Patents
Literature
292 results about "Work memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Working memory involves the conscious processing and managing of information required to carry out complex cognitive tasks such as learning, reasoning, and comprehension. It has been described as the brain's conductor.
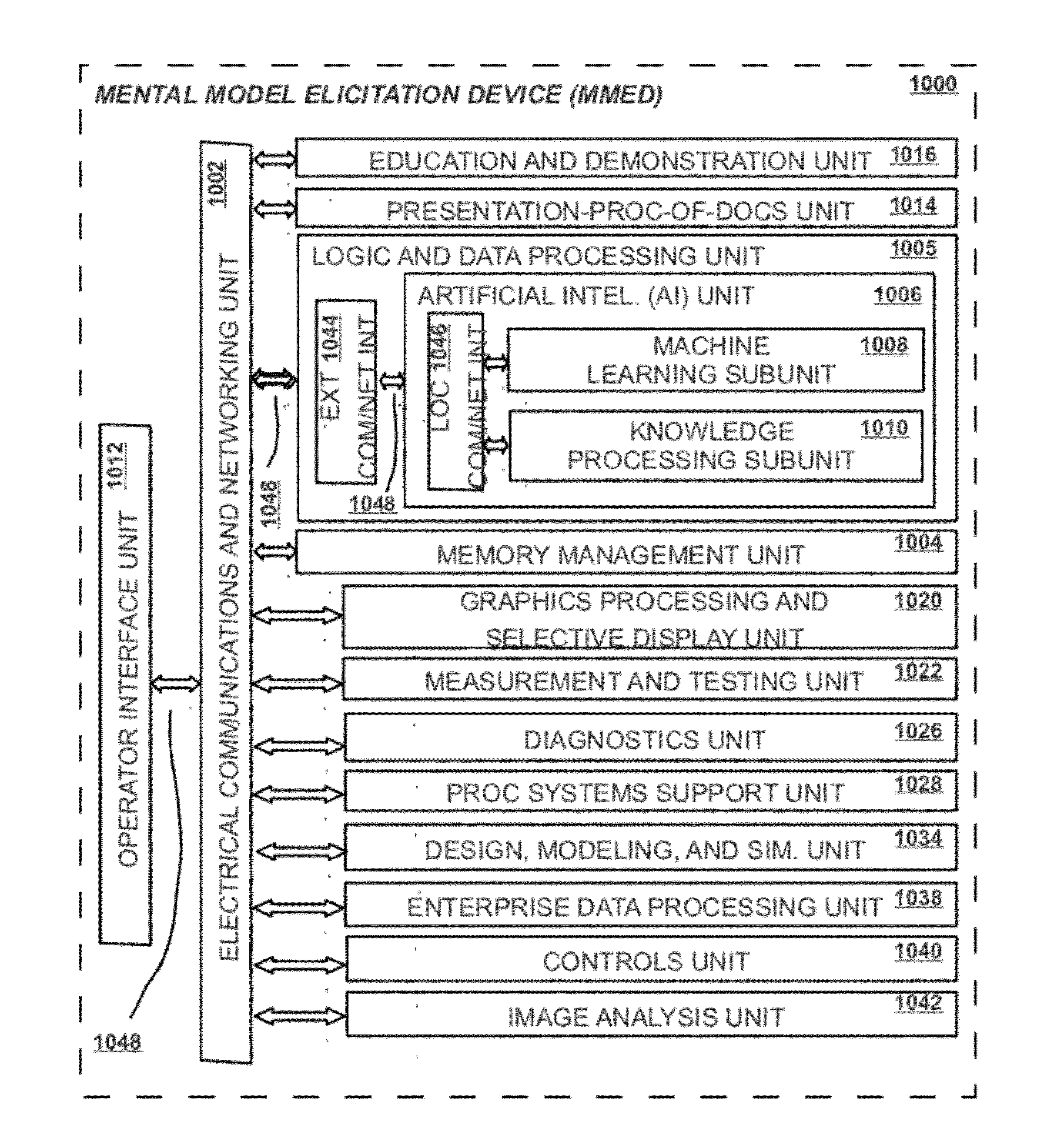
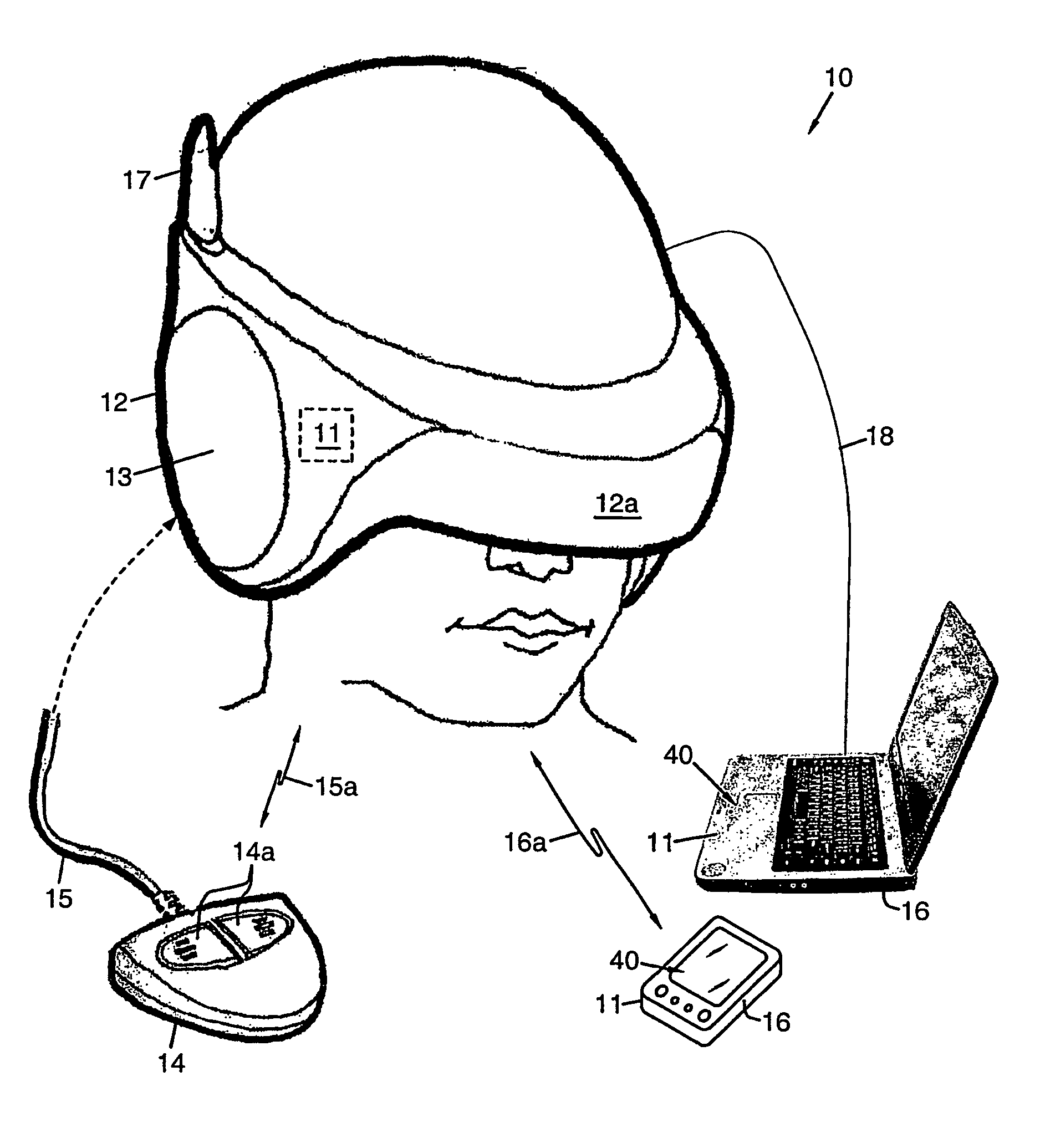
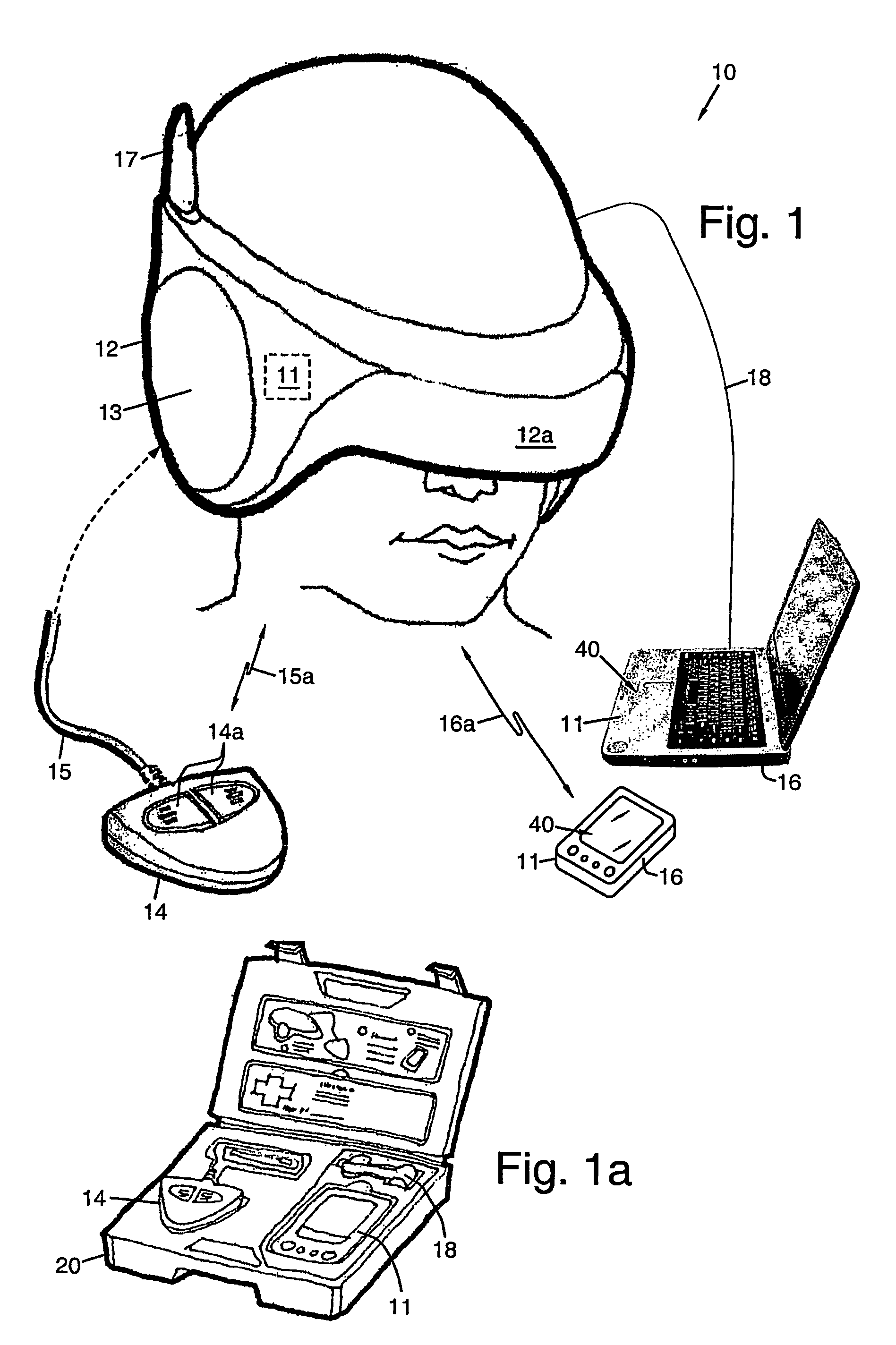
Mental Model Elicitation Device (MMED) Methods and Apparatus
InactiveUS20120330869A1Facilitate the necessary orientationEasy to createDigital computer detailsBiological neural network modelsVision basedEngineering
A mental-model elicitation process and apparatus, called the Mental-Model Elicitation Device (MMED) is described. The MMED is used to give rise to more effective end-user mental-modeling activities that require executive function and working memory functionality. The method and apparatus is visual analysis based, allowing visual and other sensory representations to be given to thoughts, attitudes, and interpretations of a user about a given visualization of a mental-model, or aggregations of such visualizations and their respective blending. Other configurations of the apparatus and steps of the process may be created without departing from the spirit of the invention as disclosed.
Owner:DURHAM JAYSON THEORDORE
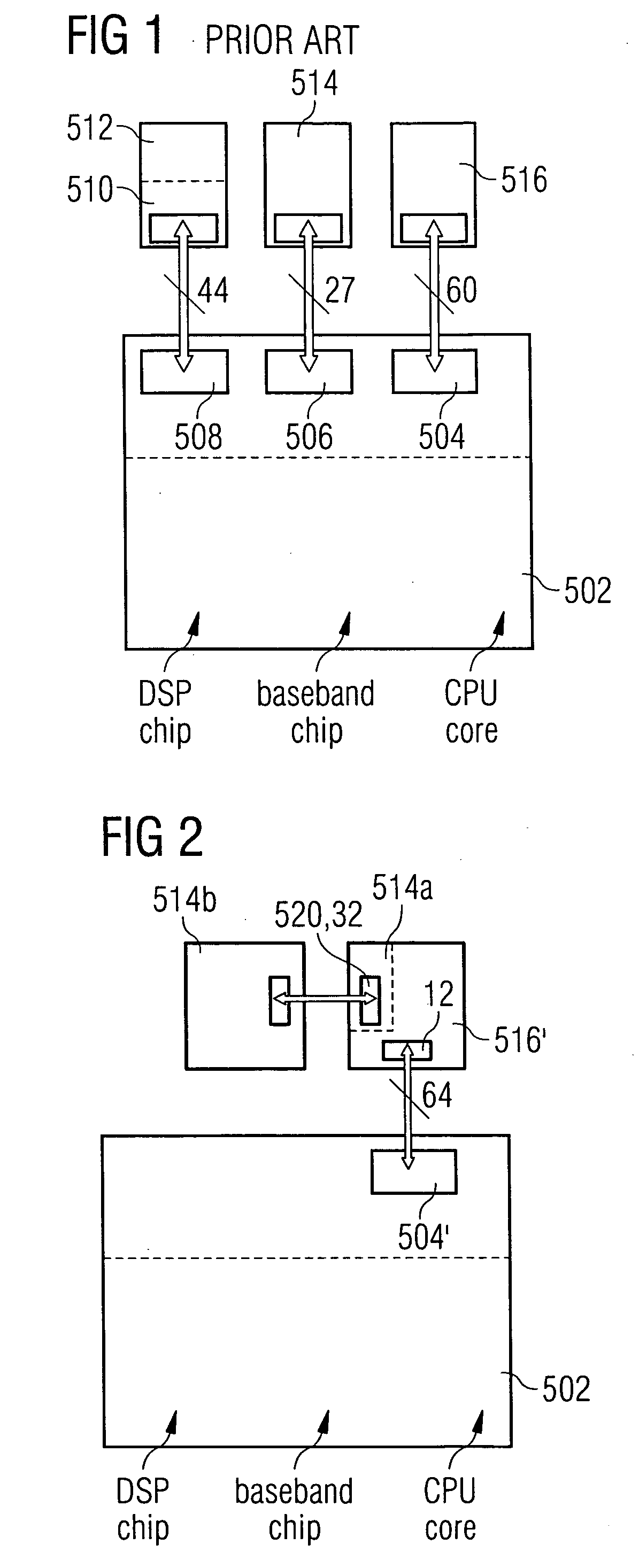
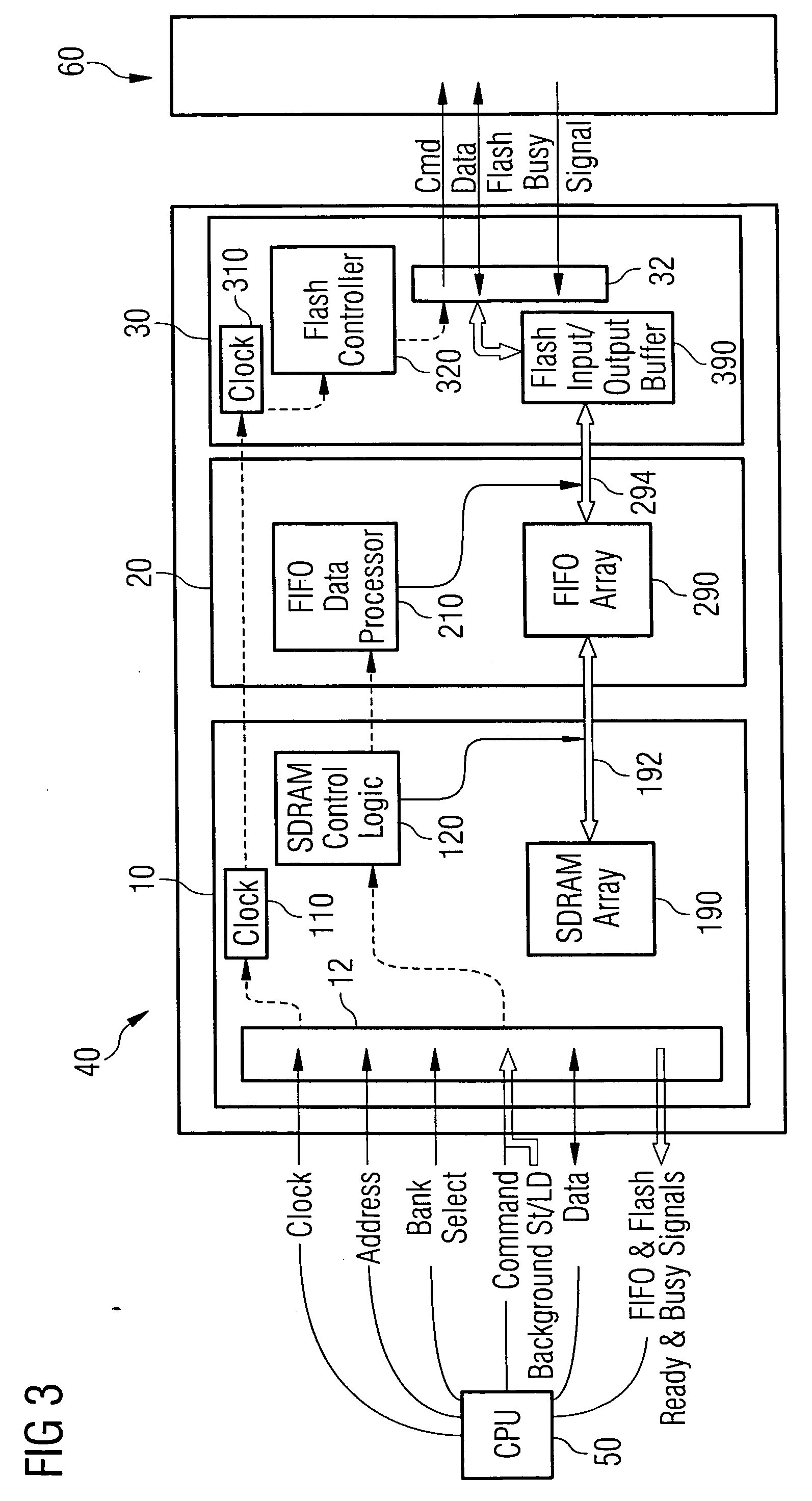
DRAM chip device well-communicated with flash memory chip and multi-chip package comprising such a device
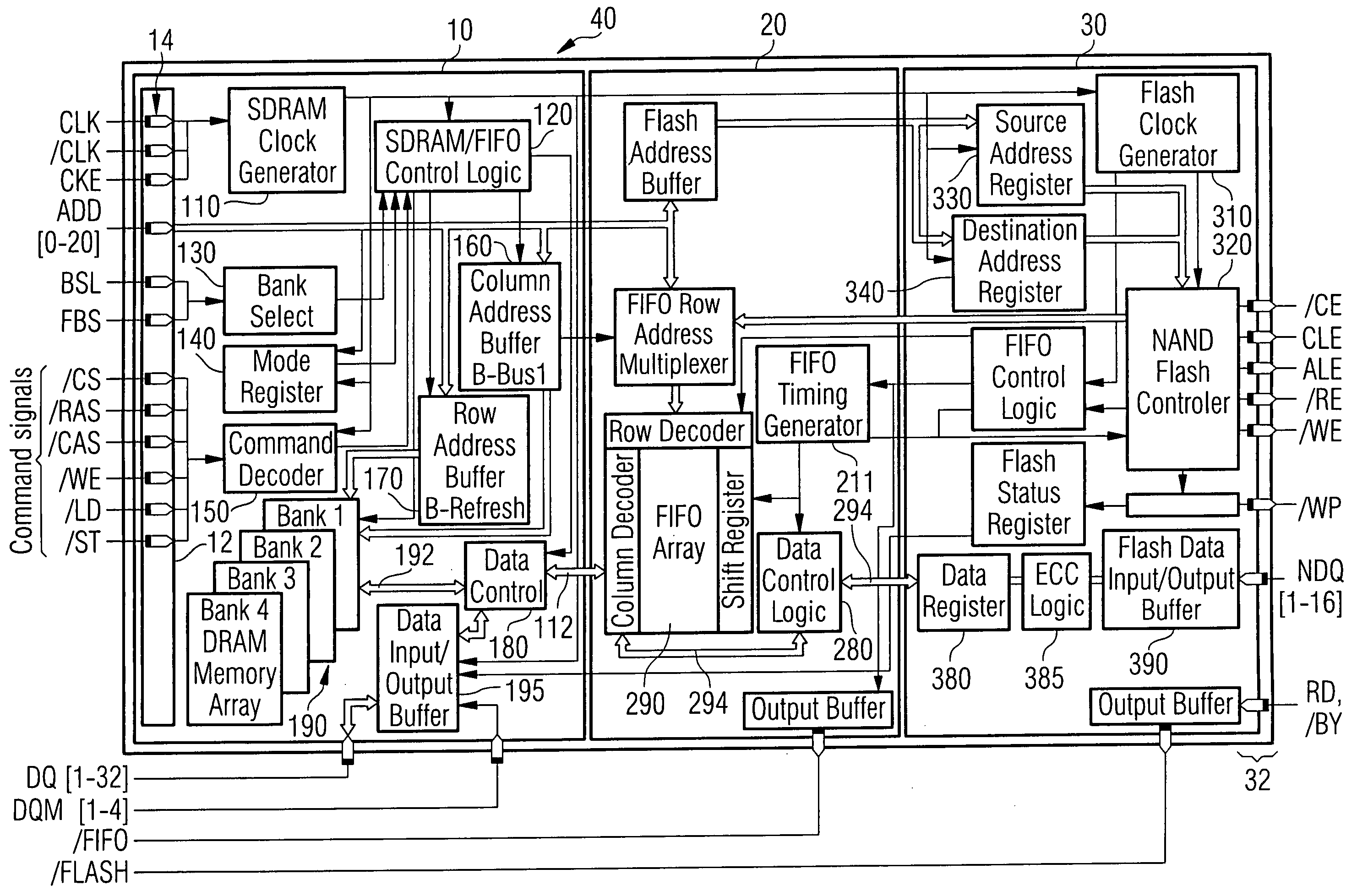
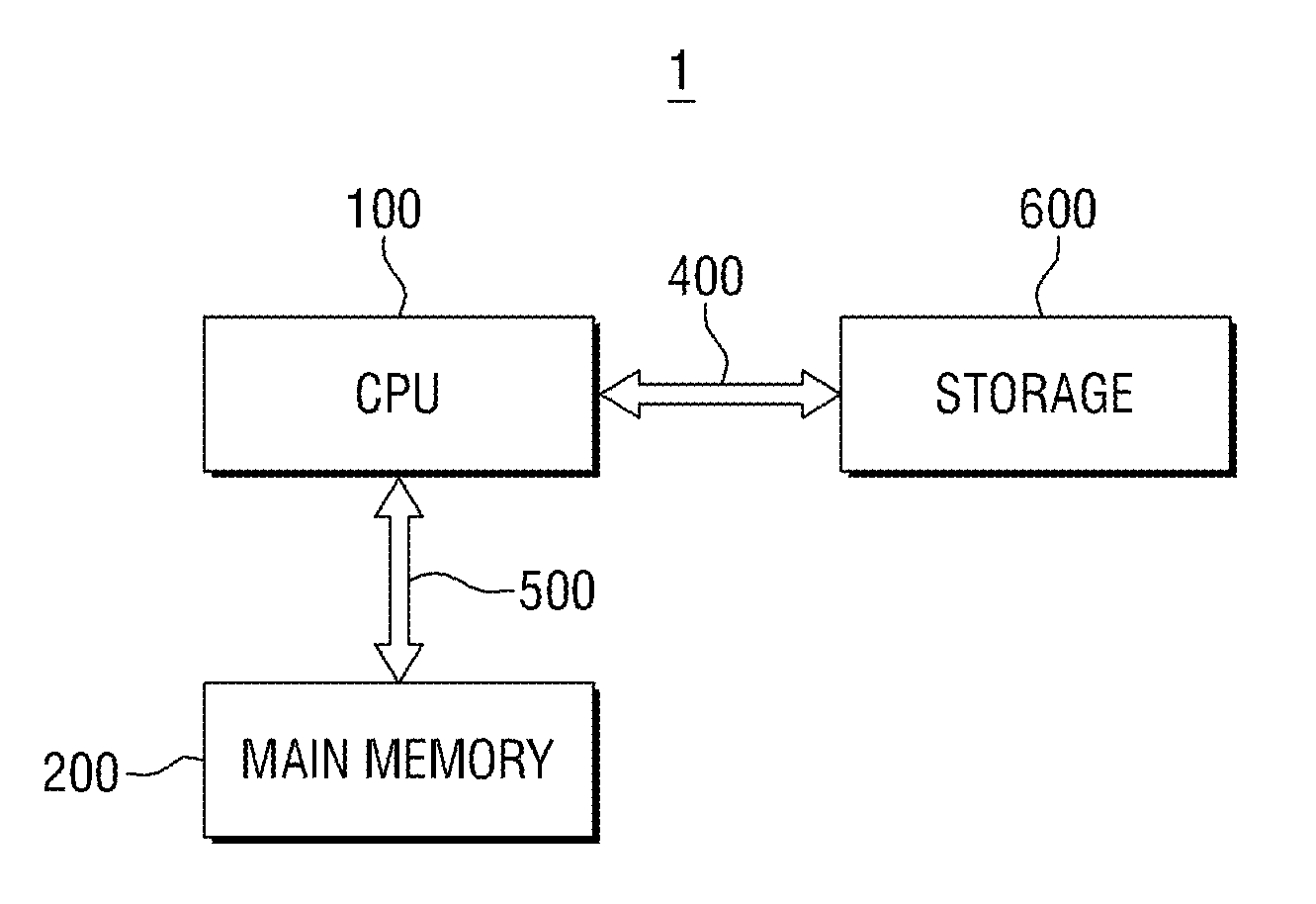
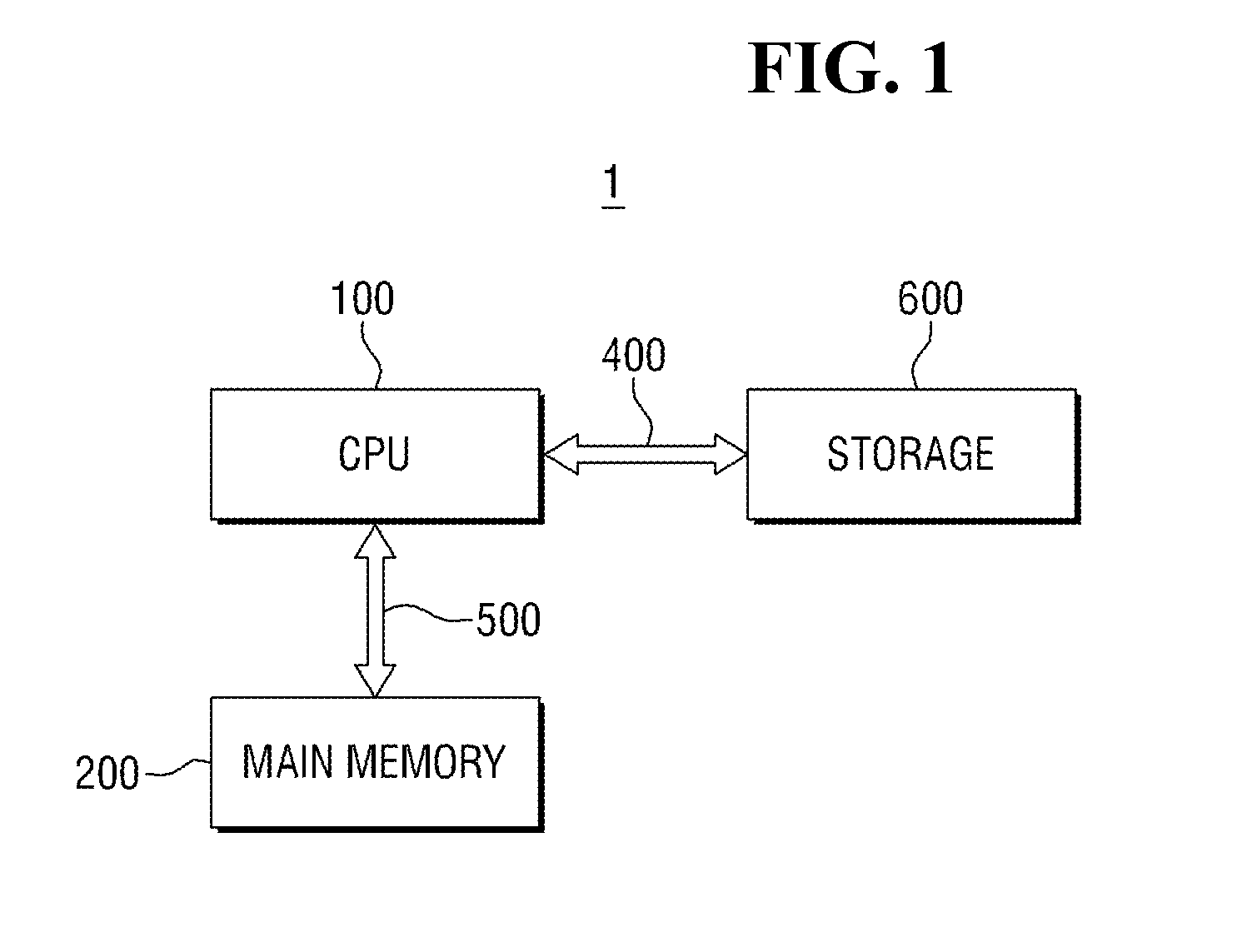
An SDRAM memory chip device comprises a non-volatile memory controller for operating a non-volatile memory, e.g., a NAND-flash, and a FIFO memory buffer. The FIFO memory buffer serves to operate background store and load operations between a FIFO buffer array and the non-volatile memory, while a host system such as a CPU exchanges data with the SDRAM work memory. The SDRAM memory chip device, therefore, has at least two additional pins as compared with conventional SDRAM standard for generating a set of additional commands. These commands are employed by the FIFO memory buffer to manage the data transfer between the FIFO buffer and each of the non-volatile memory and the volatile SDRAM memory. Two further pins reflecting the flash memory status provide appropriate issuance of load or store signals by the host system.
