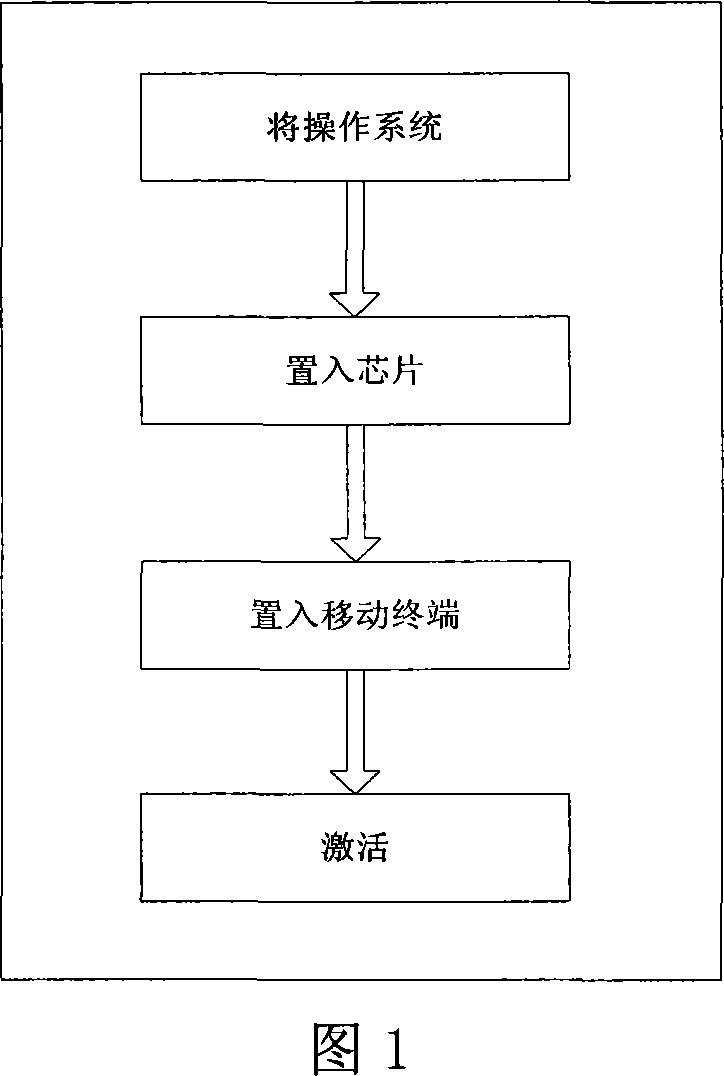
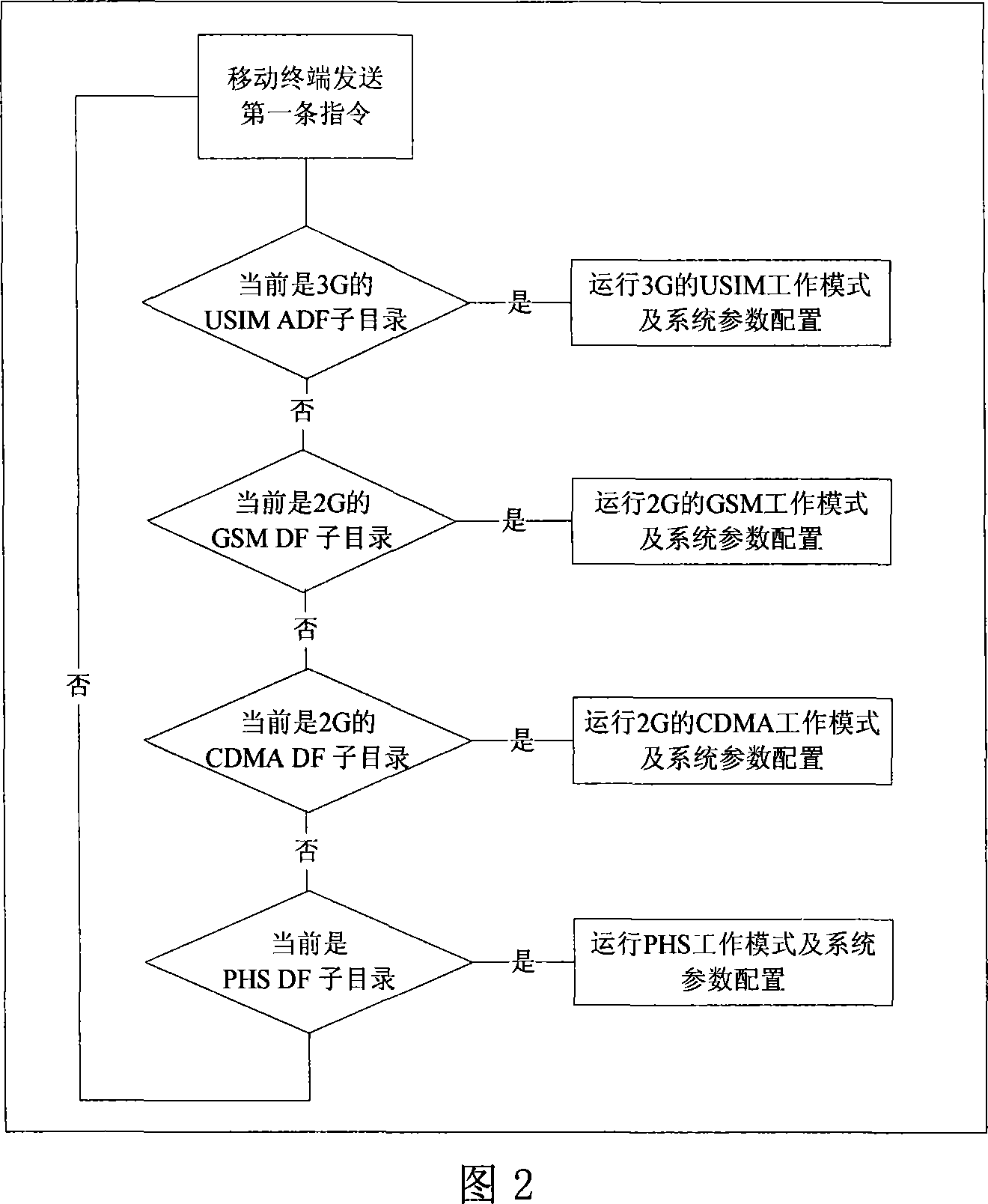
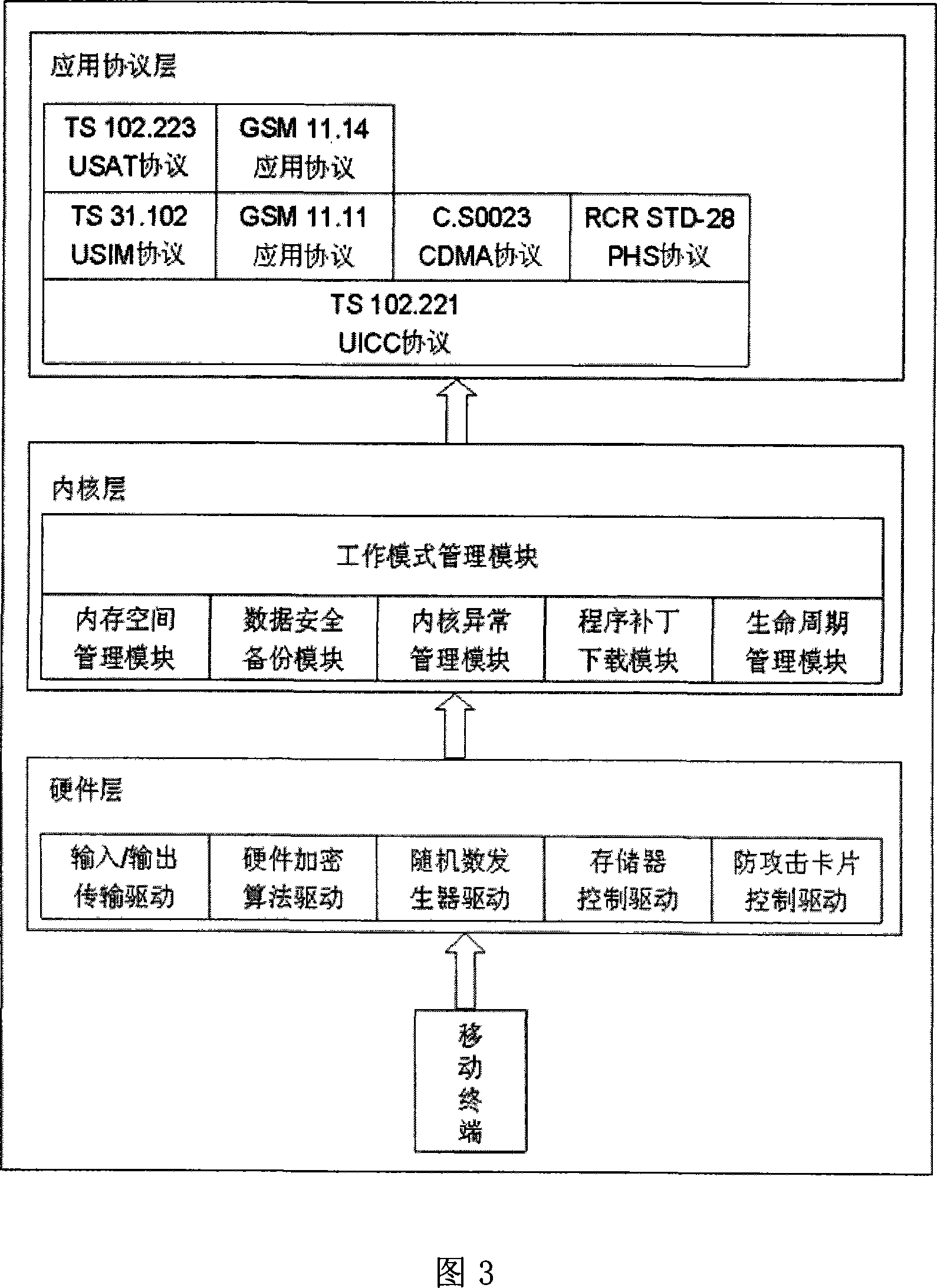
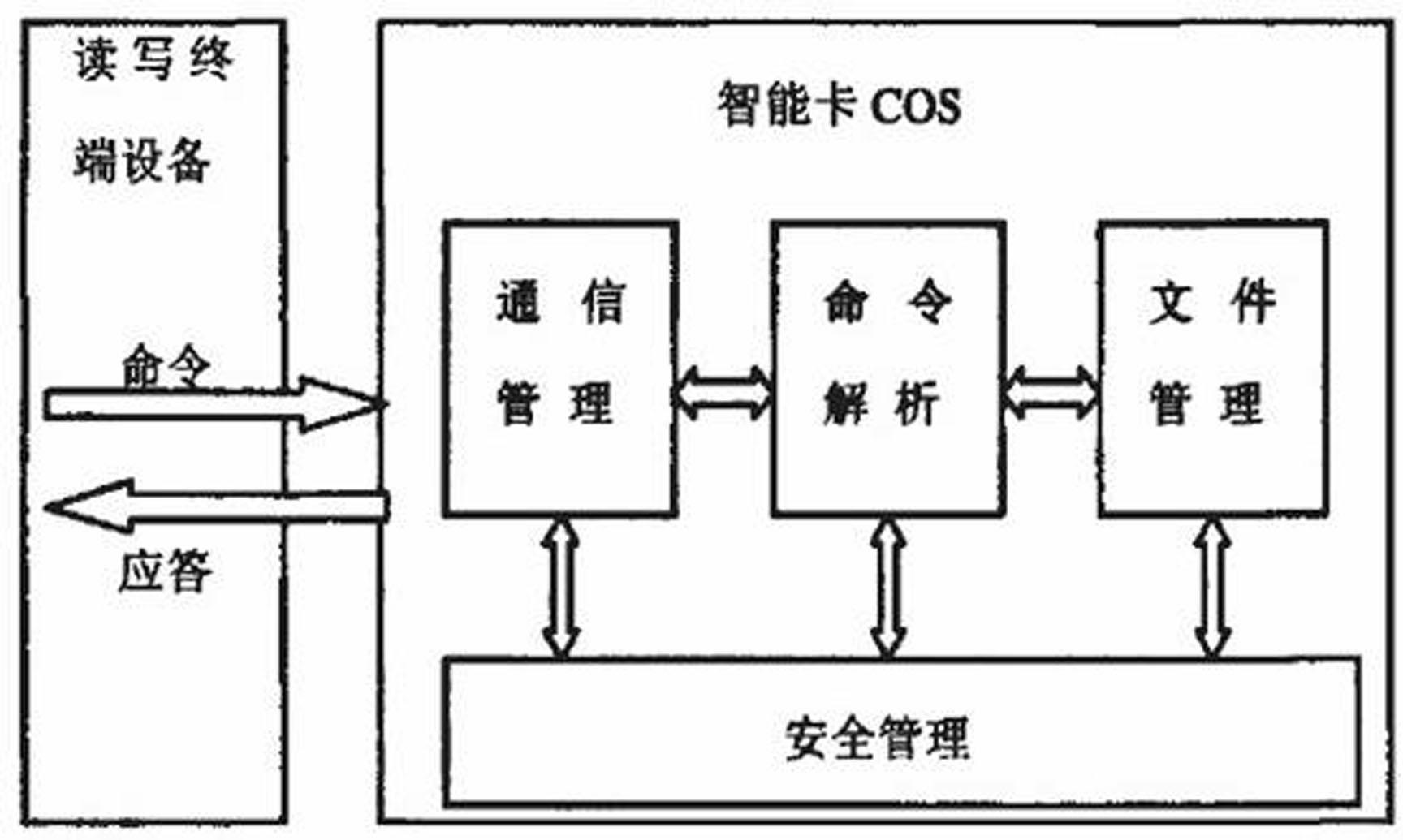
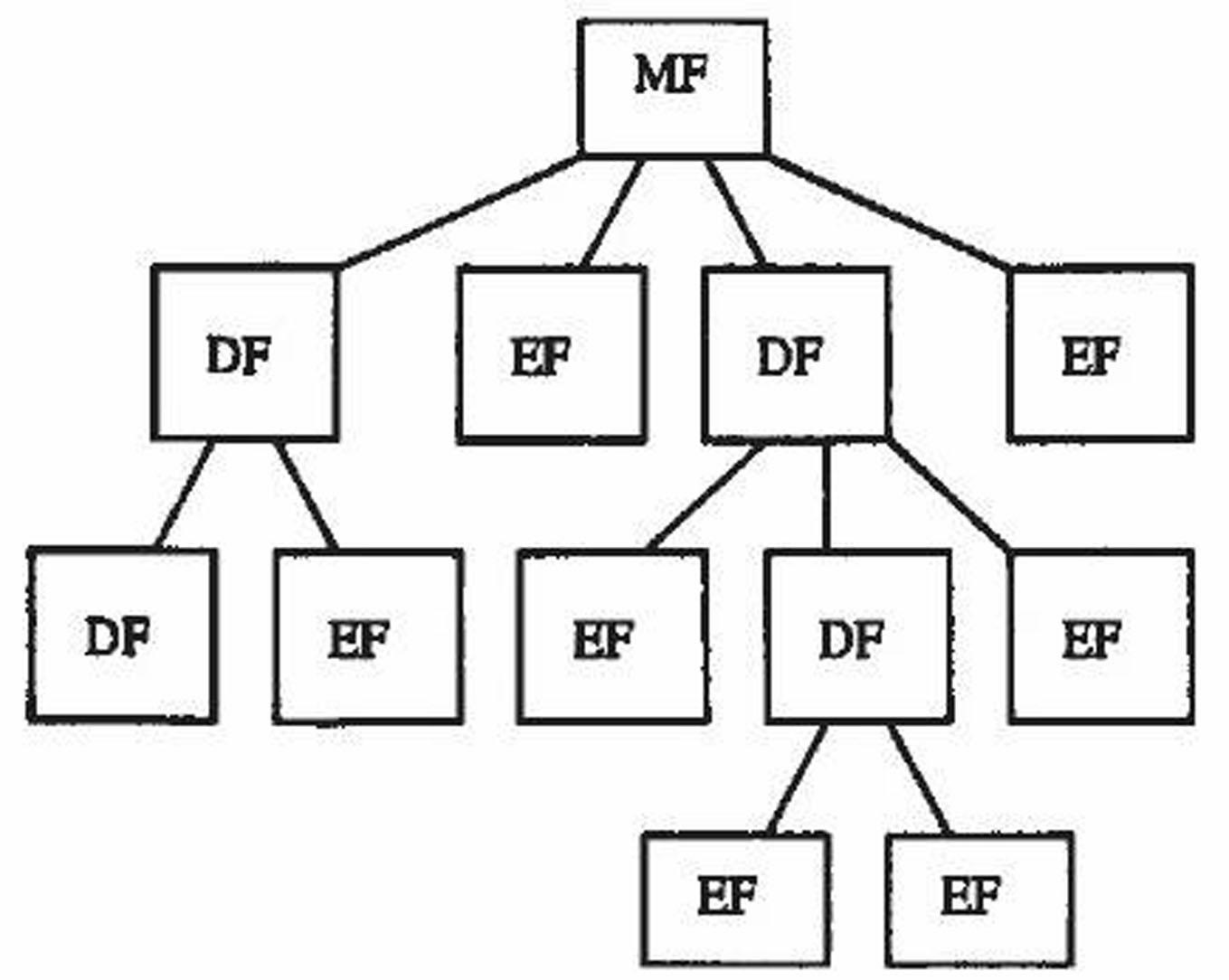
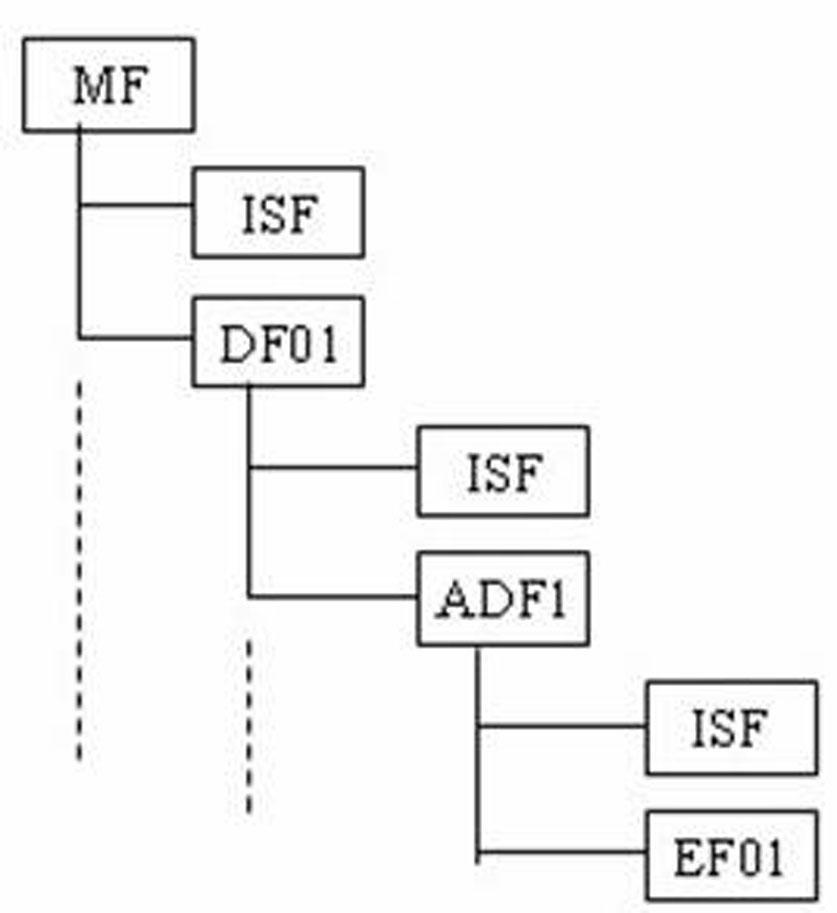
Patents
Literature
113 results about "Chip operating system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
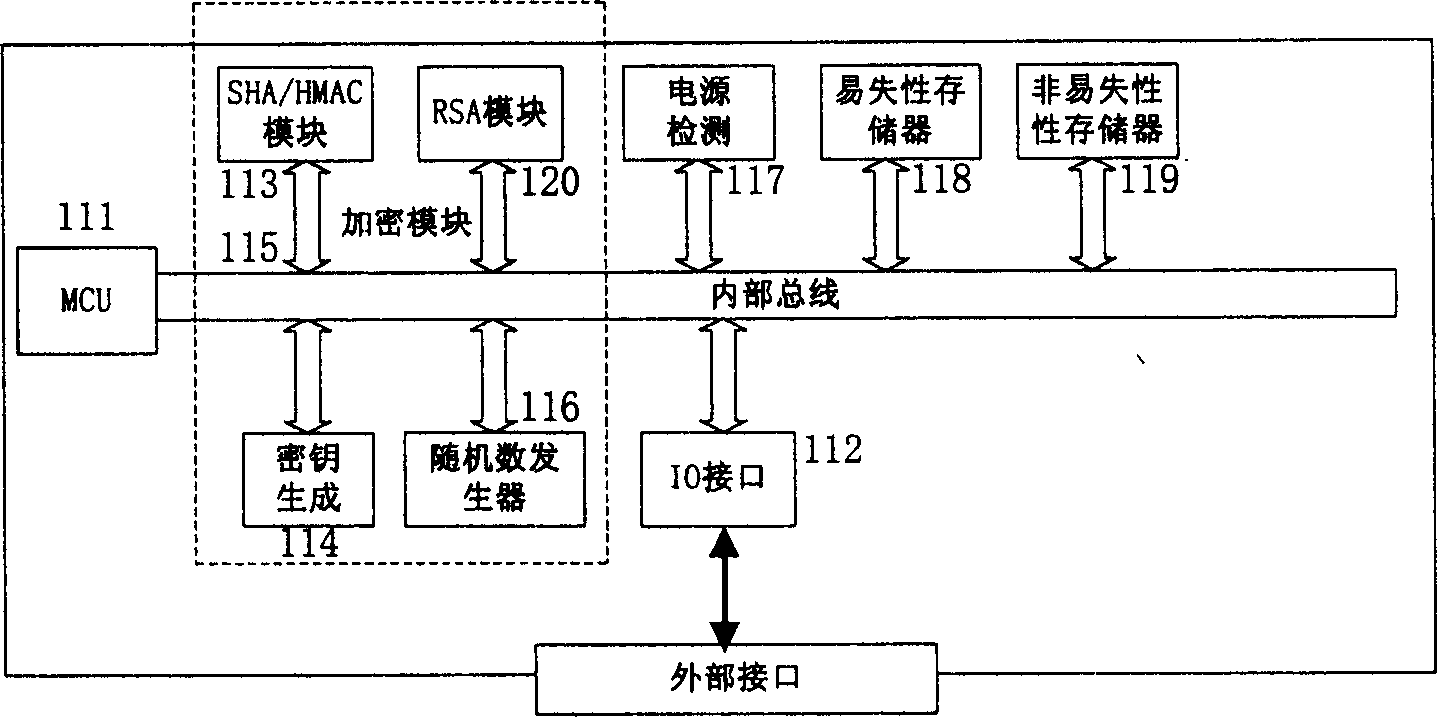
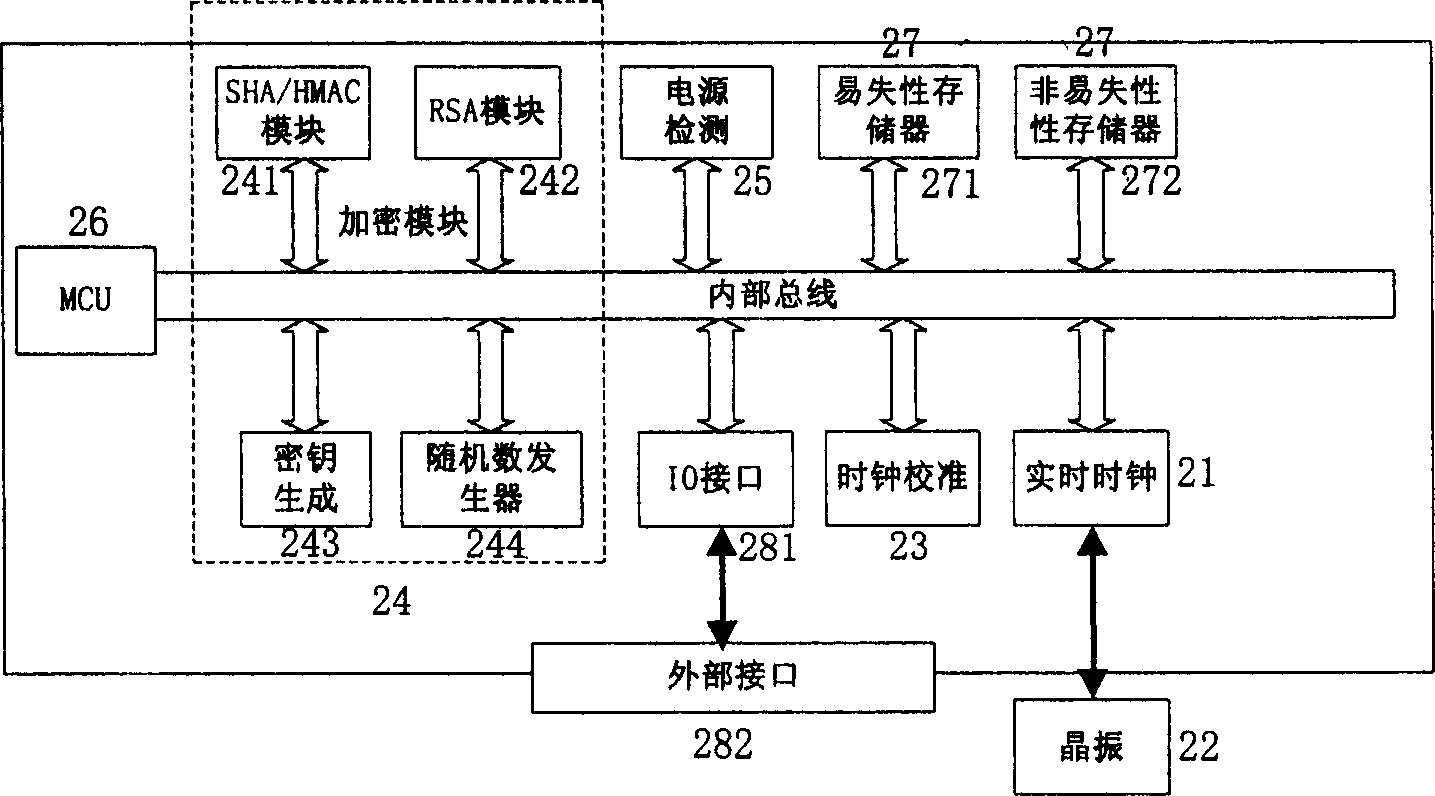
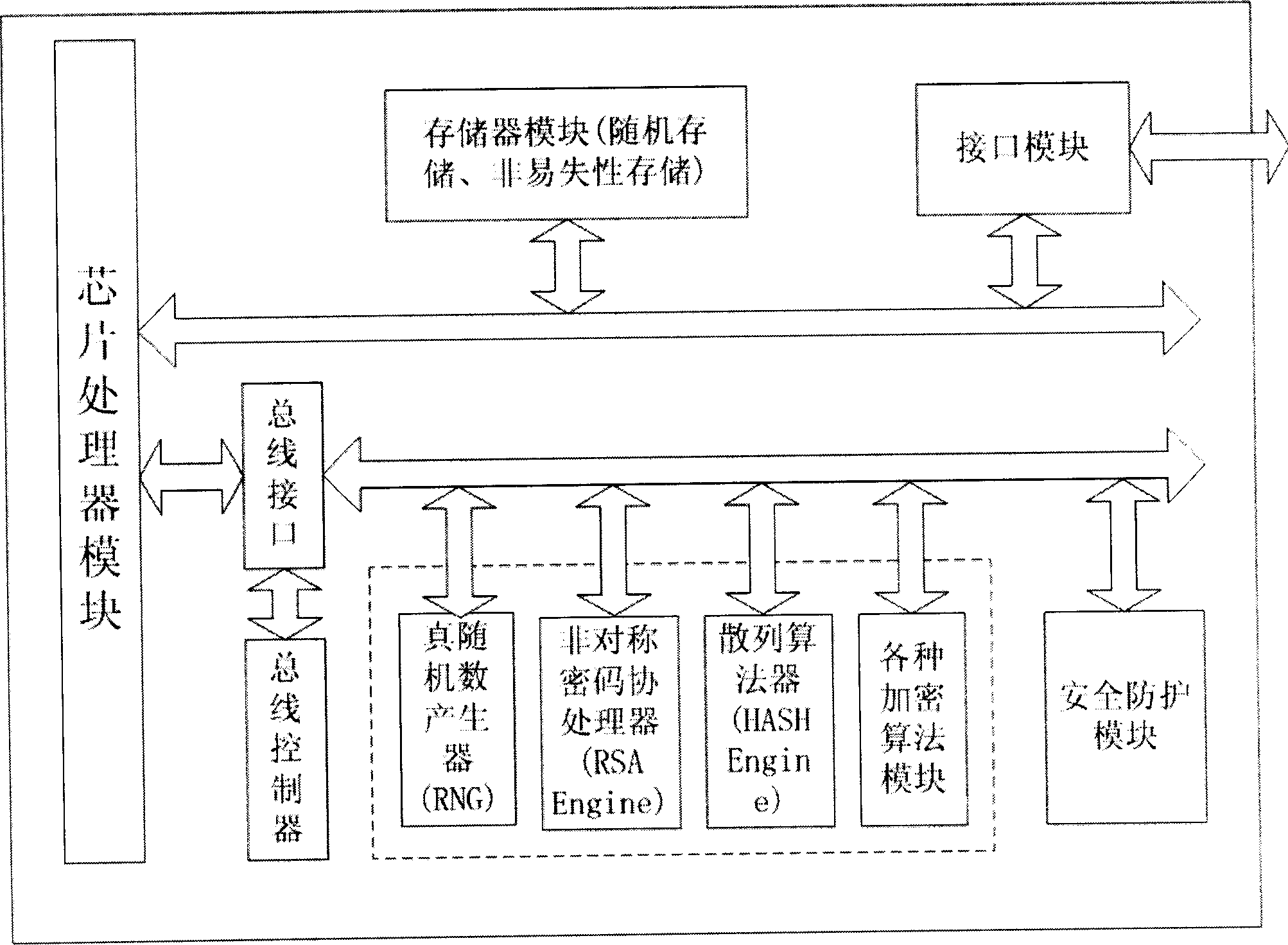
Embedded safety ship of real-time clock and method for correcting real-time clock thereof
InactiveCN1707464AVersatileGuaranteed Time AccuracyGeneral purpose stored program computerTemporal informationOperational system
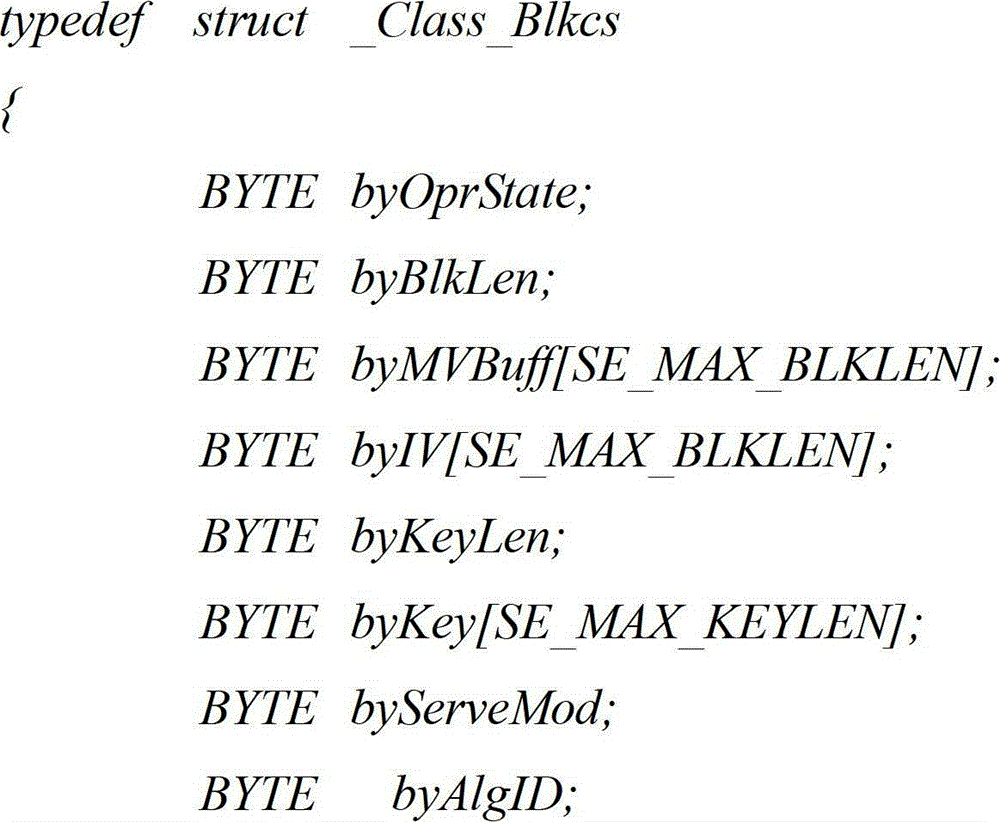
The present invention reveals one kind of safety chip with built-in real-time clock. The safety chip includes: a real-time clock unit to provide data file with current time of the safety chip as the timestamp mark; an outer frequency generator to provide the clock unit with reference clock frequency; a clock calibrator to correct the error of the real-time clock unit for clock sync; an enciphering unit to generate cipher key based on enciphering algorithm for the safety protection and confirmation of the safety chip read / write; and an MCU to provide the chip operation system with operation back-up and management. In addition, the present invention reveals also method of correcting the real-time clock of the safety chip. The safety chip provides data signature with non-repudiation timestamp, and can use time information in various kinds of safety service and perfect the function of safety chip.
Owner:LENOVO (BEIJING) CO LTD
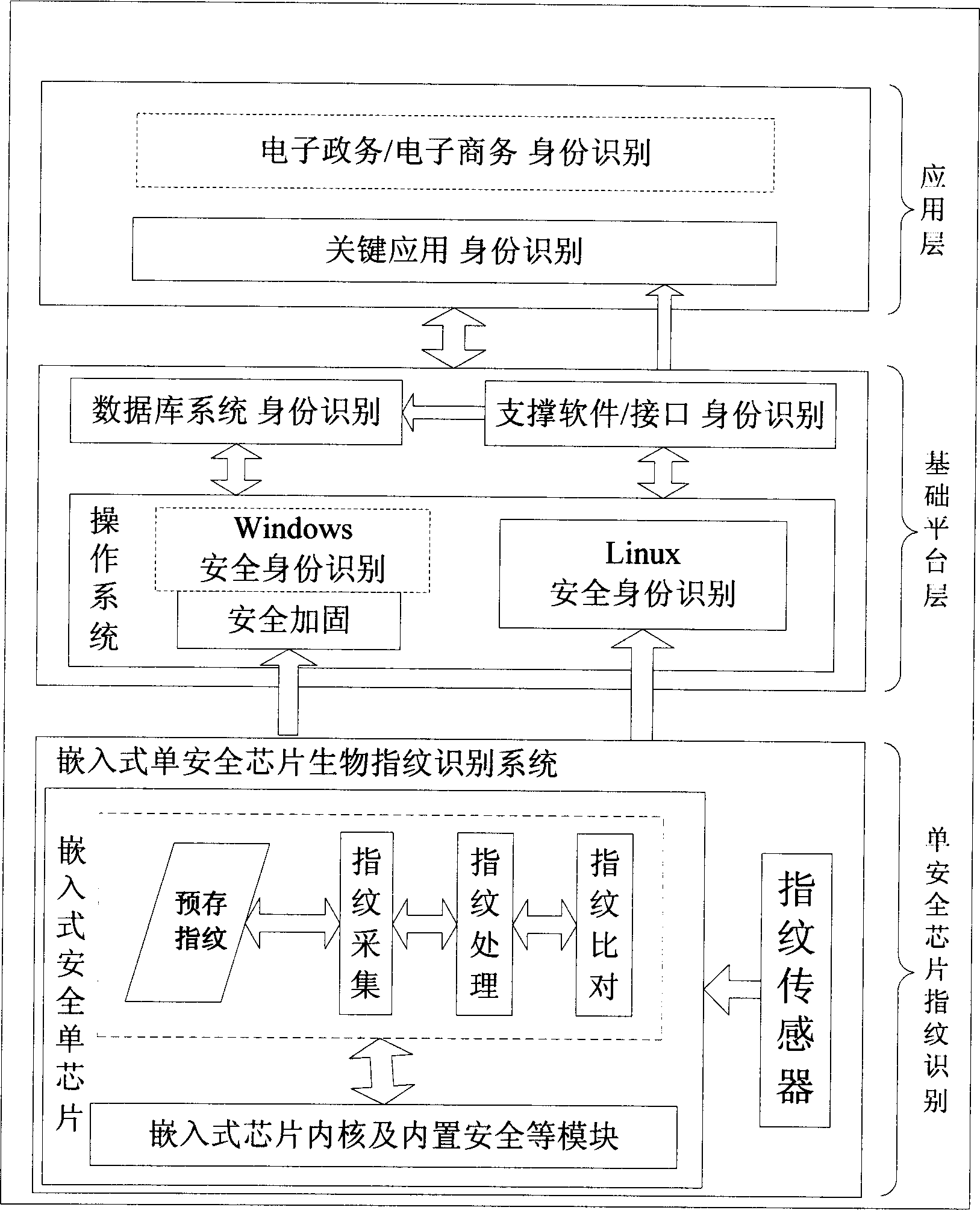
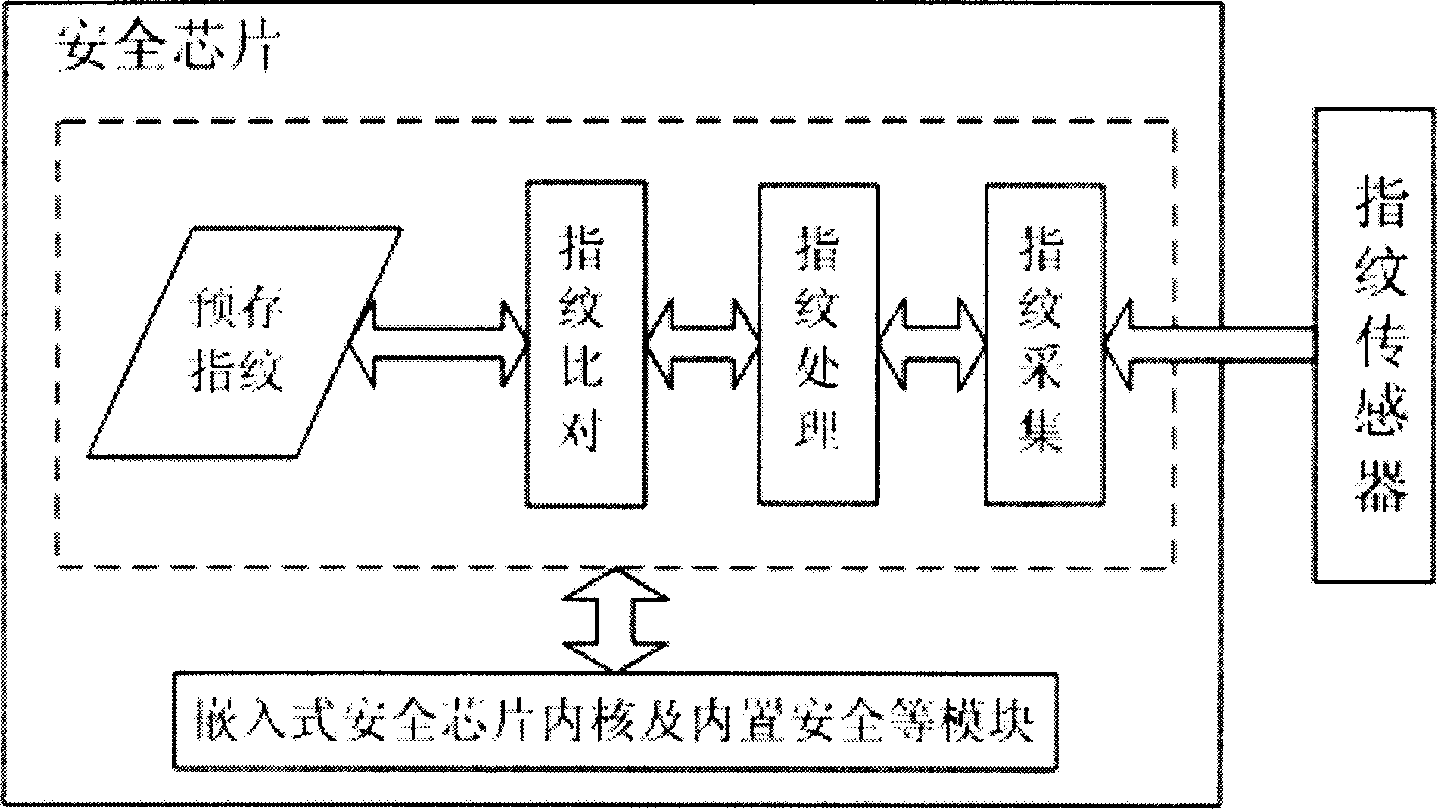
Embedded single secure chip biological fingerprint recognition system and method thereof
InactiveCN1885315AIntegrity guaranteedEnsure integrityCharacter and pattern recognitionDigital data authenticationOperational systemChip operating system
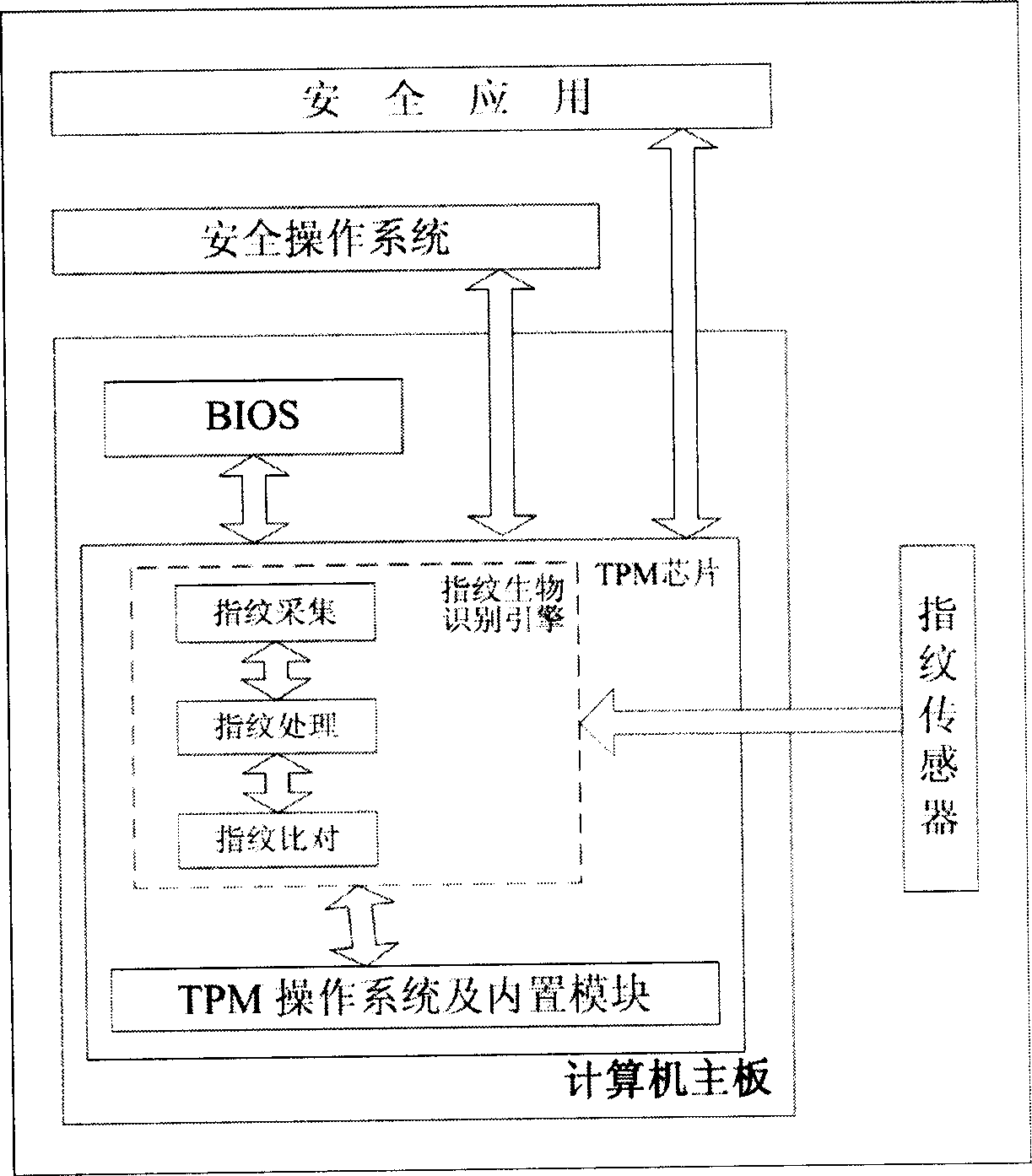
