Safety processing system and method for intelligent card (IC) card application
A security processing and card application technology, applied in electronic digital data processing, computer security devices, and key distribution, can solve the problems that smart IC cards cannot meet the security needs of partners, and achieve the effect of solving the problem of security independence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
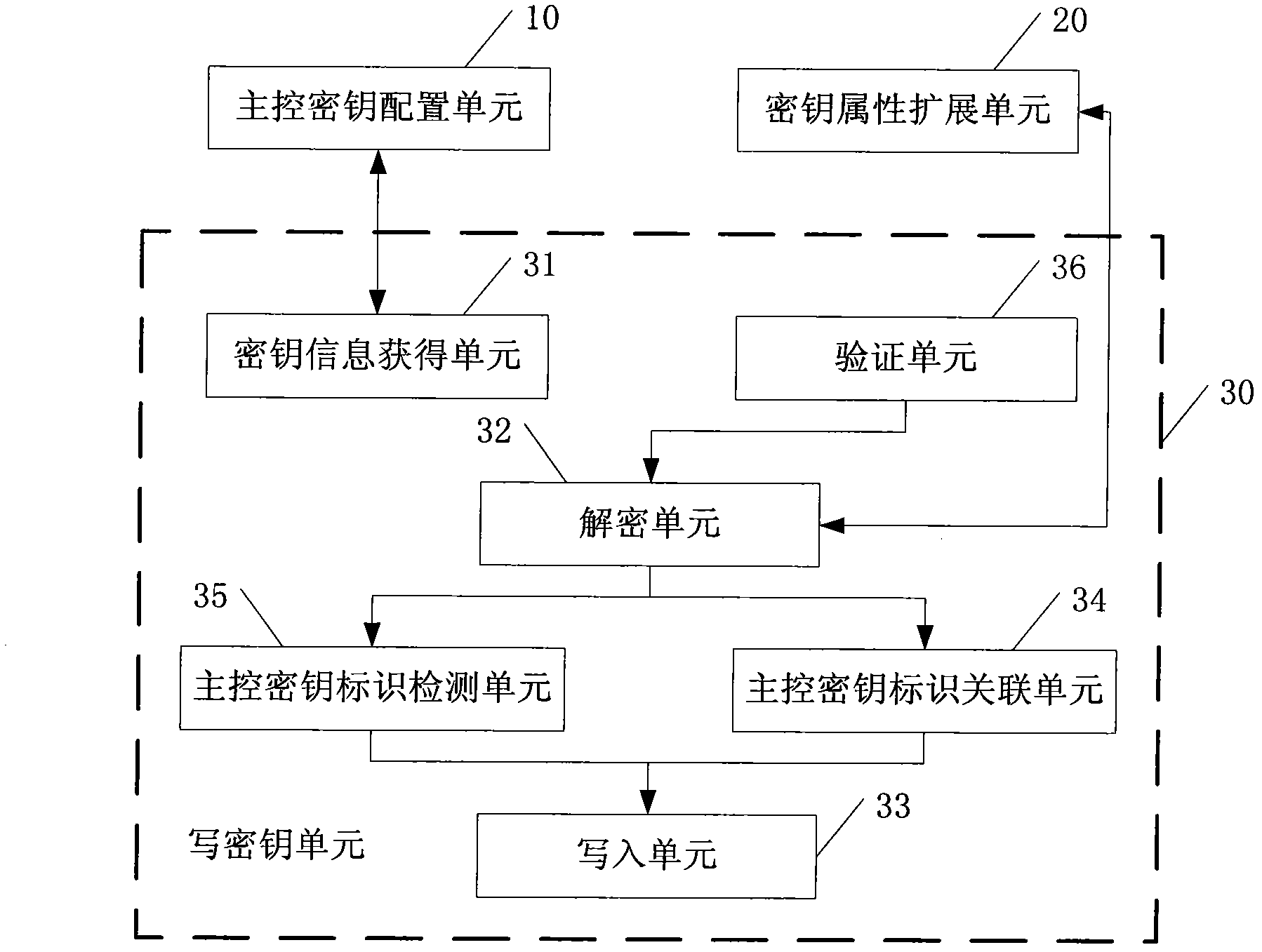
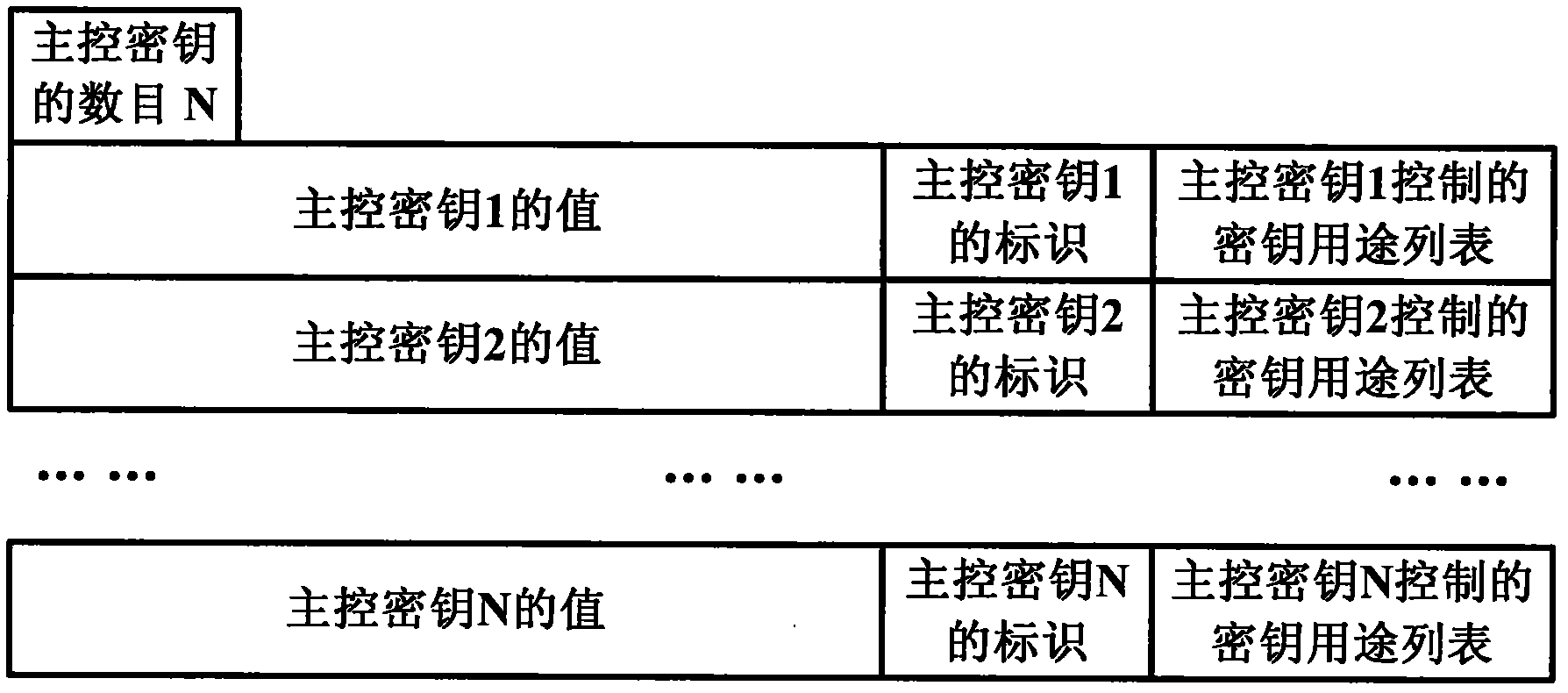