Owner:INFINEON TECH AG
Method and apparatus for automated training of language learning skills
A computer program for execution on a computing device is provided to cross-train students in language development skills such as letter-word correspondence, word recognition, vocabulary, and sentence and paragraph comprehension. A set of programs provide an adaptive methodology for training a student in decoding (semantic, syntactic, phonological, and morphological relationships), knowledge of rhymes, synonyms, antonyms, and homophones, spelling, letter-word correspondences, sentence comprehension, grammatical comprehension, working memory, vocabulary, paragraph comprehension, and improved reading comprehension. In each program, students are presented with an animated scene that poses a question, and a set of answers. The set of answers contain a correct response, and a number of incorrect responses or foils. The student advances to more complex levels by satisfying predetermined correct thresholds. Through repetition and intensity, the student's language skills are developed.
Owner:SCI LEARNING
Method and apparatus for conducting crypto-ignition processes between thin client devices and server devices over data networks
InactiveUS6263437B1Key distribution for secure communicationMultiple keys/algorithms usageTraffic capacityKey-agreement protocol
A crypto-ignition process is needed to establish an encrypted communication protocol between two devices connected by an insecure communication link. The present invention introduces a method of creating an identical secret key to two communicating parties is conducted between a thin device and a server computer over an insecure data network. The thin device generally has limited computing power and working memory and the server computer may communicate with a plurality of such thin devices. To ensure the security of the secret key on both sides and reduce traffic in the network, only a pair of public values is exchanged between the thin device and the server computer over the data network. Each side generates its own secret key from a self-generated private value along with the received counterpart's public value according to a commonly used key agreement protocol, such as the Diffie-Hellman key agreement protocol. To ensure that the generated secret keys are identical on both sides, a verification process is followed by exchanging a message encrypted by one of two generated secret keys. The secret keys are proved to be identical and secret when the encrypted message is successfully decrypted by the other secret key. To reduce network traffic, the verification process is piggybacked with a session request from the thin device to establish a secure and authentic communication session with the server computer. The present invention enables the automatic delivery of the secret keys, without requiring significant computing power and working memory, between each of the thin clients respectively with the server computer.
Owner:UNWIRED PLANET
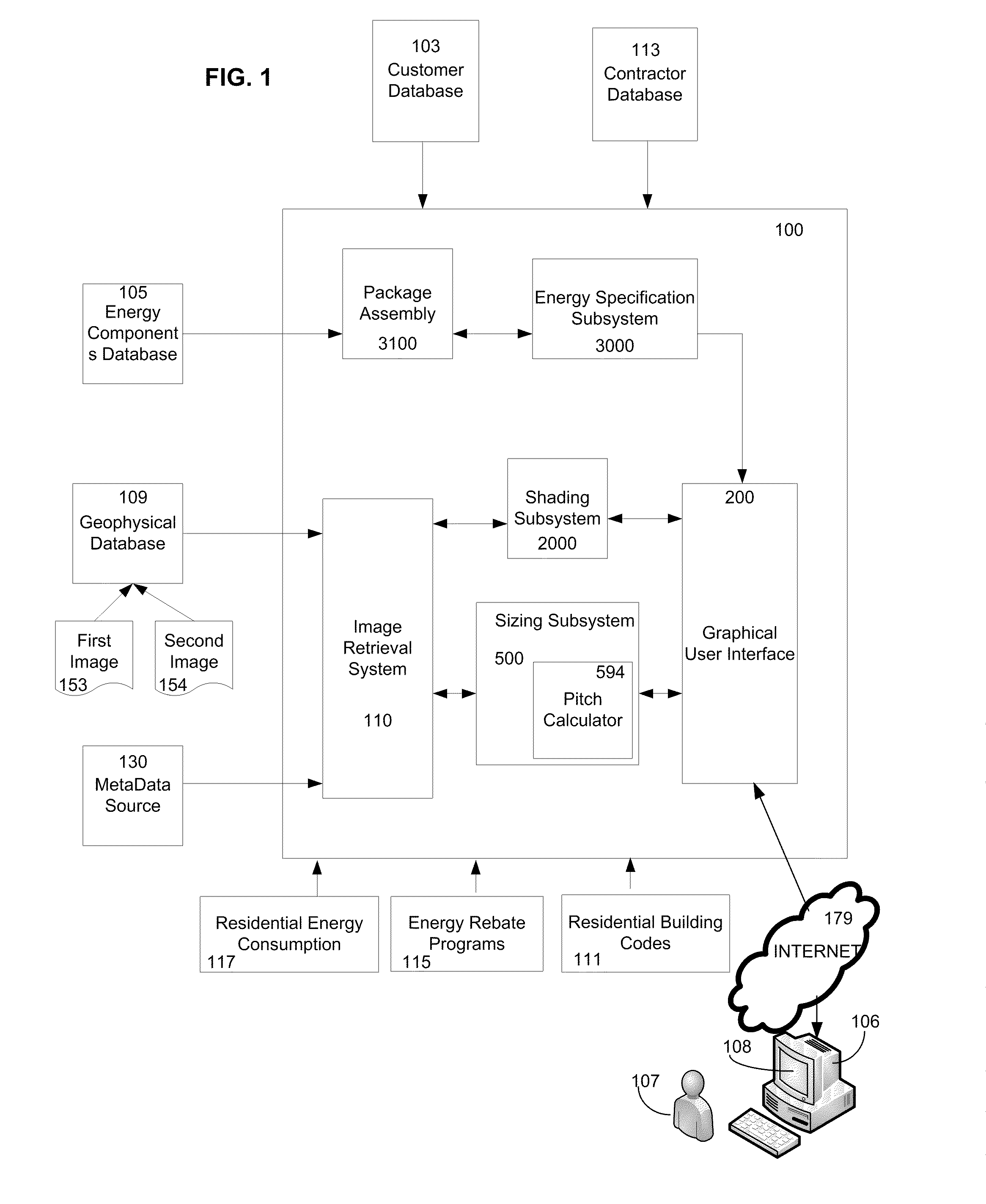
Methods and Systems for Provisioning Energy Systems
ActiveUS20090304227A1Solar heating energySolar heat simulation/predictionThird partySize determination
The invention provides consumers, private enterprises, government agencies, contractors and third party vendors with tools and resources for gathering site specific information related to purchase and installation of energy systems. A system according to one embodiment of the invention remotely determines the measurements of a roof. An exemplary system comprises a computer including an input means, a display means and a working memory. An aerial image file database contains a plurality of aerial images of roofs of buildings in a selected region. A roof estimating software program receives location information of a building in the selected region and then presents the aerial image files showing roof sections of building located at the location information. Some embodiments of the system include a sizing tool for determining the size, geometry, and pitch of the roof sections of a building being displayed.
Owner:SUNGEVITY
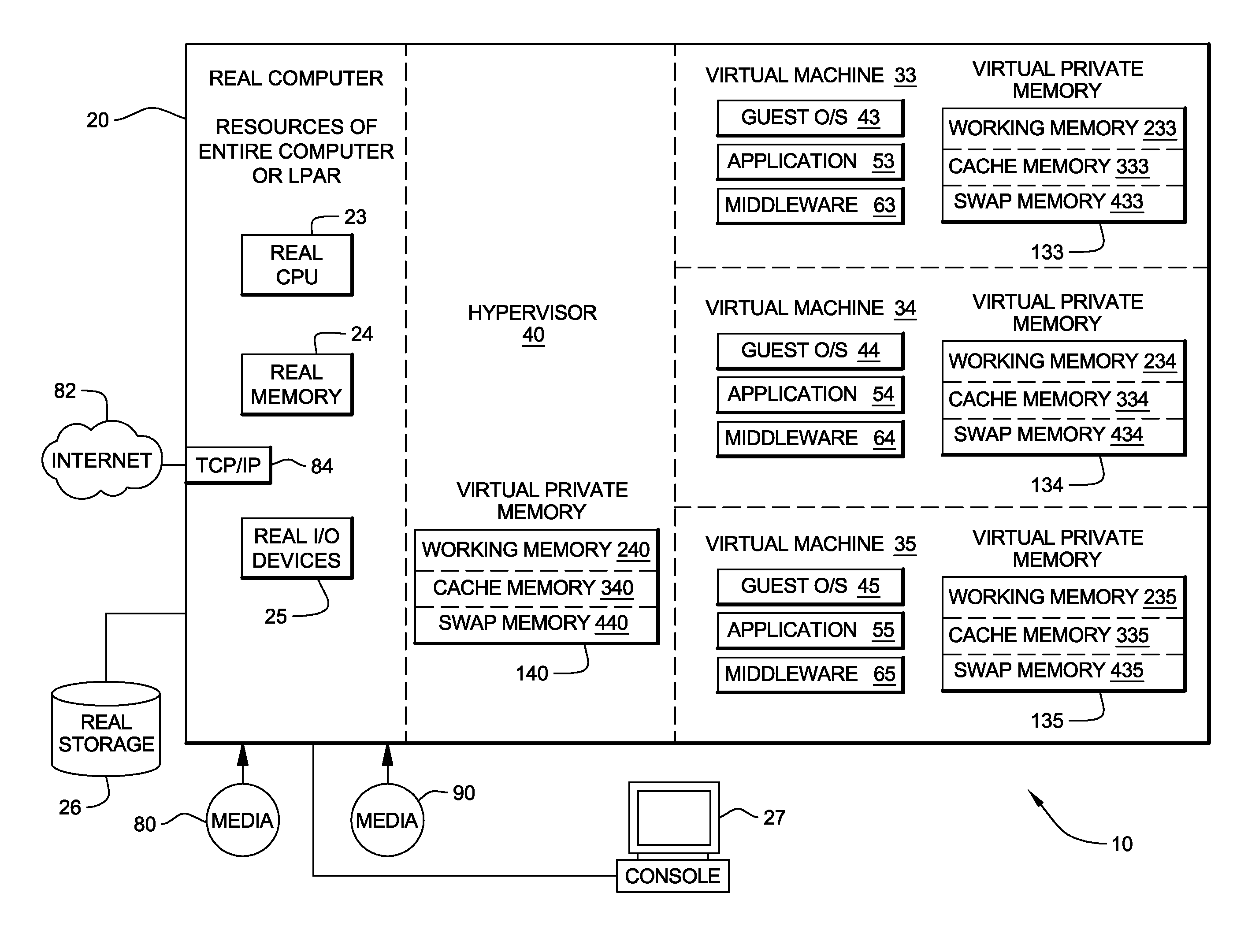
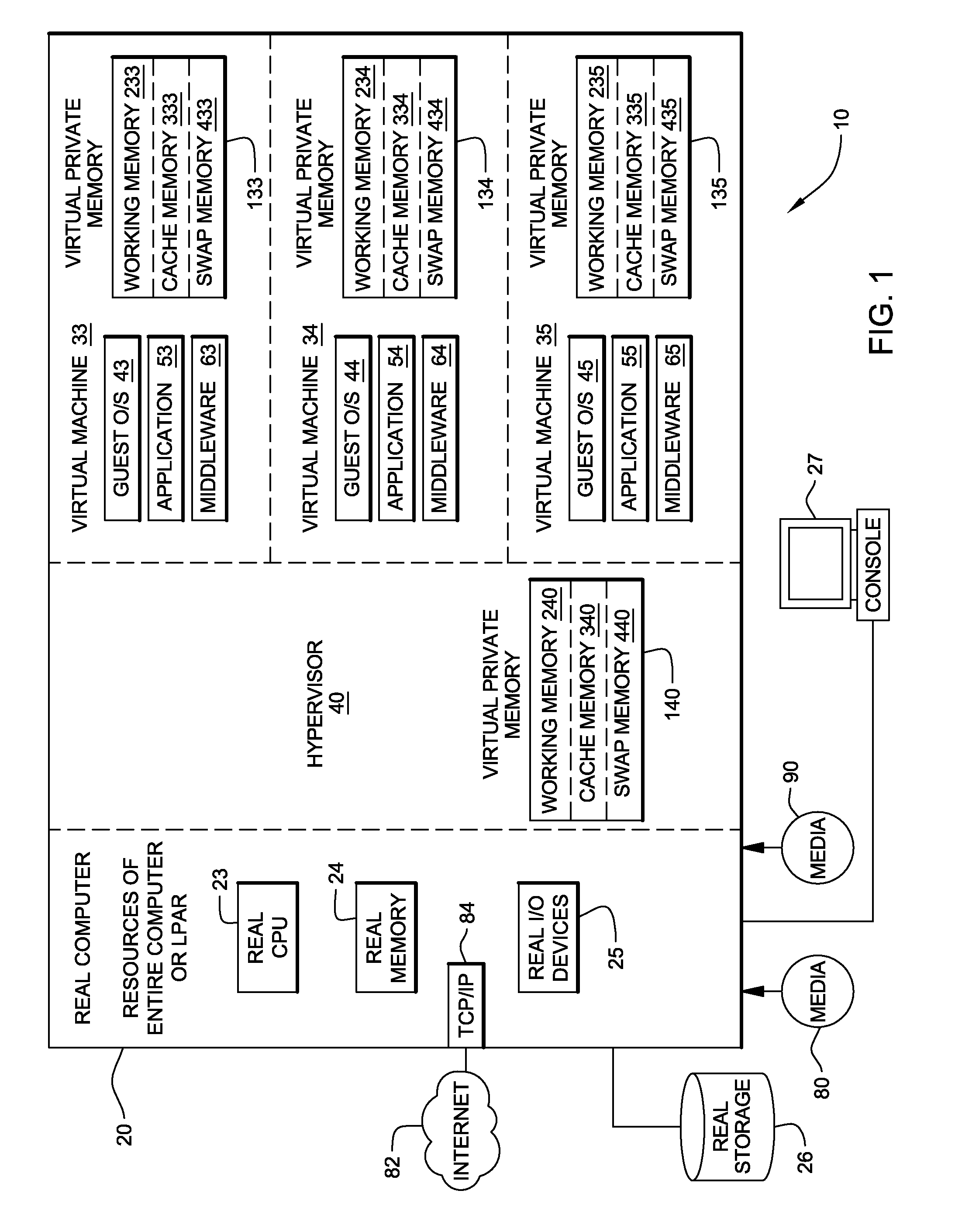
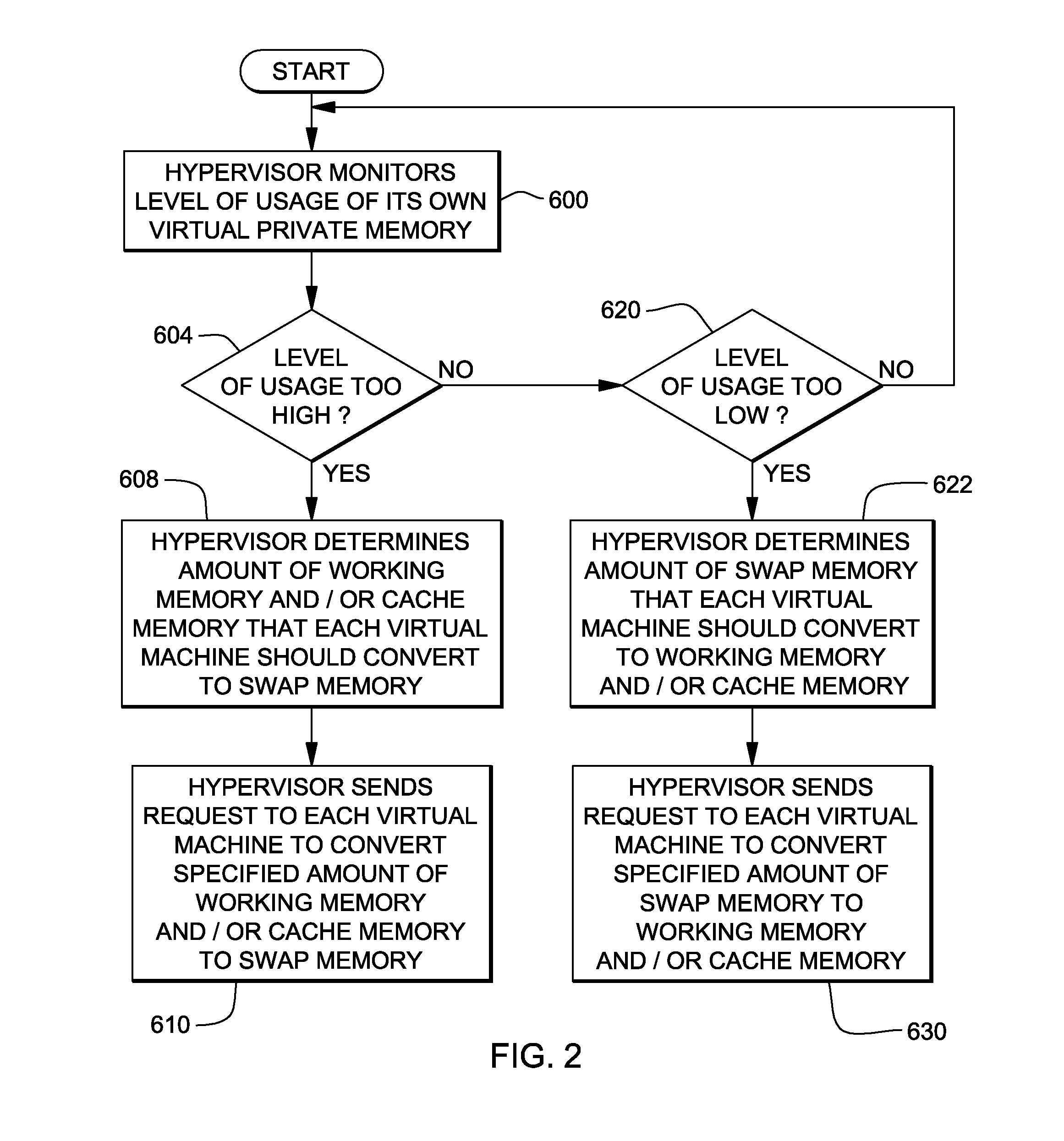
System, method and program to manage memory of a virtual machine
ActiveUS20090006801A1Less virtual memory allocationResource allocationMemory adressing/allocation/relocationVirtual memoryWork memory
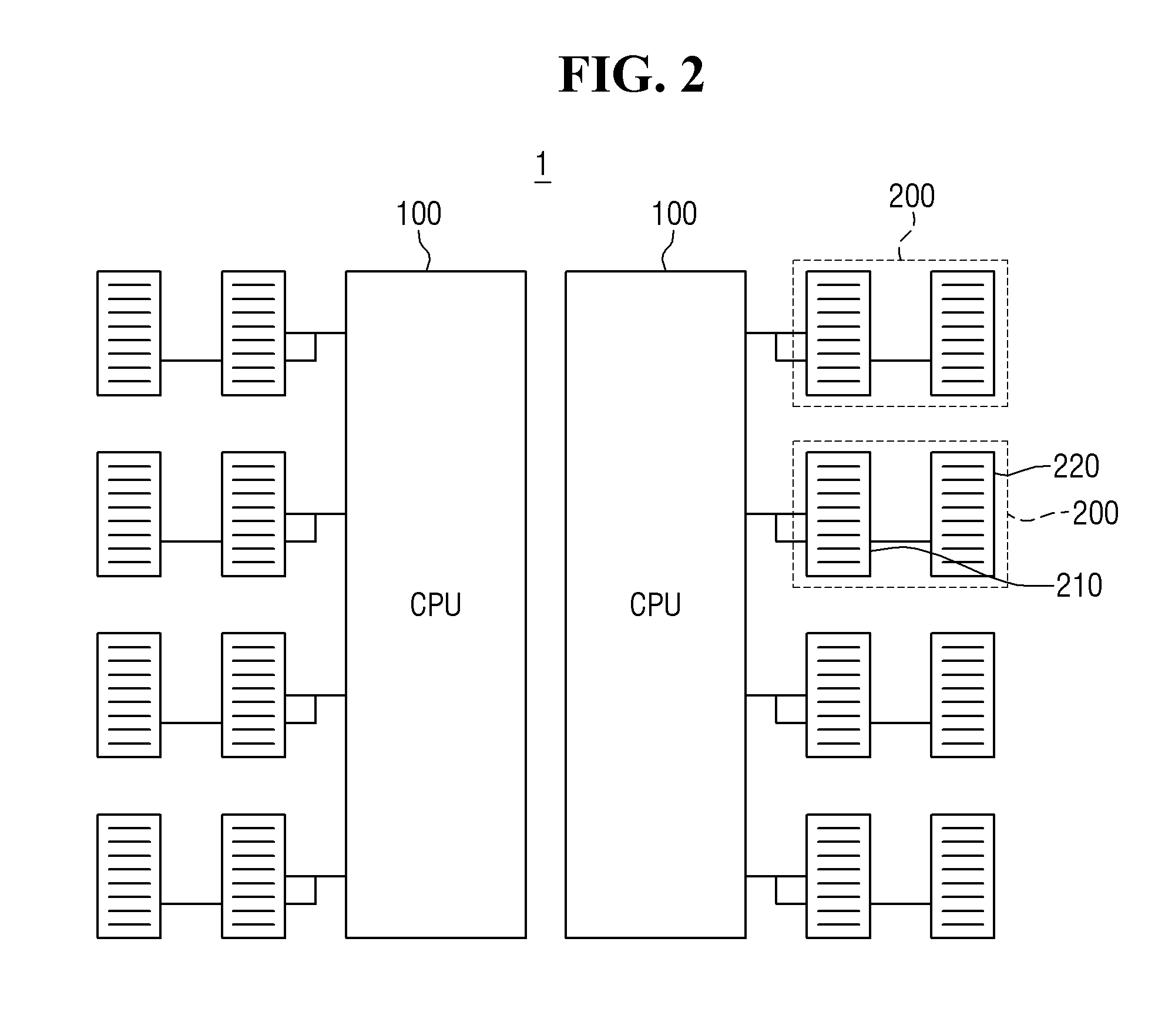
Management of virtual memory allocated by a virtual machine control program to a plurality of virtual machines. Each of the virtual machines has an allocation of virtual private memory divided into working memory, cache memory and swap memory. The virtual machine control program determines that it needs additional virtual memory allocation, and in response, makes respective requests to the virtual machines to convert some of their respective working memory and / or cache memory to swap memory. At another time, the virtual machine control program determines that it needs less virtual memory allocation, and in response, makes respective requests to the virtual machines to convert some of their respective swap memory to working memory and / or cache memory.
Owner:IBM CORP
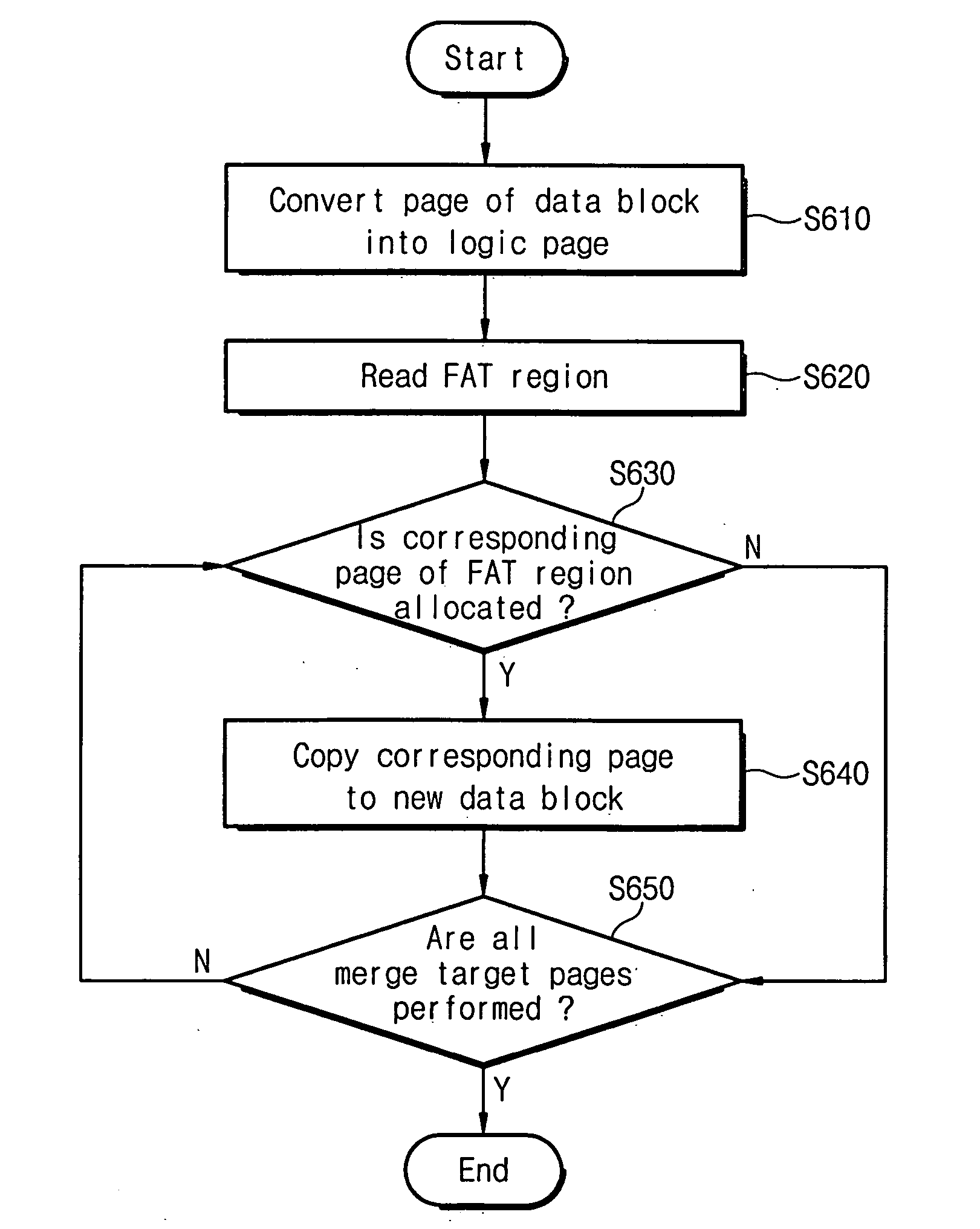
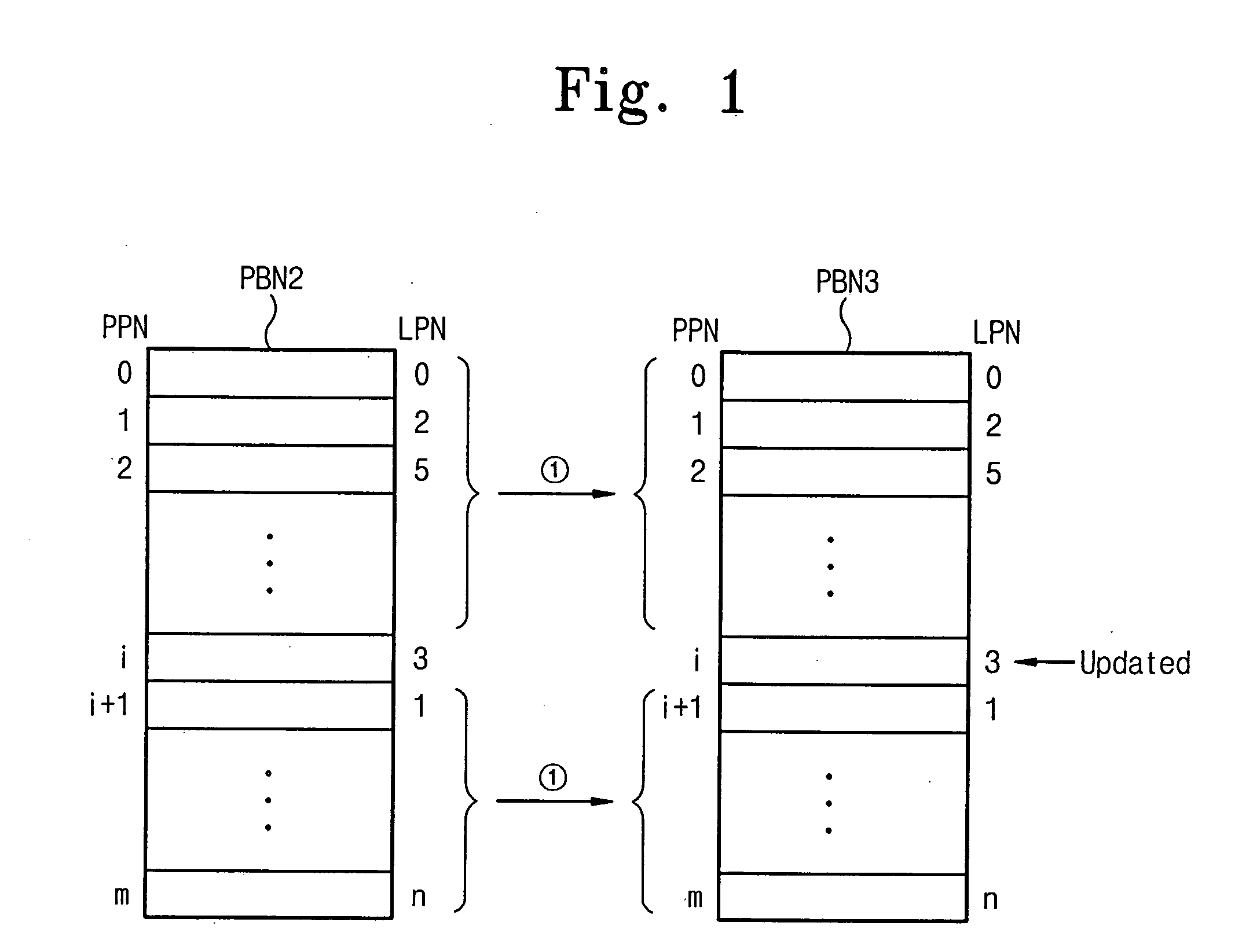
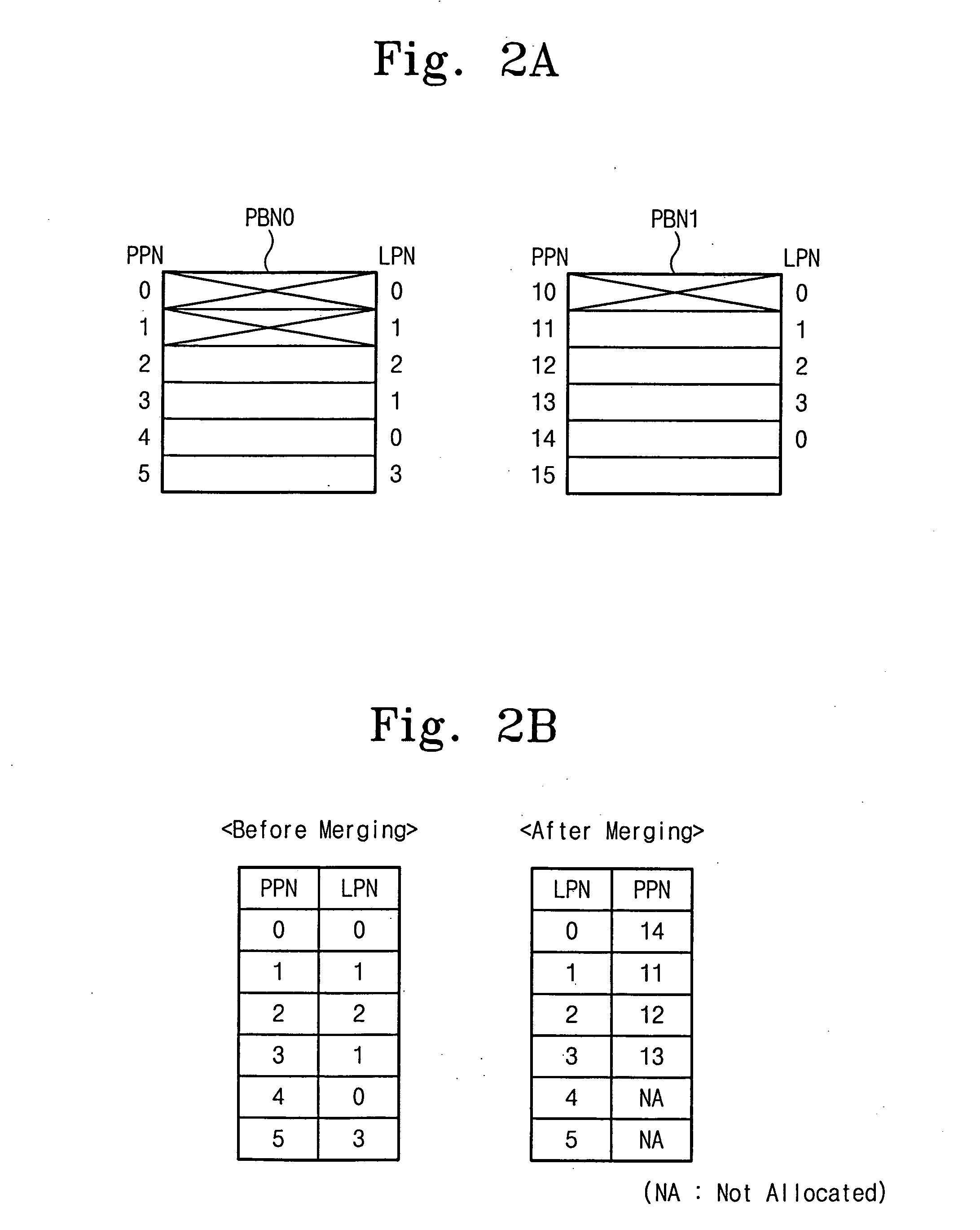
Flash memory device and associated data merge method
InactiveUS20060179263A1Ultrasonic/sonic/infrasonic diagnosticsInfrasonic diagnosticsWork memoryControl logic
A memory system comprises a flash memory and a controller comprising a control logic circuit and a working memory storing a flash translation layer. The memory system performs a merge operation by selectively copying a page from a first block of the flash memory to a second block of the flash memory. Where the page is valid and marked as allocated according to a file allocation table stored in the flash memory, the page is copied to the second block. However, where the page is valid and marked as deleted in the file allocation table, the page is not copied to the second block.