The invention relates to an embedded single safety chip biological fingerprint recognize system and relative method, wherein said safety chip contains chip operation system, internal micro processor, volatile memory and non-volatile memory, safety module and other manage module; the fingerprint collecting, processing and comparing modules are arranged inside the safety chip; the output of fingerprint sensor is connected to the fingerprint collecting module, the fingerprint processing module, and the fingerprint comparing module; and the inventive method comprises: collecting the original image information of fingerprint; extracting fingerprint character information to generate recognize code, to judge if initializing fingerprint register setting, and store recognize code into non-volatile memory of safety chip based on judged result, or extract the recognize code stored in the safety chip to be compared. The invention has high dual-factor safety and reliability, high stability and wider application.
Owner:上海一维科技有限公司
Finger print biological identifying engine system and its identifying method based on credible platform module
InactiveCN1822013AIntegrity guaranteedEnsure integrityCharacter and pattern recognitionDigital data authenticationOperational systemChip operating system
This invention relates to a fingerprint biology identifying engine system based on a trustable platform module and a method, in which, the TPM chip in the system has a functional module and a chip operation system, a fingerprint sensor, a fingerprint collection and a process module loaded by the computer mainboard, a nonvolatile memory, a fingerprint comparing module in the TPM chip of the trustable platform module, in which, the sensor is connected with the non-volatile memory by the collection module, a process module and the fingerprint comparison module. Said method includes collecting the original image information of the fingerprint, picking up its character information and generating an identification code, judging if the initial fingerprint has registered then to store the identification code in the non-volatile memory of the TPM chip or pick up the identification code stored in the TPM chip to be compared.
