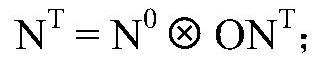Object-oriented network attack modeling method and device based on incidence matrix
A correlation matrix and network attack technology, applied in the field of network security, can solve problems such as ambiguous meaning and narrow application
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0083] The present invention provides an object-oriented network attack modeling method based on an association matrix, comprising:
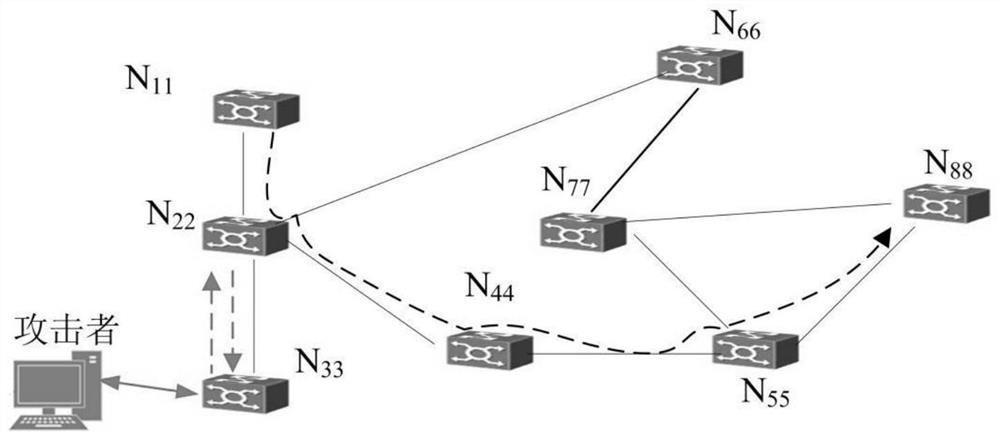
[0084] Abstract the nodes and communication links in the communication information network; and abstract the network attack behavior;
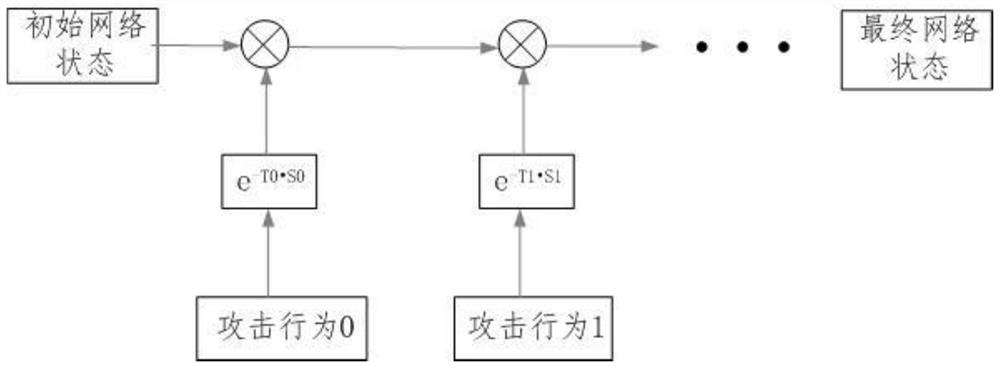
[0085] According to the topological structure of the communication information network, an association matrix of communication network objects is established based on abstract nodes and communication links. Each element in the association matrix is composed of a state space containing attribute vectors and method vectors of nodes / communication links; and, according to the network The target of the attack behavior and the path of the communication information network through which the attack data packet passes establish an attack behavior object correlation matrix, and each element in the correlation matrix is composed of a state space including the attack behavior attribute vector and method vector;
[0086]...
Embodiment 2
[0130] The present invention also provides an object-oriented network attack modeling device based on an association matrix, including:
[0131] The initialization module is used to abstract the nodes and communication links in the communication information network; and to abstract the network attack behavior;
[0132] The modeling module is used to establish a communication network object association matrix based on abstract nodes and communication links according to the topological structure of the communication information network; and, based on the abstract Network attack behavior establishes an attack behavior object correlation matrix;
[0133] as well as,
[0134] The matching module is used to match the elements in the communication network object correlation matrix and the attack behavior object correlation matrix one by one to obtain the communication information object state matrix after the network attack.
[0135] Further, the initialization module is specifical...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com