Embedded safety ship of real-time clock and method for correcting real-time clock thereof
A security chip, real-time clock technology, applied in the field of computer security, can solve the problems of counter overflow, inability to distinguish the time difference between two digital signatures, etc., to achieve the effect of complete functions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] Embodiments of the present invention will be described in detail below with reference to the accompanying drawings, and unnecessary details and functions for the present invention will be omitted during the description to prevent confusion in the understanding of the present invention.
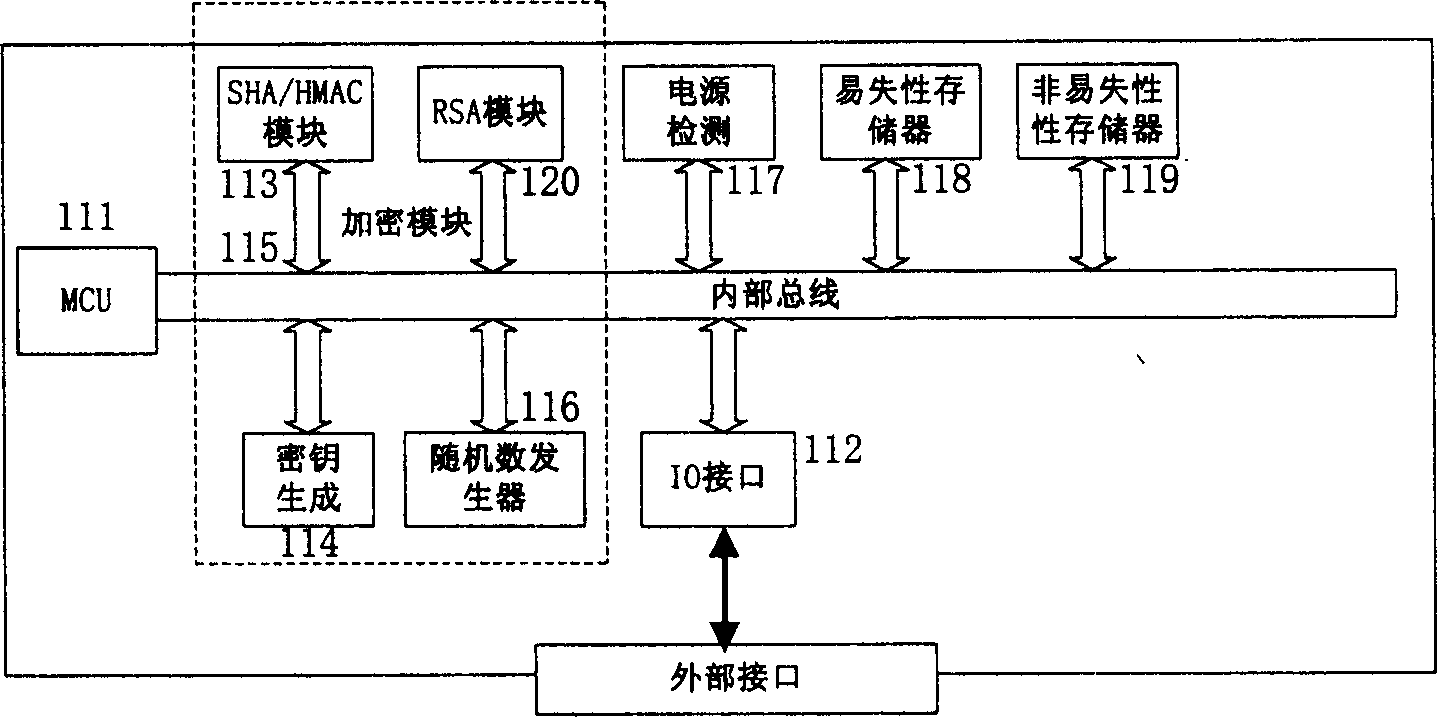
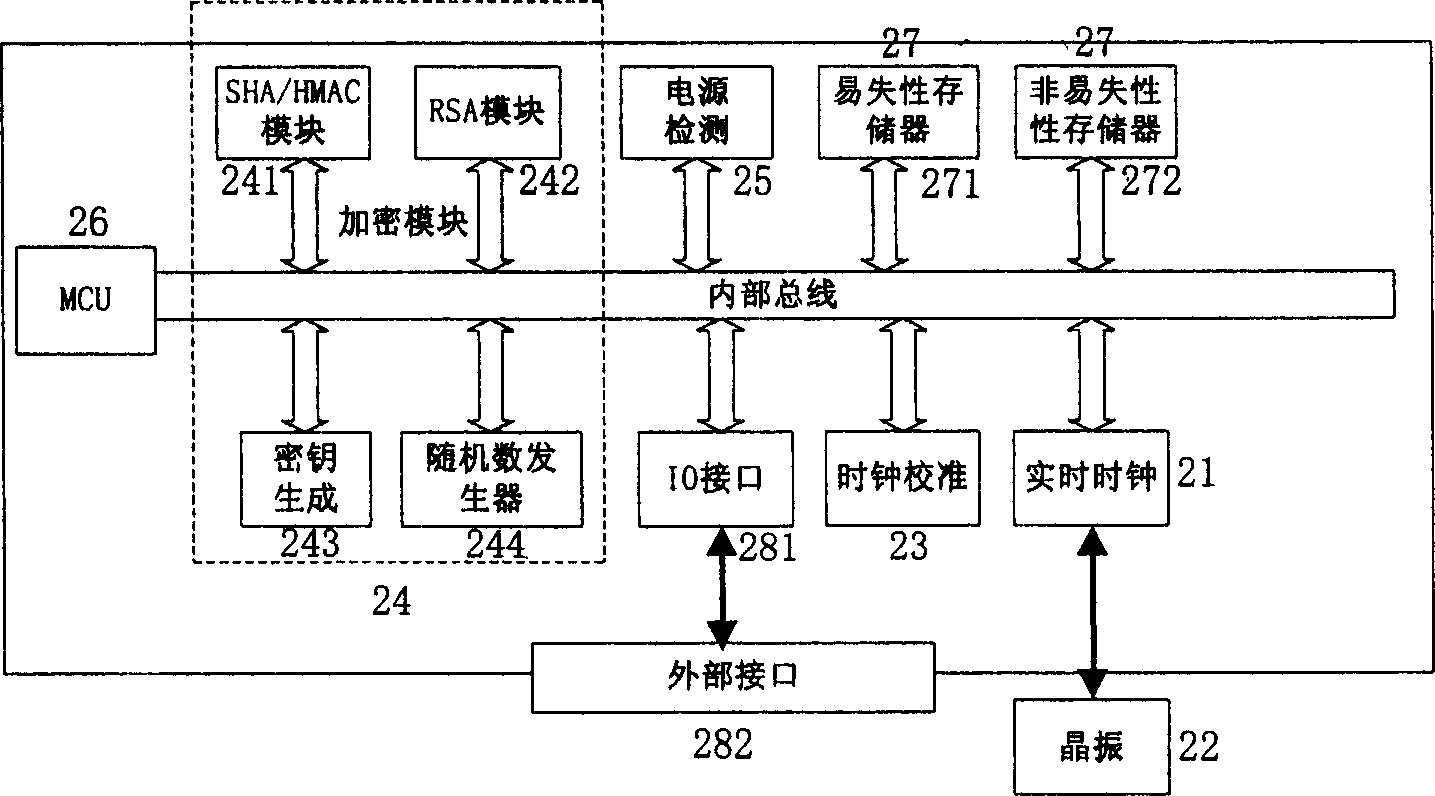
