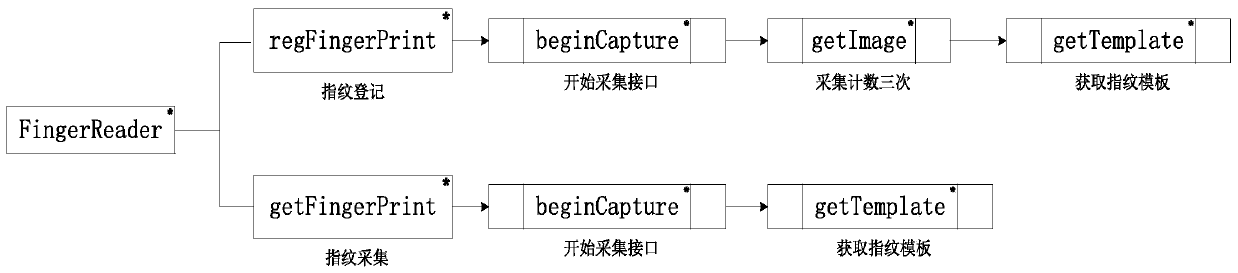
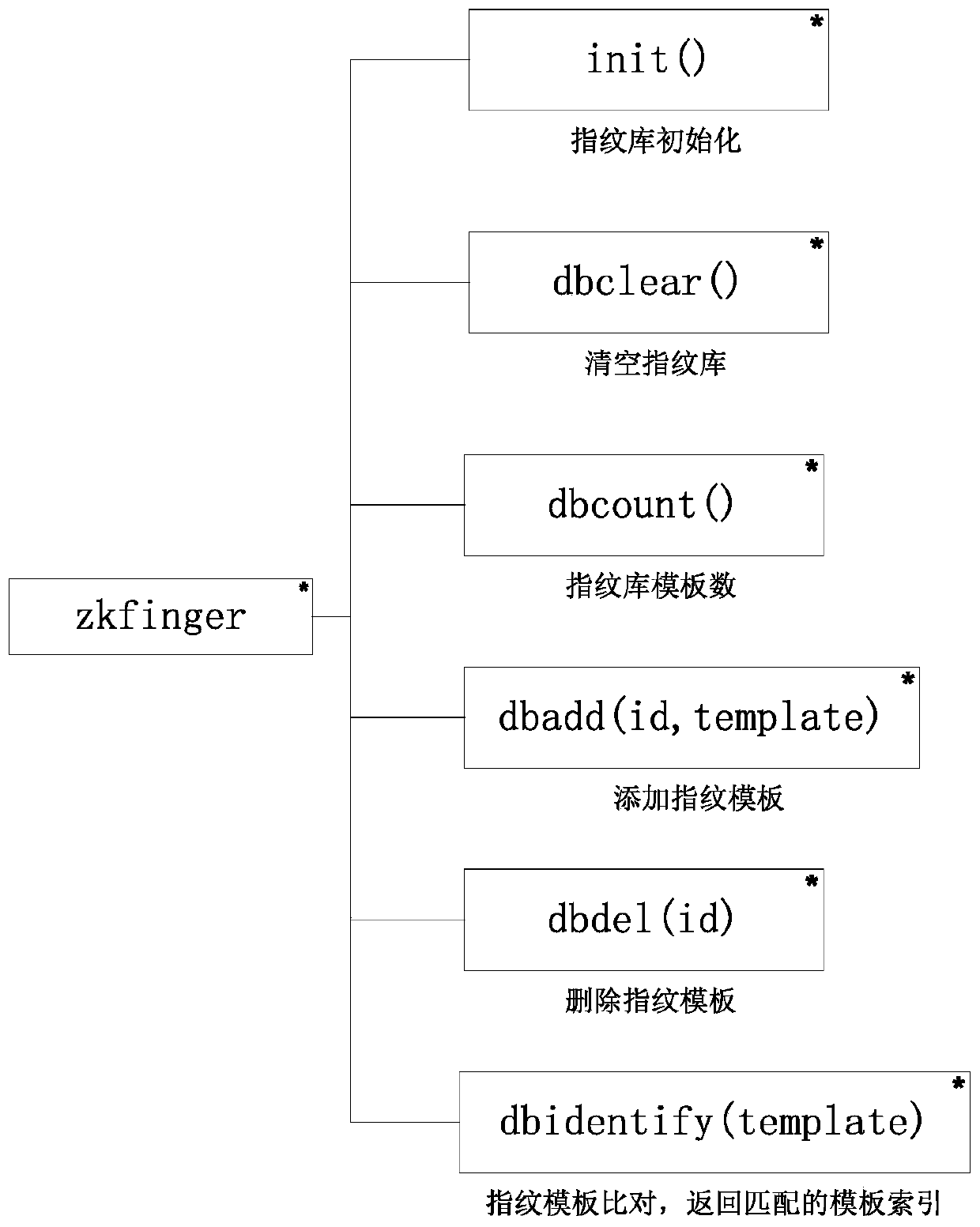
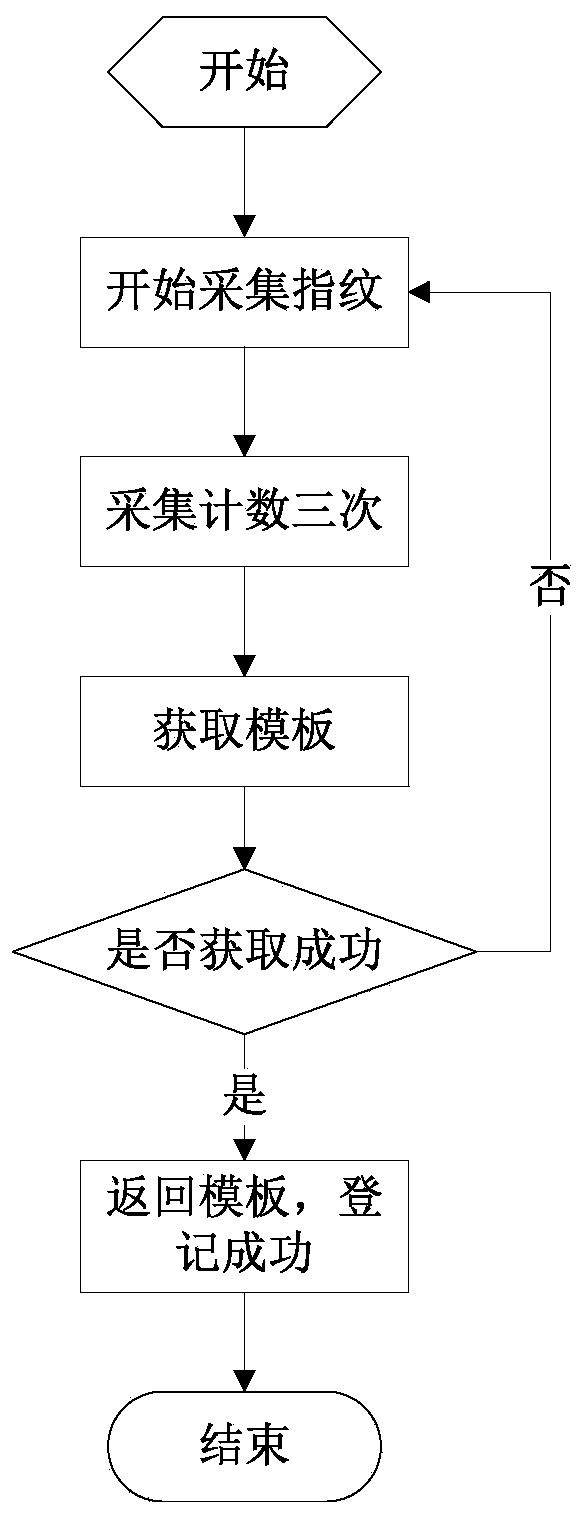
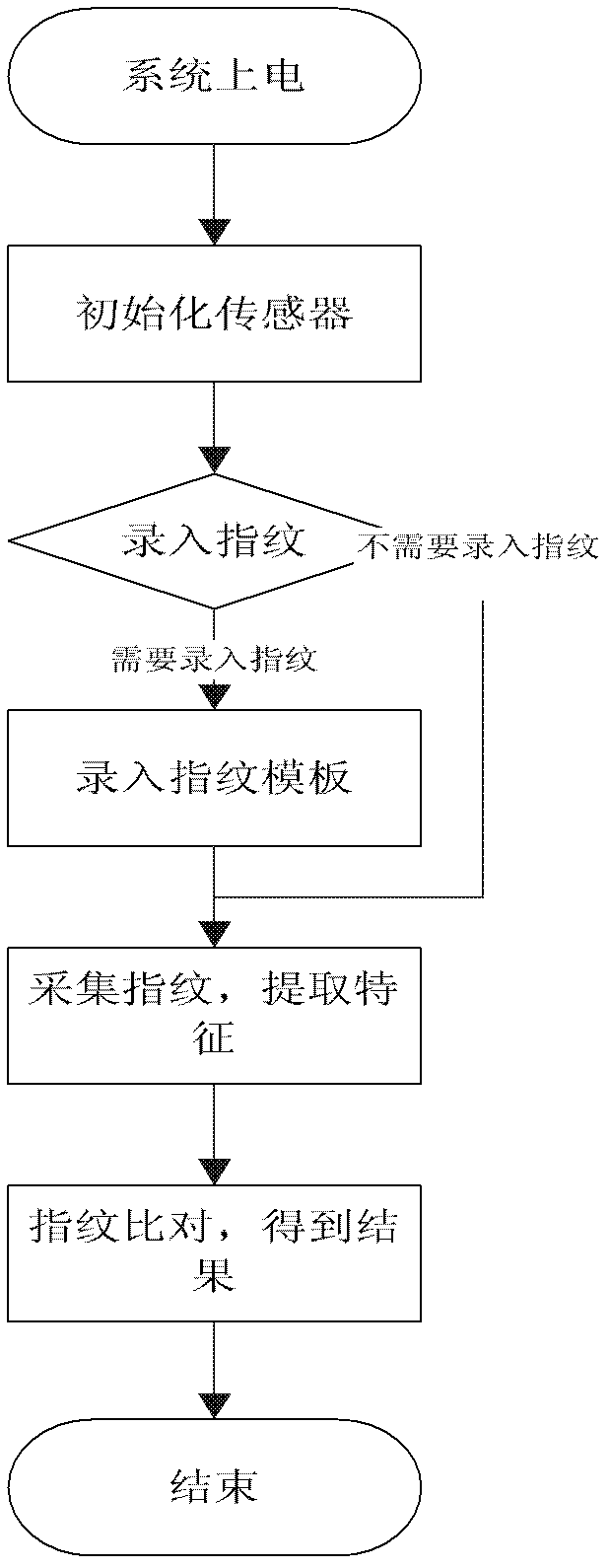
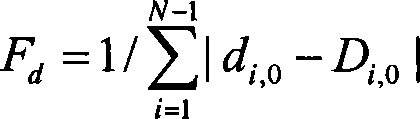Patents
Literature
79 results about "Fingerprint alignment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
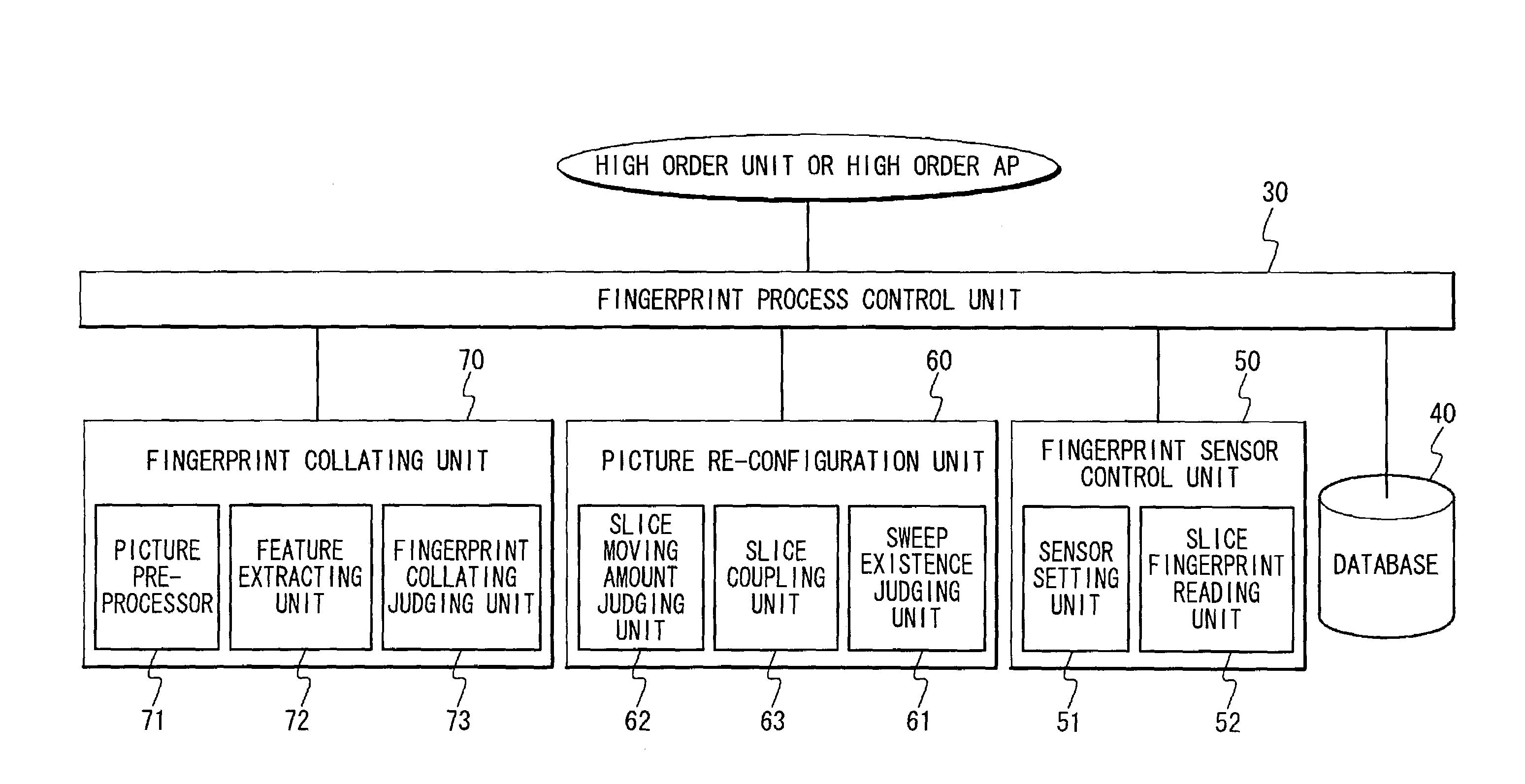
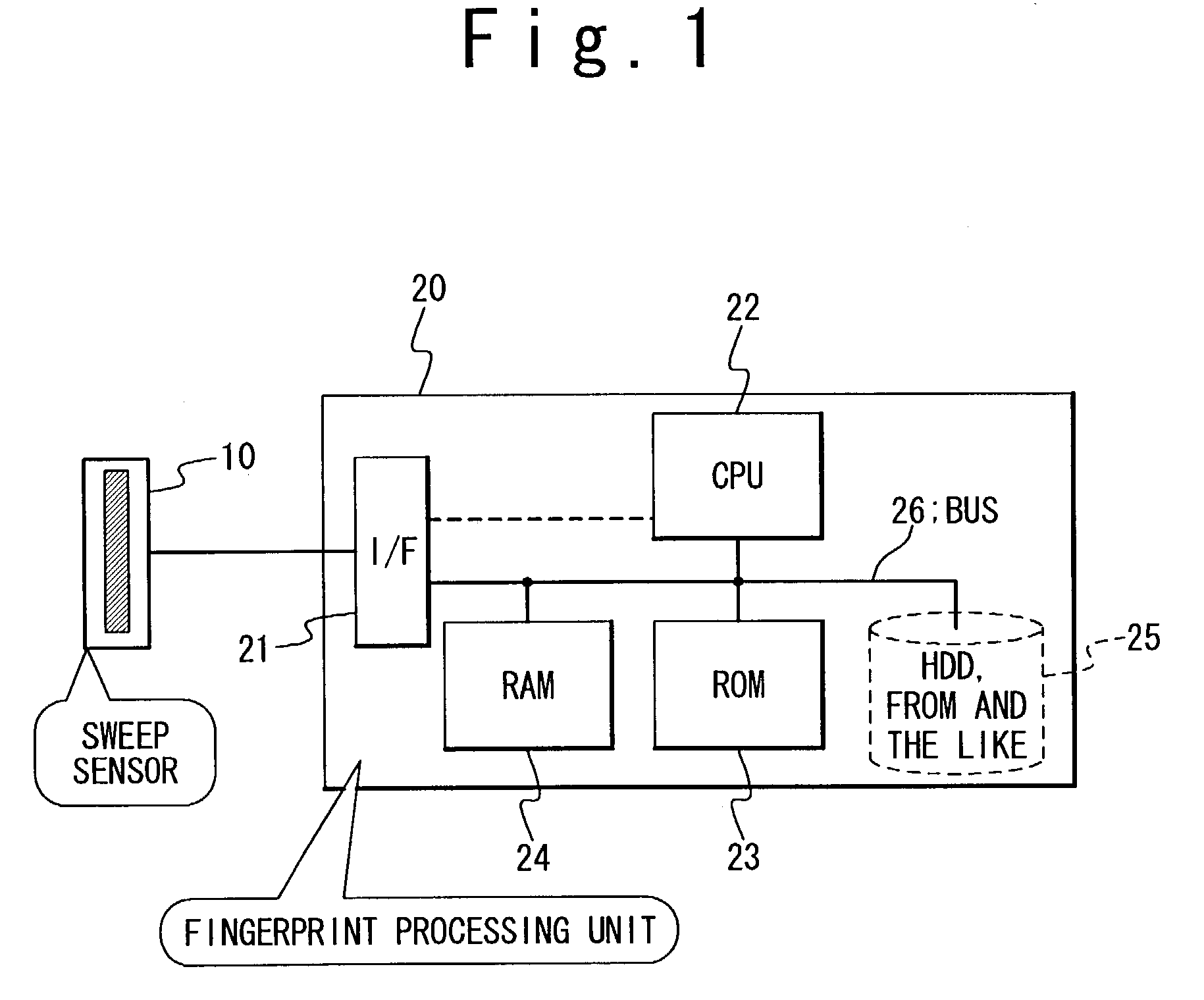
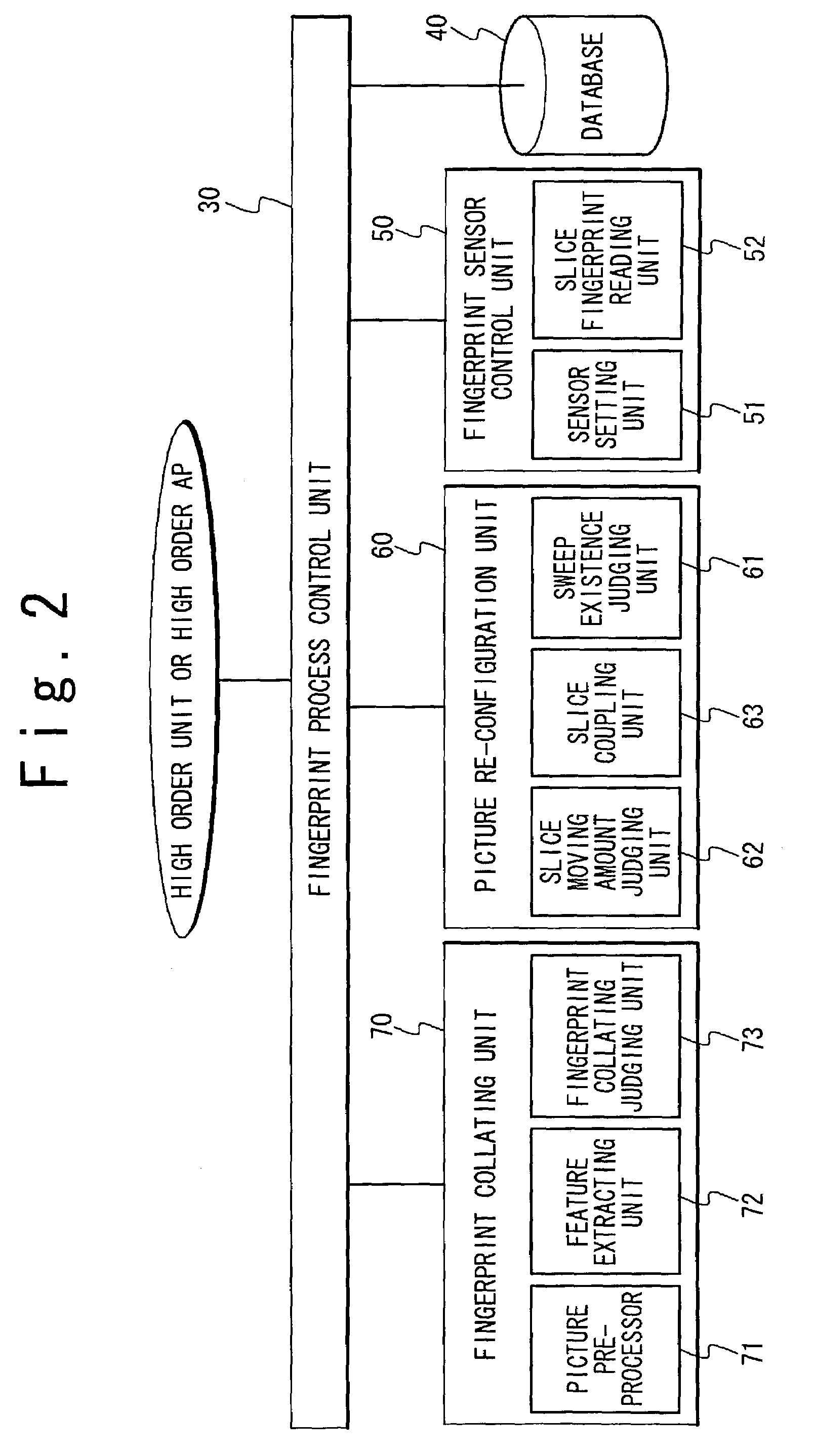
Fingerprint authenticating system for carrying out a fingerprint authentication by using a small fingerprint sensor
InactiveUS7190816B2Reduce stepsReduce the amount requiredImage analysisCharacter and pattern recognitionComputer visionFingerprint
A fingerprint authenticating system includes a fingerprint registering unit and a fingerprint collating unit. The fingerprint registering unit takes a first fingerprint data indicating a first portion of a first fingerprint from a first fingerprint sensor, registers said first fingerprint data to a memory unit, and takes a second fingerprint data indicating a second portion of a second fingerprint from a second fingerprint sensor. The fingerprint collating unit collates said second fingerprint data with said first fingerprint data to confirm whether or not said first fingerprint is equal to said second fingerprint. Here, an area of the first portion is equal to or larger than an area of the second portion.