Owner:SAMSUNG ELECTRONICS CO LTD
Cognitive and Linguistic Assessment Using Eye Tracking
ActiveUS20100092929A1Leveling precisionHealth-index calculationReadingDividing attentionVisual perception
Methods for assessing cognitive and linguistic abilities by tracking and recording the eye movements of a patient in response to predetermined verbal and visual stimuli. The methods incorporate conventional eye-tracking technology to acquire eye-fixation location and duration measures for testing linguistic comprehension, working memory, attention allocation, and the effect of semantic associative priming. Visual stimuli presented in the methods are carefully designed to reduce visually distracting features. Verbal stimuli are carefully designed to control for numerous linguistic features.
Owner:OHIO UNIV
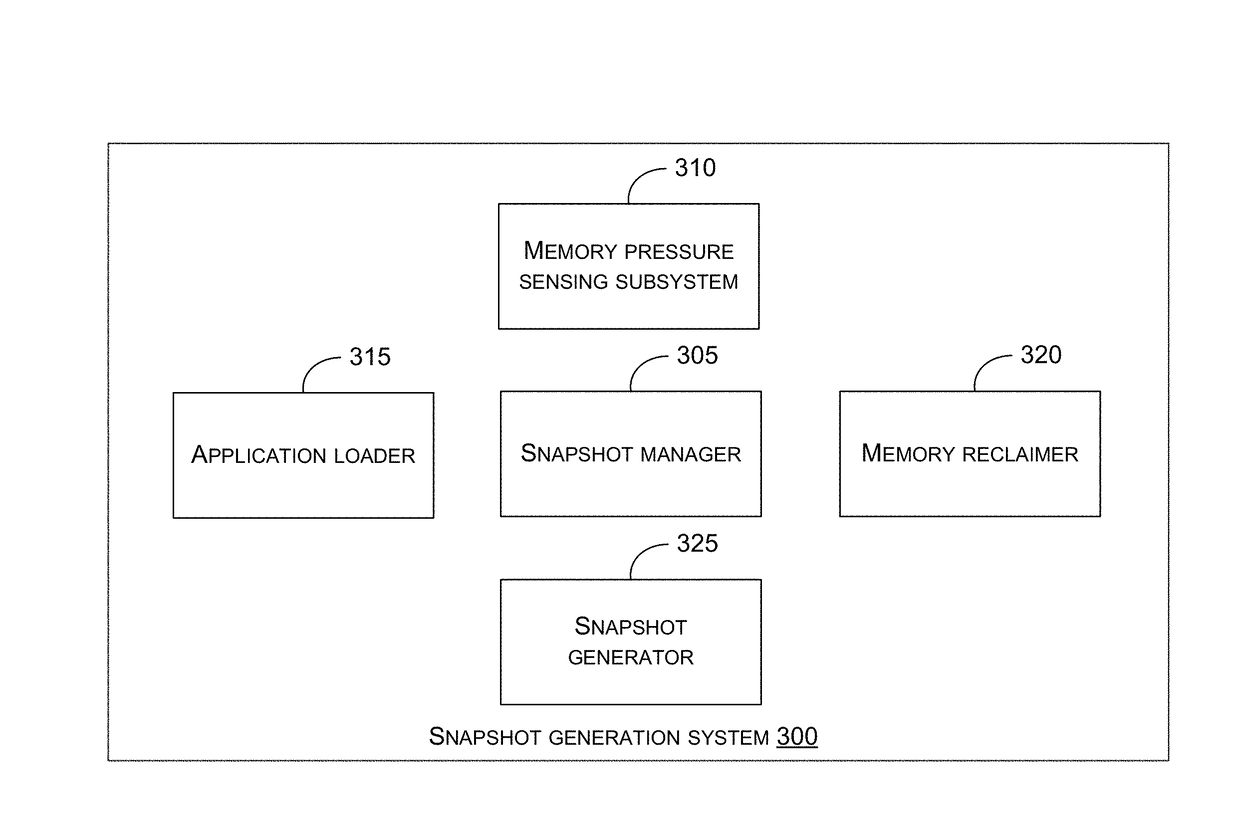
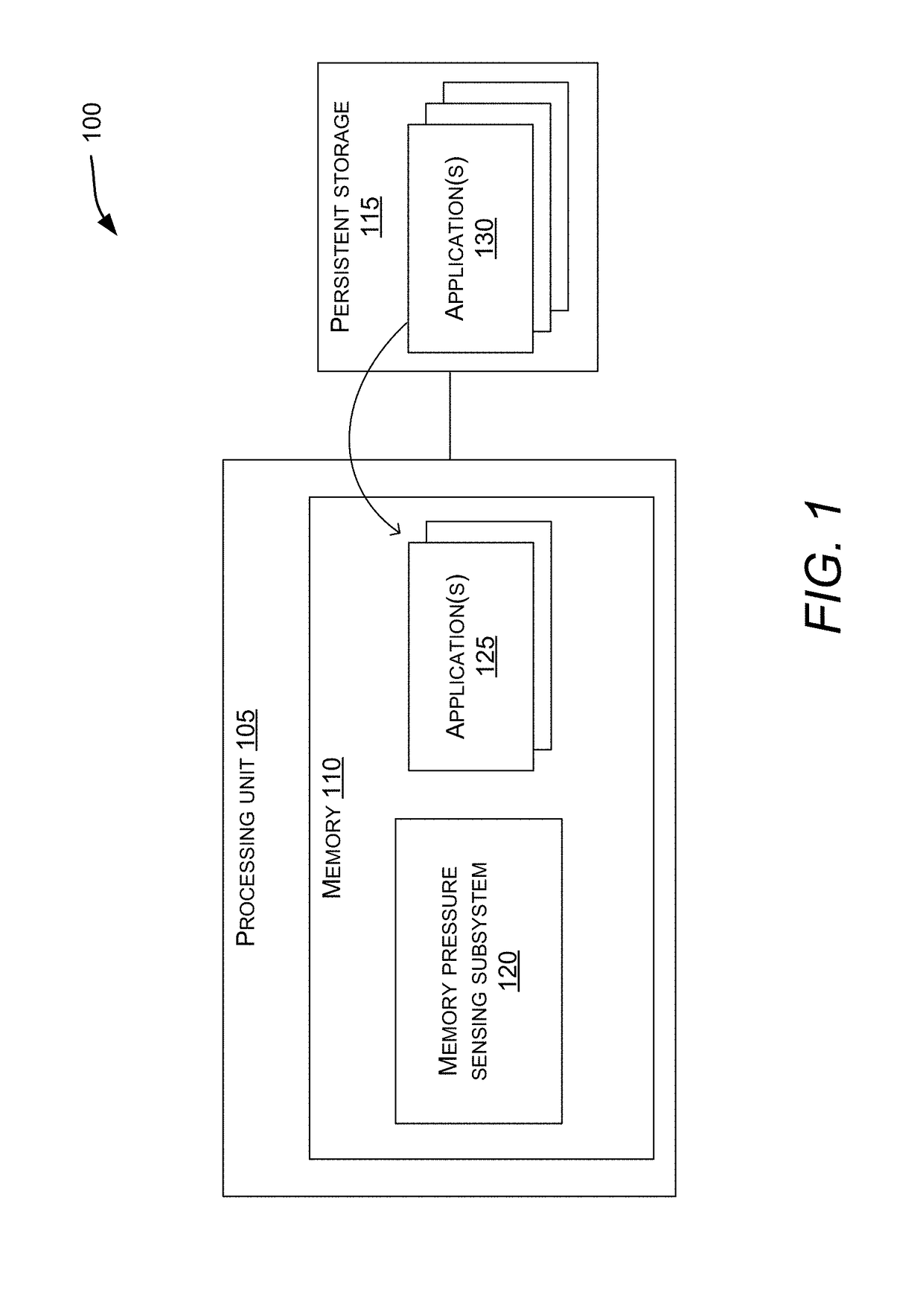
Memory management for application loading
Some embodiments can load one or more applications into working memory from persistent storage when permitted by a memory pressure level of a mobile device. Loading the applications into working memory enables the applications to be launched into the foreground quickly when the user indicates the desire to launch. Some embodiments may identify a set of applications that are designated for providing snapshots to be displayed when the mobile device is in a dock mode. Certain embodiments may determine a current memory pressure level. Some embodiments may load an application in the set of applications into working memory from a persistent storage responsive to determining that the memory pressure level is below a threshold. Certain embodiments may continue to load additional applications responsive to determining that the memory pressure level is below the threshold. After determining that the memory pressure level is above the threshold, some embodiments may reclaim memory.
Owner:APPLE INC
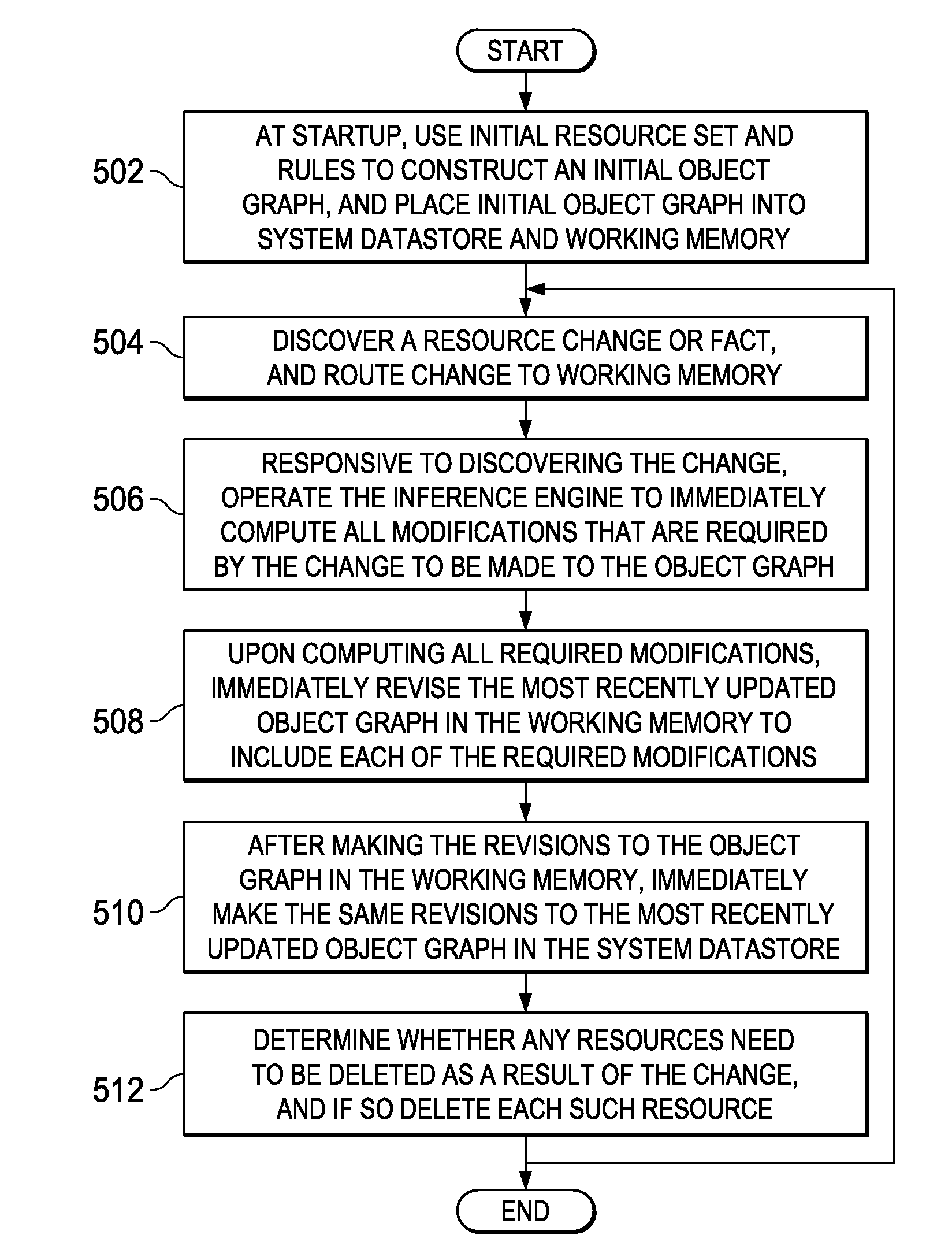
Creation and Revision of Network Object Graph Topology for a Network Performance Management System
InactiveUS20110320394A1Digital data information retrievalDigital data processing detailsManagement systemObject graph
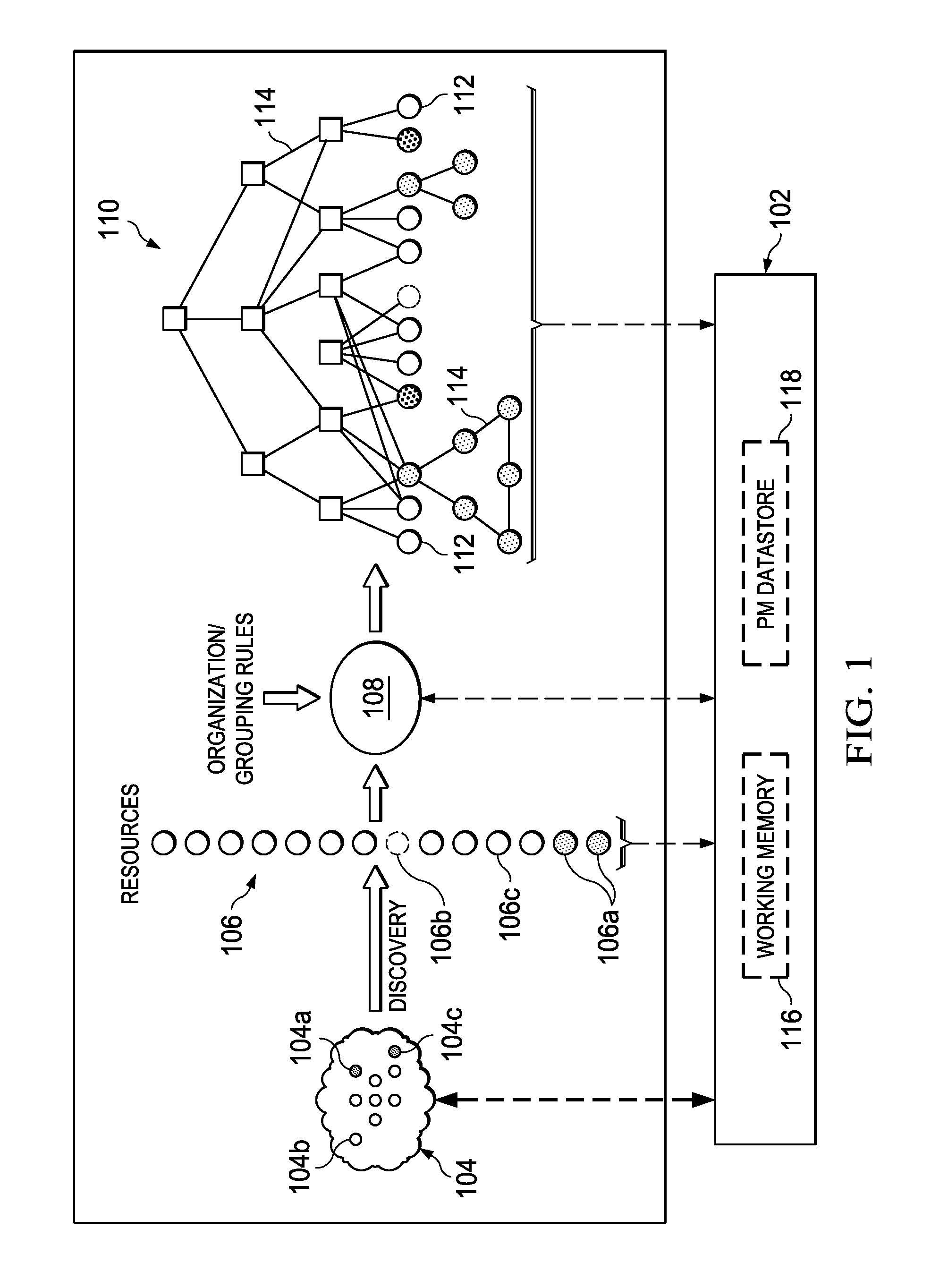
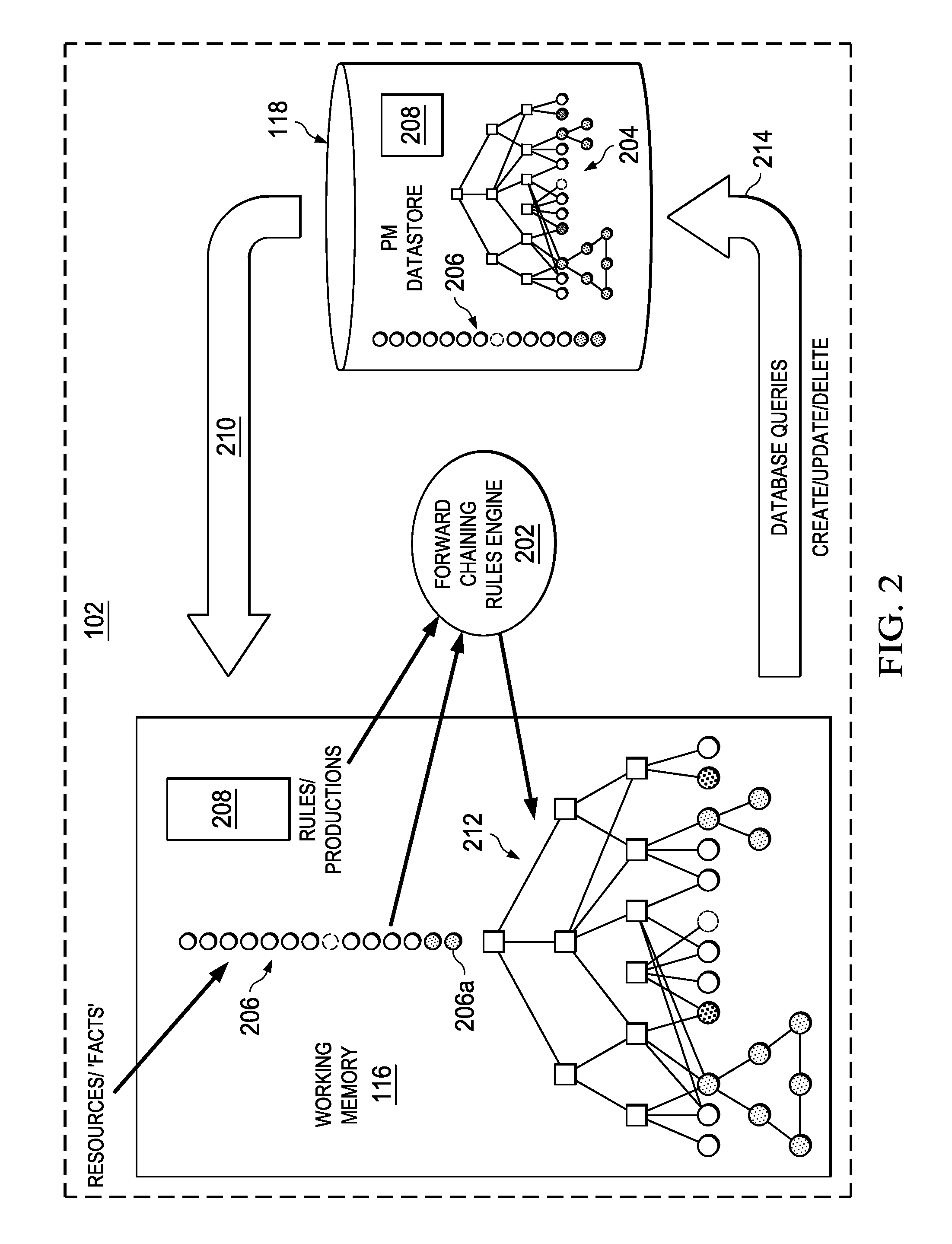
An embodiment of the invention comprises, providing an initial object graph to a database, the initial object graph being generated by applying a set of rules to resources included in a resource set at a specified time, or by revising a previous object graph at the previous time, the resource set at the specified time comprising an initial resource set. The method includes providing the initial object graph to a working memory, maintained in separation from the database; discovering a changed fact associated with one of the resources of the initial resource set; and upon discovering the changed fact, determining modifications required by the changed fact to the initial object graph. If modifications are required, the initial object graph is revised in the working memory to include such modifications. The same revisions are then made to the initial object graph in the system database.
Owner:IBM CORP
Multimedia Test Systems
ActiveUS20120260277A1Easy accessAnalogue secracy/subscription systemsBroadcast information monitoringNetwork connectionWork memory
Owner:LEVEL 3 COMM LLC
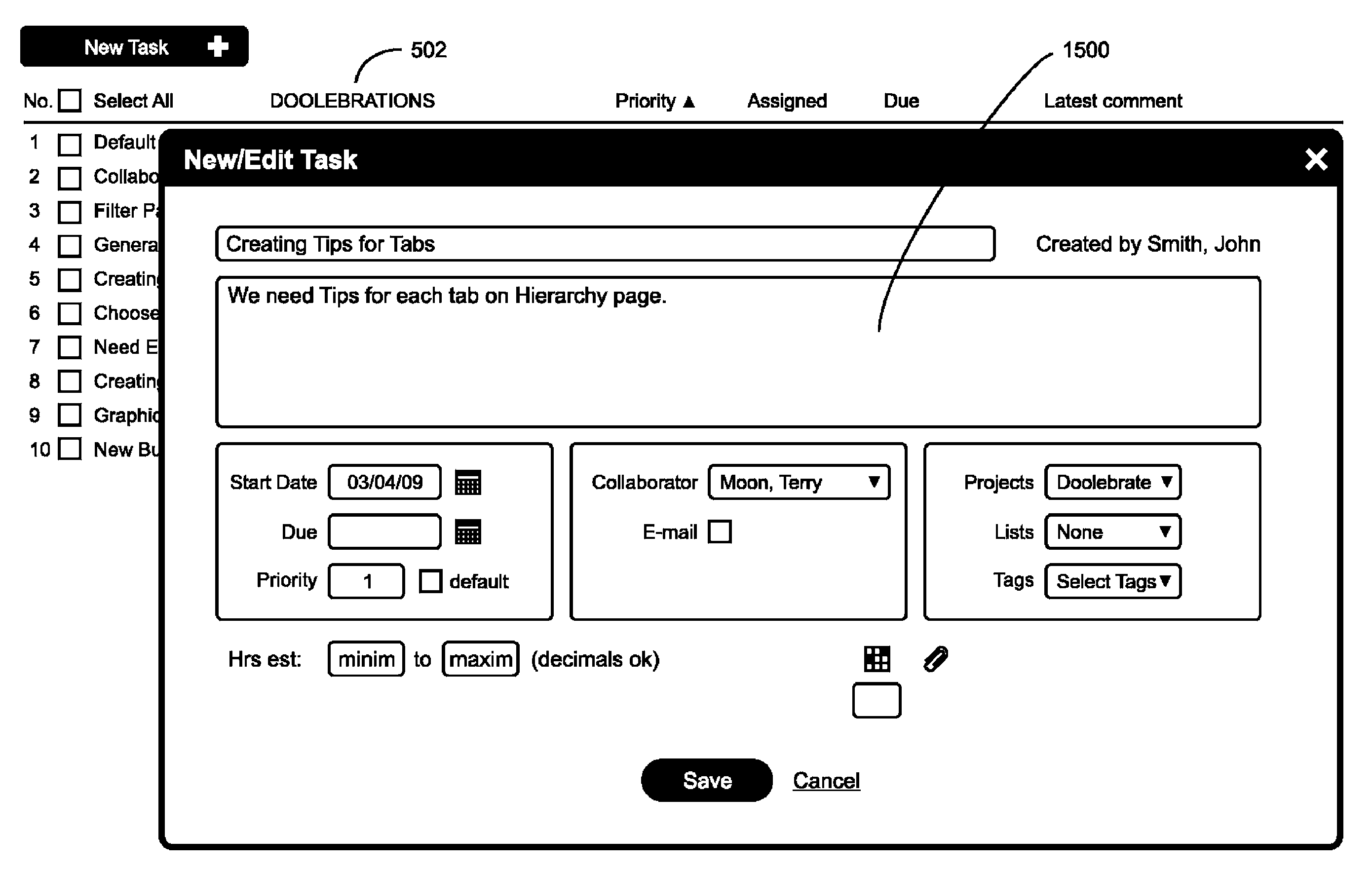
Simplified user interface and method for computerized task management systems
InactiveUS20100250322A1Easy to learnMultiple digital computer combinationsResourcesWeb browserWork memory
A system, method, and improved user interface for operating a computerized task management database, typically running on a networked server-client system such as the Internet. The system is designed to simultaneously present, on a single user interface screen, often running within a web browser, key items such as the worker (task assignee) name, and key task information items relevant to the various tasks that are assigned to this worker. Such key task information can include, for example, for each given task, the task name or distinguishing task commentary, and an instant update on the status of the task, which will usually contain at least a latest comment field that contains the most recent communication between the task worker and the task manager. The invention conserves user working memory by presenting key comments for multiple tasks on a single screen, enabling better user comprehension of complex projects.
