Defense method and device, client, server, storage medium and system
A client and server technology, applied in the field of network security, can solve problems such as inability to protect network equipment, bypass or attack
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
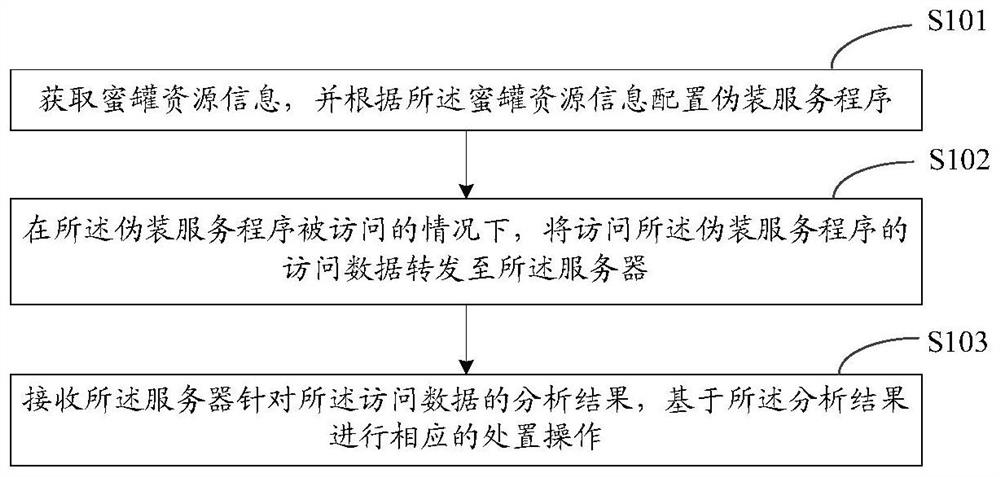
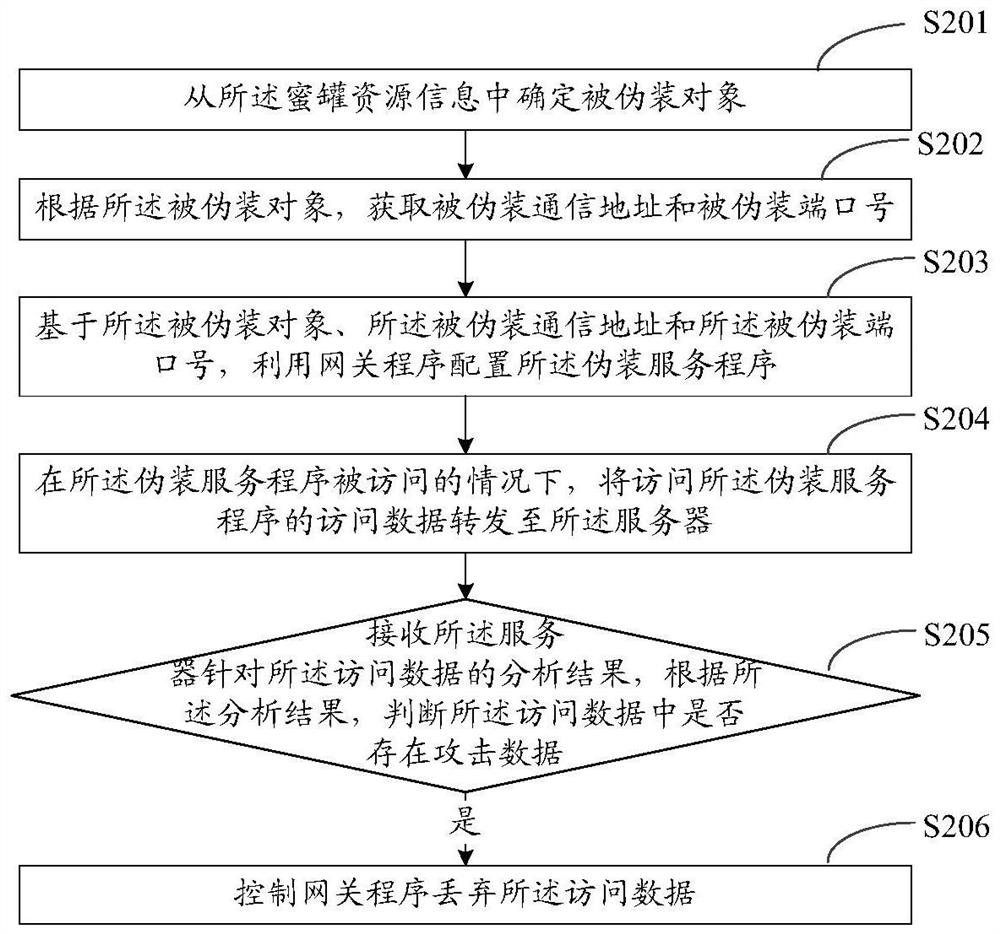
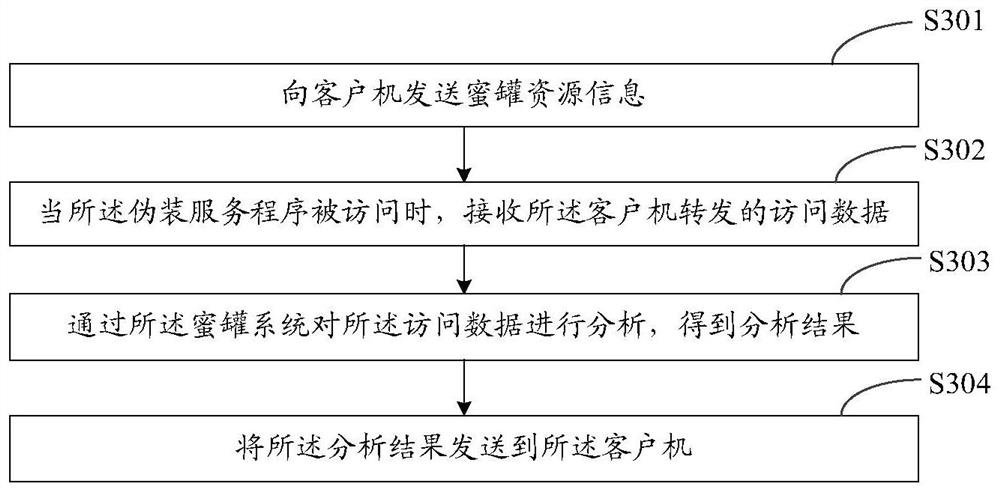
[0051] The technical solutions in the embodiments of the present application will be clearly and completely described below in conjunction with the drawings in the embodiments of the present application.
[0052] Terms involved in the embodiments of the present application are explained as follows.
[0053] Honeypot (or called honeypot network, honeypot technology): It is a virtual system or network specially used to lure hackers (or called attackers), and the honeypot can discover, save and analyze the information left by hackers on the computer system. and track their whereabouts at any time, so as to understand the latest technologies and working ideas used by hackers. By obtaining this information, you will better understand the threats encountered by the system and think about how to prevent these threats, so as to gain the greatest initiative in the war against hackers.
[0054] Next Generation Firewall (NG Firewall): It is a high-performance firewall that can comprehen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com