Owner:NEC PERSONAL COMPUTERS LTD
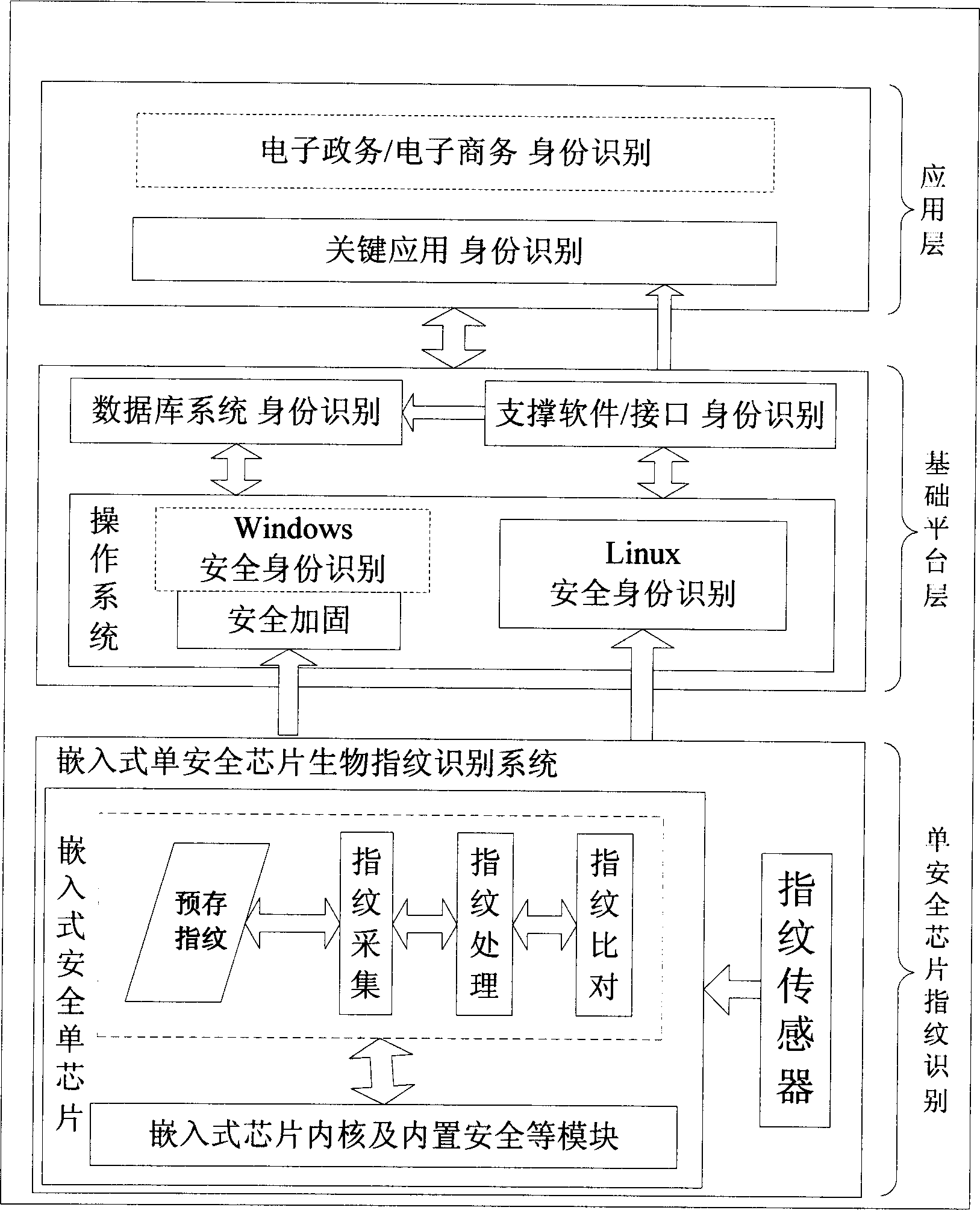
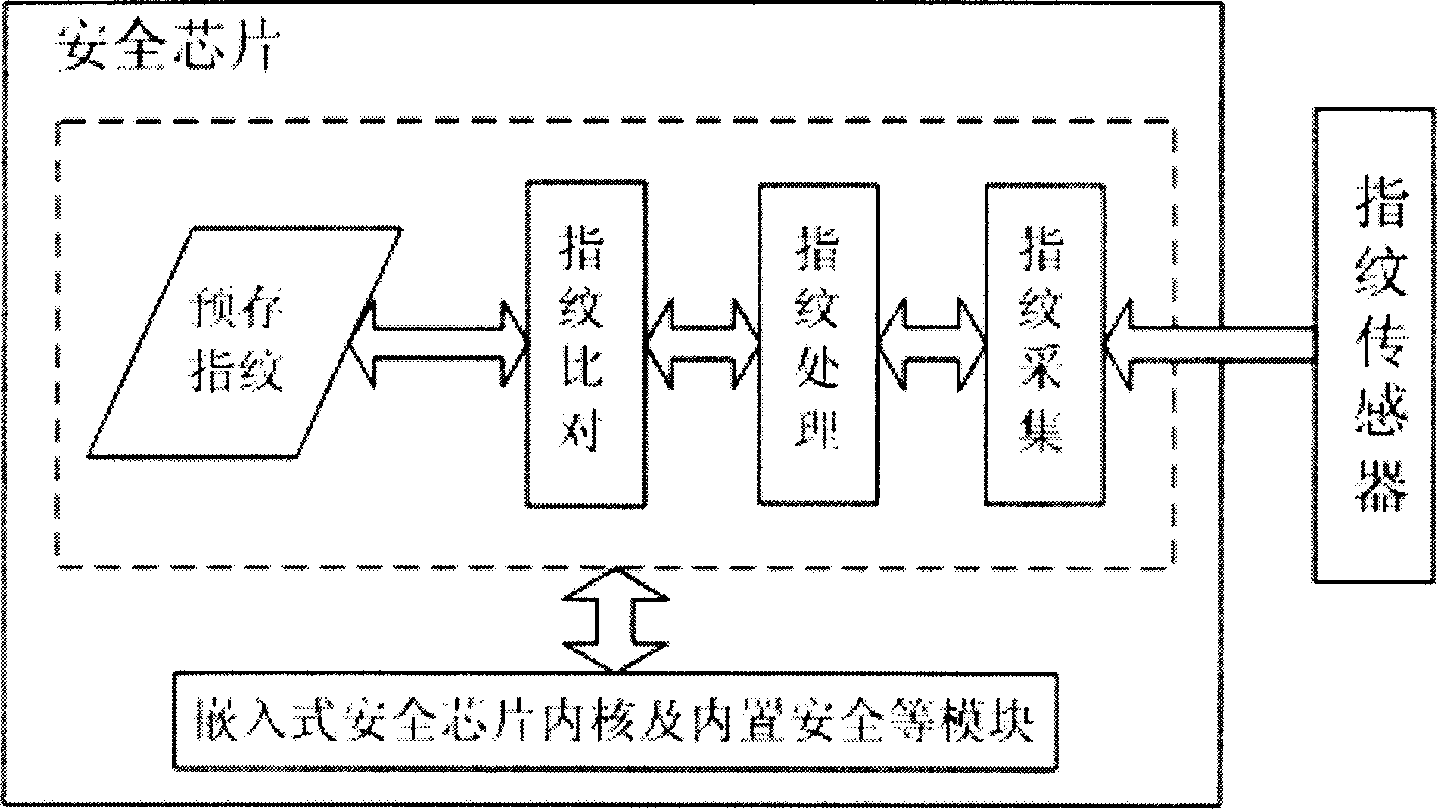
Embedded single secure chip biological fingerprint recognition system and method thereof
InactiveCN1885315AIntegrity guaranteedEnsure integrityCharacter and pattern recognitionDigital data authenticationOperational systemChip operating system
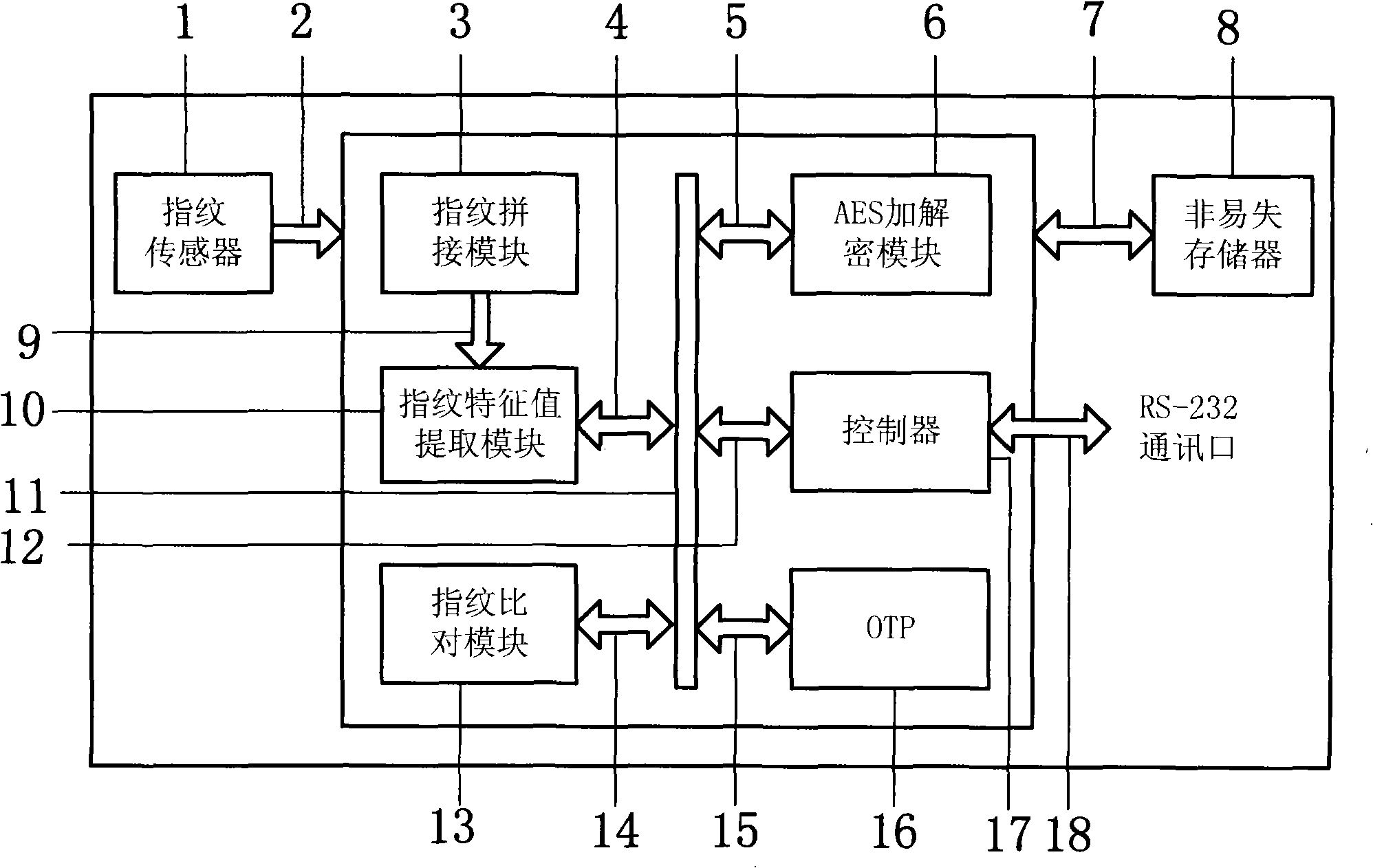
The invention relates to an embedded single safety chip biological fingerprint recognize system and relative method, wherein said safety chip contains chip operation system, internal micro processor, volatile memory and non-volatile memory, safety module and other manage module; the fingerprint collecting, processing and comparing modules are arranged inside the safety chip; the output of fingerprint sensor is connected to the fingerprint collecting module, the fingerprint processing module, and the fingerprint comparing module; and the inventive method comprises: collecting the original image information of fingerprint; extracting fingerprint character information to generate recognize code, to judge if initializing fingerprint register setting, and store recognize code into non-volatile memory of safety chip based on judged result, or extract the recognize code stored in the safety chip to be compared. The invention has high dual-factor safety and reliability, high stability and wider application.
Owner:上海一维科技有限公司
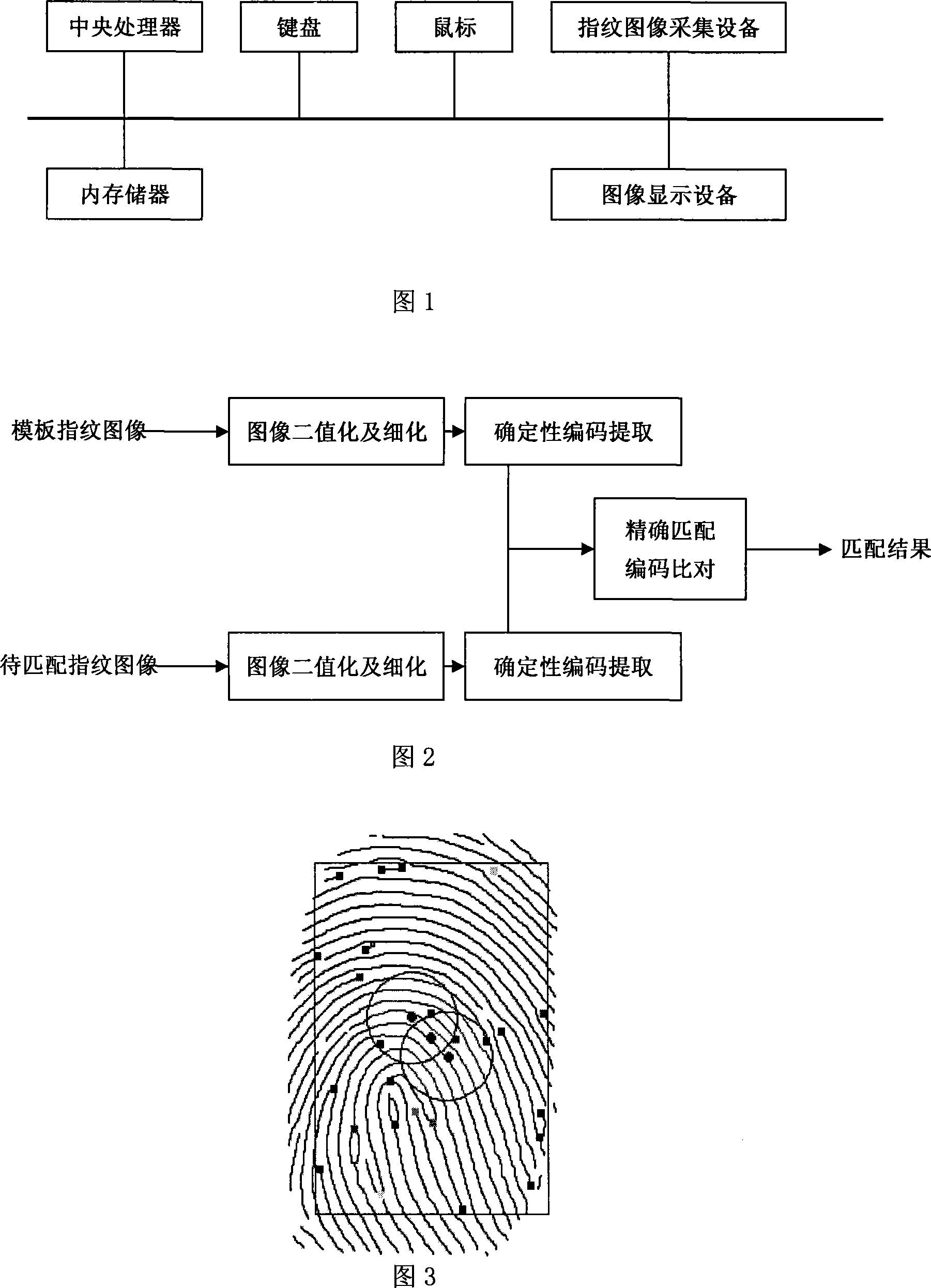
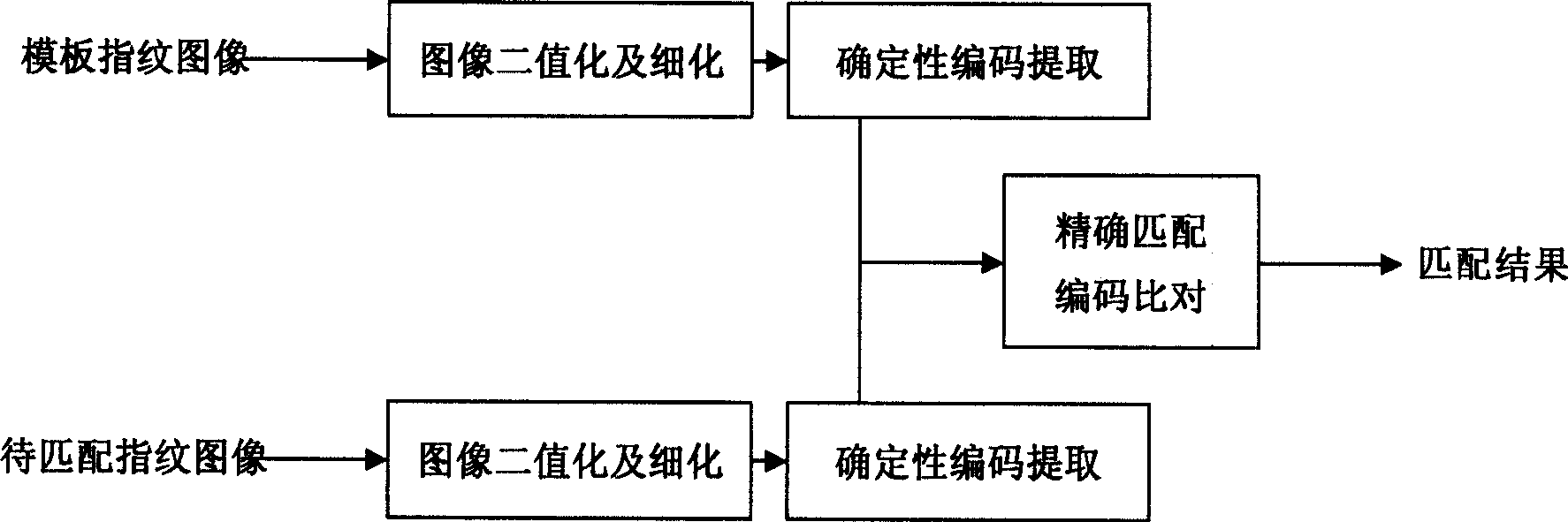
Certainty coding method and system in fingerprint identification
The present invention belongs to the computer biometrics technology and relates to a method and a system which adopt certainty coding to accurately match fingerprints during the process of fingerprint comparison. The present invention has the accurate matching by using characteristic of the certainty coding that a characteristic area can be selected from the fingerprint image and the characteristic value corresponding to the characteristic area, such as the total length of fingerprint ridge line, the entropy of the main direction of the direction field of the ridge line and the direction field of the pixel point, to conduct matching work. The certainty coding method and the fingerprint identification system built by the method overcome the defects, such as low accuracy rate and potential safety problems which are caused by adopting fuzzy matching algorithm in the traditional point fingerprint identification system.
Owner:TSINGHUA UNIV +1
Fingerprint storage comparison system based on behavioral analysis
ActiveCN103345616AImprove hit rateImprove contrast efficiencyCharacter and pattern recognitionRedundant operation error correctionComputer moduleDistributed computing
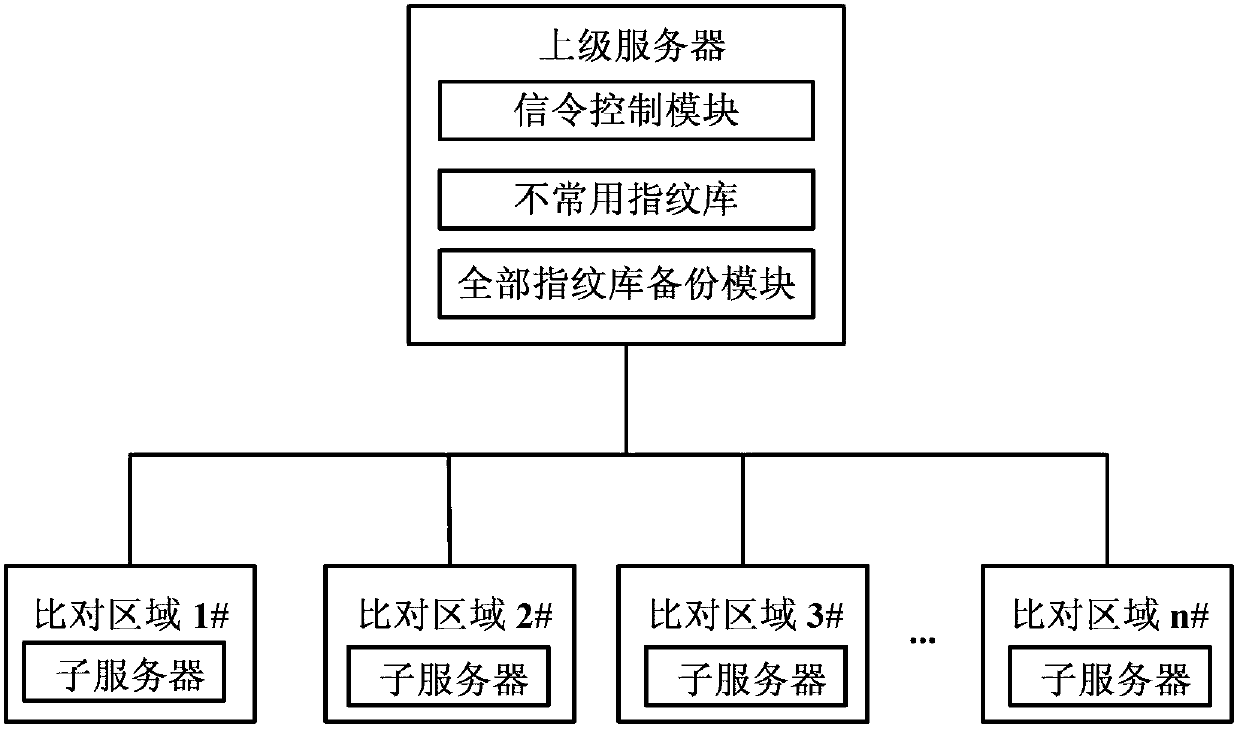
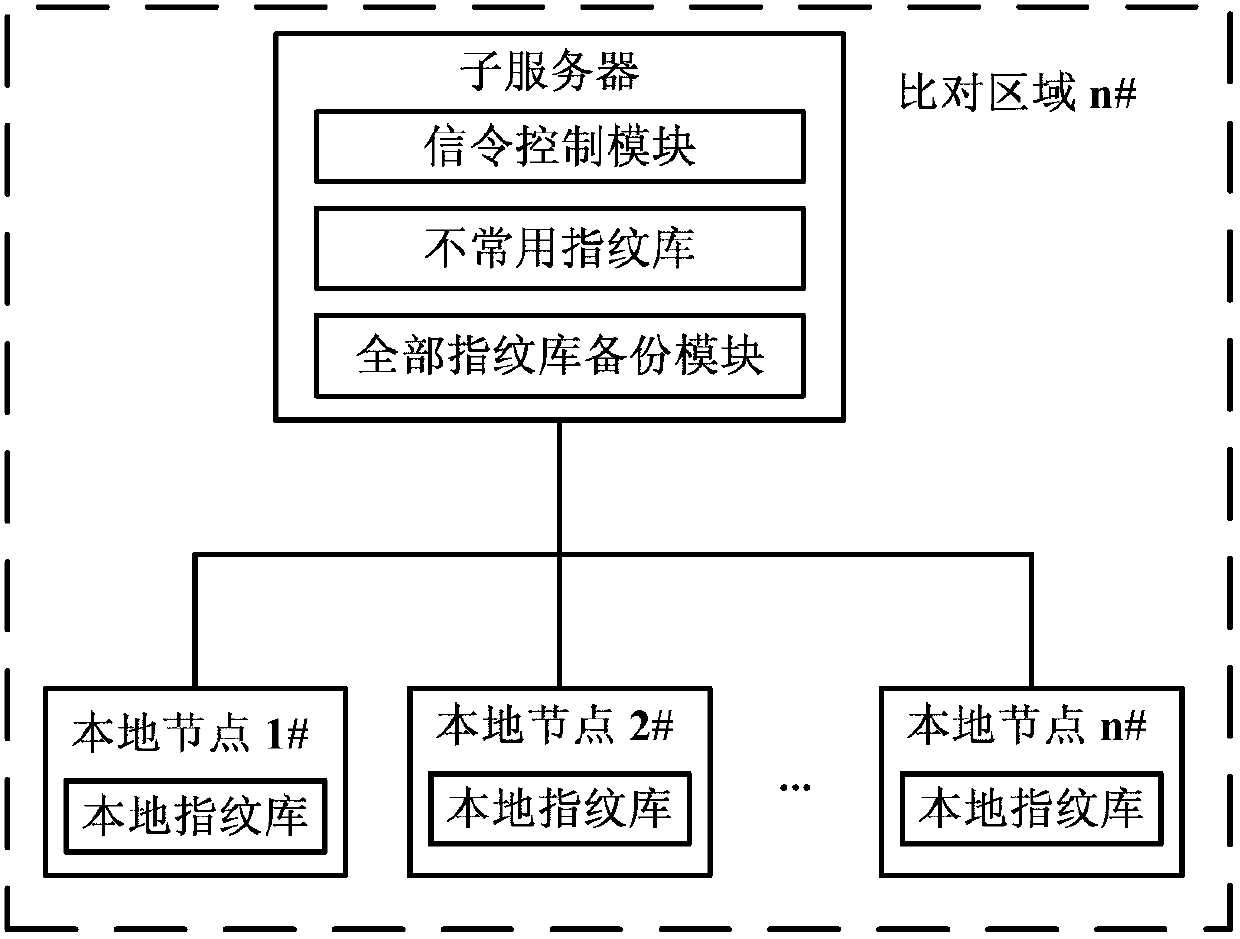
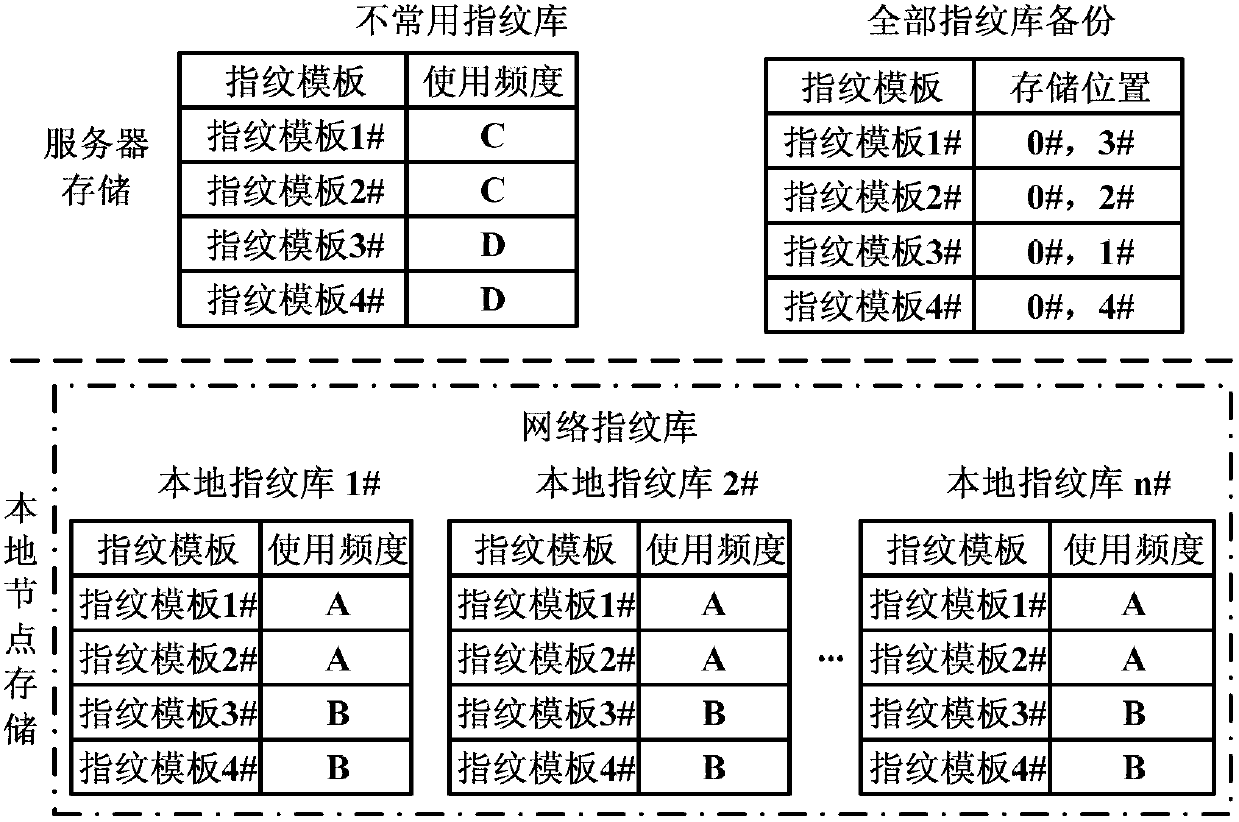
The invention discloses a fingerprint storage comparison system based on behavioral analysis, and relates to the field of fingerprint comparison. The system comprises an upper level server and a plurality of sub servers in comparison regions. The upper level server comprises a signaling control module, a fingerprint database which is not commonly used and an all fingerprint database backup module. The signaling control module is used for forwarding and responding to all signaling and controlling transmission of instructions, the fingerprint database which is not commonly used is used for storing storage and comparison of fingerprint modules which are not commonly used in a management region, the all fingerprint database backup module is used for backing up all fingerprint modules in the region, each comparison region comprises a sub server and a plurality of local nodes, and each sub server also comprises a signaling control module, a fingerprint database which is not commonly used and an all fingerprint database backup module. The fingerprint storage comparison system can effectively reduce the comparison range, shortens comparison time and improves comparison efficiency.
