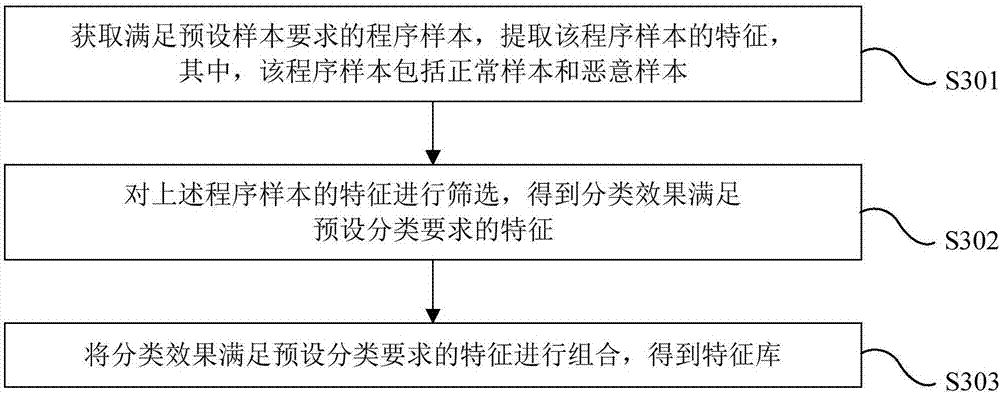
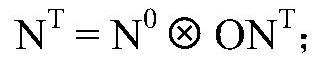Patents
Literature
59results about How to "Improve security defense performance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
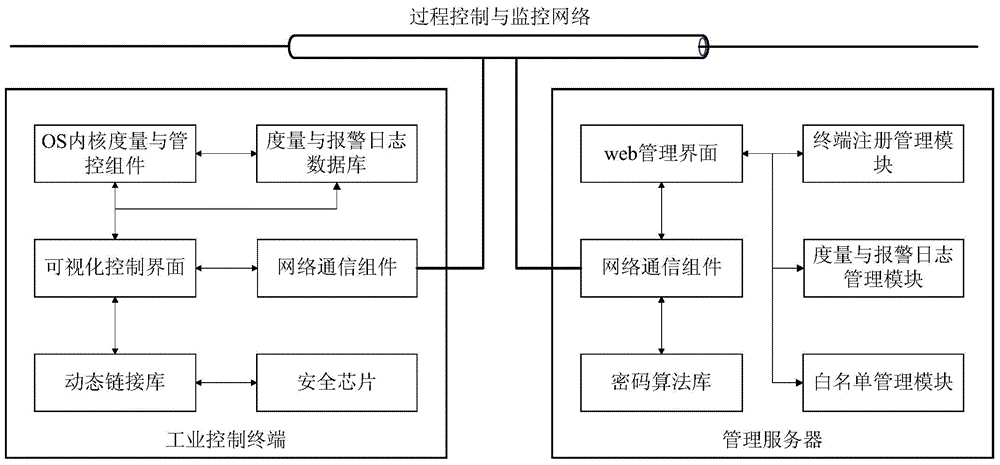
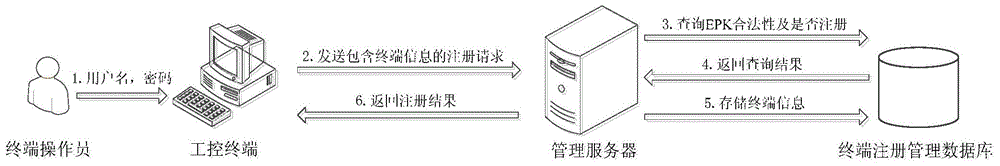
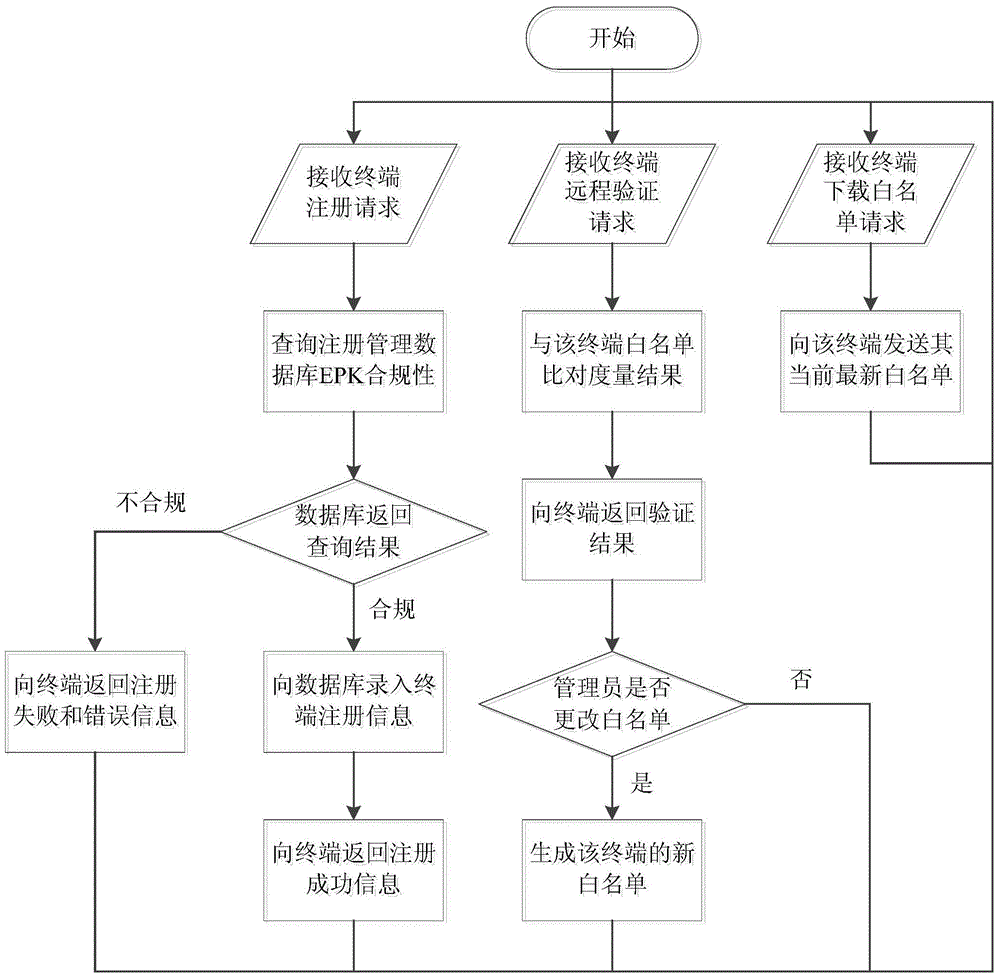
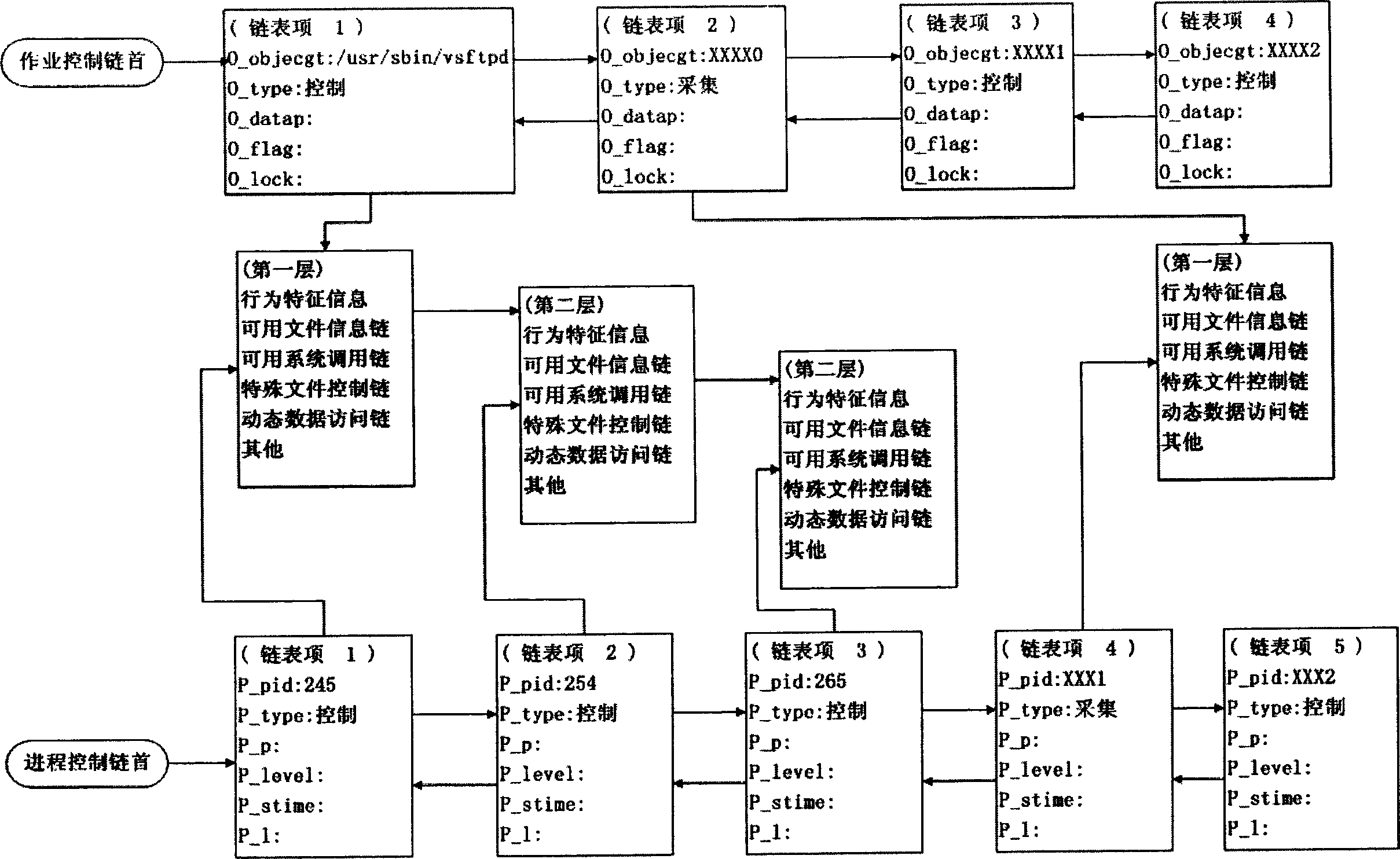
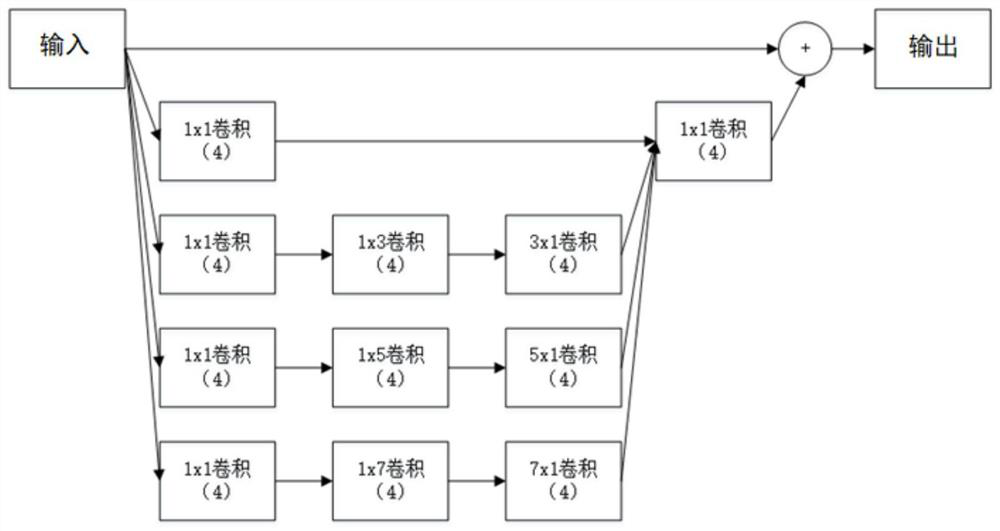
Industrial control system trusted environment control method and platform based on safety chip
ActiveCN104573516AGood cryptographic function serviceImprove security defense performanceDigital data protectionPlatform integrity maintainanceComputer terminalComputer science
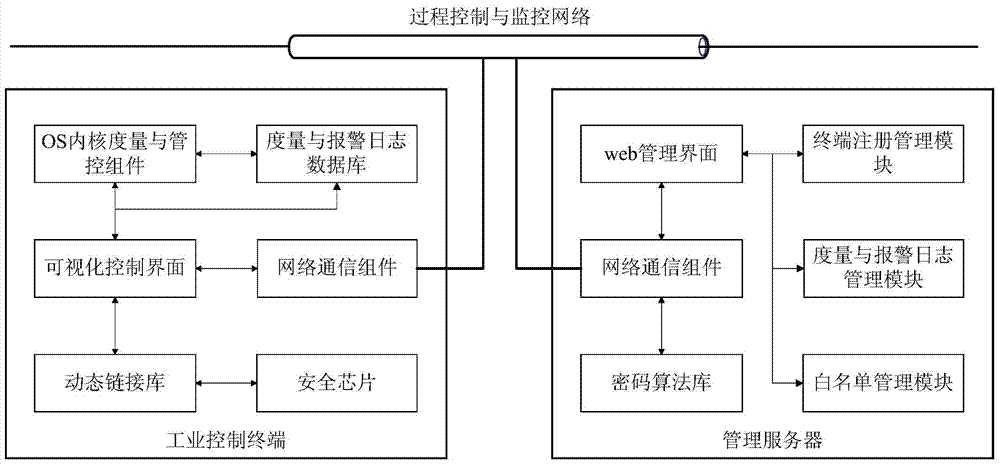
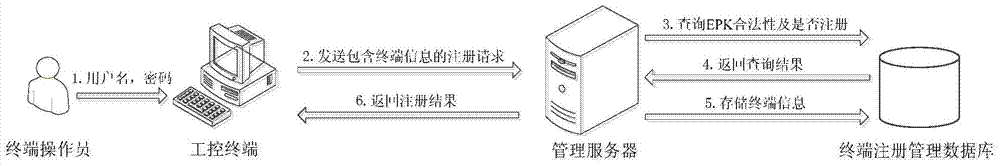
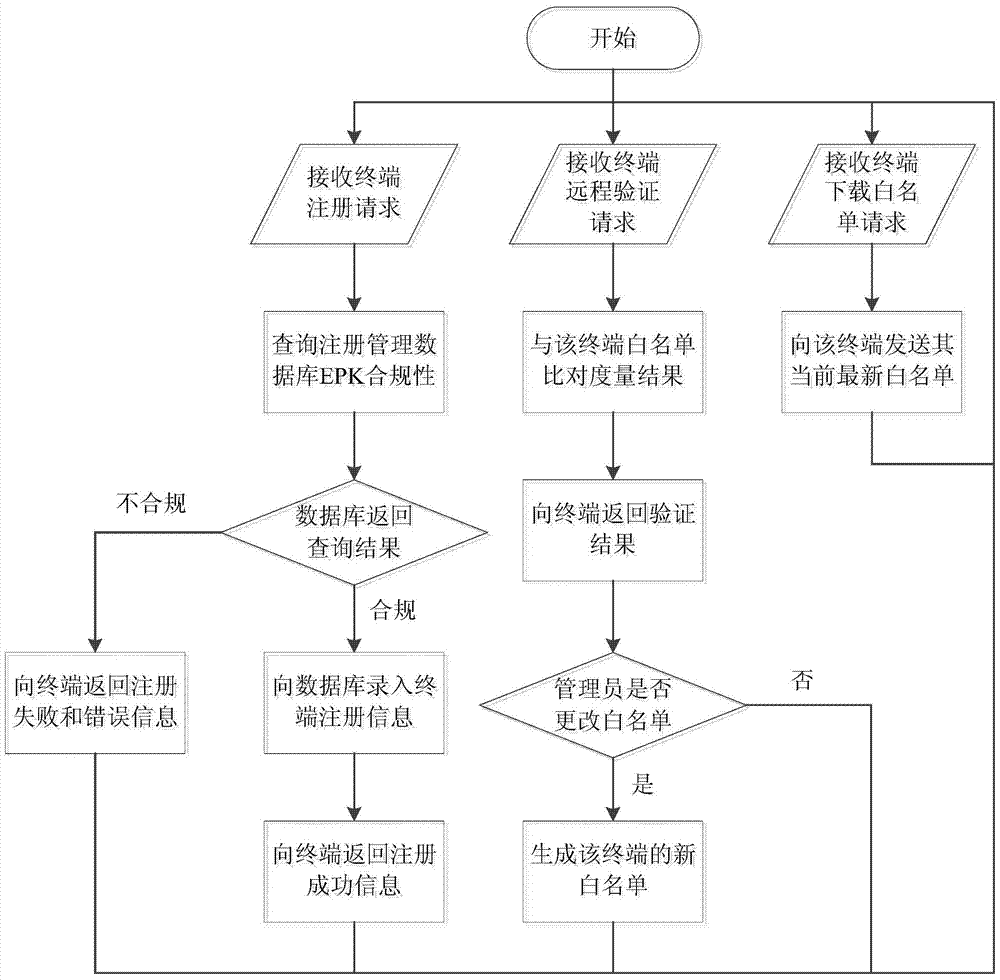
The invention provides an industrial control system trusted environment control method and platform based on a safety chip. The method comprises the steps: (1) registering an industrial control terminal to a management server on the basis of the safety chip; (2) carrying out complete measurement on each operating process by adopting the industrial control terminal; (3) checking the measurement information by the management party on the management server, and forming a white list; (4) downloading the white list formed by the management party from the management server by the industrial control terminal, leading the white list into an operating system core, and then carrying out the control on the process to be operated. By adopting the method and platform, malicious code of an untrusted, unknown and uncontrollable program process is prevented from damaging the system of the industrial control terminal, from stealing the confidential information and damaging the industrial production, so that the safety defense capacity of the industrial control system can be improved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Invading detection method and system based on procedure action
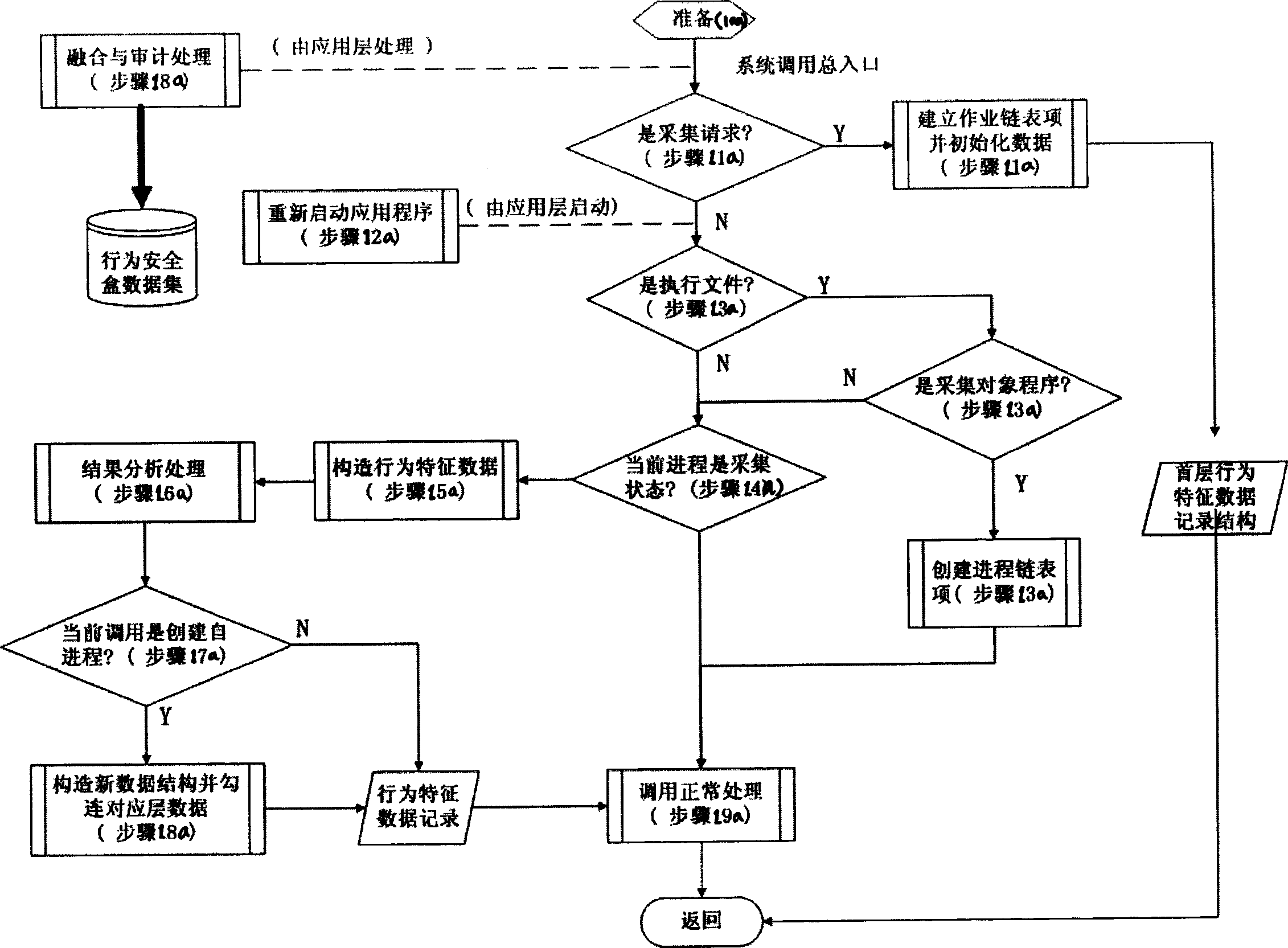
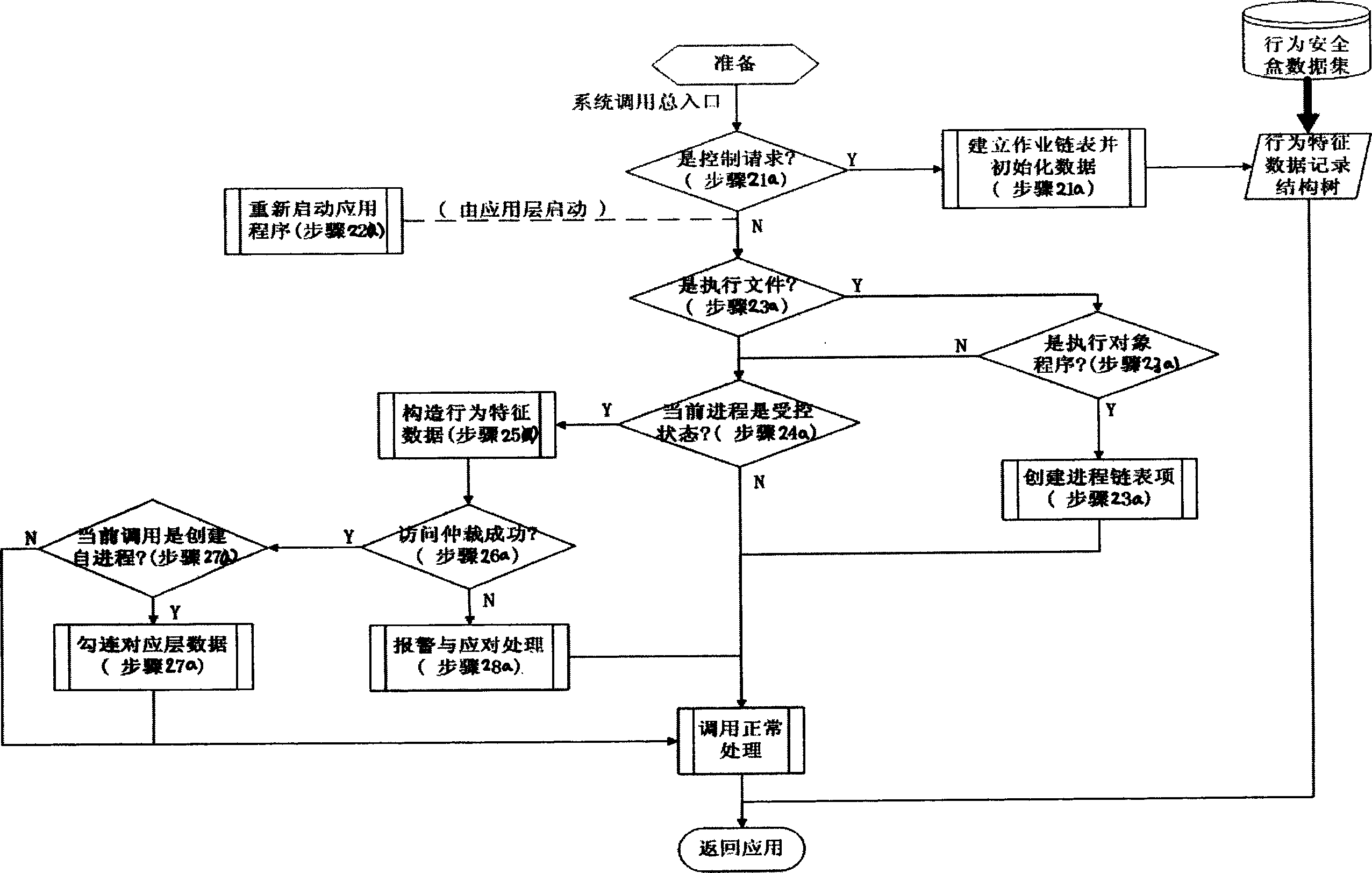
ActiveCN1794645AImprove security defense performanceClear processData switching networksClose couplingNetwork security policy
This invention discloses a method for testing inbreak, which obtains the information of software behavior characters of a program, a structure access model and acts it on the program to prevent abnormal behavior so as to protect the entire network server system to avoid network inbreak including the following basic processes: collecting and processing a behavior security box to monitor the software behavior timely and a protection system suitable for the above mentioned method is also disclosed to realize the close coupling control to the behavior of the applied program.
