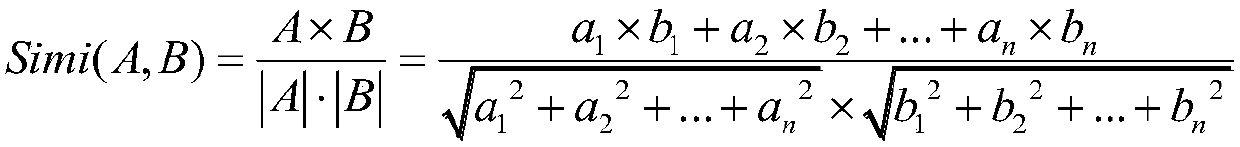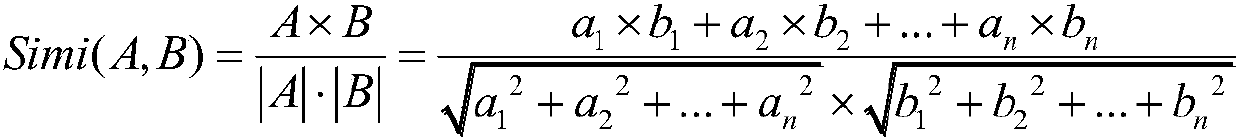Similarity detection method for unknown vulnerability discovery based on patch information
A technology of unknown vulnerabilities and detection methods, which is applied in the field of similarity detection to discover unknown vulnerabilities by using patch information, can solve problems such as low ranking results, low similarity values, high similarity, etc., to improve detection accuracy, low Performance overhead, the effect of reducing interference
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
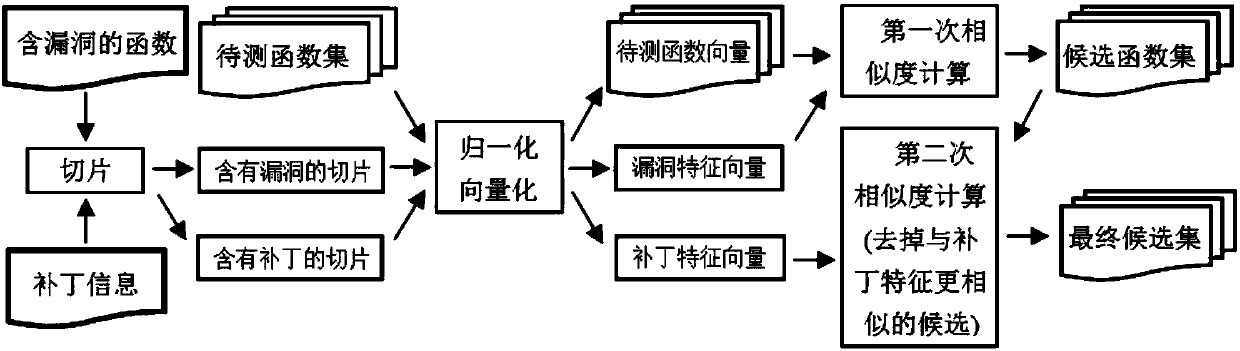
[0040] The method of the present invention is deployed on a 64-bit Ubuntu 16.04 platform, and GCC4.9 is used as a compiler. The open source audio and video processing library FFmpeg version 3.2.4 and the open source image browsing software Ghostscript version 9.21, which are widely supported by multiple platforms, are selected as the experimental objects. Among them, FFmpeg contains 1583 files and 15598 functions, and Ghostscript contains 935 files and 15875 functions. In terms of vulnerabilities, the newly announced vulnerabilities of these two softwares in 2017 were selected as known target vulnerabilities for detection experiments.
[0041] The method of the present invention involves three main steps. The slicing, normalization and vectorization are all directly deployed in GCC, and the slicing and vector mapping are simultaneously implemented in the compiling process to output feature vectors. The similarity calculation is performed separately after that, and the similar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com