Attack tree model based Android software hybrid detection method
A detection method and attack tree technology, applied in the field of mobile security, can solve problems such as hard-to-cover state, unexecuted malicious code segment, and inability to analyze program behavior, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] Specific embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings. If there are exemplary contents in these embodiments, they should not be construed as limiting the present invention.
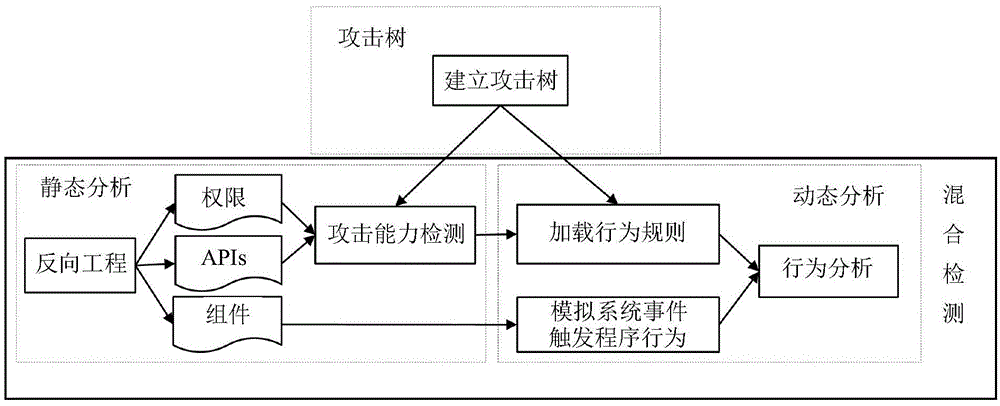
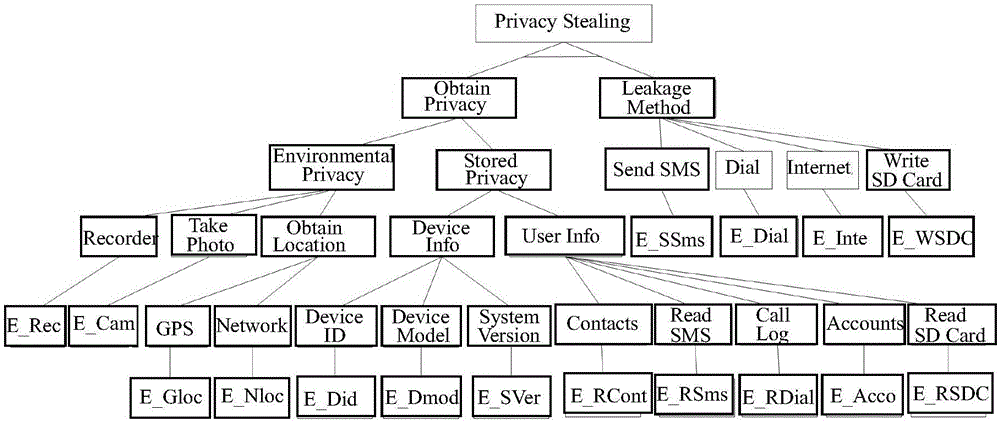
[0022] Such as figure 1 Shown is the overall framework of the Android software hybrid detection method based on the attack tree model of the present invention. Establish an attack tree model before the actual detection, use the attack tree model to analyze various malware attack types, establish the connection between the attack target and the basic capabilities of the software, and formulate a series of dynamic behavior detection rules for each attack path; The static analysis process extracts program permissions, API, and component information. The former two are used for software attack capability detection, and the latter is used for behavior triggering in dynamic analysis; dynamic analysis selects runtime detection points ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com