Owner:NORWOOD MICHAEL ROY
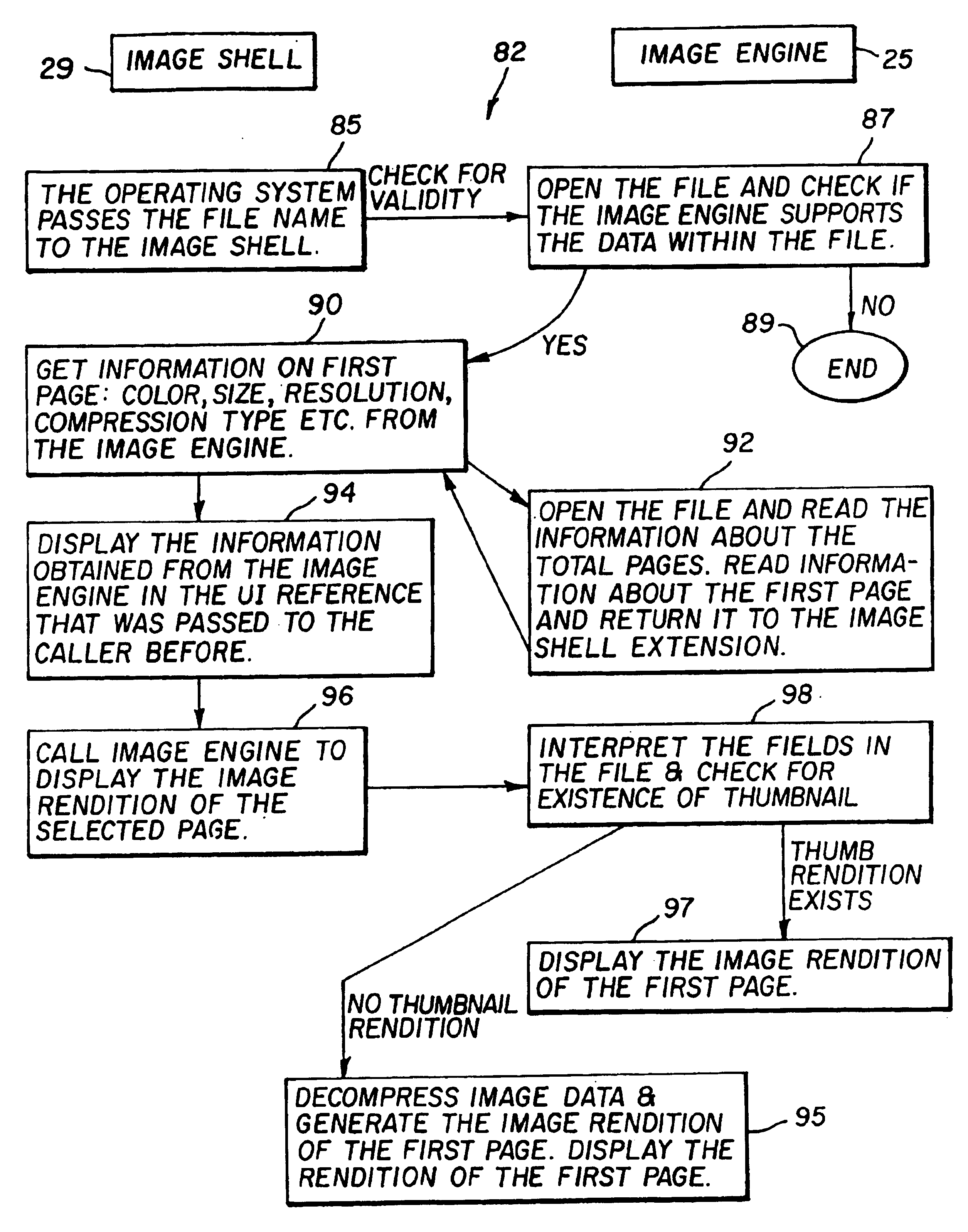
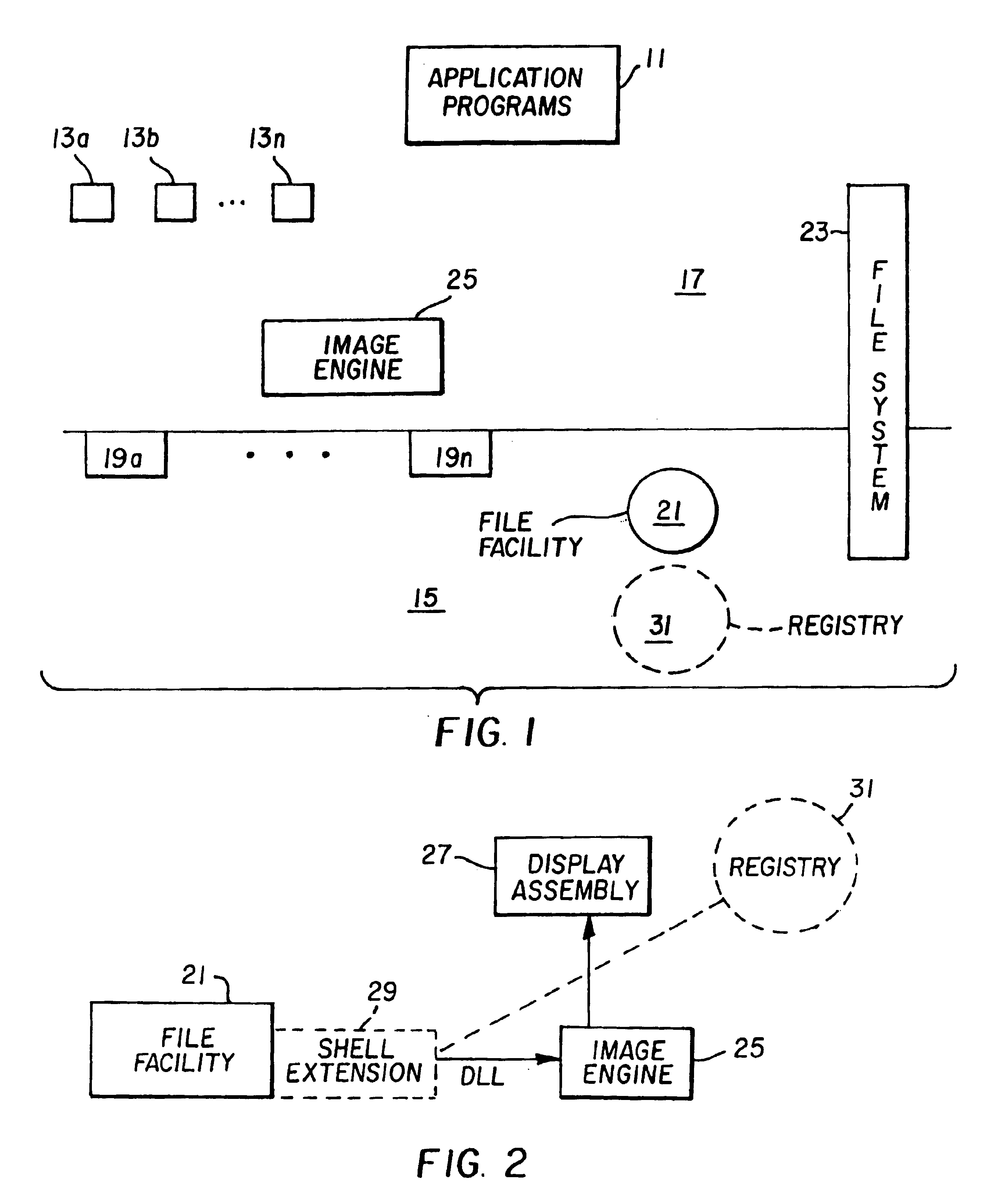
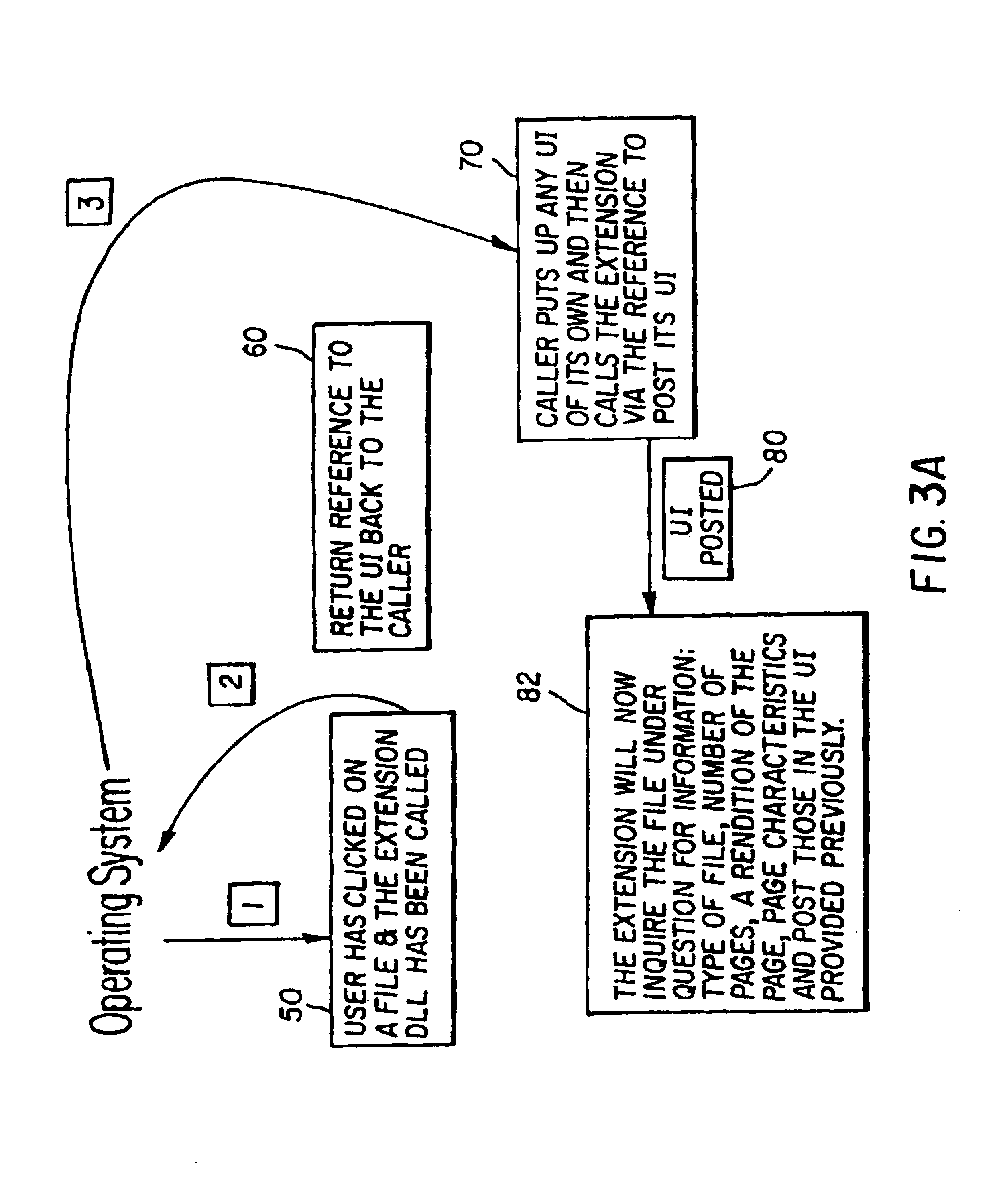
Computer method and apparatus for previewing files outside of an application program
InactiveUS6944819B2Overcome problemsDigital data processing detailsCathode-ray tube indicatorsGraphicsOperational system
A method and apparatus for previewing images and image file information without opening and running an application in working memory. The previewing of a user-selected file includes a summary of file characteristics and contents including images. The summary synopsizes file information and characteristics such as height, width, length, color type, resolution, compression type used for storing and forming the file, annotation graphics of the file and the like. The preview also provides display of the file images, preferably in a reduced size manner for ease of user previewing. The file preview apparatus and method of the present invention include operating system means coupled to a display assembly for generating display of indications of file characteristics of the user-selected files. The operating system means obtains and enables display of file characteristics indicia, external to and outside of an application program opened and running in the working memory. The display assembly is responsive to the operating system means and provides display of the file characteristics indicia in a manner free of opening an application program in the working memory.
Owner:MONUMENT PEAK VENTURES LLC
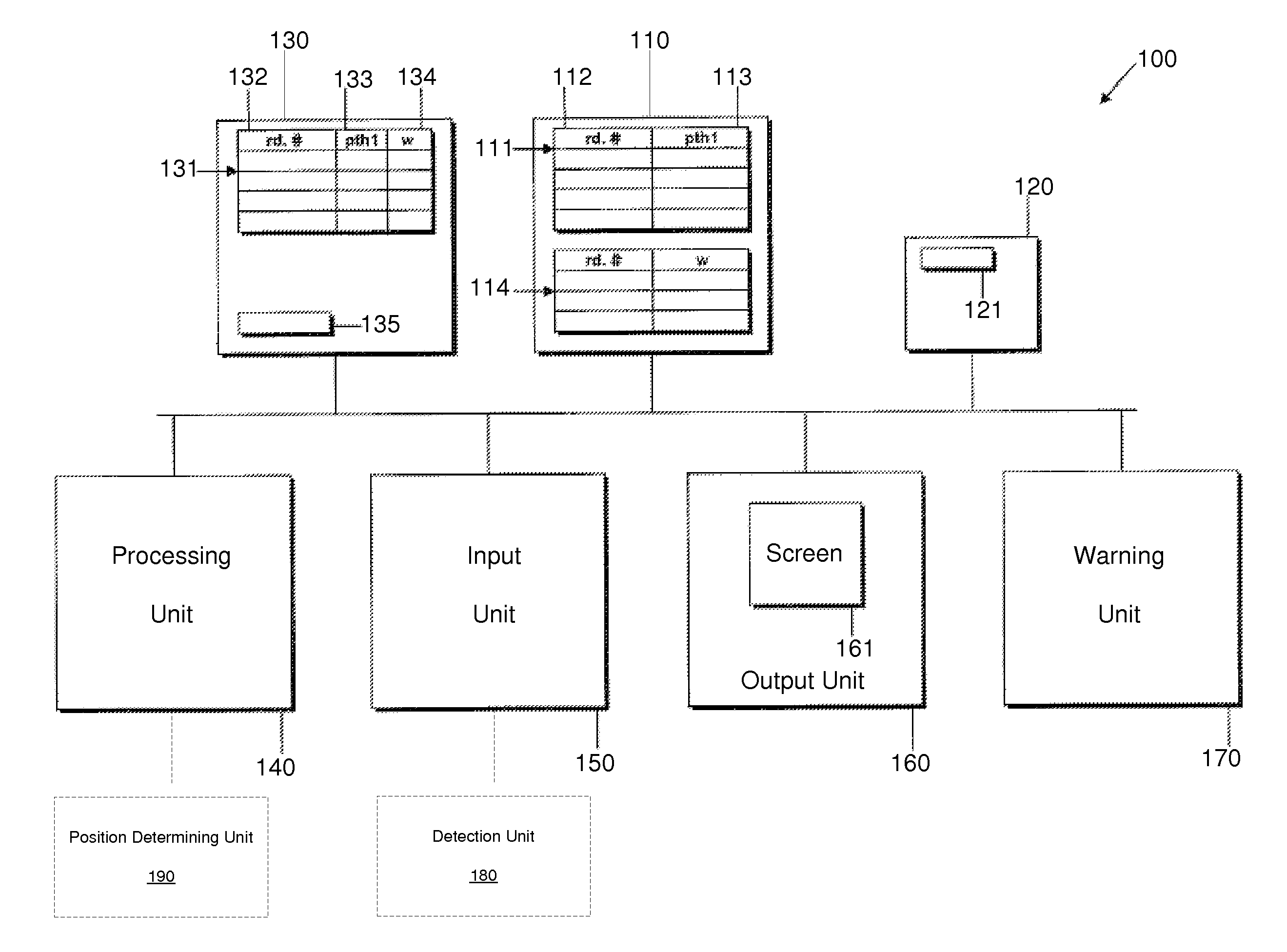
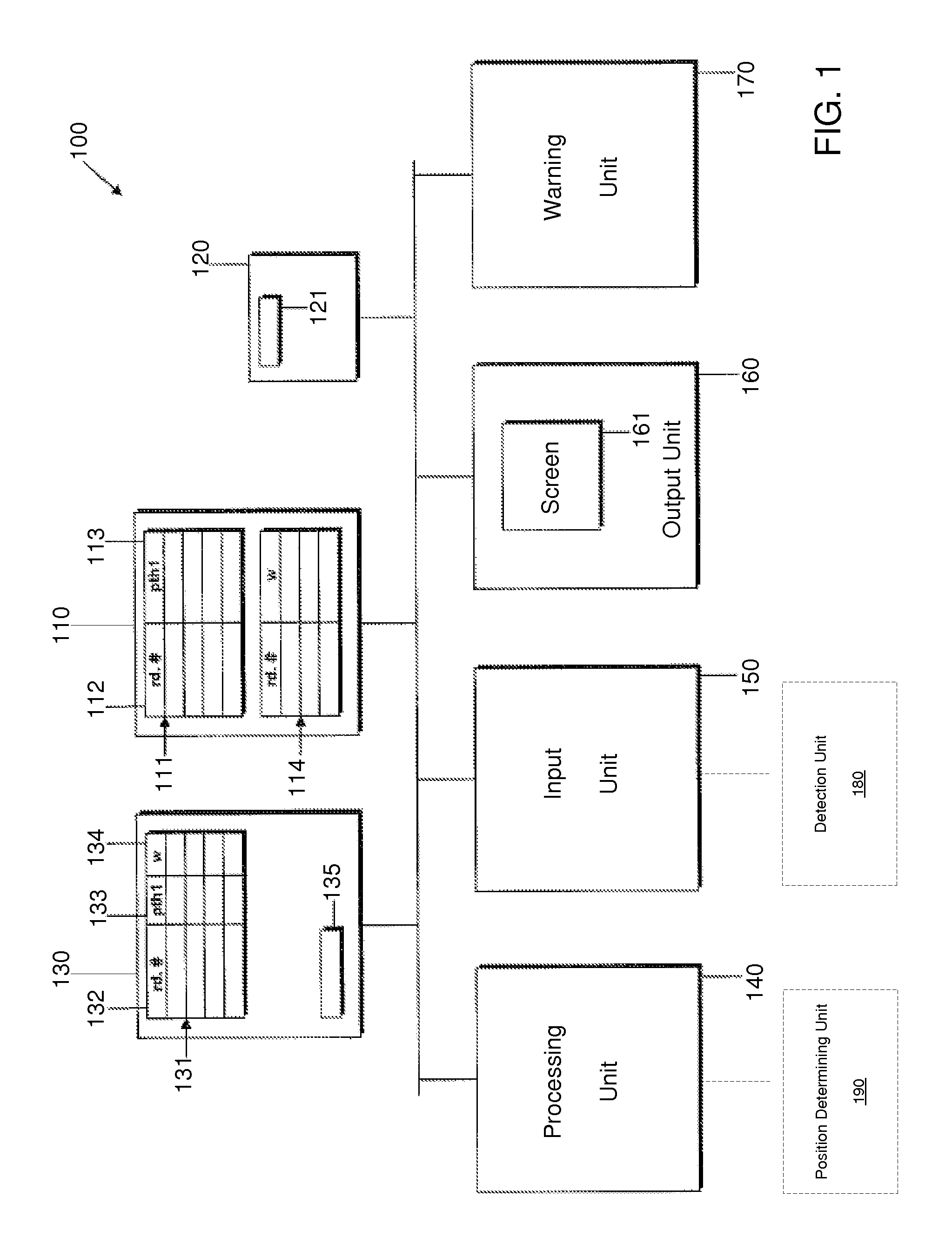
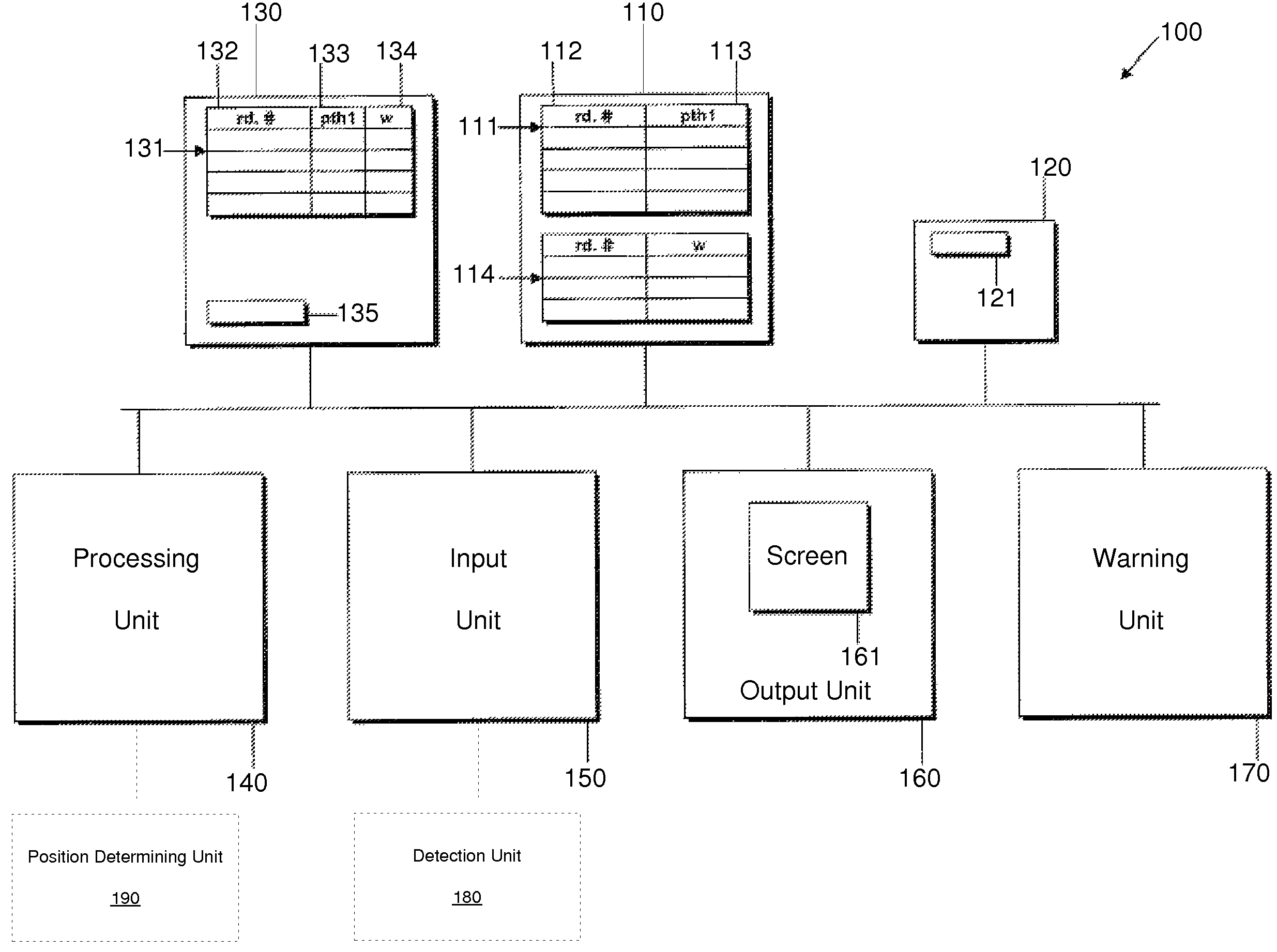
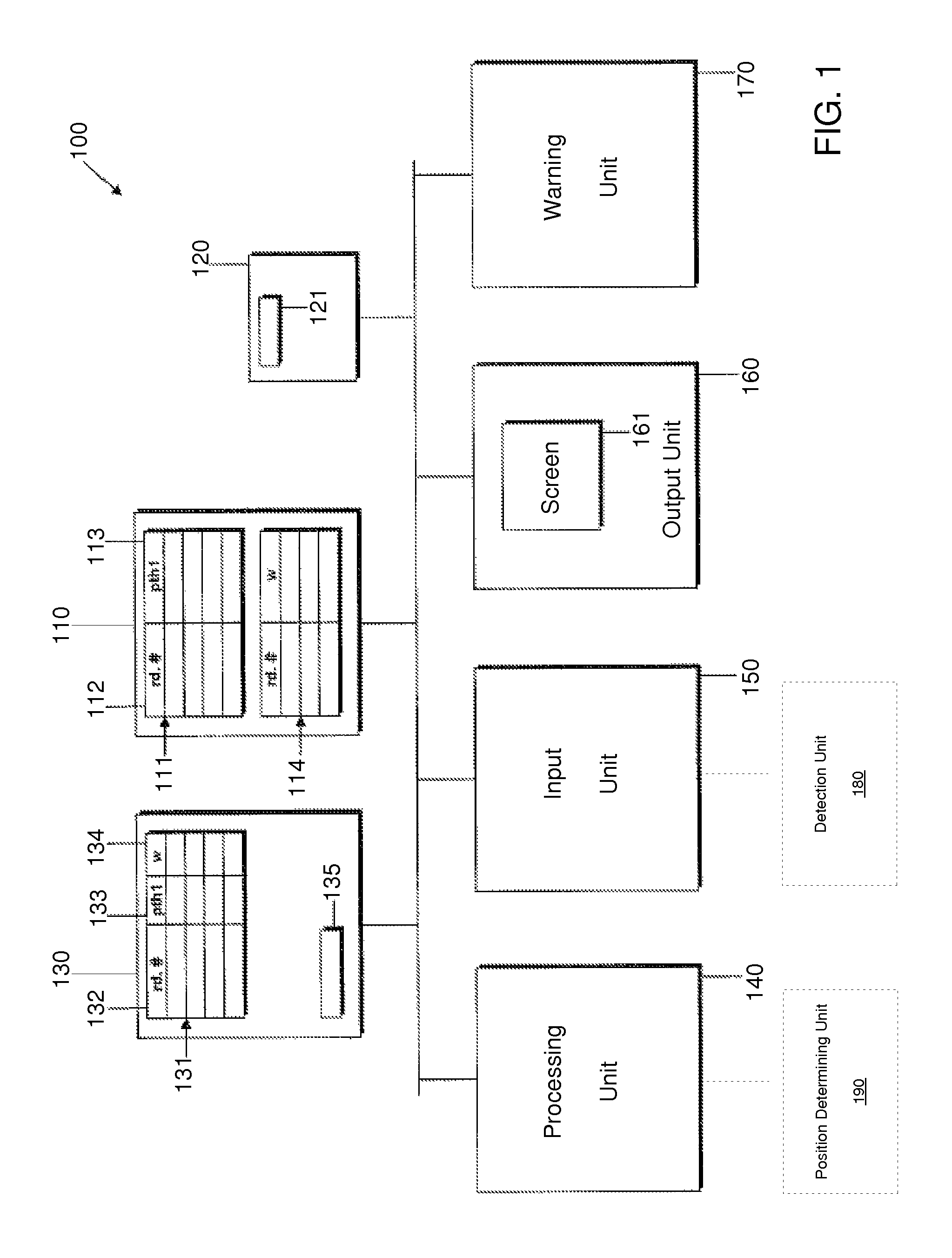
Route Determination and Driver Warning System
ActiveUS20070225900A1Instruments for road network navigationRoad vehicles traffic controlDriver/operatorWork memory
A system for determining a route and for warning a driver of a vehicle and corresponding methods are provided. The systems include storage units that store road segment passage restriction data and vehicle passage restriction data. The systems further include a working memory unit and a processing unit that determine a route to be displayed on an output unit or that provide a warning signal output, depending upon both the vehicle passage restriction data and the road segment passage restriction data.
Owner:HARMAN BECKER AUTOMOTIVE SYST
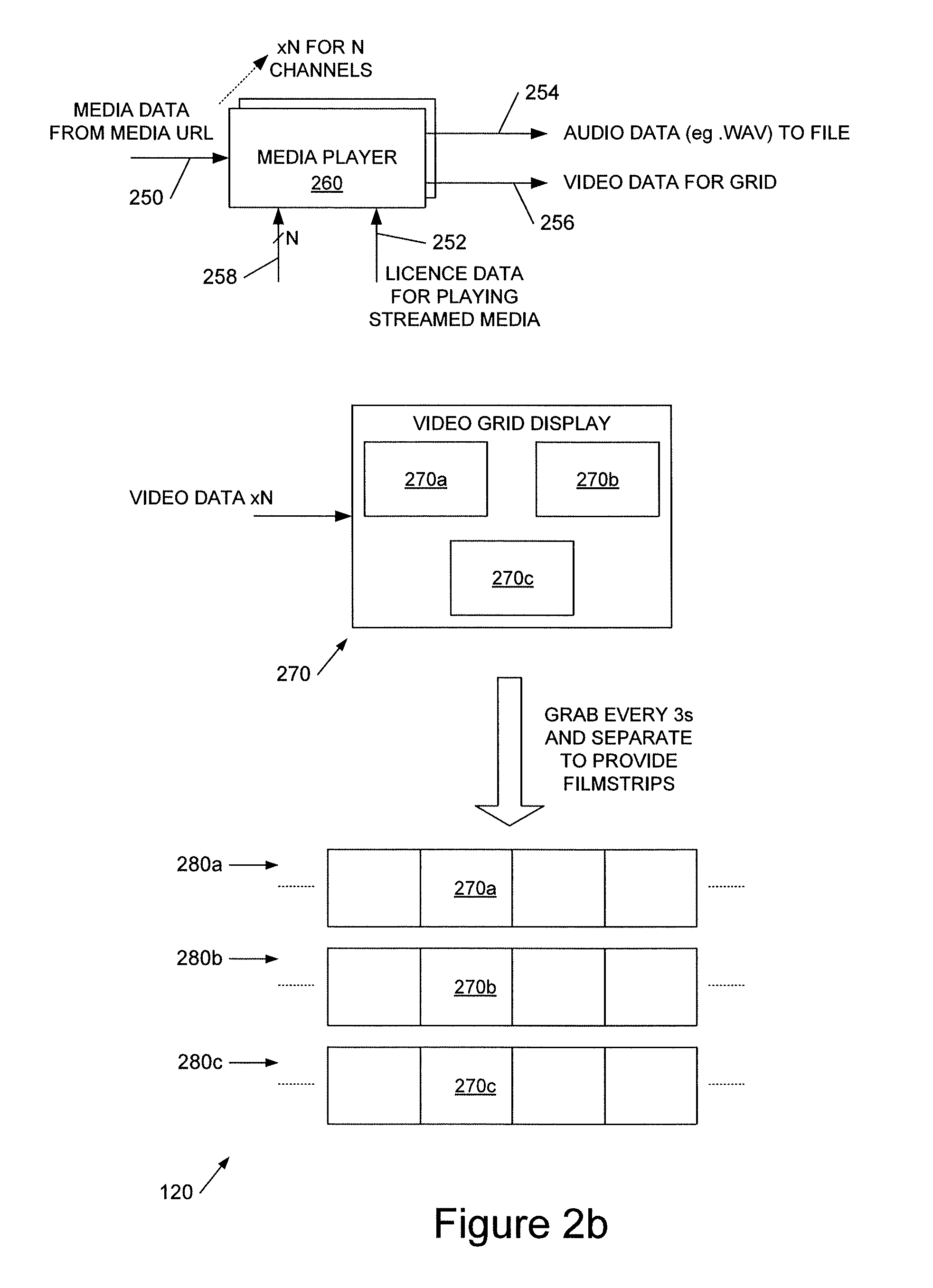
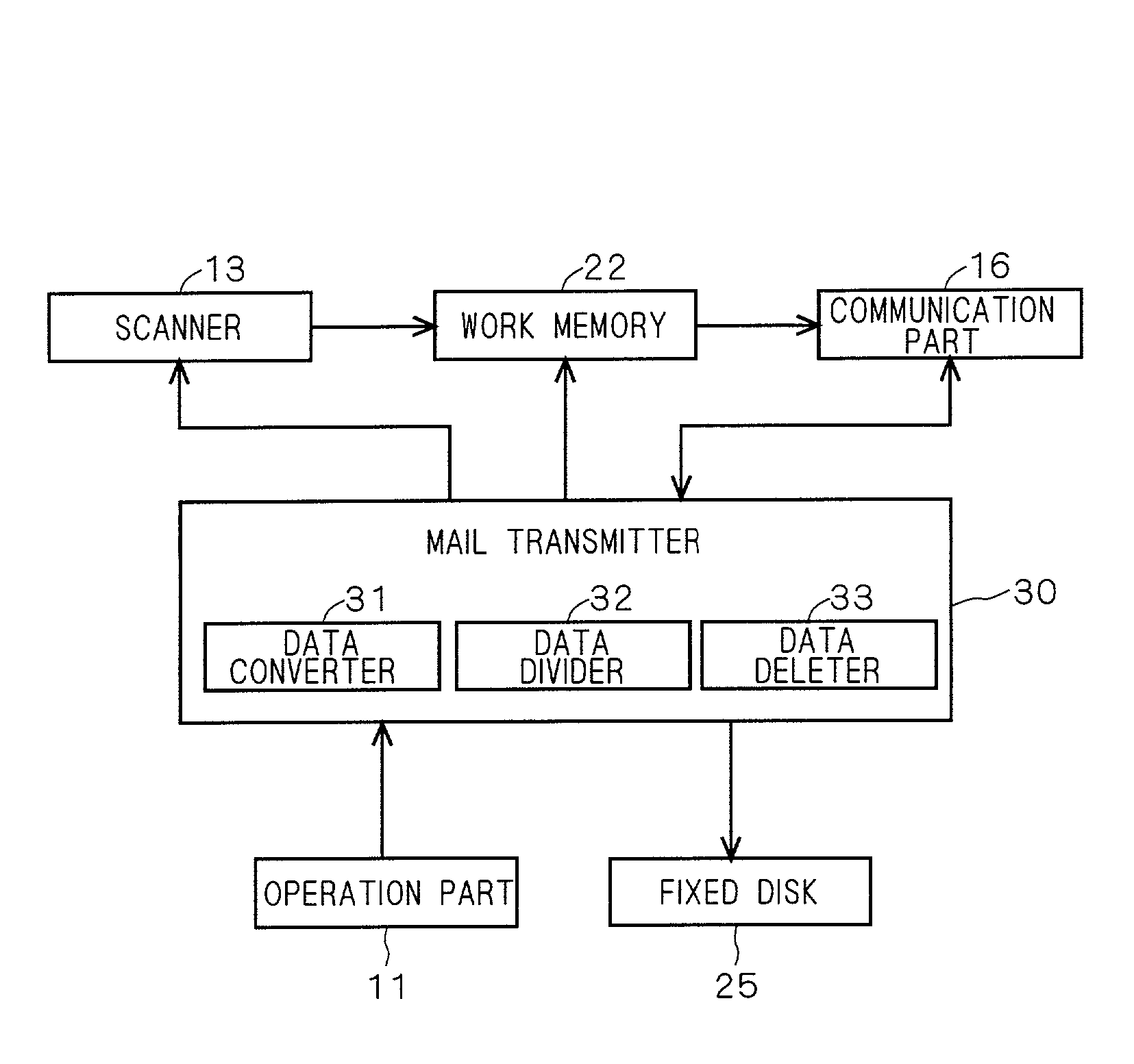
Image processing apparatus
InactiveUS20020140960A1Easy to useEfficiently re-transmittedDigitally marking record carriersHand compositionImaging processingComputer graphics (images)
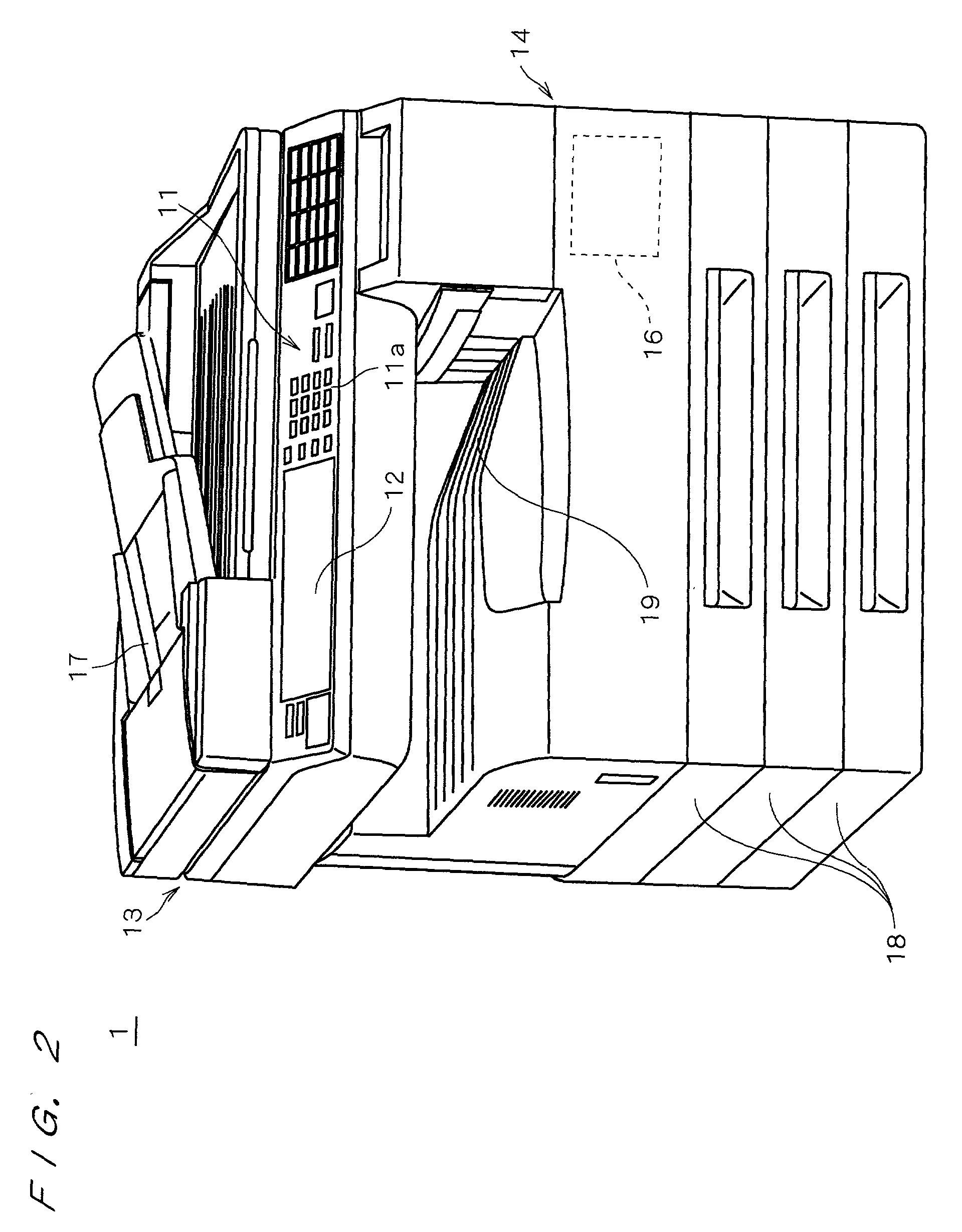
An MFP can transmit image data read by a scanner by attaching it to E-mail. At the time of transmission, the image data input by the scanner and stored in a work memory is converted into mail data so as to be transmitted by E-mail, and the mail data is stored again into the work memory. The mail data is divided every predetermined reference data size into divided files which are sequentially transmitted as divided mails. When completion of transmission of divided mails corresponding to a unit image is confirmed, the image data and mail data of the unit image are eliminated from the work memory. By sequentially performing such a process, the memory use efficiency can be improved while holding image data of a unit image which has not been transmitted yet.
