnauthorized memory use protectionHardware monitoringComputer hardwareSoftware integrity
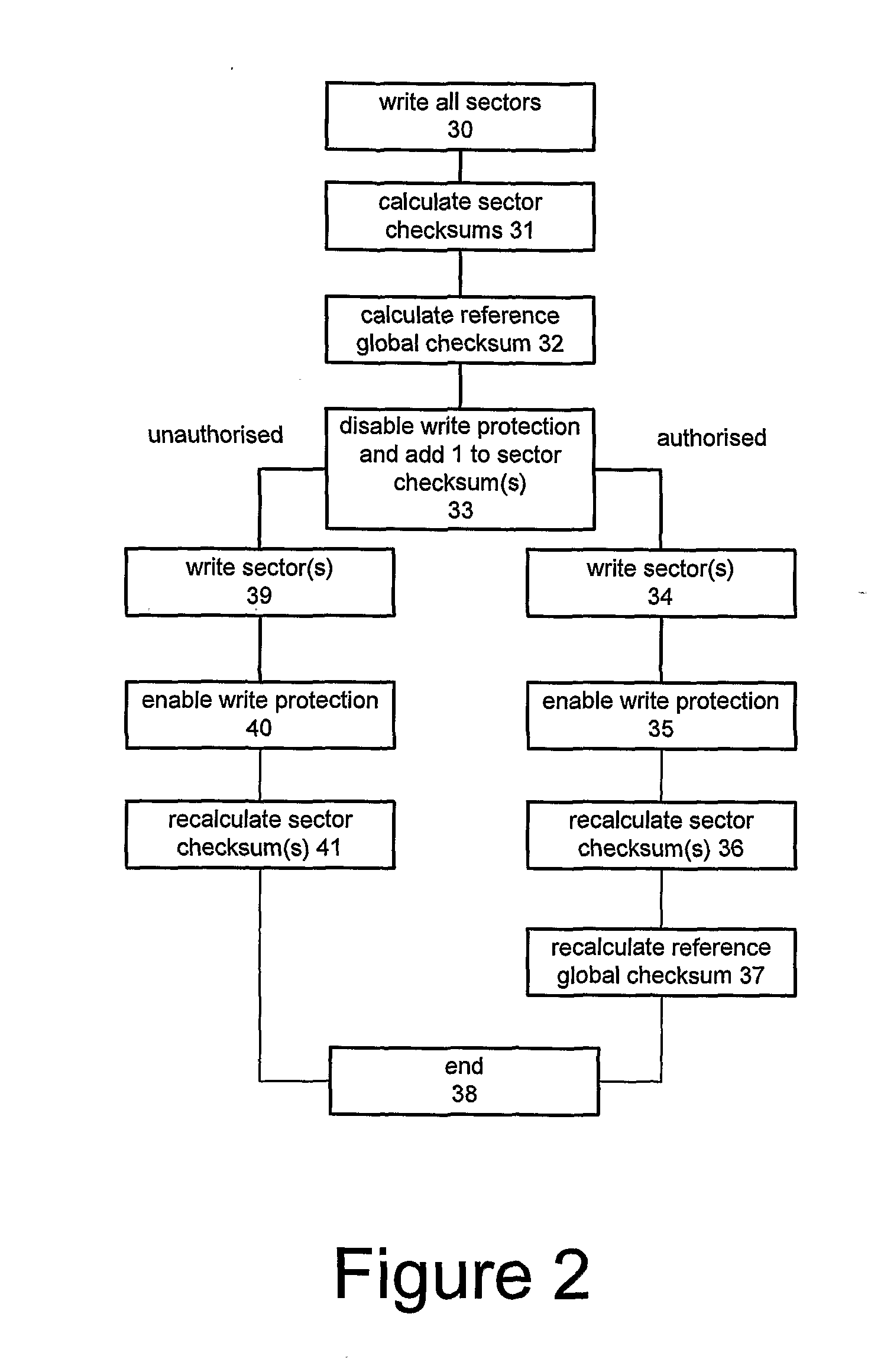
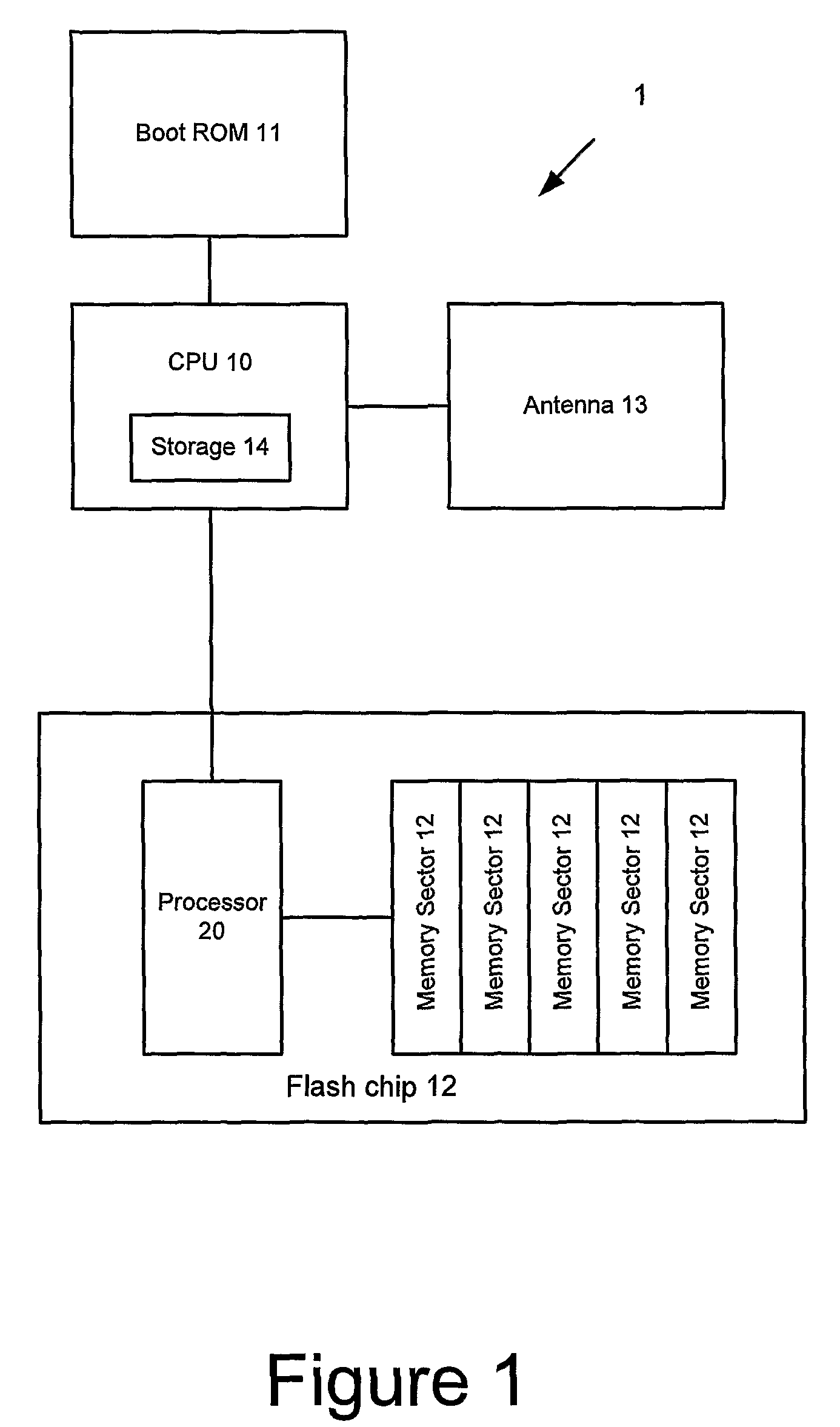
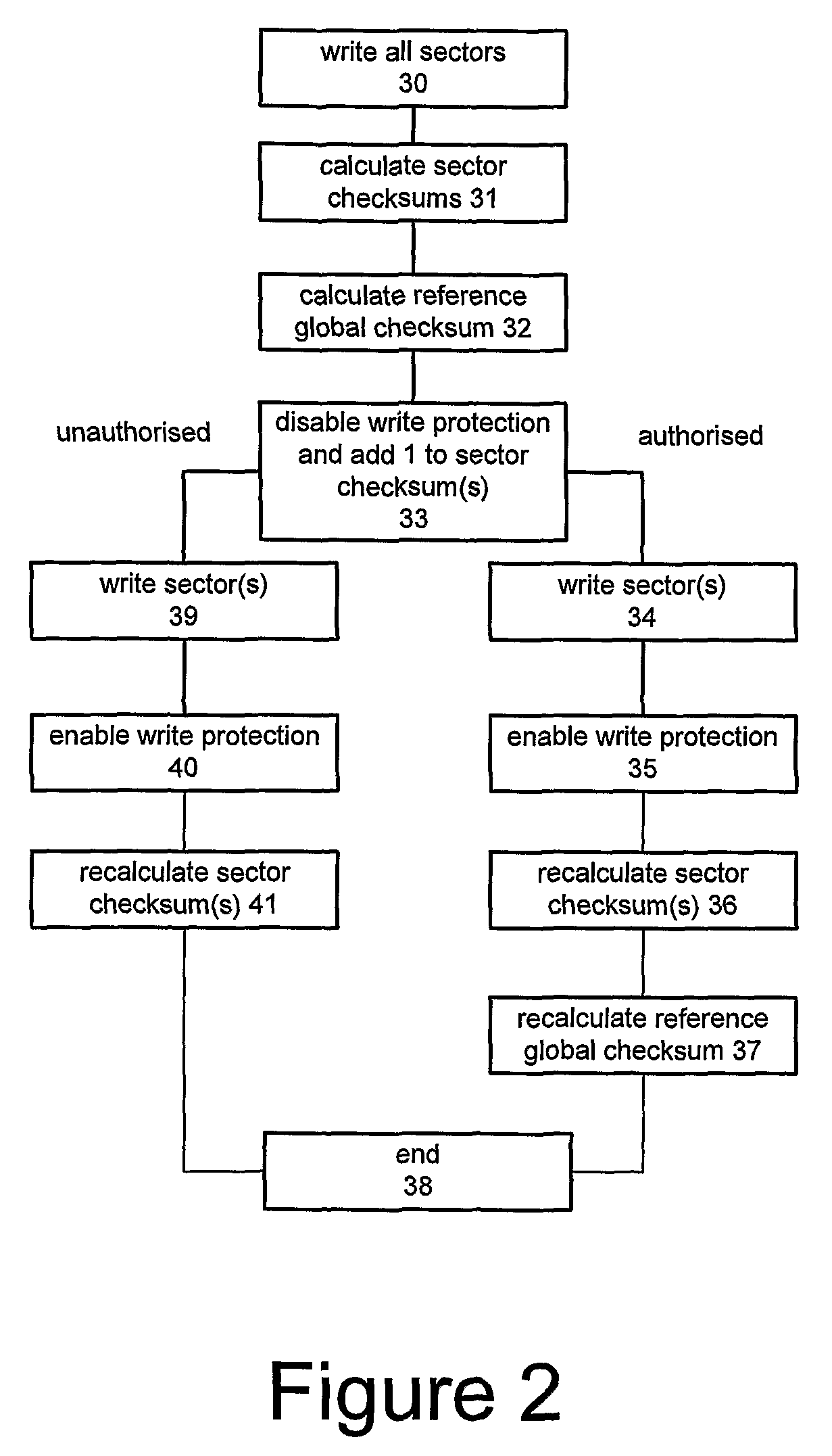
A method of maintaining the integrity of software stored in memory, the method comprising: storing an indicator associated with the memory; calculating a reference value from the stored indicator; storing the reference value; modifying the indicator when the software in the memory is modified; storing the modified indicator; recalculating the reference value from the modified indicator; storing the recalculated reference value; and verifying the integrity of the software by: retrieving the modified indicator; calculating an expected value from the modified indicator; and comparing the expected value with the recalculated reference value. Preferably the integrity of the software is verified without calculating an expected value from the software. The reference and expected values are typically calculated in accordance with a secret key.
Owner:MSTAR SEMICON PTE LTD +3
Systems and methods for distributing objects
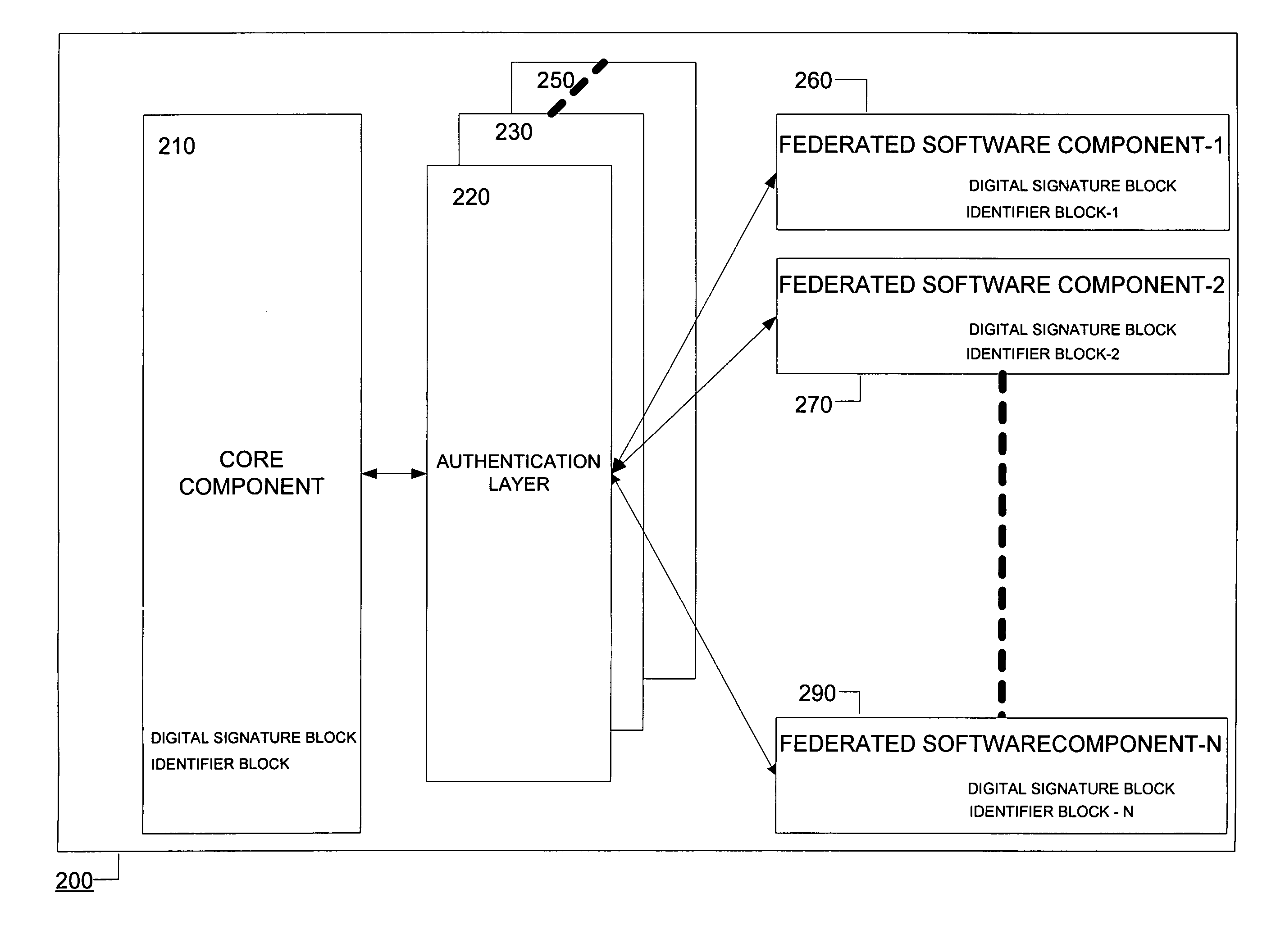
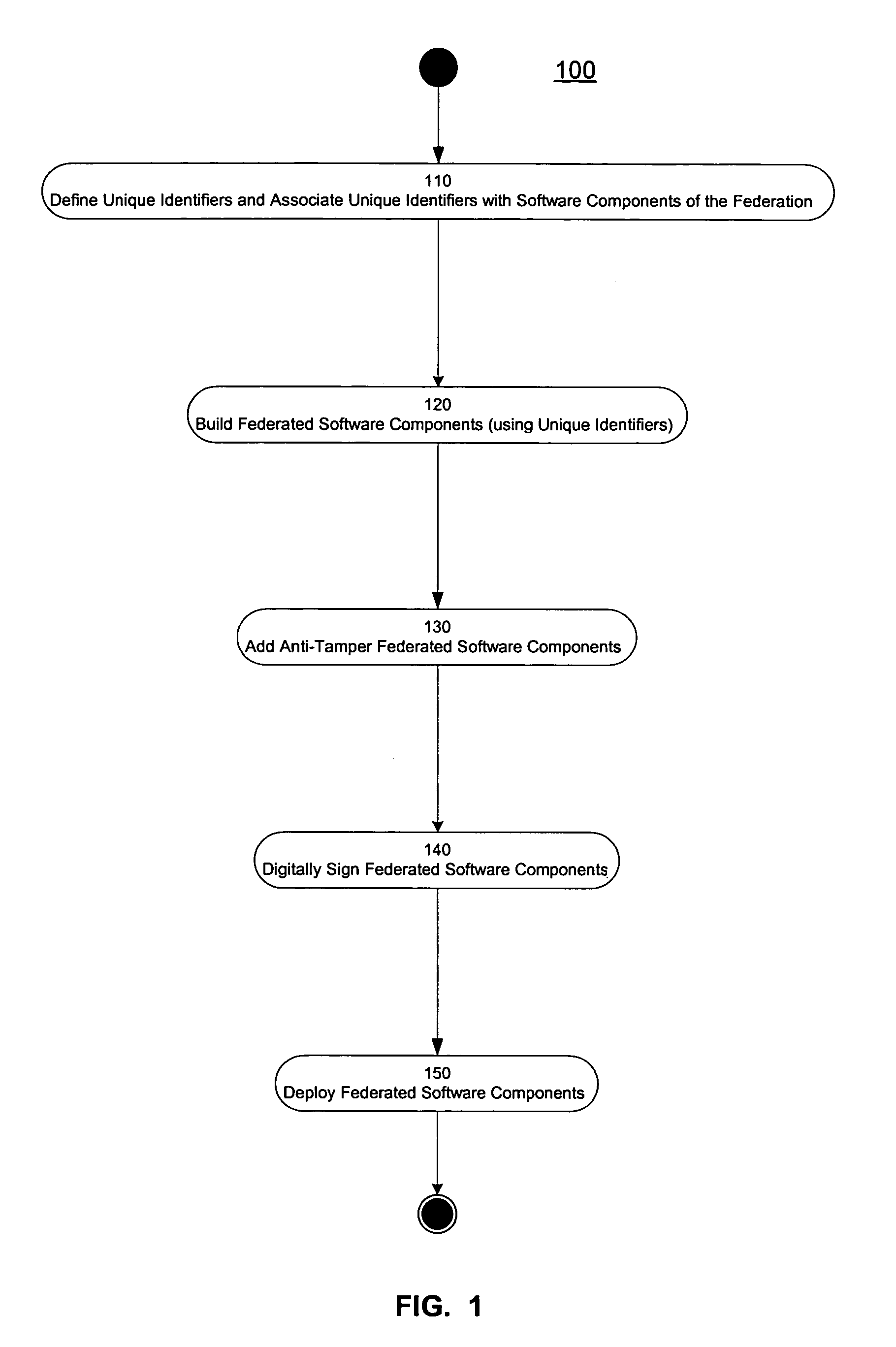
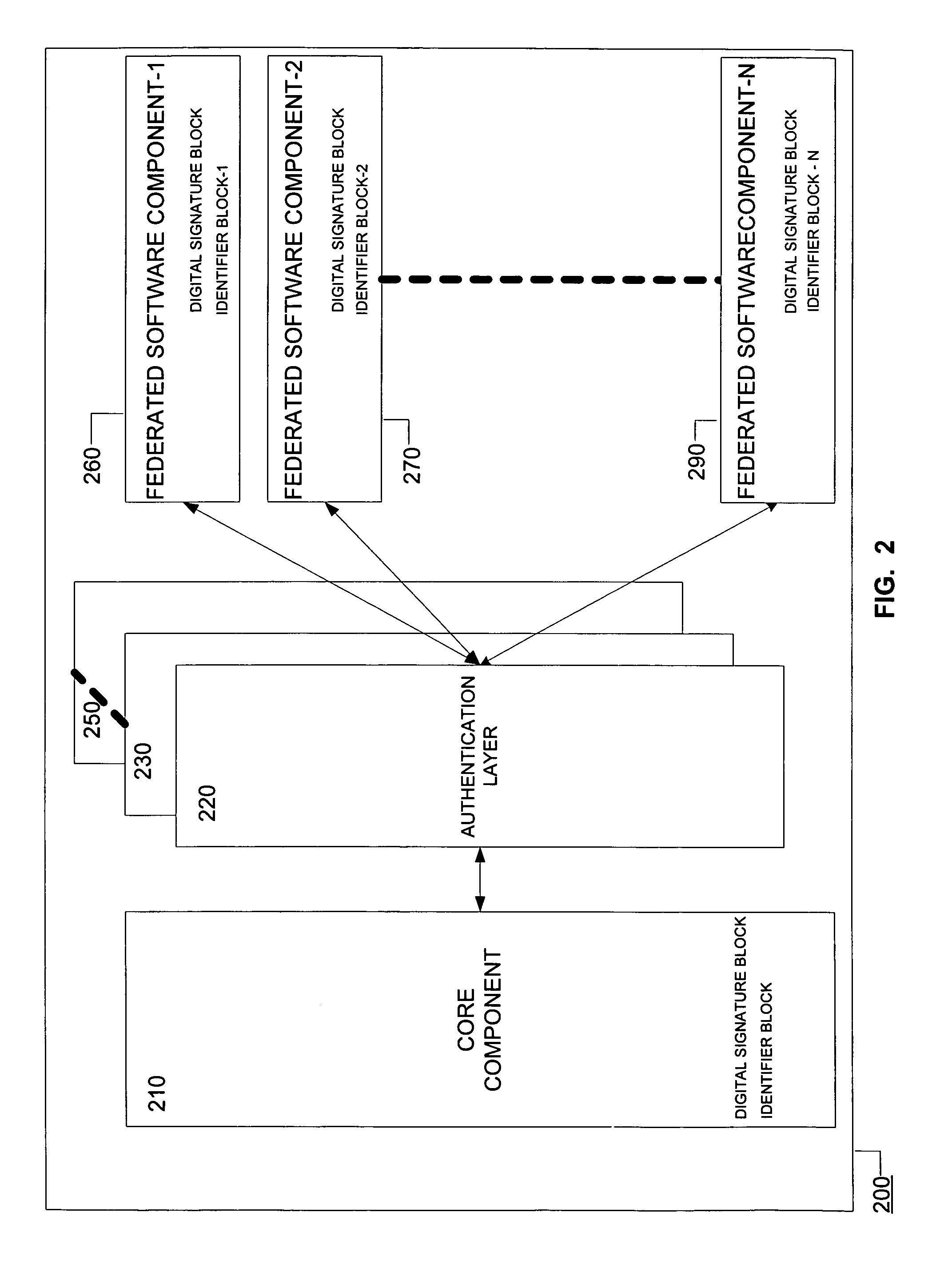