Owner:上海一维科技有限公司
Method for receiving and processing multi-terminal information by self-adapting SIM chip operating system
InactiveCN101334913AExtended pin functionRadio/inductive link selection arrangementsCoded identity card or credit card actuationCommunication interfaceOperational system
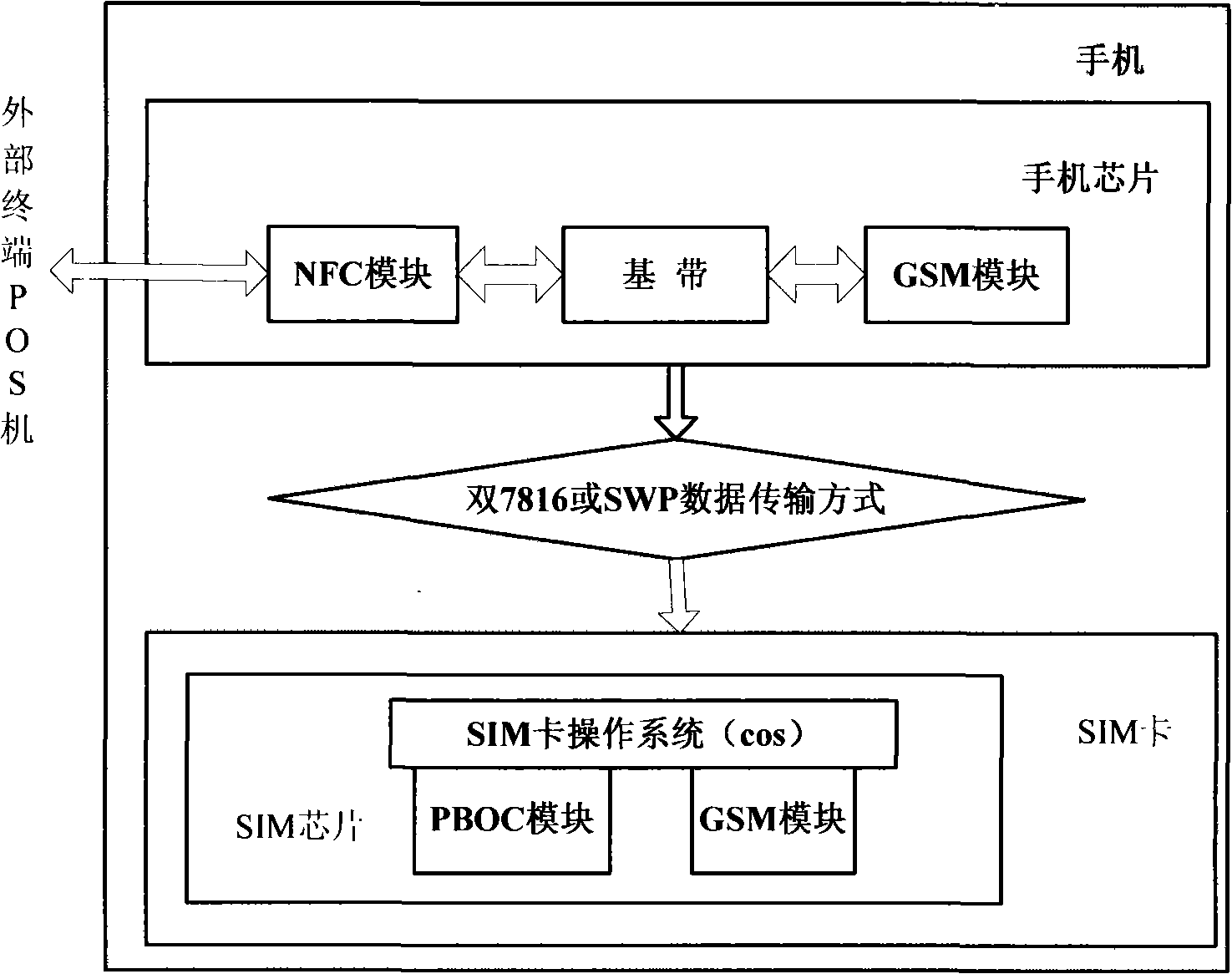
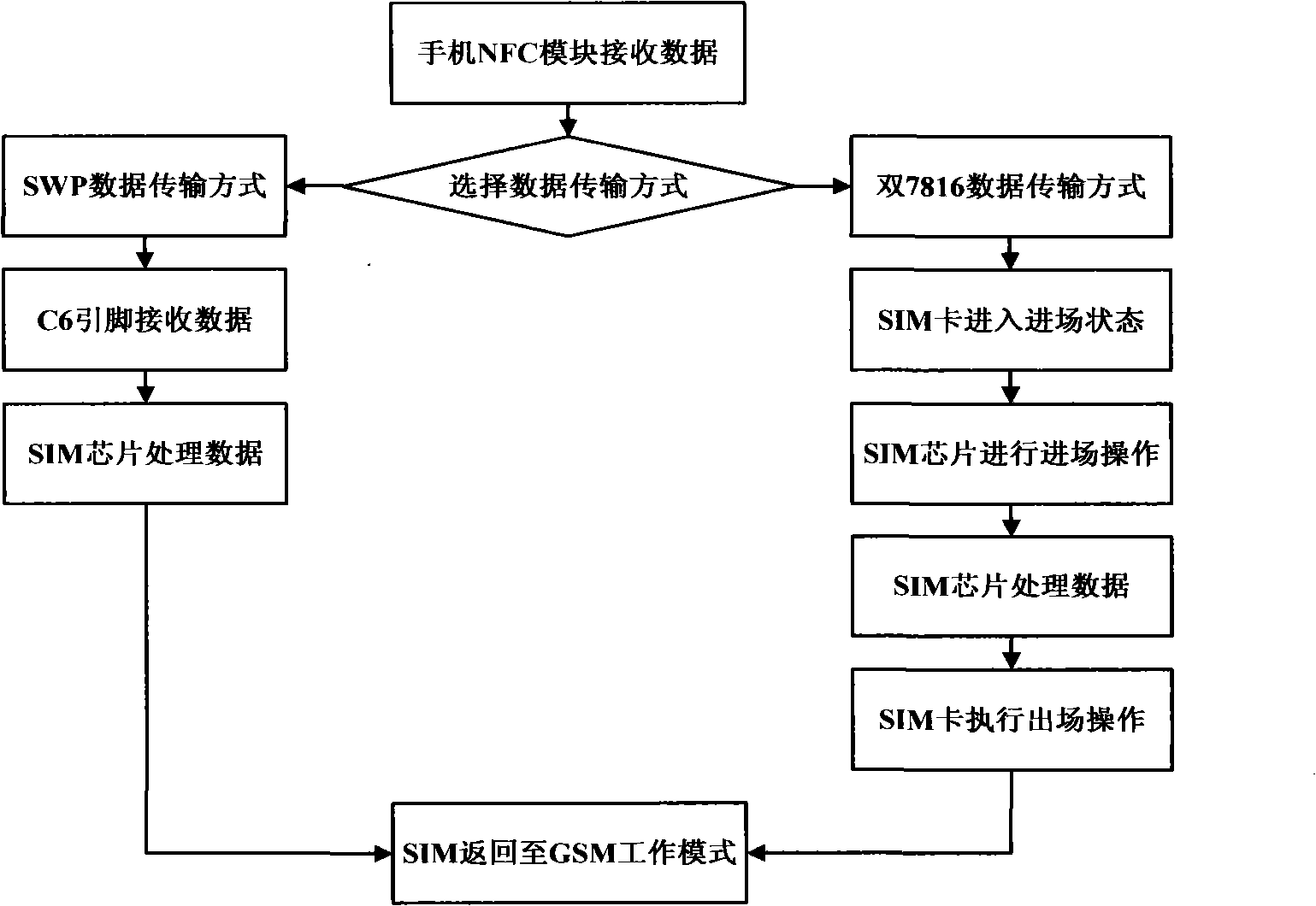
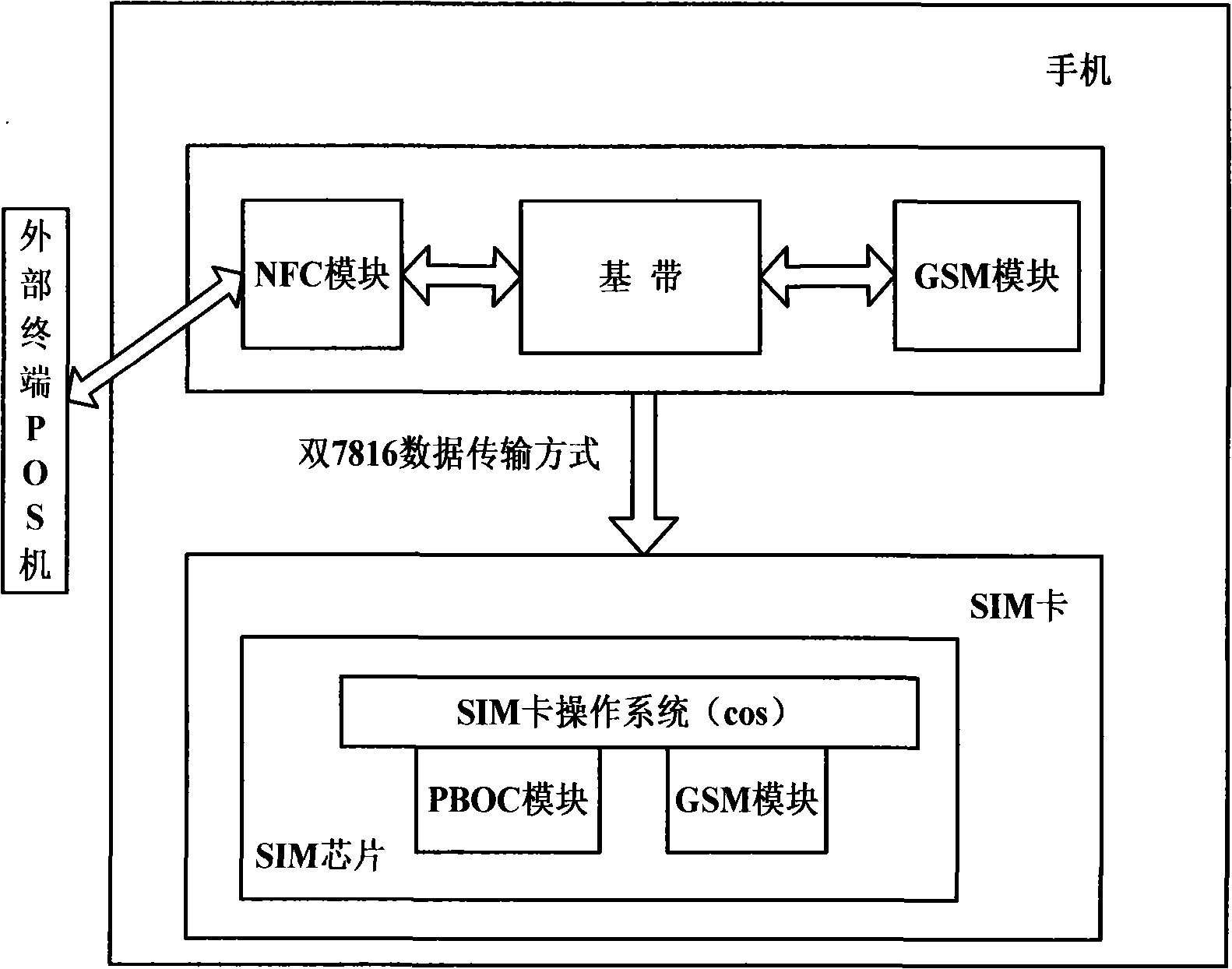
The invention relates to a multi-terminal information receiving and processing method for a self-adapting SIM chip operating system, which pertains to the technical field of mobile communication. The method comprises the steps that: first, a data communication interface of a mobile terminal is connected with a C6 pin on an SIM chip; then an NFC module in the mobile terminal receives a PBOC data command sent by an external terminal POS machine in a non-access manner according to14443 Wireless Application Protocol; the SIM chip receives data in a bidirectional 7816 standard data transmission way or in an SWP data transmission way; in the 7816 standard data transmission way, after receiving PBOC data, an SIM card enters an approach operation; a PBOC logic processing module processes credit for unload operation and credit for load operation corresponding to the PBOC data command and enters a withdrawal operation and backs to a GSM operation mode. In the SWP data transmission way, the SIM chip receives the data by the C6 pin and executes relevant operations; after operations are finished, the SIM chip is in the GSM operation mode; the two transmission ways are complementary and mutually independent and can be compatible with various mobile terminals and the hardware of the SIM chip.
Owner:SHANGHAI COS SOFTWARE CO LTD
Heterogeneous many-core chip oriented quantized power consumption control method
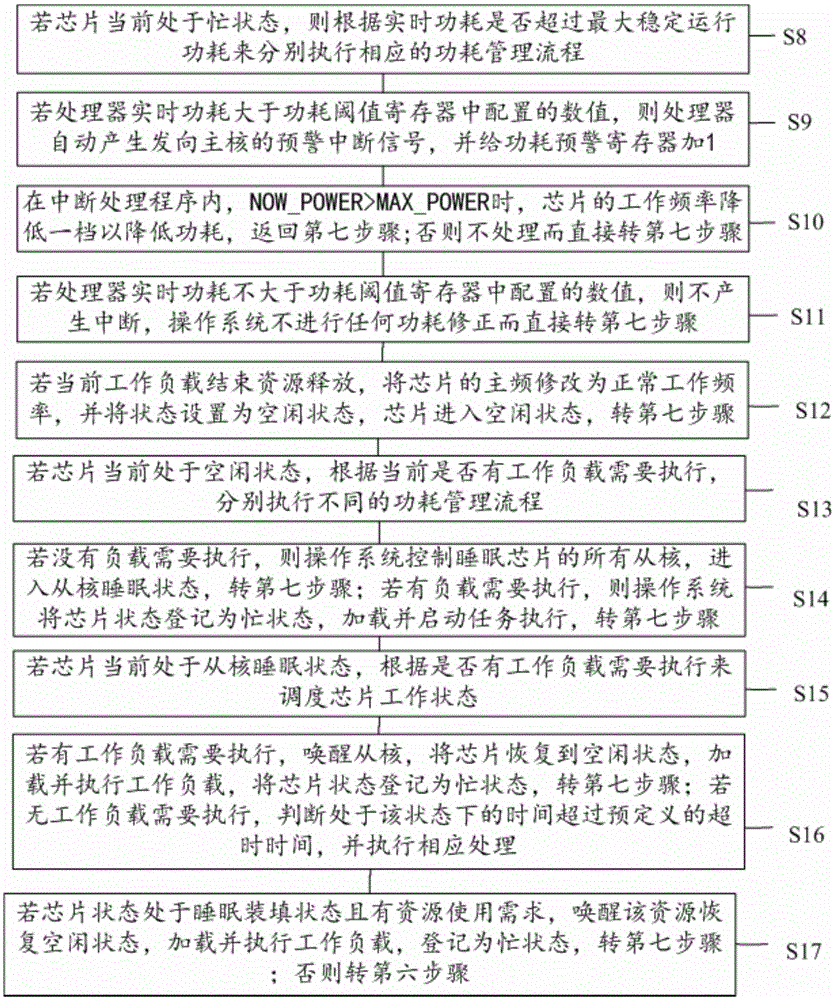
ActiveCN105487634AFast power managementIncrease incomePower supply for data processingChip operating systemManagement process
The invention discloses a heterogeneous many-core chip oriented quantized power consumption control method. The method comprises: obtaining reference power consumption data of a heterogeneous many-core chip in each state and establishing an external basic power consumption data table; obtaining a frequency grade table of all stable running frequencies supported by the heterogeneous many-core chip; and for all the stable running frequencies, establishing an existence relationship of chip power consumption of running same application codes in different frequencies, wherein the higher the frequency is and the higher the power consumption is, and the working power consumption of the lowest frequency grade is certainly smaller than the maximum stable running power consumption; establishing a power consumption management policy of the chip as a power consumption management basis; after a many-core operating system is started, initializing both a power consumption threshold register and a power consumption pre-warning register according to the maximum stable running power consumption; and when the operating system of the many-core chip runs, starting a power consumption management process by an external power consumption management system, and notifying the basic power consumption table, the frequency grade table and the power consumption management policy to the operating system of each heterogeneous many-core chip.
Owner:JIANGNAN INST OF COMPUTING TECH
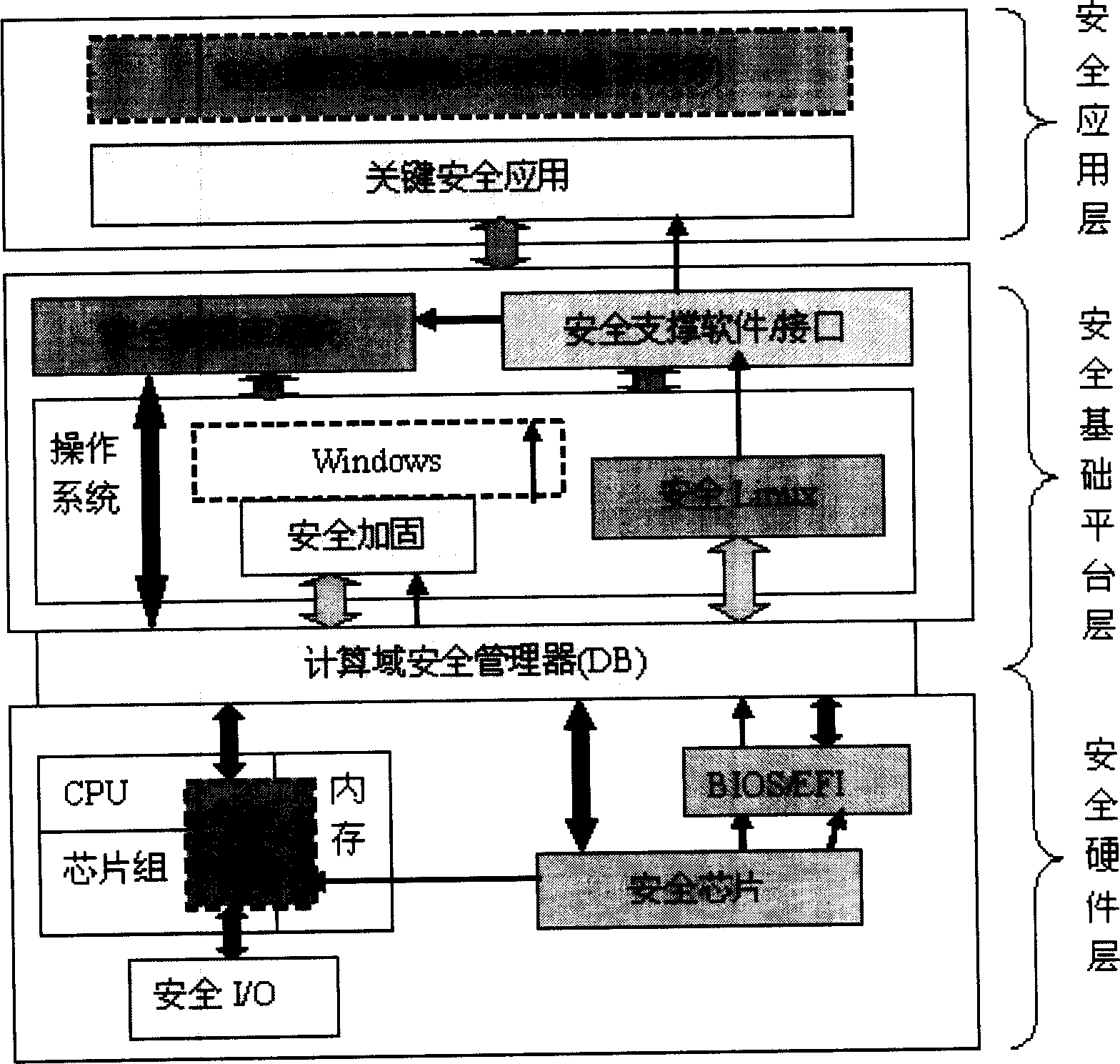
Portable trustworthy private information processing system
ActiveCN102184357AEnsure data securityConvenient and safe to carry outInternal/peripheral component protectionDigital data authenticationInformation processingTrustworthy computing
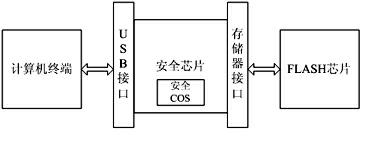
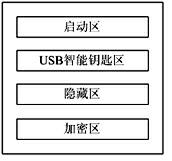
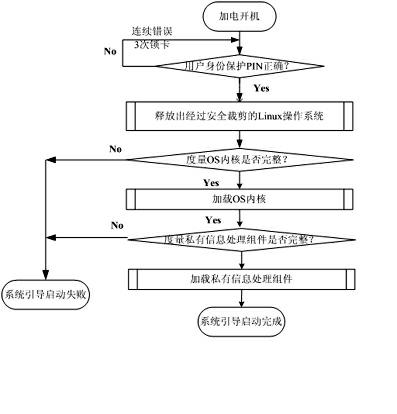
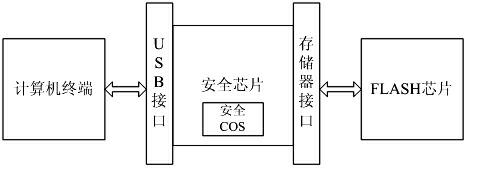
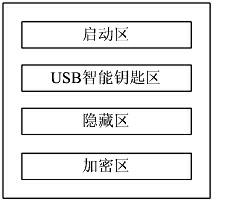
The invention discloses a portable trustworthy private information processing system. The system physically comprises a safety chip, a Flash memory chip and a safety COS (Chip Operating System), and logically comprises a starting region, a USB (Universal Serial Bus) intelligent key region, a hidden region and an encryption region. When a computer terminal is set to be booted from a USB port and is started to run through the system, an entire computing environment is guaranteed to be trustworthy through trusted boot and measurement; and when the computer terminal is not started and booted from the system, the system can be independently used as an encrypted U disk. Through the system, the problem of safety for personal private information processing is solved, and the trustworthy computing environment is constructed.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Work method of analog card reader and analog communication system
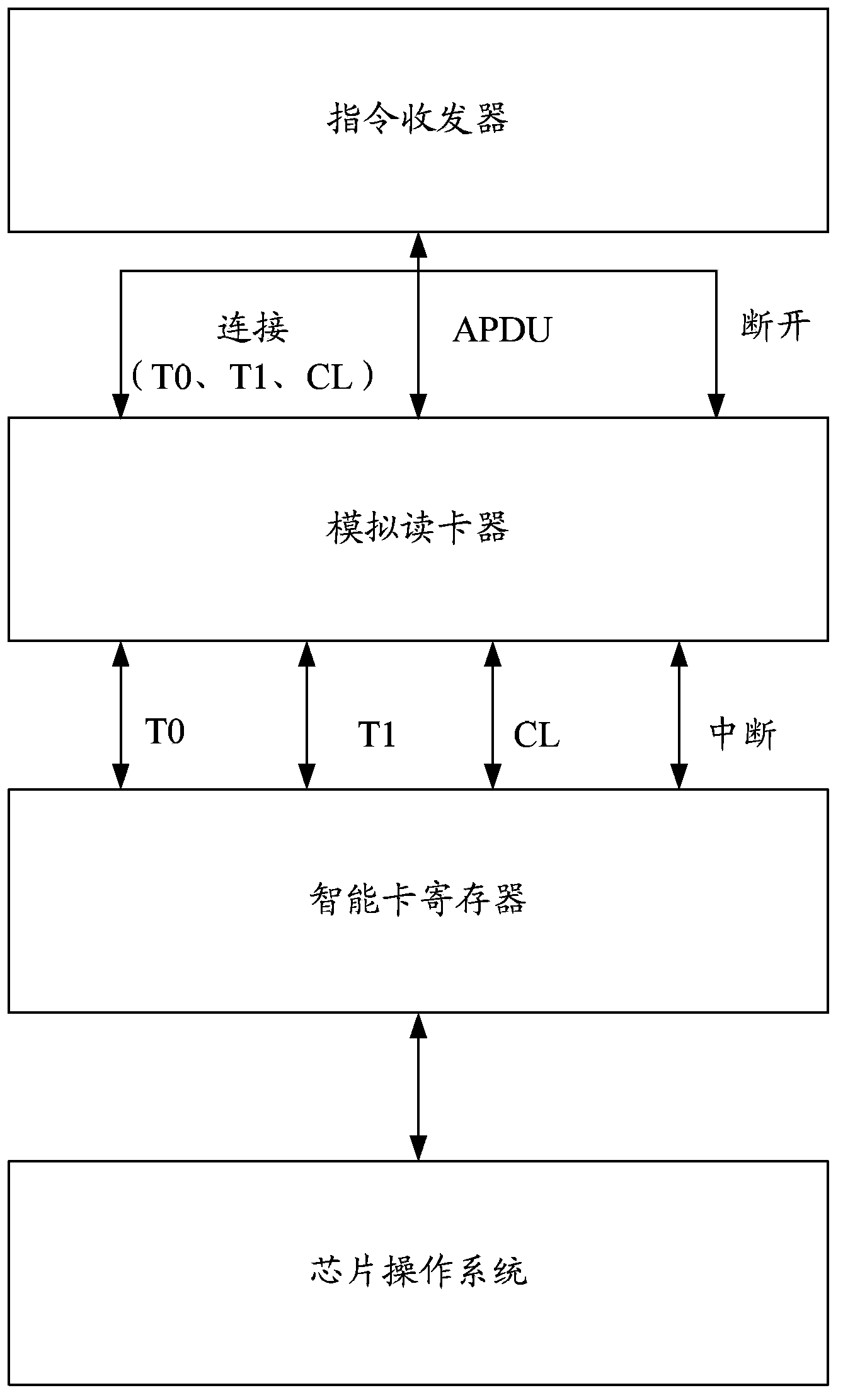
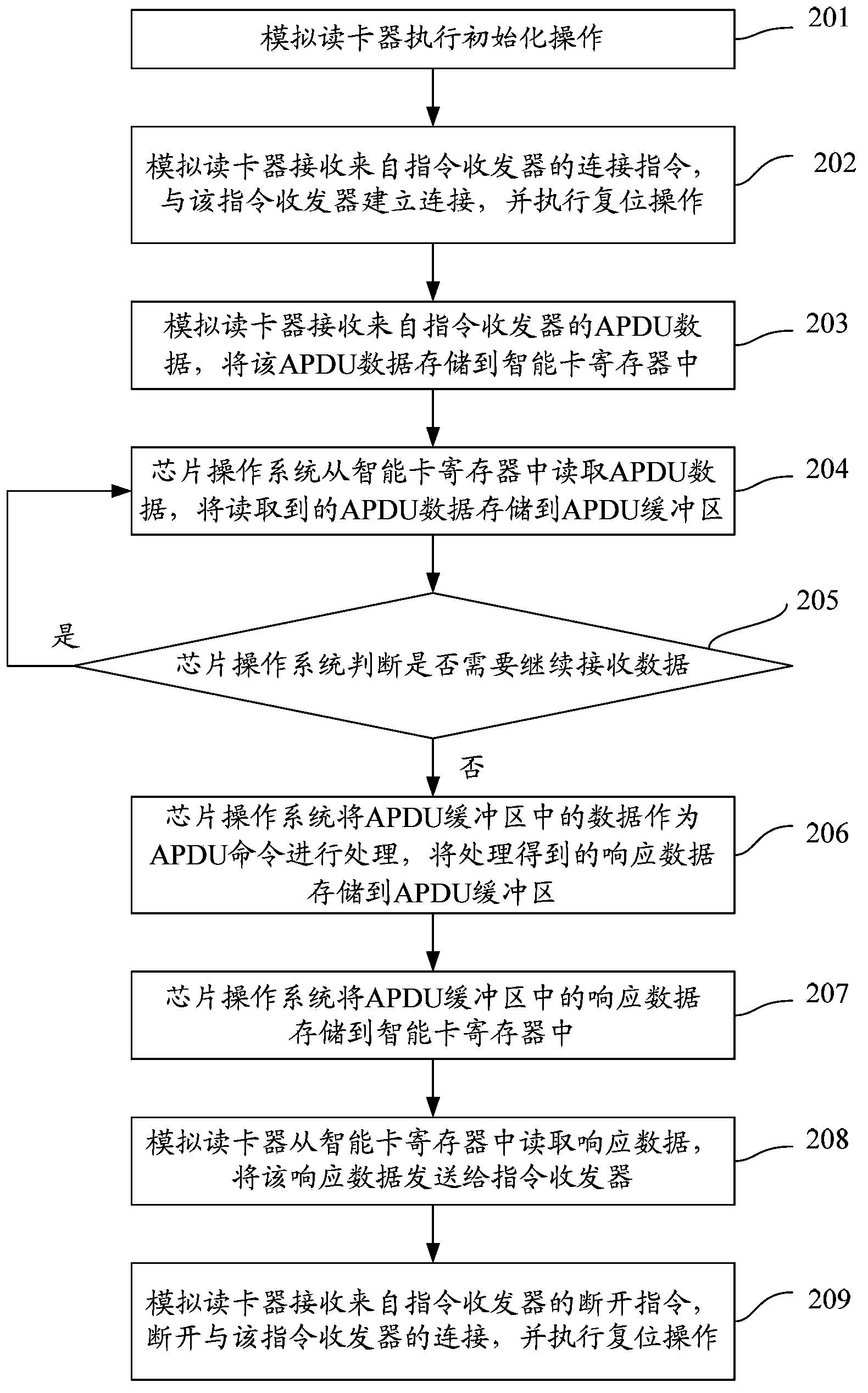
ActiveCN103365701ASave resourcesReduce Simulation Power ConsumptionSoftware testing/debuggingSoftware simulation/interpretation/emulationTransceiverChip operating system
The invention discloses a work method of an analog card reader and an analog communication system. The method is applied to a system comprising the analog card reader, a chip operating system, an instruction transceiver and a smart card register, wherein the analog card reader is used for detecting the communication state between the analog card reader and the instruction transceiver, and the state of the smart card register, conducting read-write operation on the smart card register according to the communication state and the state of the smart card register, and updating the state of the smart card register; the chip operating system is used for detecting the state of the smart card register, conducting read-write operation on the smart card register according to the detected result, and updating the state of the smart card register. As the analog communication between the chip operating system and the instruction transceiver is established through the analog card reader, the purpose of inputting terminal data to the chip operating system under the condition that no hardware simulator is used is realized, the emulation function range is broadened, hardware resource is saved, and emulation power consumption is reduced.
