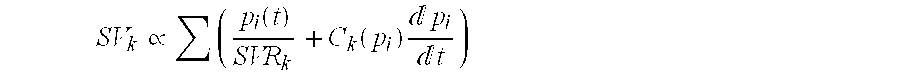Patents
Literature
131 results about "Working memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Working memory is a cognitive system with a limited capacity that is responsible for temporarily holding information available for processing. Working memory is important for reasoning and the guidance of decision-making and behavior. Working memory is often used synonymously with short-term memory, but some theorists consider the two forms of memory distinct, assuming that working memory allows for the manipulation of stored information, whereas short-term memory only refers to the short-term storage of information. Working memory is a theoretical concept central to cognitive psychology, neuropsychology, and neuroscience.
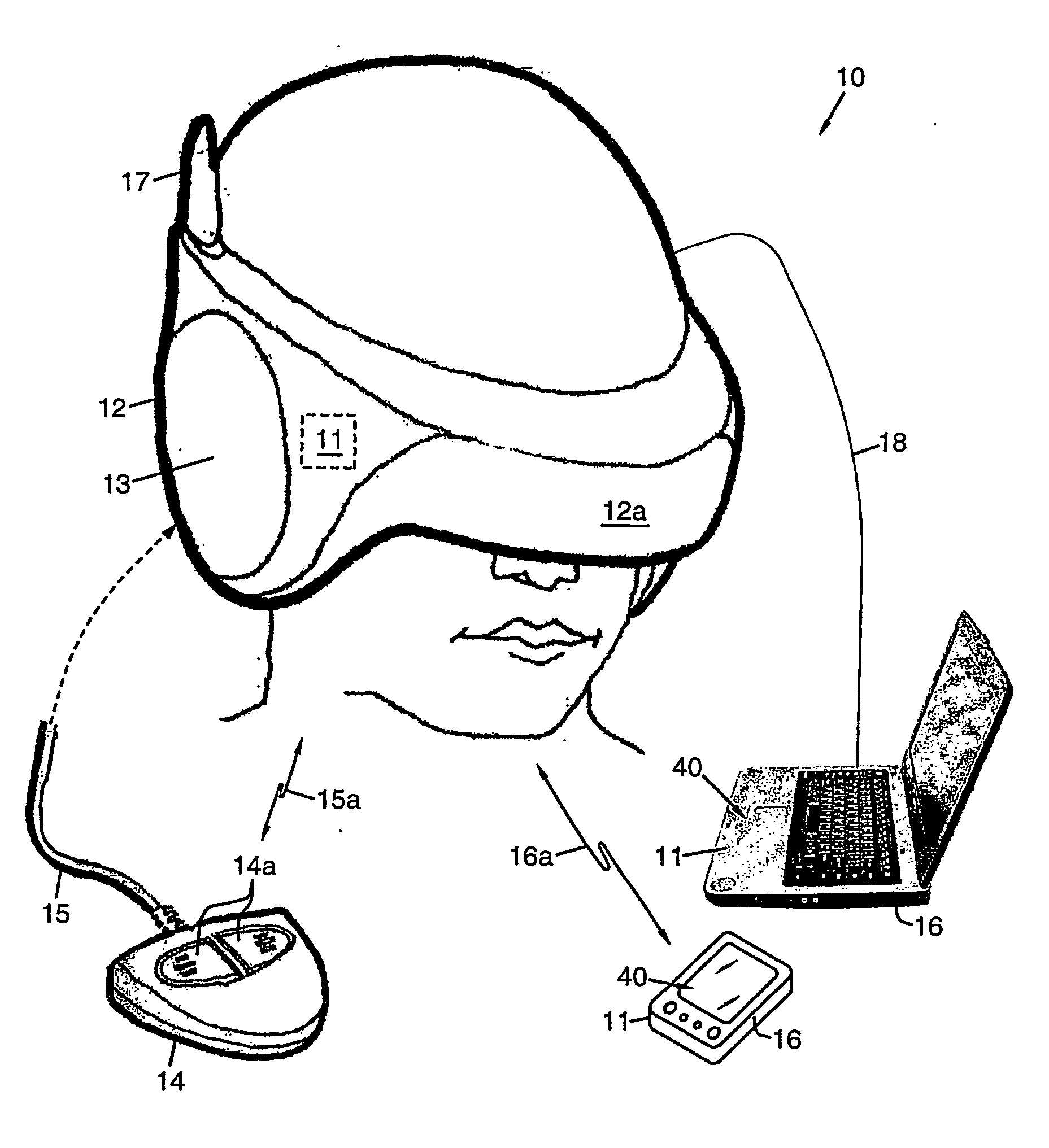
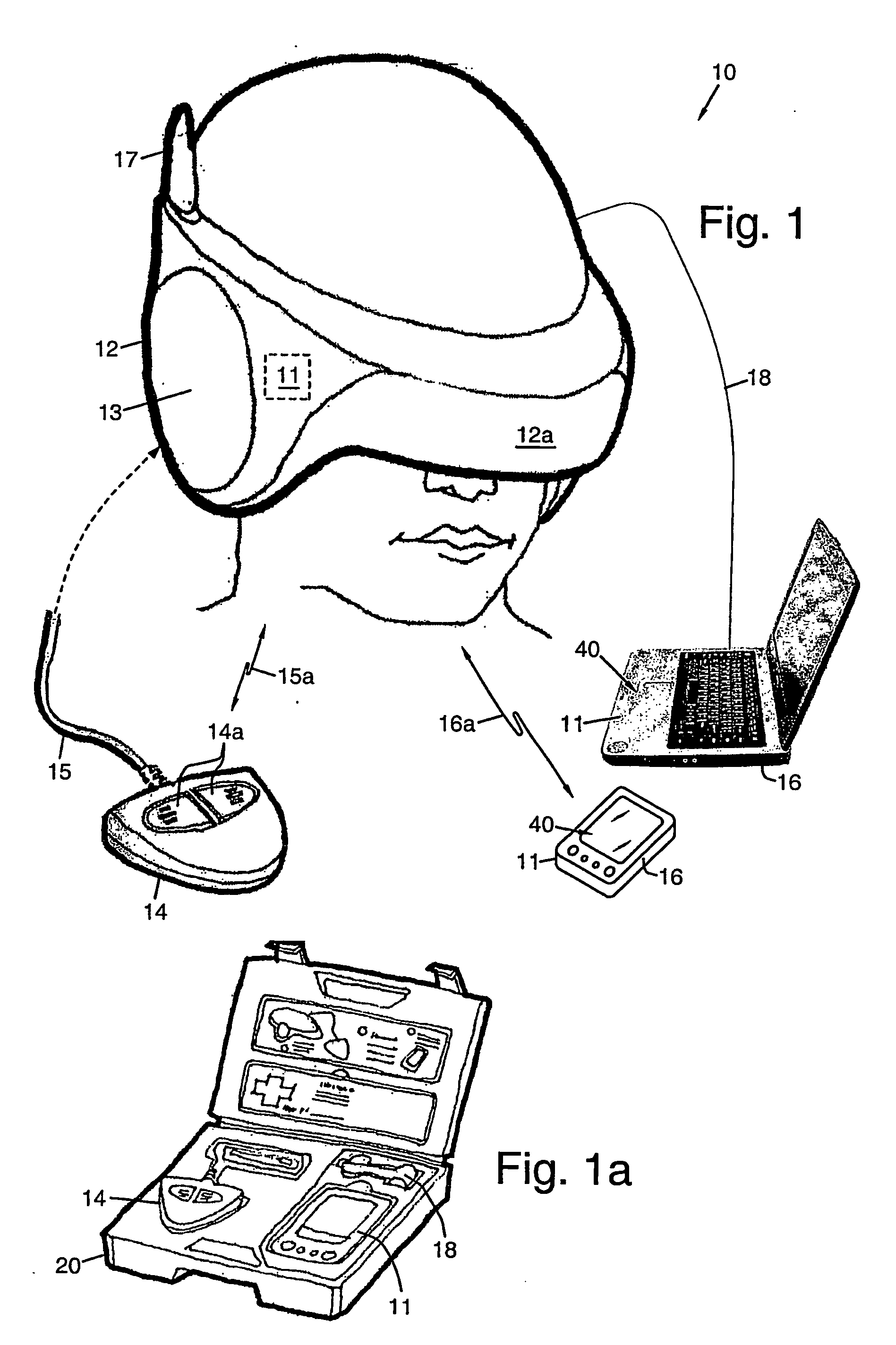
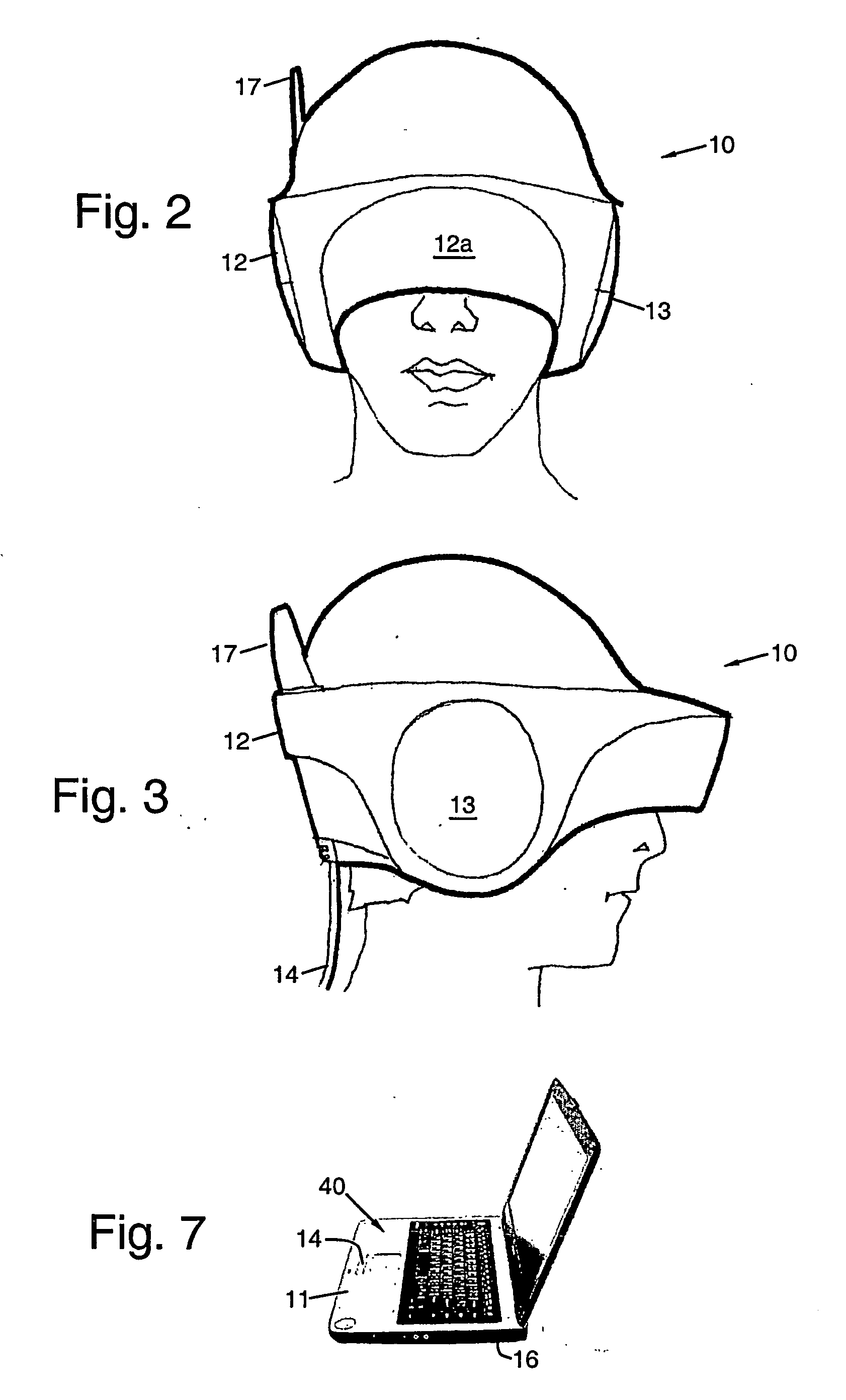
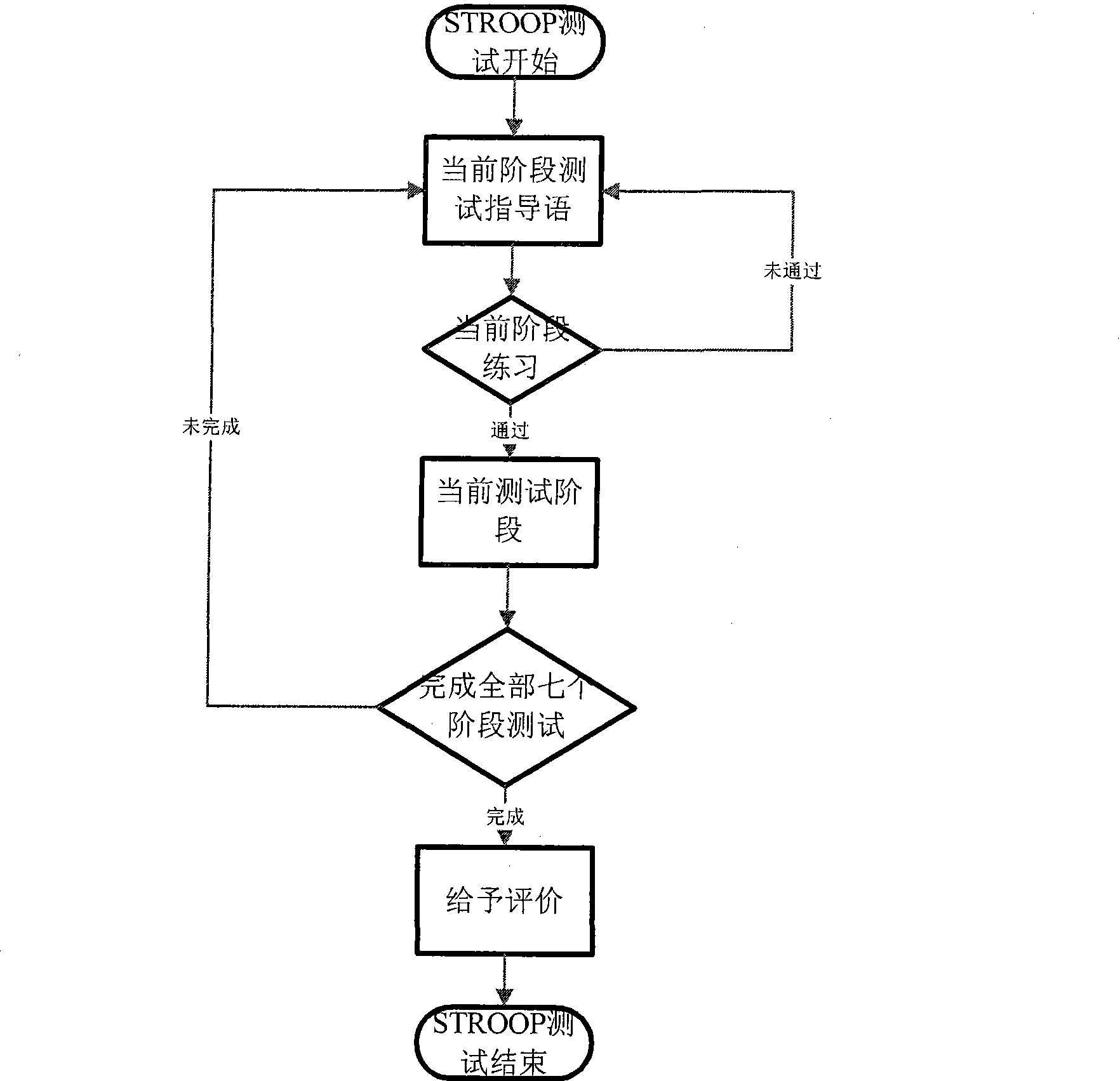
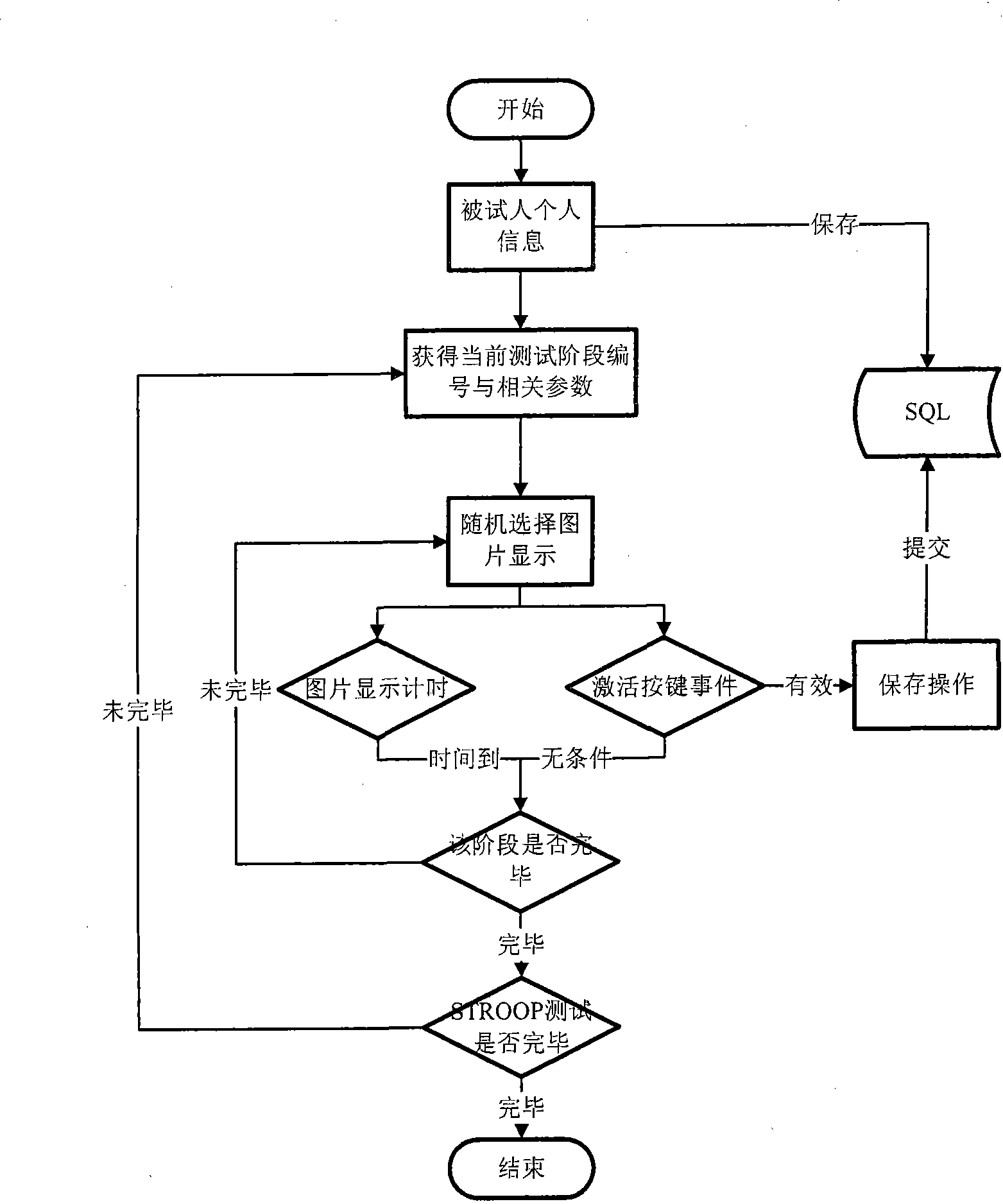
Cognitive and Linguistic Assessment Using Eye Tracking
ActiveUS20100092929A1Leveling precisionHealth-index calculationReadingDividing attentionVisual perception
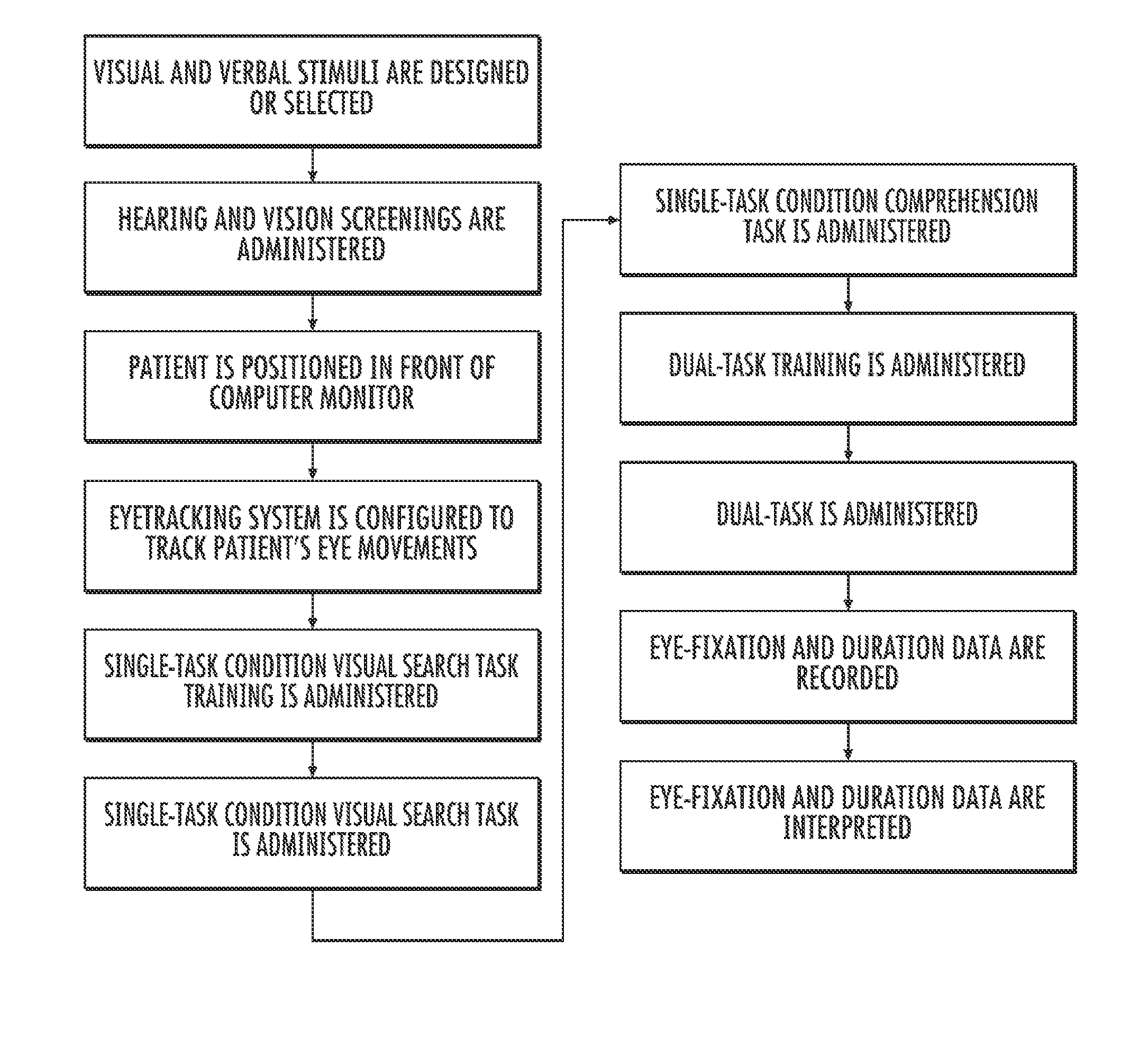
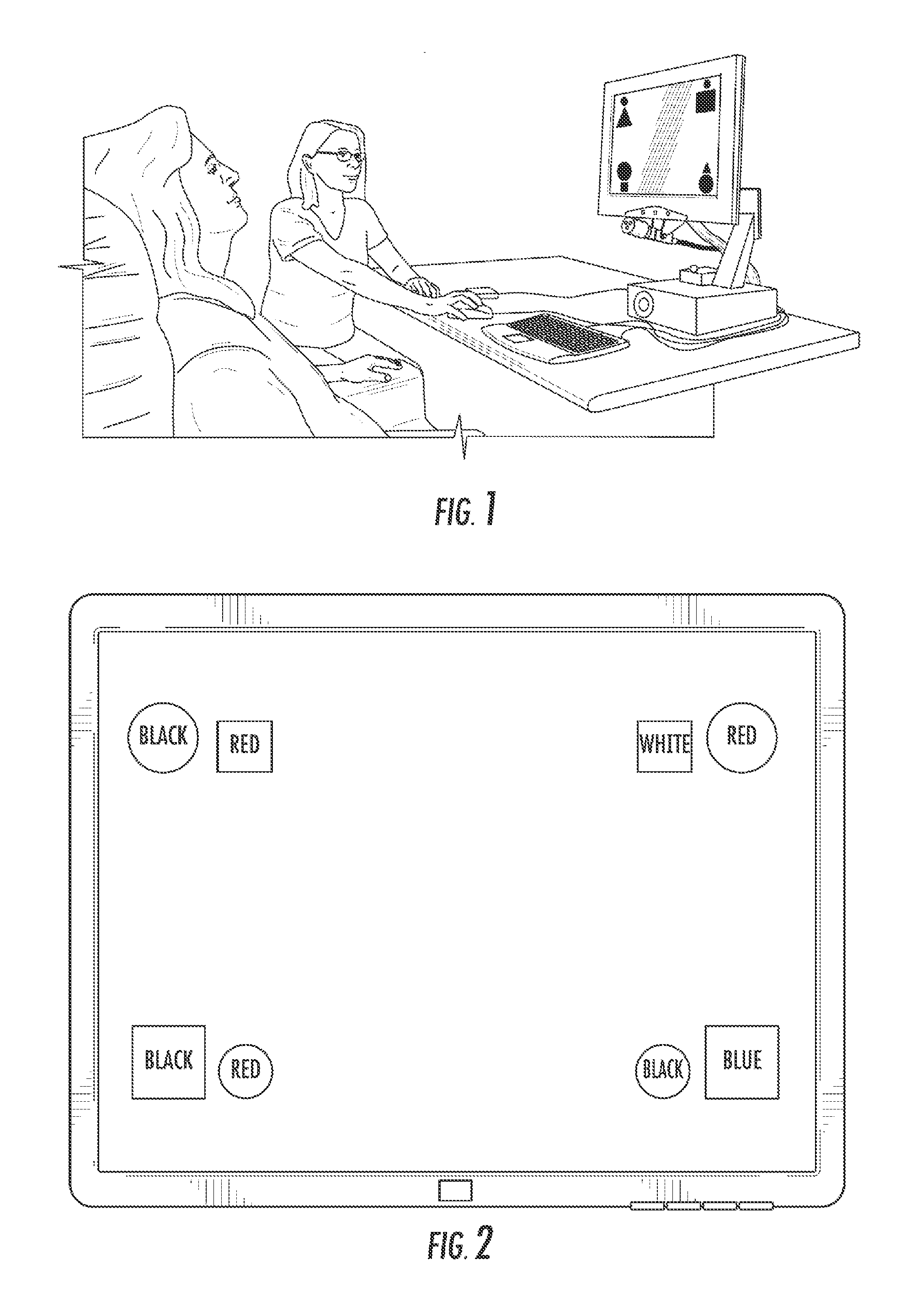
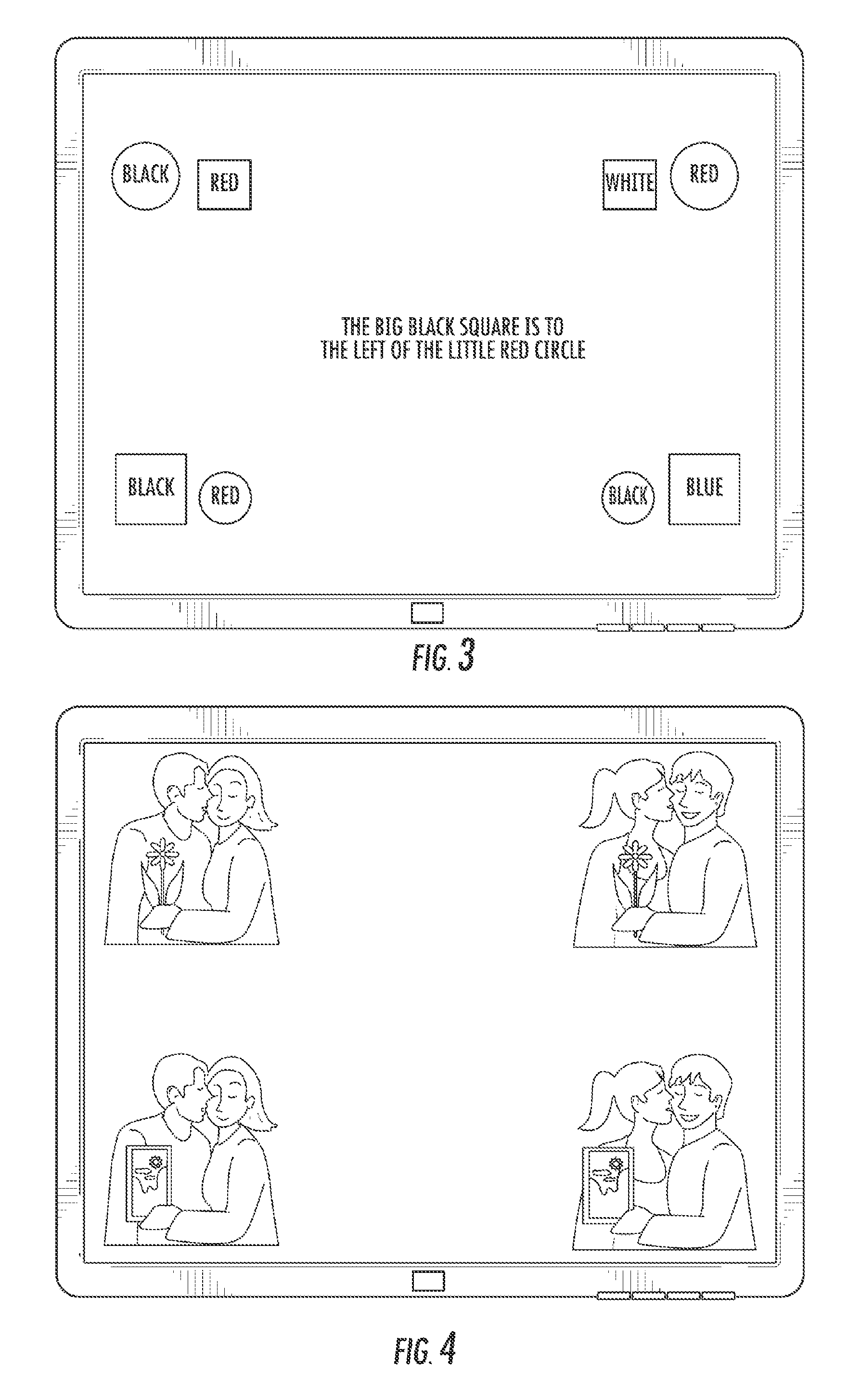
Methods for assessing cognitive and linguistic abilities by tracking and recording the eye movements of a patient in response to predetermined verbal and visual stimuli. The methods incorporate conventional eye-tracking technology to acquire eye-fixation location and duration measures for testing linguistic comprehension, working memory, attention allocation, and the effect of semantic associative priming. Visual stimuli presented in the methods are carefully designed to reduce visually distracting features. Verbal stimuli are carefully designed to control for numerous linguistic features.
