Method for extracting operation sequence of software vulnerability characteristics
A software vulnerability and operation sequence technology, applied in the field of information security, can solve the problems of large redundancy of operation sequences, ineffective utilization, and lowering the efficiency of software vulnerability analysis, so as to overcome a lot of repetitive work, reduce mining time, and reduce search effect of space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] The technical solutions of the present invention will be described in detail below in conjunction with specific embodiments.
[0060] Concrete operation steps of the present invention are as follows:
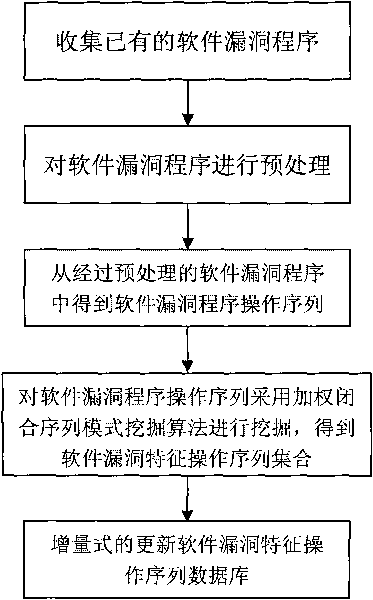
[0061] Step 1. Collect existing software vulnerability programs
[0062] Collect existing software vulnerability programs, such as buffer overflow, format string, integer overflow, etc., and store them in the database in the form of documents;
[0063] Step 2. Preprocess the software vulnerability programs collected in step 1, and filter out the function blocks and statements irrelevant to the software vulnerability analysis in the software vulnerability programs, such as the database name, database path, function call list, various string information;
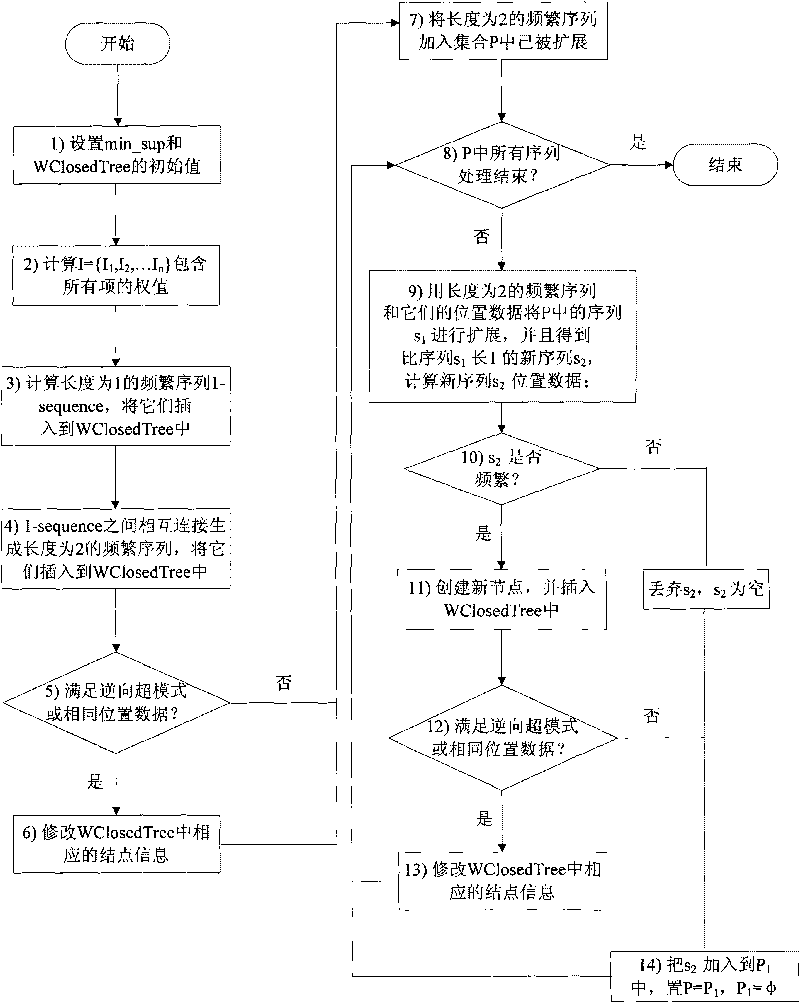
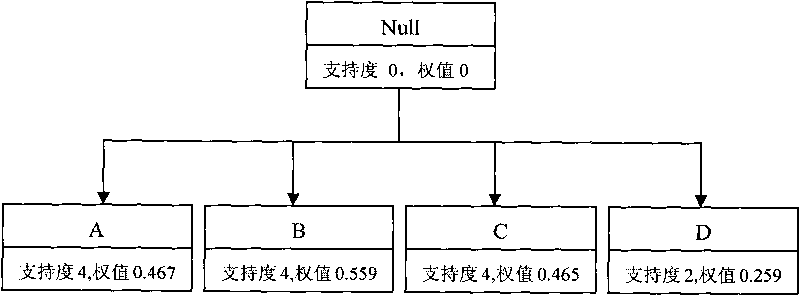
[0064] Step 3, obtain the software vulnerability program operation sequence from the software vulnerability program preprocessed in step 2, and its specific operation steps are as follows:
[0065] Step 1: Load the vul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com