InactiveUS7392523B1Digital data processing detailsUser identity/authority verificationUnique identifierSoftware engineering
Systems and methods consistent with the present invention ensure software integrity by associating each software component to be included in a federation with a distinct unique identifier. A subset of the identifiers corresponding to any two software components should match for the federation to be accepted.
Owner:GEN DIGITAL INC
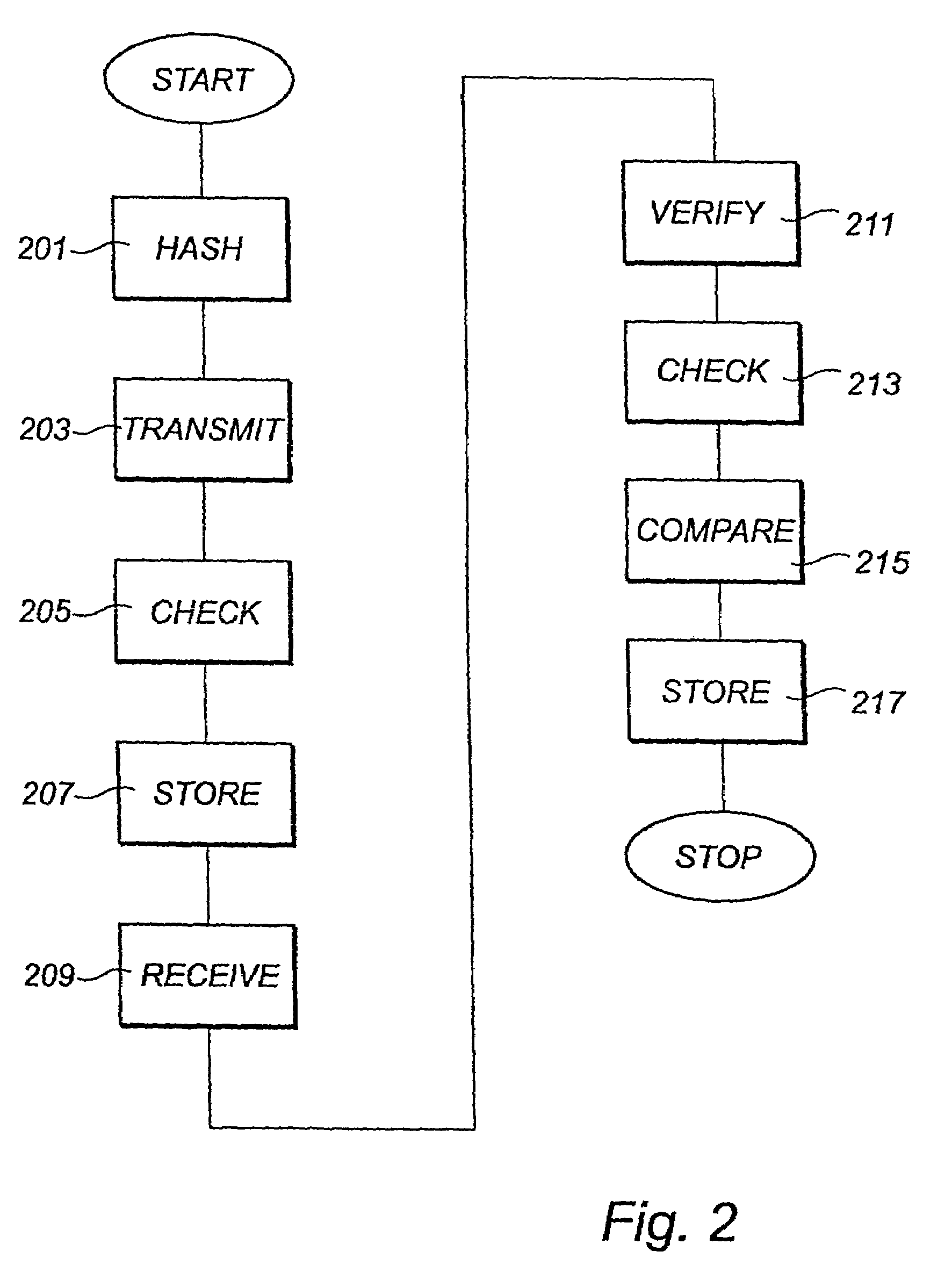
Software integrity test
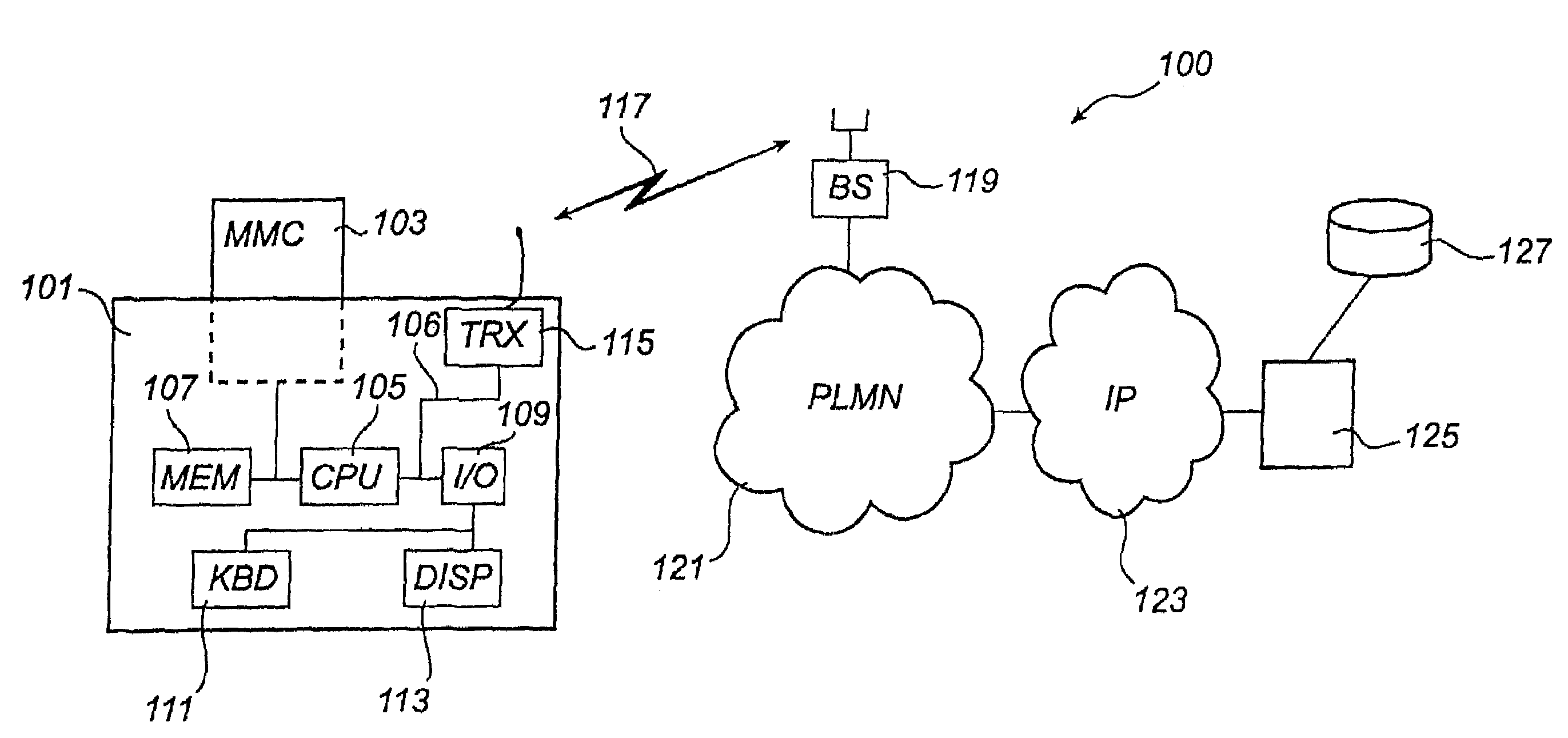
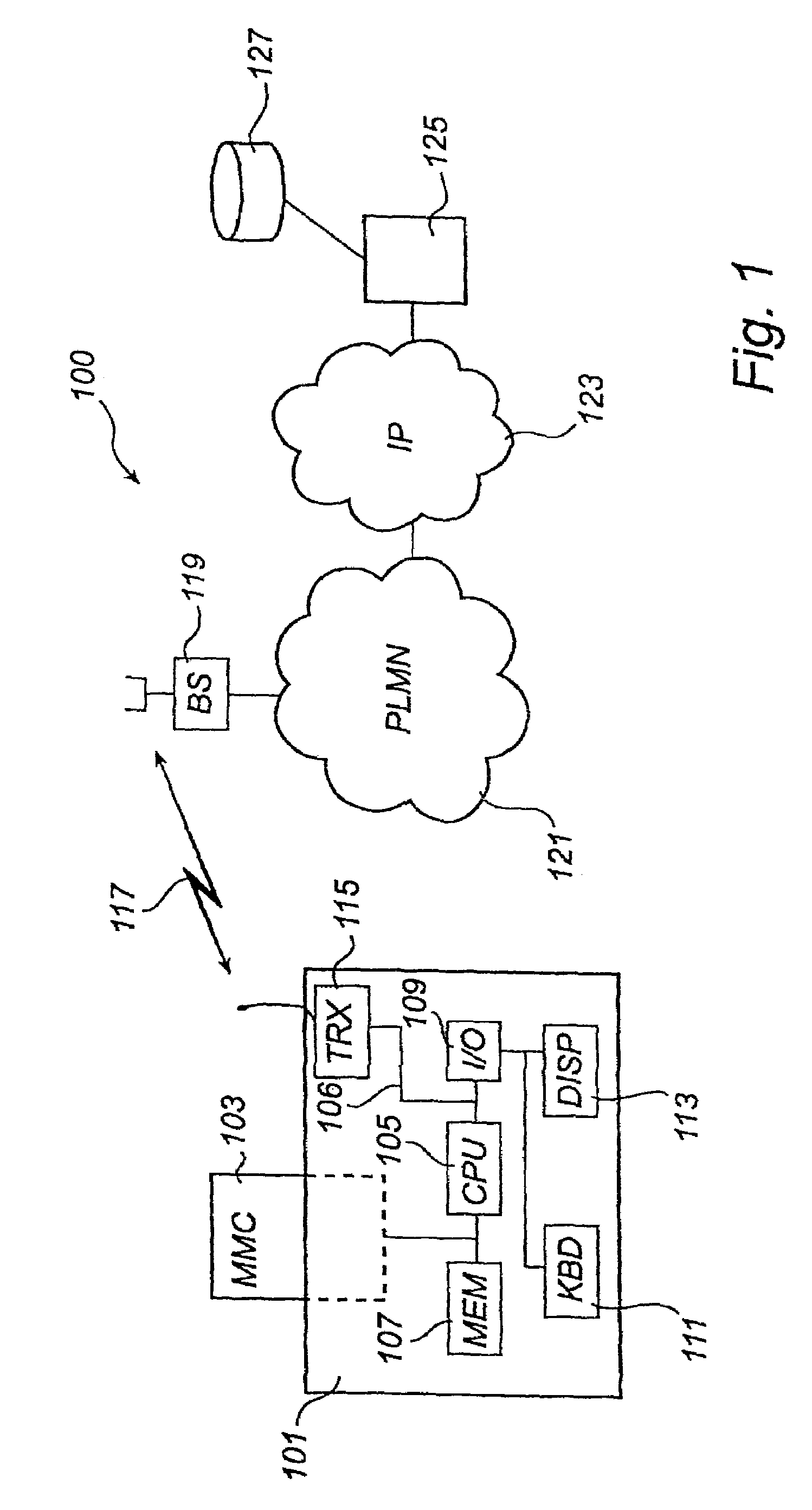
InactiveUS7437563B2Reliable copy protectionUnauthorised/fraudulent call preventionEavesdropping prevention circuitsDigital signatureRemovable media
Integrity checking of a software module to be used in a mobile communication terminal (101) is illustrated. The terminal (101) is capable of communicating in a mobile communication system (100) and the software module is stored on a removable memory unit (103) connected to the terminal (101). The terminal (101) communicates via the mobile communication system (100) with the software provider (125). During the communication a digitally signed data block comprising a reference value for use during integrity checking of said software module is received.