Owner:FEITIAN TECHNOLOGIES
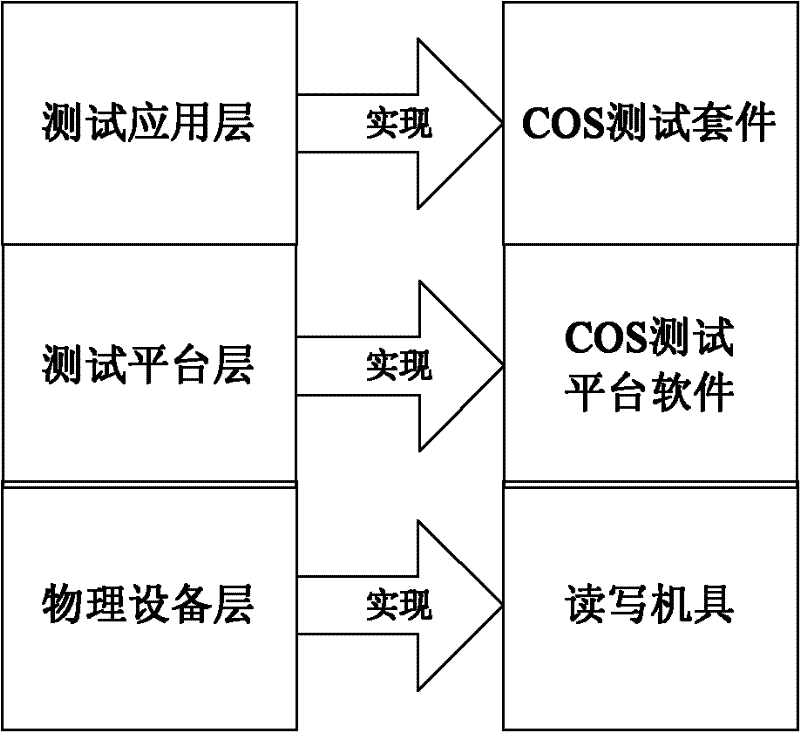
System and method for testing chip operating system (COS)
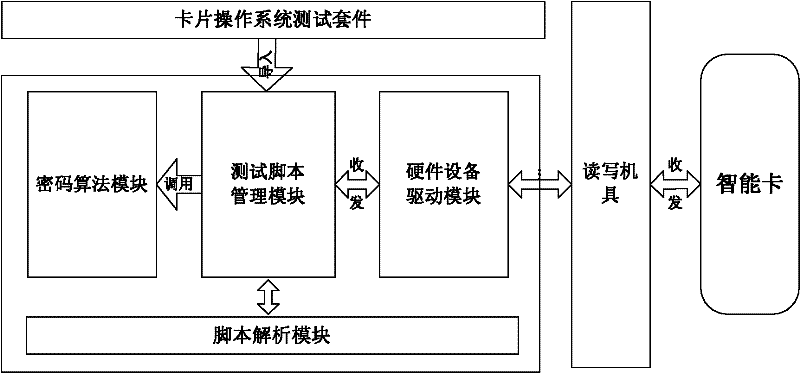
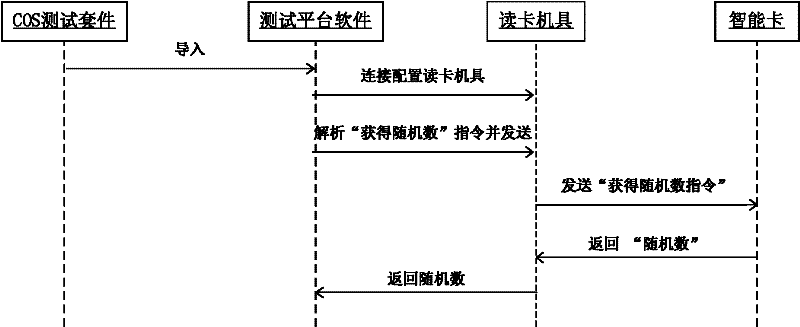
InactiveCN102479123AGuaranteed smooth executionPromote expansionDetecting faulty computer hardwareOperational systemTest script
The invention discloses a system for testing a chip operating system (COS). The system for testing the COS comprises a COS test external member, COS test platform software and COS test equipment. The test system establishes a closed loop test method for proximate coupling device (PCD) and proximate integrated chip cards (PICC); due to a modularized design, the system is easy to expand; by virtue of a script resolving core module, all test scripts can be executed successfully; by virtue of logs, shortcomings are convenient to position and track; and during the COS test, test cases are developed and executed attentively. The invention also discloses a method for testing the COS.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
USB (Universal Serial Bus) embedded trustworthiness private information processing device and system
ActiveCN102184358AEnsure data securityConvenient and safe to carry outInternal/peripheral component protectionPlatform integrity maintainanceInformation processingChip operating system
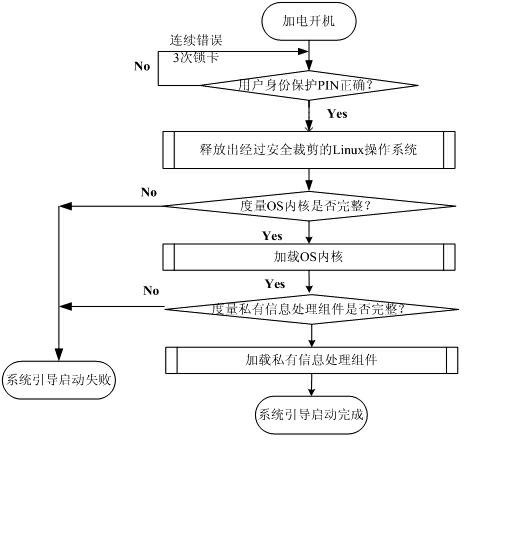
The invention discloses a USB (Universal Serial Bus) embedded trustworthiness private information processing device and system. The USB embedded type trustworthiness private information processing device is used as a hardware base and a safe support of the whole system, and a self-clipped LINUX operating system and a private information processing assembly are used as a software base of the wholesystem. The USB embedded type trustworthiness private information processing device physically comprises a safety chip, a Flash storage chip and a safety COS (Chip Operating System), and logically comprises a starting region, a USB smart key region, a hiding region and an encrypting region. When a computer terminal is set to be introduced from a USB port and operates after started by the system, the whole computing environment is trustable through trusted guide and measurement; and when the computer terminal is not started and guided by the system, the system can be individually used as an encrypted U disk. According to the invention, the safety problem of individual private information processing is solved and a trustable computing environment is constructed.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Method and device used for multi-mode smart card operating system
InactiveCN101068416AAvoid demandSimple methodRadio/inductive link selection arrangementsRecord carriers used with machinesChip operating systemOperational system
An operation system of multimode intelligent card is prepared as setting three layers of hardware layer and kernel layer as well as application protocol layer from bottom to top, using each layer as a relatively independent subsystem and setting a numbers of function-banks on each layer according to operation mode required by mobile terminal. Its operating method is also disclosed.
Owner:BEIJING HENGBAO INFORMATION TECH
Electronic anti-fake label and realizing method
InactiveCN104217241APrevent Illegal RecyclingCo-operative working arrangementsRecord carriers used with machinesChip operating systemComputer module
The invention relates to an electronic anti-fake label and a realizing method. The anti-fake label embedded into a commodity mainly comprises a hardware encryption and decryption module of a passive band chip operating system (COS), a coil and a destruction activation device, wherein the hardware encryption and decryption module of the passive band COS comprises a central processing unit (CPU) encryption chip and a memorizer, anti-fake activity is performed through an asymmetrical secret key encryption algorithm, and data read-write is performed through a non-contact mode; and the coil and the destruction activation device are connected with the CPU encryption chip, through excitation of the destruction activation device, the CPU encryption chip detects a disconnection state or changes and performs processing as follows to identify that the anti-fake label is opened: the access function of the CPU encryption chip is turned off, or internal data of the anti-fake label is cleared, or the CPU encryption chip is directly added with information that the commodity is already used.
Owner:安徽云盾信息技术有限公司
Method for achieving symmetric cipher service based on intelligent card chip operating system (COS)
ActiveCN102752104AImprove securityImprove password service efficiencyKey distribution for secure communicationChip operating systemOperational system
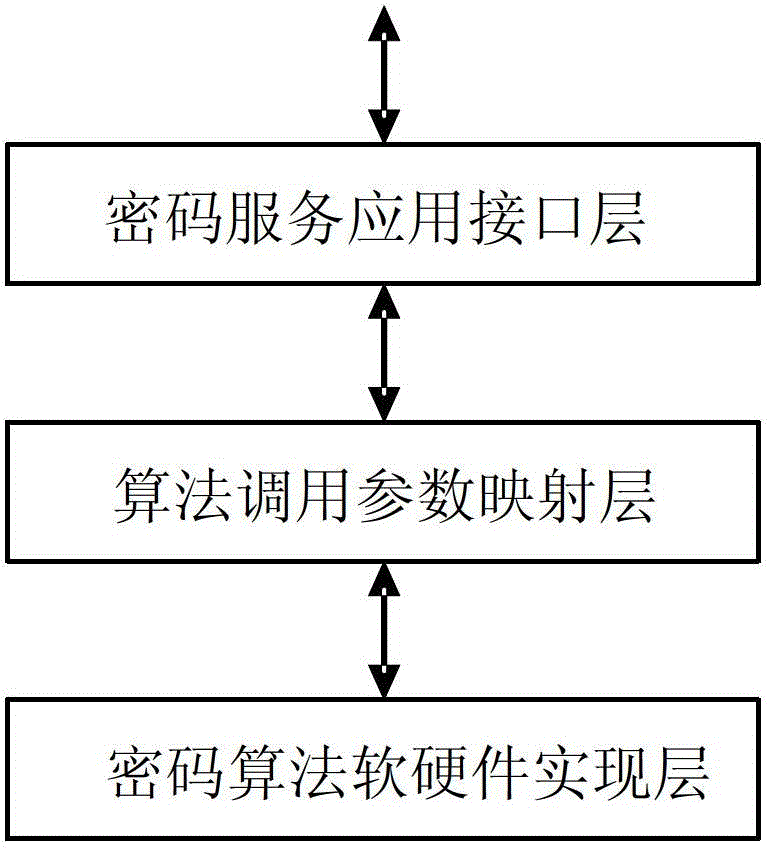
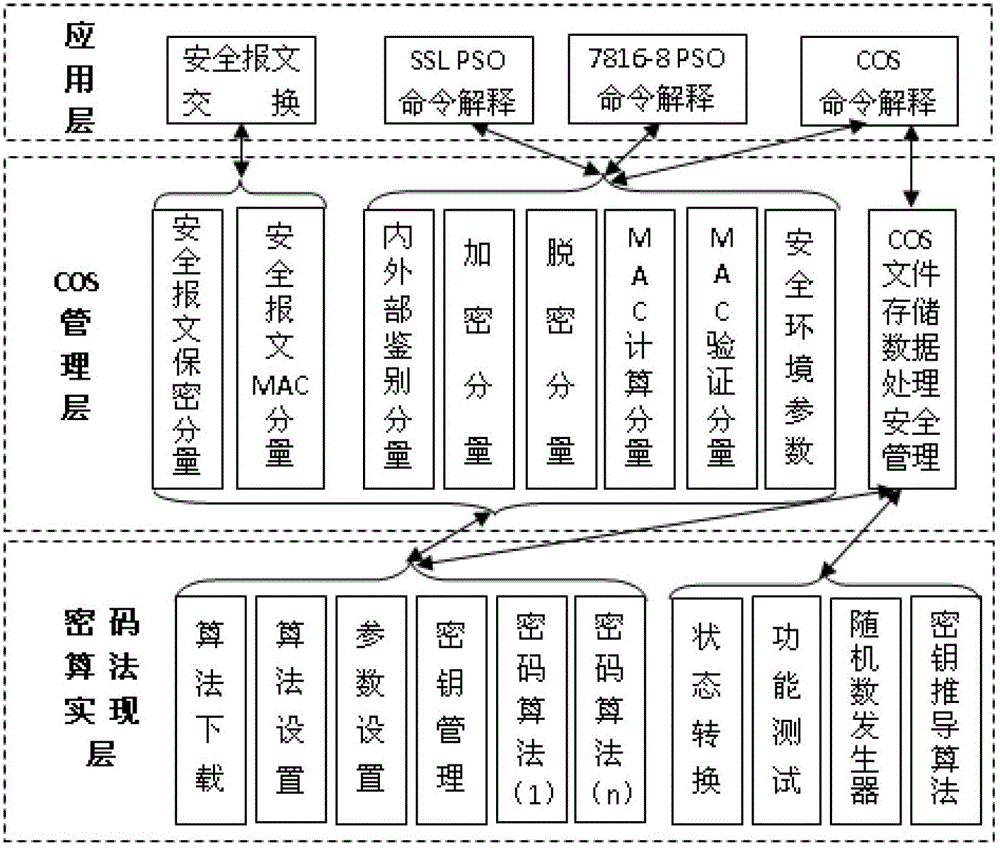
The invention provides a method for achieving symmetric cipher service based on an intelligent card chip operating system (COS). The symmetric cipher service in the intelligent card COS is packaged into an application interface layer of cipher service, an algorithm call parameter mapping layer and an algorithm software and hardware interface layer, wherein the application interface layer of the cipher service transfers corresponding data to be processed and control parameters, and the algorithm call parameter mapping layer is used for transferring corresponding cipher service parameters and performing secure environment detection. Corresponding working processes of the algorithm software and hardware interface layer are started, detection on whether cipher service processes are completed is performed, and the intelligent card operation system obtains results of the current cipher service through the application interface layer of the cipher service if crypto-operation is completed. According to the method, the object-oriented programming design concept is adopted, the symmetric cipher service in the COS is packaged, seamless transplantation and extension of the symmetric cipher service on different hardware platforms can be achieved, efficiency of the cipher service is improved, centralized safety control is performed on symmetric cipher algorithm, and safety in using of the cipher algorithm is improved.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
High security removable storage device
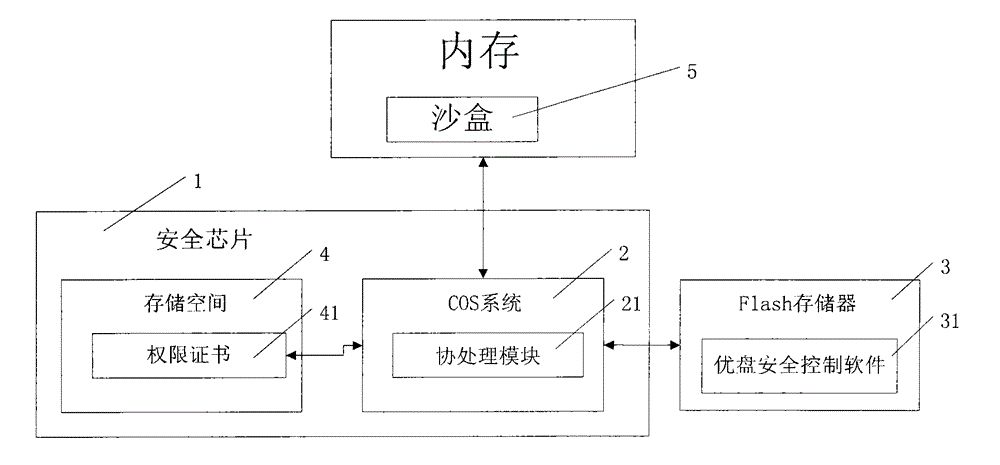
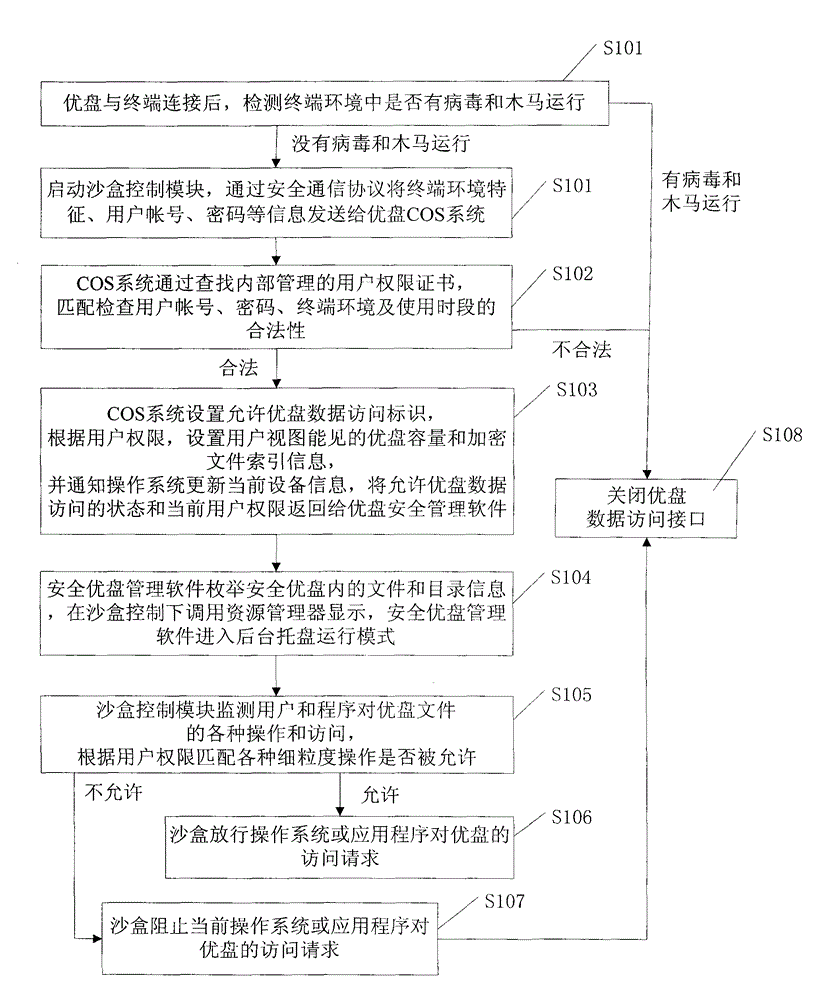
InactiveCN104102595AReduce the risk of useProtect Physical SecurityUnauthorized memory use protectionInternal/peripheral component protectionChip operating systemData view
The invention provides a high security removable storage device which comprises a safe main control chip, a chip operating system (COS) arranged in the chip, a flash memory and removable storage device safety management software arranged in the flash memory, wherein the COS system is stored in the safe chip and is used for managing the authority certificates corresponding to users; the removable storage device safety management software adopts a memory sandbox technology, and is used for monitoring and filtering various operations which are carried out on a removable storage device by the users and programs, checking the device service environment and the access authority of the removable storage device by being matched with the COS system, controlling the unauthorized use behaviors of data files of the removable storage device decoded to the memory, and recording various key sensitive operations. The high security removable storage device adopts an integral protection technology combining software and hardware, so that the security access control of the removable storage device can be realized, and the users having different authorities have different data views and fine grit operation authorities for the removable storage device; therefore, the users are prevented from privately copying the files and the content in the removable storage device, and the data of the removable storage device is prevented from being broken and stolen by viruses and Trojan horses.