Owner:上海浦东软件园信息技术股份有限公司
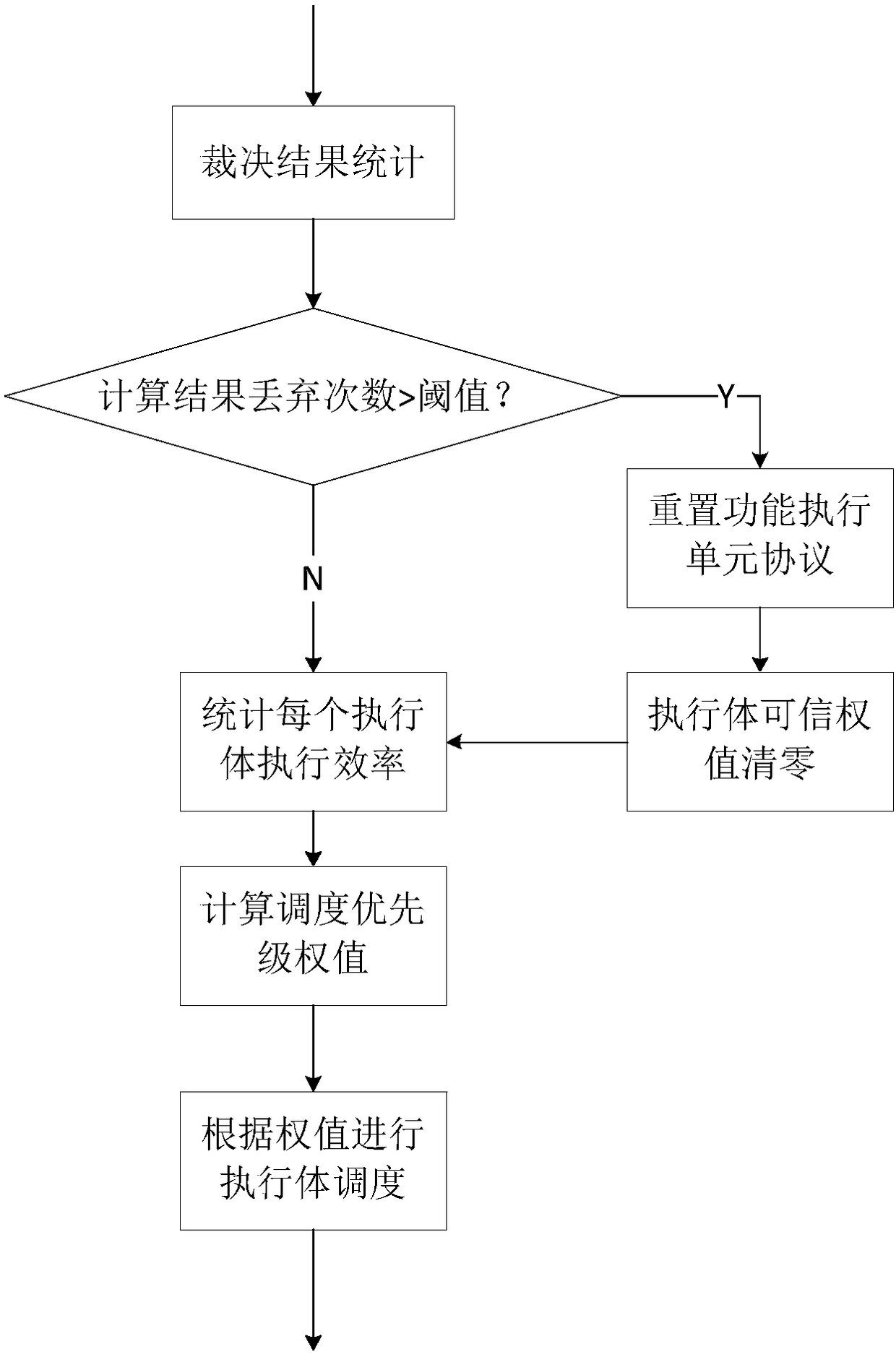
Weighted decision and random scheduling method based on physical heterogeneous redundancy
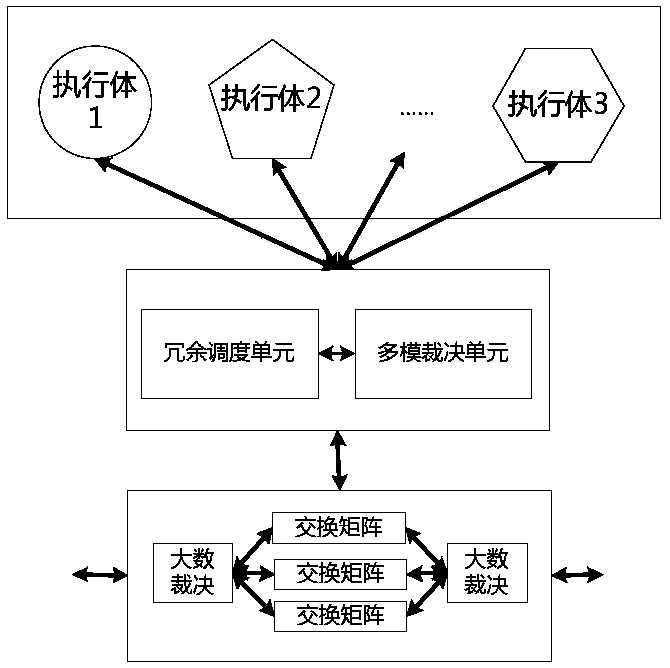
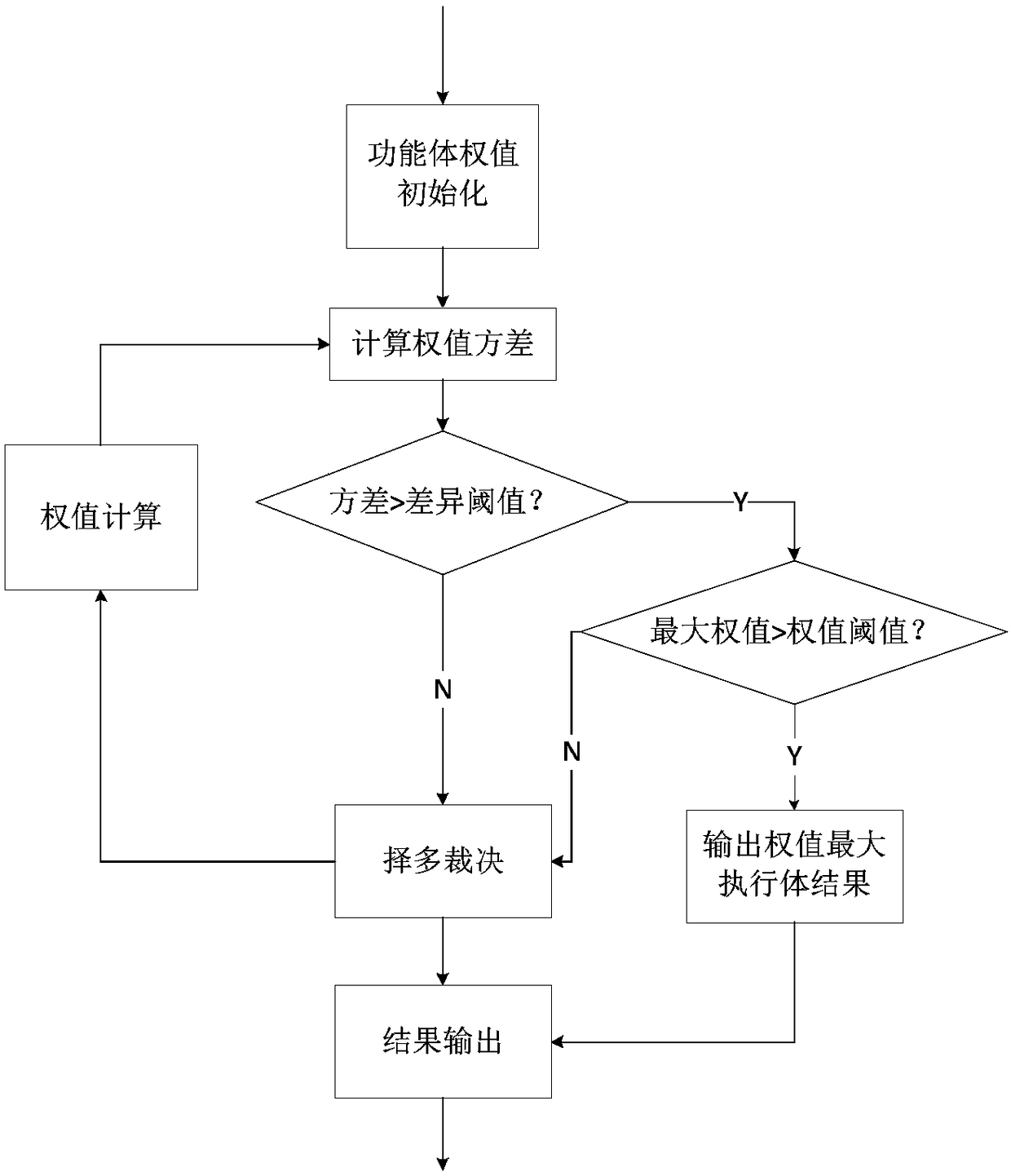
ActiveCN108134740AGuaranteed effective and credibleGuaranteed execution efficiencyData switching networksDecision methodsDecision unit
The invention discloses a weighted decision and random scheduling method based on physical heterogeneous redundancy. Different unicast, multicast routing protocols are executed in each routing protocol processing unit, and a calculation result is output to a multi-mode decision unit; the multi-mode decision unit decides the calculation result of each routing protocol processing unit, and deliversand outputs a final decision result to a data forwarding plane; a redundancy scheduling unit builds a routing protocol pool, performs protocol setting on each routing protocol processing unit, recordsand calculates each decision result, and then dynamically and randomly schedules the routing processing unit according to the calculation result. Due to design of the routing mechanism with the heterogeneous redundant decision function, the invention provides a weighted multi-mode decision method to compare output results of multiple heterogeneous routing function execution bodies, so as to perform multi-mode decision on final routing selection, dynamic random scheduling selection is performed on the execution bodies through a trust degree weight, then a simulation defense capability of a switch routing control plane is realized.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Low-altitude short-range cluster cooperative defense system and defense method
PendingCN106846922AImprove defenseRealize automatic scanning detectionDefence devicesAircraft traffic controlComputer scienceProcess information
The invention discloses a low-altitude short-range cluster cooperative defense system and defense method. The system comprises an early-warning monitoring module, an aerial counter-measure module, a ground counter-measure module and a control center. Data acquired by the early-warning monitoring module is transmitted to the control center to form visualization air situation, when an illegal low-slow small flyer invades, the early-warning monitoring module identifies, follows and monitors the illegal flyer and indicates an azimuth and height of the illegal flyer, and the control center drives the aerial counter-measure module or the ground counter-measure module to handle the illegal flyer. The control center transmits a control instruction to the aerial counter-measure module or the ground counter-measure module and can also process information returned by an aerial unmanned counter-measure module or a ground unmanned counter-measure module in real time. The aerial unmanned counter-measure module repels or hits a target by virtue of a carried task load. The ground unmanned counter-measure module repels and hits the target or effectively suppresses the low-altitude flyer by virtue of a carried task load.
Owner:武汉天宇智戎防务科技有限公司
Internet of Things safety monitoring method and system based on double engines
InactiveCN111163115ARealize centralized management and controlImprove security defense performanceTransmissionCollection analysisThe Internet
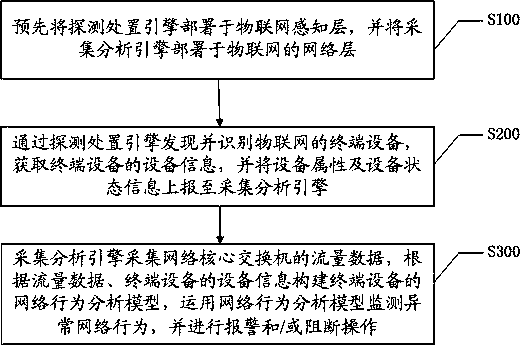
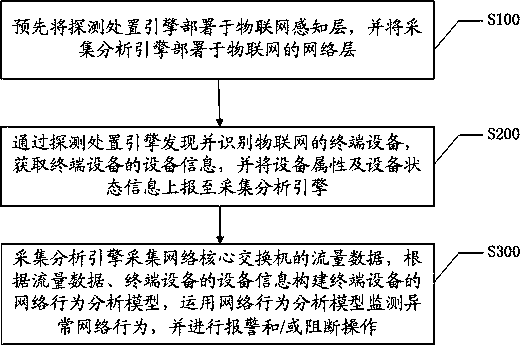
The invention discloses an Internet of Things safety monitoring method and system based on double engines, and the method comprises the steps: deploying a detection processing engine in an Internet ofThings sensing layer in advance, and deploying a collection analysis engine in a network layer of the Internet of Things; discovering and identifying terminal equipment of the Internet of Things through a detection processing engine, obtaining equipment information of the terminal equipment, and reporting equipment attributes and equipment state information to an acquisition analysis engine; andacquiring, by the acquisition and analysis engine, flow data of a network core switch, constructing a network behavior analysis model of the terminal equipment according to the flow data and equipmentinformation of the terminal equipment, monitoring abnormal network behaviors by using the network behavior analysis model, and performing alarm and / or blocking operation. Through linkage of the two types of engines, terminal equipment discovery and identification and risk disposal are realized, centralized management and control and behavior analysis are performed on the dispersedly isolated Internet of Things terminals, the comprehensiveness and accuracy of behavior analysis and monitoring are improved, and the disposal efficiency is ensured.
Owner:深圳市云盾科技有限公司
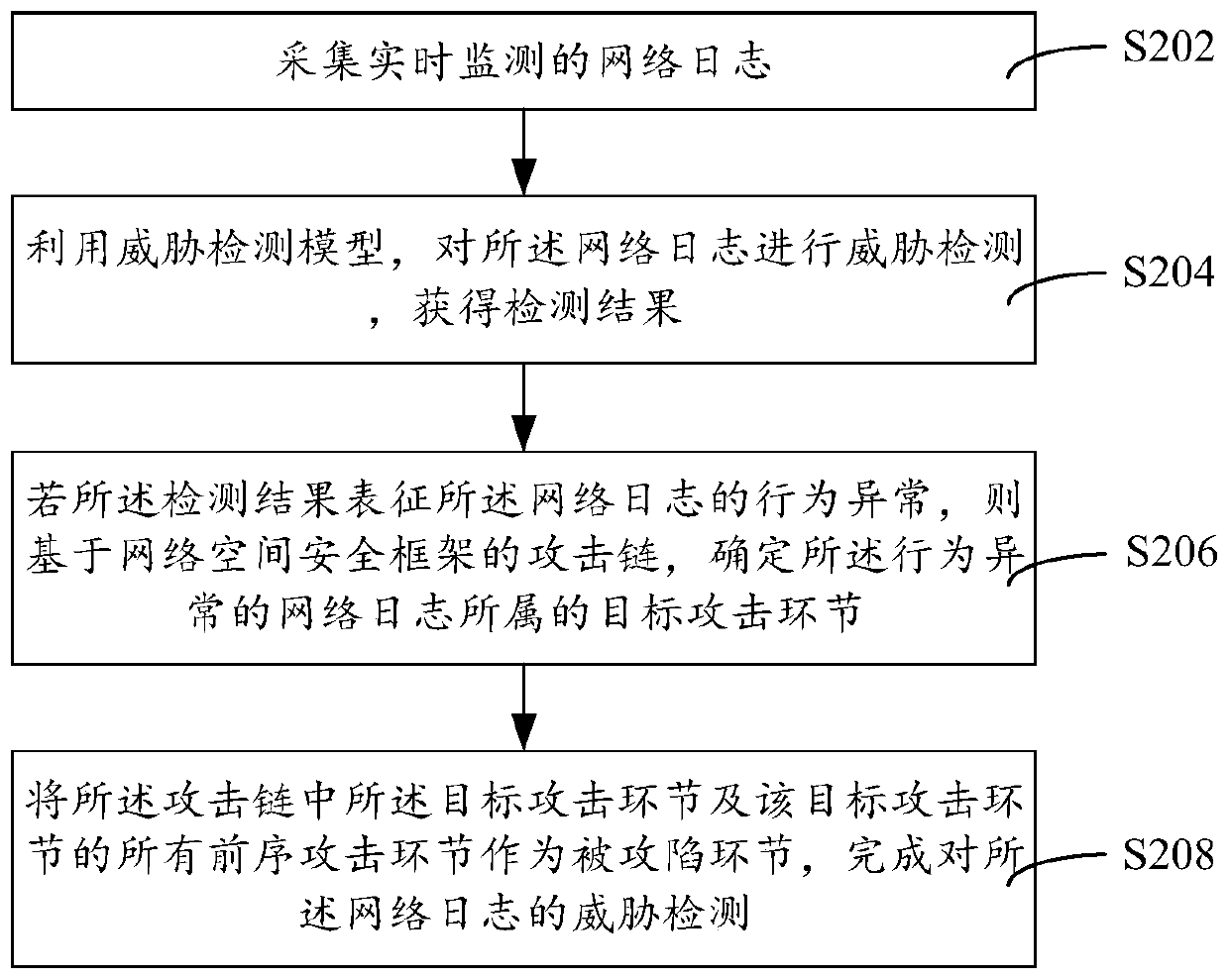
Threat detection method, device and equipment and storage medium
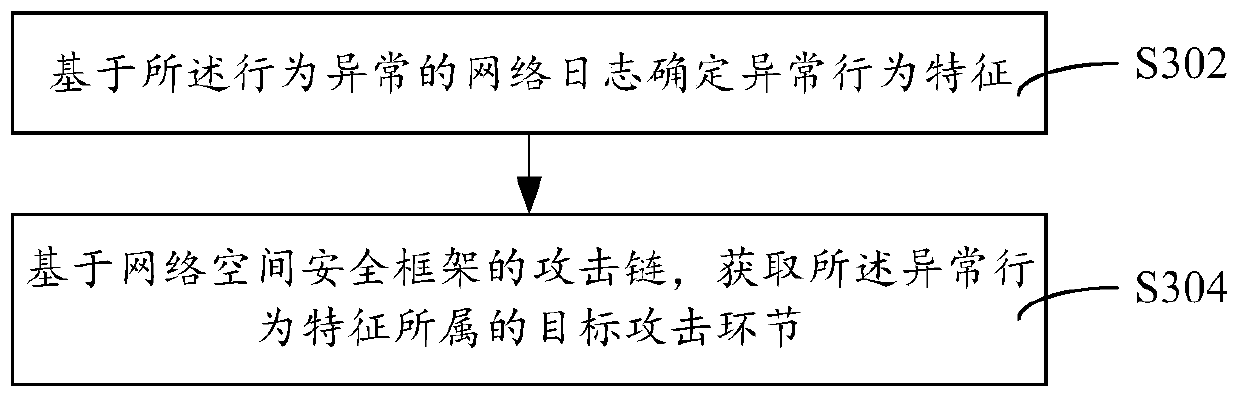
ActiveCN111147504AImprove security defense performanceNeural architecturesTransmissionAttackSecurity framework
The invention discloses a threat detection method. The method comprises the steps of collecting weblog monitored in real time; performing threat detection on the weblog by utilizing a threat detectionmodel to obtain a detection result; if the detection result represents that the behavior of the weblog is abnormal, determining a target attack link to which the weblog with the abnormal behavior belongs based on an attack chain of a network space security framework; and taking the target attack link in the attack chain and all preorder attack links of the target attack link as attacked links tocomplete threat detection of the weblog. The invention further discloses a threat detection device and equipment and a storage medium. Threat capture is carried out from the global perspective of theattack chain, and the security defense capability is improved.