Owner:NOKIA TECHNOLOGLES OY
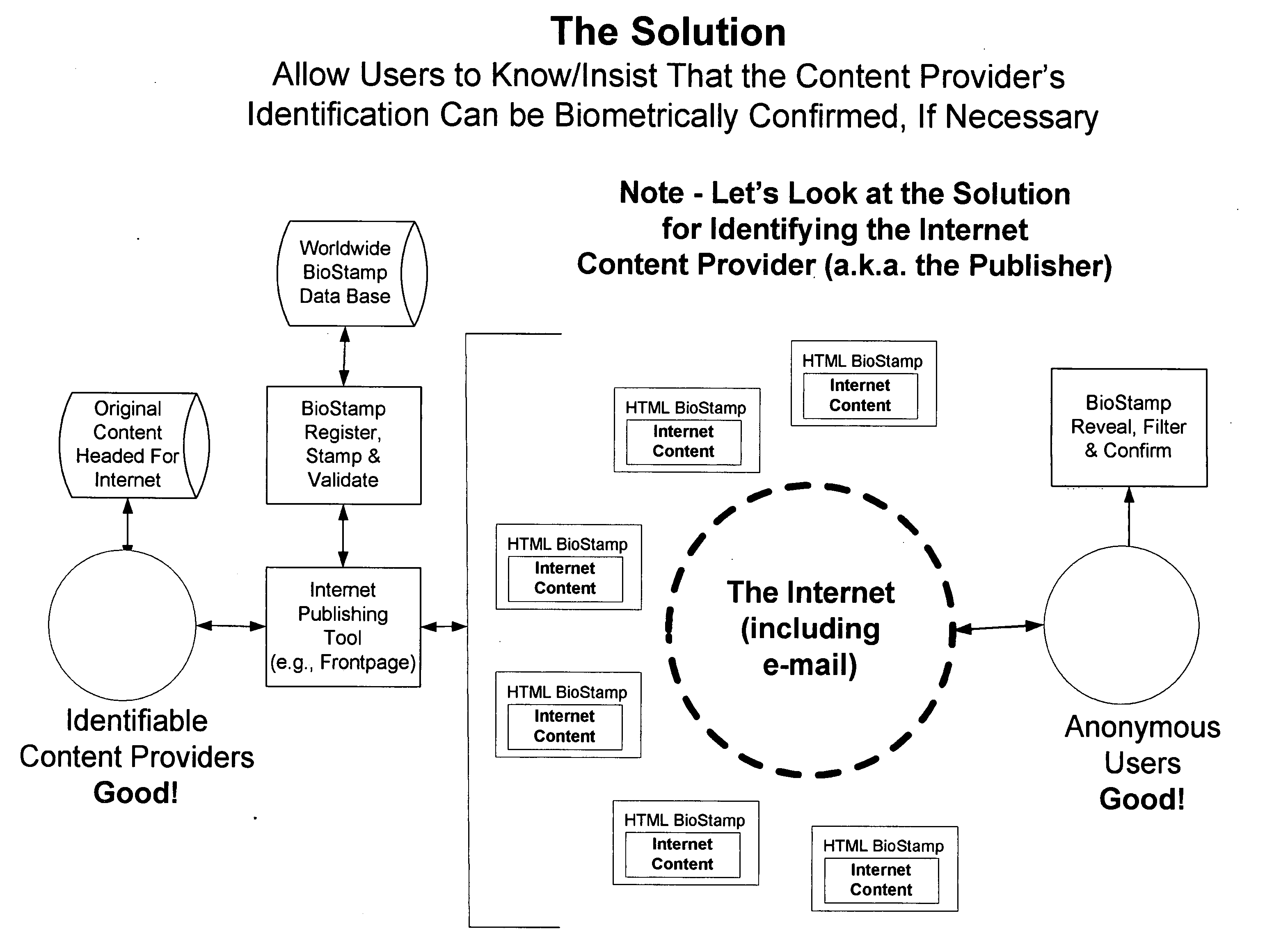
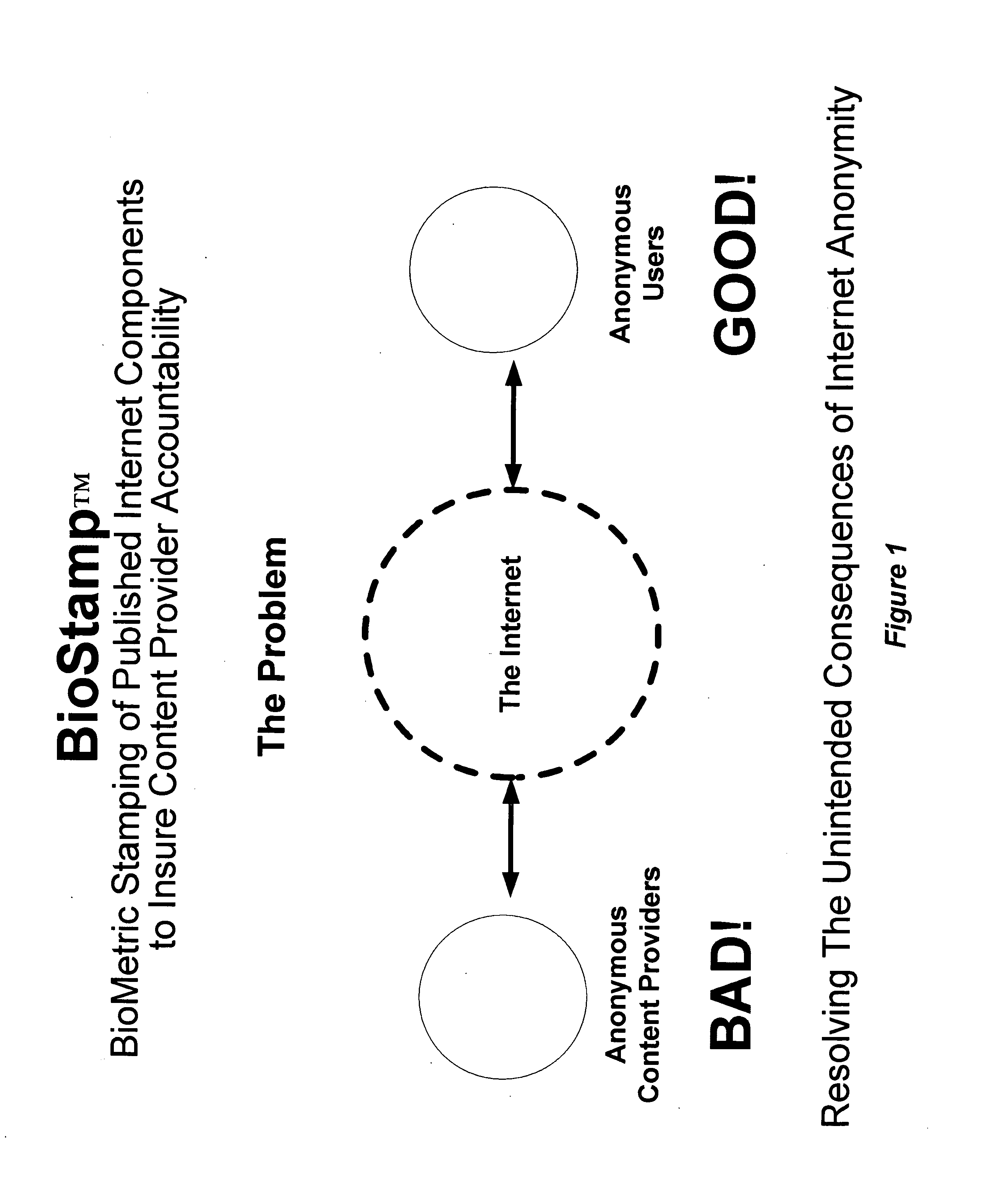
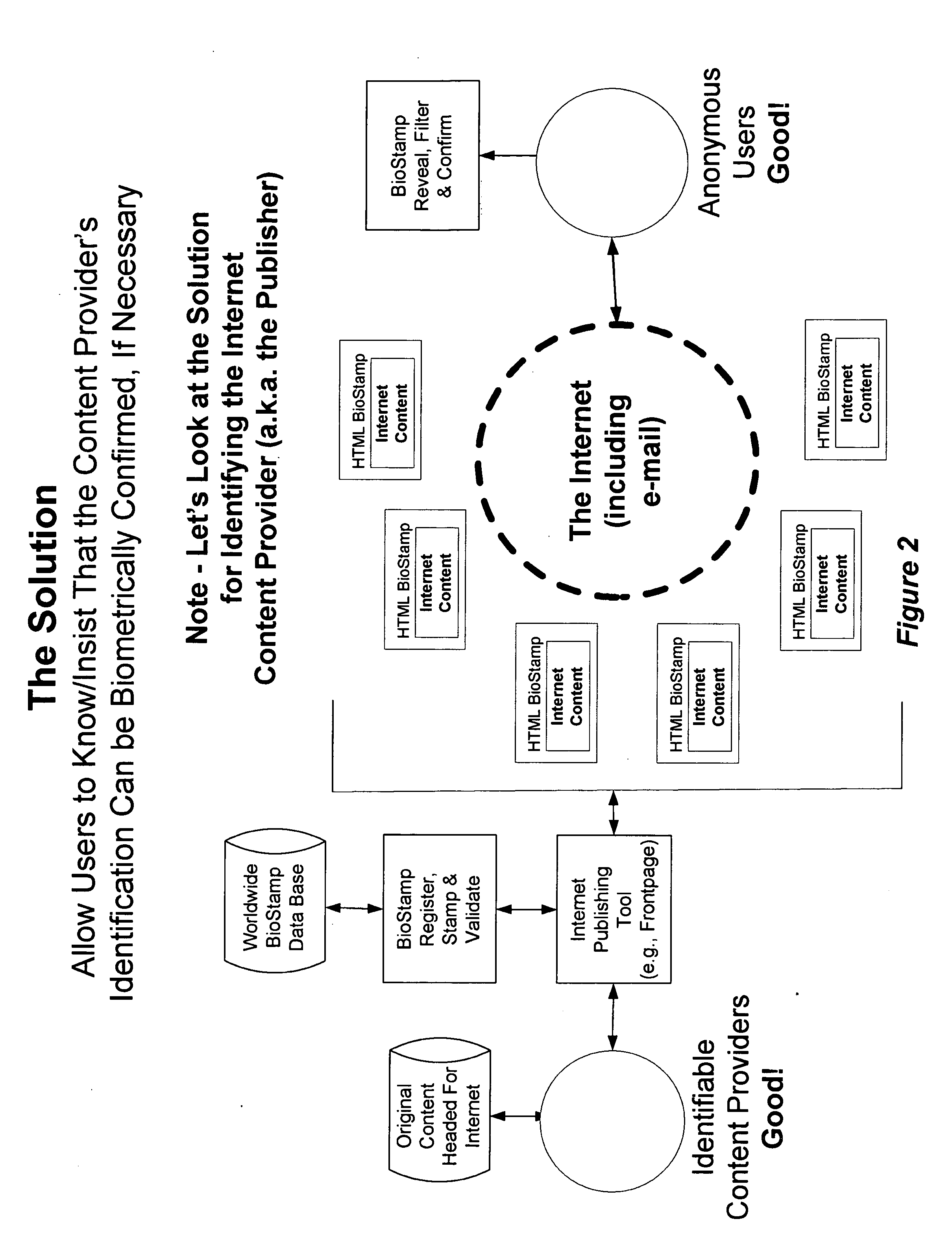
Method to improve the integrity of internet programs, websites and software
InactiveUS20070157321A1Improve integrityDigital data processing detailsUser identity/authority verificationIntellectual propertyThe Internet
The current invention is a method to improve the integrity of the internet programs, websites, and software, for example, by revealing the identity of the content provider. In particular, the method ensures the content provider's identity by requiring biometric input unique to the content provider creating a program which converts the biometric information into a unique identification number, for example, and incorporating the unique identification number into internet programs, software, websites, etc. for future reliability. The present invention allows users to know that the content provider's identification be biometrically confirmed, if necessary. It allows the content provider to further protect their intellectual property and to further identify themselves to others to demonstrate their skills.