Owner:武汉世纪金桥安全技术有限公司
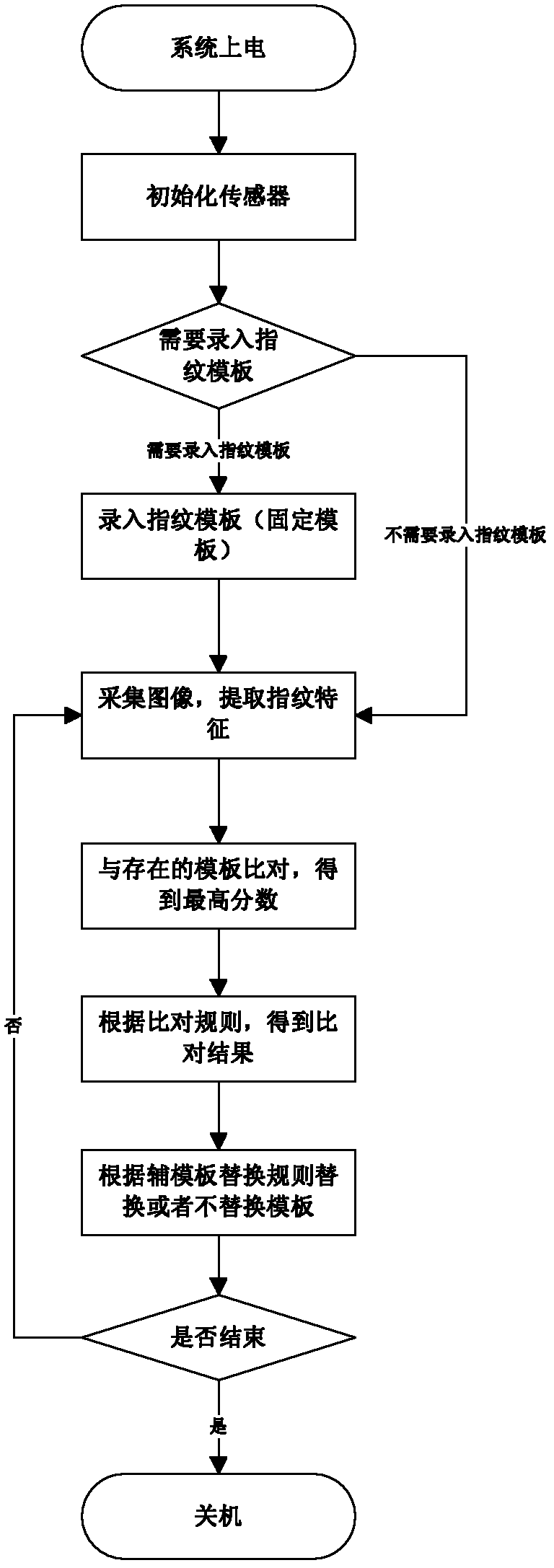
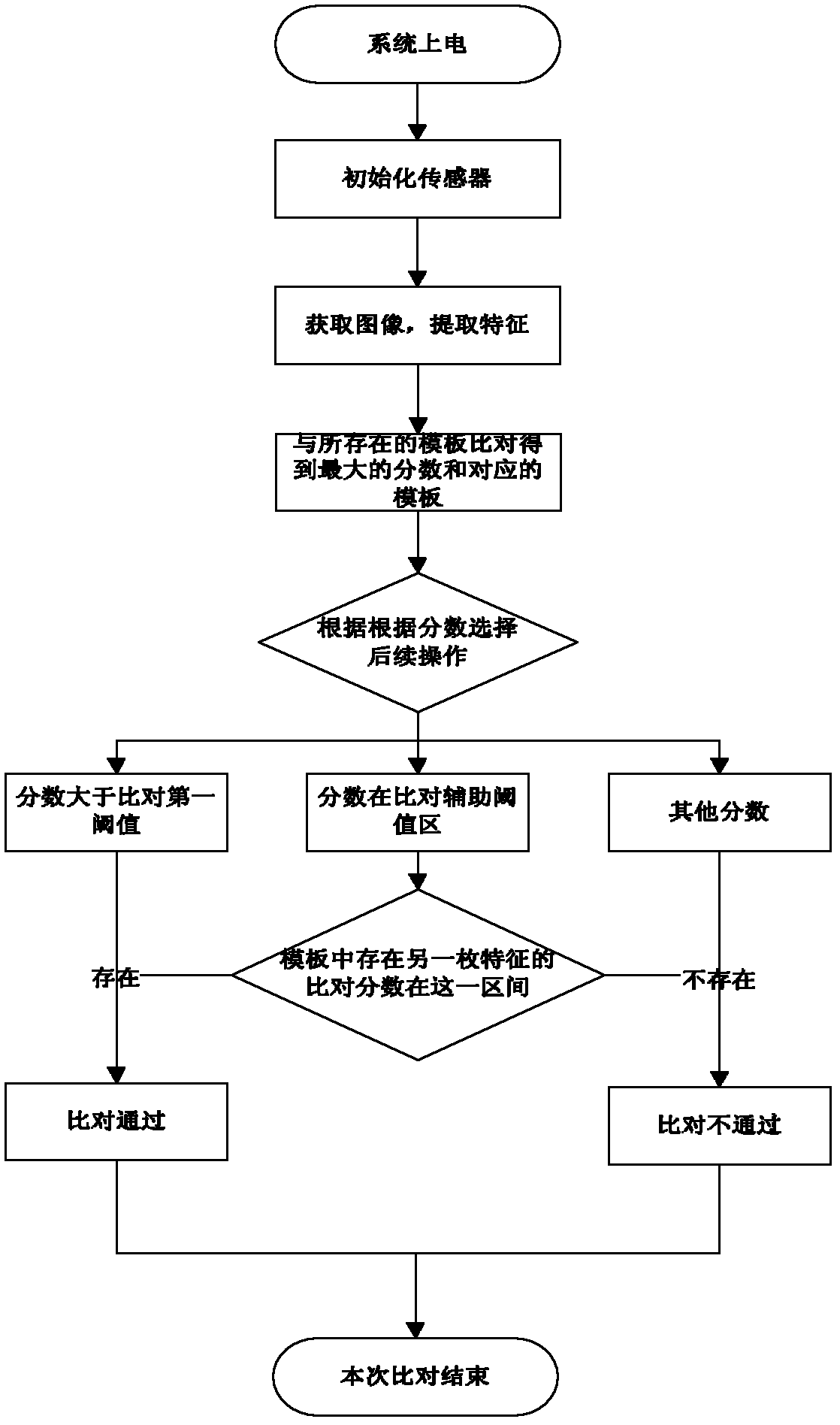
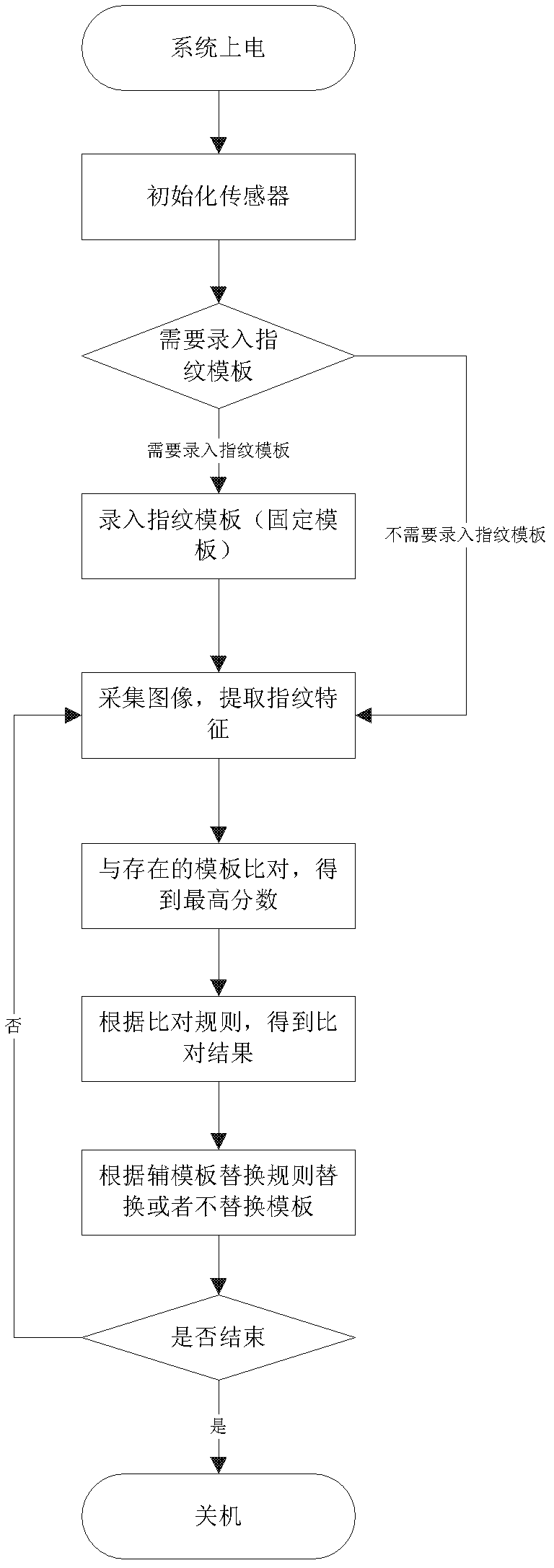
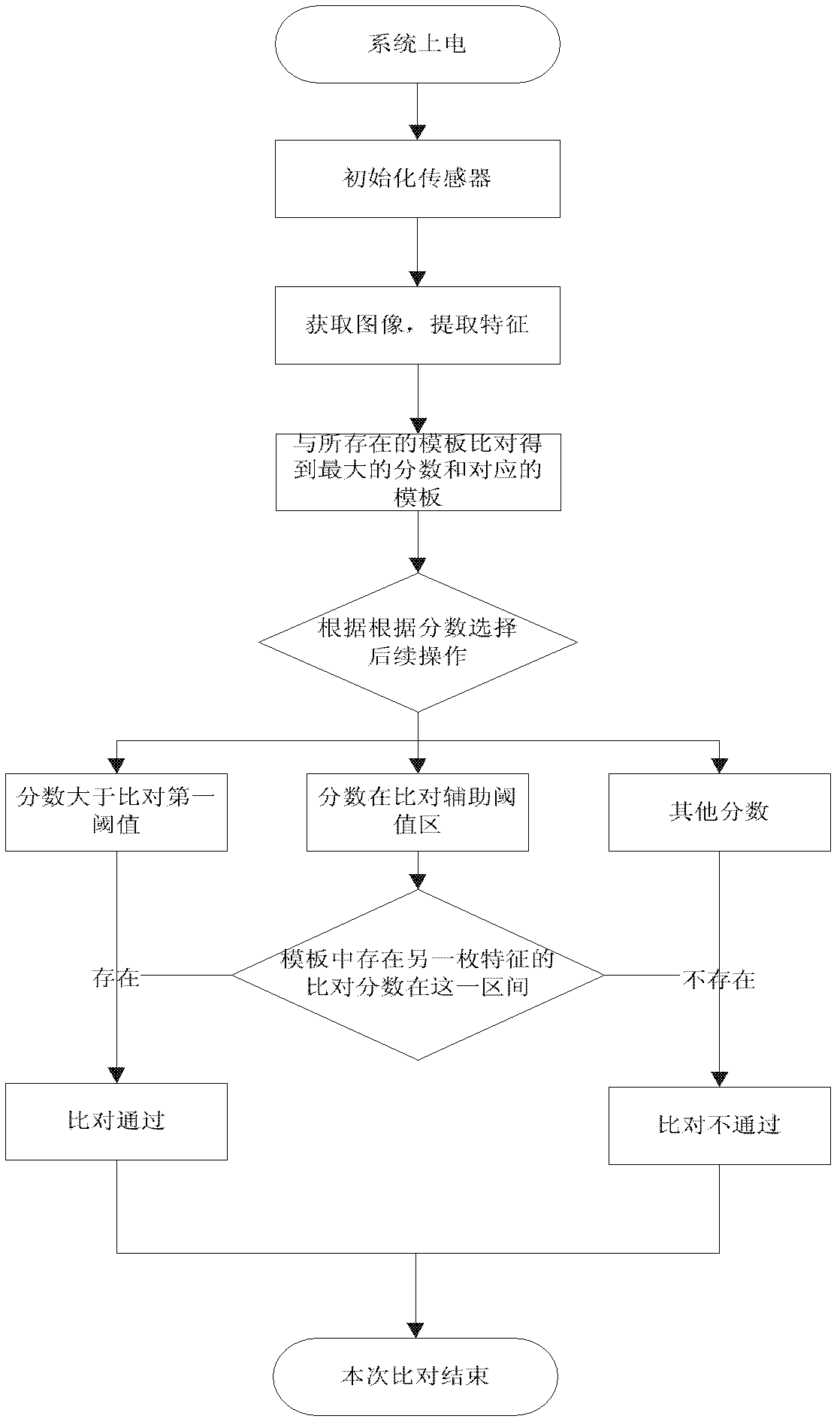
Method for reducing false reject rate of fingerprint comparison
ActiveCN102254167AReduce rejection rateEasy to useCharacter and pattern recognitionPattern recognitionEngineering
The invention relates to a method for reducing the false reject rate of fingerprint comparison. The method comprises the following steps of: extracting fingerprint characteristics by a fingerprint sensor; quickly searching in a plurality of templates, and comparing the templates with the existing template to obtain the highest comparison score; and judging whether comparison passes according to acomparison passing rule, and replacing the templates or not according to an auxiliary template replacement rule. The method has the advantages that: an auxiliary template is added and dynamically updated in an application process, so the capacity for environmental adaptation of the sensor is greatly improved, anti-aging capacity is improved, the range of a comparison object is expanded, and the false reject rate is effectively reduced; the fingerprint characteristics in a fingerprint comparison auxiliary threshold interval are required to be compared with fingerprint templates one by one; andwhen more than two characteristic comparison scores are in the fingerprint comparison auxiliary threshold interval, comparison is determined to pass, so the false reject rate of the fingerprint comparison is effectively reduced under the condition that no false accepting is guaranteed.
Owner:HANGZHOU SYNOCHIP DATA SECURITY TECH CO LTD
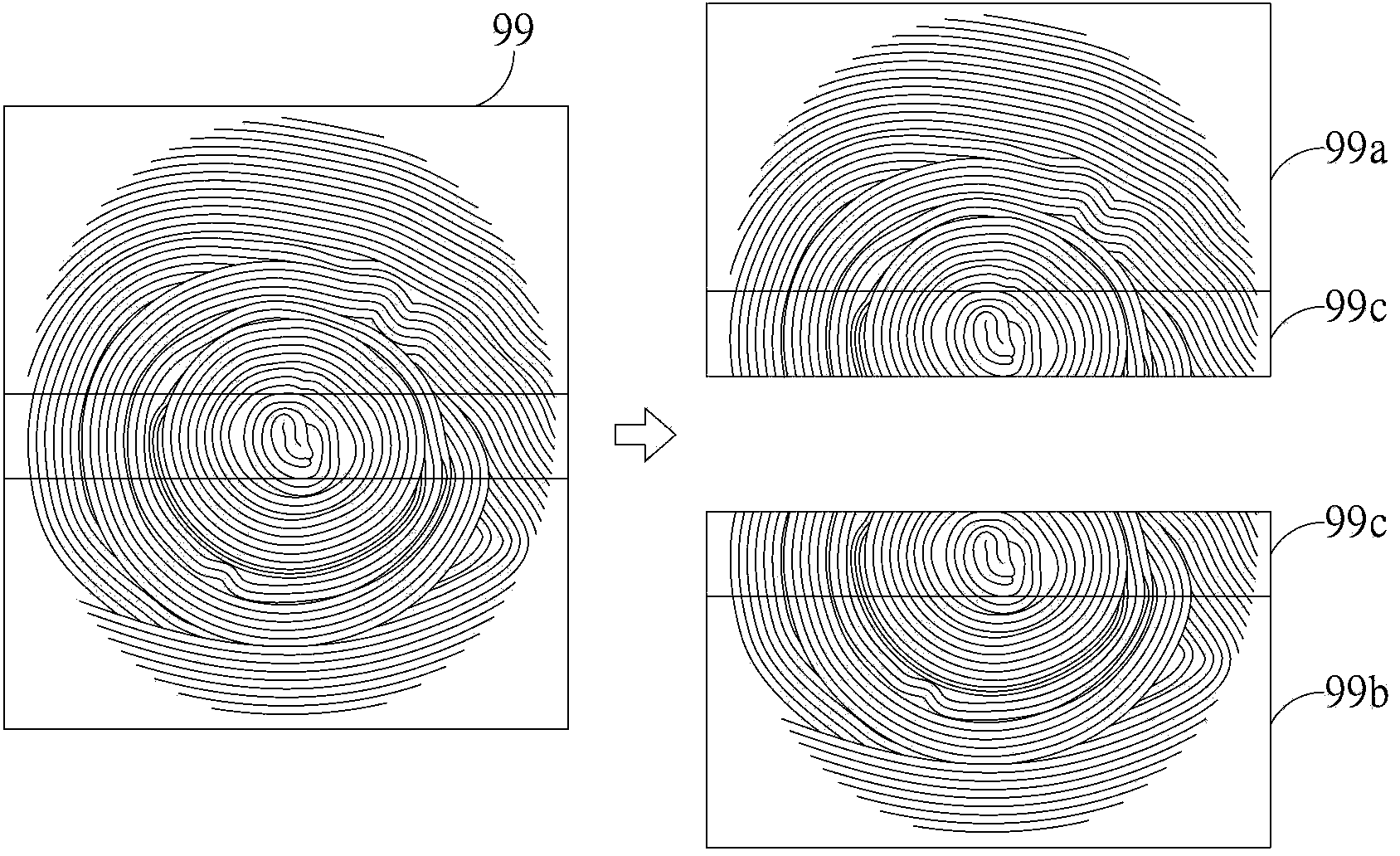
Fingerprint alignment method, fingerprint collection apparatus, fingerprint alignment apparatus
ActiveCN101504724AReduce alignment timeImprove alignment efficiencyCharacter and pattern recognitionPattern recognitionComputer vision
The invention provides a method for fingerprint alignment, a fingerprint acquisition device and a fingerprint alignment device, wherein the method for the fingerprint alignment comprises the following steps of: extracting a knuckle line from a two-dimensional fingerprint image; calculating a position relation between the extracted knuckle line and a prestored knuckle line; and aligning the extracted knuckle line with the prestored knuckle line according to the position relation so that a fingerprint containing knuckle texture aligns with a prestored fingerprint. The method for the fingerprint alignment performs contrast calculation on the extracted knuckle line and the prestored knuckle line by extracting the knuckle line, and acquires an angle between the extracted knuckle line and the prestored knuckle line, thereby achieving the aim of aligning fingerprints by rotating the angle. The method only needs to realize the coincidence of the extracted knuckle line and the prestored knuckle line, avoids the complexity of the process that the prior method for the fingerprint alignment needs to match minutiaes, shortens the time of the fingerprint alignment, and improves the efficiency of the fingerprint alignment.