Owner:OHIO UNIV
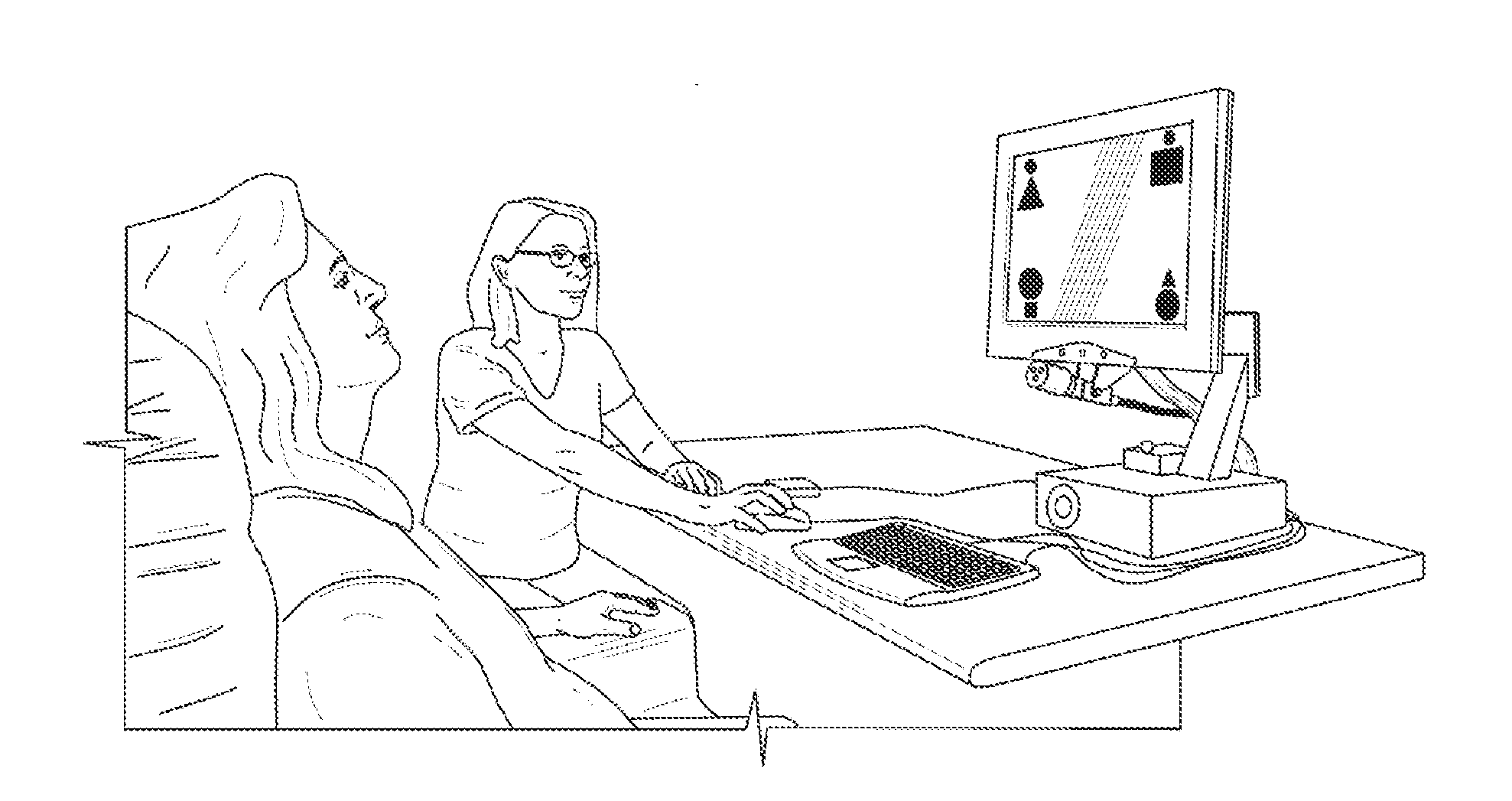
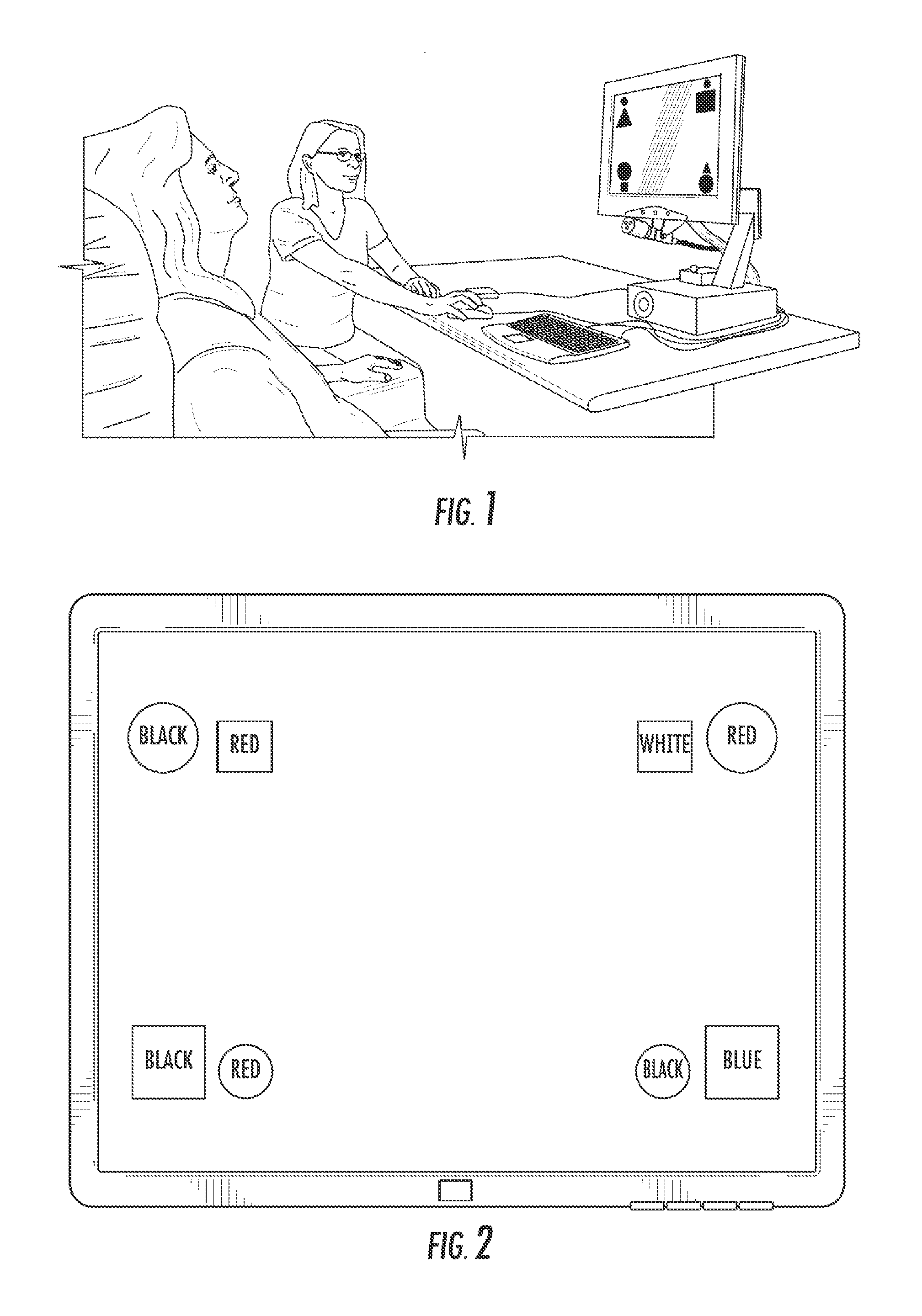
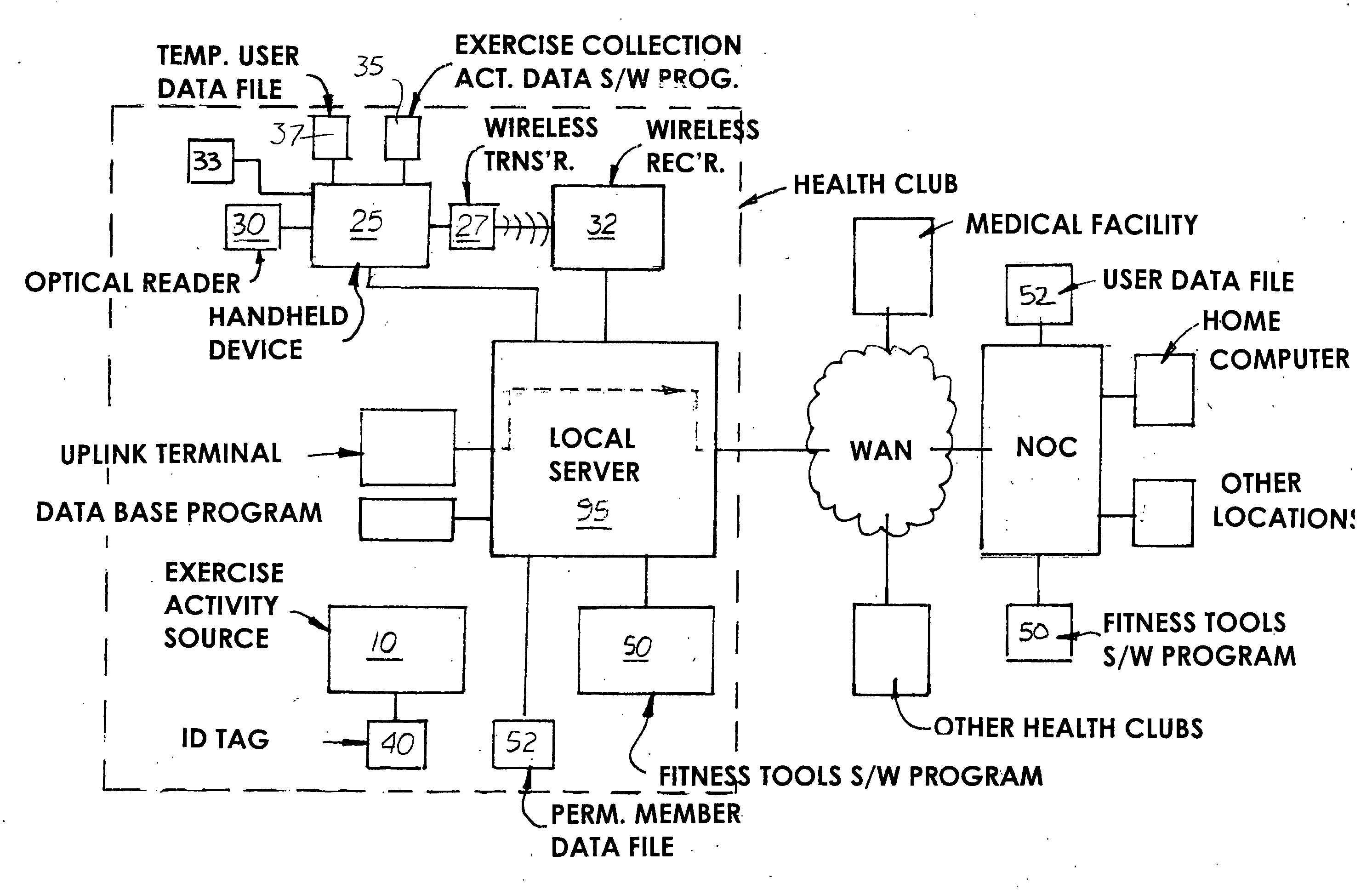
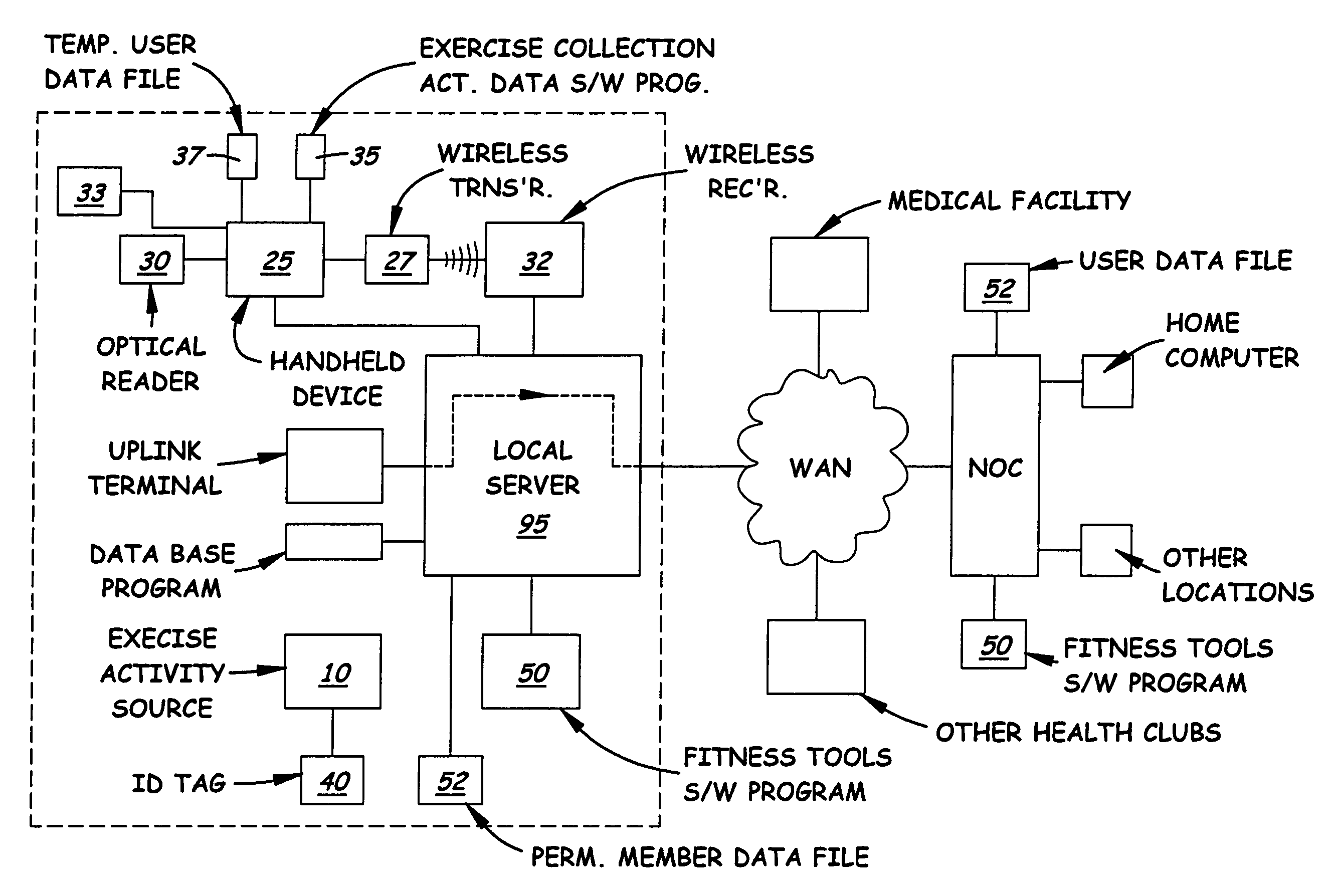
Health club exercise records system
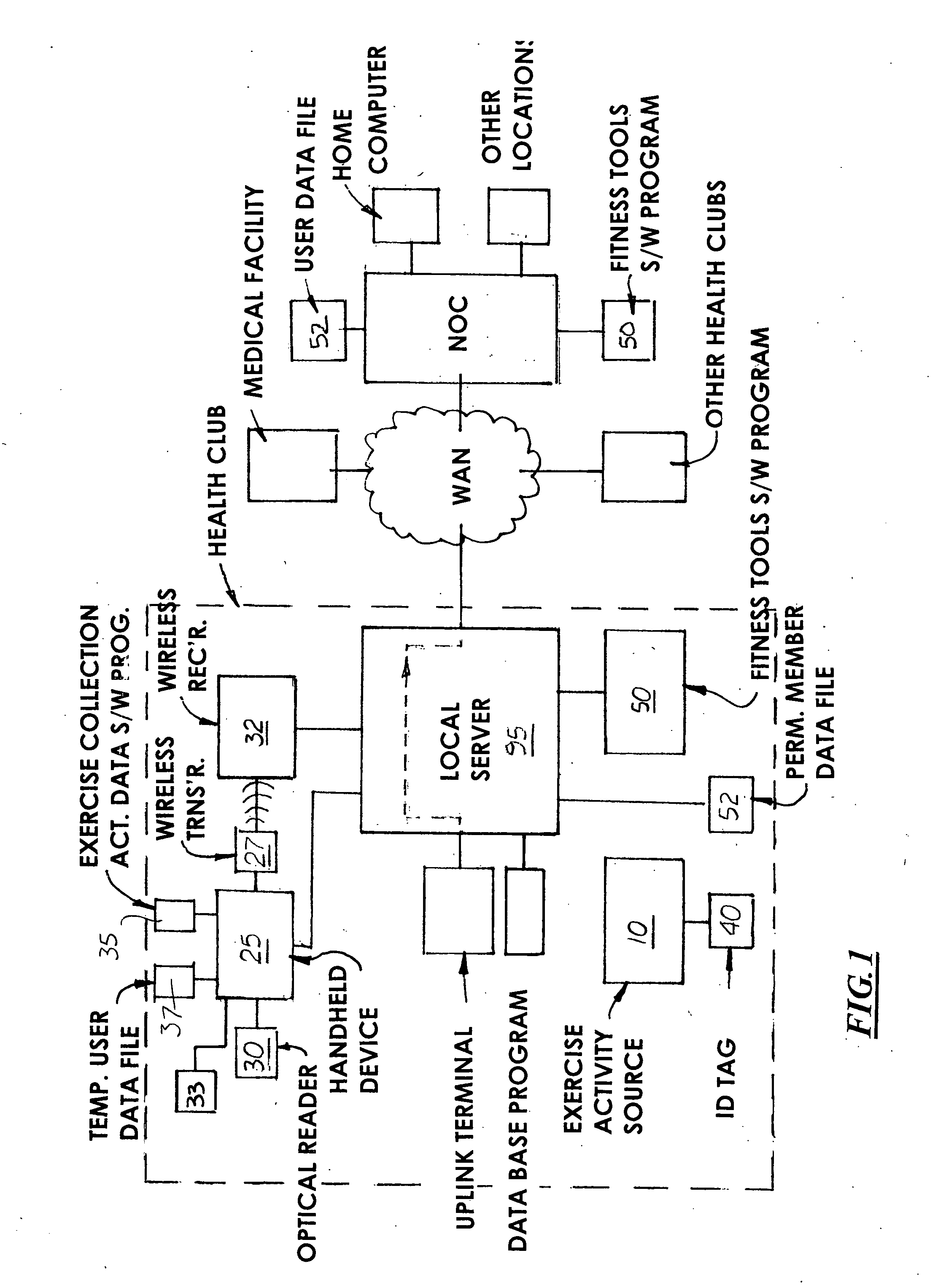
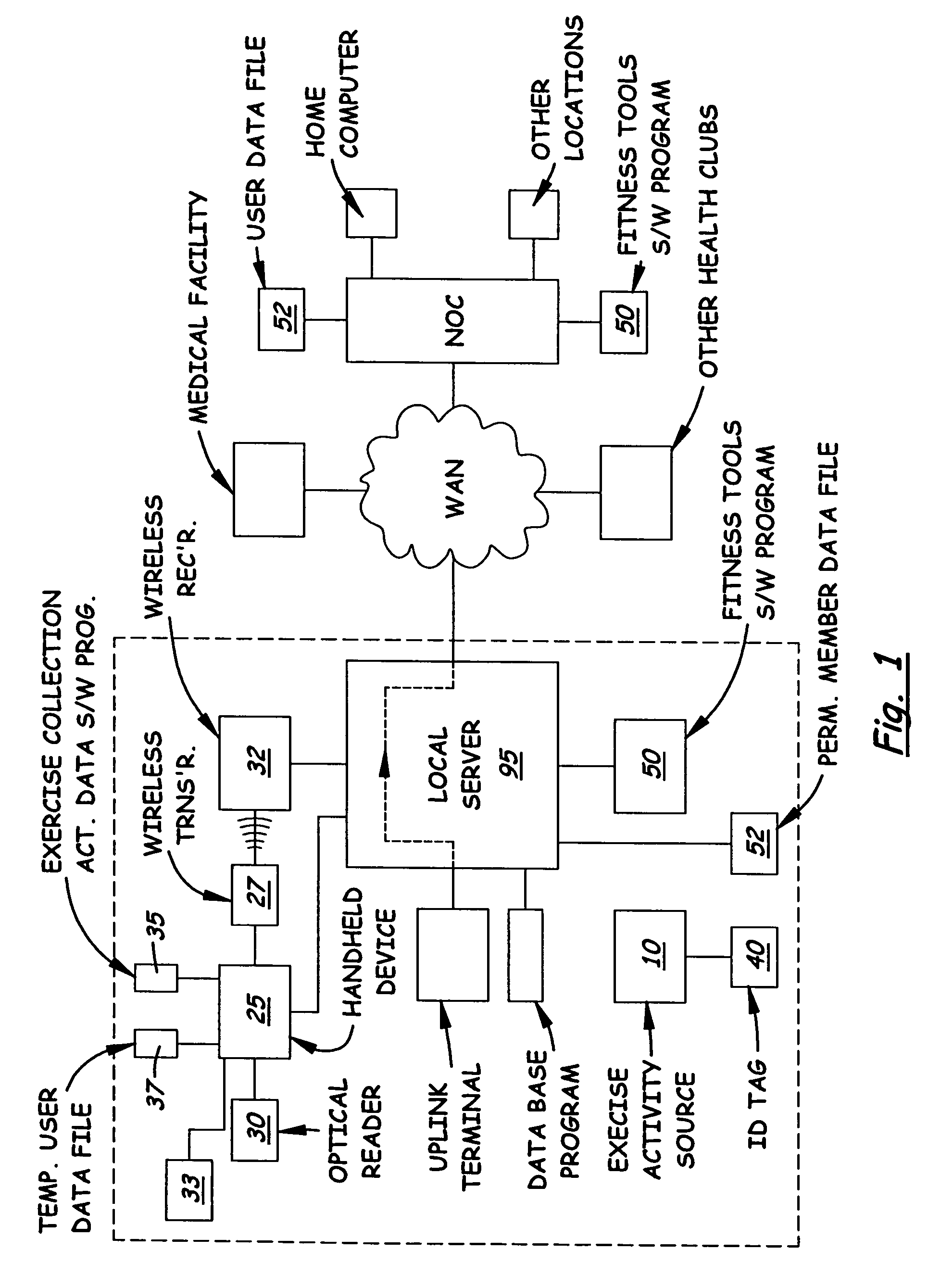
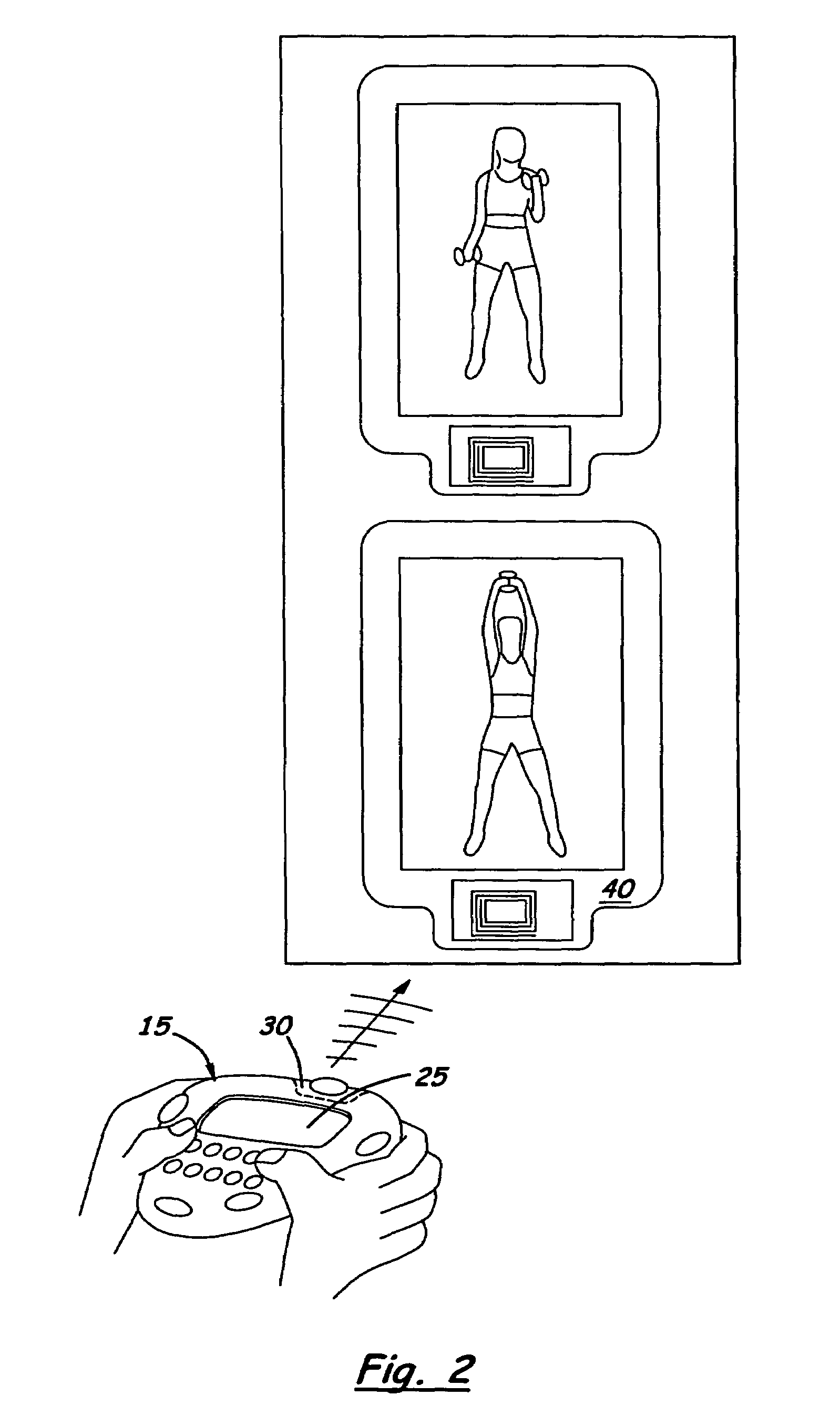
InactiveUS20040198555A1Easy to recordPhysical therapies and activitiesClubsNetwork operations centerData file
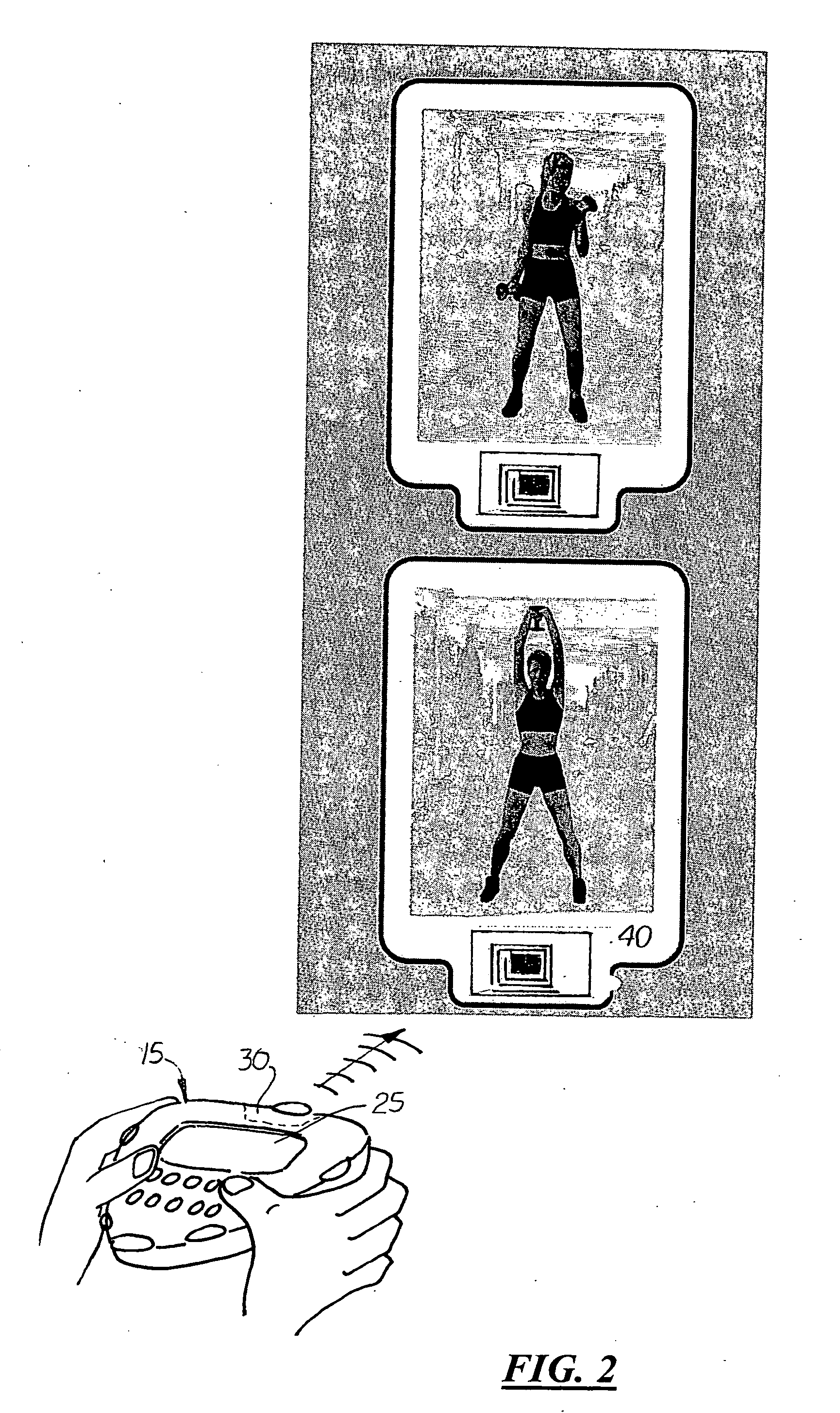
A health club exercise records system in which members to the health club are given a handheld device that is pre-programmed by the trainer or health club operator to record different exercise activities. The handheld device includes a built-in numeric keypad, a display monitor, and optical reader designed to communicate with a compatible ID tag located on or in the vicinity of the exercise activity data source. Loaded into the working memory of the handheld device is a pre-programmed exercise data collection program. The exercise data collection program displays one or more sub-routines to the member requesting the member to input information regarding the exercise. The sub-routines are specific to the exercise activity data source and present one or more prompts requiring the member to input information. The inputted information is stored in a temporary data file located on the handheld device or transmitted immediately to a permanent member data file on a local server located in the health club. The system may also include an uplink terminal for transmitting the data in the temporarily data file to a remote server connected to a network operations center. A fitness tools software program is loaded into the server for collecting and processing the data in the member's permanent data file which may be reviewed by the trainer and / or member.