Owner:PRIVACYDATASYST
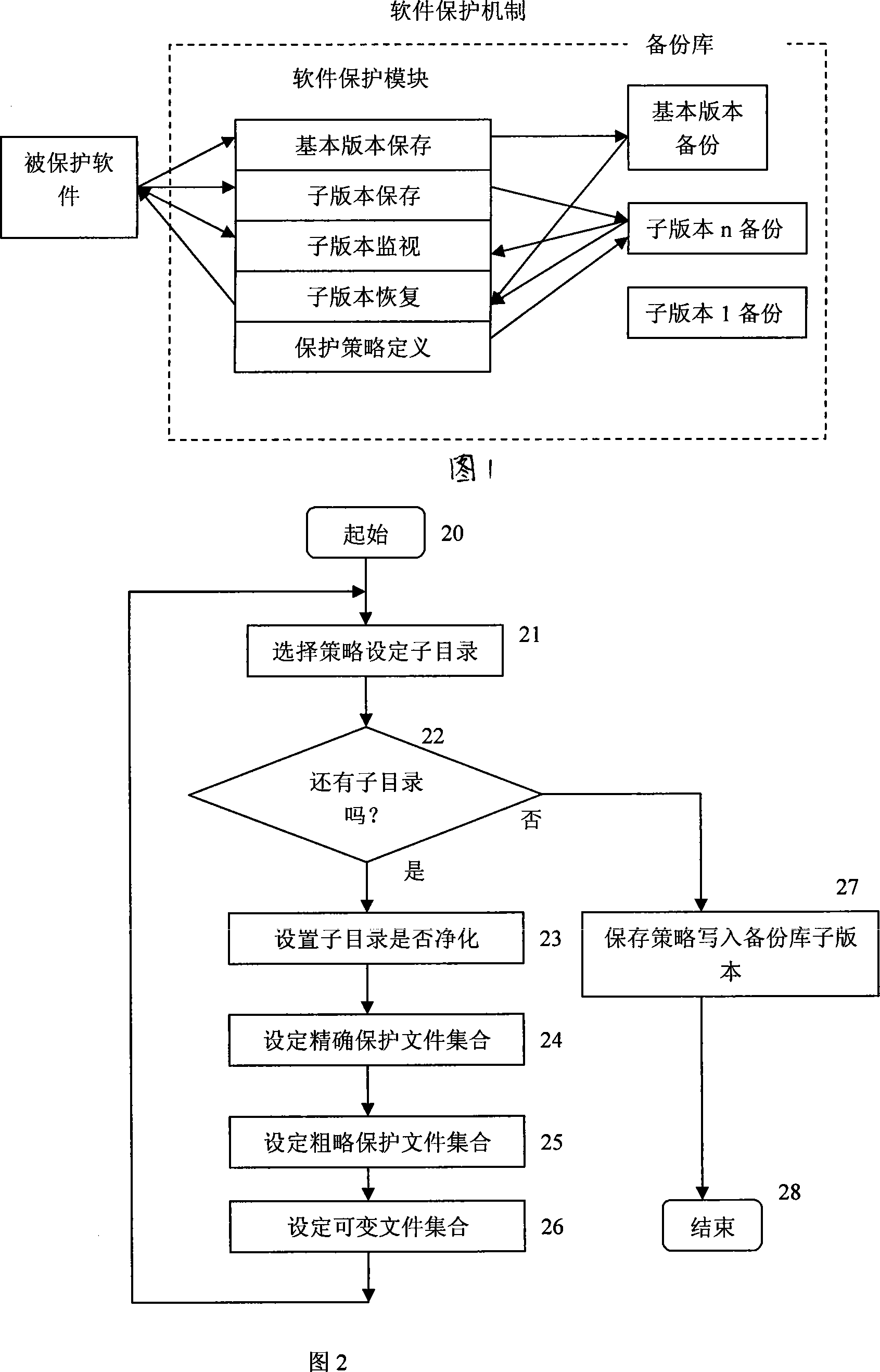
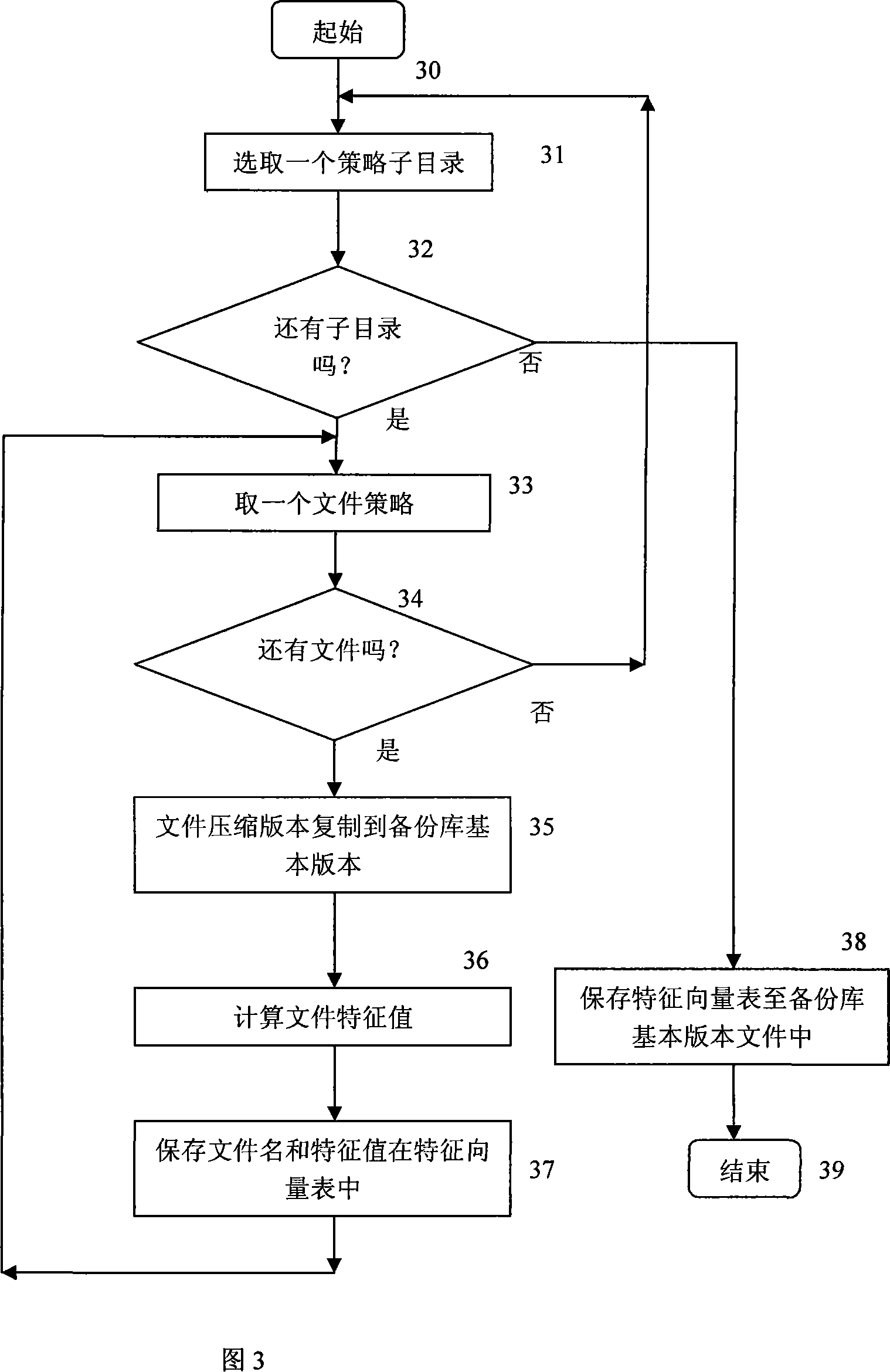
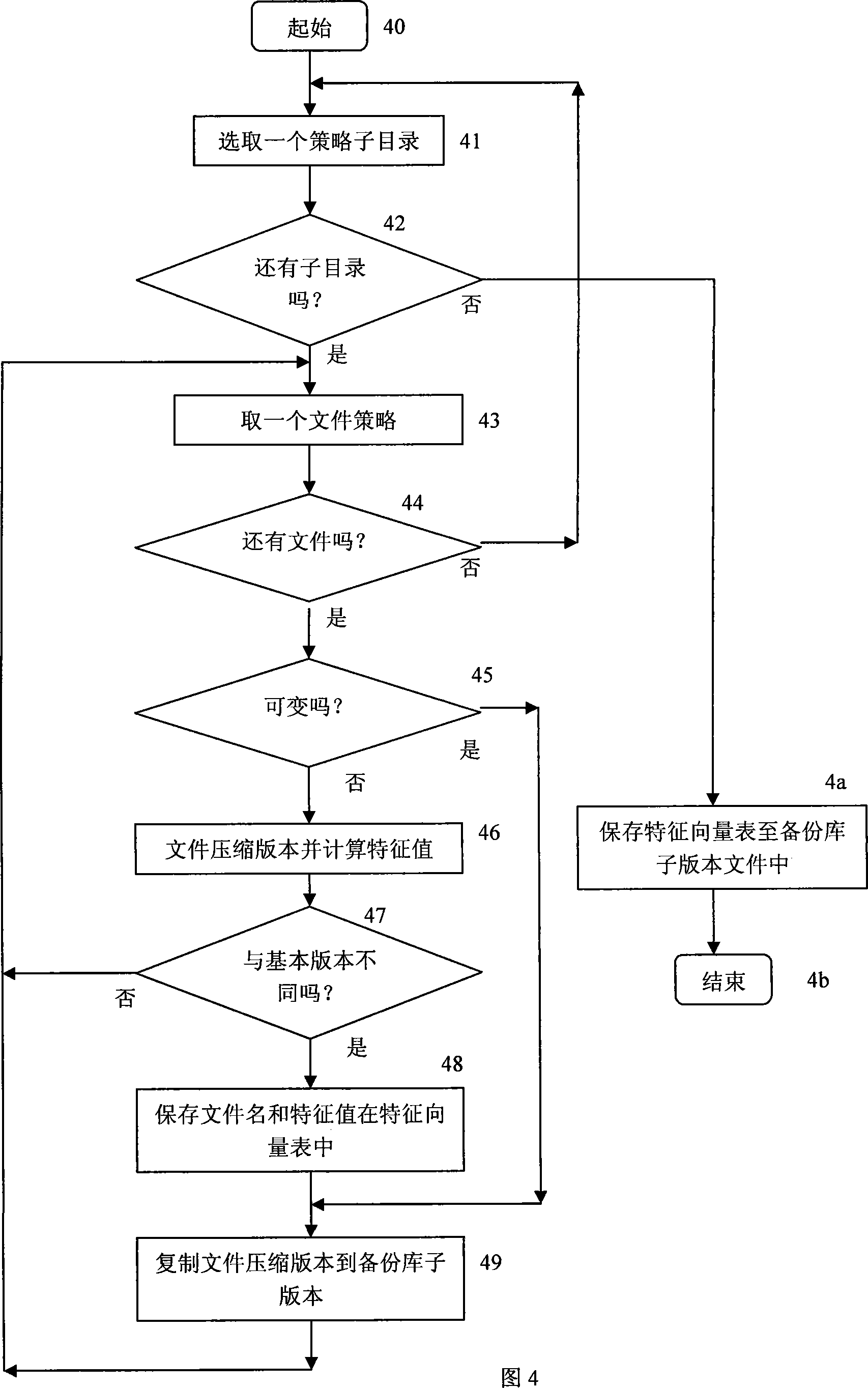
Software protection method based on version incremental backup
InactiveCN101174294AImprove integrityProgram/content distribution protectionSpecial data processing applicationsSoftware systemSoftware engineering
The invention relates to a method to protect the integrity of software based on the incremental backups of version, mainly comprising a plurality of procedures: (1) the definition of protection strategies on software version; (2) the initialization of basic software version; (3) the saving of software sub-version; (4) the surveillance and protection of software operation; (5) the recovery of software sub-version. Through the definition of the incremental backups of the basic version and subversion, the invention can adopt various protection methods to introduce purifying directory for the purpose of purifying the possible implanted files outside of the system according to the difference of the file functions and working modes. The invention has an advantage that the invention can not only protect the integrity of software system but also provide renewal function for software version.
Owner:NANJING UNIV
Method and system for verifying software completeness
InactiveCN101593259BImprove securityVersatilityPlatform integrity maintainancePathPingOperational system
The invention discloses a method for verifying software completeness. The method comprises the following steps: acquiring path of a loaded executable file through capturing system call of an upper operation system in a virtual machine monitor; acquiring a Hash value of the executable file according to the path of the executable file; comparing the Hash value of the executable file with software fingerprints in a fingerprint bank; and carrying out completeness verification on the executable file according to the result of fingerprint comparison. The invention also discloses a software completeness verification system. The method and the system for software completeness verification realize software completeness verification in the virtual monitor, is independent of the operation system without depending on completeness of the operation system, improves security of the system, and has universality and compatibility. The technical proposal belongs to completeness verification of softwarein loading period, reduces verification cost without support of auxiliary hardware, reduces cost and improves performance compared with the method for verifying completeness of a file system.
Owner:BEIHANG UNIV
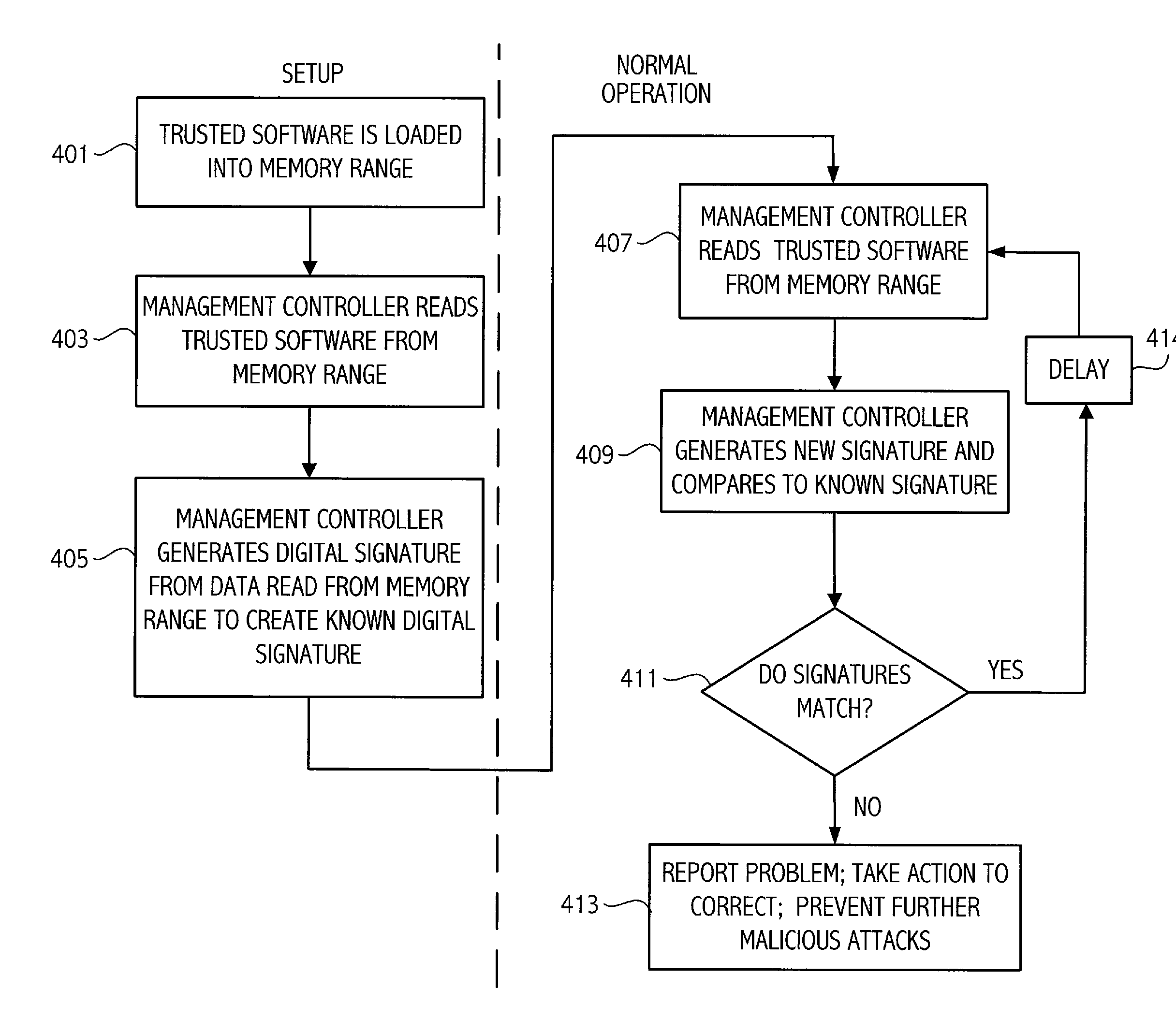
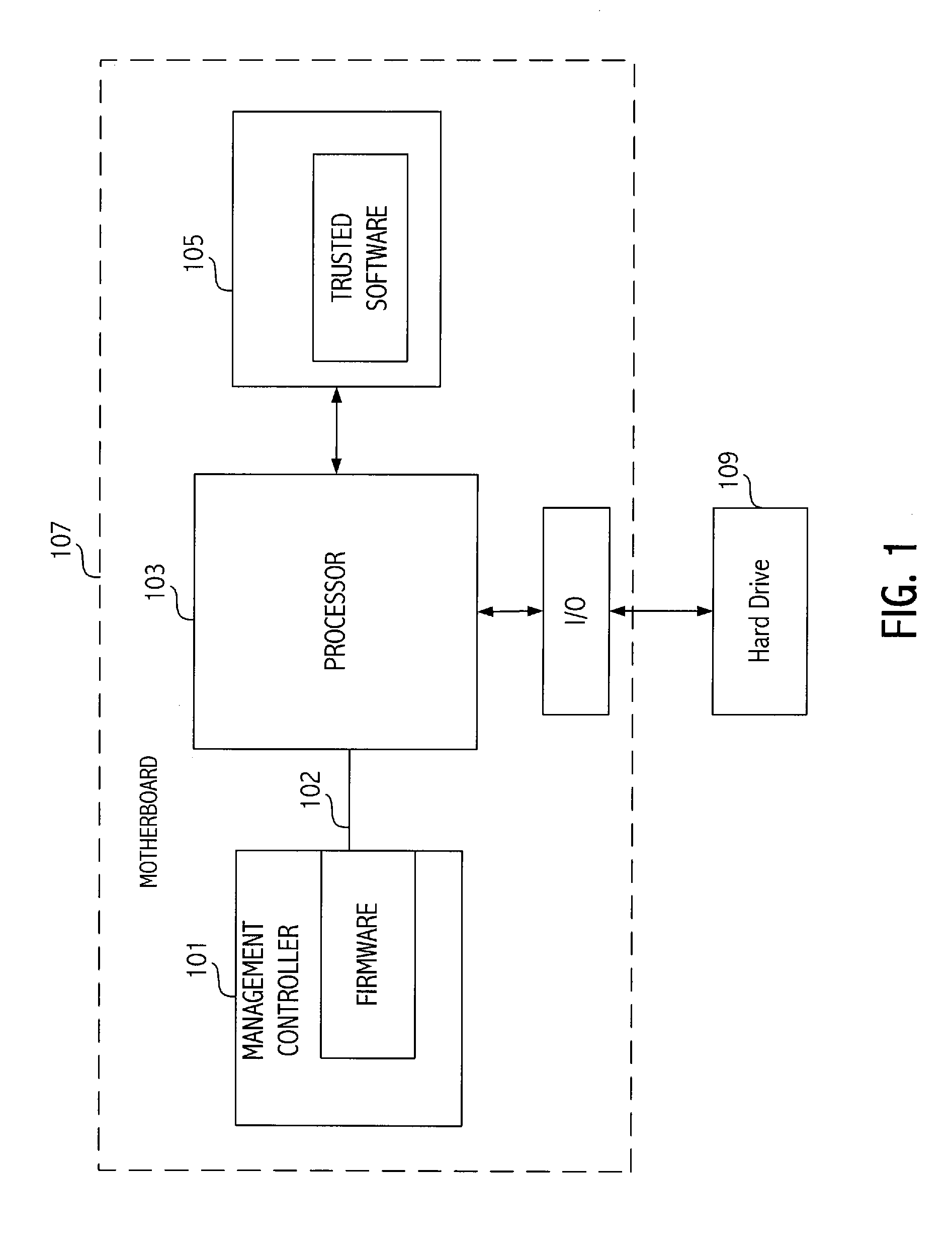
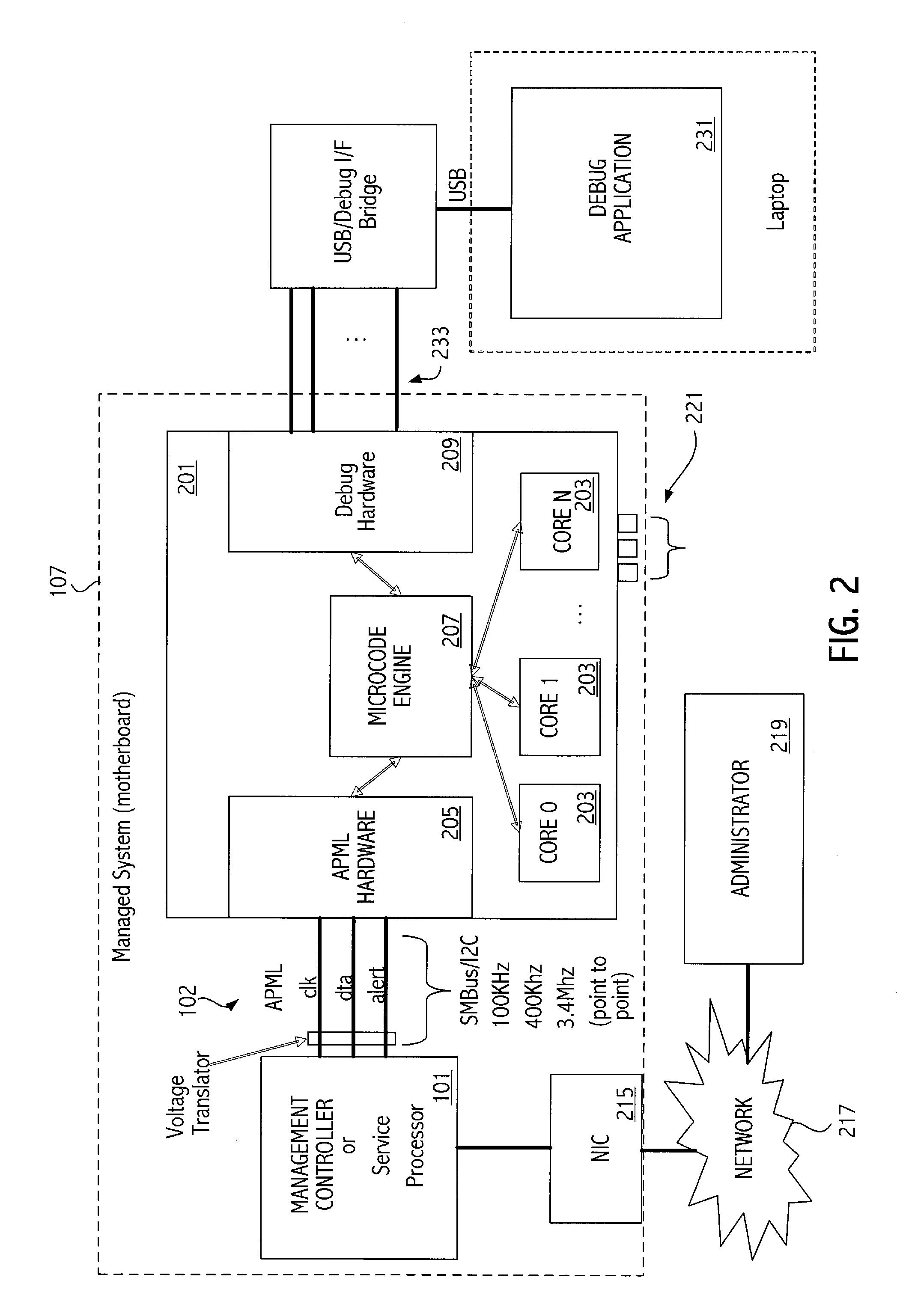
Sideband access based method and apparatus for determining software integrity
InactiveUS20090144332A1Improve reliabilityImprove securityComputer security arrangementsMemory systemsDigital signaturePosition dependent
A management controller supplies a processor with a command via a sideband interface on the processor. Responsive to the command, the processor reads storage locations accessible by the processor and supplies the contents of the storage locations to the management controller via the sideband interface. The management controller then evaluates the integrity of software associated with the storage locations by comparing a digital signature associated with the software to a known digital signature.