Owner:张永昌
Method for improving reliability of server mainboard BMC
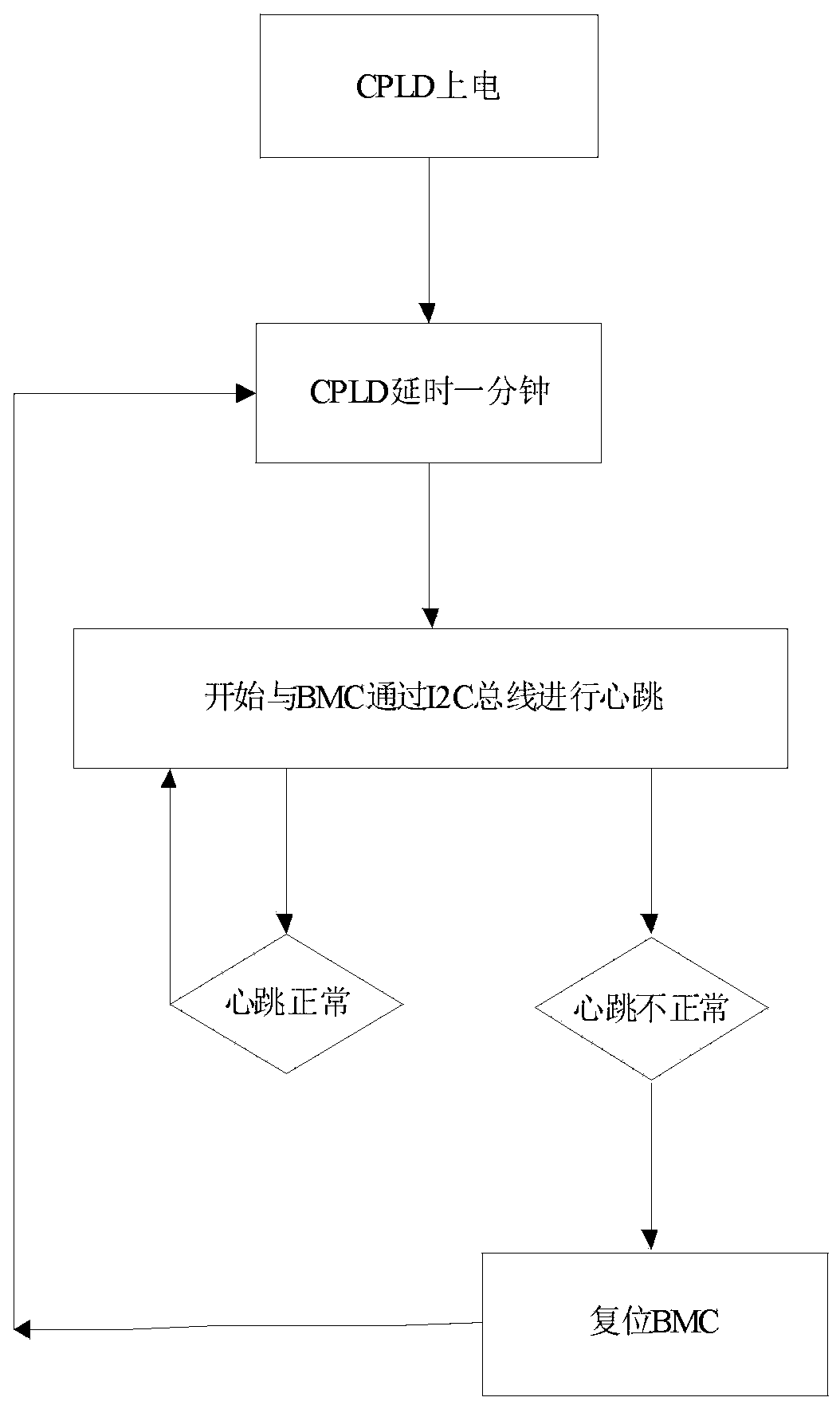
InactiveCN107797880AImprove reliabilityEasy to useFault responseData resettingChip operating systemDependability
The invention discloses a method for improving the reliability of a server mainboard BMC. Based on the server with a BMC chip, the method comprises the steps that firstly, a complex programmable logicdevice (CPLD) and the BMC chip are in communication connection; then heartbeat communication is carried out, and whether the BMC is crashed or not is judged according to the heartbeat condition; whenthe BMC is crashed, a rest signal for controlling the BMC chip is sent to the BMC chip for resetting through the CPLD, and the server BMC resetting process is completed. Compared with the prior art,the method for improving the reliability of the server mainboard BMC has the advantages that a person does not need to go up to a server to reset the server BMC, use by a client is convenient, the user experience is enhanced, the crashing problem of an existing BMC chip operating system is effectively solved, high practicality is achieved, the application range is wide, and popularization is easy.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
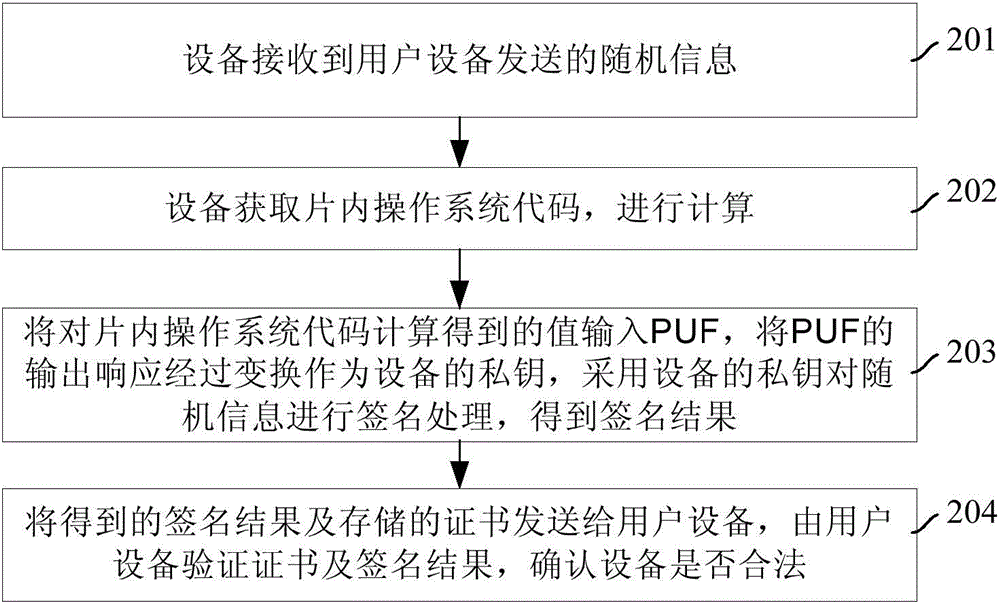
Authentication method and equipment based on PUF (Physically Unclonable Function)
InactiveCN105323069AImprove securityKey distribution for secure communicationUser identity/authority verificationChip operating systemAuthentication
The invention discloses an authentication method and equipment based on a PUF (Physically Unclonable Function). When an offline authentication method based on the PUF is carried out, a private key is generated through combining an inherent physical structure difference value based on the PUF and a chip operating system code of the equipment, and the private key is also verified through combining the inherent physical structure difference value based on the PUF and the chip operating system code of the equipment. The authenticated private key is bound with the chip operating system code of the equipment and the inherent physical structure difference value based on the PUF, any behavior which attempts to obtain the private key through modifying the chip operating system code cannot obtain the authenticated private key, so that the false equipment is prevented, and thus the safety of the equipment having the offline authentication based on the PUF is improved.
Owner:DATA ASSURANCE & COMM SECURITY CENT CHINESE ACADEMY OF SCI
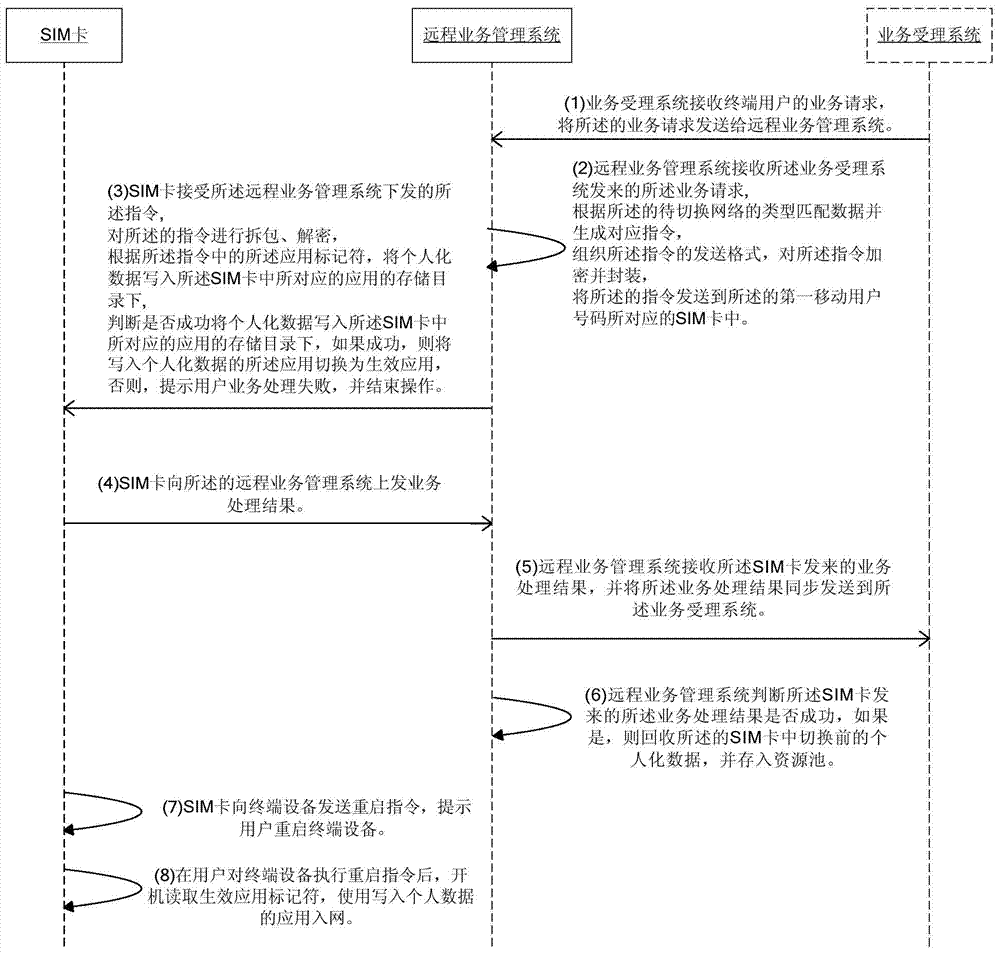
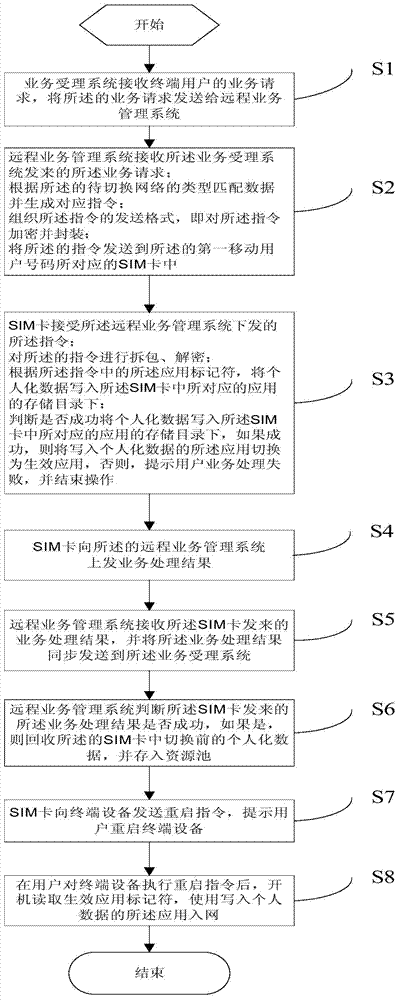
SIM (Subscriber Identity Module) card and system supporting mobile communication network switching
InactiveCN104507130AMeeting Communication NeedsFulfil requirementsWireless communicationProgrammable read-only memoryChip operating system
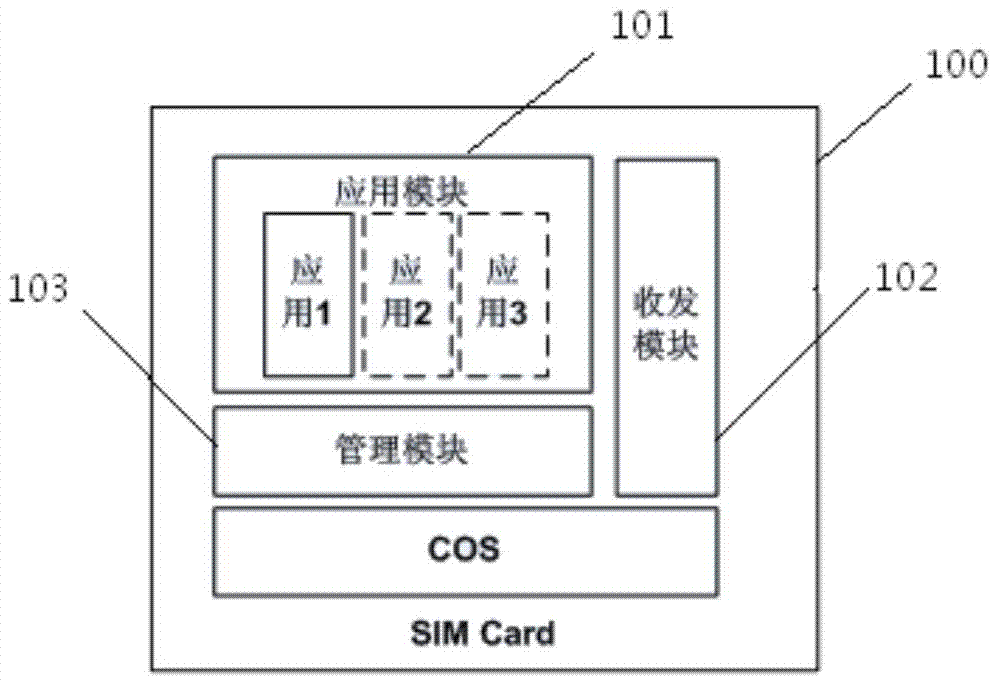
The invention relates to an SIM (Subscriber Identity Module) card and a system supporting mobile communication network switching. The conventional mobile communication network switching method requires replacing the SIM card of a user. The SIM card comprises a microprocessor CPU (Central Processing Unit), a program memory ROM (Read Only Memory), a working memory RAM (Random Access Memory), a data memory EEPROM (Electrically Erasable Programmable Read-Only Memory), a serial communication unit and an in-card operating system, wherein the in-card operating system comprises a COS (Chip Operating System). The operating system in the SIM card further comprises an application module for storing different types of applications in a grouping way, a receiving and transmitting module for receiving a command issued by a remote service management system, and a management module for processing the command received by the receiving and transmitting module, including writing personalized data into the storage directory of a corresponding application in the application module according to an application marker, calling the application module to perform application state management, and switching the application into which the personal data is written into a valid application. By adopting the SIM card and the system disclosed by the invention, a communication network can be switched without replacing the SIM card.
Owner:BEIJING WATCH DATA SYST
Electronic bill processing method, device and system
InactiveCN101945097ALarge capacityImprove securityReceipt giving machinesTransmissionChip operating systemOperational system
The invention discloses an electronic bill processing method, which comprises the following steps of: detecting whether a user logs in a chip operating system (COS) with a UKEY function device; when the user is detected to log in the COS, calling bill data in the UKEY function device to process a bill; and detecting whether the UKEY function device communicates with a bill server, and transmitting the data, which are obtained after the bill processing, to the bill server to process the data if the UKEY function device is detected to communicate with the bill server, or temporarily storing the data, which are obtained after the bill processing, in the UKEY function device if the UKEY function device is detected to not communicate with the bill server. The embodiment of the invention also discloses an electronic bill processing device and an electronic bill processing system. When the method, the device and the system are used, the drawback of a 'pure offline' or 'pure online' billing system can be overcome; and by taking the UKEY as a data carrier, the billing system has the advantages of high capacitance, high safety, convenient installation and carrying and the like.
Owner:广东亿业科技有限公司
System and method for realizing public key infrastructure (PKI) application by audio interface switching over universal serial bus (USB) protocol equipment
InactiveCN102412968AUser identity/authority verificationDigital data authenticationProtocol processingChip operating system
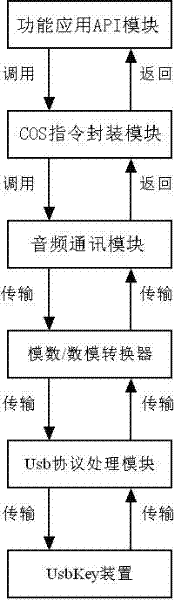
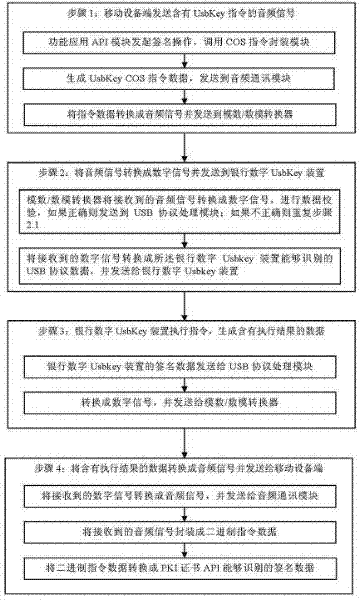
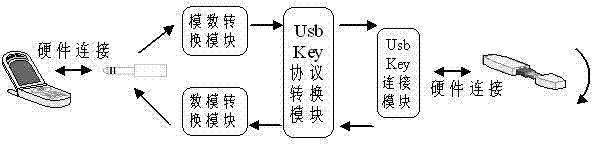
The invention disclose a system and a method for realizing public key infrastructure (PKI) application by an audio interface switching over universal serial bus (USB) protocol equipment. The system comprises a function application application programming interface (API) module, a chip operating system (CoS) instruction enclosing module, an audio frequency communication module, an analog-to-digital / digital-to-analog converter, a USB protocol processing module and a Usbkey device.
Owner:CHINA FINANCIAL CERTIFICATION AUTHORITY
Chip operating system update method, device and system
ActiveCN102855149ASimplify processing logicReduce interactionProgram loading/initiatingData connectionChip operating system
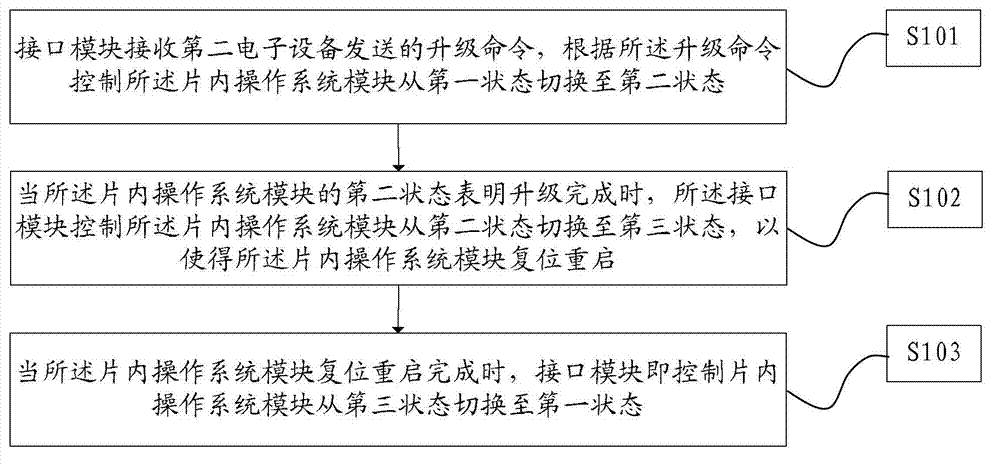
The invention relates to the technical field of data security, in particular to a chip operating system update method, a device and a system. The method is applied to a first electronic device, the first electronic device comprises a chip operating system module and an interface module, the interface module is used for controlling the reset restart state switching of the chip operating system module, and the first electronic device is in a data connection with a second electronic device. The method includes that the interface module receives an update command sent by the second electronic device, the chip operating system module is controlled to be switched from a first state to a second state according to the update command, when the second state of the chip operating system module shows that the update is completed, the chip operating system module is controlled to be switched from a second state to a third state by the interface module, so that the chip operating system module is subjected to reset restart, and when the reset restart of the chip operating system module is completed, the chip operating system module is controlled to be switched from a third state to a first state by the interface module.
Owner:FUJIAN ETIM INFORMATION & TECH
Method for realizing chip operating system (COS) safety mechanism of intelligent card
ActiveCN102663473ASecurity Mechanisms SimplifiedRecord carriers used with machinesChip operating systemSecure state
The invention discloses a method for realizing a chip operating system (COS) safety mechanism of an intelligent card. The method comprises the following steps of setting corresponding bits of a safety control word through results of external authentication and verification according to a predetermined method when the intelligent card is recognized by a reading-writing terminal equipment; reading the safety control word with set bits, analyzing the safety control word according to a predetermined method, and determining an application logic of the safety attribute; verifying whether a safety status updated by the status transfer satisfies the safety attribute under the logic condition, and executing the allowed operation; and resetting the safety control word after the predetermined operation of the intelligent card and the reading-writing terminal equipment is completed. According to the method, the realization of the safety mechanism can be simplified.
Owner:SHANDONG SYNTHESIS ELECTRONICS TECH
Safety equipment with virtual on-chip operating system, safety device with virtual on-chip operating system, systems and methods
InactiveCN102945334AComputer security arrangementsPayment protocolsChip operating systemOperational system
The invention relates to safety equipment with a virtual on-chip operating system; the safety equipment at least comprises a card body, a main chip with a virtual on-chip operating system, and IC cards, wherein the IC cards are connected with a plurality of storage secret keys, digital certificates and biological characteristic identification through a concentration line; the main chip controls the information exchange of the IC cards and the outside world through the virtual on-chip operating system; and the safety equipment is combined with memory cards, SIM cards, earphones, mobile terminal plugs, pendants and USB (Universal Serial Bus) equipment, and a safety device is combined with relevant information facilities, so that an innovative multi-application payment system, an innovative cloud service system and an innovative intelligent logistics system are built to safeguard the information safety of an intelligent city.