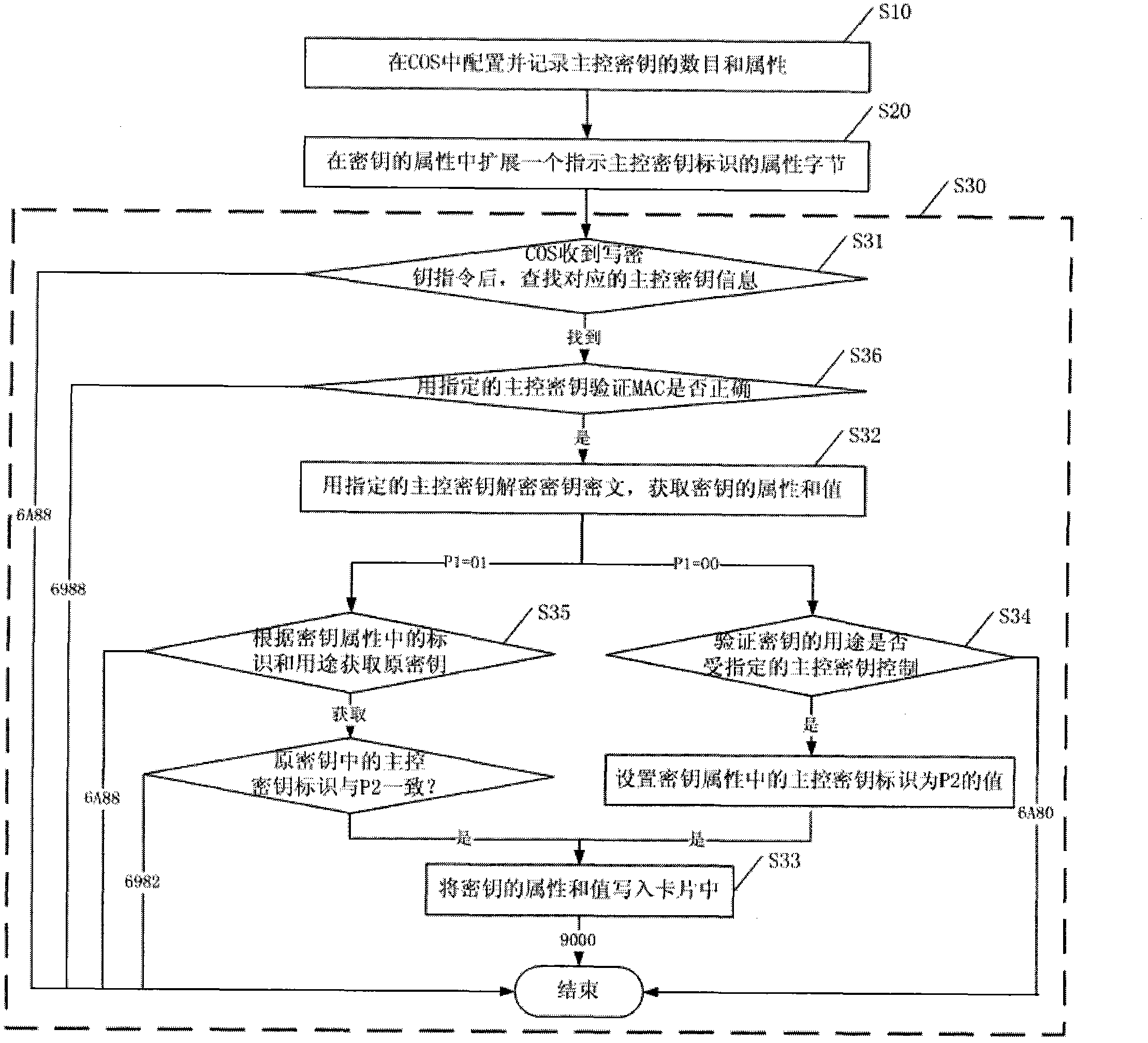
[0042] The key in the smart IC card is divided into three types: master control key, maintenance key and work key. The master key is used to control the installation and modification of other types of keys; the maintenance key is used to control the update of the data files associated with it; the working key is used to control the execution of application instructions. Wherein, the control refers to related security processing such as encryption / decryption.
[0043] The keys in the smart IC card all have attribute bytes, generally including version, identification, type and purpose. The chip operating system (Chip Operating System, COS) in the smart IC card looks up the key according to the combination of version, identification and type bytes, and checks that the key must be used according to its purpose.
[0044] The data files in the smart IC card all have attribute bytes, generally including access rights and associated maintenance key identifiers. The COS in the smart ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com