Owner:ADVANCED MICRO DEVICES INC
A processor-implemented method for ensuring software integrity
ActiveCN102959556AReduce the possibilityInternal/peripheral component protectionPlatform integrity maintainanceComputer hardwareThird party
The present invention provides a solution to the problem of guaranteeing the integrity of software programmes by encrypting all or part of each instruction of a programme using a key based on all or part of one or a plurality of previous instructions, thus resulting in a different encryption key per instruction. The invention is applicable to software programmes whose structures are not necessarily tree-like in nature and is also applicable when the programme includes loops, jumps, calls or breaks etc. The invention allows for an exception to be flagged when an encrypted instruction is wrongly decrypted. There is no need for the first instruction to be in clear, since the instruction key may be appropriately initialised as required. The invention can be realised in software or entirely in hardware thereby eliminating the possibility of a third party intercepting a decrypted instruction or a decryption key.
Owner:NAGRAVISION SA
Autonomous software integrity checker
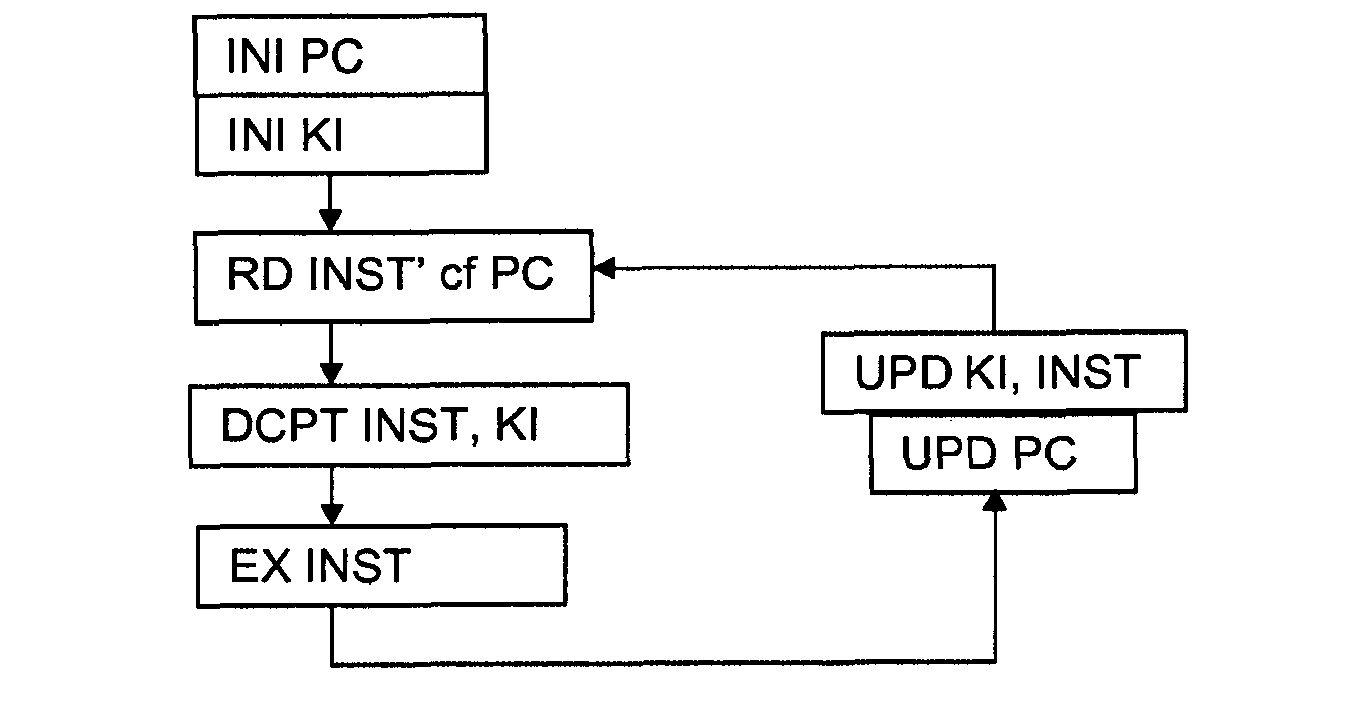
ActiveUS7707638B2Prone to hackingCannot be hackedDigital data processing detailsUnauthorized memory use protectionApplication softwareMaster processor
A semiconductor integrated circuit includes a processor for executing application code from a memory and a verifier processor arranged to receive the application code via the same internal bus as the processor. The verifier processor performs a verification function to check that the application code is authentic. The verifier processor runs autonomously and cannot be spoofed as it receives the application code via the same internal bus as the main processor.
Owner:STMICROELECTRONICS LTD
Method and apparatus for software integrity protection using timed executable agents
A method and apparatus are disclosed for evaluating the security of at least one client. An executable program is executed by the client being evaluated. A result is received from the executable program, and an evaluation of the result indicates whether the client has been corrupted. The executable program is one of a plurality of possible programs. The result may be evaluated based on an elapsed time between when the executable program is provided to the client and when the result is received. The executable program may include at least one function that writes to a memory of the client. A program blinding technique is also disclosed to generate executable programs.
Owner:WSOU INVESTMENTS LLC
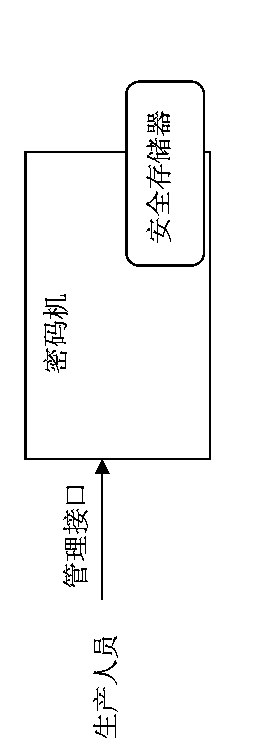
Safety protection method of software integrity of cryptographic machine
InactiveCN103873238AGuaranteed integrityAvoid compromising reliabilityPublic key for secure communicationUser identity/authority verificationByteSoftware integrity
The invention discloses a safety protection method of the software integrity of a cryptographic machine, and relates to the technical field of information safety codes. The safety protection method of the software integrity of the cryptographic machine is characterized by comprising the first step of generating check codes of the software integrity, wherein production personnel send a generation instruction of the check codes of the software integrity to the cryptographic machine through an external management interface, the cryptographic machine transmits byte streams of all software codes, firmware and property files inside the cryptographic machine to a safety storage, and the safety storage carries out check code calculation on the input byte streams to obtain the check codes of the software integrity; the second step of checking the software integrity, wherein the cryptographic machine is started, the cryptographic machine transmits the byte streams of all software codes, the firmware and the property files inside the cryptographic machine to the safety storage for check code calculation, the safety storage judges whether the newly calculated check codes of the software integrity and the check codes, on the safety storage, of the software integrity are uniform or not, if yes, the cryptographic machine starts to work, and if not, the cryptographic machine stops starting.
Owner:中电科网络安全科技股份有限公司
Software part validation using hash values
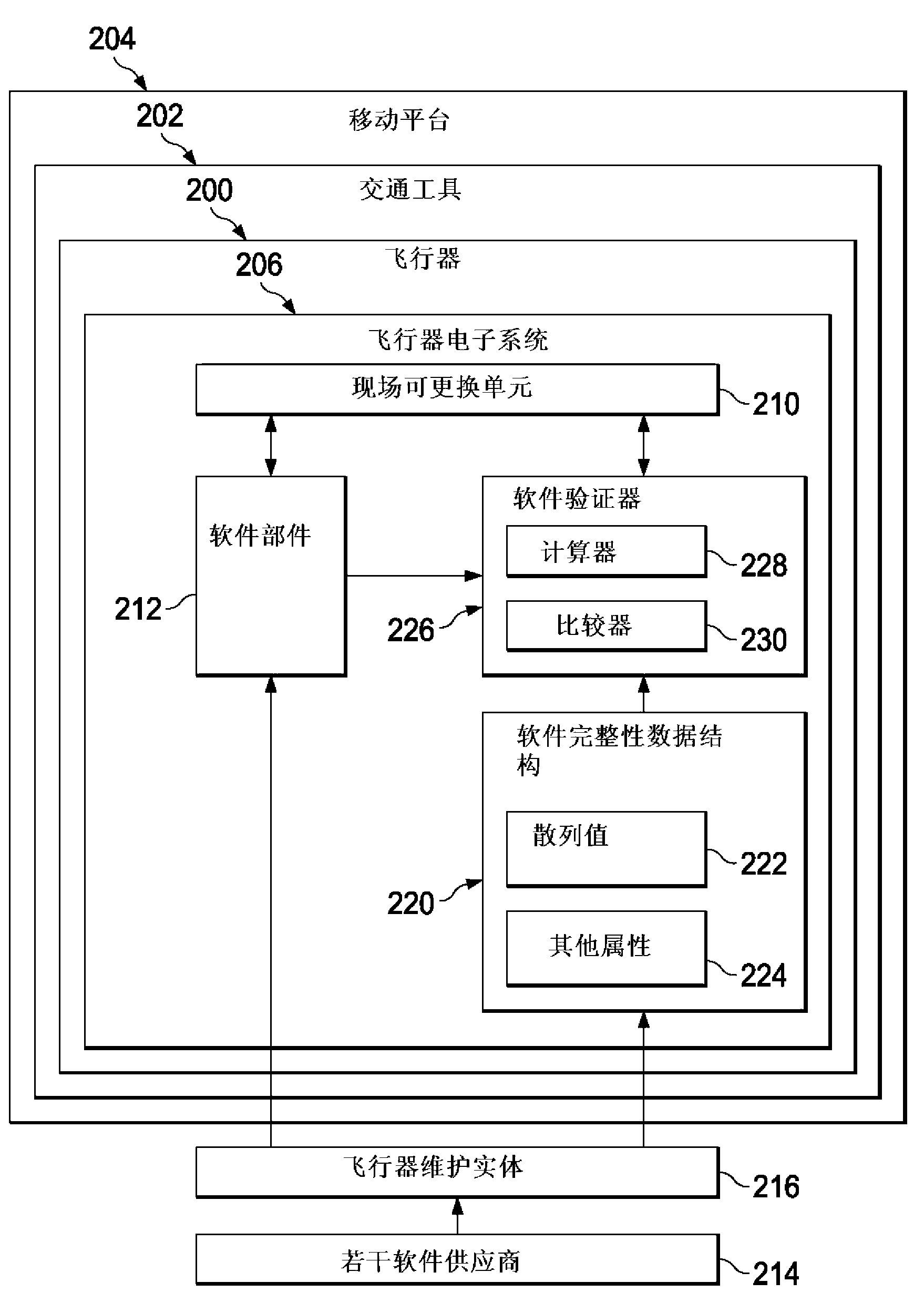
InactiveCN102915412ADigital data protectionProgram/content distribution protectionComputer hardwareHash table
A system and method for validating software parts on an aircraft is disclosed. A first hash value is calculated for a software part on the aircraft. A determination is made on the aircraft as to whether the first hash value matches a second hash value from a software integrity data structure stored on the aircraft. The software integrity data structure comprises the hash values that are not determined on the aircraft for the software parts used by the aircraft. A validation status is provided based on whether the first hash value matches the second hash value. An operation is performed on the software part on the aircraft only if the first hash value matches the second hash value.