Owner:VIMICRO ELECTRONICS CORP
Fingerprint matching method and apparatus
ActiveUS8588484B2VariationIncrease awarenessMatching and classificationComputer graphics (images)Computer vision
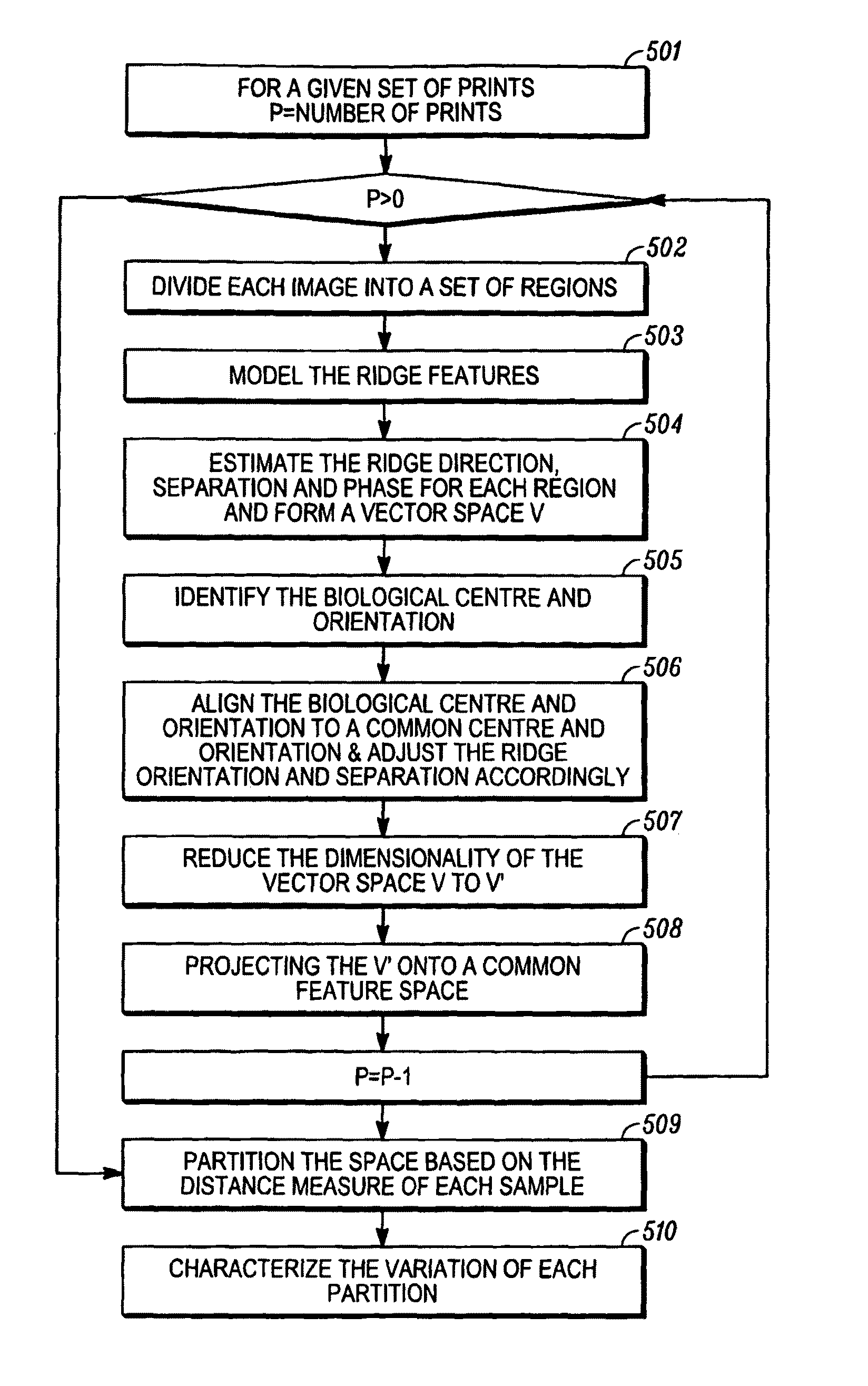
Exemplary embodiments of method and apparatus for processing the images of fingerprints can be provided. For example, aligned images can be subjected to a tessellation process, whereas each image can be partitioned into a number of regions. Within each region at least one parameter associated with the ridges can be measured and stored. Such exemplary parameter can include, e.g., the prevailing ridge orientation, the average ridge separation and the phase of the ridges. The data can be projected and stored in a multidimensional coordinate system, whereas the representations of any two data can be separated by an amount corresponding to the dissimilarity of these data.
Owner:WARWICK WARP
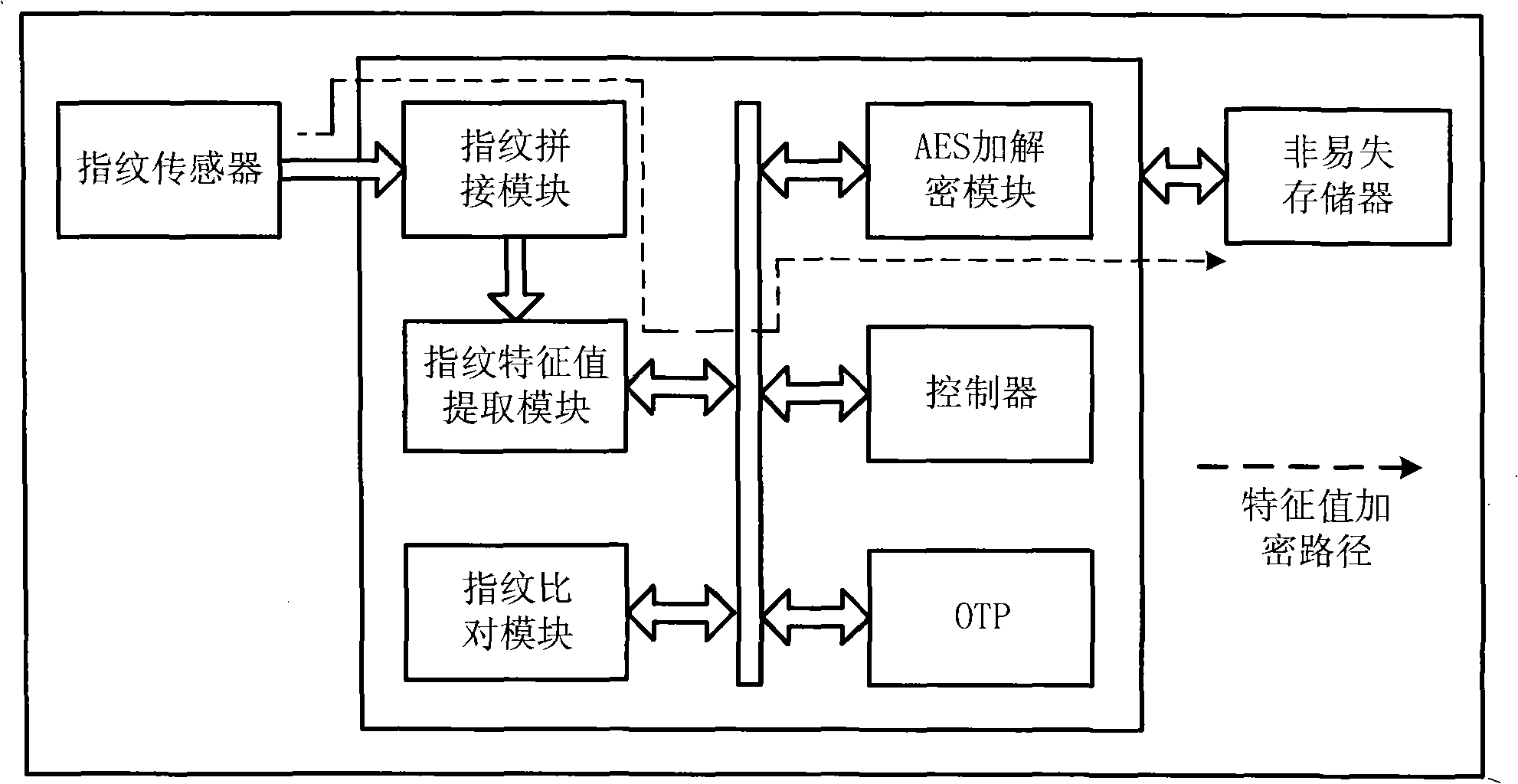
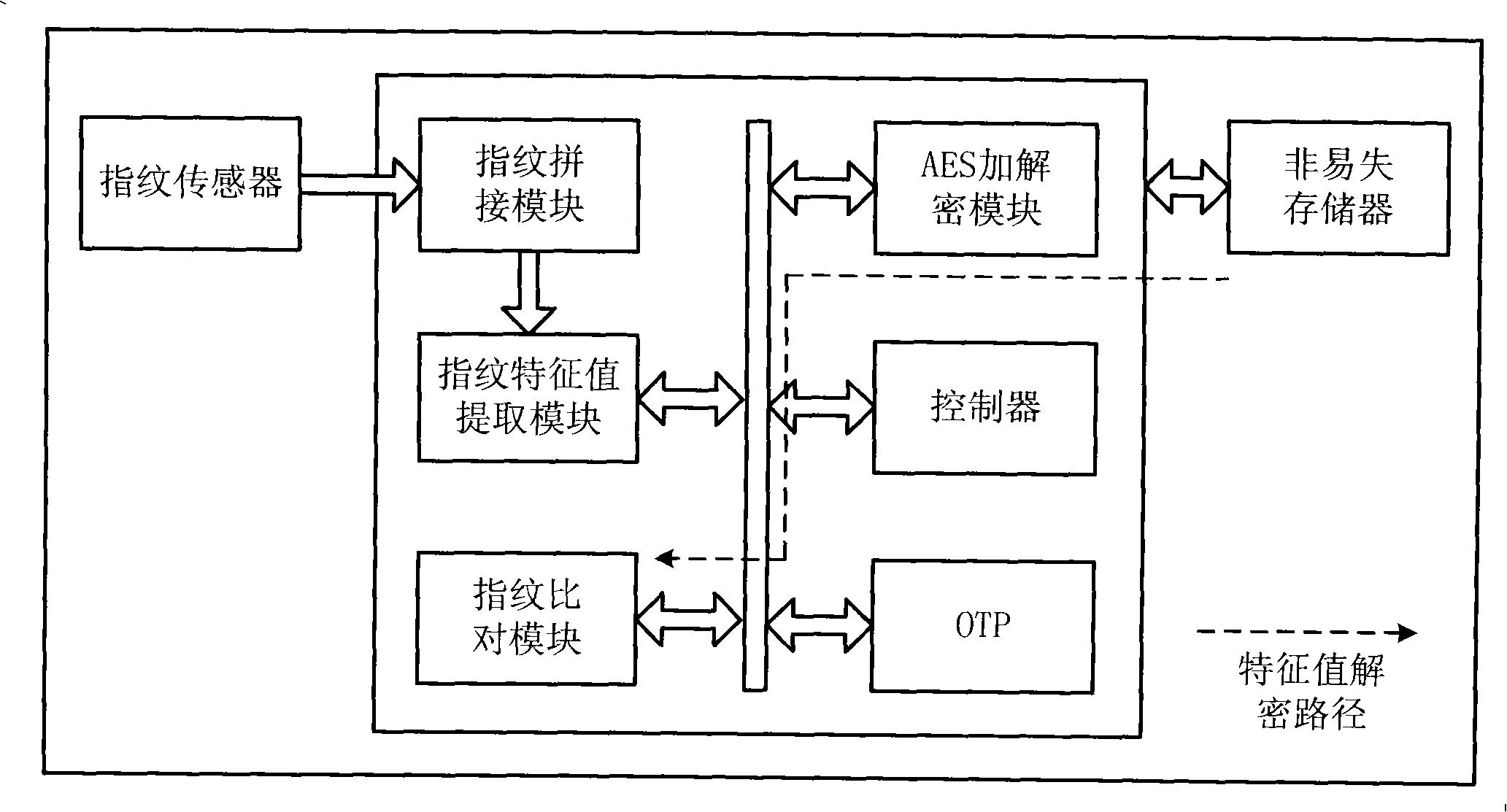
Fingerprint characteristic value encrypting/decrypting method and system
InactiveCN101272245AImprove securitySolve the security problem of remote transmissionUser identity/authority verificationBus interfaceEncryption decryption
The invention relates to a fingerprint eigenvalue encryption-decryption system which comprises a fingerprint sensor, a nonvolatile store and a fingerprint encryption-decryption chip. The fingerprint encryption-decryption chip comprises a special interface of the fingerprint sensor, a fingerprint matching module, a fingerprint eigenvalue extracting module, a special channel of the fingerprint matching and the fingerprint eigenvalue extracting, a bus interface of the fingerprint eigenvalue extracting module, a fingerprint comparing module, a bus interface of the fingerprint comparing module, an interface of the nonvolatile store, a controller, a bus interface of the controller, a communication port, an internal bus. The fingerprint encryption-decryption chip also comprises an encryption-decryption module, a one time programmable program store, a bus interface of the encryption-decryption module and a bus interface of the one time programmable program store. The invention can improve the safety of the fingerprint eigenvalue and enhancing the safety level. The integration of the fingerprint eigenvalue extracting, the fingerprint comparing and the encryption-decryption reduces the cost of the system; the system solves the safety problem of remote transmission of the fingerprint eigenvalue, thus leading a fingerprint database to be easily centralized and conveniently managed and searched.
Owner:合肥方程式电子科技有限公司
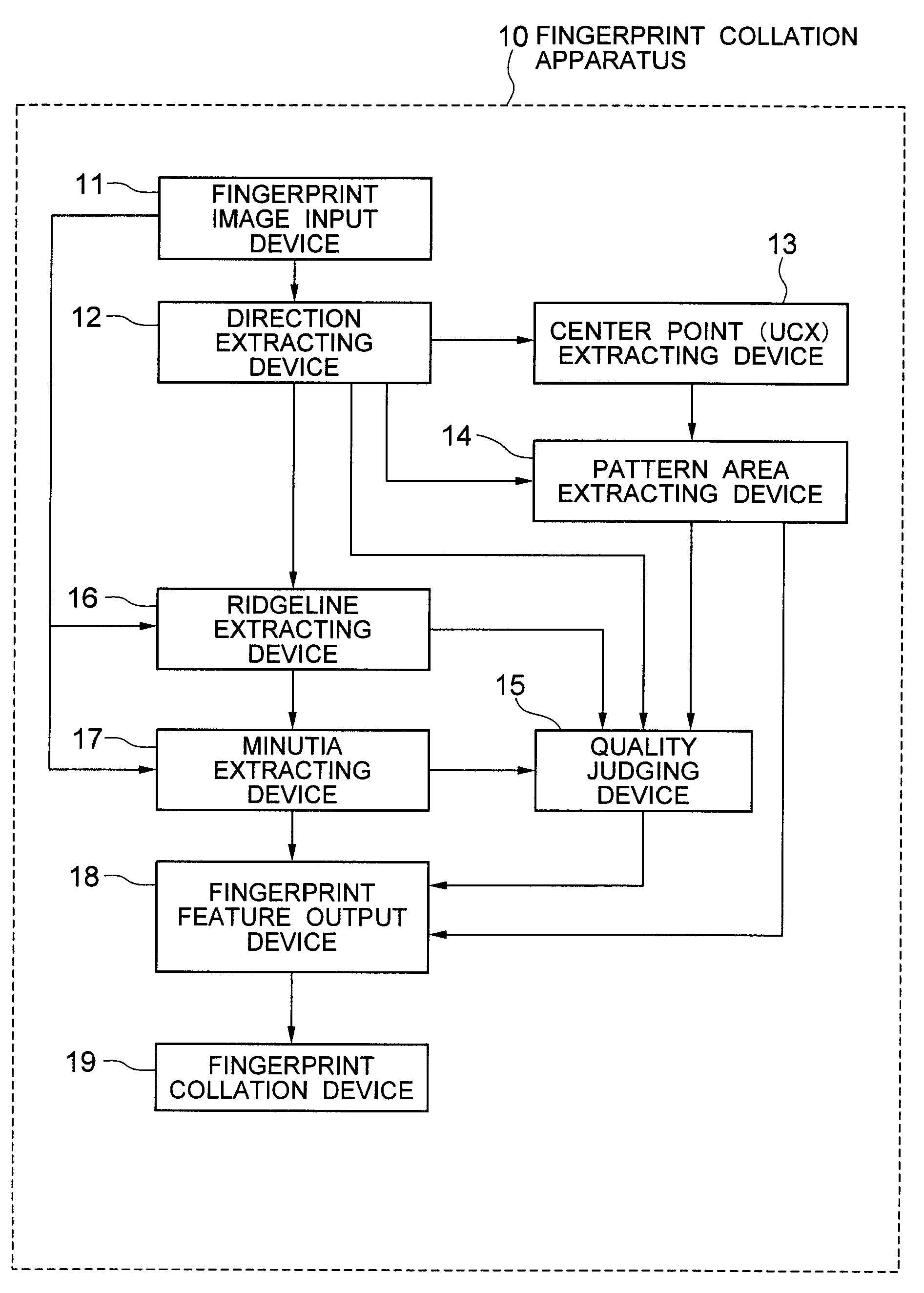
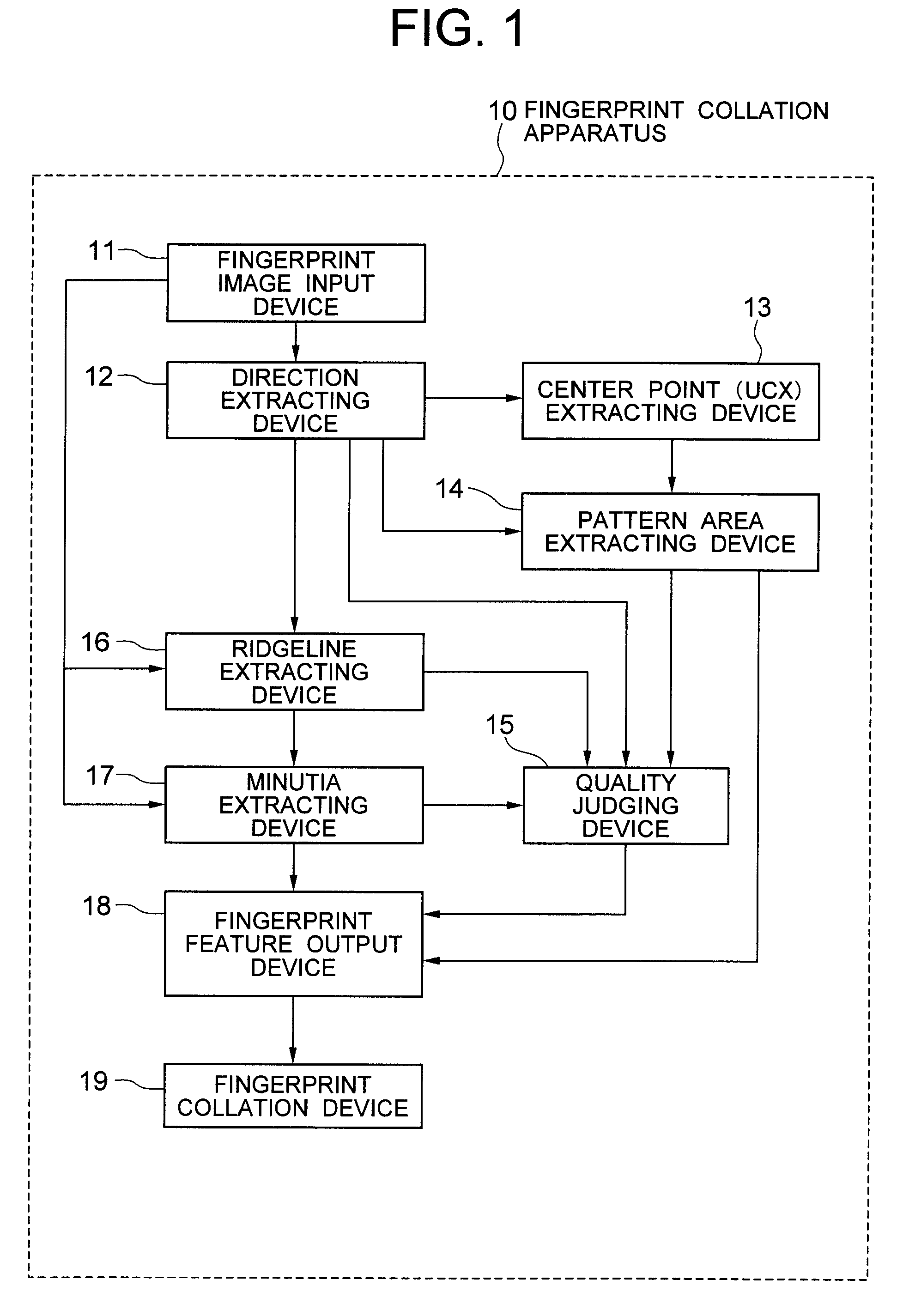
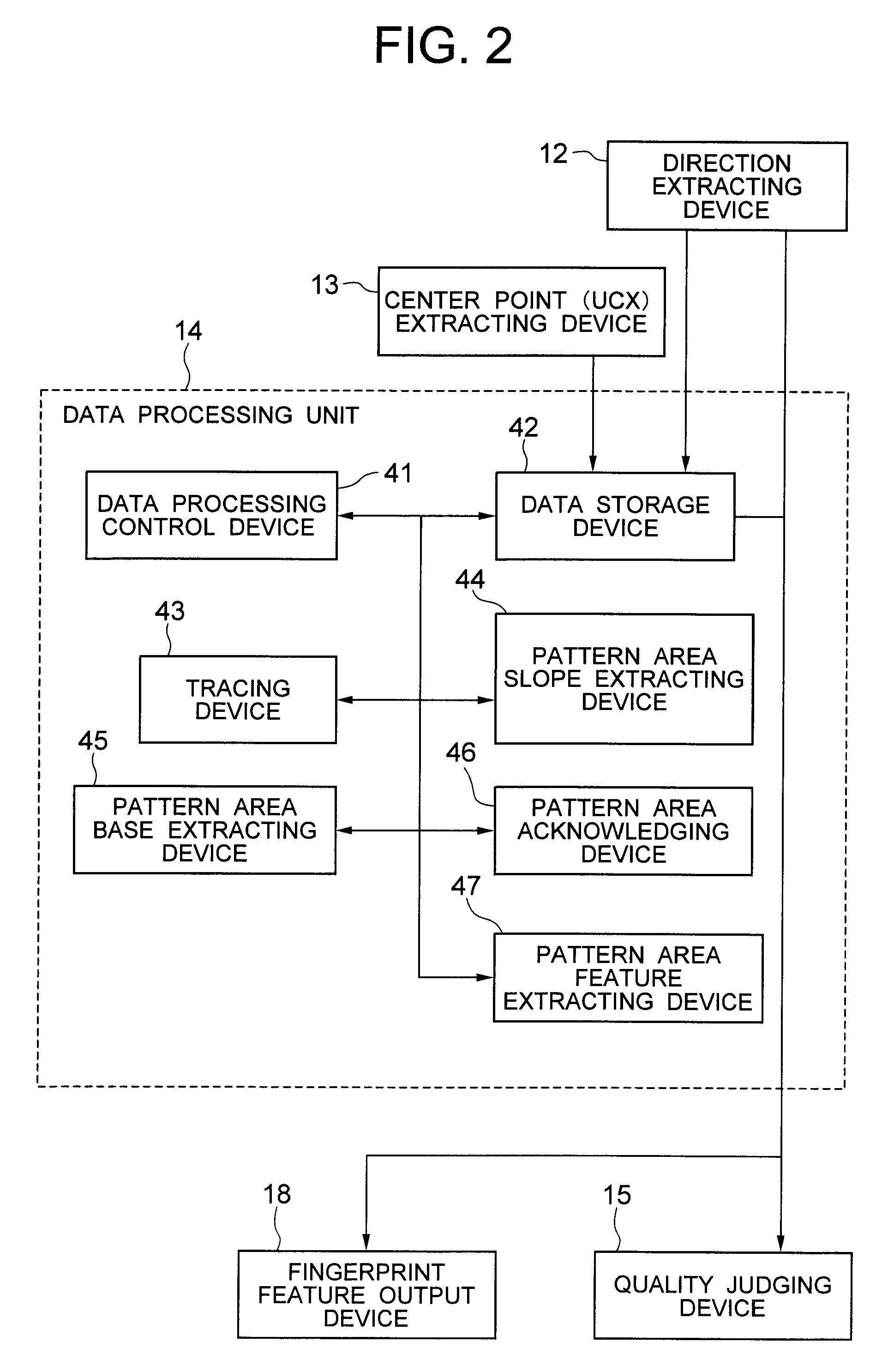
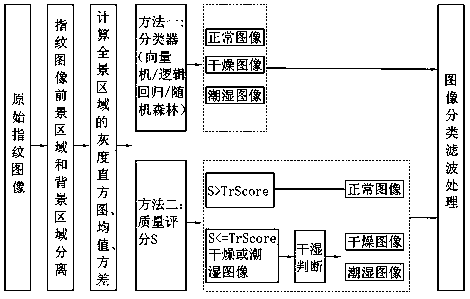
Fingerprint collation apparatus, fingerprint pattern area extracting apparatus and quality judging apparatus, and method and program of the same
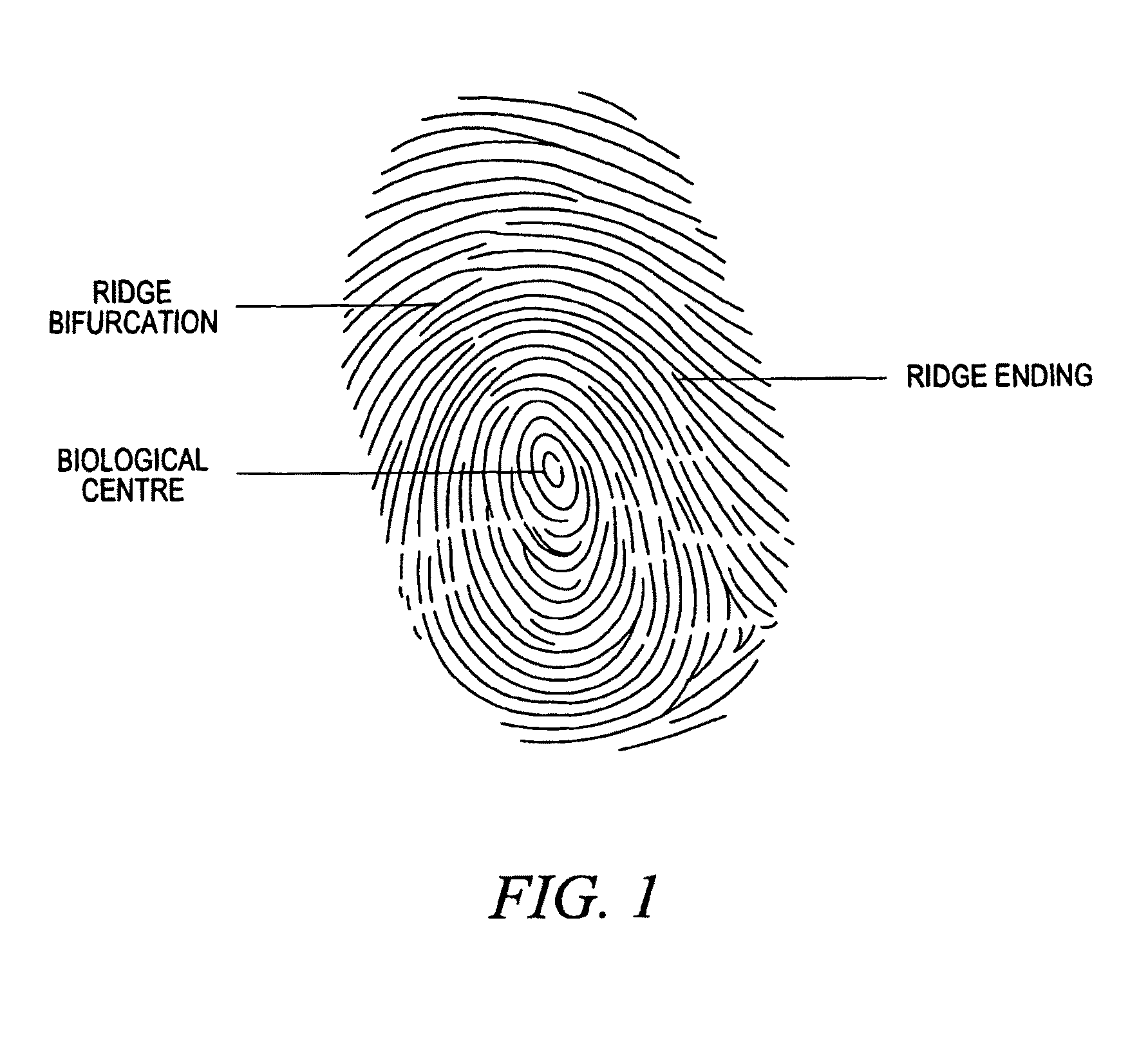
To enable extraction of a specific area (pattern area) that includes a characteristic part of the inherent pattern of individual fingerprint from an inputted fingerprint image of a human being or other creature. The pattern area is extracted as the minimum area that is surrounded by a right pattern area slope, a left pattern area slope, and pattern area bases. The right (left) pattern area slope is a fingerprint ridge which runs towards the outside on the right (left) side from the start point that is located on the upper side of the center point of the fingerprint image, and satisfies a prescribed condition. The pattern area base is a fingerprint ridge which runs on the lower side of the center and satisfies a prescribed condition.