Owner:MINOLTA CO LTD
Route determination and driver warning system
ActiveUS7761227B2Instruments for road network navigationRoad vehicles traffic controlMain processing unitDriver/operator
A system for determining a route and for warning a driver of a vehicle and corresponding methods are provided. The systems include storage units that store road segment passage restriction data and vehicle passage restriction data. The systems further include a working memory unit and a processing unit that determine a route to be displayed on an output unit or that provide a warning signal output, depending upon both the vehicle passage restriction data and the road segment passage restriction data.
Owner:HARMAN BECKER AUTOMOTIVE SYST
Method for solving finite element models using time slabbing
InactiveUS7006951B2Reduce memory usageGeometric CADComputation using non-denominational number representationElement modelEngineering
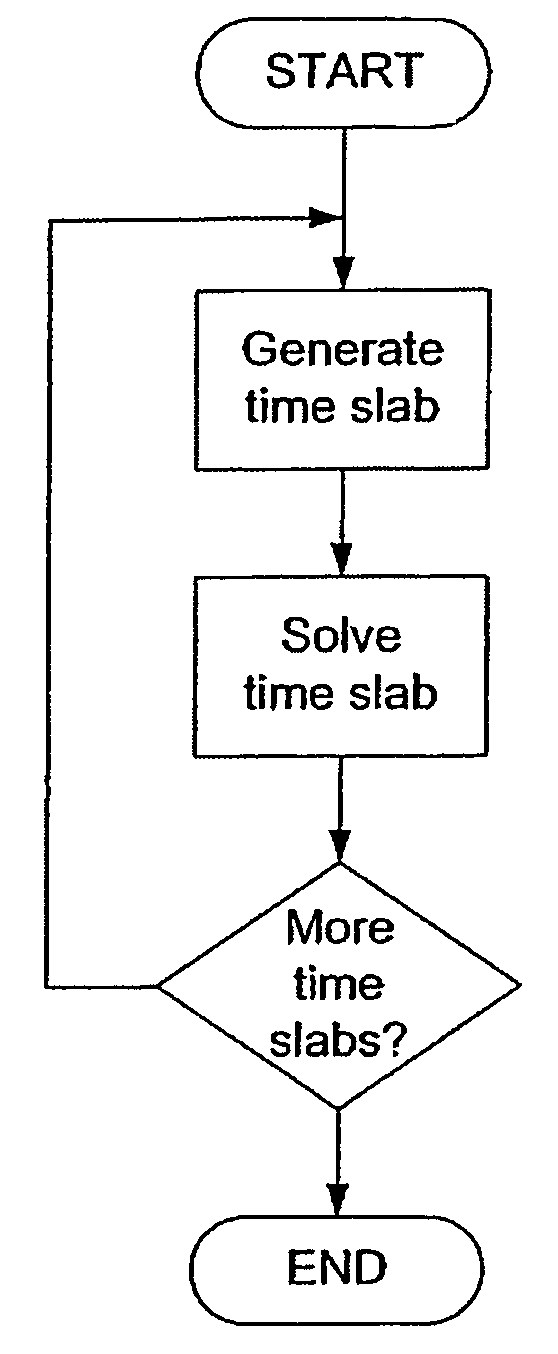
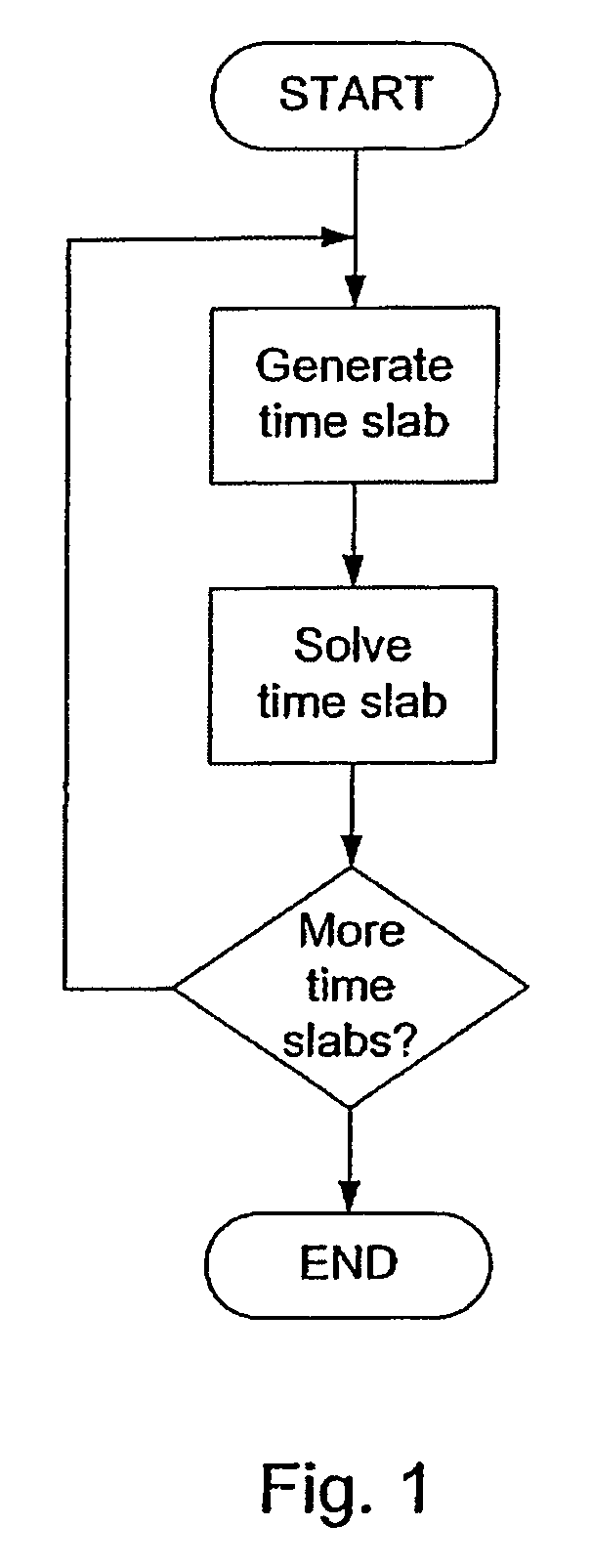
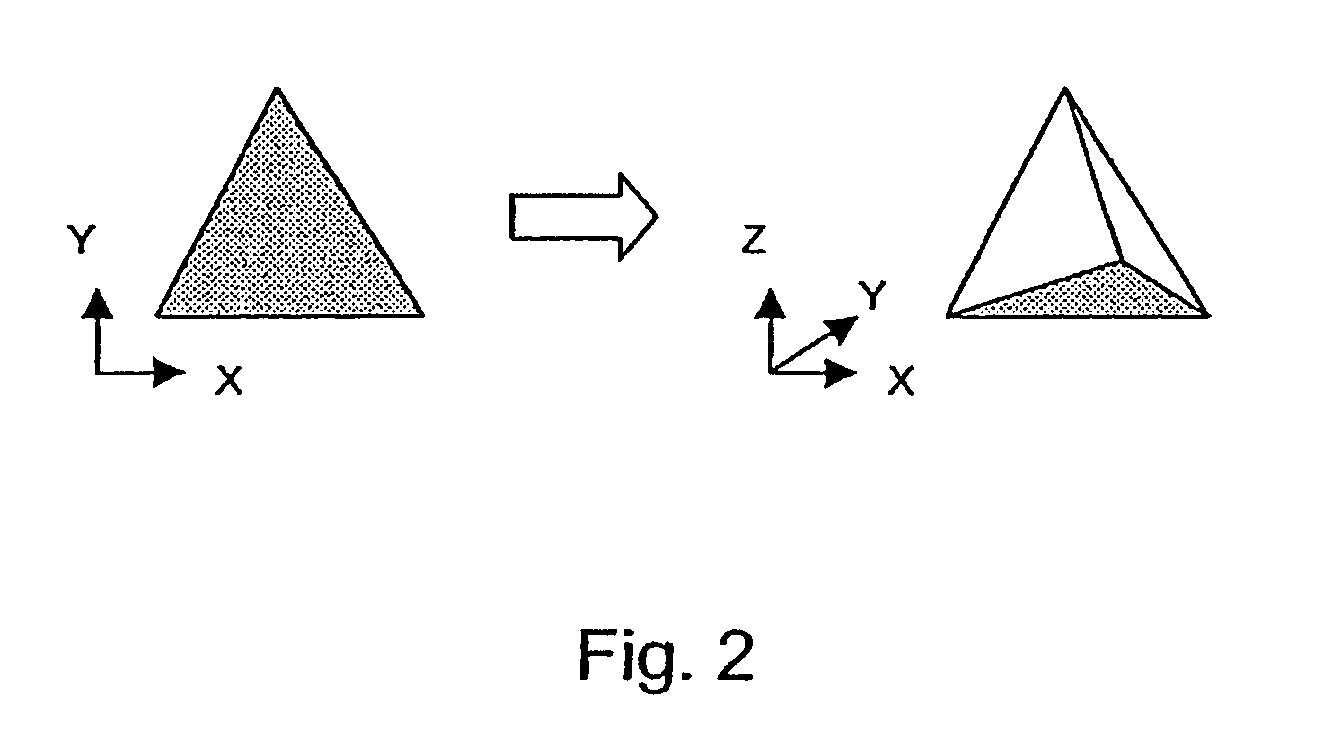
A method for solving finite element problems in n+1 dimensions by iteratively extruding an n-dimensional finite element mesh in an n+1th dimension to form “slabs” which can be more easily solved within the entire n+1-dimensional problem. In a preferred embodiment, a three-dimensional unstructured finite element mesh representing a physical system is extruded in the time dimension. The four-dimensional prisms formed by the extrusion are divided into simplices, forming the four-dimensional finite element mesh of an individual time slab. Time slabs corresponding to a series of time intervals are sequentially generated and solved. In a preferred embodiment, only a few time slabs are stored in working memory at a time so that a reduced amount of memory (in comparison to conventional methods of solving comparable problems) is required.
Owner:LANDMARK GRAPHICS CORP
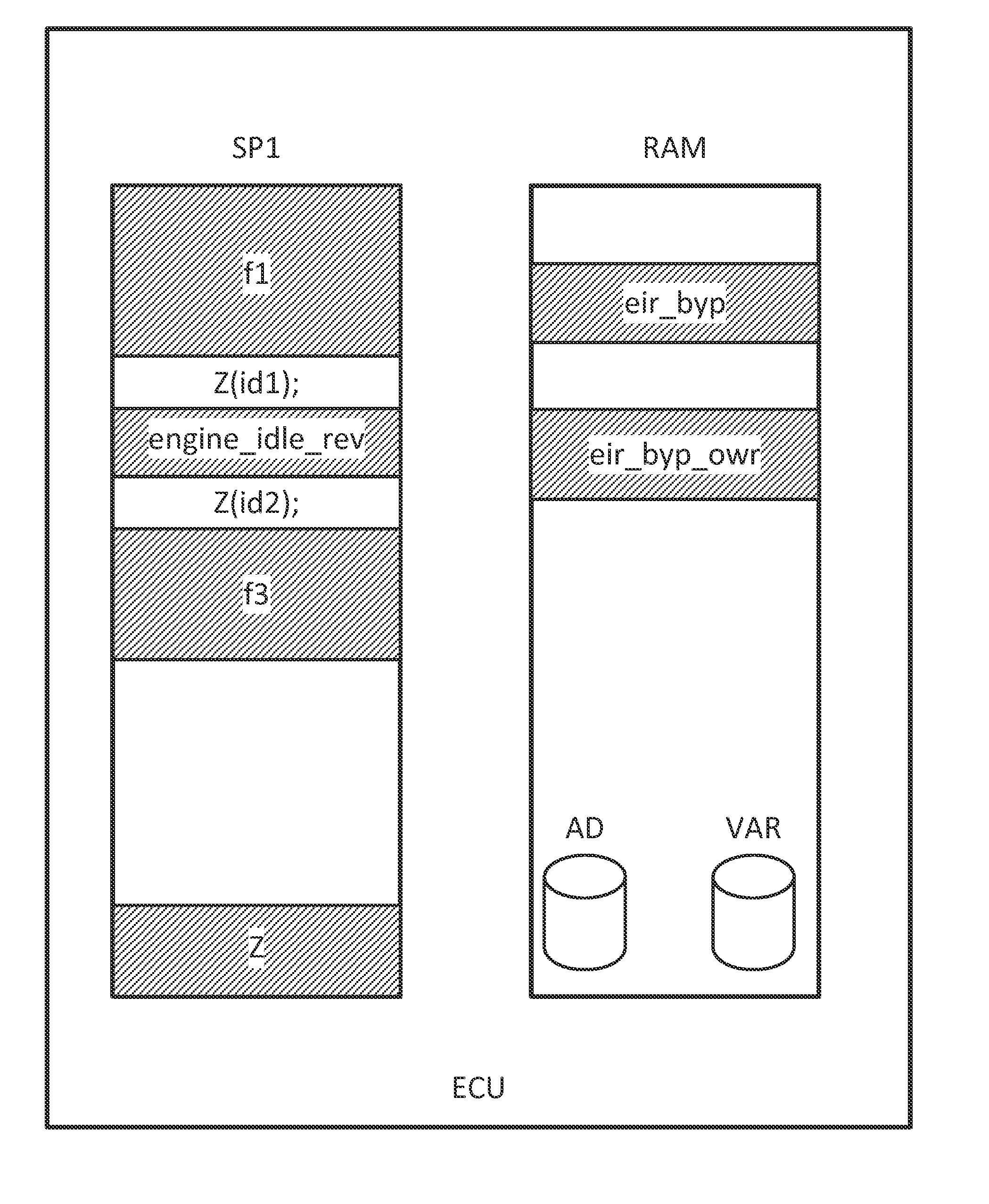
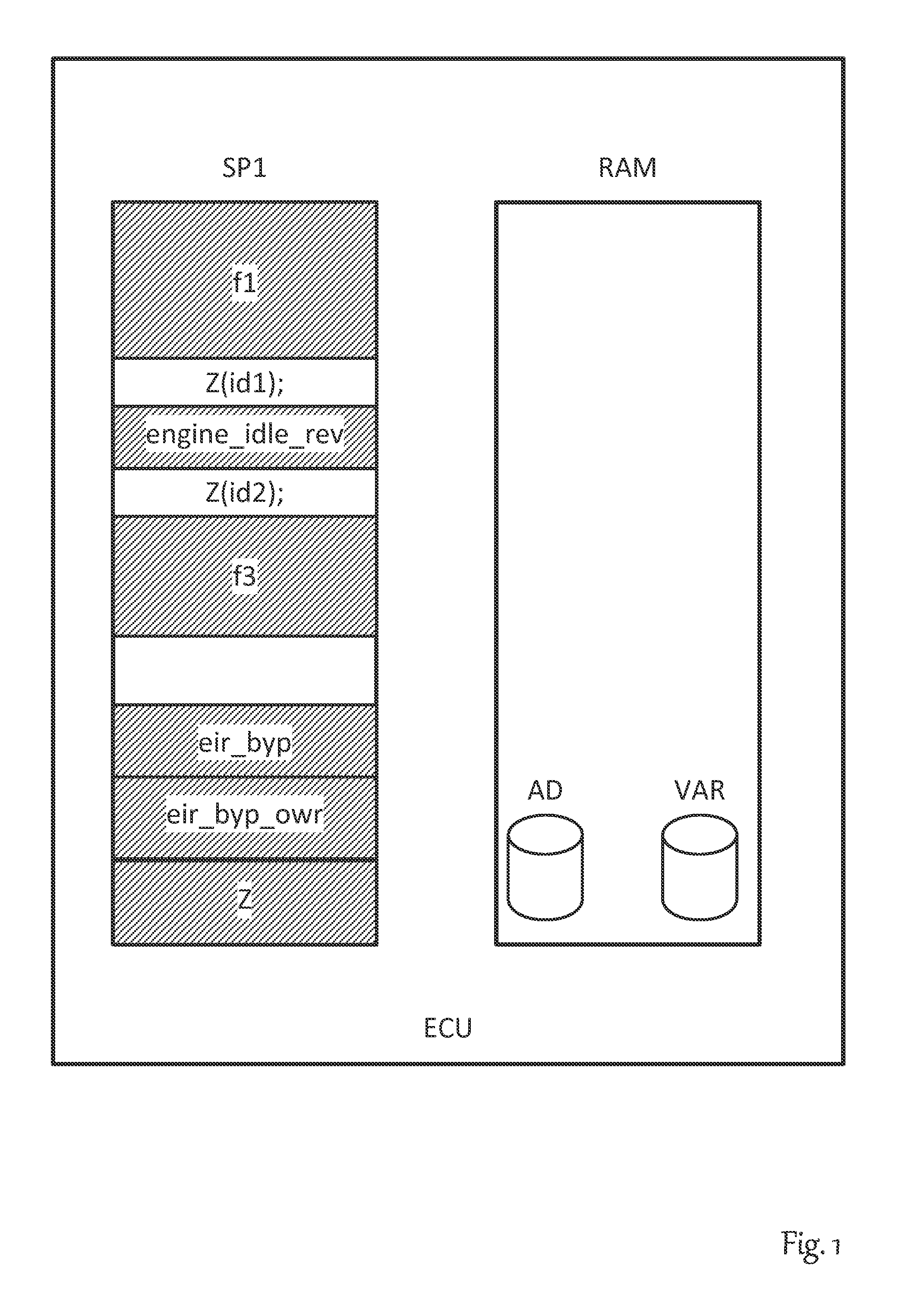
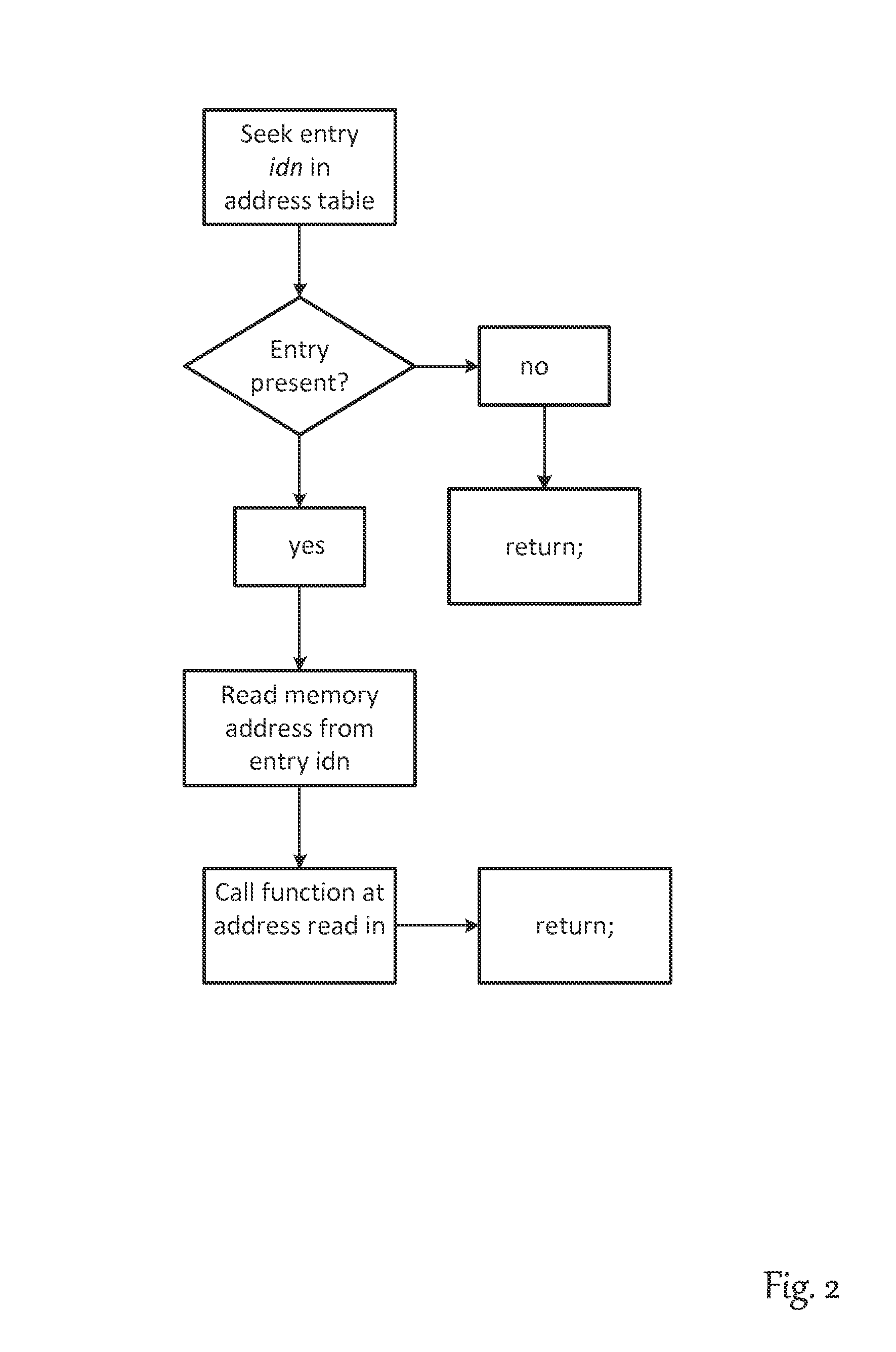
Method for changing the software in the memory of an electronic control unit
A method for changing a software in the memory of an electronic control unit. A bypass routine is stored in the working memory of the electronic control unit, and the address of the bypass function is stored in a table. A service function reads the address from the table and calls the bypass routine. The bypass routine is replaceable at the run time of the electronic control unit by erasing the table entry. The call of the service function is integrated into the program code of the electronic control unit by an overlay memory, a memory management unit, or with the aid of watch points.