Owner:THE BOEING CO
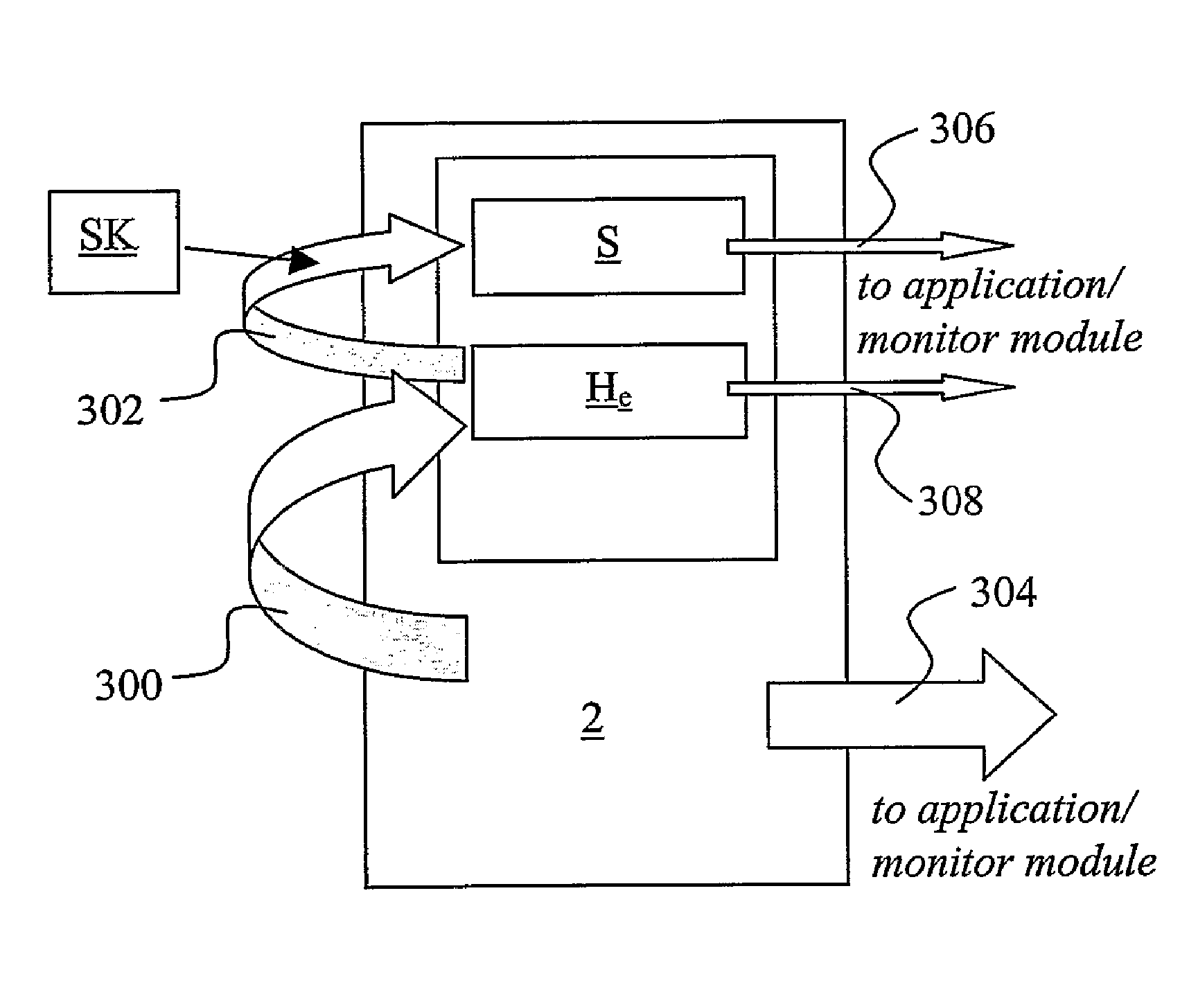
Method and device for verifying the integrity of platform software of an electronic device
ActiveUS20150019872A1The method is simple and reliableSuitable for storageUser identity/authority verificationComputer security arrangementsComputer moduleSoftware modules
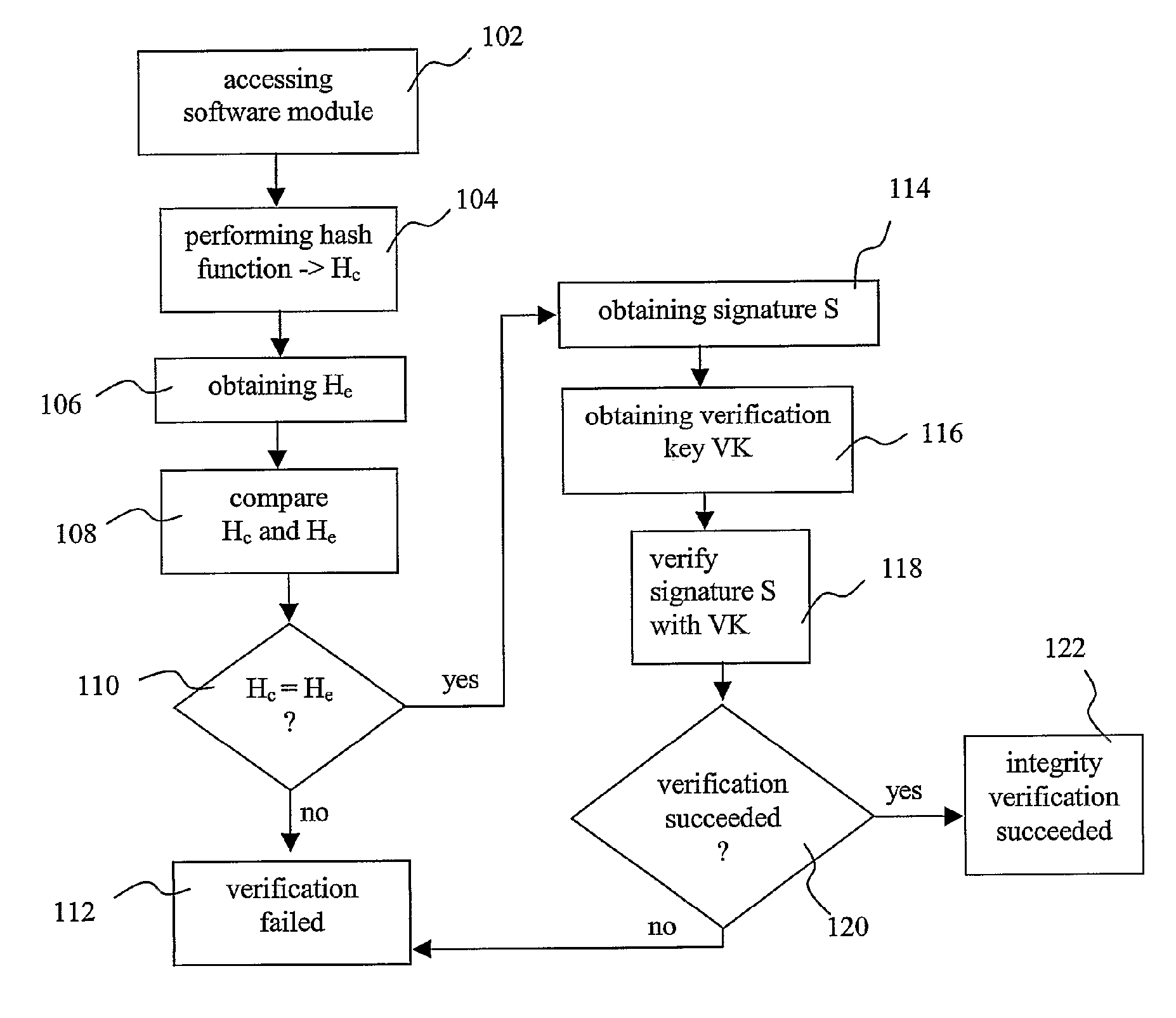
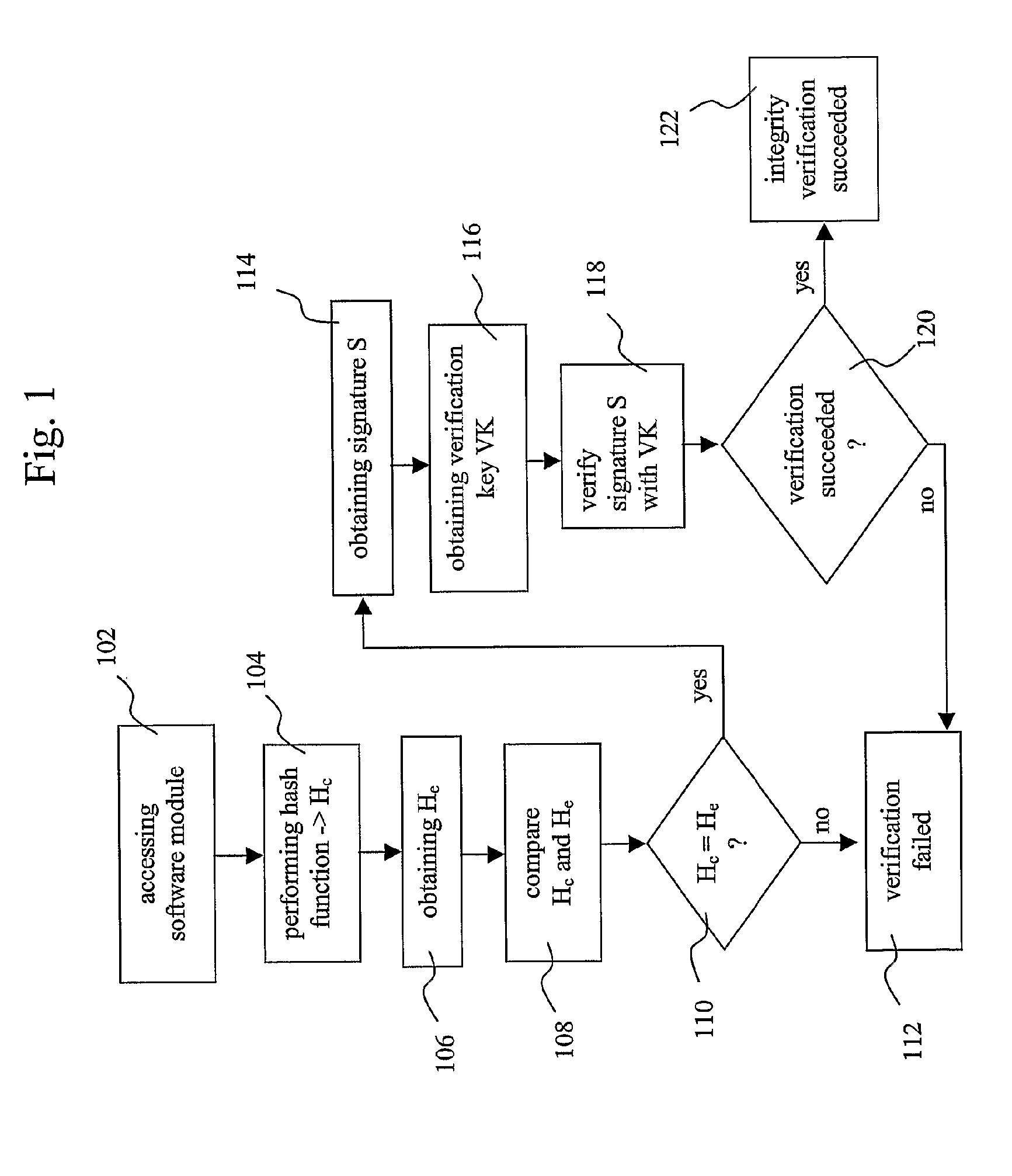
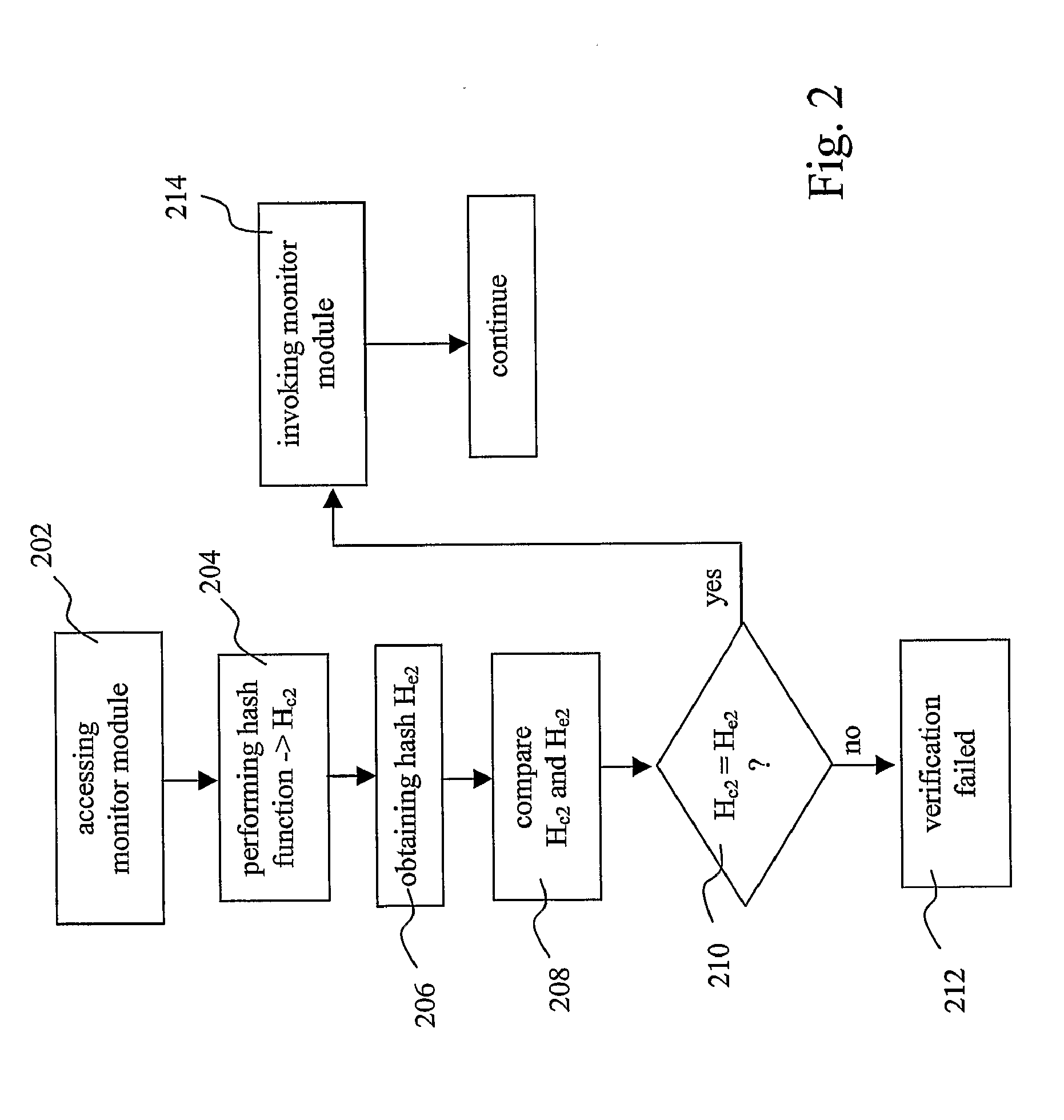
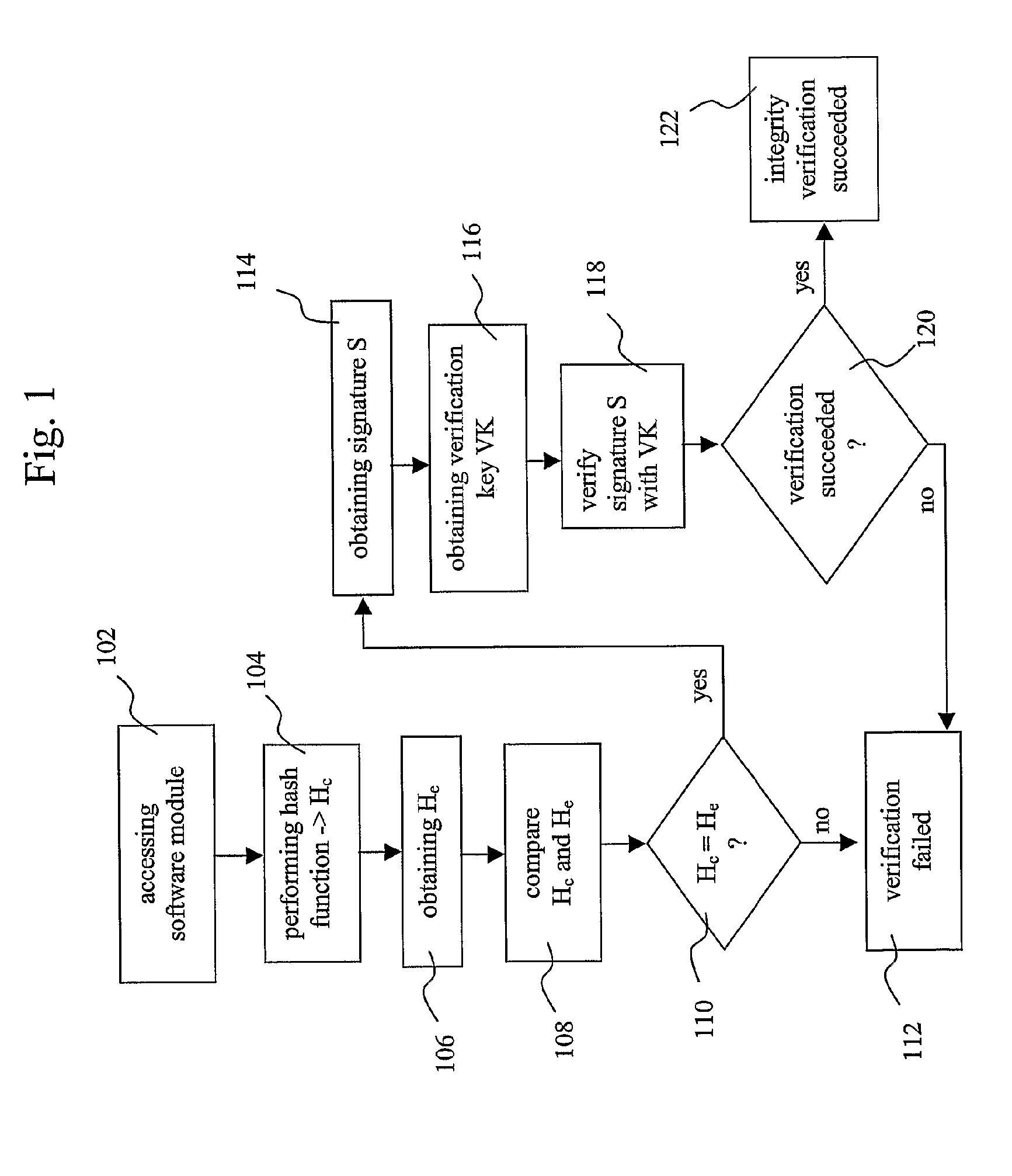
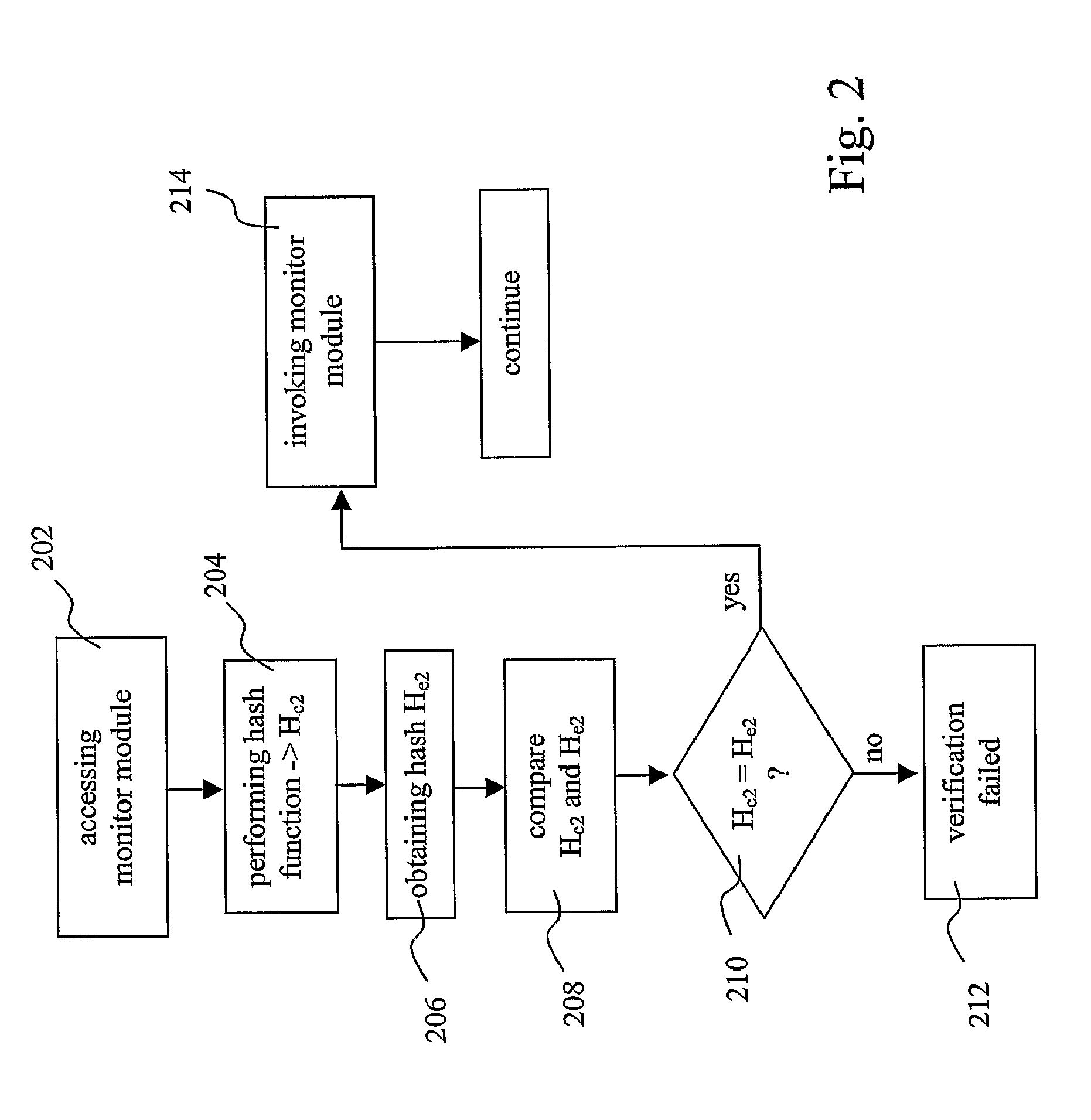
A method for verifying the integrity of platform software of an electronic device is provided, the method comprising accessing a module of said platform software, obtaining a signature (S), obtaining a verification key (VK), said verification key (VK) corresponding to a signing key (SK), verifying if said signature (S) was derived by signing said platform software module with said signing key (SK), by using said verification key (VK), and establishing a positive verification of said platform software module if said verification is successful. The invention also provides a method for providing a platform software module to perform the aforementioned method, and a device on which the aforementioned method can be performed.