Owner:ANDERSON BRENT +1
Phospholipase c beta1 (plcbeta1) knockout mice as a model system for testing schizophrenia drugs
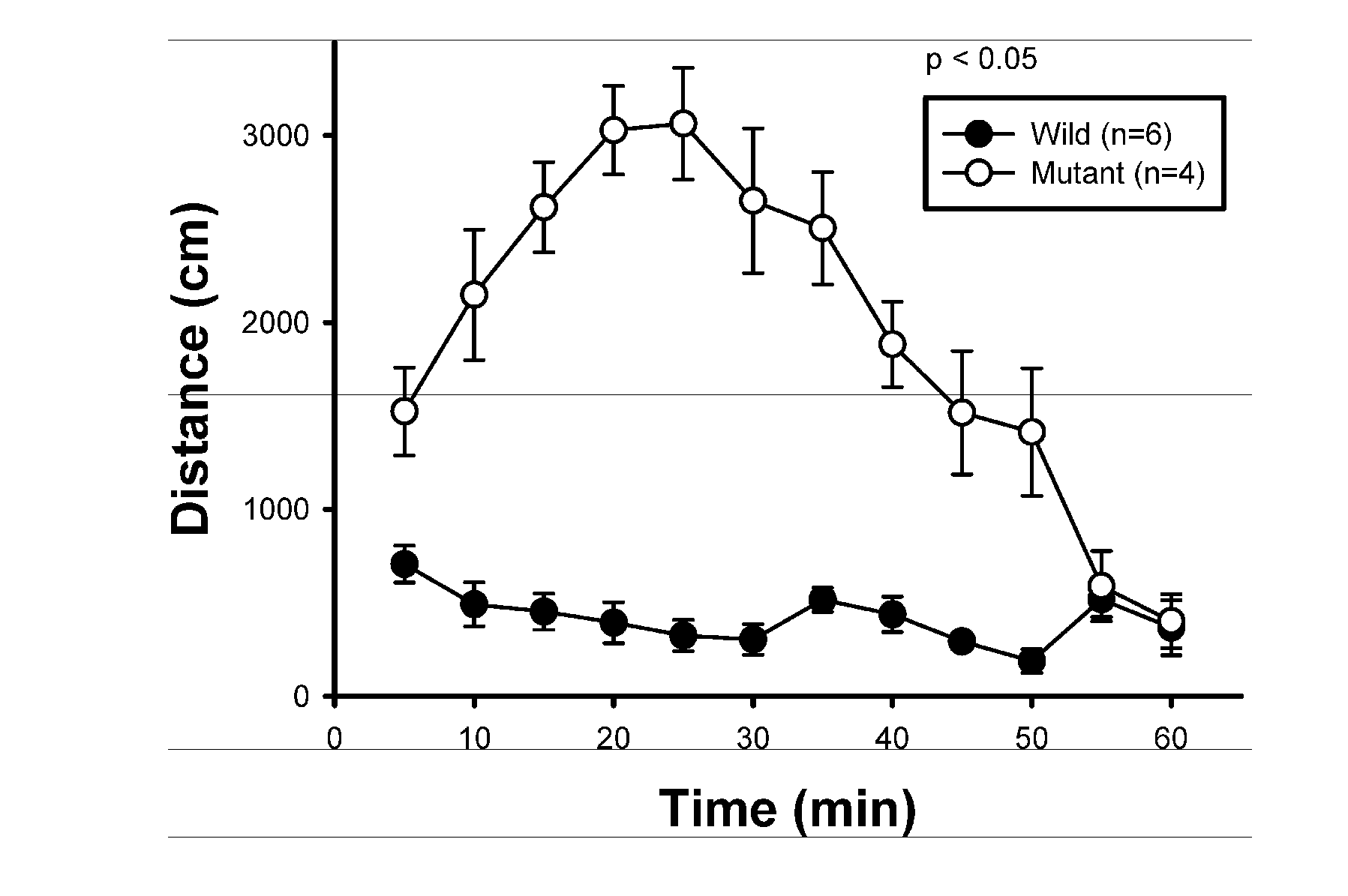
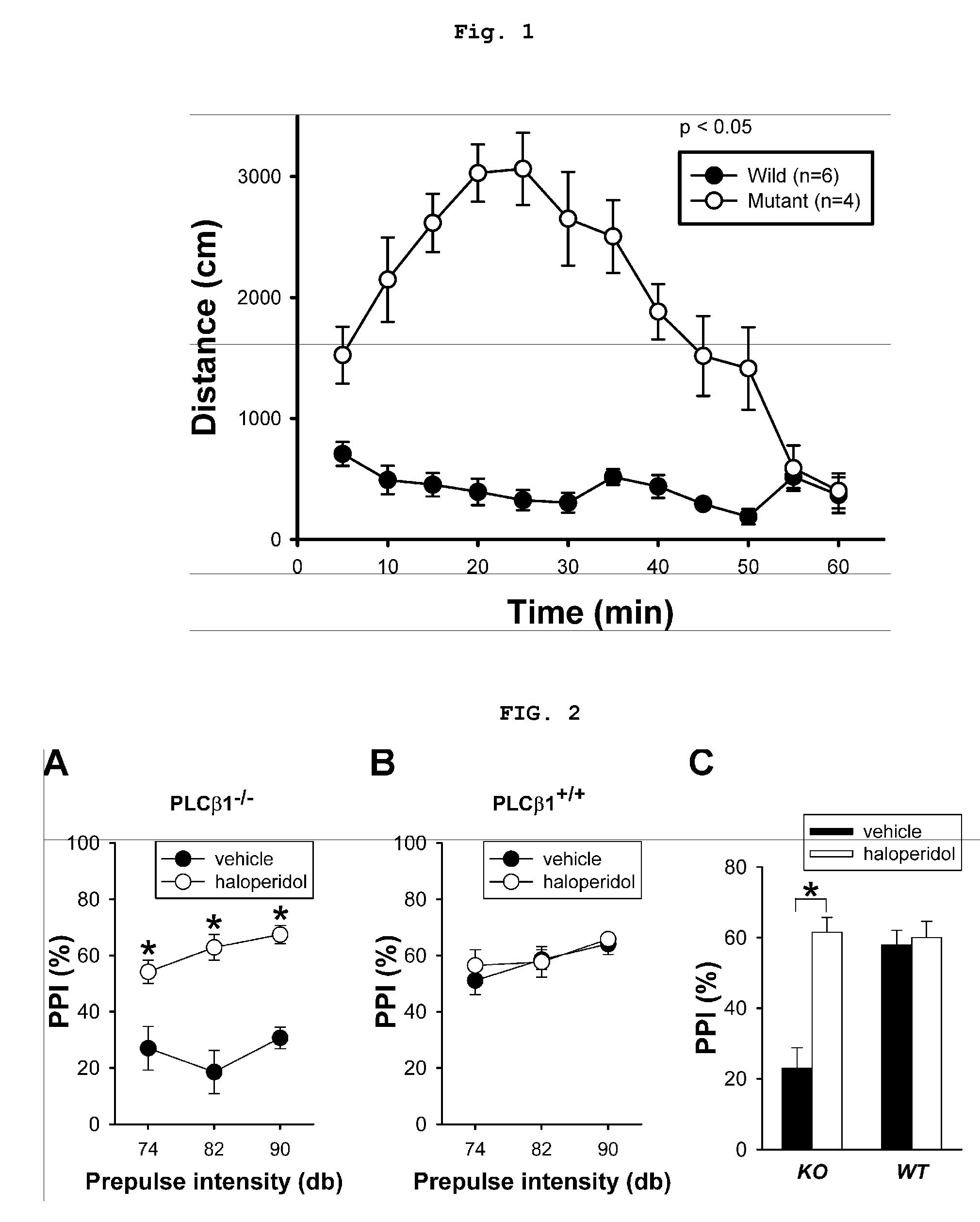
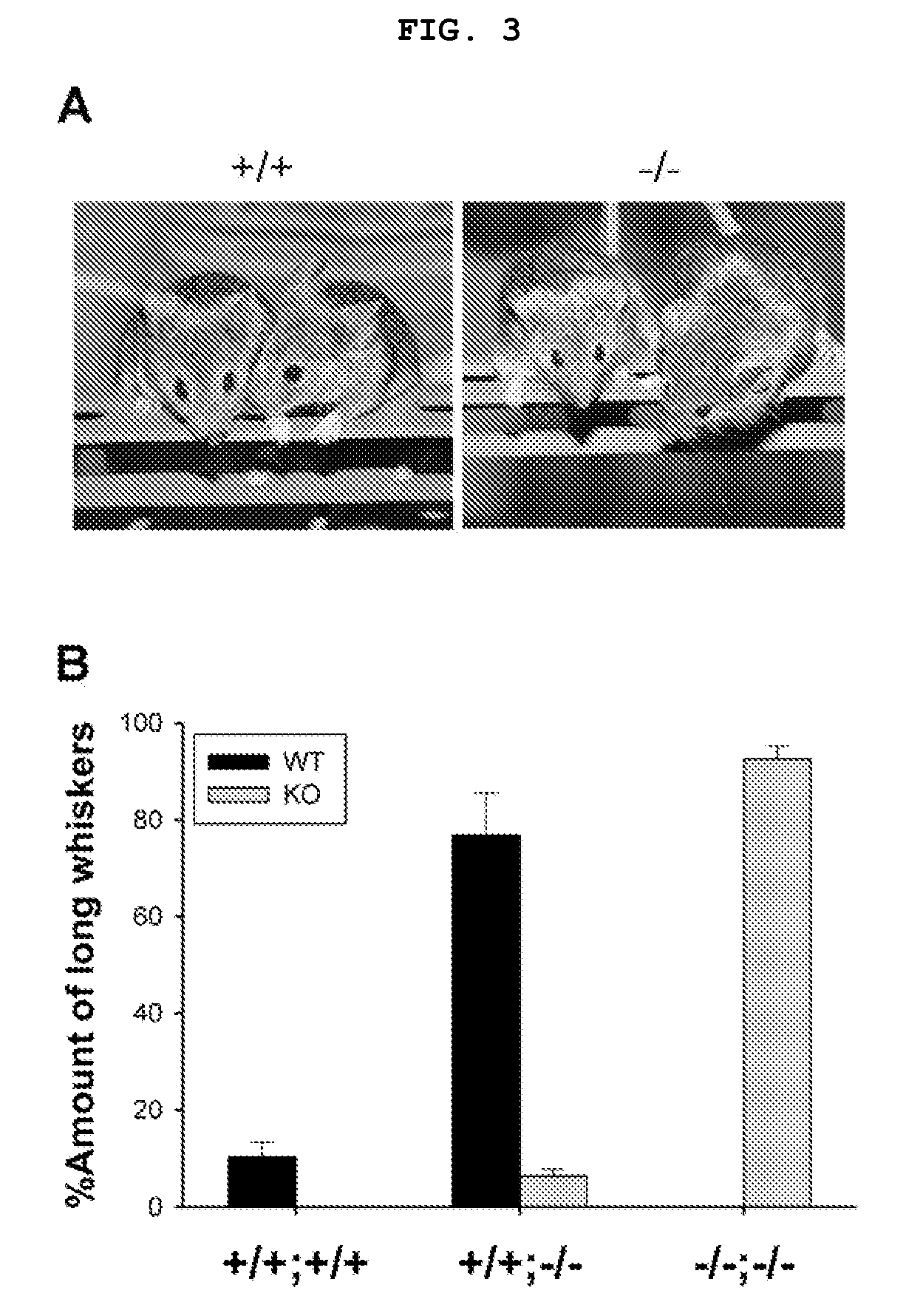
The present invention relates to a method for screening therapeutic drugs of schizophrenia using an animal model of the disease. More specifically, this invention relates to a screening method based on the phospholipase C β1 (PLCβ1) knockout mouse as an animal model of schizophrenia with all the major symptoms of the human disease. This knockout mouse exhibits symptoms similar to human schizophrenia such as locomotor hyperactivity, impaired prepulse inhibition of the startle response, lack of barbering and nesting behaviors, socially subordinate status, impaired learning, and lack of type II theta rhythm which has been implicated in working memory. Thus, the knockout mouse of the present invention can be useful as an animal for screening therapeutic drugs against schizophrenia.
Owner:KOREA INST OF SCI & TECH
Methods and systems for provisioning energy systems
Owner:SUNGEVITY
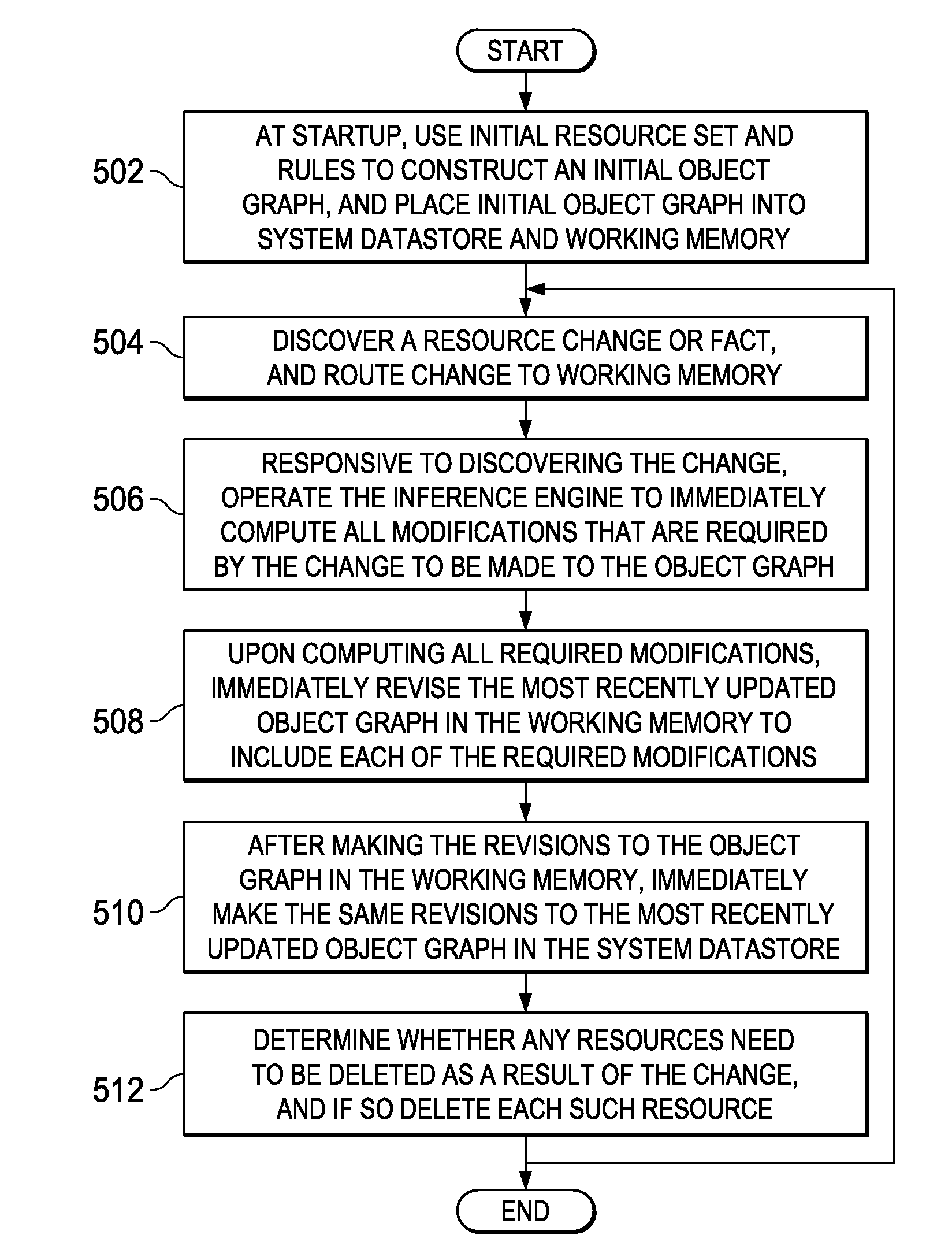
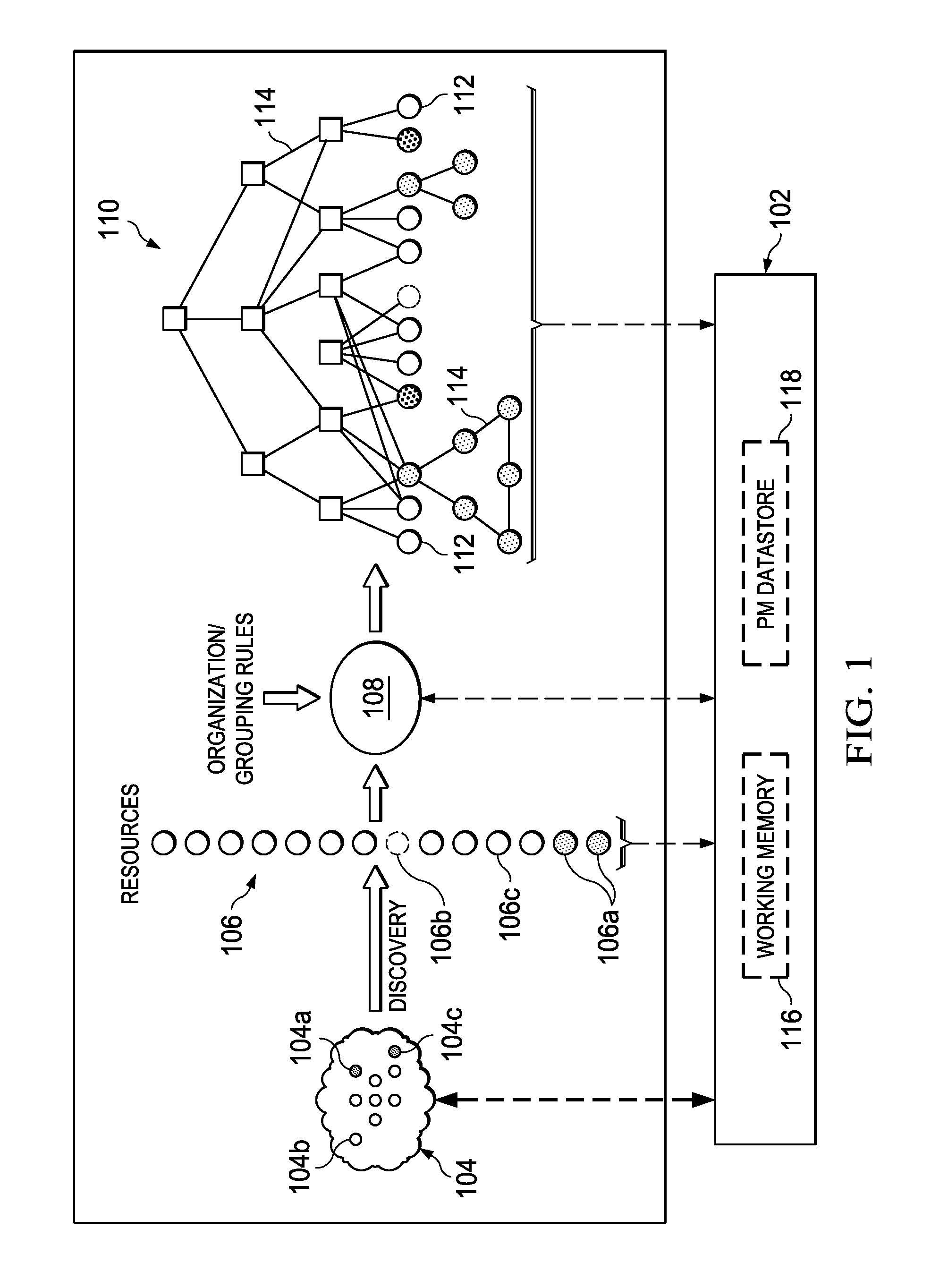
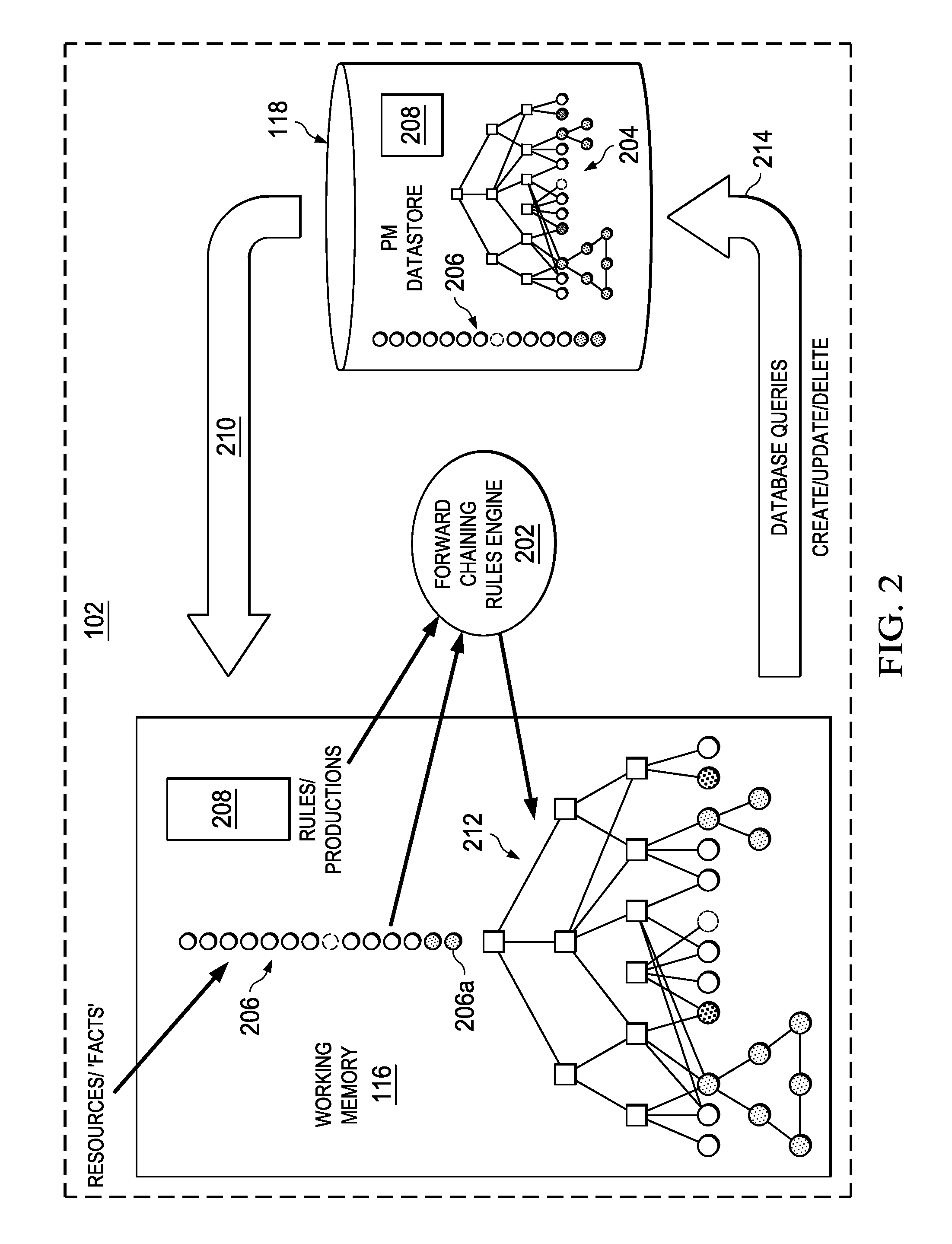
Creation and Revision of Network Object Graph Topology for a Network Performance Management System
InactiveUS20110320394A1Digital data information retrievalDigital data processing detailsManagement systemObject graph
An embodiment of the invention comprises, providing an initial object graph to a database, the initial object graph being generated by applying a set of rules to resources included in a resource set at a specified time, or by revising a previous object graph at the previous time, the resource set at the specified time comprising an initial resource set. The method includes providing the initial object graph to a working memory, maintained in separation from the database; discovering a changed fact associated with one of the resources of the initial resource set; and upon discovering the changed fact, determining modifications required by the changed fact to the initial object graph. If modifications are required, the initial object graph is revised in the working memory to include such modifications. The same revisions are then made to the initial object graph in the system database.
Owner:IBM CORP
Health club exercise records system
InactiveUS7507183B2InexpensiveEasy to usePhysical therapies and activitiesClubsNetwork operations centerData file
A health club exercise records system in which members to the health club are given a handheld device that is pre-programmed by the trainer or health club operator to record different exercise activities. The handheld device includes a built-in numeric keypad, a display monitor, and optical reader designed to communicate with a compatible ID tag located on or in the vicinity of the exercise activity data source. Loaded into the working memory of the handheld device is a pre-programmed exercise data collection program. The exercise data collection program displays one or more sub-routines to the member requesting the member to input information regarding the exercise. The sub-routines are specific to the exercise activity data source and present one or more prompts requiring the member to input information. The inputted information is stored in a temporary data file located on the handheld device or transmitted immediately to a permanent member data file on a local server located in the health club. The system may also include an uplink terminal for transmitting the data in the temporarily data file to a remote server connected to a network operations center. A fitness tools software program is loaded into the server for collecting and processing the data in the member's permanent data file which may be reviewed by the trainer and / or member.
