Method and system for verifying software completeness
A technology of integrity verification and software, which is applied in the field of computer security, can solve the problems of lack of universality and compatibility of integrity verification methods, and rely on the integrity of the operating system to achieve the effects of reducing verification overhead, enhancing security, and reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
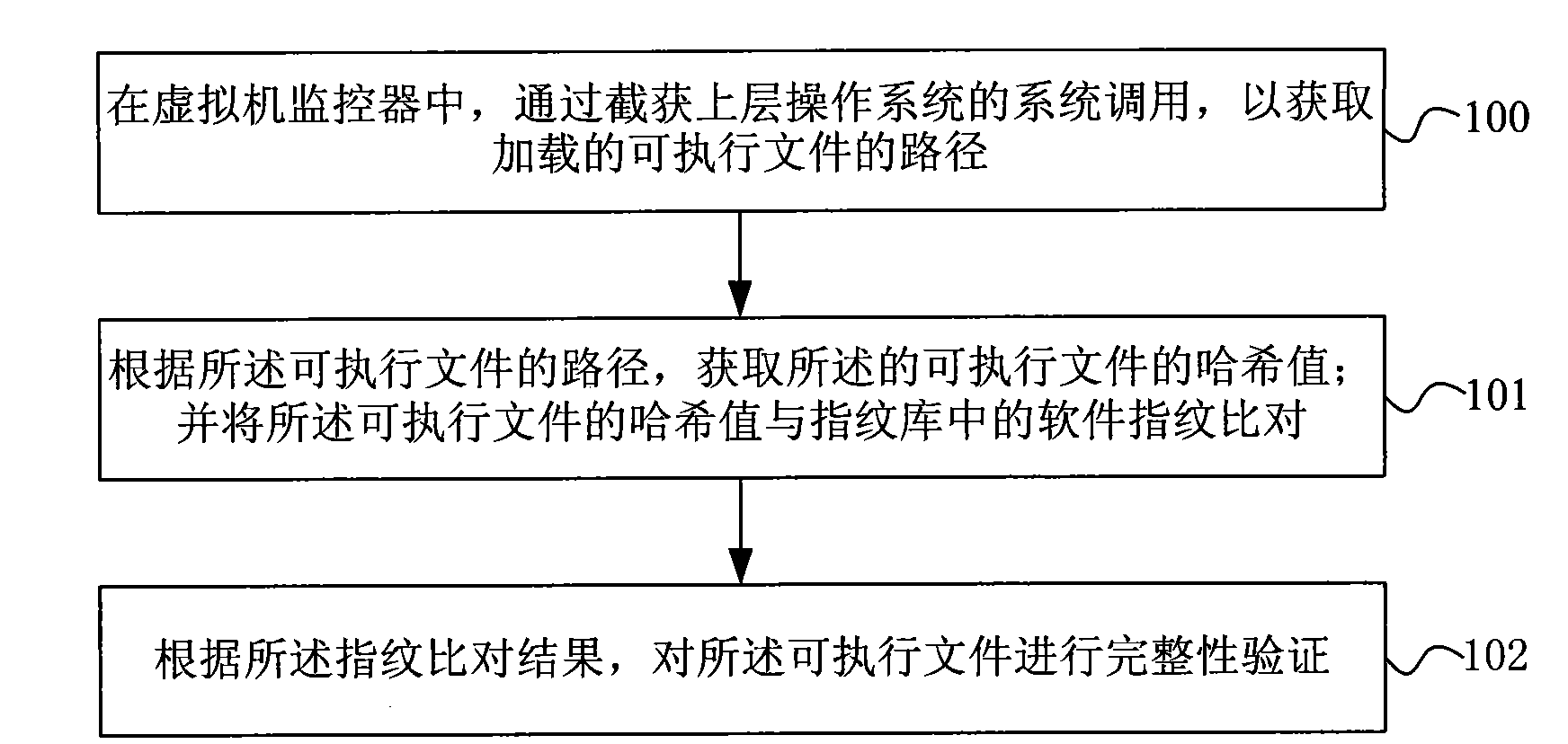