Owner:CONVERSANT WIRELESS LICENSING LTD
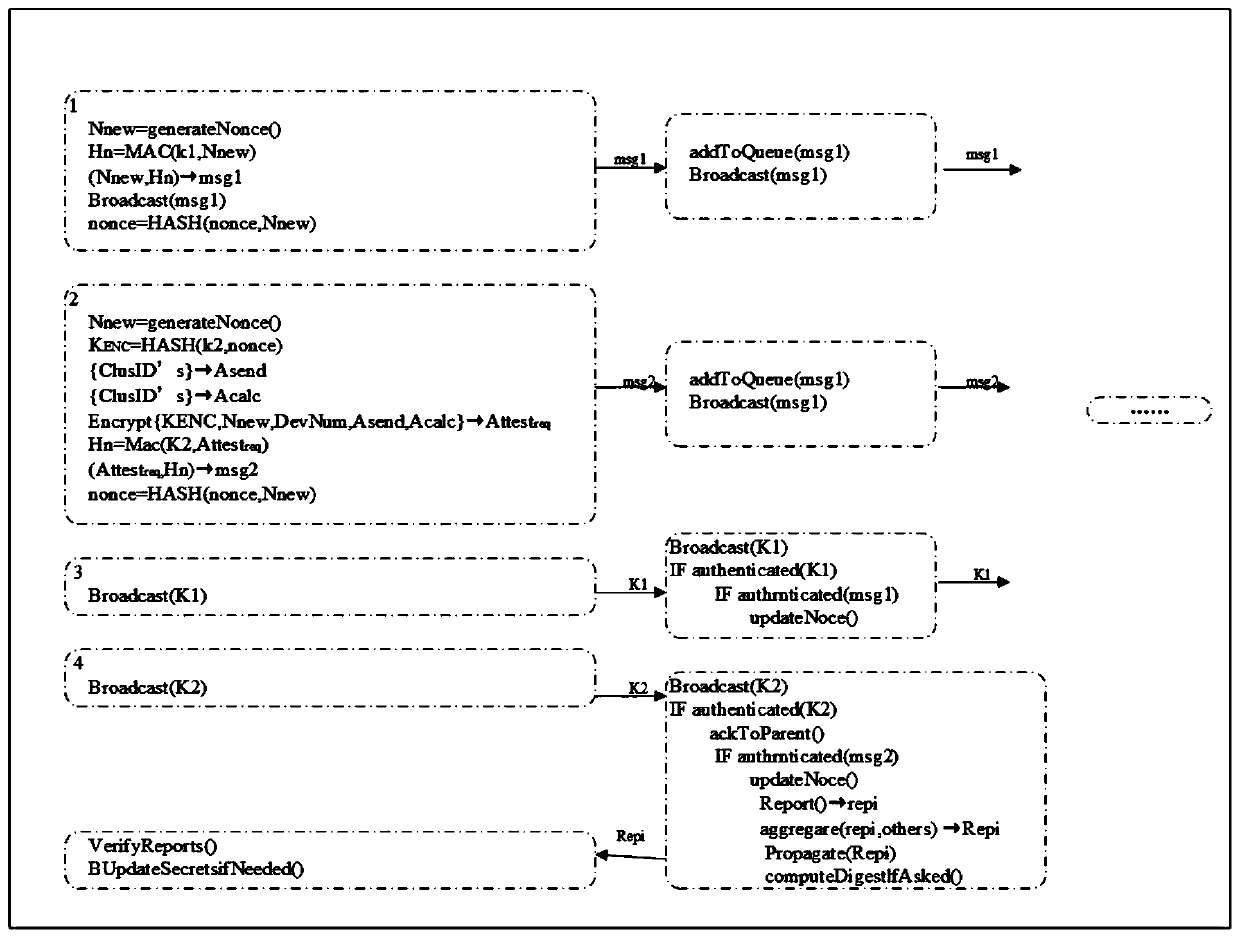
Expandable lightweight proving method for Internet of Things equipment
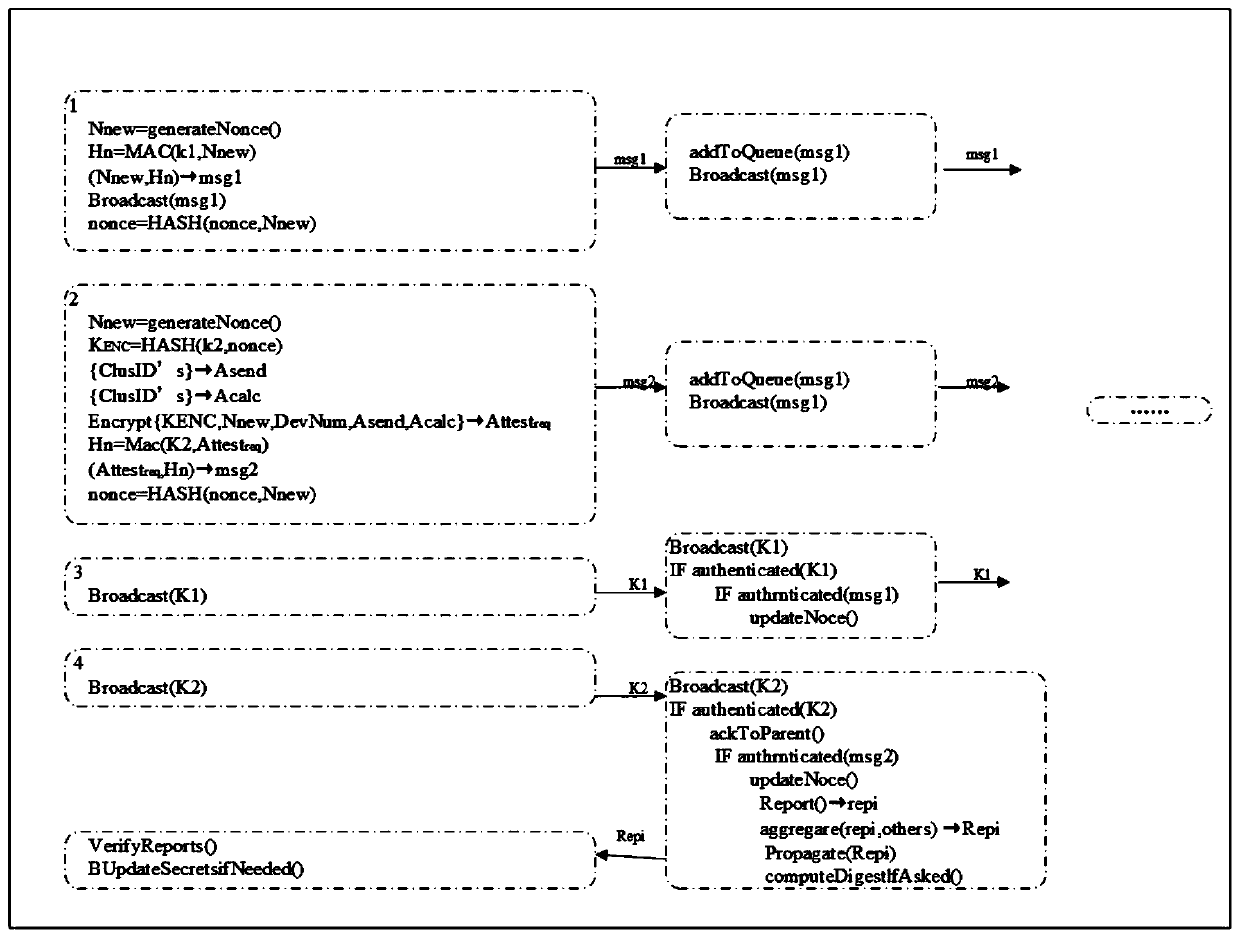
ActiveCN110022312AResist attackGuaranteed uptimeKey distribution for secure communicationMemory footprintAuthentication
An expandable lightweight proof method for Internet of Things equipment comprises the following specific steps: verifier setting: K0 is used as committed key initialization equipment, and recursion inspection of other keys is executed; prover initialization: each prover P is initialized by using public and private values, and each verifier V is initialized by using two equipment related keys for authentication and software integrity; starting of a remote proof: the verifier V generates a new random value Nnew and creates a proof request (Attest<req>); secret key leak: the verifier V broadcaststhe verification secret key to all nearby testers P; authentication report implementation: each verifier V checking whether its cluster ID is included in a second list (A<calc>) of attestation requests; physical and remote attack detection: remotely damaged devices are detected by aggregation incapable of participating in proof reports. According to the method, the running overhead and memory occupation are reduced, and the method can be used for static and dynamic networks consisting of thousands of heterogeneous Internet of Things devices.
Owner:HANGZHOU VOCATIONAL & TECHN COLLEGE
A software behavior integrity verification method
InactiveCN109558724AImplement identity authenticationReduce computing power requirementsComputer security arrangementsFeature setSoftware engineering
The invention discloses a software behavior integrity verification method, which adopts a C / S (Client / Server) architecture, and a server side comprises software strategy configuration, feature storageand feature matching functions and is responsible for software behavior feature verification. The client comprises system call collection of software, and a behavior feature set of the software can be generated according to a system call sequence; An SSL-based security channel is deployed between the server and the client, and both parties in the same way interact through corresponding communication modules to realize identity authentication and data transmission encryption during mutual access. According to the invention, the remote proving problem of software integrity is solved.
Owner:XIDIAN UNIV
Method of maintaining software integrity
InactiveUS8639916B2Shorten the timeAvoid excessive computationVolume/mass flow measurementDigital computer detailsComputer hardwareSoftware integrity
A method of maintaining the integrity of software stored in memory, the method comprising: storing an indicator associated with the memory; calculating a reference value from the stored indicator; storing the reference value; modifying the indicator when the software in the memory is modified; storing the modified indicator; recalculating the reference value from the modified indicator; storing the recalculated reference value; and verifying the integrity of the software by: retrieving the modified indicator; calculating an expected value from the modified indicator; and comparing the expected value with the recalculated reference value. Preferably the integrity of the software is verified without calculating an expected value from the software. The reference and expected values are typically calculated in accordance with a secret key.
Owner:MSTAR SEMICON PTE LTD +3
Platform software integrity proving method and apparatus
InactiveCN106953733AImprove securityIncrease flexibilityKey distribution for secure communicationUser identity/authority verificationInformation transmissionTrusted third party
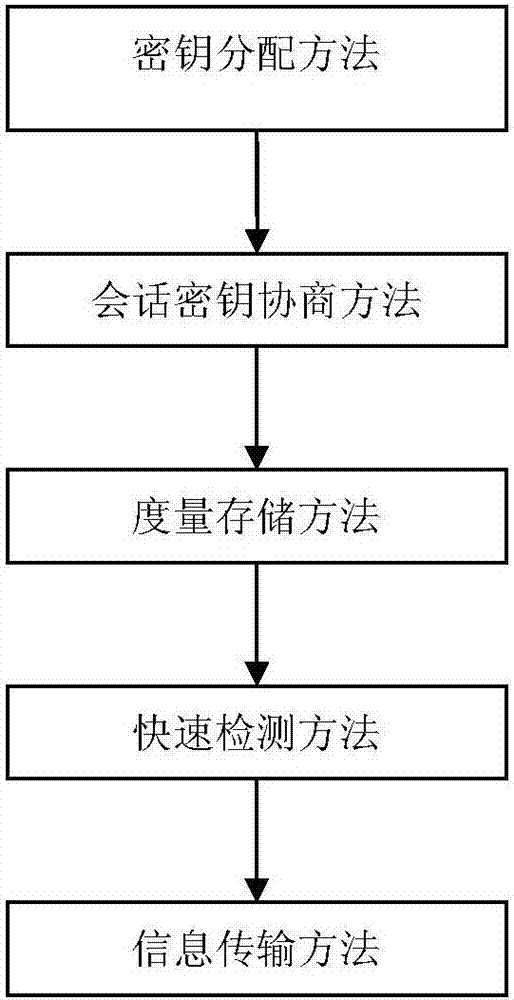
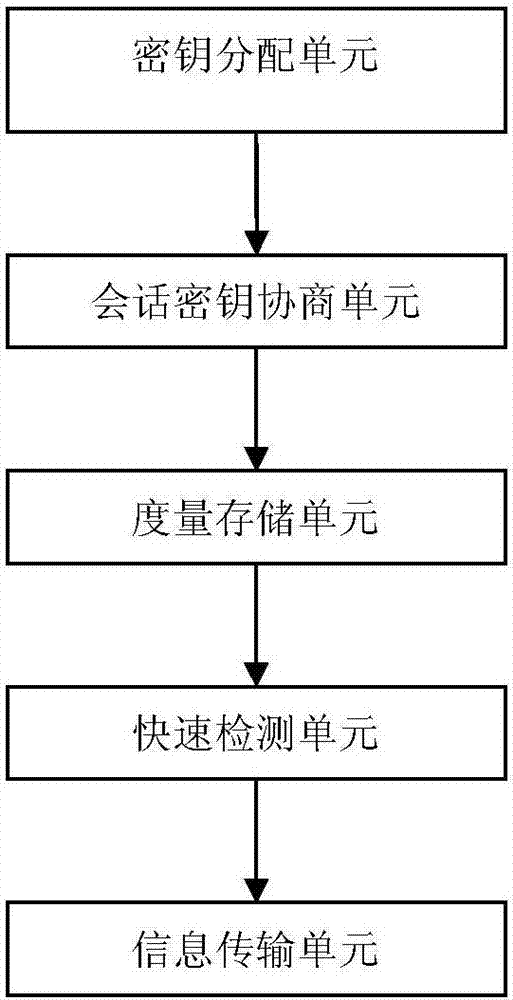
The invention provides a platform software integrity proving method and apparatus. The method includes that on the basis of a conventional three-layer information system applying PKI, a trusted third party-a measurement center is established based on the integrity measurement mechanism, and is taken as a trust arbitration and supervision party for trusted calculation to implement the trusted integrity measurement in the key links of information data transfer and transformation, so that a data measurement trusted chain can be formed, and the key data of the data measurement trusted chain is compared and analyzed, and a key distribution method, a session key negotiation method, a measurement storage method, a fast detection method, and an information transmission method are included. The provided platform software integrity proving method and apparatus improve the security and flexibility of platform security verification.