Owner:NEC CORP
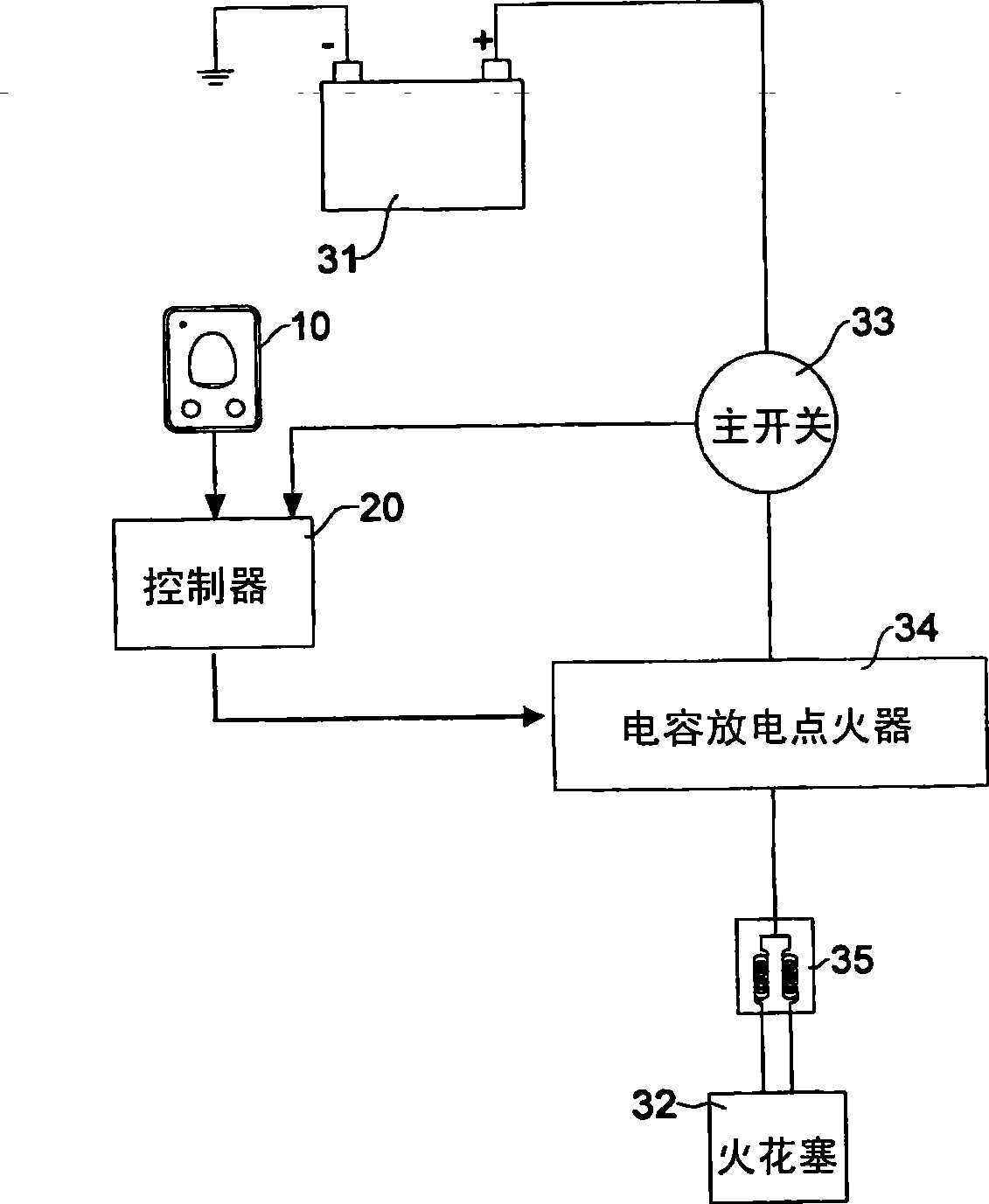
Fingerprint identification anti-theft device and method for motorcycle
InactiveCN101369354AReduce the chance of theftImprove protectionAnti-theft cycle devicesChecking apparatusComputer moduleIdentification device
Provided is a motor fingerprint identification device and a method, wherein a fingerprint identification module and a controller which are connected to a firing circuit of the motor are arranged on a car body of the motor, and main control fingerprints are presupposed and stored in the module. When a user starts the fingerprint identification module and executes locking action, the next time when starting the motor, the user is required to perform fingerprint alignment identification, if the alignment result matches with the fingerprint used for locking originally, the motor is allowed to start, otherwise start is inhibited, thereby preventing the motor from thieving.
Owner:KYMCO
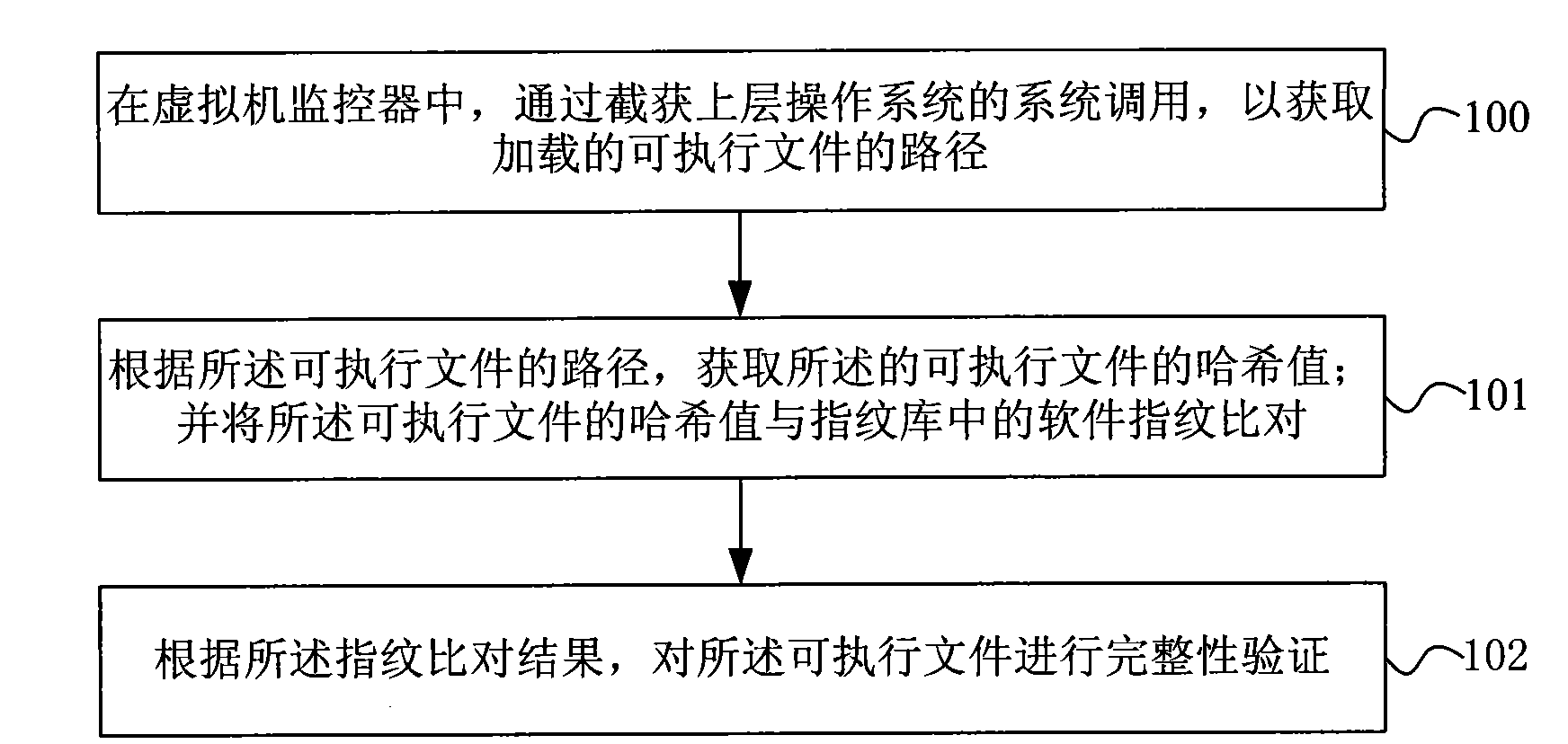
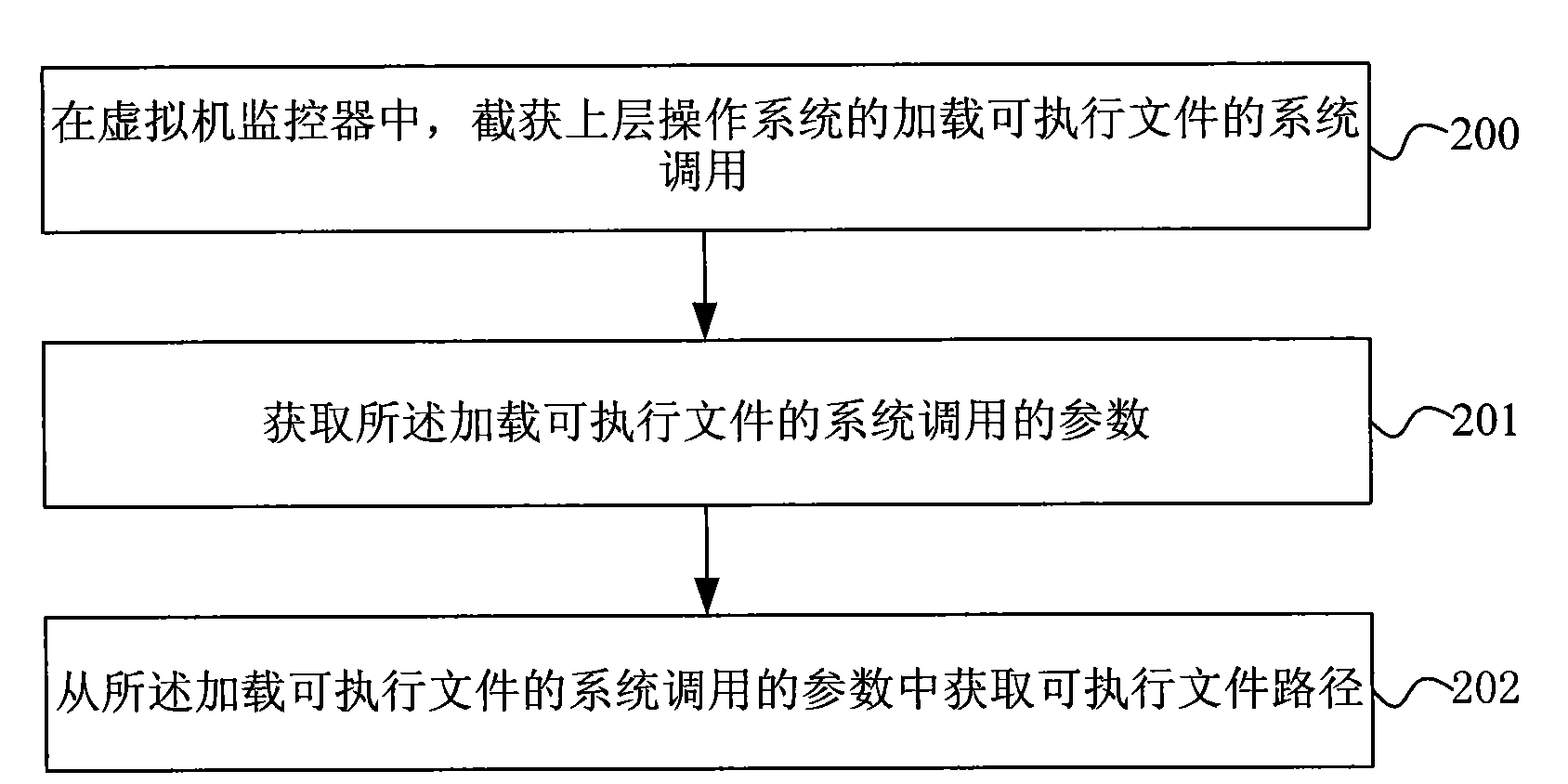
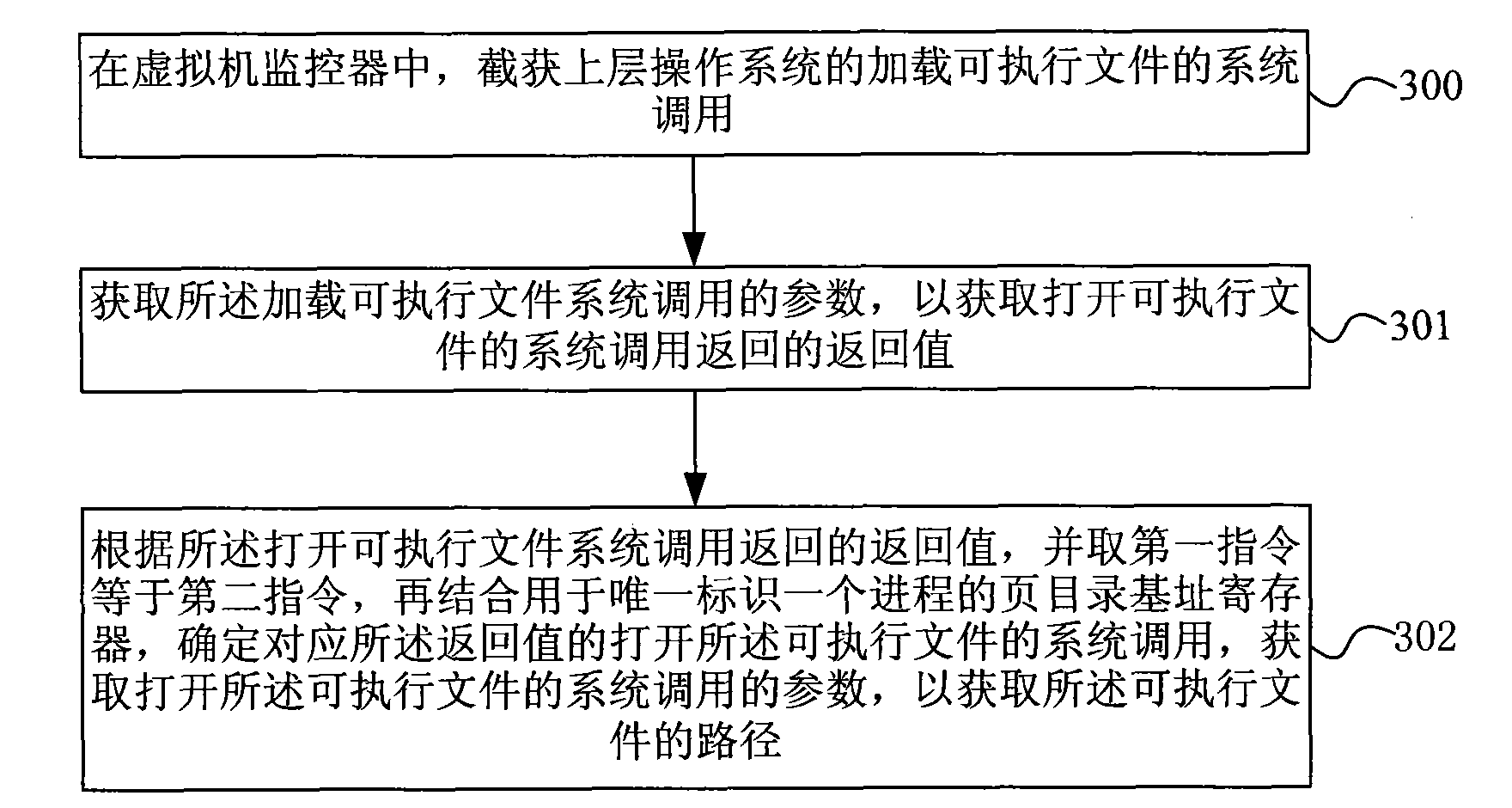
Method and system for verifying software completeness
InactiveCN101593259BImprove securityVersatilityPlatform integrity maintainancePathPingOperational system
The invention discloses a method for verifying software completeness. The method comprises the following steps: acquiring path of a loaded executable file through capturing system call of an upper operation system in a virtual machine monitor; acquiring a Hash value of the executable file according to the path of the executable file; comparing the Hash value of the executable file with software fingerprints in a fingerprint bank; and carrying out completeness verification on the executable file according to the result of fingerprint comparison. The invention also discloses a software completeness verification system. The method and the system for software completeness verification realize software completeness verification in the virtual monitor, is independent of the operation system without depending on completeness of the operation system, improves security of the system, and has universality and compatibility. The technical proposal belongs to completeness verification of softwarein loading period, reduces verification cost without support of auxiliary hardware, reduces cost and improves performance compared with the method for verifying completeness of a file system.
Owner:BEIHANG UNIV
Non-contact fingerprint identification method and device, terminal and storage medium
ActiveCN112232155AImprove experienceDigital data authenticationBiometric pattern recognitionRadiologyComputer vision
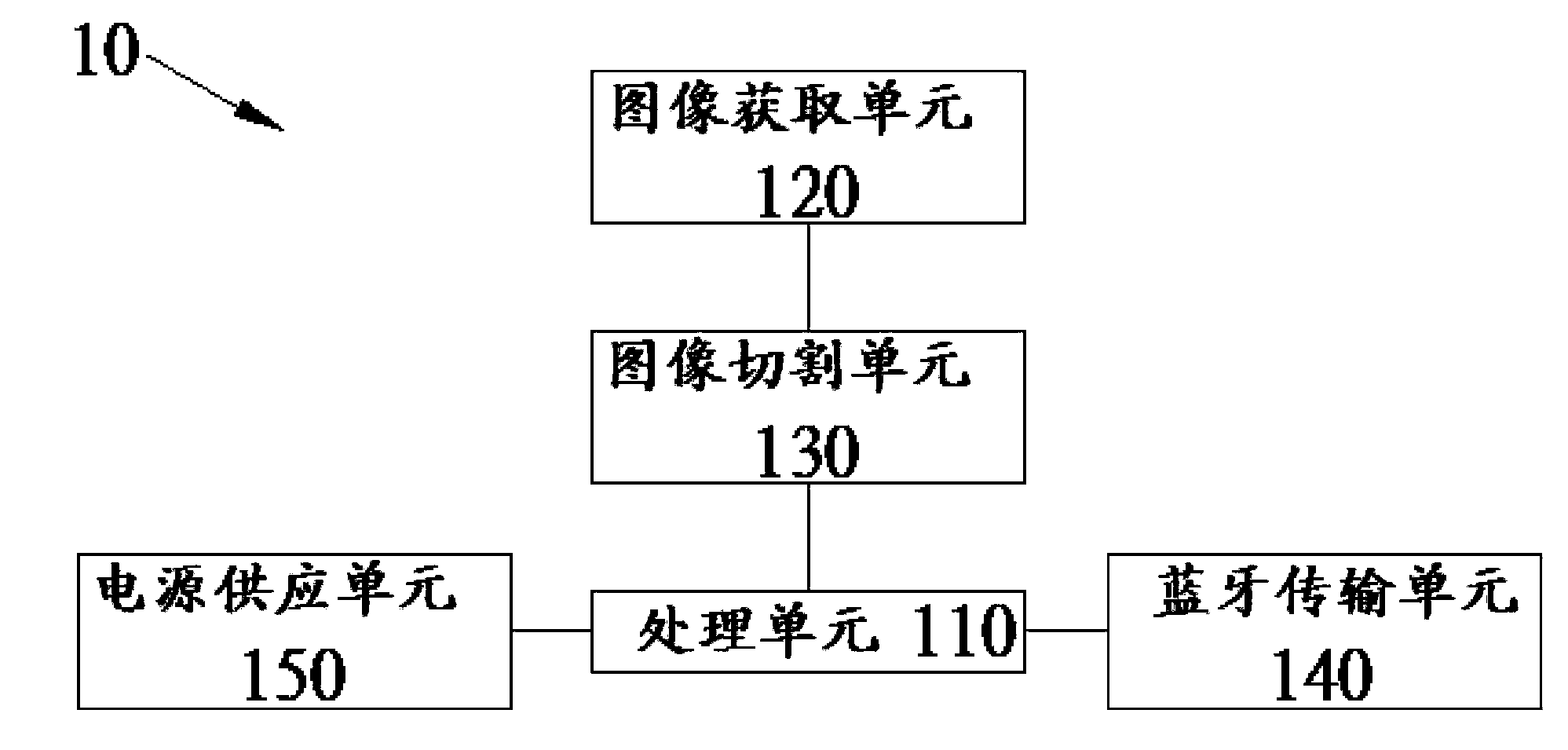
The invention provides a non-contact fingerprint identification method and device, a terminal and a storage medium. The method comprises the following steps: a finger identification step of shooting ahand of an identification object, judging whether a finger exists in a shot picture or not, and determining the position of the finger when the finger exists; a fingerprint acquisition step of performing focusing photographing on the finger under the condition that the finger is detected in the finger identification step, and acquiring respective fingerprint images of the finger; an image transmission step of encrypting the fingerprint images of the fingers acquired in the fingerprint acquisition step, and transmitting the encrypted fingerprint images to a comparison system; a fingerprint comparison step: comparing the fingerprint image with fingerprint data in the comparison system to obtain a comparison result. According to the method disclosed in the invention, non-contact fingerprintidentification can be realized, and the user experience is improved.