Owner:ANDERSON BRENT +1
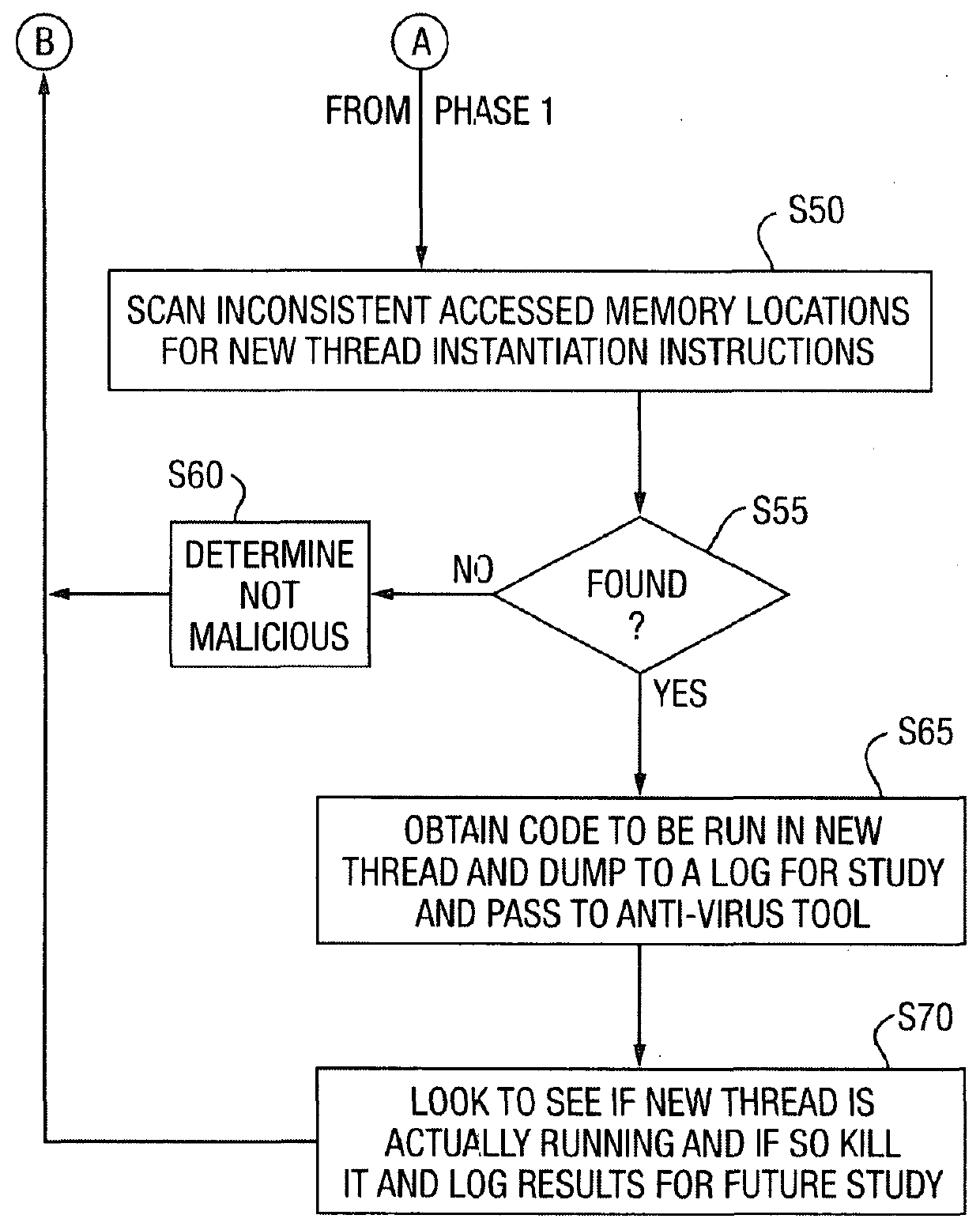
Suspicious program detection
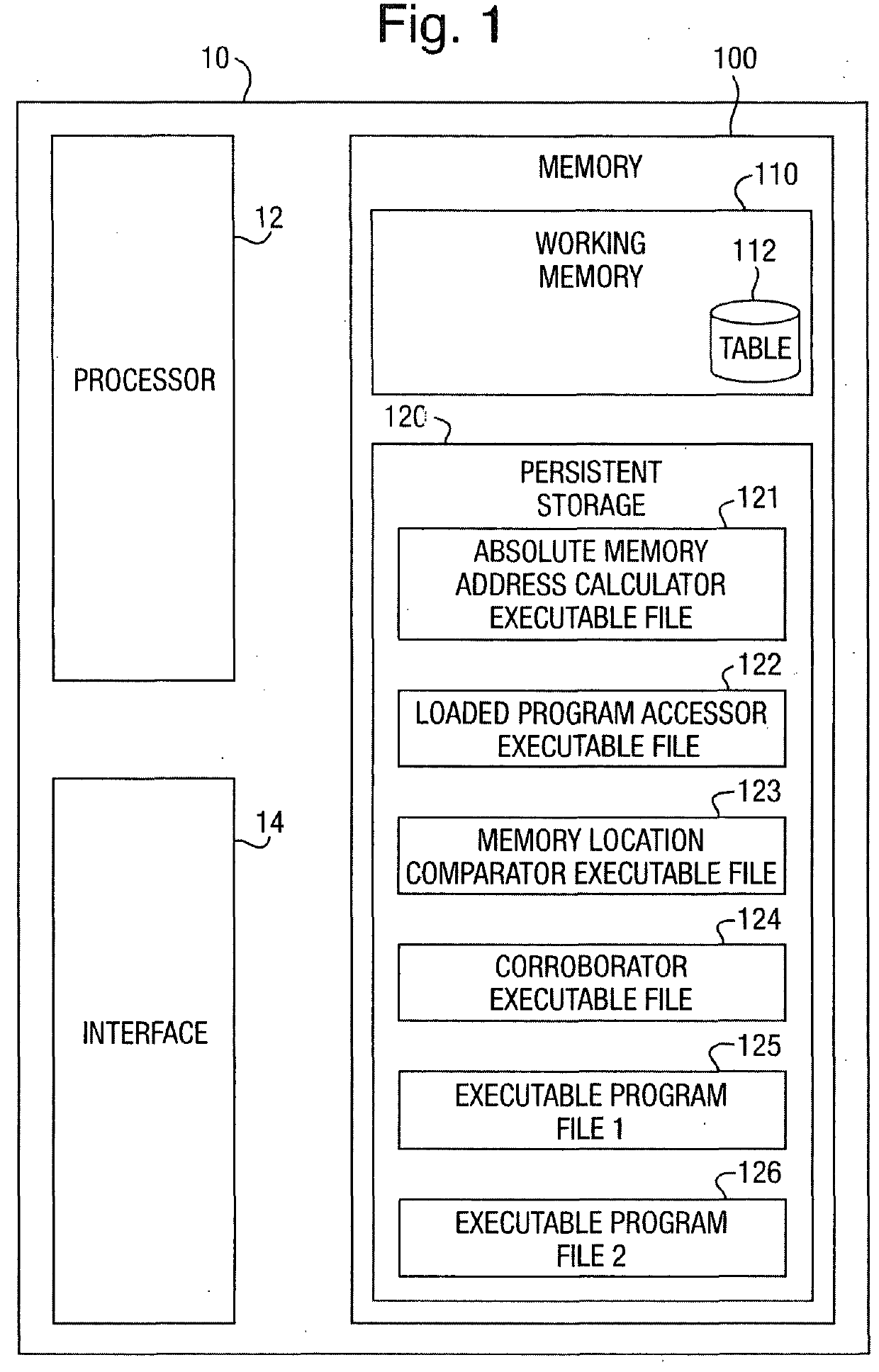
ActiveUS20160055337A1Sure easyMemory loss protectionError detection/correctionMemory addressRandom access memory
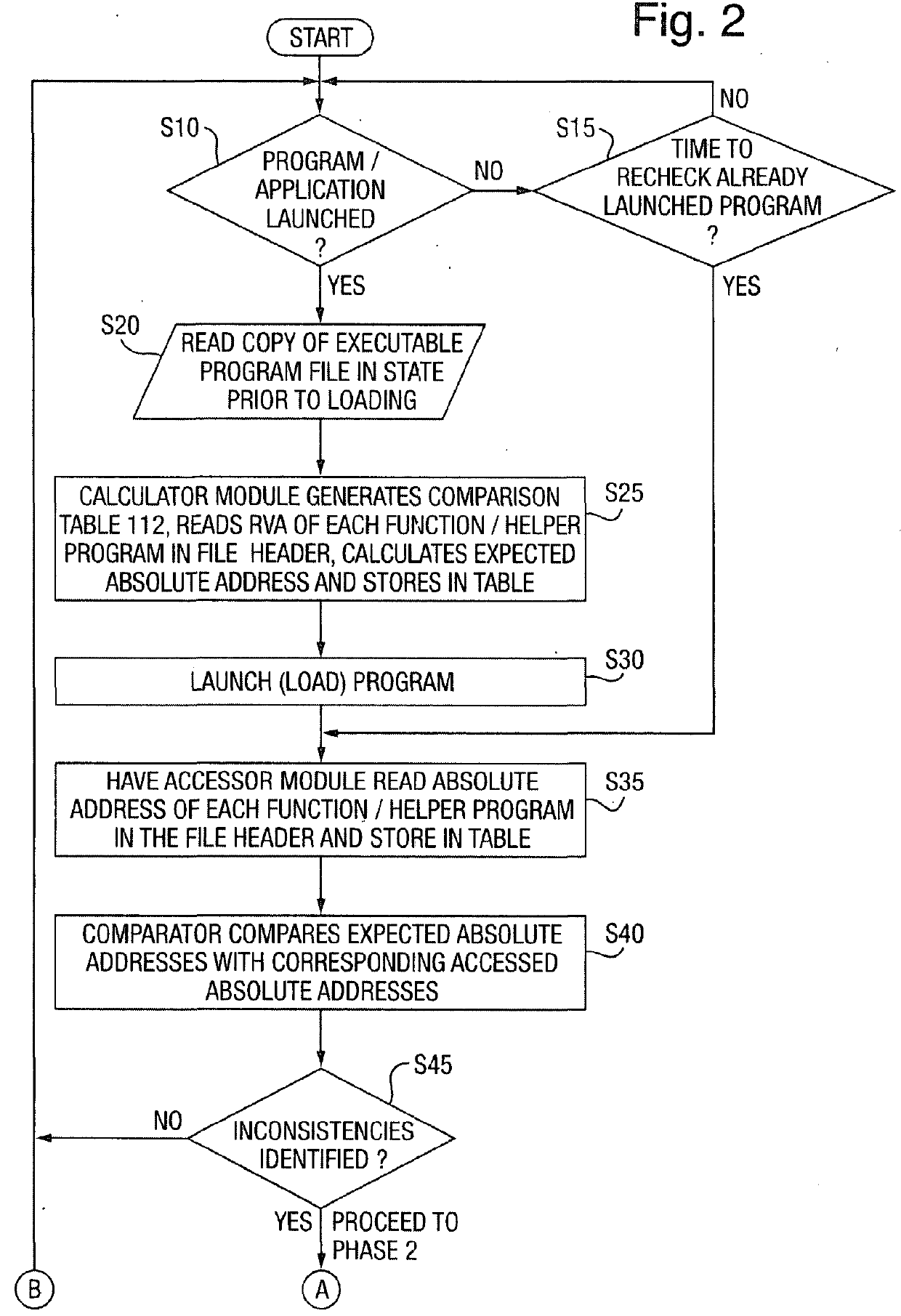
A processing device (10) includes a processor (12), an interface (14) and a memory (100). The memory (100) is formed from system Random Access Memory (RAM) and one or more other storage devices. The memory (100) can be considered as comprising working memory (110) and persistent storage (120). The working memory includes the system RAM but may also use memory from one or more other storage devices and when certain suspicious program detection modules are operating also stores a comparison table (112) discussed below. Contained within the persistent storage are several executable program files as follows: an Absolute Memory Address Calculator executable program (121) which is responsible for causing the system (10) to inspect a copy of a persistently stored (and compiled) executable program (e.g. an executable program (125, 126, 127, . . . as stored in the persistent storage 120) and to calculate expected absolute memory locations for the various functions or helper programs that it makes calls to and to store these in a table (112) that it creates in the working memory (110) for this purpose; a Loaded Program Accessor executable program (122) which is responsible for causing the system (10) to inspect a copy of an executable program as loaded in the working memory (110) of the system after loading and linking of the program have been completed, to determine the actual memory locations stored in the Import Address Table (IAT) of the loaded program, and to store these actual memory locations in the comparison table (112); a Memory Location Comparator executable program (123) which is responsible for causing the system (10) during execution of this program to compare the calculated expected absolute memory locations with their respective actual accessed memory locations as stored in the comparison table of memory locations (112); and a Corroborator executable program (124) which is responsible for causing the system (10) during execution of this program to perform a corroboration of any mismatches of memory locations detected in the memory location pairs stored in the table (112) of memory locations, by, in the present embodiment, inspecting the contents of any executable instructions contained at the actually accessed memory location to look for the presence of an instruction causing a new thread of execution to be instantiated.
Owner:BRITISH TELECOMM PLC
Display enhanced testing for concussions and mild traumatic brain injury
Cognitive assessment systems and methods that provide an integrated solution for evaluating the presence or absence of cognitive impairment. The present invention is used to test cognitive functions of an individual including information processing speed, working memory, work list learning and recall, along with variations of these tasks. Immersive and non-immersive systems and methods are disclosed. Testing and results feedback using the present invention may be completed in real time, typically in less than 15 minutes.
Owner:EMORY UNIVERSITY +1
Cognitive and linguistic assessment using eye tracking
ActiveUS8602789B2Leveling precisionHealth-index calculationReadingDividing attentionComputer science
Methods for assessing cognitive and linguistic abilities by tracking and recording the eye movements of a patient in response to predetermined verbal and visual stimuli. The methods incorporate conventional eye-tracking technology to acquire eye-fixation location and duration measures for testing linguistic comprehension, working memory, attention allocation, and the effect of semantic associative priming. Visual stimuli presented in the methods are carefully designed to reduce visually distracting features. Verbal stimuli are carefully designed to control for numerous linguistic features.
Owner:OHIO UNIV
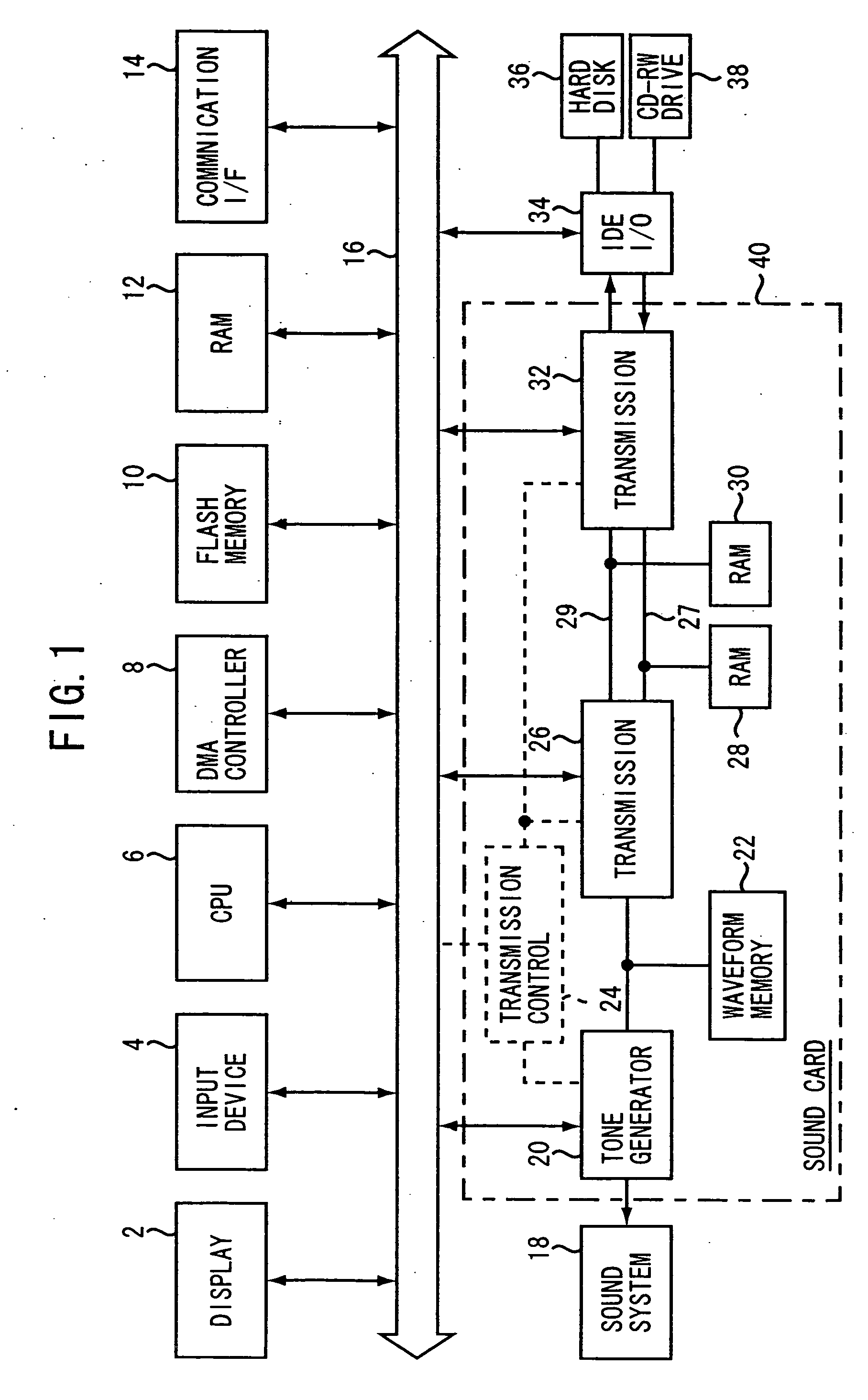
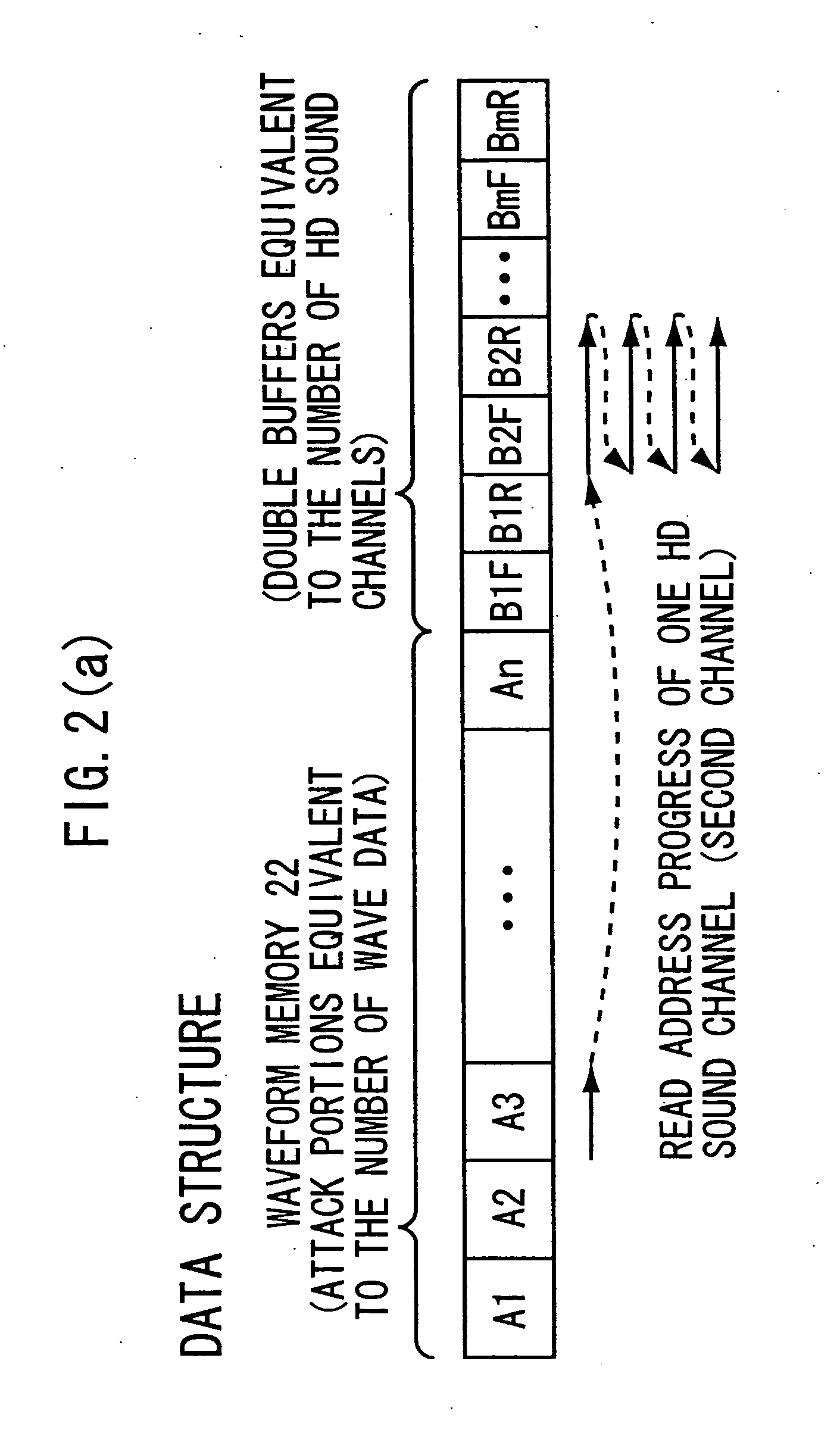
Memory access controller for musical sound generating system
ActiveUS20060137515A1Promote disseminationFacilitate transmissionGearworksMusical toysComputer hardwareMusical tone
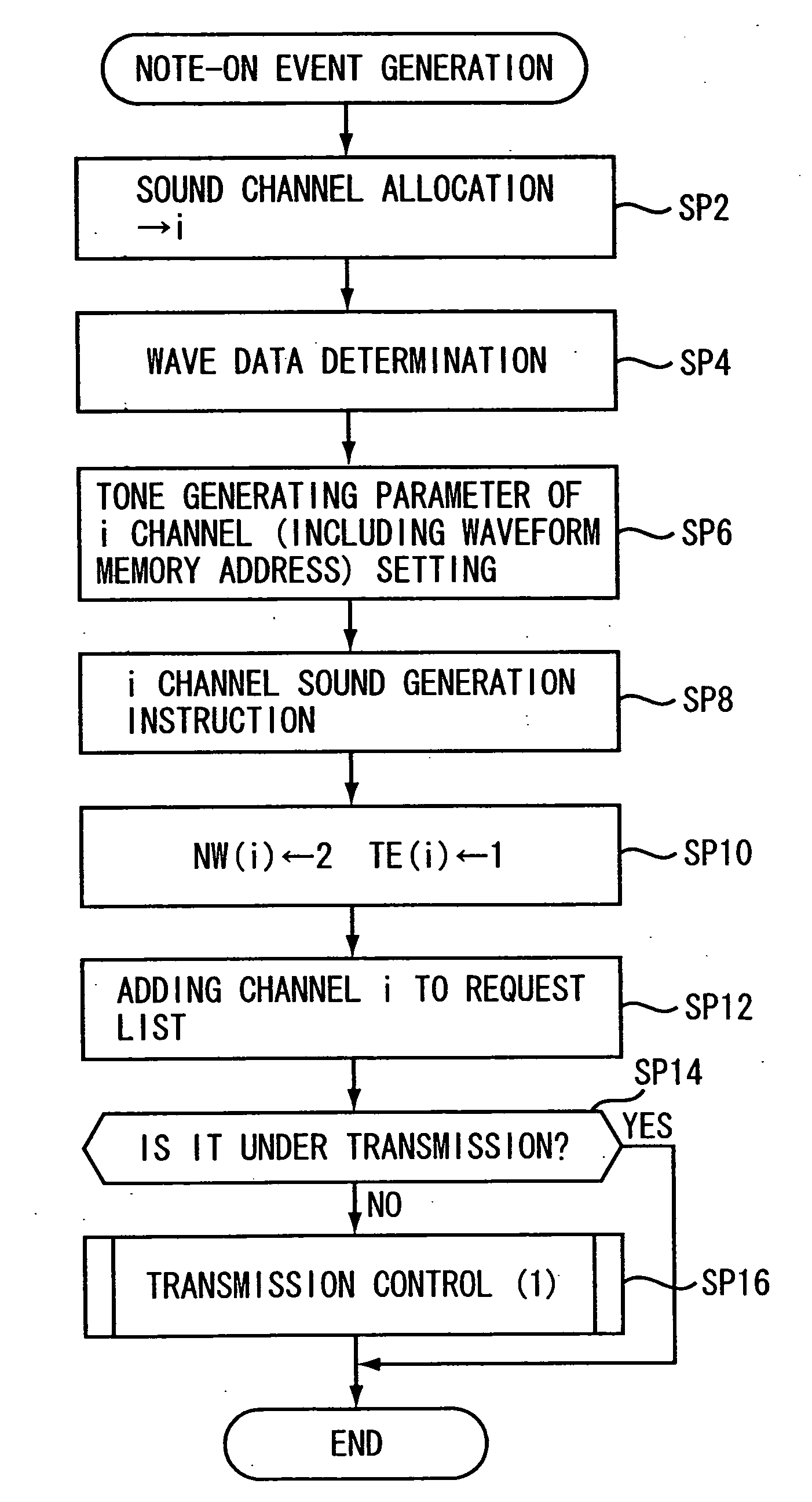
In an access controller provided for a musical sound signal generating system, a signal generating section operates when a readout of wave data of one block stored in a working memory is completed in a sound channel, for supplying a next waveform request signal to a CPU, which requests a next block of the wave data for the sound channel. First and second buffer memories are connected between a recording medium and the working memory respectively through first and second buses which are independent from each other. A first transmitting section operates when receiving block specifying information from the CPU, which specifies a block to be read next from the recording medium, for transmitting the wave data of the specified block to either of the first or second buffer memory while reading the specified block of the wave data from the recording medium. A second transmitting section operates when the transmitting of the wave data to either of the first or second buffer memory is finished and during a period when the musical sound signal generation system is not accessing the working memory, for transmitting the wave data of the specified block to the working memory from either of the first or second buffer memory, to which the wave data of the specified block has been transmitted by the first transmitting section.
Owner:YAMAHA CORP
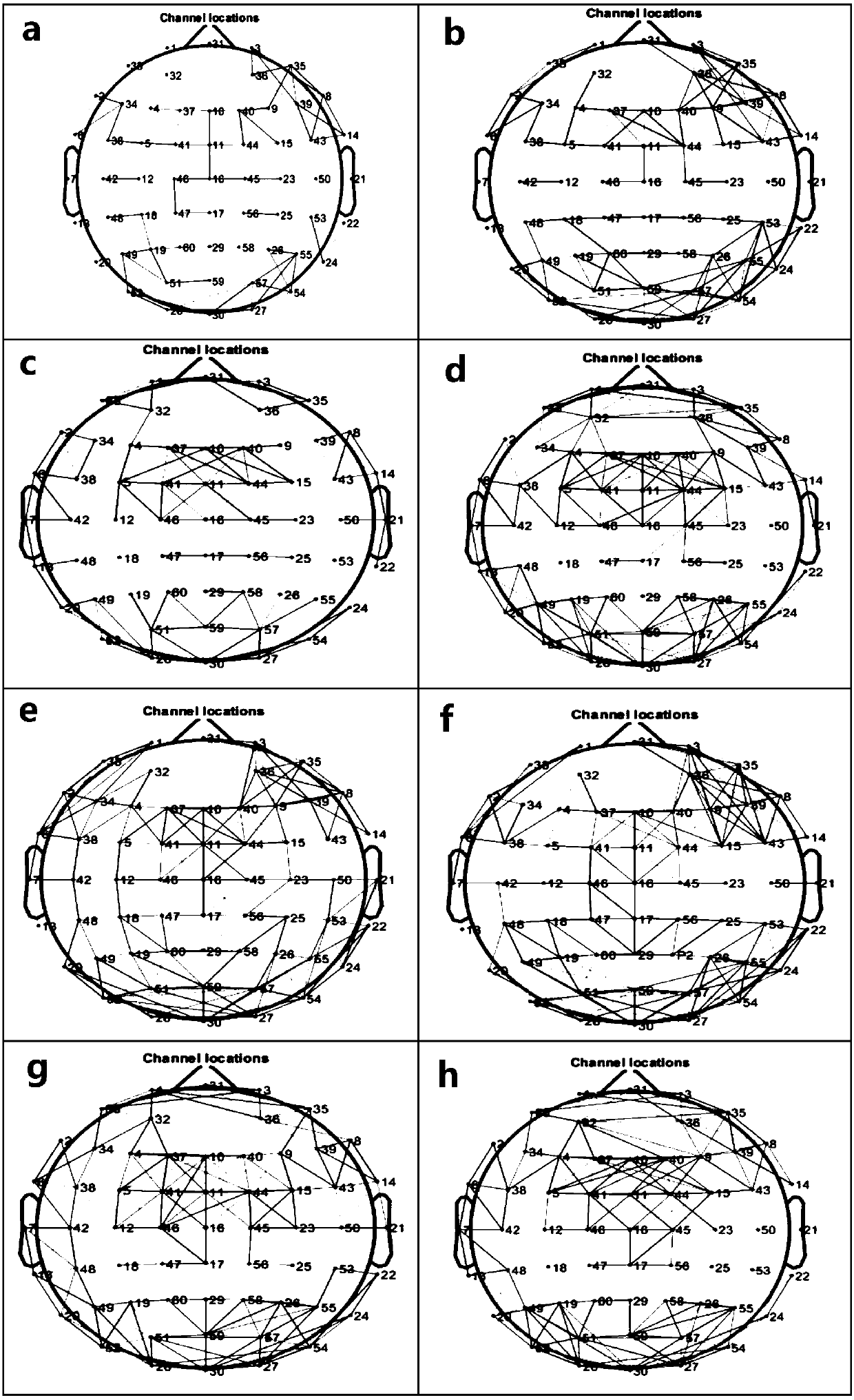
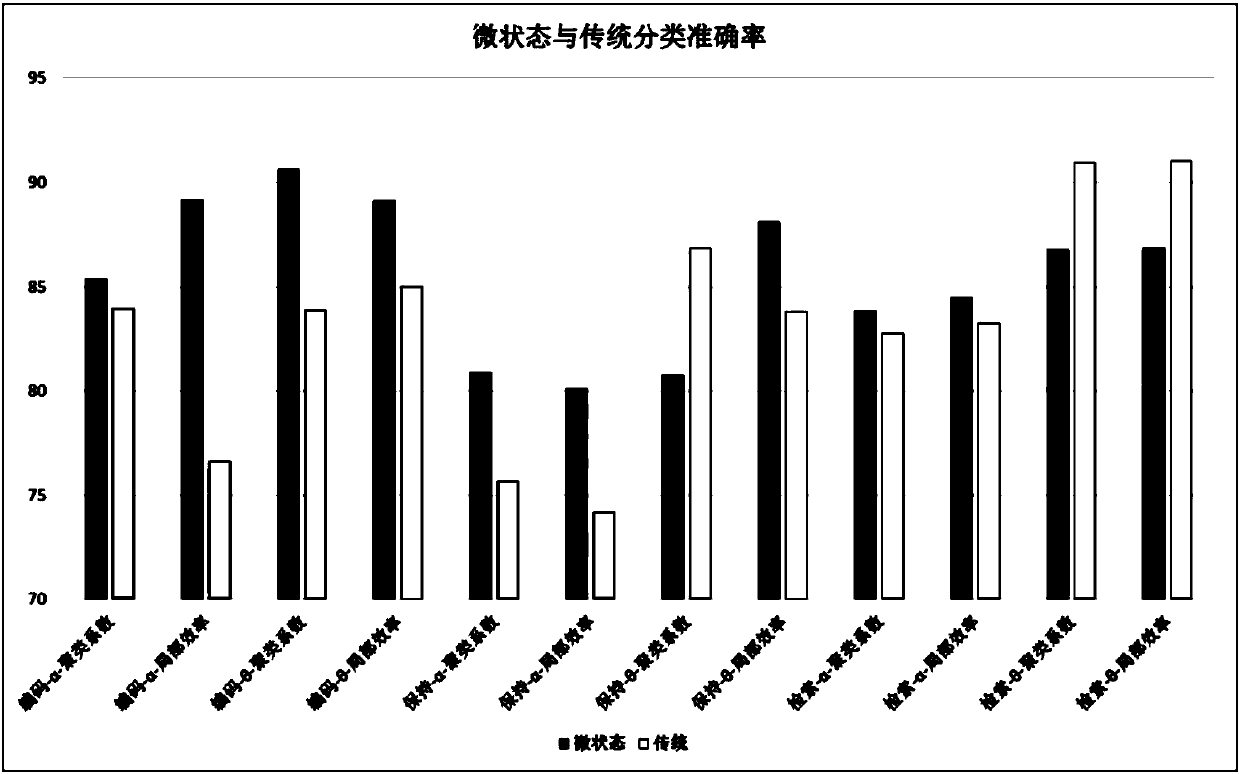
Brain function network construction method based on micro-state
InactiveCN108577835AHigh density distributionIncrease electrode densityDiagnostic recording/measuringSensorsEeg dataAlgorithm
The invention relates to the technical field of brain function network research and more particularly relates to a brain function network construction method based on a micro-state. Starting from theconstruction of an EEG brain function network, according to the theory of EEG micro-state related aspects, namely that the EEG micro-state is the most basic state which reflects the brain activity, proposing that the EEG micro-state can also be applied to construction of the brain function network. The method provided by the invention solves the problem that the time consumed for construction of the traditional brain function network is too long and reduces a large quantity of redundant information in an original EEG time sequence by using the time sequence after micro-state reconstruction. Byapplying the method to an EEG data set of mental disease working memory collected in a hospital, the EEG brain function network for schizophrenia patients and normal persons is constructed; and compared with the brain function network constructed by using an original EEG signal, the brain function network constructed by the time sequence after micro-state reconstruction has the advantage that thecharacteristics of the human brain network can be more accurately reflected.