Owner:成都麟成科技有限公司
Method and system for establishing secure computing environment of intelligent electric energy meter
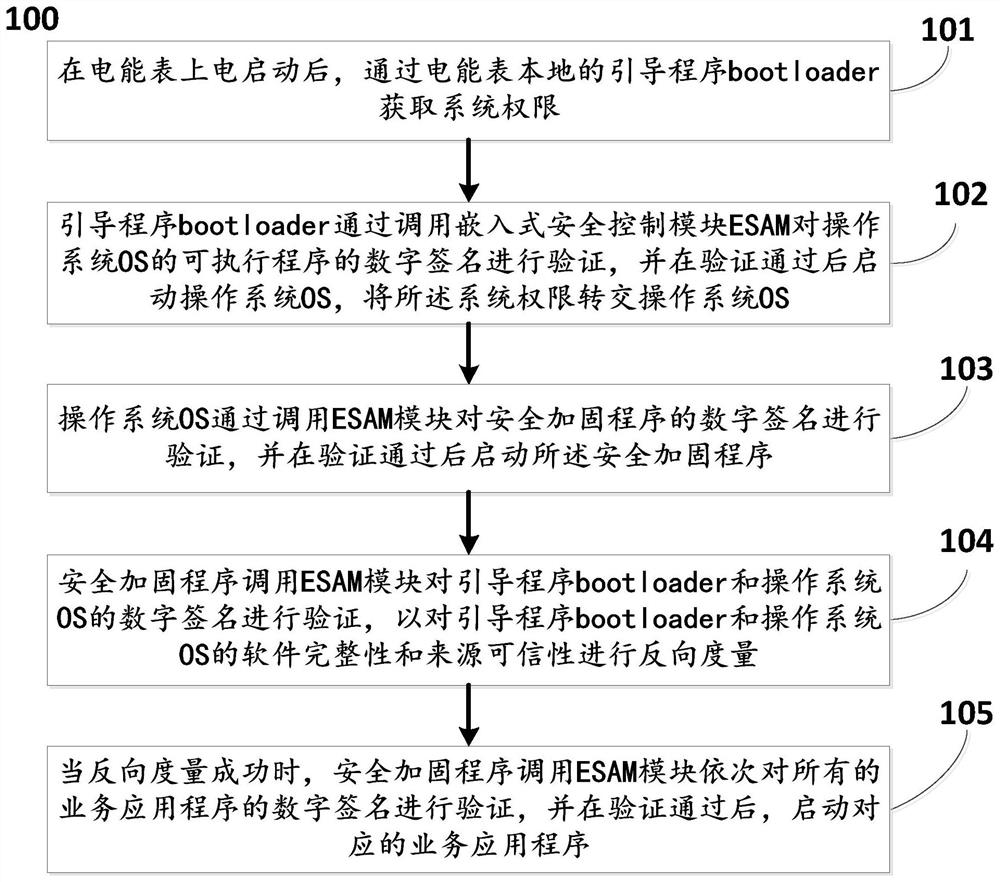
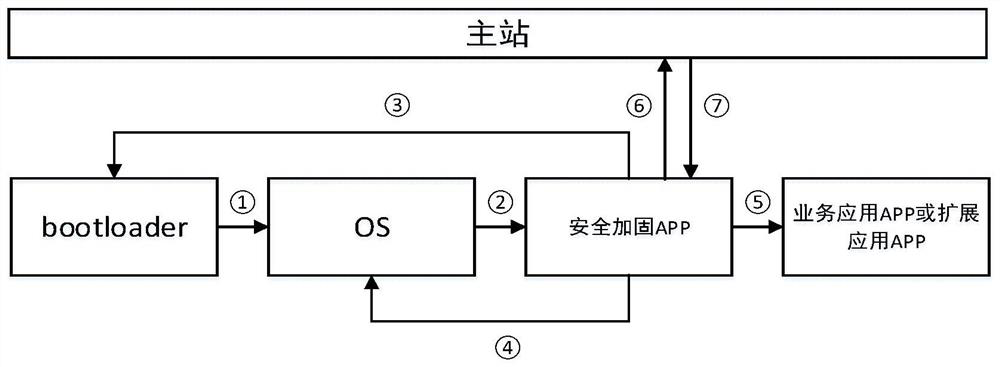
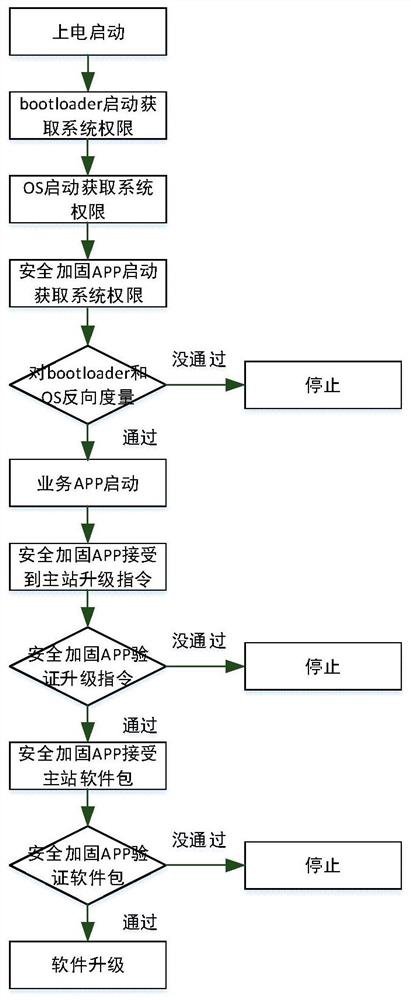
ActiveCN112163216AIntegrity guaranteedAvoid Failsafe RisksDigital data authenticationBootstrappingTamper resistanceOperational system
The invention discloses a method and system for establishing a secure computing environment of an intelligent electric energy meter, and the method comprises the steps: constructing a software integrity and source credibility verification chain starting from a bootloader and ending at a business application APP based on a digital certificate mechanism, and achieving the credible source verification and tamper-proof protection of local software of the electric energy meter. A local security computing environment is constructed for the electric energy meter, so that attack behaviors such as malicious code implantation for the electric energy meter can be effectively prevented. Master station fault security risks caused by spreading malicious codes and viruses to a master station system through the electric energy meter are avoided; the bootloader and the operating system OS are subjected to reverse measurement by introducing the security reinforcement APP, so that the software integrityand source credibility of the bootloader and the operating system OS are ensured; all software supports regular or any-time full-life-cycle management of the master station, the master station can see, manage and control the local operation software condition of the electric energy meter, and safety risks faced by the novel intelligent electric energy meter can be avoided.
Owner:CHINA ELECTRIC POWER RES INST +1
Method and device for verifying the integrity of platform software of an electronic device
ActiveUS9438608B2Improve securitySimple wayUser identity/authority verificationComputer security arrangementsComputer moduleSoftware modules
A method for verifying the integrity of platform software of an electronic device is provided, the method comprising accessing a module of said platform software, obtaining a signature (S), obtaining a verification key (VK), said verification key (VK) corresponding to a signing key (SK), verifying if said signature (S) was derived by signing said platform software module with said signing key (SK), by using said verification key (VK), and establishing a positive verification of said platform software module if said verification is successful. The invention also provides a method for providing a platform software module to perform the aforementioned method, and a device on which the aforementioned method can be performed.
Owner:CONVERSANT WIRELESS LICENSING LTD
Global offset table measurement method, dynamic measurement method, related device and apparatus
ActiveCN110598378ADigital data protectionEnergy efficient computingSoftware engineeringIntegrity measurement
The embodiment of the invention discloses a GOT table measurement method. The method comprises the steps of during the process of running a process, obtaining the initial address and length of a GOT table to determine the complete GOT table needing to be measured according to the initial address and length of the GOT table, wherein the GOT table specifically comprises the GOT table of the processand the GOT table of a dynamic library on which the process depends; furthermore, carrying out the integrity measurement on each element in the determined GOT table, or carrying out the integrity measurement on the whole GOT table, so that the integrity measurement of the GOT table is realized, and the integrity measurement of the GOT table is added during the process of dynamically measuring thesoftware integrity.
Owner:HUAWEI TECH CO LTD
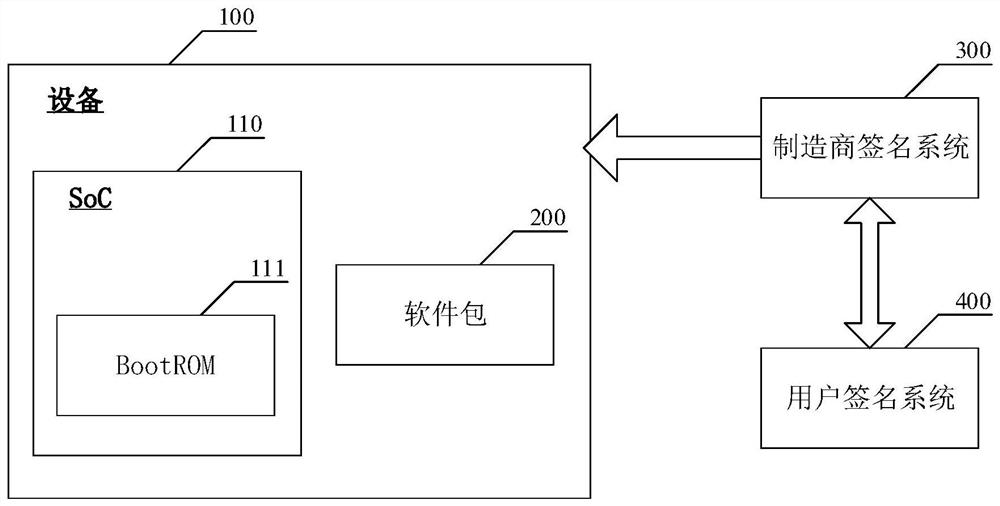
Software integrity protection and verification method and device
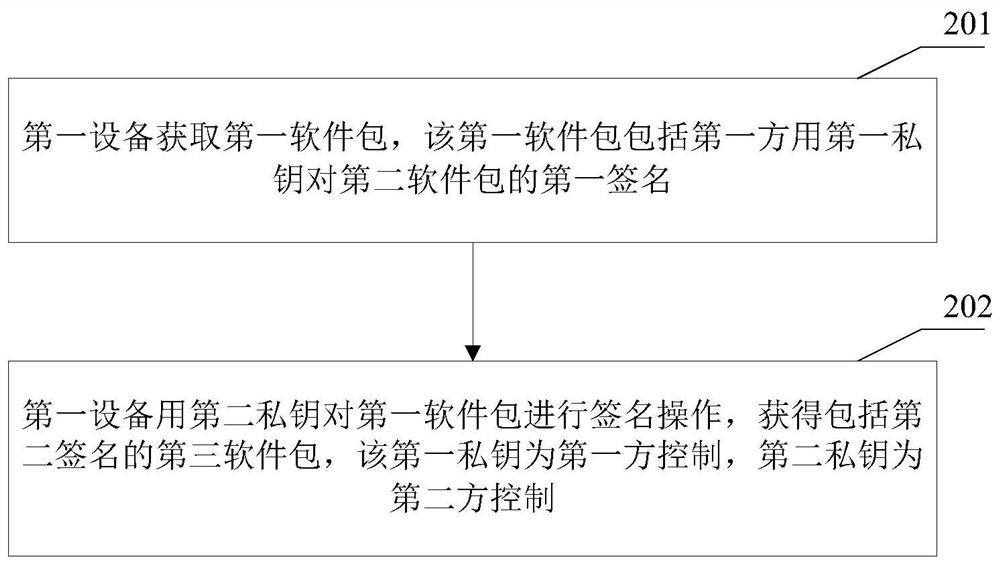
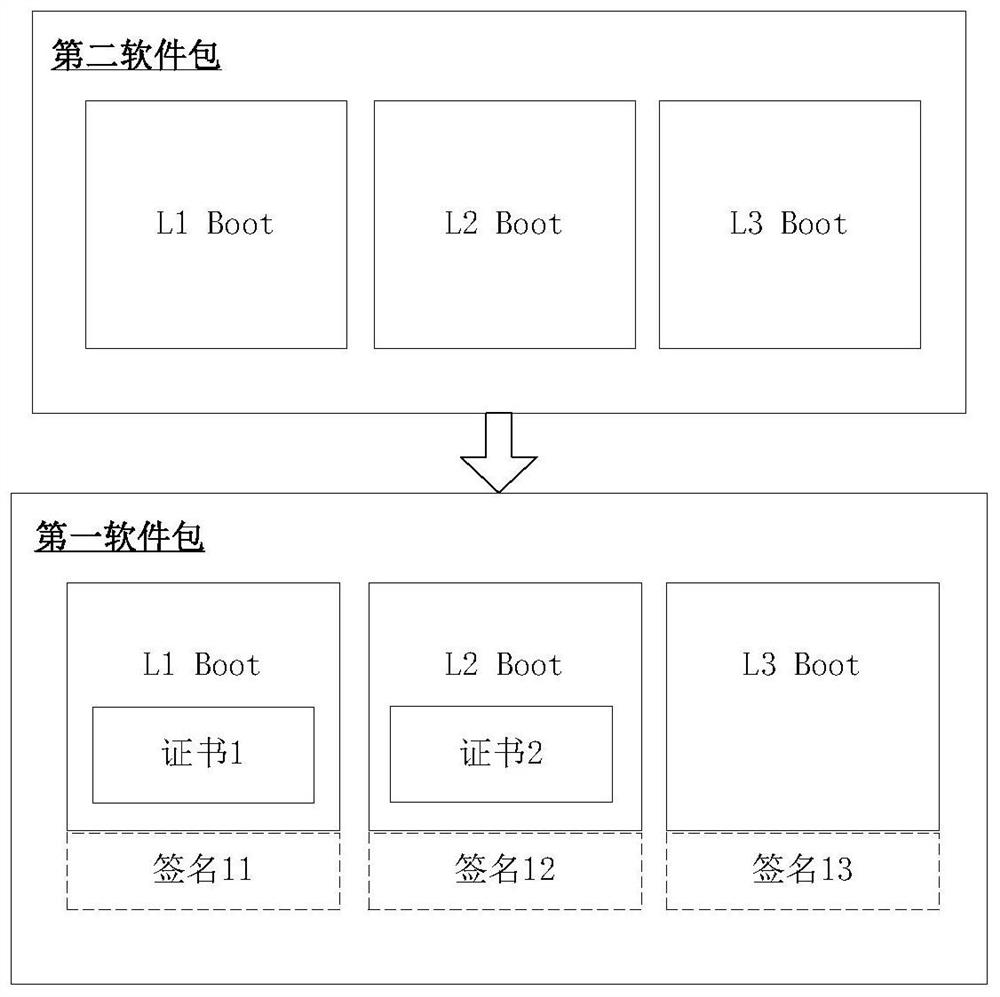
PendingCN112699343AImprove securityImprove reliabilityDigital data protectionPlatform integrity maintainanceSoftware engineeringVerification
The embodiment of the invention discloses a software integrity protection and verification method and device. The protection process comprises the steps that first equipment obtains a first software package, wherein the first software package comprises a first signature of a first side for a second software package through a first private key; the first equipment uses the second private key to perform signature operation on the first software package to obtain a third software package including a second signature, the first private key being first-party control, and the second private key being second-party control. After the third software package is sent to the second device, the verification process comprises the steps that the second device obtains a first software package, and the first software package comprises a first signature, a second signature and a second software package; the second equipment verifies the first signature and the second signature based on a pre-stored first public key and a pre-stored second public key to obtain a verification result. Thus, protection of the integrity of the secret key software provided by a manufacturer and a user is adopted, dual software integrity verification bases are provided for the user, and the trust problem of the user is solved.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com