Owner:BEIJING ZHIJIAN MOQI TECH CO LTD
Fingerprint identification and verification system and method thereof
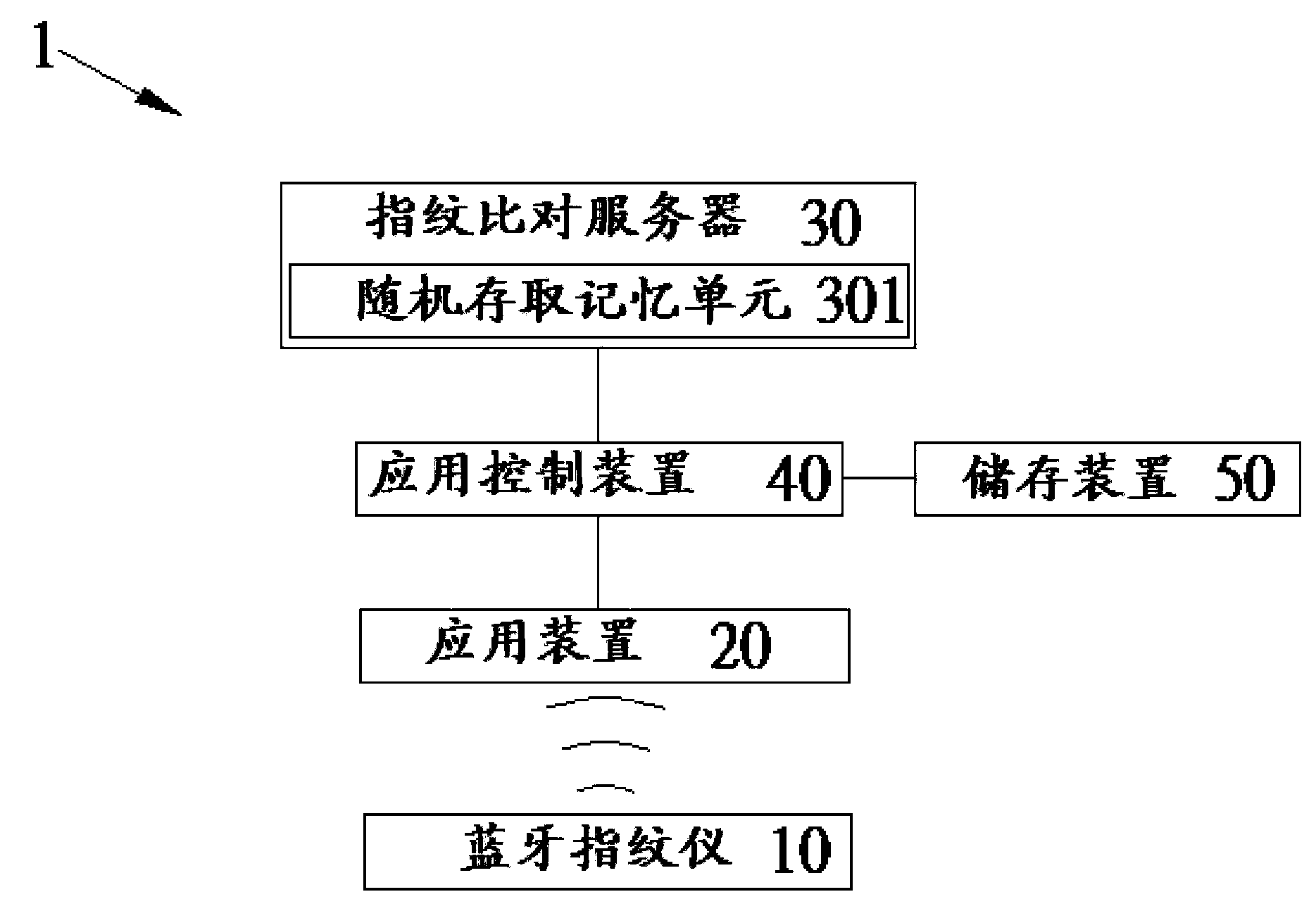
InactiveCN103678978AShorten the timeFaster thanCharacter and pattern recognitionDigital data authenticationComputer hardwareBluetooth
The invention provides a fingerprint identification and verification system and a method thereof. The fingerprint identification and verification system includes a Bluetooth fingerprint device, an application device, a fingerprint identification server, and an application control device. The Bluetooth fingerprint device captures a fingerprint image, extracts the minutiae data from the fingerprint image, and sends the minutiae data to the application device. The application device transmits the minutiae data and a verification request to the application control device and the application control device transmits the minutiae data to the fingerprint identification server to perform the fingerprint identification process. The fingerprint identification server sends a verification result on which the application control device depends to accept or refuse the verification request from the application device. As a result, the speed of the user's identification process can be increased by using the Bluetooth fingerprint device to derive the minutiae data.
Owner:EGIS TECH
Alignment-free fingerprint matching method based on encrypted circuit and computing circuit
InactiveCN103761509AImplement fingerprint matchingProtect data privacyCharacter and pattern recognitionPattern recognitionAuthentication server
The invention discloses an alignment-free fingerprint matching method based on an encrypted circuit. The alignment-free fingerprint matching method based on the encrypted circuit comprises the steps that a detail point template set of fingerprints and an onsite sample detail point set are established, a line characteristic set OT and a local structure characteristic set DT are established based on the detail point template set, and a line characteristic set OQ and a local structure characteristic set DQ are established based on the onsite sample detail point set; point-by-point comparison is carried out on elements in the line characteristic set OT and elements in the line characteristic set OQ and on elements in the local structure characteristic set DT and elements in the local structure characteristic set DQ, and thus an NT*NQ matrix UO and an NT*NQ matrix UD are formed; similarity computing is carried out on the matrix UO and the line characteristic set OQ, the similarity computing is carried out on the matrix UD and the local structure characteristic set DQ, and the matching of the fingerprints is completed according to similarity. The invention discloses a computing circuit at the same time. The alignment-free fingerprint matching method based on the encrypted circuit and the computing circuit achieve the purpose that the fingerprint matching can be achieved without fingerprint alignment on the basis that private data of users and private data of authentication servers are protected.
Owner:GANSU AGRI UNIV
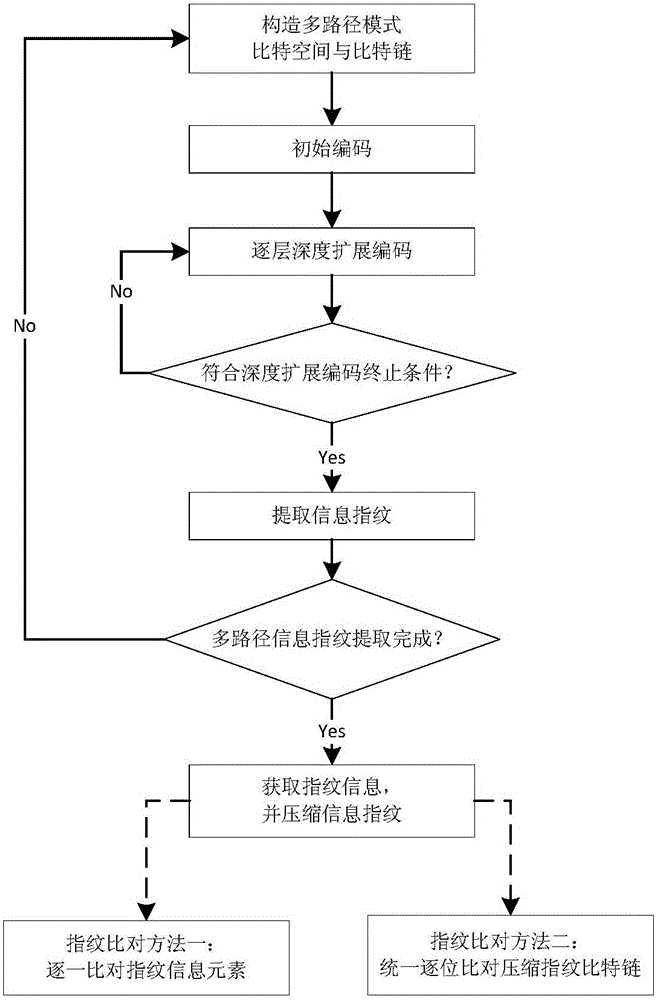
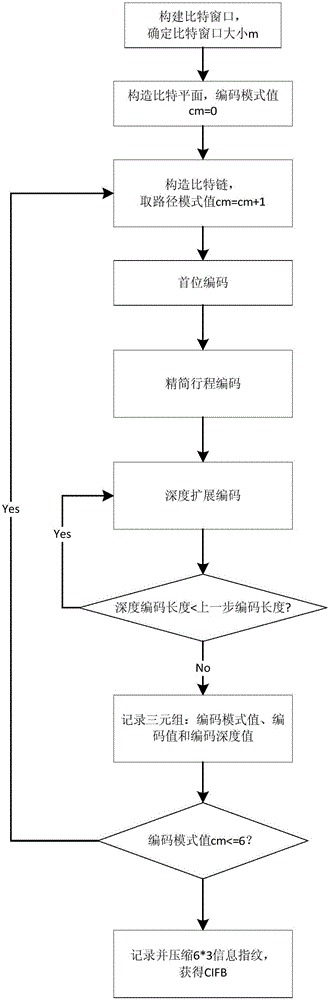
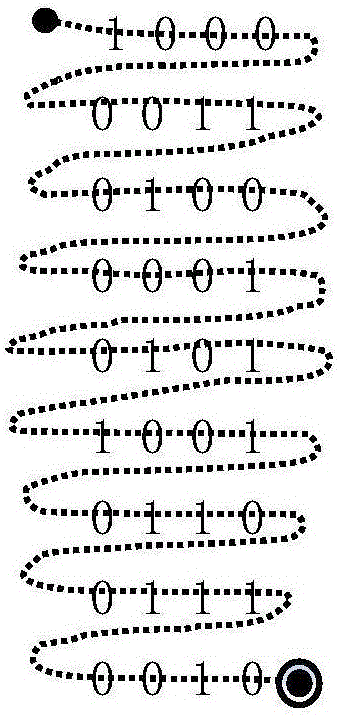
Multi-path depth encoded information fingerprint extraction method based on bit space
ActiveCN105844214AReduce digitsImprove work efficiencyMatching and classificationBit planeComputer science
The invention discloses a multi-path depth encoded information fingerprint extraction method based on the bit space. The method comprises a first step of constructing a bit window; a second step of constructing a bit plane; a third step of reducing dimensions and constructing a bit chain; a fourth step of encoding the bit chain; and a fifth step of comparing fingerprints. The fourth step includes conducting transversal and statistics for the constructed bit chain with reduced dimensions, acquiring the number of continuous 0 and the number of continuous 1 in sequence, and constructing a new decimal sequence of number; and binarizing the obtained decimal sequence of number to obtain a new binary bit chain with the first bit not being 0, repeating the transversal and statistics operation for the obtained bit chain, carrying out loop iteration in sequence until the newly obtained decimal sequence of number has only one element, and recording the value of the element obtained at last and the number of times of loop iteration as a feature value of an information fingerprint feature space The invention has the advantages of improving the efficiency in the same information detection and the like.
Owner:SOUTH CHINA UNIV OF TECH
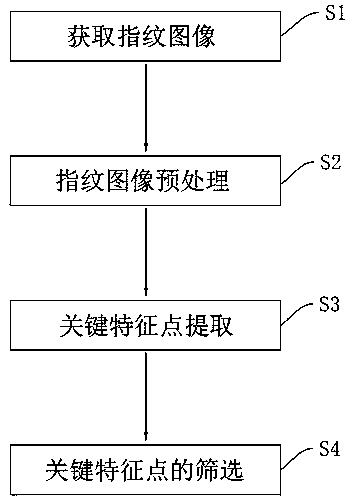
Small-area fingerprint image feature extraction method and system, terminal and storage medium
ActiveCN111428701AReduce the impactGuaranteed to proceed normallyMatching and classificationFeature extractionData information
The invention relates to a small-area fingerprint image feature extraction method and system, a terminal and a storage medium, belongs to the technical field of fingerprint identification, is appliedto small-area fingerprint feature information extraction, and comprises the following steps: S1, acquiring a fingerprint image; s2, preprocessing the fingerprint image, separating a foreground regionand a background region of the fingerprint image, obtaining data information of the foreground region, and performing classification filtering processing on the fingerprint image according to the datainformation of the foreground region; s3, extracting key feature points, performing block division on the fingerprint image, selecting the key feature points according to data information of a fingerprint image foreground area in a corresponding block, wherein the data information of the fingerprint image foreground area comprises curvature information of pixel points; and step S4, screening of key feature points: screening out the key feature points with good stability through comparative analysis. The method is used for solving the problem of insufficient extraction of small-area fingerprint feature information, is effectively suitable for small-area fingerprint comparison and has good reliability.
Owner:深圳市诺赛特系统有限公司
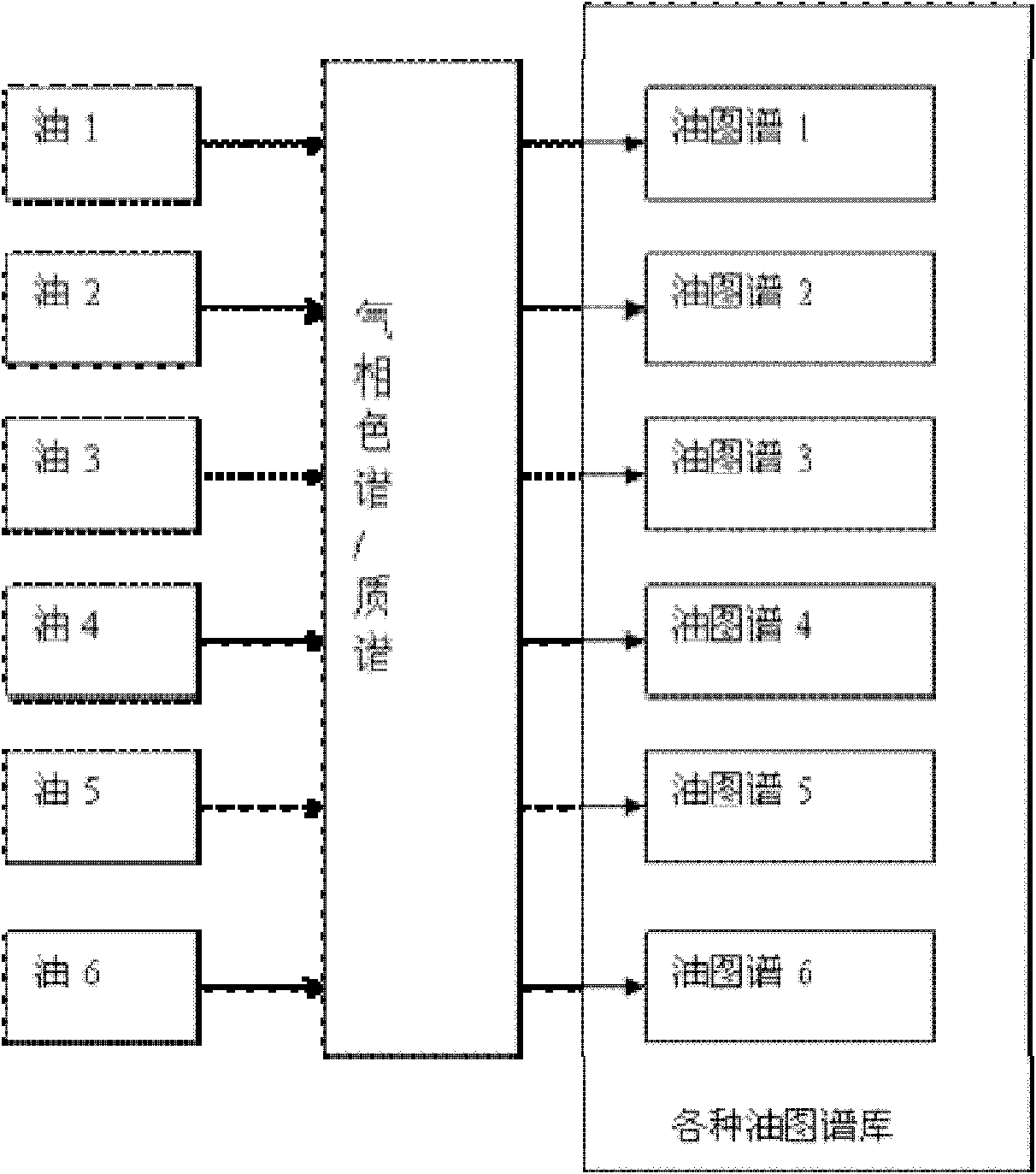
Gas chromatography/mass spectrum (GC/MS) identification method for oil stained cigarettes
ActiveCN102253144AReduce inflowGuaranteed direct reputationComponent separationGas liquid chromatographicPhysical chemistry
The invention relates to the technical field of chemical detection of cigarettes, and especially provides an identification method for oil stained cigarettes. The GC / MS identification method for oil stained cigarettes comprises the following steps: 1) collecting a plurality of types of oil directly related to production of cigarettes and respectively dissolving and extracting the types of oil with ethyl acetate; 2) adjusting GC / MS parameters, carrying out gas phase / mass spectrometry detection on the extracted solutions of oil, establishing different chromatograms to form a chromatogram database, and determining fingerprints; 3) taking cigarette papers having oil stains, immersing the cigarette papers with ethyl acetate, carrying out extracting, concentrating the extract with a distillation apparatus, and carrying out gas phase / mass spectrometry on the concentrate to obtain a chromatographic fingerprint; 4) comparing fingerprints of the chromatographic fingerprint of oil stained cigarettes with fingerprints in the established chromatogram database to identify which oil stain is on the oil stained cigarettes. The invention enables fast and effective identification of oil stains generated in the production of cigarettes, provides a basis for identifying a problematic process in the production of cigarettes, and allows problematic cigarettes to be traceable.
Owner:CHINA TOBACCO ZHEJIANG IND
Application system fingerprint login method and system based on domestic CPU and operating system
InactiveCN110287675AImprove versatilityImprove compatibilityDigital data authenticationMatching and classificationOperational systemTransfer procedure
The invention provides an application system fingerprint login method and system based on a domestic CPU and an operating system, belonging to the field of fingerprint authentication technology, the method is based on domestic CPU and operating system environment; fingerprint collection and fingerprint comparison services which can be operated independently are provided; fingerprint registration and fingerprint authentication login of an application system user are realized; a complete rich service interface required by a service process from fingerprint collection, fingerprint registration to initialization, addition, deletion and fingerprint comparison verification of a 'fingerprint template library 'is provided for the outside; encrypted transmission is carried out on the fingerprint template in the transmission process, and a simple, convenient, safe and stable application system login solution based on a domestic CPU and an operating system environment is provided.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Method for reducing false reject rate of fingerprint comparison
ActiveCN102254167BReduce rejection rateEasy to useCharacter and pattern recognitionPattern recognitionMedicine
The invention relates to a method for reducing the rejection rate of fingerprint comparison. The fingerprint feature is extracted by a fingerprint sensor, quickly searched among many templates, and compared with the existing templates to obtain the highest comparison score; the comparison is judged according to the comparison passing rules Whether it is passed, the template is replaced or not replaced according to the secondary template replacement rules. The beneficial effects of the present invention are: the auxiliary template is added, and the auxiliary template is dynamically updated during the application process, which greatly improves the adaptability of the sensor to the environment, improves the anti-aging ability, and increases the range of comparison objects to effectively The rejection rate is reduced; at the same time, the fingerprint comparison assists the threshold interval. The fingerprint features in this interval need to be compared with the fingerprint template one by one. If the comparison scores of more than two features are found within this interval, the comparison Yes, this effectively reduces the rejection rate of fingerprint comparison while ensuring that no false identification is made.
Owner:HANGZHOU SYNOCHIP DATA SECURITY TECH CO LTD
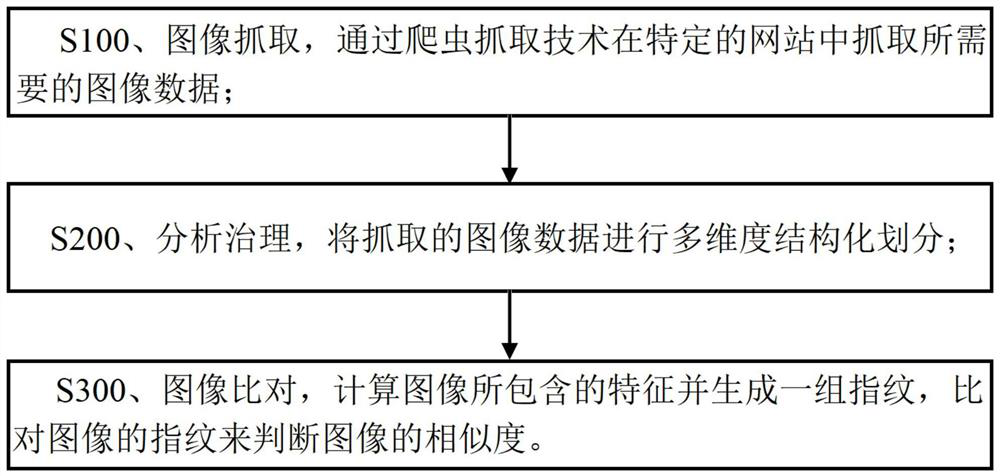
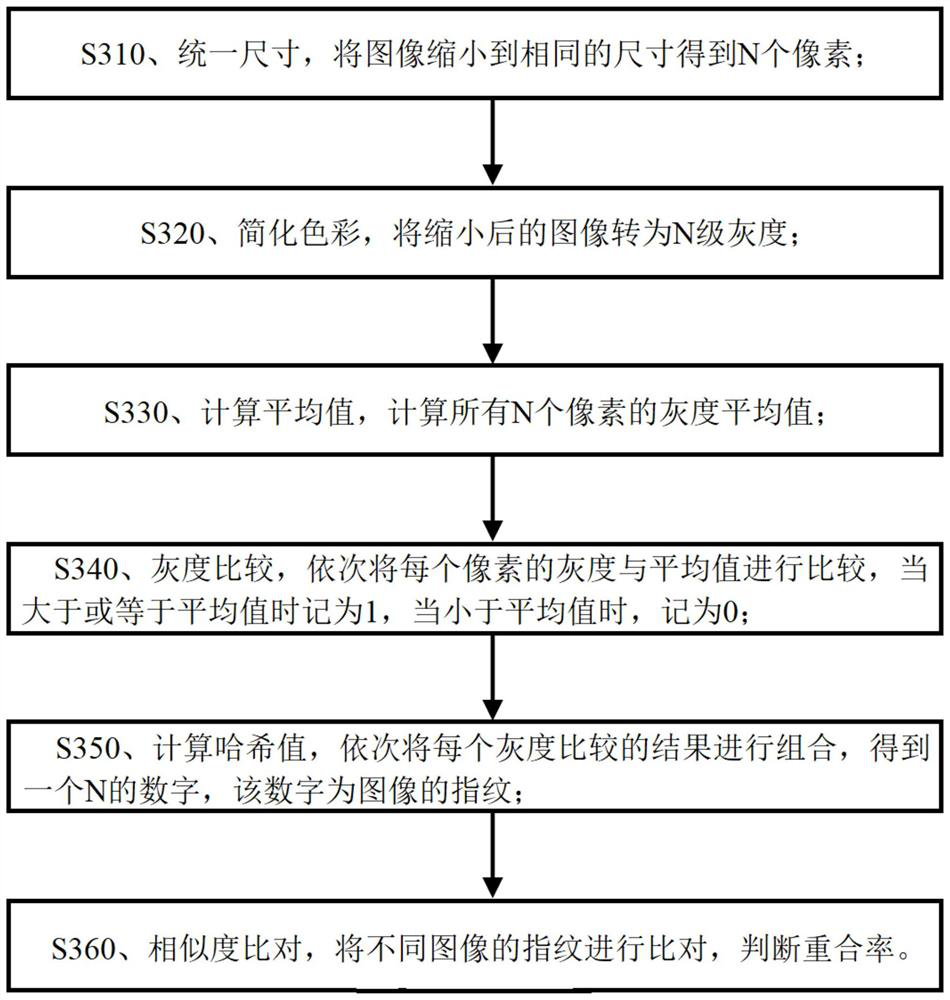
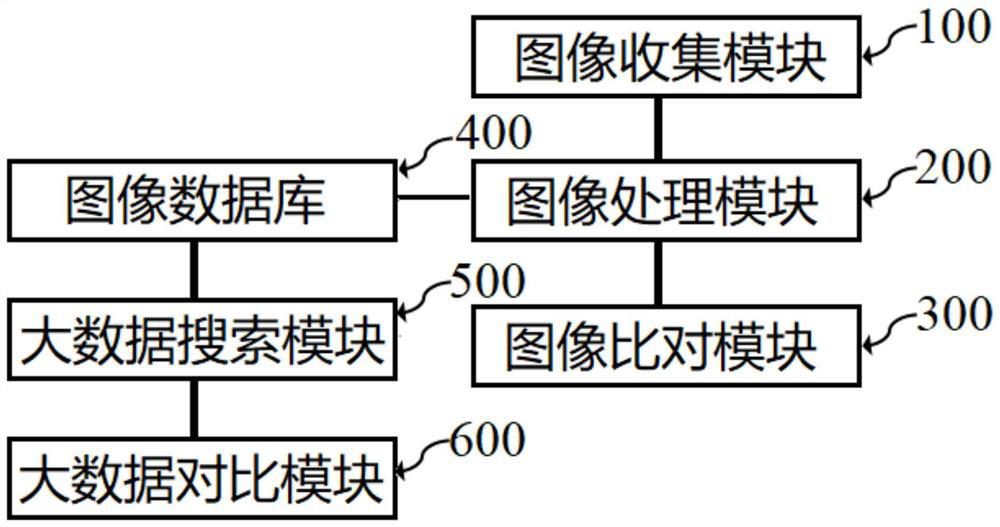
Image big data similarity comparison method and system
PendingCN112308162AImprove recognition efficiencyComparison to achieveWeb data indexingCharacter and pattern recognitionPattern recognitionFingerprint alignment
The invention discloses an image big data similarity comparison method, and the method comprises the steps: capturing the image data to be compared through a crawler capture technology and big data search, analyzing and processing the captured image data and storing the image data in a structured mode, and performing classification comparison according to attributes of images, wherein the comparison process is that the features contained in the images are calculated a set of fingerprints are generated and the fingerprints of the images are compared to judge the similarity of the images; therefore, the image recognition efficiency can be improved, the method can be combined with big data, and the comparison of the similarity of the images in the big data range is achieved.