Owner:TAIYUAN UNIV OF TECH
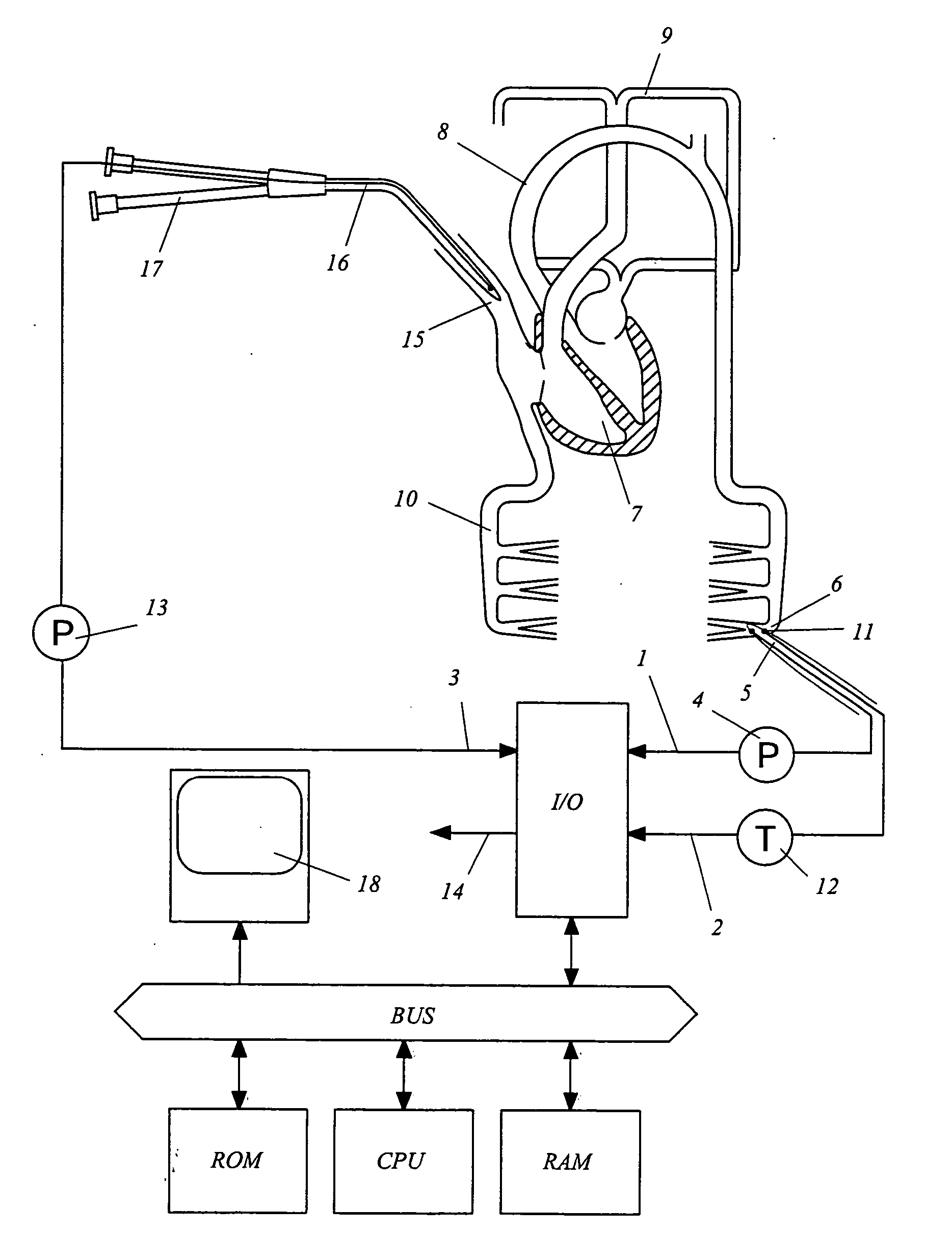
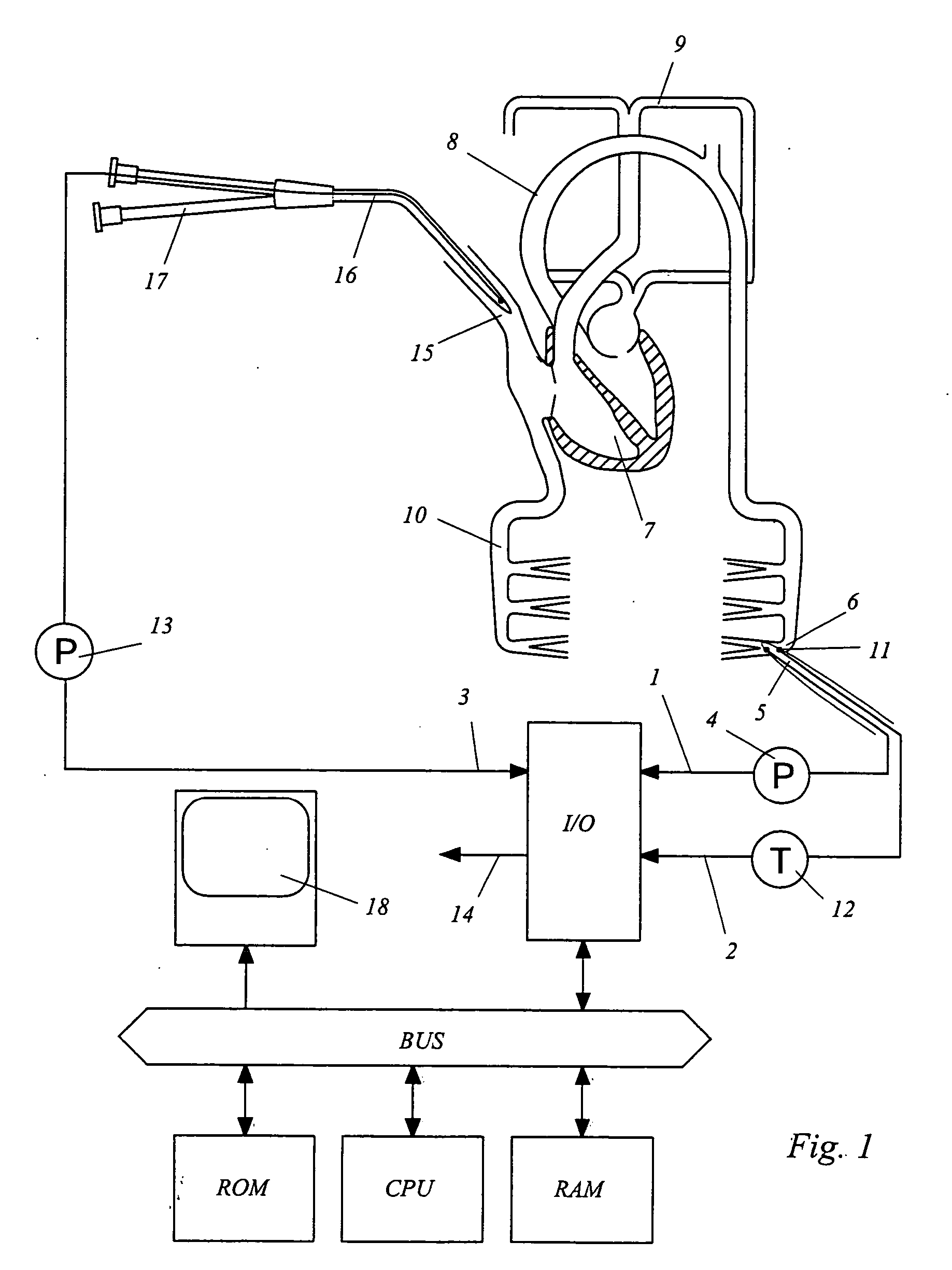
Device for determining a hemodynamic parameter
Owner:PULSION MEDICAL SYSTEMS SE
Learning capability test device
InactiveCN101419758AEasy to testEasy to usePsychotechnic devicesTeaching apparatusLiquid-crystal displayProficiency testing
Owner:TIANJIN NORMAL UNIVERSITY
Systems and methods for enhancing cognition
ActiveUS8821242B2Increase awarenessIncrease or decrease sizeBoard gamesDiagnostic recording/measuringMammalHuman–computer interaction
Owner:LUMOS LABS
Method for determining lengths of upstream transition regions of construction operation area
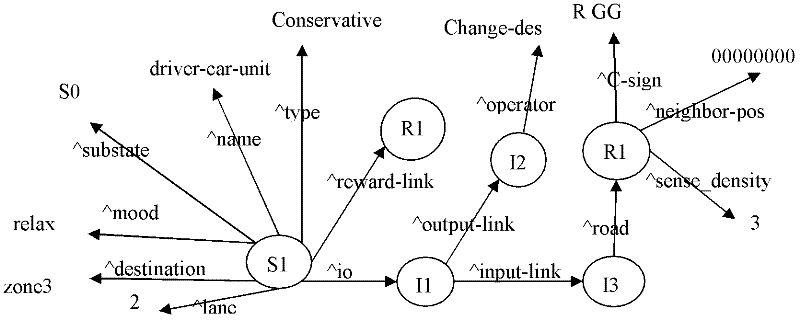
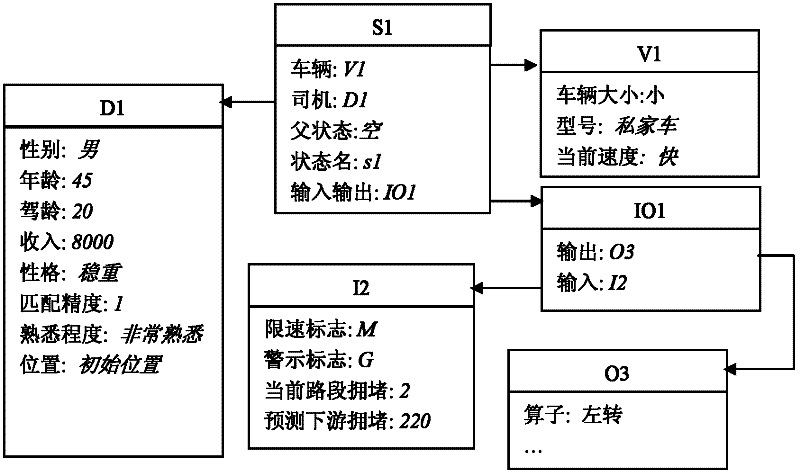
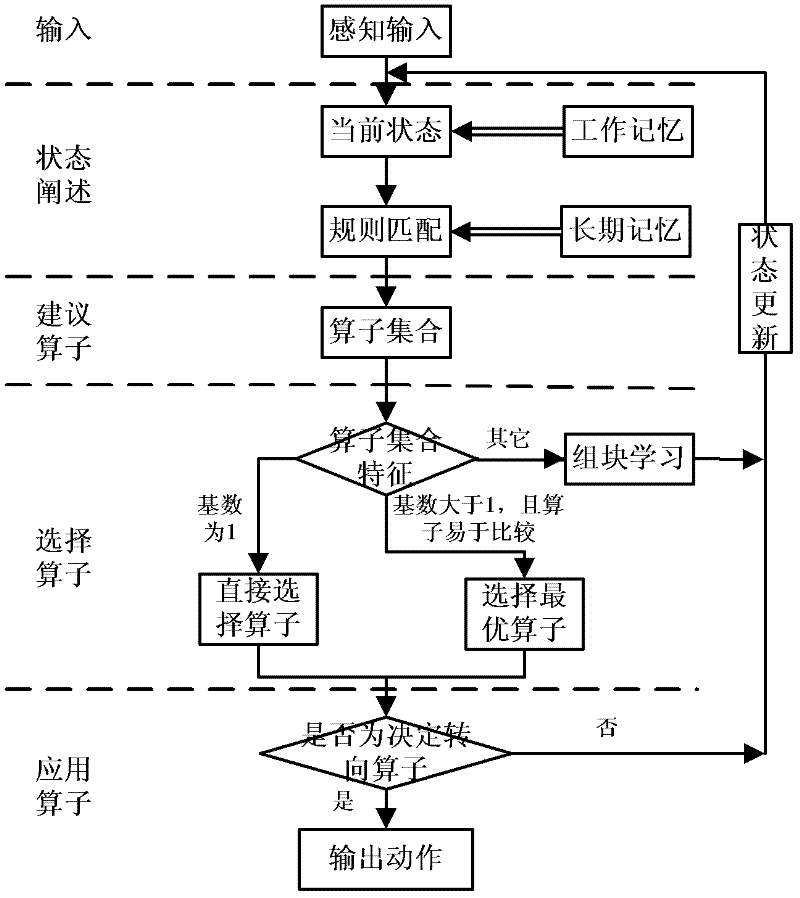
ActiveCN102505591AImprove calculation accuracyPlay a guiding roleRoadwaysTraffic capacityDriver/operator
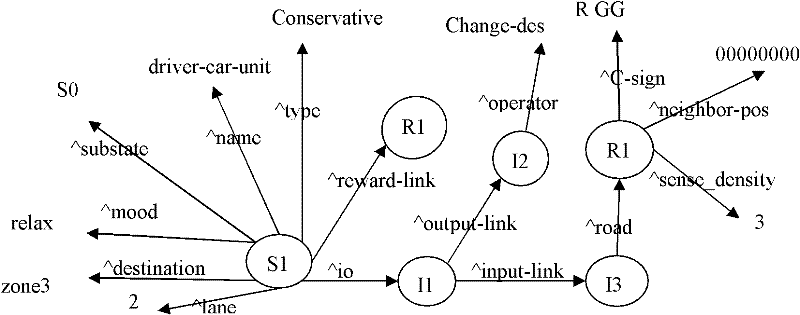
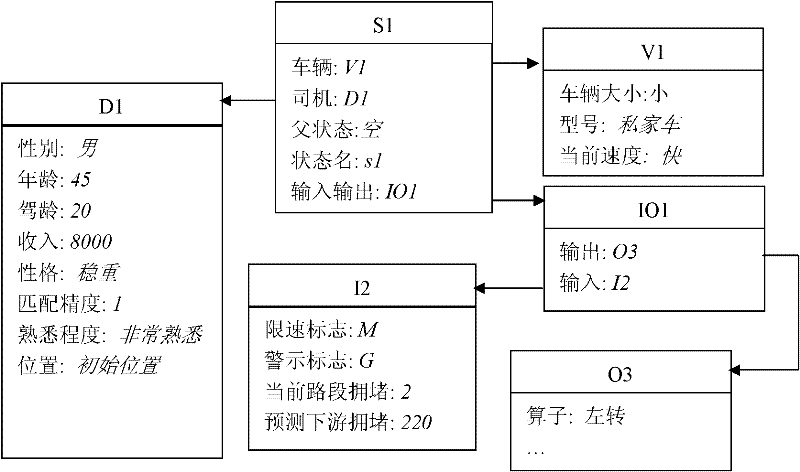
The invention belongs to the technical field of road design, which relates to a method for determining lengths of upstream transition regions of a construction operation area. The method comprises the steps of: firstly, designing a driver SOAR (state, operator and result) intelligent agent working memory structure, secondly, designing initial long-term memory rules, and establishing a long-term memory rule base of driver SOAR intelligent agent, thirdly, establishing the decision-making period of the driver SOAR intelligent agent, fourthly, establishing a method for evaluating the road network traffic capacity through road network balance degree, and fifthly, setting lengths of different upstream transition regions and different road load coefficients to perform simulation, to obtain the road network balance degree data under lengths of different upstream transition regions of the construction operation area through simulation, and selecting simulation conditions with high balance degrees and good astringency, to obtain lengths of the appropriate upstream transition regions of the construction operation area under different traffic conditions. The method can accurately reflect the influence on the road construction traffic capacity by the lengths of the upstream transition regions of the construction operation area, thereby determining the lengths of the upstream transition regions of the construction operation area.
Owner:TIANJIN MUNICIPAL ENG DESIGN & RES INST
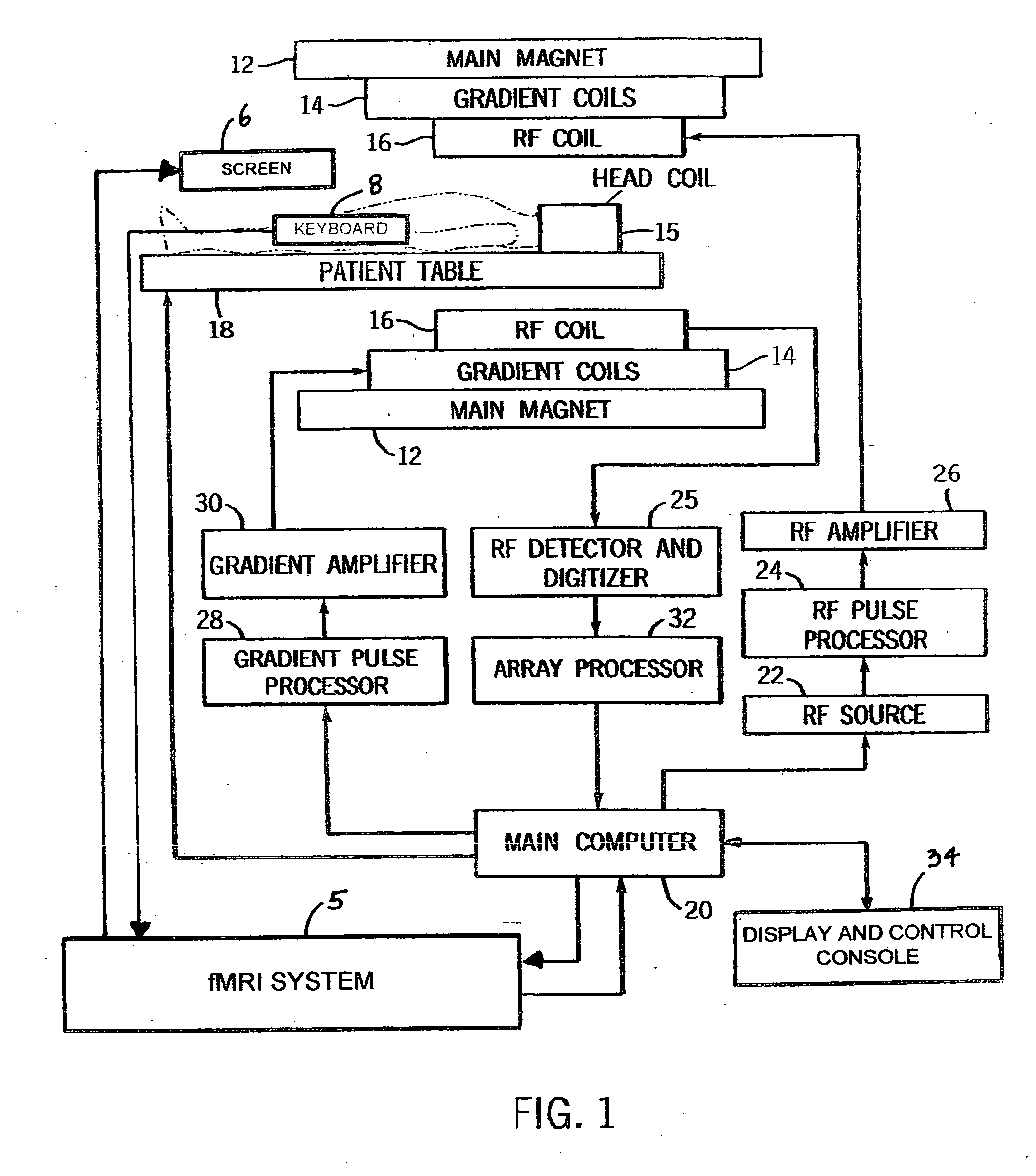
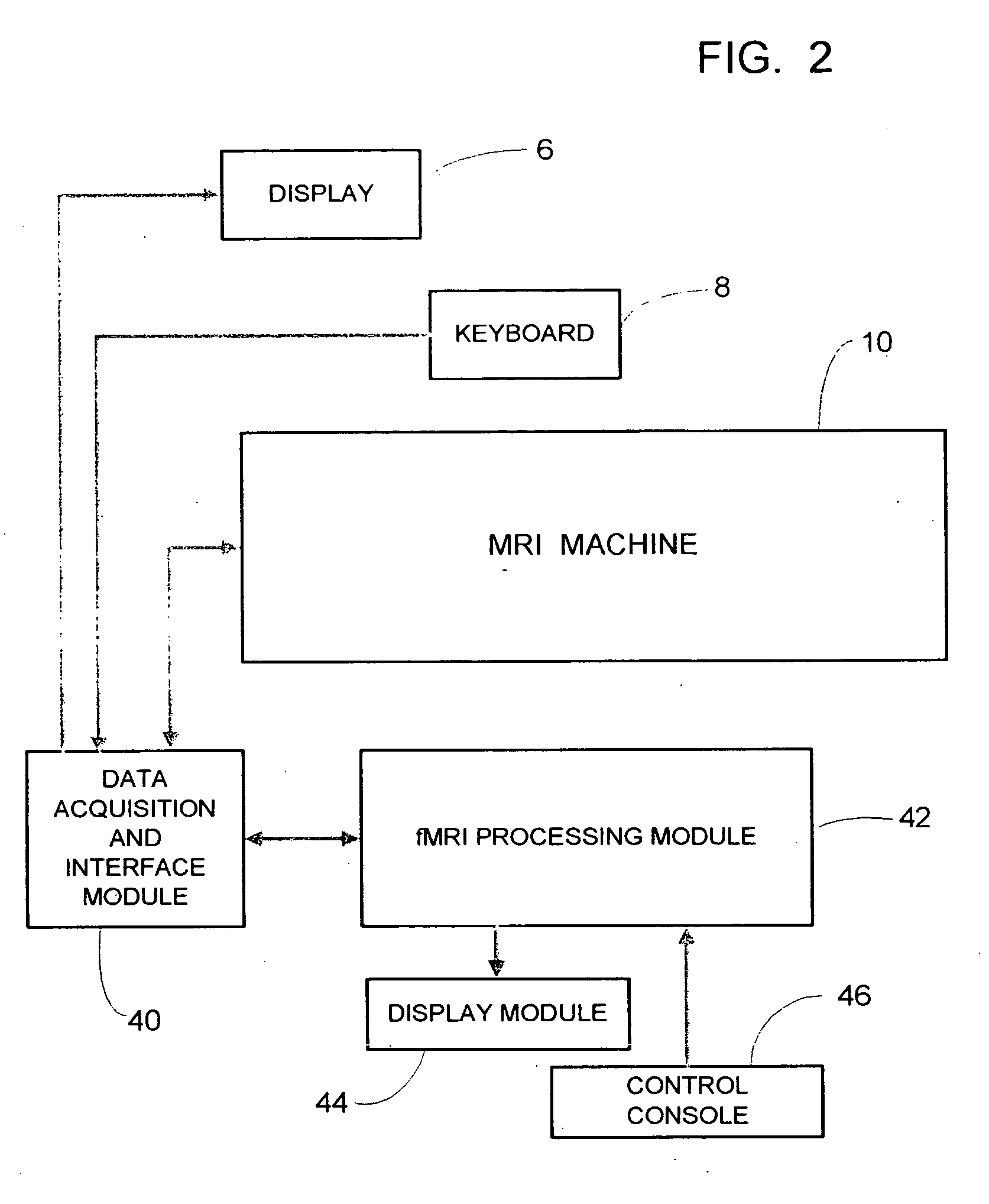
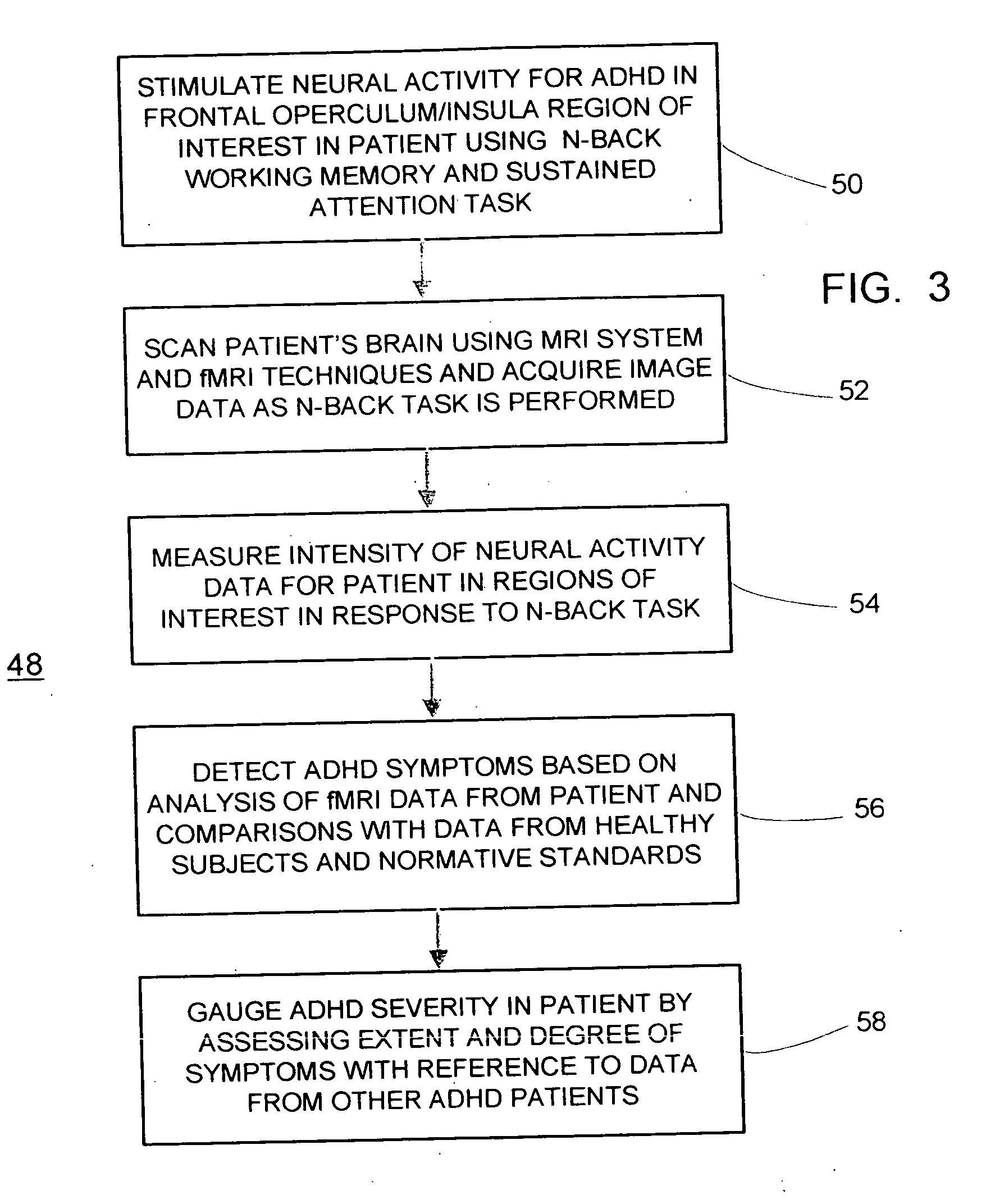
fMRI system for detecting symptoms associated with Attention Deficit Hyperactivity Disorder
InactiveUS20050267357A1Efficient and consistent and reliable mannerAccurate diagnosisComputer-assisted medical data acquisitionDiagnostic recording/measuringSustaining attentionPatients symptoms
A system based on the use of fMRI techniques for use in detecting neurological abnormalities indicative of Attention Deficit Hyperactivity Disorder (ADHD), in determining the severity of ADHD and in gauging the efficacy of medications used in treating ADHD. The system includes the steps of activating a selected region of the brain which is known to be affected by ADHD using a working memory and sustained attention task such as an N-Back task and concurrently acquiring fMRI image data responsive to the task. The patient's task-active fMRI data is then compared to reference fMRI data derived from a database of task-active fMRI data acquired from healthy individuals and determining whether the patient has symptoms related to ADHD. The extent of the patient's ADHD related symptoms and the severity of the disorder may also be assessed. Additionally, patients who are affected by ADHD may be administered medications intended to address their symptoms and based on comparing the severity of the patient's symptoms on and off therapy, the efficiency of the medication may be gauged and a measure may be provided of how well individual patients respond to a given medication.
