A Server Hardening Method Based on File Access Control and Process Access Control
A technology of access control and file access, applied in the fields of instruments, electrical components, digital data authentication, etc., can solve the problem of "difficult connection", and achieve the effect of protection security, high performance and security, and good compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
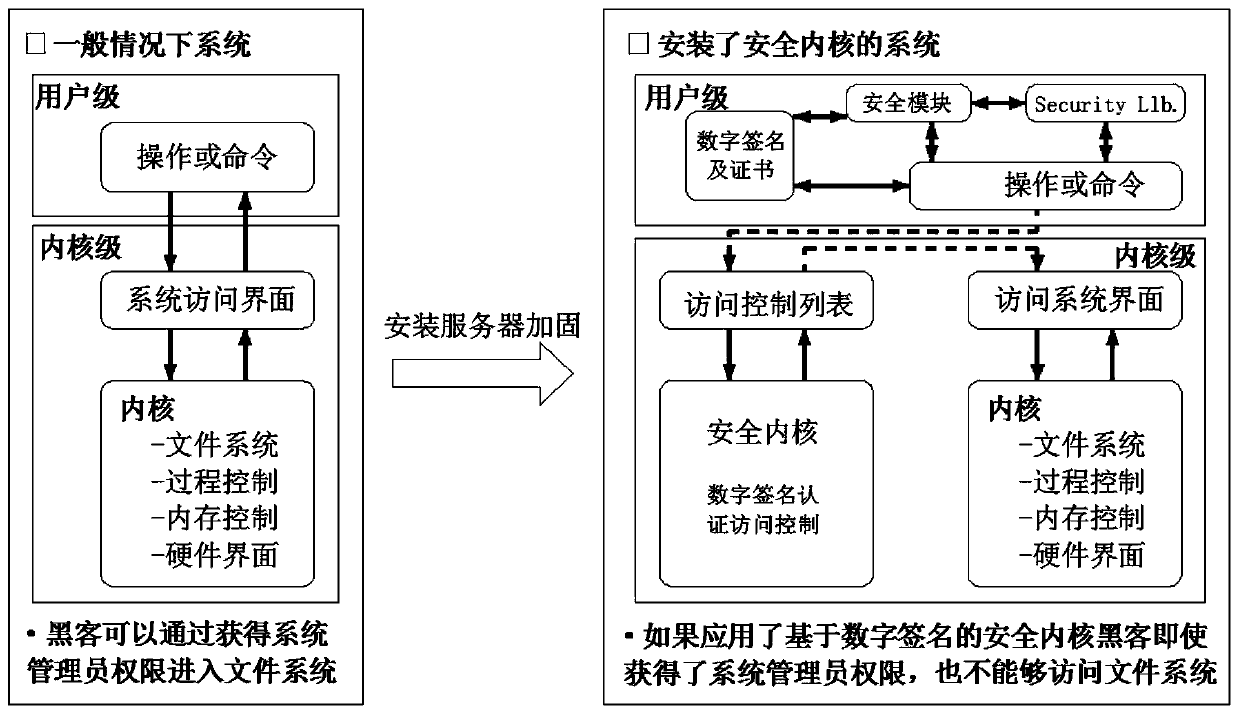
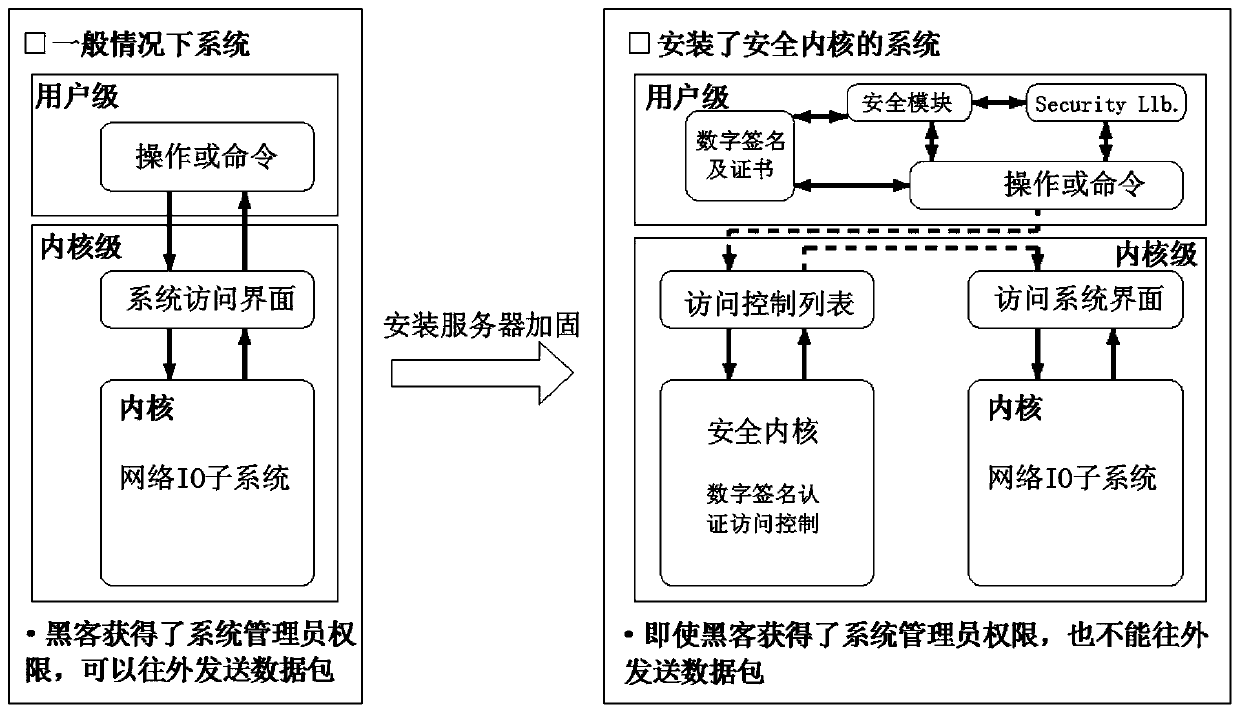
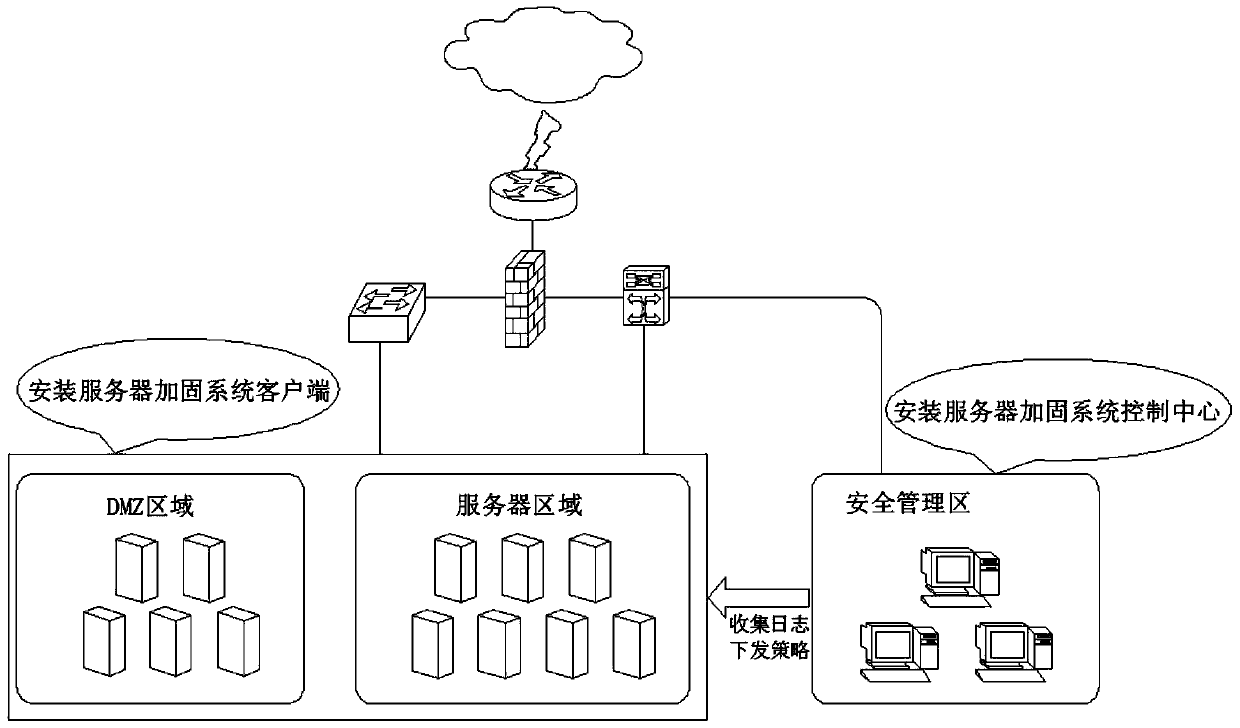
[0035] In the embodiment of the present invention, a server hardening method based on file access control and process access control uses a server hardening device to harden the server, making the system a system with a security kernel installed. The server hardening device includes dual identity authentication Module, USB peripheral control module, registry access control module, network control module, process protection mechanism module, sensitive data access control module, system self-protection module, the functions of each module are as follows: dual identity authentication module, users use USB Key In the way of dual ID card and password, you can log in only by inserting the USB Key and entering the correct password, otherwise you cannot log in; the USB peripheral control module disables the USB storage device and prohibits its use without authorization, but does not affect the non-USB storage device Its normal use; the registry access control module monitors registry a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com