Owner:潘铁军
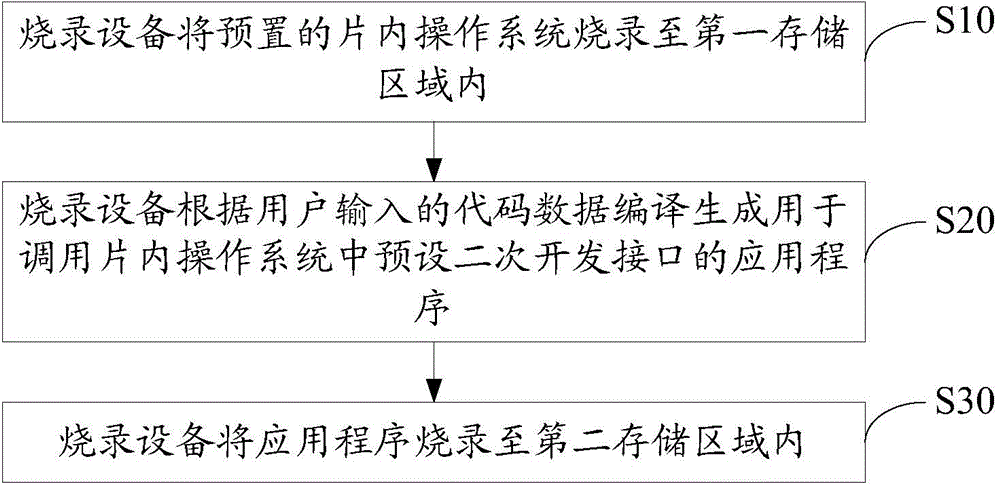
Application program burning method and system
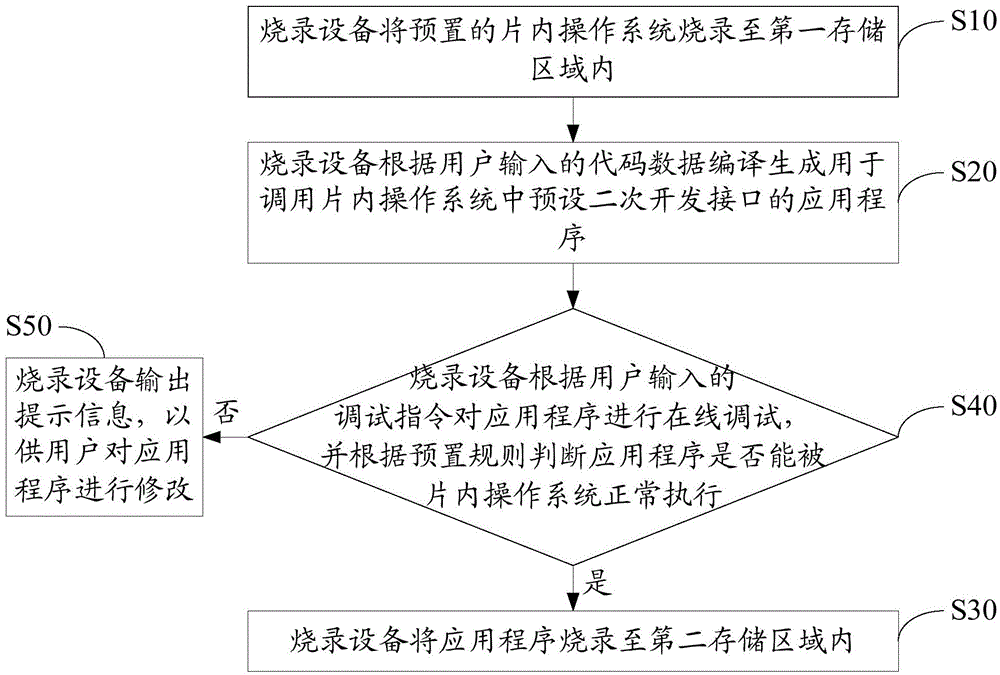
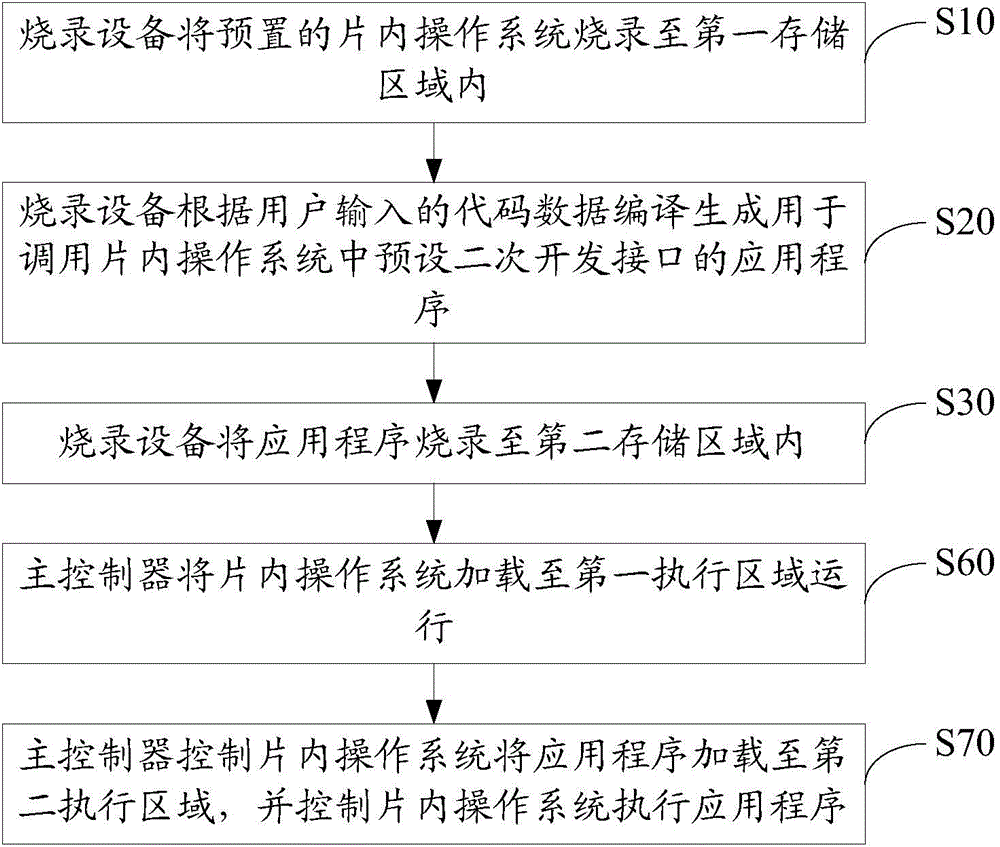
The invention discloses an application program burning method which is used for burning application programs into a mobile storage device. The mobile storage device comprises a flash memory, and the flash memory comprises a first storage area and a second storage area. The application program burning method for the mobile storage device comprises the following steps that a burning device can burn a preset on-chip operating system into the first storage area, the burning device can compile and generate application programs according to code data input by a user, the application programs are used for calling a preset secondary developing interface in the on-chip operating system, and the burning device can burn the application programs into the second storage area. The invention further discloses an application program burning system. The application program burning method and system solve the problem that the mobile storage device is inconvenient to use.
Owner:SLICONGO MICROELECTRONICS INC
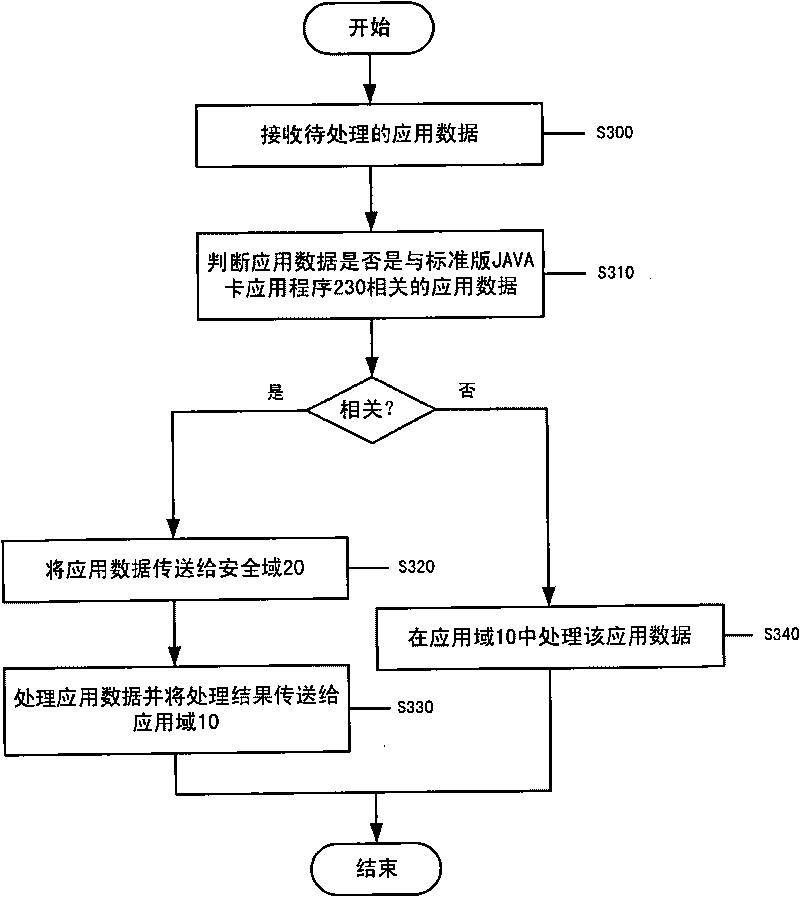
Smart card and application data processing method
InactiveCN101739246AGood application effectShorten the timeInterprogram communicationRecord carriers used with machinesOperational systemChip operating system
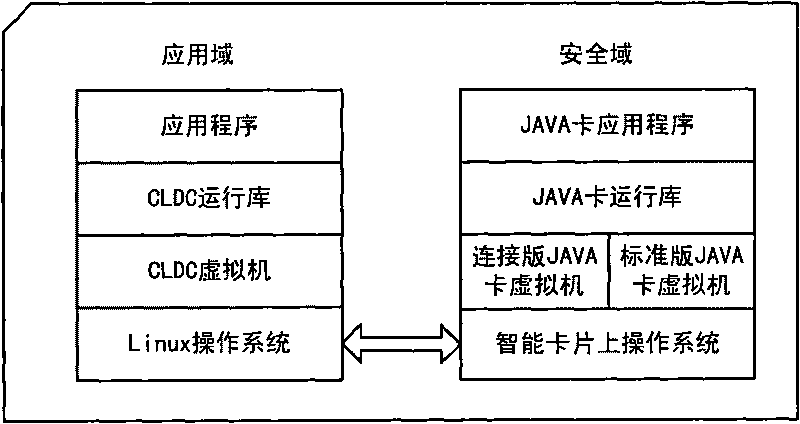
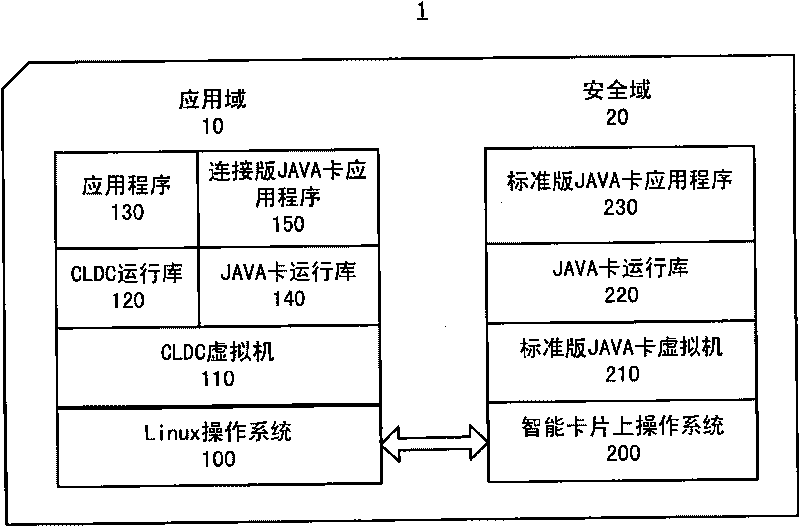
The invention relates to a smart card and an application data processing method. The smart card comprises a security domain and an application domain, wherein the security domain comprises an on-chip operating system, a standard-version JAVA card virtual machine operated on the on-chip operating system, a JAVA card runtime library and a standard-version JAVA card application program; and the application domain comprises an operating system, a virtual machine operated on the operating system, a JAVA card runtime library and a connection-version JAVA card application program. The smart card and the application data processing method can reduce the transmission waiting time and the communication delay of application data and improve the application performance of the smart card under the condition that the system safety of the smart card is not reduced and an extra cost is not increased.
Owner:爱思开电讯投资(中国)有限公司
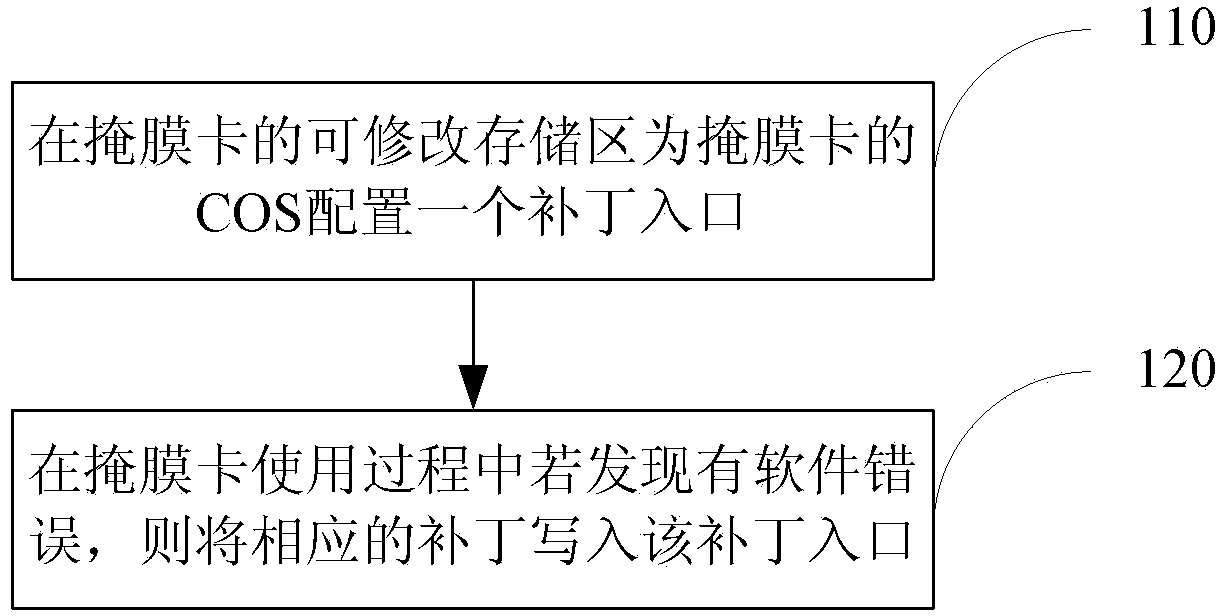
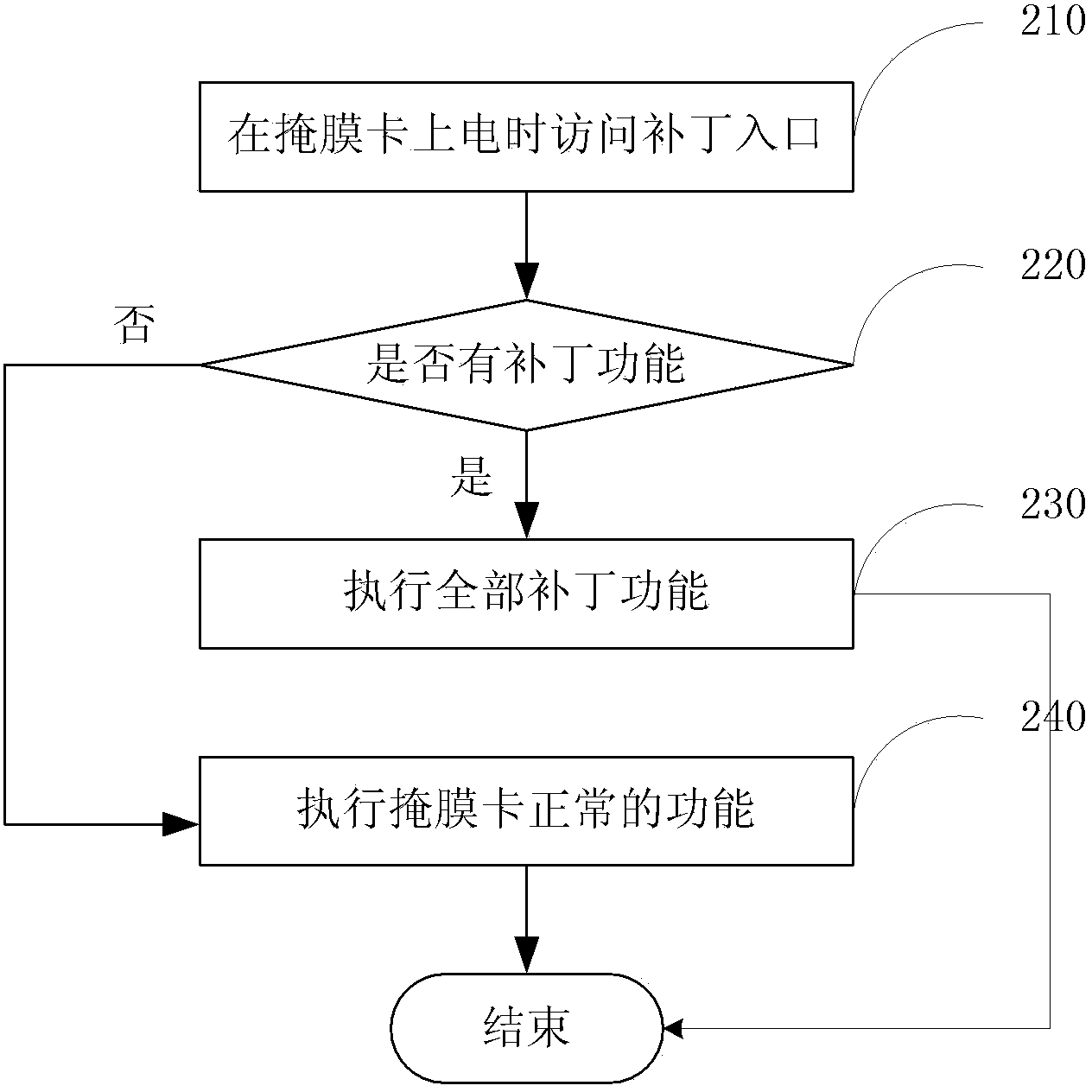
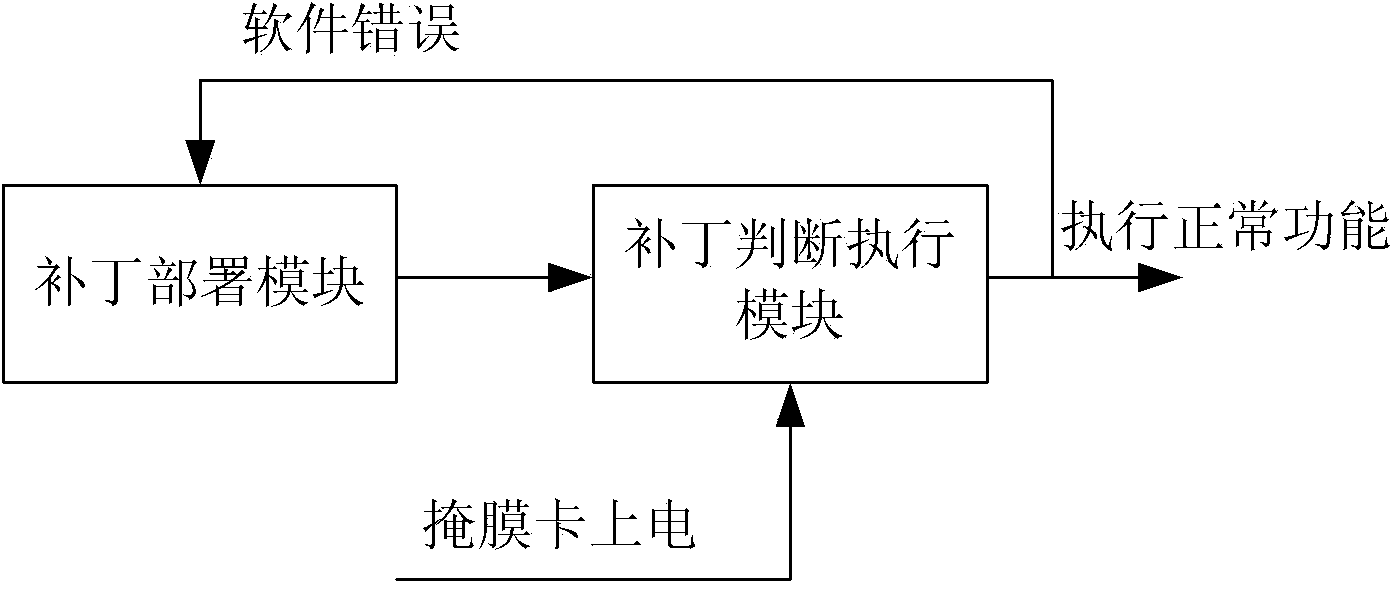
Method and device for achieving mask card patch mechanism
The invention discloses a method and device for achieving a mask card patch mechanism. The method includes the process of patch deployment, and the process of patch deployment includes the following steps that a patch entrance is configured for a chip operating system of a mask card in a revisable storage area of the mask card; in the use process of the mask card, if software errors are found out, a corresponding patch is written into the patch entrance. The method further includes the process of patch judgment and execution, and the process of patch judgment and execution includes the following steps that when the mask card is powered on, the patch entrance is subjected to access according to a fixed address, and if normal state information is returned, the normal functions of the mask card are executed. Compared with an existing mask card patch mechanism, the patch scheme is simple, convenient to use and efficient due to the fact that the patch entrance mode is adopted; due to the fact that the patch entrance is positioned in the revisable area of the mask card, the patch function can be freely expanded, and then adaptability is high.