Owner:RAO STEPHEN M +1
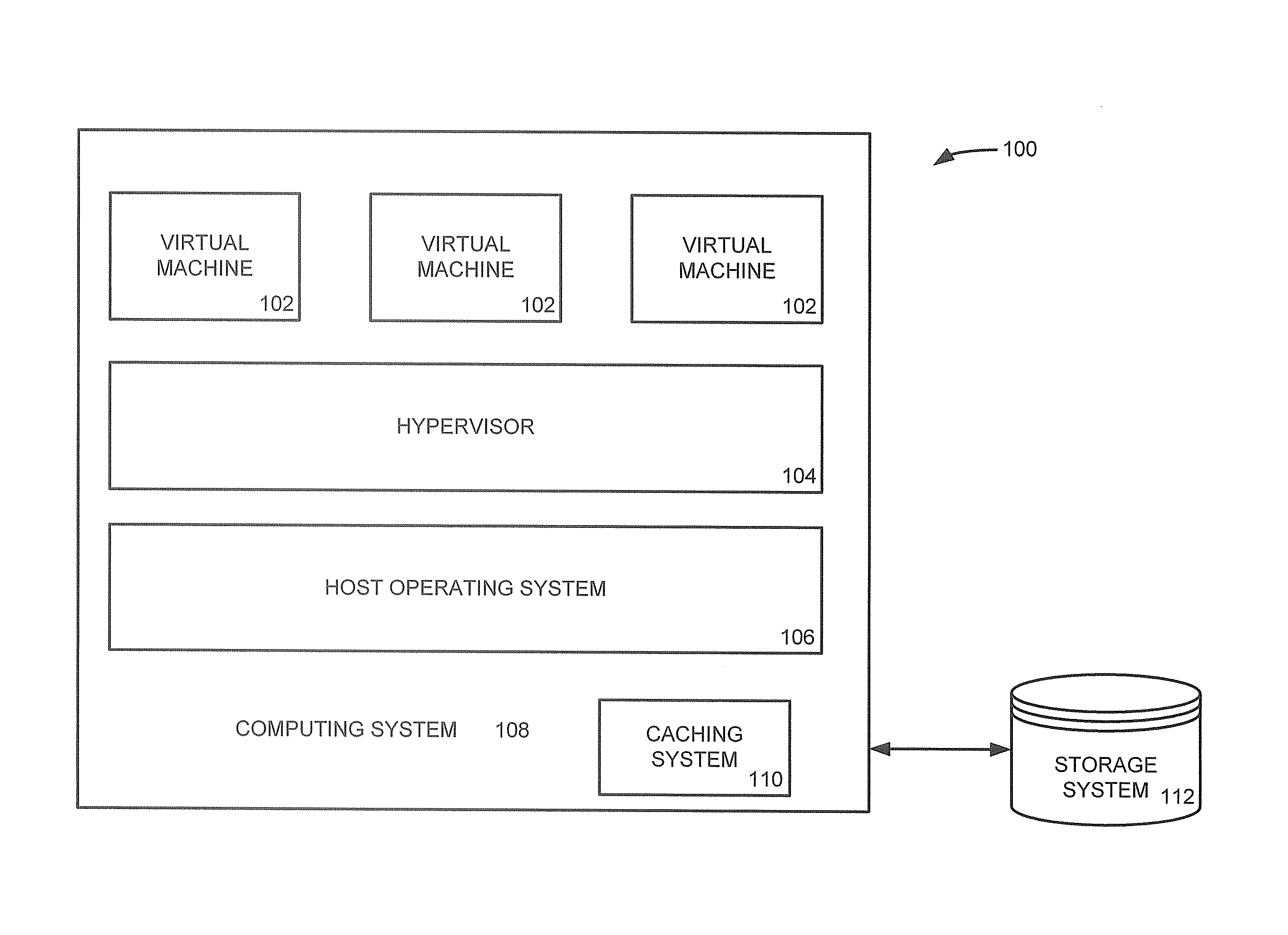
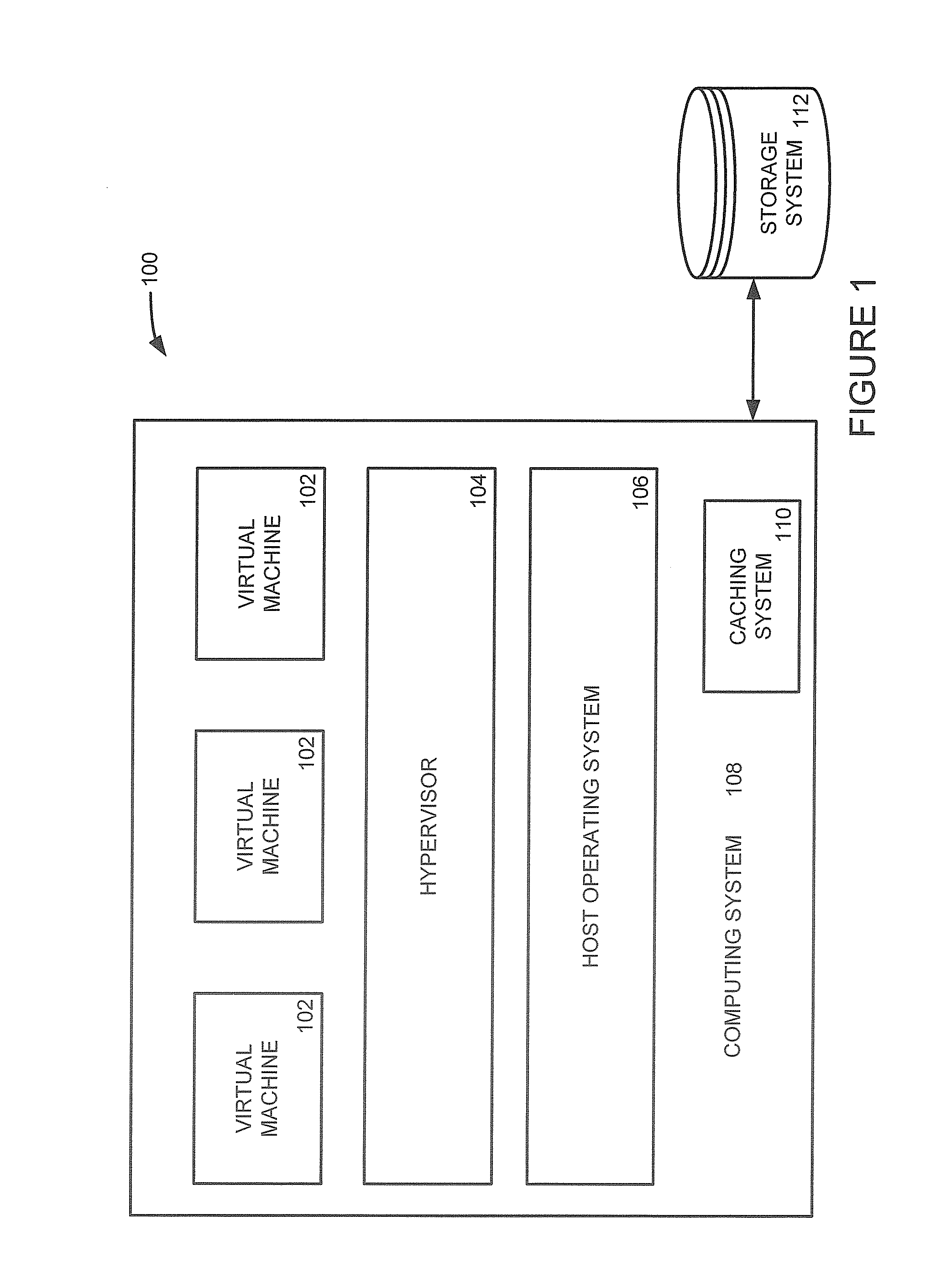
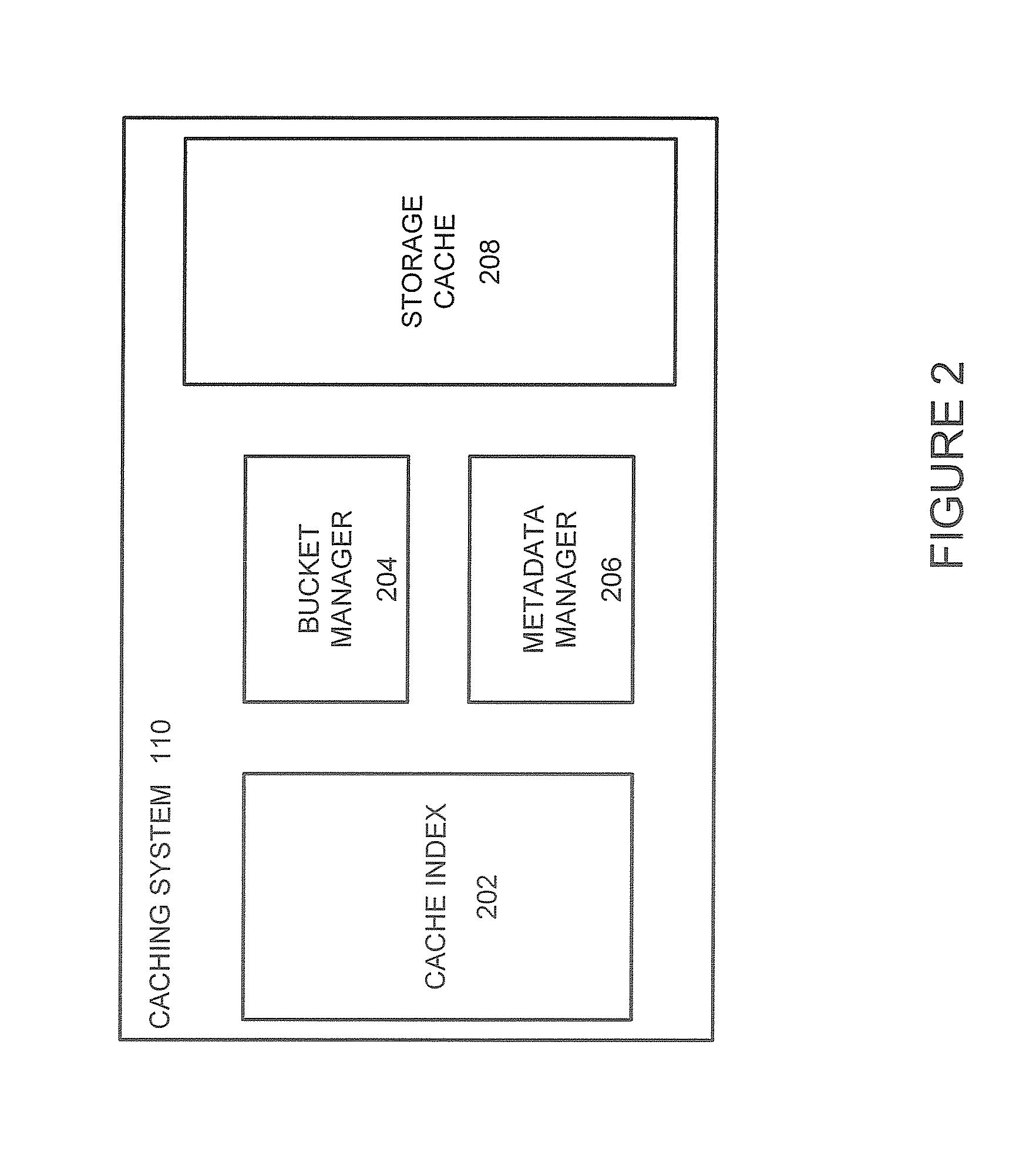
Systems and Methods to Manage Cache Data Storage in Working Memory of Computing System
ActiveUS20160041927A1Memory architecture accessing/allocationMemory adressing/allocation/relocationMetadata managementParallel computing
Systems and methods for managing records stored in a storage cache are provided. A cache index is created and maintained to track where records are stored in buckets in the storage cache. The cache index maps the memory locations of the cached records to the buckets in the cache storage and can be quickly traversed by a metadata manager to determine whether a requested record can be retrieved from the cache storage. Bucket addresses stored in the cache index include a generation number of the bucket that is used to determine whether the cached record is stale. The generation number allows a bucket manager to evict buckets in the cache without having to update the bucket addresses stored in the cache index. In an alternative embodiment, non-contiguous portions of computing system working memory are used to cache data instead of a dedicated storage cache.
Owner:PERNIXDATA
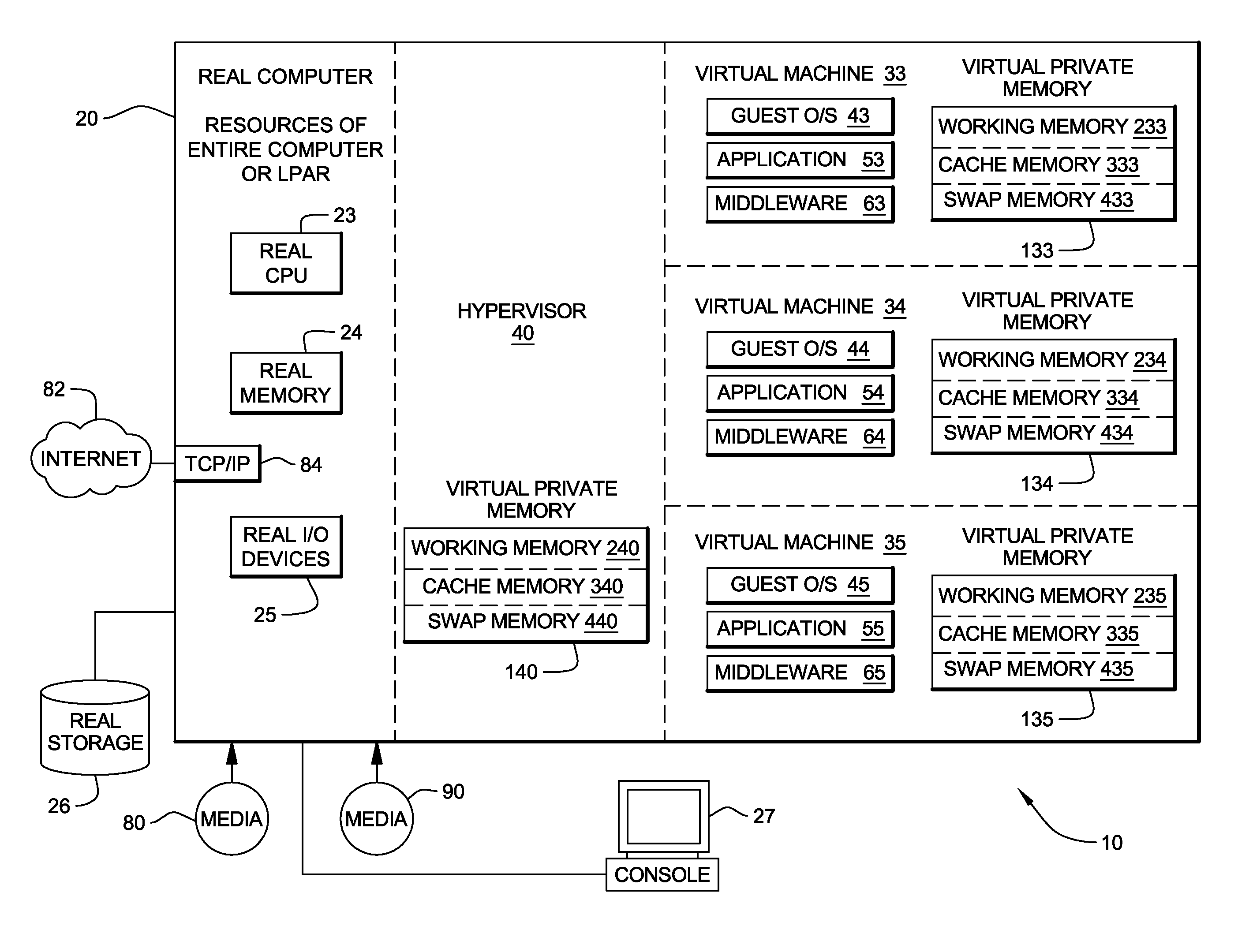
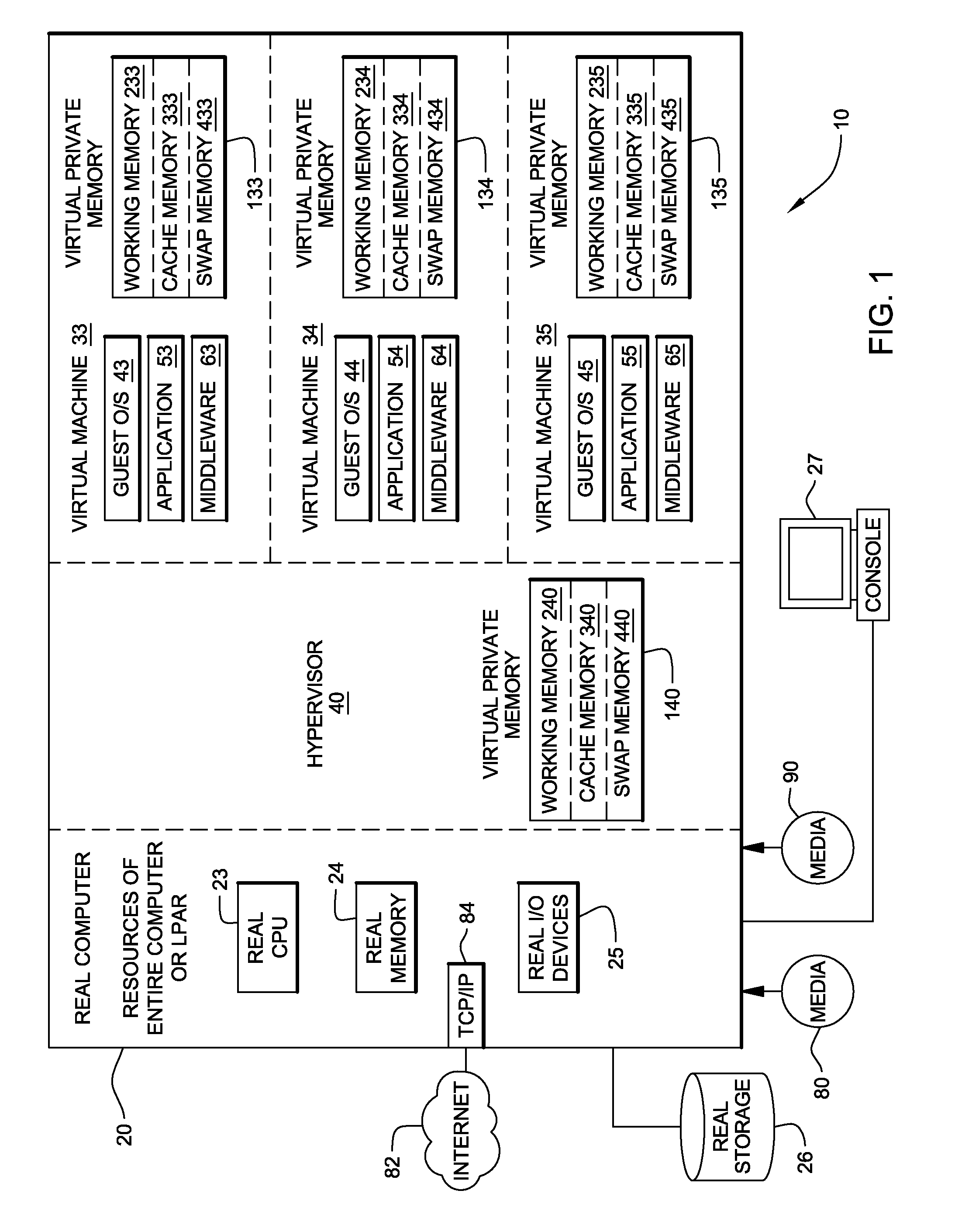
System, method and program to manage virtual memory allocated by a virtual machine control program
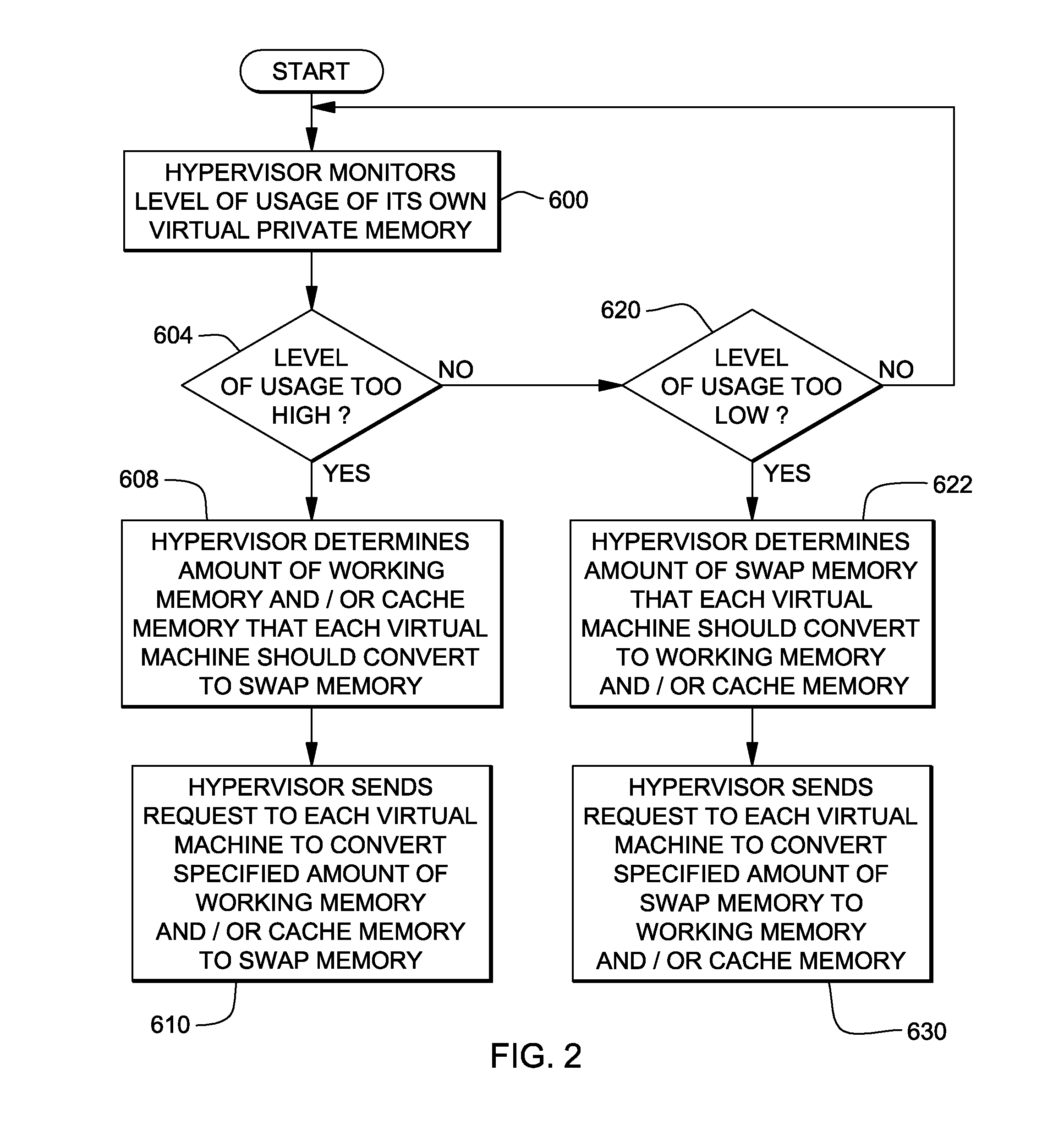
Management of virtual memory allocated by a virtual machine control program to a plurality of virtual machines. Each of the virtual machines has an allocation of virtual private memory divided into working memory, cache memory and swap memory. The virtual machine control program determines that it needs additional virtual memory allocation, and in response, makes respective requests to the virtual machines to convert some of their respective working memory and / or cache memory to swap memory. At another time, the virtual machine control program determines that it needs less virtual memory allocation, and in response, makes respective requests to the virtual machines to convert some of their respective swap memory to working memory and / or cache memory.
Owner:INT BUSINESS MASCH CORP
Cognitive training method and system for improving memory
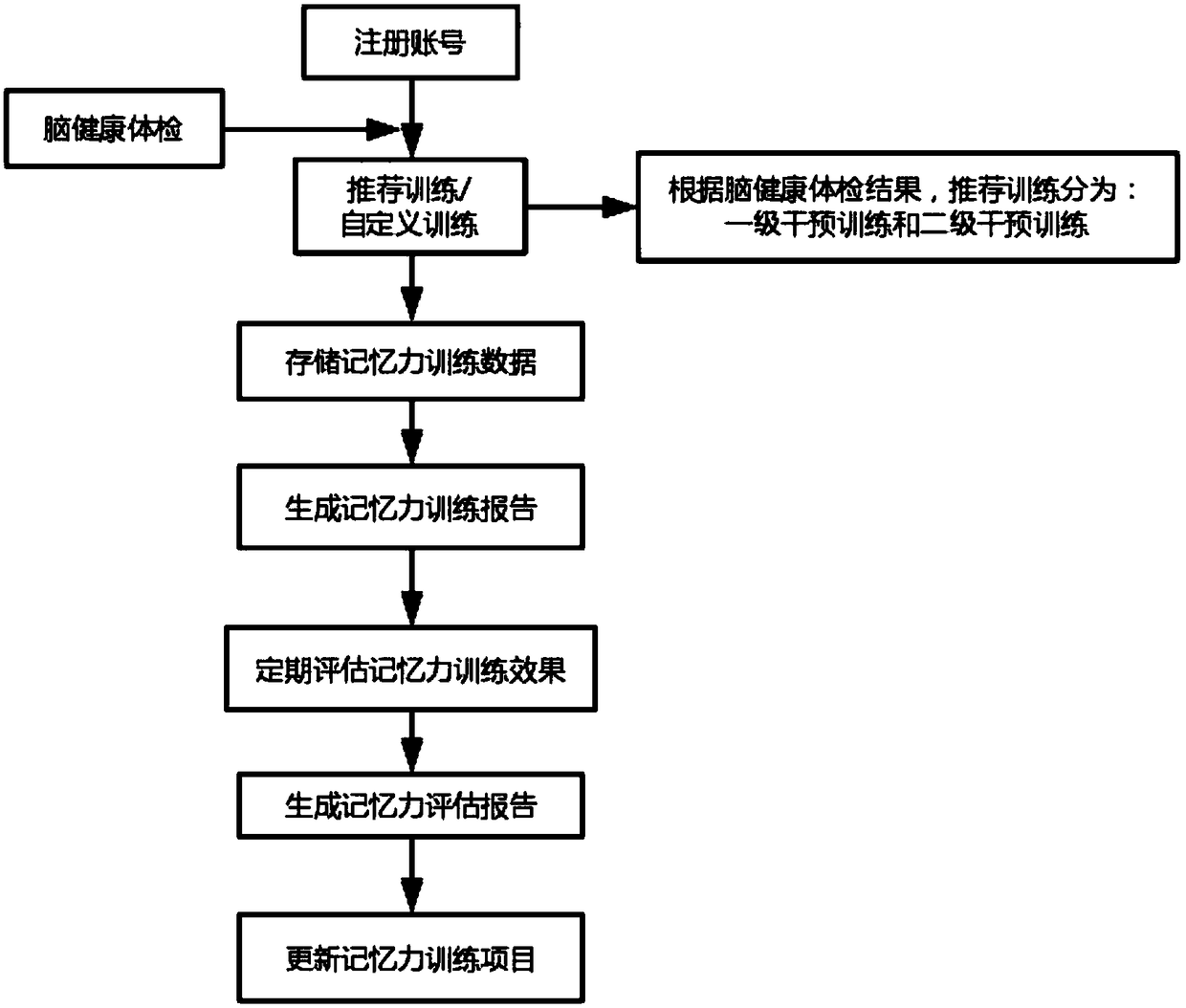
The invention relates to the field of cognitive rehabilitation training for brain health and provides a cognitive training method and system for improving memory. The training method comprises the following steps: the personal information of a user is inputted for account registration; a corresponding training mode is selected for training according to the cognitive disability level of the user; the data generated in the training process and the personal information of the user are stored in a database, and a training report is generated; and the cognitive ability of the user is evaluated after a training cycle is completed, and a training project is updated. Based on the cognitive impairment characteristics, the occurrence regularity and the nerve plasticity of dementia, the method and the system provided by the invention are researched and developed on the basis of multiple classical experimental paradigms of cognitive psychology, both interestingness and playability are considered,elements of traditional Chinese culture and the like are incorporated, and scientific and effective individualized and intelligent training is carried out on the memory (situational memory, working memory and the like) of people with chief complaint cognitive impairment and mild cognitive impairment and at risk of dementia.