Owner:SANGFOR TECH INC
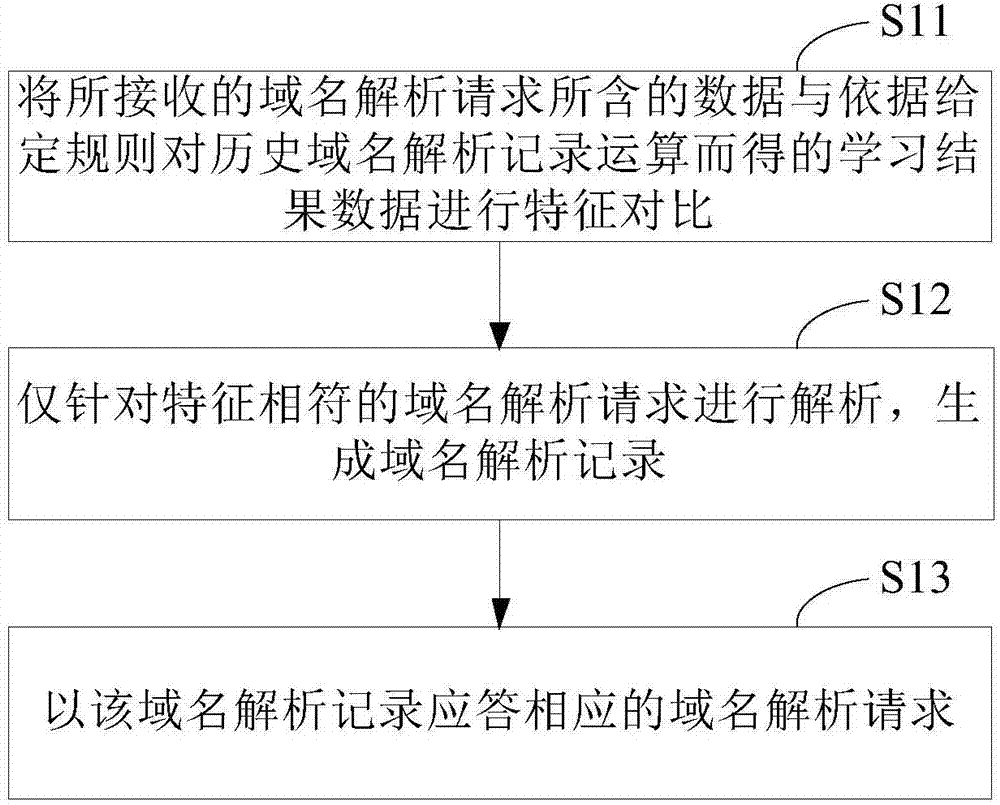
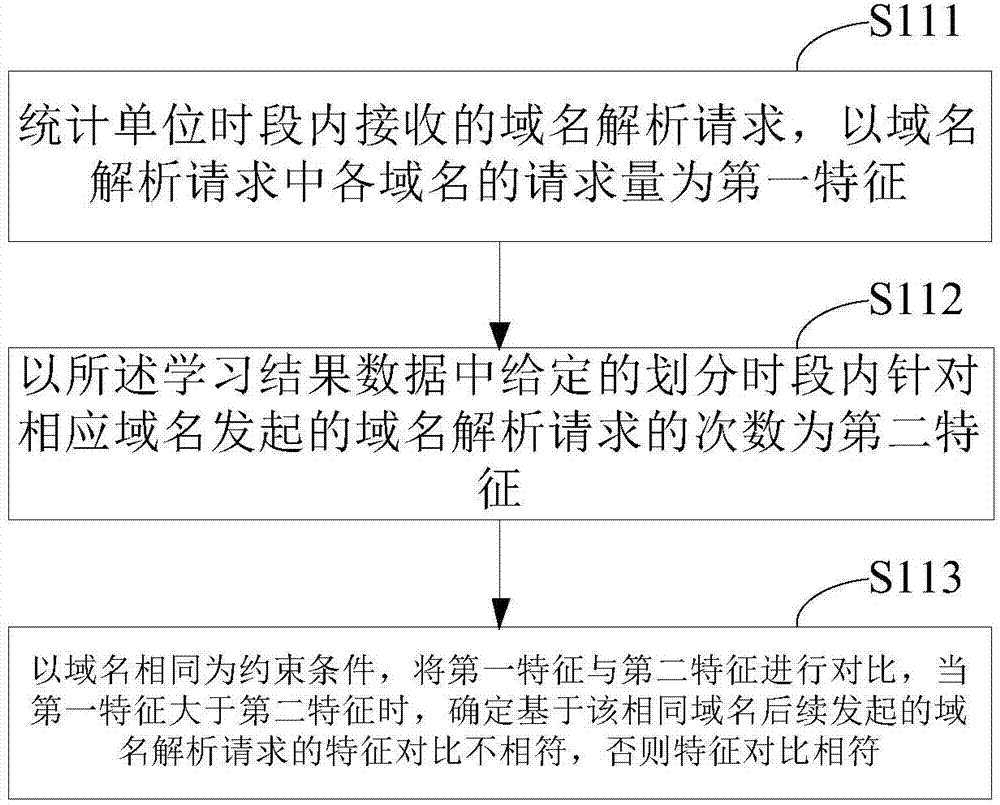
Machine learning type domain name system security defense method and device
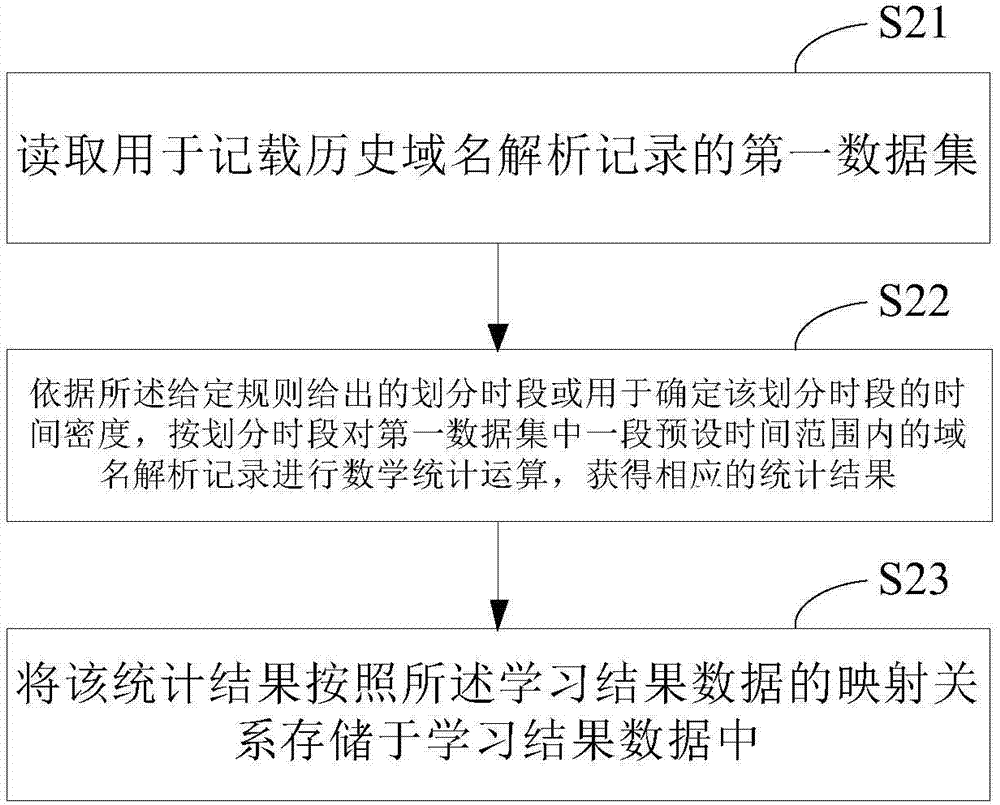
ActiveCN104506538ADoes not affect operating loadQuickly identify access exceptionsTransmissionDomain nameModularity
The invention relates to a machine learning type domain name system security defense method. The method includes the following steps: performing characteristic contrast on data included in received domain name resolution requests and learning result data obtained by historical domain name resolution record operation according to given regulations; resolving for the characteristic-conformed domain name resolution request to generate a domain name resolution record; responding to the corresponding domain name resolution request with the domain name resolution record. Besides, the invention further discloses a device corresponding to the device according to modularized thinking. By implementation of the method and the device, a DNS (domain name server) can understand DNS attacks more intelligently, operation efficiency is optimized, and the function of a disaster recovery system is achieved.
Owner:BEIJING QIHOO TECH CO LTD
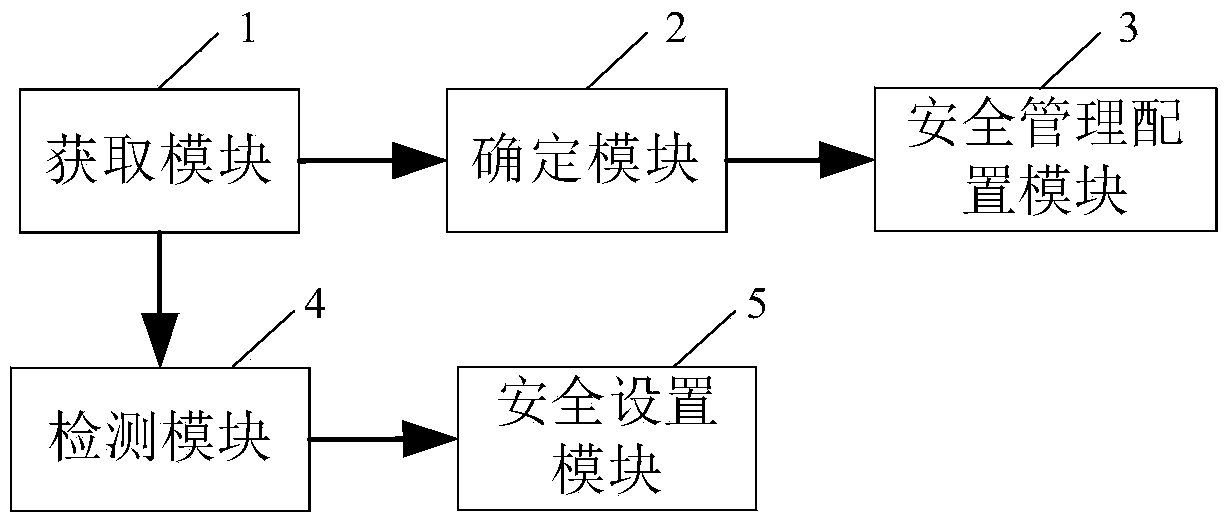
Home network security management method and device and system
InactiveCN104079575AStrengthen security managementRealize a comprehensive physical examinationData switching by path configurationNetwork connectionComputer terminal
The invention relates to a home network security management method and device and a system. The method includes the steps of conducting security scanning on a home network so as to obtain network connection information of all terminals in the home network and network configuration information of gateway devices, confirming whether unknown terminals have access to the home network or no according to the network connection information of all the terminals, conducting security management configuration on the unknown terminals if the unknown terminals have access to the home network so that the unknown terminals can be allowed or refused to have access to the home network, detecting the network configuration information to obtain a detection result, and conducting security set operation on the gateway devices according to the detection result. According to the technical scheme, security vulnerabilities can be effectively checked, resource occupancy and / or security threats caused when unknown devices have access to the network can be effectively avoided, and the security defense capacity of the home network is improved.
Owner:BEIJING QIHOO TECH CO LTD +1
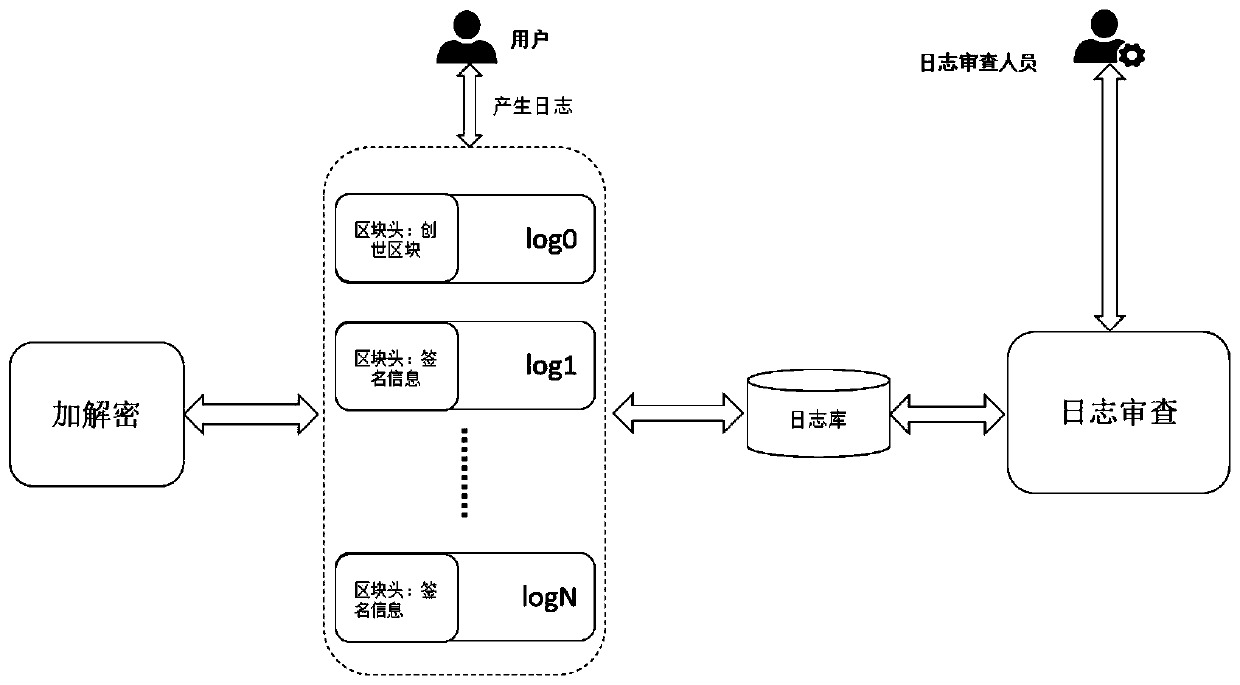
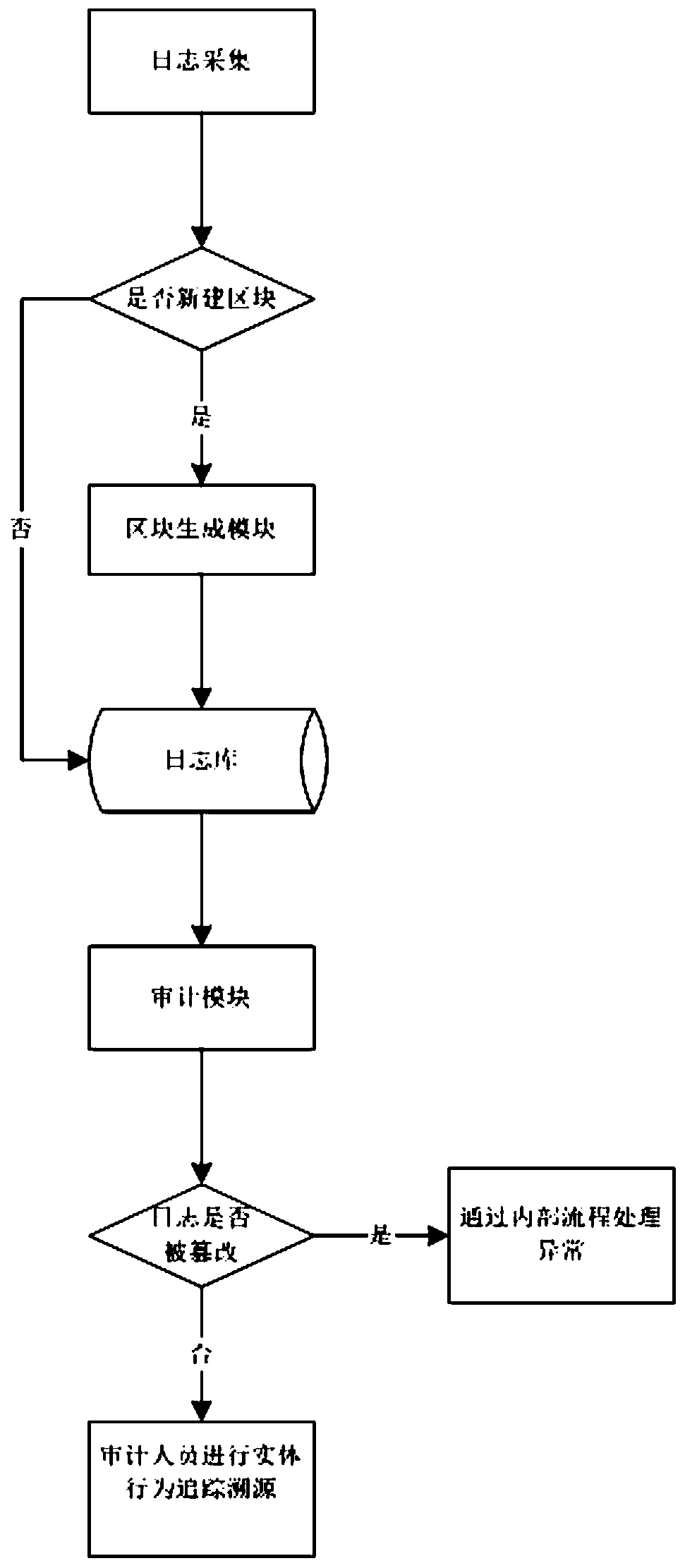
Tamper-proof data storage method, device and system based on blockchain
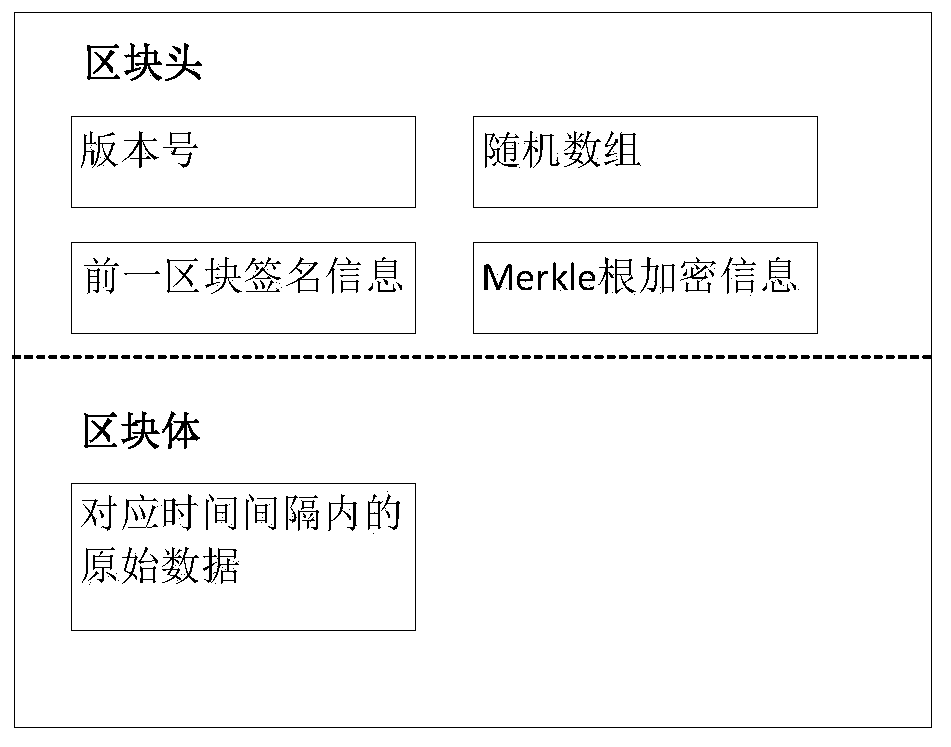
InactiveCN110443073AGuaranteed credibilityIncrease time costFinanceDigital data protectionData validationTamper resistance
The invention discloses a tamper-proof data storage method, device and system based on a block chain, and the method comprises the steps: storing original data as blocks, and enabling all blocks to belinked into the block chain; wherein original data is stored in the block body; wherein the block head comprises a version number, signature information, a random number set and a Merkle root; wherein the signature information is generated by encrypting a hash value generated by performing hash operation on a previous block; wherein the random number set comprises N elements, and the elements arerandom block version numbers or set values; and when the random number group element is the version number corresponding to the block, the leaf node of the Merkle root is the hash value of the corresponding block, otherwise, the leaf node of the Merkle root is the hash value of the set value. During data review, chain verification can be carried out through block signature information, and merkleroot verification can be carried out through merkle roots to verify whether the data is tampered or not. According to the method, whether the data is tampered or not is verified through the stored data, hardware does not need to be additionally added, the time cost for tampering the data is very high, and the credibility of data auditing can be effectively guaranteed.
Owner:NANJING NARI GROUP CORP +4
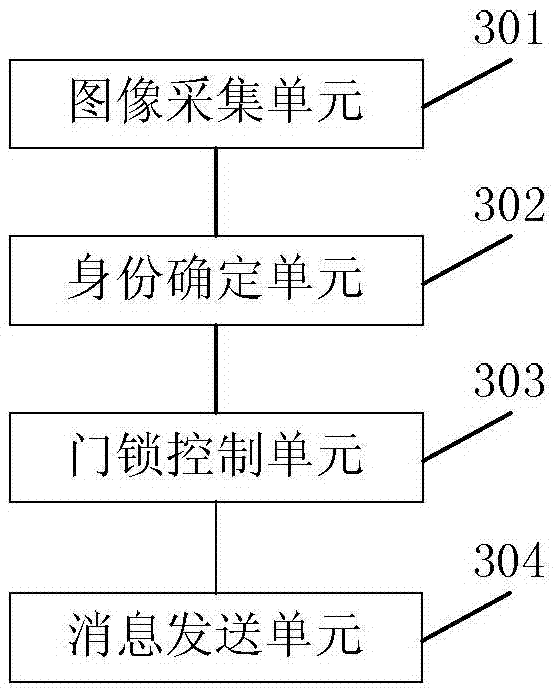
Door lock control method and device
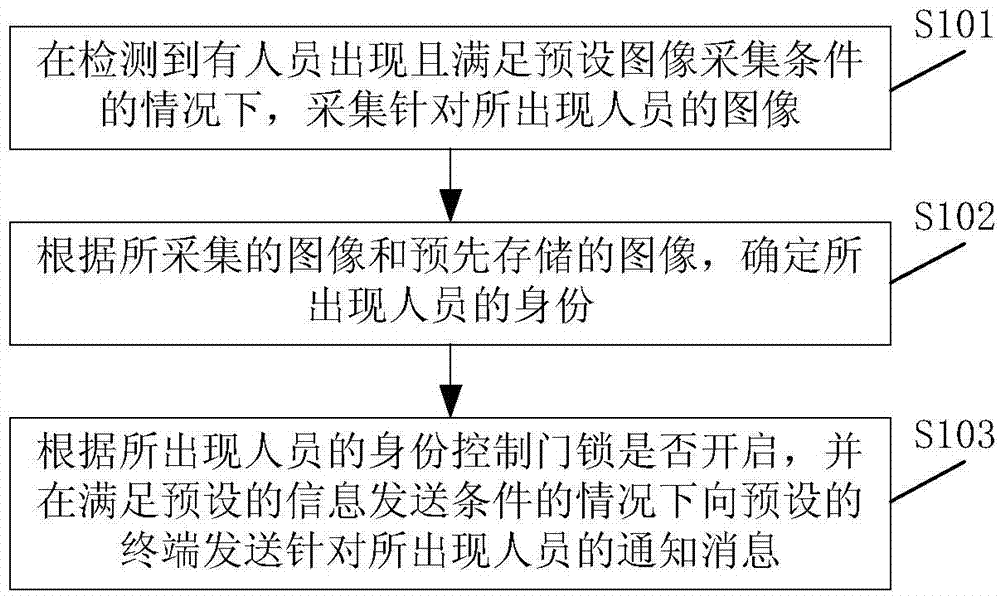
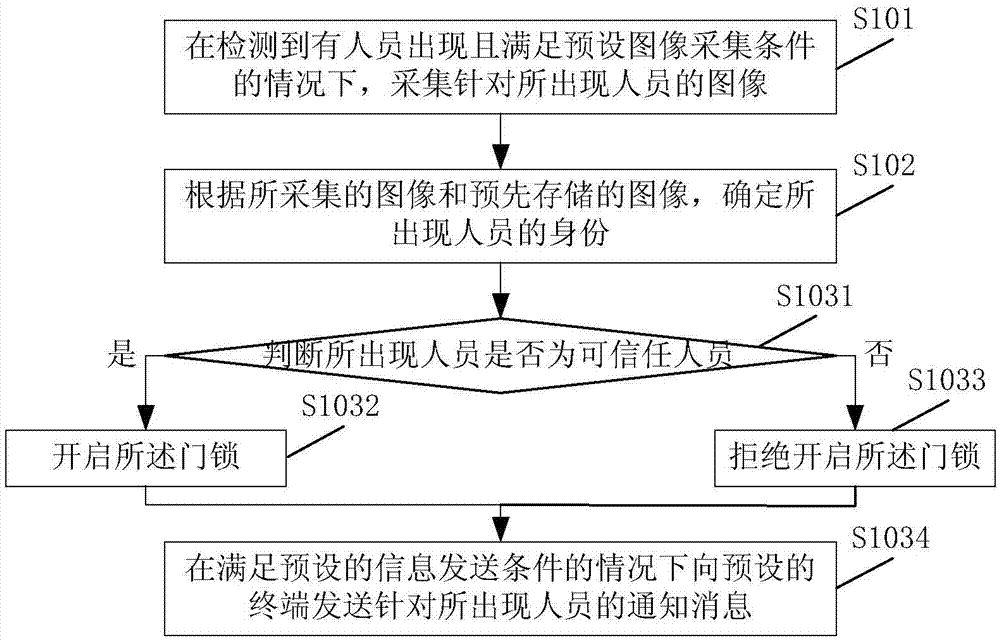
InactiveCN106939731AImprove security defense performanceAdd linkage functionElectric permutation locksAlarm locksInformation transmissionComputer terminal
The embodiment of the present invention discloses a door lock control method and device. The method includes the steps of: when a person is detected and the preset image collection conditions are met, collect an image of the person present, and according to the collected image and the pre-stored image, determine the identity of the person who appears, control whether the door lock is opened according to the identity of the person who appears, and send a notification message for the person who appears to the preset terminal when the preset information sending conditions are met . Applying the technical solutions provided by the embodiments of the present invention to control the door lock can improve the security defense capability of the door lock.
