A processor-implemented method for ensuring software integrity
An integrity and processor technology, applied in the direction of platform integrity maintenance, electrical digital data processing, instruments, etc., can solve problems such as decision-making
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
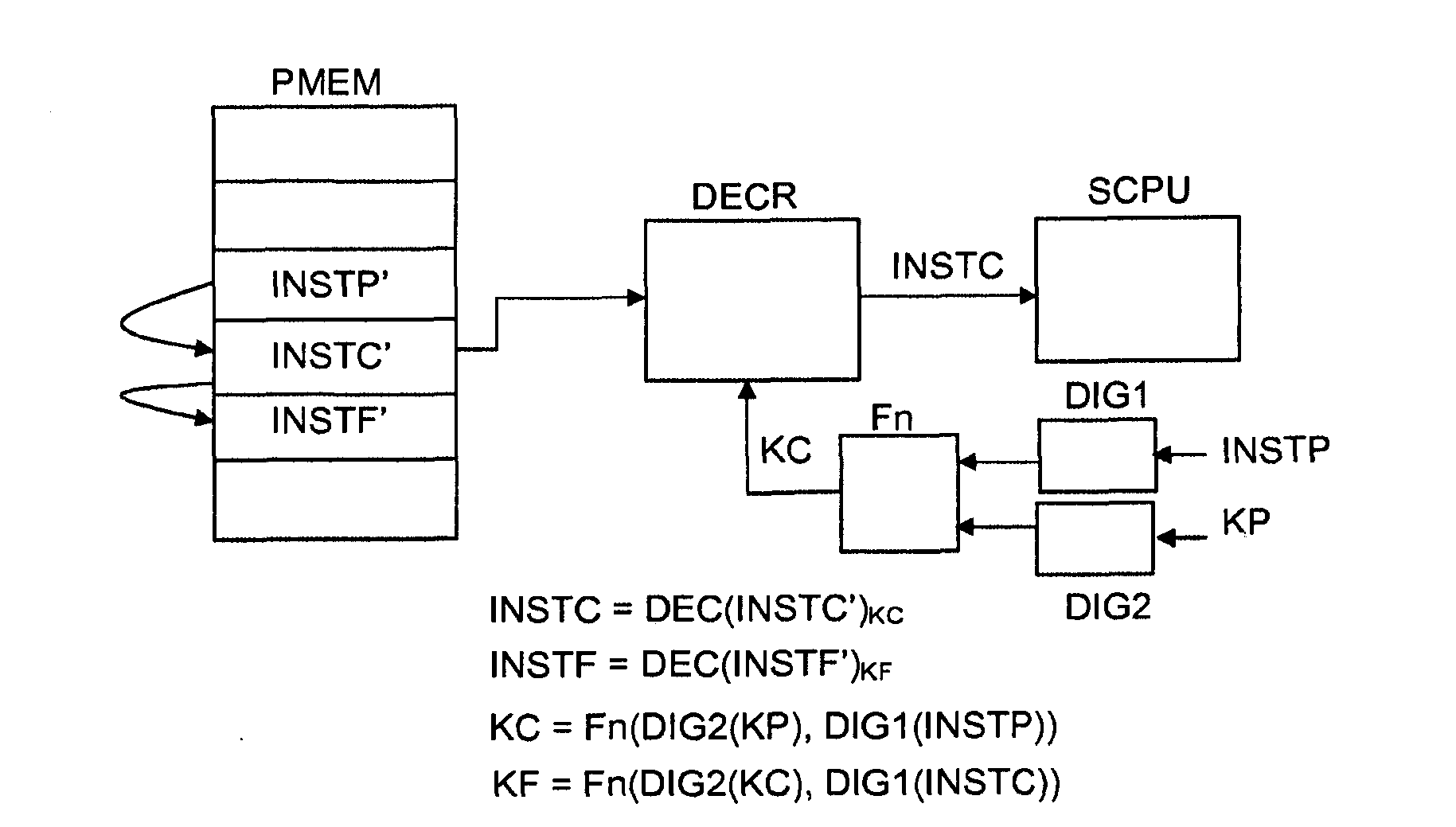
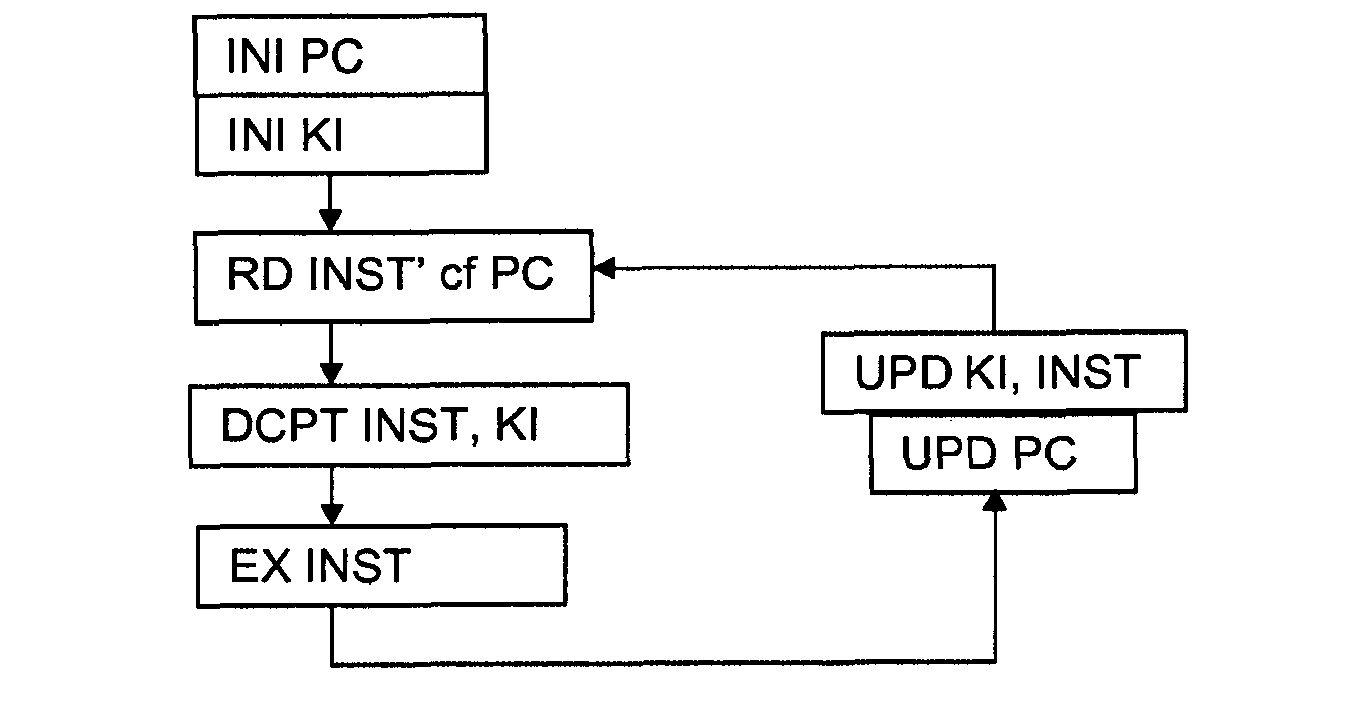
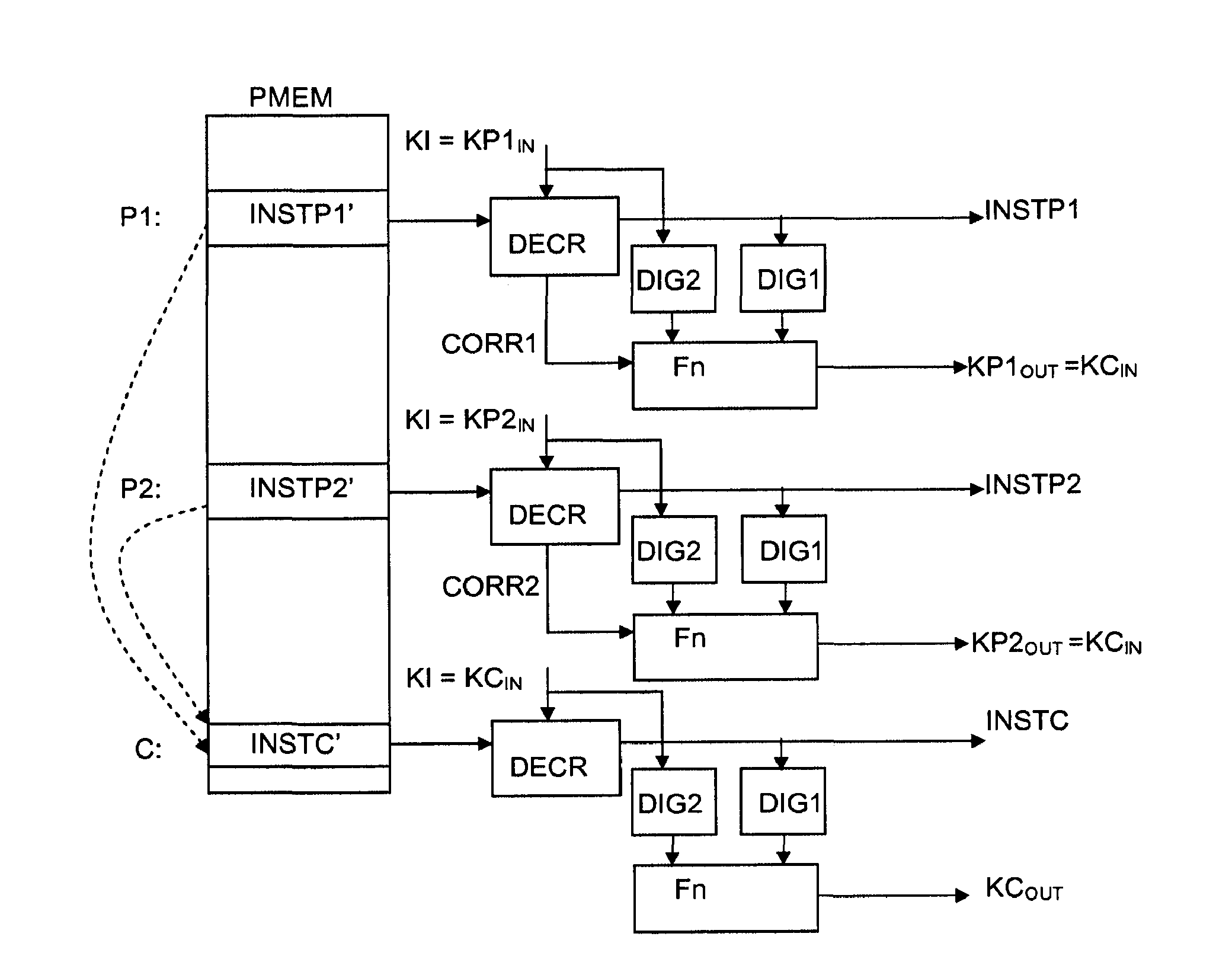
[0019] As stated above, the present invention seeks to provide a means for running software in a secure manner, whereby the software is stored in encrypted form in a memory and decrypted and executed instruction by instruction within a secure processor without the possibility of surveillance sex. The key used for the decryption of the current instruction depends on at least one previous instruction having been correctly decoded, while the key used for the decryption of the following instruction depends on the correct decryption of the current instruction. In this way, a self-checking means for ensuring the integrity of a software is realized. The successful execution of software is to ensure that the process and content are not tampered with, because the modification of an instruction will make the ability to decrypt the following instructions lost, resulting in the hasty termination of the program or at least the collapse of the program execution tracking. The scheme used in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com