Owner:北京京师脑力科技有限公司
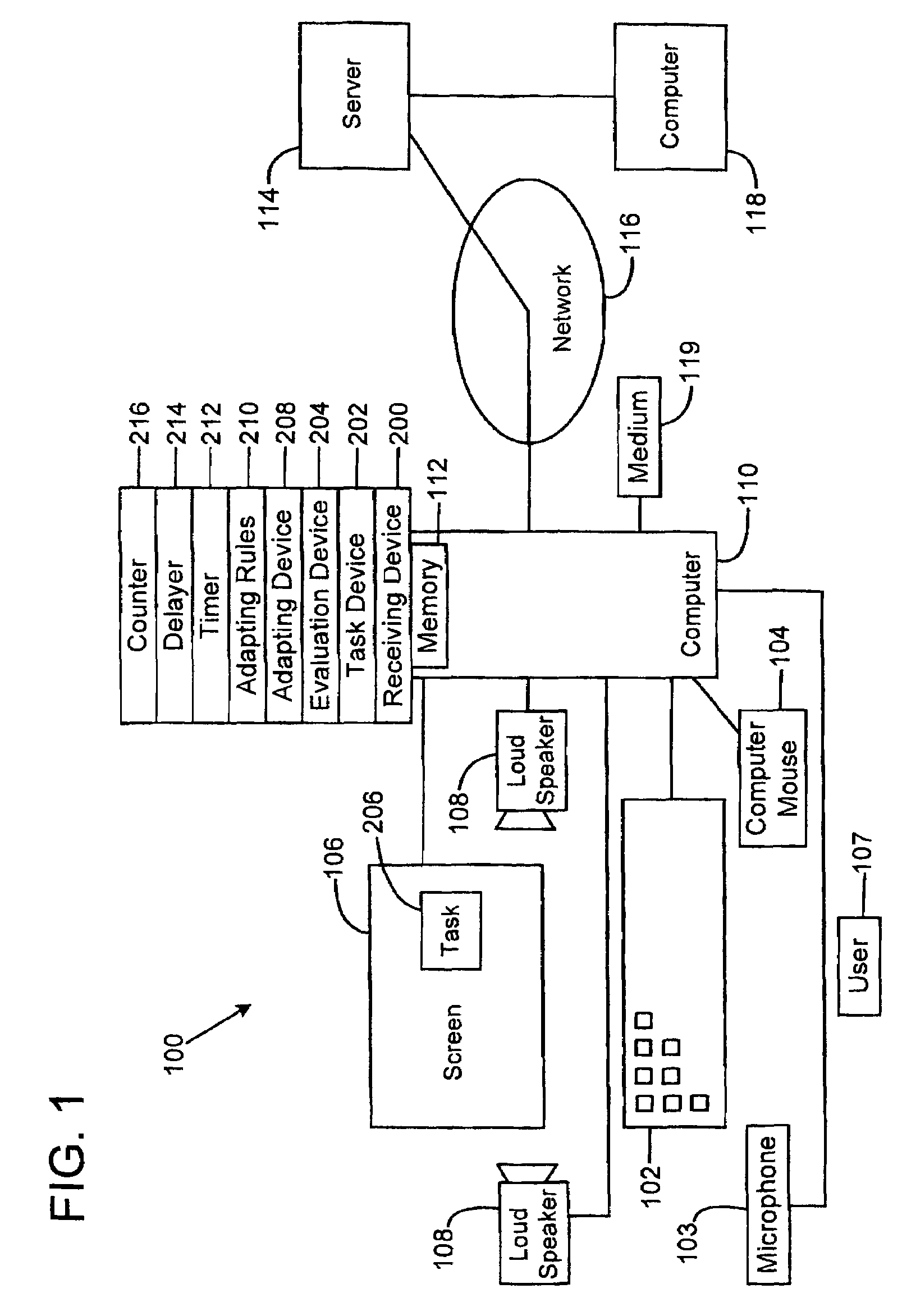
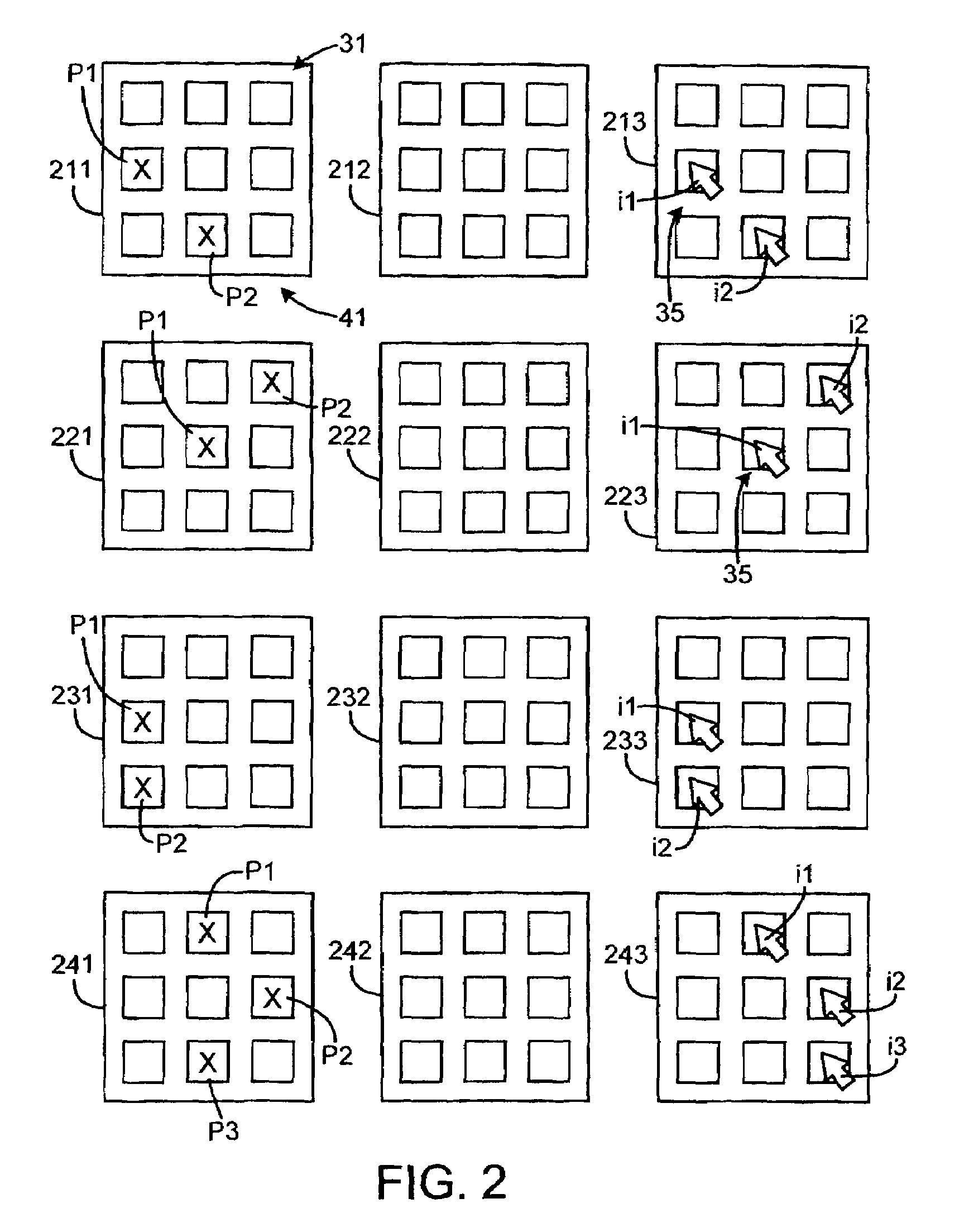
System and method for improving memory capacity of a user
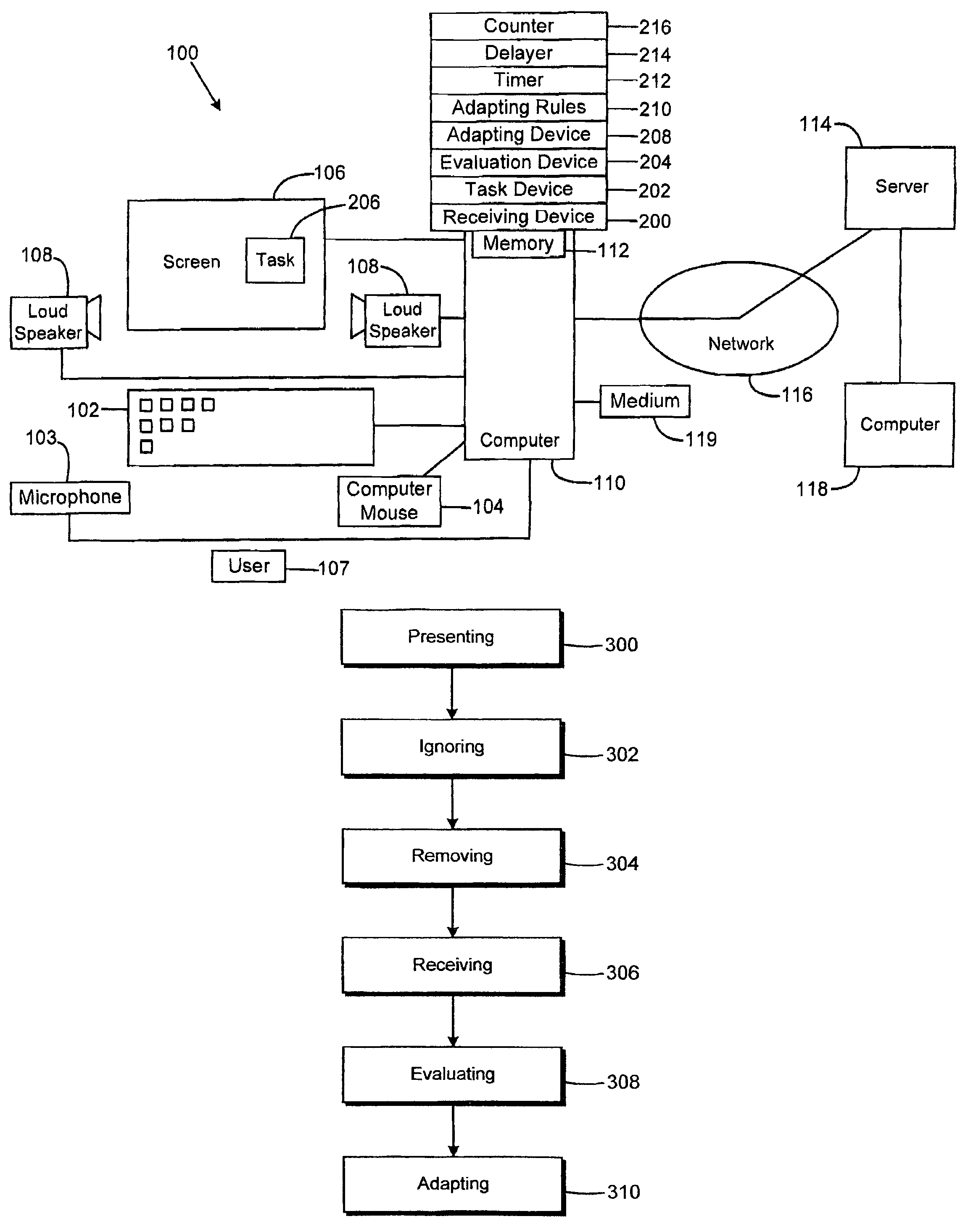
The computer training system is for training working memory capacity of a user of a computer within the system. A computer program is used within the system. A first task of a first difficulty level is presented to the user. A delay of a predetermined time is performed, during which delay the task is not visible or audible to the user. During the delay it is not possible to enter an answer into the computer. The difficulty level of a subsequent task to be presented to the user is changed in accordance with predetermined adaptation rules and the evaluation such that the difficulty level of the subsequent task approaches the memory capacity of the user. Subsequent tasks are presented to the user until a predetermined time limit is exceeded or until a predetermined number of tasks have been performed.
Owner:NEURAL ASSEMBLY INT AB
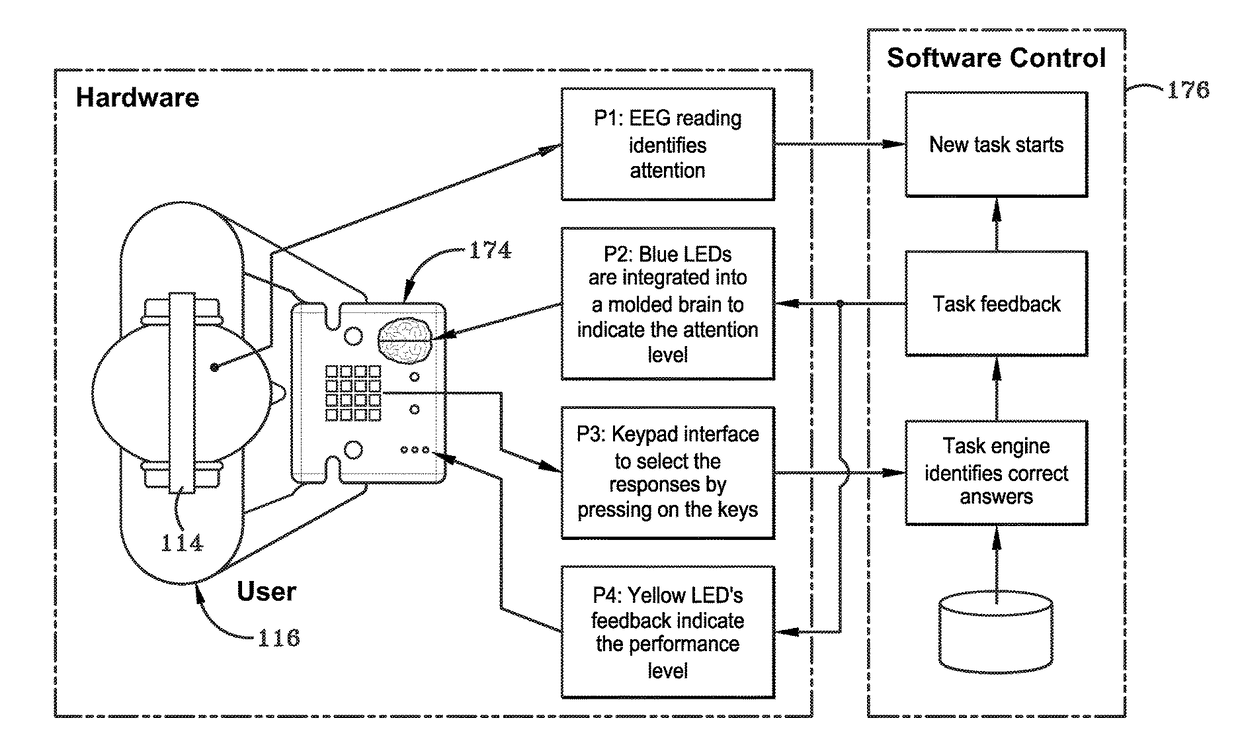
Interactive brain trainer
InactiveUS20170337834A1Improve concentrationNot alleviating taskElectroencephalographySensorsCentral databaseCerebrum
A brain training system and method are provided that incorporates a first phase and a second phase of brain training. The first phase is designed to increase attention by requiring the completion of an attention-based activity or task. This may require the identification of match or mismatched images. The second phase is designed to increase working memory by requiring the completion of a working memory-based task that requires the repetition of an illumination sequence. Each phase may be implemented in a self-contained handheld device, similar to the shape of a tablet, or may be implemented in a computer application, such as software. The answers of each phase are recorded in a central database and the system may provide recommendations based on the answers.
Owner:SHINDI RAJAA
Cognitive mapping using transcranial magnetic stimulation
The present invention relates to the field of mapping cognitive brain functions, more specifically to non-invasive systems for and methods of cognitive mapping. Examples of cognitive brain function which can reliably be mapped according to embodiments of the present invention are speech, language, working-memory and decision-making. According to certain embodiments, navigated Transcranial Magnetic Stimulation (TMS) is utilized along with accurate baseline determination in order to provide accurate, non-invasive cognitive mapping.
Owner:NEXDIM GMBH & CO KG
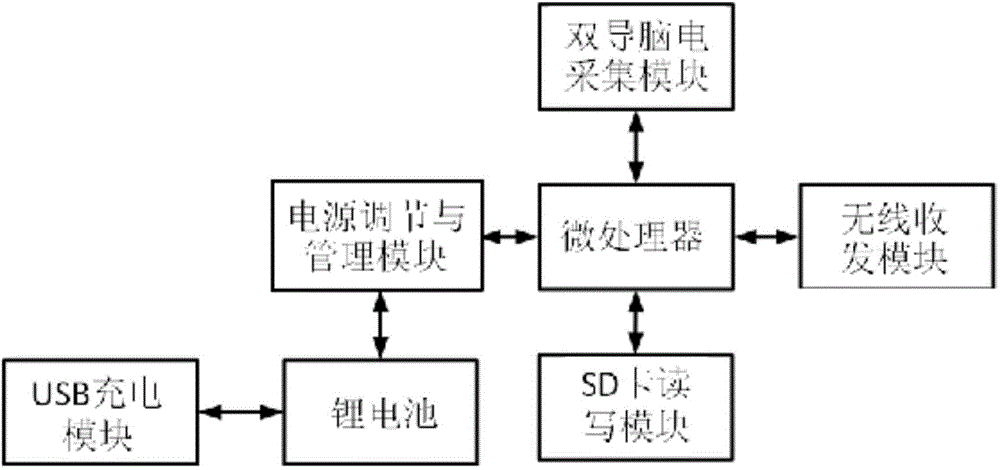
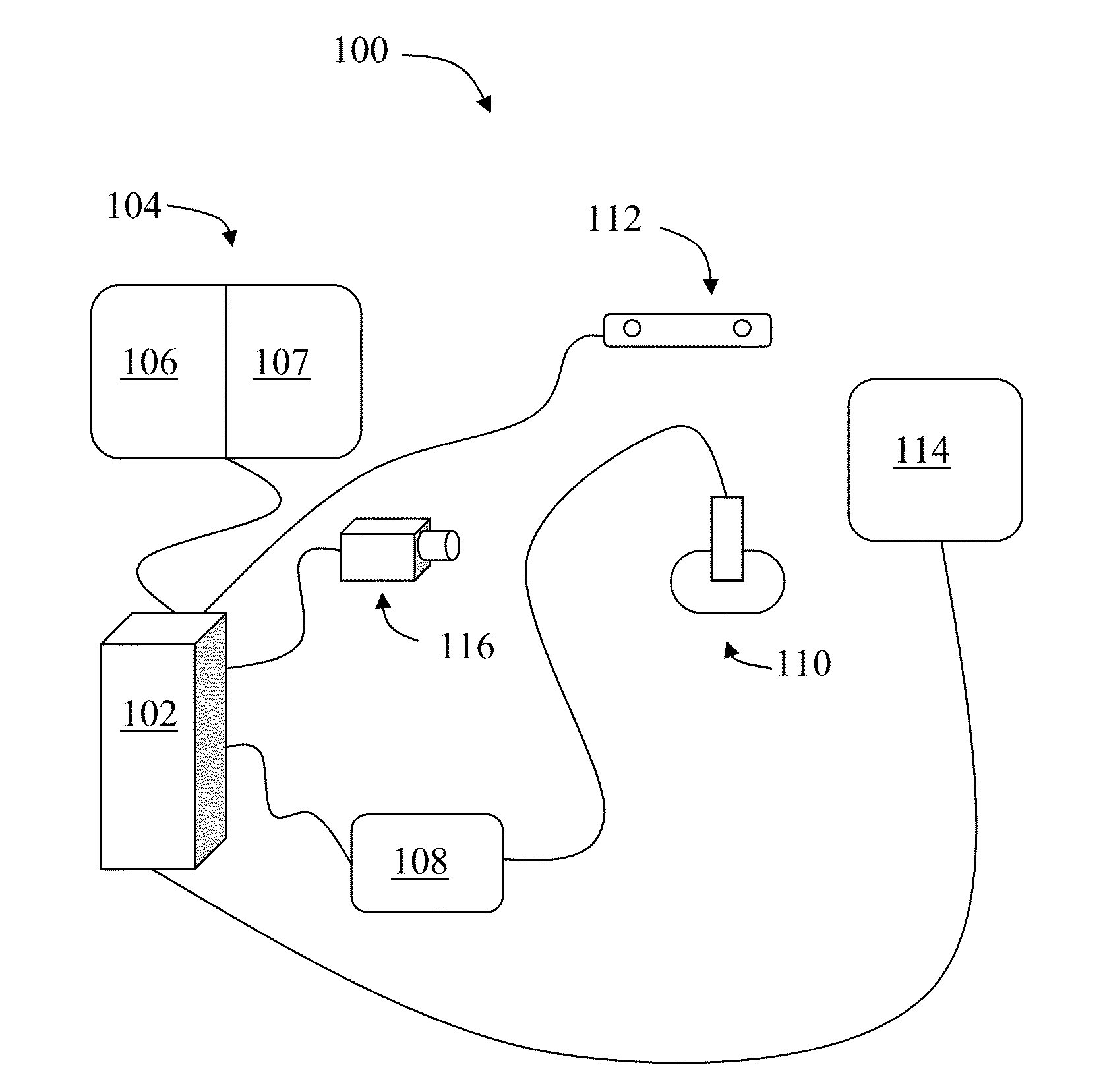
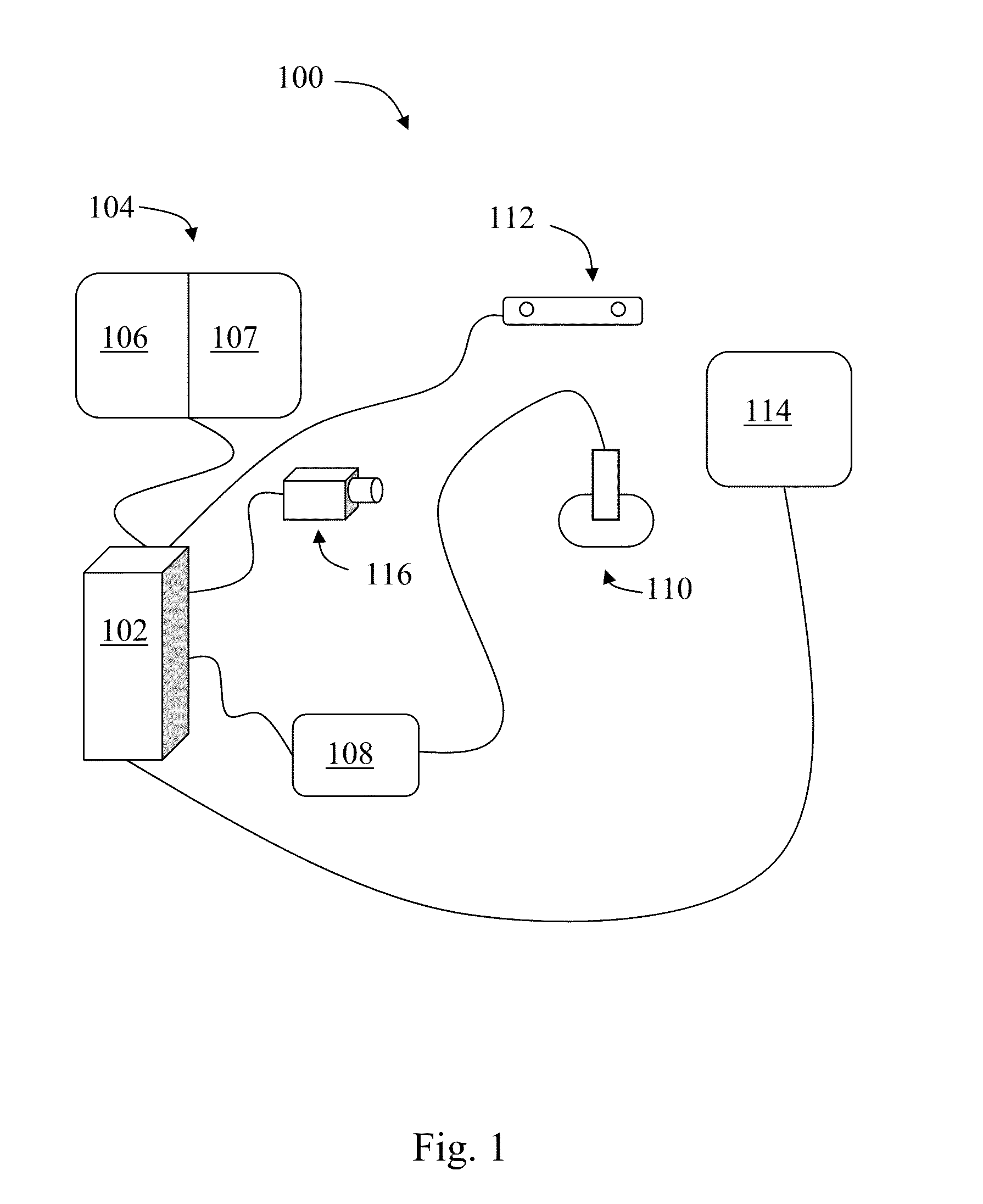
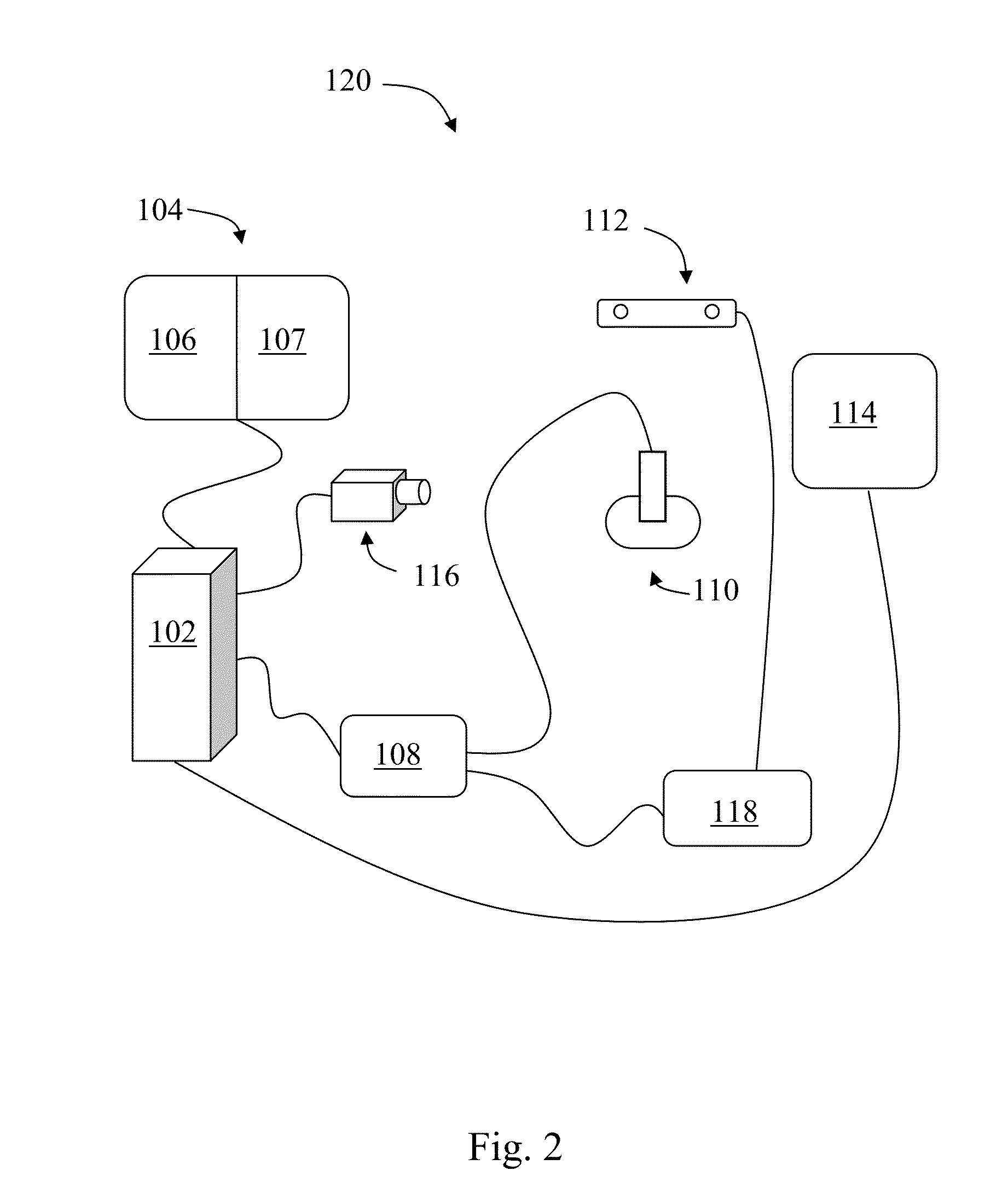
Portable working memory evaluation and training device
InactiveCN104306006AOvercome only bluetoothOvercome wifiSensorsPsychotechnic devicesTablet computerLearning disability
The invention discloses a portable working memory evaluation and training device. The portable working memory evaluation and training device comprises a tablet computer, a wireless signal repeater, a portable electrocerebral acquisition and analysis system and a cloud server, wherein the tablet computer is respectively and bi-directionally communicated with the portable electrocerebral acquisition and analysis system and the cloud server through the wireless signal repeater; the wireless signal repeater is connected with an input-output data interface of the tablet computer; the cloud server reads the data in the tablet computer through the wireless signal repeater. By adopting the portable working memory evaluation and training device, not only can the evaluation and training problem of the working memory skill of children aged from 3 to 6 and special children (such as hyperactivity children, autism children and learning disability children) be solved, but also the intellectual deterioration of the elderly can be delayed, the applicability is wide, and the market prospect is wide.