Owner:北京大唐智能卡技术有限公司
Safety processing system and method for intelligent card (IC) card application
ActiveCN102437911ASolve the problem of security independenceKey distribution for secure communicationComputer security arrangementsChip operating systemSafe handling
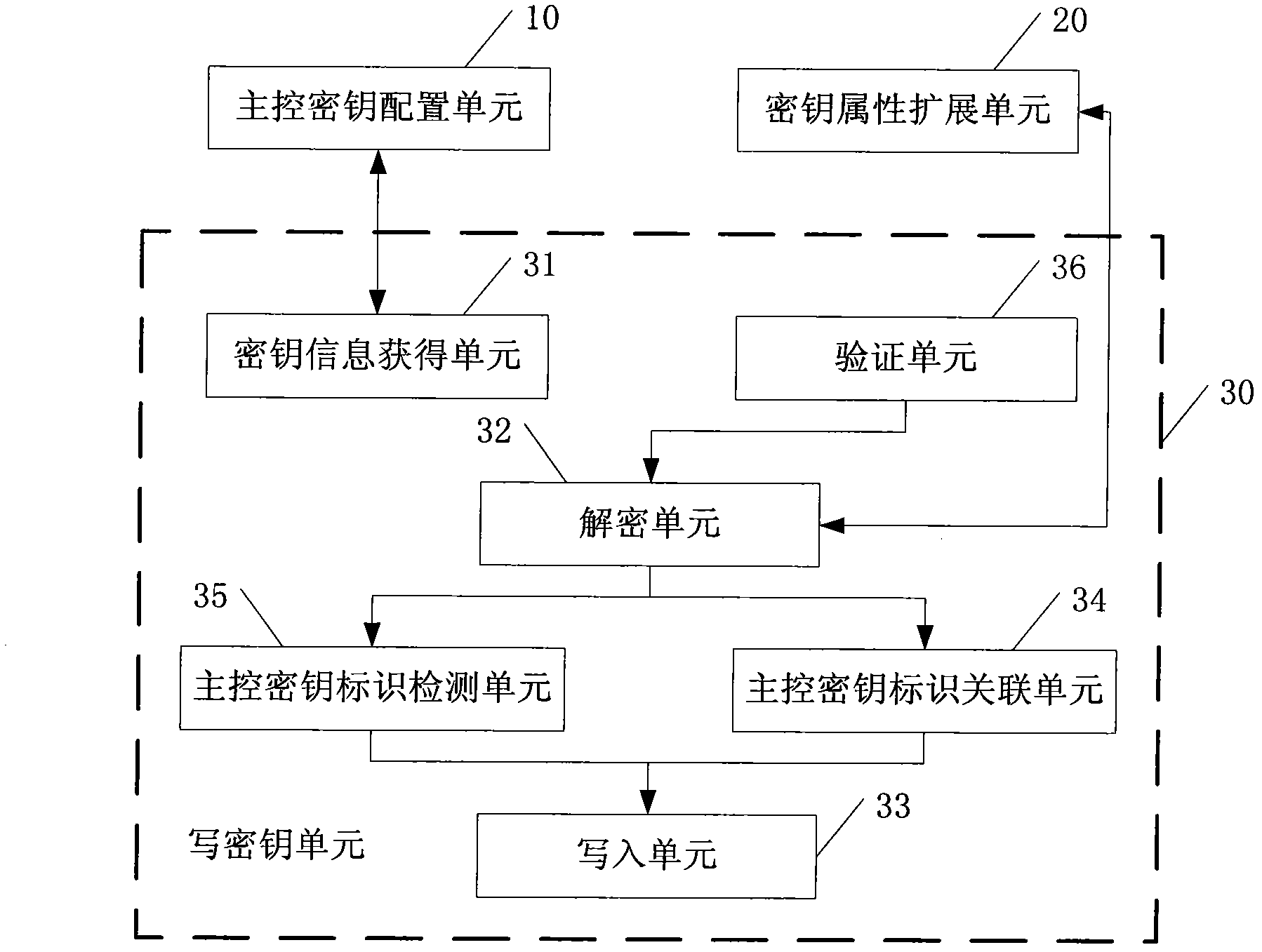
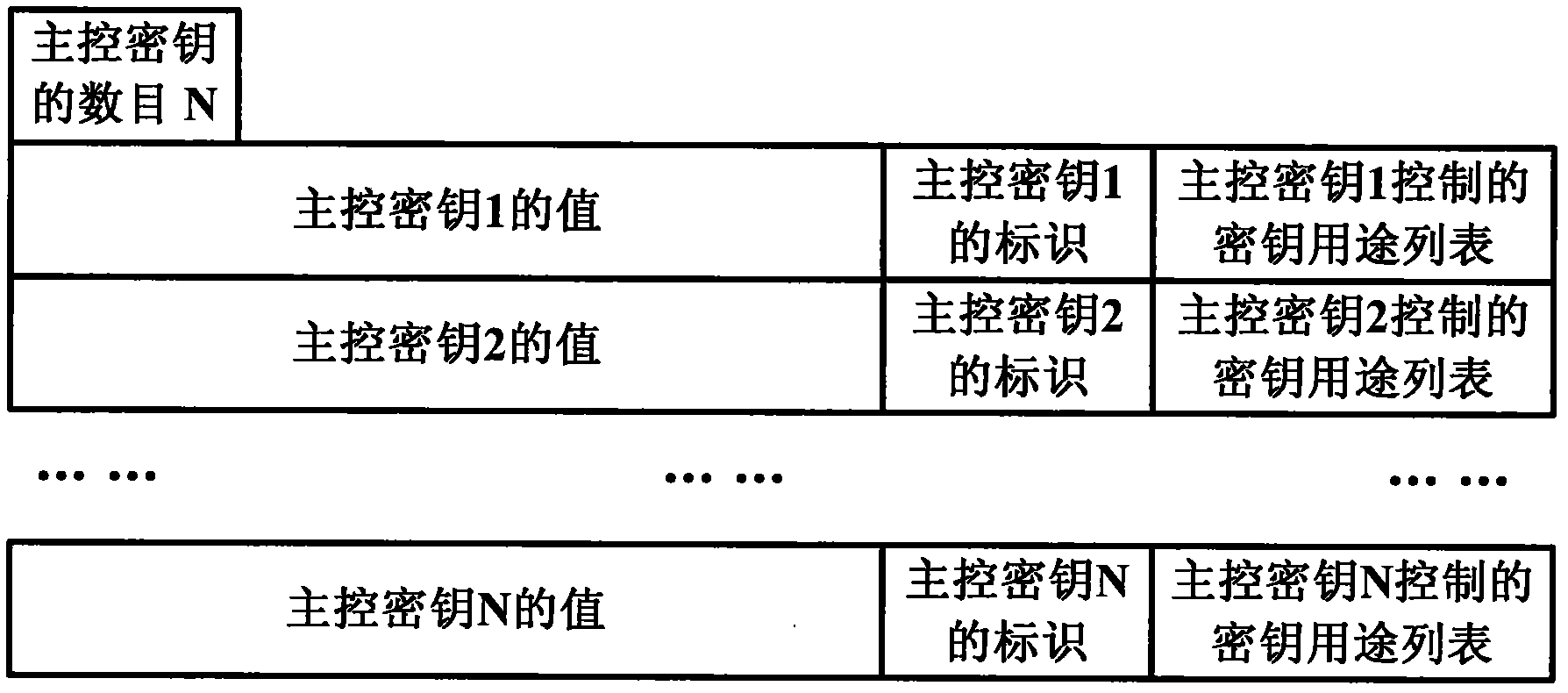
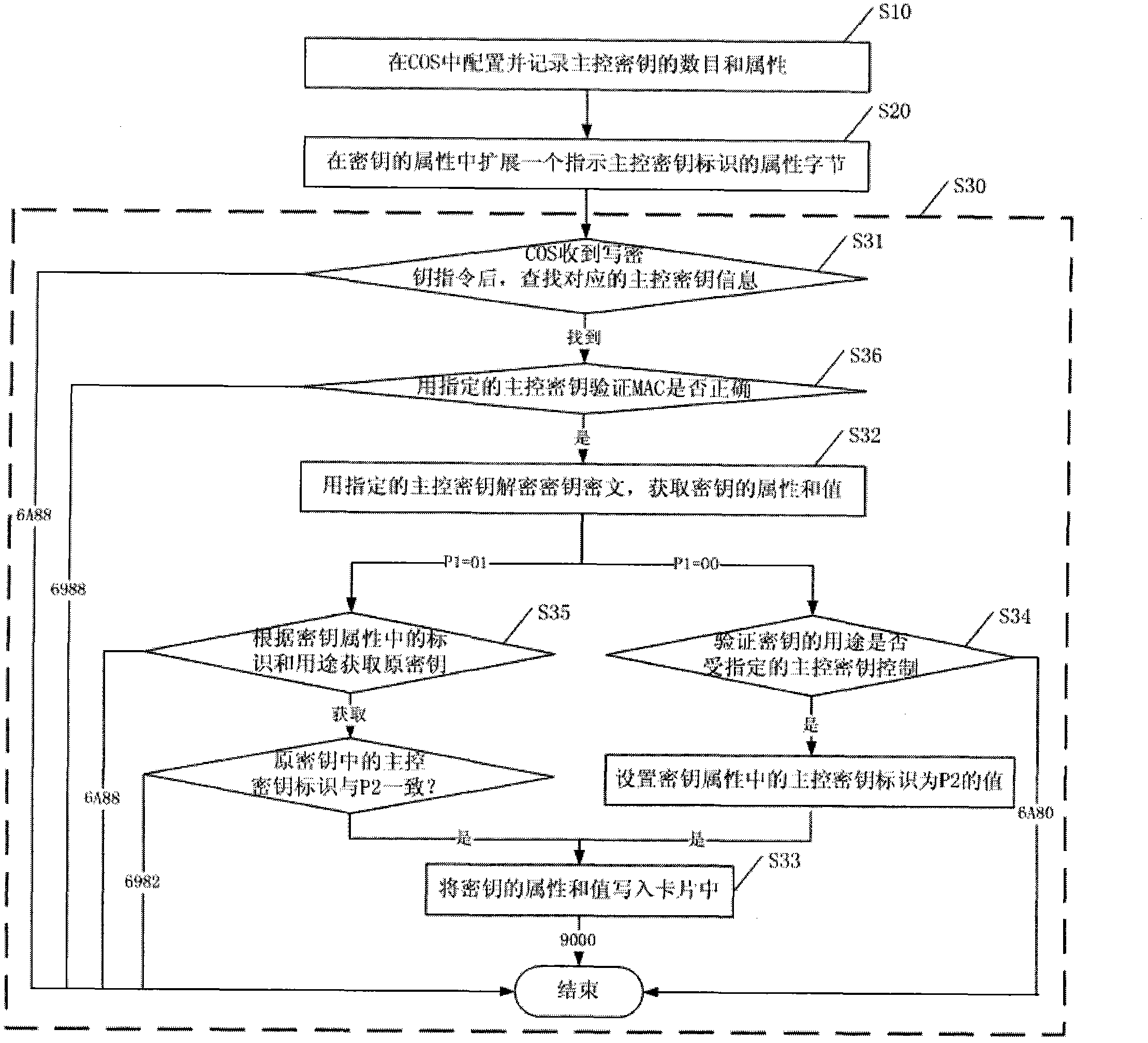
The invention discloses a safety processing system for an intelligent card (IC) card application, which comprises a main control key configuration unit, a key attribute expansion unit and a write key writing unit, wherein the main control key configuration unit is used for configuring and recording the quantity of main control keys and attribute of each main control key in an chip operation system, and the attribute of the main control key comprises a main control key value, a main control key identifier and a key purpose list controlled by the main control key; the key attribute expansion unit is used for expanding a main control key identifier byte in the attribute of each key, and the byte is used for indicating the main control key identifier of the key; and the write key writing unit is connected with the main control key configuration unit and the key attribute expansion unit and is used for utilizing a write key writing order withcarrying the main control key identifier and for writing the key into a card. The invention also discloses a corresponding safety processing method of the intelligent IC card application. Due to the adoption of the system and the method, multiple main control keys can be realized under one application, and the safety independence problem of each party when a card is issued by multiple parties.
Owner:WUHAN TIANYU INFORMATION IND
Testing device for operating system of security chip
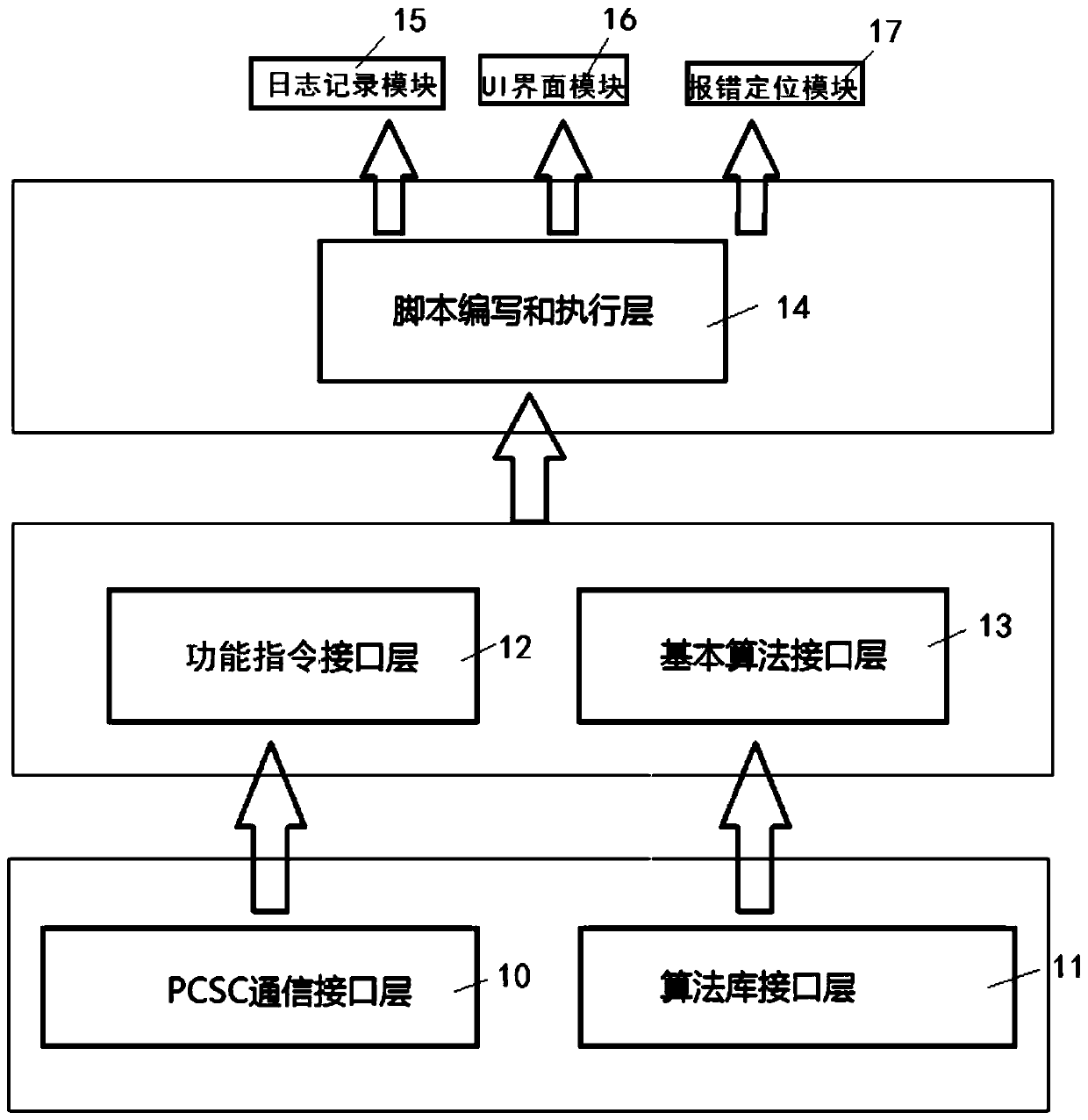
PendingCN109918338AEfficient execution speedTargetedSoftware engineeringSoftware testing/debuggingCommunication interfacePython language
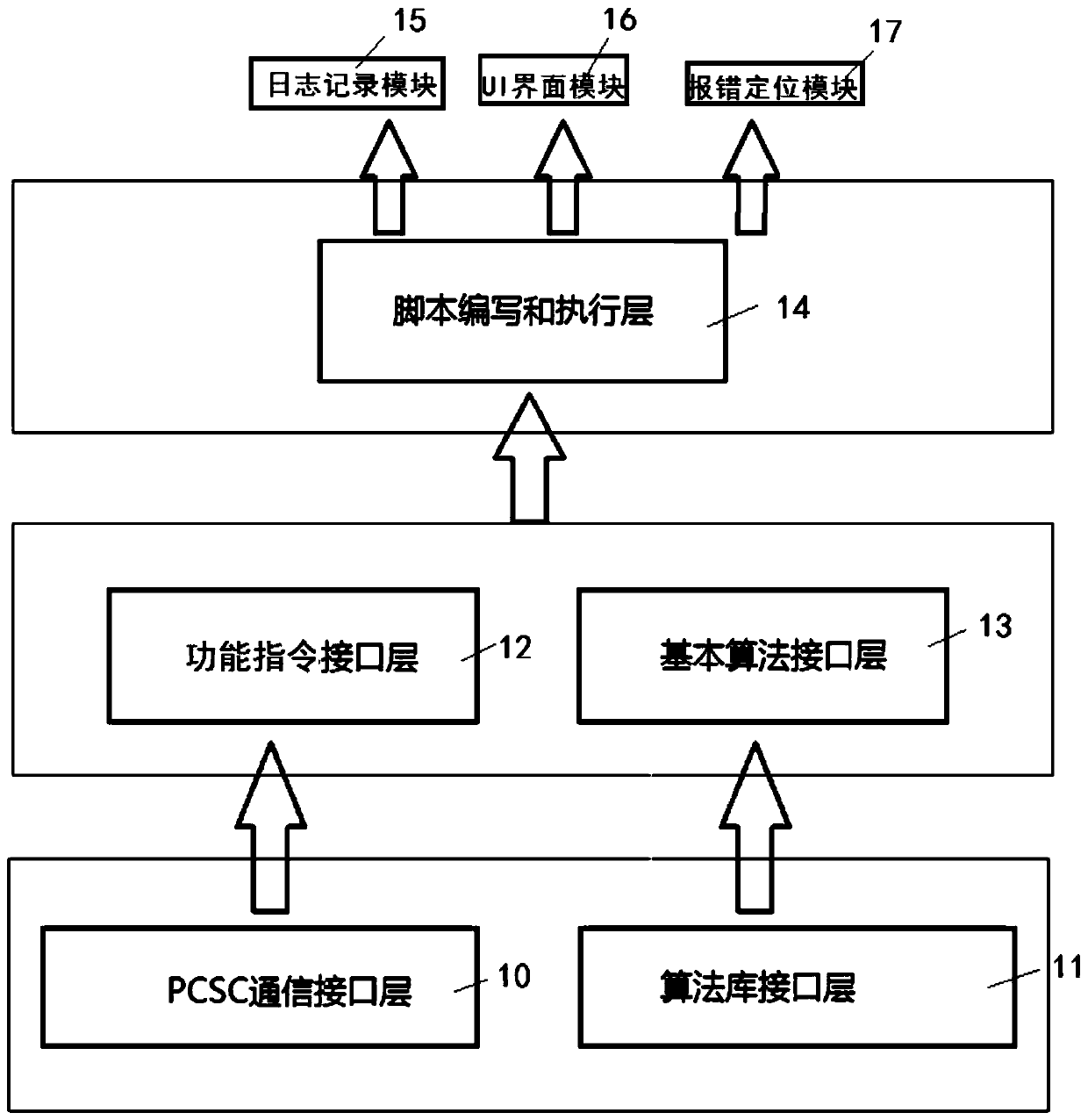
The invention discloses a testing device for a security chip operating system, which is constructed through Python language and comprises a PCSC communication interface layer, an algorithm library interface layer, a function instruction interface layer, a basic algorithm interface layer and a script writing and executing layer. And communication with the to-be-tested security chip is realized through the PCSC communication interface layer. And the algorithm library interface layer is used for packaging interfaces of various security algorithms applied by the to-be-tested security chip. And thefunction instruction interface layer is used for packaging a function instruction in an operating system of the to-be-tested security chip. And the basic algorithm interface layer is used for performing secondary combination and packaging on the interface of the algorithm library interface layer and newly adding an operation function. The script writing and executing layer is used for storing, executing and modifying test scripts, and the script writing and executing layer achieves testing by combining and calling the PCSC communication interface layer, the algorithm library interface layer,the function instruction interface layer and the basic algorithm interface layer. The testing device for the operating system of the security chip can effectively improve the writing and debugging speed of the testing script.
