Invading detection method and system based on procedure action
A technology of intrusion detection and behavior, applied in transmission systems, digital transmission systems, electrical components, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0095] The technical solution of the present invention will be further described below in conjunction with the accompanying drawings.
[0096] For the convenience of explaining the content of the invention, some necessary definitions and explanations are first made:
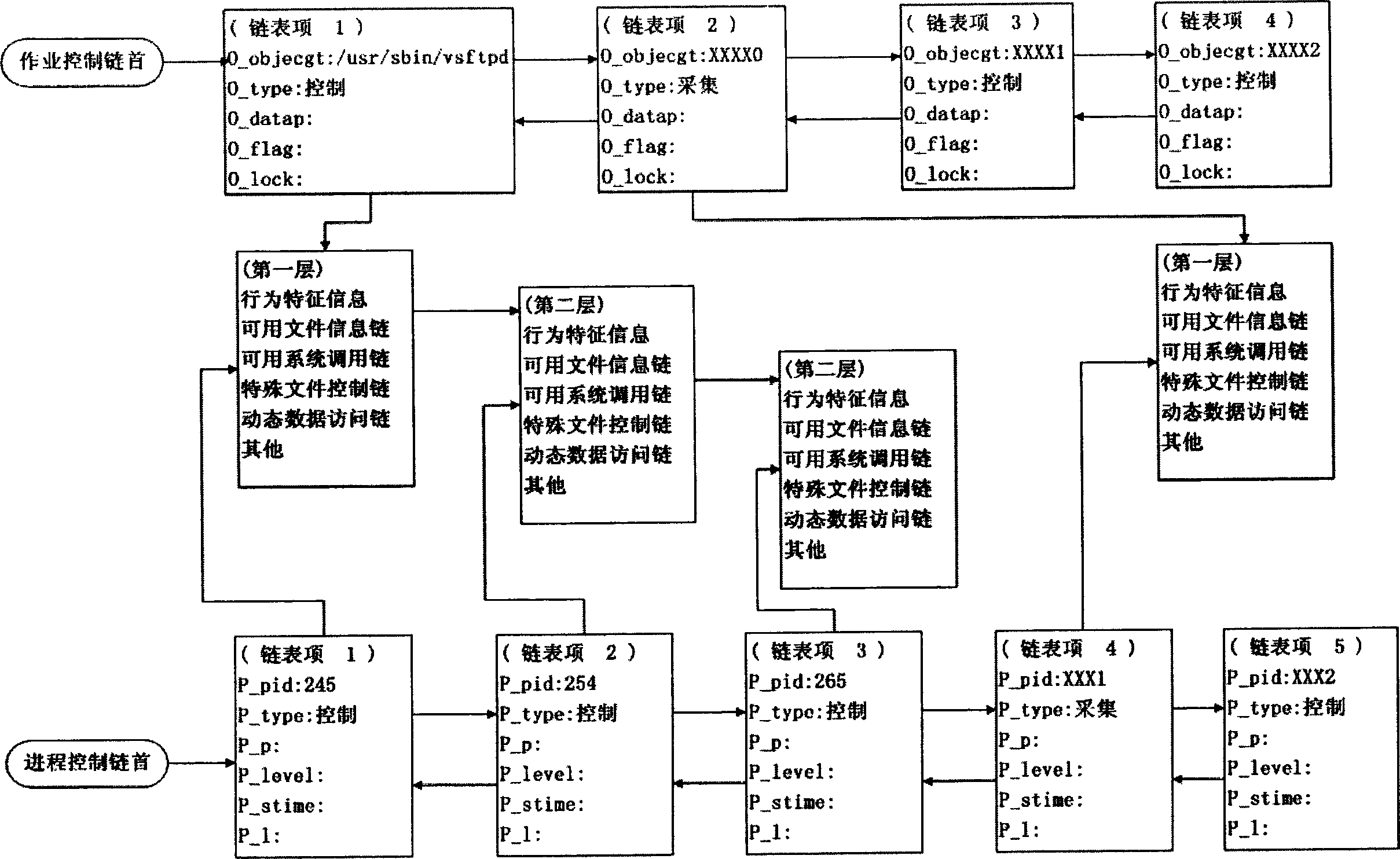
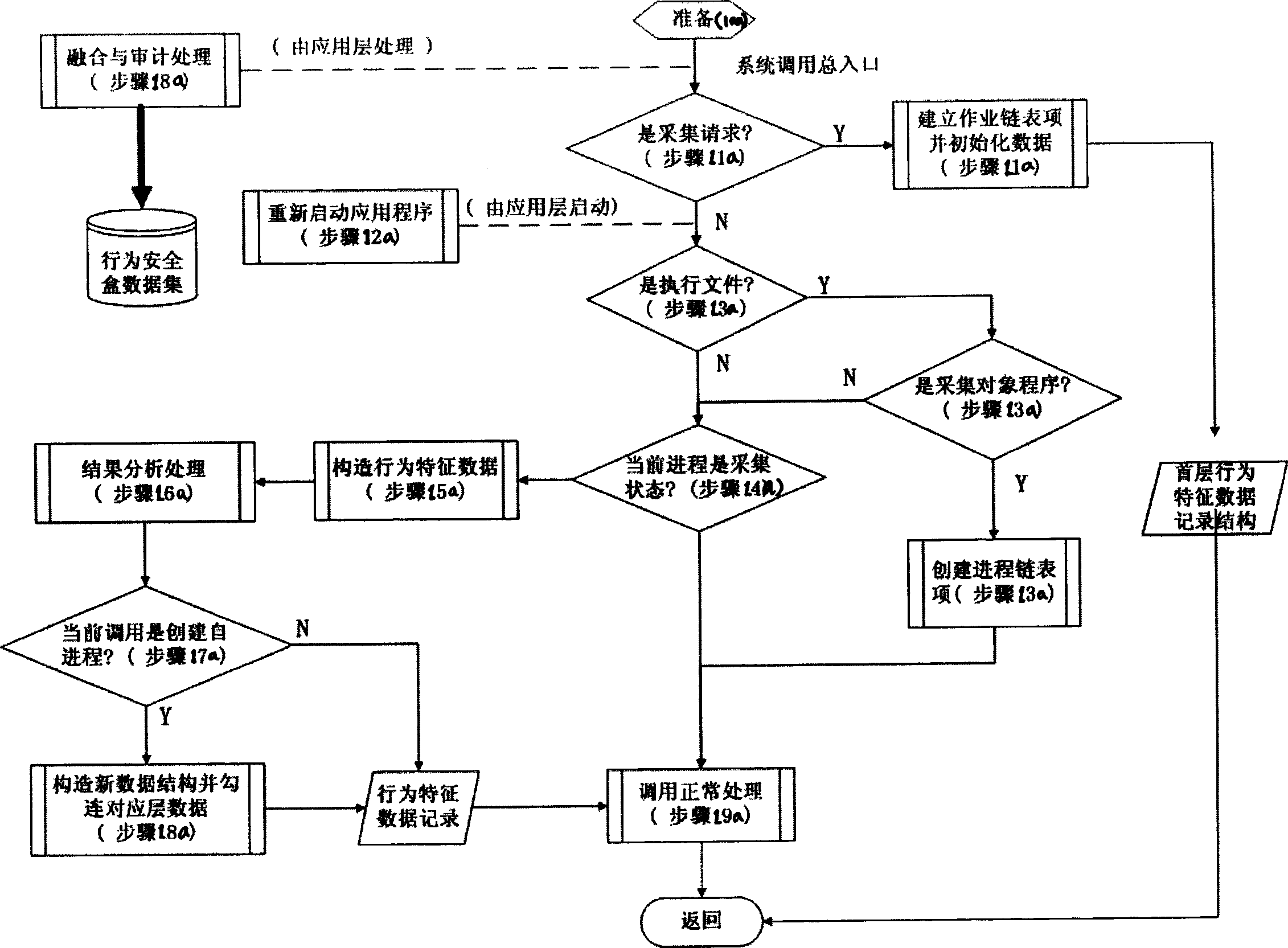
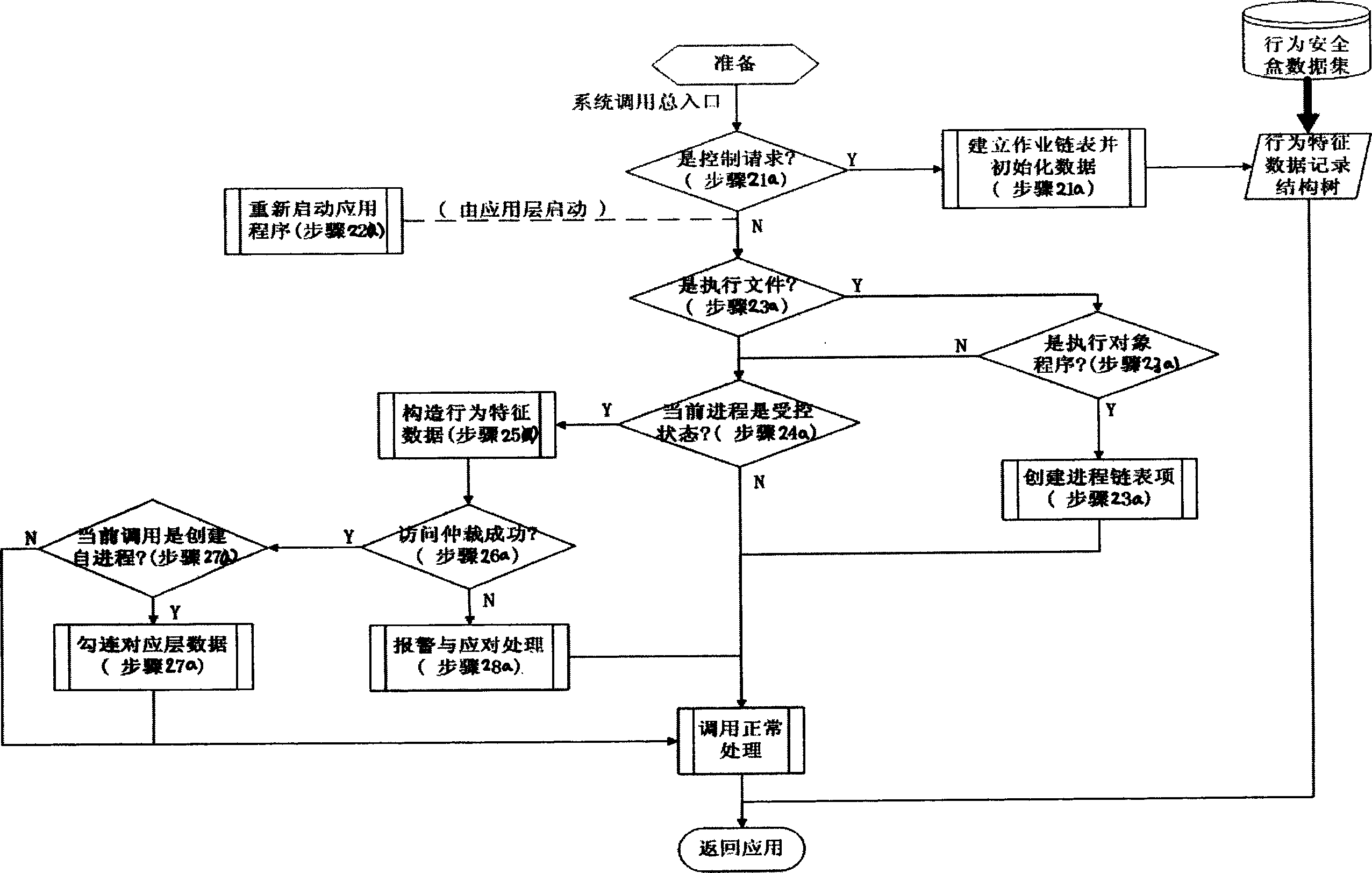
[0097] Behavior characteristics of a certain software: the service and resource requests made to the system software operating platform (OS) in order to achieve all or part of the functions designed by the software, and the information collection composed of various characteristics of these requests. The so-called service refers to various facilities provided by the system, such as creating processes, network connections, etc. The so-called resources refer to files (including data files, configuration files, and execution files of shared libraries), devices, etc. that need to be accessed in order to complete predetermined functions. Characteristics refer to its order, associativity, and (virtual) address space c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com