Owner:SOUTHEAST UNIV
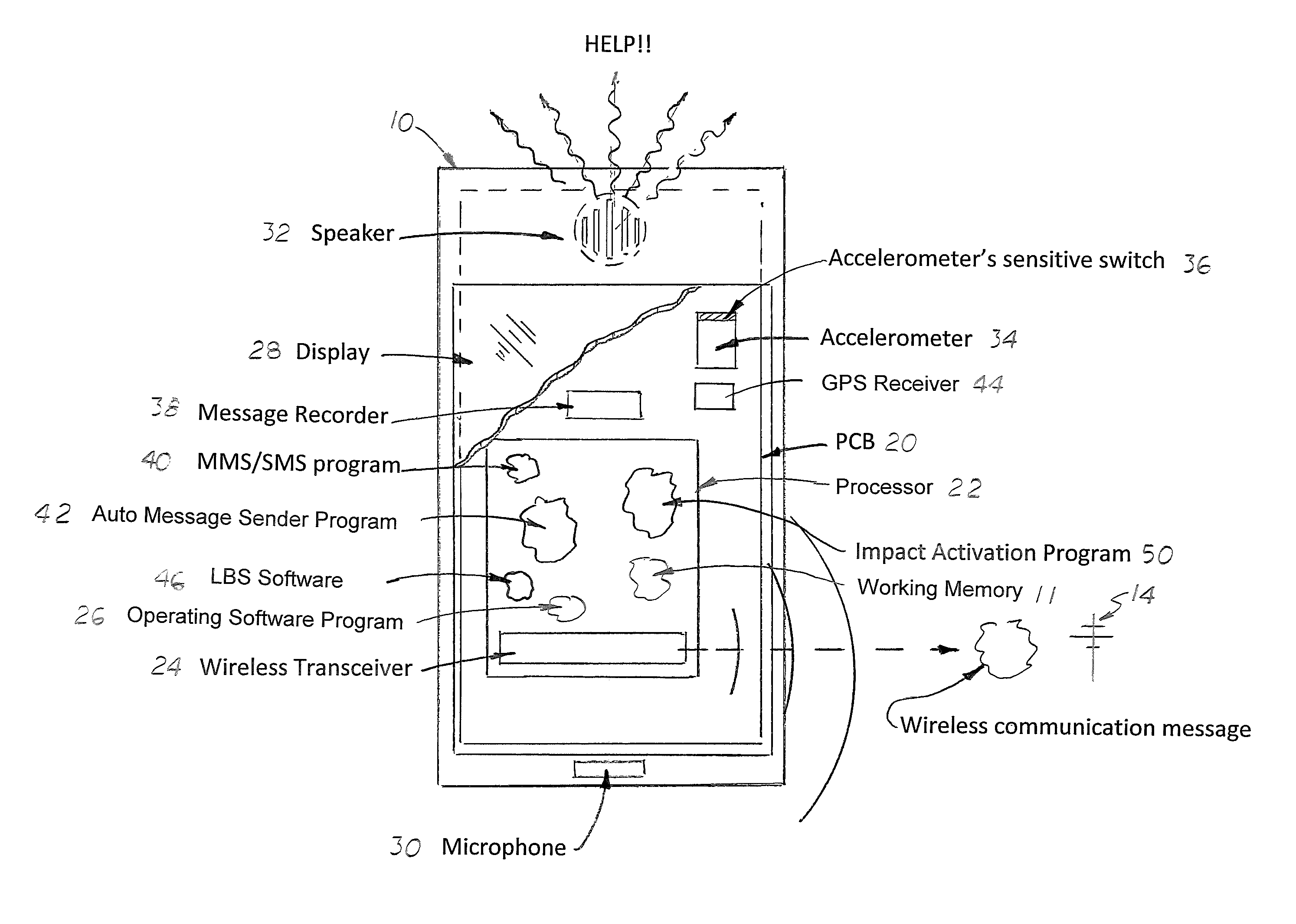
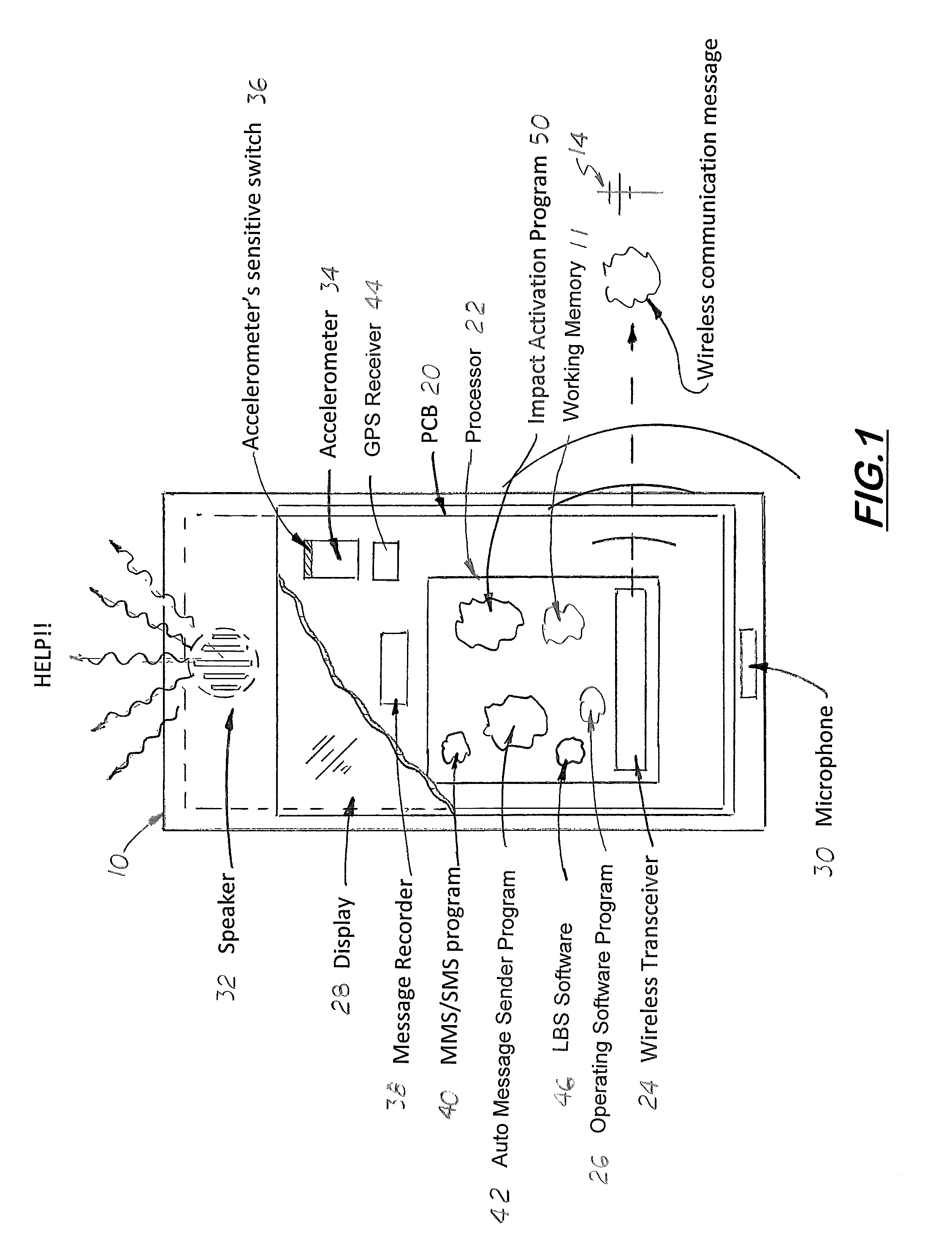
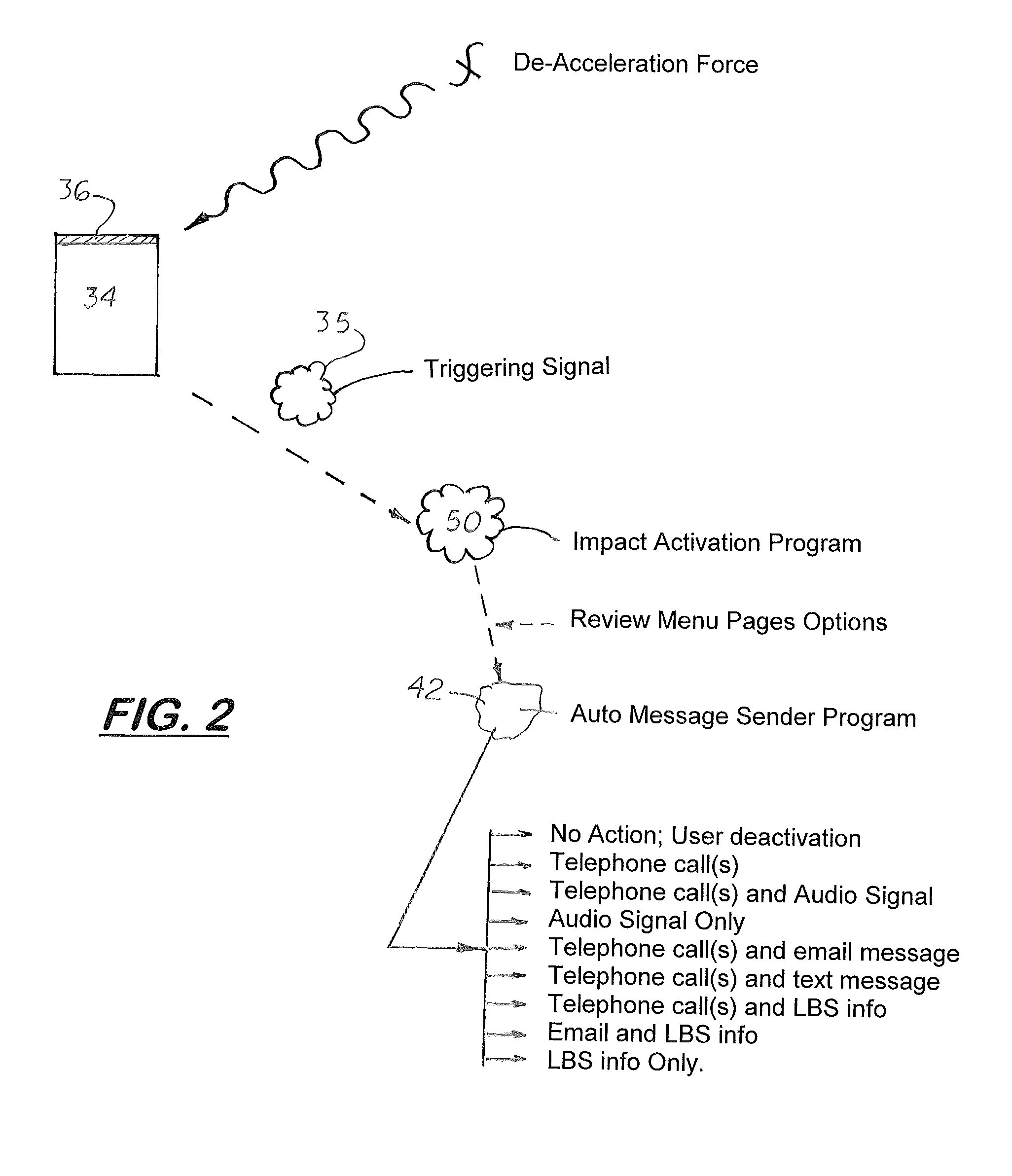
Mobile telephone sudden impact warning and reporting feature
A warning system for wireless mobile telephones that notifies designated users and broadcast an audible sound when suddenly de-acceleration. The telephone is coupled to a wireless telephone transmitter configured to operate with a nearby compatible wireless telephone network. The telephone includes a display, a speaker, an internal accelerometer and a programmable, impact-activated software program loaded into its working memory. The software program when executed continuously monitors for triggering signals from the internal accelerometer. When a triggering signal is produced, the software program is activated into an alarm state which then performs the notifications tasks designated by the user during the setup steps. The software program is configured to presents various input menus on the display that enables the user to turn the system ON and OFF, selective an alarm mode to be used, select a pre-alarm time period, an alarm duration period, and adjust the sensitivity of the accelerometer.
Owner:CHUN JAMES
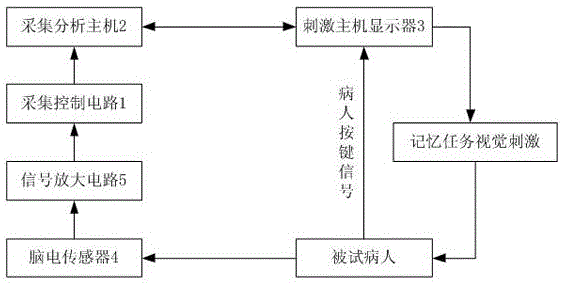
Cognitive disorder electroencephalogram recognition system
InactiveCN105147282AQuantifiableEasy to implementDiagnostic recording/measuringSensorsDisplay deviceUSB
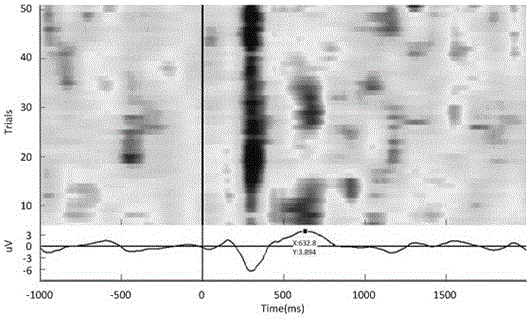
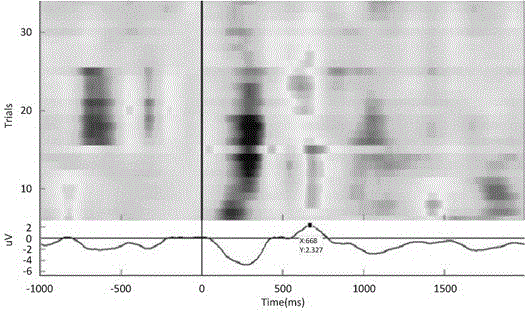
A cognitive disorder electroencephalogram recognition system comprises an electroencephalogram acquisition circuit, an acquisition control circuit connected with the electroencephalogram acquisition circuit via optical fibers, an acquisition analysis host connected with the acquisition control circuit via a USB port, wherein the acquisition control circuit is configured to send signals received via the optical fibers to the acquisition analysis host through the USB port, a stimulation host display used for providing stimulation signals used for inducting changes of electroencephalogram to a patient, a photosensitive detector mounted to the stimulation host display and used for detecting the stimulation signals together with the electroencephalogram. The photosensitive detector is configured to send the detected stimulation signals to the acquisition analysis host. The acquisition analysis host is configured to extract cognition potential P300 in electroencephalograms in 1-back tasks of work memory of a normal contrast and an apoplexy patient as classification features, and send the classification features to an ensemble learning classifier of a support vector machine to classify the normal contrast and the apoplexy patient. The cognitive disorder electroencephalogram recognition system is available for quantification, easy to achieve and high in precision.
Owner:SHANGHAI UNIV OF MEDICINE & HEALTH SCI
Cognitive mapping using transcranial magnetic stimulation
ActiveUS20130338483A1Accurate mappingMagnetotherapy using coils/electromagnetsDiagnostic recording/measuringMedicineBrain function
The present invention relates to the field of mapping cognitive brain functions, more specifically to non-invasive systems for and methods of cognitive mapping. Examples of cognitive brain function which can reliably be mapped according to embodiments of the present invention are speech, language, working-memory and decision-making. According to certain embodiments, navigated Transcranial Magnetic Stimulation (TMS) is utilized along with accurate baseline determination in order to provide accurate, non-invasive cognitive mapping.
Owner:NEXSTIM
Capturing replayable information at software defect locations in a multi-tenant environment
ActiveUS8726240B2Error detection/correctionSpecific program execution arrangementsParallel computingLong-term memory
A method for software debugging in a multi-tenant database network system is provided. When an exception occurs the stack frames in temporary working memory are dumped into long term memory for later analysis. A stack trace is performed from which performance information may be derived, which may aid in discovering the cause of the exception.
Owner:SALESFORCE COM INC
Method for confirming set positions of speed limit signs and size of speed limit during road construction
ActiveCN102505644AAccurately describe complex driving behaviorTraffic signalsRoad signsTraffic capacityLTM - Long-term memory
The invention belongs to the technical field of road design, and relates to a method for confirming set positions of speed limit signs and size of speed limit during road construction, and the method comprises the following steps of: (1) designing a working memory structure of a driver SOAR intellectual body; (2) designing an initial long-term memory rule, and building a long-term memory rule base of the driver SOAR intellectual body; (3) building a decision period of the driver SOAR intellectual body; and (4) setting the set positions of the different speed limit signs, the size of speed limit, and different road loading coefficients so as to perform simulation, judging traffic conflict and severity degree according to overlapping degree of road cells which are occupied by a current vehicle and adjoining vehicles, selecting a simulation condition with the lower traffic conflict and severity degree, and obtaining the set positions of the speed limit signs and the size of the speed limit within a proper construction operation area under different traffic conditions. The method can be used for more accurately reflecting the influence of the set positions of the speed limit signs and the size of the speed limit on the traffic capacity during road construction, thus providing the method for setting the speed limit signs during road construction.
Owner:TIANJIN MUNICIPAL ENG DESIGN & RES INST
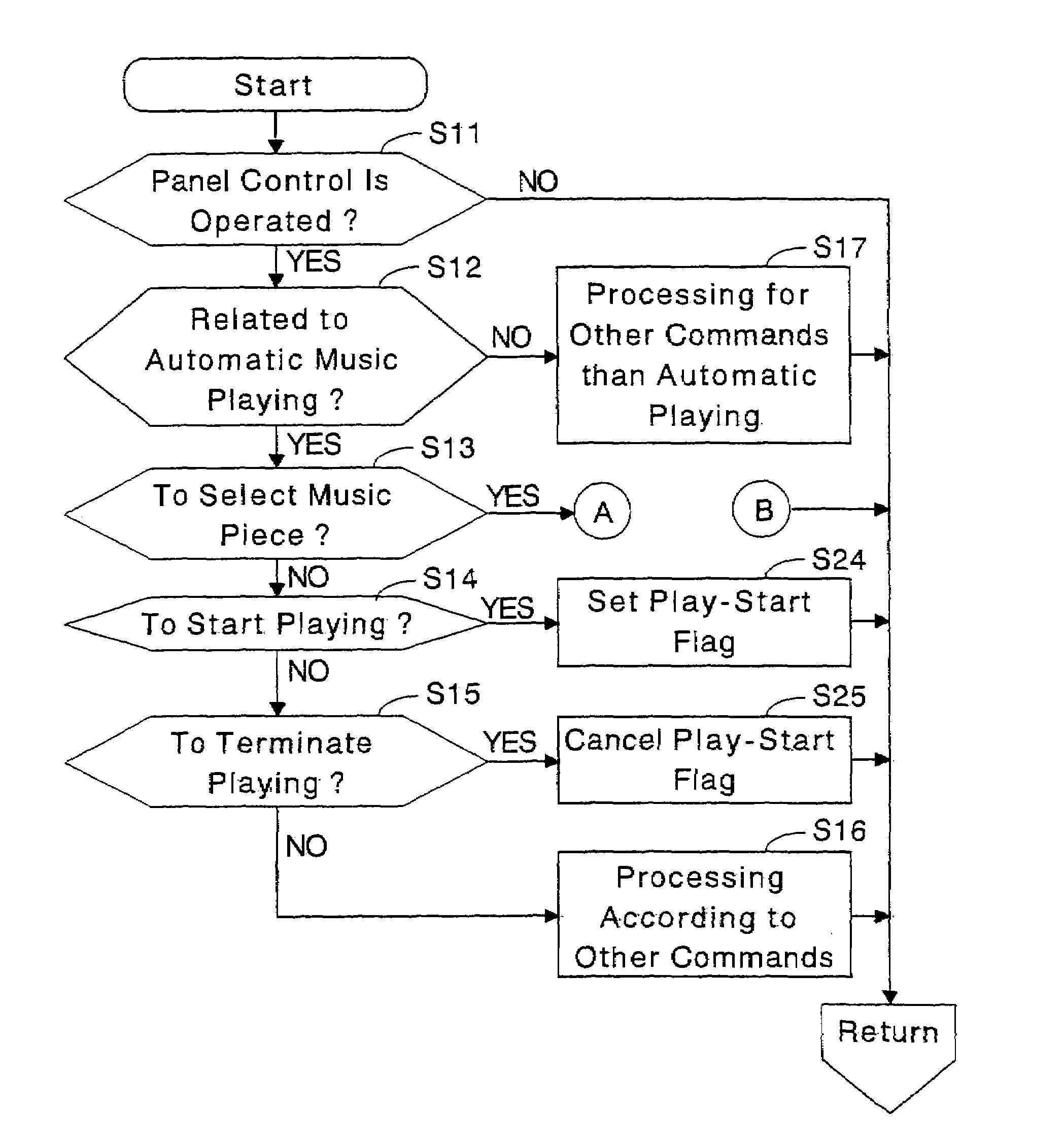
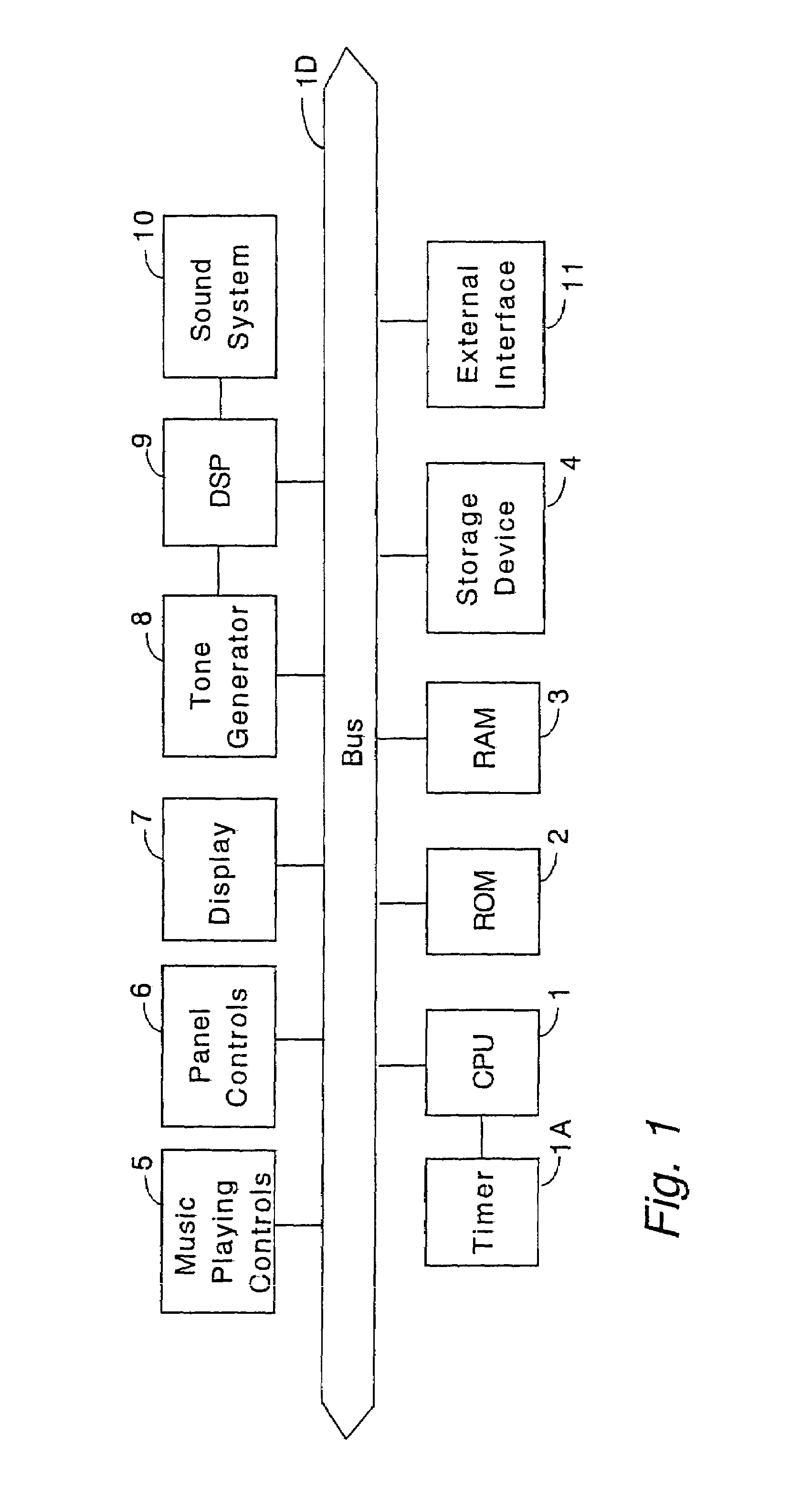
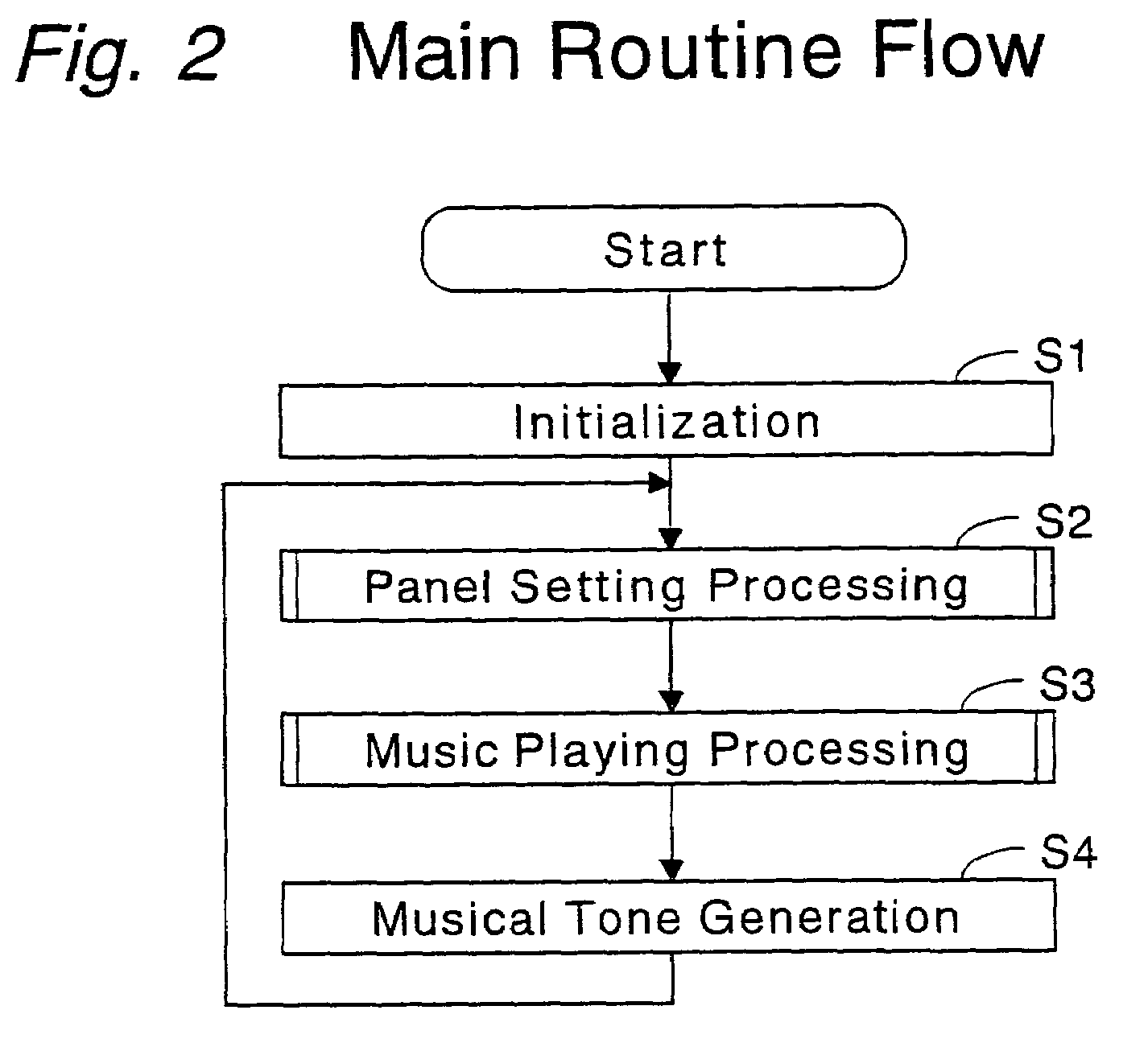
Automatic music playing apparatus and computer program therefor
An external storage device stores automatic music playing data files, each file including data of a progression of musical notes constituting a performance of a music piece, and registration data files, each file including data of a set of parameters to determine the conditions for the performance of the music piece. While an automatic music playing data file of a piece of music and registration data files are loaded into a working memory and are being processed to play the current piece of music automatically, the next automatic music playing data file of the next piece of music to be played and the registration data files to be used next are prefetched from the external storage device into an internal storage device temporarily to be prepared for being transferred to the working memory for the successive automatic music playing after the automatic playing of the current music piece is over. Thus, dead time between the adjacent pieces of automatically played music and delay in effectuating the registrations will be avoided.
Owner:YAMAHA CORP
Device for determining a hemodynamic parameter
Owner:PULSION MEDICAL SYSTEMS SE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com