Owner:DSPACE DIGITAL SIGNAL PROCESSING & CONTROL ENG
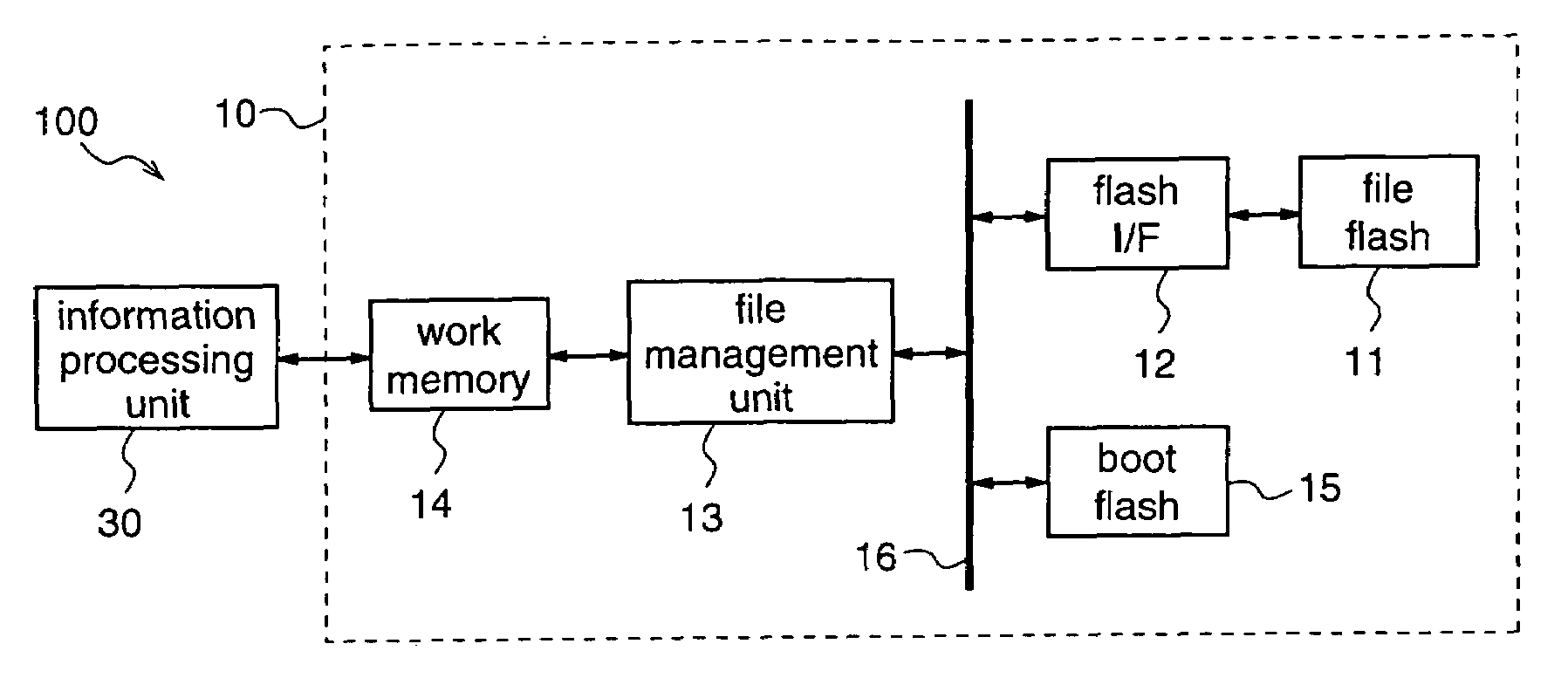
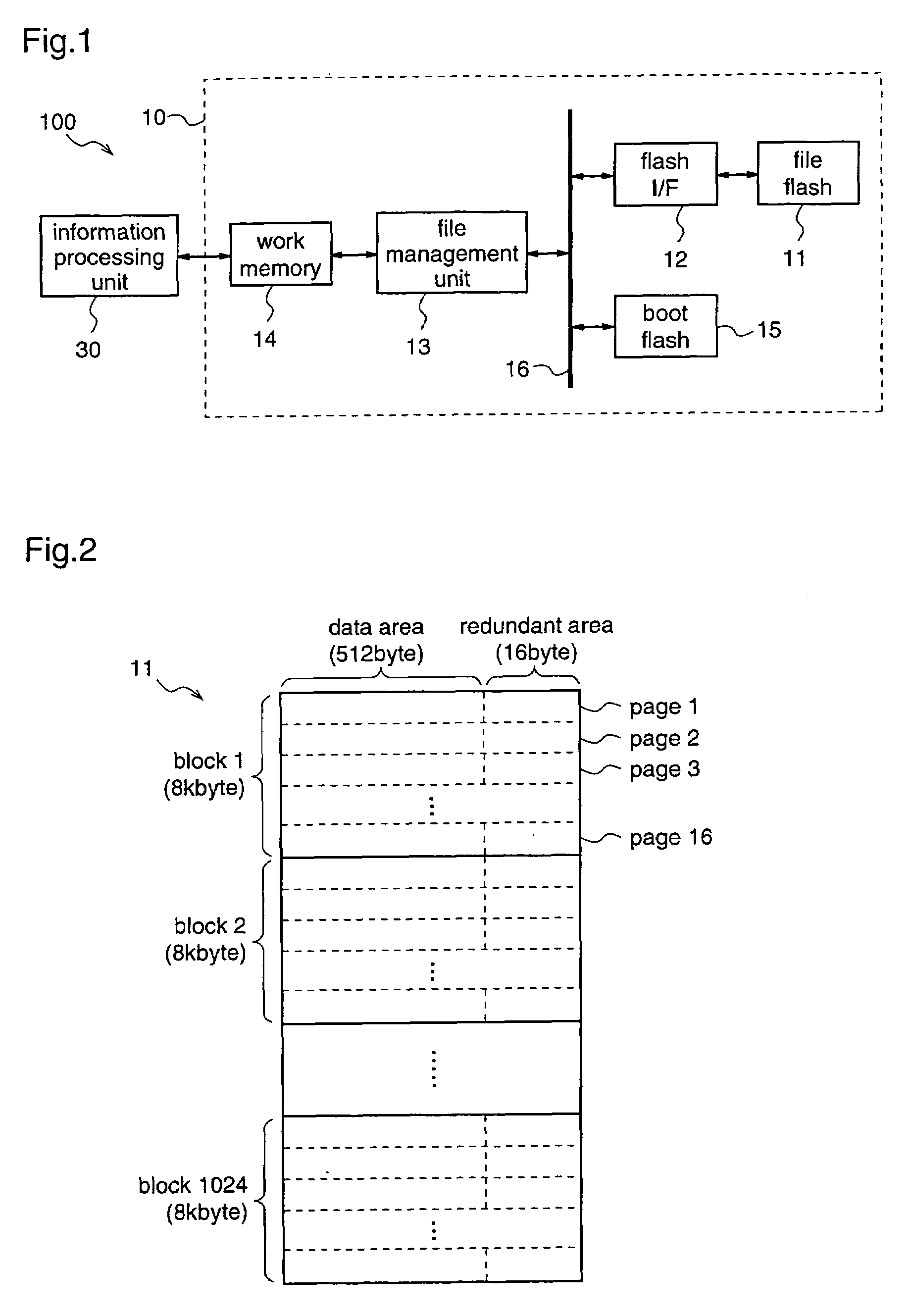
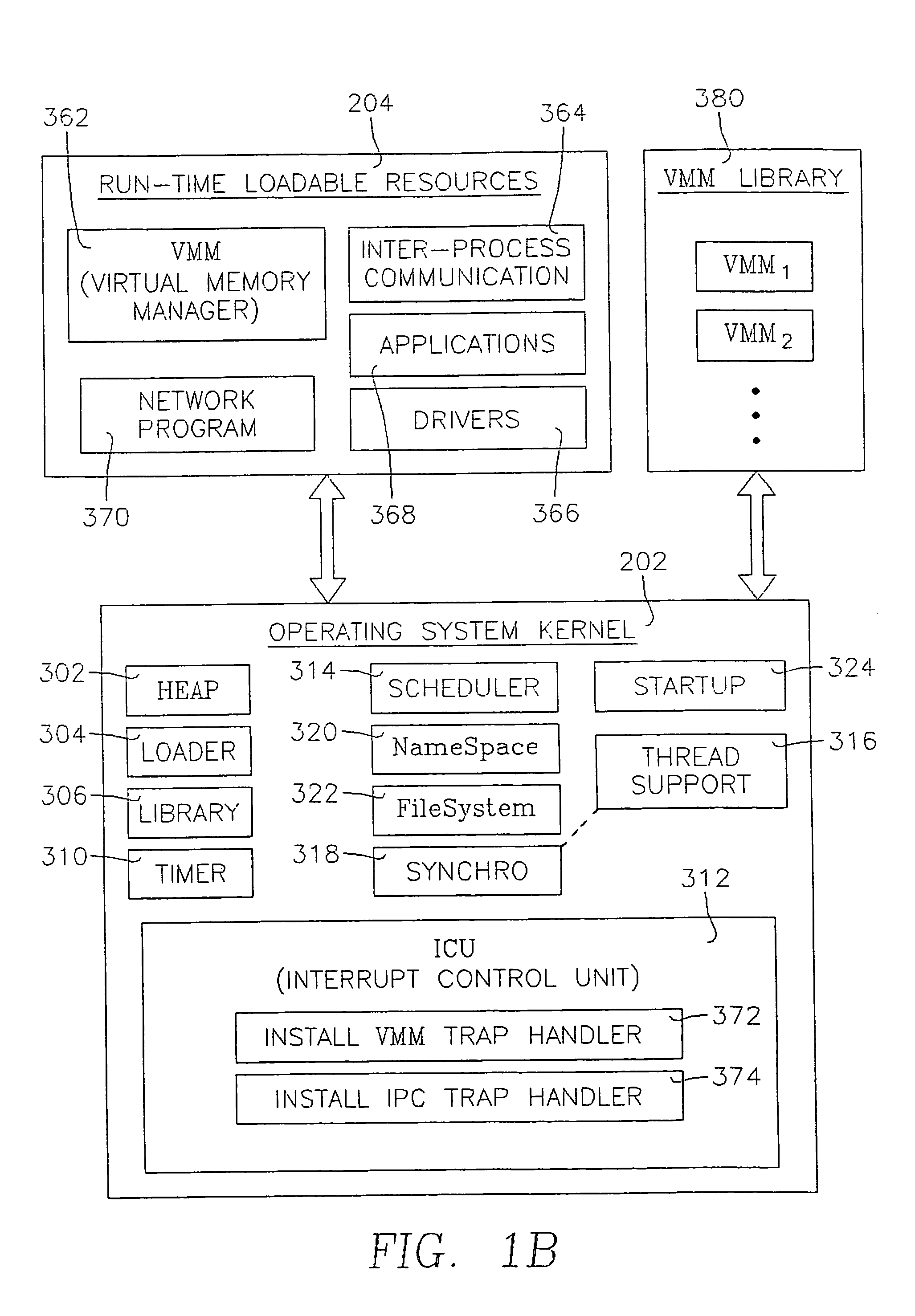
Information processing apparatus, memory management apparatus, memory management method, and information processing method
InactiveUS7418436B2Improve processing speedReduced execution timeData processing applicationsLink editingInformation processingWork memory
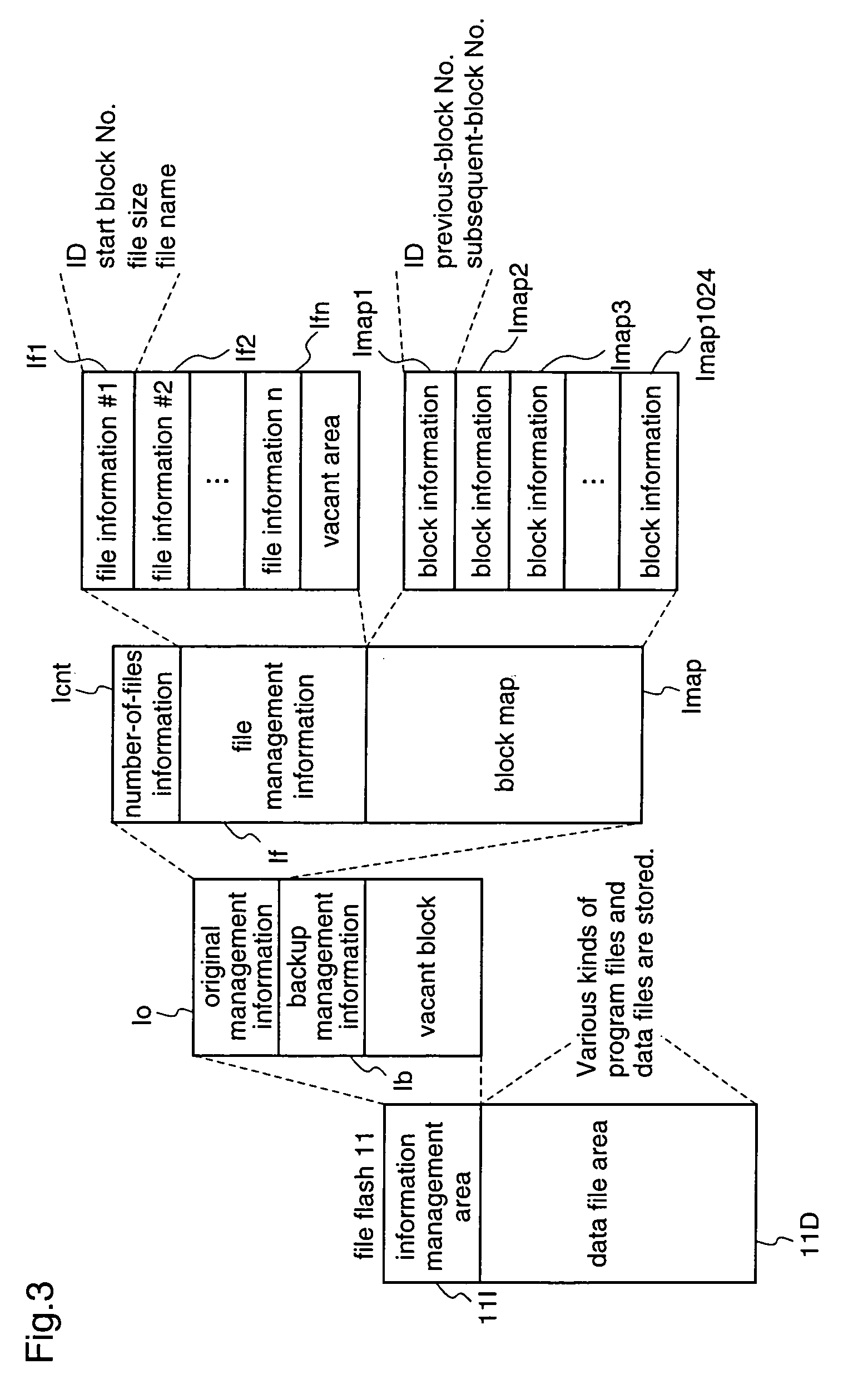
It is an object to provide an information processing apparatus and a memory management method, which realize highly reliable writing and reading of data into / from a serial flash memory, and reduce the execution time of a CPU by booting at power-on. An information processing apparatus is composed of a memory management unit for storing files, and an information processing unit for performing processing on the basis of a program file supplied from the memory management unit, and the memory management unit is composed of a file flash for storing files, a file management unit for managing the files stored in the file flash, a work memory as a work area of the information processing unit, a flash I / F 12 for making access from the file management unit to the file flash, and a boot flash for storing a boot program.
Owner:GK BRIDGE 1
Method and apparatus for booting a computer system
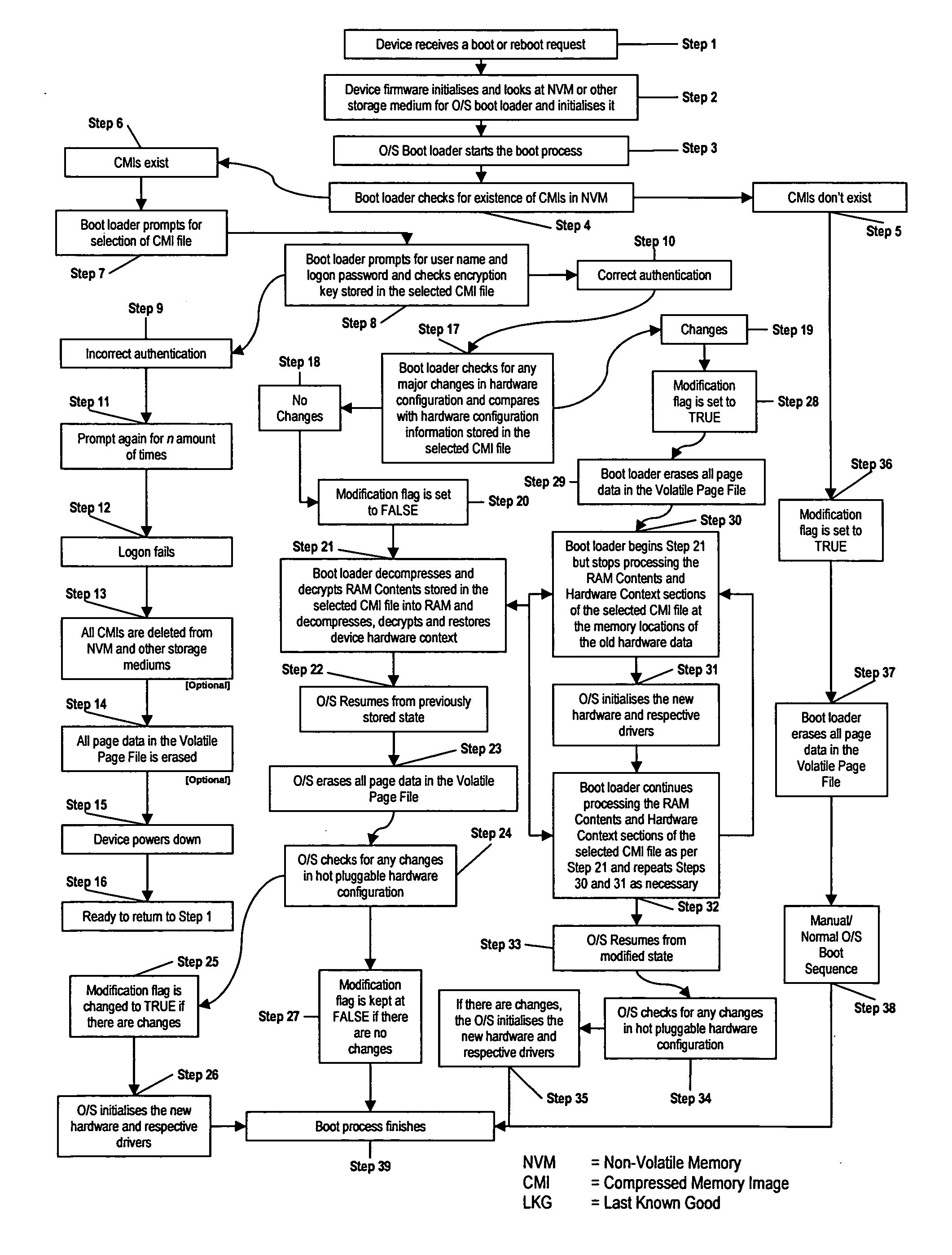
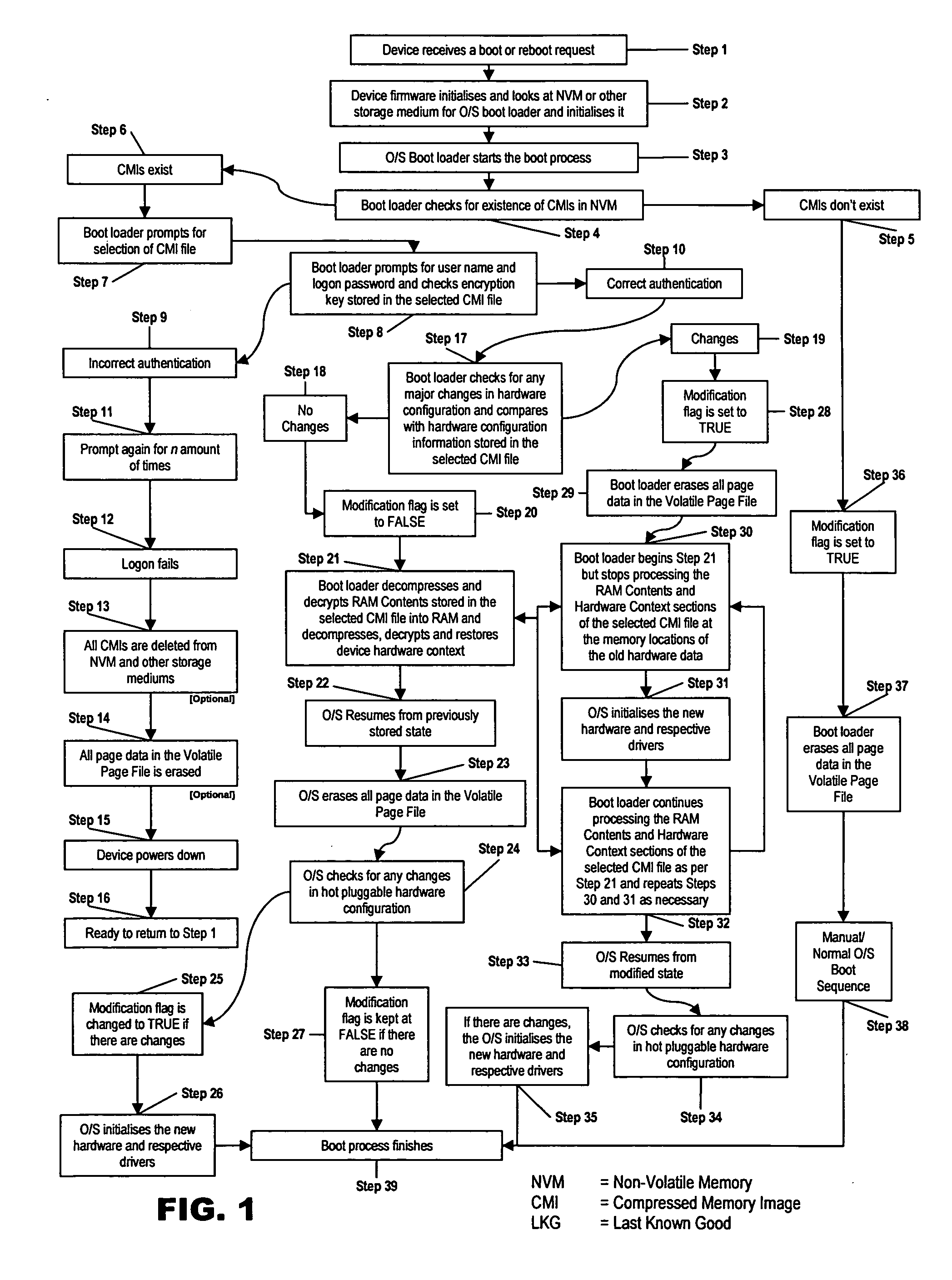
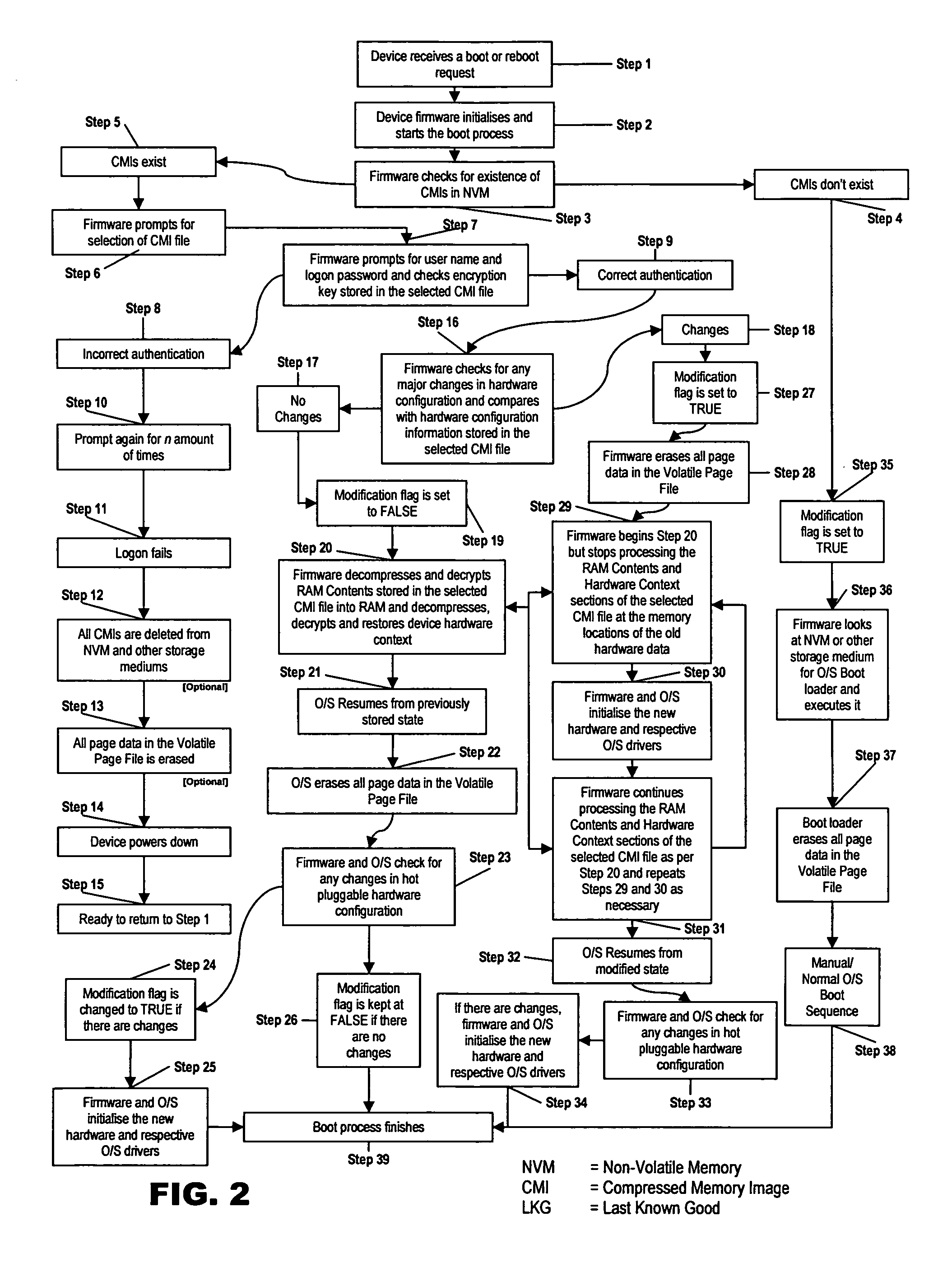
InactiveUS20050044348A1Shorten the timeEnvironment safetyDigital computer detailsData resettingWork memoryPersonal computer
A method for quickly booting a personal computer system using a non-volatile reprogrammable memory device. A compressed memory image of the contents of the system working memory, hardware configuration and other information stored in memory when the system is in a desired operational state is stored in the non-volatile reprogrammable memory. When rebooting the process detects changed hardware and diverts from the reboot to identify the hardware before continuing.
Owner:TI TECH
Mobile device and a method of controlling the mobile device
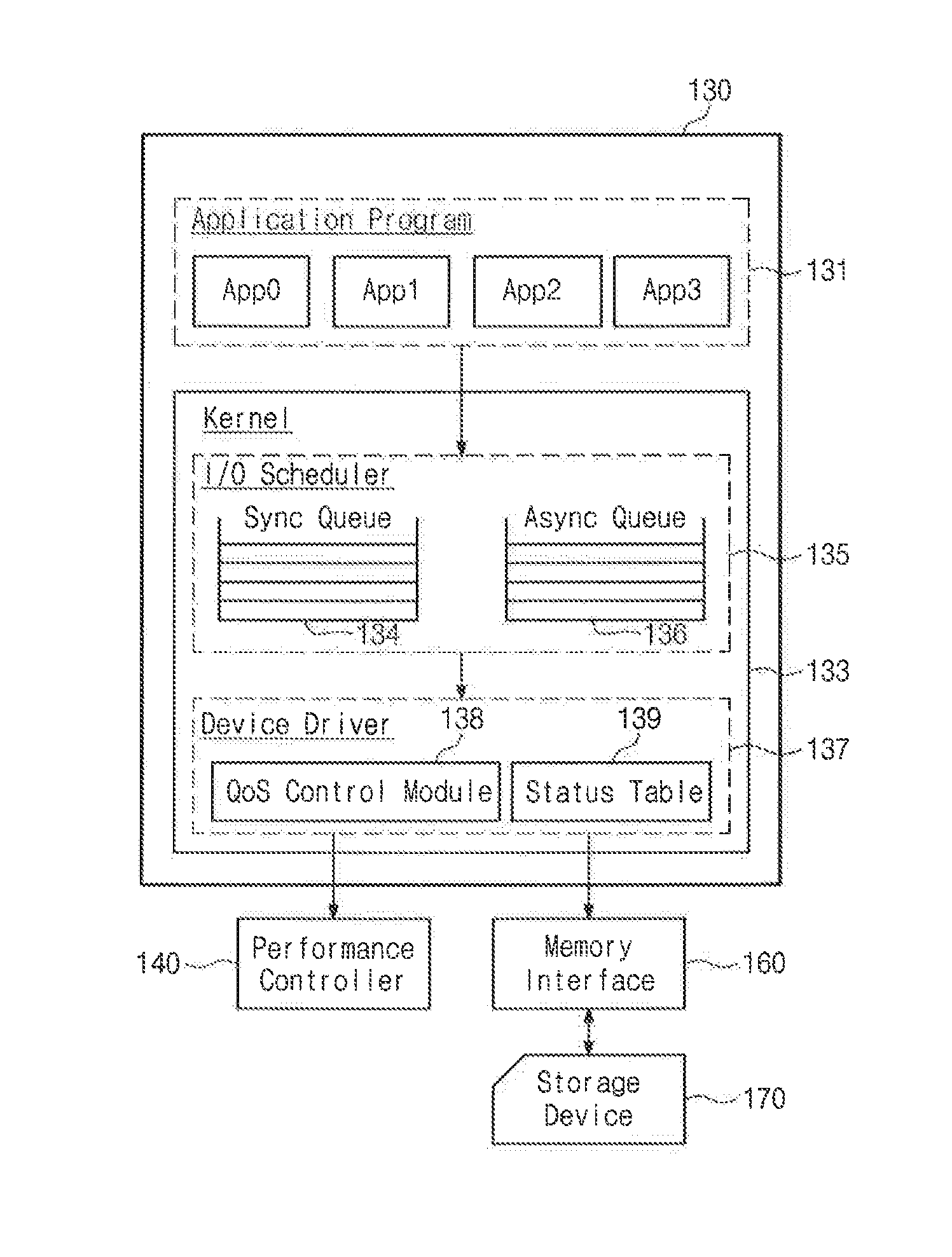
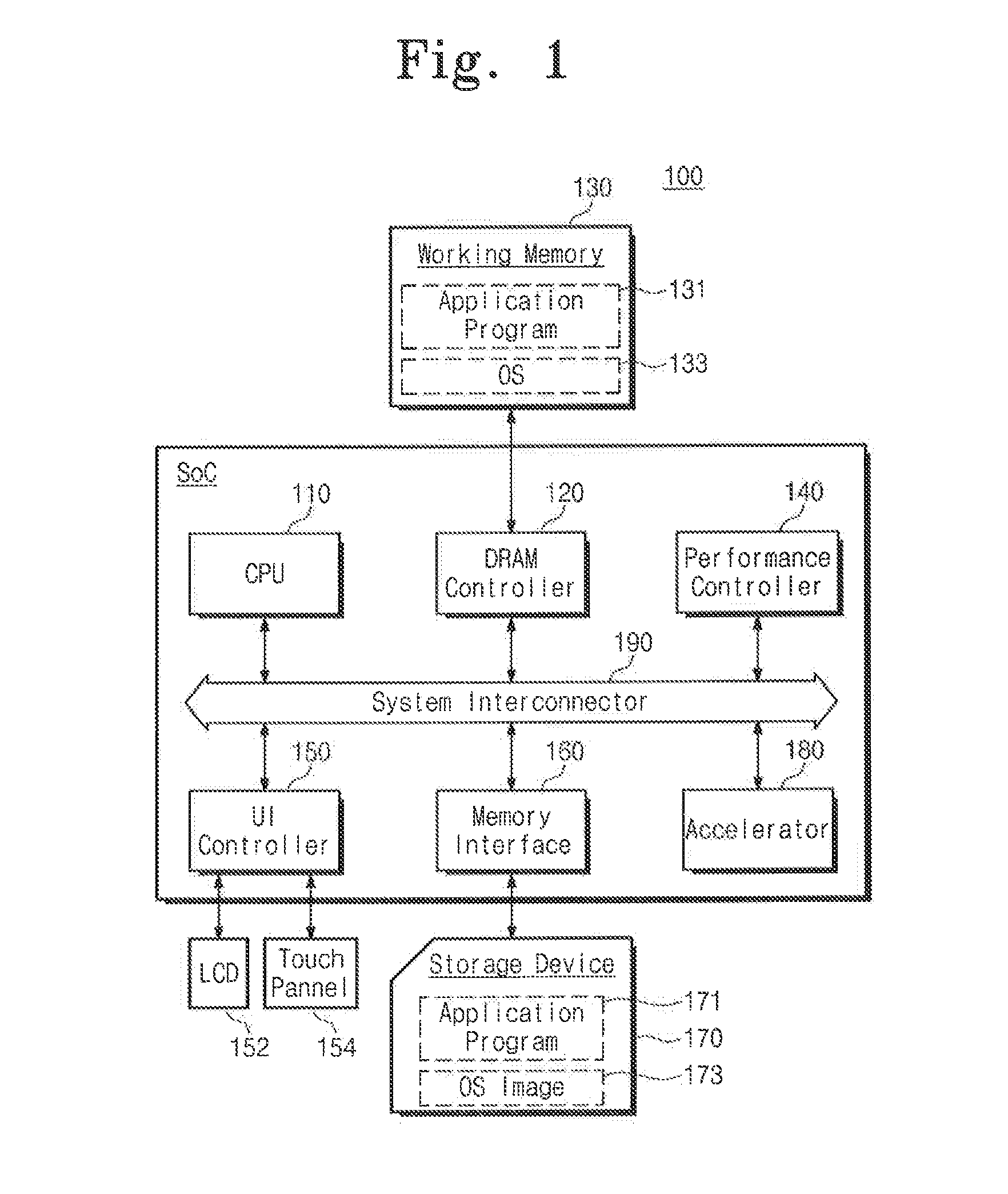
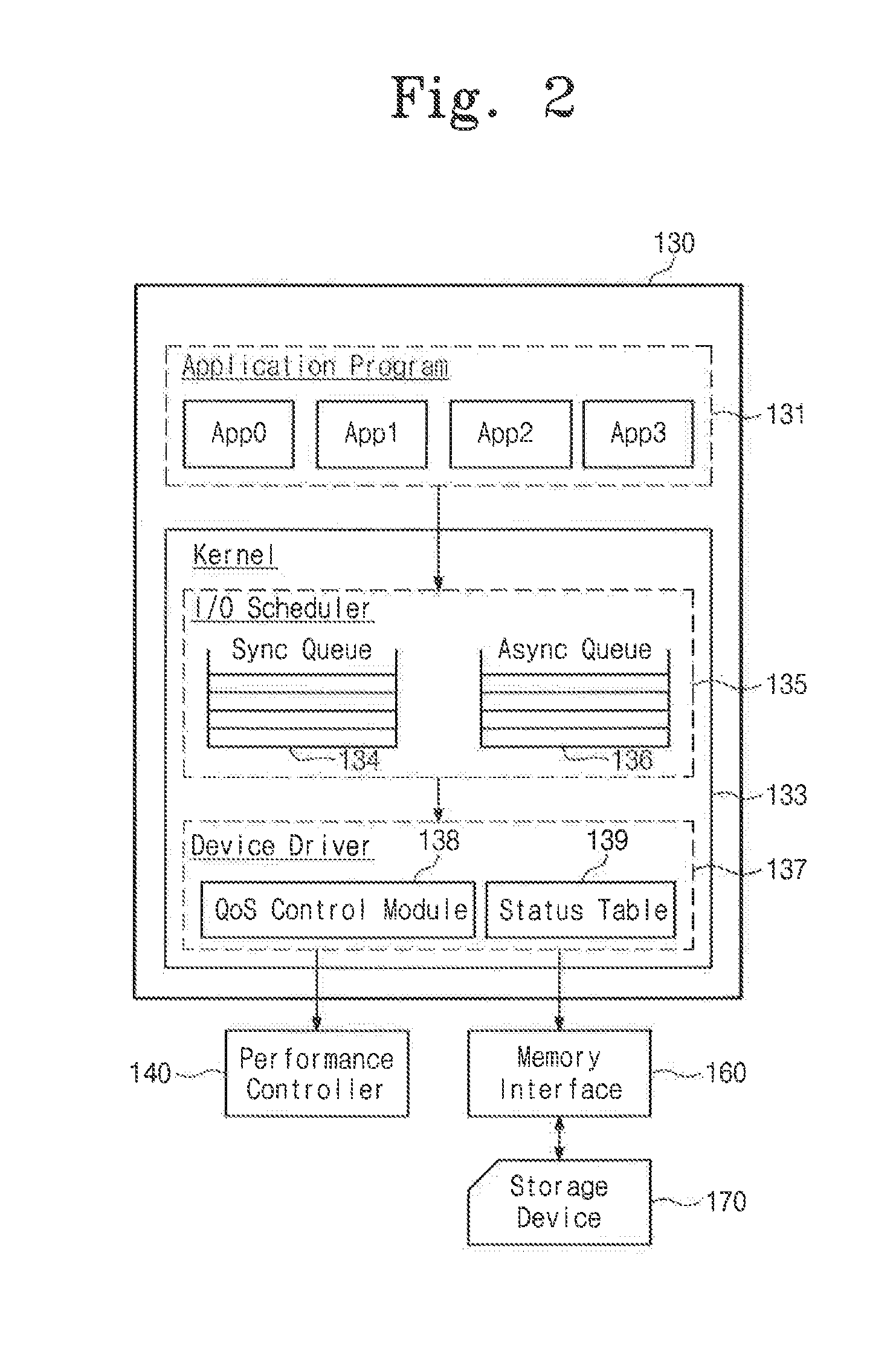
A mobile device including: a storage device; a system-on-chip (SOC) including a central processing unit (CPU) and a memory interface configured to access the storage device in response to a request of the CPU; and a working memory including an input / output (I / O) scheduler and a device driver, the I / O scheduler configured to detect real time processing requests and store the real time processing requests in a sync queue, and detect non-real time processing requests and store the non-real time processing requests in an async queue, the device driver configured to adjust the performance of the mobile device based on the number of requests in the sync queue.