Owner:HANGZHOU HIKVISION DIGITAL TECH
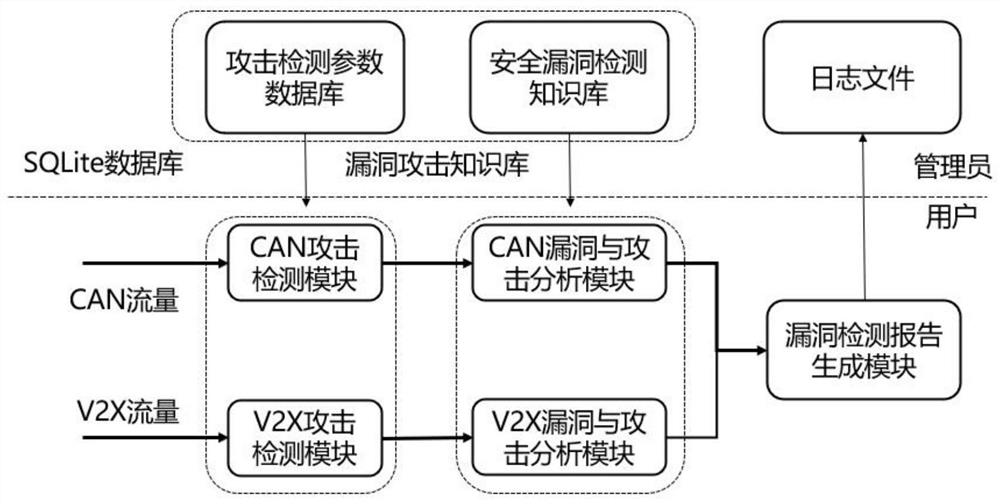
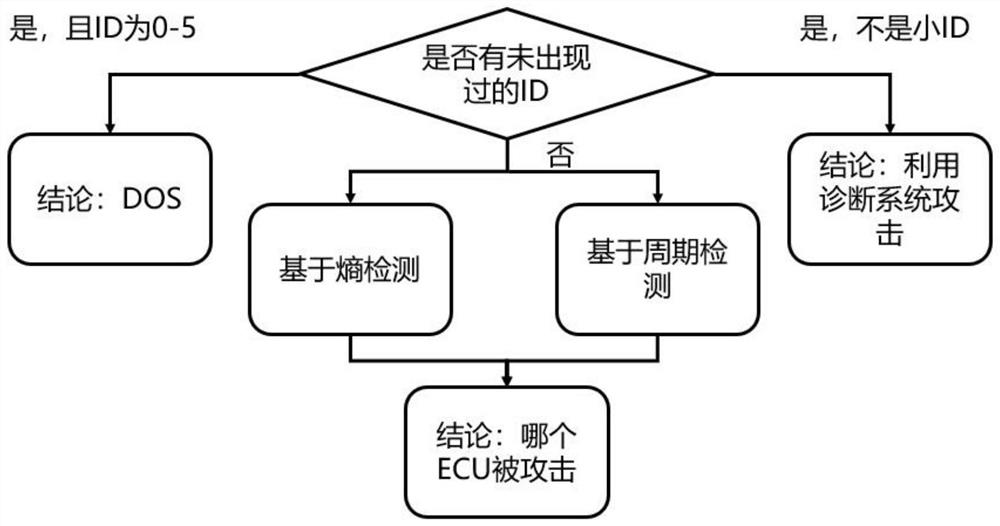
Lossless information security vulnerability detection system and method for Internet of Vehicles
ActiveCN111885060AImprove security defense performanceEfficiencyParticular environment based servicesPlatform integrity maintainanceIntelligent NetworkAttack
The invention provides an Internet of Vehicles-oriented lossless information security vulnerability detection system and method, and the method comprises a module M1: enabling a vulnerability detection subsystem in the detection system to analyze the flow data of an out-vehicle network and / or an in-vehicle network, and obtaining an attack detection result; a module M2: comparing the attack detection result with a vulnerability knowledge base in the detection system to discover vulnerabilities and generating a vulnerability detection report; a module M3: generating a log file according to the vulnerability detection report, modifying the vulnerability knowledge base according to the log file, and updating the detection system according to the detection system configuration data. According to the invention, before the intelligent networked automobile is attacked on a large scale, the security hole is detected in time under the condition of not influencing the normal running of the automobile, and the security defense capability of the intelligent networked automobile is improved.
Owner:SHANGHAI JIAO TONG UNIV +1
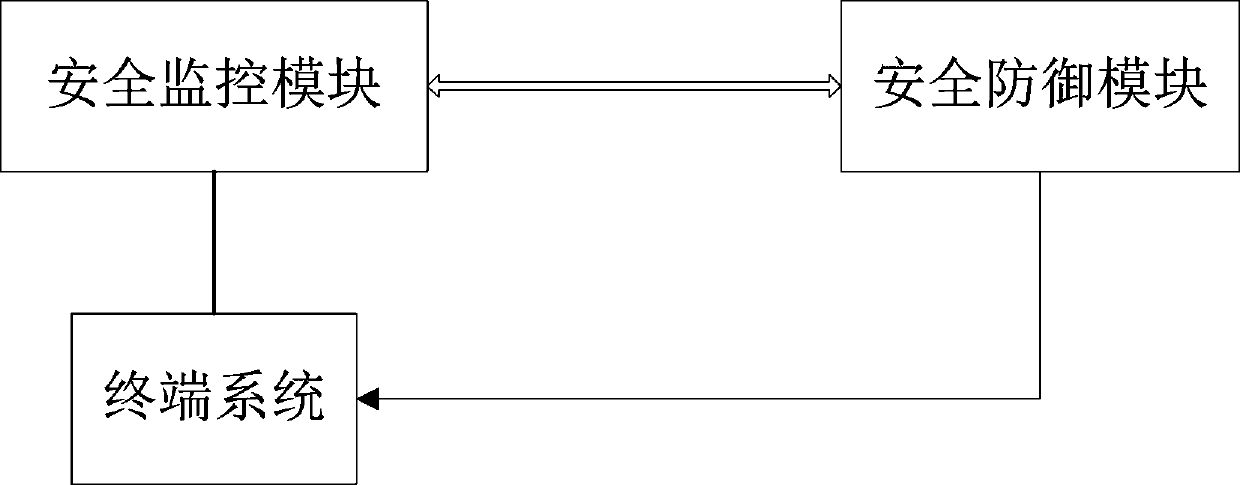
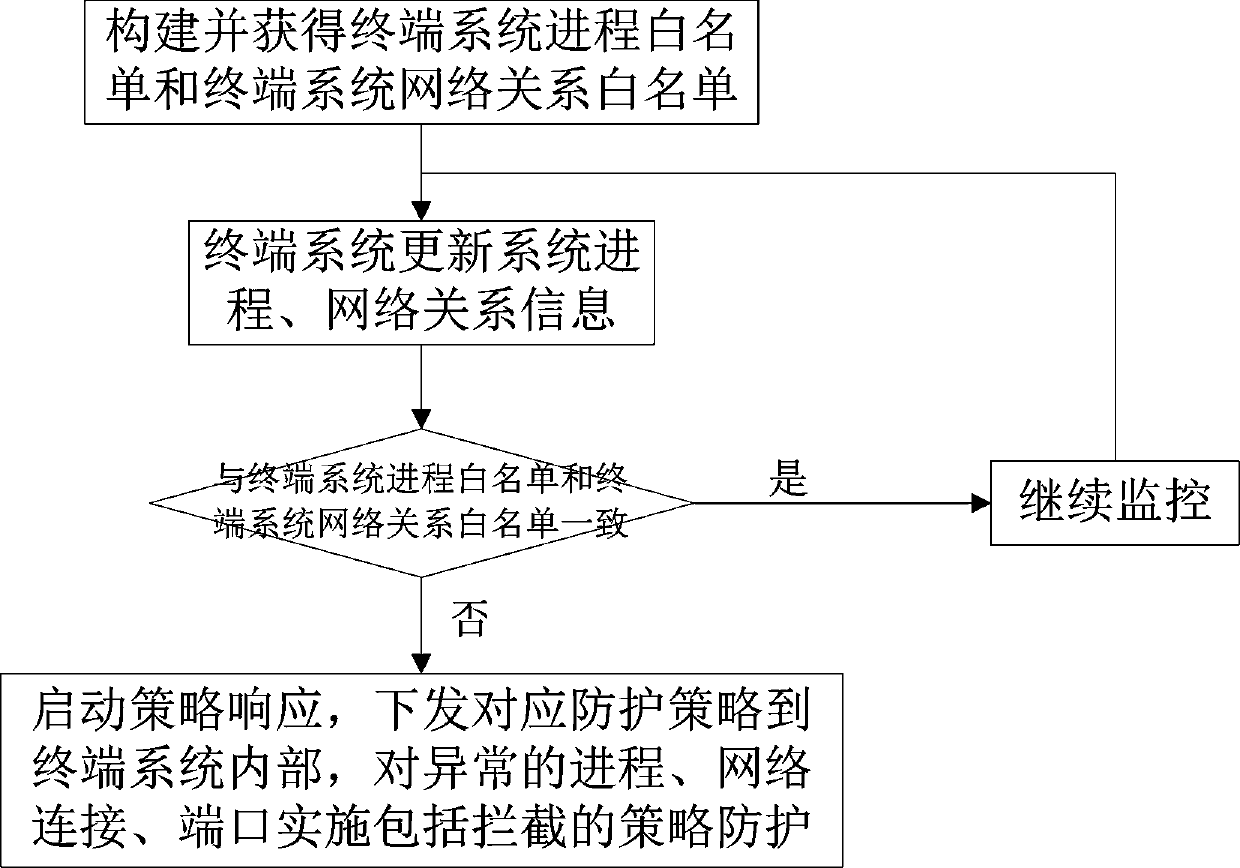
Self-security defense system and security defense method thereof for Internet of Things terminal
InactiveCN111010384AImprove security levelImprove security defense performanceTransmissionNetwork connectionAttack
The invention relates to a self-security defense system and a security defense method thereof for an Internet of Things terminal. The system comprises a security monitoring module used for monitoringan Internet of Things terminal system in real time and transmitting information to a security defense module, and the security defense module which is used for comparing the transmitted information byutilizing an analysis model matched with the terminal system and performing processing based on a comparison result. The method comprises the steps: constructing and obtaining a terminal system process white list and a terminal system network relationship white list; after the terminal system updates the system process and the network relationship information, continuing the monitoring if the updated content is consistent with the white list, otherwise, starting the strategy response, and sending a corresponding protection strategy to the interior of the terminal system, so the strategy protection is implemented on an abnormal process, network connection and a port. According to the invention, the Internet of Things terminal is helped to establish a self-security defense mechanism, self-security protection for attack threats and virus invasion is realized, the security level of the terminal system is comprehensively improved, and the information security of a user using the intelligent Internet of Things terminal is ensured.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
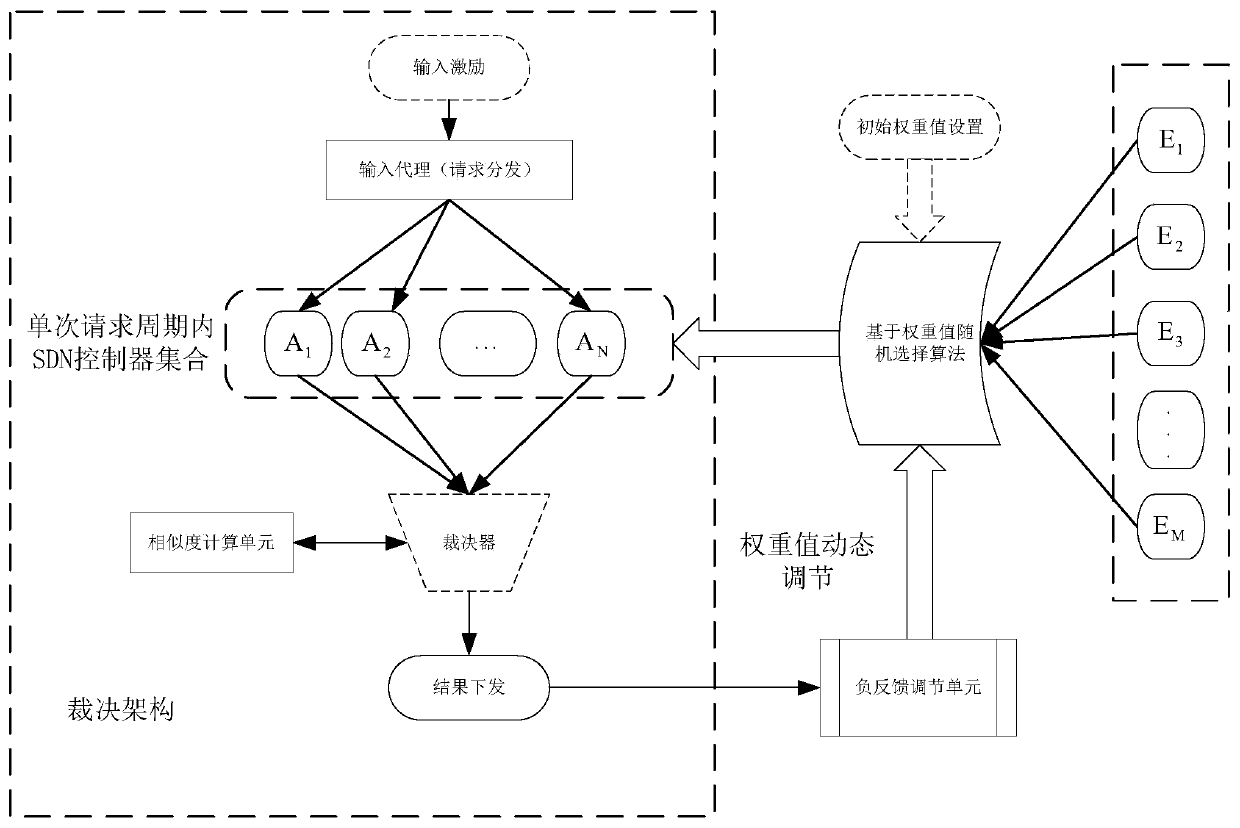
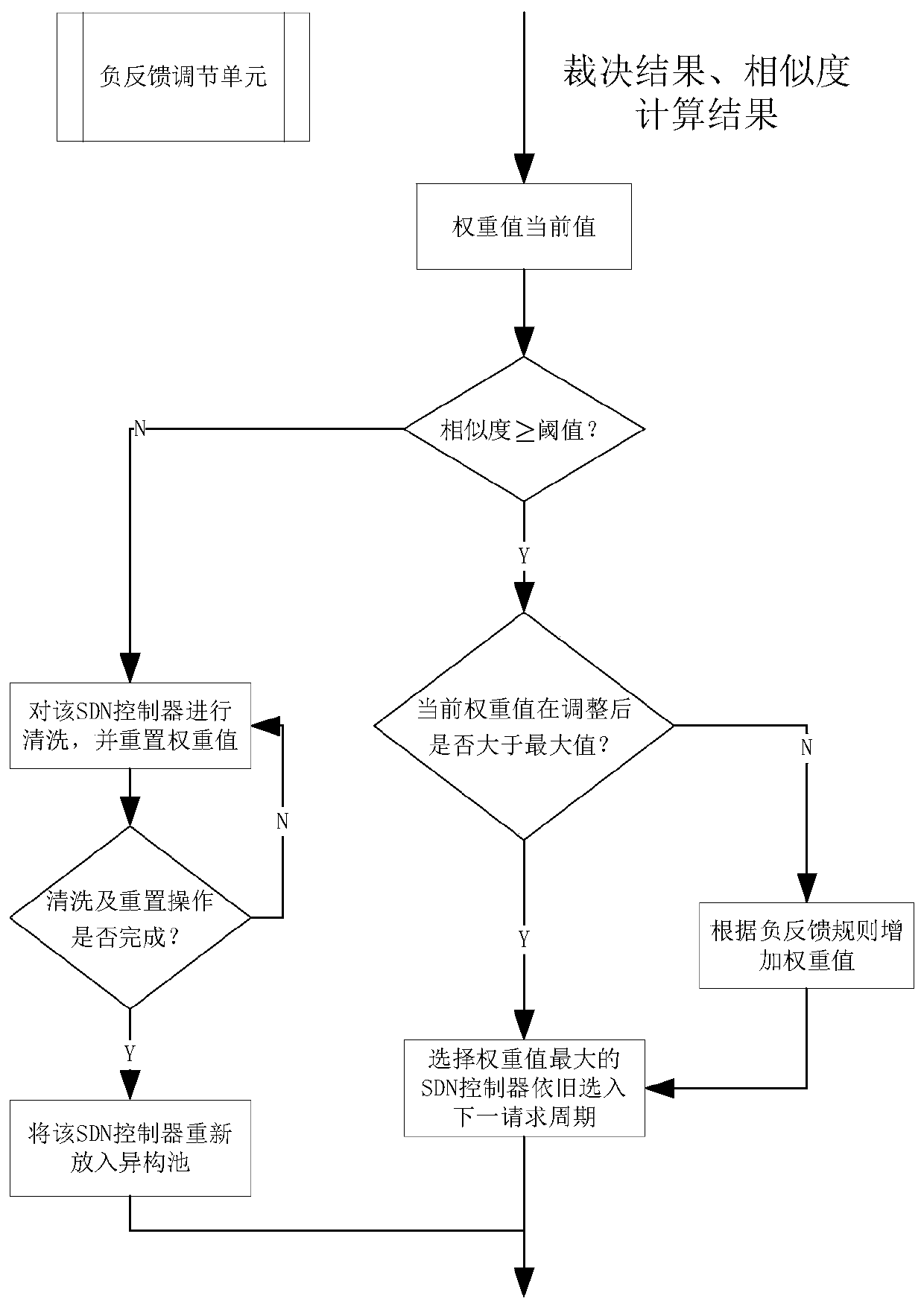
Multimode ruling system based on time iteration and negative feedback mechanism
ActiveCN111385299AReduce the likelihood of being successfully attackedImprove security defense performanceTransmissionNegative feedbackControl layer
The invention discloses a multi-mode ruling system based on time iteration and a negative feedback mechanism. The multi-mode ruling system comprises a heterogeneous pool unit, a multi-mode ruling device and a negative feedback unit, wherein the heterogeneous pool unit comprises three or more heterogeneous SDN controllers; in each SDN control layer, the heterogeneous SDN controllers are used for processing input requests at the same time, and submit an output result set of each SDN controller in unit time to the multi-mode ruling device; the multi-mode ruling device performs consistency rulingon information distribution in a flow table of the output result set, and issues a ruling result to a switch; and after each judgment, the negative feedback mechanism adjusts the confidence of the corresponding heterogeneous SDN controller according to the ruling result, so that dynamic selection of the heterogeneous SDN controllers in the heterogeneous pool is realized, and the security defense capability of the system is improved.