Owner:SHANGHAI SOFTLINE INFORMATION TECH
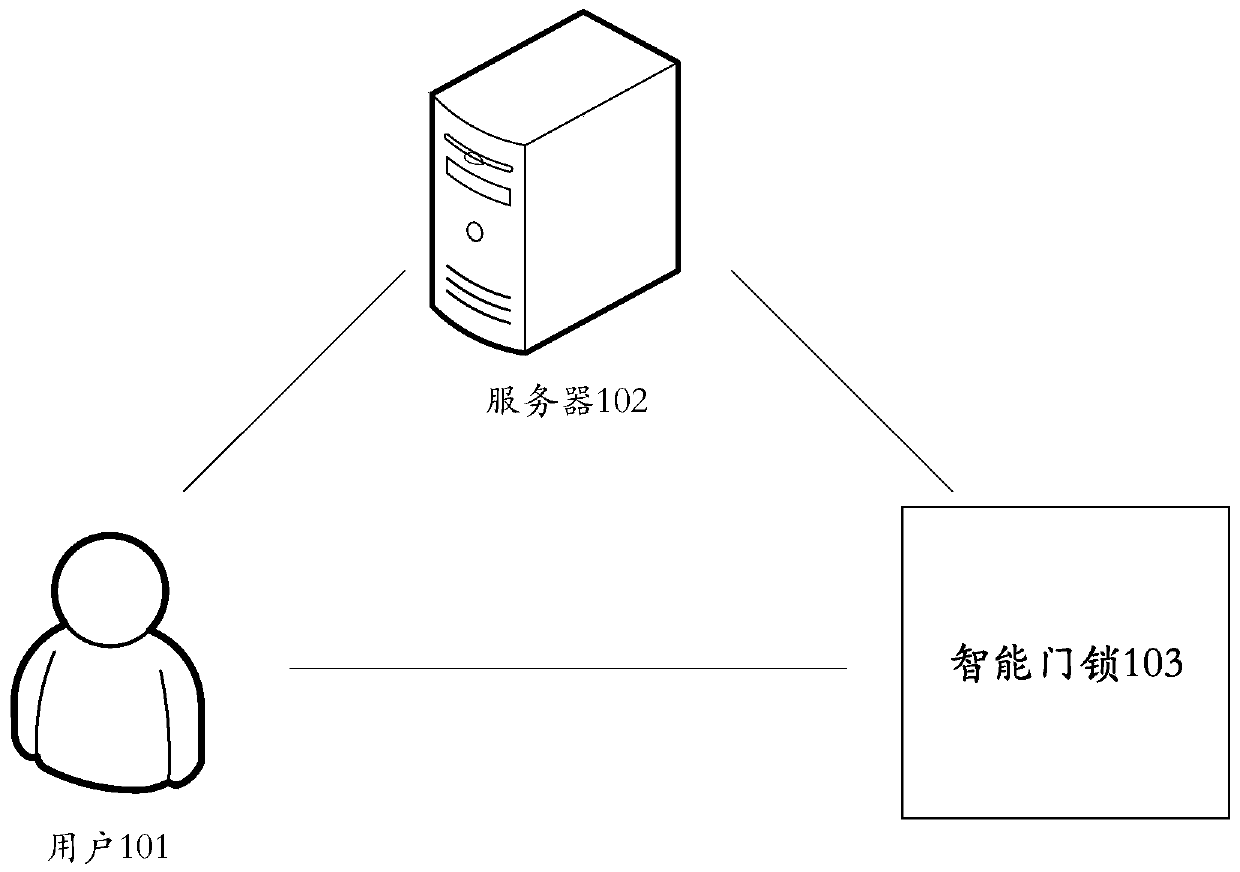
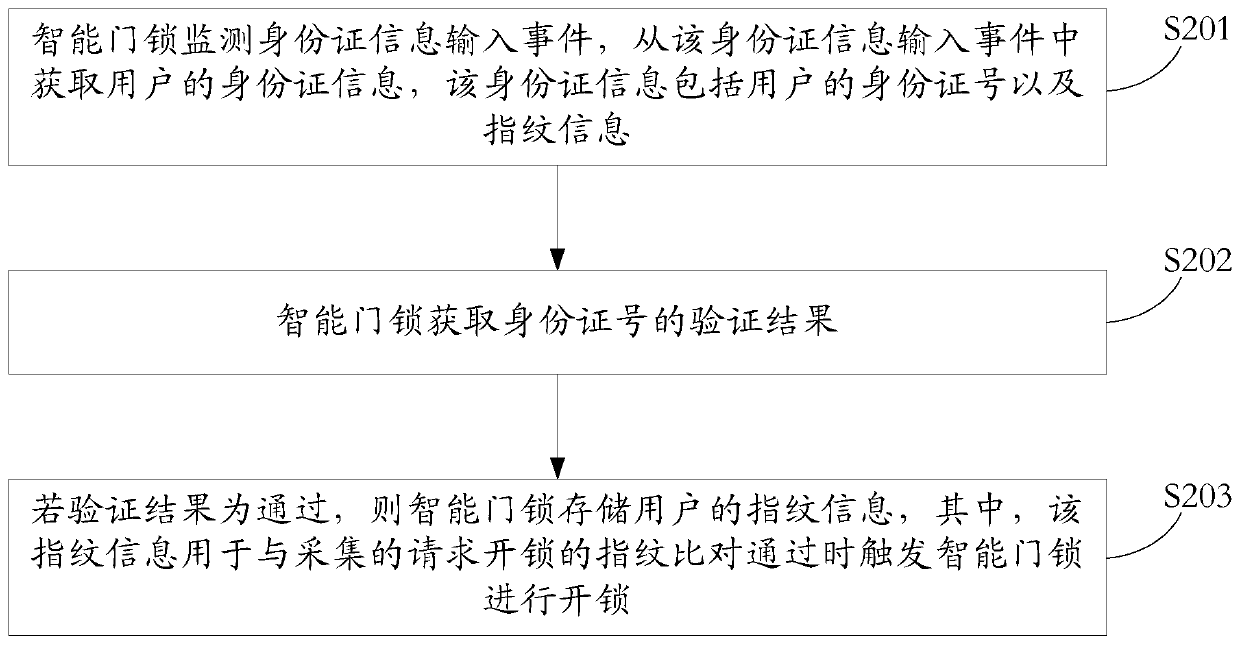
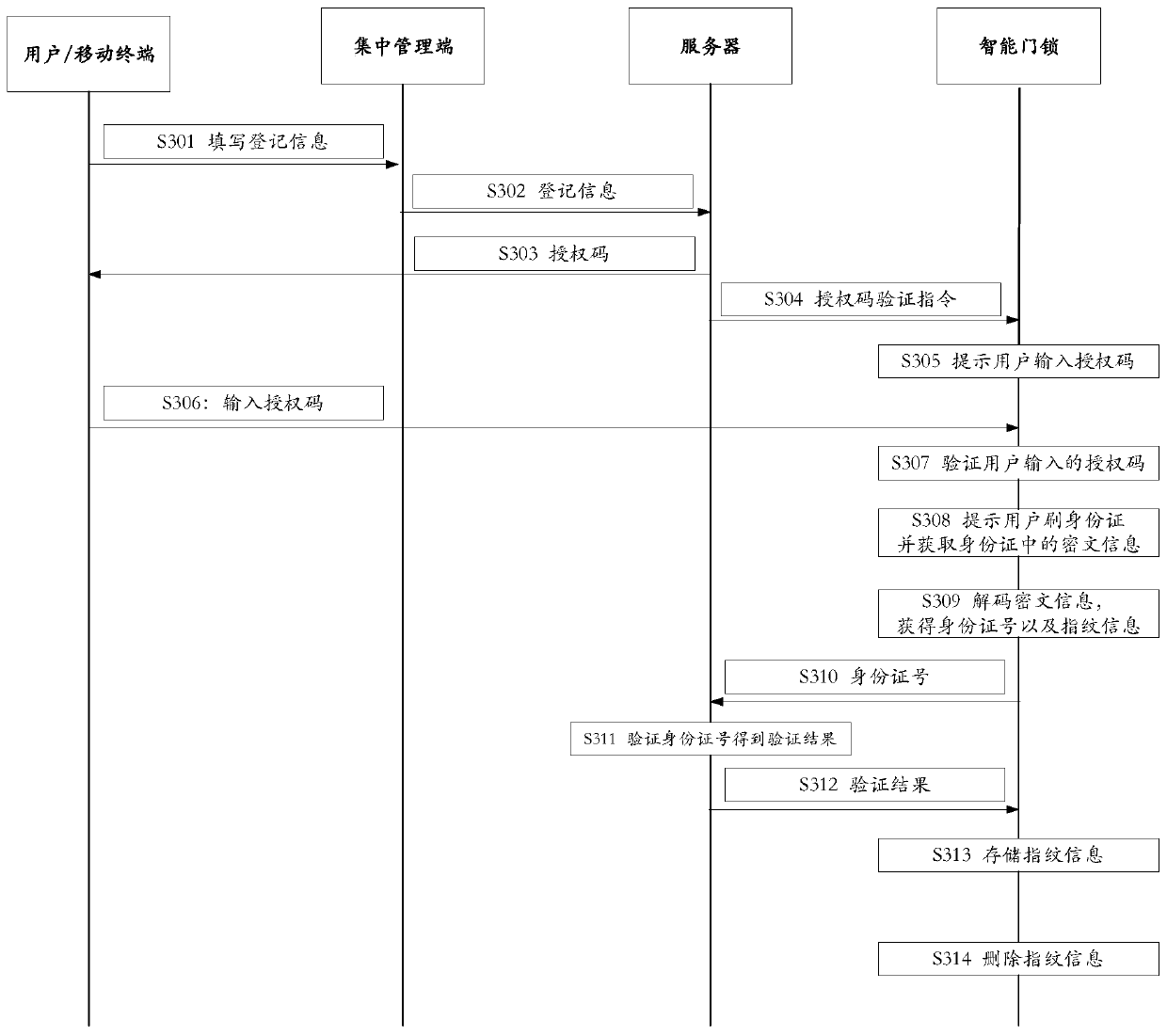
Fingerprint storage method, and authentication method, device and system
InactiveCN110738759AImprove securityRealize self-service fingerprint entryIndividual entry/exit registersComputer hardwareFingerprint alignment
An embodiment of the application discloses a fingerprint storage method, and an authentication method, device and system, and the fingerprint storage method comprises the following steps of a smart door lock monitors an ID card information input event, and obtains a user's ID card information from the ID card information input event, wherein the ID card information includes the user's ID number and fingerprint information; the smart door lock obtains an authentication result of the ID number; and if the authentication result indicates that the ID number has pass the authentication, the smart door lock stores the fingerprint information, wherein the fingerprint information is used to trigger the smart door lock to be unlocked when the comparison with the collected request unlock fingerprintindicates a success. The above scheme is used to not only realize the user self-entering of the fingerprint and reduce the management cost, but also reduce the risk of remote transmission of the fingerprint. Compared with the direct fingerprint entry method, the invention is simpler and can guarantee the integration of person and witnesses.
Owner:BEIJING HUADA ZHIBAO ELECTRONICS SYST +1
Certainty coding method and system in fingerprint identification
The present invention belongs to the computer biometrics technology and relates to a method and a system which adopt certainty coding to accurately match fingerprints during the process of fingerprint comparison. The present invention has the accurate matching by using characteristic of the certainty coding that a characteristic area can be selected from the fingerprint image and the characteristic value corresponding to the characteristic area, such as the total length of fingerprint ridge line, the entropy of the main direction of the direction field of the ridge line and the direction field of the pixel point, to conduct matching work. The certainty coding method and the fingerprint identification system built by the method overcome the defects, such as low accuracy rate and potential safety problems which are caused by adopting fuzzy matching algorithm in the traditional point fingerprint identification system.
Owner:TSINGHUA UNIV +1
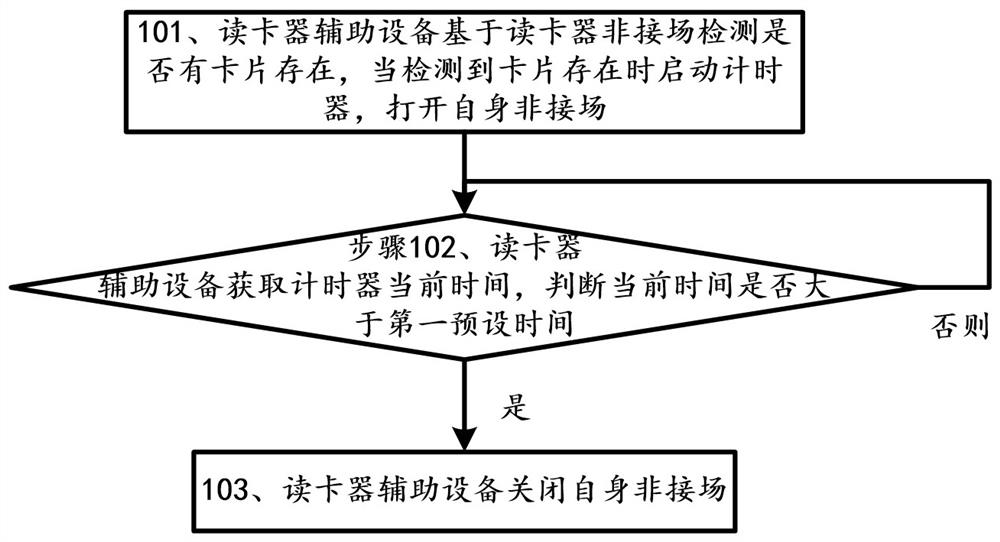
Card reader auxiliary equipment and working method thereof
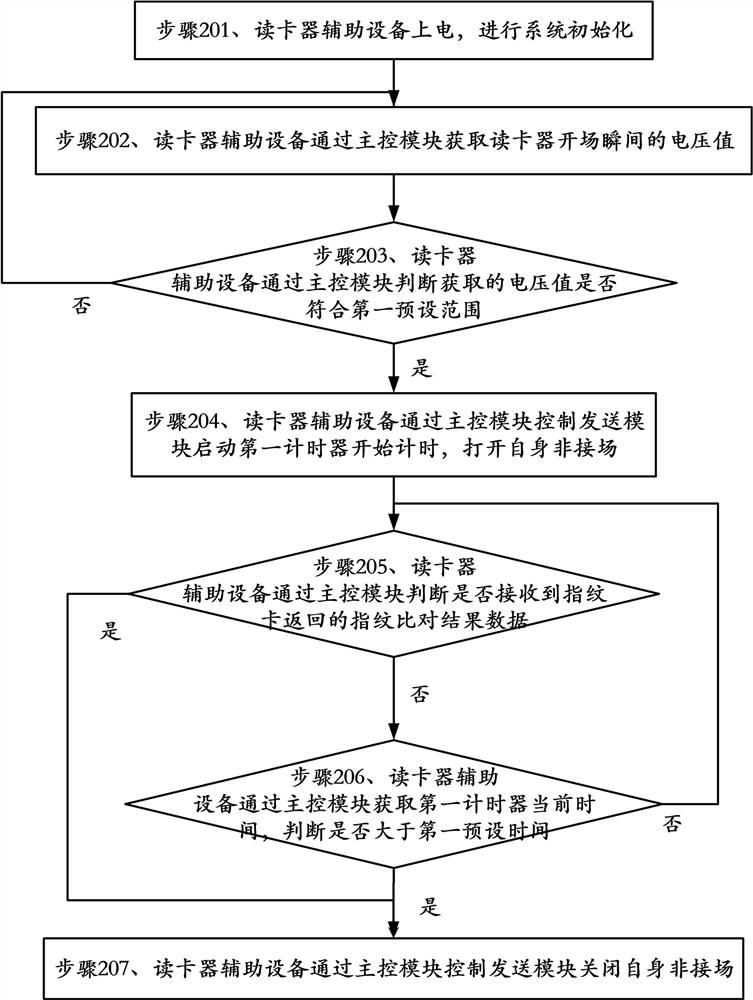
ActiveCN112307783AIncrease field strengthCommunication securityMemory record carrier reading problemsEngineeringCard reader
The invention discloses card reader auxiliary equipment and a working method thereof, and belongs to the field of card readers. Whether a card exists or not is detected through the card reader auxiliary equipment based on the card reader non-contact field, the card reader auxiliary equipment opens the self non-contact field when detecting that the card exists, enough field intensity is provided for the fingerprint card, fingerprint comparison of the fingerprint card can be completed, the card reader auxiliary equipment obtains the current time of the timer, whether the current time is greaterthan a first preset time is judged, and if so, the own non-contact field is closed. According to the invention, fingerprint comparison of the card can be realized without upgrading the card reader, sothat communication between the card and the card reader can be completed smoothly.
Owner:FEITIAN TECHNOLOGIES
Interference source individual identification method based on envelope fingerprint features
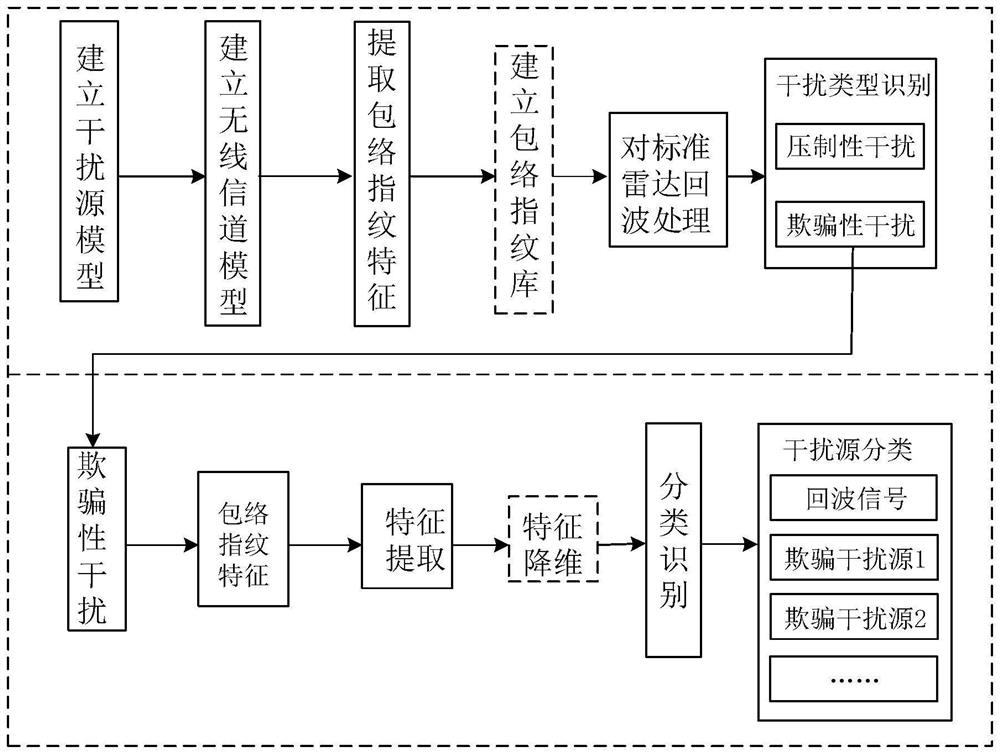
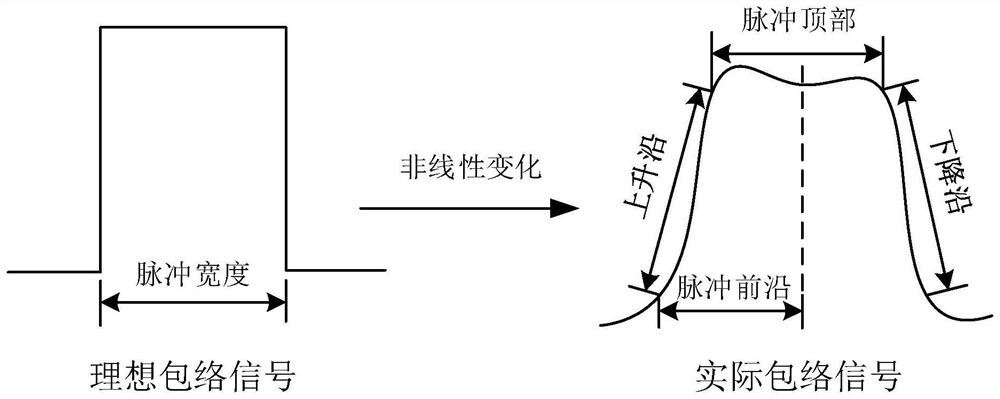
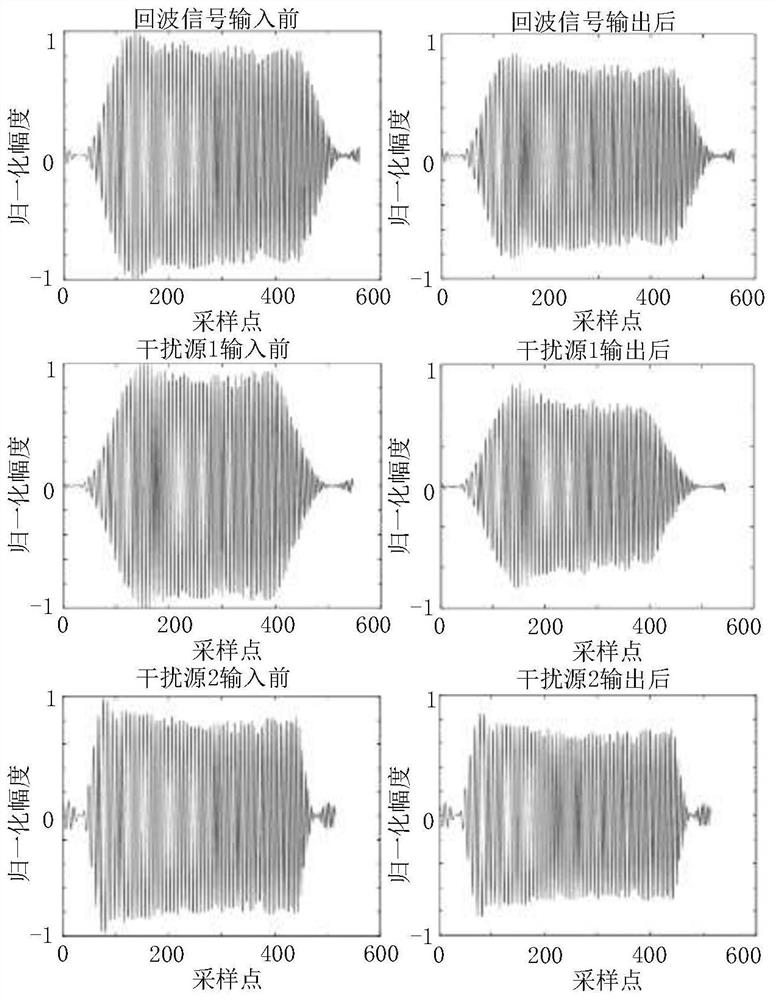
PendingCN113219415ARich nonlinear featuresImprove recognition efficiencyWave based measurement systemsPattern recognitionElectronic systems
The invention relates to an interference source individual identification method based on envelope fingerprint features and belongs to the technical field of target identification. The method comprises the following steps of 1) establishing a radar interference source signal model; 2) establishing a simulation model of a wireless channel; 3) extracting a leading edge feature enveloped by a radar interference source signal as a fingerprint feature identified by a radiation source individual; 4) repeating the step 3), extracting the envelope leading edge feature of each radar interference source signal, and establishing an envelope fingerprint feature library; 5) processing the radar echoes to obtain envelope fingerprint features of the standard radar echoes; 6) identifying active interference signals, and classifying the active interference signals into suppressing interference and deceptive interference; and 7) receiving and analyzing the echo envelope fingerprints of the deceptive interference identified in the step 6), and comparing the echo envelope fingerprints with the envelope fingerprints in the envelope fingerprint feature library in the step 4). The method is simple and convenient; scientific basis is provided for electronic system design, and identification efficiency is improved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +1
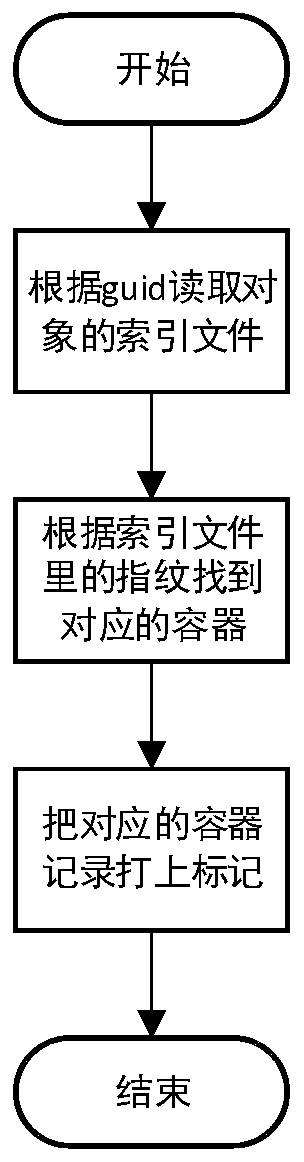
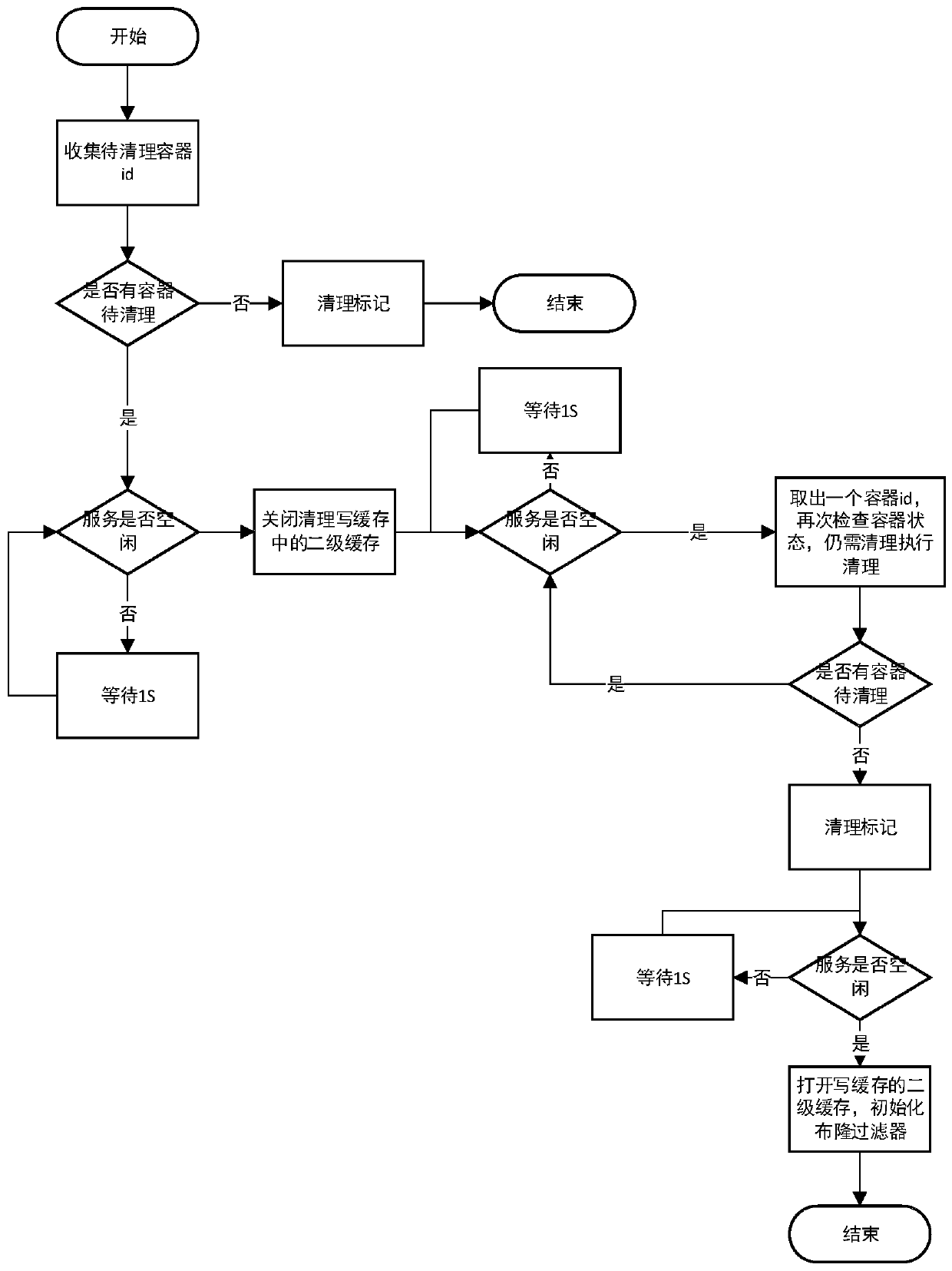
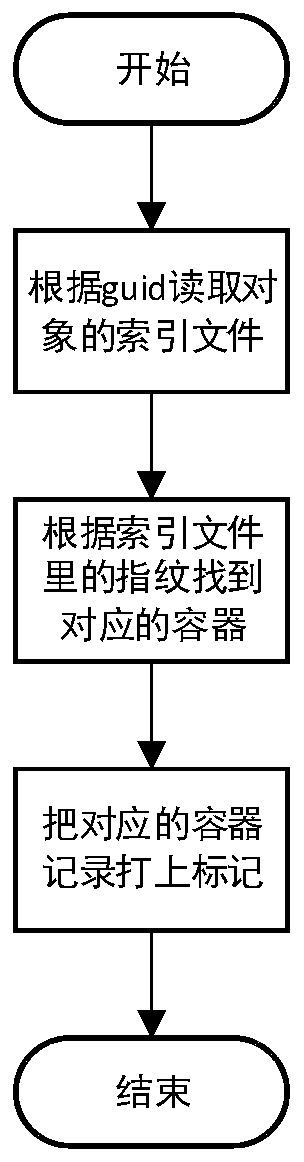
Data efficient deletion method and system based on source end deduplication
PendingCN111143343AAchieve the purpose of freeing up spaceStatistical logic is simpleDigital data information retrievalRedundant operation error correctionData streamData file
The invention discloses an efficient data deletion method based on source end deduplication. In the backup process, a data stream of a source end is segmented into data blocks, fingerprints are calculated, the fingerprints are compared, if the fingerprints do not exist, it is indicated that the data stream is a new block, the corresponding data blocks are transmitted to a container of a server tobe stored, the corresponding container is marked as 1, the container is written into a data file after the container is full, and then a new container is created; automatically clearing up the expiredbackup set, and clearing up the guid object record; and performing data block and fingerprint cleaning on the container marked as 0 by utilizing a preset cyclic deletion logic in idle time beyond thenormal service window period, wherein the container marked as 0 indicates that the data block and the fingerprint in the container can be cleaned when not being referenced. The method has the advantages that a marking mode is adopted, the statistical logic is simpler, the cleaning logic is not influenced by the size of the deduplication library, and the method is more efficient.