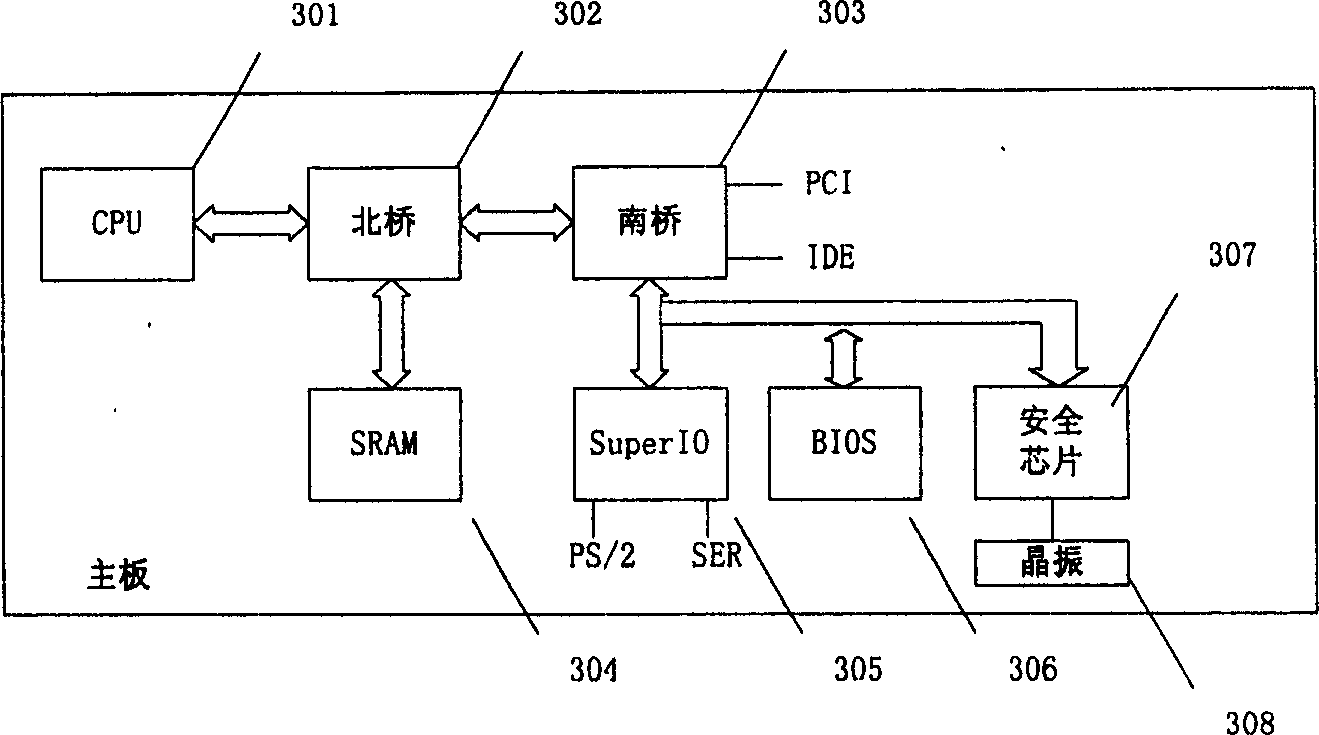
[0023] figure 2 An embodiment of the security chip with embedded real-time clock according to the present invention is shown. Such as figure 2 Shown, according to the security chip of embedded real-time clock of the present invention comprises real-time clock module 21, external frequency generator 22, clock calibration module 23, encryption module 24, power supply detection module 25; Central processing unit (CPU) core 26 (ie , MCU), storage unit 27, and external interface module 28. The real time clock module 21 provides an accurate current time value for the digital signature. The external frequency generator 22 provides the reference clock frequency for the real-time clock modu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com