Owner:ZHEJIANG LAB
Ocean nuclear power platform power grid grounding fault line selection protection method and system
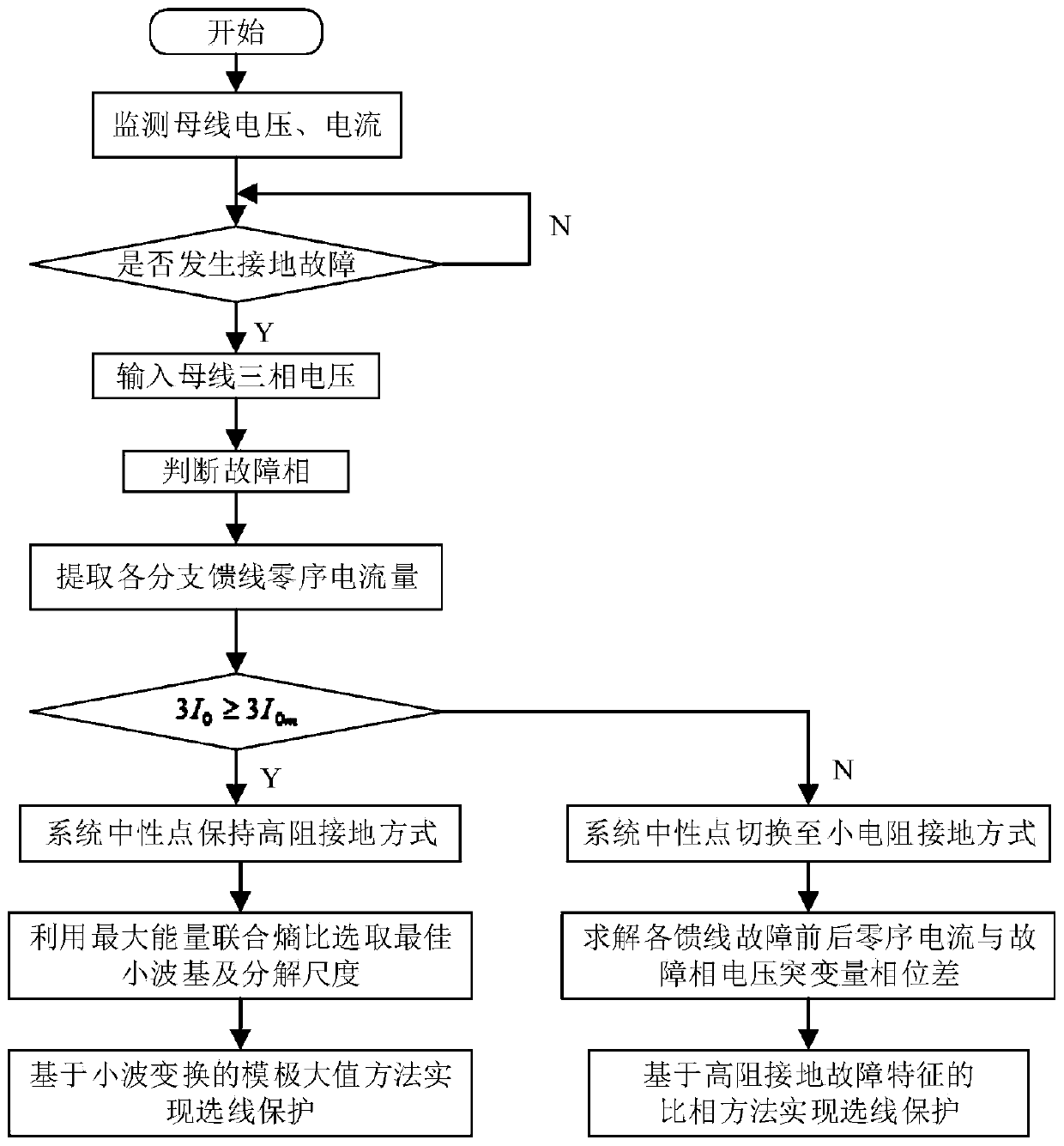
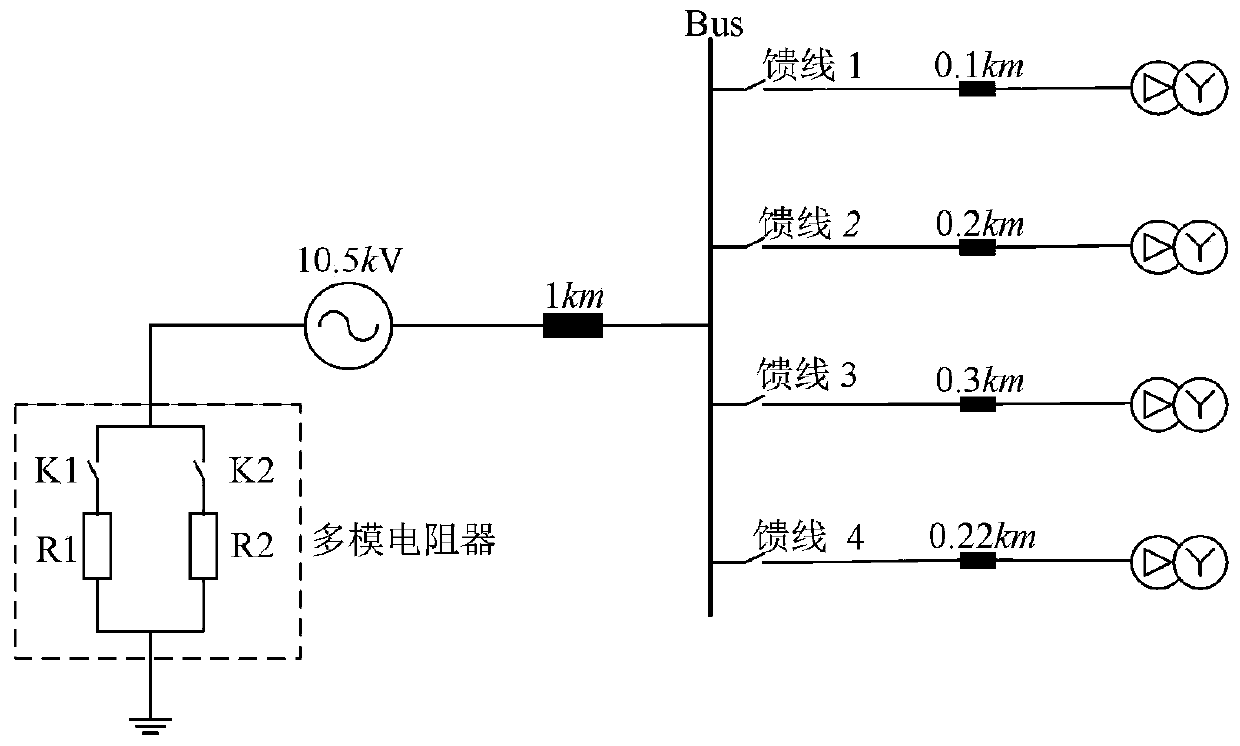
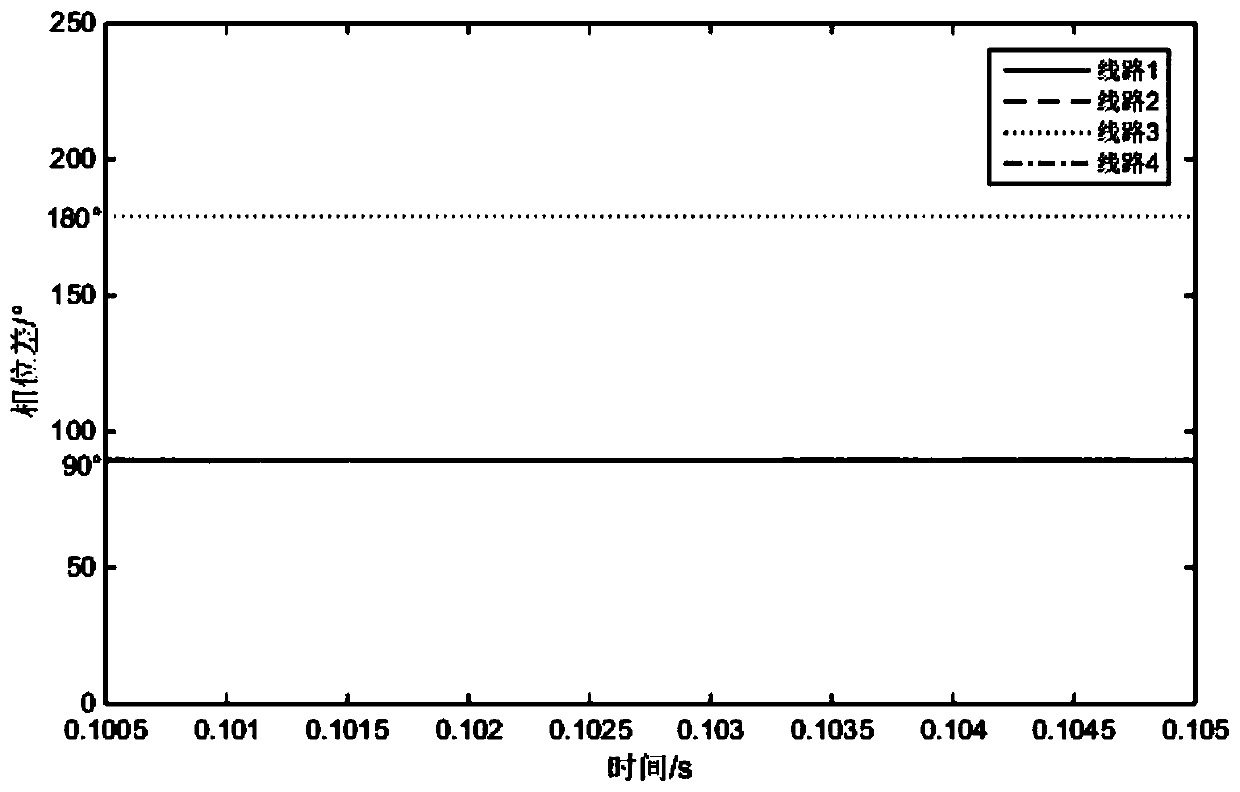
ActiveCN111398733AImprove security defense performanceHigh protection sensitivityFault location by conductor typesShort-circuit testingElectric power systemPower grid
The invention discloses an ocean nuclear power platform power grid grounding fault line selection protection method and an ocean nuclear power platform power grid grounding fault line selection protection system, belonging to the field of ocean nuclear power platform power grid protection. The ocean nuclear power platform power grid grounding fault line selection protection method comprises the following steps of: when a single-phase earth fault occurs in the system, if a fault current amplitude is higher than a given threshold, keeping a neutral point in a high-resistance grounding mode, selecting an optimal wavelet basis and a decomposition scale based on a maximum energy joint entropy ratio, and performing earth fault line selection by utilizing a wavelet transformation method based ona modulus maximum value; when a high-transition resistance grounding fault occurs in the system, switching the neutral point to a small-resistance grounding mode, and constructing a branch zero-sequence current and fault phase voltage break variable phase comparison line selection protection method based on features of the high-resistance grounding fault to perform grounding fault line selection.The ocean nuclear power platform power grid grounding fault line selection protection method can be effectively matched with the operation mode and the grounding fault features of an ocean nuclear power platform power system, is high in line selection accuracy rate, is suitable for various grounding fault modes possibly happening to the platform system, and effectively improves the safety defensecapacity of the ocean nuclear power platform.
Owner:HUAZHONG UNIV OF SCI & TECH
Defense method and device, client, server, storage medium and system
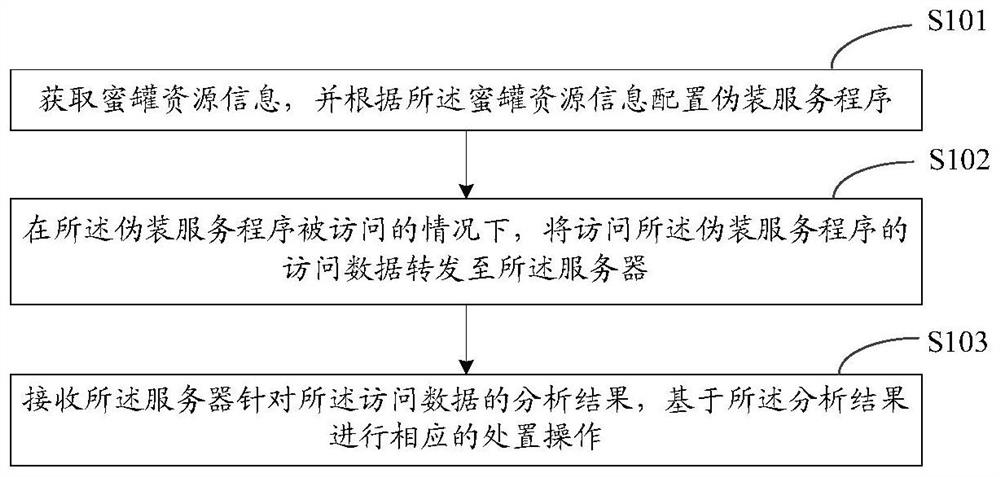
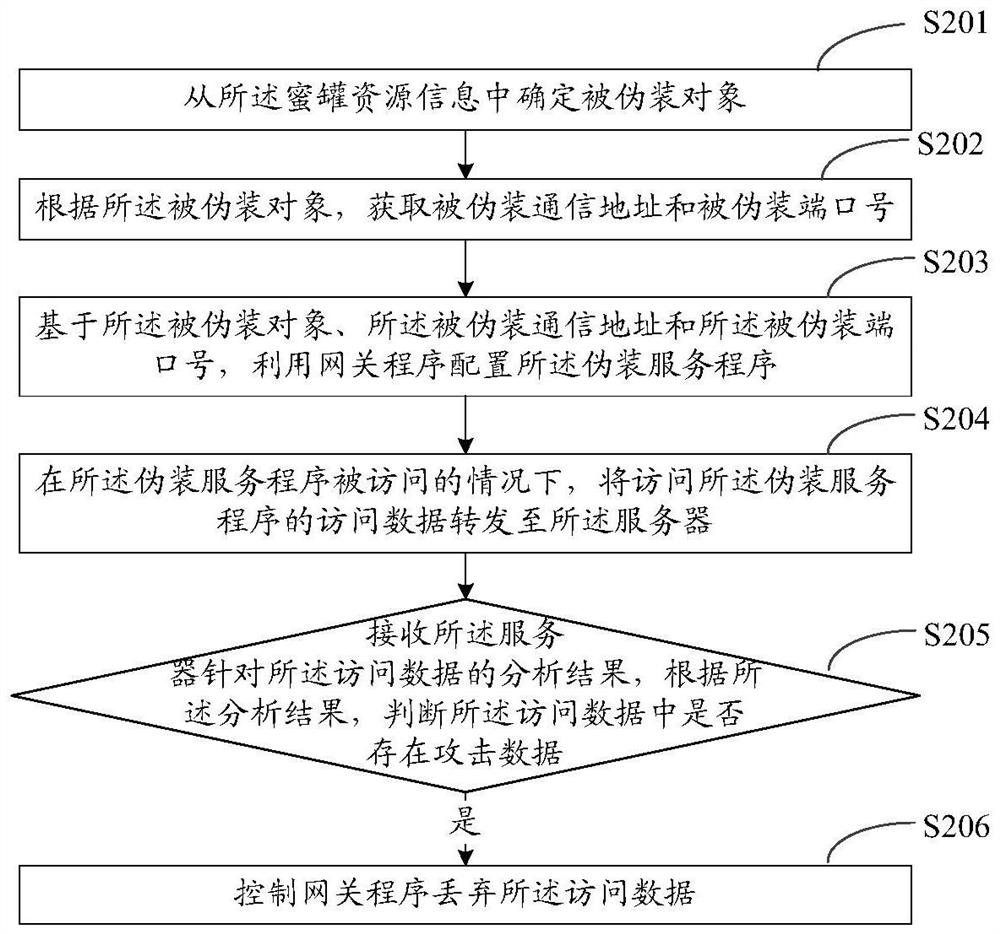
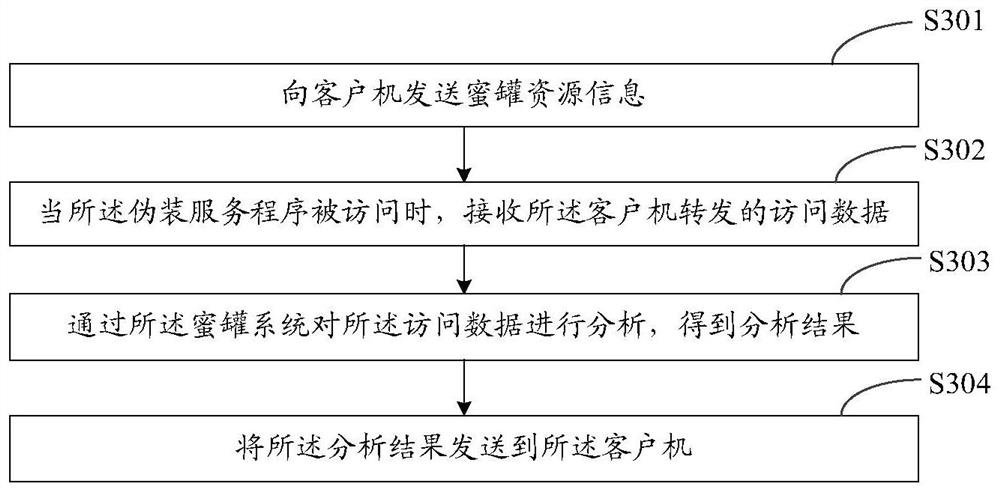
PendingCN112910907ACapable of active defenseImprove security defense performanceTransmissionResource informationHoneypot
The invention provides a defense method and device, a client, a server, a storage medium and a system. The method is applied to the client and comprises the steps of: obtaining honeypot resource information, wherein a camouflage service program is configured according to the honeypot resource information; under the condition that the disguised service program is accessed, forwarding access data for accessing the disguised service program to the server, wherein the server is deployed with a honeypot system; and receiving an analysis result of the server for the access data, and performing corresponding disposal operation based on the analysis result. Thus, by configuring the disguise service program in the client and combining the honeypot system in the server, the client has the active defense capability, and the overall security defense effect is improved; in addition, an attacker can be decoy to attack only by configuring a normal client, so that the deployment cost and the hardware cost are greatly reduced.
Owner:SANGFOR TECH INC
Network security protection method and device and electronic device
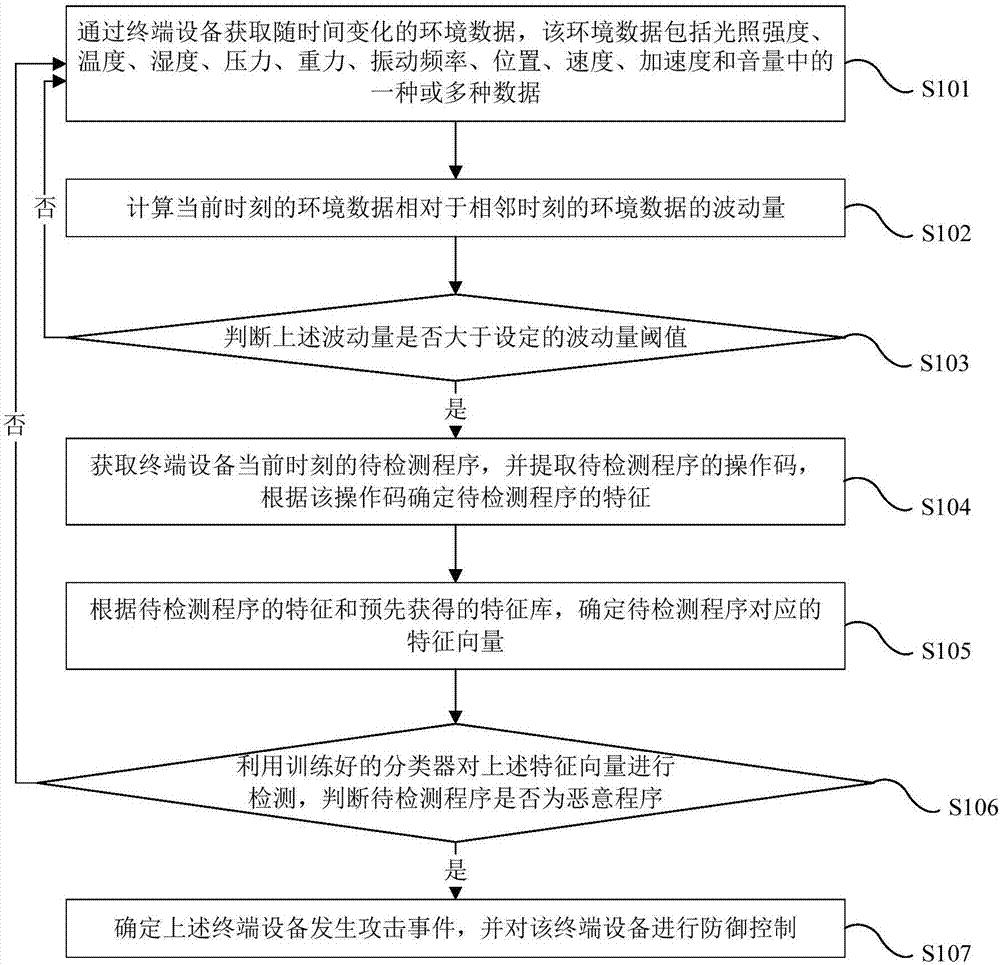
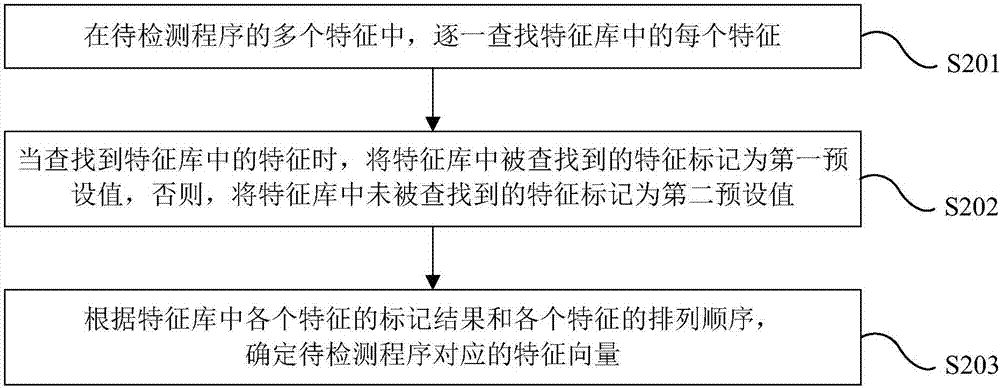
InactiveCN107241350AImprove security defense performanceAbnormal situations are detected in timeMeasurement devicesTransmissionFeature vectorAcquired characteristic
The invention provides a network security protection method, device and an electronic device and relates to the technical field of network security. The method comprises the steps of obtaining environmental data changing along with time through a terminal device; calculating the fluctuation quantity of the environmental data at current moment relative to the environmental data at the adjacent moment and judging whether the fluctuation quantity is greater than a set fluctuation quantity threshold or not; if so, obtaining a to-be-detected program of the terminal device at the current moment, extracting an operation code of the to-be-detected program and determining characteristics of the to-be-detected program according to the operation code; determining a characteristic vector corresponding to the to-be-detected program according to the characteristic of the to-be-detected program and a characteristic library obtained in advance; detecting the characteristic vector by using the trained classifier and judging whether the to-be-detected program is a malicious program or not; and if so, determining that an attack event appears in the terminal device and carrying out protection control on the terminal device. The abnormal condition of a physical network sensing layer can be timely found out and the security protection performance of the Internet of Things is improved.
Owner:紫光恒越技术有限公司
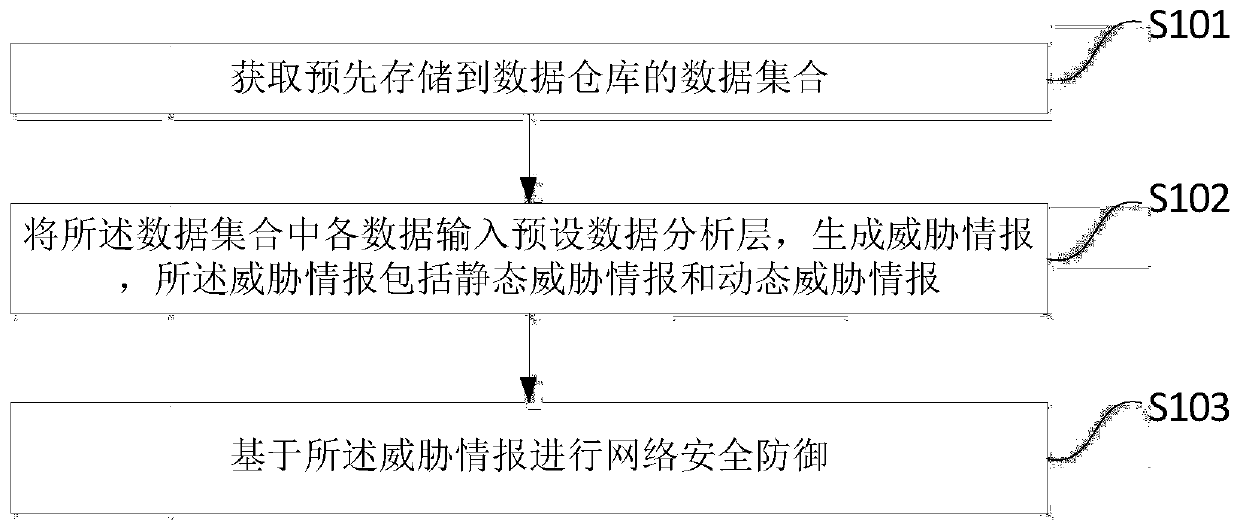
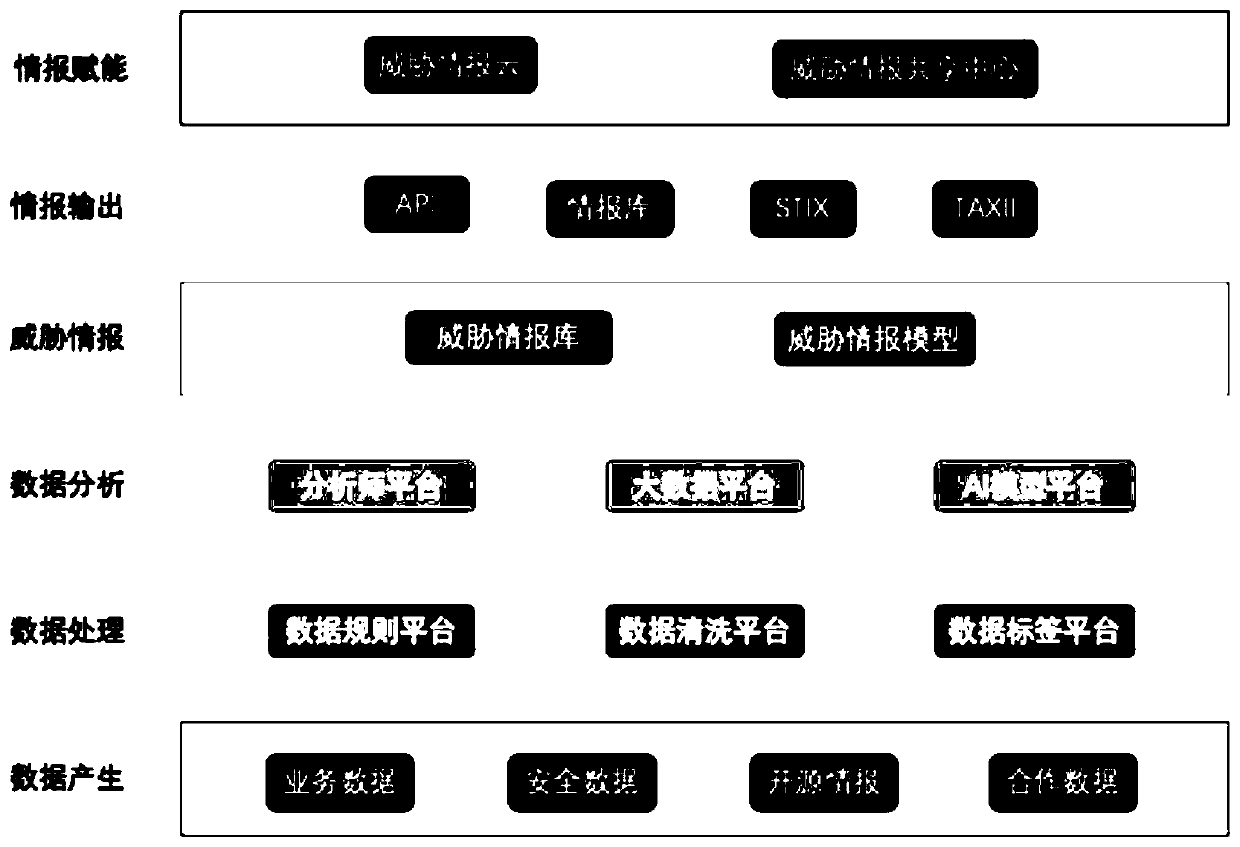
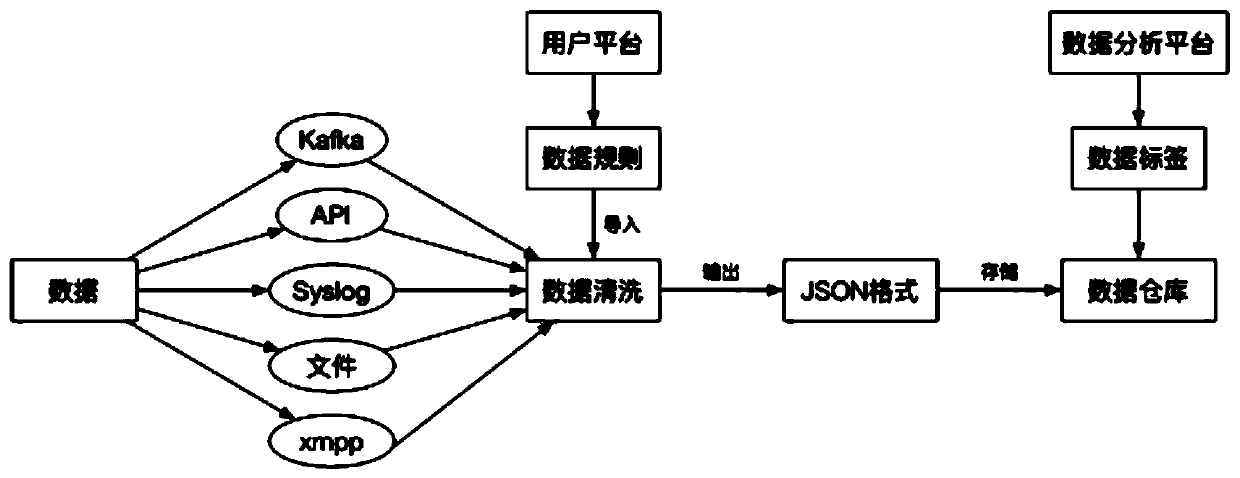
Security threat intelligence management method and system based on big data, storage medium and terminal
ActiveCN111327607AImprove security defense performanceRealize the synchronization of the whole networkTransmissionThreat intelligenceData entry
The invention discloses a security threat intelligence management method and system based on big data, a storage medium and a terminal. The method comprises the steps of obtaining a data set pre-stored in a data warehouse; inputting each piece of data in the data set into a preset data analysis layer to generate threat intelligence which comprises static threat intelligence and dynamic threat intelligence; and performing network security defense based on the threat information. Therefore, by adopting the embodiment of the invention, the security defense capability of the whole network can be improved.