Owner:BEIJING SMARTCHIP MICROELECTRONICS TECH COMPANY +2
Automatic production equipment control system and control method for realizing chip filling
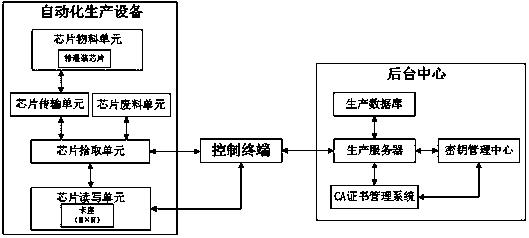
ActiveCN108388152AImprove efficiencyImprove accuracyKey distribution for secure communicationUser identity/authority verificationOperational systemChip operating system
The invention provides an automatic production equipment control system and control method for realizing chip filling. The system comprises automatic production equipment, a control terminal and a background center. Batch and continuous writing of a chip operating system and chip personalized information can be realized through the automatic production equipment, the control terminal and the background center, and chip filling efficiency and accuracy are improved; and through a CA certificate management system and a key management center, on one hand, chip keys and chip digital certificates can be ensured; and on the other hand, since the chip keys are rich in type, and comprise a chip master key, a chip symmetric key, a chip password key, a chip signing key pair and a chip encryption keypair, and chip digital certificates comprise a dual-certificate system of a chip signature digital certificate and a chip encryption digital certificate, safety of the chip when communicating with theoutside world in the application process can be ensured effectively.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
Fingerprint KEY device
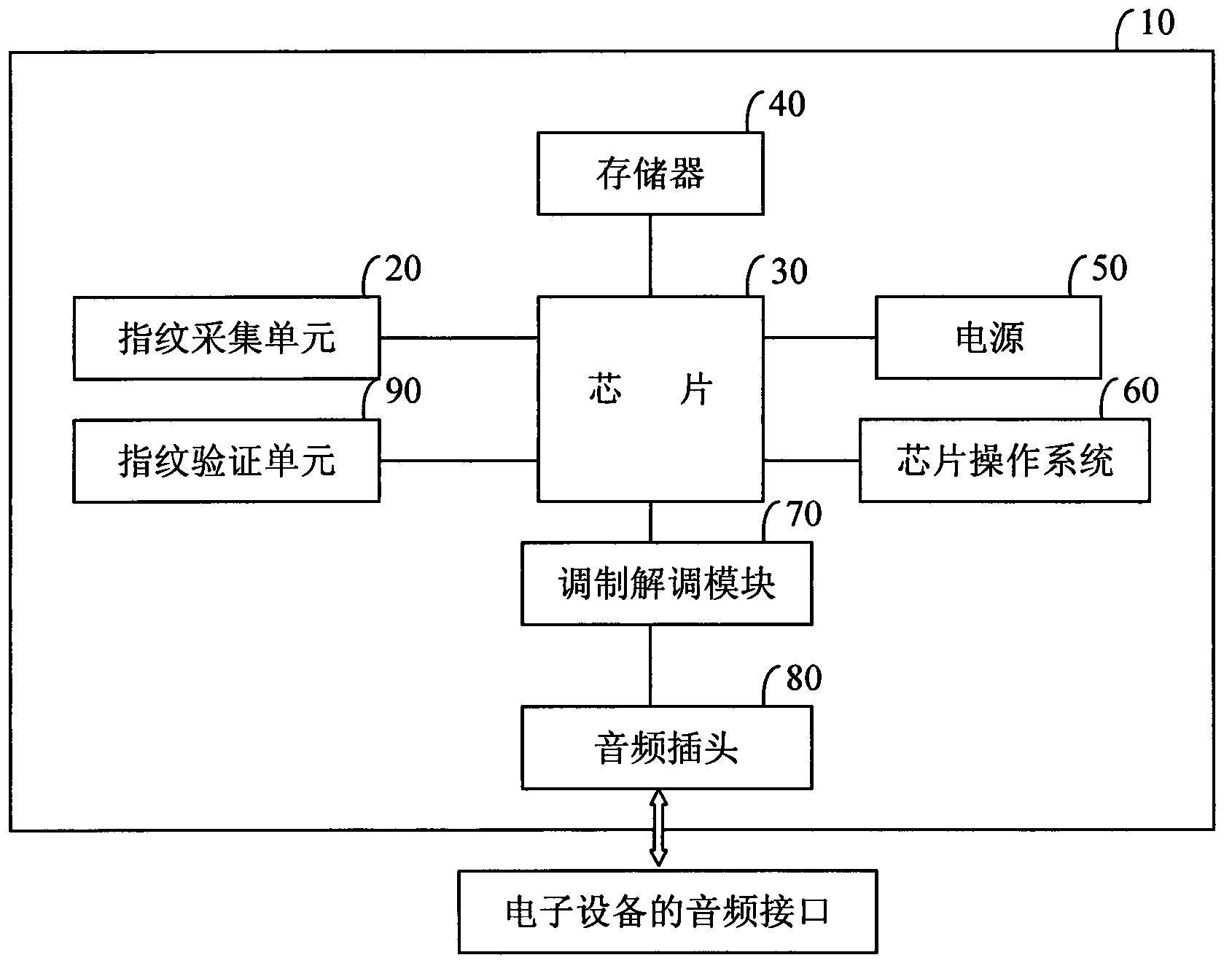
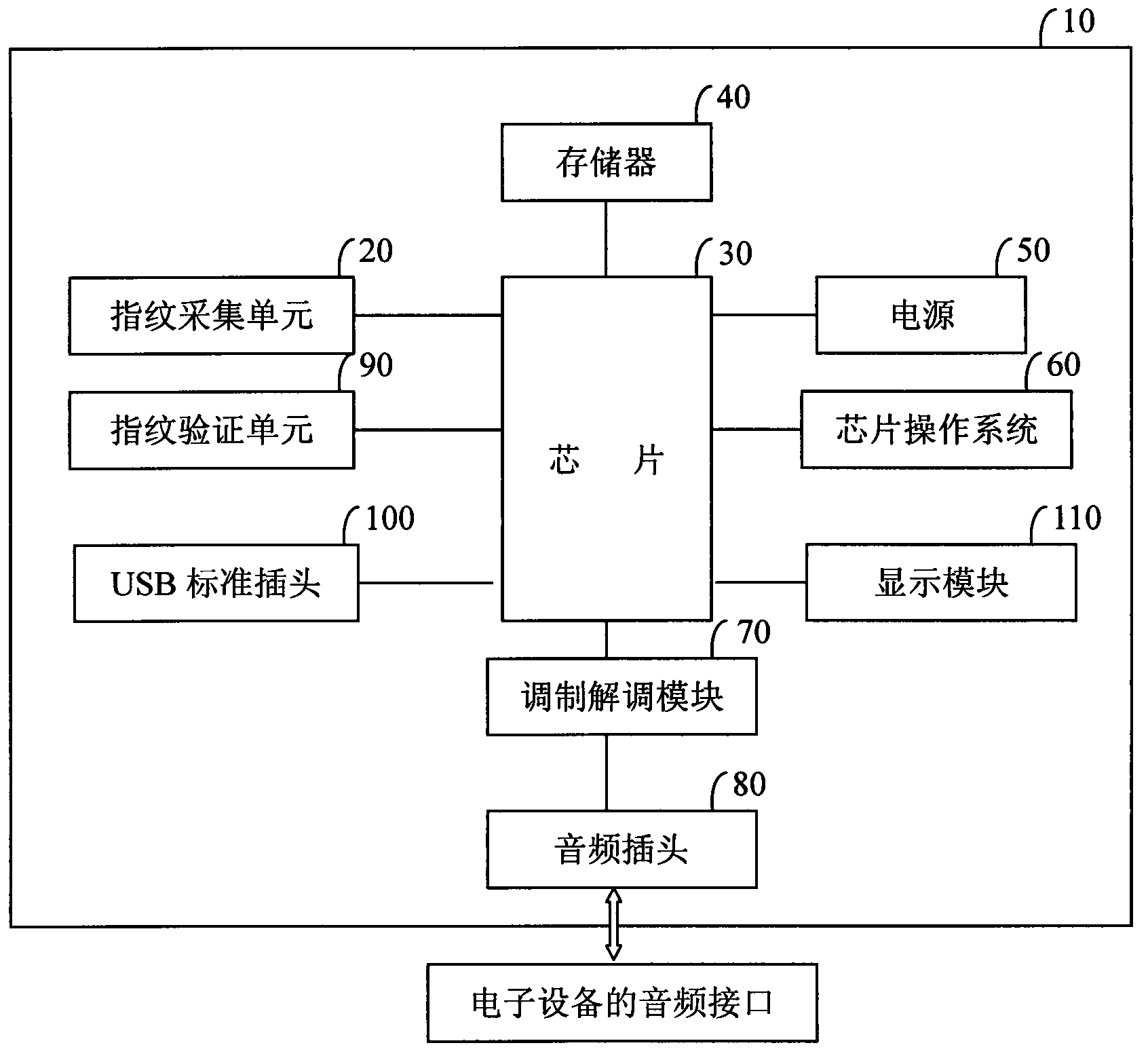
InactiveCN103186736AImprove securityImprove adaptabilityDigital data authenticationDigital dataOperational system
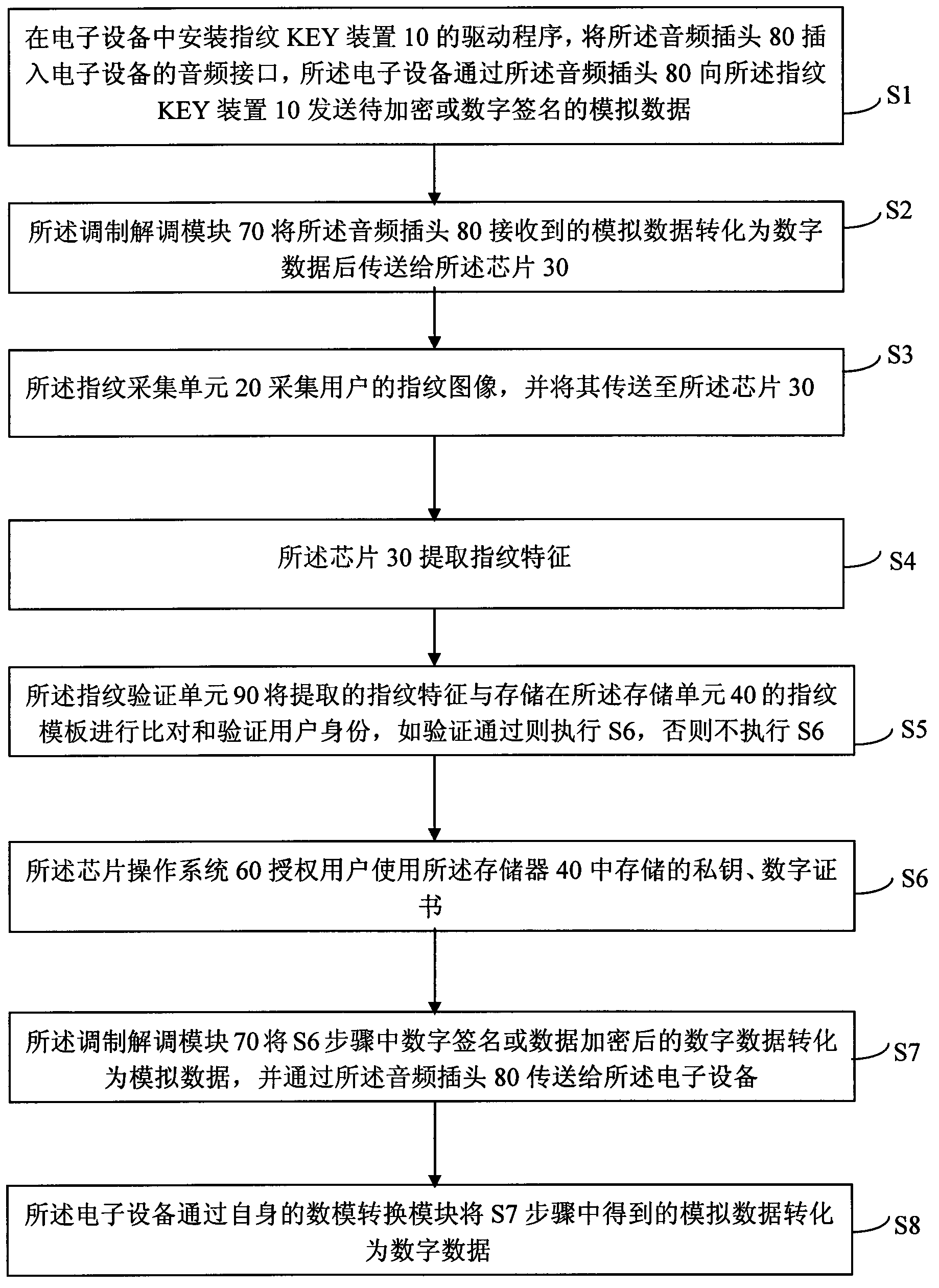
The invention discloses a fingerprint KEY device, comprising a chip, a memory, a housing, a power supply, a fingerprint collecting unit, a fingerprint verification unit, a modulation and demodulation module, and an audio plug, wherein the fingerprint collecting unit, the fingerprint verification unit and the modulation and demodulation module are connected with the chip; the audio plug is connected with the modulation and demodulation module; the chip has a chip operation system; the memory is used for storing a private key, a digital certificate, and a fingerprint template; the audio plug includes an MIC (microwave integrated circuit) pole and a sound track pole; the modulation and demodulation module is used for converting an analogue data received from the audio plug into a digital data and then transmitting to the chip, and converting the digital data to be conveyed by the fingerprint KEY device into the analogue data and then transmitting to the audio plug; and the chip can authorize to use the private key and the digital certificate in the memory after the fingerprint verification unit verifies. The fingerprint KEY device replaces PIN code verification with fingerprint verification, and can achieve information interaction of the fingerprint KEY device and electric equipment with an audio interface through the modulation and demodulation module and the audio plug. Therefore, the security and the reliability of identity authentication of a user are improved; and meanwhile, the adaptability and the convenience are also enhanced.
Owner:SHENZHEN ARATEK BIOMETRICS TECH CO LTD
Operating system in double-interface smart card and its implementing method
InactiveCN101370079AEasy to handleImprove processing efficiencyTelevision system detailsAnalogue secracy/subscription systemsOperational systemChip operating system
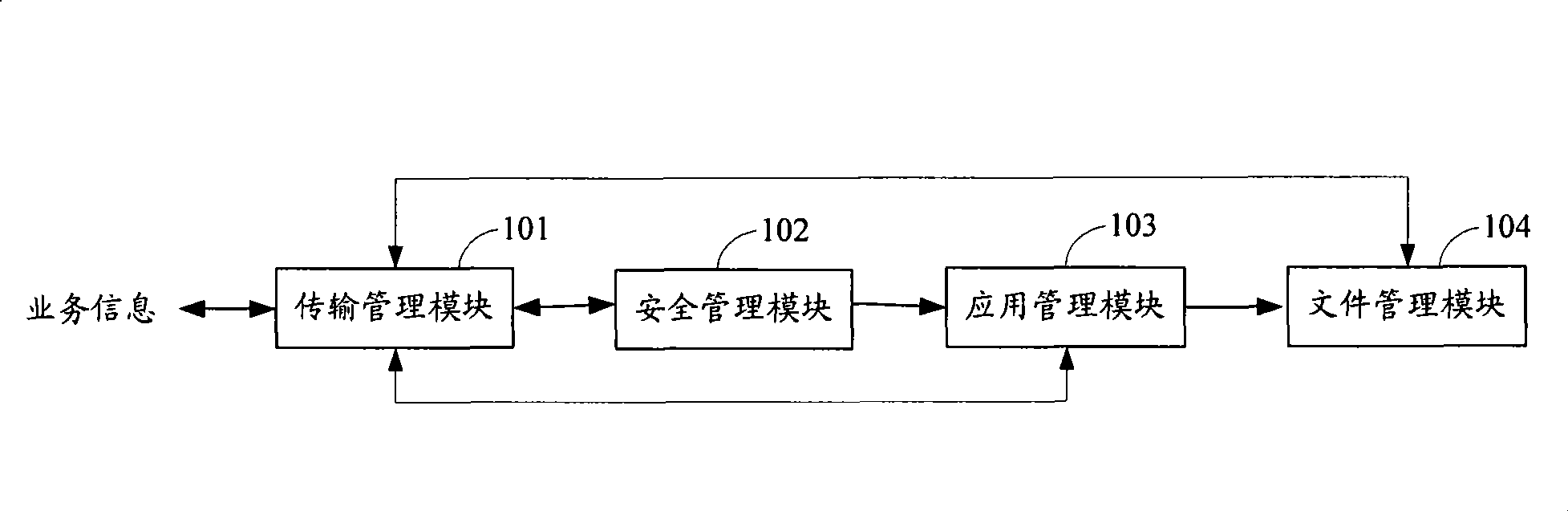
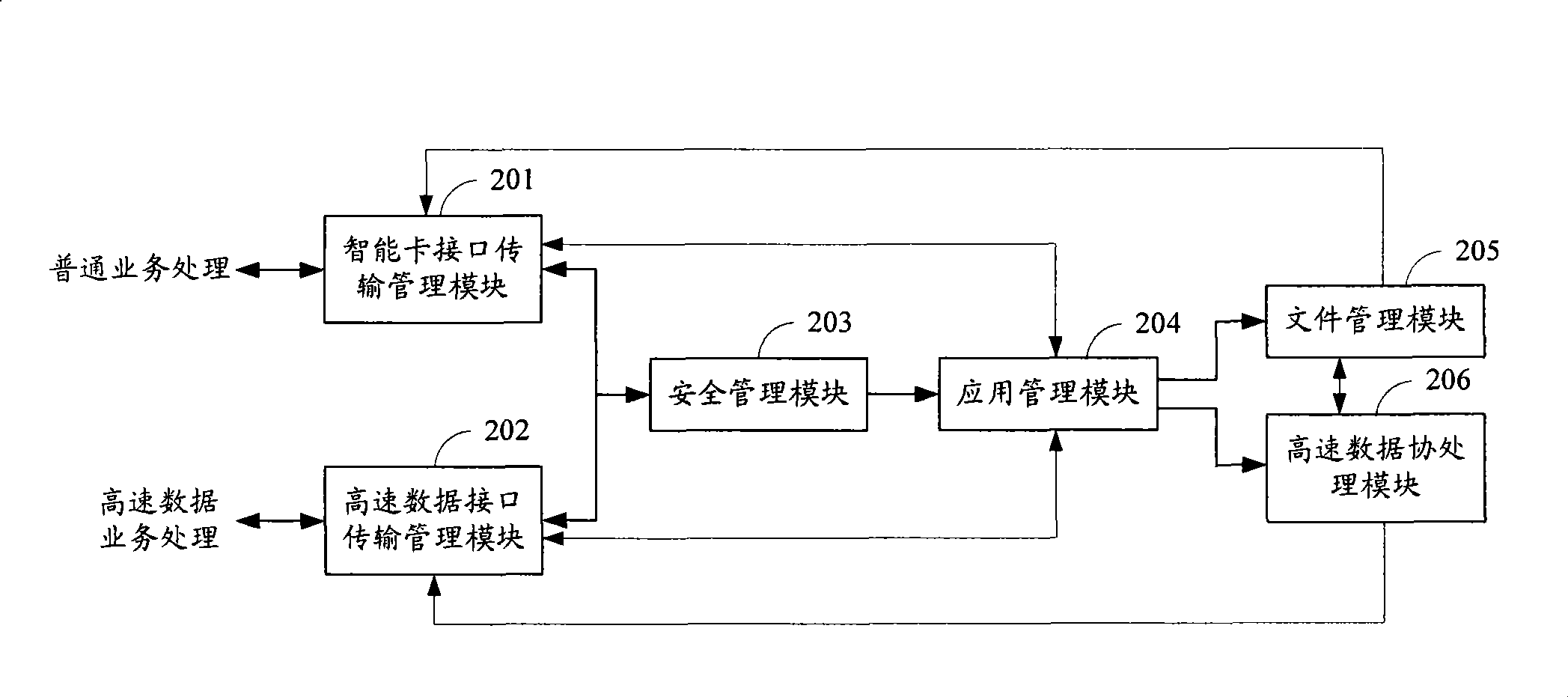
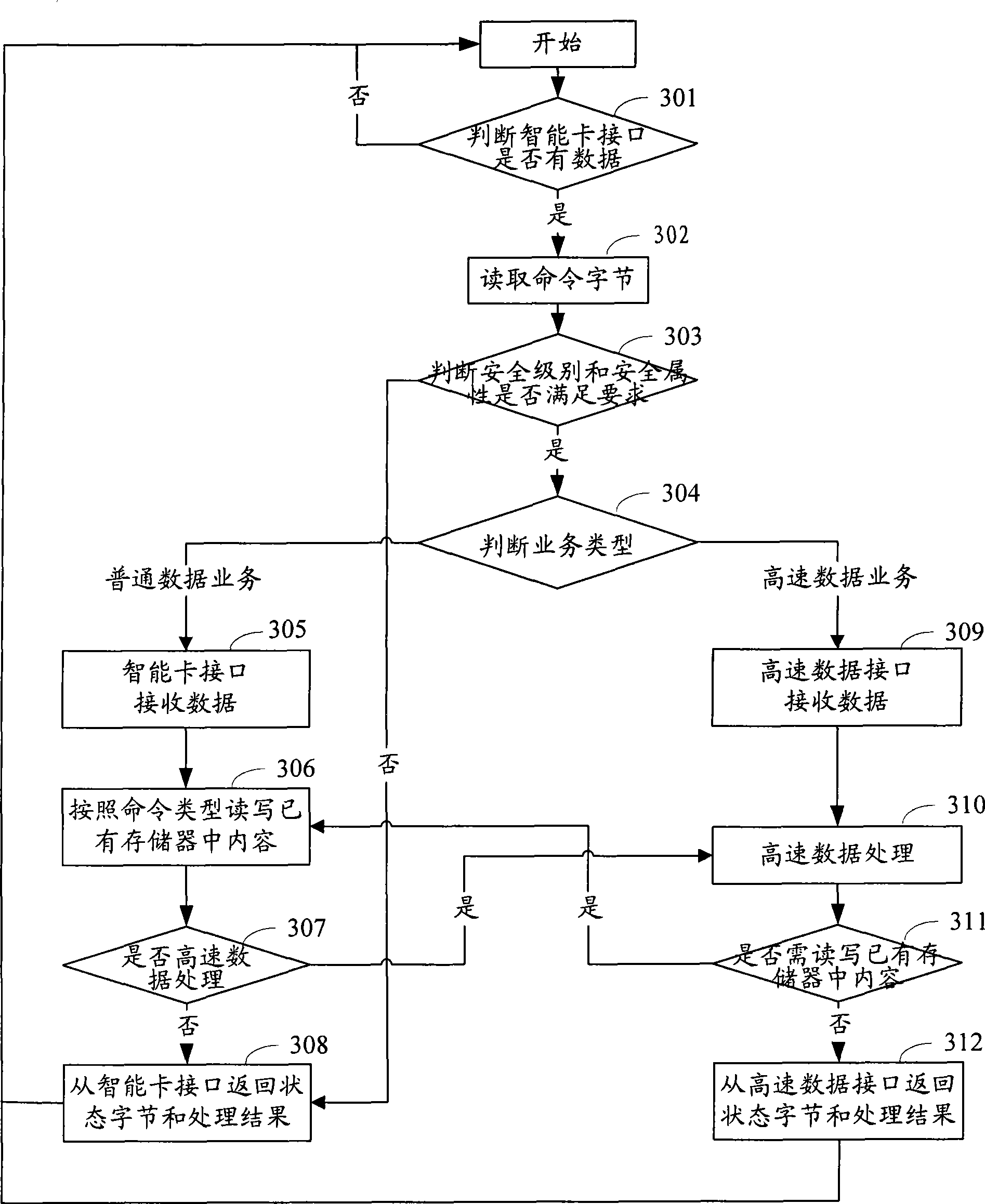
The invention discloses an on-chip operating system of a dual-interface smart card and a realization method thereof, the system comprises: a smart card interface transmission management module, a high speed interface transmission management module, a security management module, an application management module, a file management module and a high speed data co-processing module; the inventive method judges type of services via performing a security mechanism checkup for a received order head, if the order head represents the type of services is general data service, a general data service processing is carried out; if the order head represents the type of services is high speed data service, a high speed data service processing is carried out. The inventive on-chip operating system and the realization method thereof can be applied to the dual-interface smart card having a high speed data interface, which shakes off limit of conditions in conventional smart card interface such that transmission for high speed data is possible.
Owner:POTEVIO INFORMATION TECH
Initialization control method and device of smart card
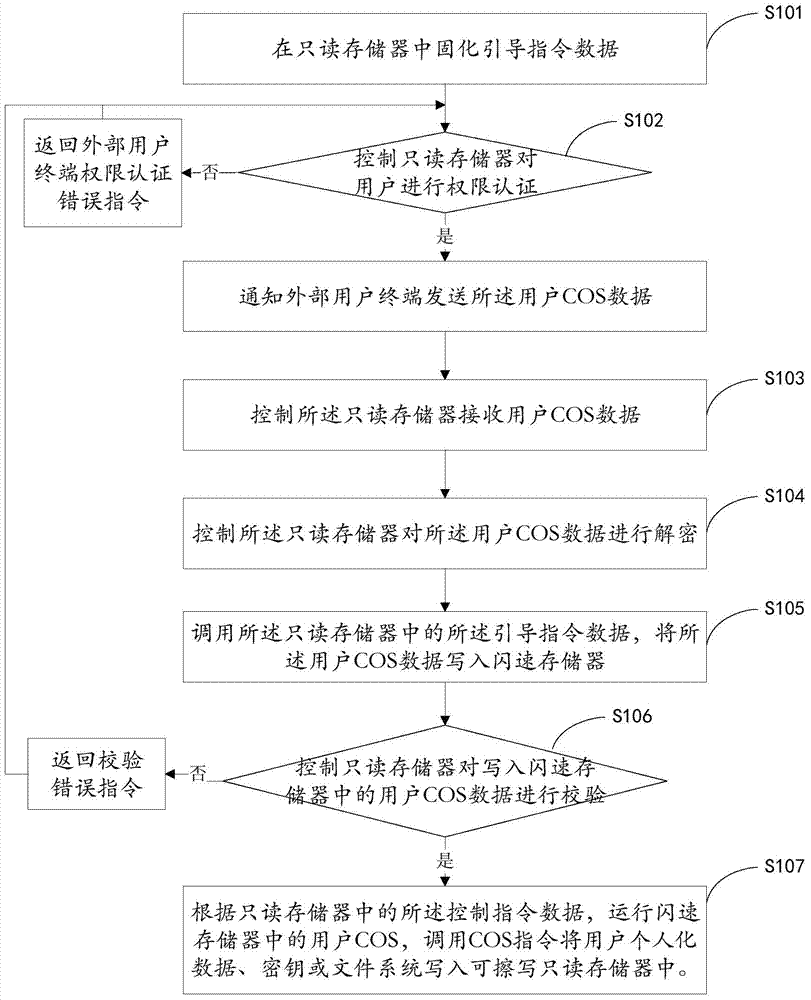
InactiveCN104778053ARealize online upgradeRealize online programmingProgram loading/initiatingChip operating systemRead-only memory
The invention belongs to the communication technology, and provides an initialization control method and device of a smart card. The method comprises the following steps: curing bootstrapping data in a read-only memory; controlling the read-only memory to receive user COS (Chip Operating System) data; calling the bootstrapping data in the read-only memory; and writing the user COS data into a flash memory. The bootstrapping data is cured in the read-only memory to guide the user to write the user COS data into the flash memory, the flash memory is adopted to serve as a carrier of the user COS data, an encryption algorithm or a dynamic program; on the basis of the characteristic that the flash memory can be repeatedly written, an algorithm is written by self according to requirements, the encryption algorithm or codes do not need to be handed to a chip manufacturer, safety is increased, program revision becomes possible in a development process of the smart card so as to greatly shorten a development period, save development time and reduce development cost expenses, and the on-line upgrading and the on-line programming of the smart card are realized.
Owner:NATIONZ TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com