Owner:SAMSUNG ELECTRONICS CO LTD
Video-based system and method for counting persons traversing areas being monitored
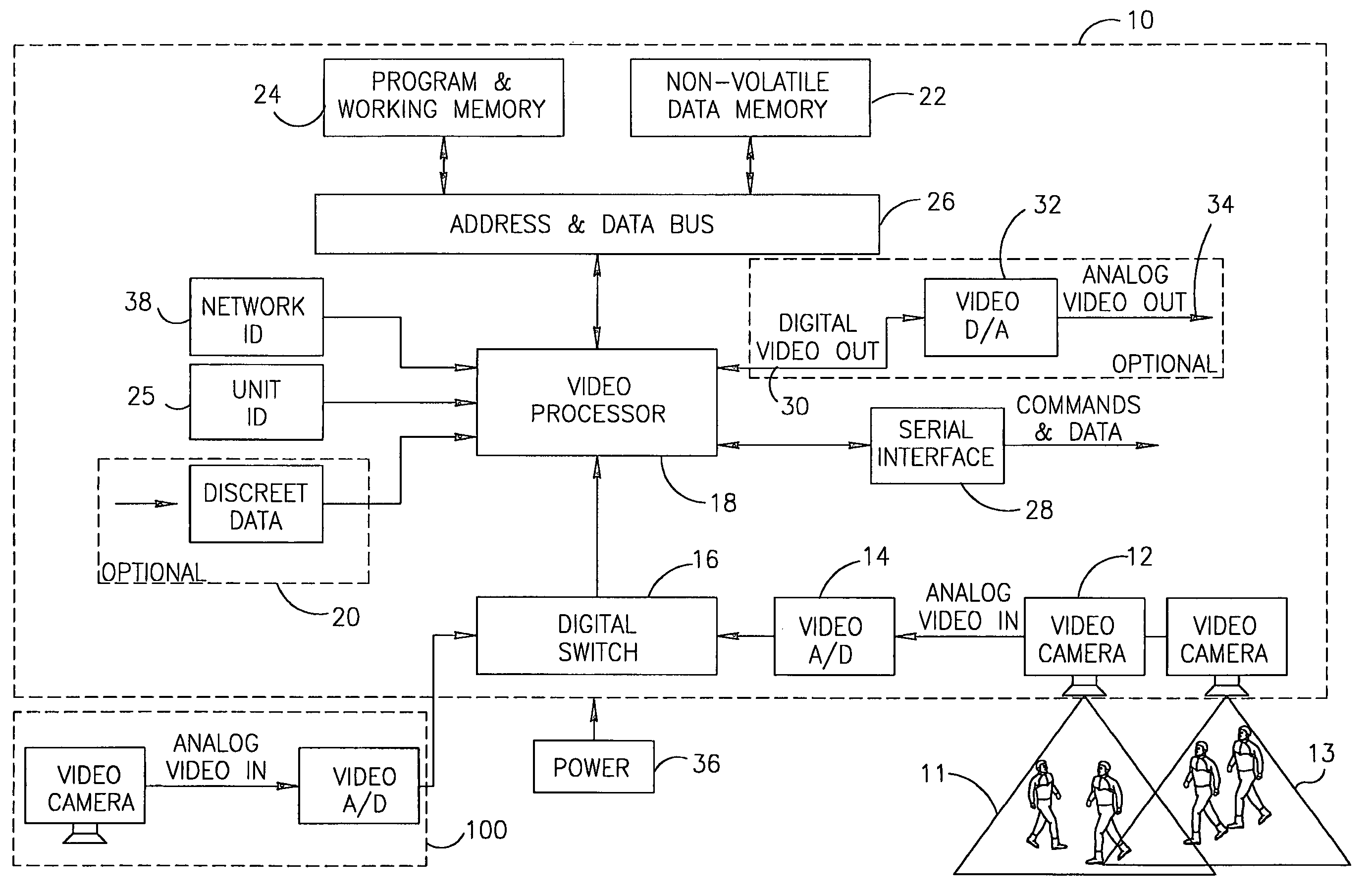
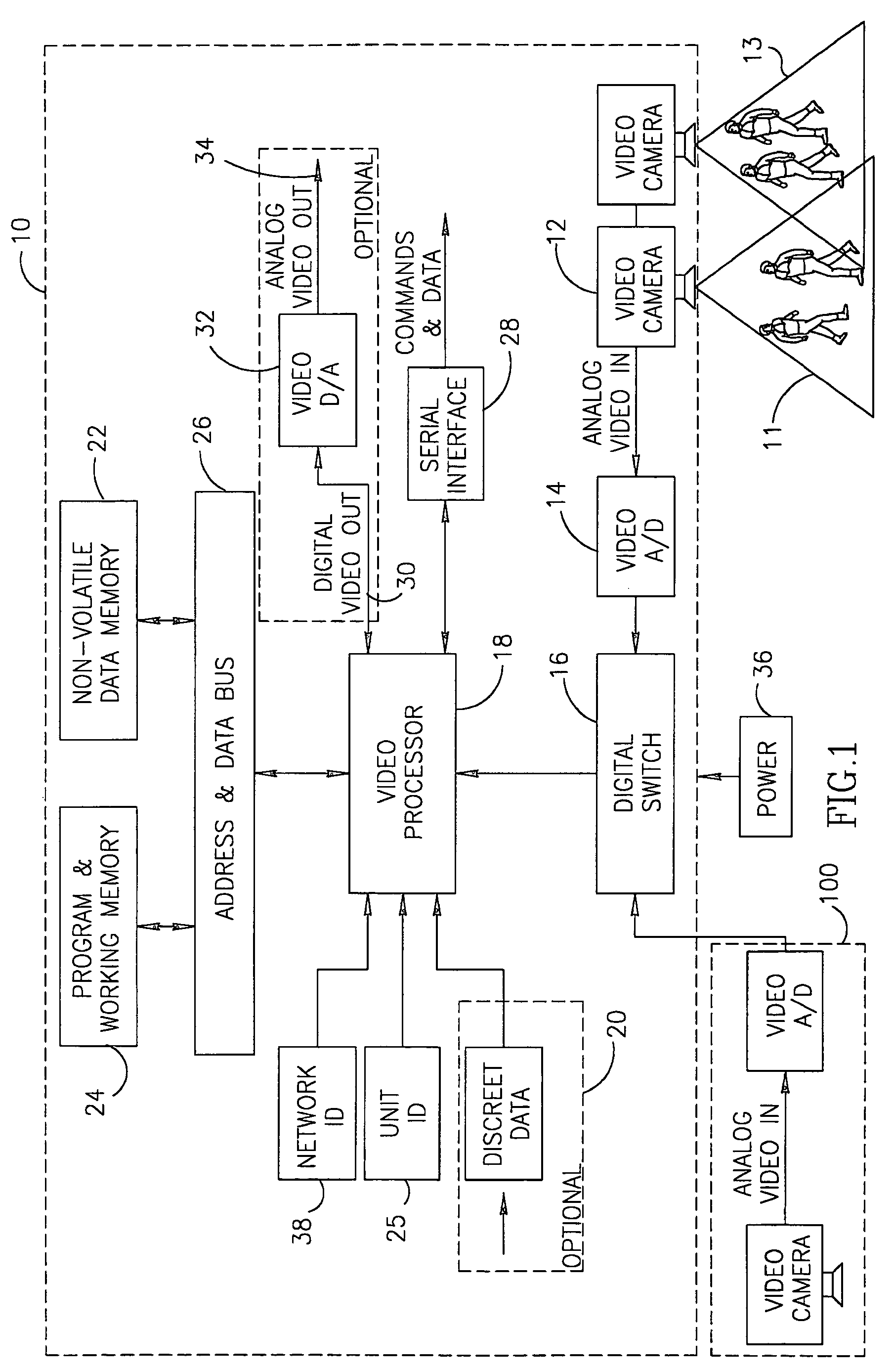
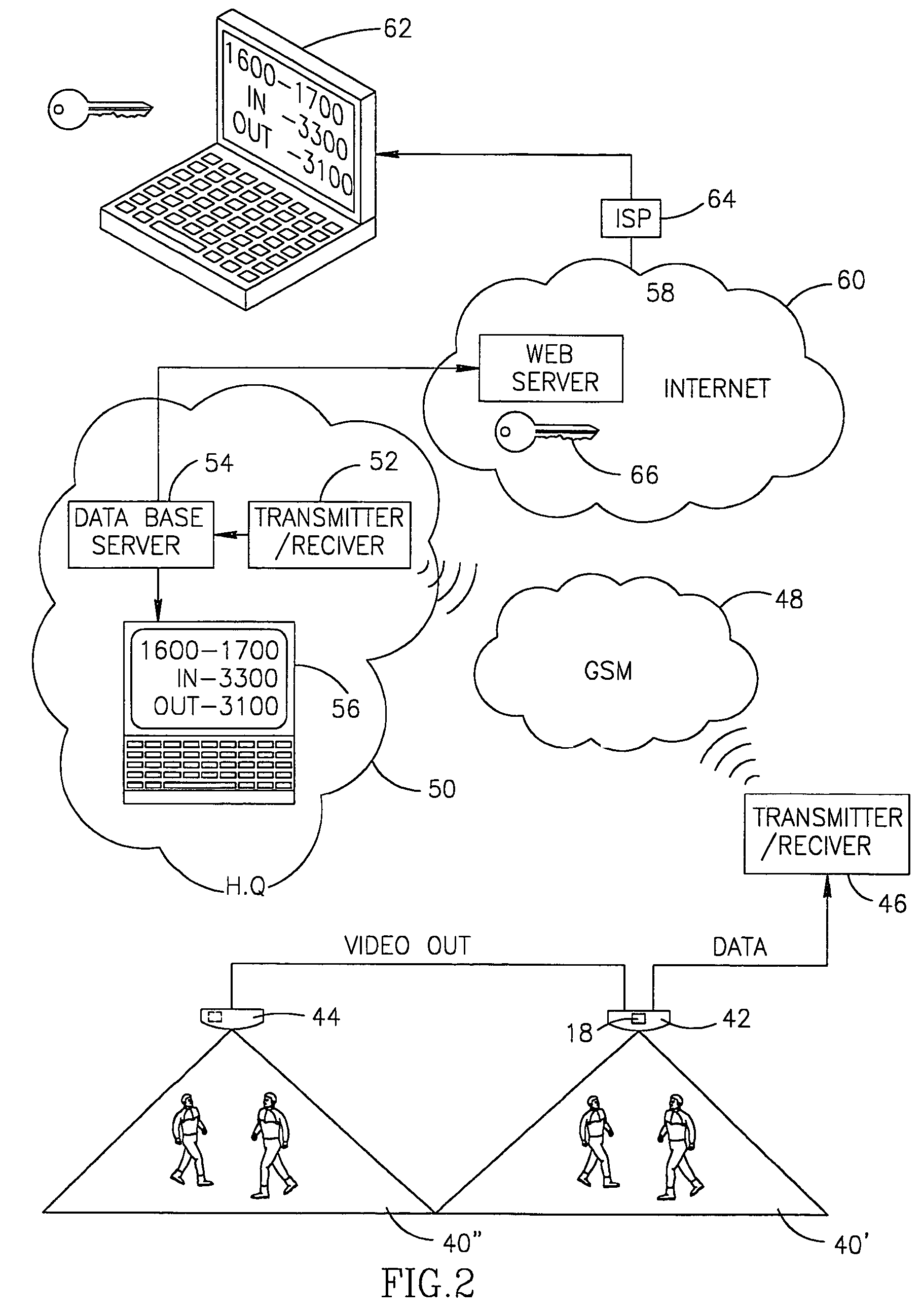
InactiveUS7612796B2Easy transferEasy to installCharacter and pattern recognitionColor television detailsGraphicsWork memory
A video based system and method for detecting and counting persons traversing at least two areas being monitored. The method includes the steps of initialization of at least one end unit, having at least a camera, the camera producing images of at least a first area being monitored and a second area being monitored, digitizing the images and storing the digitized images in a non-volatile memory unit and a working memory unit; detecting potential persons in the images; comparing the digitized images of objects detected in the first area and second area being monitored with digitized images stored in the working memory unit to determine whether the detected object is a new figure in such area or whether the detected object is a known figure that has remained within such area and to determine that a figure which was not detected has left such area; incrementing a counter for such area with an indication of the number of persons that have passed through such area, and comparing the number of persons passing through a first area with the number of persons passing through a second area.
Owner:COUNTWISE
In-vehicle handsfree apparatus
InactiveUS20080085745A1Improve usabilitySubstation equipmentRadio transmission for post communicationTelecommunications linkIn vehicle
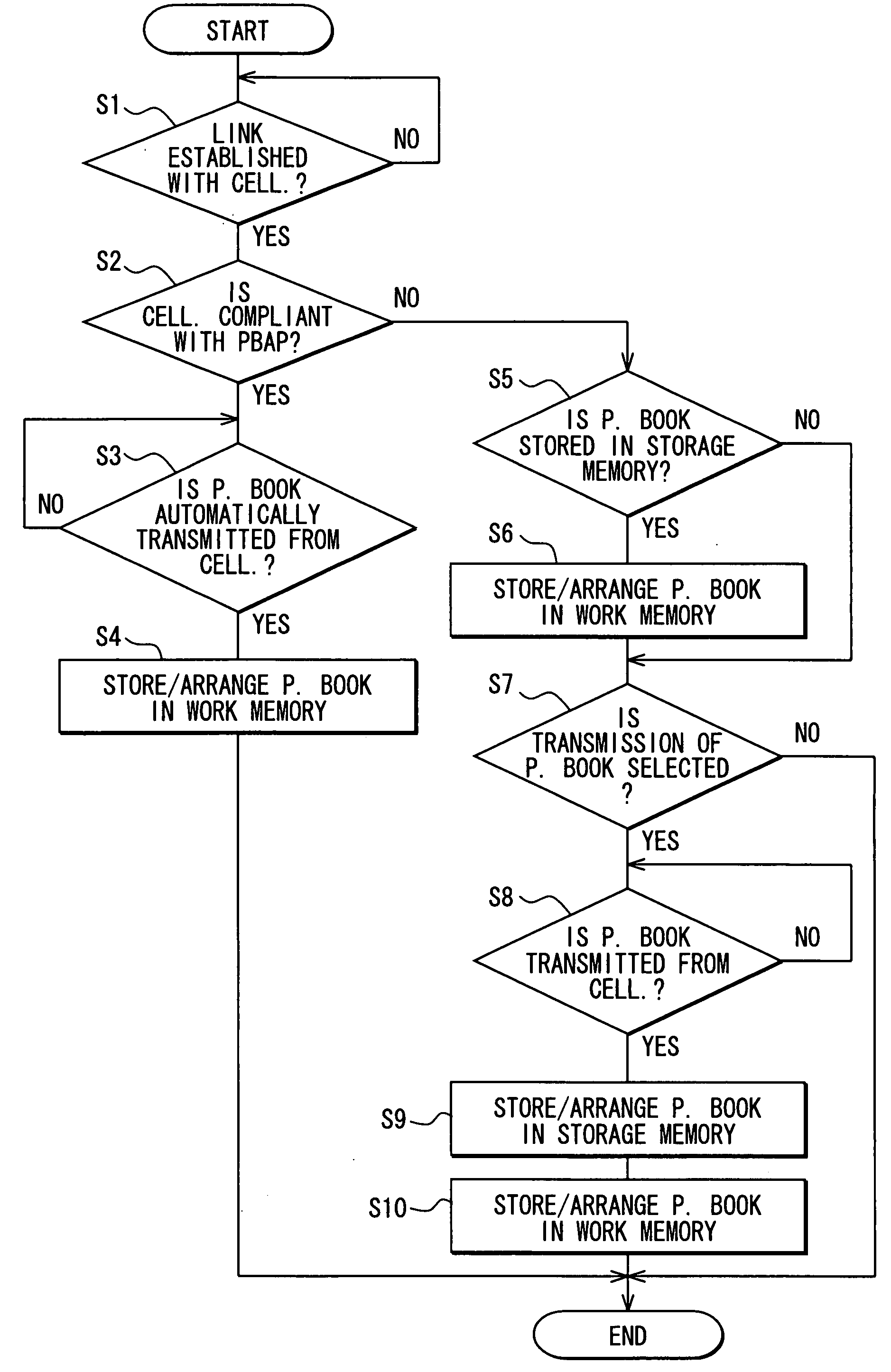
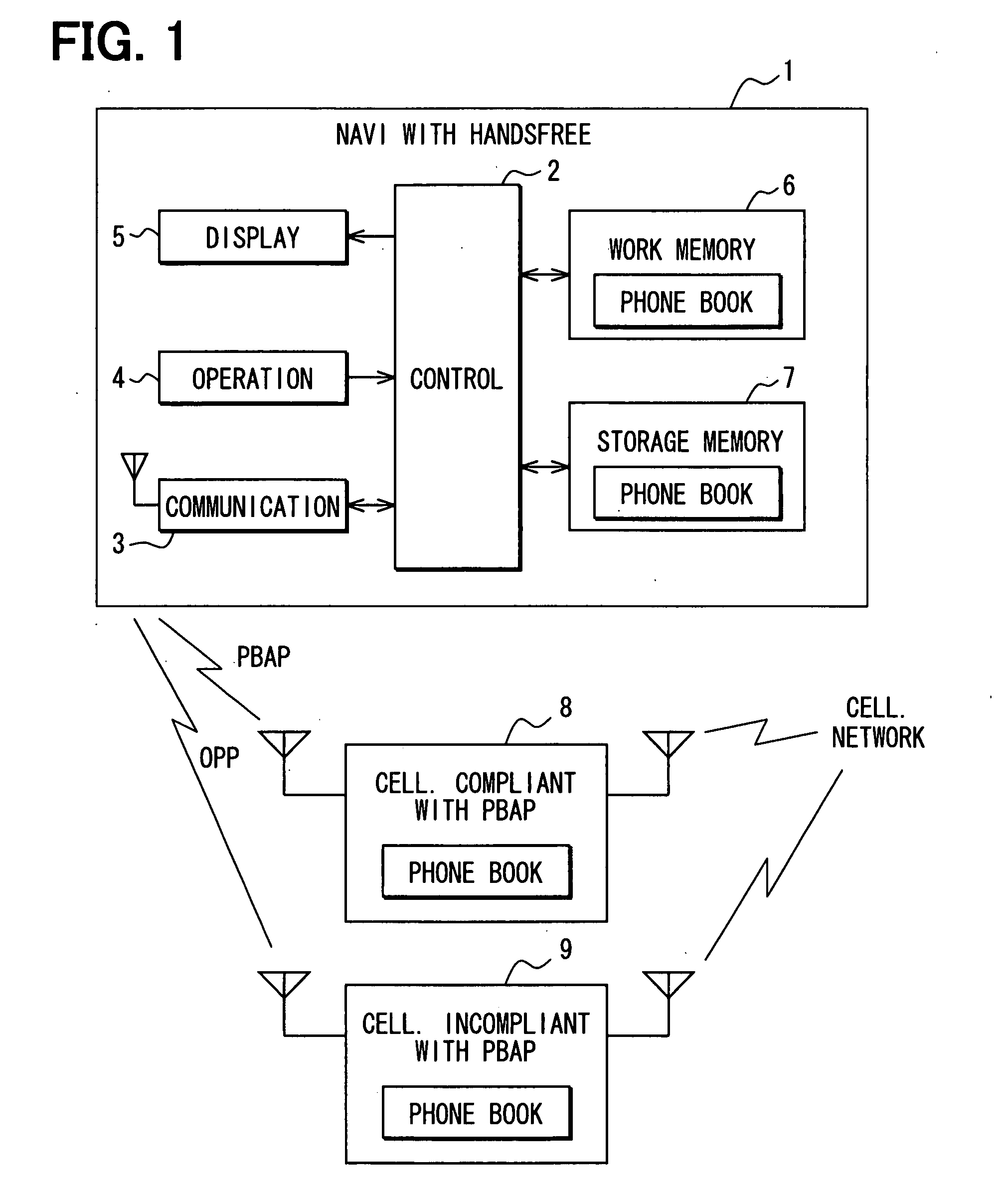
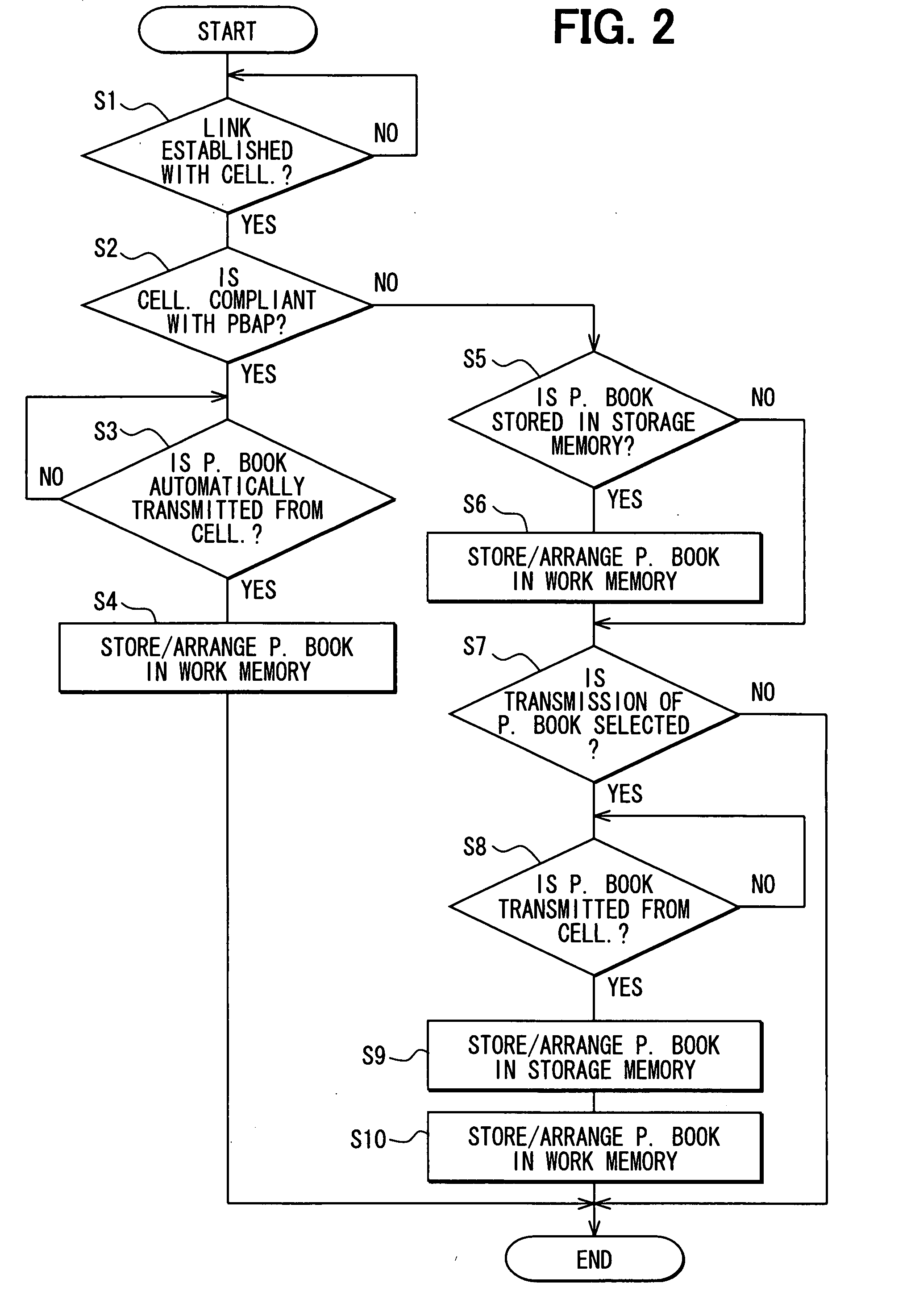
If a cellular phone with which a communication link is established is compliant with PBAP (Phone Book Access Profile), an in-vehicle navigation apparatus with a handsfree function stores and arranges, in a work memory device, phone book data transmitted automatically from the cellular phone. Thus, the newest phone book data can be made available. On the other hand, if the cellular phone is not compliant with PBAP, the in-vehicle navigation apparatus stores and arranges, in the work memory device, phone book data, which are presently stored in a storage memory device. Thus, if the presently stored phone book data, which are not newest, are desirable, they can be made available.