Owner:重庆特斯联智慧科技股份有限公司
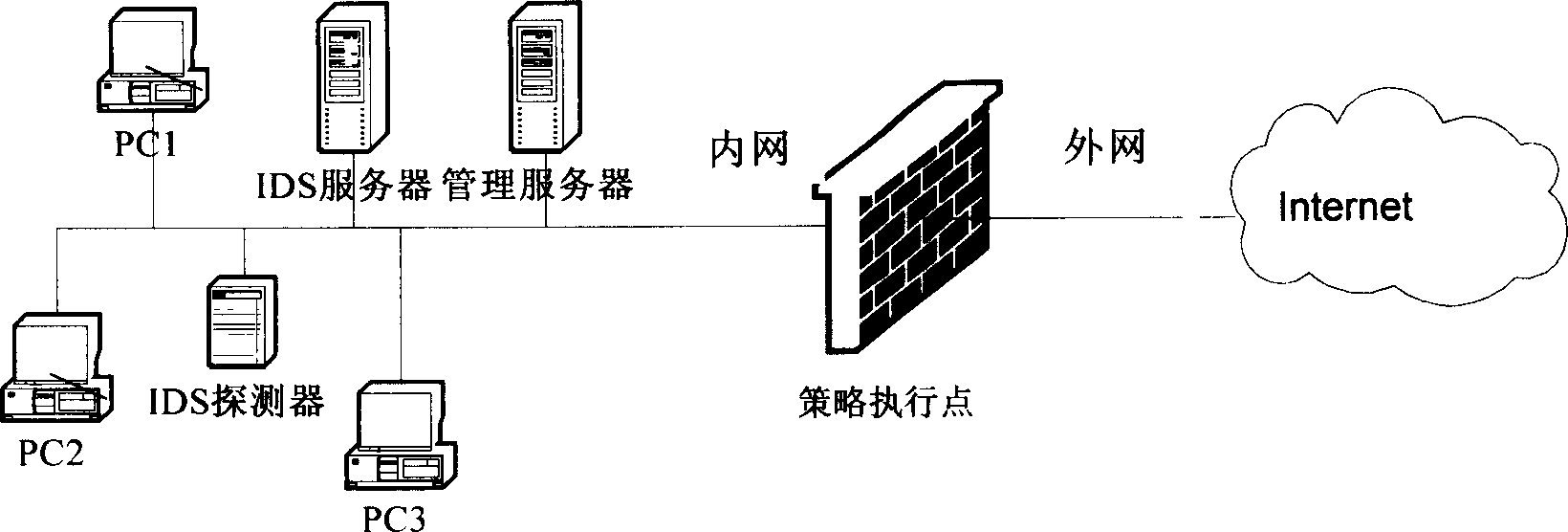
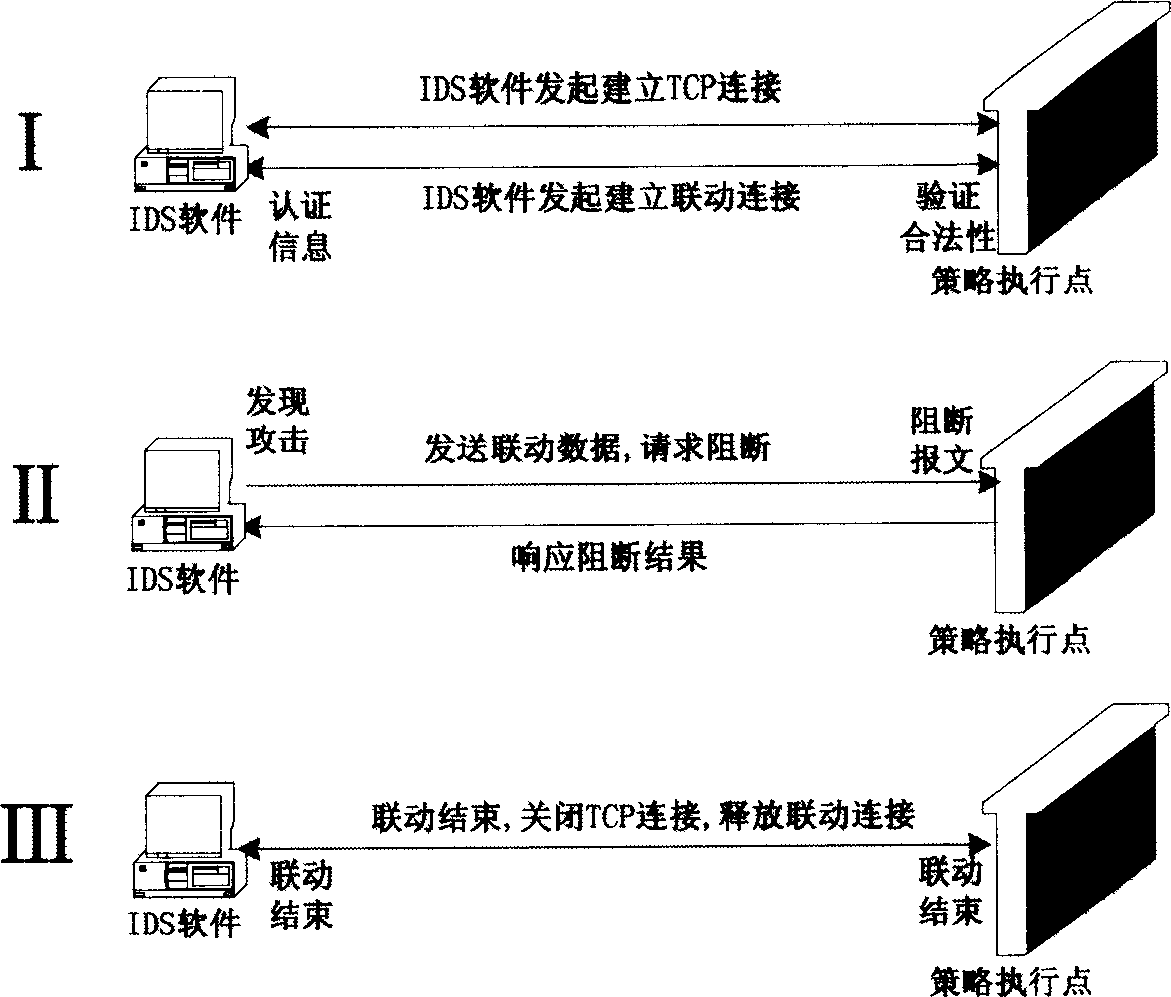
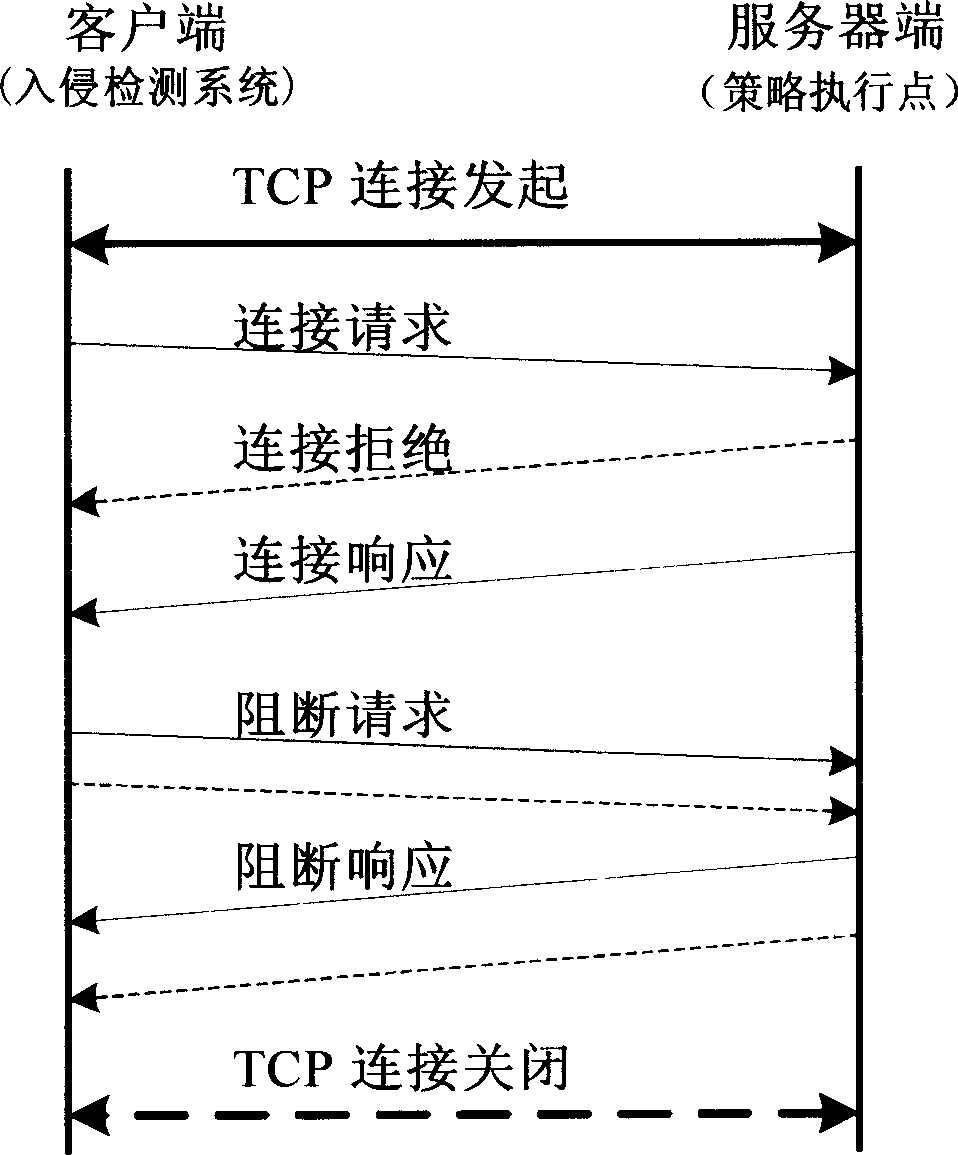
Tactics executing point and linking method of it and intrusion detection system
InactiveCN1863093AImprove security defense capabilitiesAvoid attackPlatform integrity maintainanceData switching networksIntrusion detection systemStrategy execution
The invention supplies a method of interlocking between strategy execution points and invading testing system. It includes the following steps: building up interlocking connection between invading testing system and strategy executing points; keeping communication between the strategy execution points and the invading testing system; if checking invading action, the strategy execution points would response invading process result. The invention improves the safety and defending ability of the system.
Owner:HUAWEI TECH CO LTD
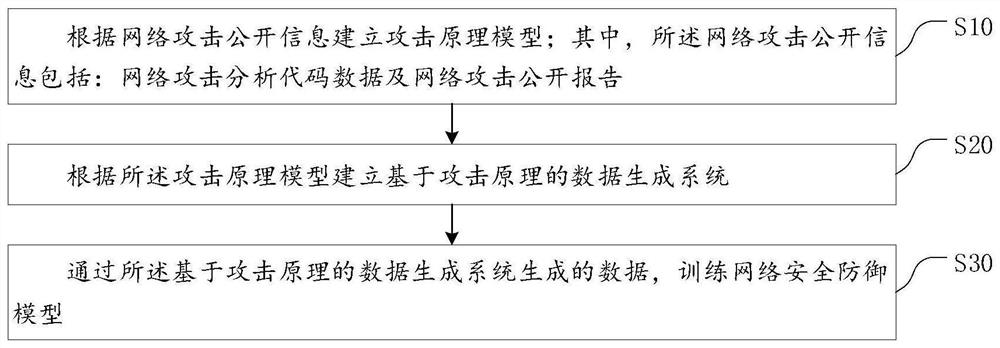
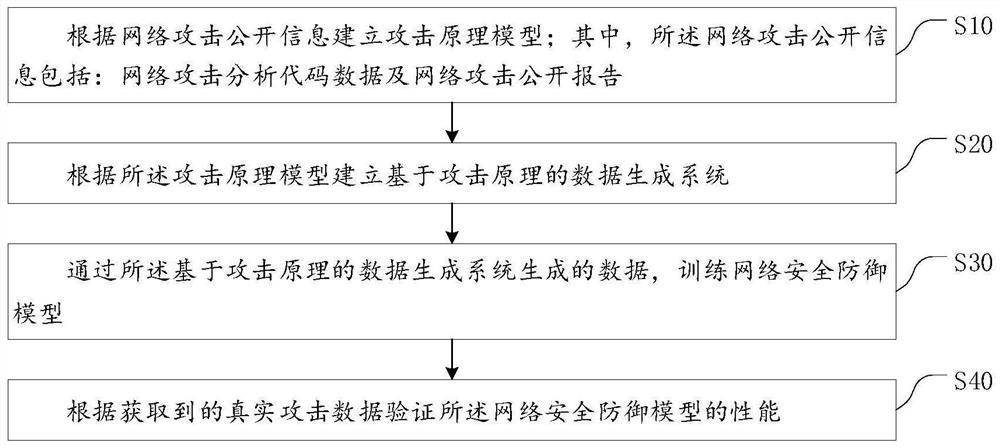
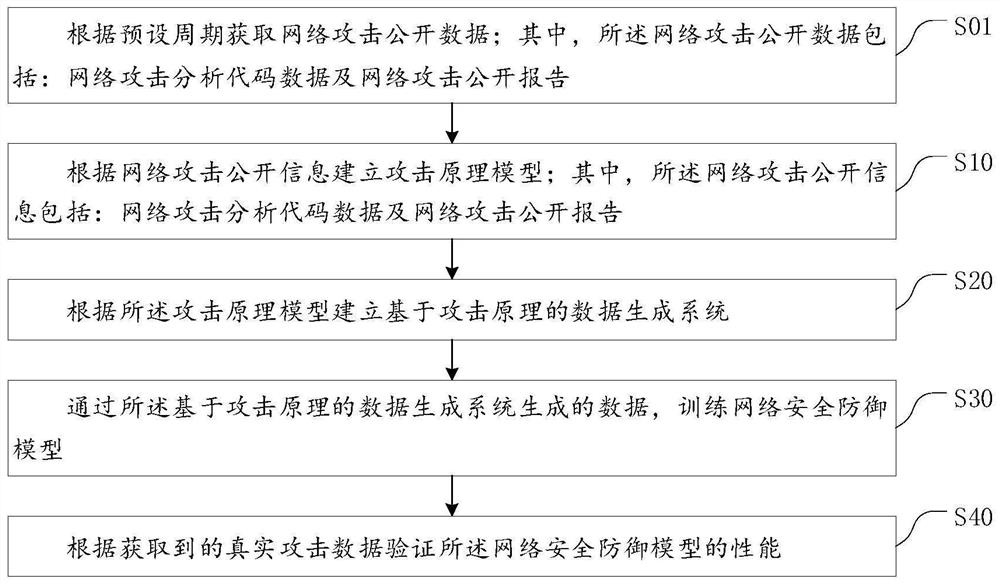
Network attack data automatic generation method and system based on attack principle
PendingCN112261045AMeet needsAddressing the Scarcity of Available DataMachine learningTransmissionAttackData needs
The invention provides a network attack data automatic generation method and system based on an attack principle, and the method comprises the steps: building an attack principle model according to the public information of a network attack, wherein the network attack public information comprises network attack analysis code data and a network attack public report; establishing a data generation system based on an attack principle according to the attack principle model; and training a network security defense model through the data generated by the data generation system based on the attack principle. According to the invention, vivid and effective target data can be generated in a large-batch and customized mode through editing of the configuration file, the data requirements of the network security defense AI model in the training and testing stages can be met, and according to the generation system designed and achieved through the method, a network security defense AI model user can edit the configuration file simply, and therefore, a large amount of target attack data can be generated in a customized manner for model training and testing.
Owner:GUANGZHOU UNIVERSITY
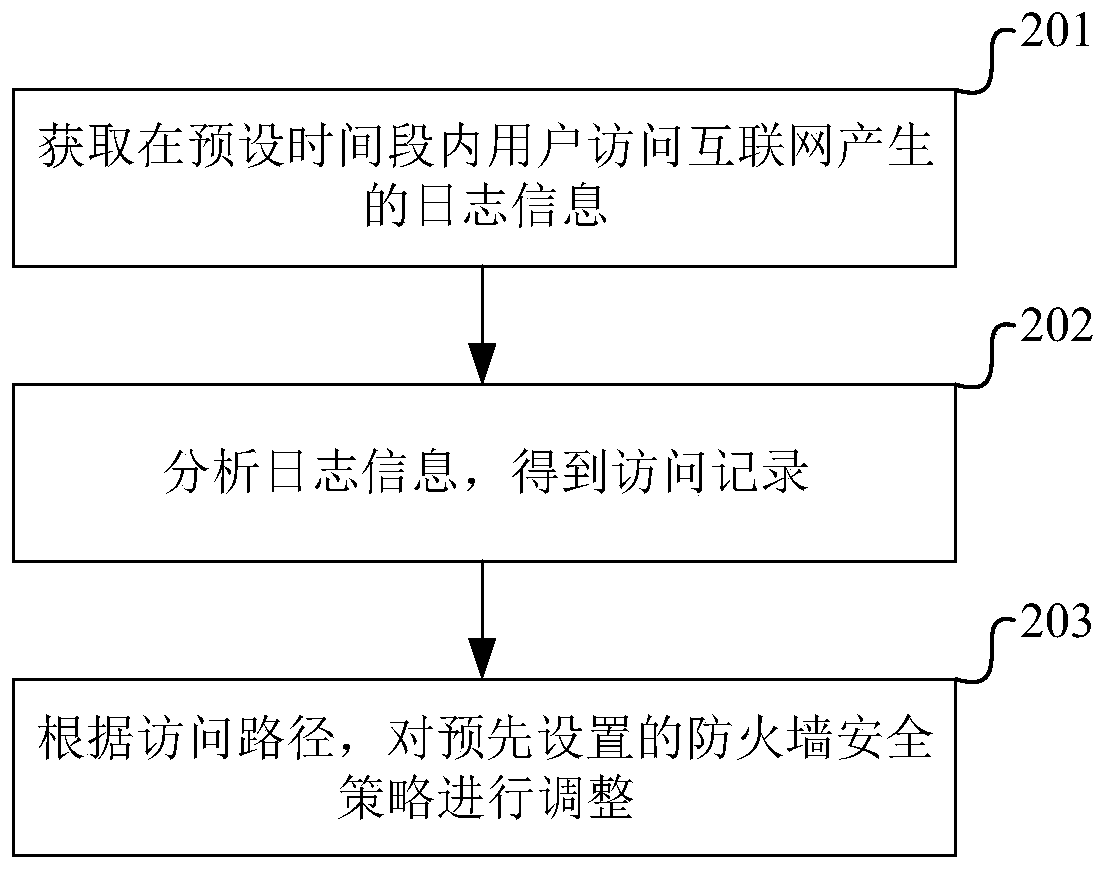
Firewall security policy adjusting method and device
InactiveCN111277586AImprove security defense performanceAvoid the problem of human error in judgmentTransmissionPathPingThe Internet
The invention provides a firewall security policy adjustment method and device. The method comprises the steps that in a preset time period, after log information generated when a user accesses the Internet is obtained, an access record can be obtained by analyzing the log information, and the access record can comprise multiple access paths; then, a preset firewall security policy can be adjustedaccording to the access path. Thus, compared with the mode of considering to configure the security policy in the prior art, the method provided by the embodiment of the invention can adjust the security policy according to the actual access situation, so that the problem of artificial judgment errors can be avoided, and the overall security defense capability of the network can be improved.