[0060] figure 1 It is a flowchart of a software integrity verification method in Embodiment 1 of the present invention; specifically, it includes the following steps:
[0061] Step 100, in the virtual machine monitor, obtain the path of the loaded executable file by intercepting the system call of the upper-layer operating system;
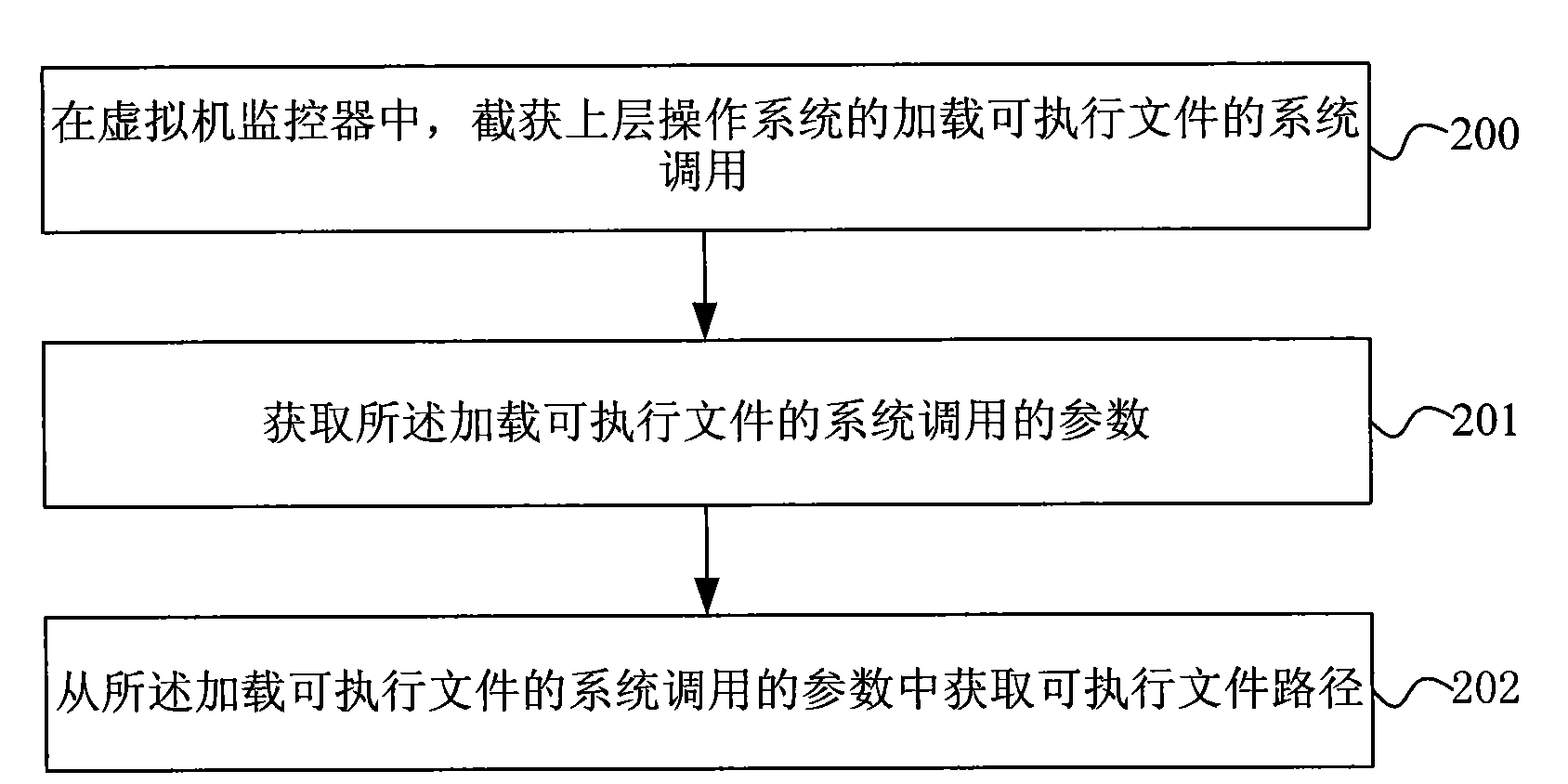
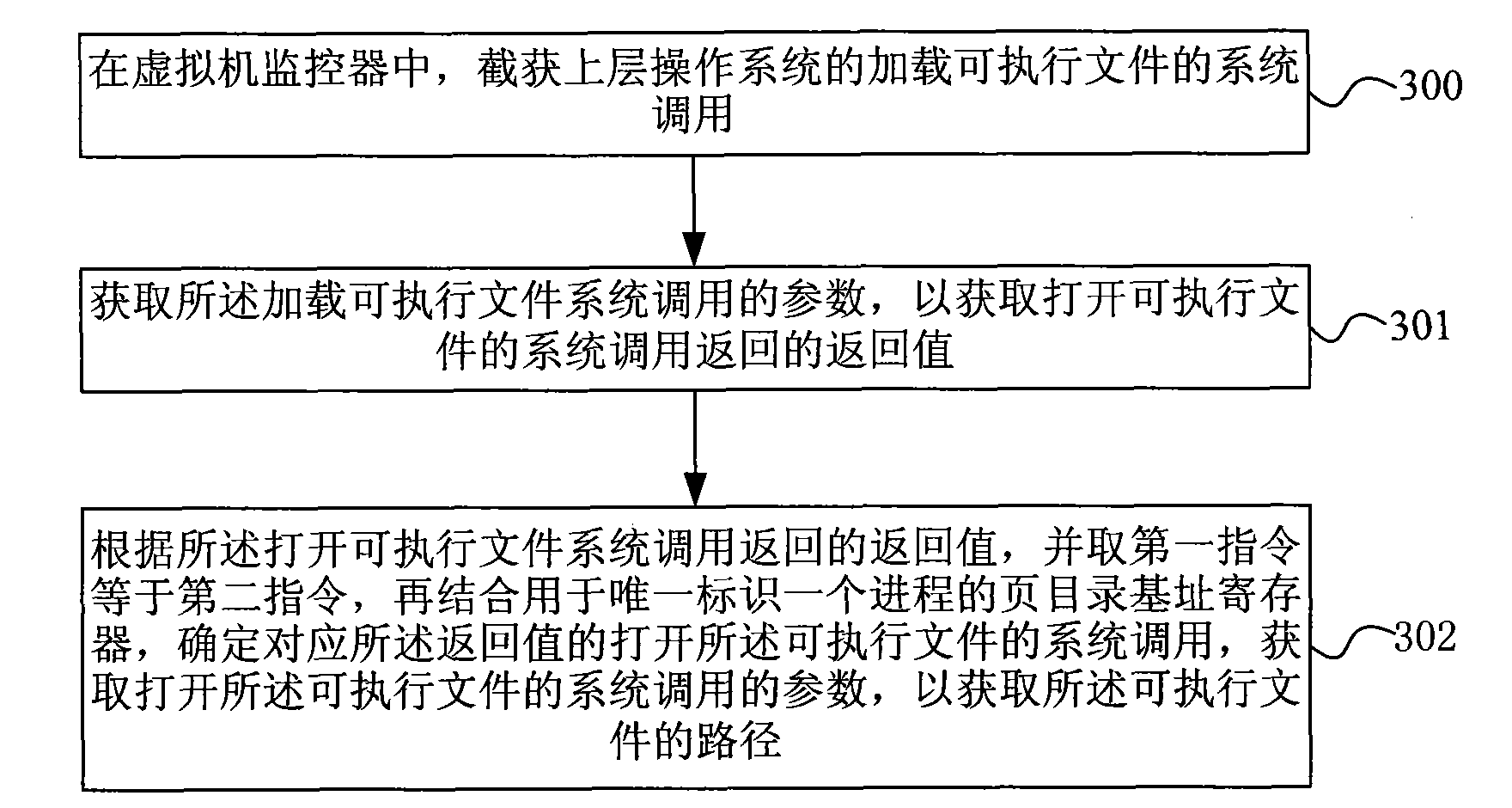
[0062] To implement the software integrity verification method of this implementation, first, a virtual machine monitor must be inserted under the operating system, and the integrity verification of executable files must be implemented at the virtual machine monitor layer. In this embodiment, the integrity verification is carried out for the executable file in the file, that is, the executable code or executable software; in the existing operating system, the executable code is divided into an application program (Application); It is a shared library); there are three types of kernel modules (also called drivers under windows). During the loadin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com