Owner:DENSO CORP
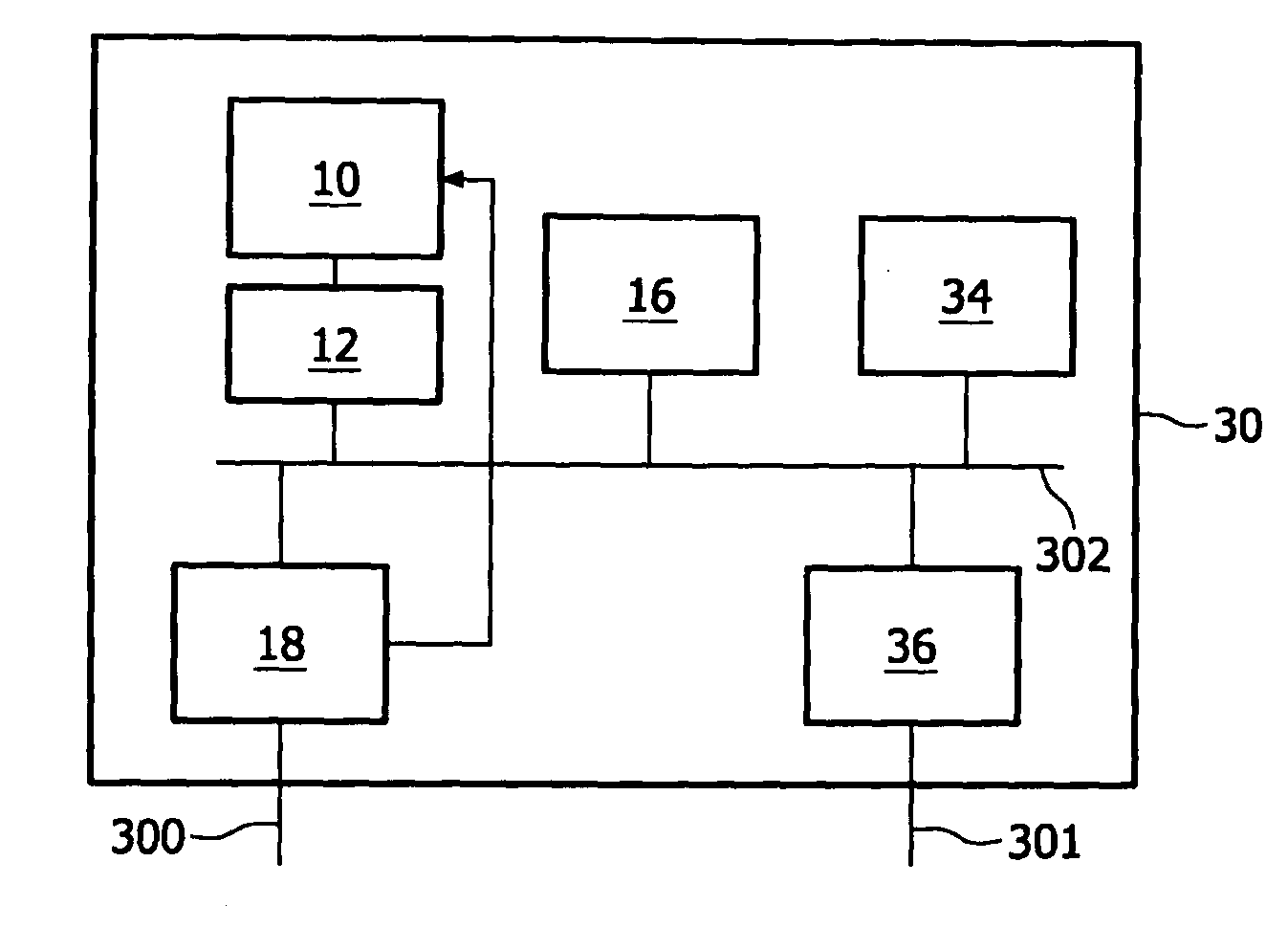
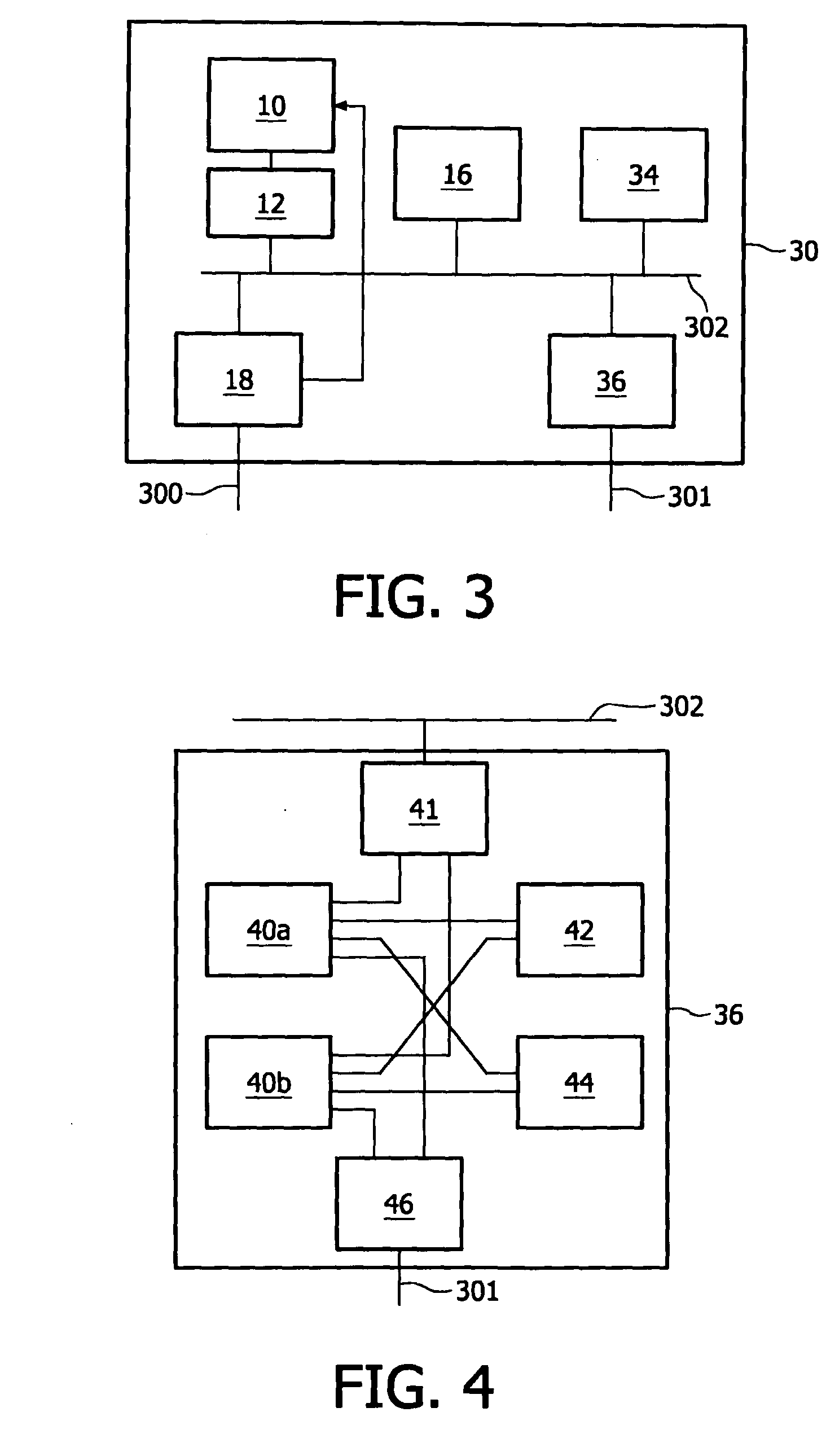
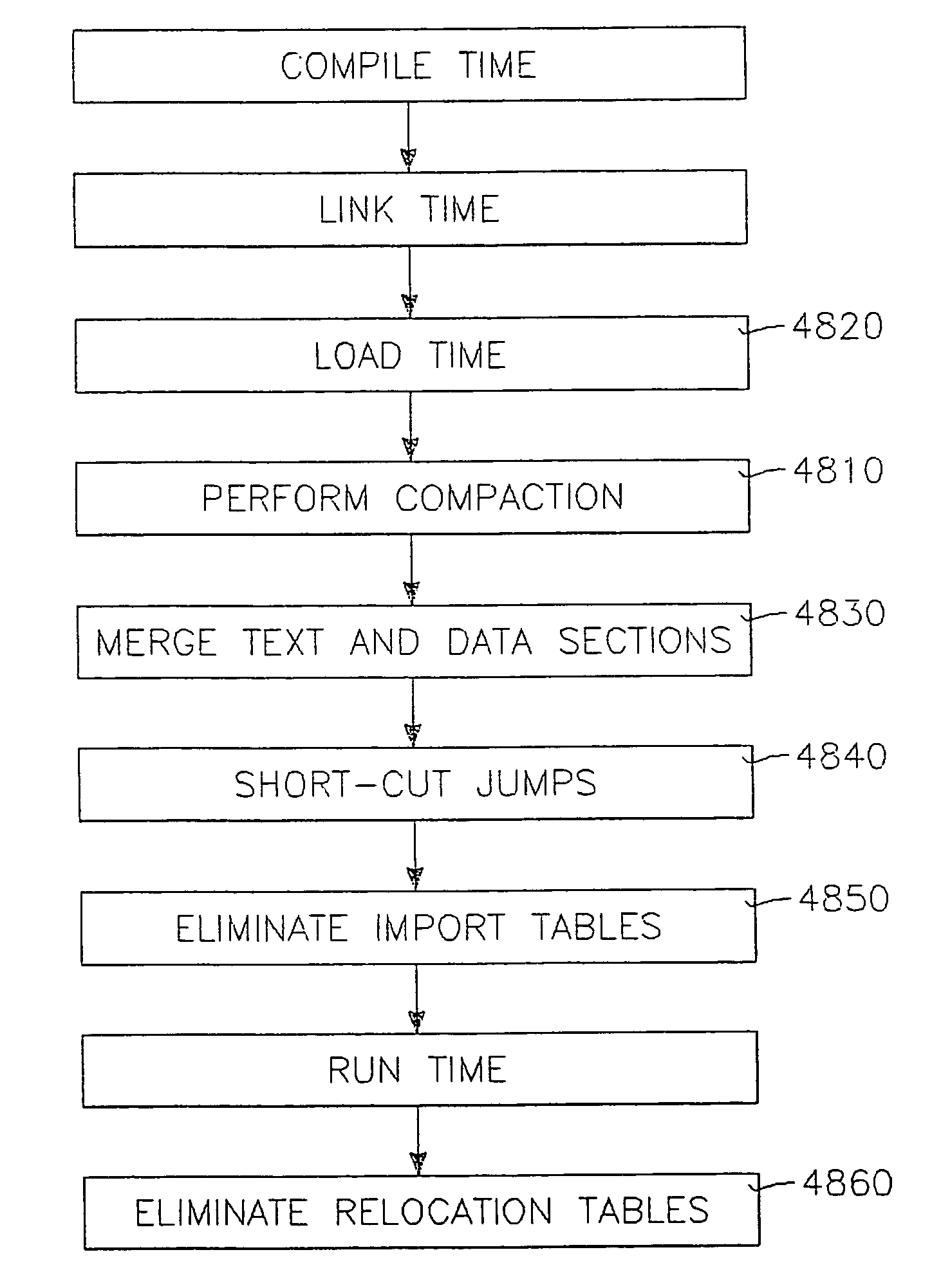
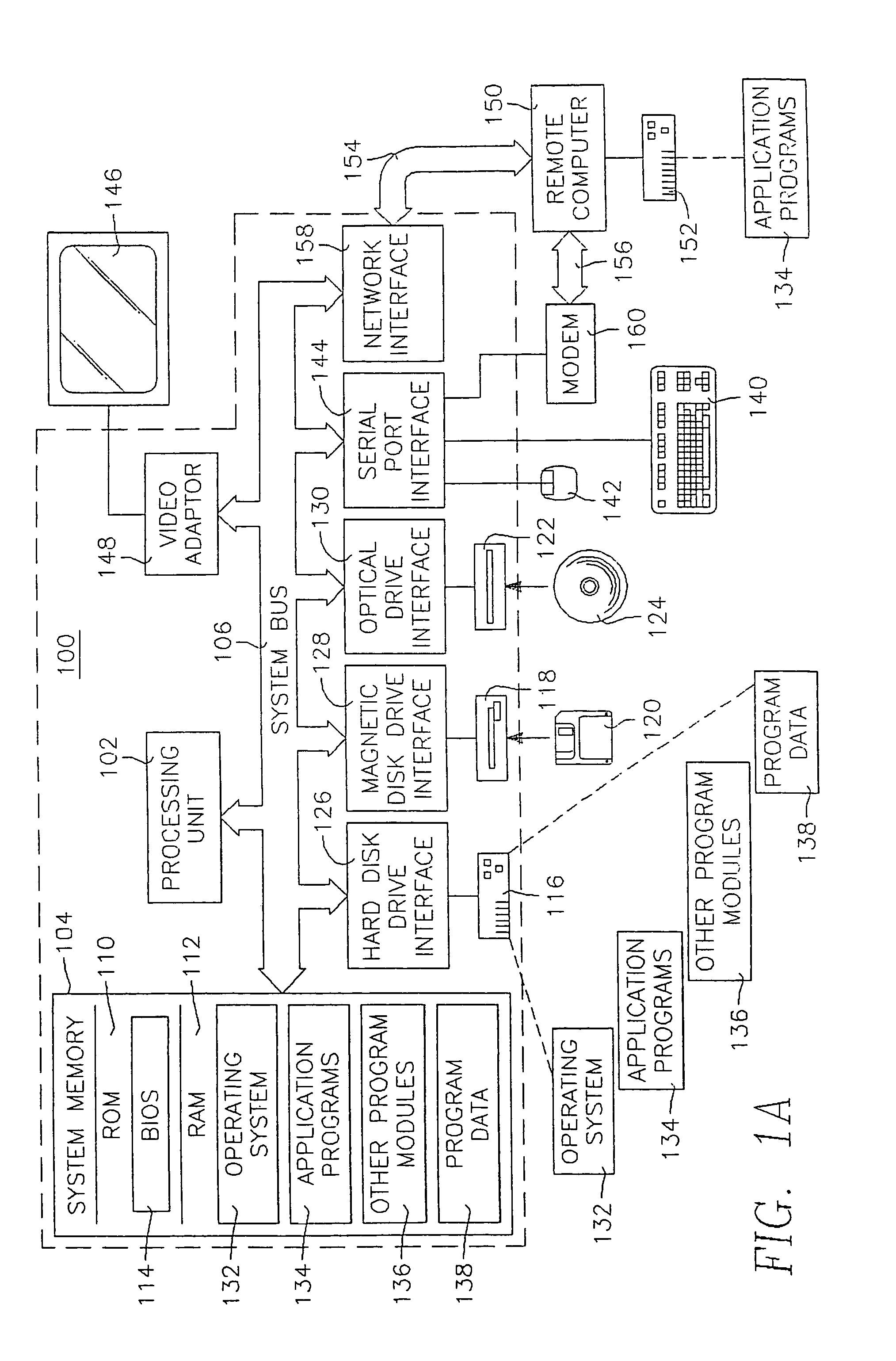
Efficient linking and loading for late binding and platform retargeting
InactiveUS20050223018A1Severely restrictedFacilitates version control of versionFinanceDigital data processing detailsWork memoryAddress space
A method of producing an executable image from an object file without shared library support from the operating system, wherein the executable image requires a shared library file in order to resolve at least one of the symbols called for in the object file. A method of optimizing the loading of a previously linked file into working memory in a computer for executing in a single address space of the working memory, the file containing an instruction to make an indirect jump to a location in a shared library through an import section of the file. A method for optimizing the loading of a previously linked file into working memory in a computer for executing in a single address space of the working memory, the file containing plural sections with number-filled padding between the end of each section and a succeeding page boundary. A method of optimizing the loading of a previously linked file into working memory in a computer for executing in a memory sharable with other executables. This method includes selecting a portion of code in the previously linked file, removing the portion of code from the previously linked file, and constructing a dynamically linked library file containing the portion of the code, the dynamically linked library file being available to plural files including the previously linked-file. A method of converting an image which has been previously linked for executing in an unshared memory into an image optimized for use with virtual memory.
Owner:MICROSOFT TECH LICENSING LLC
Hybrid memory module structure and method of driving the same
InactiveUS20160110102A1Faster access timeInput/output to record carriersDigital storageWork memoryMemory module
A hybrid memory module structure includes a channel for receiving data from and transmitting data to a device external to the hybrid memory module structure, a first memory module connected to the channel, and a second memory module connected to the channel. The first memory module includes at least a first memory and a second memory, the first memory being a working memory and the second memory being a storage memory. The second memory module includes at least a third memory and a fourth memory, the third memory being a working memory and the fourth memory being a storage memory. The channel includes a first data line commonly connected to the first memory and the second memory, and a second data line commonly connected to the third memory and the fourth memory.
Owner:SAMSUNG ELECTRONICS CO LTD
Apparatus and Method for Content Handling
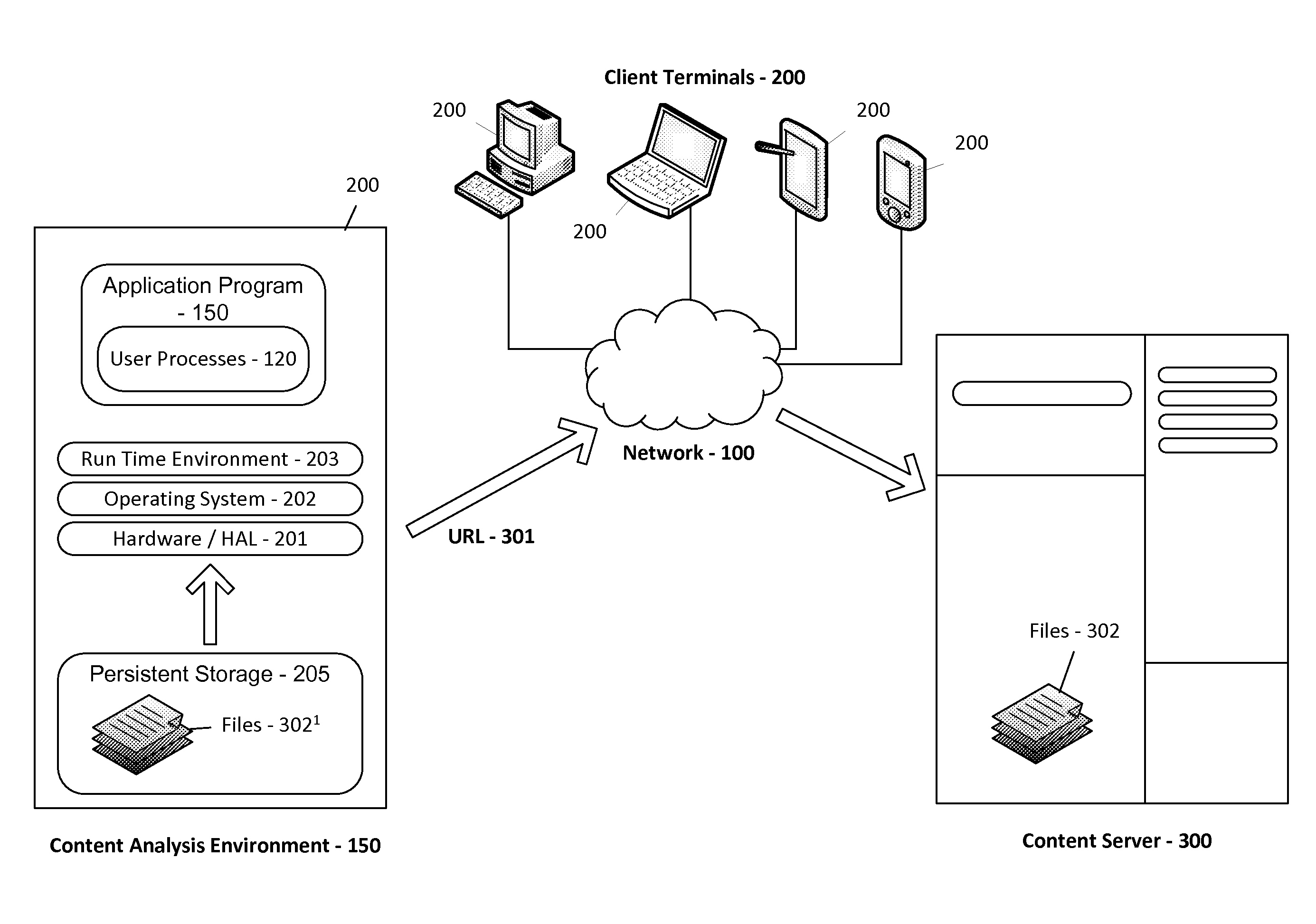
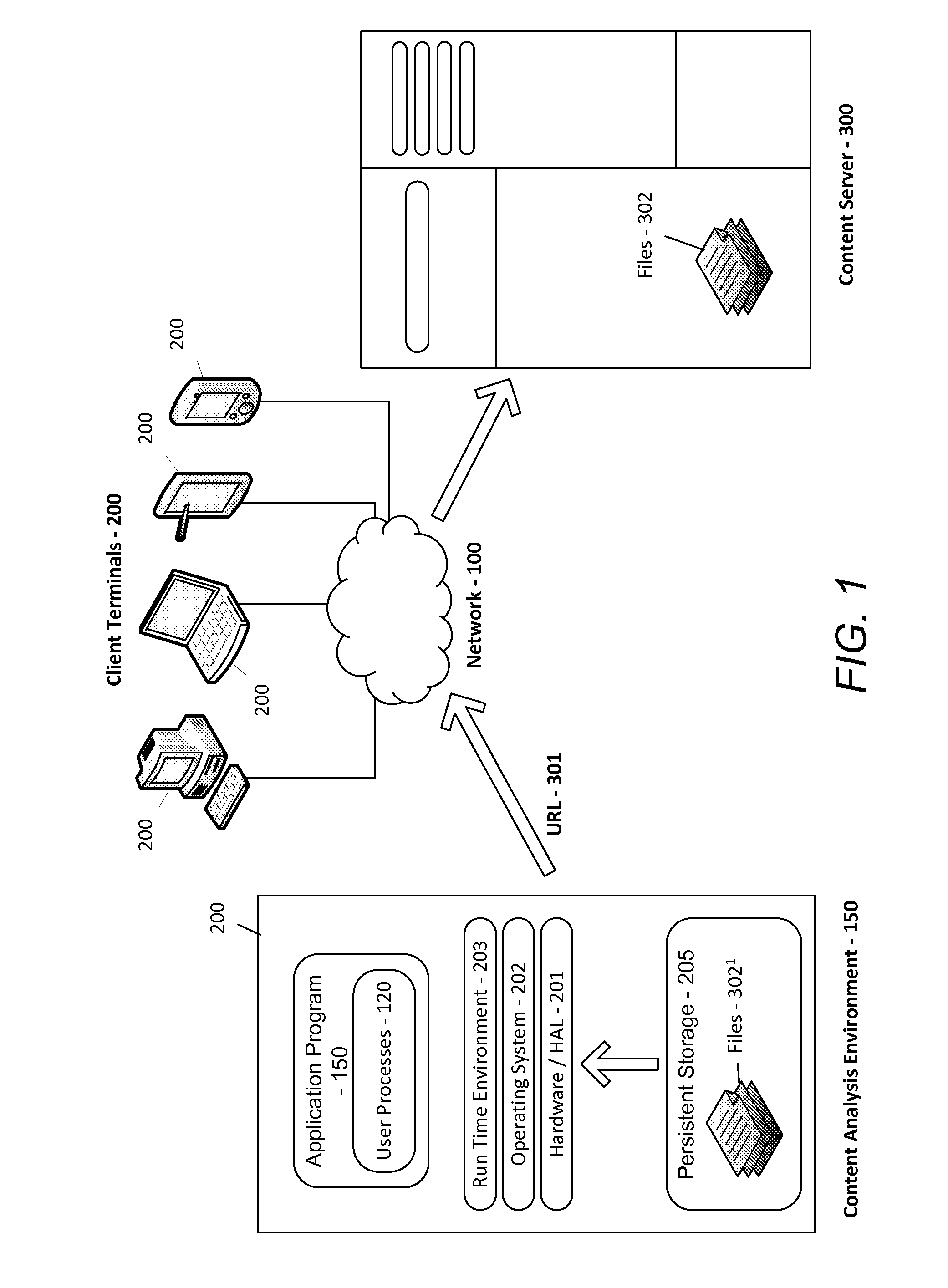
ActiveUS20150269358A1Increase contentFacilitates the secure uploading of related contentKey distribution for secure communicationWeb data indexingWork memoryContent analytics
An apparatus for content handling is provided. The apparatus comprises a content server arranged to provide a content analysis environment to a client terminal, and to provide content to the client terminal for analysis within the content analysis environment once the content analysis environment has been established at the client terminal, wherein the client terminal is arranged: to download the content from the content server into the content analysis environment; to encrypt the downloaded content and store the encrypted content therein in a persistent form; to decrypt the encrypted content into working memory therein for analysis within content analysis environment; to encrypt analysed content and store the encrypted analysed content therein in a persistent form; and to decrypt the encrypted analysed content and to upload this decrypted content to the content server.
Owner:GOULD TECH SOLUTIONS
Optimization of queries using retrieval status of resources used thereby
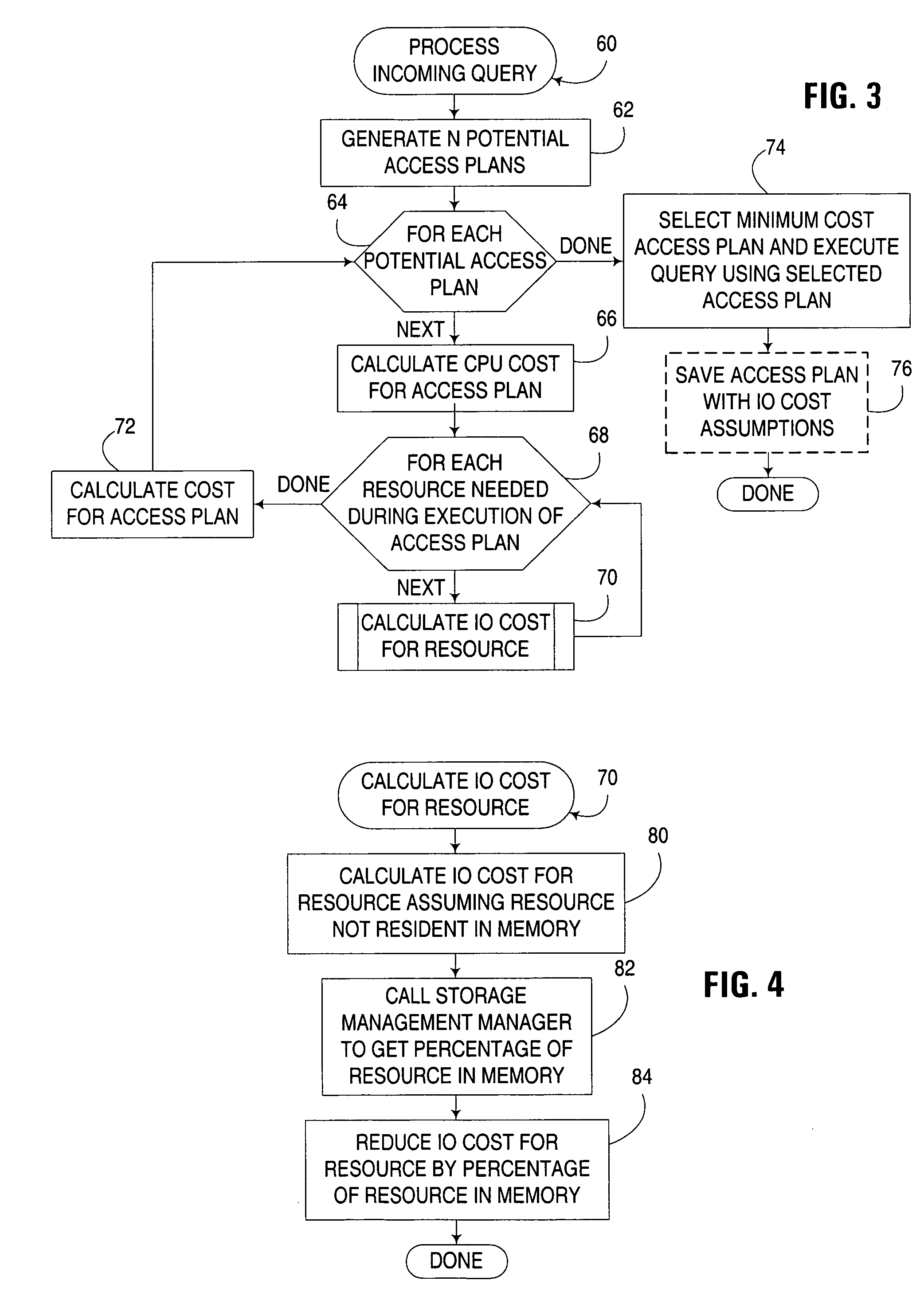
ActiveUS20050091196A1Accurate input/output cost estimateGood choiceData processing applicationsDigital data information retrievalQuery optimizationWork memory
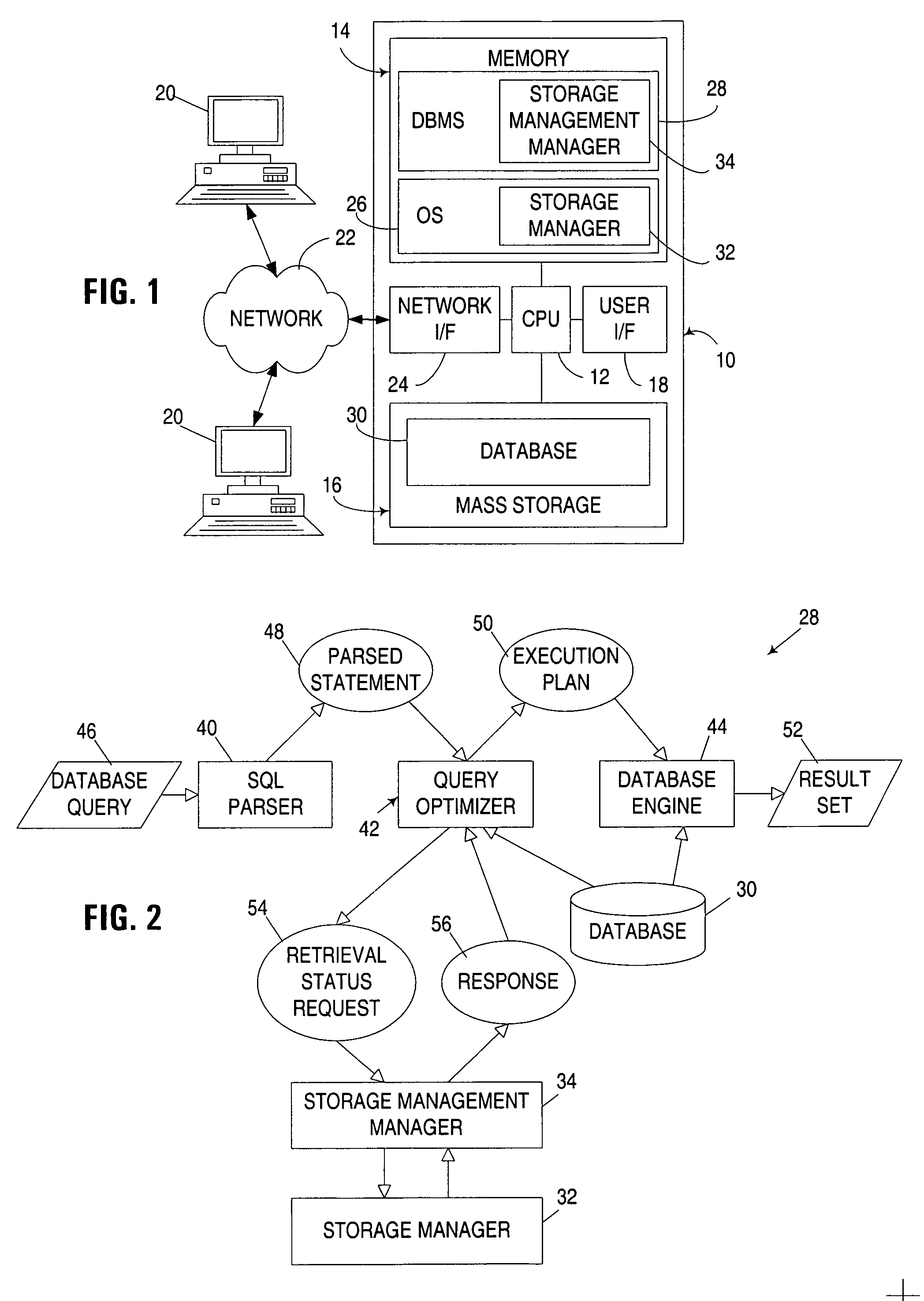
An apparatus, program product and method utilize the retrieval status of a resource to generate an access plan for a database query that uses the resource. The retrieval status, which indicates, for example, what percentage of a given resource is already stored in working memory, and thus need not be separately retrieved during query execution, may be used to generate more accurate input / output cost estimates for access plans, and thus enable a query optimizer to better select an access plan that is optimal under given runtime conditions.
Owner:GOOGLE LLC
Display enhanced testing for concussions and mild traumatic brain injury
ActiveUS8568311B2Data processing applicationsSensorsInformation processingPhysical medicine and rehabilitation
Cognitive assessment systems and methods that provide an integrated solution for evaluating the presence or absence of cognitive impairment. The present invention is used to test cognitive functions of an individual including information processing speed, working memory, work list learning and recall, along with variations of these tasks. Immersive and non-immersive systems and methods are disclosed. Testing and results feedback using the present invention may be completed in real time, typically in less than 15 minutes.
Owner:EMORY UNIVERSITY +1
Flash memory access circuit
InactiveUS20100169546A1Maximum speed for handlingWithout overheadMemory adressing/allocation/relocationProgram controlLoad instructionWork memory
A system comprises an instruction processor (10), a flash memory device (14a), a flash control circuit (14) and a working memory (16). Instructions of an interrupt program are kept stored in the flash memory device (14a). When the instruction processor (10) receives an interrupt signal, the instruction processor (10) executes loading instructions, to cause the flash control circuit (14) to load said instructions of the interrupt program from the flash memory device (14a) into the working memory (16). The instructions of the interrupt program are subsequently executed with the instruction processor (10) from the working memory (16). Preferably it is tested whether a copy of said instructions of the interrupt program is stored in the working memory (16) at the time of the interrupt. If the copy is found stored, execution of said instructions from the copy is started before completing execution of of access instructions that were in progress at the time of the interrupt. If the copy is not found stored, execution of the access instructions is first completed and subsequently the instruction processor (10) executes the loading instructions, followed by execution of the instructions of the copy of interrupt program from the working memory (16).
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Efficient linking and loading for late binding and platform retargeting
InactiveUS7565665B2Severely restrictedFacilitates version control of versionFinanceDigital data processing detailsVirtual memoryOperational system
A method of producing an executable image from an object file without shared library support from the operating system, wherein the executable image requires a shared library file in order to resolve at least one of the symbols called for in the object file. A method of optimizing the loading of a previously linked file into working memory in a computer for executing in a single address space of the working memory, the file containing an instruction to make an indirect jump to a location in a shared library through an import section of the file. A method for optimizing the loading of a previously linked file into working memory in a computer for executing in a single address space of the working memory, the file containing plural sections with number-filled padding between the end of each section and a succeeding page boundary. A method of optimizing the loading of a previously linked file into working memory in a computer for executing in a memory sharable with other executables. This method includes selecting a portion of code in the previously linked file, removing the portion of code from the previously linked file, and constructing a dynamically linked library file containing the portion of the code, the dynamically linked library file being available to plural files including the previously linked file. A method of converting an image which has been previously linked for executing in an unshared memory into an image optimized for use with virtual memory.
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com