Owner:武汉思普崚技术有限公司
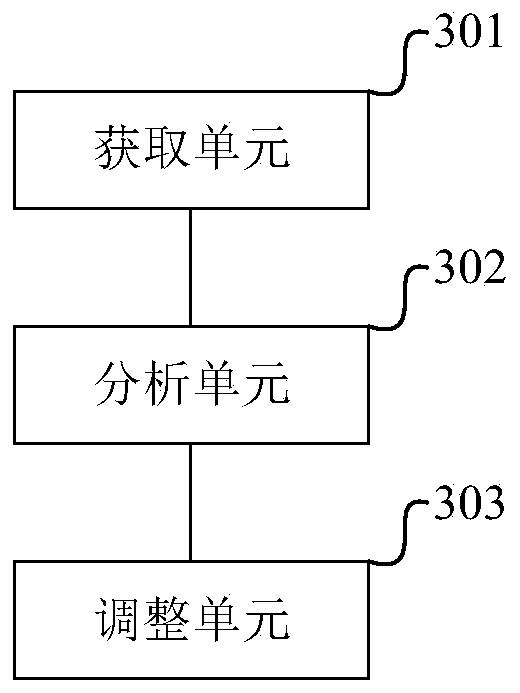
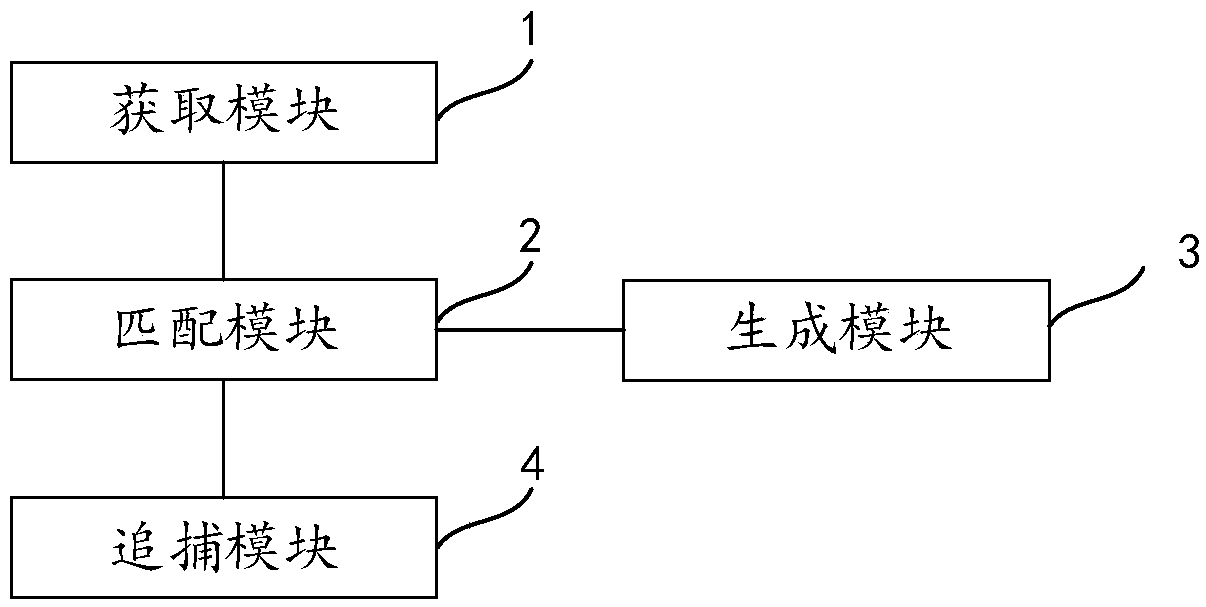
Threat pursuit method, device and equipment in network security defense
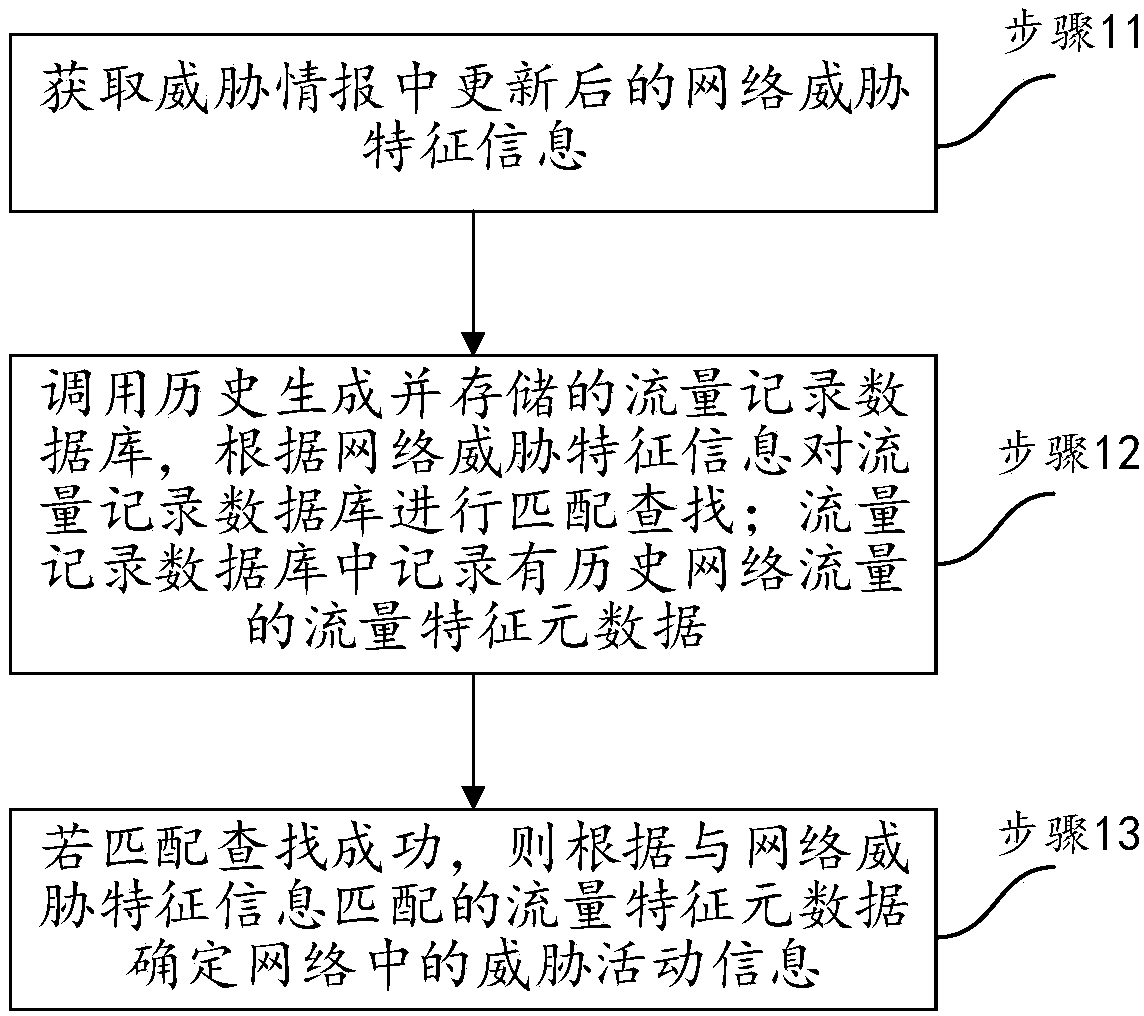
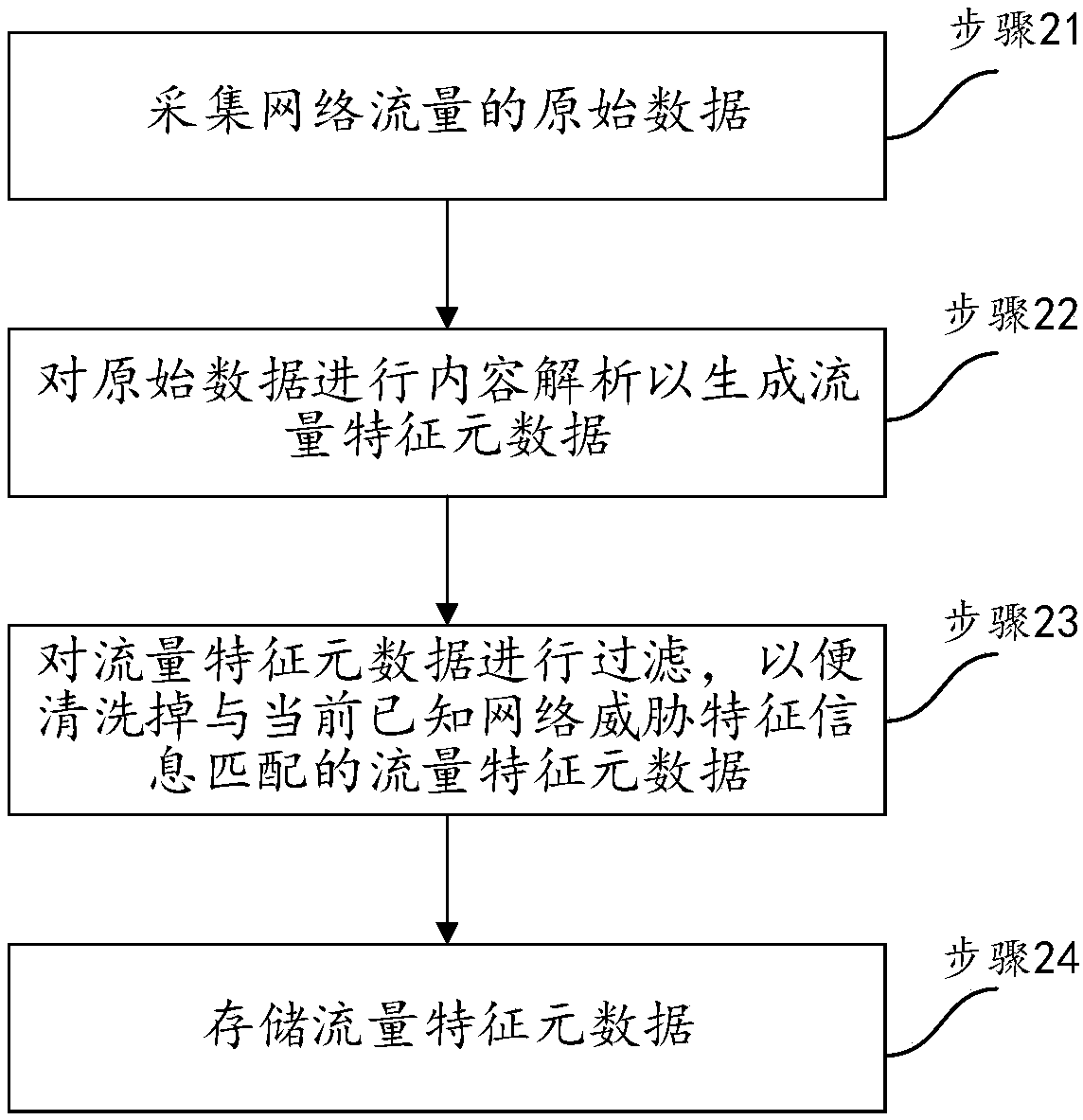
InactiveCN110798429AReduce the possibility of missed detectionEasy to detectTransmissionTraffic characteristicInternet traffic
The invention discloses a threat pursuit method in network security defense. The method comprises the steps of obtaining updated network threat feature information in threat intelligence; calling a flow record database which is generated and stored in history, and performing matching search on the flow record database according to the network threat feature information, wherein traffic characteristic metadata of historical network traffic is recorded in the traffic record database; and if the matching search succeeds, determining threat activity information in the network according to the traffic feature metadata matched with the network threat feature information. According to the invention, the flow record database is established to store the flow characteristic metadata of the network flow, and the backtracking detection is utilized to effectively improve the detection capability for the network threat and enhance the network security defense capability. The invention also disclosesa threat pursuit device and equipment in network security defense and a computer readable storage medium, which also have the above beneficial effects.
Owner:SANGFOR TECH INC
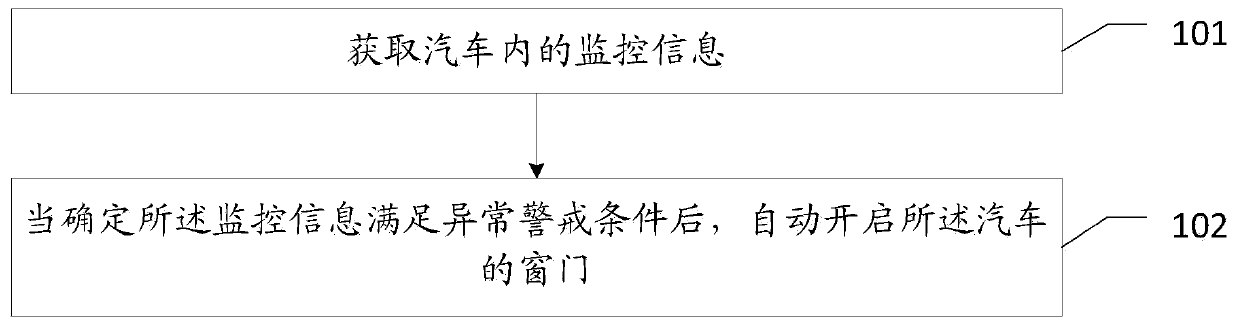
Automobile safety pre-warning method, automobile safety pre-warning device, equipment and storage medium
InactiveCN110341639AImprove security defense performanceRespond accuratelyAcoustic signal devicesPedestrian/occupant safety arrangementAutomobile safetyAtmospheric pressure
The invention relates to the field of automobile visual surveillance intelligent safe-guard system, and provides an automobile safety pre-warning method, an automobile safety pre-warning device, equipment and a storage medium. The method comprises the following steps: obtaining monitoring information inside an automobile, wherein the monitoring information comprises environmental state, video dataand using state of the automobile, the video data comprises moving objects inside the automobile, the moving objects comprise persons and / or animals, the using state of the automobile comprises the condition whether an engine operates and whether windows and doors are locked; after the monitoring information is determined to meet abnormal warning conditions, automatically opening the windows anddoors of the automobile, wherein the abnormal warning conditions comprise one of the following items: the oxygen concentration is lower than preset concentration, the temperature is higher than a first temperature value and lower than a second temperature value, the temperature is higher than the second temperature value, the humidity is lower than a first humidity value, the air pressure is higher than a first air pressure value, the air pressure is higher than a second air pressure value, or the concentration of harmful gas is higher than a warning value. By using the scheme, the occurrenceof unnecessary tragedies can be avoided, and the safety defense performance of the automobile is improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
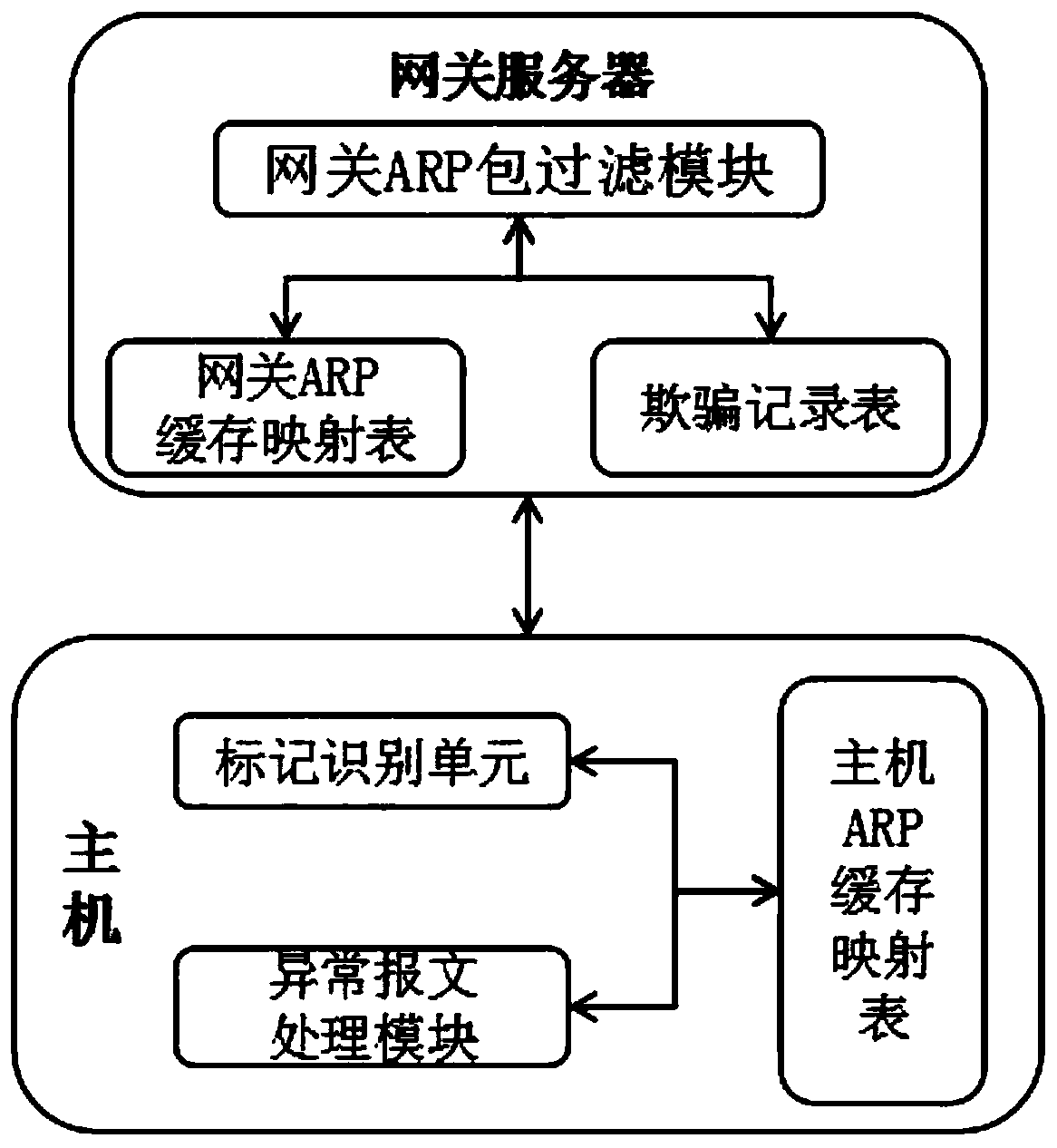
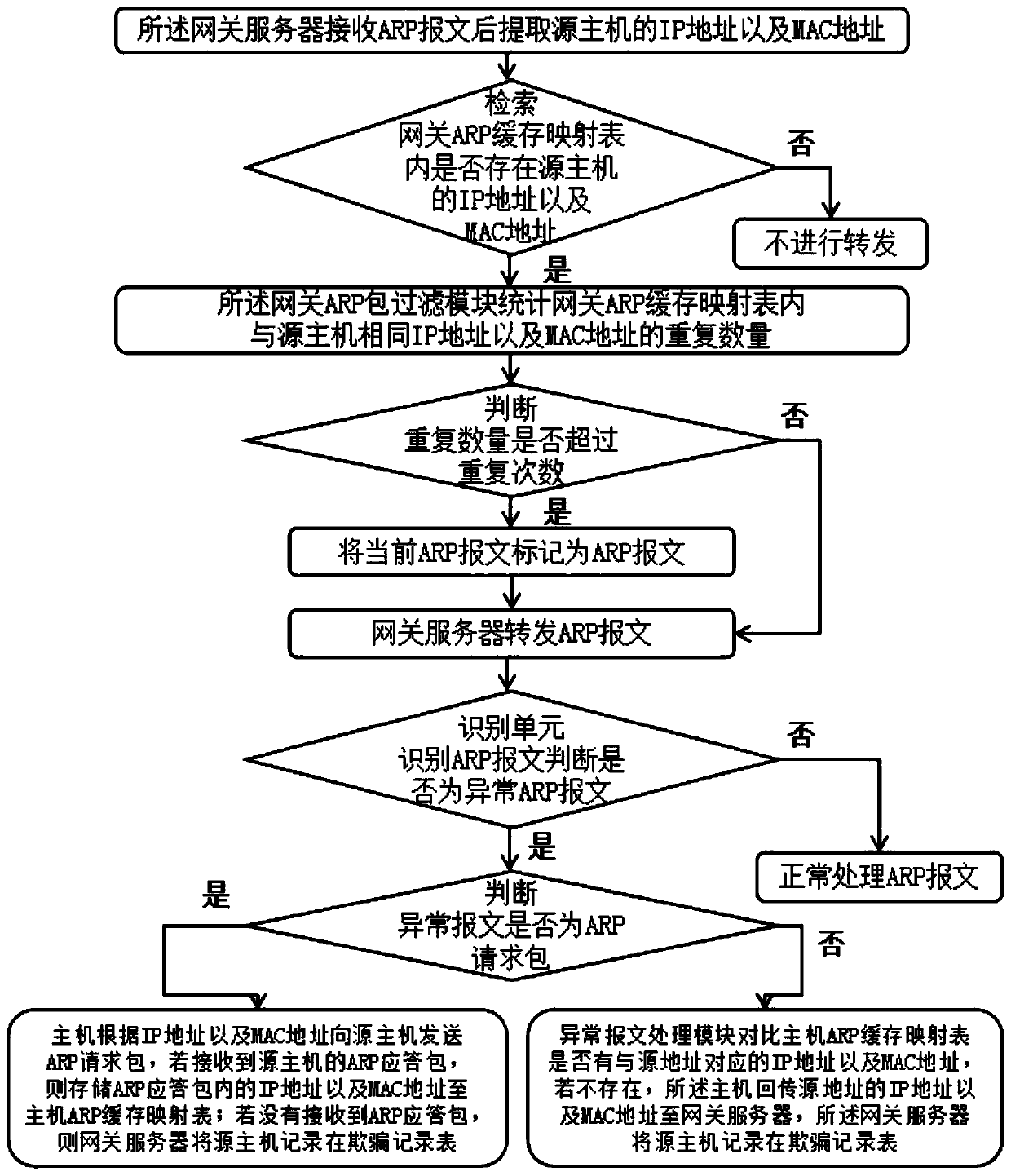
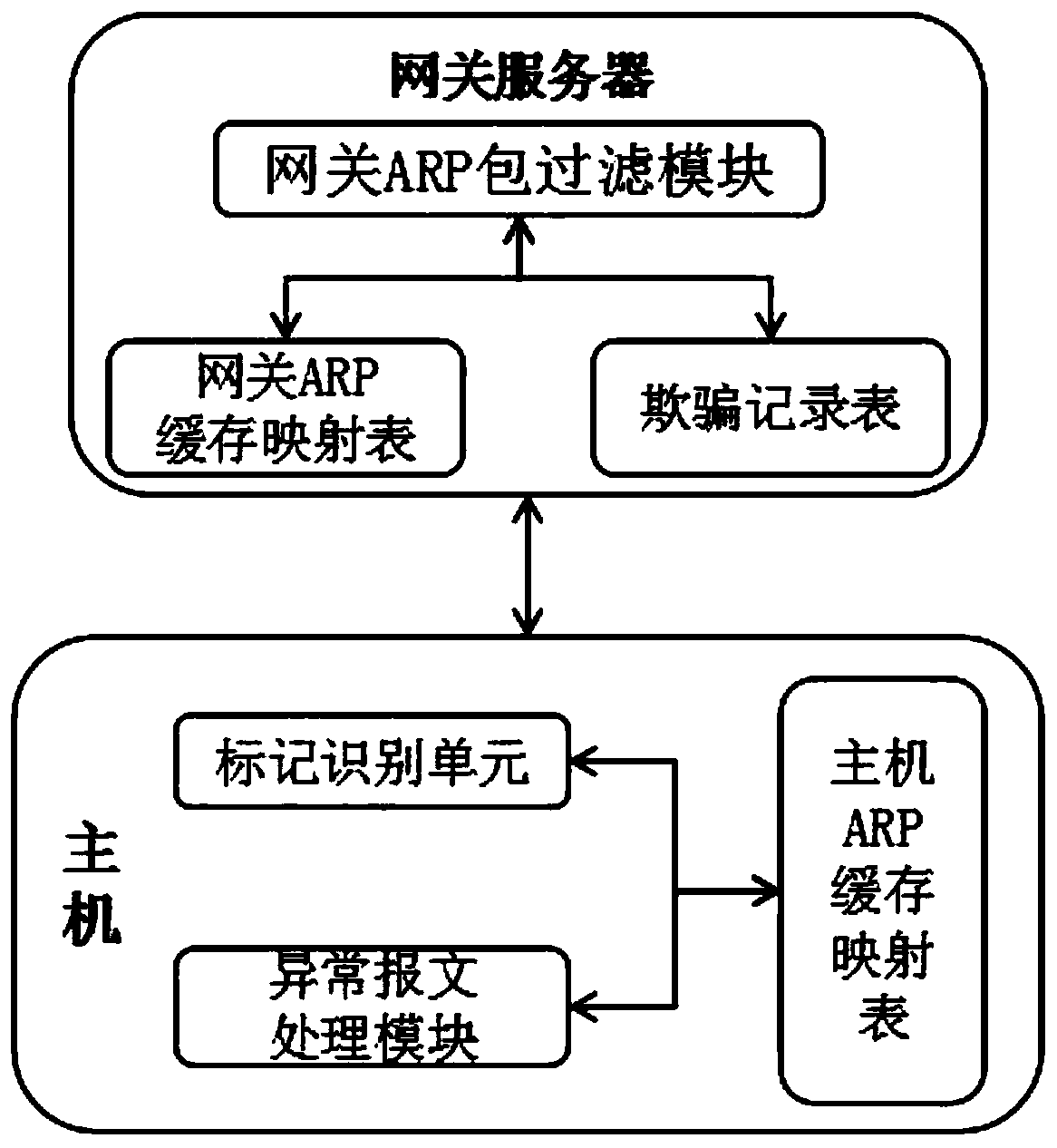
ARP bidirectional defense system and method
The invention discloses an ARP bidirectional defense system and method, and relates to the technical field of ARP defense. The system comprises a gateway server comprising a gateway ARP packet filtering module and a plurality of hosts provided with host ARP packet filtering modules, the plurality of hosts are connected with the gateway server and are used for actively acquiring the gateway MAC ofthe gateway server; a gateway ARP cache mapping table is also arranged in the gateway server; wherein an ARP request packet and an ARP response packet which are sent to the host through the gateway server within a preset time threshold value are stored in the gateway ARP cache mapping table. A gateway ARP packet filtering module is arranged in a gateway server, and whether an IP address and an MACaddress in an ARP message exist in a cheating record table or not is retrieved through the gateway ARP packet filtering module and used for surface monitoring of a malicious attack source host; then,the abnormal ARP message in the ARP message is identified through the gateway ARP packet filtering module and is marked as abnormity, the source host for deceptive attack is efficiently removed, andthe security is improved.
