Software behavior credibility detecting method based on state transition diagram
A state transition diagram and detection method technology, applied in the field of information security, can solve problems such as complex models, low practicability, and overall security detection of difficult target software, and achieve real-time monitoring, simple operation, and clear layers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0038] Attached below figure 1 Specifically introduce the steps of the implementation method of the present invention:
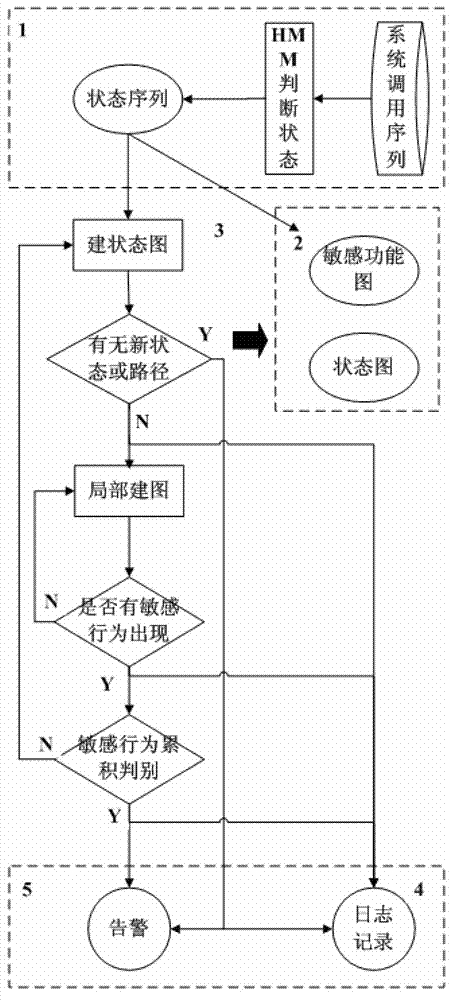
[0039] See attached figure 1 , the invention is a software behavior credibility detection scheme based on a state transition diagram. The detection system is divided into five modules: 1. Data preprocessing module, 2. State diagram training module, 3. Behavior detection module, 4. Real-time monitoring module, 5. Abnormal alarm module. The detection process is as follows:
[0040] First, the data preprocessing module intercepts the system calls of the running software, digitizes them, and then uses the hidden horse model to transform the system call sequence into a state sequence of multiple call combinations.
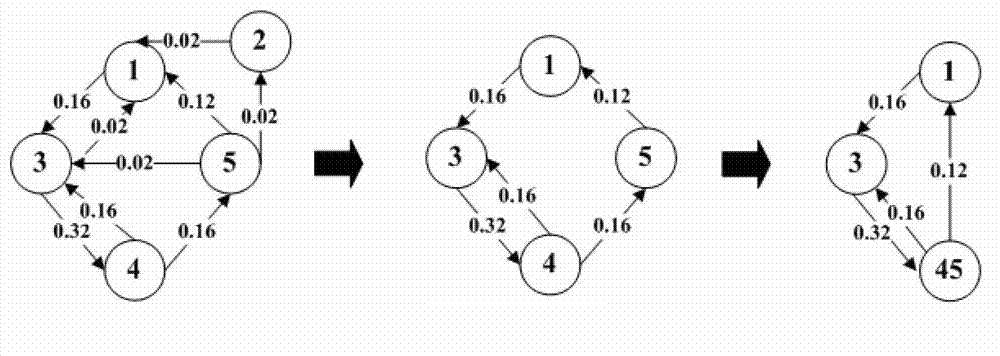
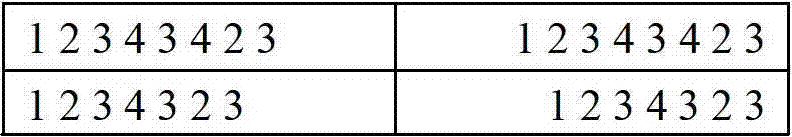
[0041] Then the state sequence is sent to the behavior detection module, and the state sequence is grouped into a state graph, for example, a string of state sequences 1343452134345313445134345134345134345134345, the process of building a graph is a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com