Owner:NANJING UNARY INFORMATION TECH
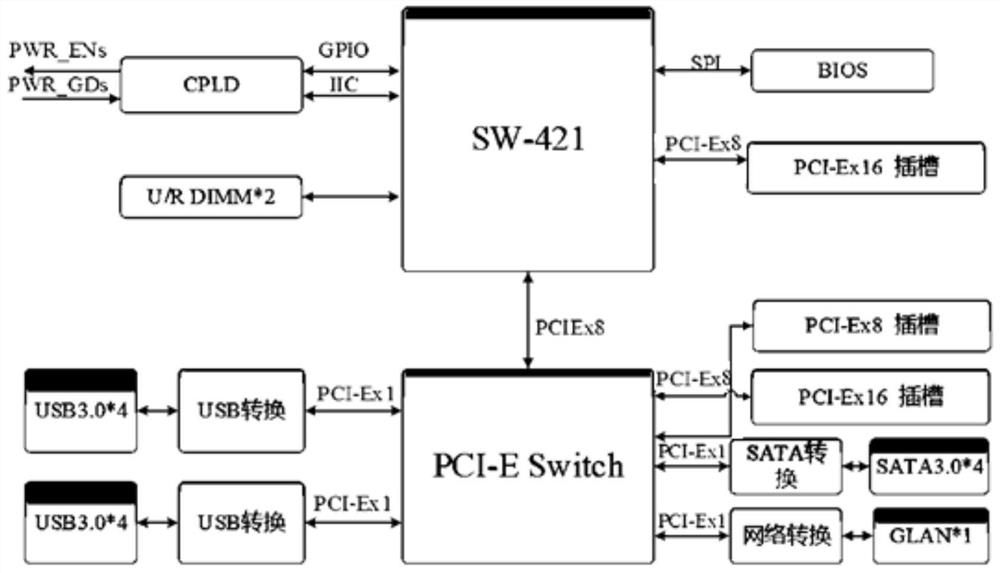
Integrated computer based on Shenwei 421 processor
PendingCN112257127AAvoid hidden dangersAccurately definedInternal/peripheral component protectionDigital data authenticationTerm memoryFingerprint alignment
The invention discloses an integrated computer based on an Shenwei 421 processor and relates to the technical field of computers. The computer comprises a case, wherein a mainboard, a hard disk, a display screen, a biological recognition module and a gravity sensing module are arranged in the case, an SW 421 processor, a CPLD control chip, a memory, domestic UEFI firmware and a display card are arranged on the mainboard, the display screen is embedded in a front panel of the case, and the display screen is connected with the display card and used for displaying a user interface; the biologicalrecognition module is used for carrying out biological recognition to determine whether to log in the operating system or not and comprises an image collector and a fingerprint recognition module, the image collector is used for shooting an image of a user for face recognition, and the fingerprint recognition module is used for collecting fingerprints for fingerprint comparison and recognition; the gravity sensing module is used for sensing rotation of the case and sending out a screen rotation instruction to adjust the display direction of the display screen.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
Method for preventing web system data migration based on asymmetric encryption algorithm
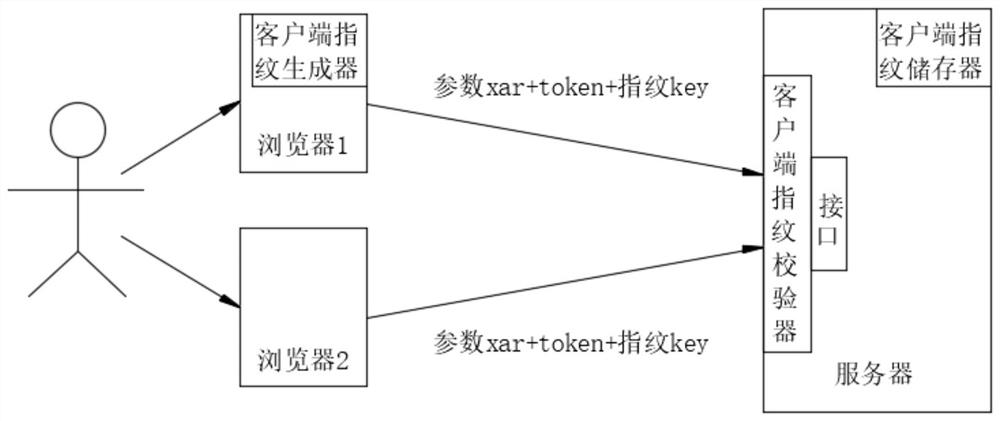
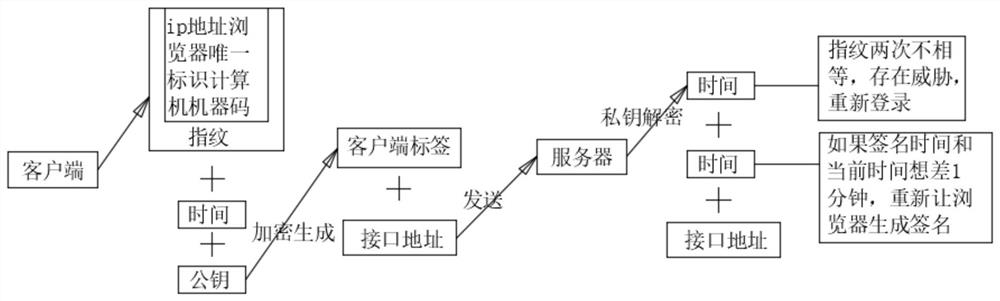
PendingCN113630421AAnti-counterfeitingWith anti-parameter tamperingUser identity/authority verificationAlgorithmTheoretical computer science
The invention discloses a web system data transplantation prevention method based on an asymmetric encryption algorithm. The method comprises the following steps: S1, a user logs in a system through a browser 1, reads a unique data calculator machine code and calculator feature information of a client through a client fingerprint generator to generate a client fingerprint, and stores and binds the client fingerprint with the user and the browser; S2, the client fingerprint is combined with the current time and the public key to encrypt and generate a string of character strings, and the character strings are client signatures; S3, a server interface is visited, and when a normal interface accesses a server, a client signature and a server private key are carried for encrypting to obtain a fingerprint and time; S4, the parameter is copied to access the server interface through the browser 2, and if the verification of the client fingerprint verifier is not passed, the service response fails. The method has the characteristics of preventing pretending, authenticating identity and preventing parameter tampering, and a timestamp comparison and fingerprint comparison technology exists, so that replay attacks can be prevented when the data of the previous timestamp is invalid.
Owner:神州网云(北京)信息技术有限公司
Fingerprint identification method and electronic device
ActiveCN108073885BPrint image acquisitionMatching and classificationFingerprint alignmentFeature point matching
Owner:BYD SEMICON CO LTD
Picture fingerprint comparison method and device based on large integer type, equipment and medium
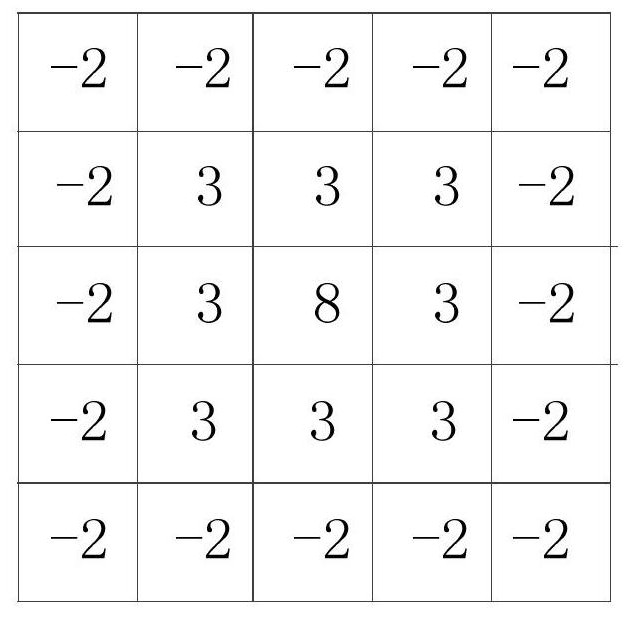
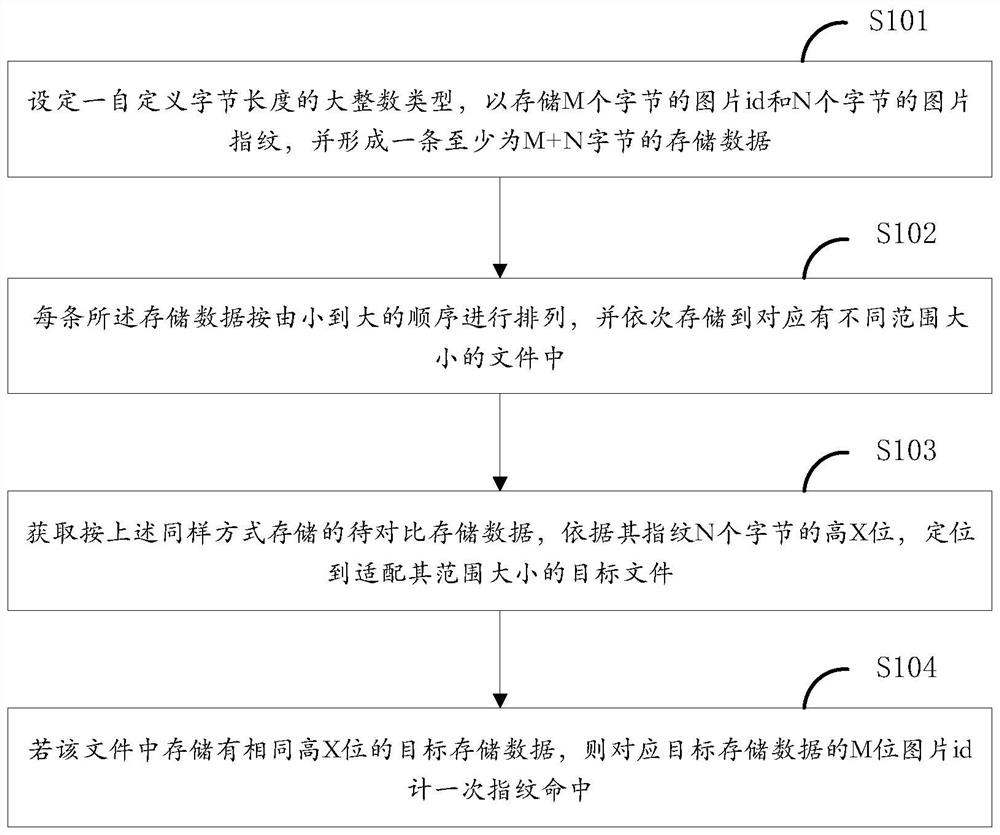
PendingCN113849671AEasy to storeImprove efficiencyStill image data indexingSpecial data processing applicationsAlgorithmEngineering
The invention provides a picture fingerprint comparison method and a device based on a large integer type, equipment and a medium, and the method comprises the steps: setting a large integer type with a user-defined byte length to store a picture id of M bytes and a picture fingerprint of N bytes, and forming storage data of at least M + N bytes; arranging the storage data according to a sequence from small to large, and sequentially storing the storage data into corresponding files with different ranges and sizes; obtaining to-be-compared storage data stored in the same way, and positioning a target file matched with the range size of the to-be-compared storage data according to the high X bits of the N bytes of the fingerprint of the to-be-compared storage data; if target storage data with the same high X bits are stored in the file, counting the M-bit picture id corresponding to the target storage data to be hit by the fingerprint for one time. According to the method, a large integer type with an adjustable length is set, so that storage and comparison are facilitated, and the efficiency of picture storage and picture fingerprint comparison is greatly improved.
Owner:计易数据科技(上海)有限公司
Unlocking method and system
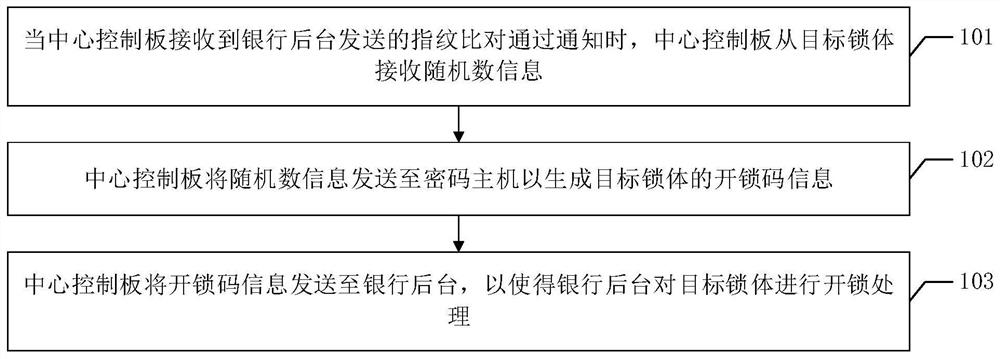
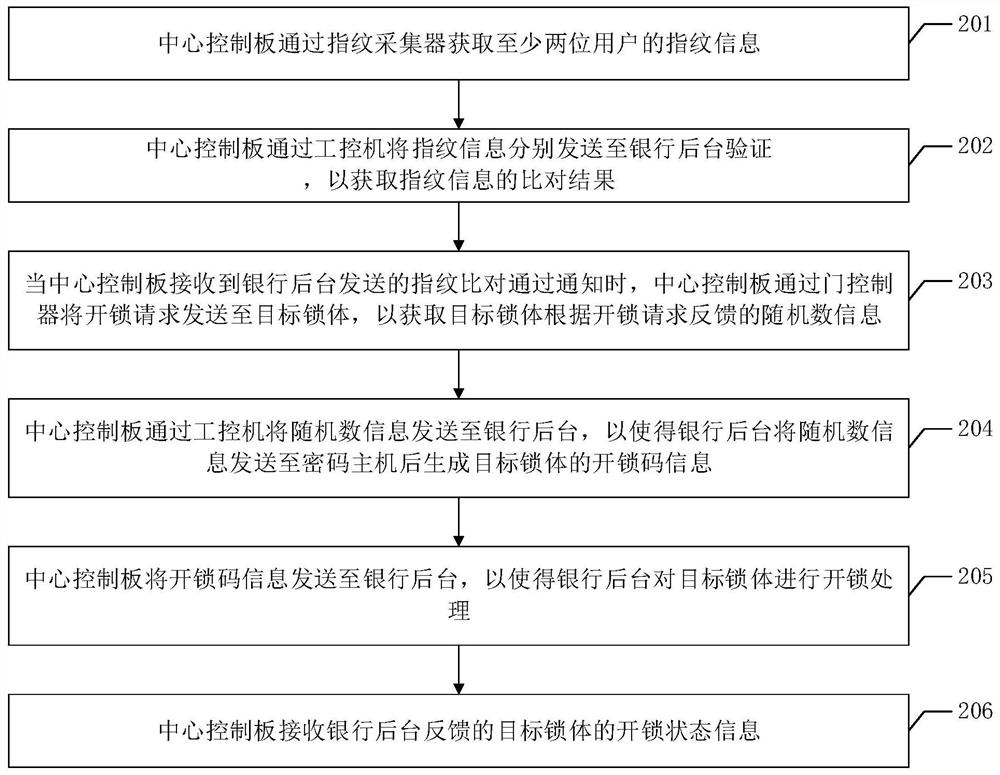
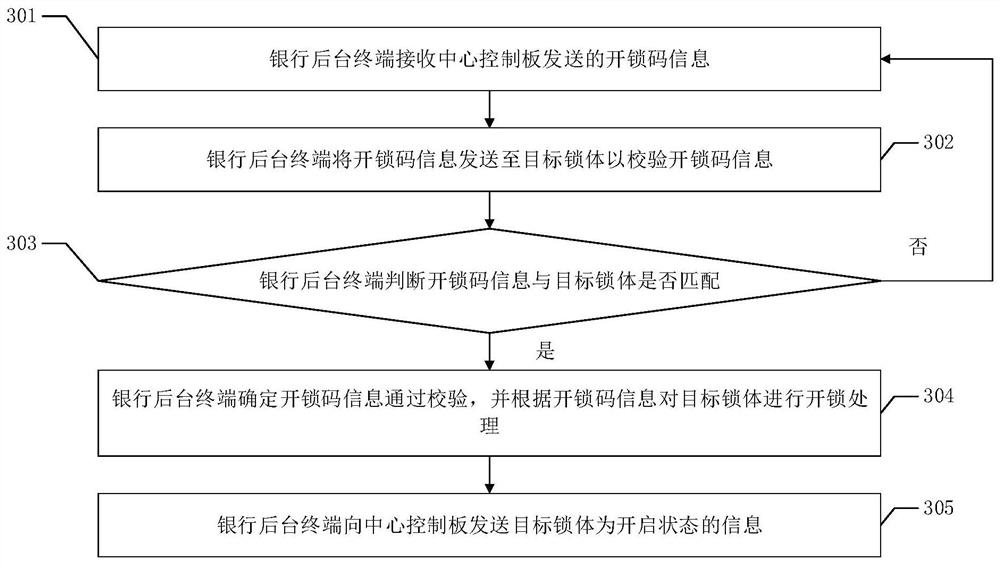
ActiveCN113487766ARealize double insurance mechanismImprove securityIndividual entry/exit registersComputer networkSecret code
The embodiment of the invention discloses an unlocking method, which is used for realizing a double insurance mechanism of a service library so as to improve the use safety of the service library. The method provided by the embodiment of the invention comprises the following steps: when the central control board receives a fingerprint comparison passing notification sent by a bank background, the central control board receives random number information from a target lock body; the central control board sends the random number information to the password host to generate unlocking code information of the target lock body; and the central control board sends the unlocking code information to the bank background, so that the bank background carries out unlocking processing on the target lock body.
Owner:SGSG SCI & TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com