Owner:北京华安普特网络科技有限公司
Object-oriented network attack modeling method and device based on incidence matrix
ActiveCN112491801AImprove security defense performanceEffective analysis methodData switching networksInformation technology support systemPathPingAttack
The invention discloses an incidence matrix-based object-oriented network attack modeling method and device, and the method comprises the steps: describing a communication information network structure and a network attack path through employing an incidence matrix method; and describing the modes and processes of network attacks with an object-oriented method. According to the method, the influence of attack behaviors on a single node or link can be analyzed, and potential vulnerabilities of the single node or link can be found; the method and the process of the network attack and the attackpath in the network can be visually reflected, the vulnerability of the system can be conveniently analyzed by the network security personnel, the attack source and the attack path can be found out, and the network security analysis is promoted to be expanded from a local area network or a smaller network to the whole network, so that the management capability of the network is improved.
Owner:NARI TECH CO LTD +3
Network security protection method and apparatus in uni-direction environment
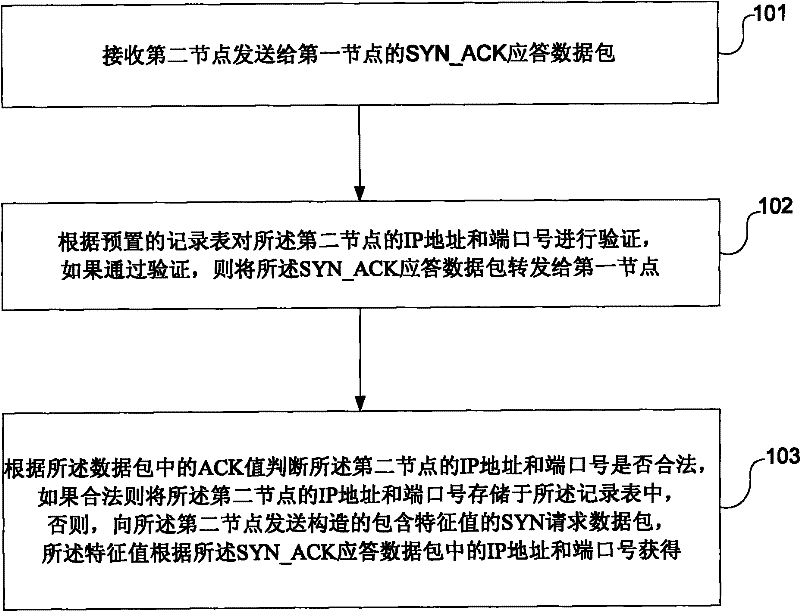
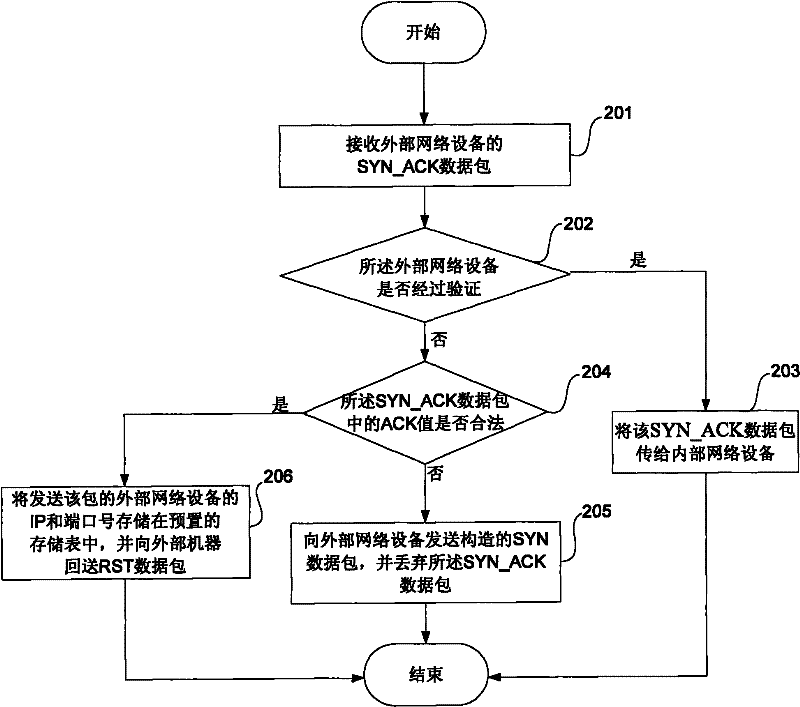
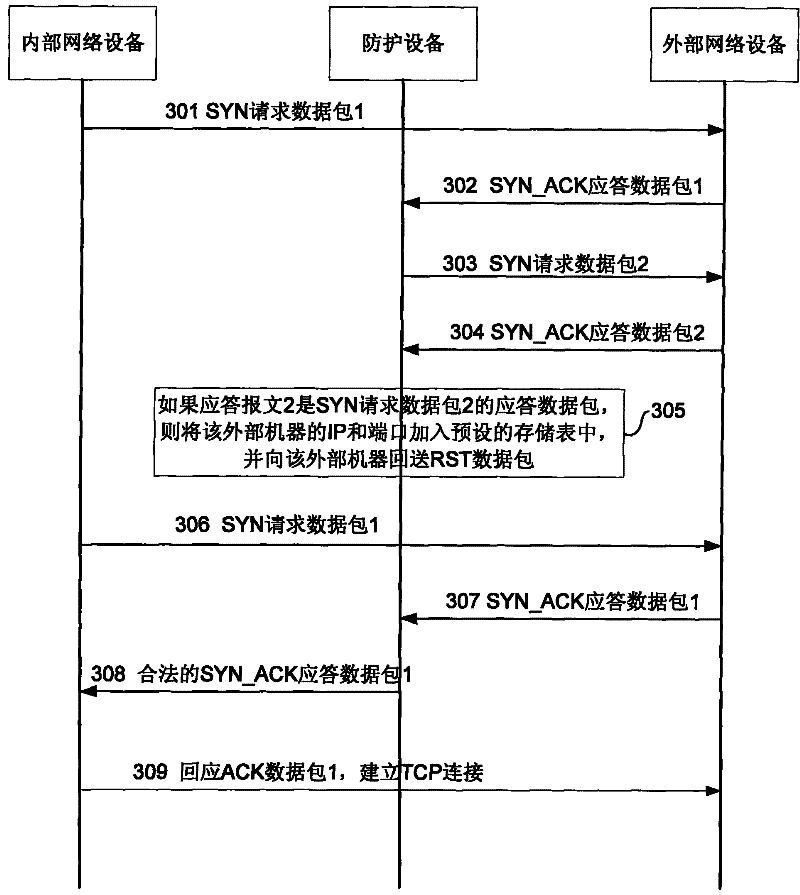
ActiveCN101478537BImprove security defense performanceAvoid attackError prevention/detection by using return channelData switching networksIp addressPacket forwarding
The invention discloses a network safety protection method in a unidirectional environment comprising: receiving SYN_ACK responsion data packet transmitted to a first node by a second node; verifying the second node IP address and port number according to a presetting data sheet, if the verification is passed, transmitting the SYN_ACK responsion data packet to the first node; if the verification is not passed, judging whether the second node IP address and port number are legal according to the ACK value in the SYN_ACK responsion data packet, if legal, storing the second node IP address and port number in the data sheet, else transmitting the structural SYN request data packet containing feature values to the second node to verify the second node. The method effectively stops the SYN_ACK attack to an in-house network appliance from an outer network appliance in the unidirectional environment and improves the network security defense ability in the unidirectional environment.
Owner:CHENGDU HUAWEI TECH
Rotary door type radar imaging security detector
InactiveCN106932831AReduce radiationPrivacy protectionGeological detection using milimetre wavesLow frequency bandEngineering
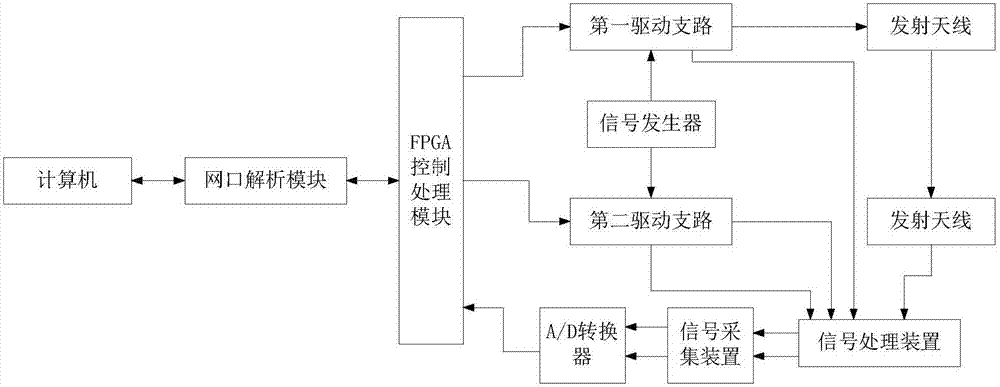
The invention discloses a revolving door radar imaging security inspection device, which includes a radar imaging security inspection system, and the radar imaging security inspection system includes a computer, a network port analysis module, an FPGA control processing module, a first driving branch, and a second driving branch , a signal generator, a transmitting antenna, a receiving antenna, a signal processing device, a signal acquisition device and an A / D converter; the first driving branch and the second driving branch are respectively provided with a first input end, a second input end, a second An output terminal and a second output terminal; the signal processing device is provided with a first input terminal, a second input terminal, a first output terminal and a second output terminal; the signal acquisition device is provided with a first input terminal, a second input terminal, a second input terminal An output terminal and a second output terminal. The invention utilizes the characteristics of low radiation in the millimeter wave frequency band and the ability to penetrate clothing, which is not only suitable for human body security inspection, but also can detect weapons hidden under clothing.
Owner:SICHUAN LAIYUAN TECH CO LTD
A method and platform for trusted environment management and control of industrial control system based on security chip
ActiveCN104573516BGood cryptographic function serviceImprove security defense performanceDigital data protectionPlatform integrity maintainanceOperational systemComputer science
The invention provides an industrial control system trusted environment control method and platform based on a safety chip. The method comprises the steps: (1) registering an industrial control terminal to a management server on the basis of the safety chip; (2) carrying out complete measurement on each operating process by adopting the industrial control terminal; (3) checking the measurement information by the management party on the management server, and forming a white list; (4) downloading the white list formed by the management party from the management server by the industrial control terminal, leading the white list into an operating system core, and then carrying out the control on the process to be operated. By adopting the method and platform, malicious code of an untrusted, unknown and uncontrollable program process is prevented from damaging the system of the industrial control terminal, from stealing the confidential information and damaging the industrial production, so that the safety defense capacity of the industrial control system can be improved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Terahertz time-domain spectroscopy hidden dangerous goods classification method based on fusion of ResNet and LSTM
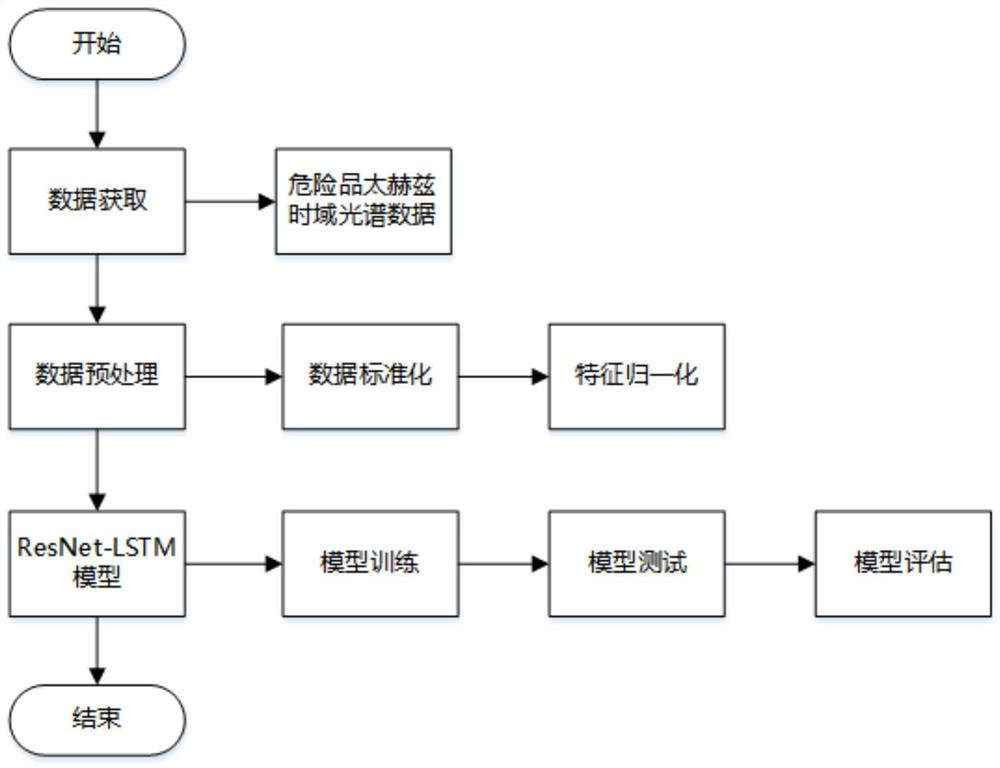
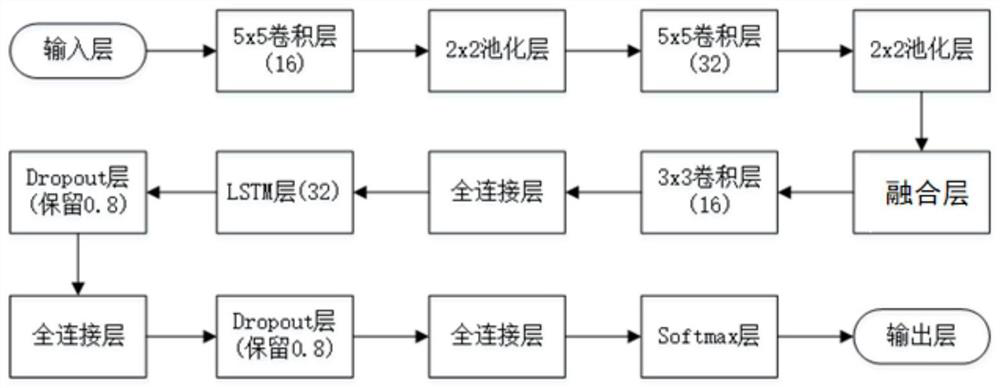
PendingCN113935367AImprove security defense performanceReduce incidenceCharacter and pattern recognitionNeural architecturesTime domainData set
The invention discloses a terahertz time-domain spectroscopy hidden dangerous goods classification method based on fusion of an ResNet and LSTM. The method comprises the following steps: collecting terahertz time-domain spectroscopy data for a dangerous goods sample to construct a data set, and carrying out preprocessing on the data in the data set; and constructing a ResNet-LSTM network model, then training, testing and evaluating the network model by using the preprocessed data set, and finally obtaining a trained network model for real-time classification of dangerous goods. According to the invention, with the combination of passive terahertz human body imaging security inspection equipment and a terahertz time-domain spectroscopy technology, the security defense capability of public places in cities can be obviously enhanced, the occurrence rate of public security incidents is effectively reduced, and the economic loss caused by the incidents is greatly reduced; and the invention is of great significance to maintain social security and stability.
Owner:GUANGDONG UNIV OF TECH
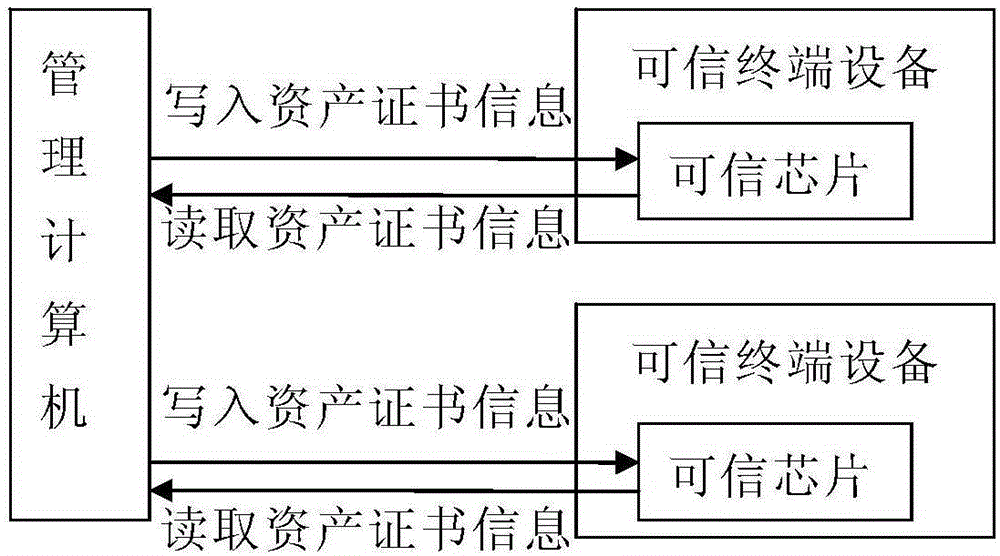
Asset certificate based method for managing trusted terminal device
InactiveCN105184188AFull Reliability GuaranteedImprove security defense performanceDigital data protectionOperational systemUnique device identifier
The present invention provides an asset certificate based method for managing a trusted terminal device. The trusted terminal device is a terminal device comprising a trusted chip; the trusted chip is provided with a nonvolatile memory, and asset certificate information of the trusted terminal device is stored in the nonvolatile memory of the trusted chip of the trusted terminal device; the asset certificate information is attribute information of the trusted terminal device or encrypted attribute information after the attribute information is subjected to encryption; and the attribute information of the trusted terminal device comprises a unique device identification number, owner information, a start use time, user information, a use period, configuration information and the like. According to the asset certificate based method for managing the trusted terminal device provided by the present invention, the asset certificate information of the trusted terminal device is stored in the nonvolatile memory of the trusted chip, so that the asset certificate information is not liable to be lost; and even if an operating system of the terminal is reinstalled, a write operation can be performed on the asset certificate information only by inputting a correct operation password, so that completeness and reliability of the asset certificate information can be ensured.
Owner:GOHIGH DATA NETWORKS TECH CO LTD +1
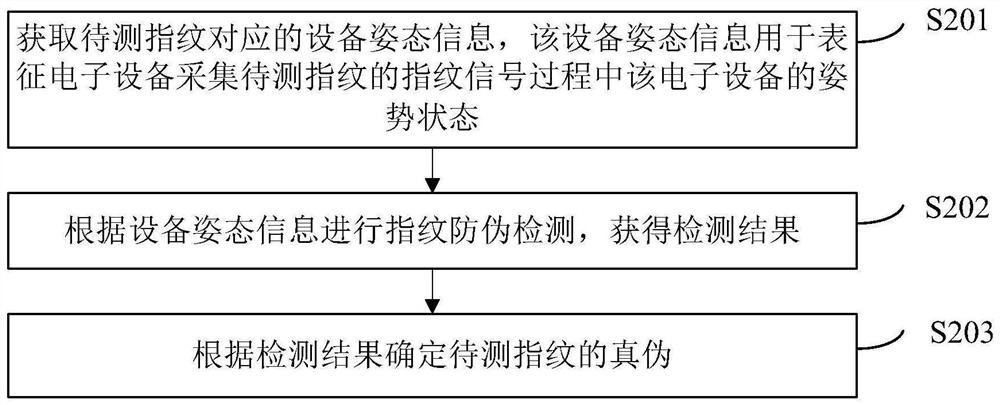
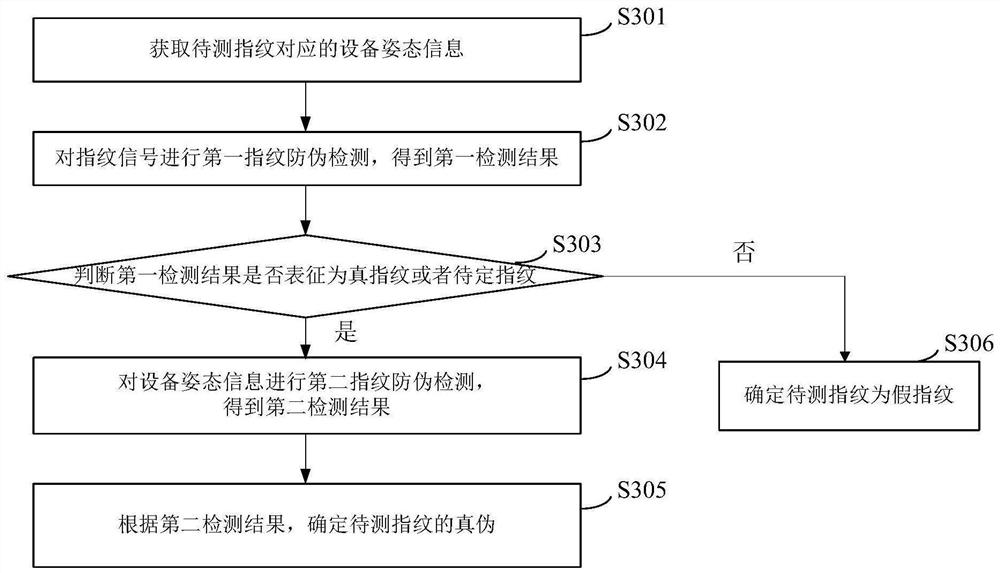
Fingerprint anti-counterfeiting detection method and device and electronic equipment
PendingCN113591571AIncrease the difficultyImprove security defense performanceCharacter and pattern recognitionDigital data authenticationArtificial intelligenceReliability engineering
The invention provides a fingerprint anti-counterfeiting detection method and device and electronic equipment. The method comprises the steps of acquiring equipment posture information corresponding to a fingerprint to be detected, wherein the equipment posture information is used for representing the posture state of the electronic equipment in the process that the electronic equipment collects a fingerprint signal of the fingerprint to be detected; performing fingerprint anti-counterfeiting detection according to the equipment posture information to obtain a detection result; and determining the authenticity of the fingerprint to be detected according to the detection result. Anti-counterfeiting detection is carried out on the fingerprint by using the equipment attitude information, so that the detection capability of the false fingerprint is enhanced, the difficulty of an attacker using the false fingerprint to carry out operation is improved, and the equipment security defense capability is effectively improved.
Owner:BEIJING JIIOV TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com