Software integrity verifying system and method based on VMM (virtual machine monitor)
A technology of integrity verification and software, applied in the computer field, can solve problems such as inability to defend against memory patch modification, software integrity verification, and affecting system performance, and achieve the goal of overcoming memory integrity, reducing performance overhead, and small performance overhead Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described in detail below with reference to the accompanying drawings.
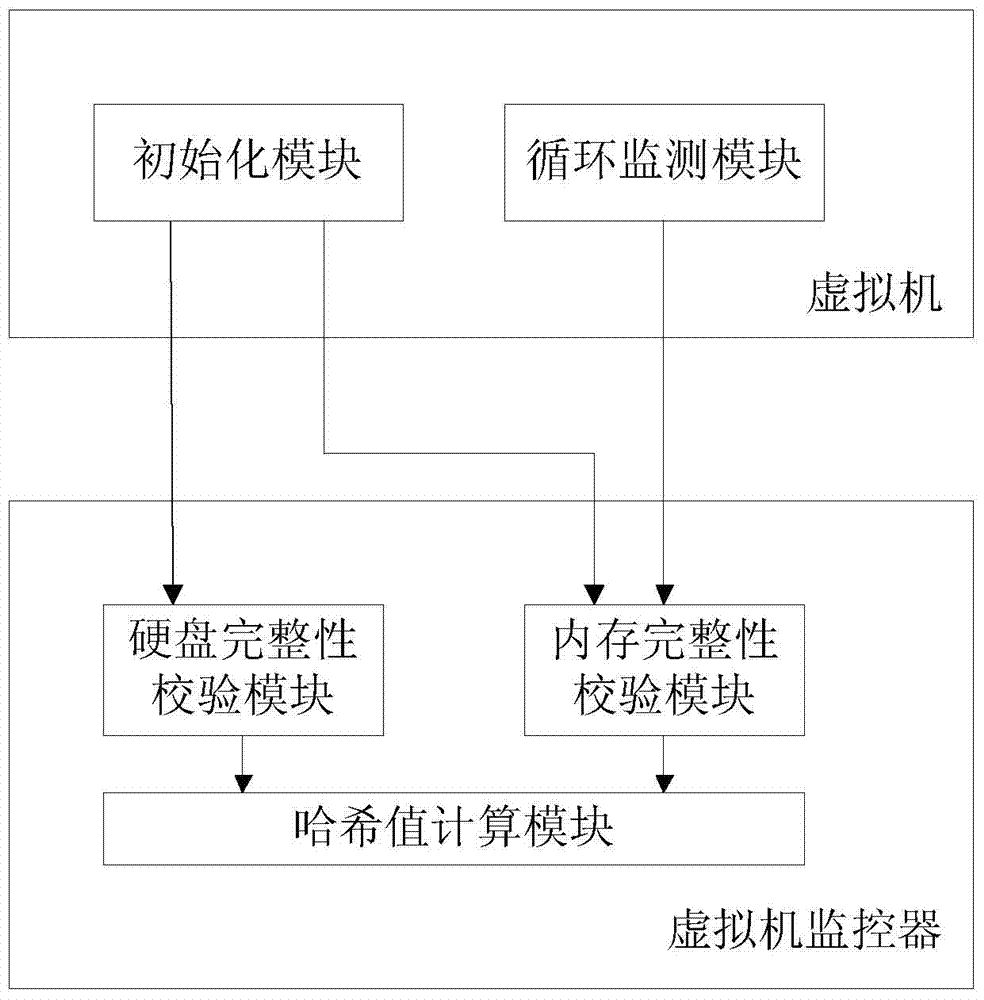
[0035] Refer to the attached figure 1 The system of the present invention includes a virtual machine and a virtual machine monitor, the virtual machine includes an initialization module and a loop detection module, and the virtual machine monitor includes a hard disk integrity check module, a memory integrity check module and a hash value calculation module. in:
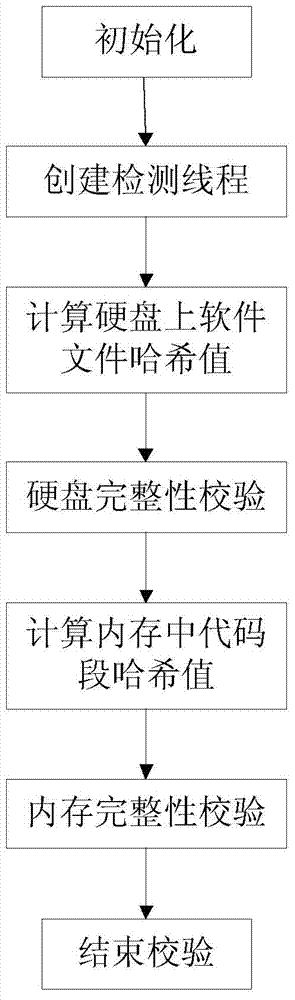
[0036] The initialization module completes the initialization work, including detecting whether the current CPU supports the virtualization feature, calling the CPUID instruction to enable the hardware virtualization feature, calling the hardware virtualization instruction, migrating the operating system to the virtual machine monitor, falling into the virtual machine monitor, calling Hard disk integrity check module and memory integrity check module.
[0037] The loop detection module periodically ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com