Software behavior monitor and verification system
A technology for verifying systems and behaviors, applied in transmission systems, payment systems, electrical components, etc., can solve problems such as the inability to guarantee the security of electronic network transactions and the difficulty of preventing diversity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
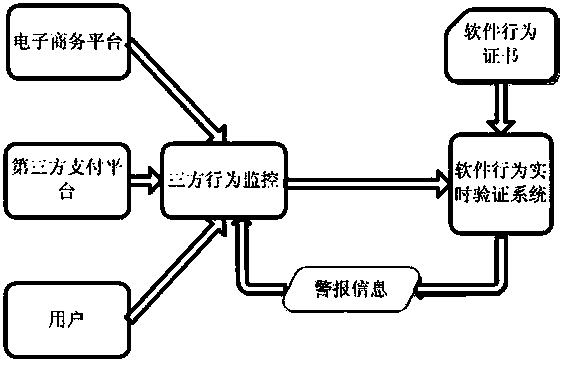
[0021] The architecture of the entire software behavior monitoring and verification system is as follows: figure 1 shown.
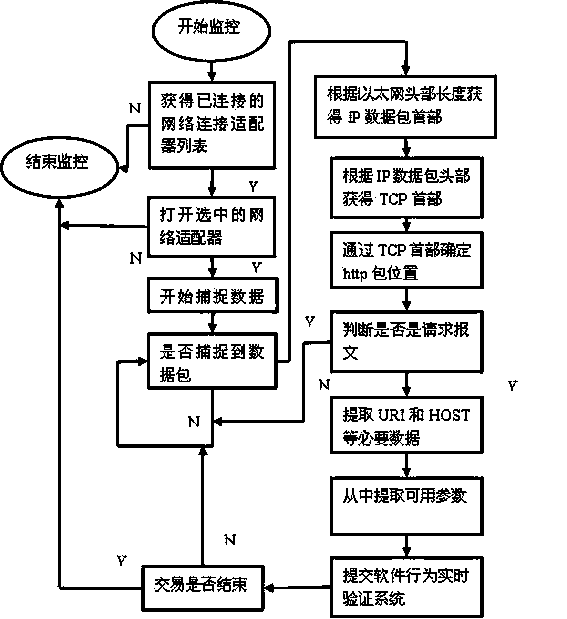
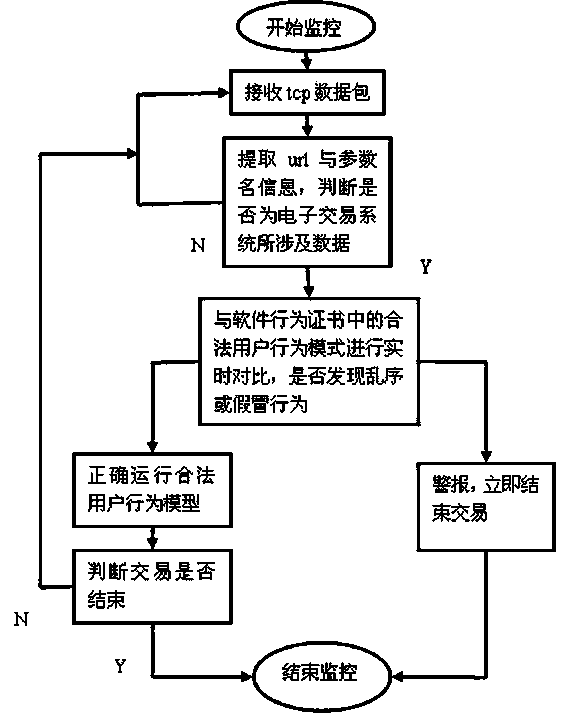
[0022] The entire software behavior monitoring and verification system solidifies the behavior of real legitimate users to form a software behavior certificate. Then, mainly based on the unique order number in the world, the three-party interactive behavior sequence in the transaction process is compared with the software behavior certificate in real time, and one-step verification is performed. Once any party has illegal behaviors such as message disorder or fake identity, it will alarm or take certain measures. .
[0023] Three-party software behavior monitor: Install data packet monitors on e-commerce websites, third-party payment platforms, and user clients to monitor in real time the data packets transmitted between the three parties involved in a complete transaction, and perform data packet monitoring. The extraction and integration of the neces...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com